Patents
Literature
249 results about "Link protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
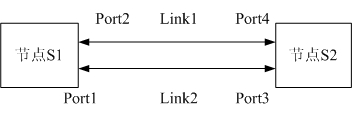
Link protection is designed to safeguard networks from failure. Failures in high-speed networks have always been a concern of utmost importance. A single fiber cut can lead to heavy losses of traffic and protection-switching techniques have been used as the key source to ensure survivability in such networks. Survivability can be addressed in many layers in a network and protection can be performed at the physical layer (SONET/SDH, Optical Transport Network), Layer 2 (Ethernet, MPLS) and Layer 3 (IP).
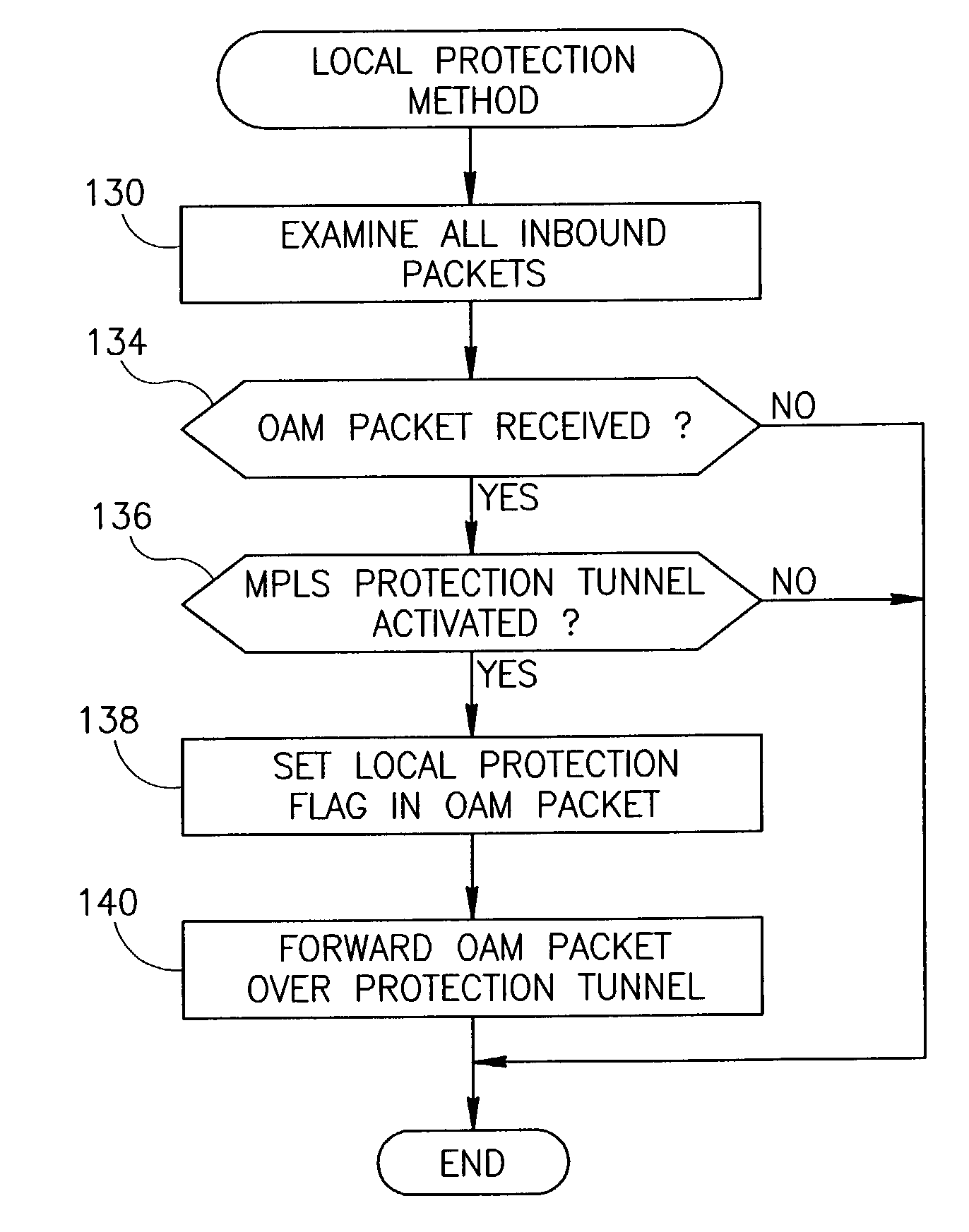
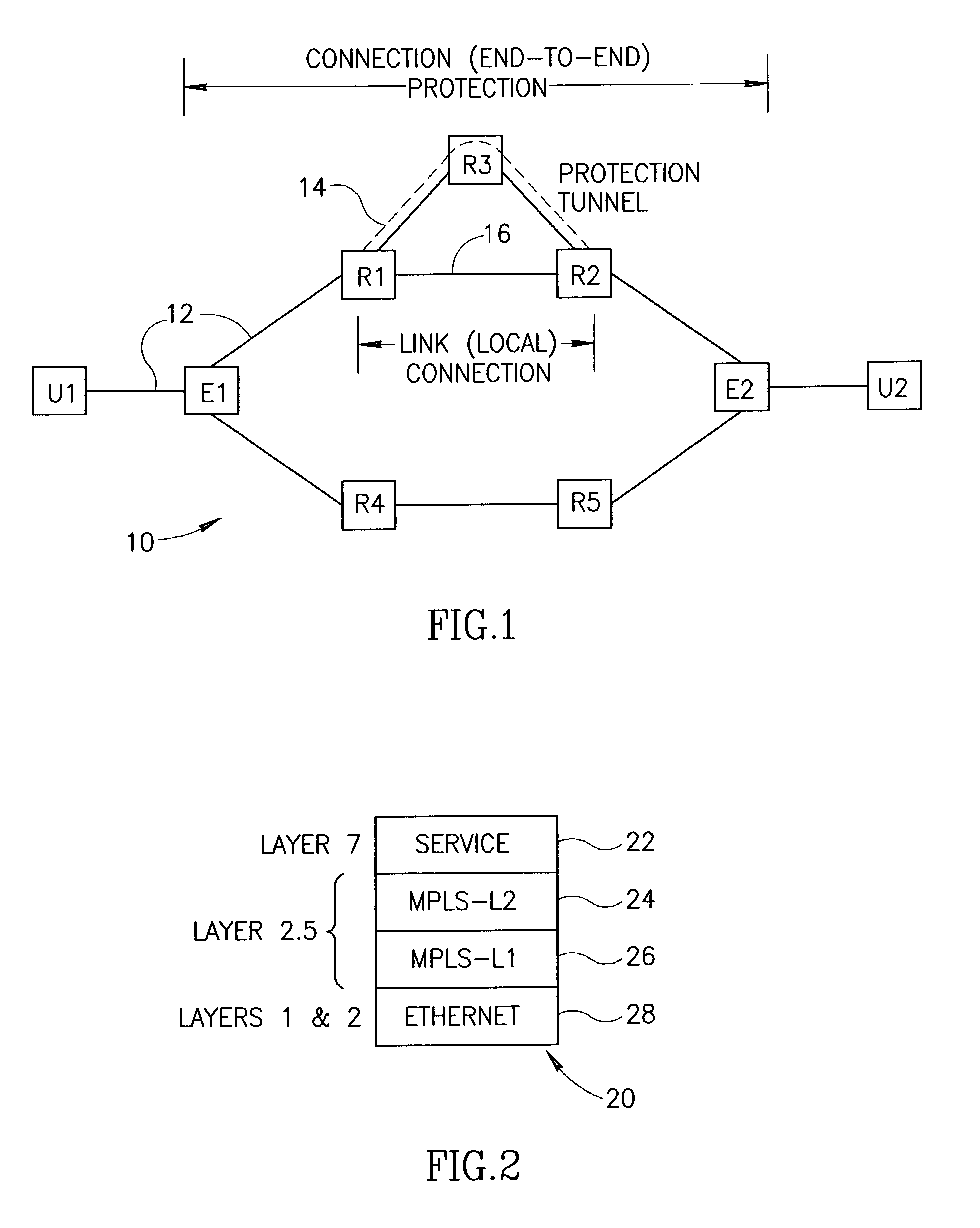
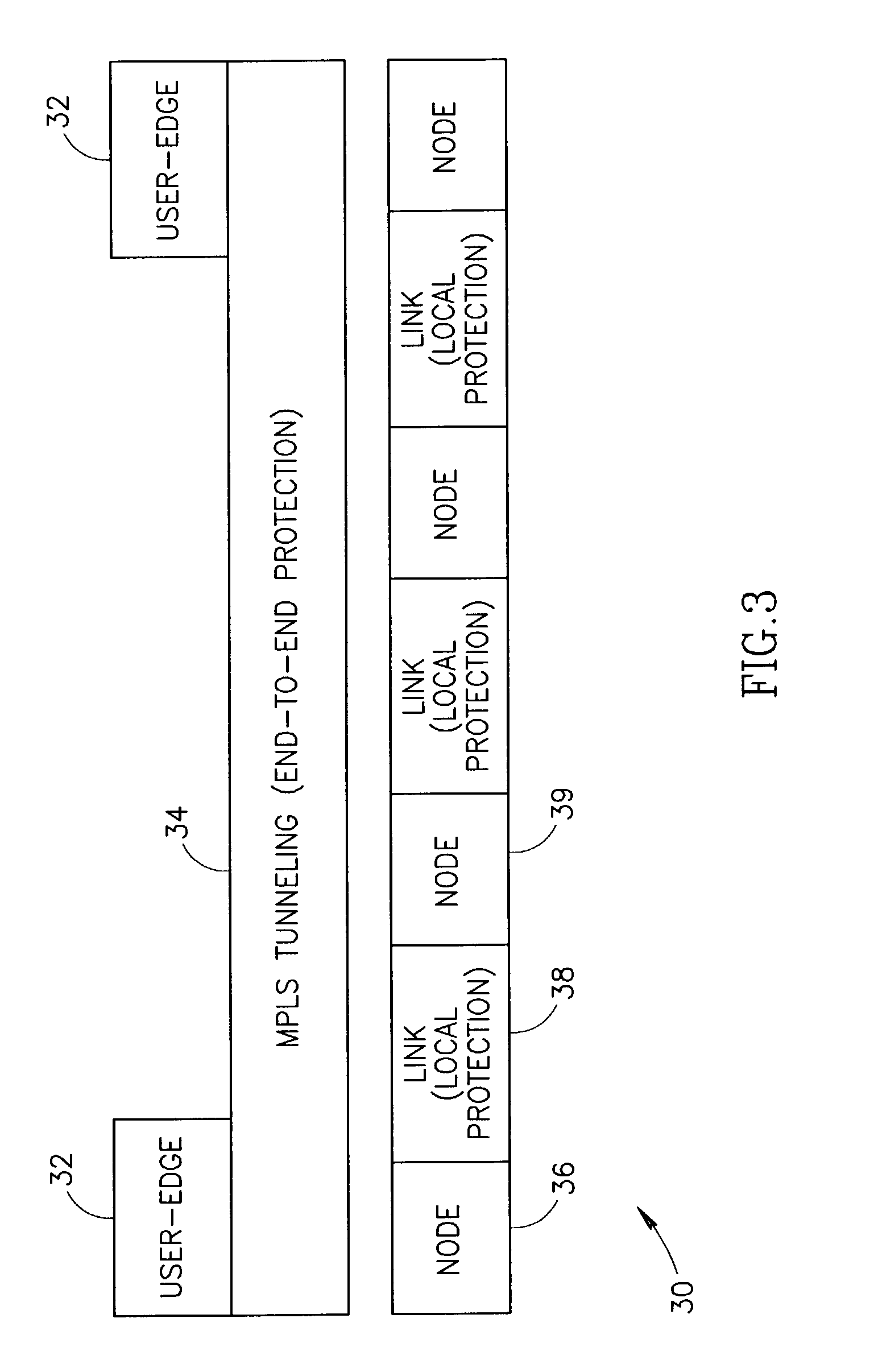
End-to-end notification of local protection using OAM protocol
ActiveUS7197008B1Lower performance requirementsMinimum interruptionError preventionTransmission systemsTraffic capacityCommitted information rate
An end-to-end monitoring mechanism whereby edge nodes are notified that a particular path flows through a local protection tunnel along the way. The notification mechanism utilizes OAM packets which include a link protection indication that are transmitted on the Ethernet service layer. The link protection indication may be represented by one or more flags to indicate that local protection is in place along the path. The mechanism enables fast local protection to be used with slower end-to-end protection by informing the latter when local protection is activated. In an implementation in which local-protection does not preserve the CIR of the protected traffic, the invention provides minimal interruption of Committed Information Rate (CIR) connections by minimizing the time traffic is diverted through local protection tunnels. Notification of the edge node that local protection is in use occurs very quickly, thus allowing the edge node to rapidly switch to a backup path.
Owner:RPX CORP +1
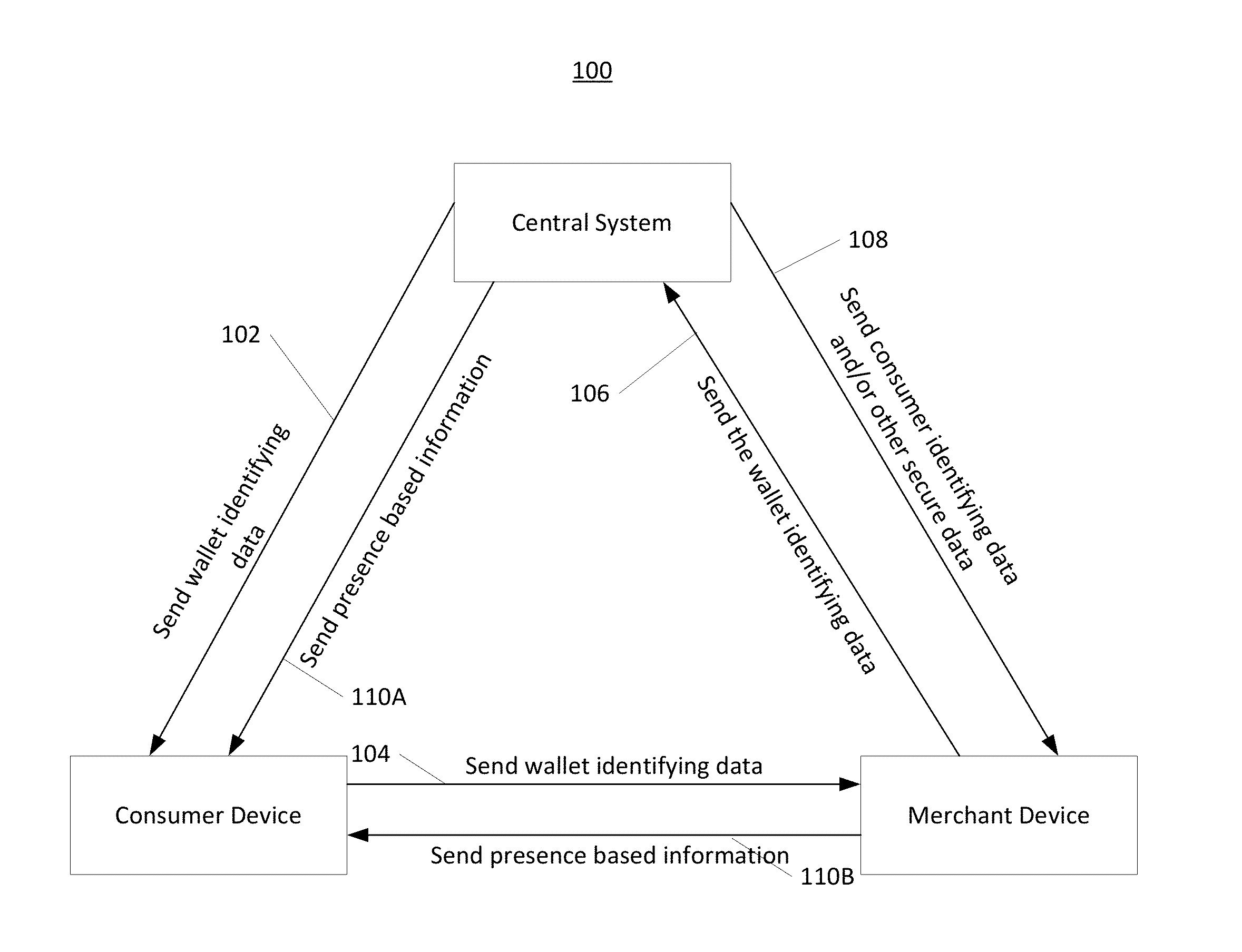
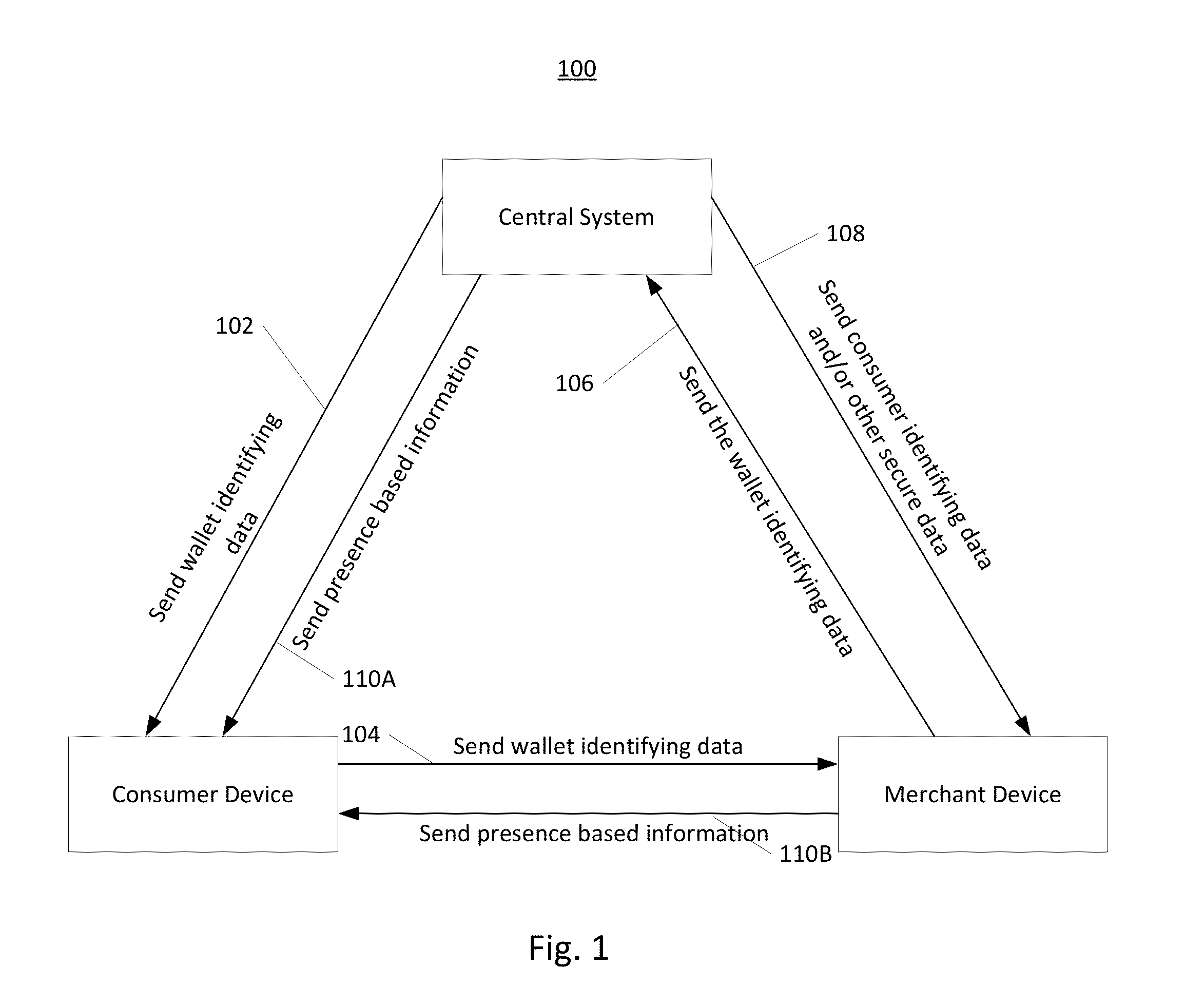
Consumer presence based deal offers
ActiveUS20140108108A1Easy to judgeFinanceProtocols using social networksVoucherFinancial transaction
Systems and related methods facilitating payments with a mobile device are discussed herein. Circuitry in a networked-based central system, which may be a promotional system or payment system, may be configured to receive payment information from a consumer device. The consumer device may include circuitry configured to receive wallet identifying data from the central system. The wallet identification data may be used to secure messages between the consumer device and another device, such as a merchant device, over a wireless link. In some embodiments, the consumer device may receive promotional offers, such as deal vouchers or rewards, and make payments to the other device via the wireless link.
Owner:GROUPON INC
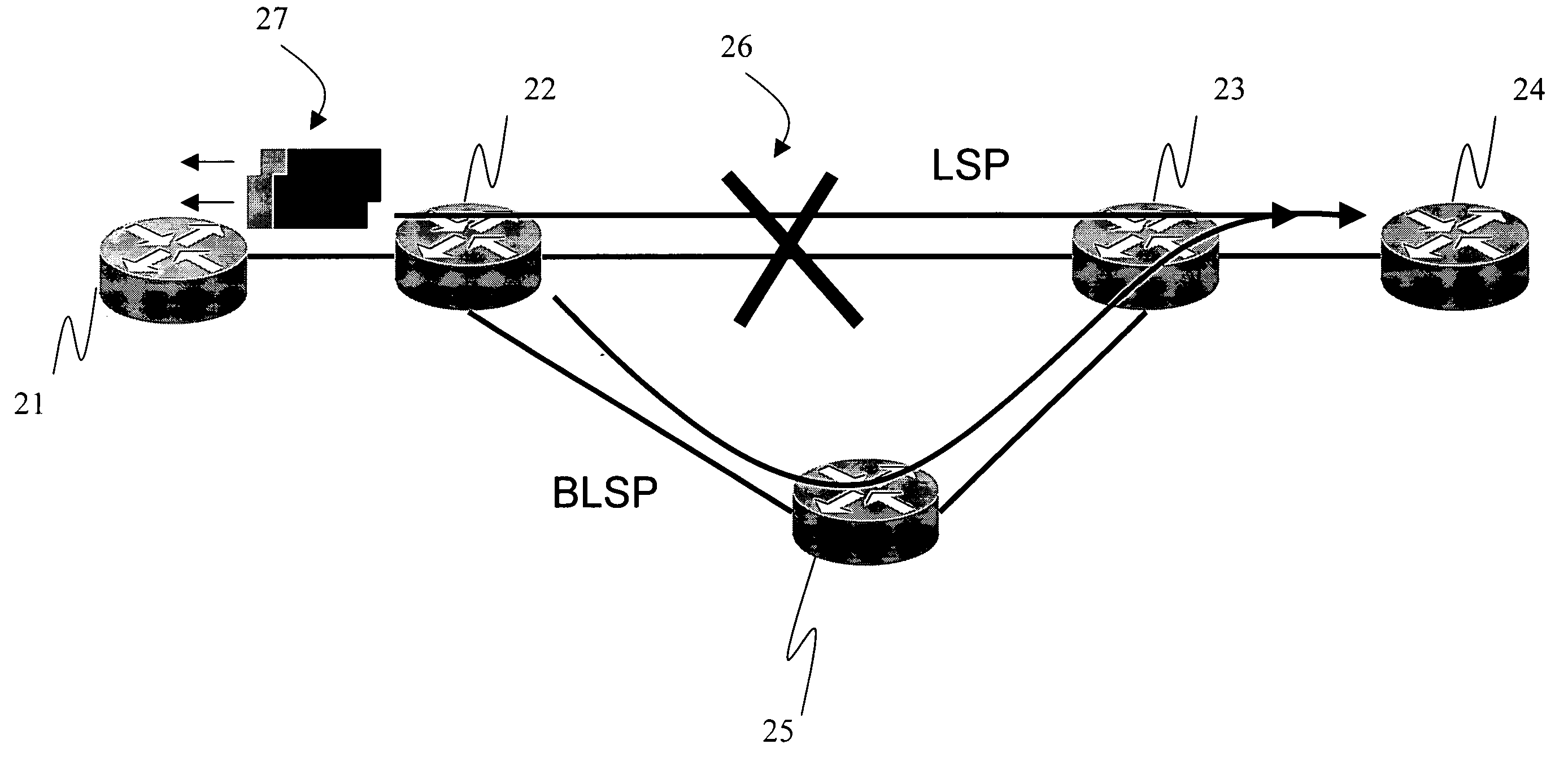
Method for MPLS link protection
InactiveUS20050152269A1Improve bandwidth utilizationShort service interrupted timeLaser detailsError preventionReal-time computingBackup
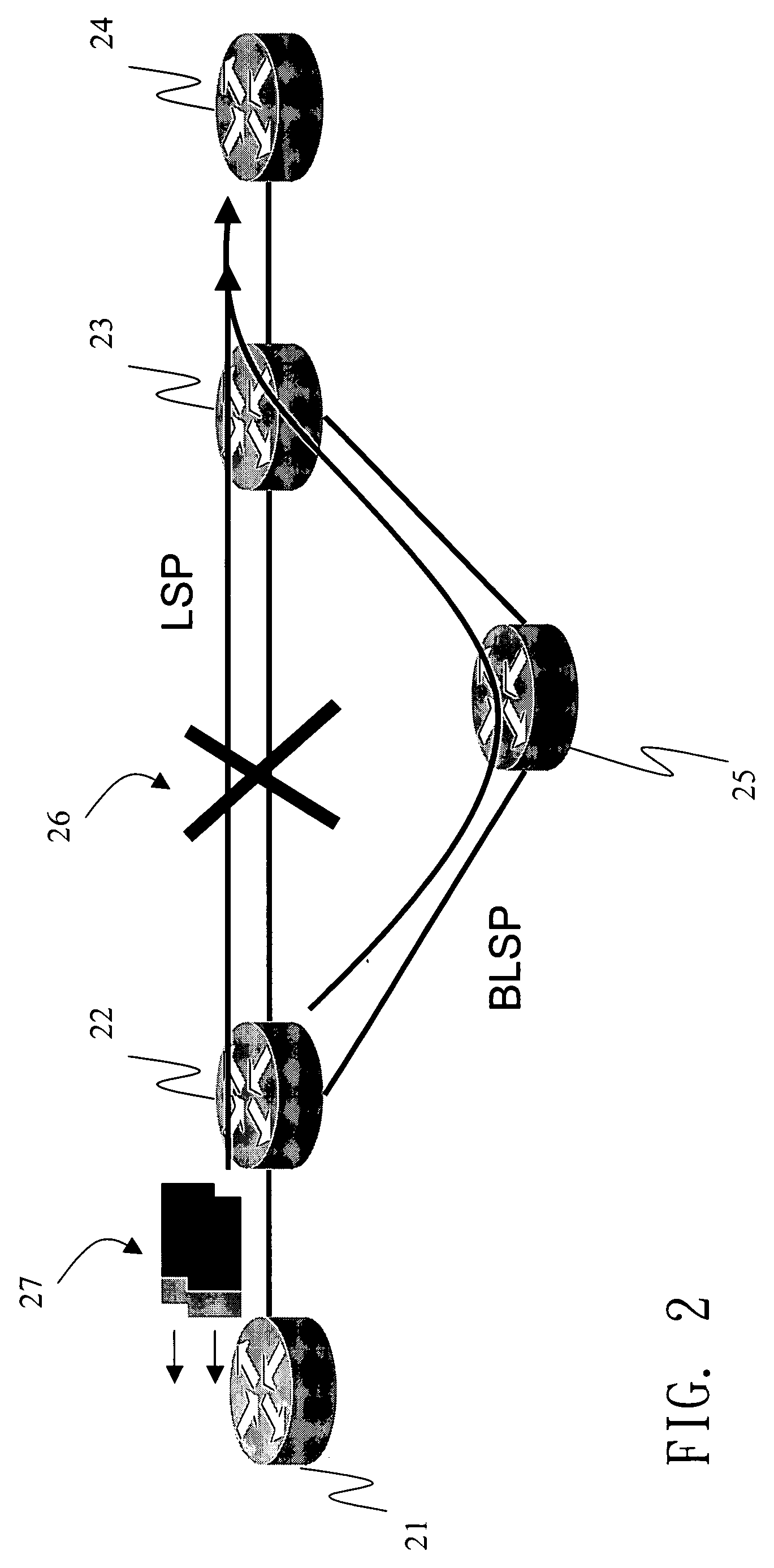
A method for MPLS link protection pre-builds backup LSP. When the LSP breaks down, it can redirect the LSP to the backup LSP within the minimal time and rearrange an auxiliary LSP after breaking down for a default time. By the guiding and the rearrangement, the method prevents the service of the MPLS from being unavailable when the MPLS breaks down and optimizes the utilization of the MPLS resources.
