Patents
Literature
129 results about "Tree traversal" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
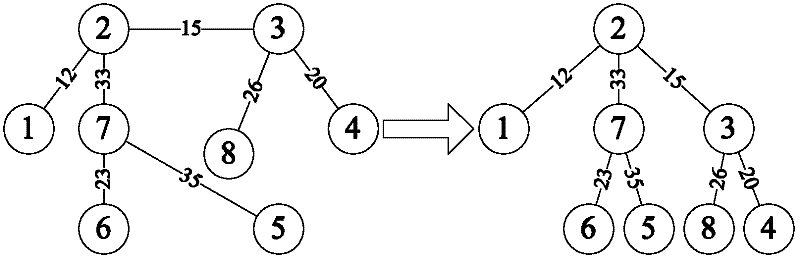
In computer science, tree traversal (also known as tree search) is a form of graph traversal and refers to the process of visiting (checking and/or updating) each node in a tree data structure, exactly once. Such traversals are classified by the order in which the nodes are visited. The following algorithms are described for a binary tree, but they may be generalized to other trees as well.
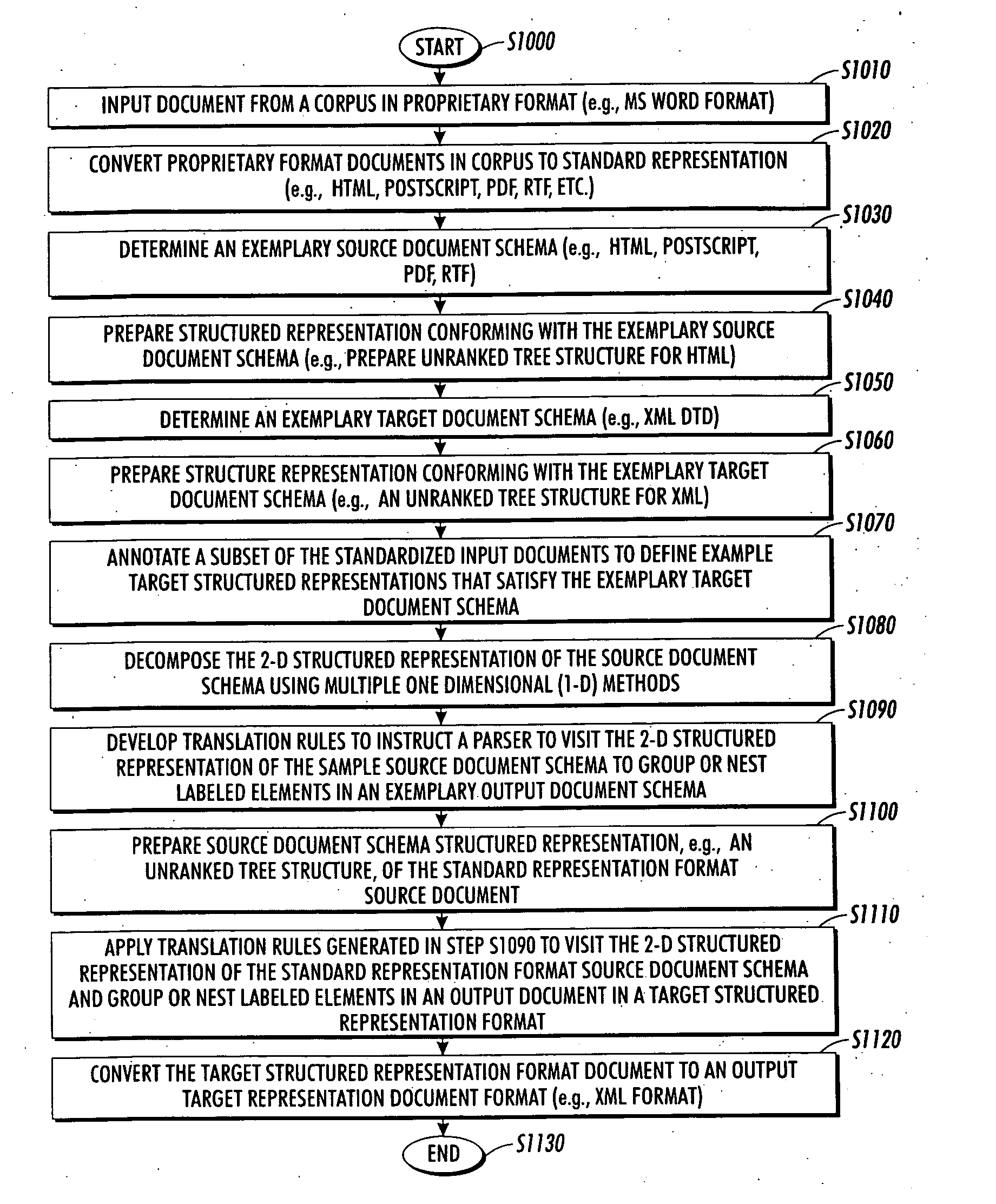
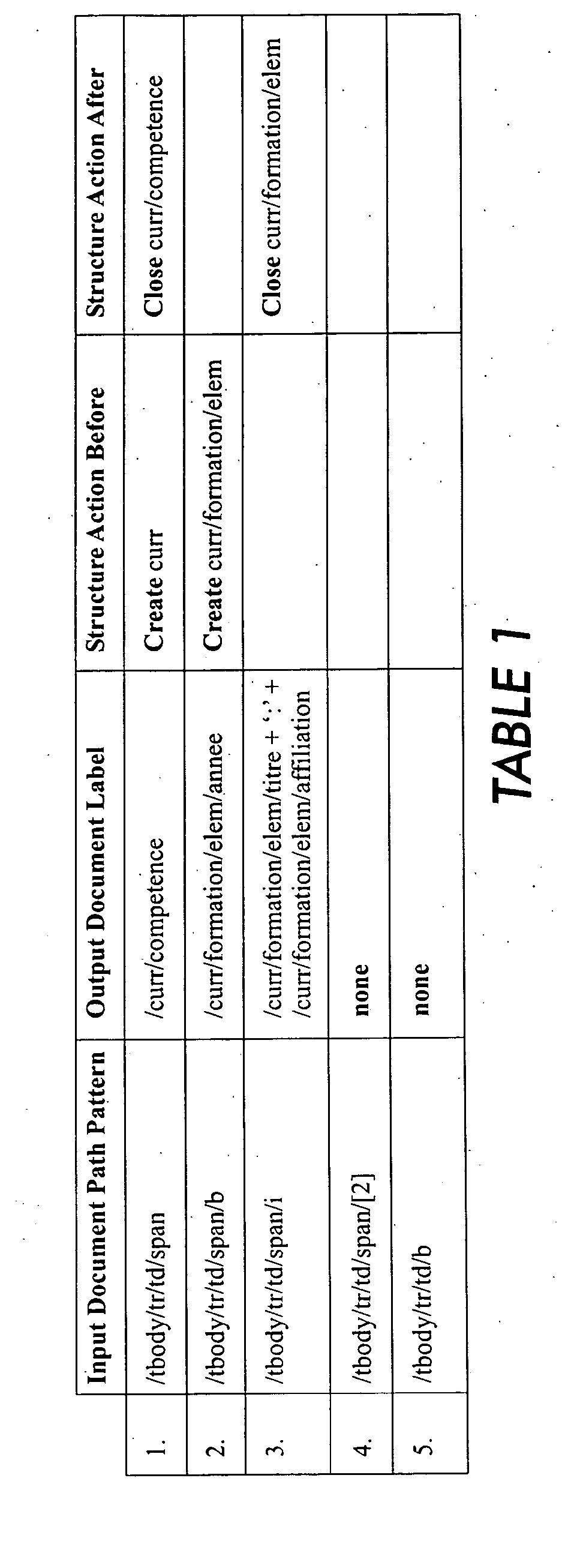
Systems and methods for converting legacy and proprietary documents into extended mark-up language format
InactiveUS20050154979A1Reduce learningNatural language data processingSemi-structured data mapping/conversionTree traversalTransformer
A system and method that converts legacy and proprietary documents into extended mark-up language format which treats the conversion as transforming ordered trees of one schema and / or model into ordered trees of another schema and / or model. In embodiments, the tree transformers are coded using a learning method that decomposes the converting task into three components which include path re-labeling, structural composition and input tree traversal, each of which involves learning approaches. The transformation of an input tree into an output tree may involve labeling components in the input tree with valid labels or paths from a particular output schema, composing the labeled elements into the output tree with a valid structure, and finding such a traversal of the input tree that achieves the correct composition of the output tree and applies structural rules.
Owner:XEROX CORP
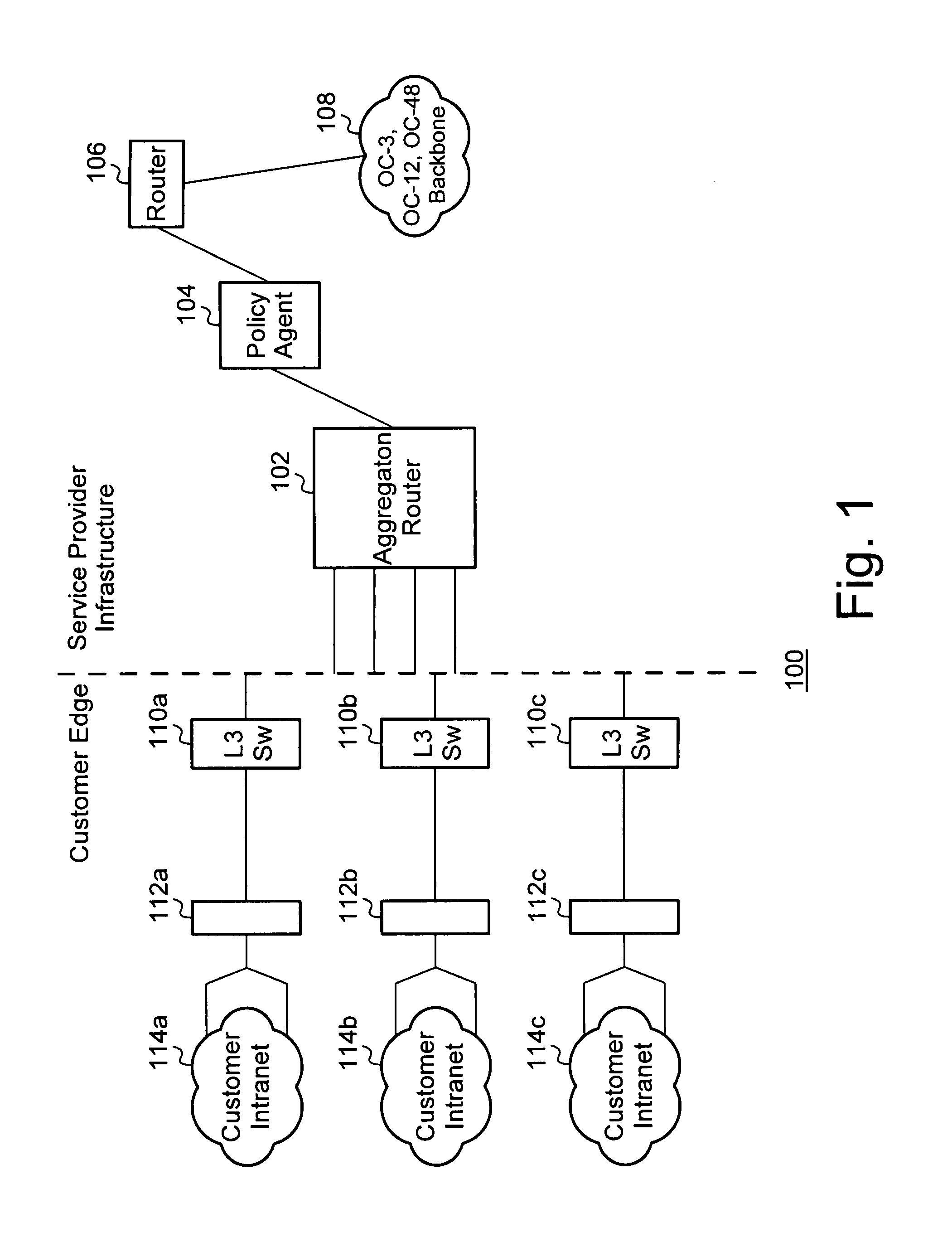
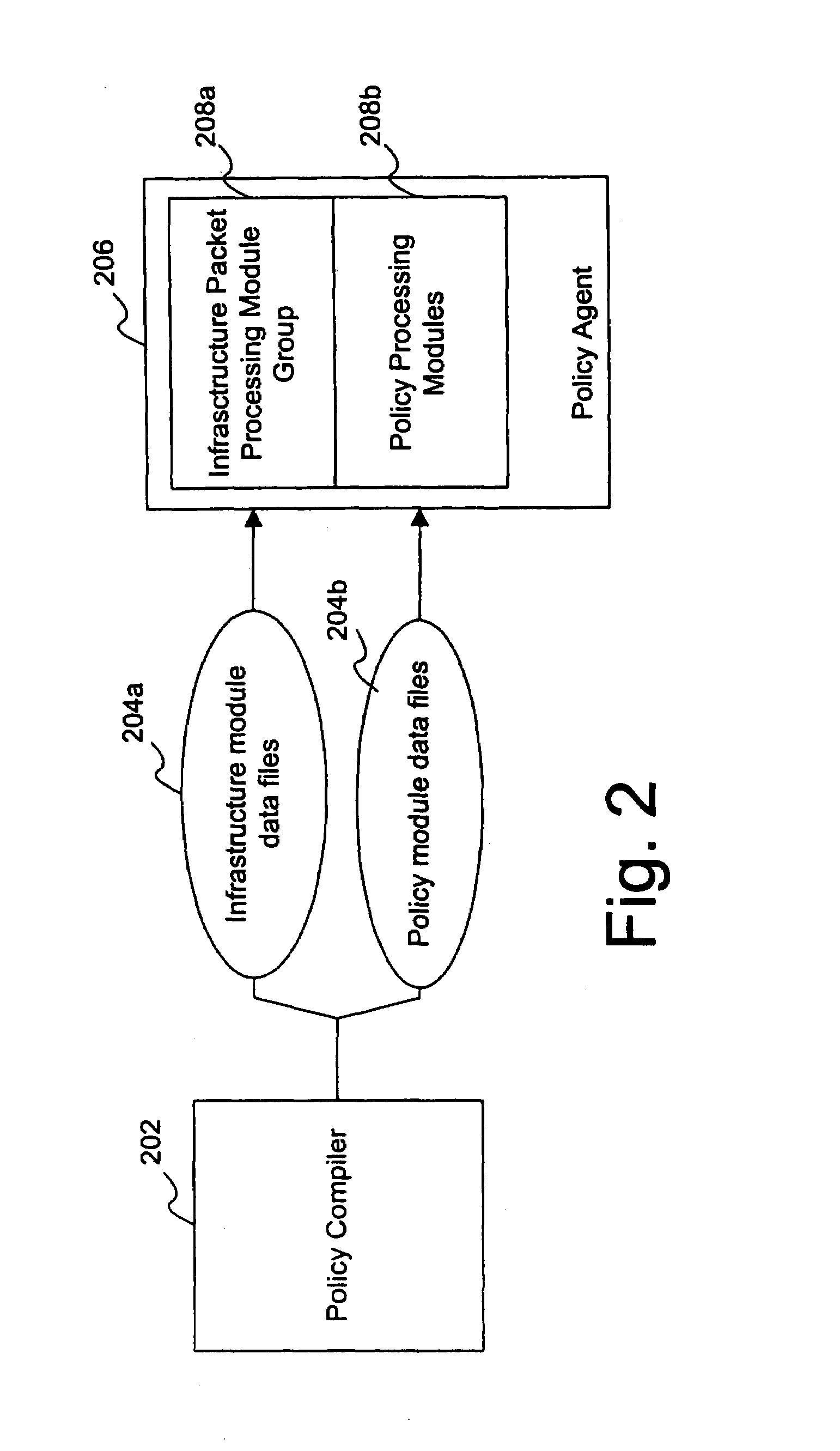
Architecture for an integrated policy enforcement system
InactiveUS7257833B1Increase enforcementHigh-speed performanceSpecial data processing applicationsSecuring communicationTree traversalPolicy enforcement
Enforcing a plurality of different policies on a stream of packets is disclosed. In lieu of running separate algorithms for each policy, the system exploits the commonalities of all of the policies. The conditions corresponding to the compiled rules are arranged in a condition tree and processed in a pipelined architecture that allows the results of the various stages to be carried forward into subsequent stages of processing. The rules for which all conditions have been satisfied can be identified by one stage of processing in one pass of condition tree traversal and are passed to subsequent stages. A rule table corresponding to an individual policy type can then be readily examined to determine partial or complete satisfaction of the rule of that policy type, without requiring a re-examination of the conditions underlying the rule. Additionally, corresponding actions can be taken where rule satisfaction is determined. This approach allows extremely high-speed policy enforcement performance.
Owner:TECH MAHINDRA INDIA
Optimization of a binary tree traversal with secure communications
InactiveUS20040134984A1Improve securityData switching detailsMemory record carrier reading problemsSecure communicationTree traversal
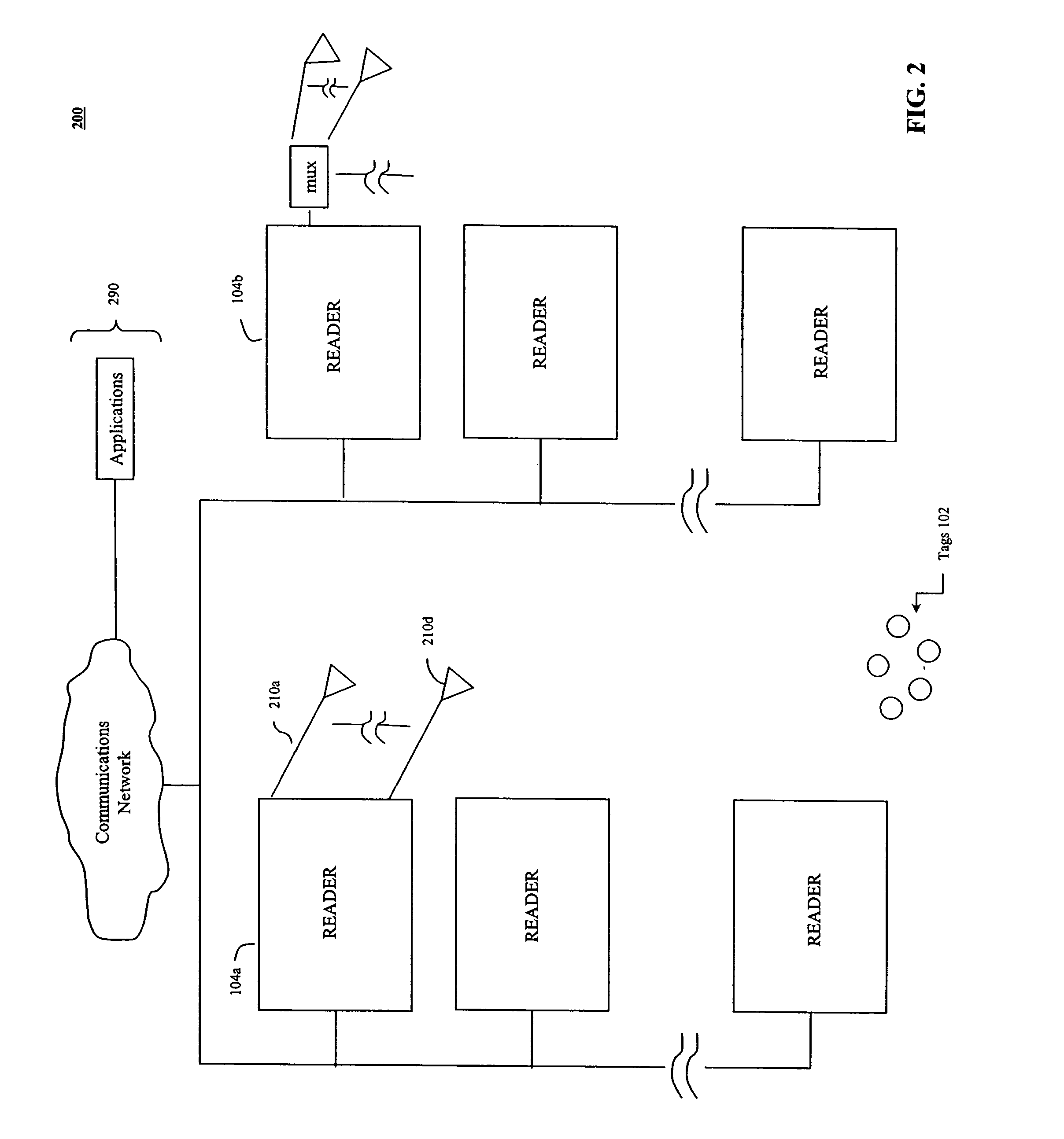
Methods and systems for the negotiation of a population of RFID tags with improved security is provided. In one aspect, a binary traversal is performed to singulate tags without using information that directly identifies the tags in the tag population. A key is generated to identify each RFID tag of the population of RFID tags. The generated key does not include bits identifying an item with which the particular RFID tag is associated. A binary tree algorithm is operated to identify one or more tags in the population of RFIDs tags using the generated keys. In another aspect, frequency hopping and / or spread spectrum techniques are used to provide improved security while negotiating tags. In another aspect, the reader causes the tags to scroll series of bits back to the reader for each bit sent to the tags to provide improved security.
Owner:SYMBOL TECH INC
Tree data structures based on a plurality of local coordinate systems
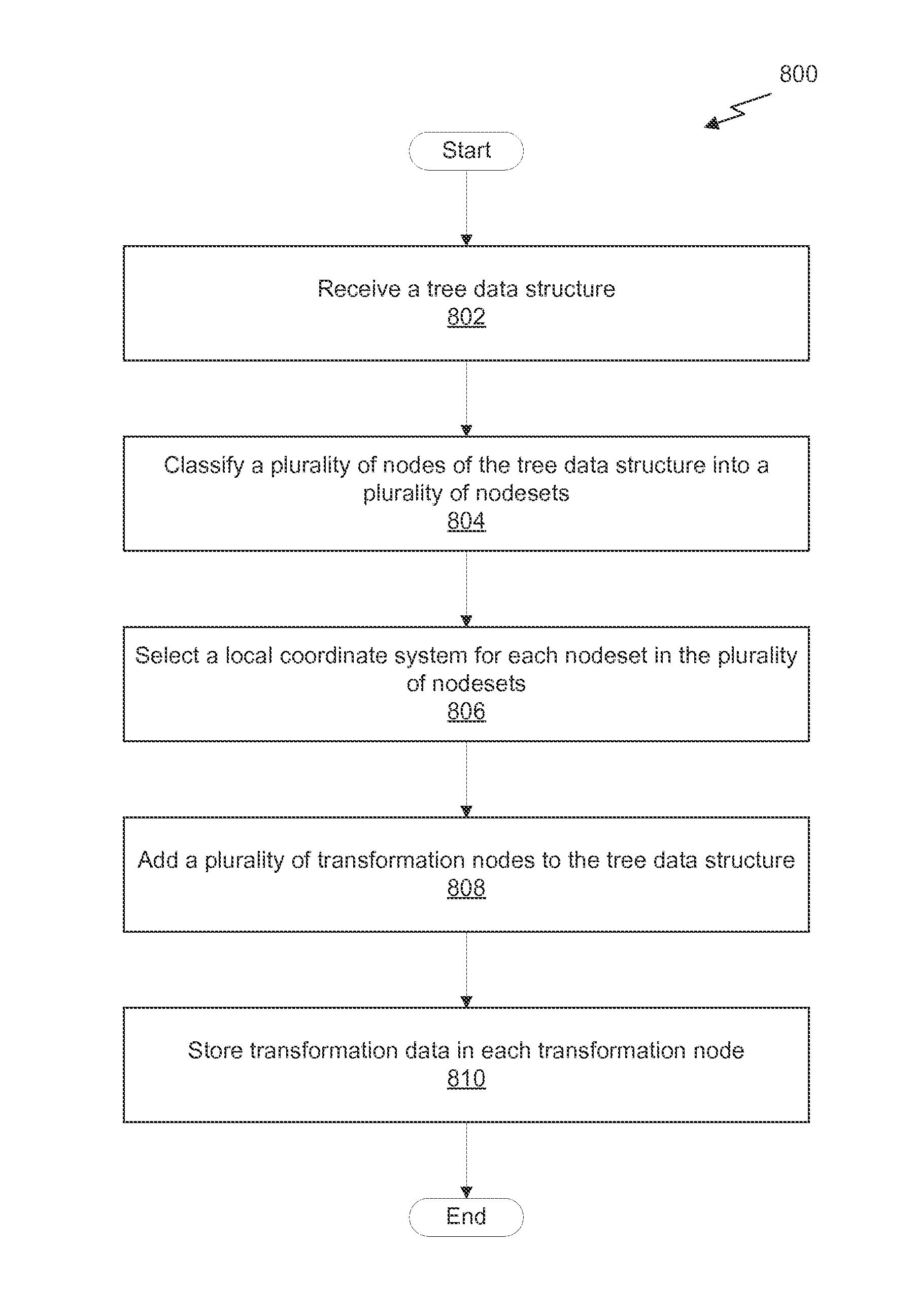
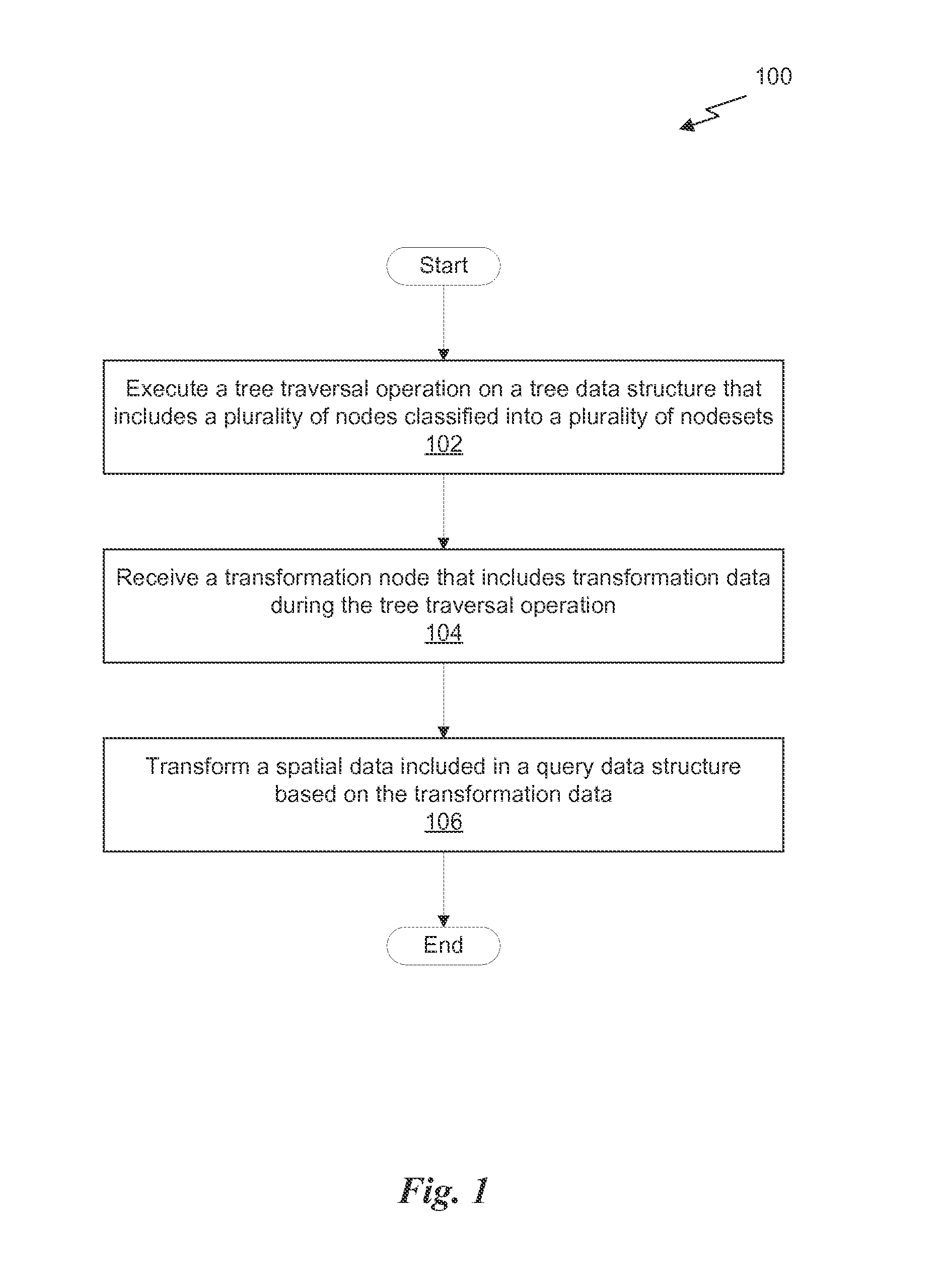
ActiveUS20160070767A1Digital data information retrievalDigital data processing detailsTree traversalTheoretical computer science
A system, computer readable medium, and method are disclosed for performing a tree traversal operation. The method includes the steps of executing, via a processor, a tree traversal operation for a tree data structure, receiving a transformation node that includes transformation data during the tree traversal operation, and transforming spatial data included in a query data structure based on the transformation data. Each node in the tree data structure is classified according to one of a plurality of nodesets, the plurality of nodesets corresponding to a plurality of local coordinate systems. The processor may be a parallel processing unit that includes one or more tree traversal units, which implement the tree traversal operation in hardware, software, or a combination of hardware and software.
Owner:NVIDIA CORP
Systems and methods for converting legacy and proprietary documents into extended mark-up language format
InactiveUS7165216B2Digital computer detailsNatural language data processingTree traversalTransformer
A system and method that converts legacy and proprietary documents into extended mark-up language format which treats the conversion as transforming ordered trees of one schema and / or model into ordered trees of another schema and / or model. In embodiments, the tree transformers are coded using a learning method that decomposes the converting task into three components which include path re-labeling, structural composition and input tree traversal, each of which involves learning approaches. The transformation of an input tree into an output tree may involve labeling components in the input tree with valid labels or paths from a particular output schema, composing the labeled elements into the output tree with a valid structure, and finding such a traversal of the input tree that achieves the correct composition of the output tree and applies structural rules.
