Method for intercepting business object and browser client
A browser client and business object technology, applied in the network field, can solve problems such as inability to intercept business objects, and achieve the effect of effective interception, wide interception range, and workload reduction.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
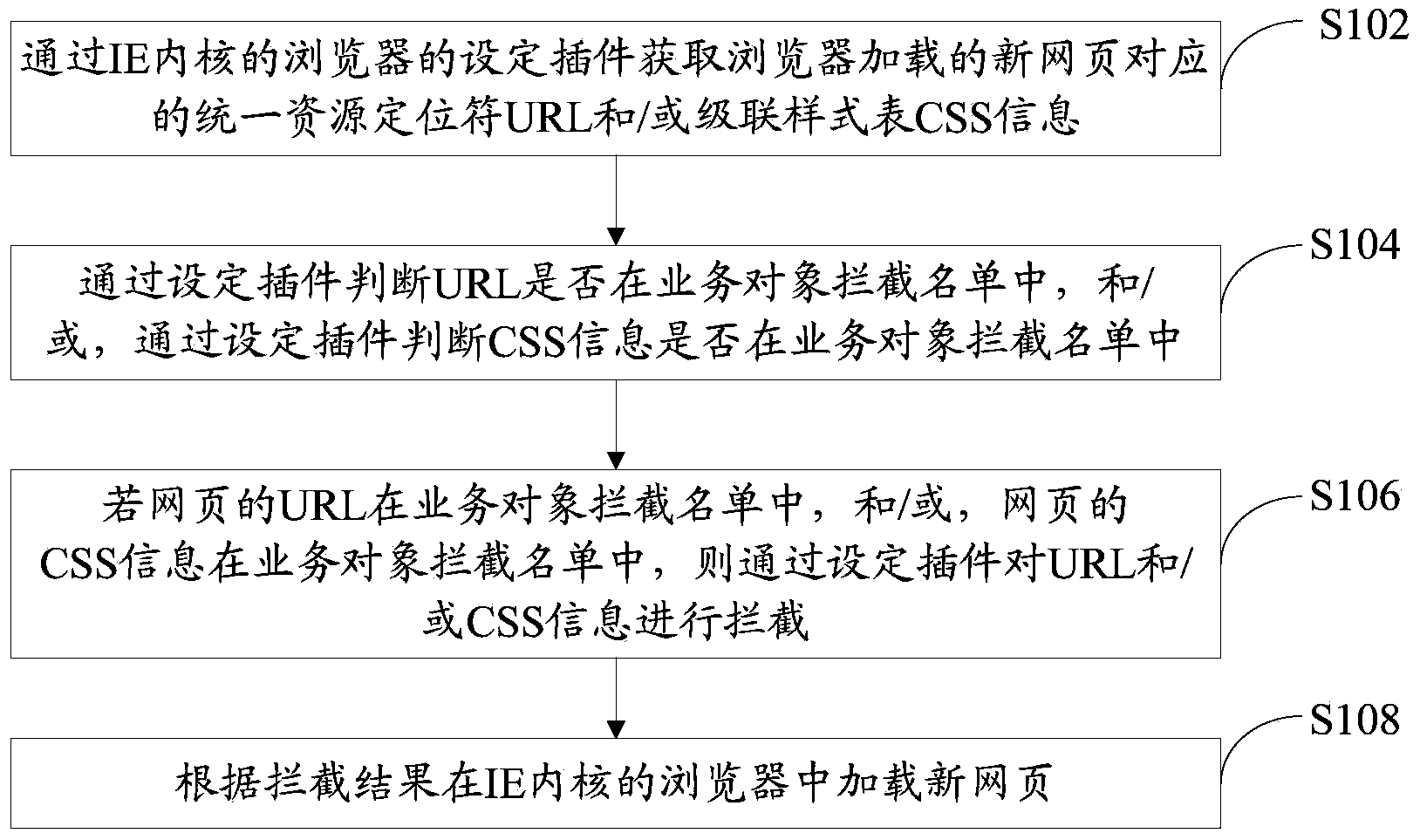
[0025] refer to figure 1 , shows a flow chart of steps of a method for intercepting a business object according to Embodiment 1 of the present invention.
[0026] In this embodiment, the method for intercepting business objects of the present invention is described from the browser side, and the method for intercepting business objects in this embodiment includes the following steps:
[0027] Step S102: Obtain the URL and / or CSS information corresponding to the new webpage loaded by the browser through the browser setting plug-in of the IE core.
[0028] In this embodiment, the configuration plug-in is injected into the browser of the IE kernel by an application program independent of the browser through BHO (Browser Helper Objects, browser helper objects).
[0029] It should be noted that, in the actual operation process, those skilled in the art can set to obtain only the URL or CSS information of the webpage when obtaining the information corresponding to the new webpage, ...
