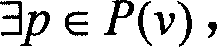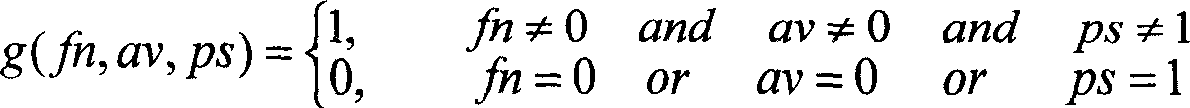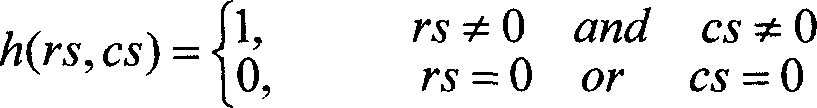Patents
Literature
37 results about "Predicate logic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In mathematical logic, predicate logic is the generic term for symbolic formal systems like first-order logic, second-order logic, many-sorted logic, or infinitary logic. This formal system is distinguished from other systems in that its formulae contain variables which can be quantified. Two common quantifiers are the existential ∃ and universal ∀ quantifiers. The variables could be elements in the universe under discussion, or perhaps relations or functions over that universe. For instance, an existential quantifier over a function symbol would be interpreted as modifier "there is a function". The foundations of predicate logic were developed independently by Gottlob Frege and Charles Sanders Peirce. In informal usage, the term "predicate logic" occasionally refers to first-order logic. Some authors consider the predicate calculus to be an