Owner:XEROX CORP
Technique for finding rest resources using an n-ary tree structure navigated using a collision free progressive hash
InactiveUS20090164485A1Easy to adaptBroaden applicationDigital data information retrievalData processing applicationsRepresentational state transferPattern matching
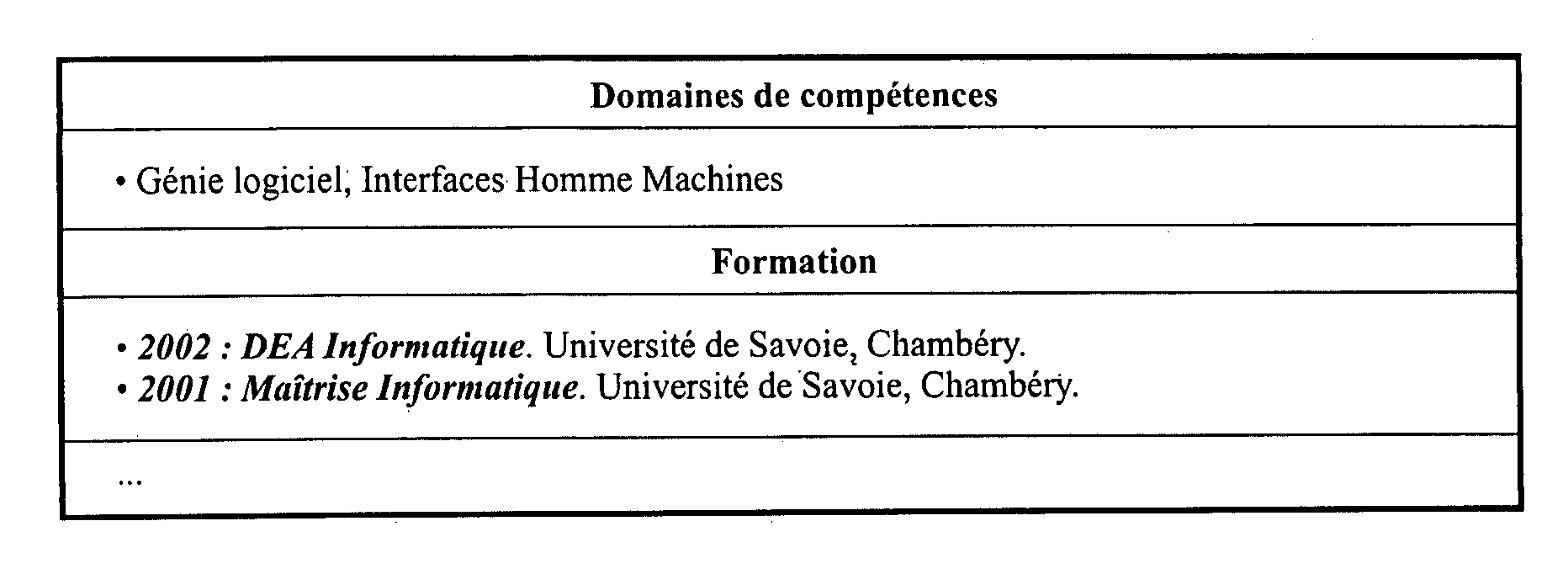
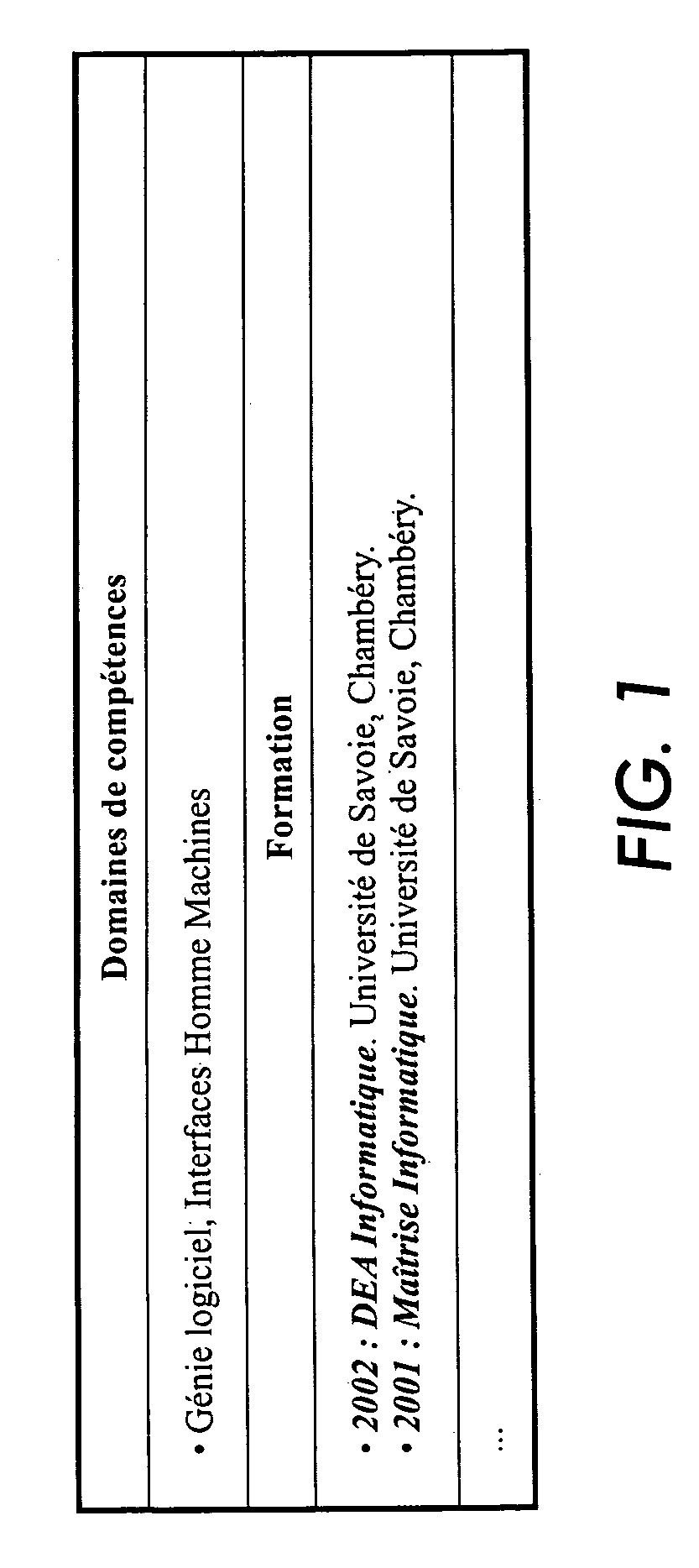
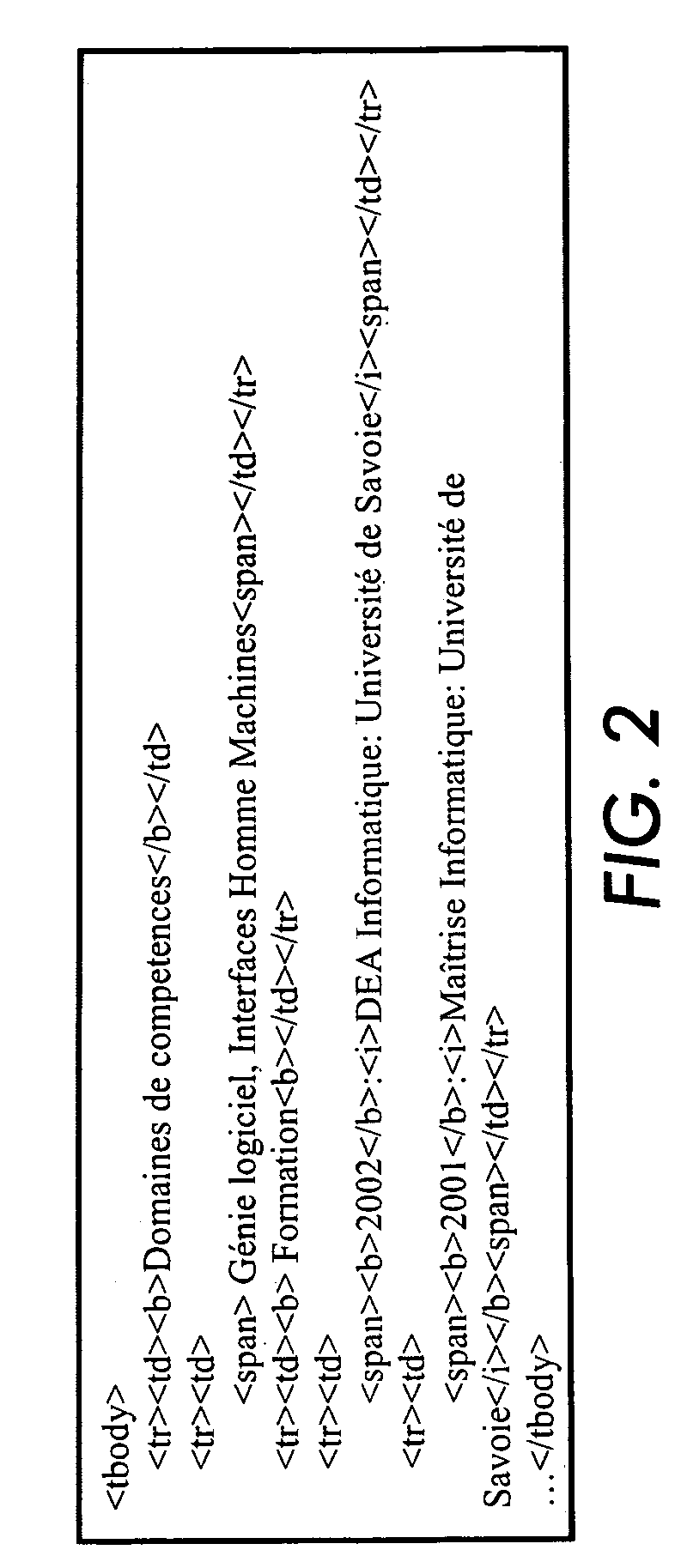
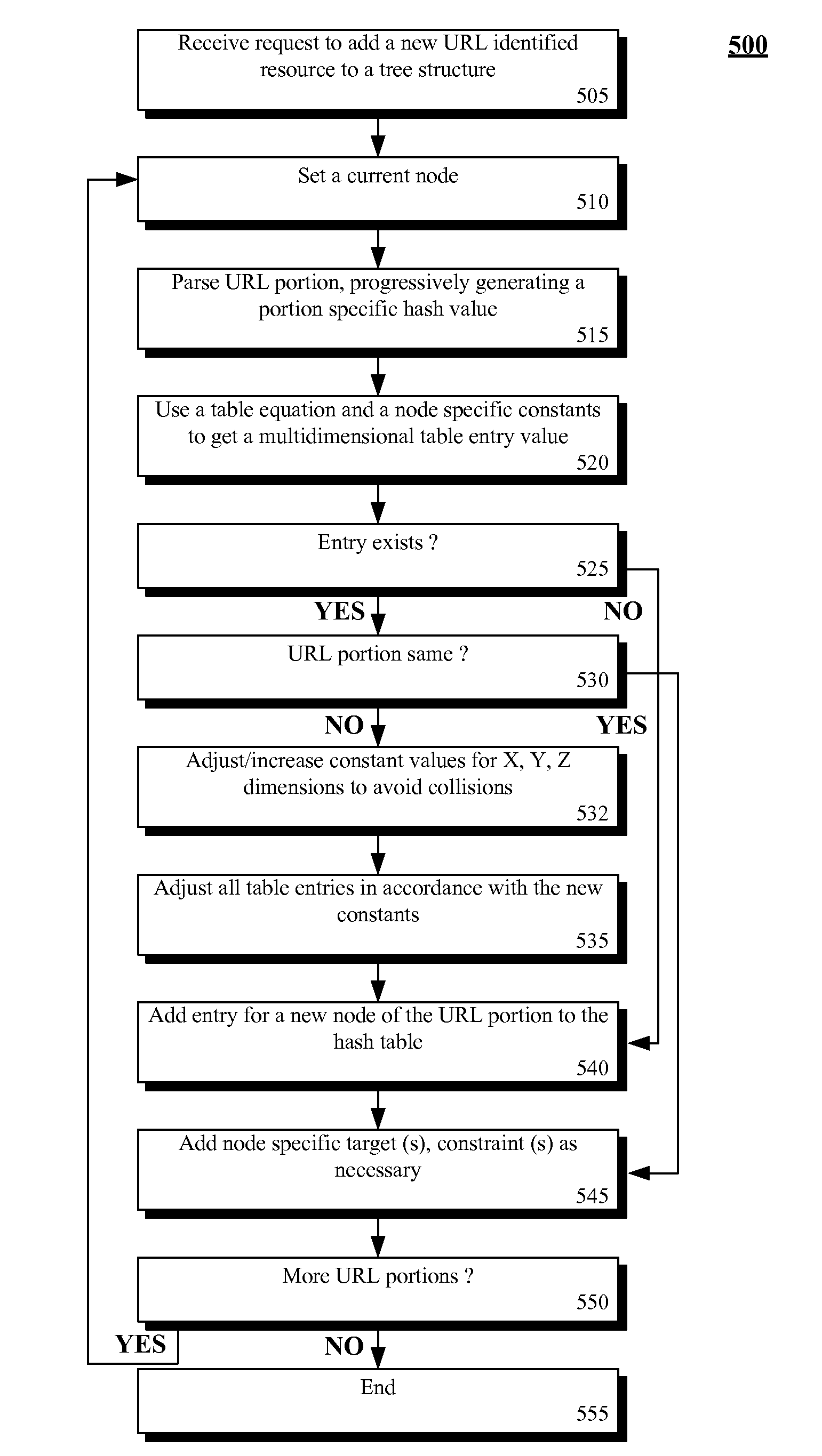
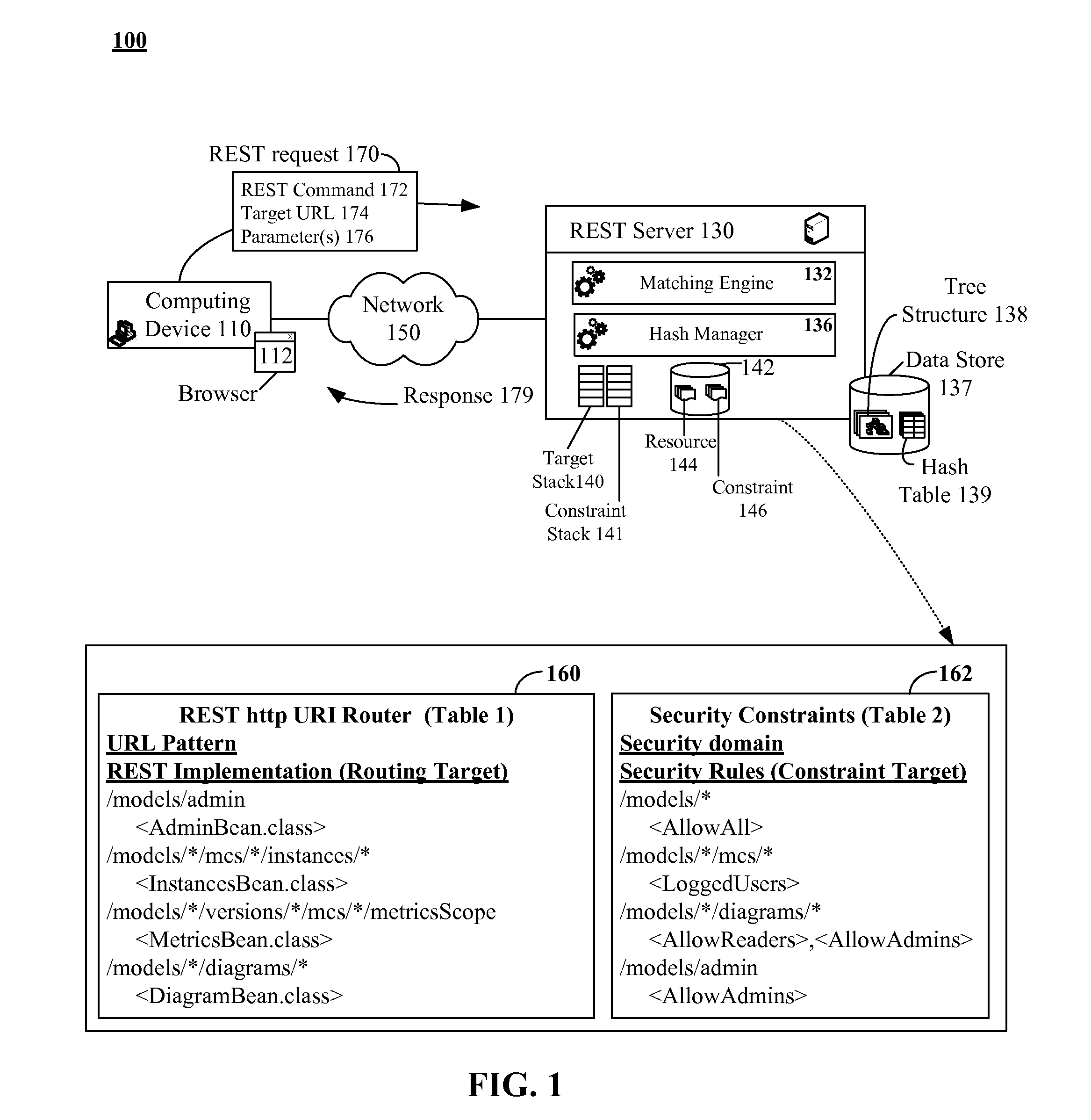
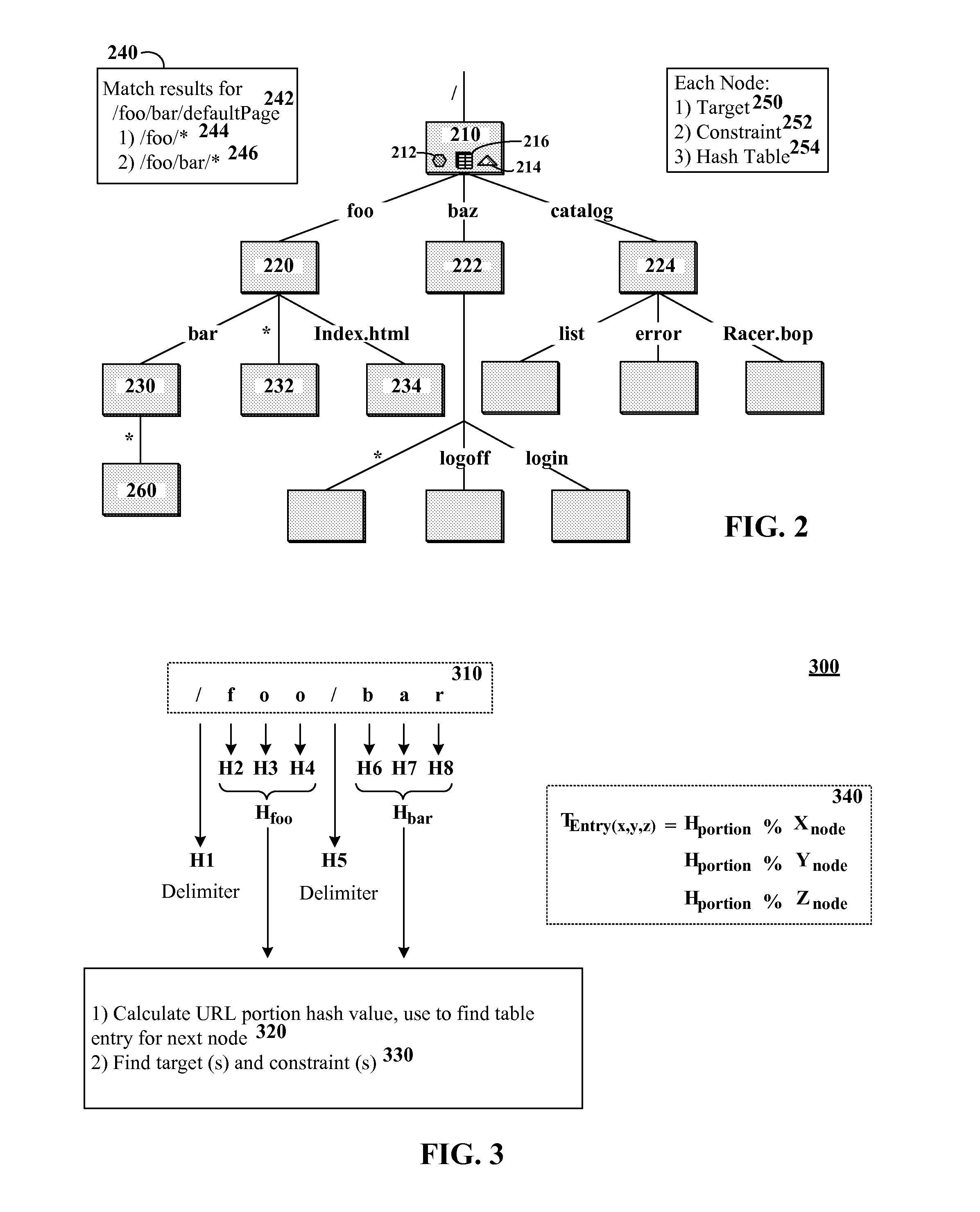
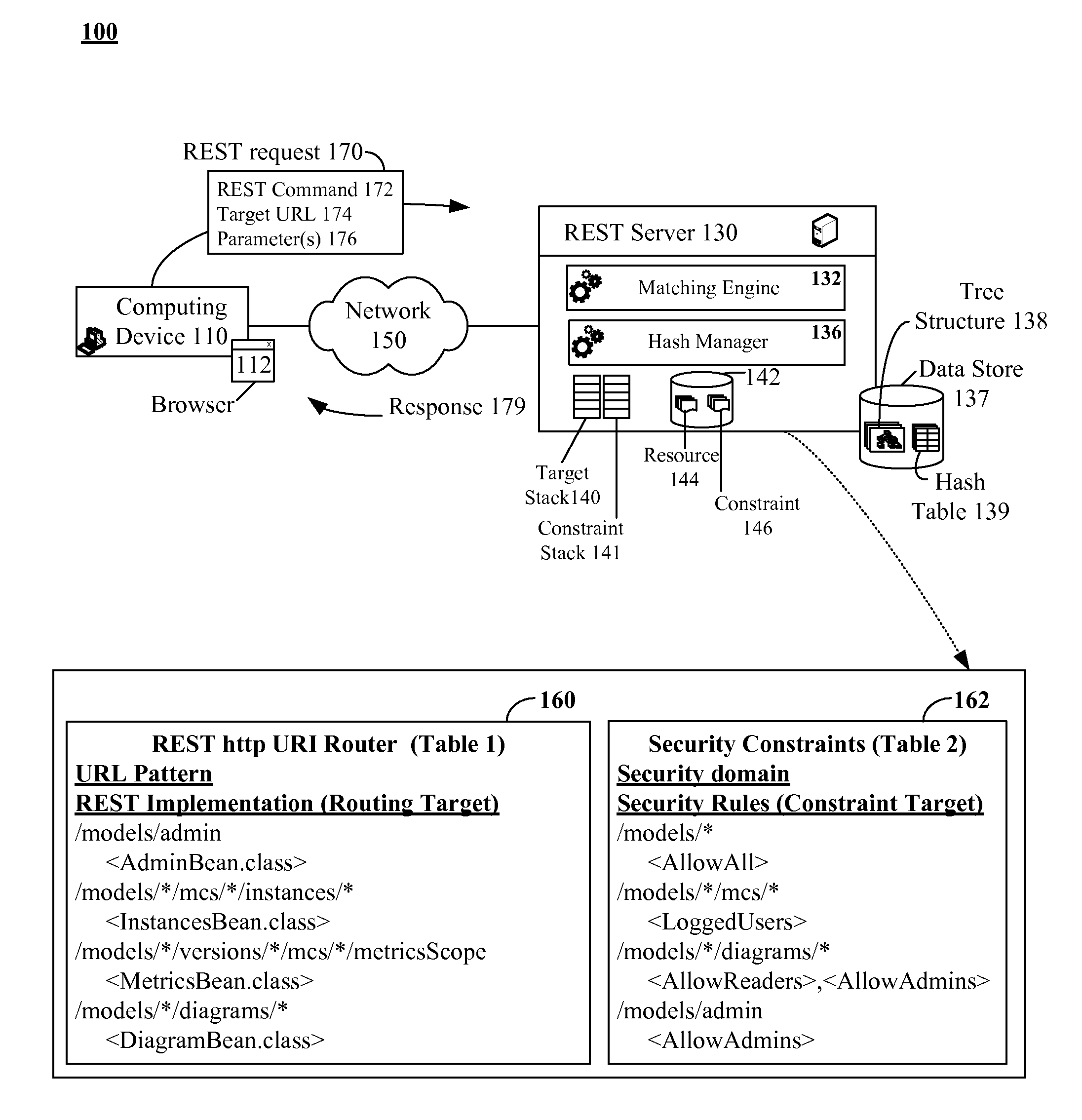
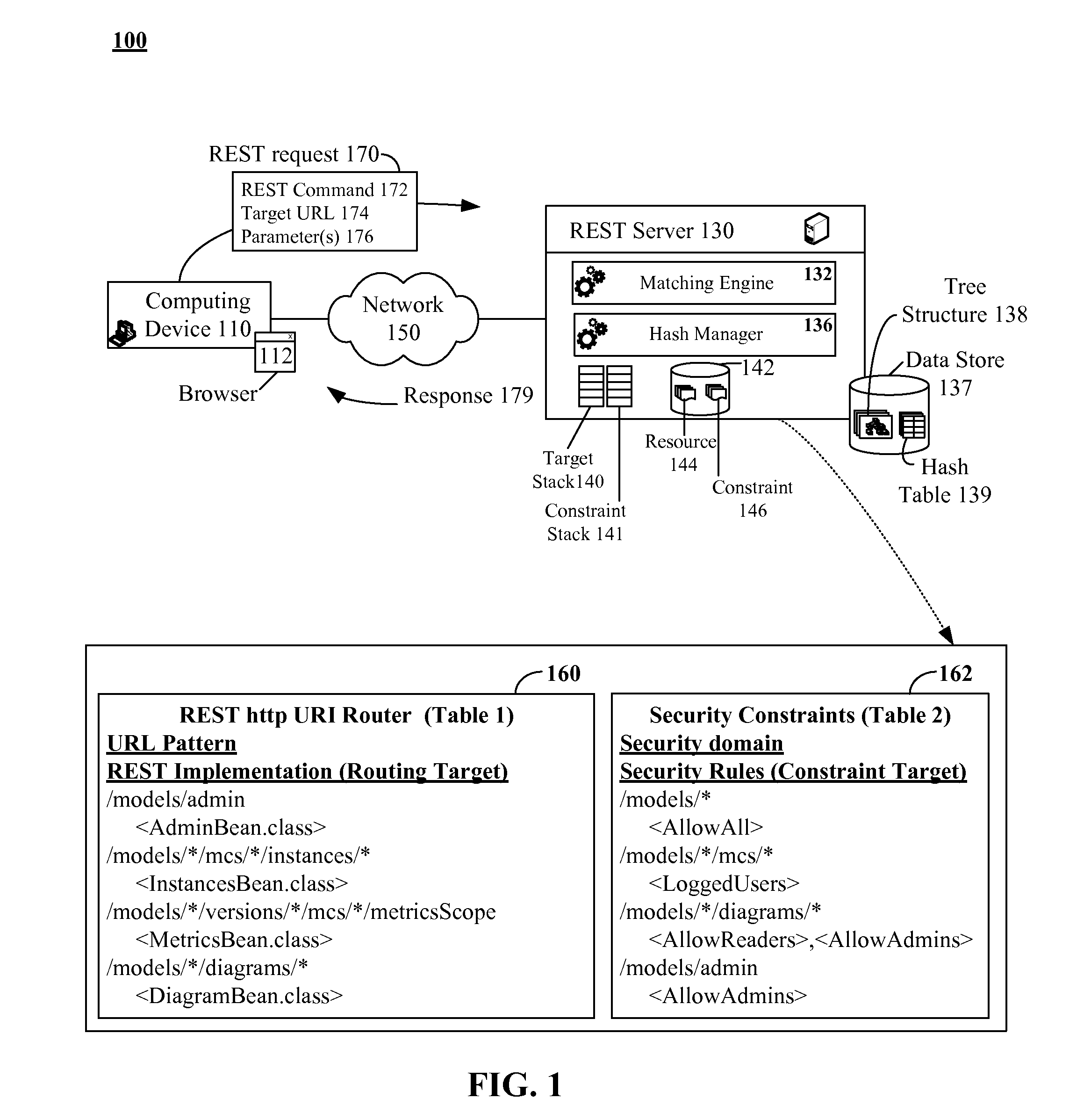
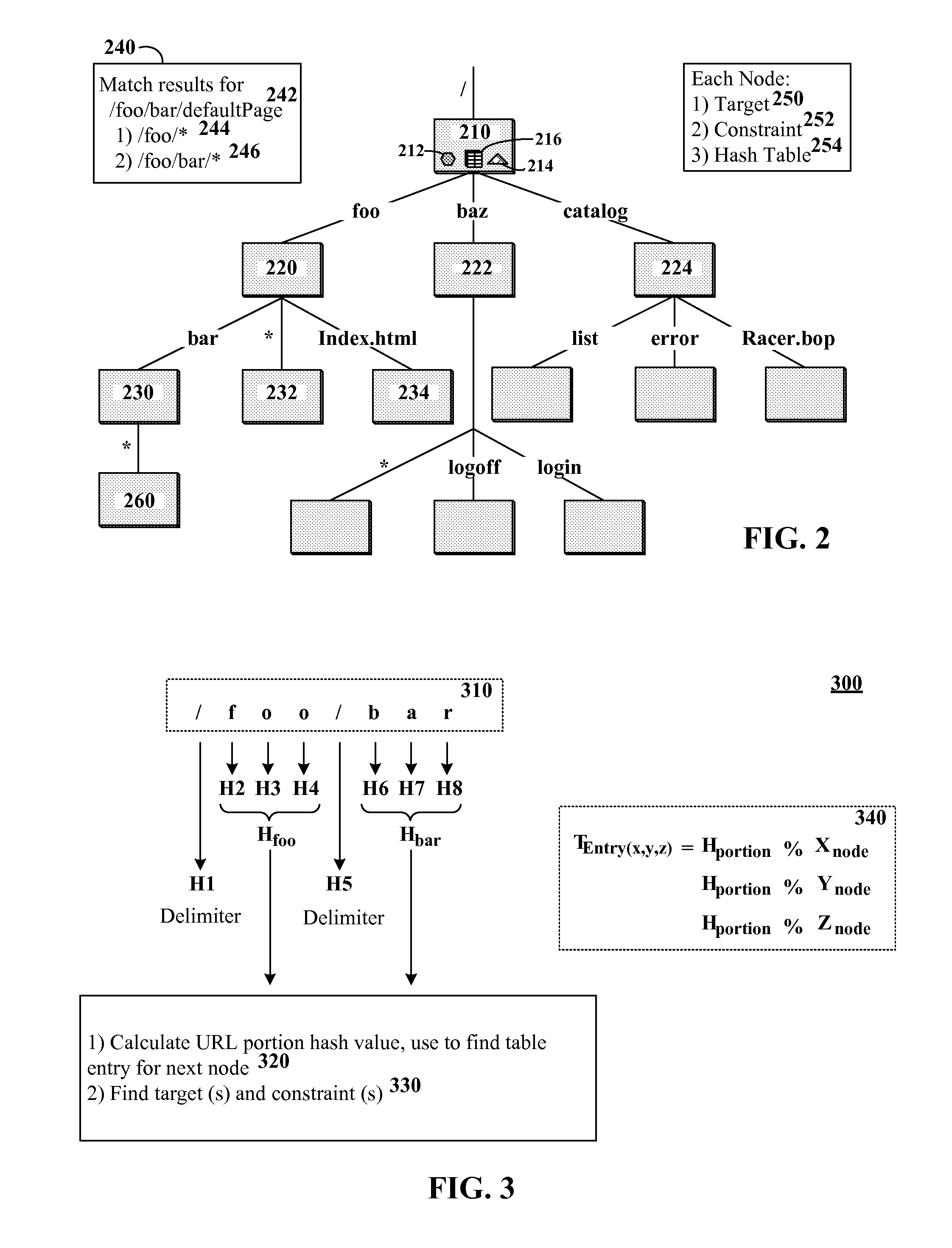
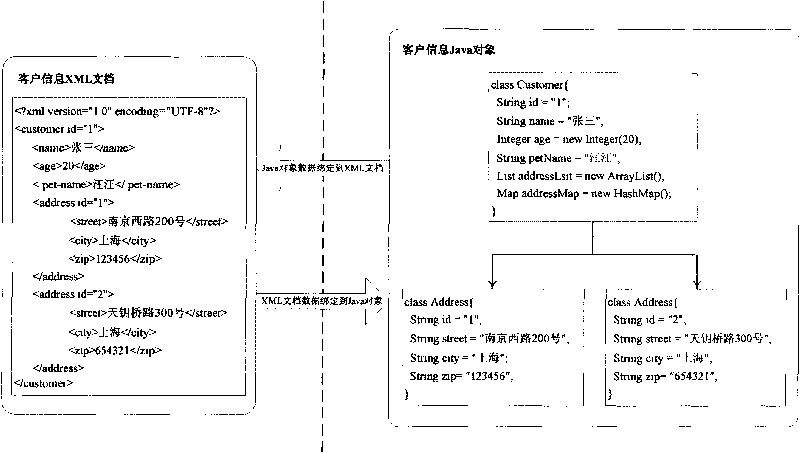
The present invention discloses a data structure which, given an identifier for a Representational State Transfer (REST) resource, can rapidly yield a configured target and simultaneously yield all configured pattern based rules and constraints for the target. The disclosed data structure is a tree structure including nodes for URL portions. Each node is associated with a hash tree specifically grown in a manner that ensures collision occurrences are non-existent. The tree structure is effectively two or more superimposed trees; one for URL pattern matching to determine a target, another for determining constraints. A single tree traversal, which can be based on a progressive hash, can be used to concurrently determine a target and a set of constraints, which represents improved performance over conventional implementations that require multiple, distinct query / response operations to produce equivalent results.