Embodiment 2
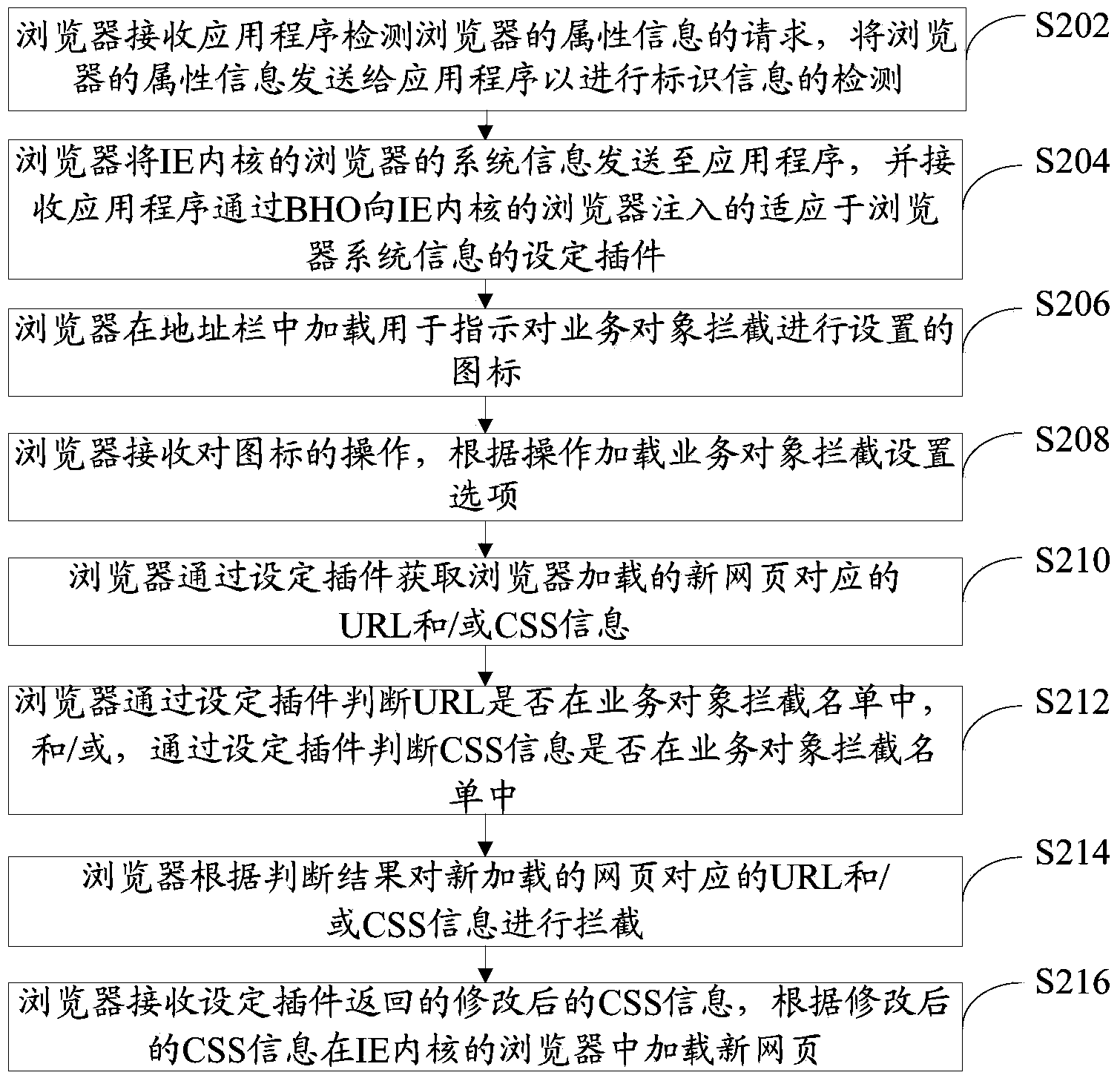
[0038] refer to figure 2 , shows a flow chart of steps of a method for intercepting a business object according to Embodiment 2 of the present invention.
[0039] The method for intercepting a business object in this embodiment is realized by injecting a setting plug-in into the browser of the IE kernel. The method for intercepting a business object of the present invention will be described below from the side of the IE kernel browser.
[0040] The method for intercepting business objects in this embodiment specifically includes the following steps:
[0041] Step S202: The browser receives the application program's request to detect the browser's attribute information, and sends the browser's attribute information to the application program to detect the identification information.
[0042] The browser in this embodiment is a browser with an IE kernel. Wherein, the request is used for the application program to detect whether there is identification information in the prop...
Embodiment 3
[0072] refer to image 3 , shows a flow chart of steps of a method for intercepting a business object according to Embodiment 3 of the present invention.
[0073] In this embodiment, the interception of the business object is carried out by the setting plug-in injected into the browser of the IE kernel by the application program. The method for intercepting the business object of the present invention will be described below from the application program side. The method includes the following steps:
[0074] Step S302: The application program registers and sets the plug-in with the system.
[0075] After the application program generates a setting plug-in of a version matching the browser version for the browser with the IE kernel, it will register the setting plug-in with the system. After the registration is successful, the system generates identification information uniquely identifying the identity of the setting plug-in for the setting plug-in in the registry, for exampl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com