Owner:IND TECH RES INST
Apparatus and method for preventing one way connectivity loops in a computer network
InactiveUS7076594B2Eliminates formation of loopError preventionTransmission systemsNetwork managementSoftware
Ports of a switch are assigned by a person, for example a network manager, to be for communication up the spanning tree toward the root switch (“up ports”), or down the spanning tree away from the root switch (“down ports”). This assignment is made by enabling “Uplinkguard” status for a desired up port, and by connecting the desired port to a switch which it is desired to place in the higher layer of the spanning tree. A port having Uplinkguard enabled is prevented, for example by software or firmware in its switch, from transitioning to a designated role. Uplinkguard-enabling a port, by preventing the port from transitioning to the designated role, has at least two consequences: preventing the port from being selected by the STP to transmit to lower switches in the spanning tree; and, preventing the port from transmitting when a one way connectivity fault develops on that port. A port with Uplinkguard enabled may transition to root port role. In the event that there is one way connectivity from a port, that port will not receive BPDU messages, and if the port is in blocked state, it will believe that it should take over and become the designated port for the external link to which it is connected. Uplinkguard prevents the port from transitioning to designated role. When the port attempts to transition into designated role, Uplinkguard forces the port to transition into blocked role, thereby eliminating formation of loops caused by one way connectivity faults.
Owner:CISCO TECH INC
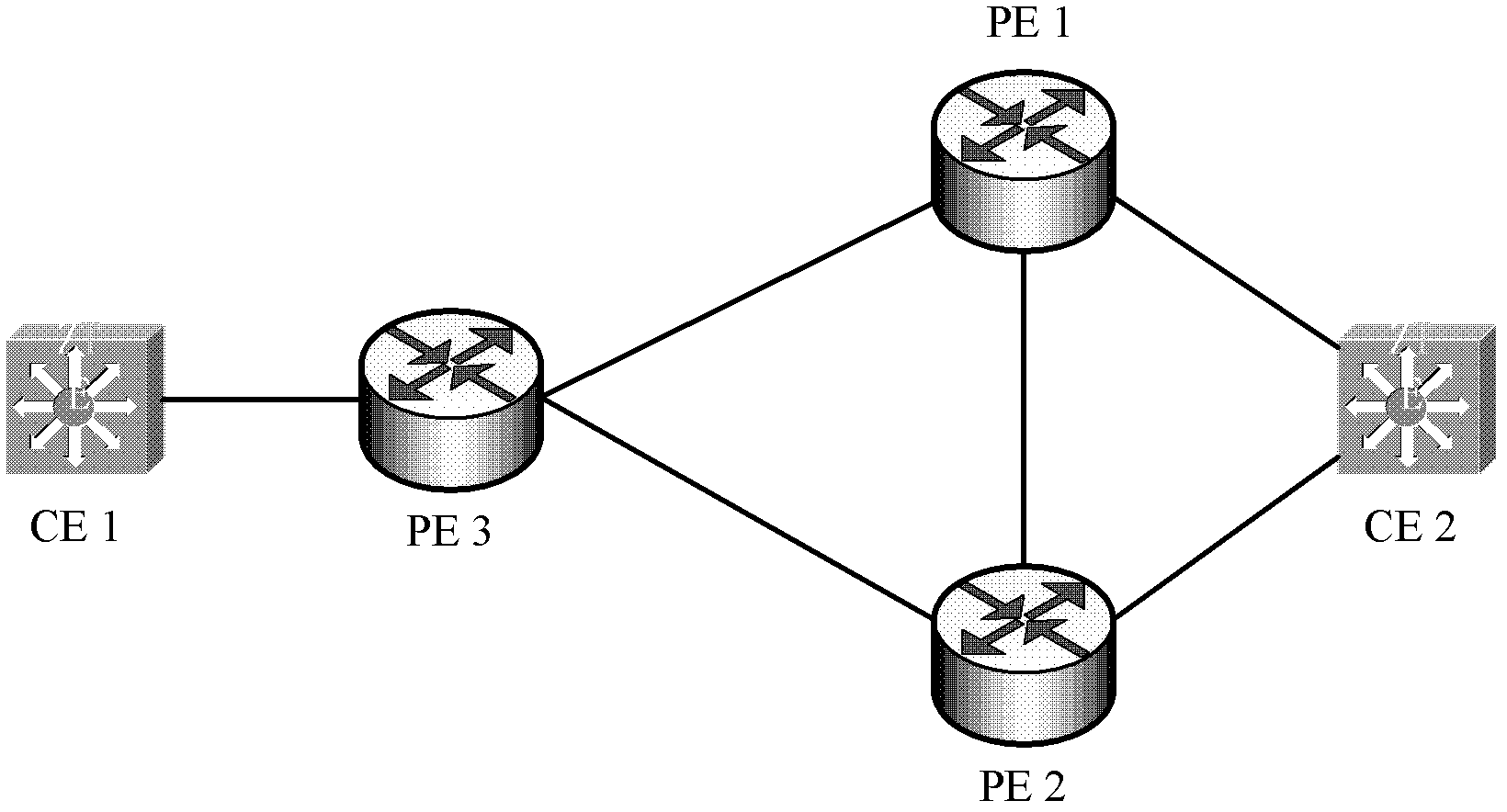
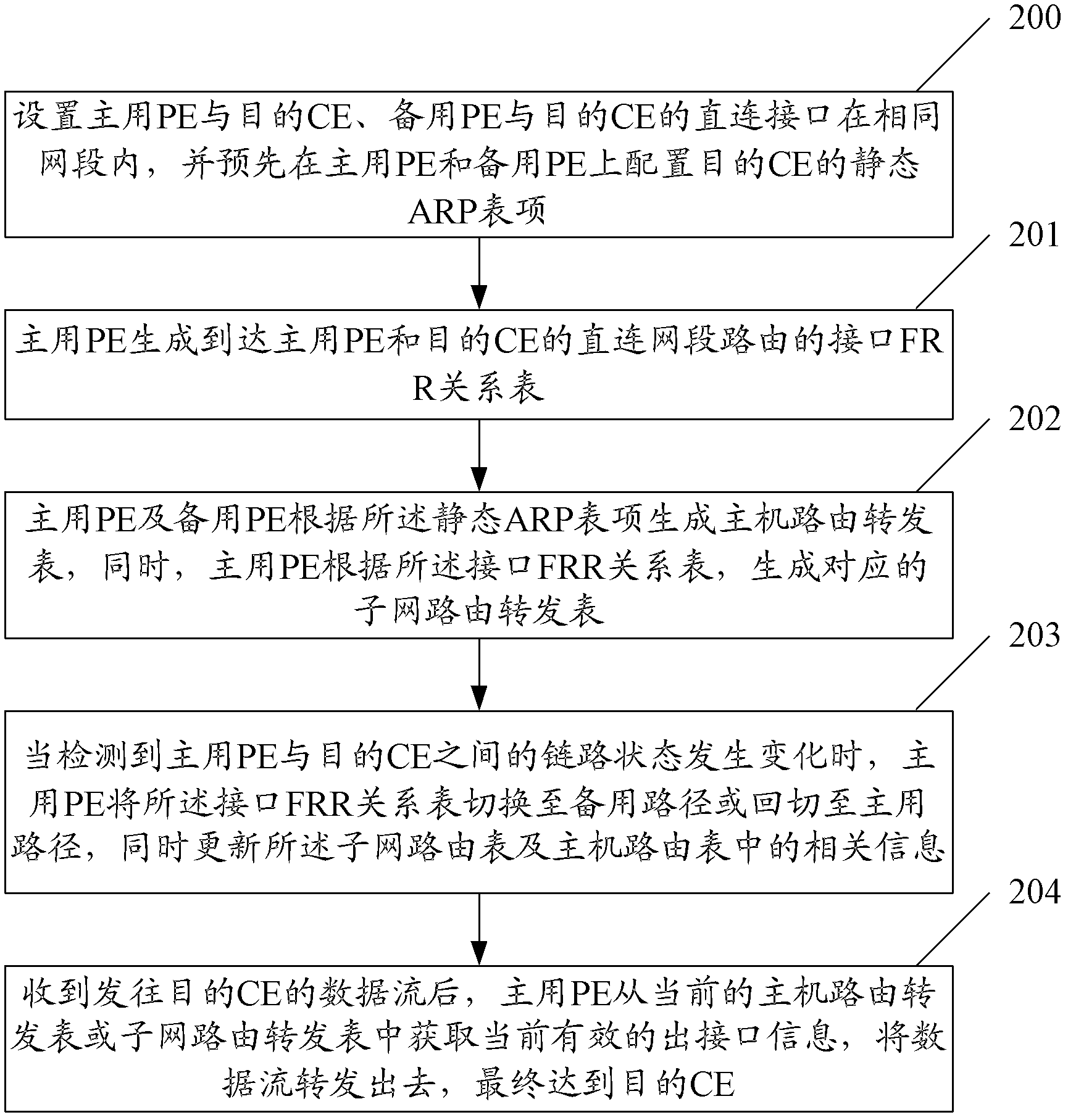
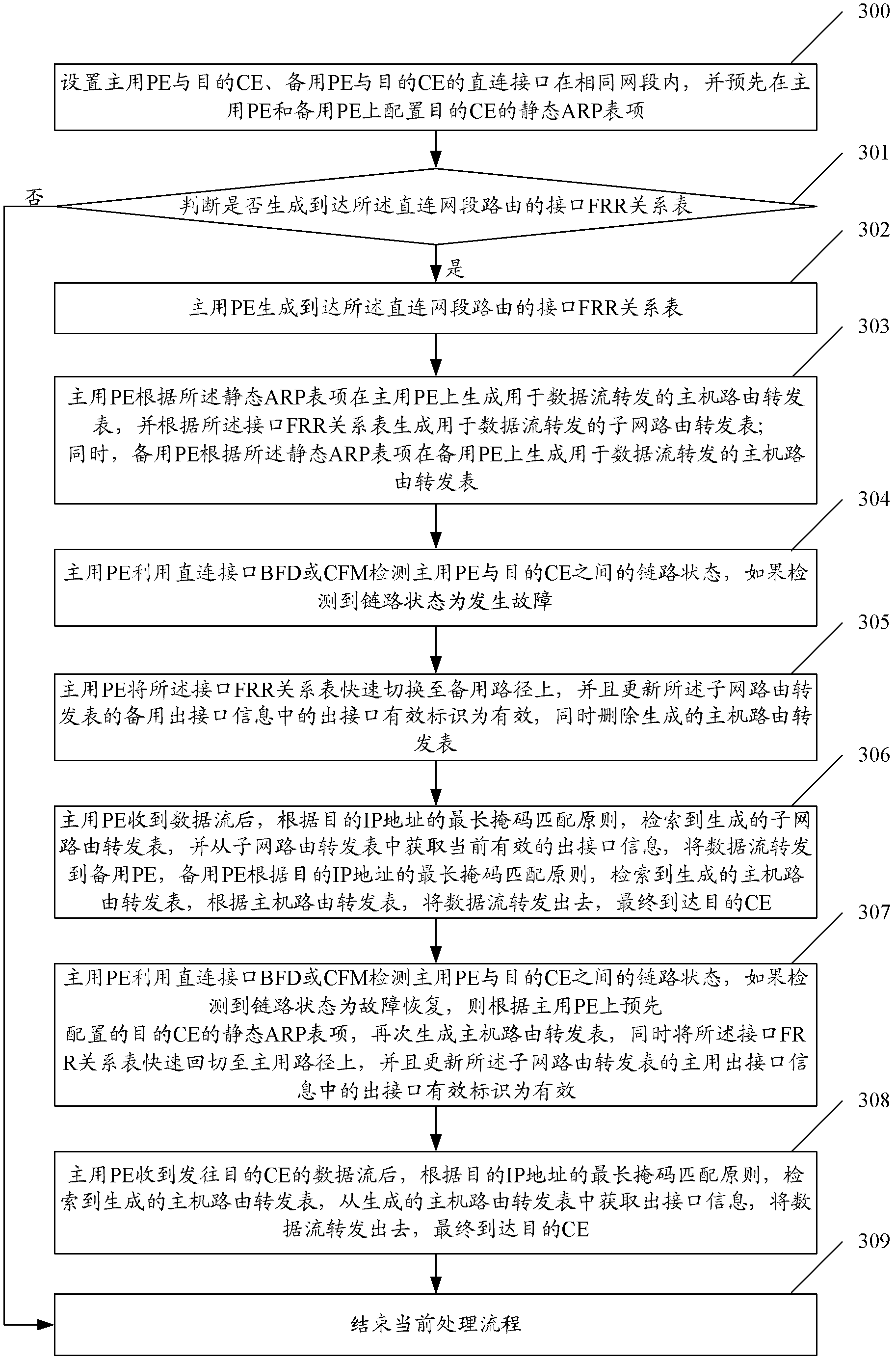
CE dual-homed link protection method in MPLS L3VPN and system thereof
The invention discloses a CE dual-homed link protection method in MPLS L3VPN and a system thereof. The method comprises the following steps: ARP items of a target CE are configured on a main PE and a standby PE; the main PE generates an interface FRR relation table of a direct connecting network segment route which reaches the main PE and the target CE; simultaneously, the main PE and the standby PE generate a host route forwarding table according to static ARP items, and the main PE generates a corresponding subnet route forwarding table according to the interface FRR relation table; after detecting that a link state between the main PE and the target CE changes, the main PE switches the interface FRR relation table into a standby path or switches the interface FRR relation table back into a main path, and updates related information in a subnet routing table and a host routing table; after receiving a data flow, the main PE obtains present effective out interface information from the present host route forwarding table or subnet route forwarding table, and forwards the data flow to reach the target CE. By employing the method and the system of the invention, the rapid switching of the data flow can be effectively realized.
Owner:ZTE CORP
Method, equipment and system for forwarding message as well as equipment for receiving message
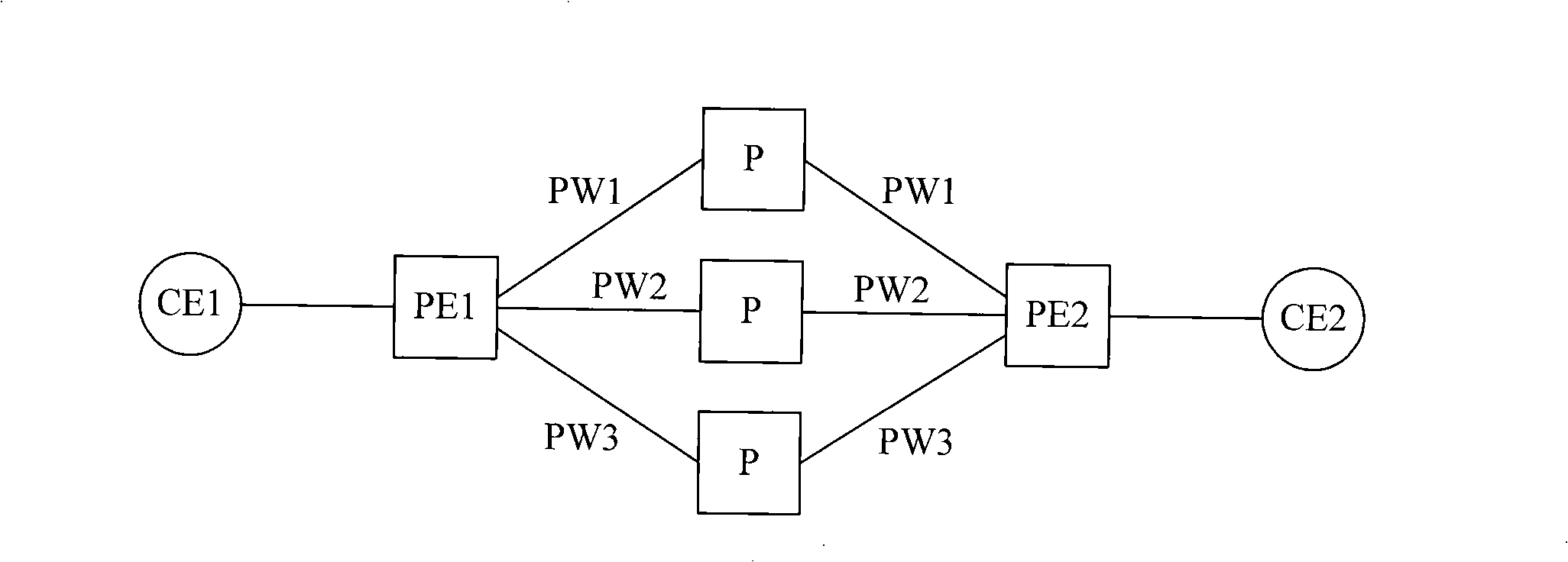
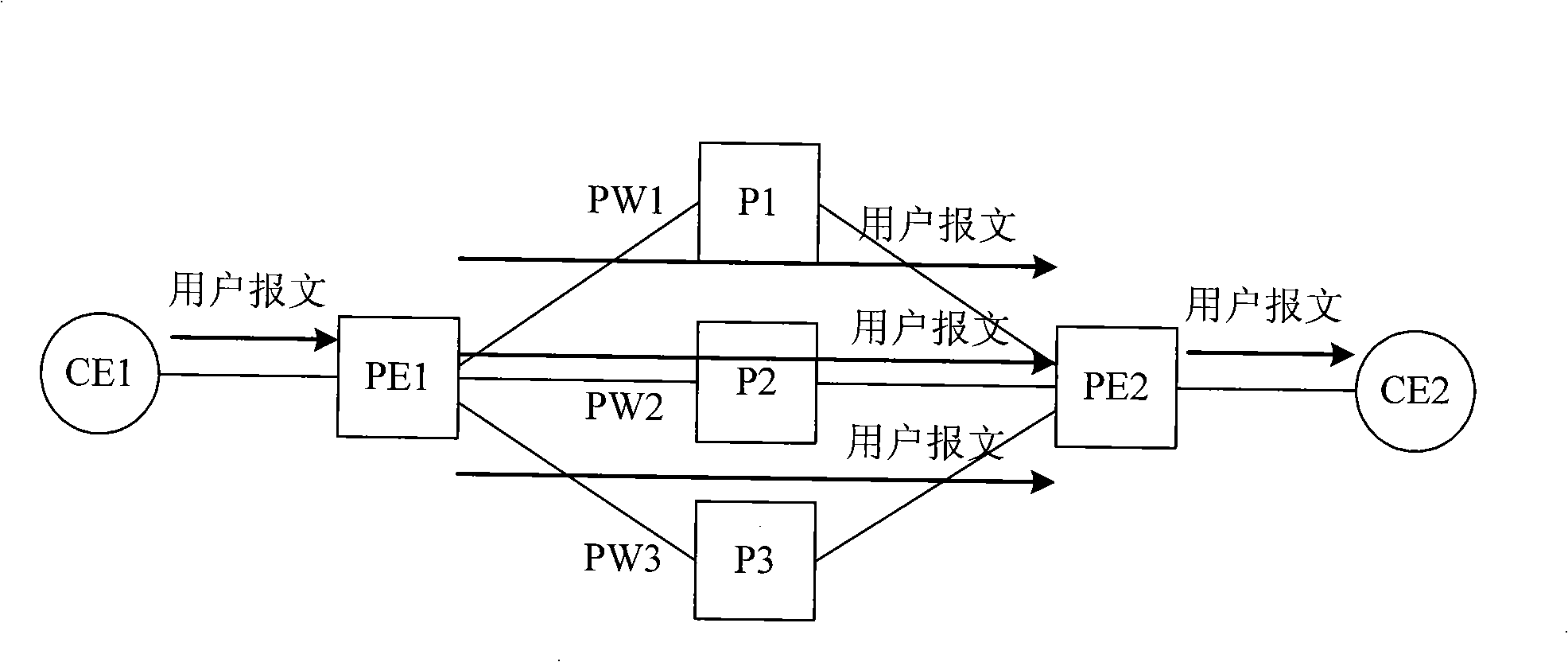
InactiveCN101257441AAchieve protectionReduce consumptionNetworks interconnectionTraffic capacityPseudo-wire
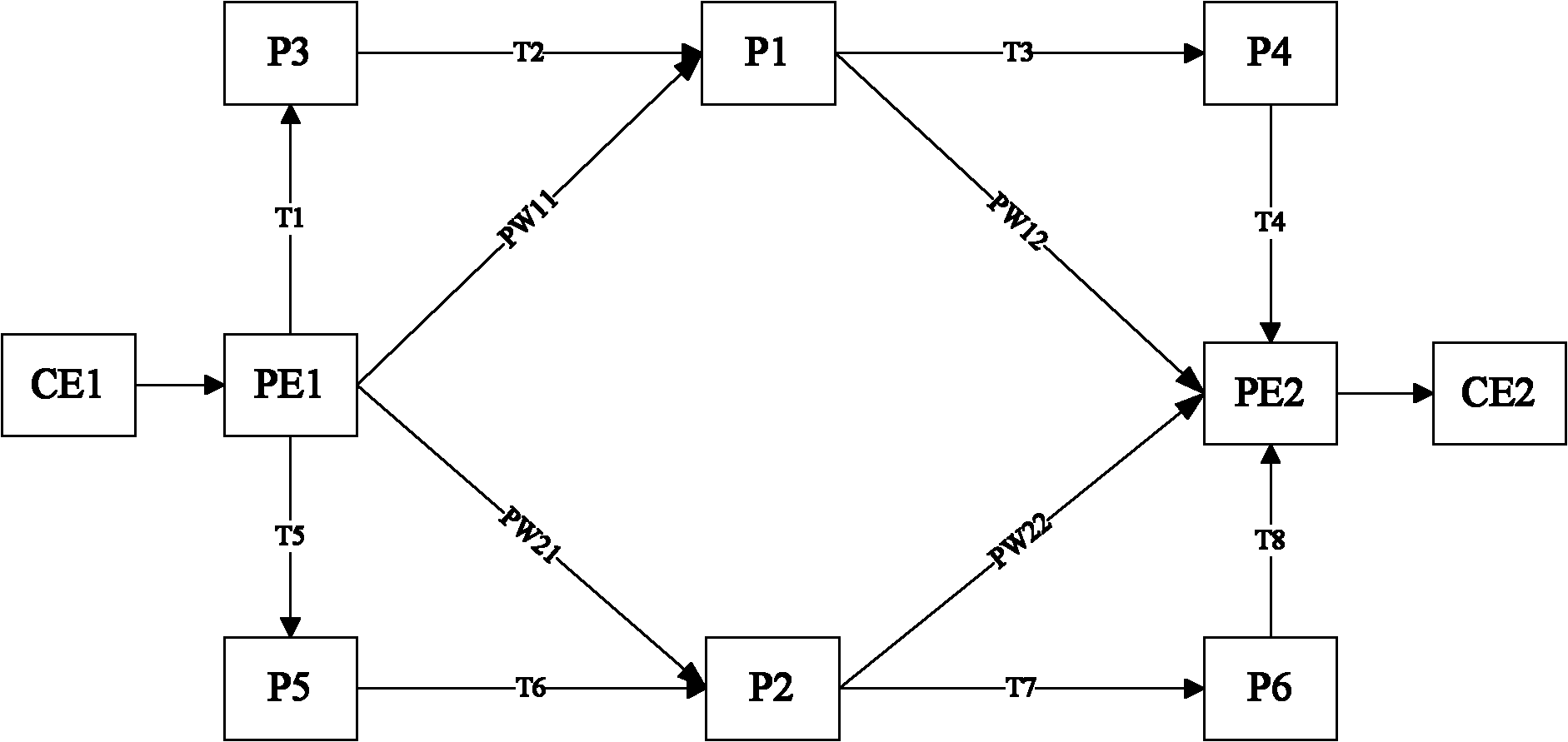
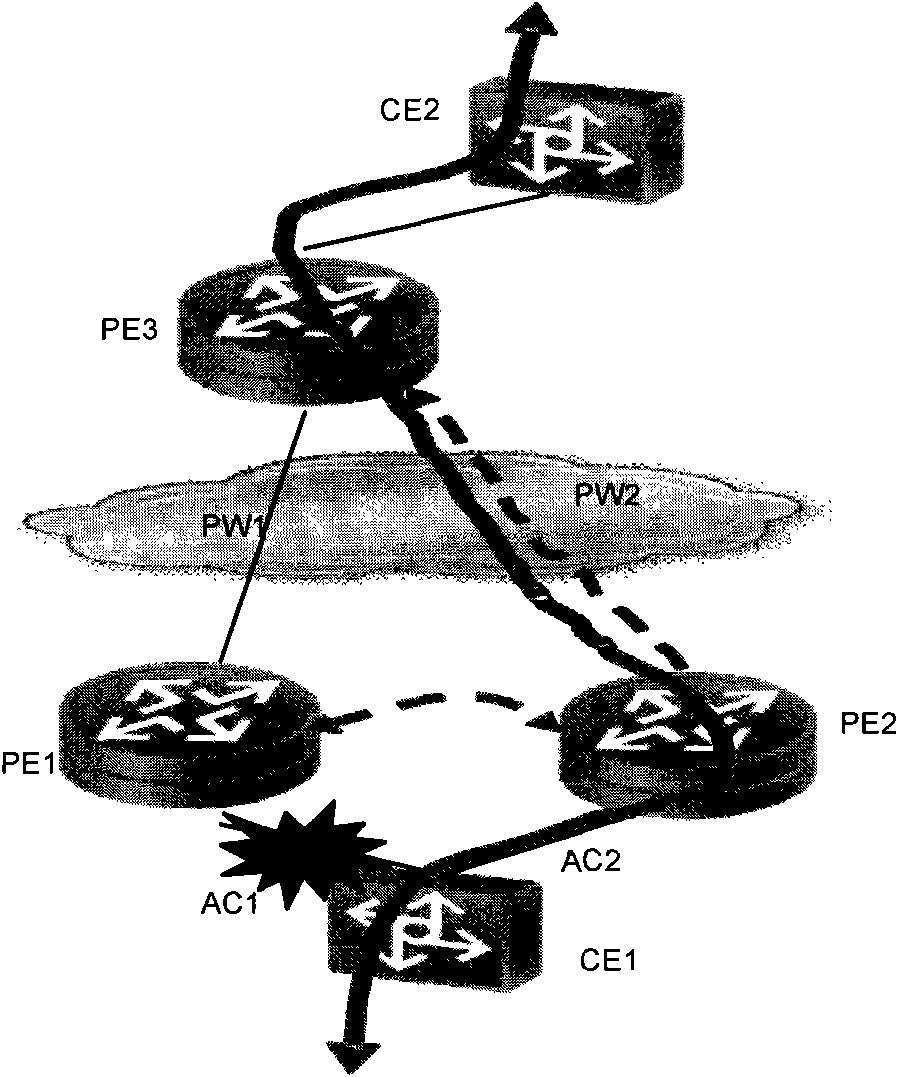
The invention discloses method, device, system for transferring message and a device for receiving message, belonging to the communication technology art. The method comprises: receiving message; obtaining at least one message by copying the message; and transferring the received message and the copied message to a receiving end PE by presetting at least two pseudowires from a plurality of pseudowires, according to the principle that each pseudowire only transfers one message. The transferring device includes: a receiving module and a transferring module. The receiving device comprises: a receiving module and a processing module; or receiving module, a recombining module and a processing module. The system contains a sending end equipment and a receiving end equipment. Due to the plurality of pseudowires simultaneously bears the user traffic, when any link goes wrong, the other links can continuously transfer the traffic to protect the links and avoid the situation of user traffic lost in the transferring and failback process caused by protecting the links using a backup link, thereby, the invention can provide higher level reliability assurance.