Owner:LINKEDIN
Technique for finding rest resources using an n-ary tree structure navigated using a collision free progressive hash
InactiveUS7774380B2Easy to adaptImprove performanceData processing applicationsDigital data information retrievalRepresentational state transferPattern matching
Owner:LINKEDIN
Method for binding Java and XML data
ActiveCN101699397ASimplify development workReduce development difficultySpecial data processing applicationsSpecific program execution arrangementsTree traversalJava classes
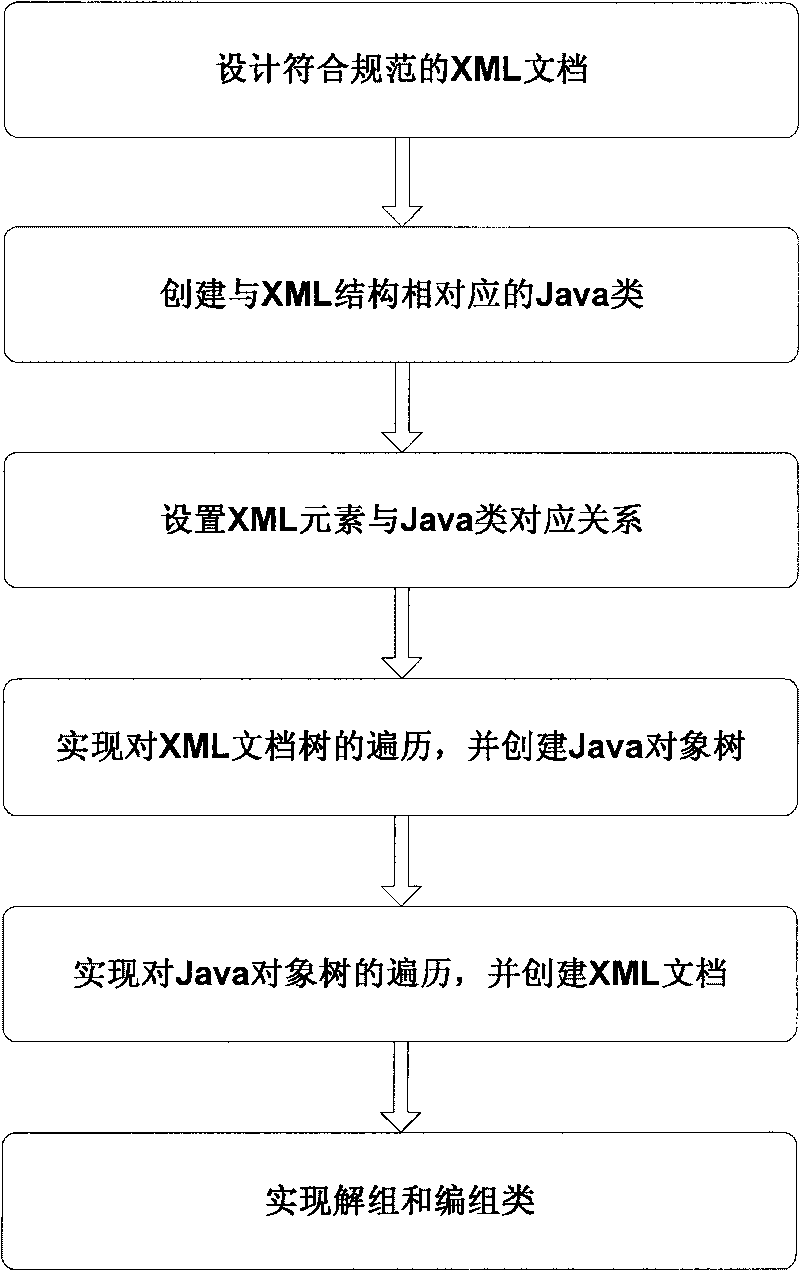
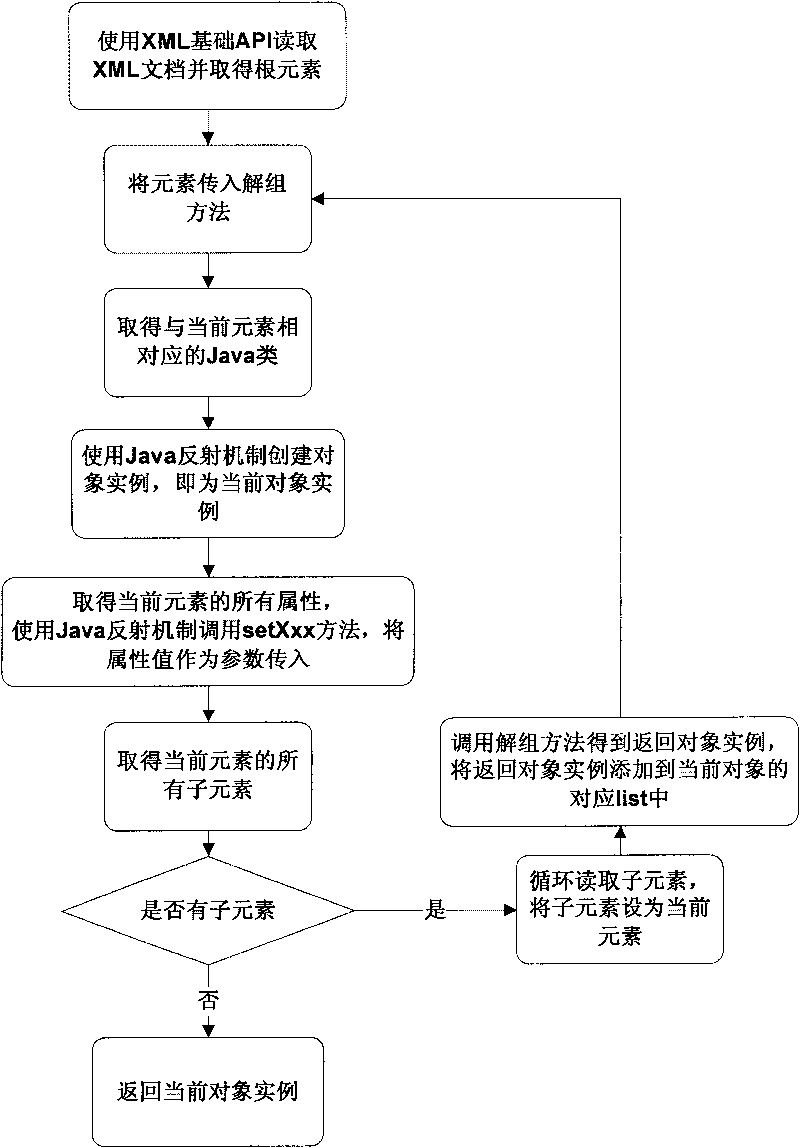
The invention discloses a method for binding Java and XML data, which comprises the following steps of: 1) designing an XML document; 2) creating a Java class corresponding to an element according to the structure of the XML document; 3) setting a corresponding relationship between the XML element and the Java class; 4) realizing a disorganization algorithm, adopting a recursive algorithm to transverse an XML document tree, and creating a Java object corresponding to the structure of the XML document; 5) realizing a grouping algorithm, adopting the recursive algorithm to transverse a Java object tree, and creating an XML document corresponding to the whole Java object tree; and 6) realizing a disorganization class and a grouping class. The method realizes bidirectional data mapping binding between the Java object and the XML document, simplifies development work by using the XML, realizes an automation process from resolving the XML document to creating the Java object, and can write the modified Java object back to the XML document and conveniently adapt to the change of the structure of the XML document by modifying few Java codes.
Owner:SHANGHAI BAOSIGHT SOFTWARE CO LTD
Tree shaped fast connection establishing method based on multi-Agent cooperation
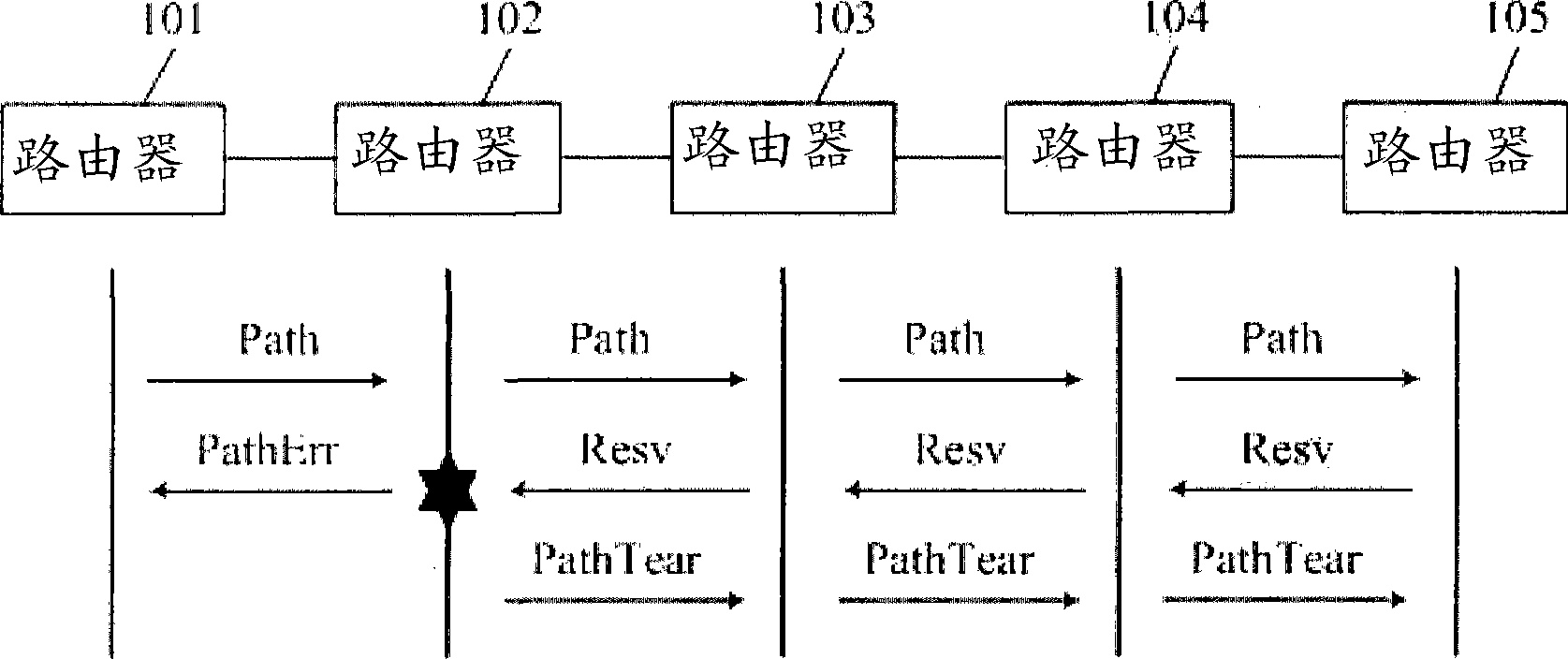
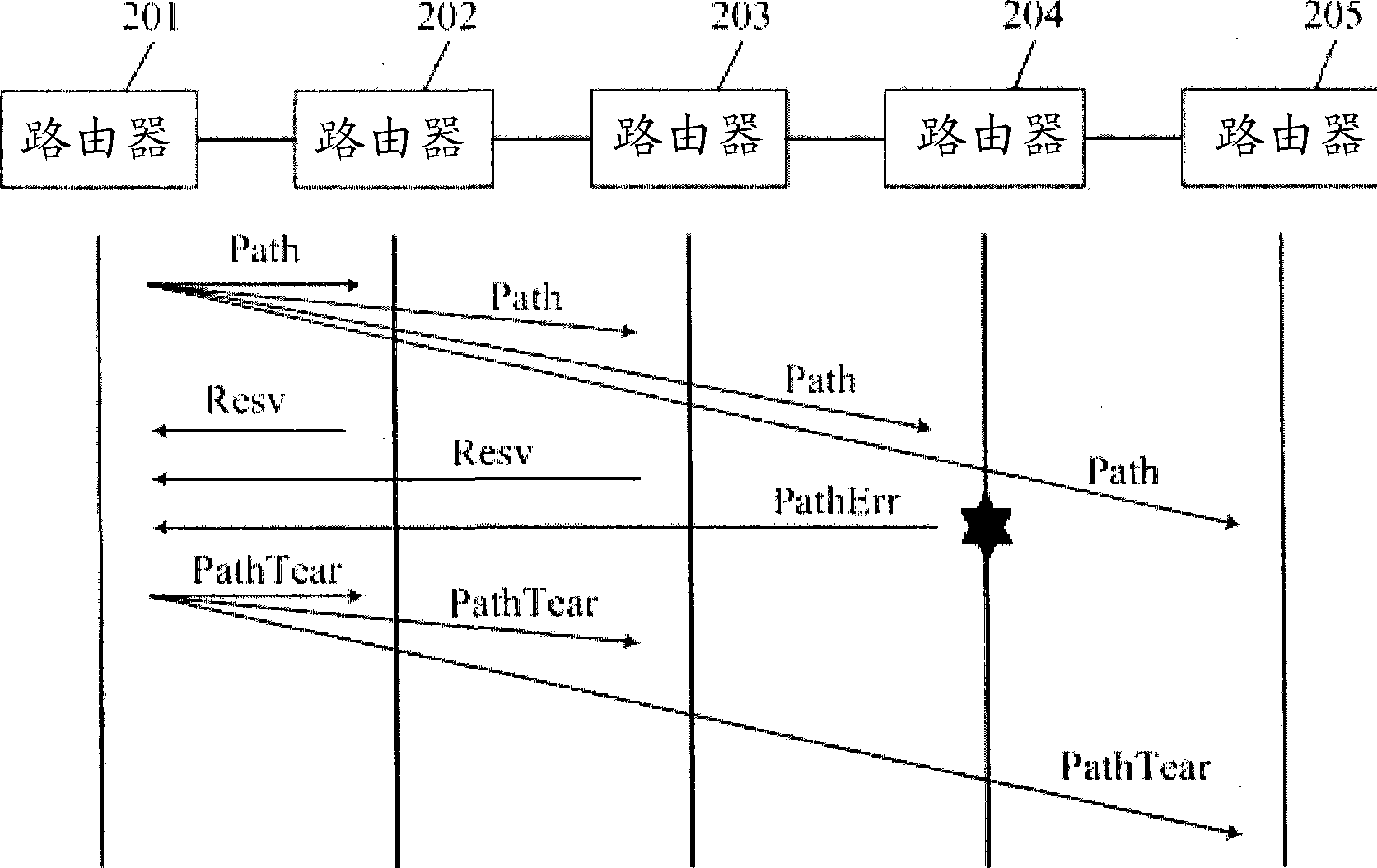
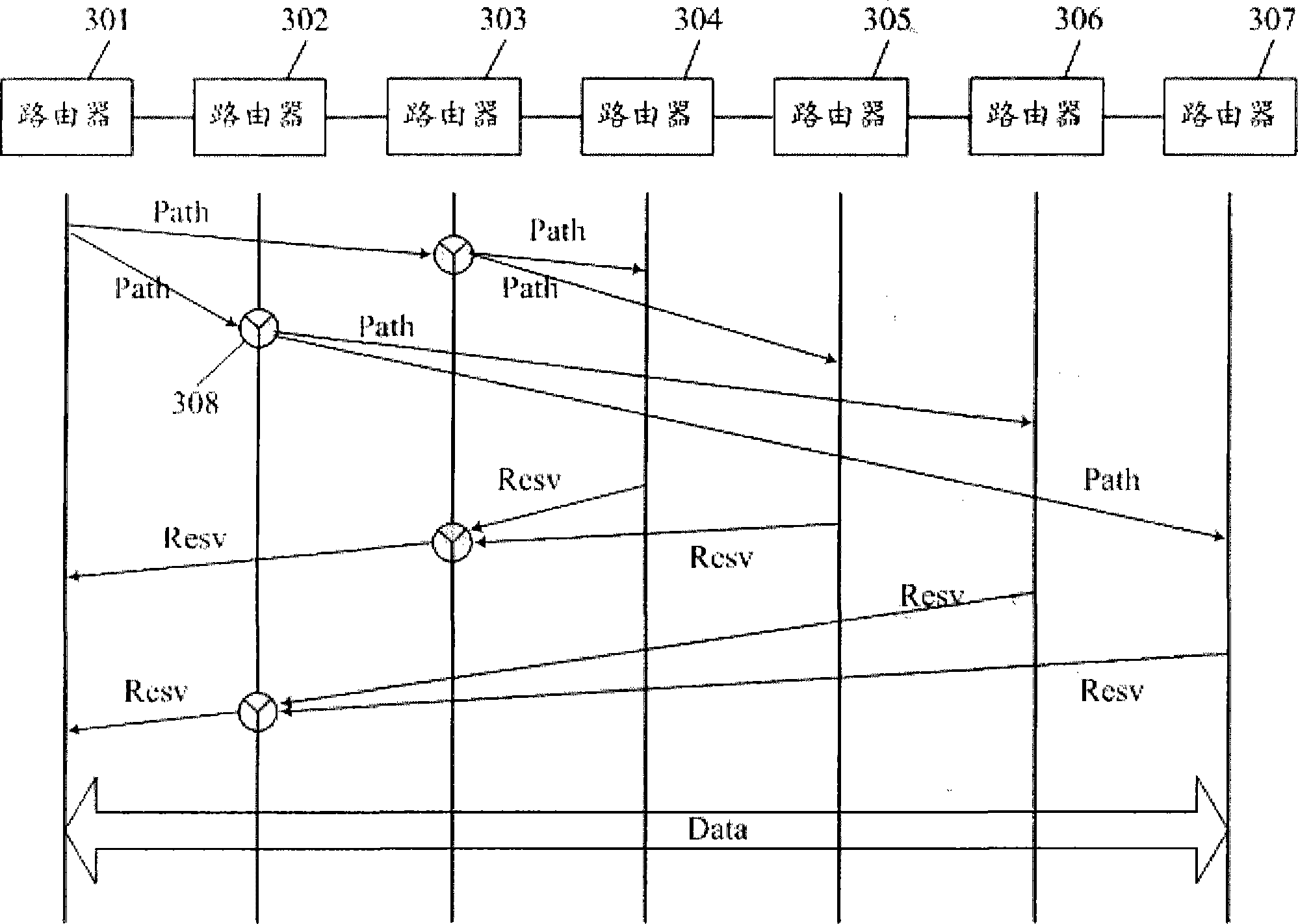
ActiveCN101488898APrevent false reservationsPrevents errors from being preempted by other requestsStar/tree networksStructure of Management InformationConnection control
The invention relates to the communication field, the invention embodiment discloses a tree-shaped fast connecting establishing method based on multiple-Agent cooperation. The method comprises: an integral establishing process flow of single service tree-shaped signaling; a signaling expanding abstraction logical function in a network with control plane; a topological abstract method of multiple-Agent collaboration signaling forwarding tree; a traversing mode of tree-shaped signaling forwarding tree based on non-balance type binary forwarding tree; a traversing mode of tree-shaped signaling forwarding tree based on non-balance type N-branch forwarding tree; a resource invalidation processing method in the tree-shaped signaling service process flow. According to the method of the invention, the entity logical function can be forwarded by expanding the signaling, the connection control operation can be performed between a plurality of Agents to establish a layered structure for a calling connection controller, the higher grade calling connection controller implements the control function for a first stage calling connection controller to rapidly implement the connection establishment and respectively provide processing flows for different resource invalidation conditions. After considering the queue processing and exterior transmission time delay, the connection can be optimized by a non-standard binary forwarding tree structure. The tree-shaped signaling implementing interface of the multiple-Agent system comprises a GUI interface for taking charge of the transmitting of the control command, the real-time data detection, the data filtering, the center resource database access and the Agent information report and so on operations.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Source code protection method and device
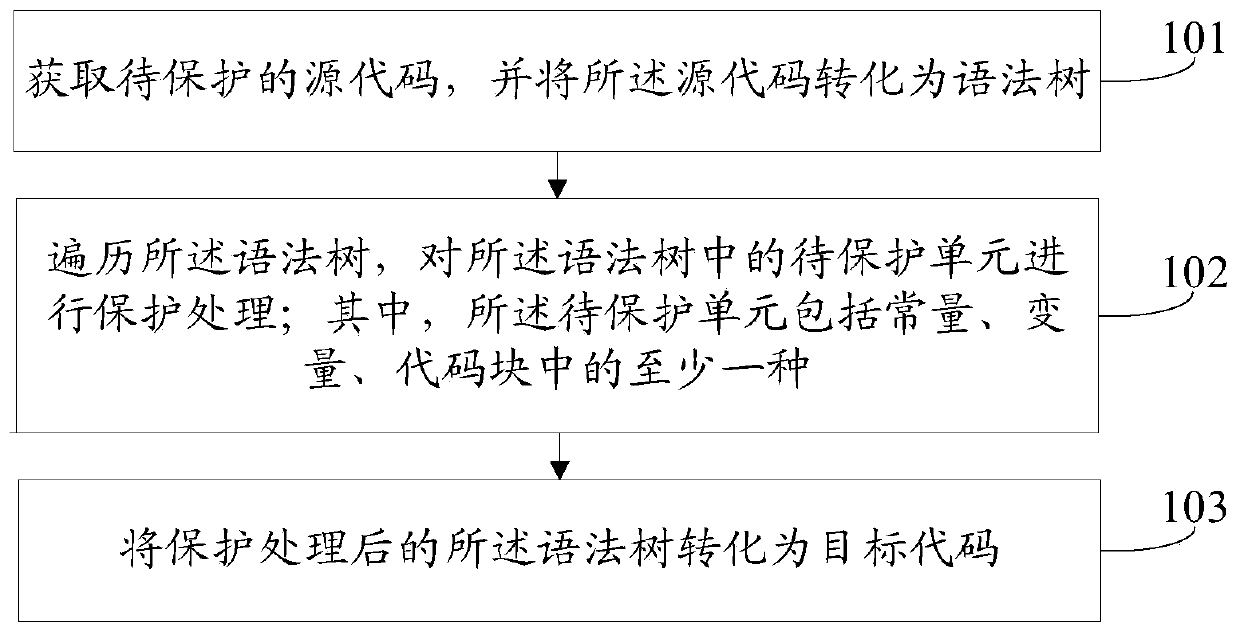
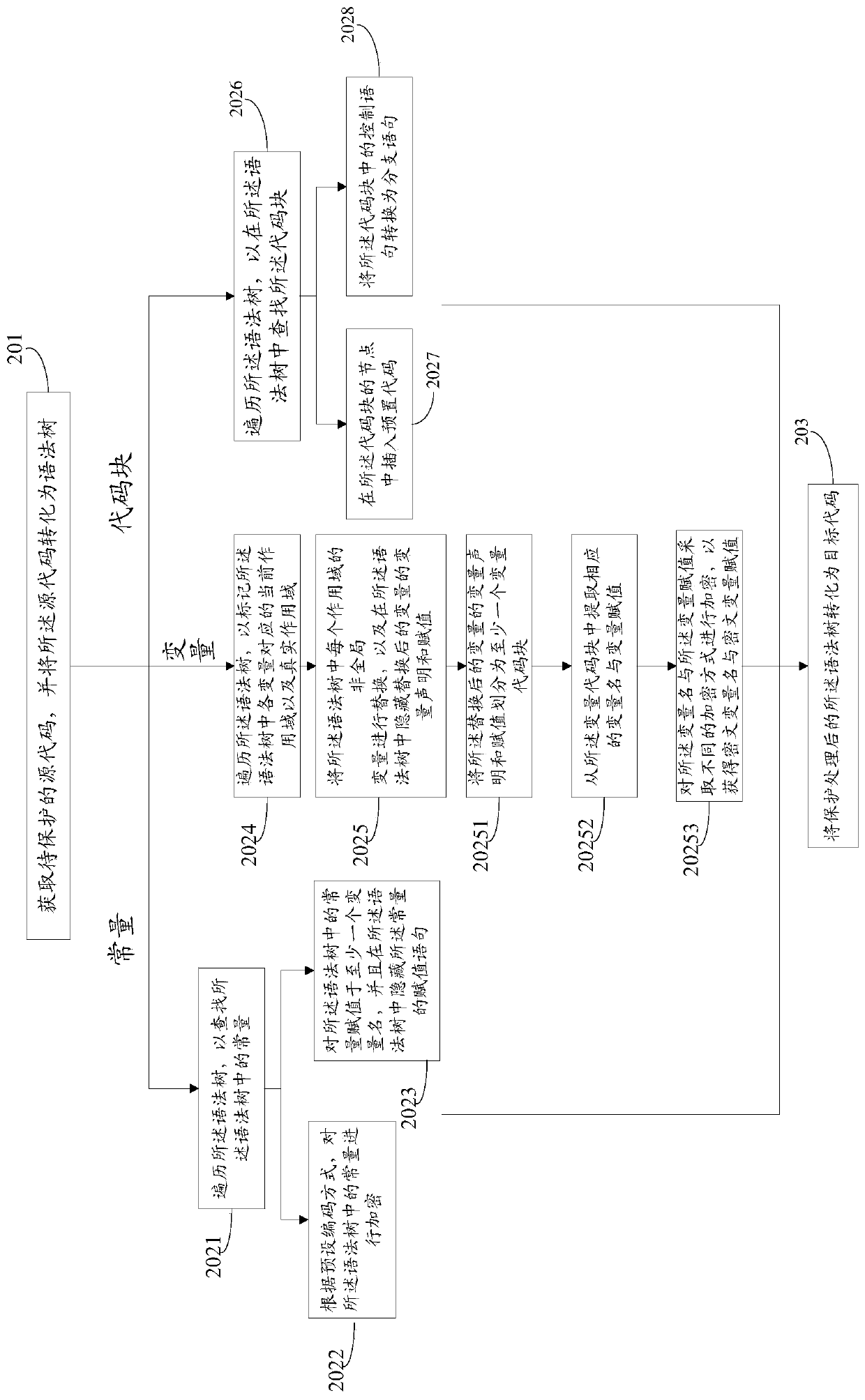
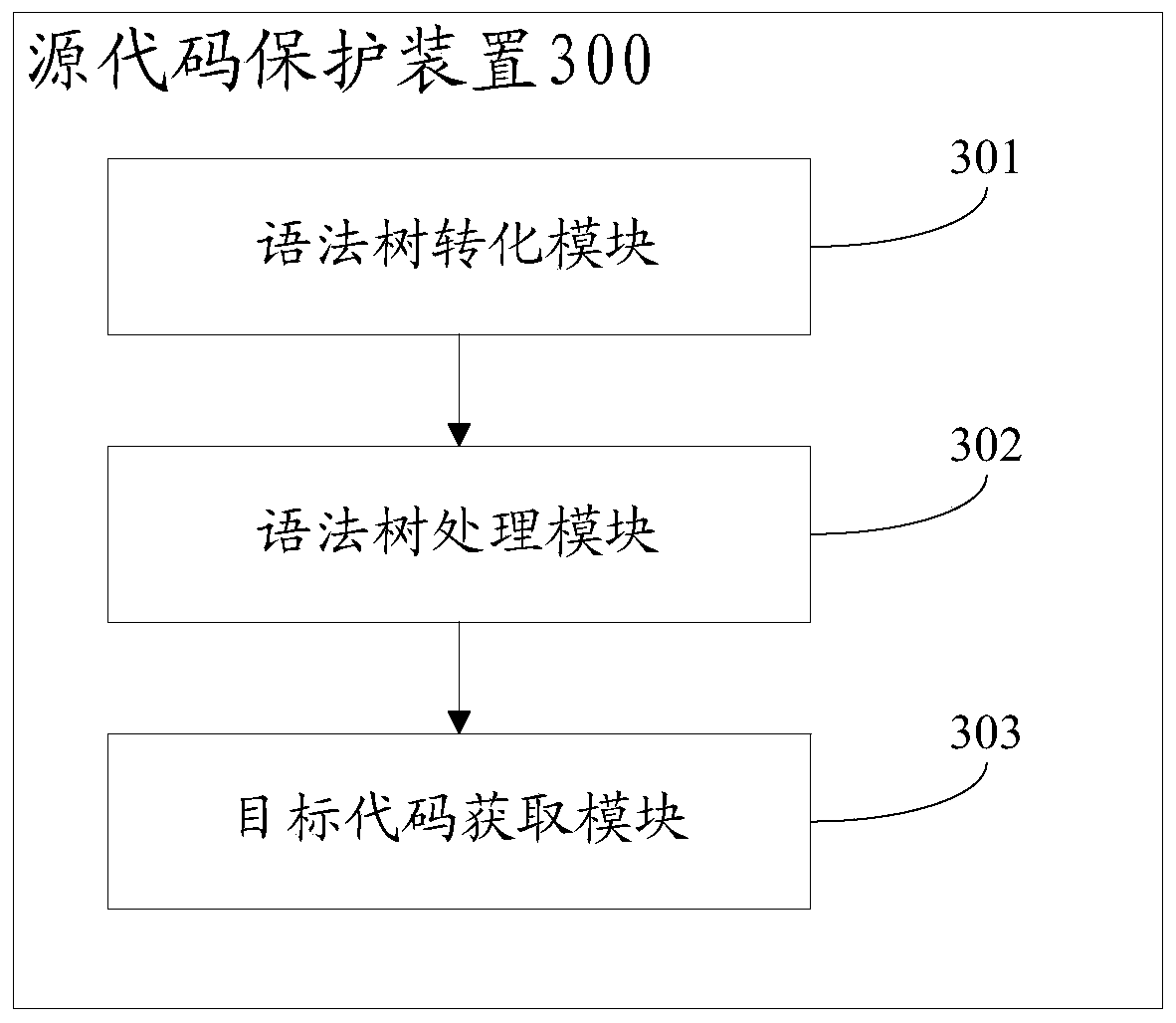
ActiveCN109992935ADoes not affect executionReduce readabilityDigital data protectionProgram/content distribution protectionCoding blockObject code
The invention provides a source code protection method, and belongs to the technical field of computers. The method comprises the following steps: obtaining a source code to be protected, and converting the source code into a syntax tree; traversing the syntax tree, and performing protection processing on a to-be-protected unit in the syntax tree; wherein the unit to be protected comprises at least one of a constant, a variable and a code block; and converting the syntax tree subjected to protection processing into a target code. According to the embodiment of the invention, a powerful sourcecode protection scheme is provided, and meanwhile, the bottom layer structure of the MINA JS engine is universally adapted, so that the scheme of the embodiment of the invention can be applied to deepprotection of WeChat applet codes.