axiomatized form of predicate logic, and the predicate logic to be derived from an informal, more intuitive development. Predicate logics also include logics mixing modal operators and quantifiers. See Modal logic, Saul Kripke, Barcan Marcus formulae, A. N. Prior, and Nicholas Rescher.
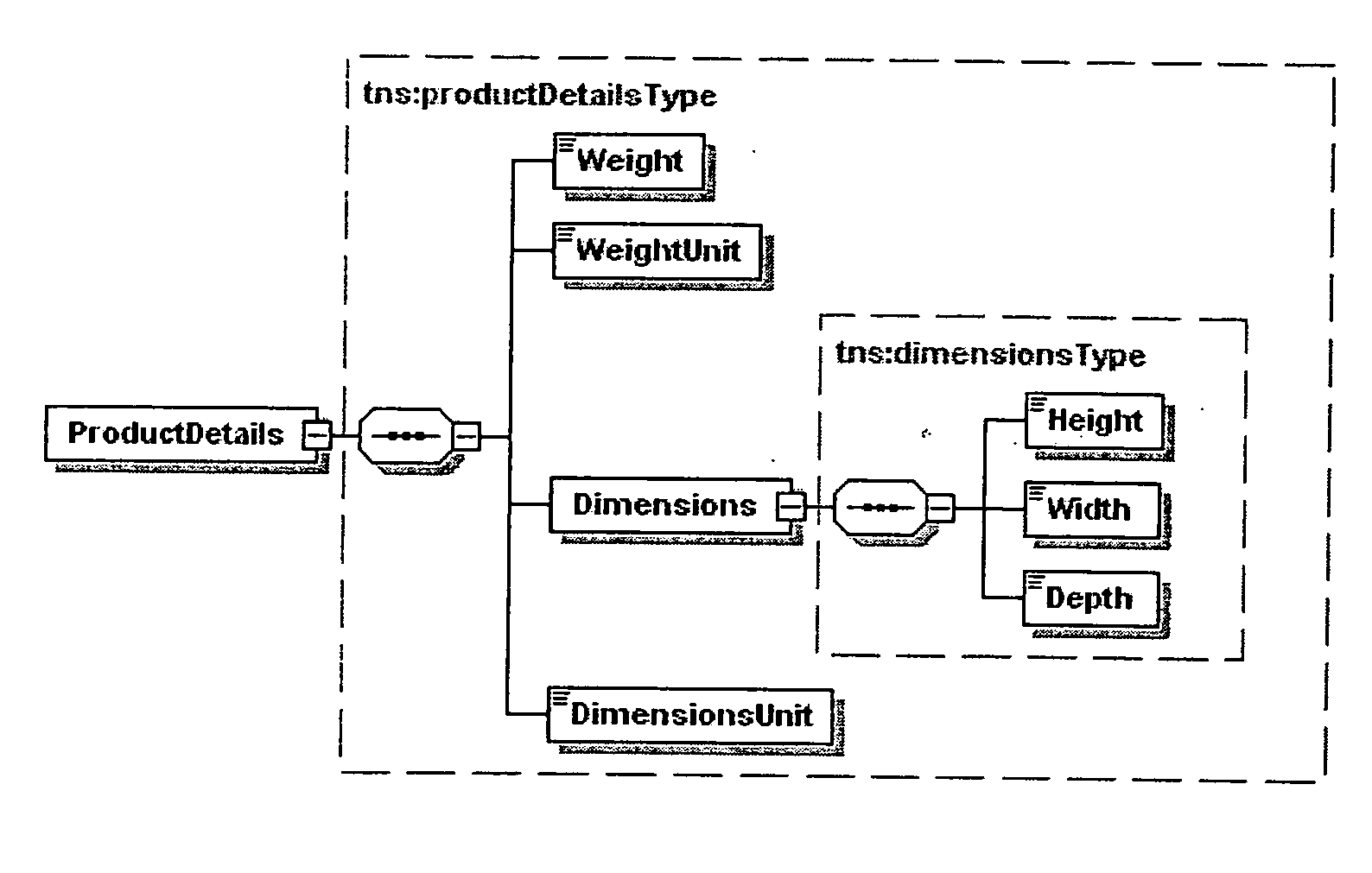
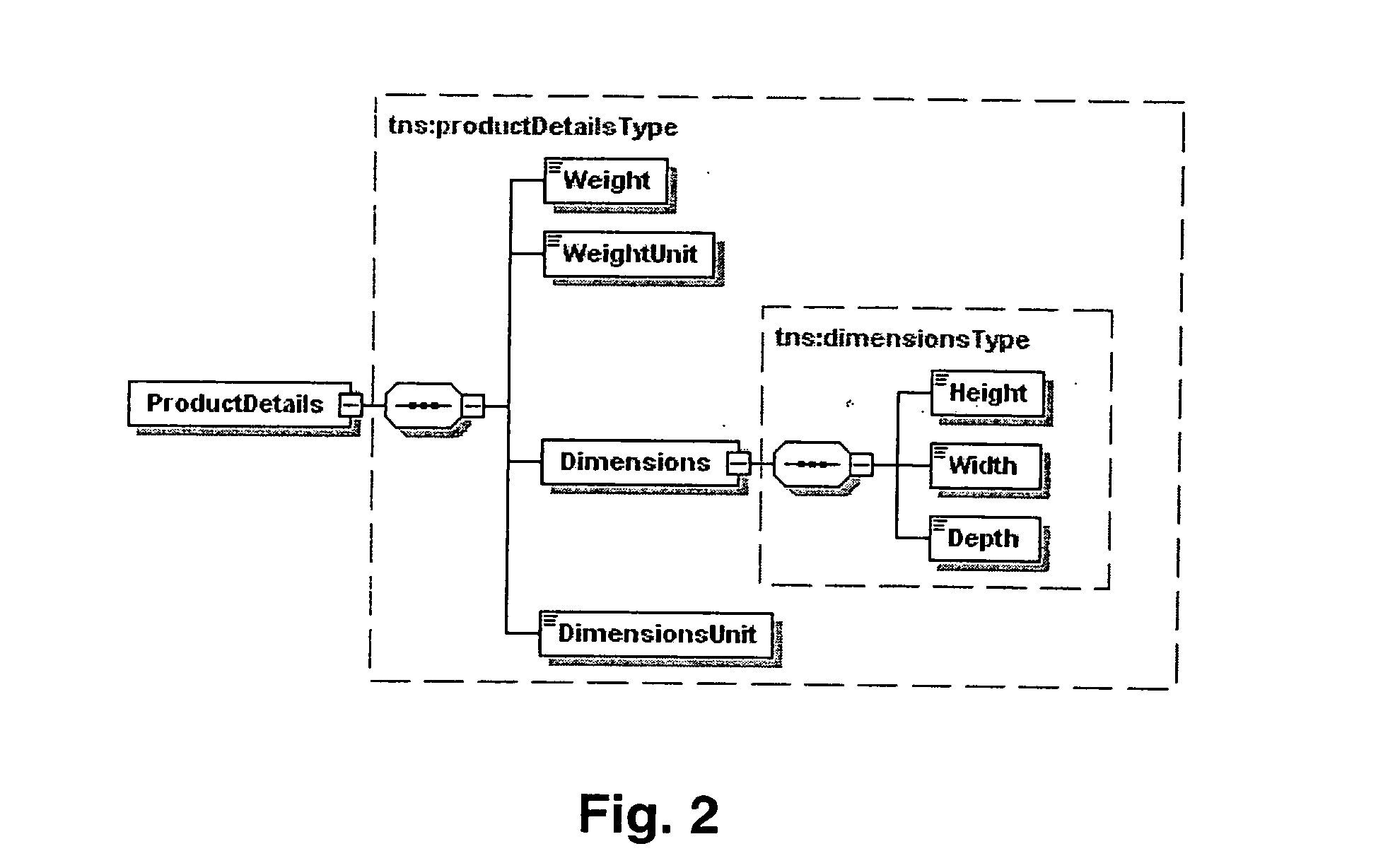
Enterprise information integration platform
InactiveUS20060167856A1Easy to integrateImprove usabilityData processing applicationsDatabase management systemsWeb serviceData source
A system for enterprise information integration is described. The system is based on different layers: the data sources, source ontologies corresponding to the data schema of the data sources, an integration ontology integrating the different source ontologies, a level of query input, preferably in the form of a web service. Between the levels, mapping rules are used. These mapping rules and the entire system are based on predicate logic. The queries are answered with the help of the rules using inference based on predicate logic.