Owner:JIANGSU HENGBO PNEUMATIC CONVEYING EQUIP MFG CO LTD
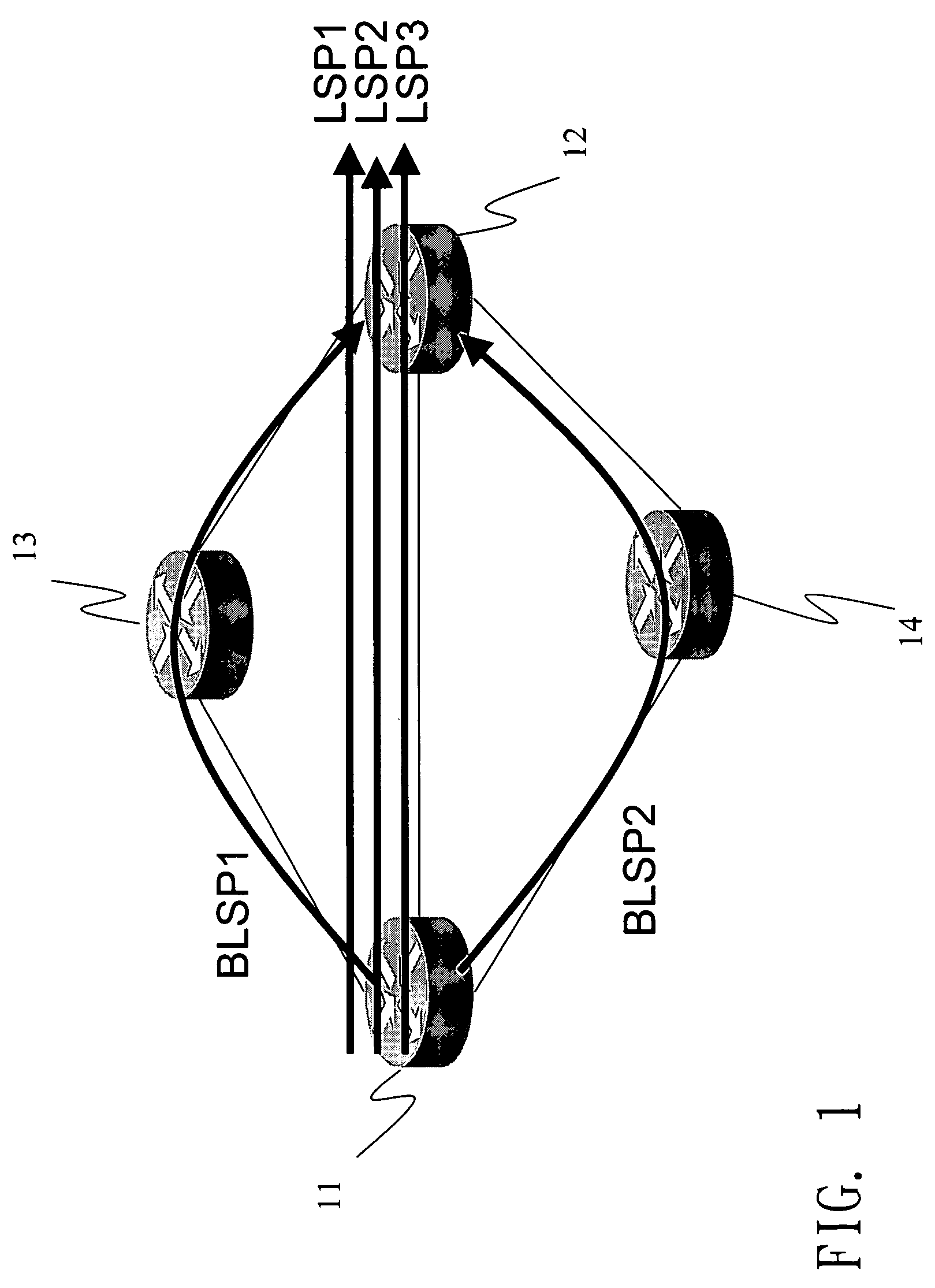
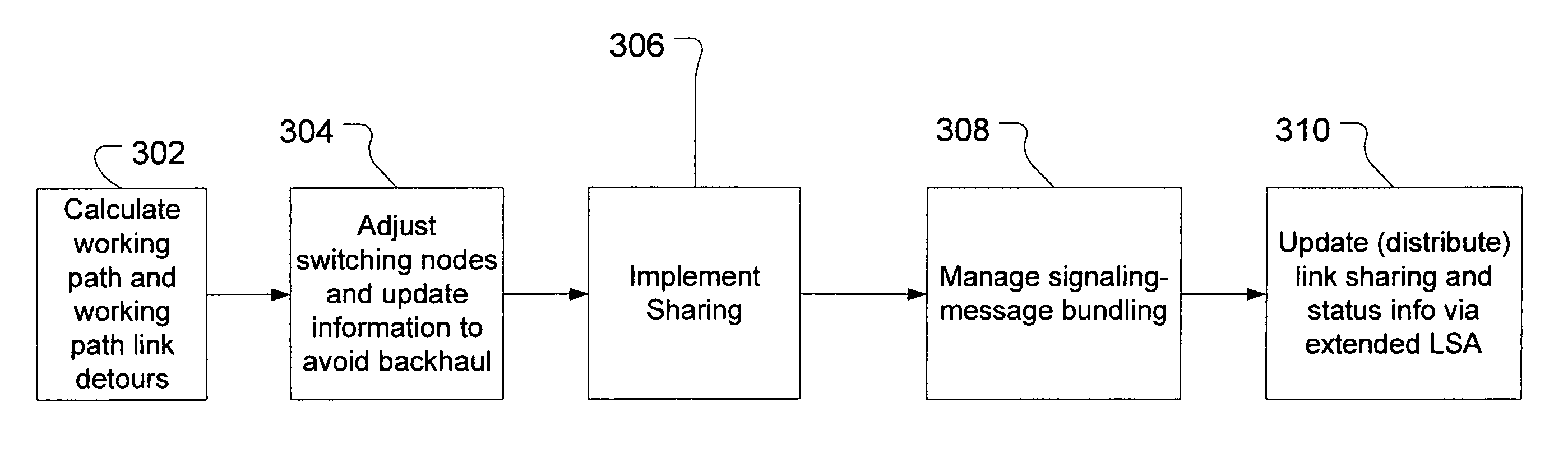
Calculation of link-detour paths in mesh networks
InactiveUS7500013B2Easy to shareError preventionData switching by path configurationLink-state advertisementMesh networking
A protected communication network utilizes a link-based recovery strategy that includes methods for calculating and distributing link-protection parameters and calculating primary and link-detour paths based on these parameters. These link-protection parameters support the computation of more-optimal link-detour paths and a corresponding increase in sharing of network resources between disjoint failures. A joint-optimization mechanism can be employed that considers both the cost of link-detour paths as well as the cost of links in candidate primary paths in the selection of a primary path for a demand. Information for the joint optimization is preferably distributed using link-state advertisements.
Owner:WSOU INVESTMENTS LLC +1
Protection of control networks using a one-way link
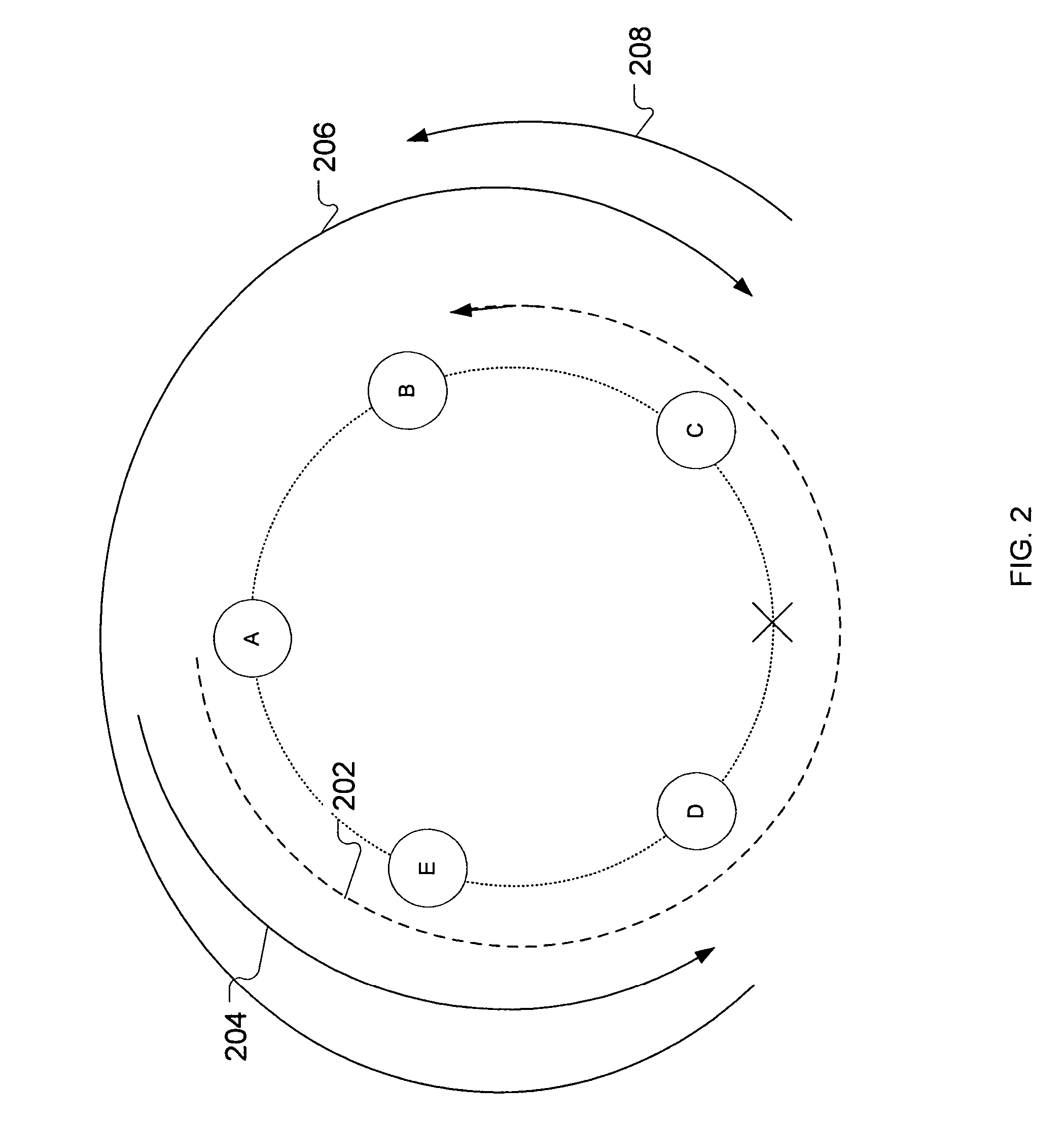
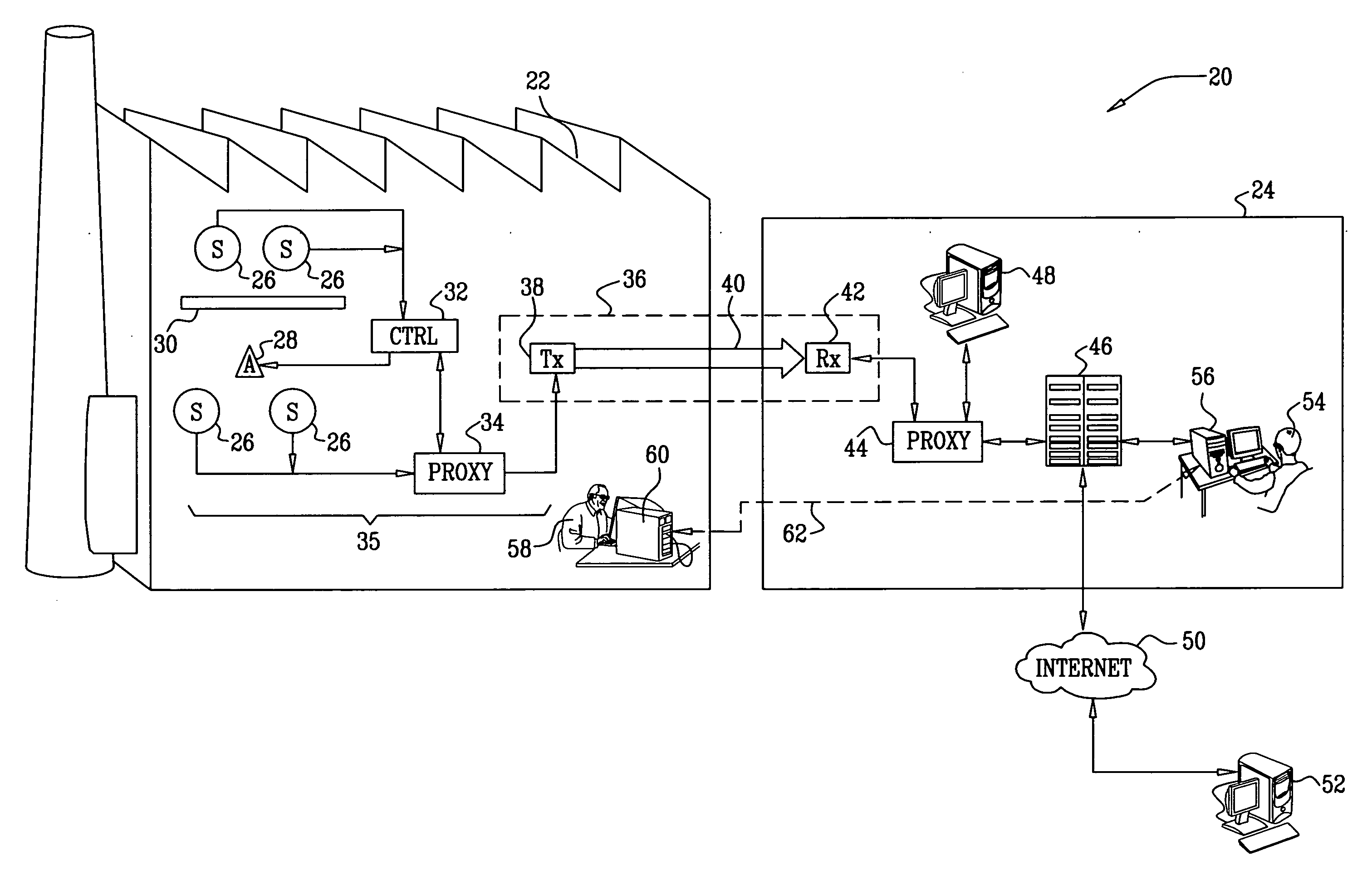
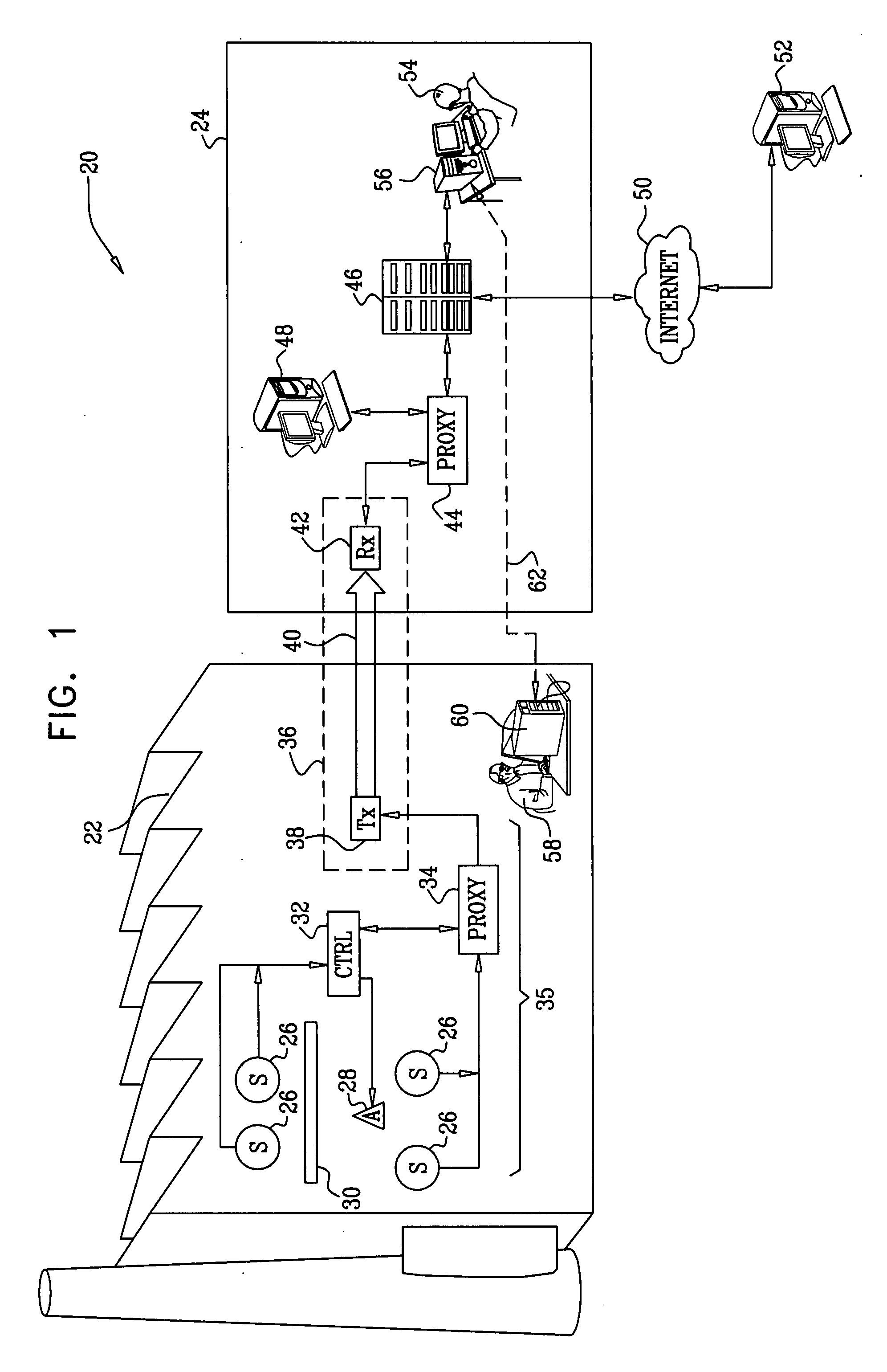
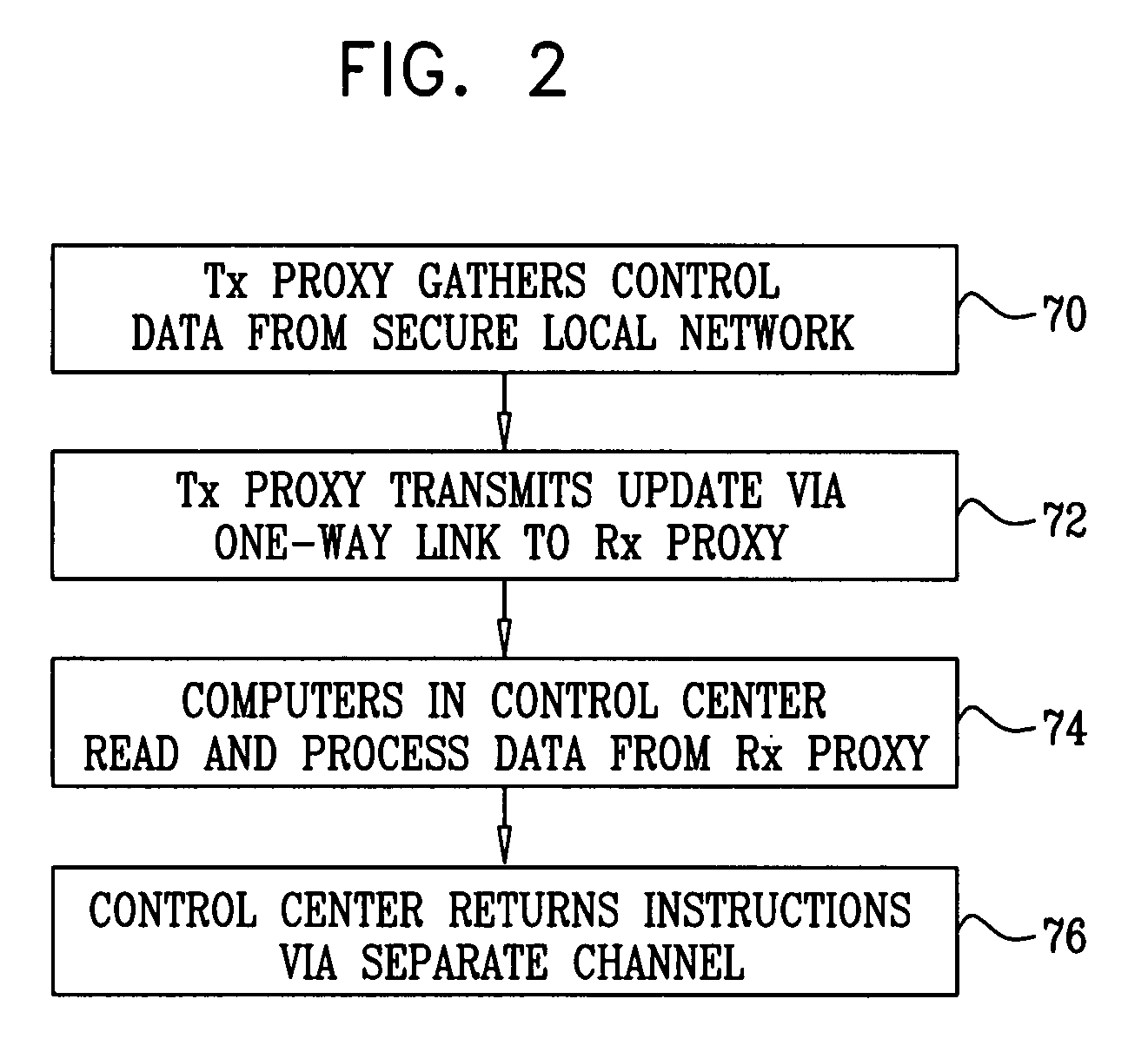
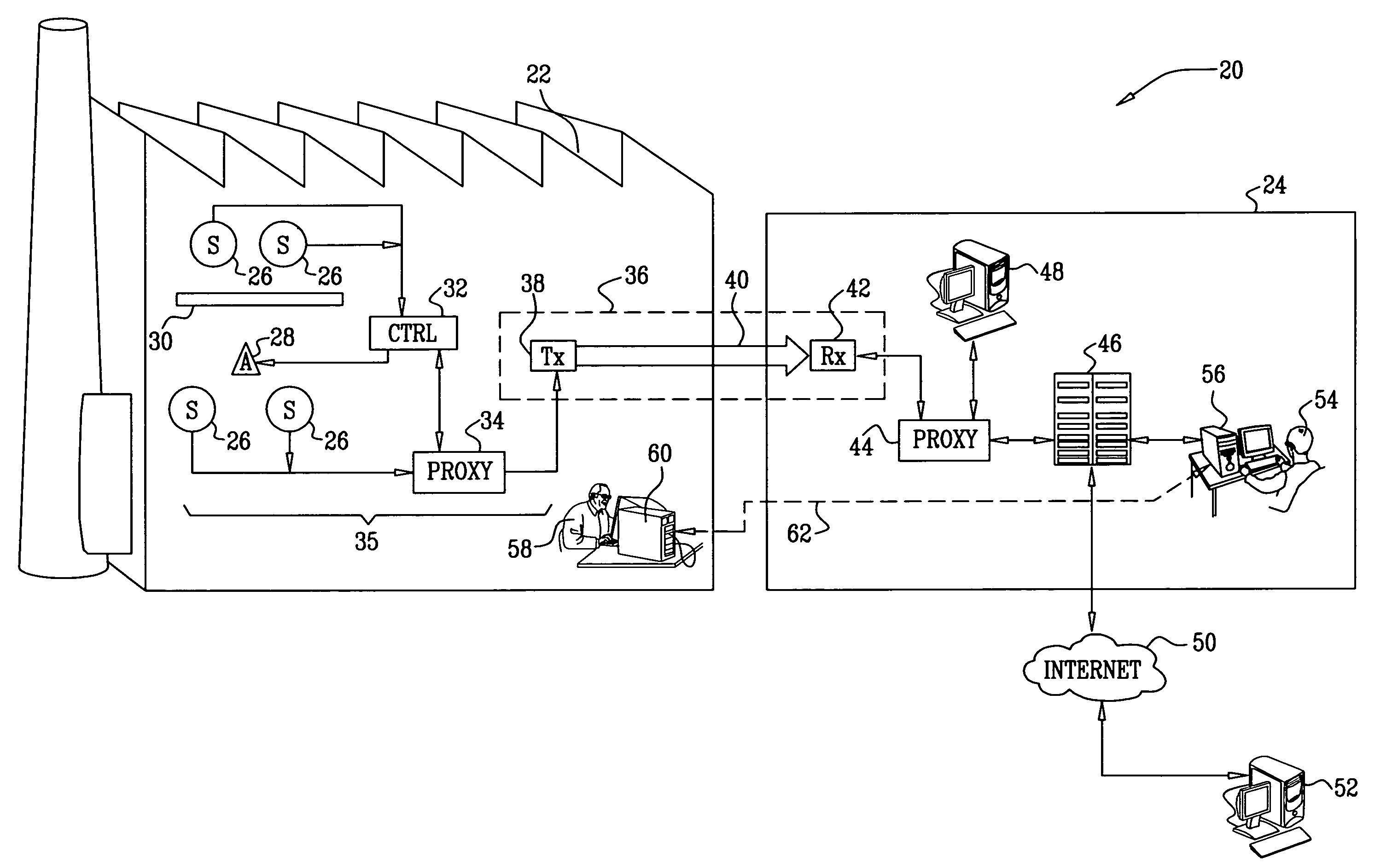
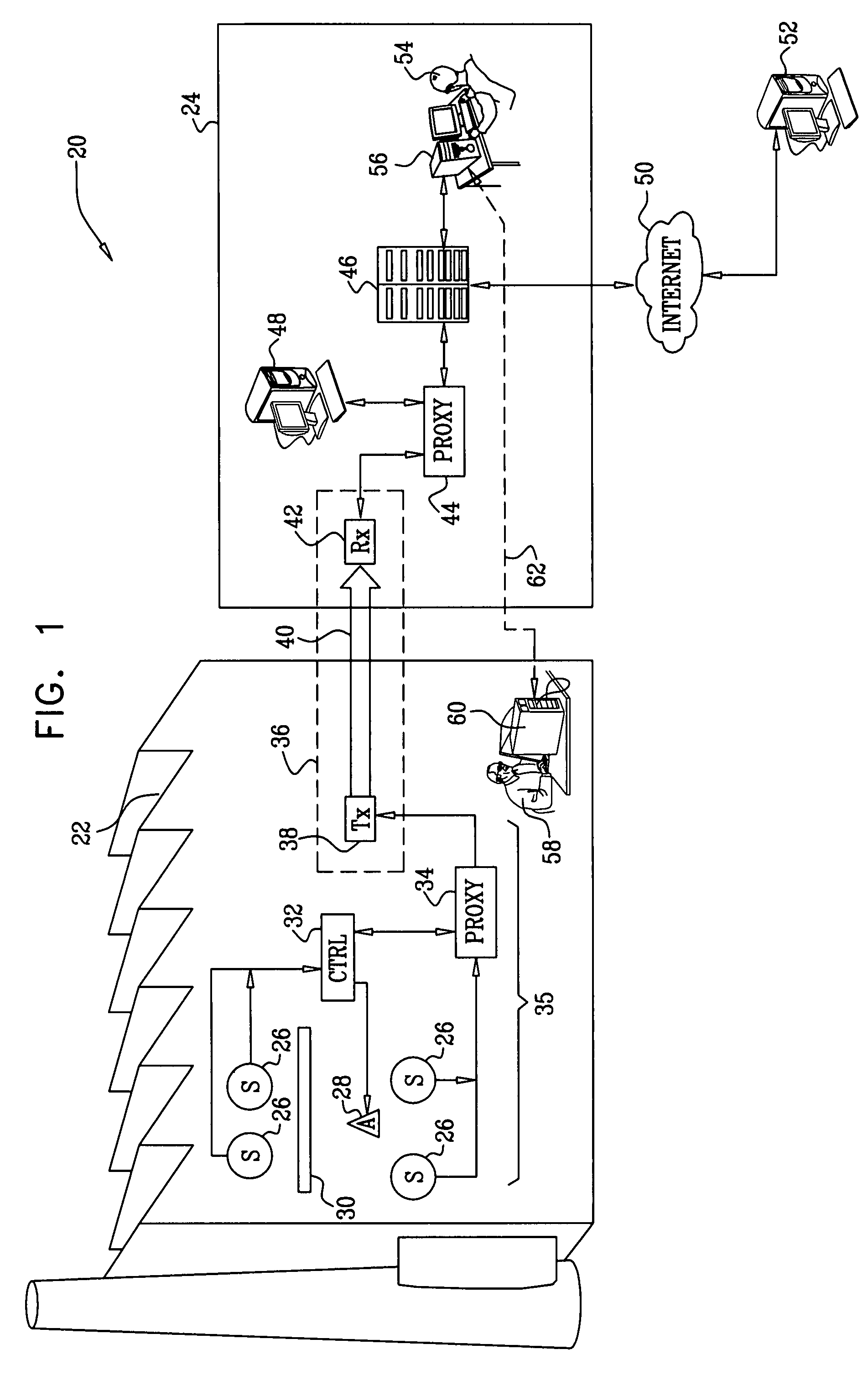
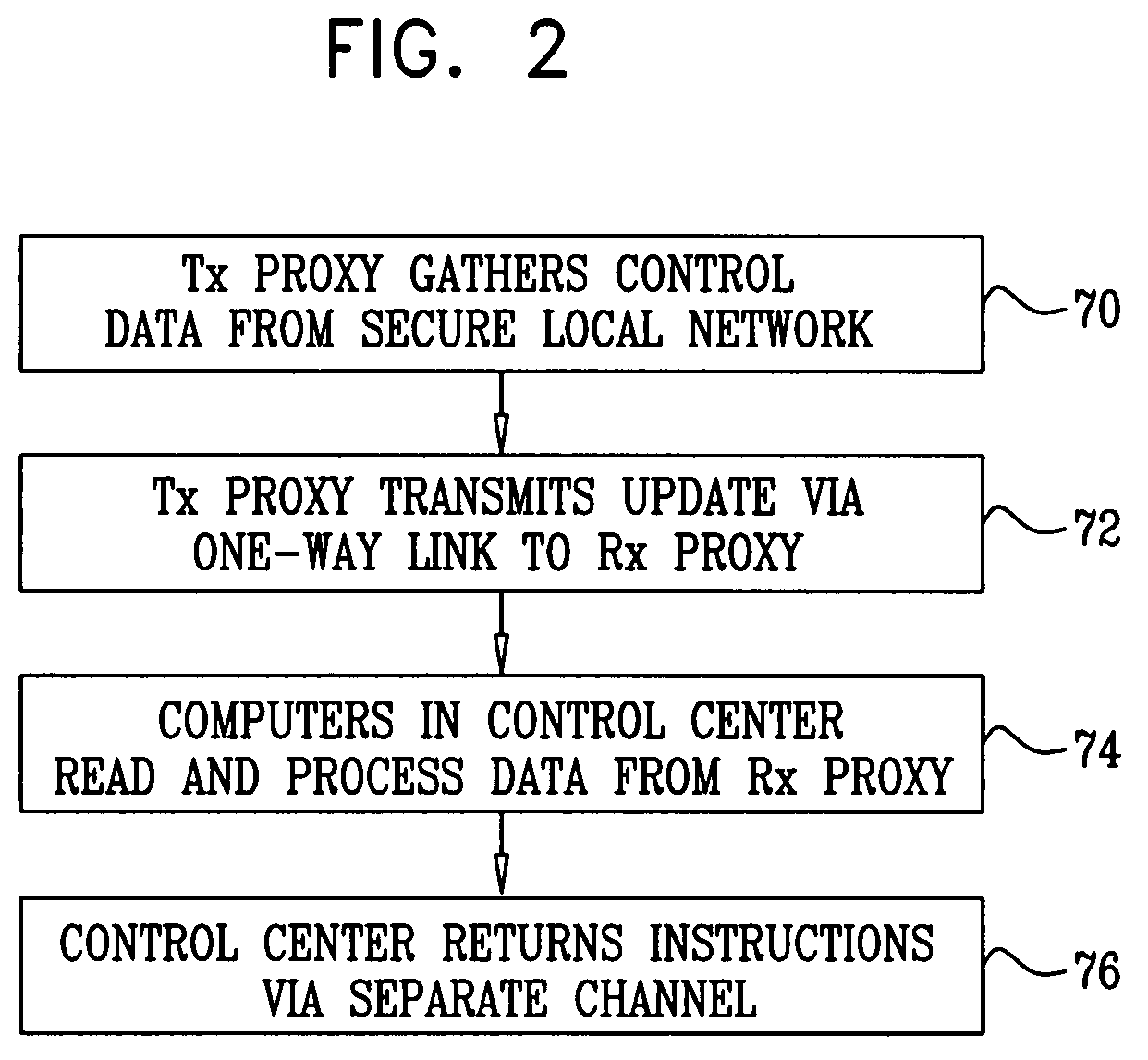
ActiveUS20090002150A1Telemetry/telecontrol selection arrangementsFrequency-division multiplex detailsReal-time computingLink protection
A method for monitoring a process includes receiving a signal from a sensor that is indicative of a physical attribute associated with the process and transmitting data indicative of the received signal over a one-way link. The transmitted data received from the one way link are used in monitoring the process.