Owner:HANGZHOU FRAUDMETRIX TECH CO LTD
Method for analyzing abnormal index based on rule engine
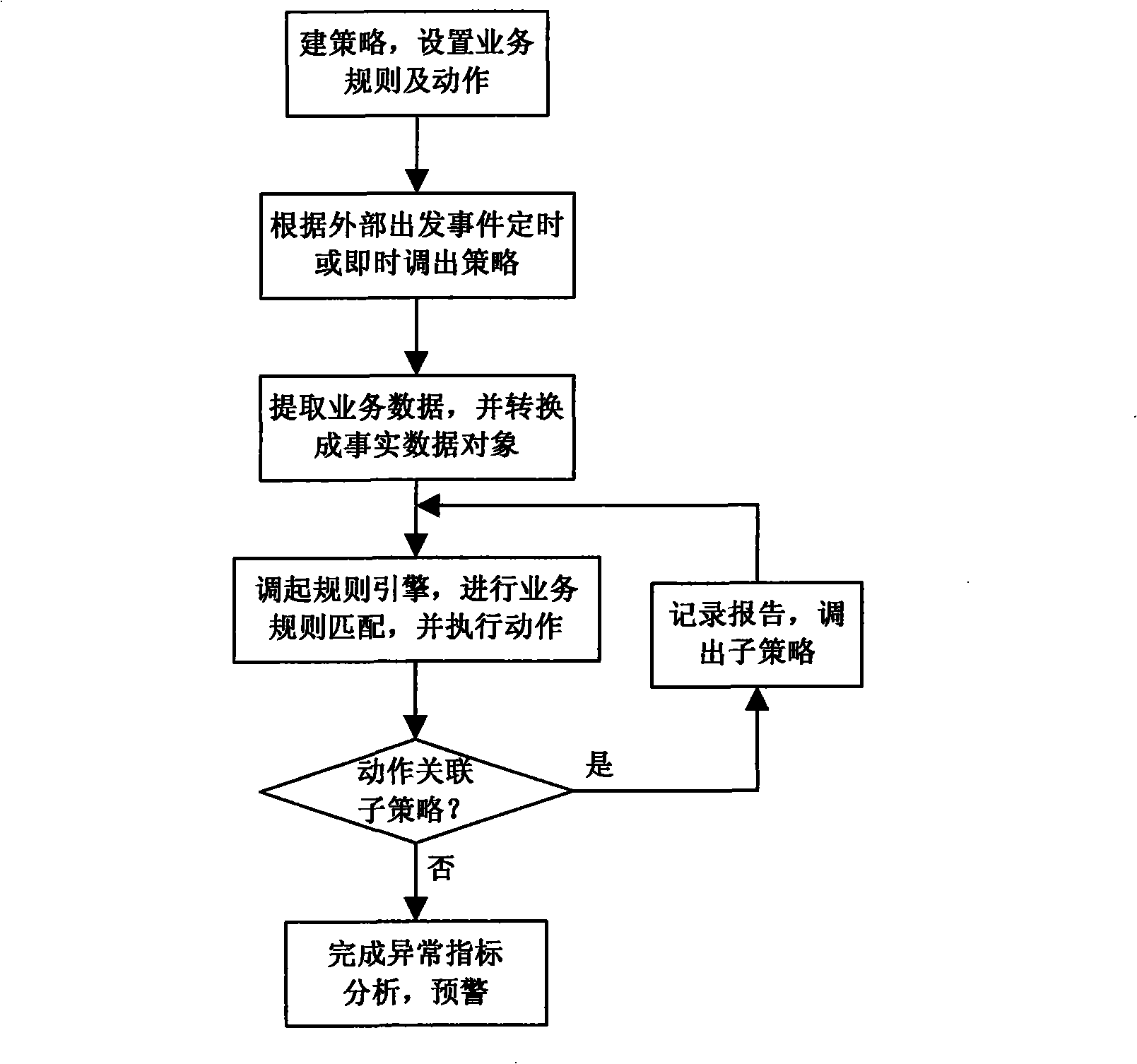
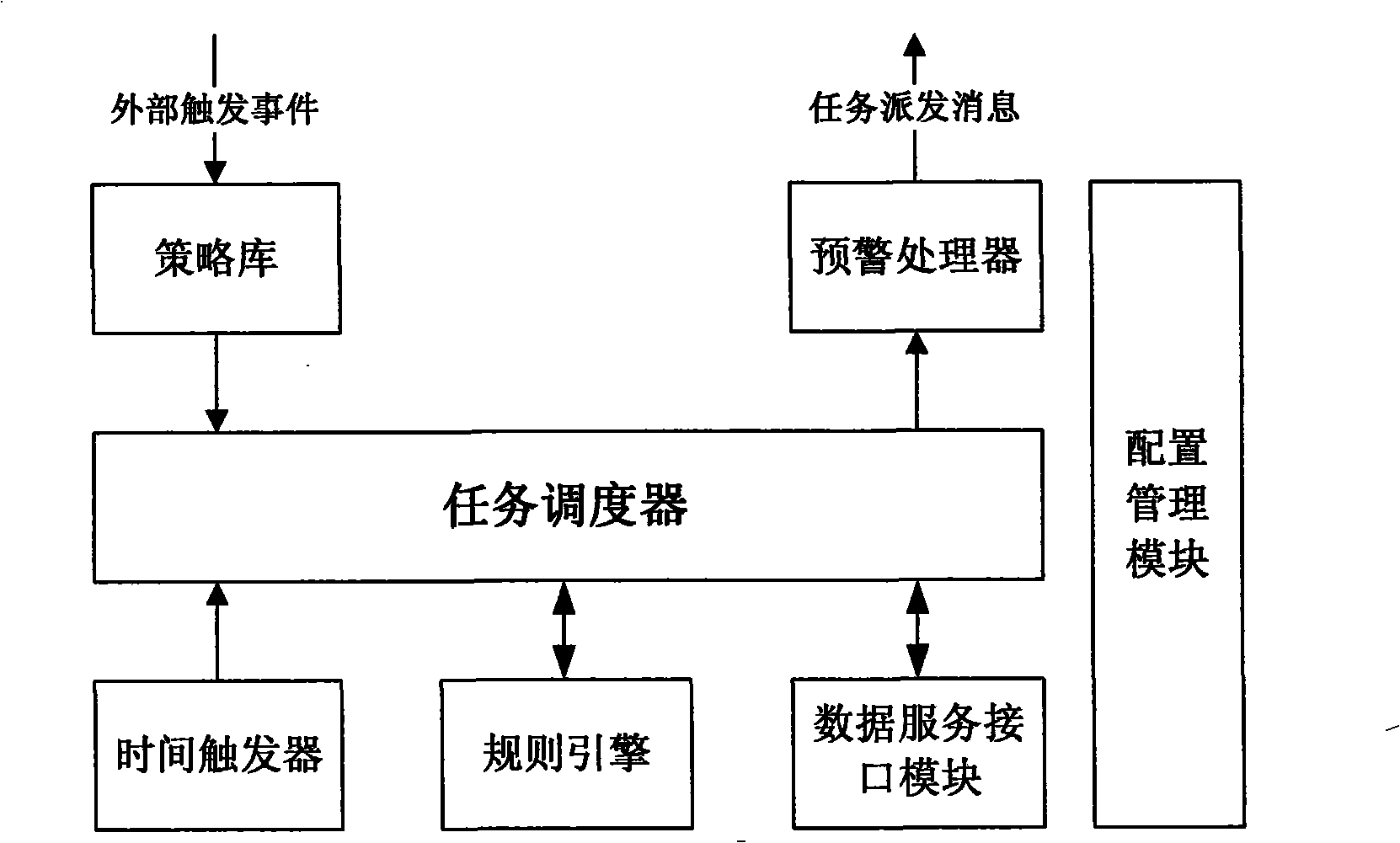
InactiveCN101409885AHigh degree of automationFast analysisWireless communicationTree traversalData mining
The invention relates to a mobile communication technology field, in particular to an abnormal index analysis method. The method is implemented according to the following steps of: (1) establishing policies and setting corresponding service rules and motions; (2) regularly or immediately calling out corresponding policies according to the external trigger event; (3) extracting service data through a data service interface module and converting the data into fact data objects which can be identified by a rule engine; (4) adjusting the rule engine for carrying out intelligent matching of service rules and calling corresponding motions; (5) calling out corresponding sub-policies if the motion is associated with sub-policies and repeating the step (4) until the motion of service rule matched with the fact data object in the sub-policy is not associated with the sub-policy any more; and (6) recording the ergodic process of a policy tree and the analysis results of intermediate nodes, forming the final abnormal index analysis report and carrying out pre-warning. The method can automatically, quickly and accurately position to the reasons of events causing abnormal index.
Owner:CHINA MOBILE GRP FUJIAN CO LTD
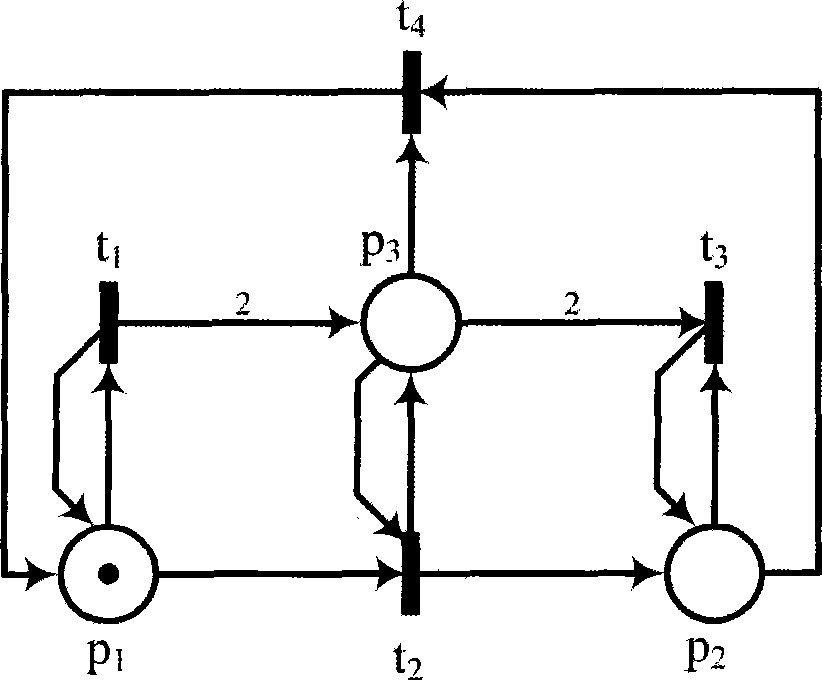
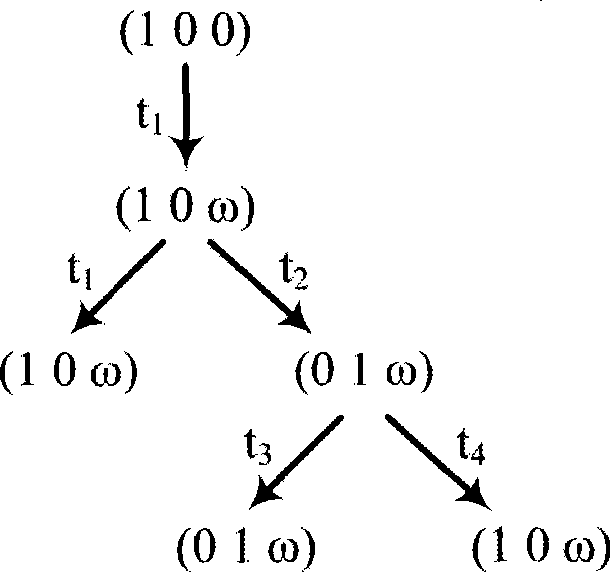
Property analysis method and system of general-purpose Petri net based on quasi-perfect finite reachable tree
The invention discloses a method and a system for analyzing property of a quasi-perfect limited reachability tree based general Petri network. A quasi-perfect limited reachability tree which is different from the prior reachability tree and derivatives of the prior reachability tree is generated by Petri network model description data; by node identification of a traversal tree, the boundedness and the safety of the Petri network are determined; the trees are converted to generate a series of local reachability trees, the number of arc labels in the local trees is counted, and the conditions of activity and deadlock of variances and the network of the Petri network are analyzed; and the appearance conditions of an initial label of the Petri network in the local reachability trees are checked, and the reversibility of the Petri network is analyzed and judged. Compared with the prior art, the invention is suitable to be used to analyze the property of the general Petri network model, and is not restricted to bounded Petri networks and certain Petri networks, so that the invention can be widely applied to related dynamic characteristic analysis of a concurrent system and a discrete event dynamic system.
Owner:SOUTHEAST UNIV
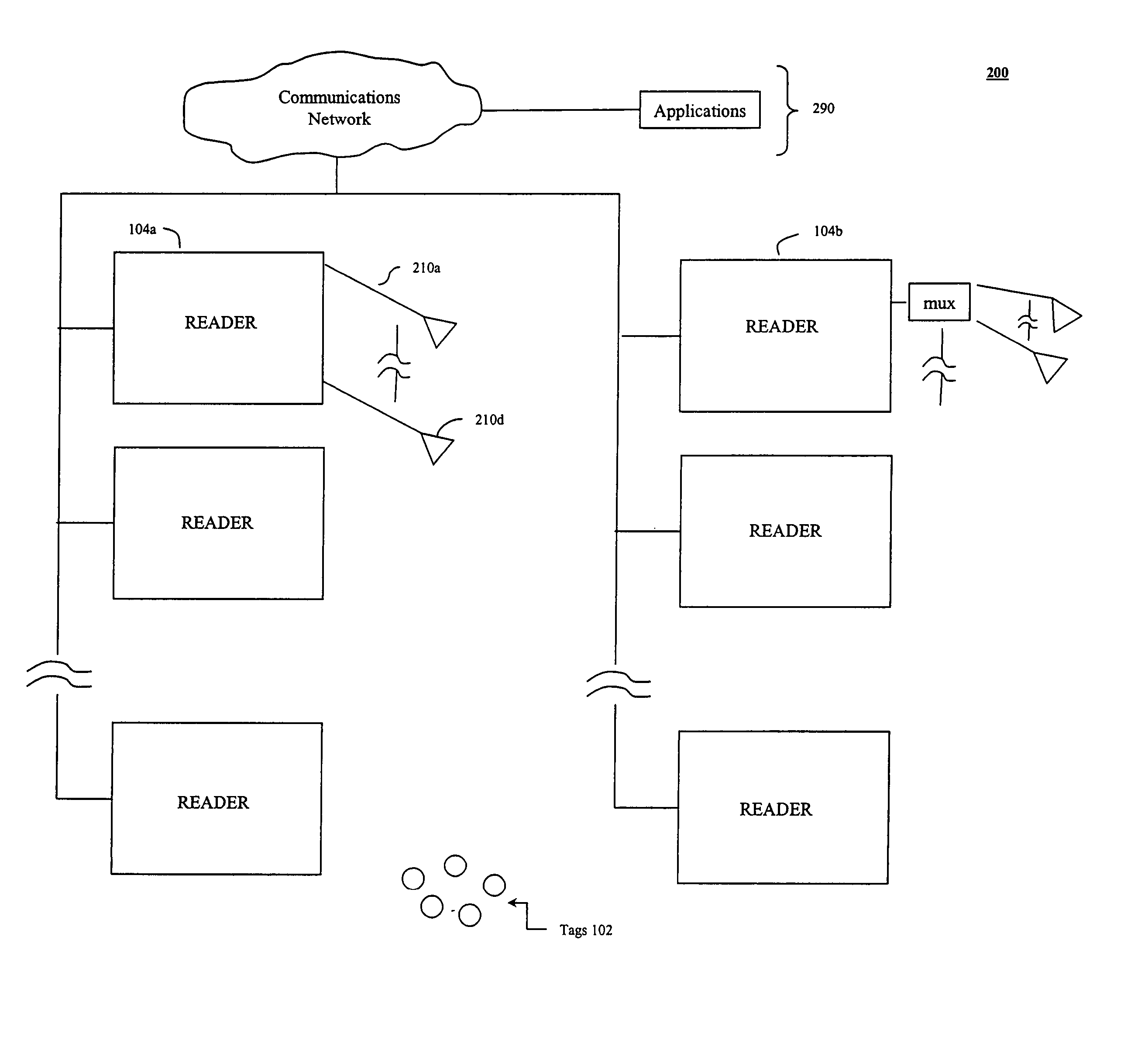
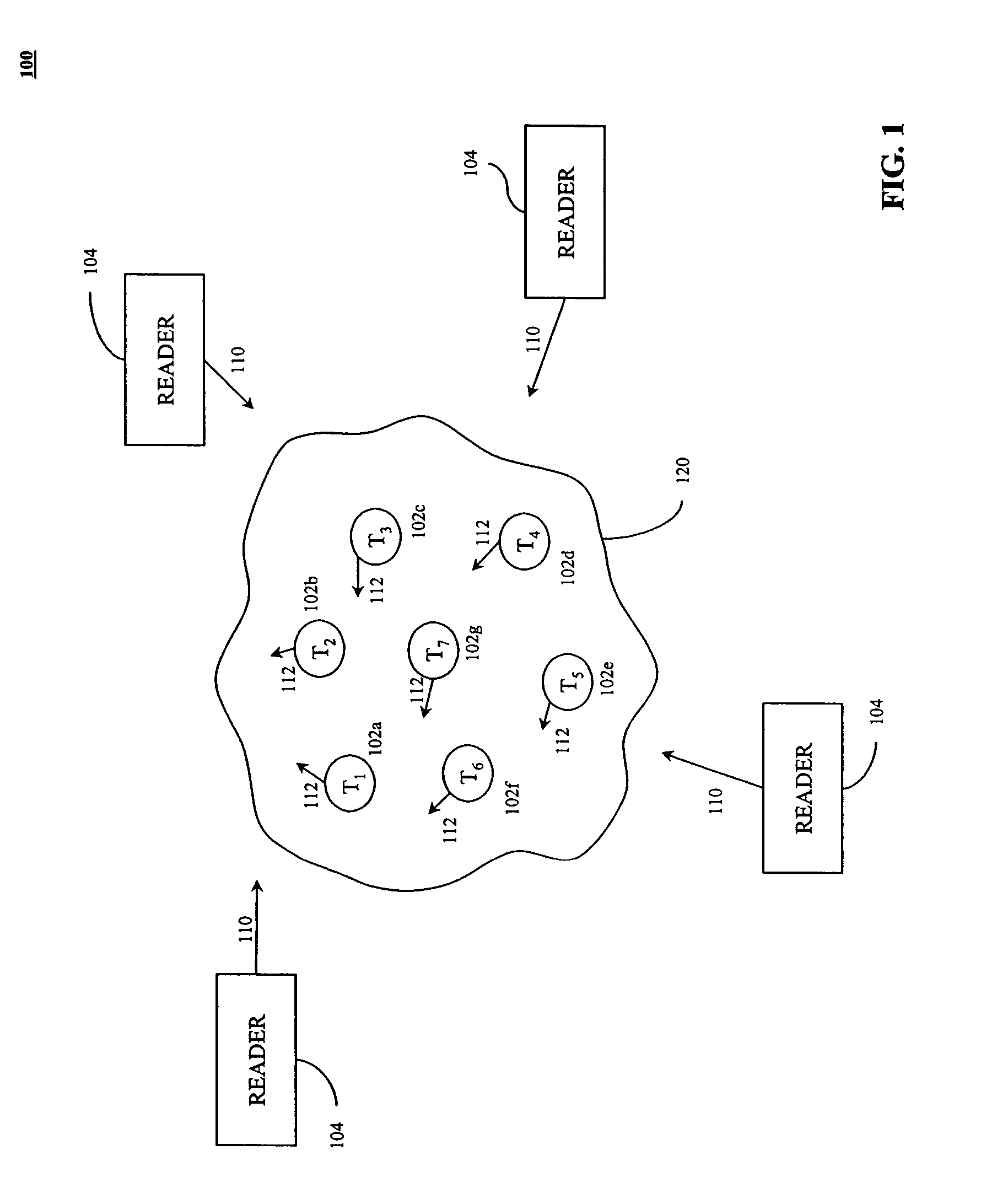
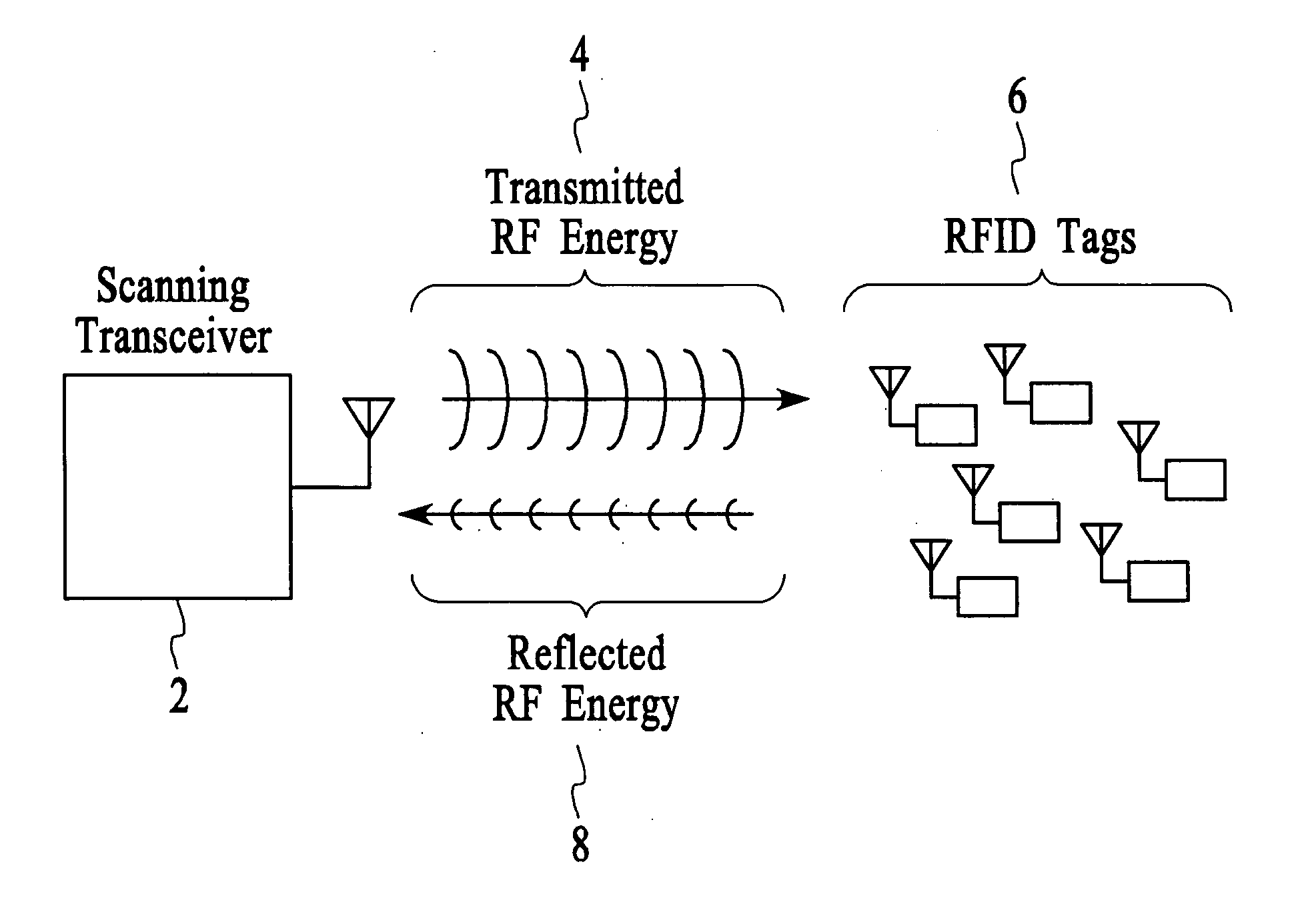
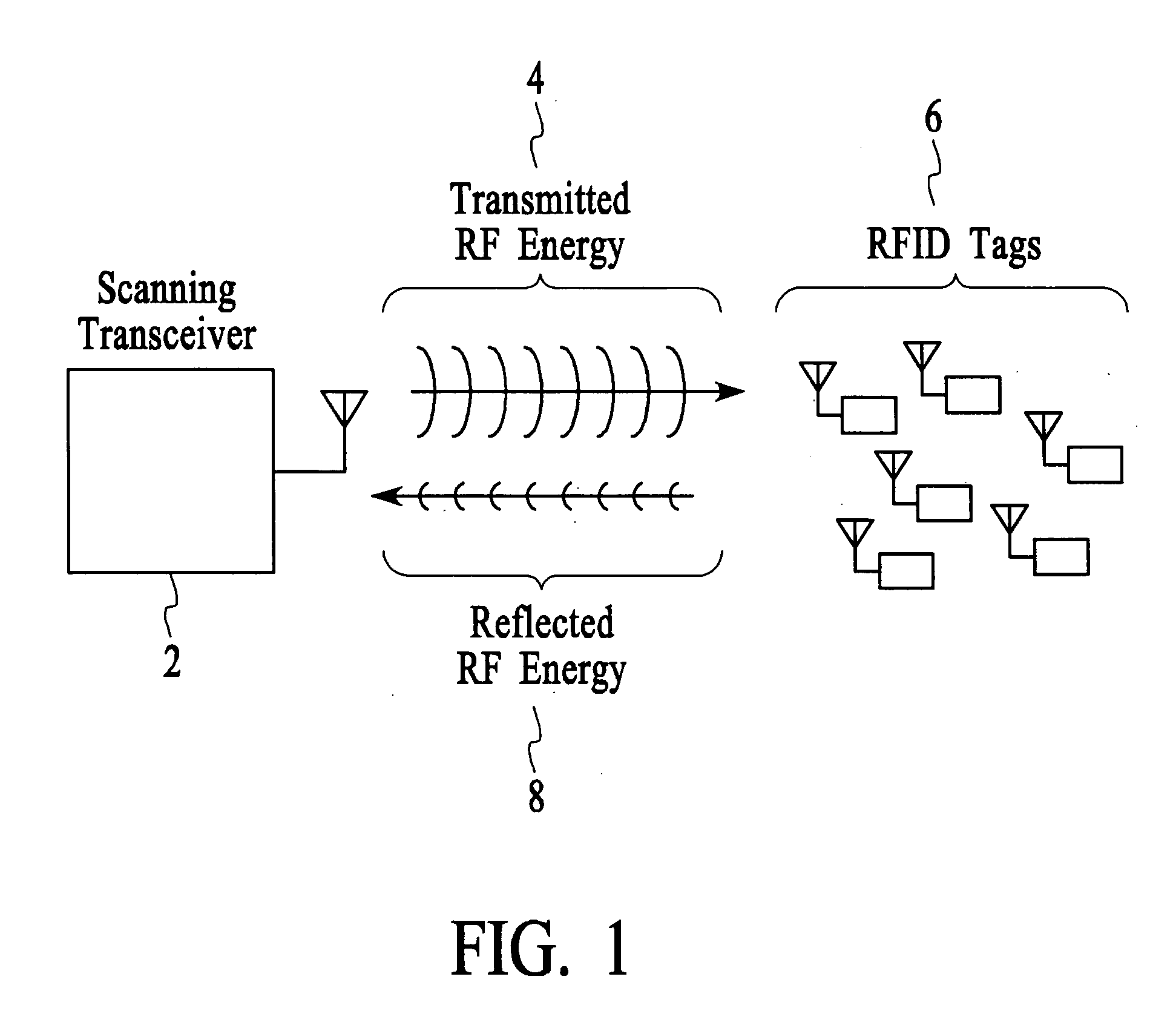
Method and apparatus for efficiently querying and identifying multiple items on a communication channel
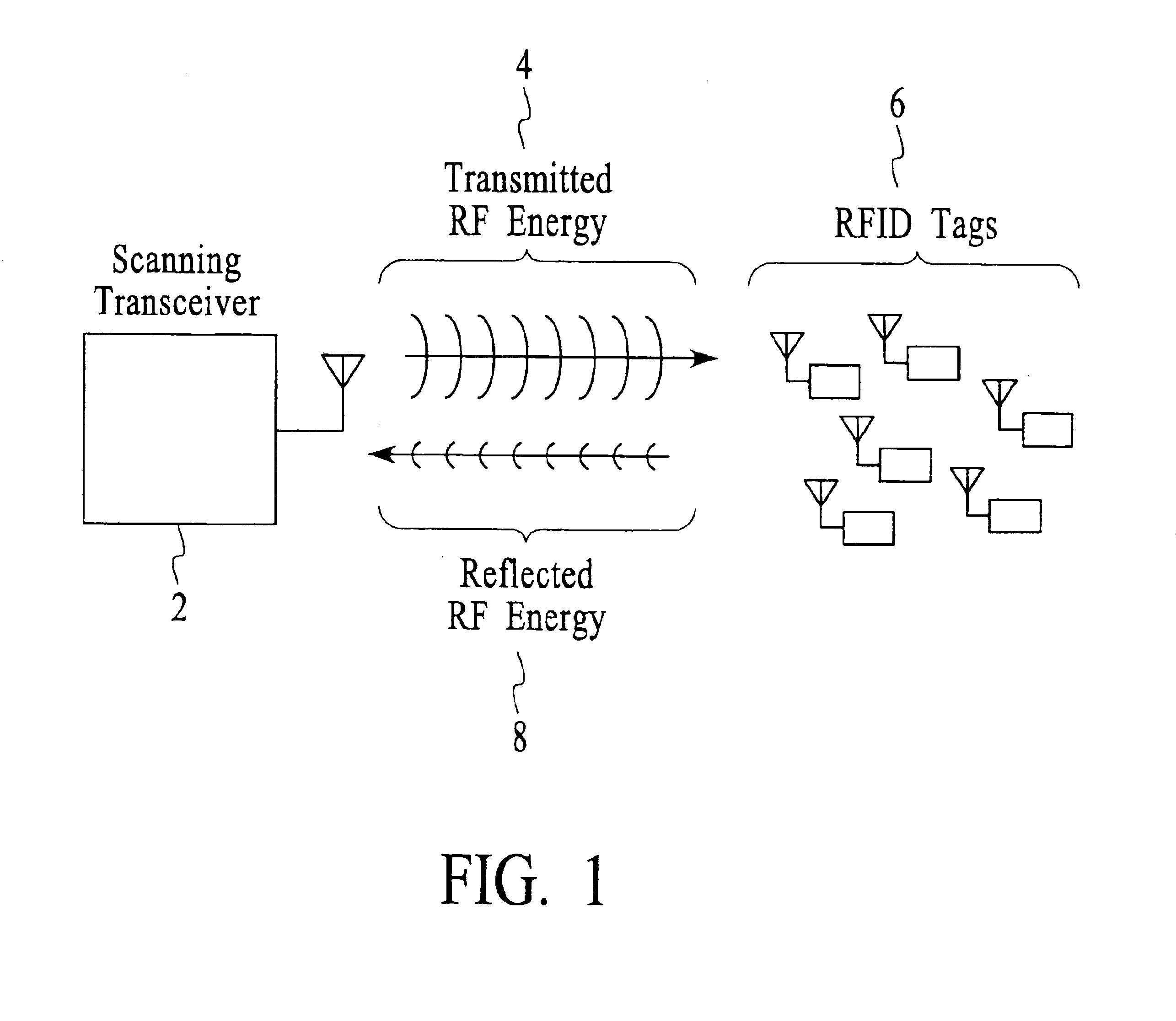
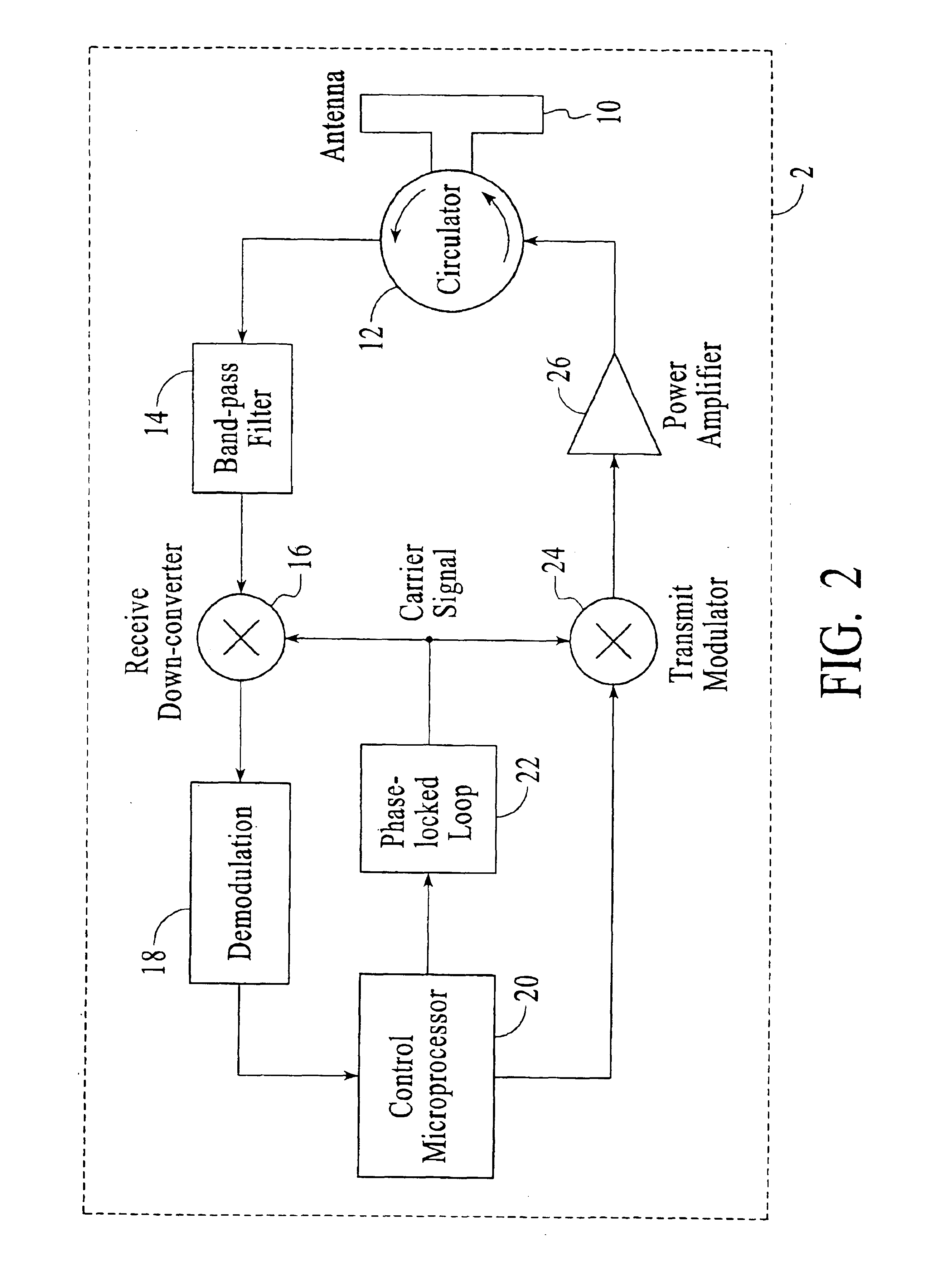
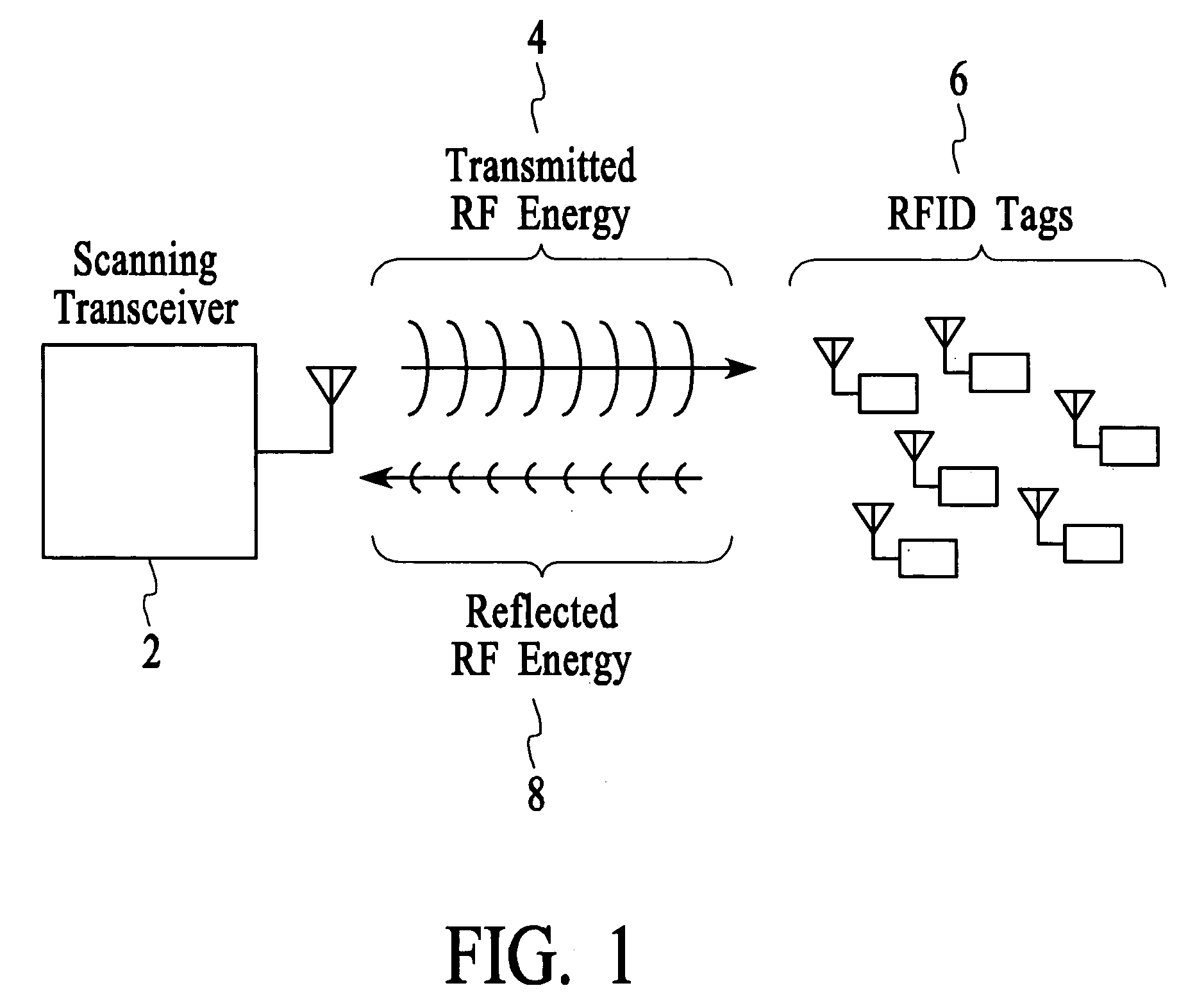
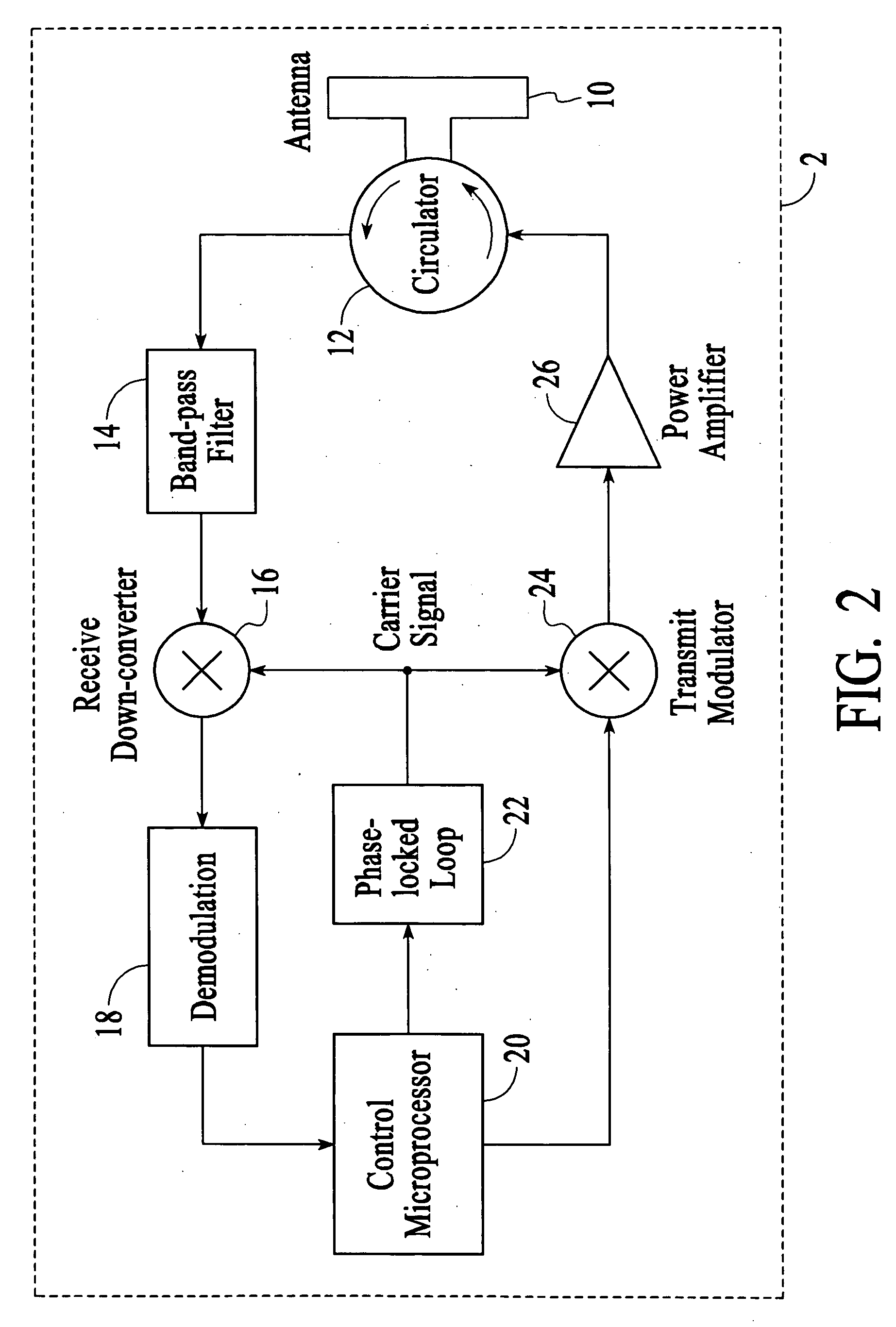