Owner:SEMEO SERVICES GMBH +1
Predicate Logic based Image Grammars for Complex Visual Pattern Recognition
InactiveUS20100278420A1Quick and efficient system setupImprove performanceCharacter and pattern recognitionChaos modelsNerve networkAlgorithm
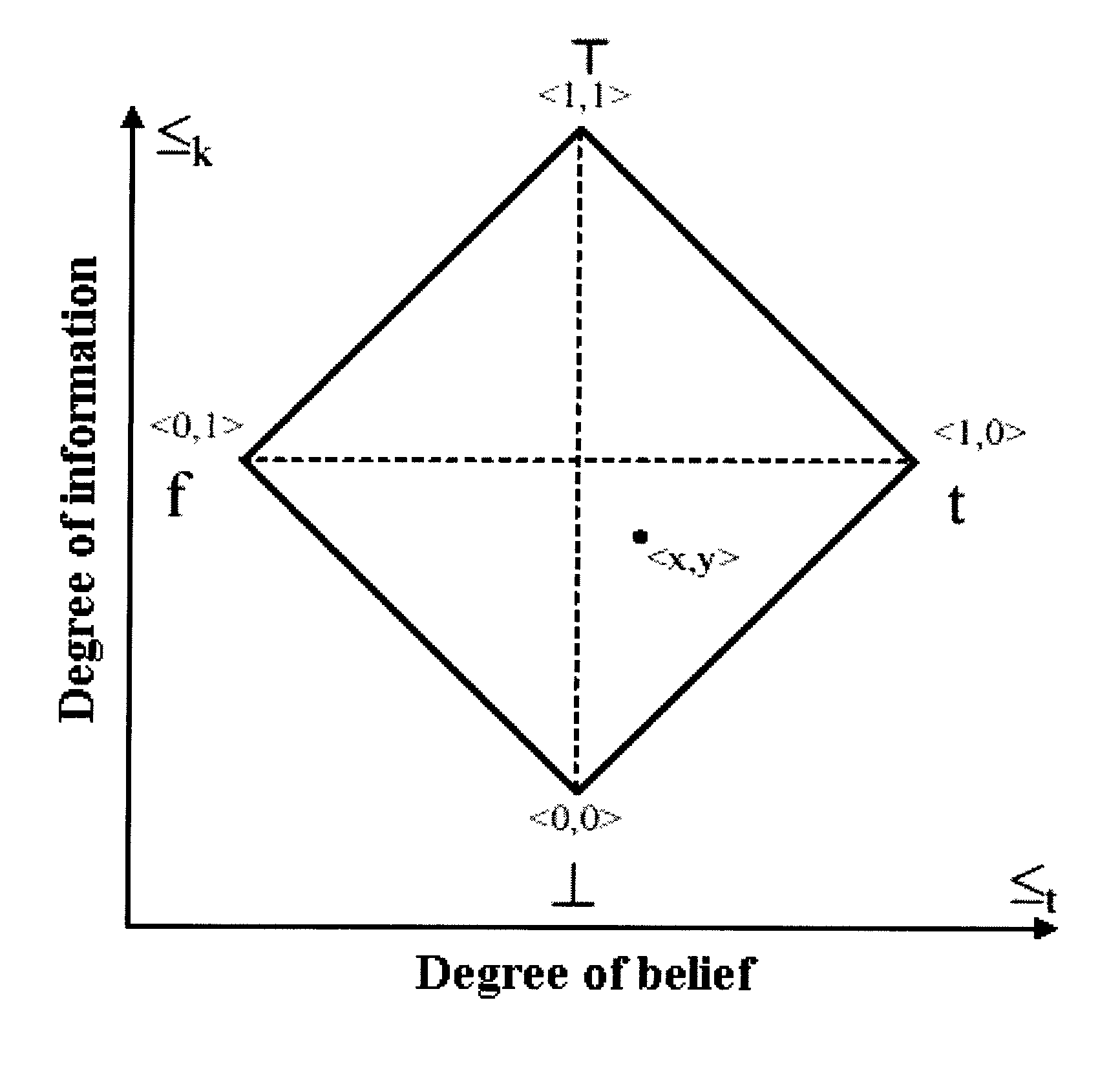
First order predicate logics are provided, extended with a bilattice based uncertainty handling formalism, as a means of formally encoding pattern grmmars, to parse a set of image features, and detect the presence of different patterns of interest implemented on a processor. Information from different sources and uncertainties from detections, are integrated within the bilattice framework. Automated logical rule weight learning in the computer vision domain applies a rule weight optimization method which casts the instantiated inference tree as a knowledge-based neural network, to converge upon a set of rule weights that give optimal performance within the bilattice framework. Applications are in (a) detecting the presence of humans under partial occlusions and (b) detecting large complex man made structures in satellite imagery (c) detection of spatio-temporal human and vehicular activities in video and (c) parsing of Graphical User Interfaces.