Owner:WATERFALL SECURITY SOLUTIONS LTD
Protection of control networks using a one-way link
ActiveUS7649452B2Telemetry/telecontrol selection arrangementsFrequency-division multiplex detailsReal-time computingLink protection
A method for monitoring a process includes receiving a signal from a sensor that is indicative of a physical attribute associated with the process and transmitting data indicative of the received signal over a one-way link. The transmitted data received from the one way link are used in monitoring the process.
Owner:WATERFALL SECURITY SOLUTIONS LTD
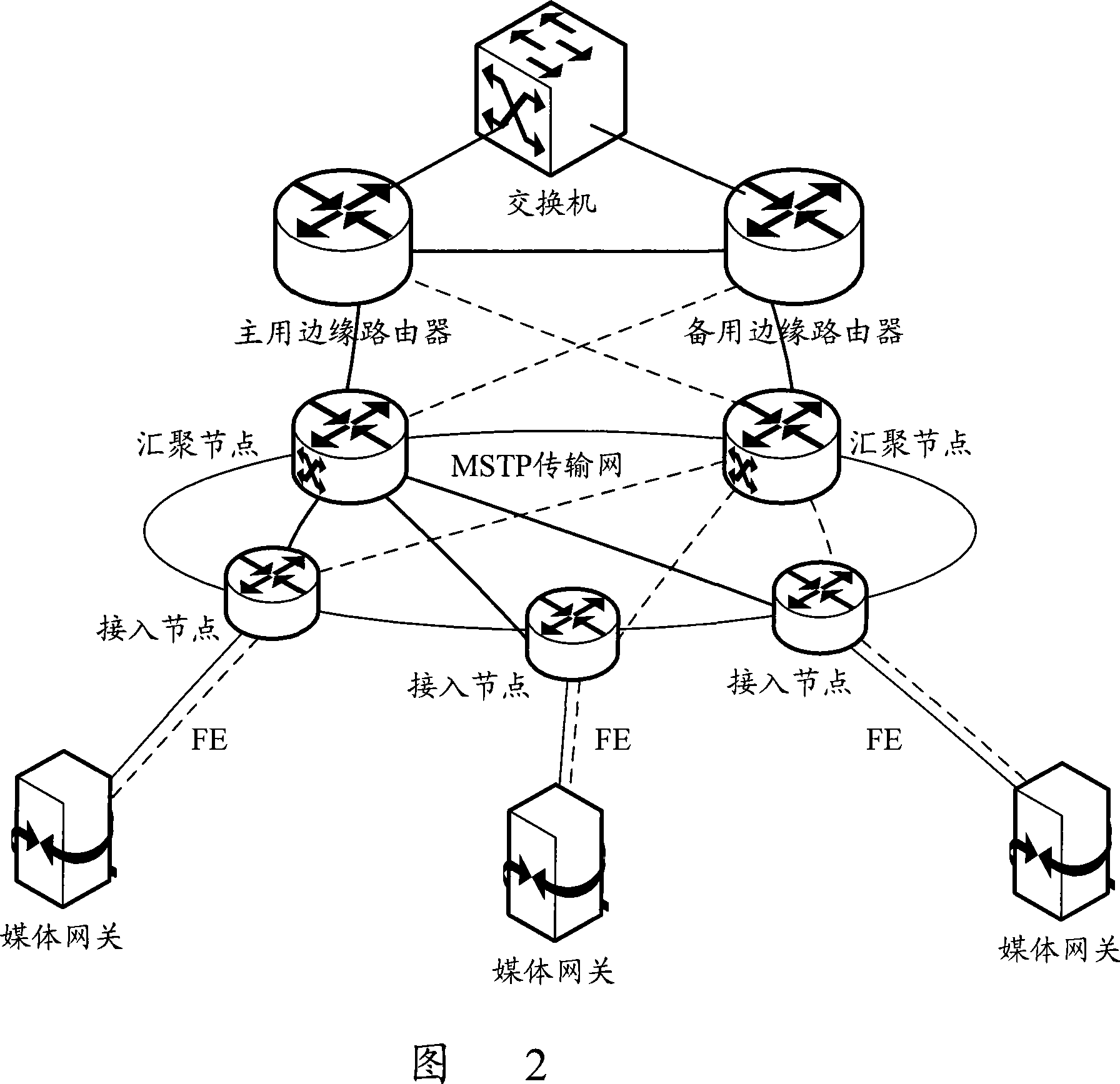
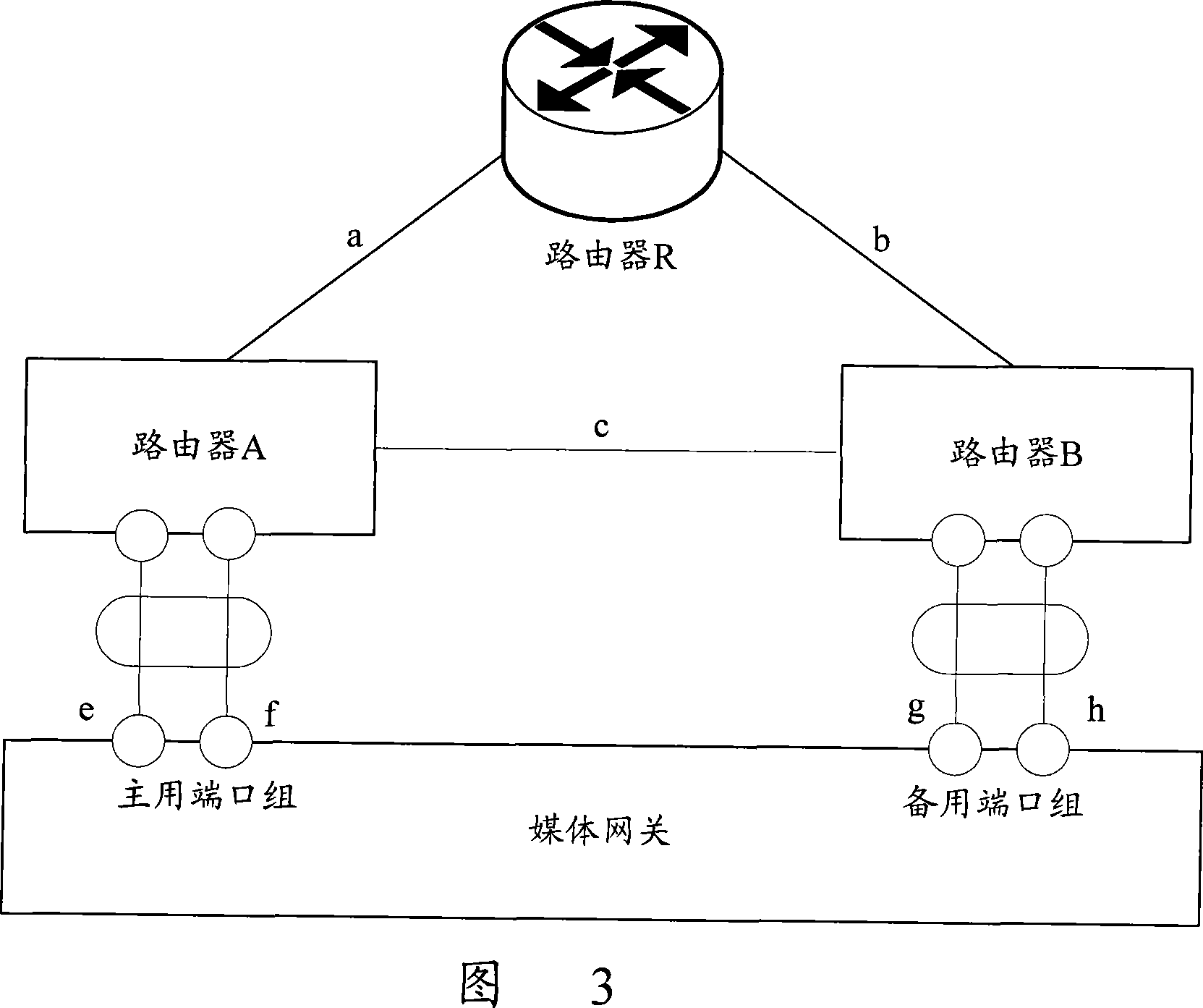
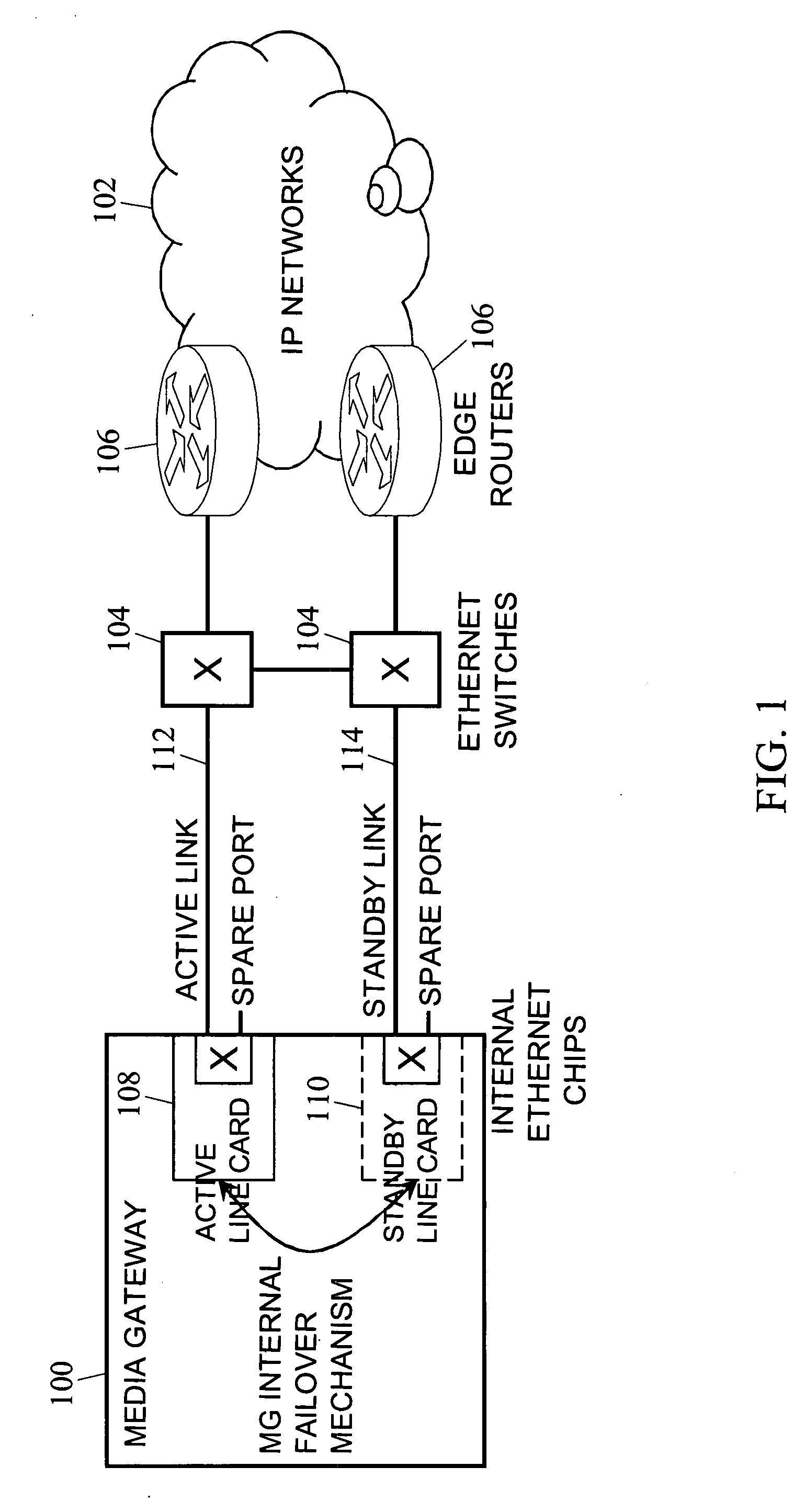
Media gateway upper connection link main spare protecting method
InactiveCN101068139AOvercoming the disadvantages of protectionAchieve conversionError preventionNetwork connectionsEngineeringSelf adaptive
A master-backup protecting method of up-link on media gateway includes setting up up-link port protection set on MG, making master port set and back-up port set separately be energized state and forbidden state, using up-level software to continuously detect master port set and forbidding to use port of master port set when port on master port set is found to be abnormal, energizing port on back-up port set and switching master up-link set corresponding to master port set onto backup up-link set corresponding to backup port set.
Owner:ZTE CORP
Method and system for shared backup allocation in networks based on partial information
Owner:WSOU INVESTMENTS LLC
Method for finding protected path in mesh networks
ActiveUS20100157794A1Guarantee fullyError preventionTransmission systemsTopology informationBackup path
A method of finding a primary communication path in a mesh network, which would be at once a protected path having a fully guaranteed segmented node or node-link protection. The method comprises defining a required protection type and further selecting each specific path segment of the desired communication path based on initial user's requirements and topology information of the network. Each specific node path segment N for the communication path is selected upon ensuring that it can be protected in the network by a node backup path satisfying the initial user's requirements. Each specific link path segment L for the communication path is chosen if it can be protected in the network by a link backup path satisfying the initial user's requirements and if the node path segment N to which segment L leads cannot be protected by a suitable node backup path.
Owner:ECE TELECOM LTD
Method, system and equipment for protecting ring network link
ActiveCN101001192ASolve the problem of communication loopError preventionData switching networksRing networkLoop network
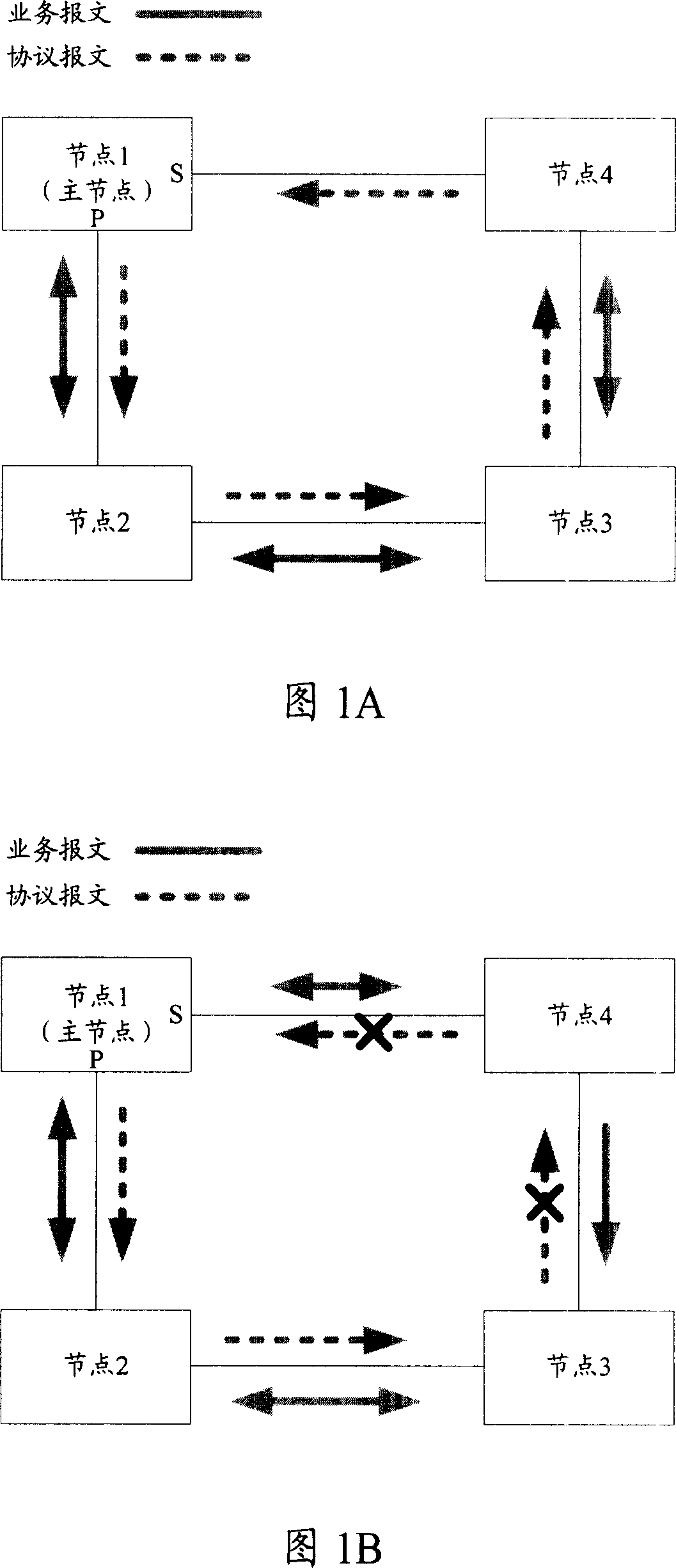
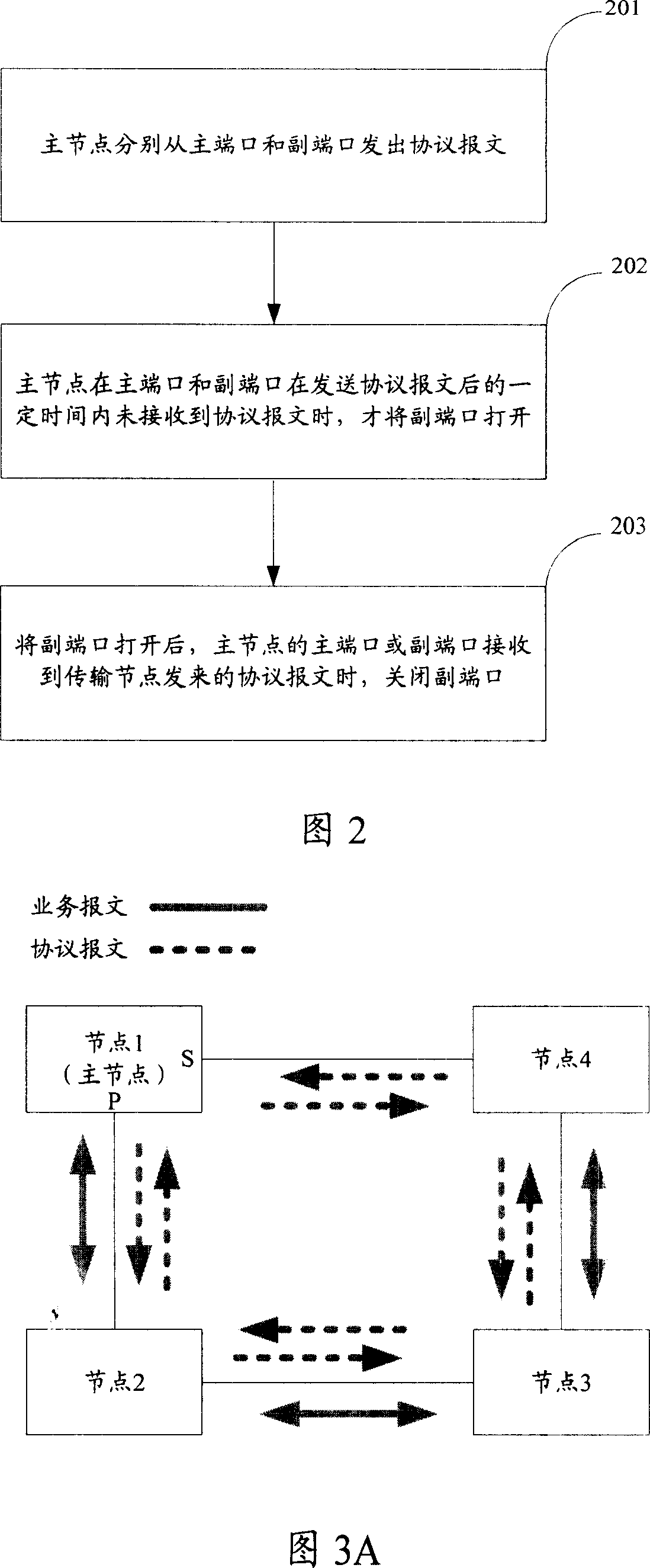
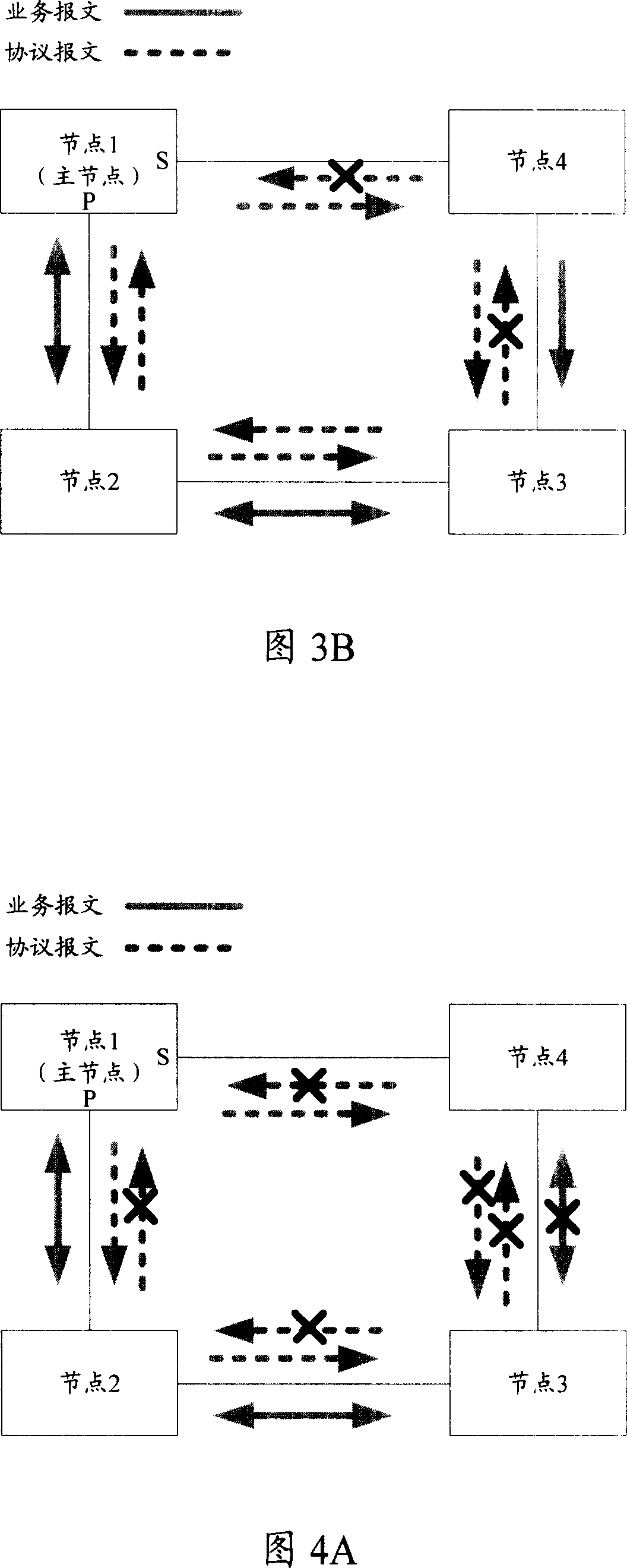
This invention discloses a method for protecting ring network links including a main node and more than one transmission nodes, in which, said main node includes a primary port and a sub-port, and the method includes said main node transmits protocol messages to the transmission nodes from the main and sub-ports, if they have not received the messages in a certain period of time, said main node opens said sub-port. This invention also discloses a system and a device for ring link protection.
