Source code protection method and device
A source code and code technology, applied in the network field, can solve problems such as weak protection, and achieve the effect of reducing success rate and readability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
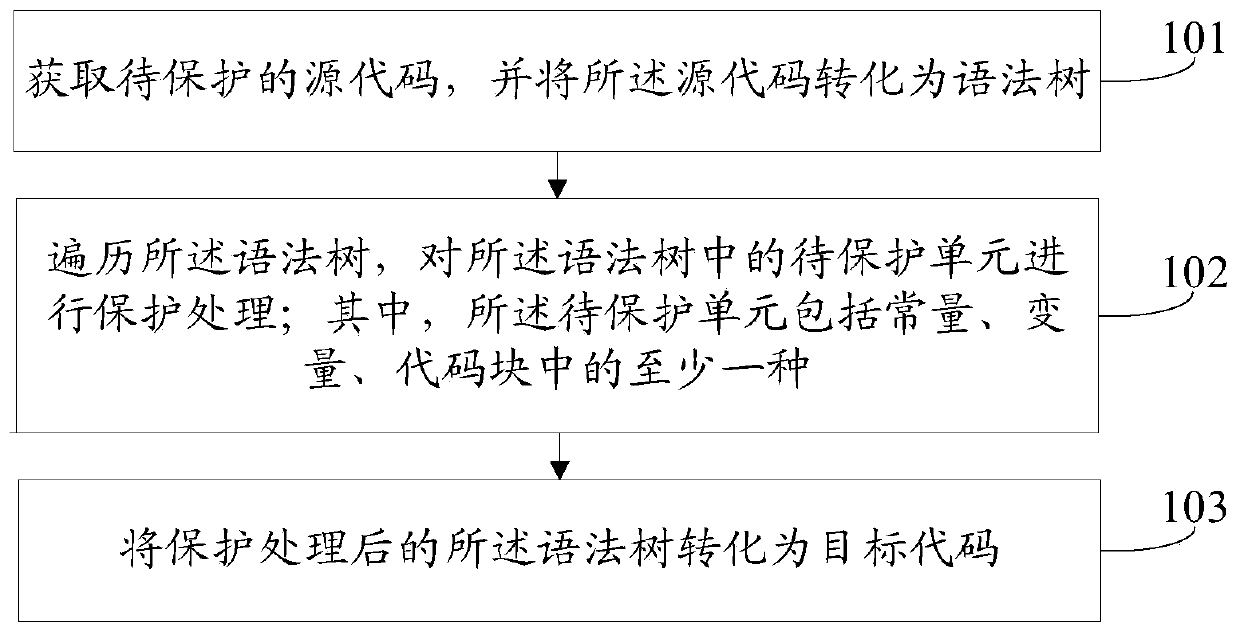
[0027] figure 1 It is a flow chart of steps of a source code protection method provided by an embodiment of the present invention, such as figure 1 As shown, the method may include:
[0028] Step 101, obtain the source code to be protected, and convert the source code into a syntax tree.
[0029] The syntax tree, also known as the abstract syntax tree, is an abstract representation of the grammatical structure of the source code. It expresses the grammatical structure of the programming language in the form of a tree structure, but the syntax here does not represent every detail that appears in the real grammar. , generally speaking, "syntax highlighting", "keyword matching", "scope judgment", and "code compression" can be performed through the syntax tree. In addition to deconstructing syntax, it is also necessary to provide various functions to traverse and Modify the syntax tree.
[0030] In the embodiment of the present invention, it is necessary to obtain the source co...