InactiveUS6967564B2Rapid interrogationShort timeMemory record carrier reading problemsTime-division multiplexTree traversalComputer science
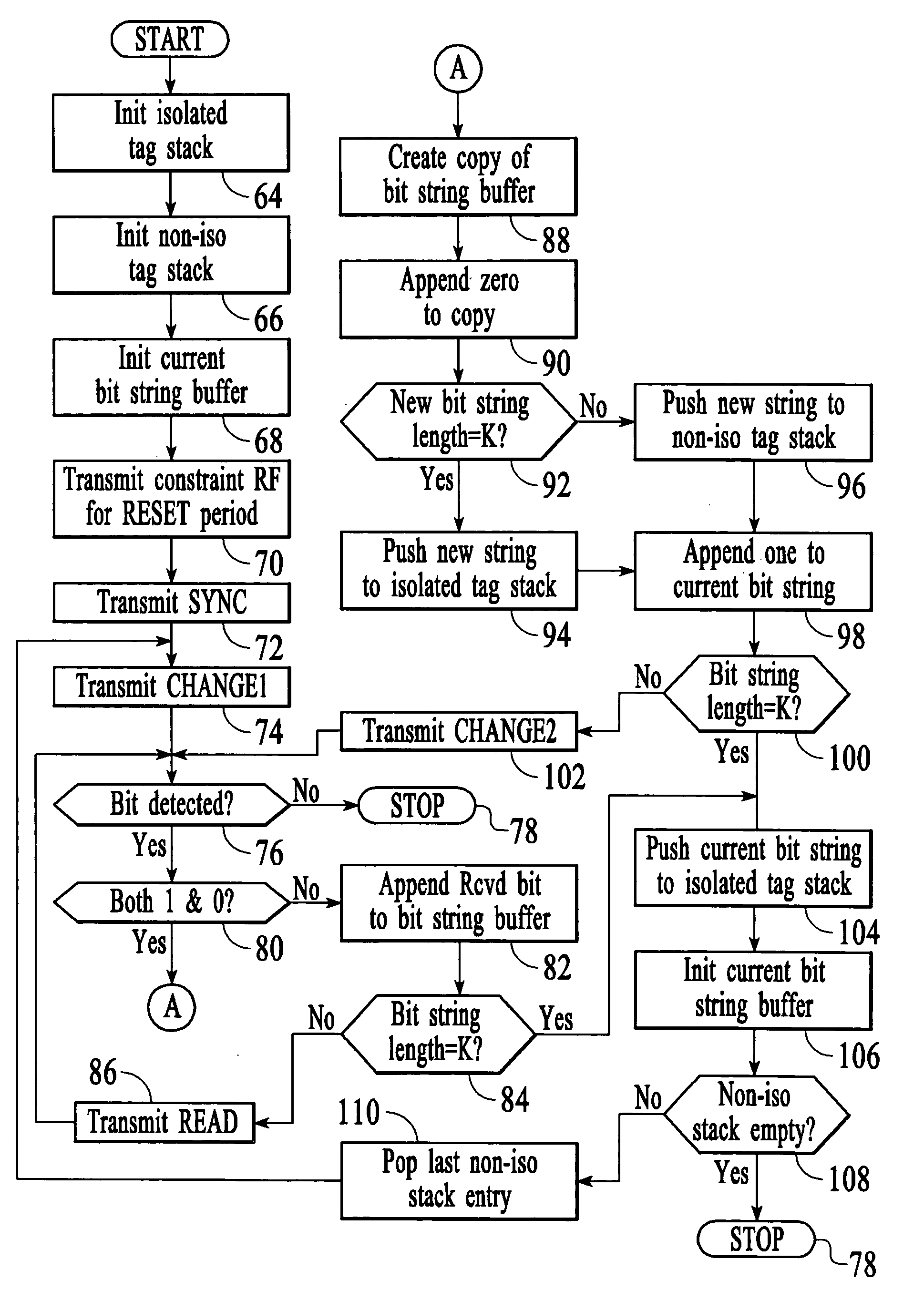
Systems and methods for efficiently querying and identifying multiple items on a communication channel are disclosed. The invention is well suited to use with radio frequency identification with interrogation devices and systems that identify radio frequency identification transponders. A depth-first tree traversal protocol algorithm, including commands and symbols, is used to more efficiently interrogate a plurality of transponders in a short amount of time.
Owner:E TAG SYST
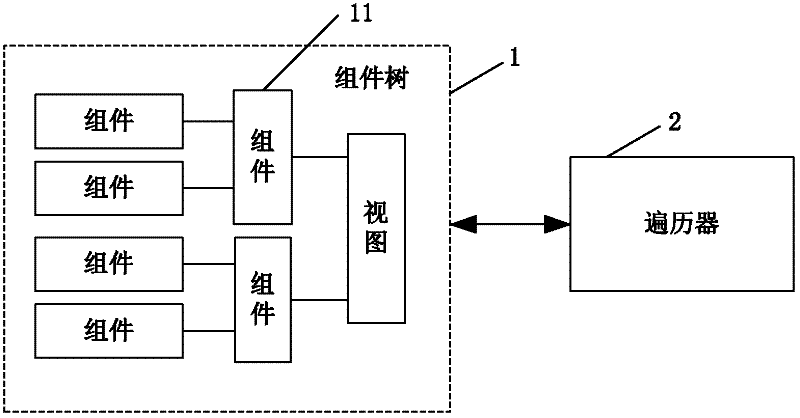
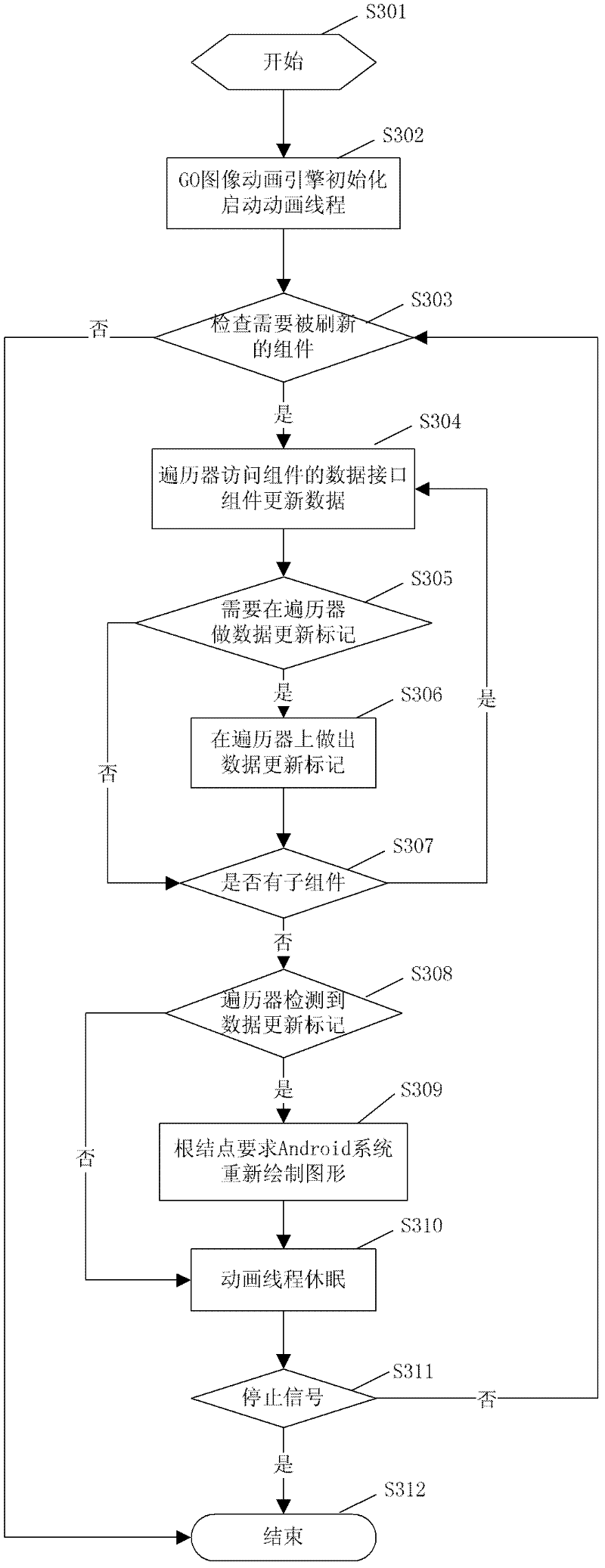
GO image animation engine based on Android system
ActiveCN102385515ASmooth displayRun fastAnimationSpecific program execution arrangementsGraphicsTree traversal
The invention discloses a GO image animation engine based on an Android system, belonging to a drawing device and a drawing method for displaying various animations and graphs on the Android system. The GO image animation engine comprises a component tree and a traversing device, wherein the traversing device traverses the component tree so as to update the data of the components and draw graphs. The technical scheme provided by the invention can present the animations and the graphs on a UI (User Interface) more quickly and preferably at a very smooth speed.
Owner:GUANGZHOU GOMO SHIJI TECH CO LTD
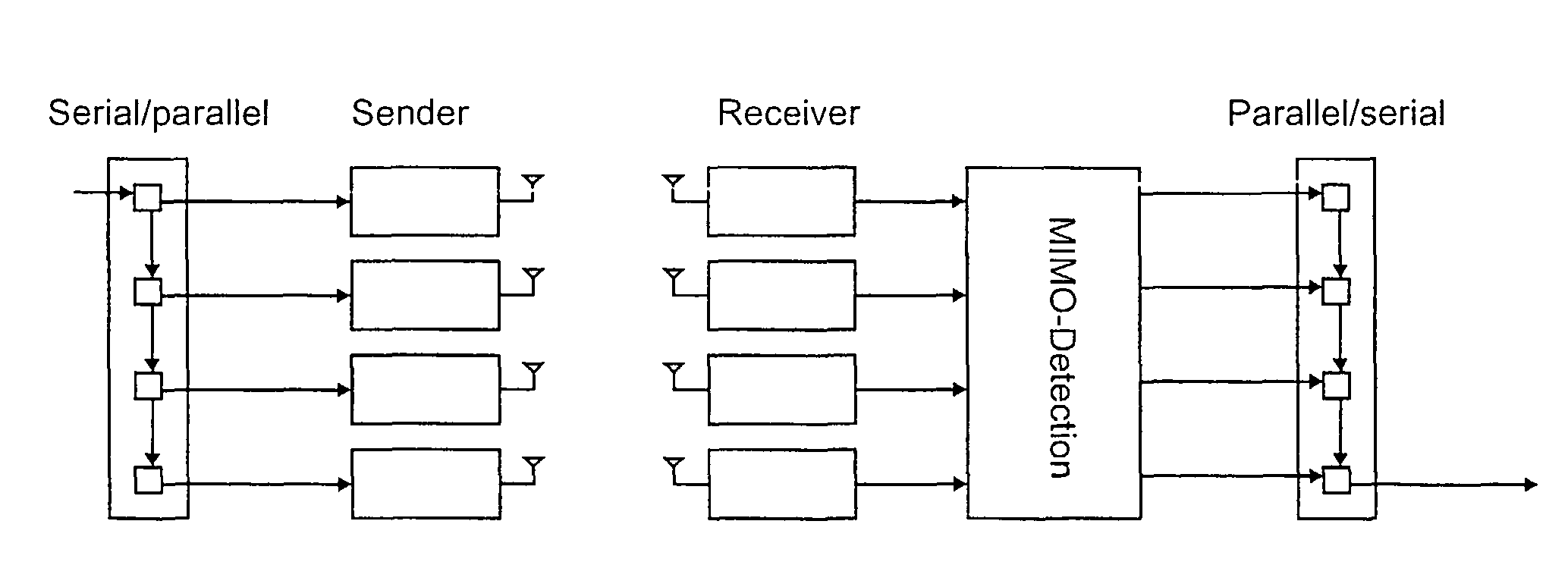
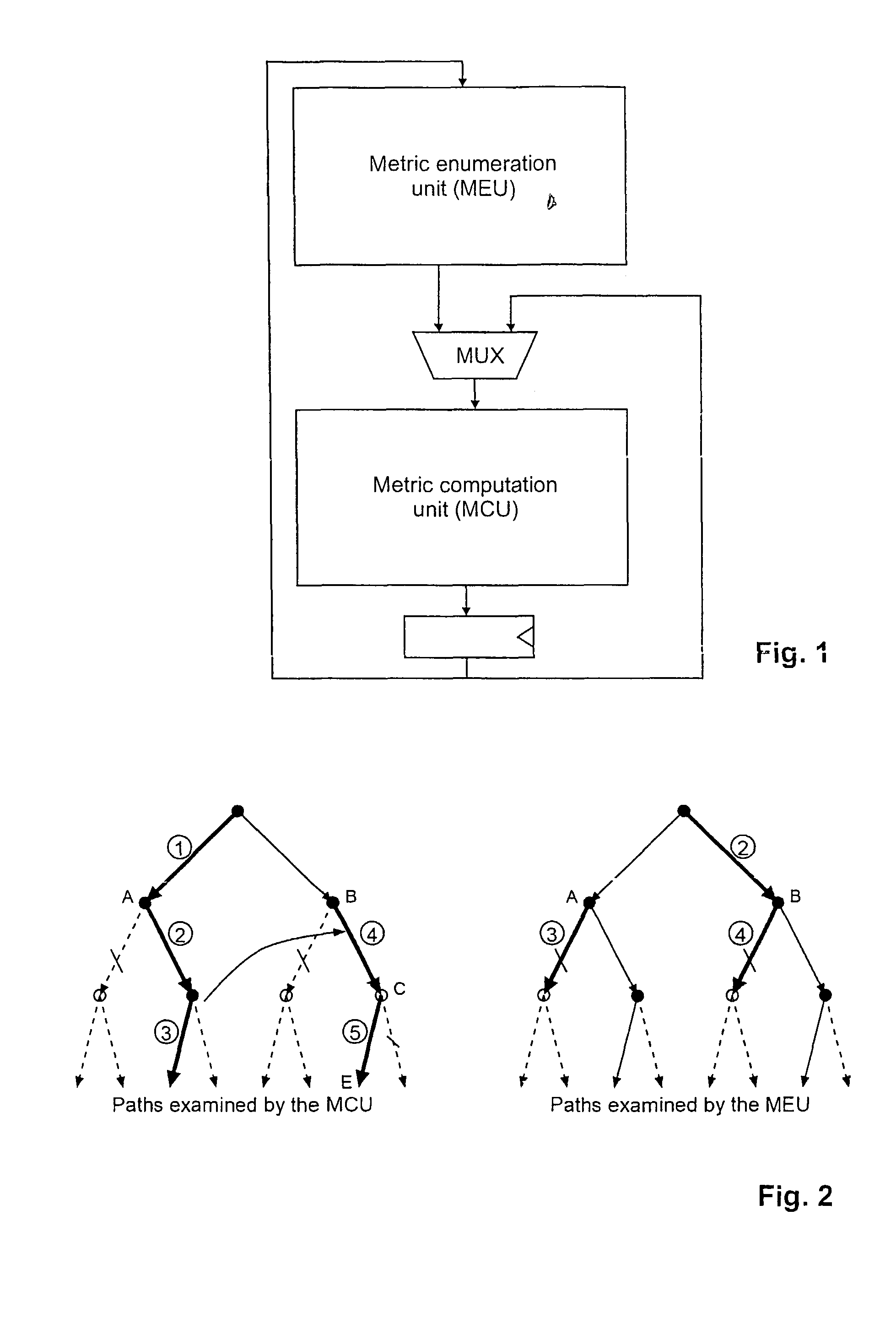
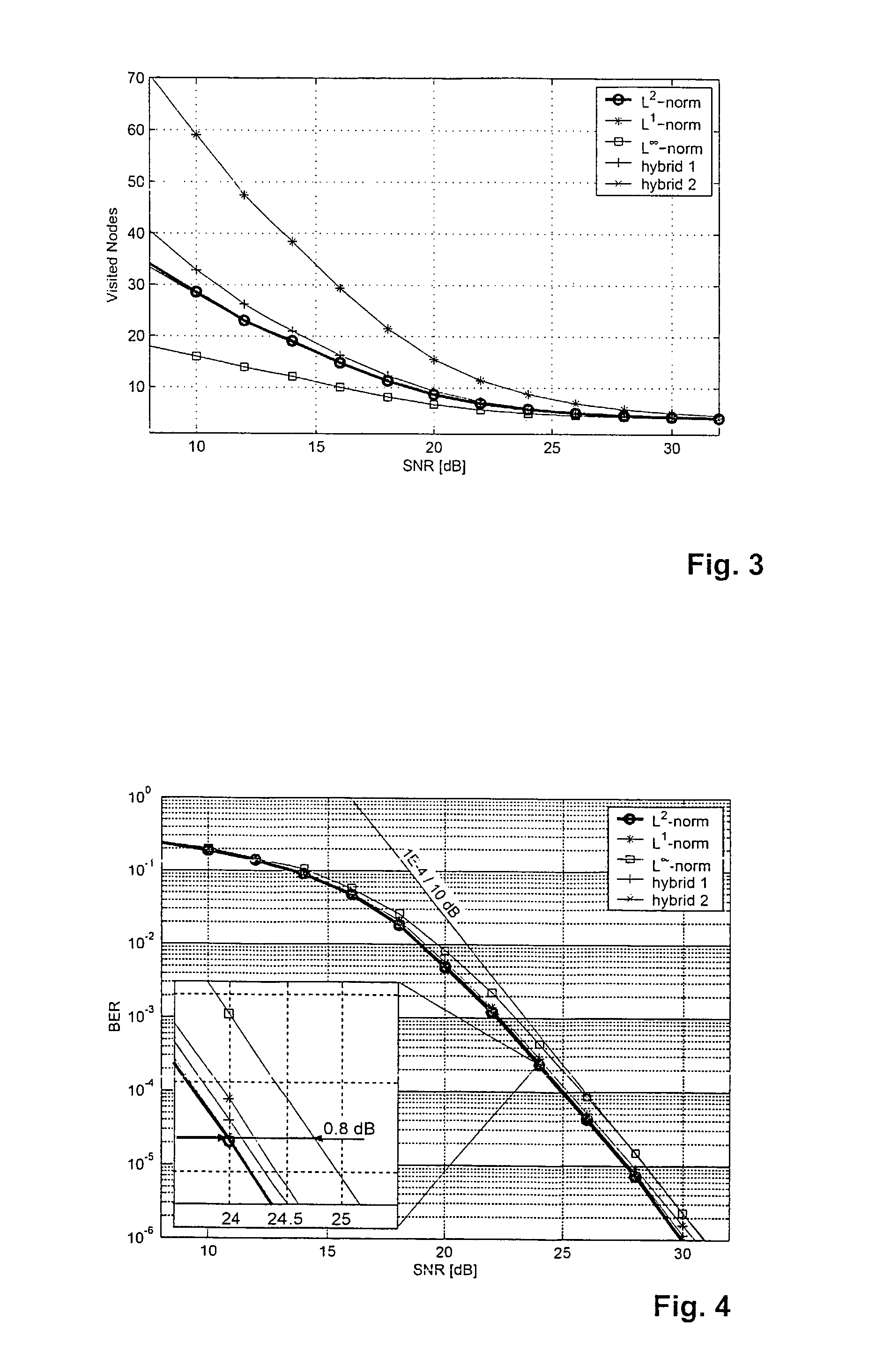
Method and device for decoding a signal of multiple input/multiple output system
InactiveUS7782971B2Efficient implementationReduce error rateDiversity/multi-antenna systemsBaseband systemsQR decompositionDecision boundary
The method for decoding a received signal in a multiple input / multiple output system uses QR-decomposition of the linear channel matrix, but then applies a non-Euclidean norm during tree traversal. Two separate hardware units, namely an MCU and a MEU, art provided for concurrent operation. The MCU determines a next child node, while the MEU determines next best parent nodes on the previously processed tree levels, which makes it possible to retrace the path to a next starting node without investing dedicated processing steps (e.g., cycles). On each tree level, the possible coordinates are grouped into several circular sets in the complex plane, and a series of decision boundaries is calculated for each set that allows a quick evaluation of the optimum coordinate in each set.
Owner:ETH ZZURICH
Method and apparatus for efficiently querying and identifying multiple items on a communication channel
InactiveUS20060103505A1Solve the slow scanning speedQuick identificationMemory record carrier reading problemsSubscribers indirect connectionTree traversalComputer science
Systems and methods for efficiently querying and identifying multiple items on a communication channel are disclosed. The invention is well suited to use with radio frequency identification with interrogation devices and systems that identify radio frequency identification transponders. A depth-first tree traversal protocol algorithm, including commands and symbols, is used to more efficiently interrogate a plurality of transponders in a short amount of time.