Owner:HUAWEI TECH CO LTD
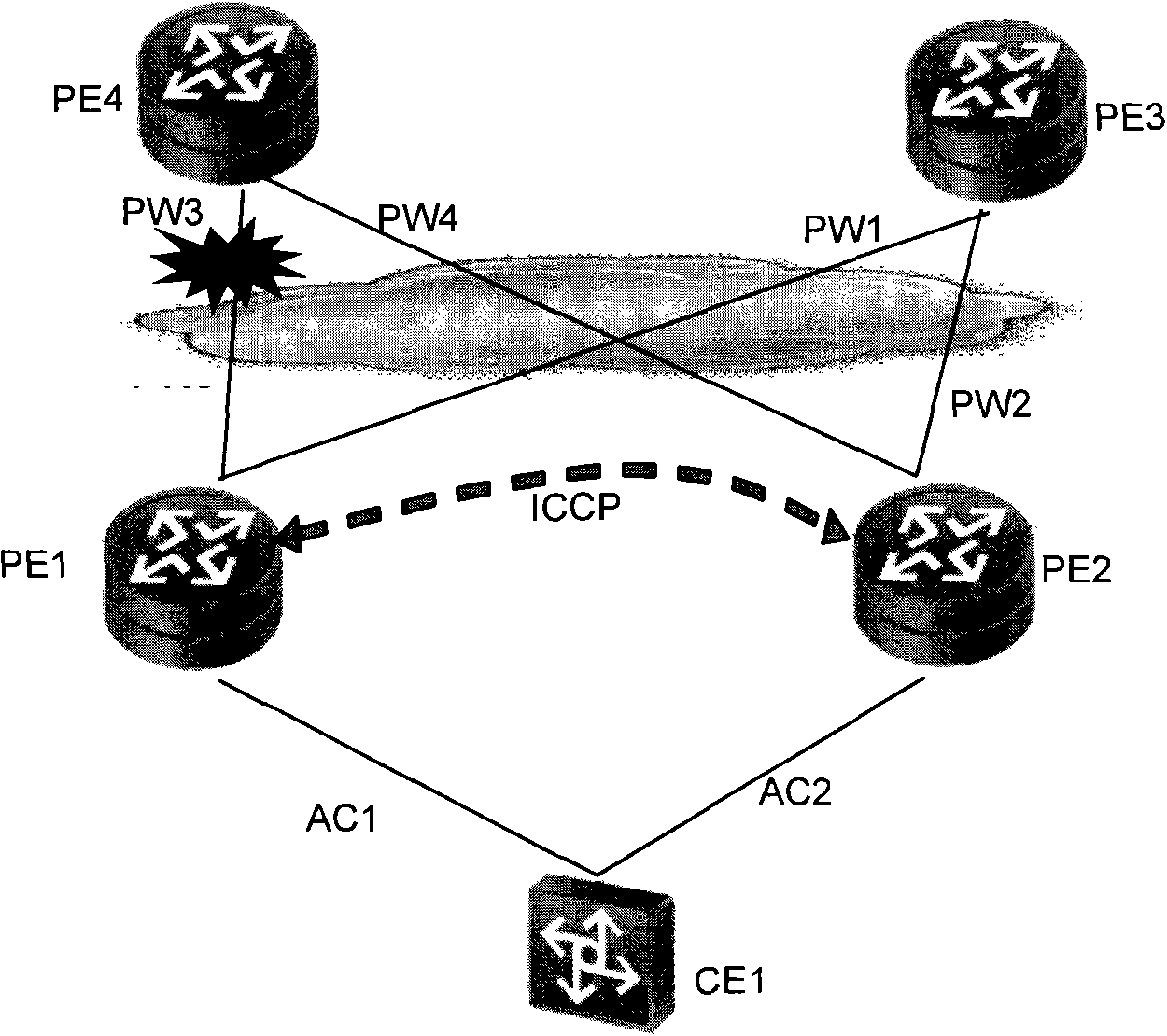
Double-homing protection method and device
ActiveCN102571426AEasy to manageData switching networksWireless communicationPseudo-wireLabel switching
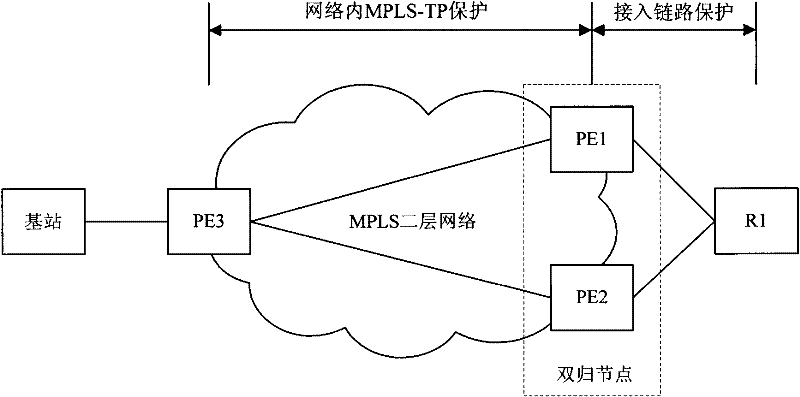
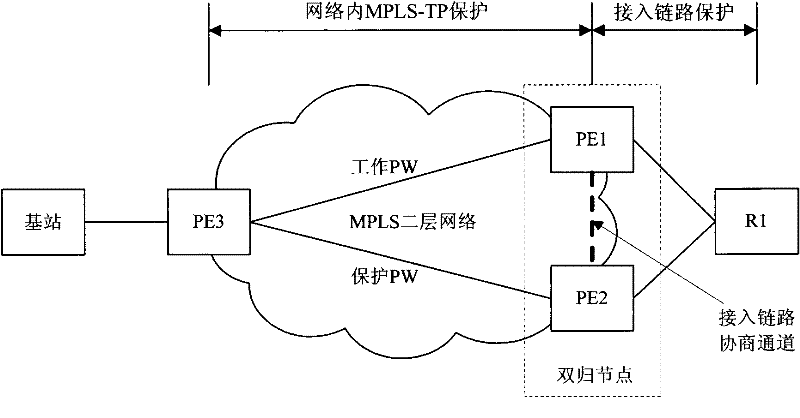
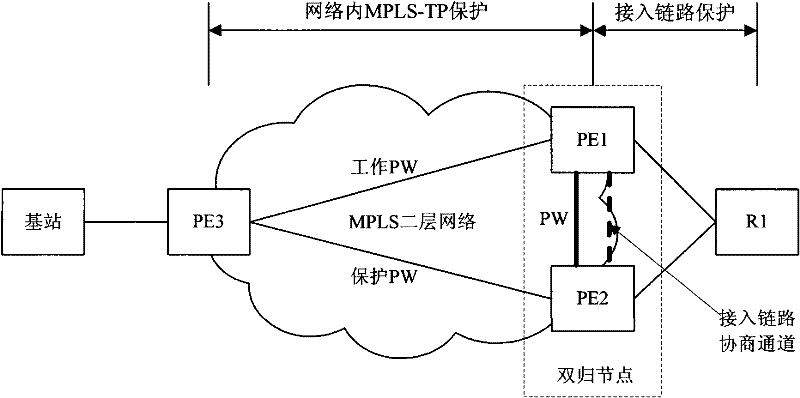
The invention provides double-homing protection method and device. According the method provided by the invention, a forwarding item synchronizing channel and a data sending channel are built between two PE (Provider Edge) devices of a double-homing node; and a PW (Pseudo Wire) and an LSP (Label Switched Path) protection group bearing the PE are built between an opposite end PE device and a logic device which is actually formed by two PE devices, thereby realizing the LSP protection in the network. Through the invention, the in-network protection and the access link protection do not influence each other, the management is simple.
Owner:NEW H3C TECH CO LTD
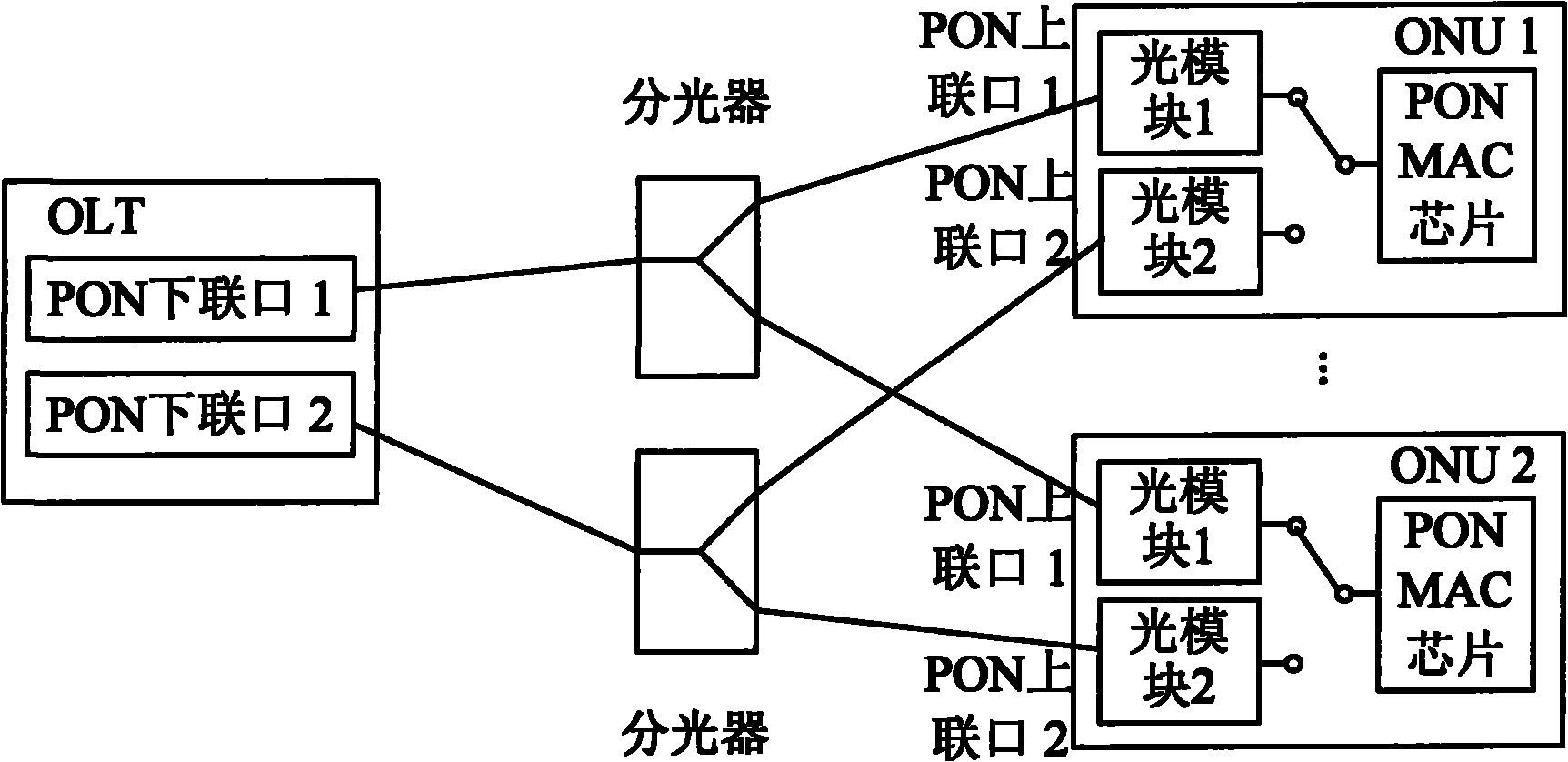
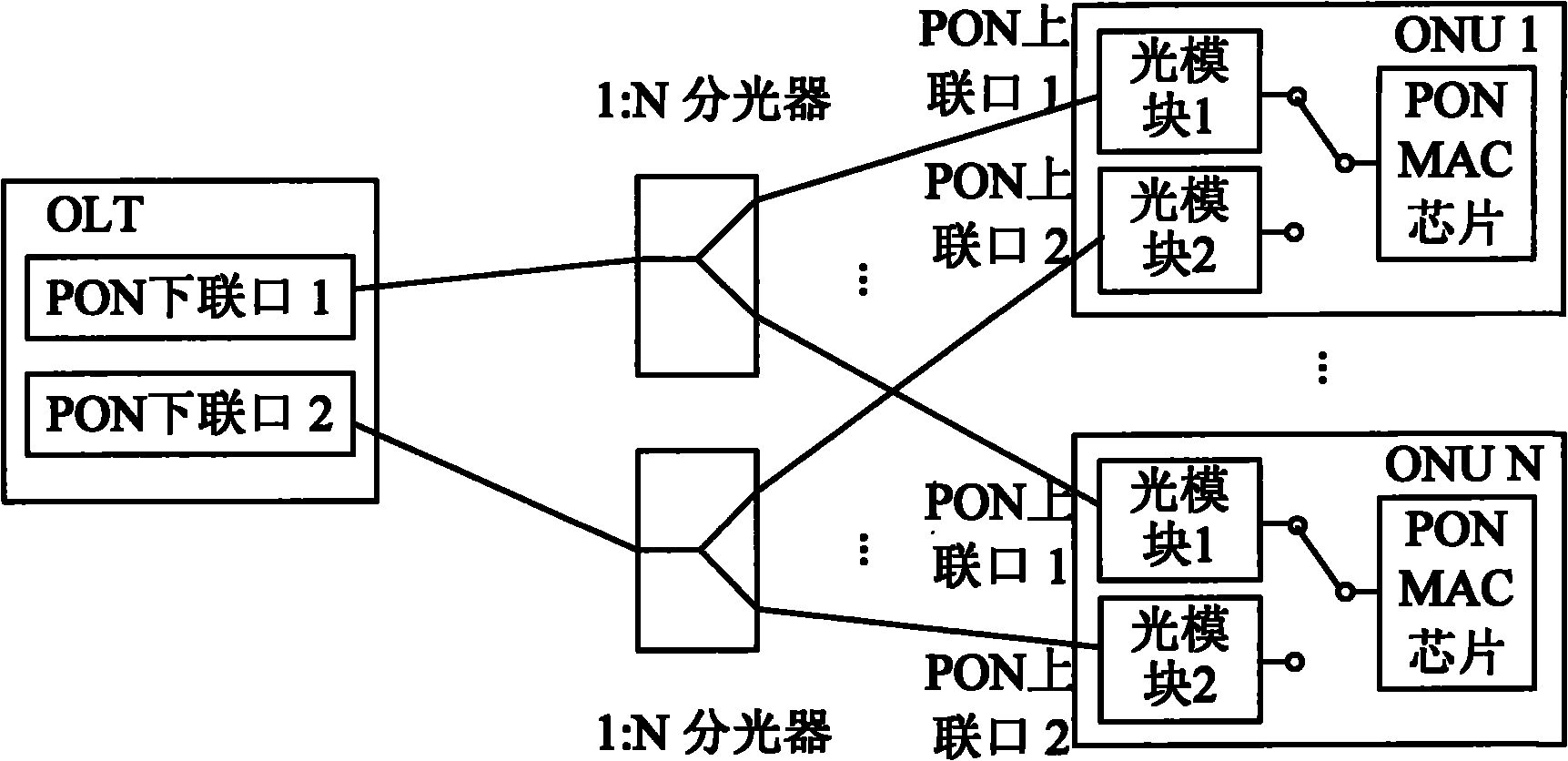
System for protecting optical link of passive optical network, device thereof and method thereof
ActiveCN101877612AAvoid switchingFrequent switchingMultiplex system selection arrangementsElectromagnetic transmissionSignal onEngineering
The invention discloses a system for protecting an optical link of a passive optical network, a device thereof and a method thereof. The system comprises an optical line terminal, two optical splitters and a plurality of optical network units, wherein the optical line terminal is respectively connected with the two optical splitters through two lower connecting ports; the optical splitters the optical link which is from one lower connection port of the optical line terminal into a plurality of optical links; the plurality of optical network units respectively and correspondingly connect two upper connecting ports with one optical link on the two optical splitters; the mutually-protected optical links are formed between the optical line terminal and the two optical splitters; and the mutually-protected optical links are formed between each optical splitter and every two optical network units. By fast detecting the optical link, the invention effectively filters the dither of an optical signal on the optical link caused by the noise, the fault and the manual unplugging and plugging, thereby being capable of preventing from frequently switching between the two mutually-protected optical links.
Owner:ZTE CORP
Method for implementing double chain circuits among master-salve equipments
ActiveCN101257405AEffective protectionAchieve protectionData switching networksComputer hardwareComputer science
Owner:ZTE CORP
Switch-over protection method of link between satellites
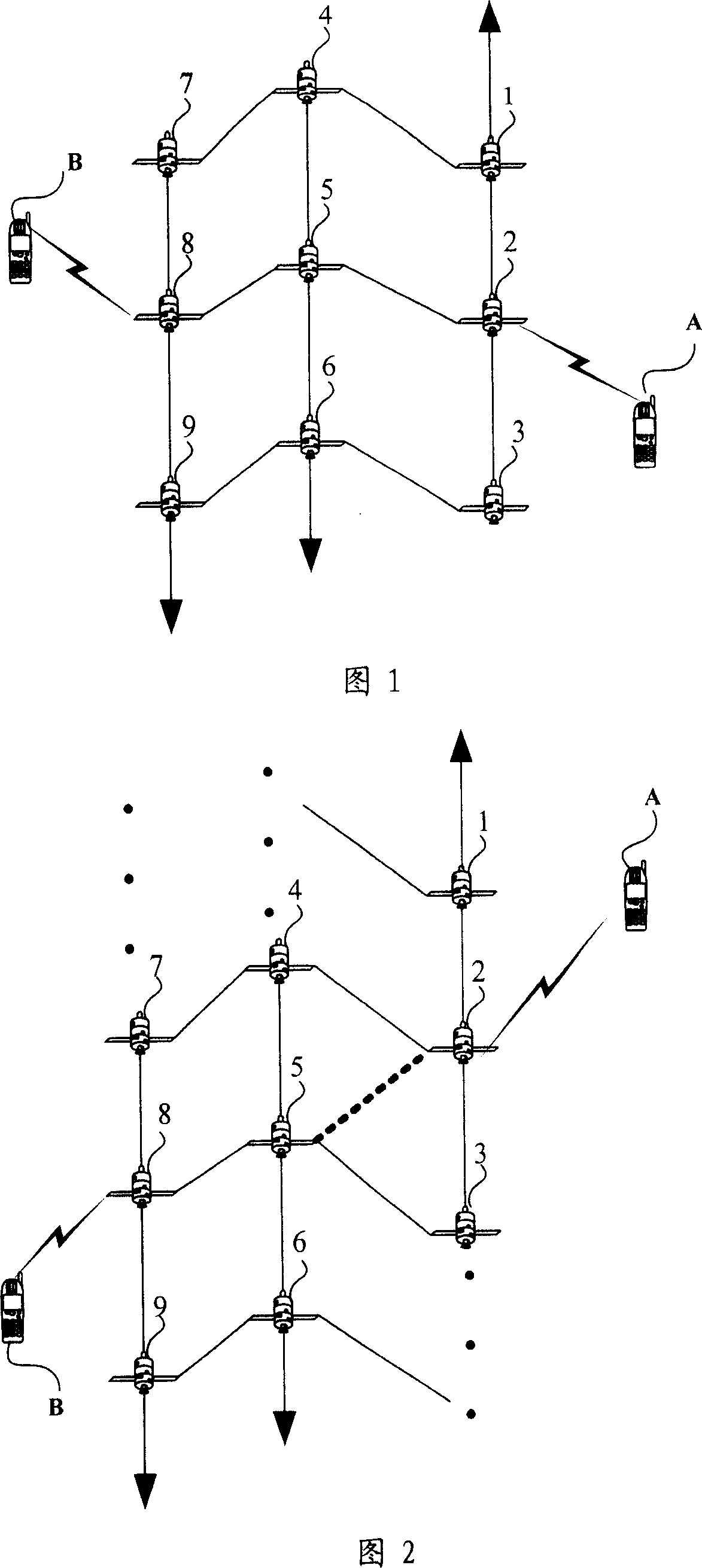
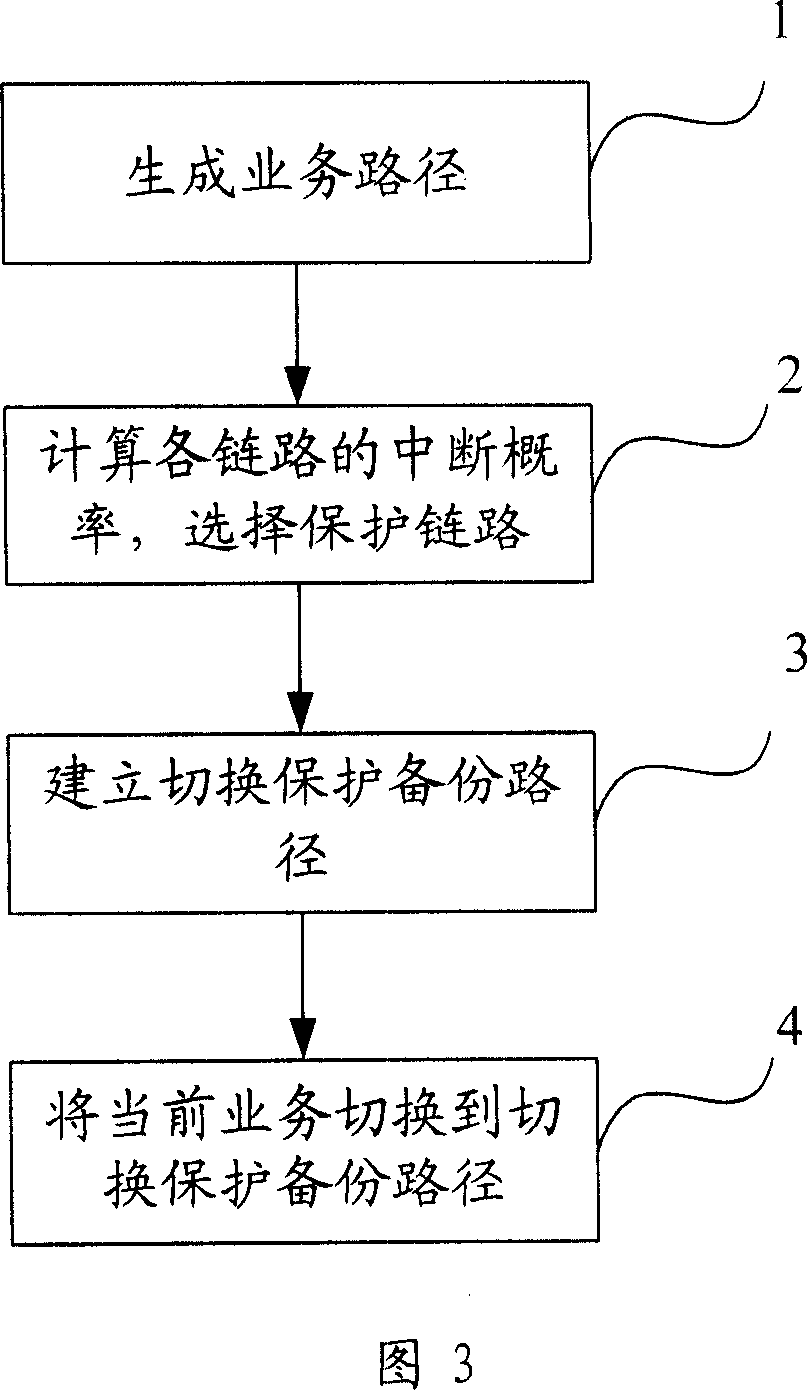
InactiveCN101001100AGuaranteed continuityNot destroyedRadio relay systemsPath switchingProtected mode
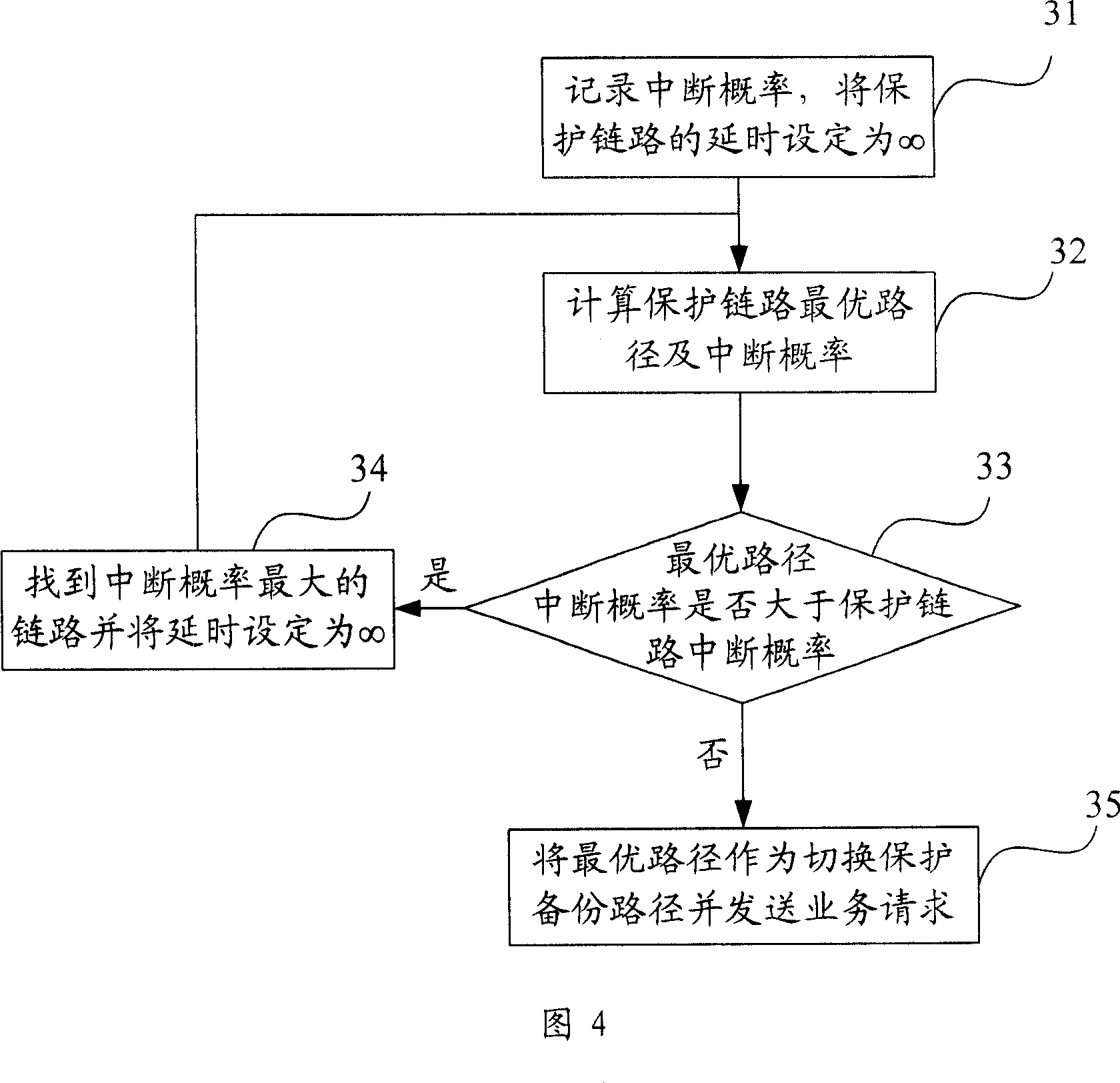
This invention provides a switch protection method for links among satellites including: 1, generating service paths according to the service requirement of a terminal, 2, computing the interruption probability of each link in the service routes to select protection links for interruption protection, 3, setting up switch protection backup route between two switch nodes in the protection link, 4, when the protection link switches paths, it switches the current service between two nodes to said back up path. This invention applies a mode of resuming protection locally to recover the interrupted paths because of switch quickly to guarantee the durative of service communication and that related QoS target will not be broken.