Embodiment 2
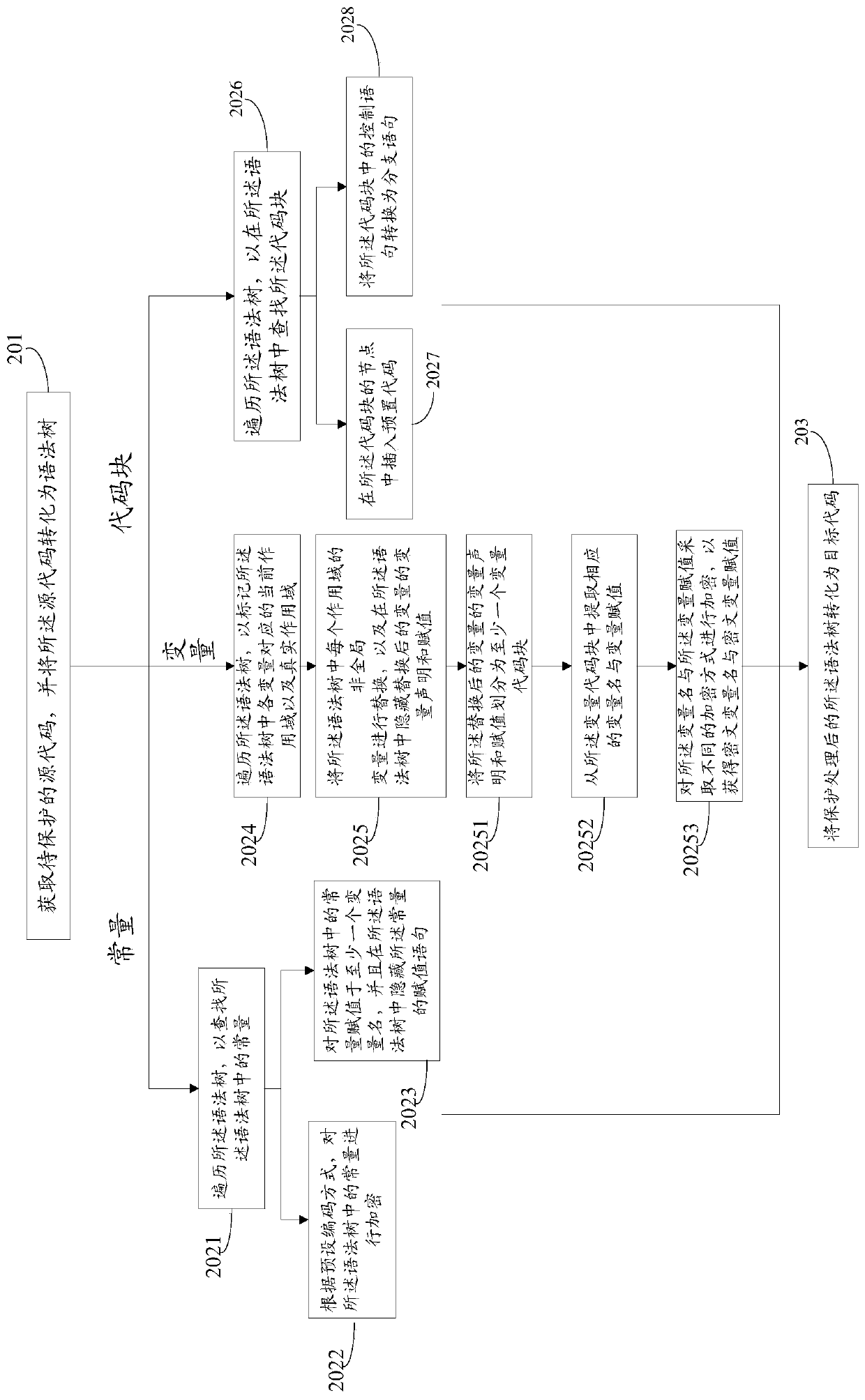
[0039] figure 2 is a flow chart of steps of another source code protection method provided by an embodiment of the present invention, such as figure 2 As shown, the method may include:
[0040] Step 201, obtain the source code to be protected, and convert the source code into a syntax tree.
[0041]In the embodiment of the present invention, the source code to be protected can be obtained by the staff themselves, or the source code that has been launched in the platform can be obtained, and the method of obtaining the source code is not limited in the present invention.
[0042] Step 202, traverse the syntax tree, and perform protection processing on the units to be protected in the syntax tree; wherein, the units to be protected include at least one of constants, variables, and code blocks.
[0043] In the embodiment of the present invention, in the process of loop traversing the syntax tree, the execution logic of the code can be marked first, such as marking the variabl...