Owner:E TAG SYST
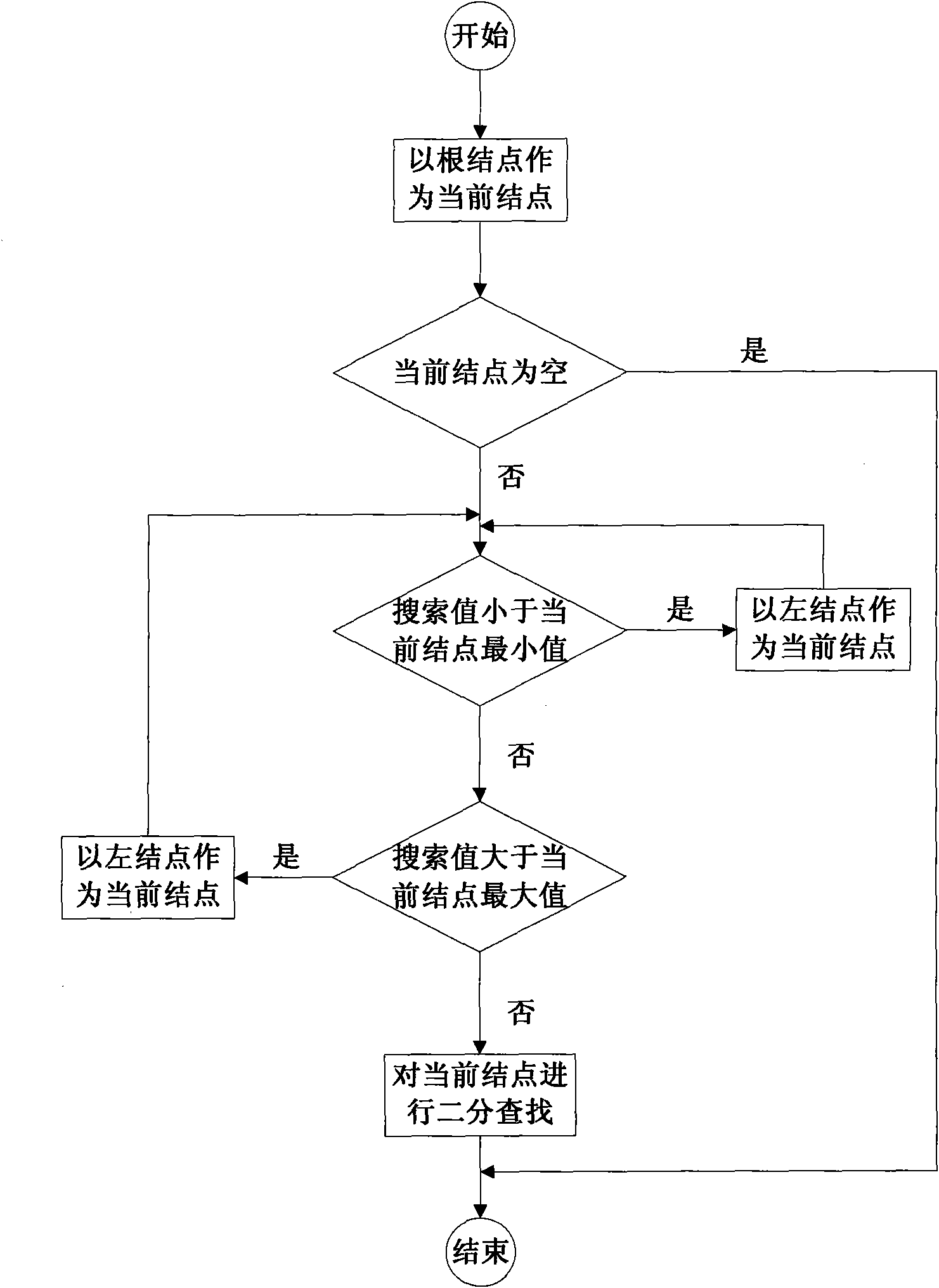
Index method for main storage database based on T-lt tree
InactiveCN101587484AReduce the number of traversalsImprove efficiencySpecial data processing applicationsTree traversalTheoretical computer science
The invention provides an index method for a main storage database based on a T-lt tree, improving the defect of the T tree, adding a tail pointer on each node of the T tree which directly points to a successor of the node to form a T-lt tree. The index method comprises a database inquiring operation, a keyword insertion operation and a keyword deleting operation. The node structure of the T-lt tree has one more tail pointer than the T node. If the node has a tail node, the tail pointer points to the tail node. If the node has no tail node, the tail pointer directly points to the successor. The tail node of the T-lt tree has one more pointer which directly points to the successor than the T node. The method reduces the traversal number to the tree, decrease the rotation number of the tree, can improve the inquiring efficiency in the main storage database and saves the space time spending.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
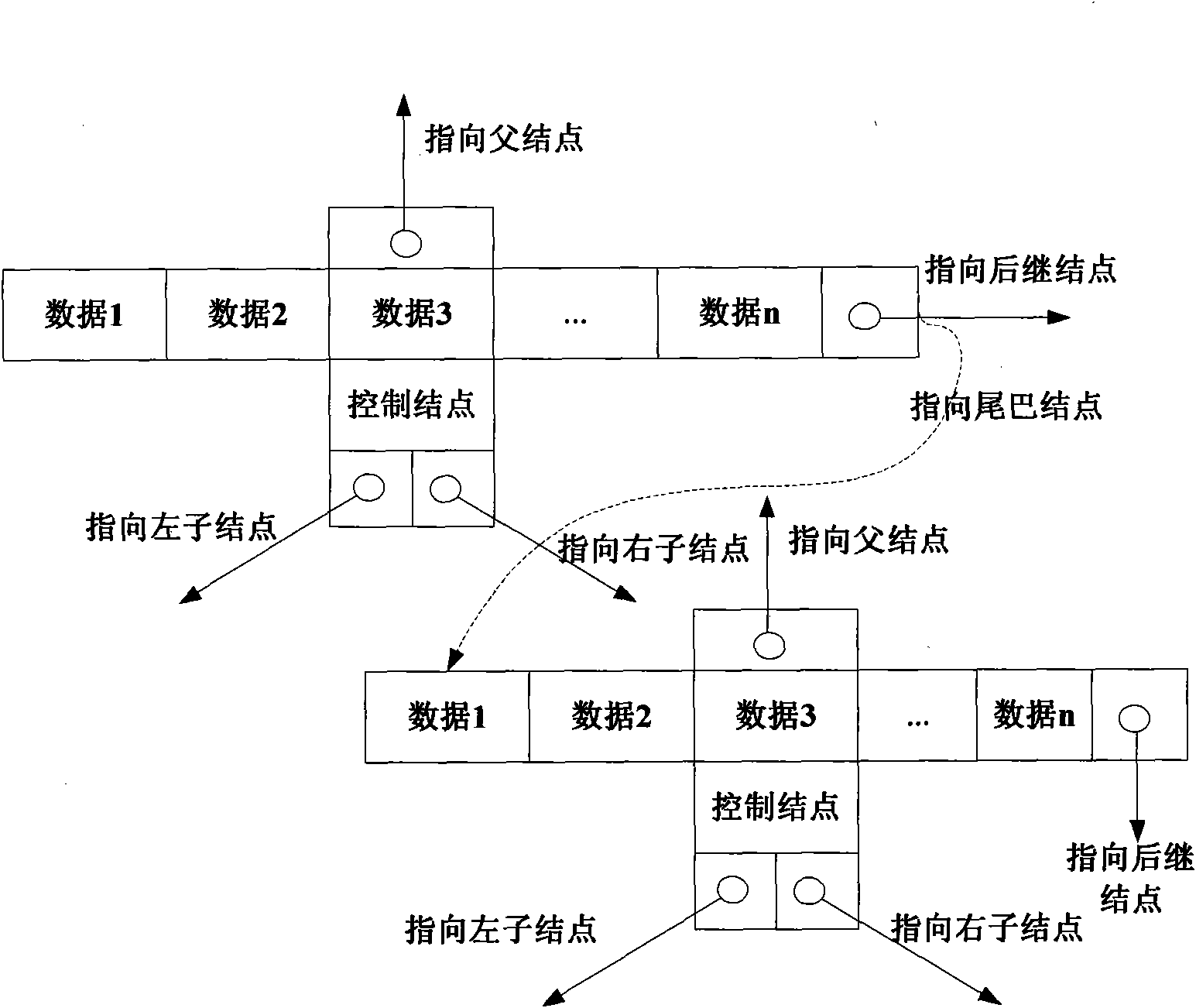
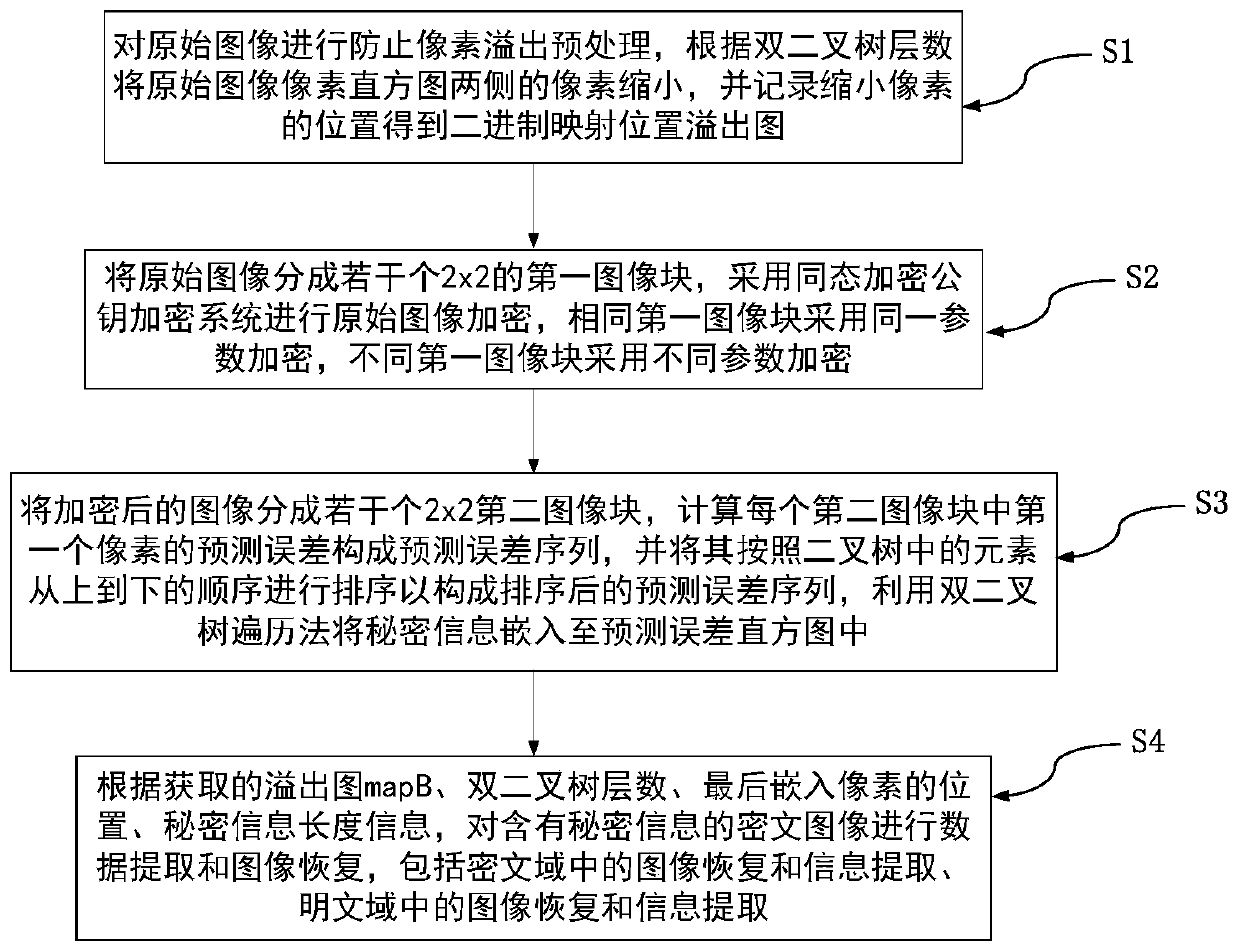
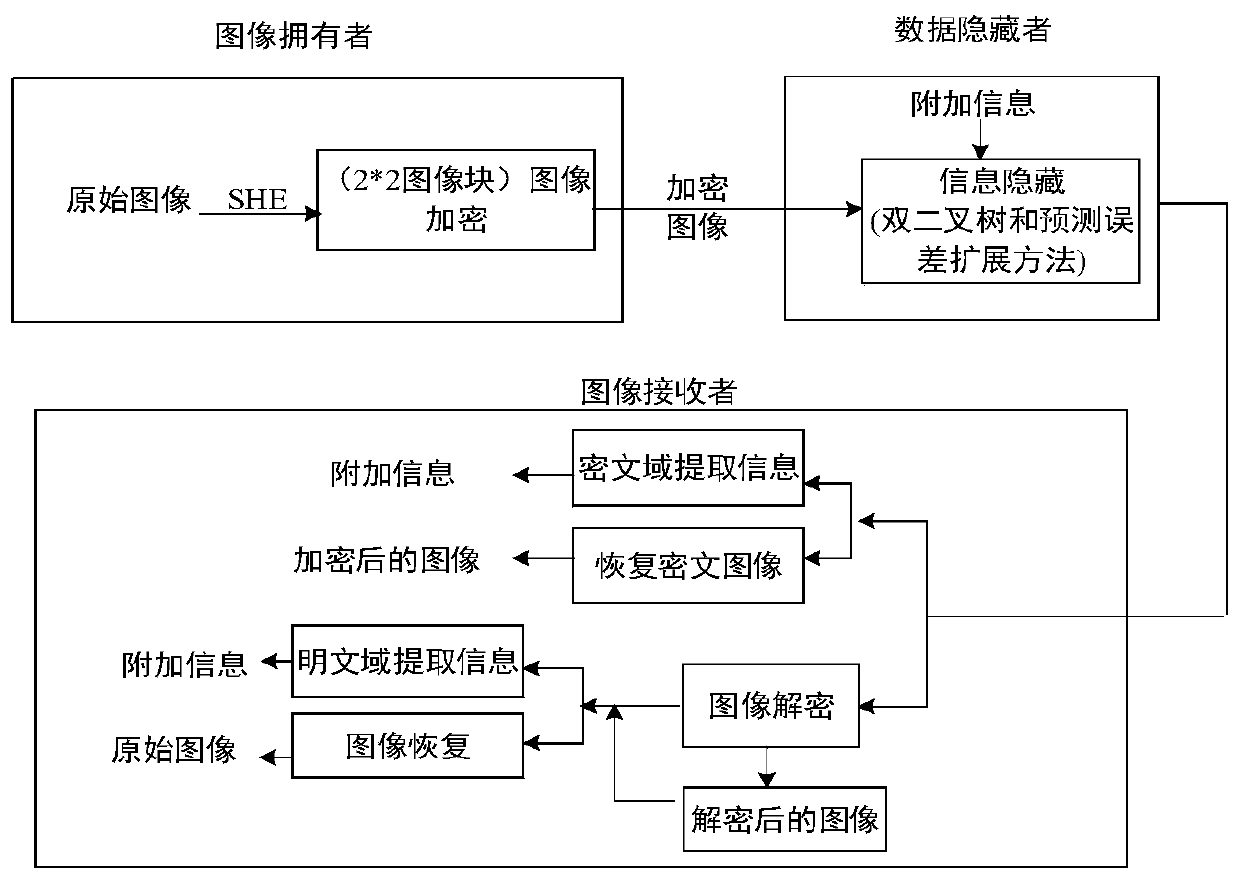
Encryption domain reversible information hiding method based on dual binary tree extension and public key encryption
ActiveCN110337000AEnsure safetyReduce computational complexityDigital video signal modificationCommunication with homomorphic encryptionPlaintextCiphertext
The invention discloses an encryption domain reversible information hiding method based on dual binary tree extension and public key encryption. The method comprises the steps of performing pixel overflow prevention preprocessing on an original image; reducing pixels on the two sides of the pixel histogram of the original image according to the number of layers of the double binary tree; dividingthe original image into a plurality of 2 * 2 first image blocks; encrypting an original image by adopting a homomorphic encryption public key encryption system, embedding secret information into a ciphertext image by utilizing a dual-binary tree traversal and prediction error extension method, and achieving image recovery and information extraction in a ciphertext domain and / or a plaintext domainaccording to a data hiding key and a decryption key. According to the encryption domain reversible information hiding method based on dual binary tree extension and public key encryption, the aspects of encryption cost, secret information embedding capacity, decrypted image quality and the like are greatly improved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
A method to rank documents by a computer, using additive ensembles of regression trees and cache optimisation, and search engine using such a method
ActiveUS20180217991A1Reduce scoring timeImprove recallEnsemble learningInference methodsDocumentation procedureData set
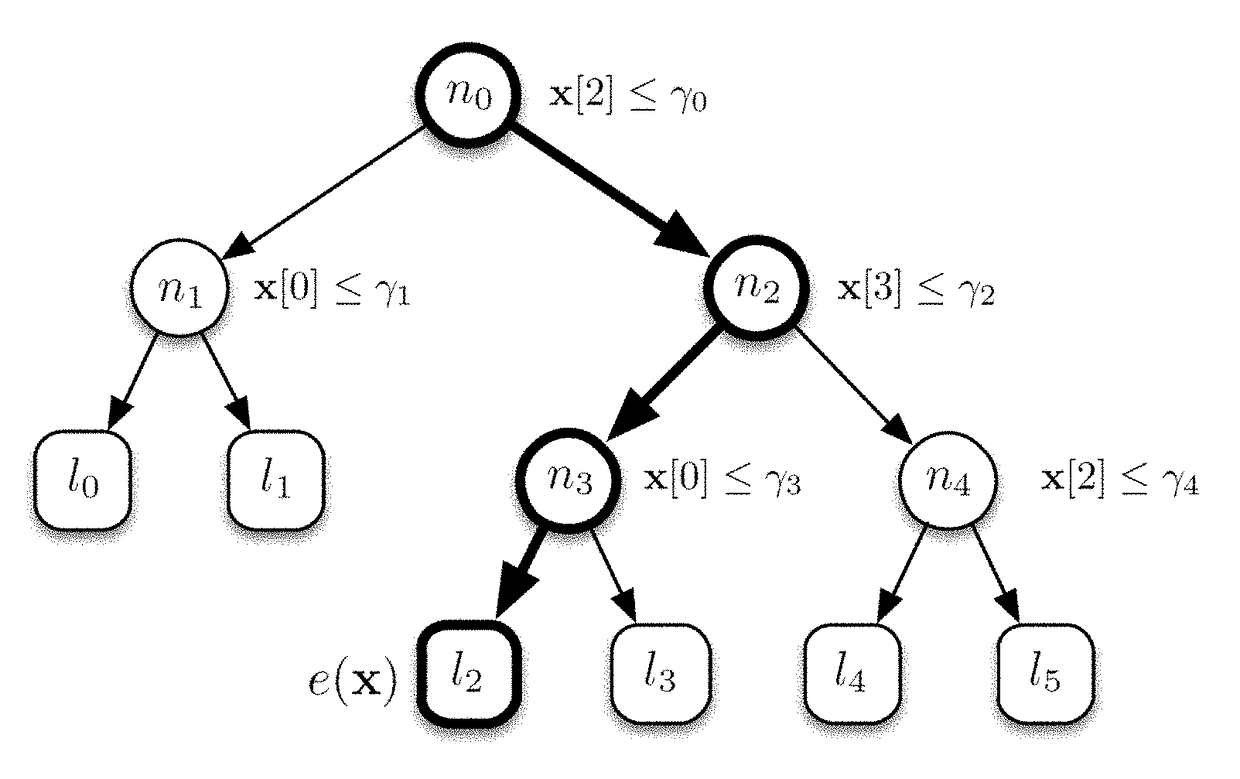
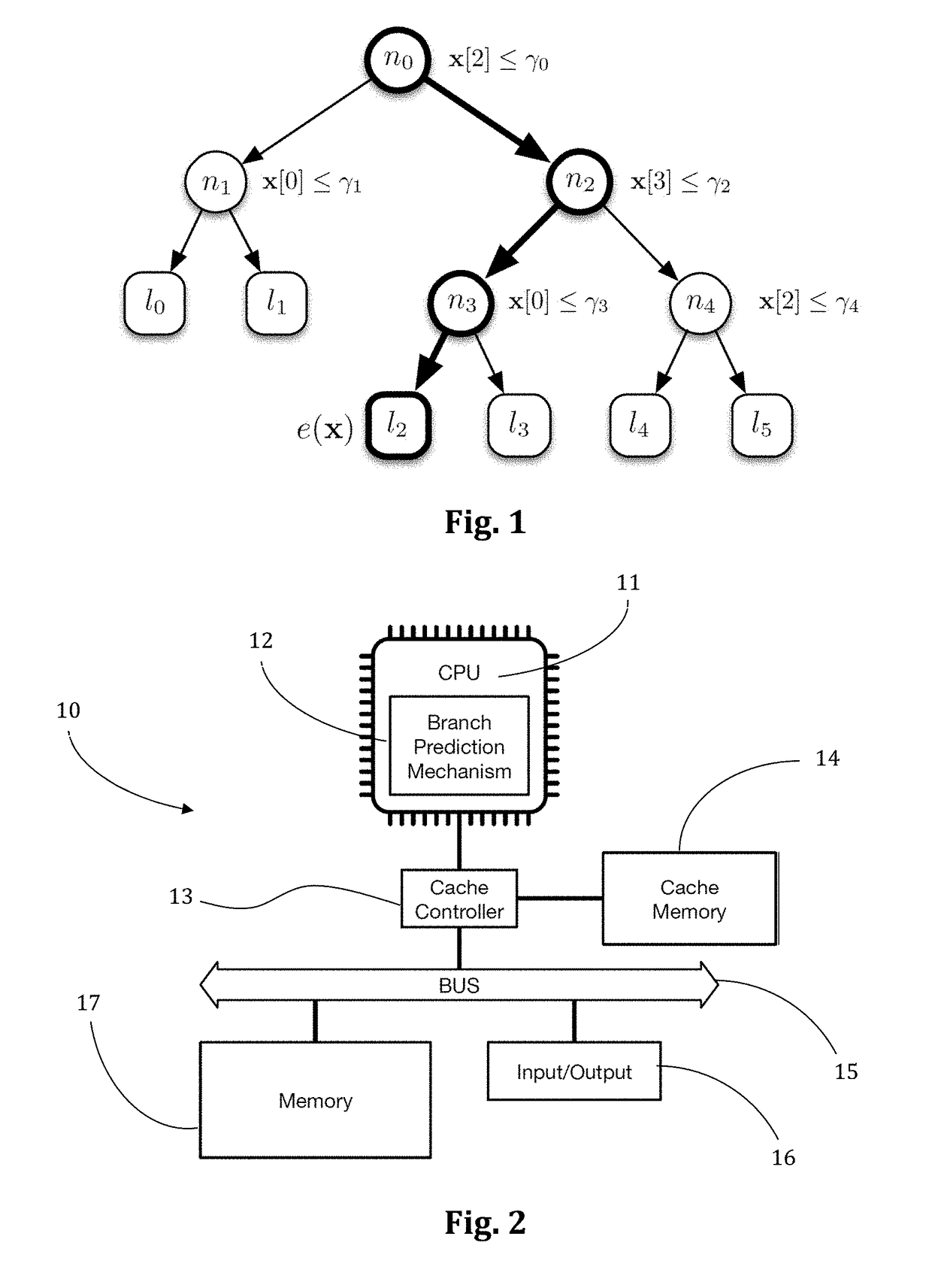
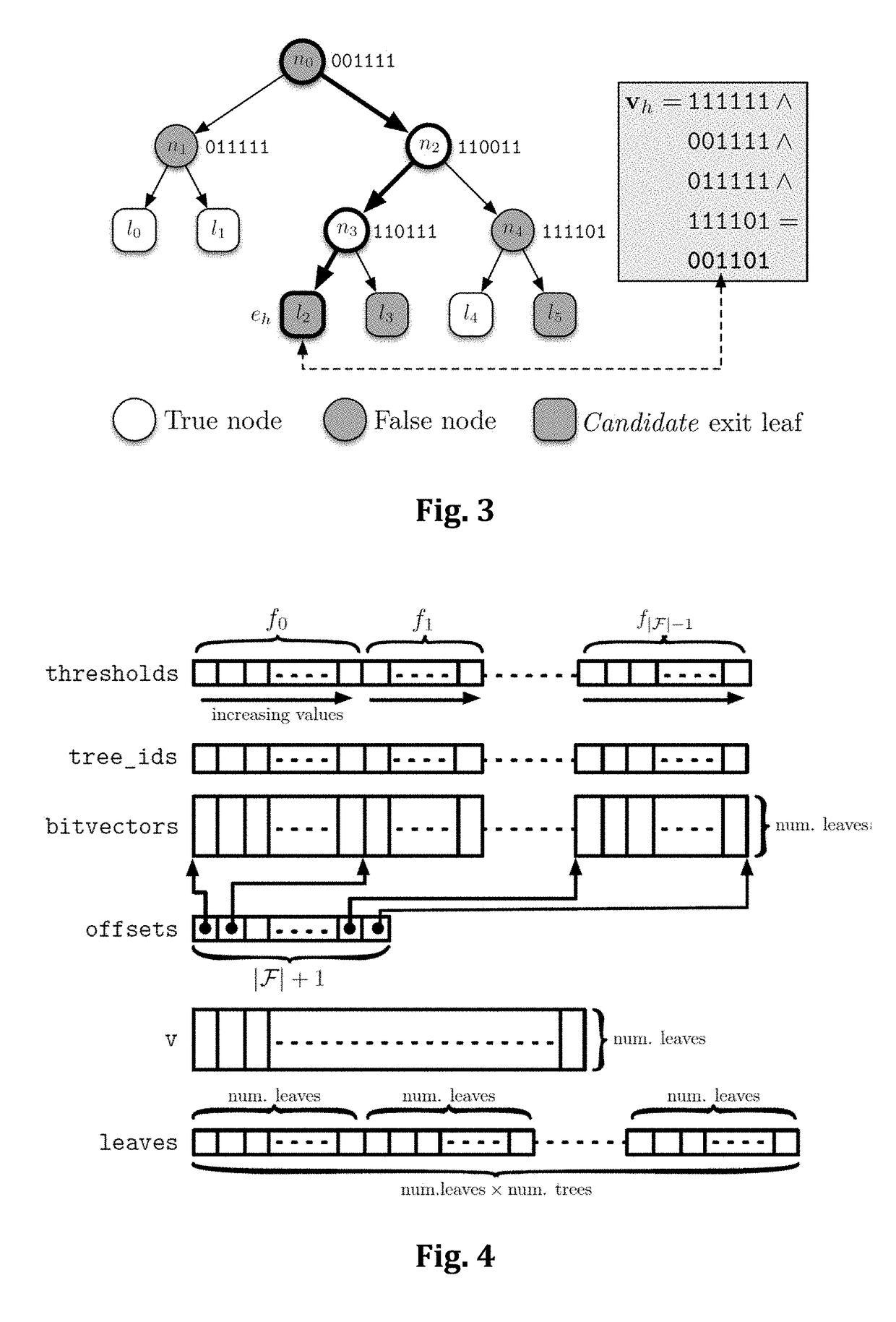
The present invention concerns a novel method to efficiently score documents (texts, images, audios, videos, and any other information file) by using a machine-learned ranking function modeled by an additive ensemble of regression trees. A main contribution is a new representation of the tree ensemble based on bitvectors, where the tree traversal, aimed to detect the leaves that contribute to the final scoring of a document, is performed through efficient logical bitwise operations. In addition, the traversal is not performed one tree after another, as one would expect, but it is interleaved, feature by feature, over the whole tree ensemble. Tests conducted on publicly available LtR datasets confirm unprecedented speedups (up to 6.5×) over the best state-of-the-art methods.
Owner:TISCALI SPA
HThe invention discloses a human body behavior identification method and system based on attention perception and a tree skeleton point structure
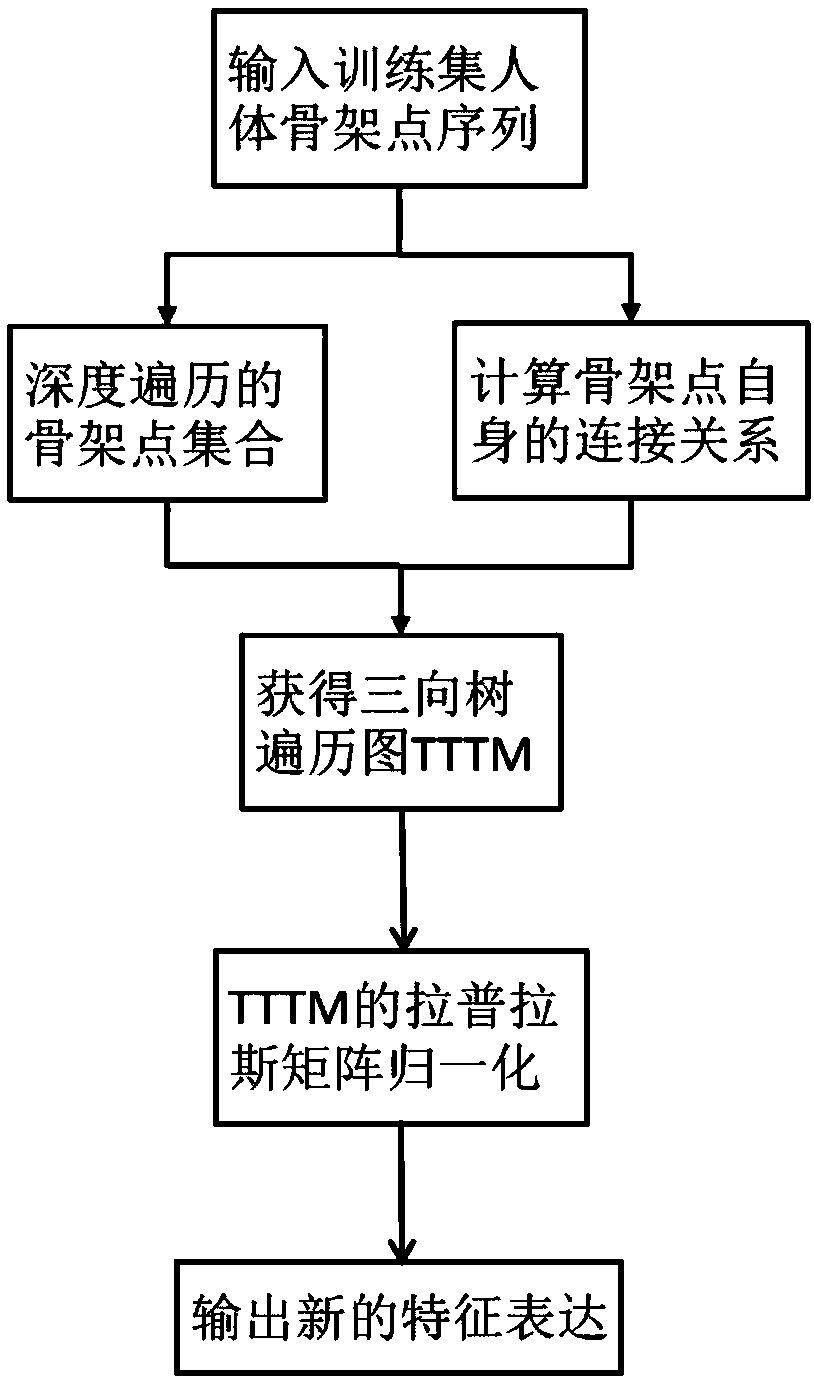
ActiveCN109614874AReduce distractionsHigh precisionCharacter and pattern recognitionEnergy efficient computingZero paddingHuman body
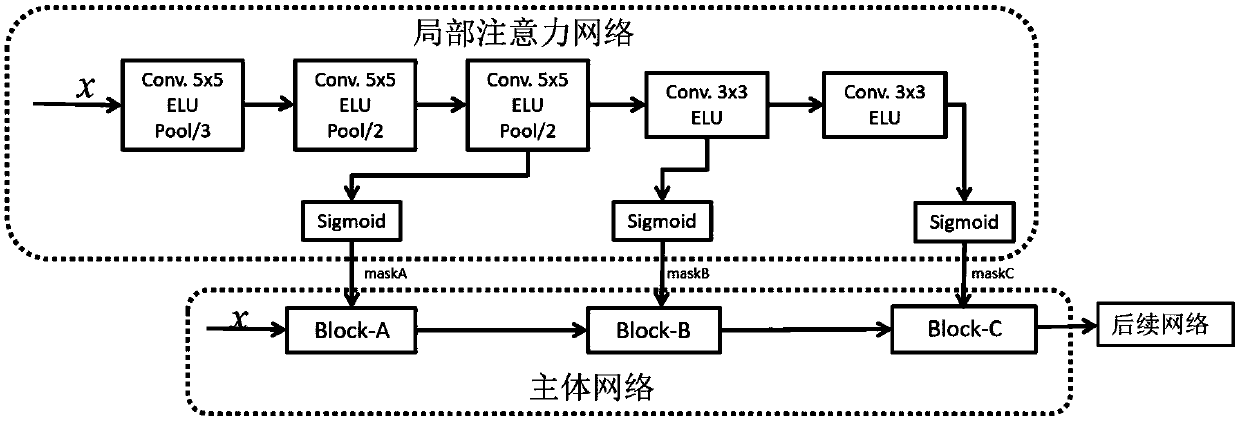
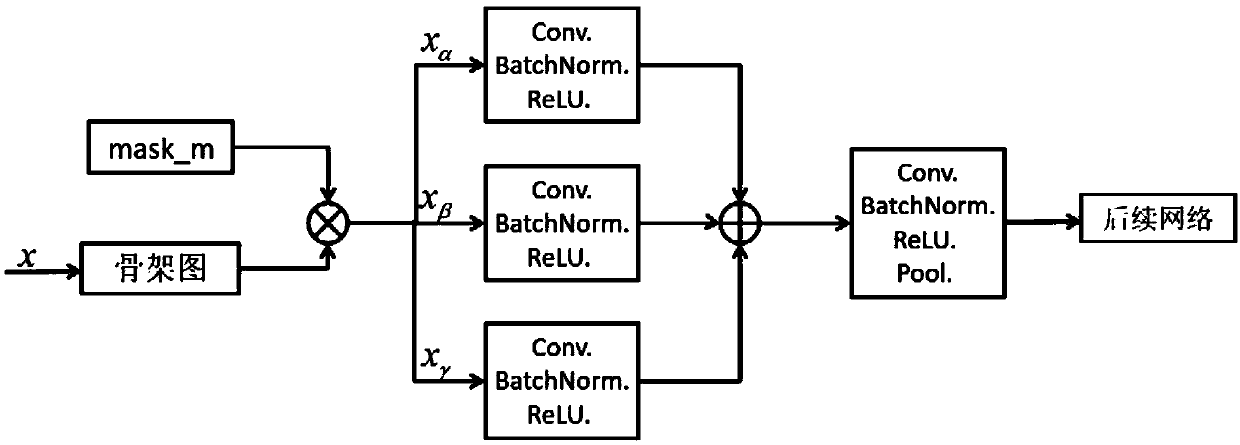
The invention discloses a human body behavior identification method and system based on attention perception and a tree skeleton point structure. The method comprises the following steps: 1) inputtingskeleton point information of all behavior samples in a training set; 2) enabling the number of frames of each sample to be consistent by adding a zero-padding frame; 3) reconstructing disordered skeleton points by using a three-way tree traversal rule; 4) performing normalization processing on the Laplacian matrix of the feature map obtained after reconstruction; 5) constructing an attention perception network and a main body network; T. The behavior recognition method comprises the steps of (1) establishing a behavior recognition network model, (2) establishing a behavior recognition network model, (6) connecting the attention perception network with the main body network in a hierarchical manner, (7) inputting the reconstructed feature map into the main body network and the attention perception network respectively to train the behavior recognition network model, and (8) carrying out behavior recognition by utilizing the trained behavior recognition network model.