Owner:BEIHANG UNIV
Link protection method and system for virtual private network
ActiveCN102035681AAchieving partial protectionProcessing content lessNetworks interconnectionPseudo-wireMobile virtual private network
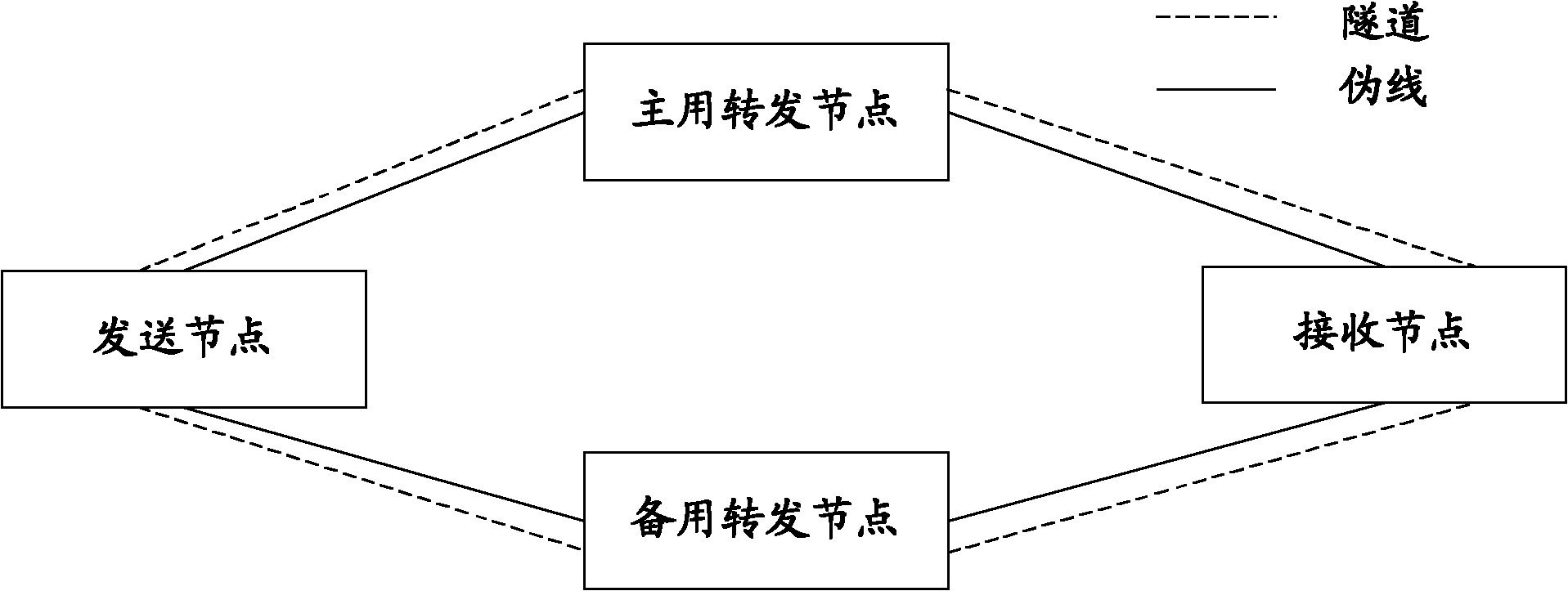
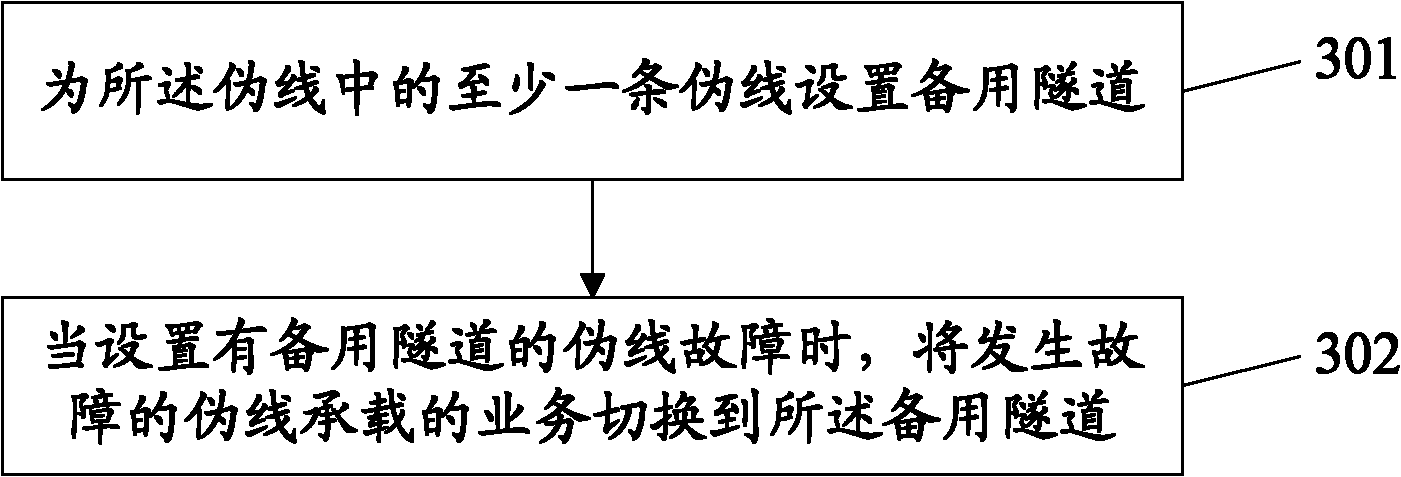
The invention provides a link protection method and a link protection system for a virtual private network and relates to the field of communication. Transmitting nodes and receiving nodes in the virtual private network are connected with main forwarding nodes and standby forwarding nodes through pseudowires. The method comprises the following steps of: setting a standby tunnel for at least one pseudowire in the pseudowires; and when the pseudowire provided with the standby tunnel breaks down, switching failed pseudowire-born service to the standby tunnel. The provided technical scheme can be applied to link protection management of a double-layer virtual private network.
Owner:ZTE CORP
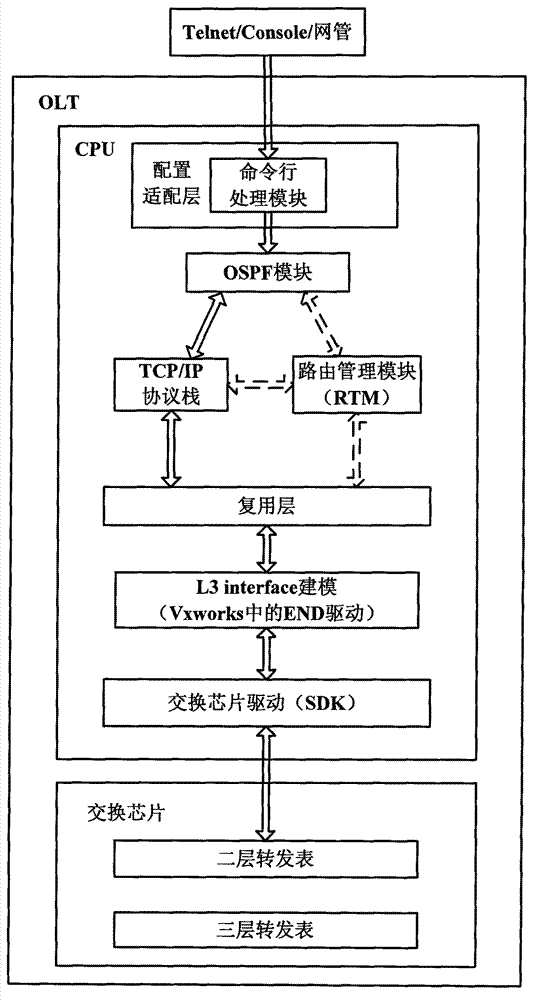
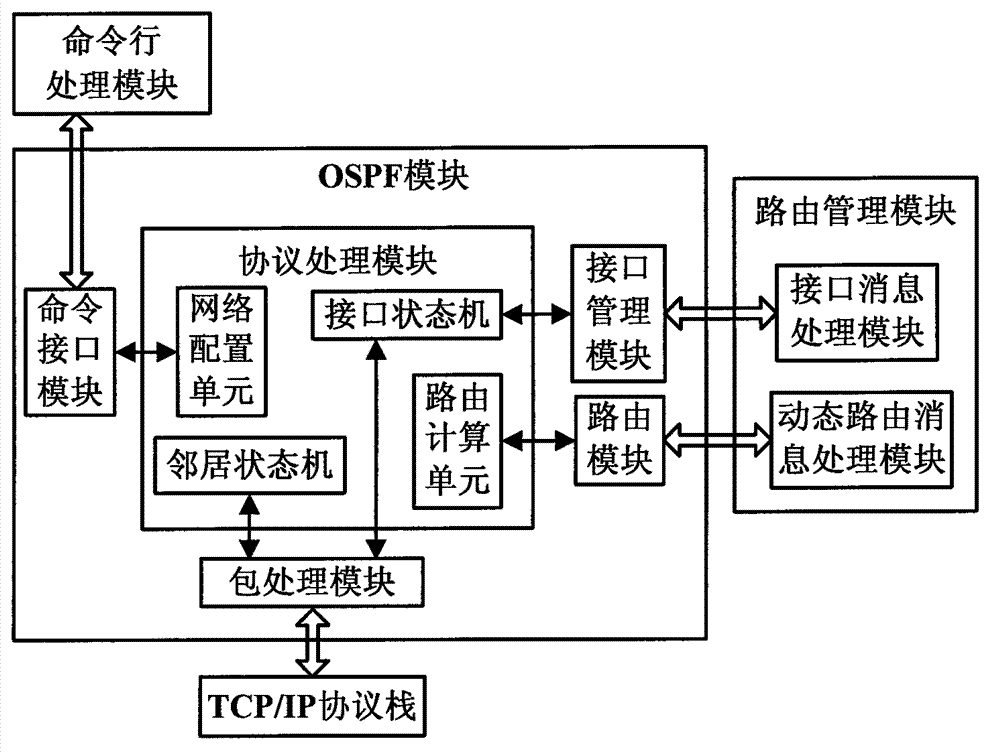
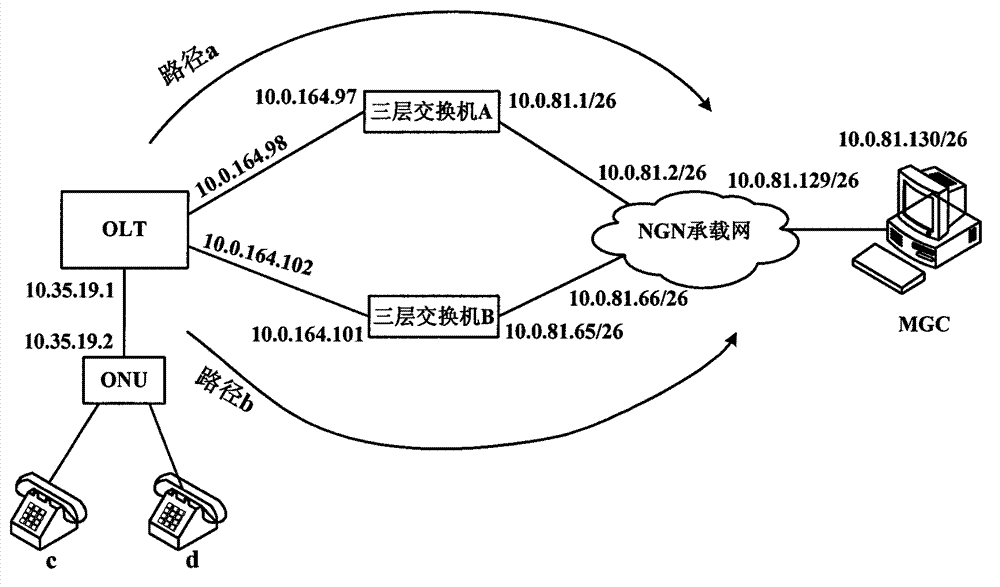
System and method for realizing OLT voice double upper-link protection based on OSPF routing protocol
ActiveCN102857422ARealize dual uplink protectionFast protection switchingData switching networksRouting tableProtocol for Carrying Authentication for Network Access
The invention discloses a system and a method for realizing OLT (Optical Line Terminal) voice double upper-link protection based on OSPF (Open Shortest Path First Interior Gateway Protocol) routing protocol, and relates to the field of PON (Passive Optical Network). A CPU of an OLT master control panel in the system comprises an OSPF module and an RTM (Running Timer Meter) module. Two upper-link ports of an OLT are respectively connected with a NGN (Next Generation Network) through three-layer exchangers A and B to connect with a remote-end MGC (Media Gateway Controller) server; paths A and B are formed between the OLT and the MGC server; the OLT and the three-layer exchangers A and B are respectively configured with the OSPF protocols and operate; the OLT learns the routes of all network sections on the paths A and B through the OSPF route protocol; the OSPF module stores the learnt routes in the route table of the OSPF module and announces the learnt routes to the RTM module; and the RTM modules collects the route items and writes the route items in an RIB table. When a main link breaks, the OSPF route protocol learns the route of a backup link and carries out rapid protective rearrangement to the high real-time voice business among internetworking nodes.
Owner:FENGHUO COMM SCI & TECH CO LTD
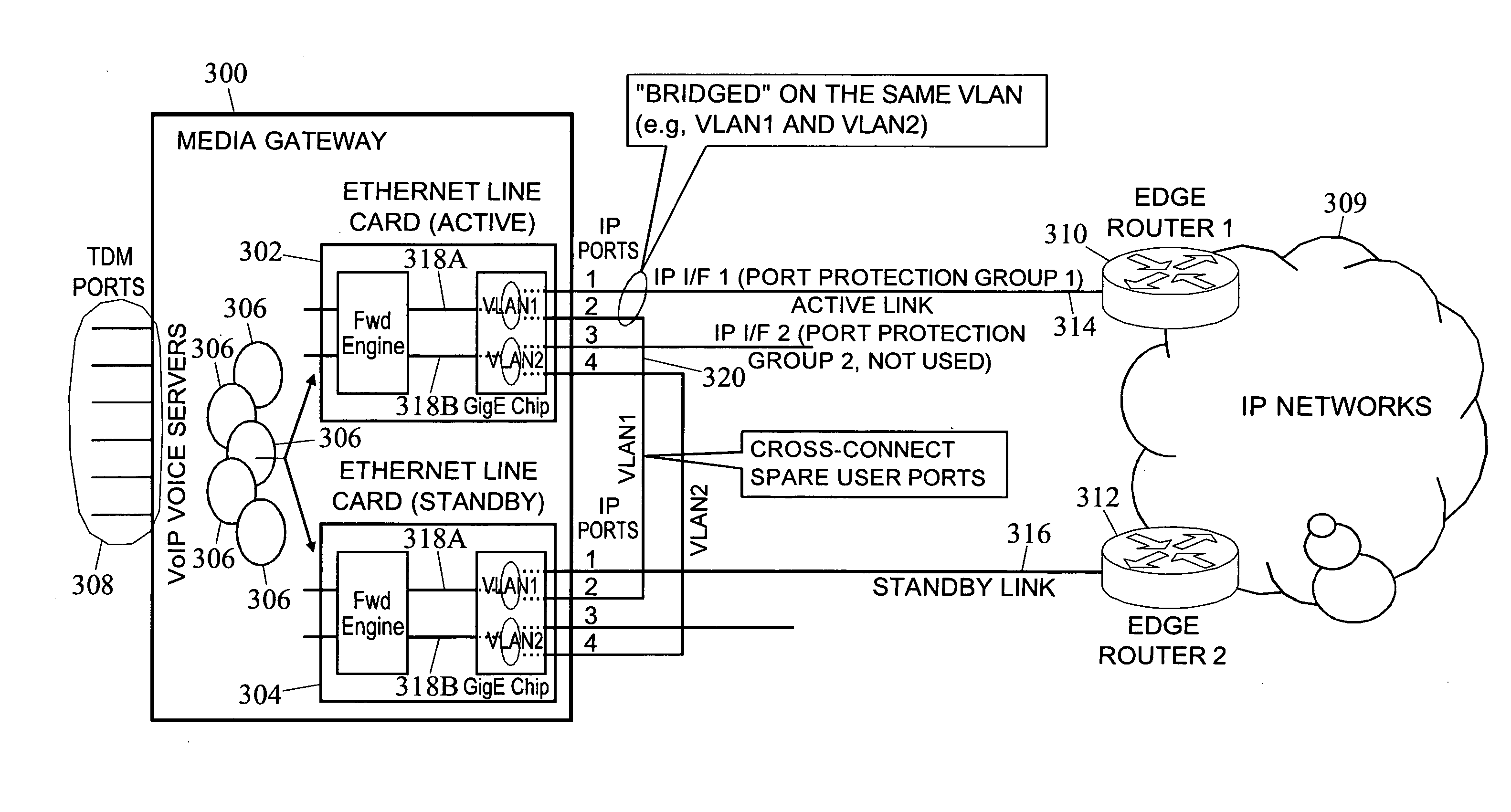
Methods, systems, and computer program products for implementing link redundancy in a media gateway
Methods, systems, and computer program products for implementing link redundancy in a media gateway are provided according to one method, a media gateway link protection group is provisioned to associate with a common VLAN a common virtual local area network (VLAN) primary and secondary links associated with at least one line card in a media gateway. The primary and secondary links are connected using a cross connection between ports associated with the at least one line card. At run time, traffic is automatically bridged between the primary and secondary links using the common VLAN and the cross connection.
Owner:GENBAND US LLC
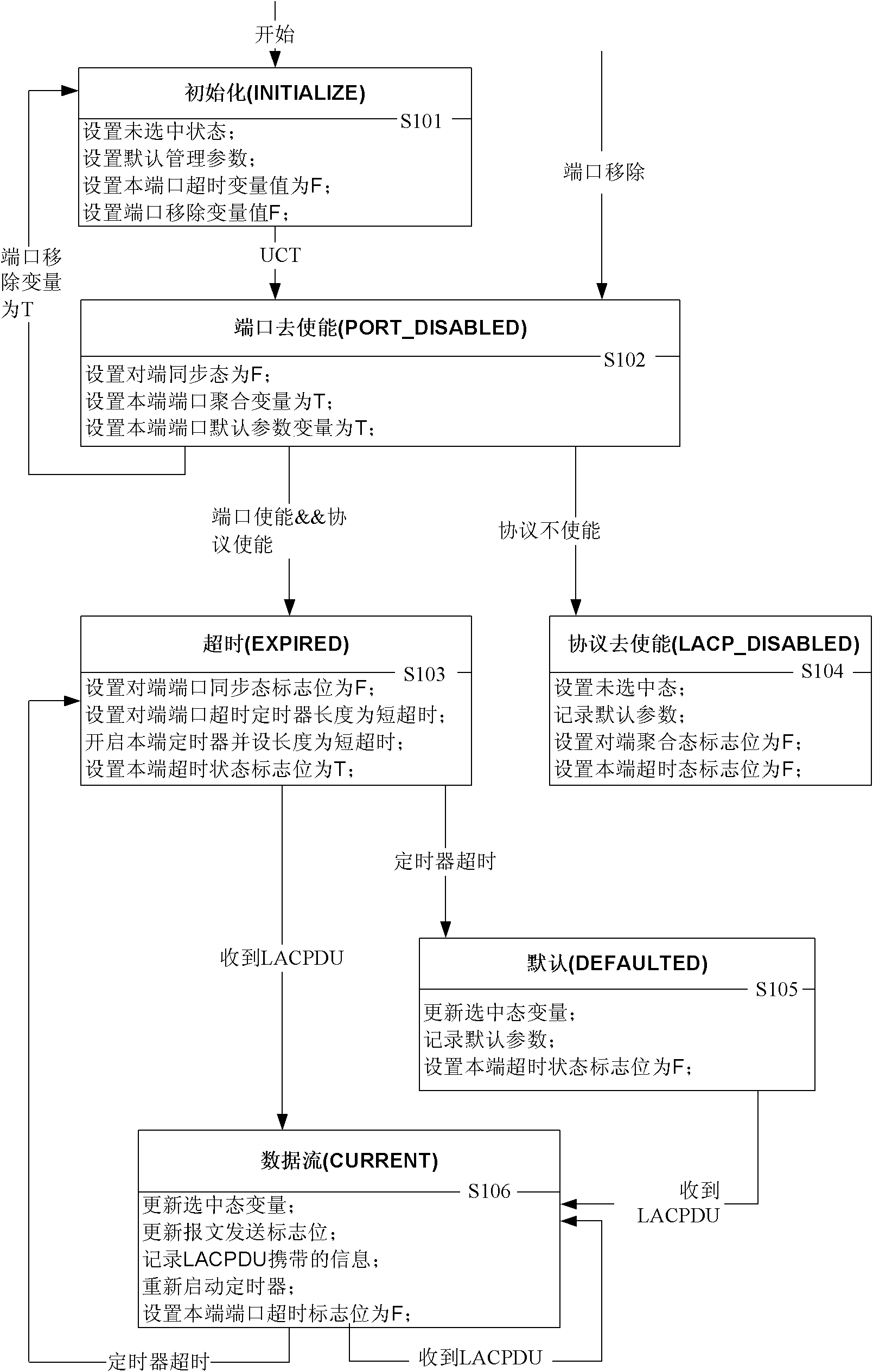
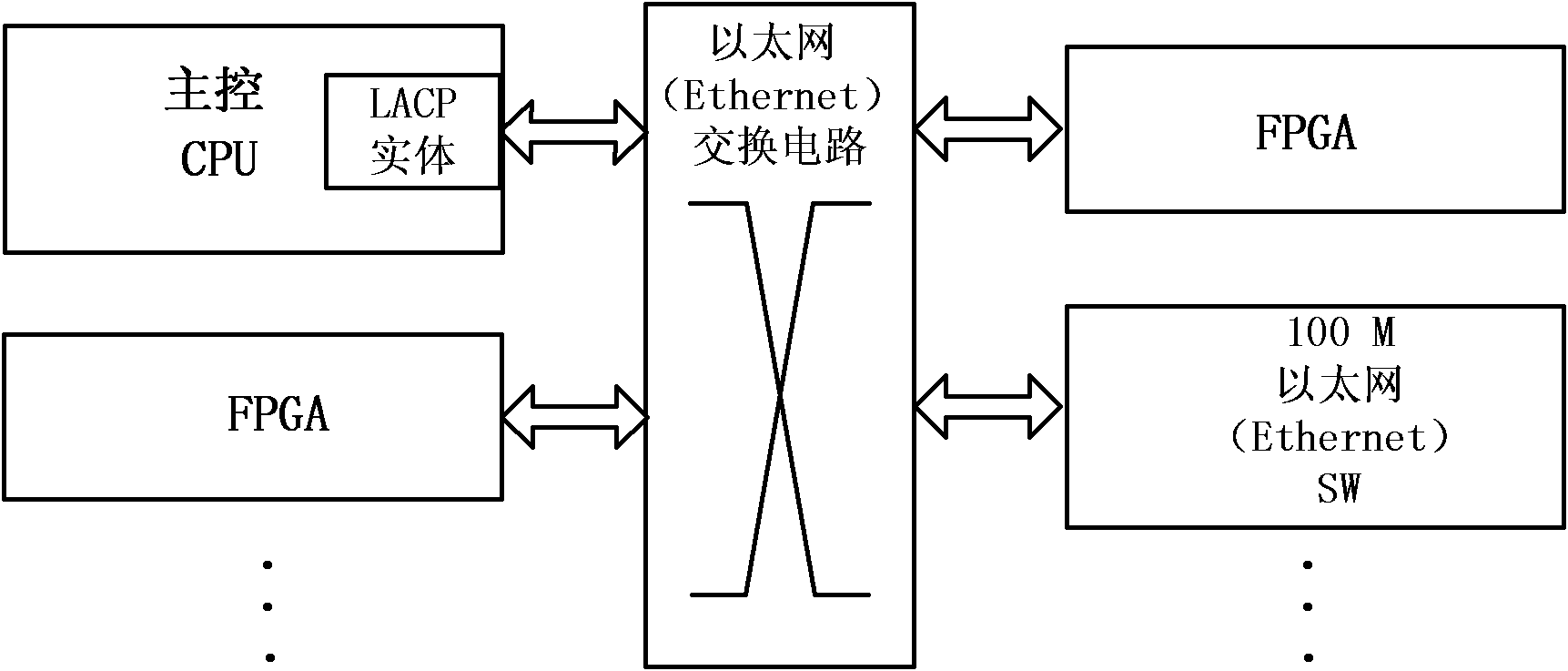
Link aggregation abnormity recovery method and exchange equipment
ActiveCN103188172AWill not affect normal forwardingData switching networksHigh level techniquesRecovery methodLink aggregation
The invention provides a link aggregation abnormity recovery method, an LACP (Link Aggregation Control Protocol) message processing method and exchange equipment. The link aggregation abnormity recovery method comprises the steps that the home-end exchange equipment receives an LACP message that is sent by the opposite-end exchange equipment and carries a request link protection event, and the home-end exchange equipment shuts down a receiving timer of the LACP message. According to the link aggregation abnormity recovery method and the exchange equipment, the receiving timer of the LACP message is shut down after the LACP message carrying the request link protection event is received, so that the equipment cannot detect a port of an opposite end to be unavailable due to the fact that the opposite-end equipment conducts abnormal events such as warm start and cannot send a data packet, normal forwarding of data cannot be influenced, and key network service can be influenced less.
Owner:ZTE CORP
Method and device for forwarding message based on multilink
InactiveCN101094185ALow costIncrease flexibilityData switching networksTraffic capacityResource utilization
The method comprises: pre-determining the traffic forwarding ratio of output interface corresponding to different link; according to the traffic forwarding ratio, outputting all messages via the corresponding output interface; due to different traffic forwarding ratios of output interfaces corresponding to different links, the different links can load different traffics while realizing the load balance and link protection such that the links with different physical properties can selected to be as equivalent chain.
