Non-fullness complete-non-correlation double-tree traversal protection method in mesh network
A non-correlated, tree traversal technology, applied in the field of communication networks, can solve the problems of short failover time, consumption of computing time, waste of resources, etc., and achieve the effects of clear transmission purpose, reduced link congestion, and high transmission efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] In order to make the purpose, technical solution, and advantages of the present invention clearer, the present invention will be further elaborated below in conjunction with the accompanying drawings and specific implementation examples.
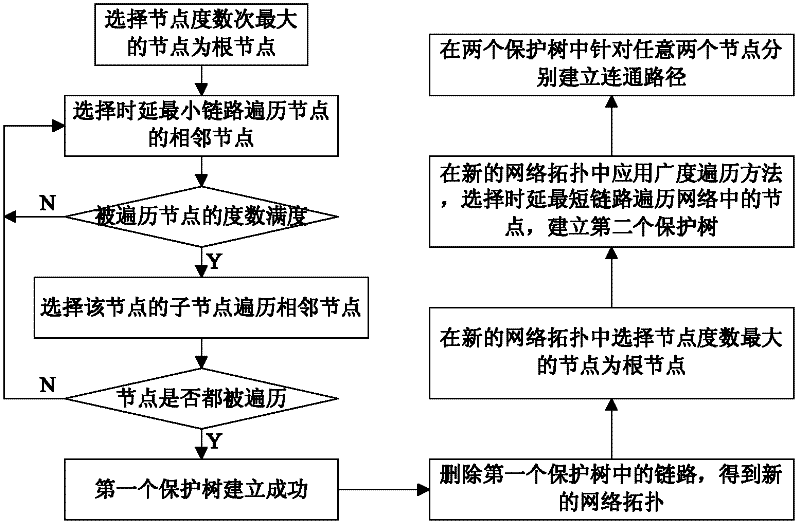
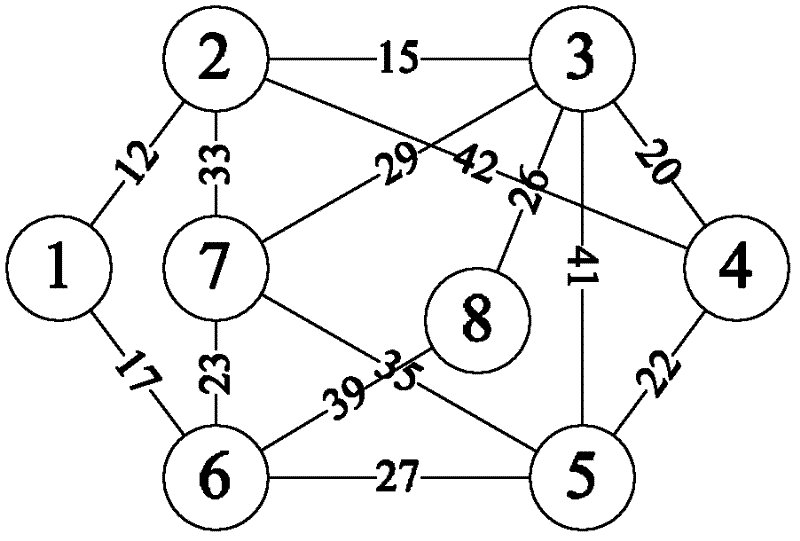
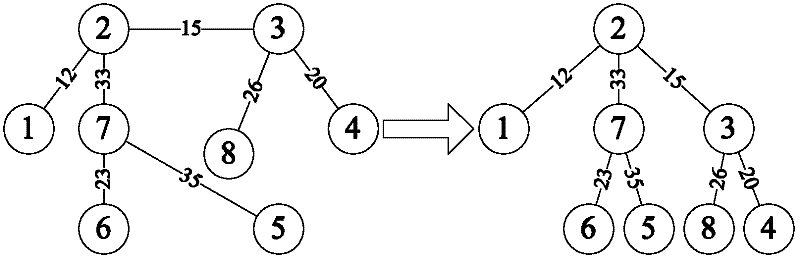
[0044] figure 1 To establish a flowchart for the "non-full degree and completely irrelevant" protection tree, the present invention first needs to establish two protection trees satisfying the "non-full degree and completely non-correlation" condition, and the algorithm for establishing the protection tree is as follows:
[0045] Step 1: Select the node with the largest node degree as the root node;
[0046] Step 2: Select the adjacent node of the minimum link traversal node with delay;
[0047] Step 3: Whether the degree of the traversed node is full;
[0048] Step 4: If the traversed node is full, the link cannot be selected, and the child node of the traversed node is selected to traverse the adjacent nodes; if the traversed node...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com