Owner:深圳市感动智能科技有限公司 +1
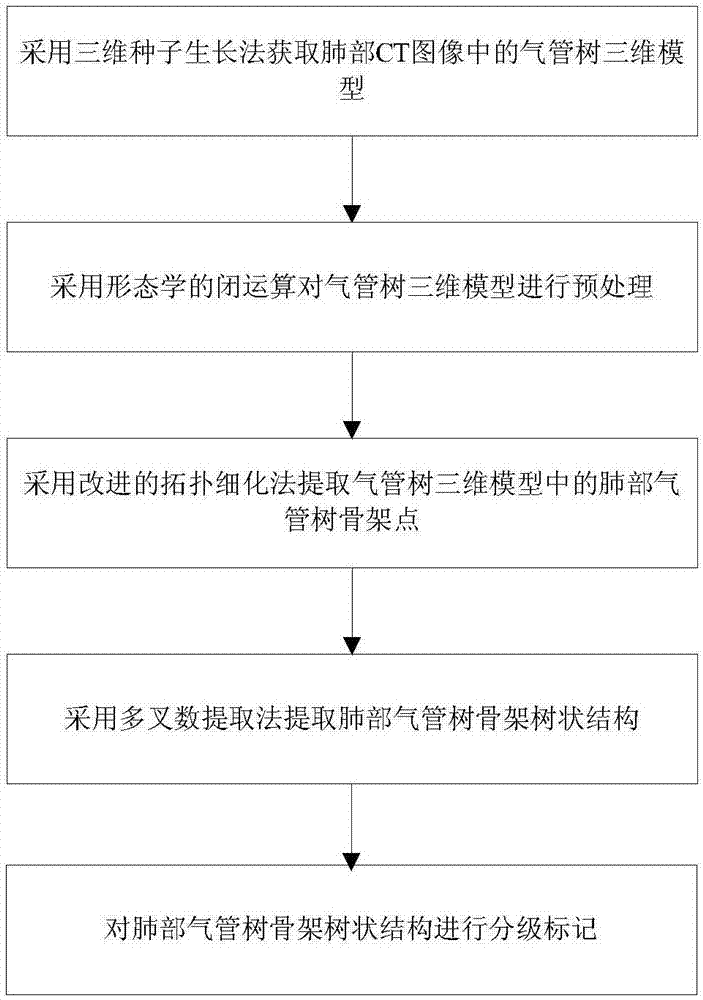
Pulmonary CT image airway three-dimensional skeleton dendritical structure extracting and marking method
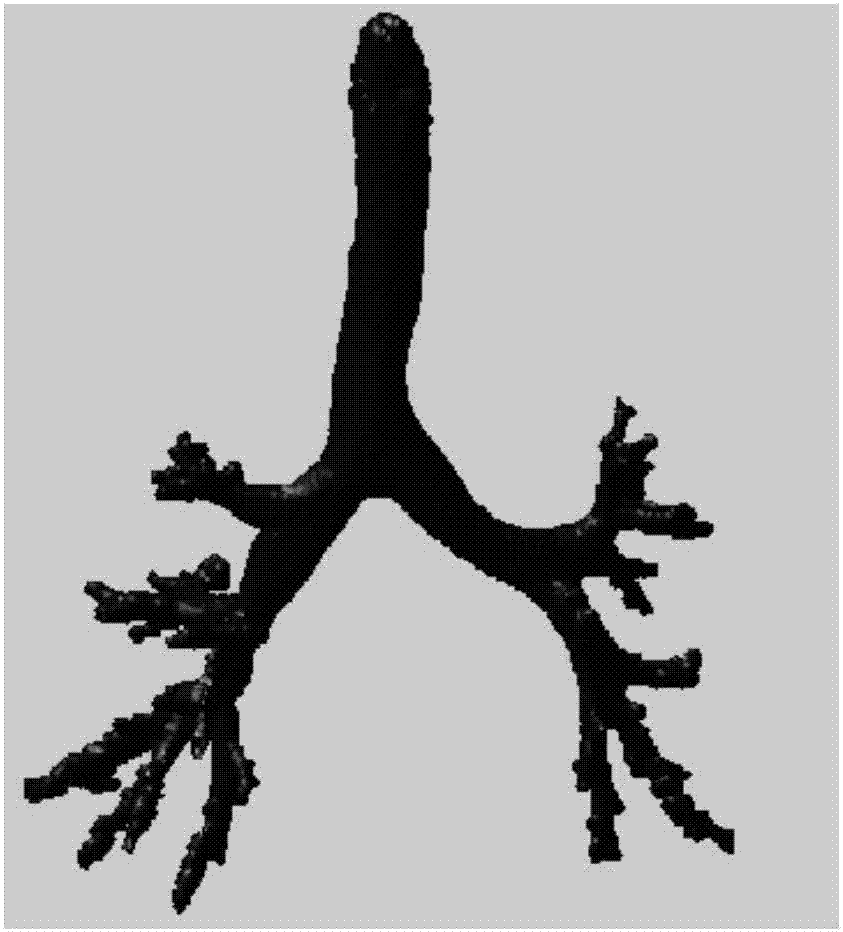
The invention provides a pulmonary CT image airway three-dimensional skeleton dendritical structure extracting and marking method. The method comprises the steps that a three-dimensional seed growth method is used to acquire a tracheal tree three-dimensional model in a pulmonary CT image; morphological closed operation is used to preprocess the tracheal tree three-dimensional model; pulmonary tracheal tree skeleton points in the tracheal tree three-dimensional model are extracted through an improved topological refinement method; a pulmonary tracheal tree skeleton dendritical structure is extracted through a multi-fork number extraction method; and grading marking is carried out on the pulmonary tracheal tree skeleton dendritical structure. According to the method provided by the invention, when the pulmonary tracheal tree skeleton of a human body is extracted, the topological refinement method is used and improved on the basis of the method; a corresponding solution is provided according to a special situation in a human pulmonary tracheal tree segmentation image; the algorithm practicality is improved; the idea of multi-fork tree traversal is used to extract the pulmonary tracheal tree dendritical structure of the human body, and at the same time the dendritical structure is graded; and the method laids the foundation for the quantitative analysis of the human pulmonary tracheal tree.
Owner:NORTHEASTERN UNIV LIAONING
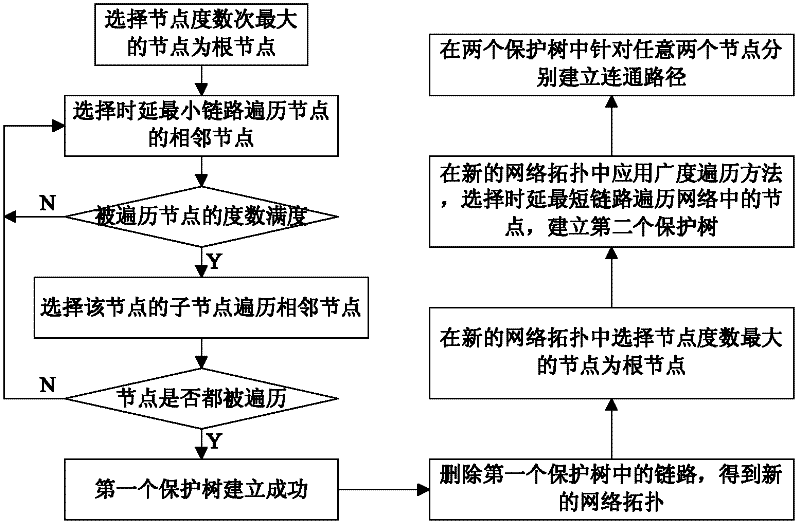
Non-fullness complete-non-correlation double-tree traversal protection method in mesh network
InactiveCN102395131ANo conflictReduce transmission delayTransmissionNetwork planningResource utilizationTree traversal
The invention discloses a non-fullness complete-non-correlation double-tree traversal protection method in a mesh network. The method comprises the following steps of: providing network topology conditions which are required for establishment of non-fullness complete-non-correlation double trees; and by selecting a node with the maximum node degree as a root node, using time delay as cost and using a breadth-first generation tree algorithm, calculating two protection trees. In the case of causing of a fault in a link or the node (a non-source node, a destination node and the root node) in an operating path, the fault of the link can be subjected to switching of channel protection and link protection, and the fault of the node can be also subjected to switching of the channel protection and the corresponding node protection, so that shorter protection switching time can be provided, higher resource utilization rate can be provided by using the mesh network, and complicated configuration and switching motions can be avoided.
Owner:XI AN JIAOTONG UNIV
Data processing method and system
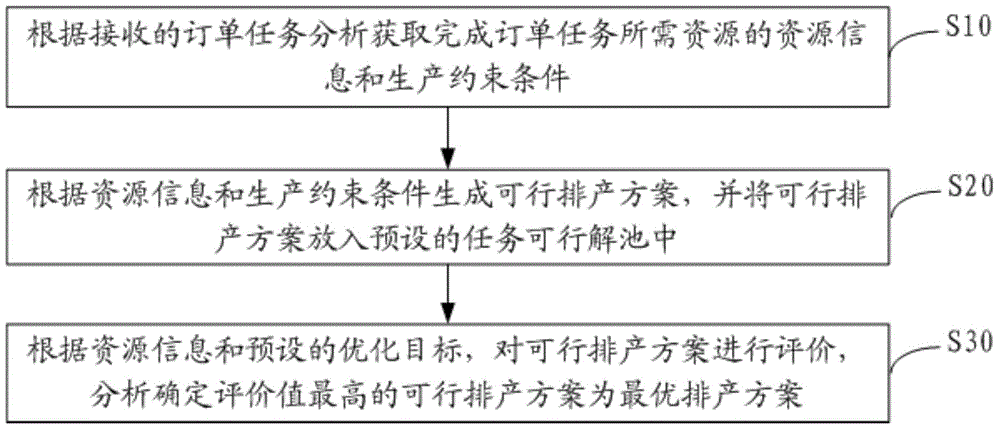
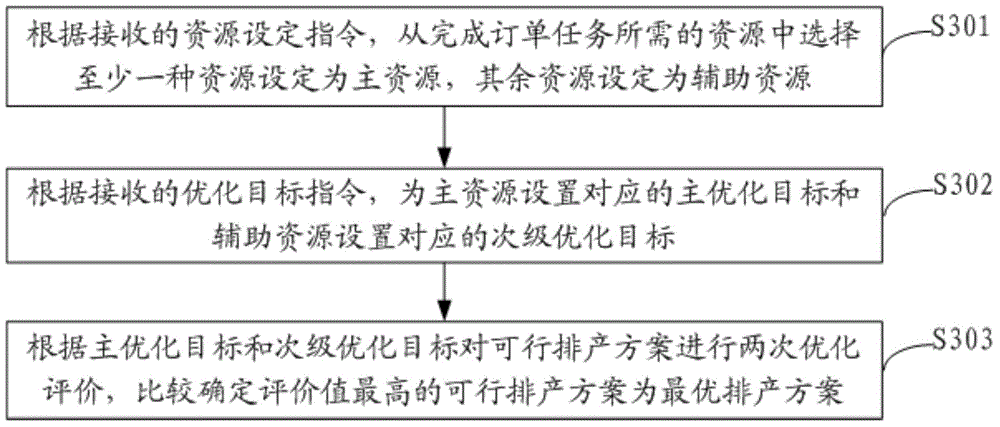
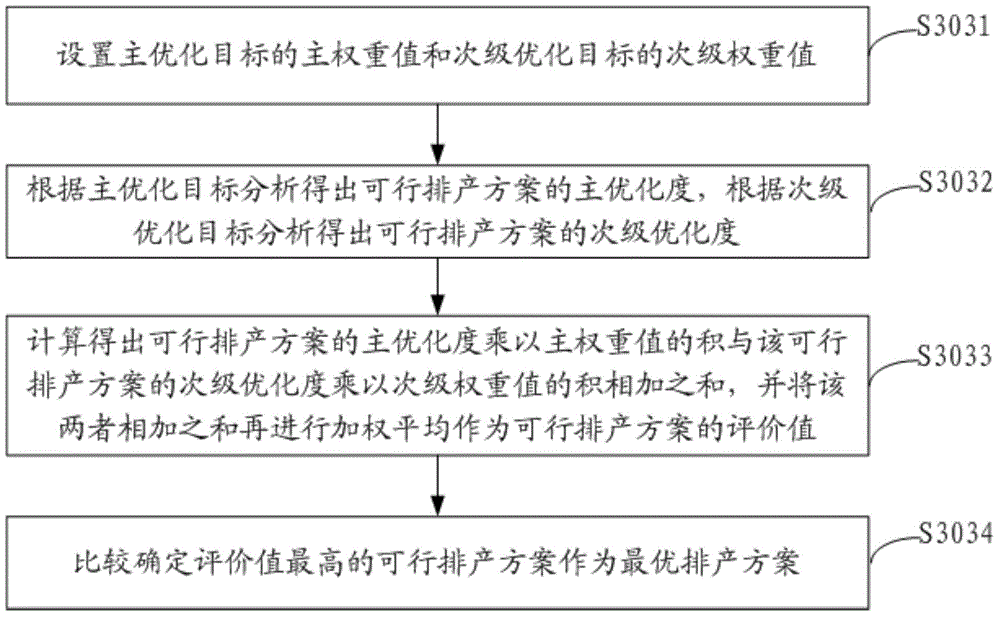
The invention discloses a data processing method. The method includes the steps that according to analysis of received order form tasks, resource information of resources needed for completing the order form tasks and production constraint conditions are obtained; according to the resource information and the production constraint conditions, feasible production scheduling schemes are generated and put into a preset task feasible solution pond; according to the resource information and a preset optimization objective, the feasible production scheduling schemes are evaluated, and the feasible production scheduling scheme with the highest evaluation value is analyzed and determined as the optimal production scheduling scheme. The invention further discloses a data processing system. With the resources as the leading factor, the feasible production scheduling schemes of the current resources are recursively captured and matched and are evaluated according to the preset optimization objective, finally the feasible production scheduling scheme with the highest evaluation value is determined as the optimal production scheduling scheme, the steps are repeated until resource traversal of all production tasks in the order form tasks is completed, and in this way, the technical problems that as a reasonable production scheduling scheme is selected out, duration is prolonged, and cost is increased are solved.
Owner:SHENZHEN VUV TECH CO LTD
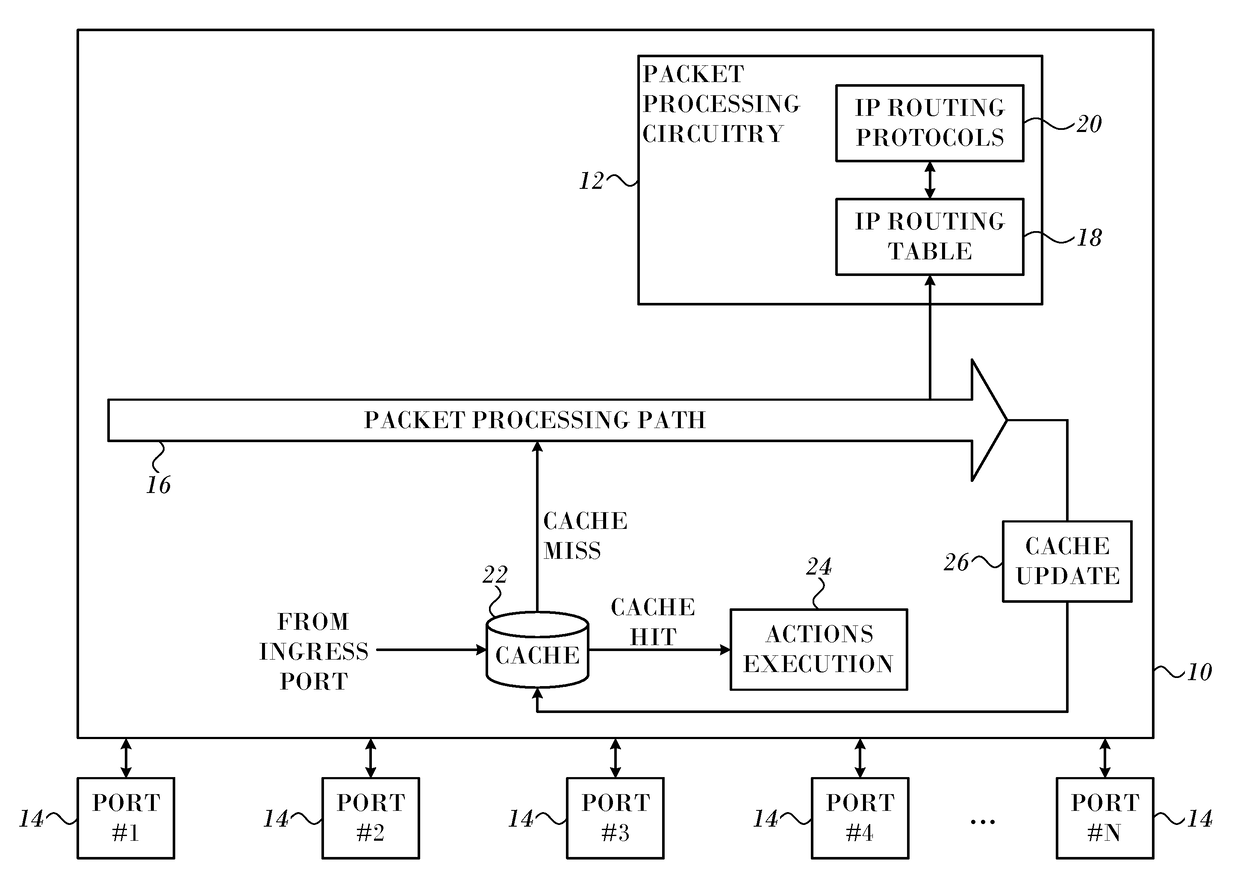
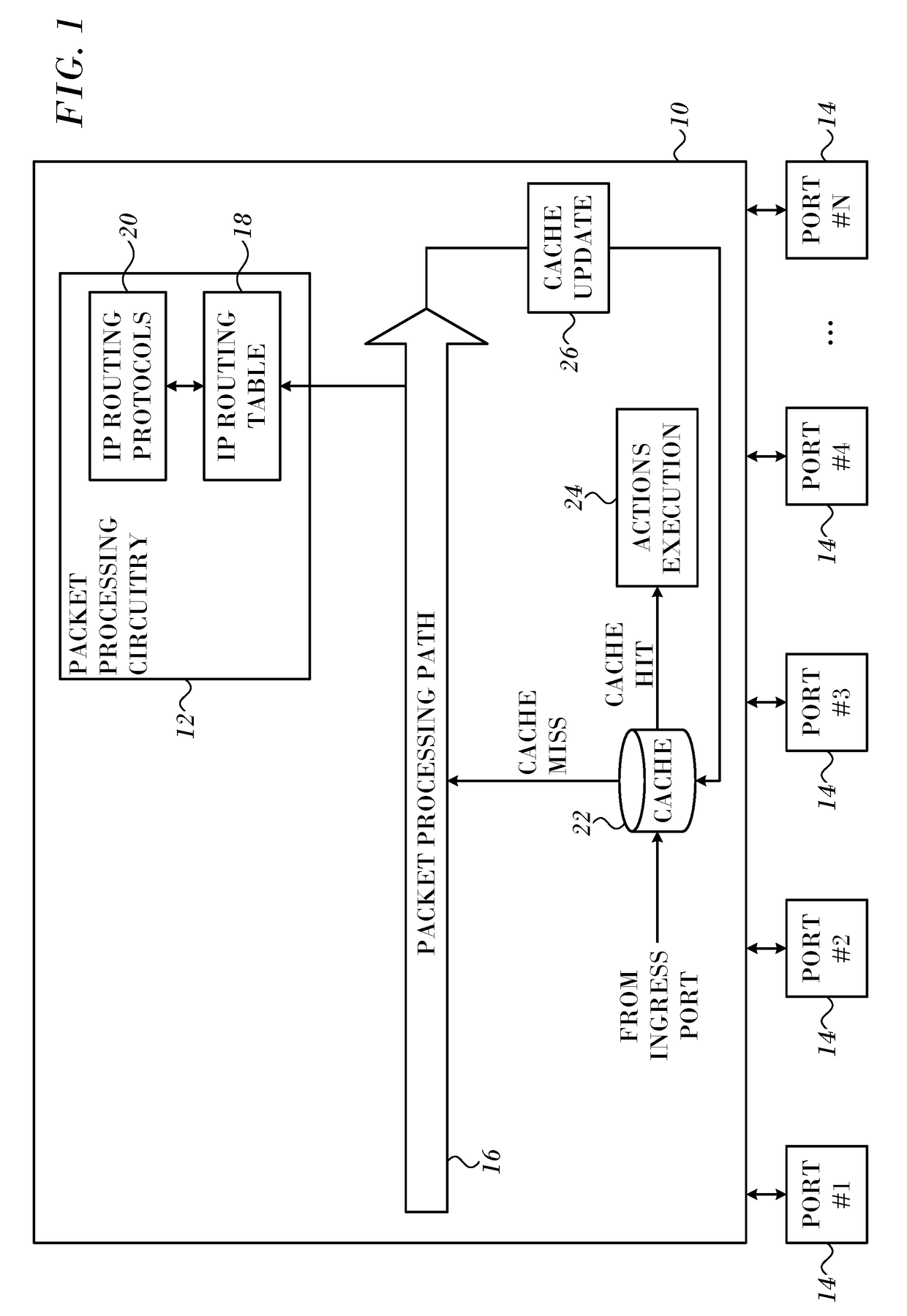
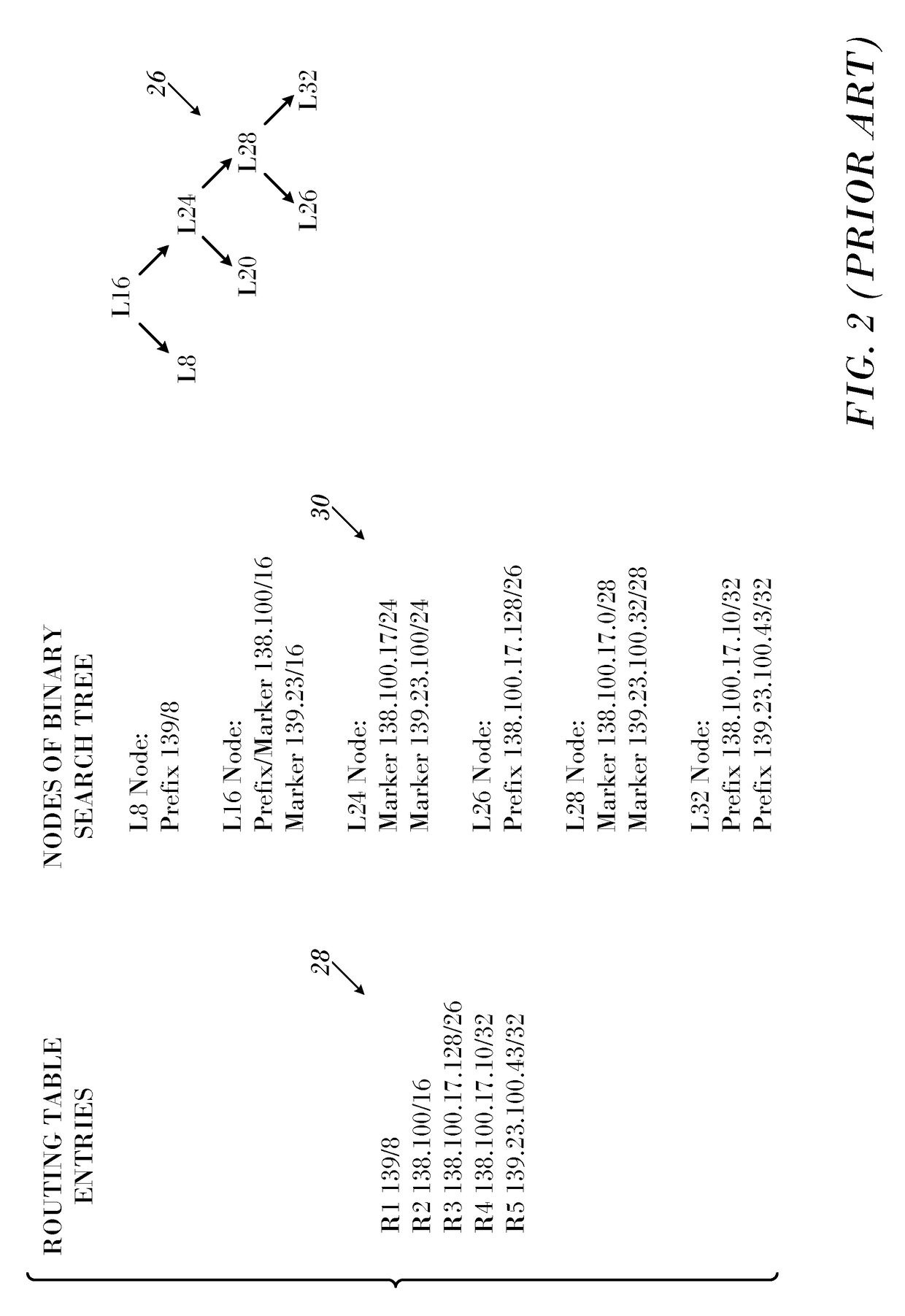
Jump on a Match Optimization for Longest Prefix Match using a Binary Search Tree
ActiveUS20170366459A1Easy to implementReduce visitsData switching networksNetwork packetTree traversal
A routing table is represented as a binary search tree ordered by prefix lengths. Markers are placed to guide accessing nodes in designated subtrees to search for a longest prefix match with destination addresses of data packet. Destination descendant nodes in remote hierarchical levels of the tree are associated with the markers. The traversal of the binary search tree is conducted by accessing the respective destination descendant nodes while avoiding accessing nodes in intermediate hierarchical levels. The packet is processed using the longest prefix match.
Owner:MELLANOX TECHNOLOGIES LTD
Data processing
ActiveUS20080016106A1Minimise tree traversalDigital data processing detailsFile access structuresAnalysis dataTree traversal
Data is stored and data objects are indexed by an index having a tree configuration and the tree is traversed to identify the location of a data object. Data objects are analysed to assess the extent to which a second data object is related to a first data object, and locations of related data objects within the tree are clustered so as to minimise tree traversal when accessing data objects considered to be related.
Owner:DATA EQUATION
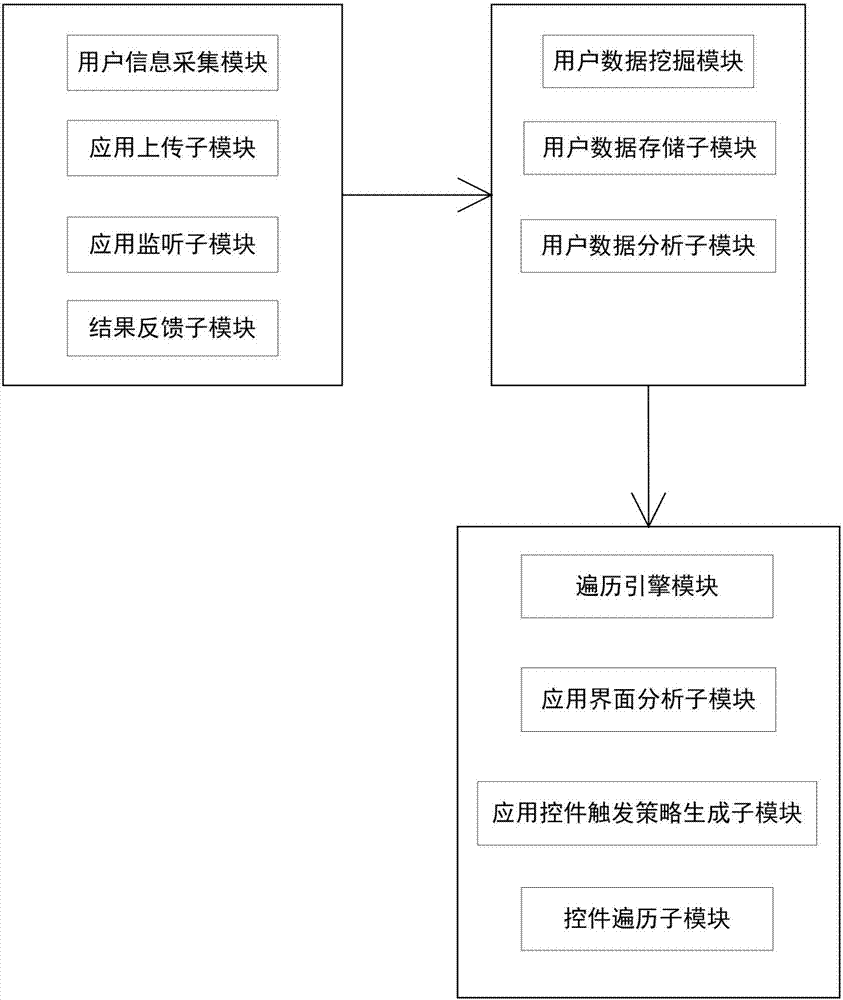
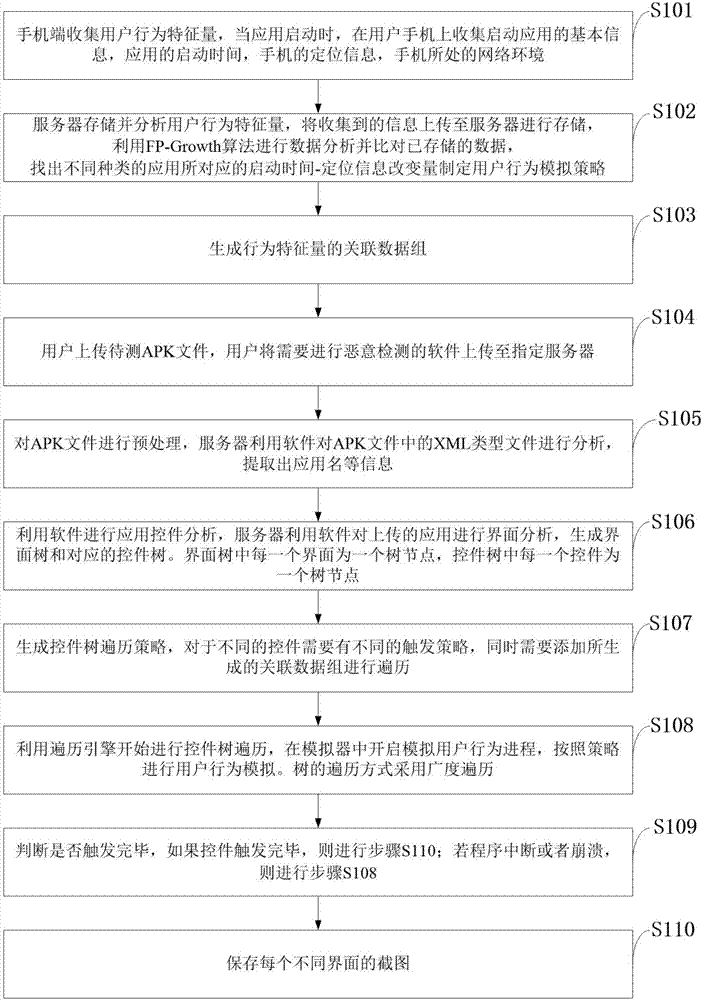
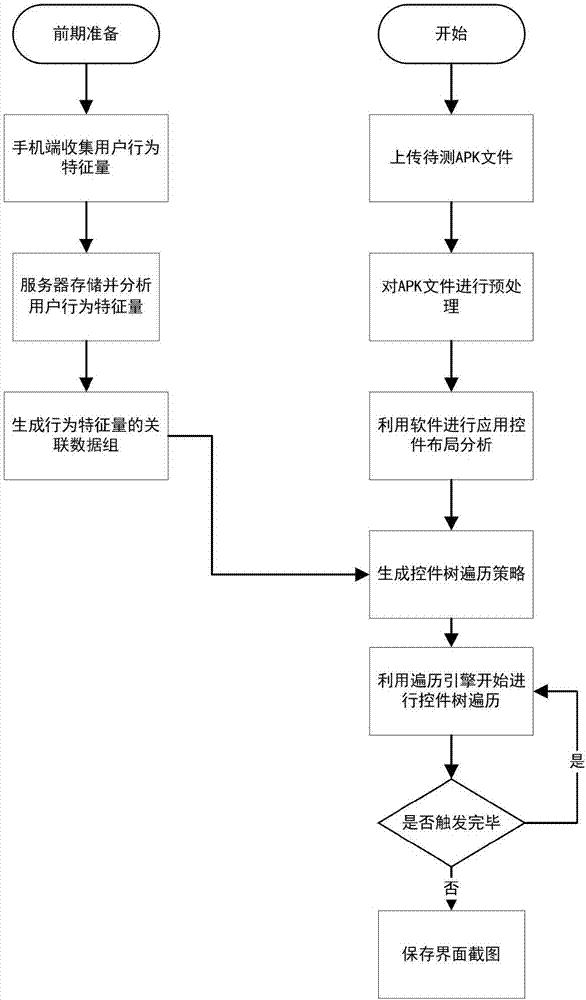
Malicious behavior trigger system and method for android software capable of simulating user behaviors
ActiveCN106874763AImprove experienceTrigger efficiencyPlatform integrity maintainanceData setTree traversal
The invention discloses a malicious behavior trigger system and a malicious behavior trigger method for android software capable of simulating user behaviors. A technology of simulating a real environment change of a mobile phone of a user is added, so that triggering of malicious software behaviors in a dynamic detection technology is more efficient and difficulty is created for malicious software in identification of a simulator environment. The system comprises a user information collection module, a user data mining module and a traversal engine module. The method comprises the specific steps of collecting a user behavior characteristic quantity by a mobile client, storing and analyzing the user behavior characteristic quantity by a server, generating an associated data set of the user behavior characteristic quantity, uploading a to-be-tested APK file by a user, preprocessing the APK file, analyzing an application control by using software, generating a control tree traversal policy, starting control tree traversal by using a traversal engine, judging whether triggering is completed or not, and storing screenshots of different interfaces. The traversal coverage rate is higher, triggering of the malicious behaviors is more comprehensive and the traversal speed is higher.