Owner:NEW H3C TECH CO LTD
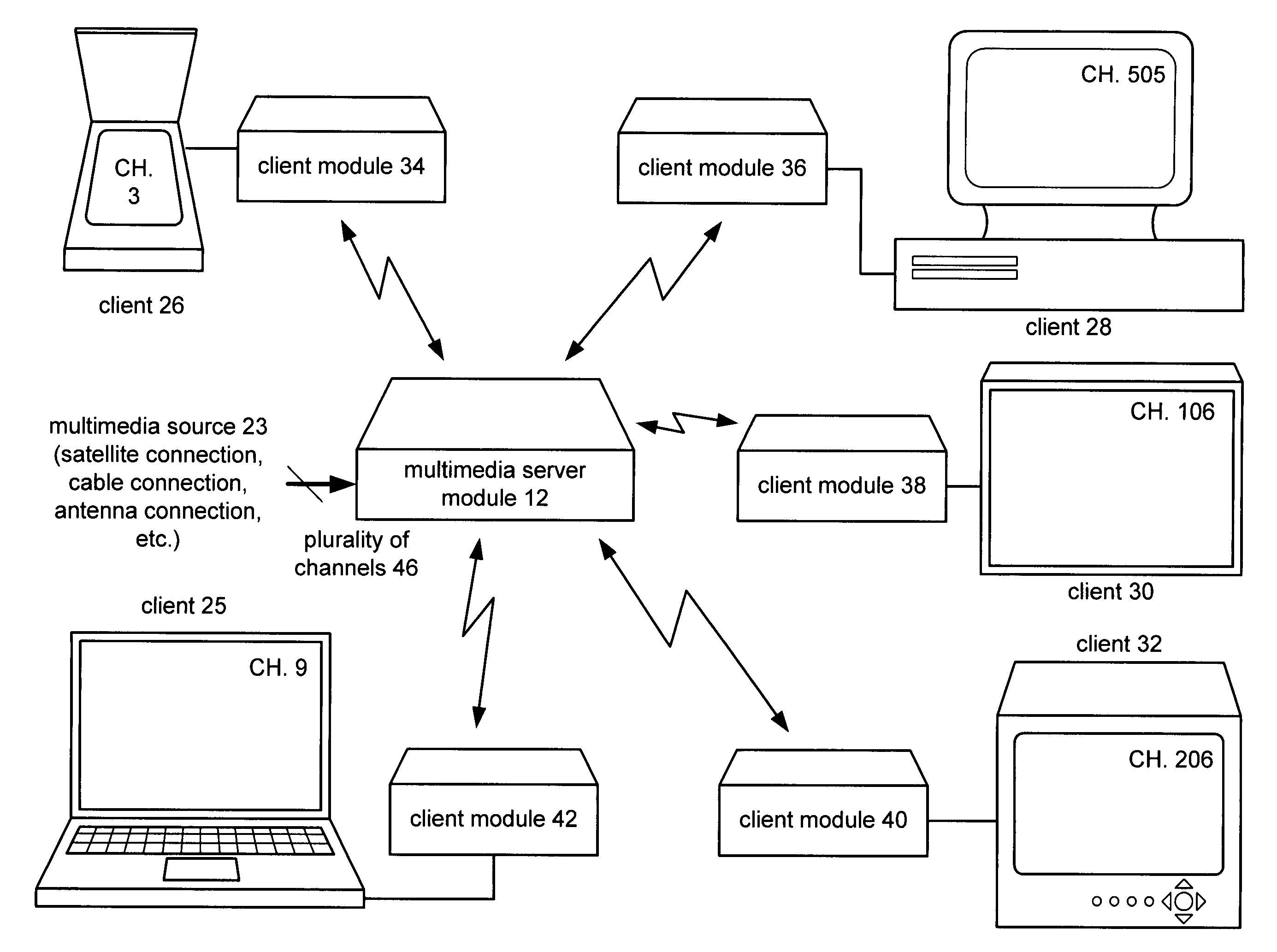
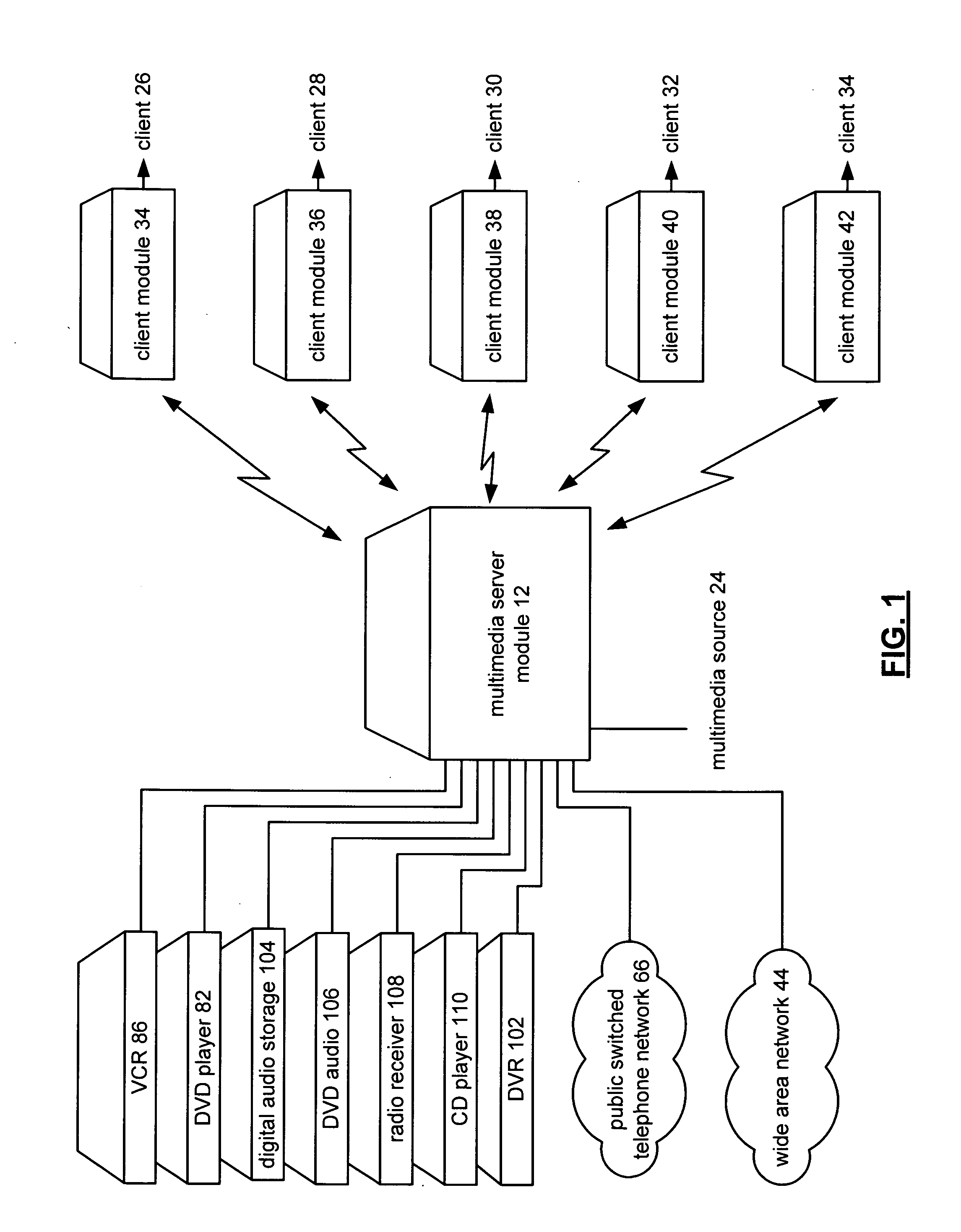
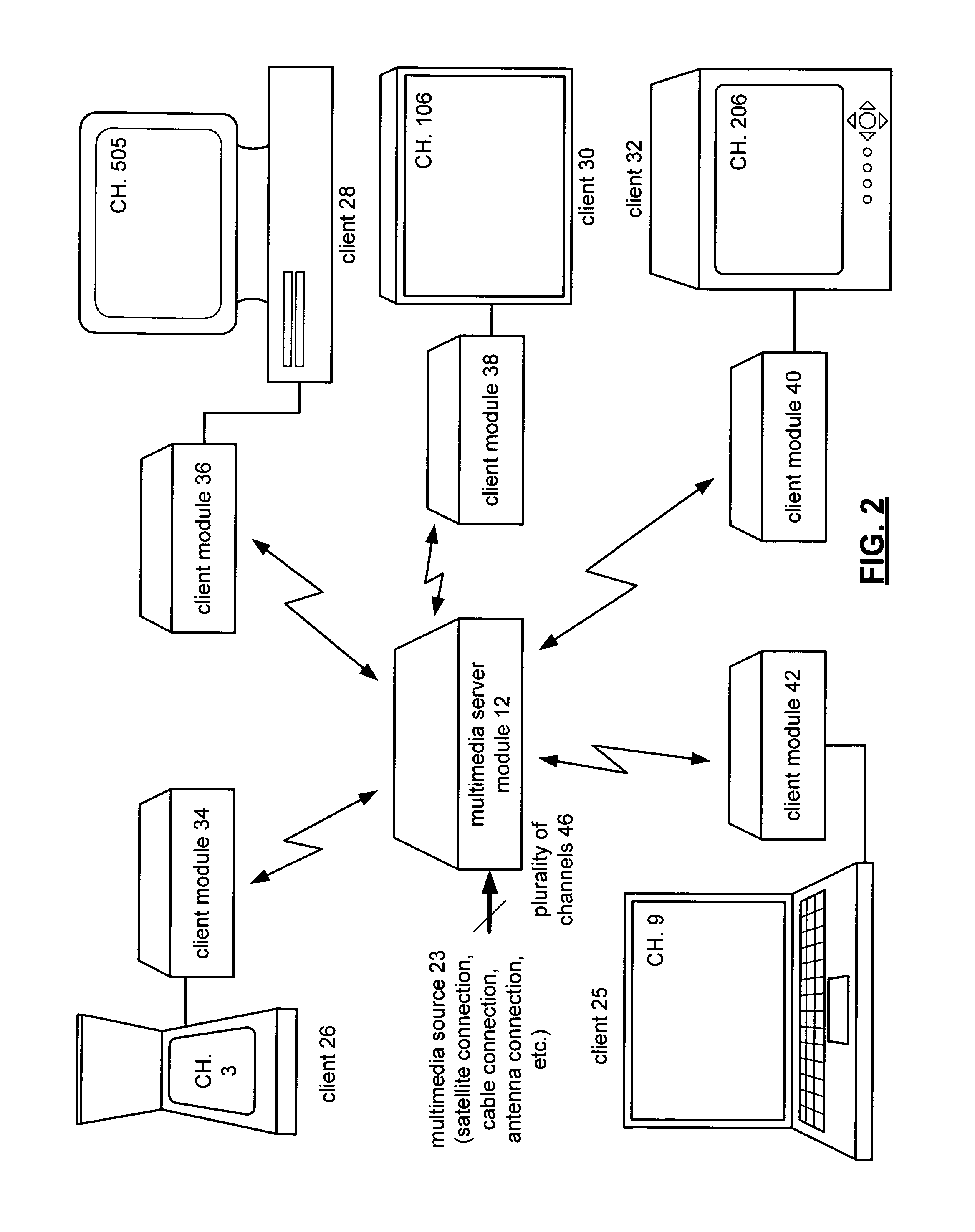
Multimedia client/server system with secure access data sharing and methods for use therewith
InactiveUS20080120657A1Television system detailsDigital data processing detailsSecure communicationTransceiver
A multimedia client / server system, prior to transmitting multimedia data over an RF communication link, shares secure access data between the client module. The secure access data is used to securing communication between the server transceiver module and the client transceiver module over the RF communication link.
Owner:VIXS INC A CORP
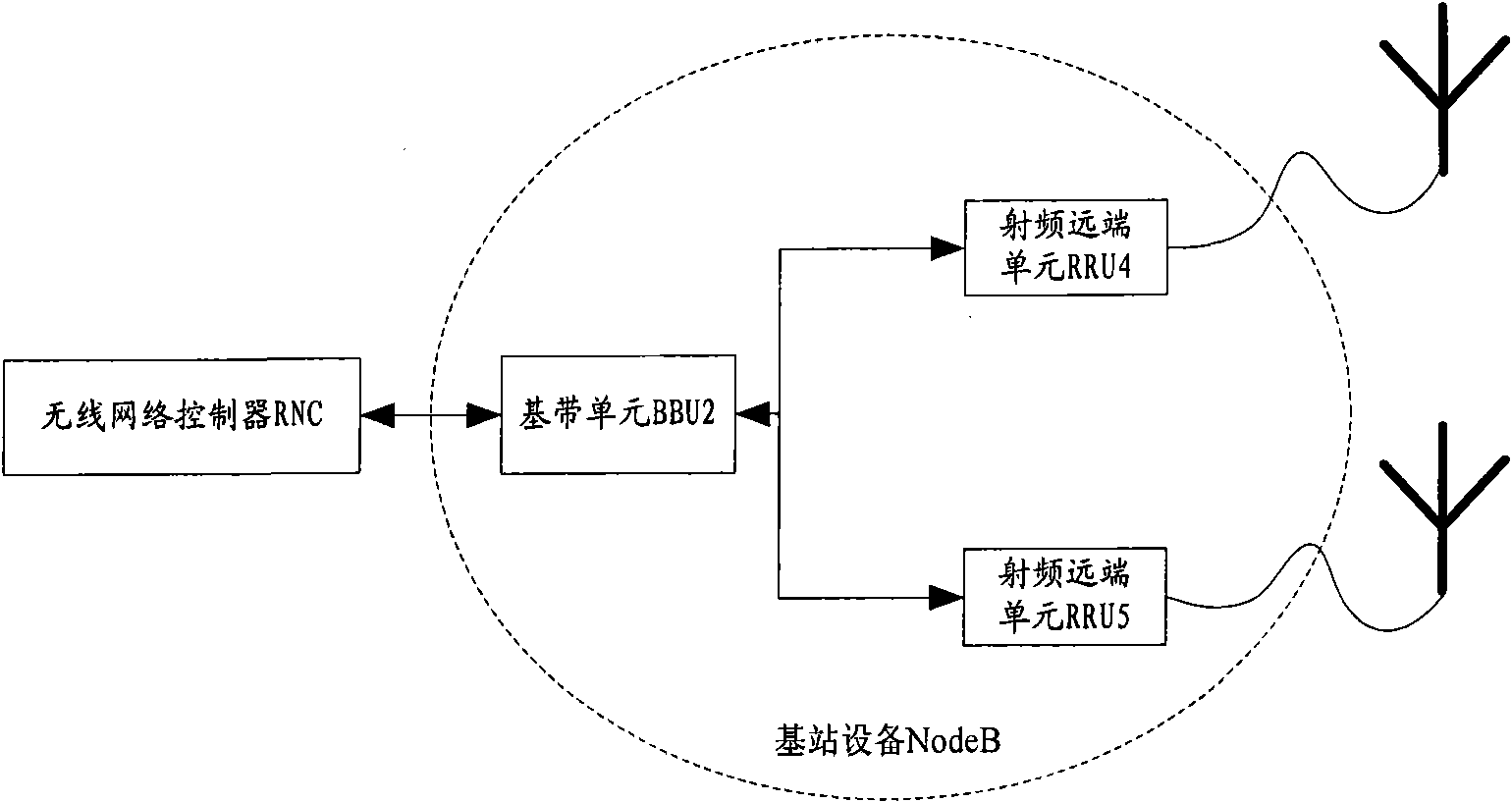
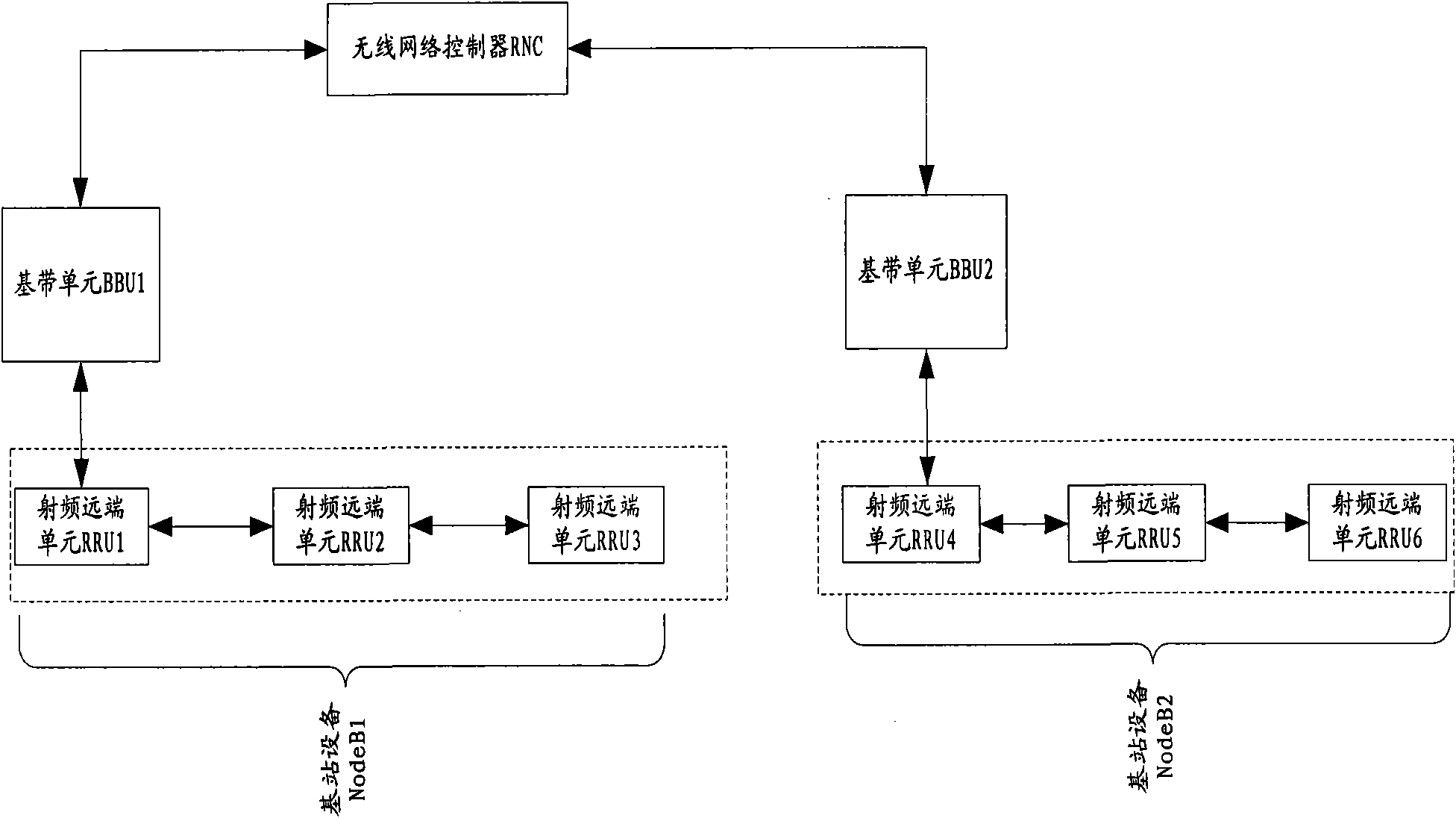
Distributed link system of base station and link protecting method thereof
ActiveCN102082586AGuaranteed to workIncrease profitTransmissionNetwork planningMobile communication systemsSystem protection
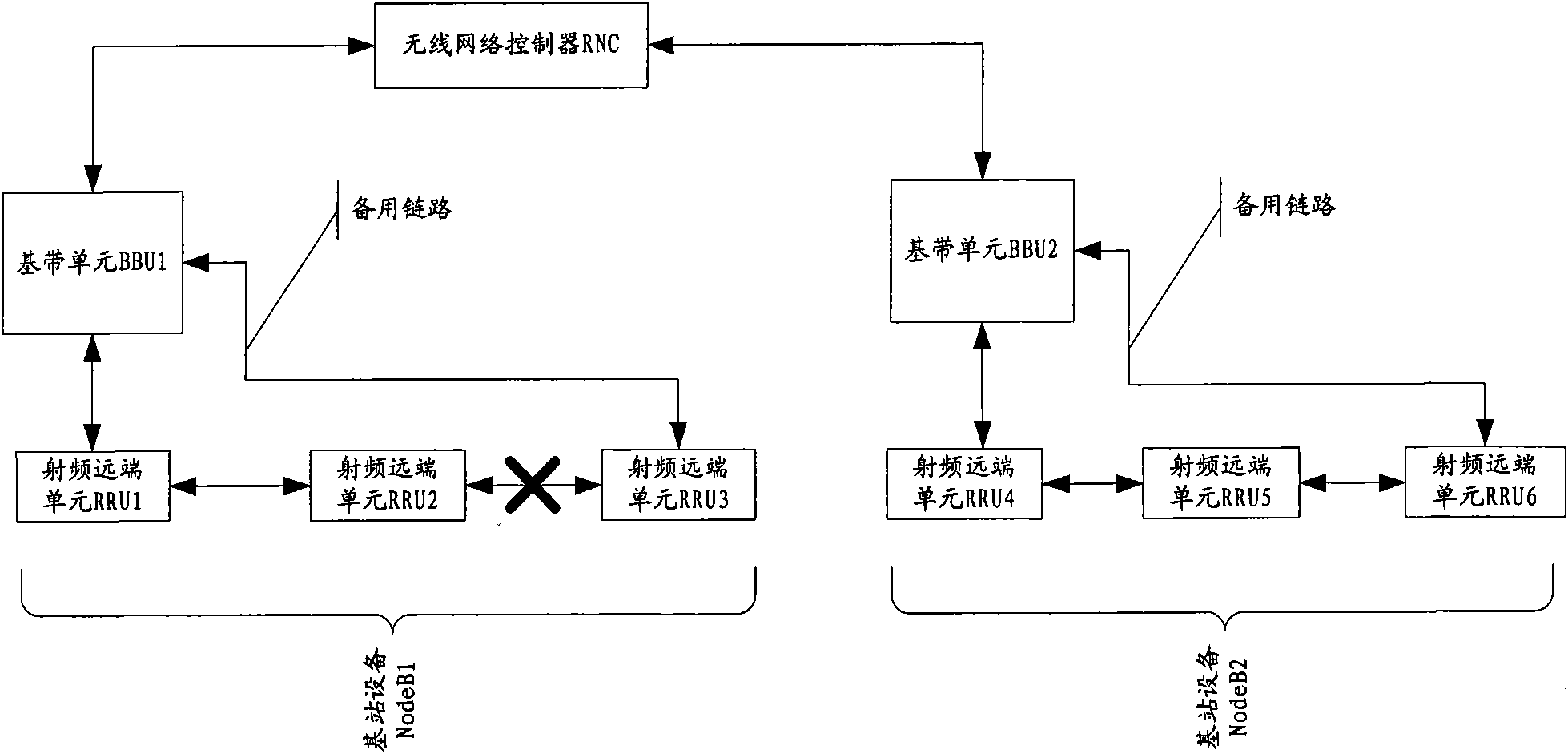
The embodiment of the invention provides a distributed link system of a base station, comprising a wireless network controller and a plurality of distributed base station devices controlled by the wireless network controller, wherein each distributed base station device comprises a base band unit connected to the wireless network controller and a plurality of serially-connected radio frequency far-end units connected to the base band units; and in the first distributed base station device and the second distributed base station device which are adjacent to each other, a last-stage radio frequency far-end unit in the serially-connected radio frequency far-end units connected to the distributed base station device is connected with the second distributed base station device by a standby link. According to the distributed link system of the base station, provided by the embodiment of the invention, the last-stage radio frequency far-end unit in the distributed base station device is linked to the adjacent distributed base station device by using the standby link, so that the utilization rate of the equipment of a mobile communication system is effectively improved while the link system is protected.
Owner:CHINA MOBILE GROUP DESIGN INST
Double PON ONU optical link protection switching device and protection method
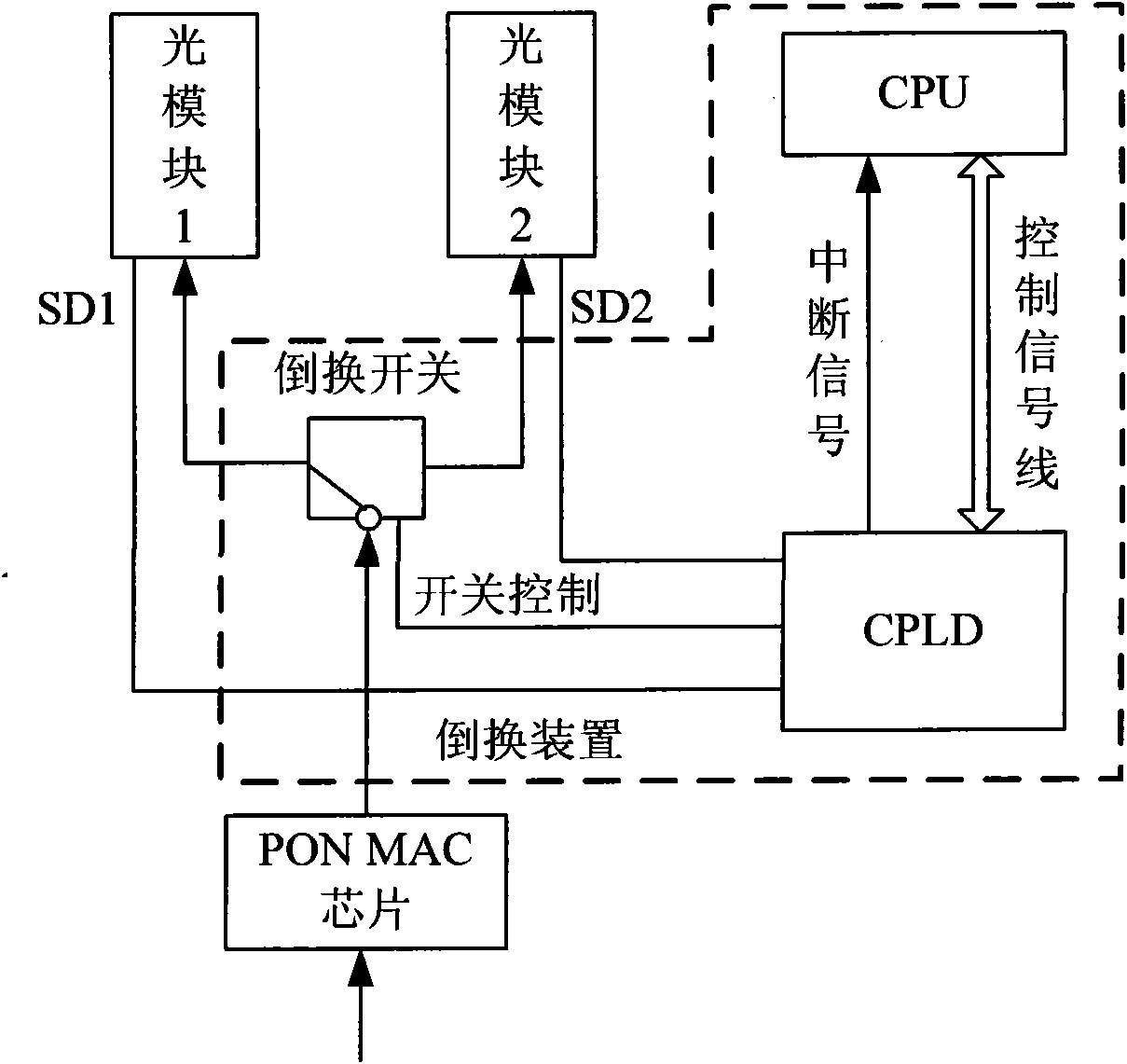
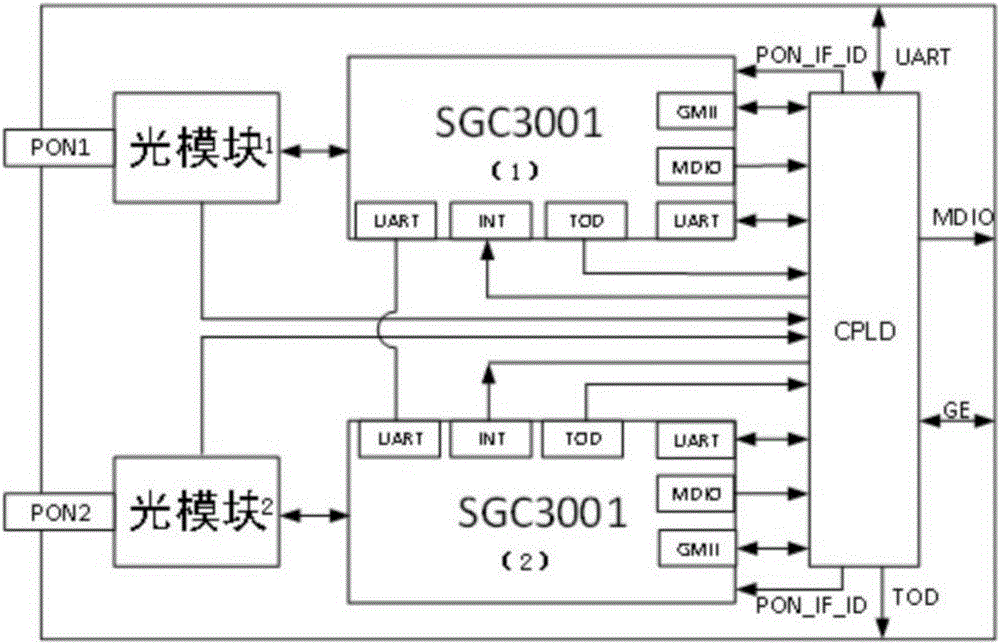
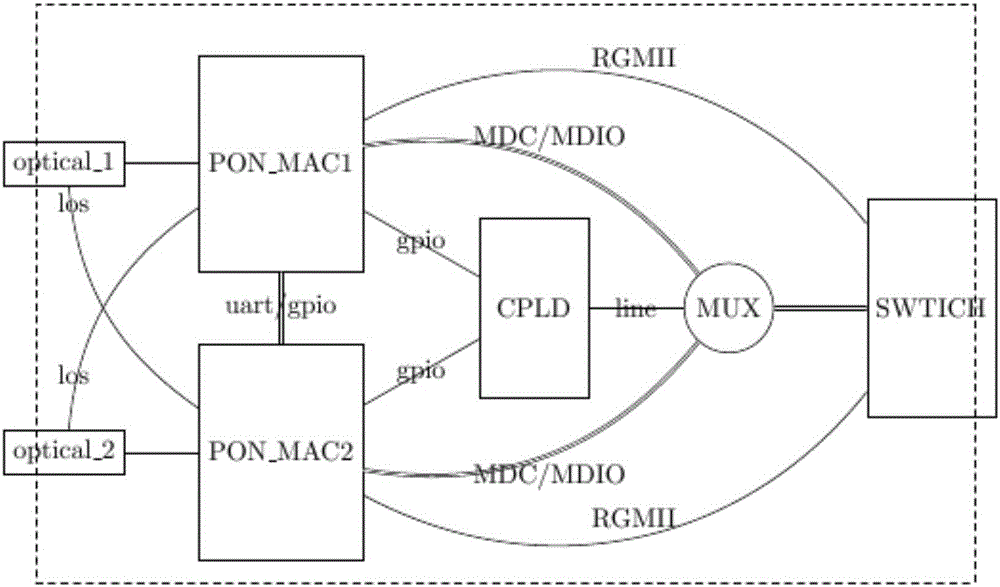
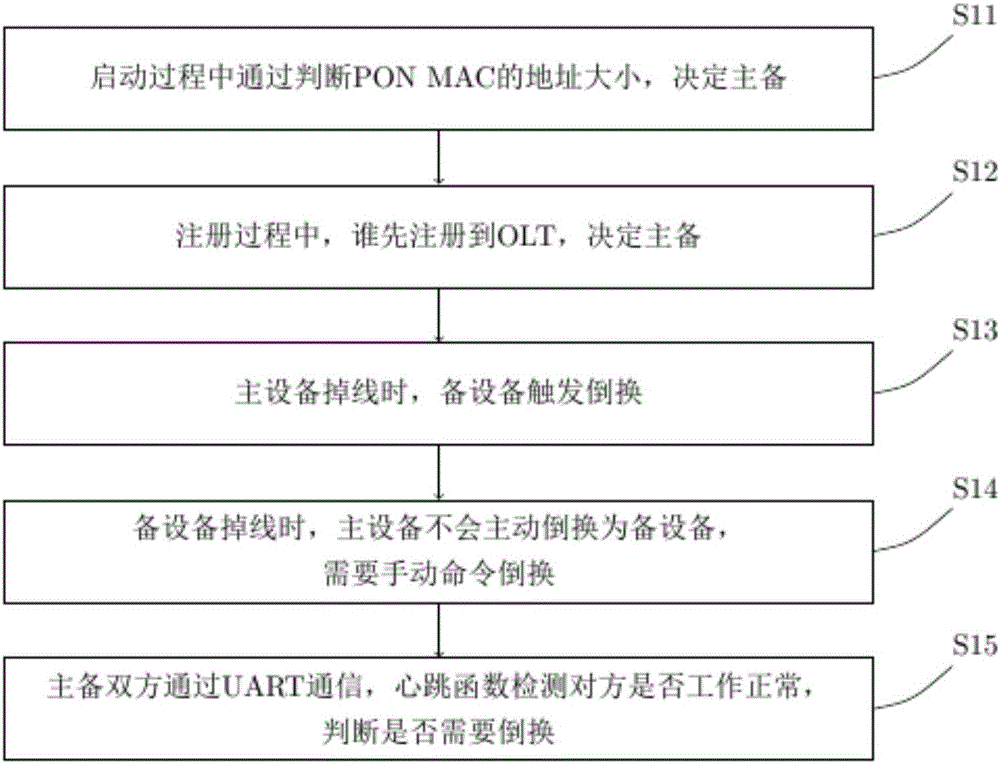
ActiveCN105743566ASmart switchingComplete switchingElectromagnetic transmissionOptical ModuleMultiplexer
The invention discloses a double PON ONU optical link protection switching device and protection method. The device comprises a first optical module, a second optical module, a first PON_MAC chip, a second PON_MAC chip, a complex programmable logic device CPLD, a multiplexer MUX and an exchange chip. The first optical module and the second optical module are connected with two different optical line terminals OLT to form a protection link hand in hand. According to the invention, an uplink interface RGMII of the exchange chip is in direct line connection with the PON_MAC chip interface, MDC / MDIO is in direct connection with the multiplexer, a control line is used to control the CPLD to complete a switching motion, and the problems in the prior art that the CPLD source is insufficient and the main-standby switching time is long are solved.