Embodiment 3
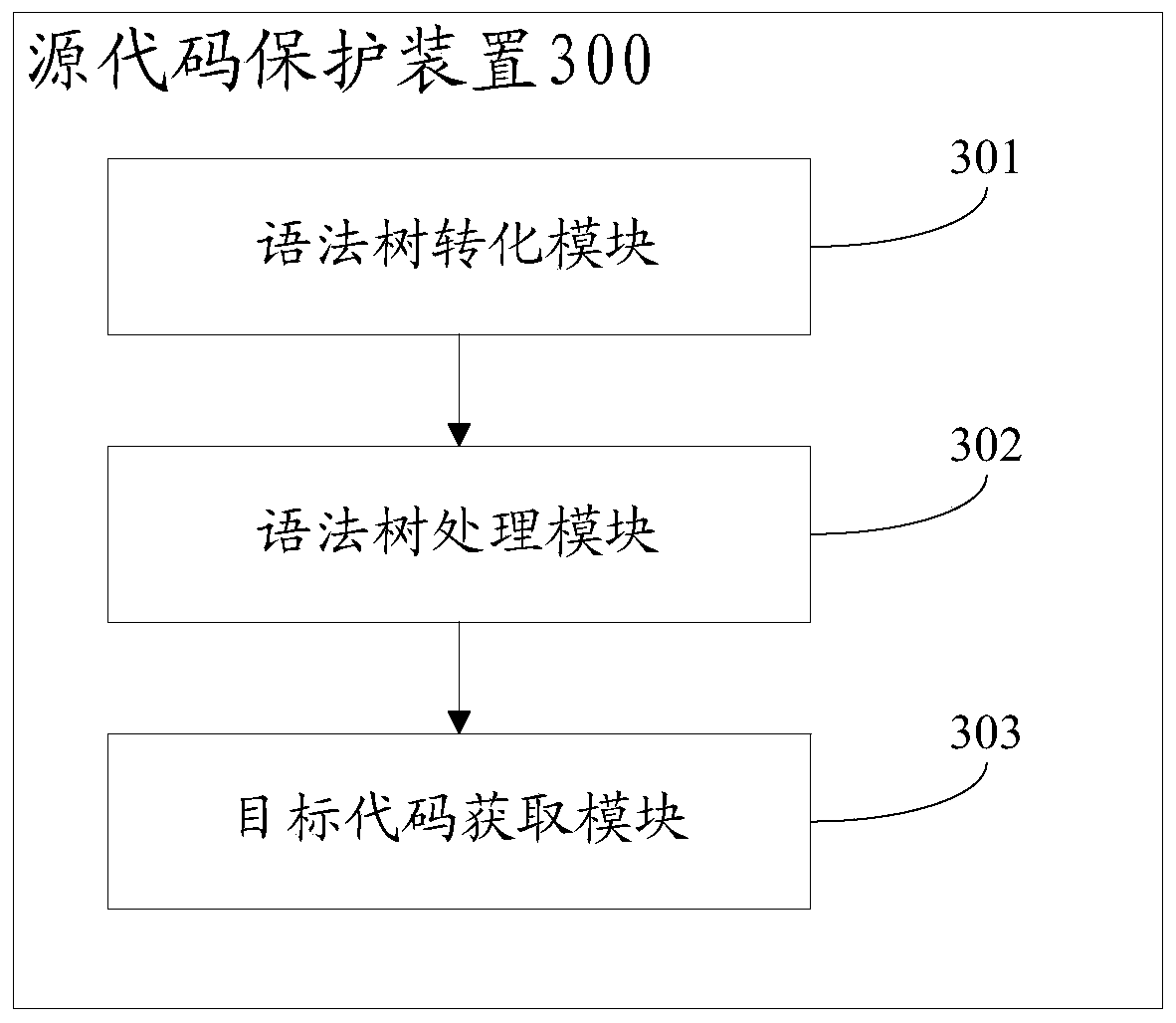
[0081] image 3 is a block diagram of a source code protection device provided by an embodiment of the present invention, such as image 3 As shown, the device may include:
[0082] The syntax tree converting module 301 is configured to obtain the source code to be protected, and convert the source code into a syntax tree.
[0083] The syntax tree processing module 302 is configured to traverse the syntax tree and perform protection processing on the units to be protected in the syntax tree; wherein the units to be protected include at least one of constants, variables, and code blocks.
[0084] An object code acquisition module 303, configured to convert the protected syntax tree into an object code.
[0085] Optionally, the unit to be protected is a constant, and the syntax tree processing module 302 includes:
[0086] The constant acquisition submodule is used for traversing the syntax tree to find the constant in the syntax tree.
[0087] The constant encryption submod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com