Owner:XIDIAN UNIV
Method and apparatus for stack management
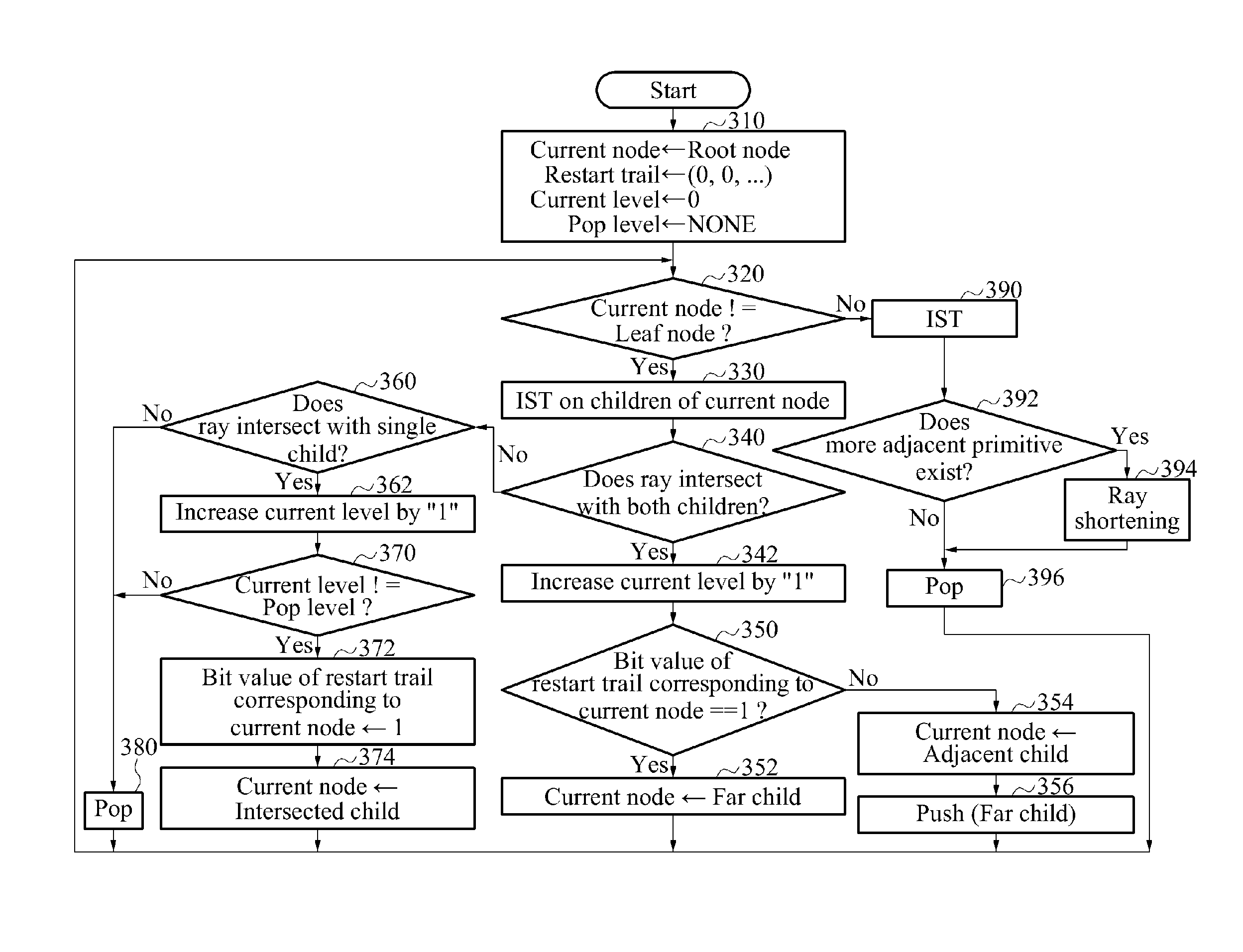
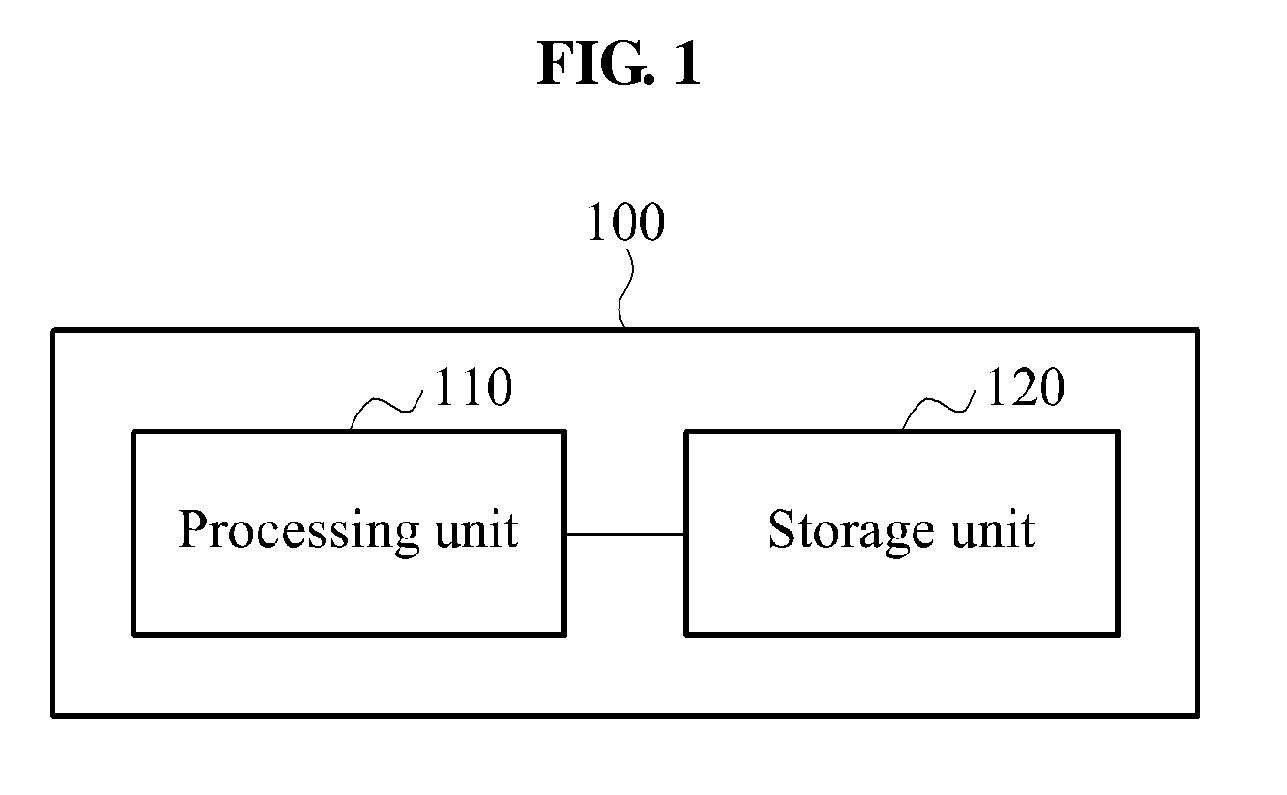
ActiveUS20140244693A1Digital data information retrievalDigital data processing detailsTree traversalProcessing element
A method and apparatus for managing a stack used for a tree traversal (TRV) may include a processing unit that may manage a short stack for a tree TRV, and a storage unit that may store data of the short stack. The processing unit may perform a restart of the tree TRV from an intermediate node of a tree to fill the short stack when the short stack is empty.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Data processing method and apparatus
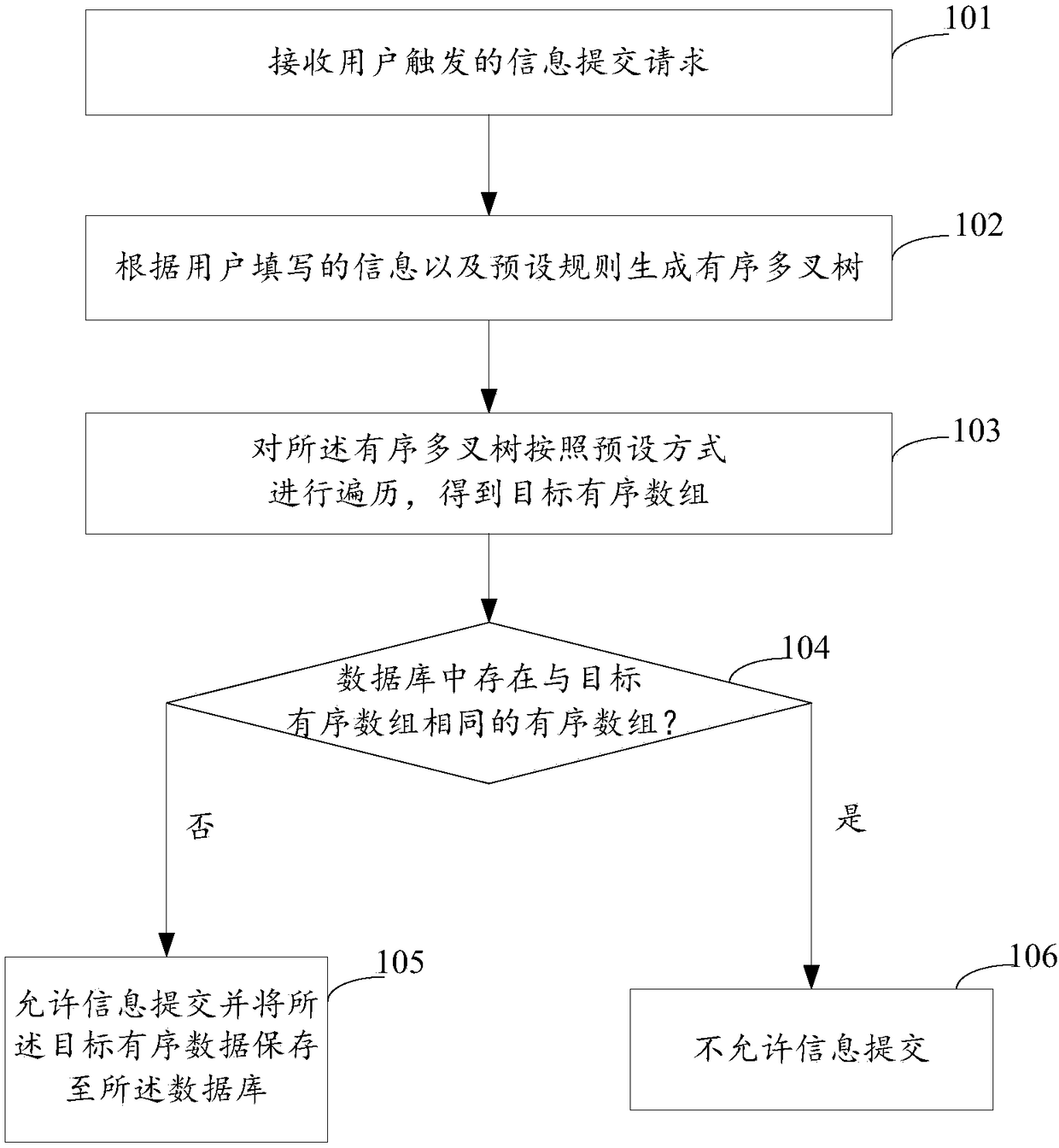
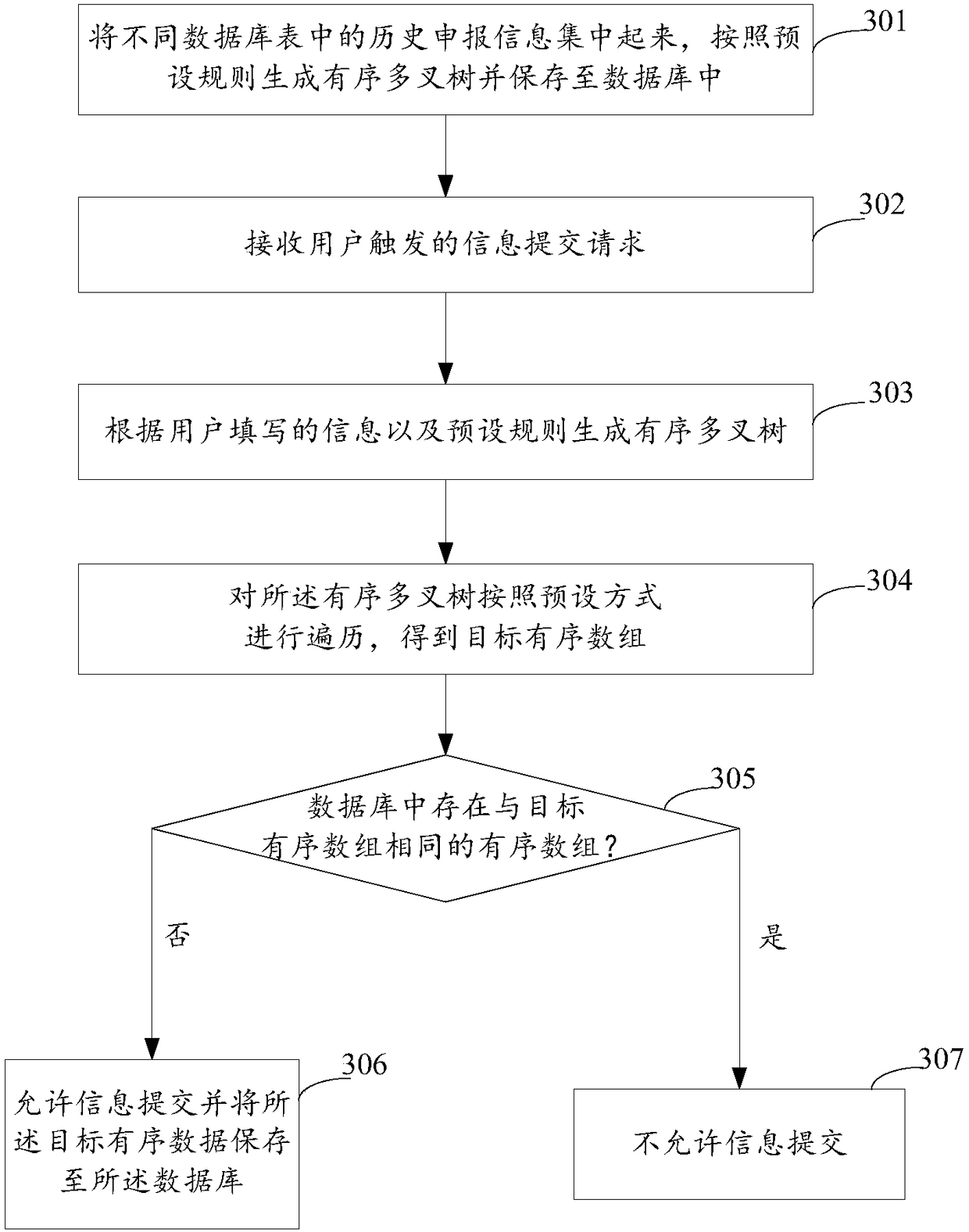
InactiveCN108170772AAvoid Duplicate ReviewsImprove review efficiencySpecial data processing applicationsArray data structureTree traversal
The invention discloses a data processing method and apparatus. The method comprises the steps of firstly receiving an information submitting request triggered by a user; secondly according to information filled by the user and preset rules, generating an ordered multi-way tree, and performing traversal on the ordered multi-way tree in a preset mode to obtain a target ordered array; and thirdly judging whether an ordered array as same as the target ordered array exists in a database or not, and if yes, not allowing information submitting. According to the data processing method and apparatus,multiple pieces of scattered information filled by the user in a declaration system can be concentrated to generate the ordered multi-way tree to be stored; the ordered array is obtained through traversal of the ordered multi-way tree; whether currently submitted data has repetition and redundancy with previous data or not is judged through comparison between the current ordered array and the previously stored ordered array during submitting; and submitting is not allowed when the currently submitted data has repetition and redundancy with the previous data, so that repeated audit of same declaration materials is avoided and the audit efficiency is improved on the whole.
Owner:TAIKANG LIFE INSURANCE CO LTD
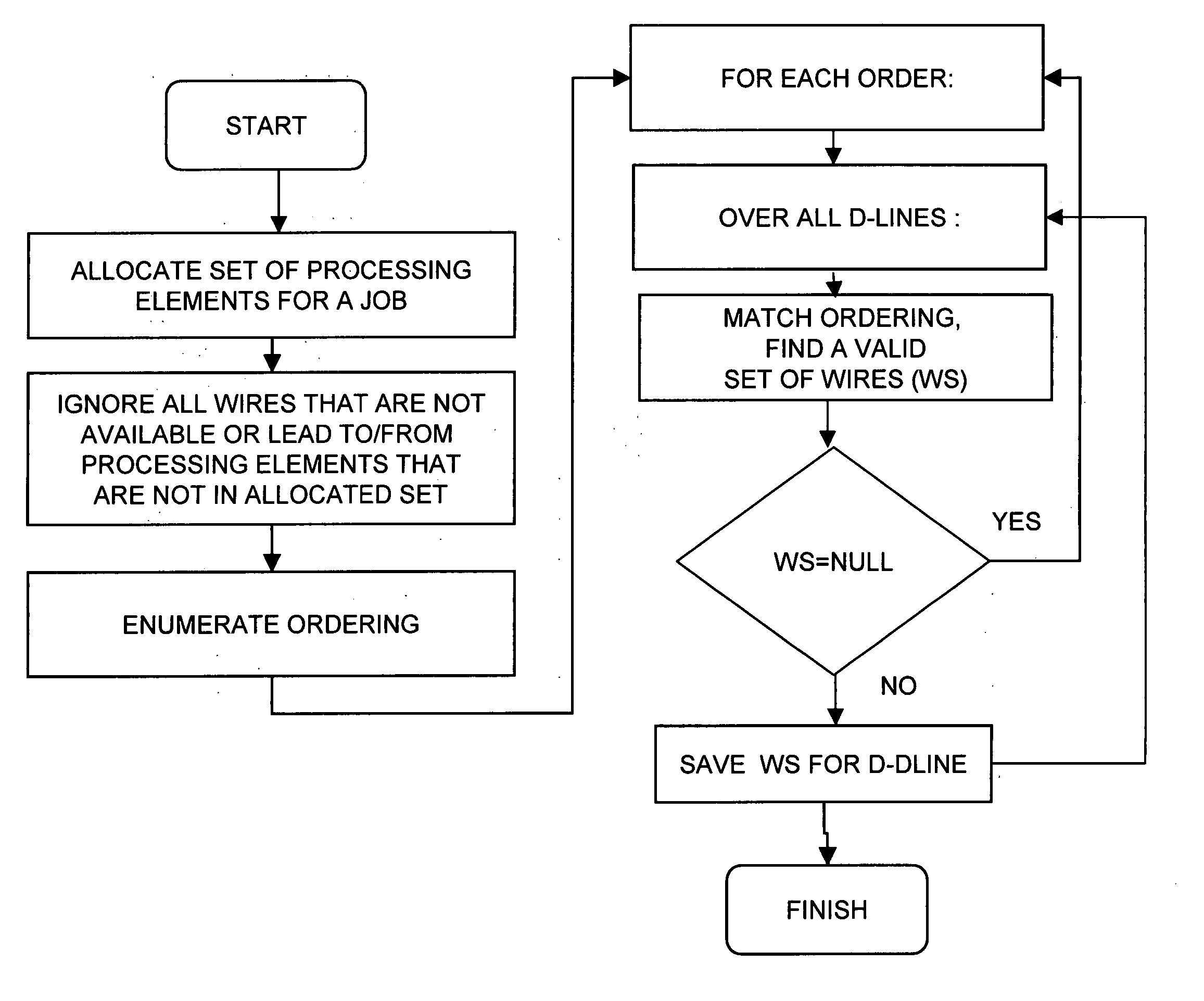
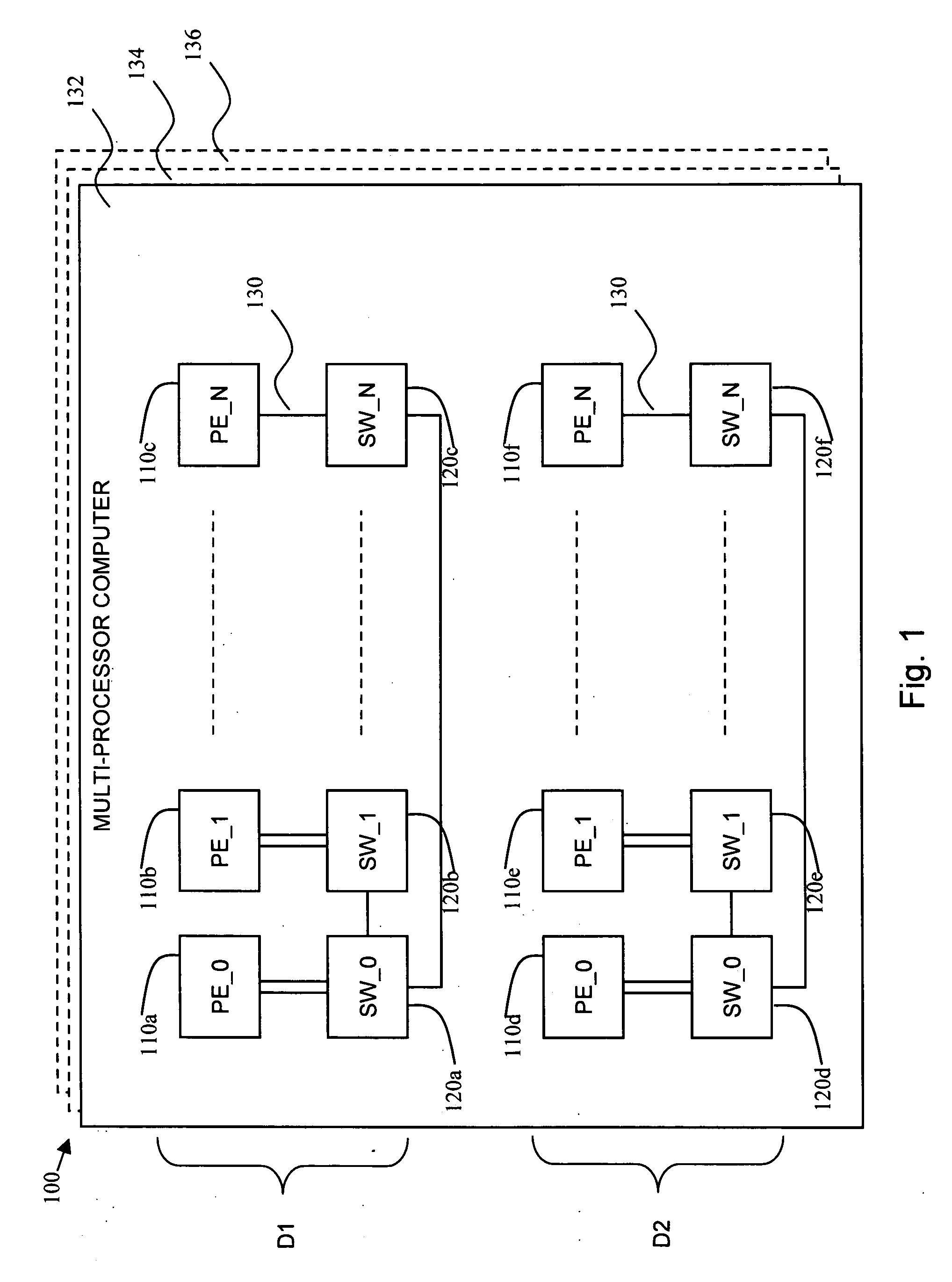
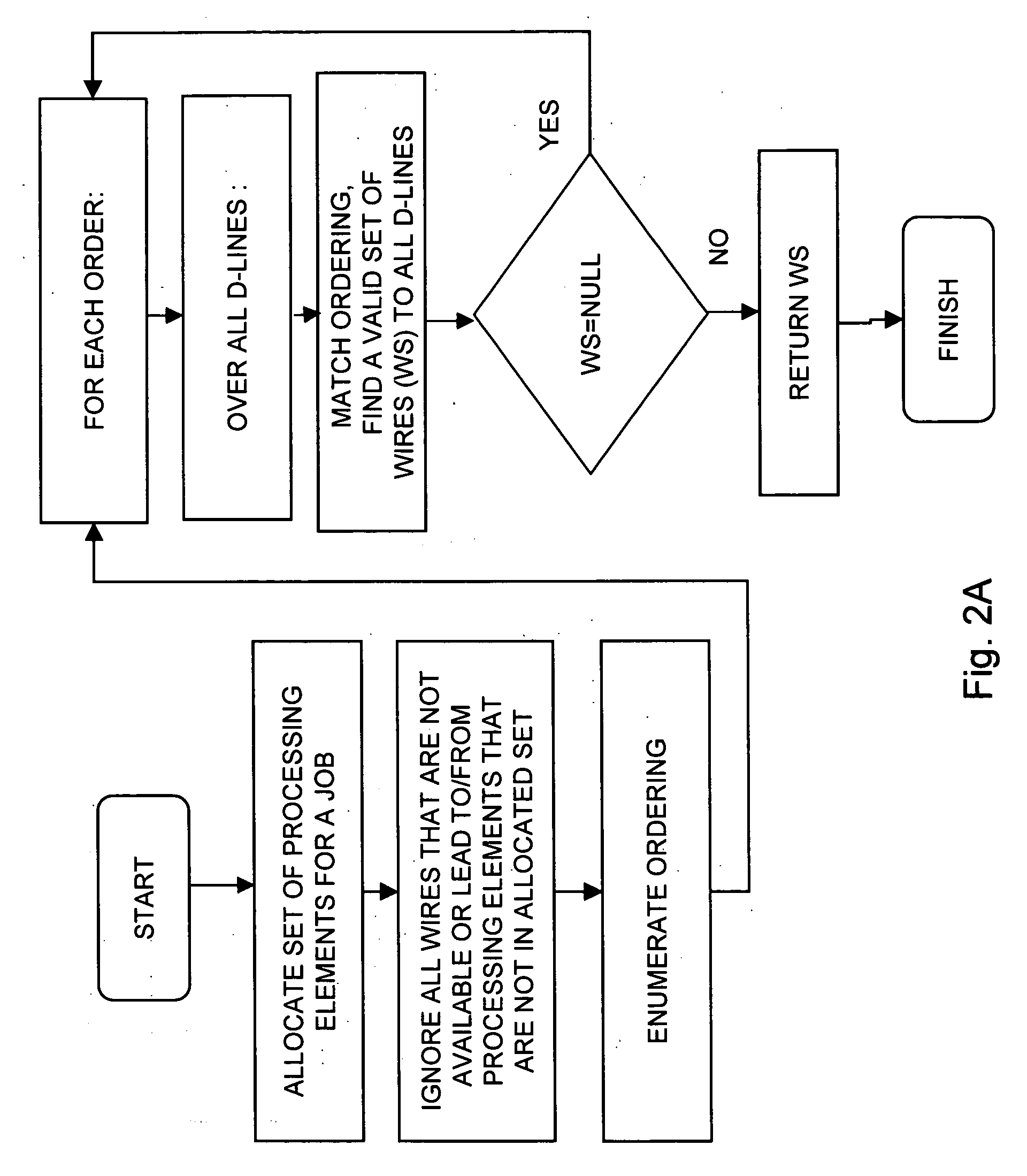
Method for wiring allocation and switch configuration in a multiprocessor environment
InactiveUS20060095711A1General purpose stored program computerProgram controlMulti processorTree traversal
A method for wiring allocation and switch configuration in a multiprocessor computer, the method including employing depth-first tree traversal to determine a plurality of paths among a plurality of processing elements allocated to a job along a plurality of switches and wires in a plurality of D-lines, and selecting one of the paths in accordance with at least one selection criterion.
Owner:IBM CORP
Method for efficiently querying and identifying multiple items on a communication channel
InactiveUS20050007240A1Eliminate needSolve the slow scanning speedElectric signal transmission systemsDigital data processing detailsTree traversalRadio frequency
Systems and methods for efficiently querying and identifying multiple items on a communication channel are disclosed. The inventions preferably uses radio frequency identification with interrogation devices and systems that identify radio frequency identification transponders. A depth-first tree traversal protocol algorithm, including commands and symbols, is used to more efficiently interrogate a plurality of transponders in a short amount of time.
Owner:E TAG SYST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com