Owner:SHENZHEN NEW GREENNET TECH +1
Fiber optic link protection apparatus
Owner:LIGHTECH FIBEROPTICS
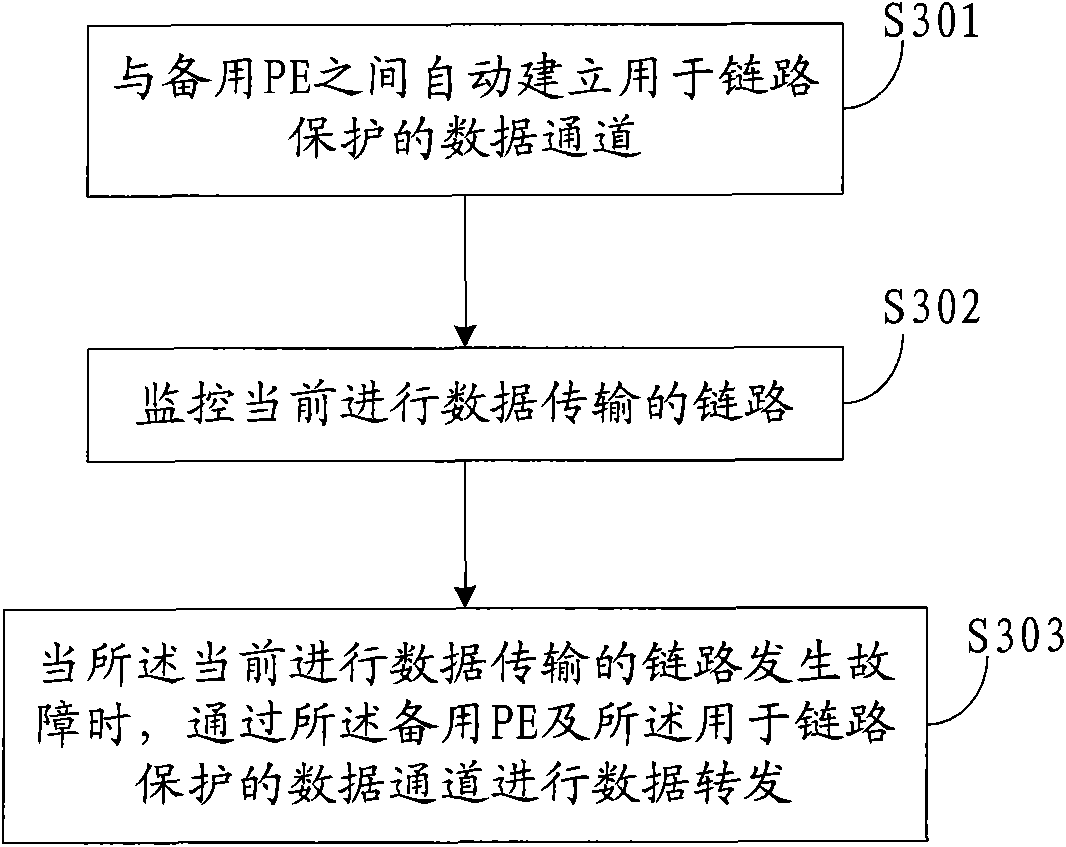
Data forwarding method, device and system
InactiveCN102142948AReduce latencyGuaranteed normal forwardingError preventionData switching networksPacket lossService provision
The invention discloses a data forwarding method, device and system which are used in a two-layer virtual private network system. The two-layer virtual private network system comprises provider edges (PEs) and a customer edge (CE), wherein the main PE and the backup PE form a cross-node redundancy group (RG). The method comprises the following steps: automatically establishing a data channel for link protection with the backup PE; monitoring a current data transmission link; and when the current data transmission link fails, performing data forwarding through the backup PE and the data channel for link protection. According to the invention, the link delay as well as the packet loss can be reduced.
Owner:HUAWEI TECH CO LTD
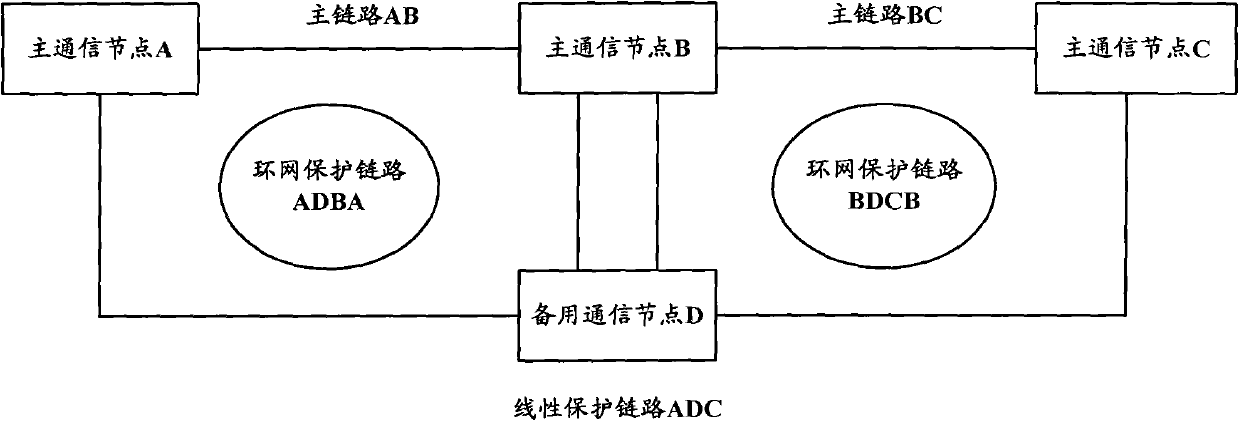
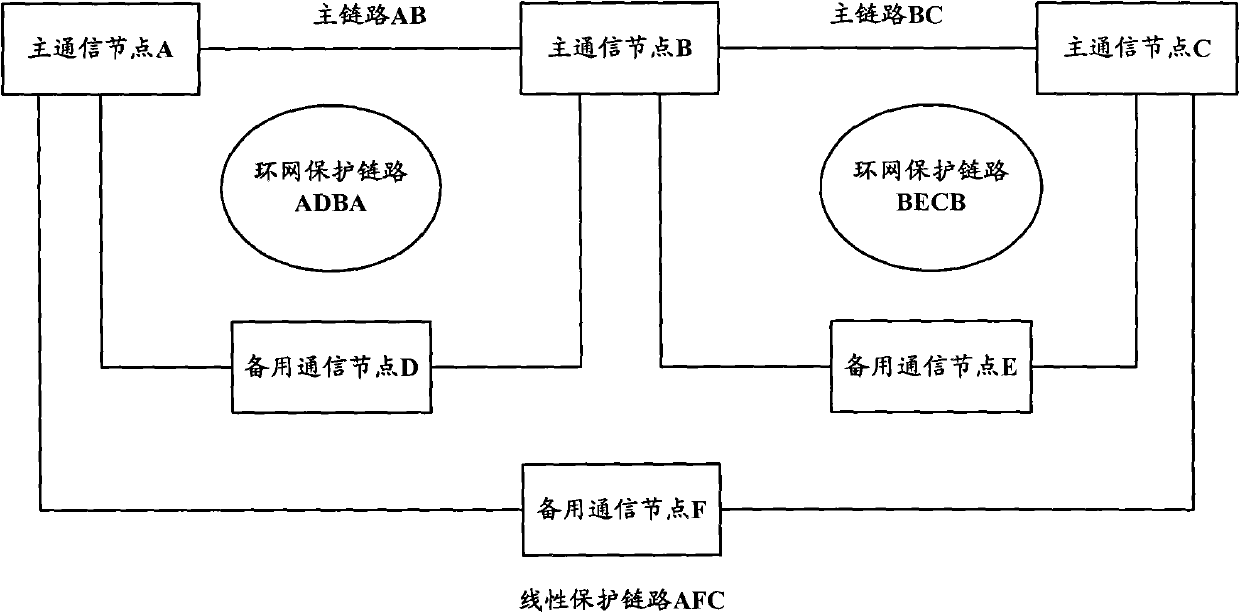
Transport multiprotocol label switching network (T-MPLS) system for and link protection method
InactiveCN101771610AImprove protectionData switching networksMultiprotocol Label SwitchingRing network
The invention provides a transport multiprotocol label switching (T-MPLS) network system and a link protection method. The network system comprises a main link, a ring network protection link, a linear protection link, a first switching module and a second switching module, wherein the main link comprises at least three main communication nodes; the ring network protection link is located between two adjacent main communication nodes; the linear protection link is located between the head main communication node and the tail main communication node of the main link; the first switching module is used for transmitting data messages through the ring network protection link between the two adjacent main communication nodes when the main link between the two adjacent main communication nodes fails; and the second switching module is used for transmitting the data messages through the linear protection link when the middle main communication node of the main link fails. The invention can provide more effective and reliable link protection for the T-MPLS network system.
Owner:ZTE CORP
Link protection method and equipment
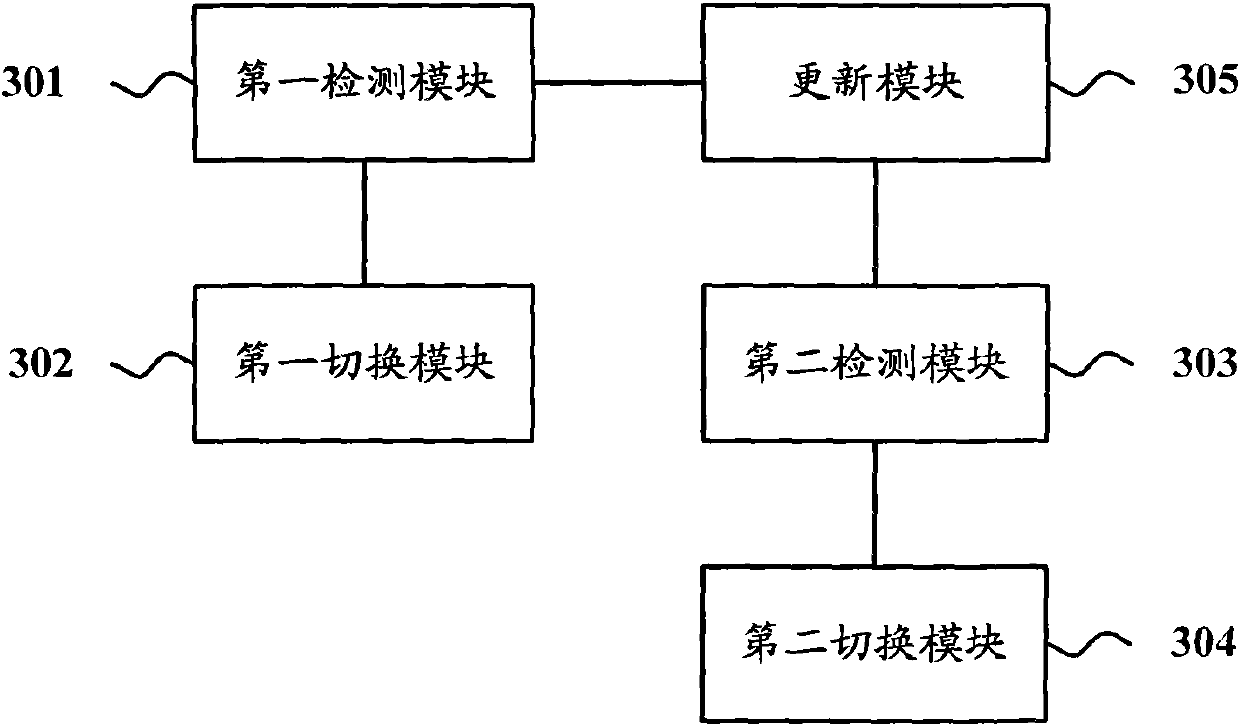
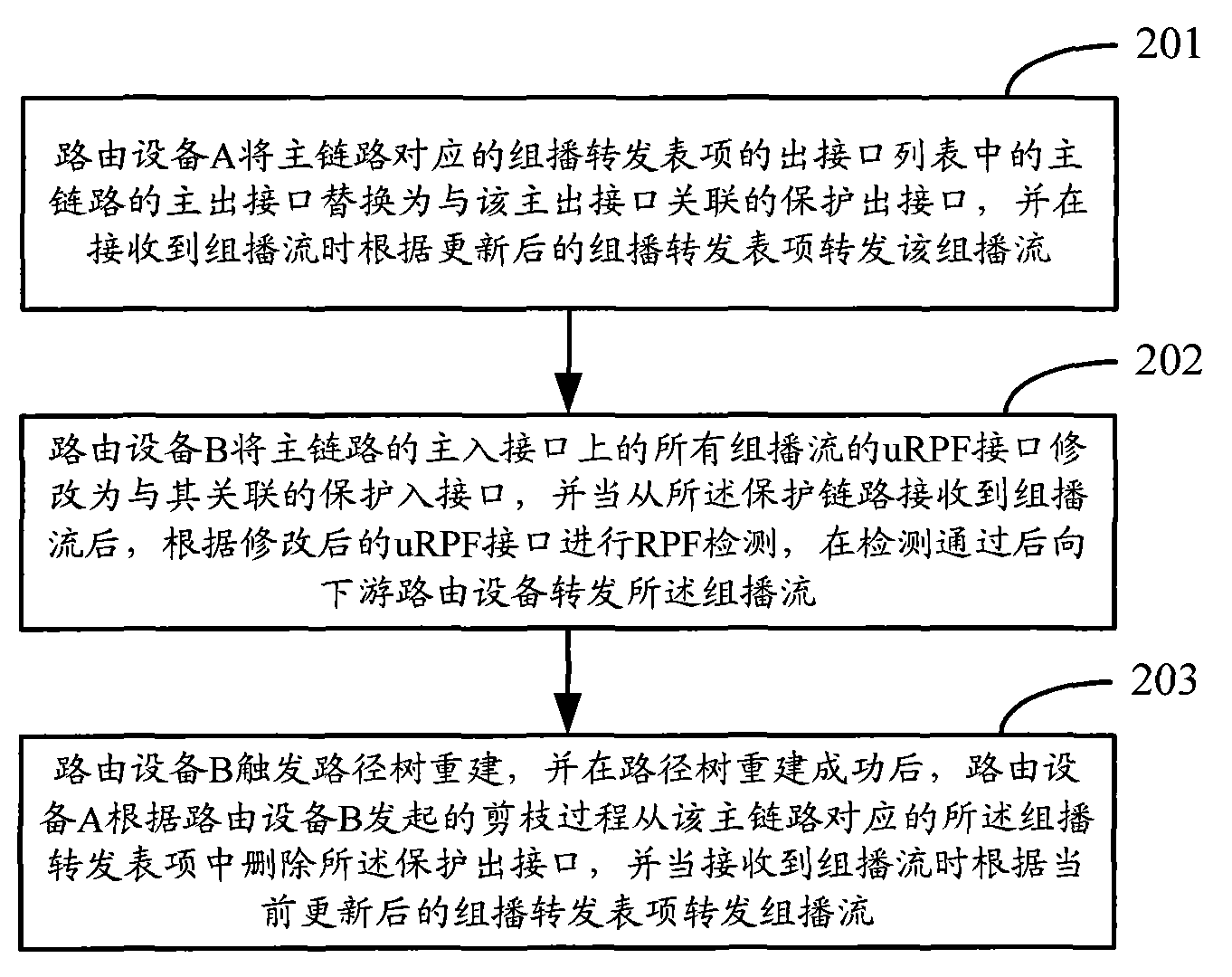
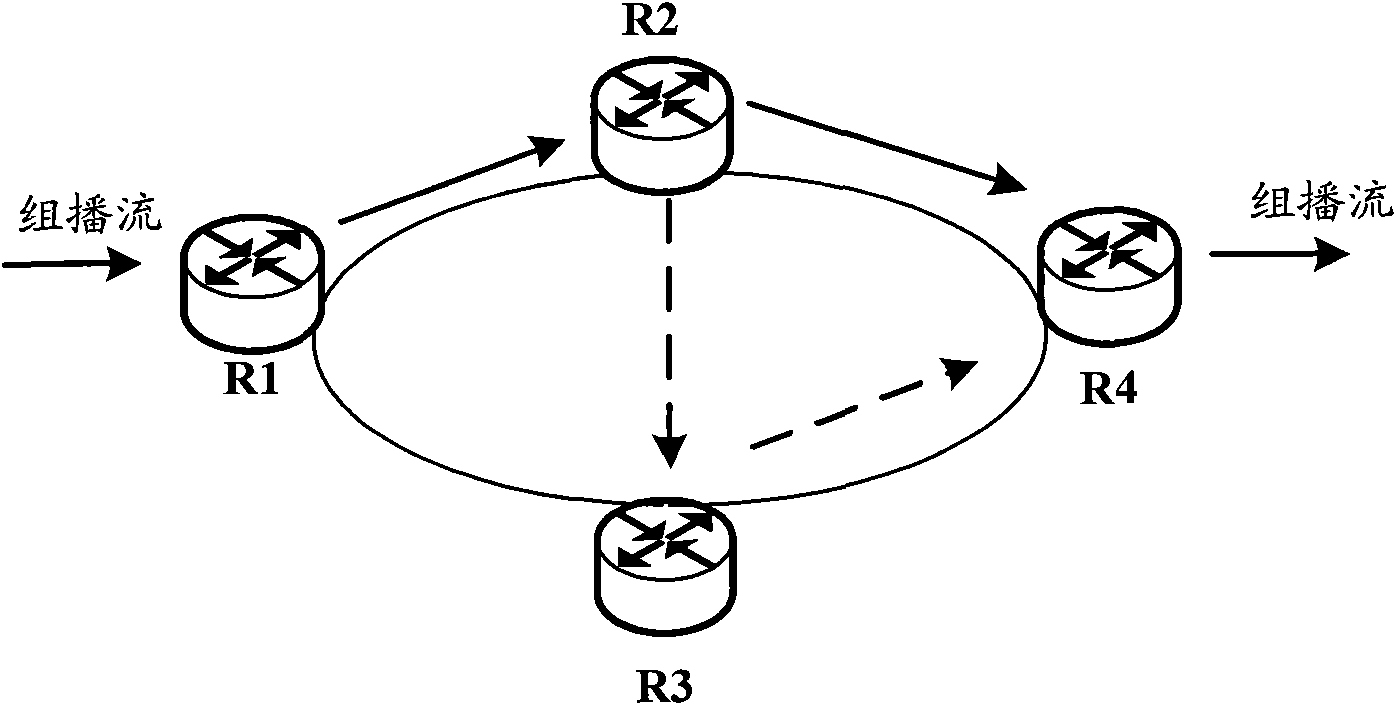
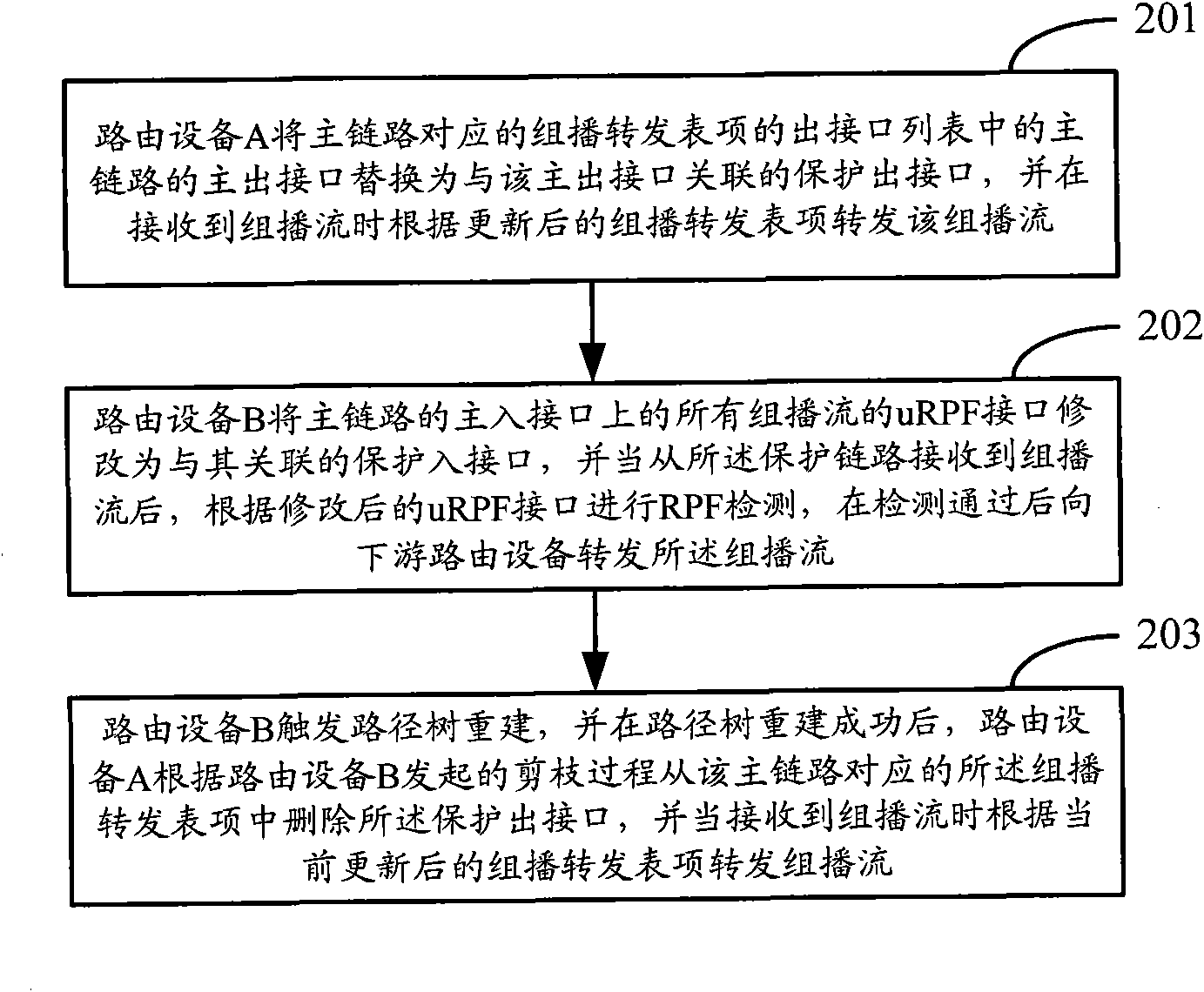
ActiveCN102111342AGuaranteed continuityGuaranteed reliabilityData switching networksReverse path forwardingPruning
The invention discloses a link protection method and ink protection equipment for solving the problem that the multicast stream cannot be normally forwarded all the time before reconstruction of a forwarding tree is completed in the prior art. In the method, a main link and a corresponding protection link are configured between first routing equipment and second routing equipment on the downstream of the first routing equipment; when the main link fails, the first routing equipment changes a main output interface of the main link in a multicast forwarding table entry output interface list corresponding to the main link into an associated protection output interface, and forwards the multicast stream according to the updated multicast forwarding table entry; the second routing equipment modifies unicast reverse path forwarding (uRPF) interfaces of all multicast stream on a main input interface of the main link into associated protection input interfaces; and the reconstruction of a path tree succeeds, the first routing equipment forwards the multicast stream according to the multicast forwarding table entry updated in the path tree reconstruction process after receiving the multicast stream, and cancels the protection output interface in the multicast forwarding table entry according to the pruning process initiated by the second routing equipment.
Owner:NEW H3C TECH CO LTD
Cross-equipment link protection method and system
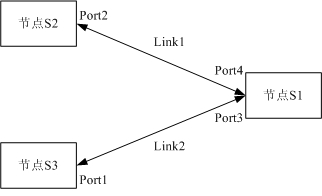
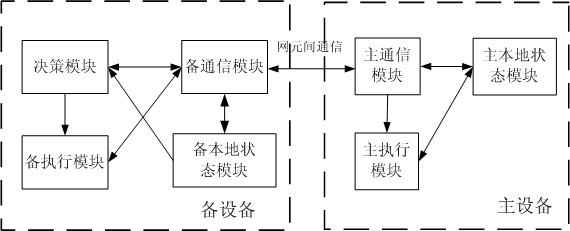
InactiveCN102035680AAchieve protectionWavelength-division multiplex systemsData switching networksMultiplexingEngineering
The invention discloses a cross-equipment link protection method and a cross-equipment link protection system. The system comprises a protective group formed by master equipment in which an operating link is positioned and spare equipment in which a protective link is positioned, wherein the master equipment is used for sending switching decision information to the spare equipment; and the spare equipment is used for making decision according to the received switching decision information and sending synchronous notification to the master equipment according to a switch result of the decision. By the method and the system, networking of three network elements and four network elements can be subjected to the protection of a multiplexing section of cross equipment, so that the protective link protects the operating link.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com