Owner:SIEMENS CORP
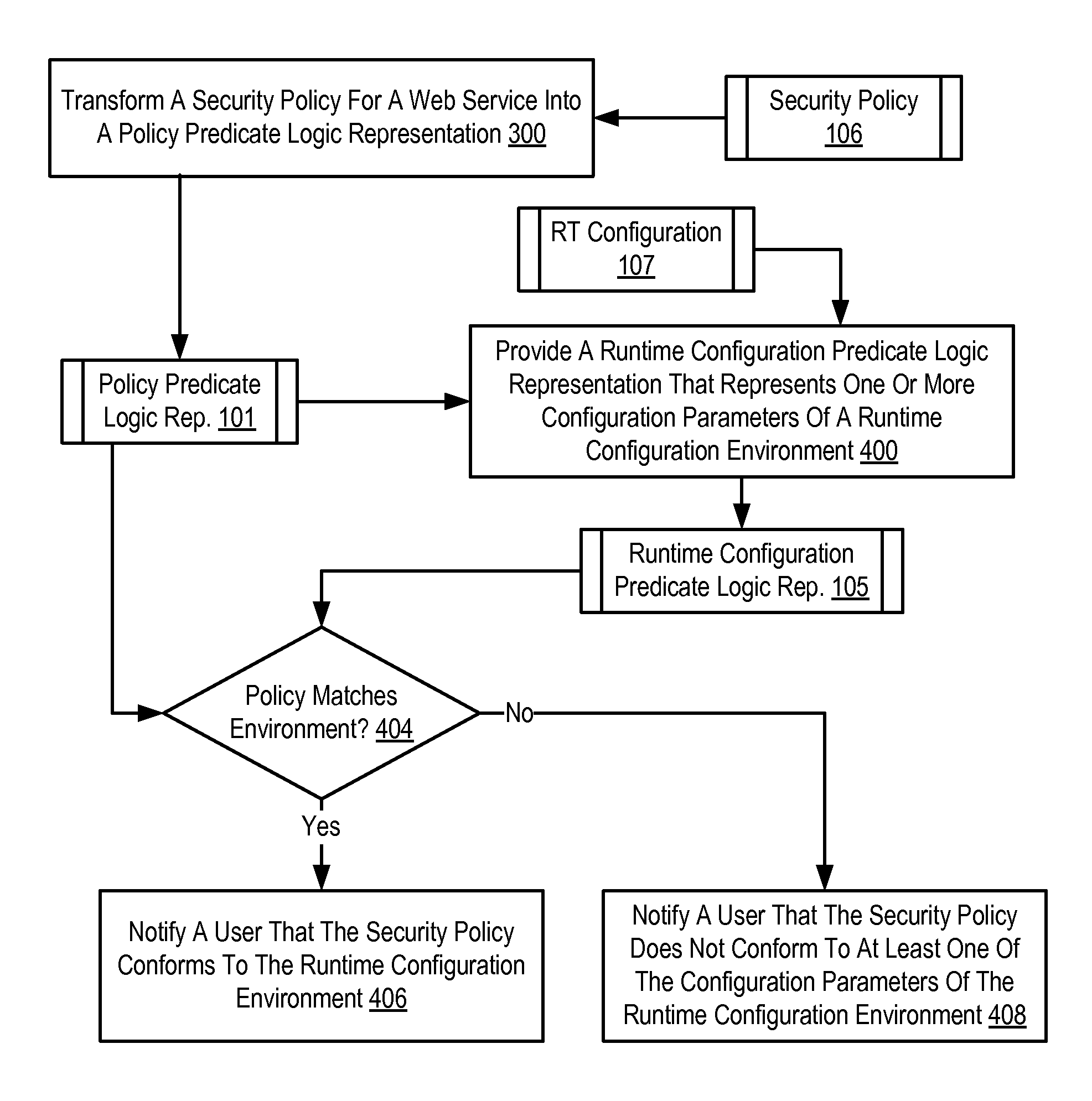
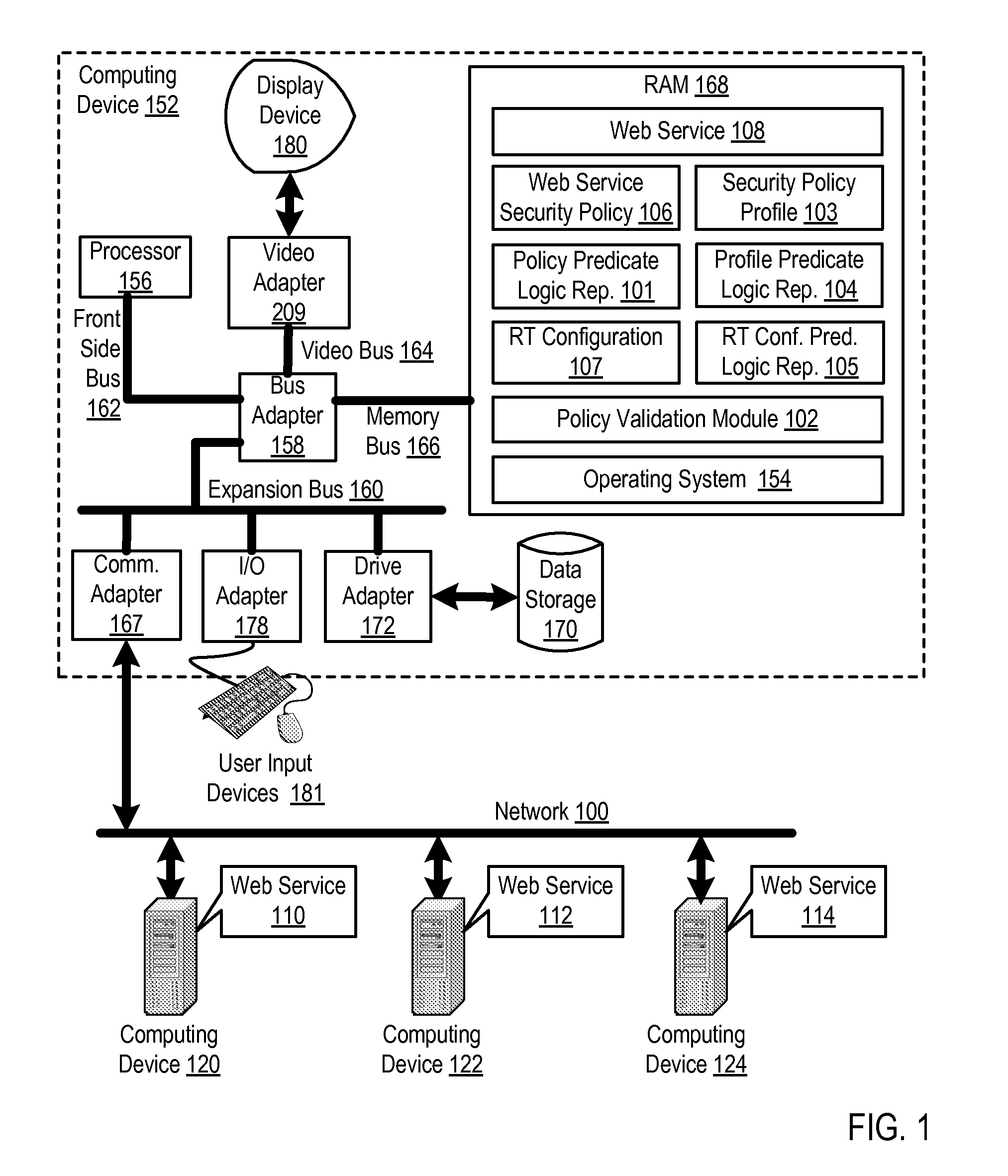
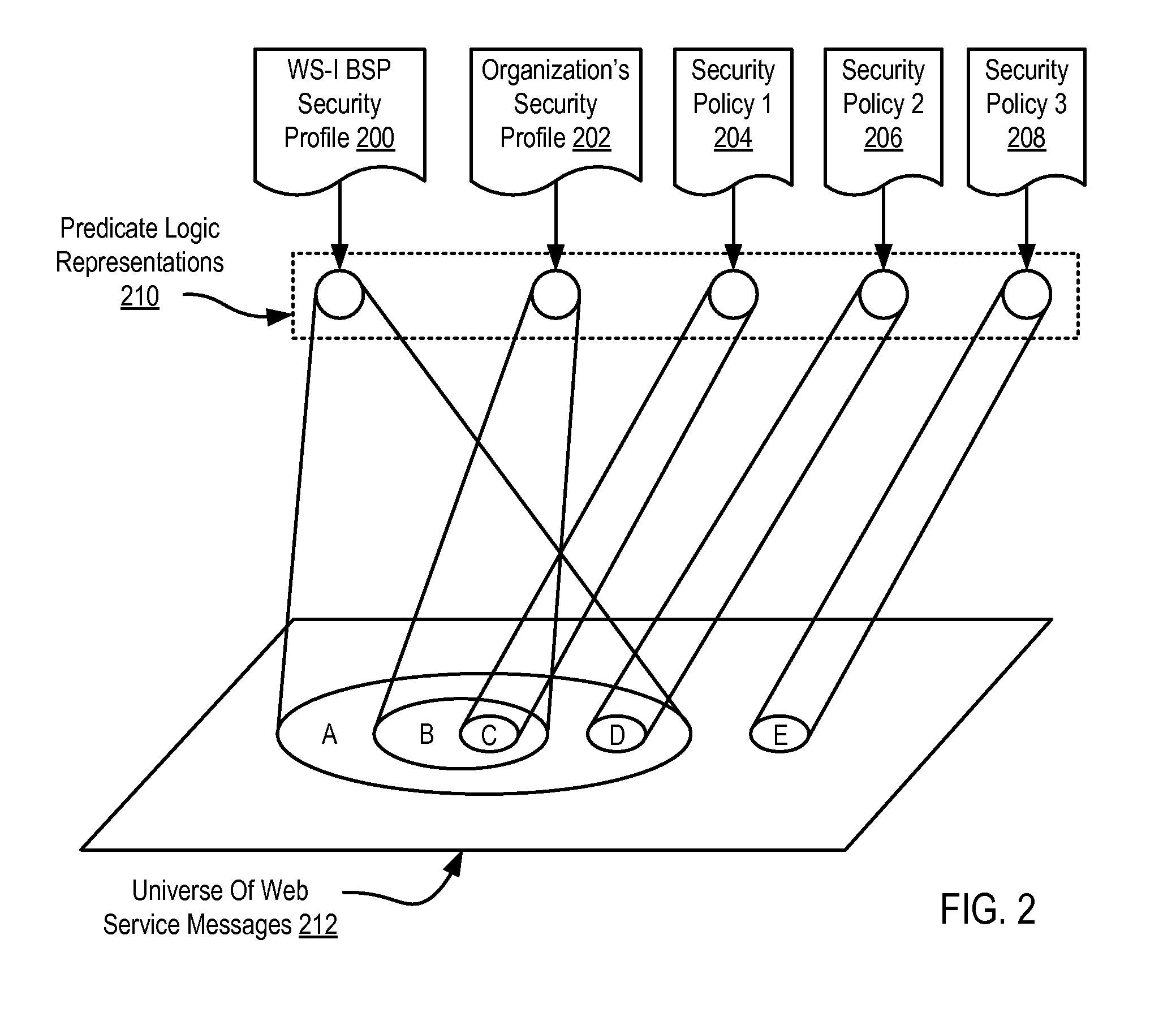
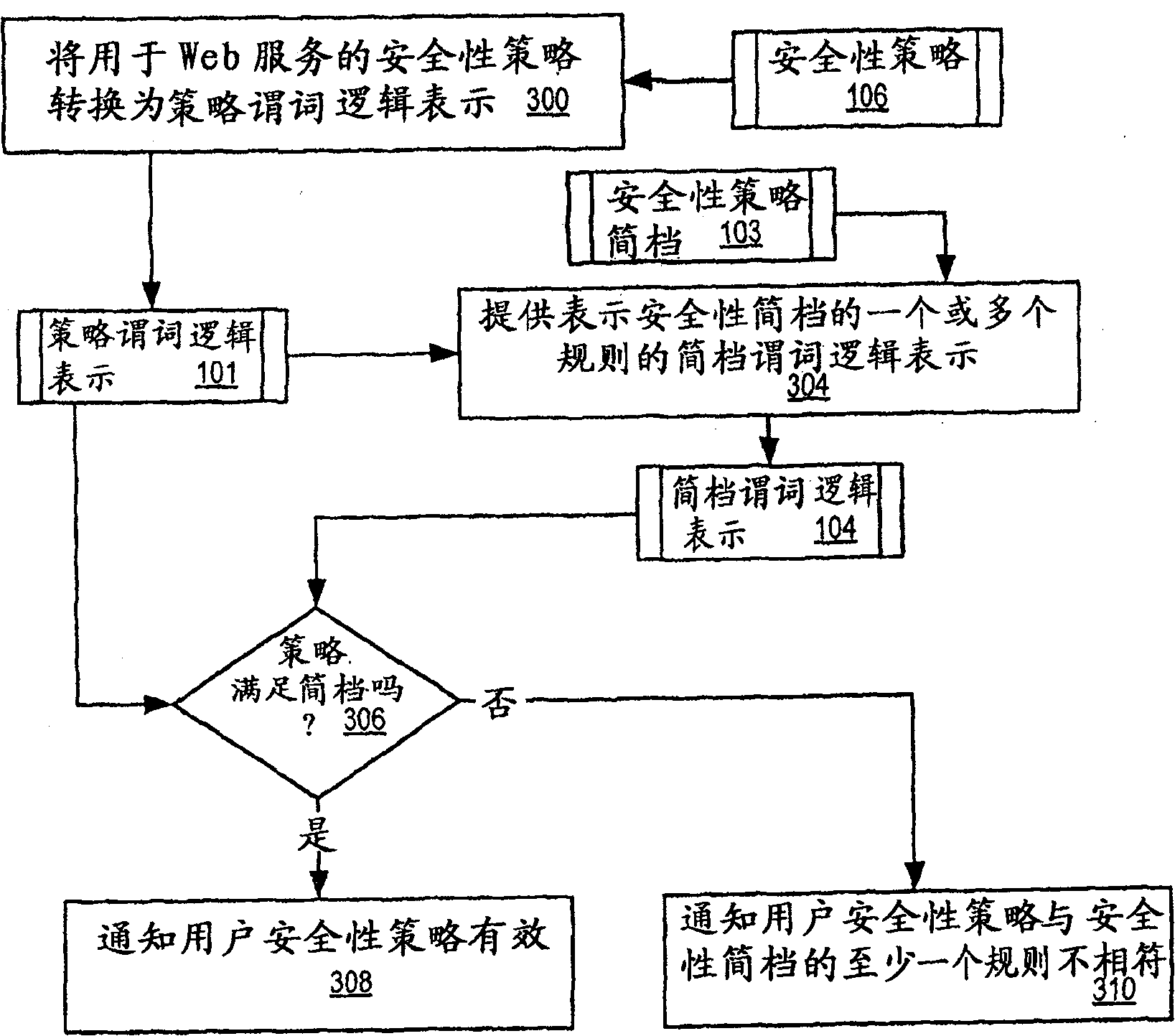
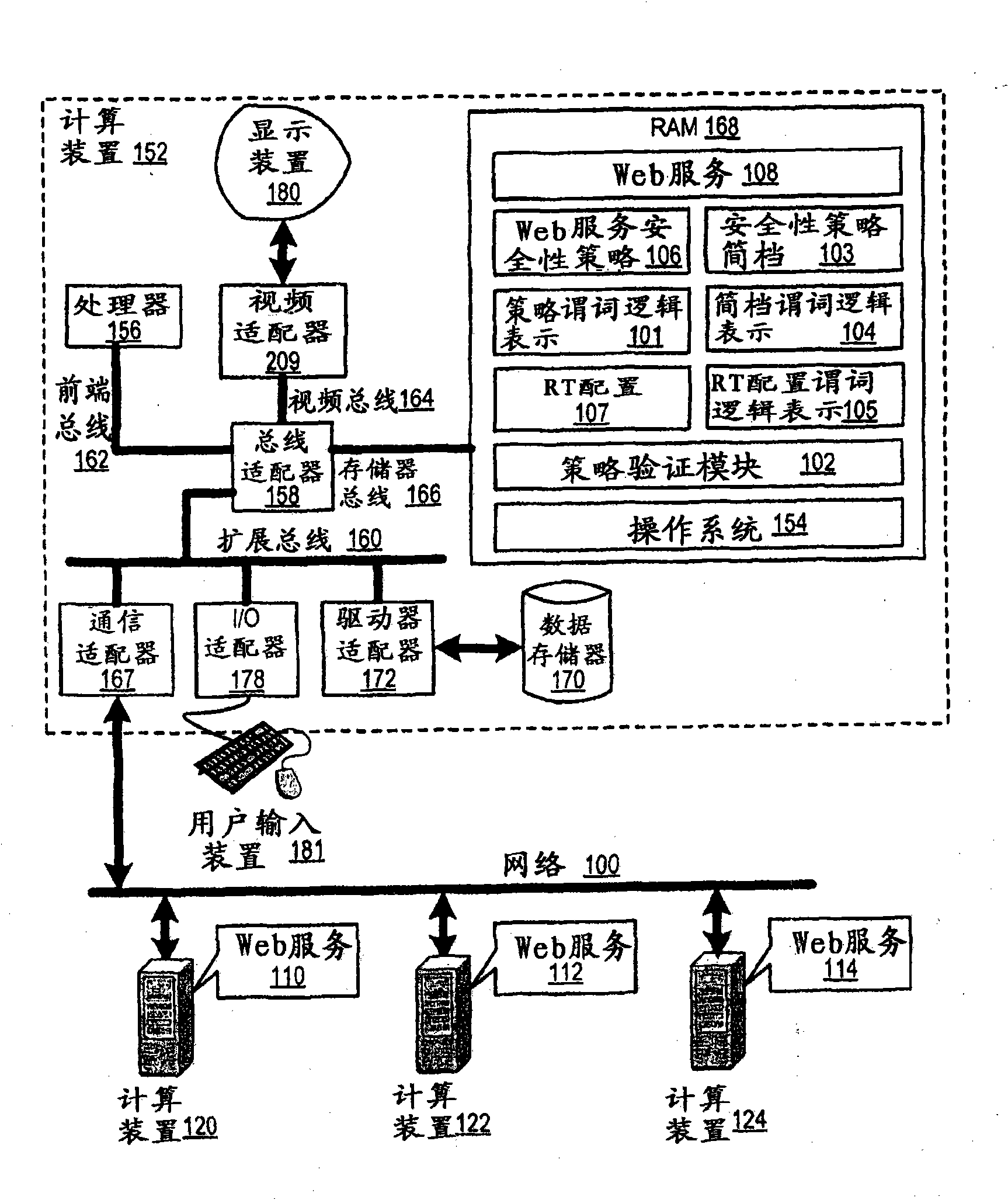
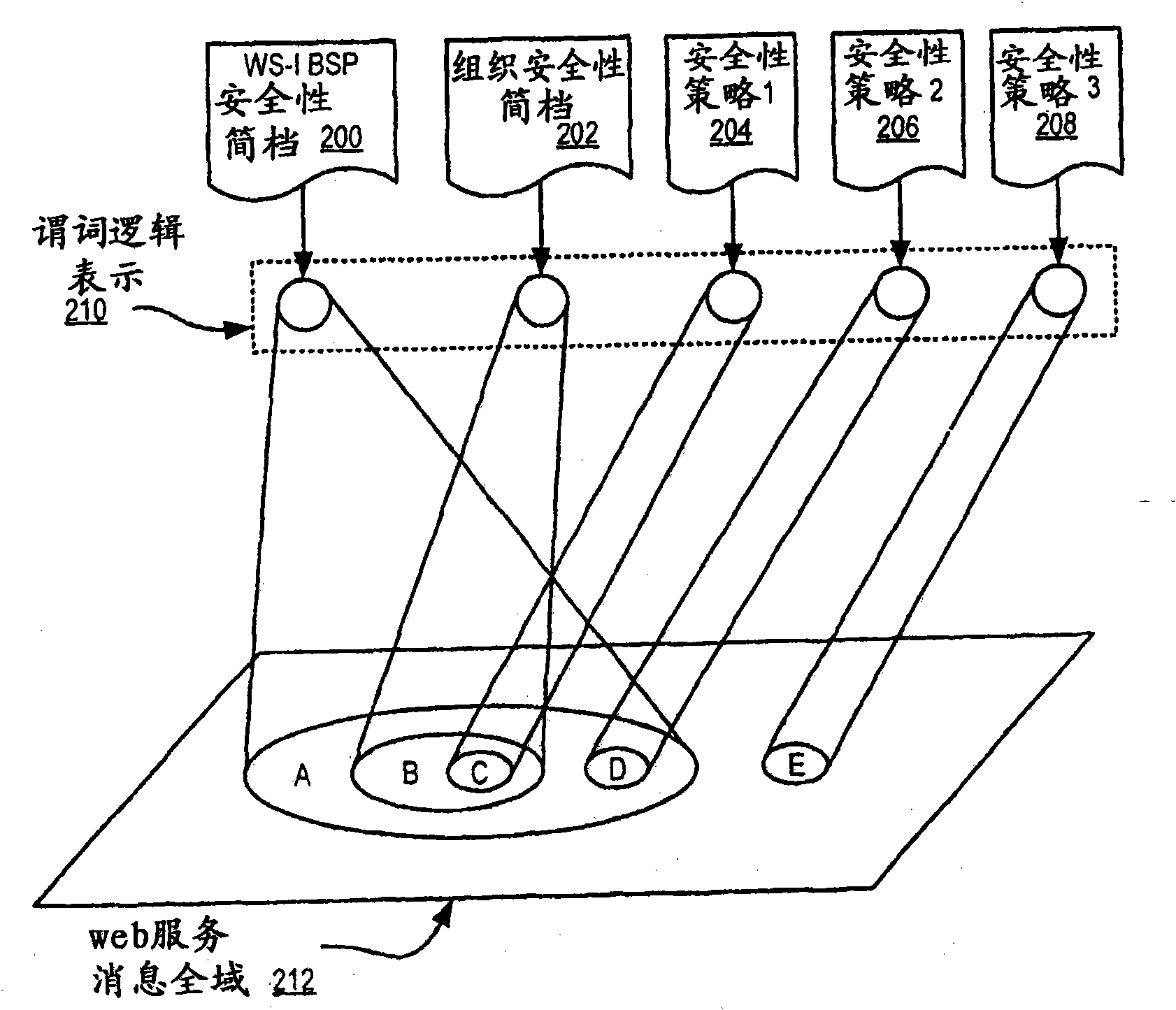
Security Policy Validation For Web Services
Methods, apparatus, and products are disclosed for security policy validation for web services that include: transforming a security policy for a web service into a policy predicate logic representation; providing a profile predicate logic representation that represents one or more rules of a security policy profile; and determining whether the security policy satisfies the security policy profile in dependence upon the policy predicate logic representation and the profile predicate logic representation.
Owner:IBM CORP
Enterprise information integration platform
InactiveUS7293010B2Easy to integrateImprove usabilityData processing applicationsDatabase management systemsData OriginWeb service
A system for enterprise information integration is described. The system is based on different layers:the data sources,source ontologies corresponding to the data schema of the data sources,an integration ontology integrating the different source ontologies,a level of query input, preferably in the form of a web service.Between the levels, mapping rules are used. These mapping rules and the entire system are based on predicate logic. The queries are answered with the help of the rules using inference based on predicate logic.
Owner:SEMEO SERVICES GMBH +1
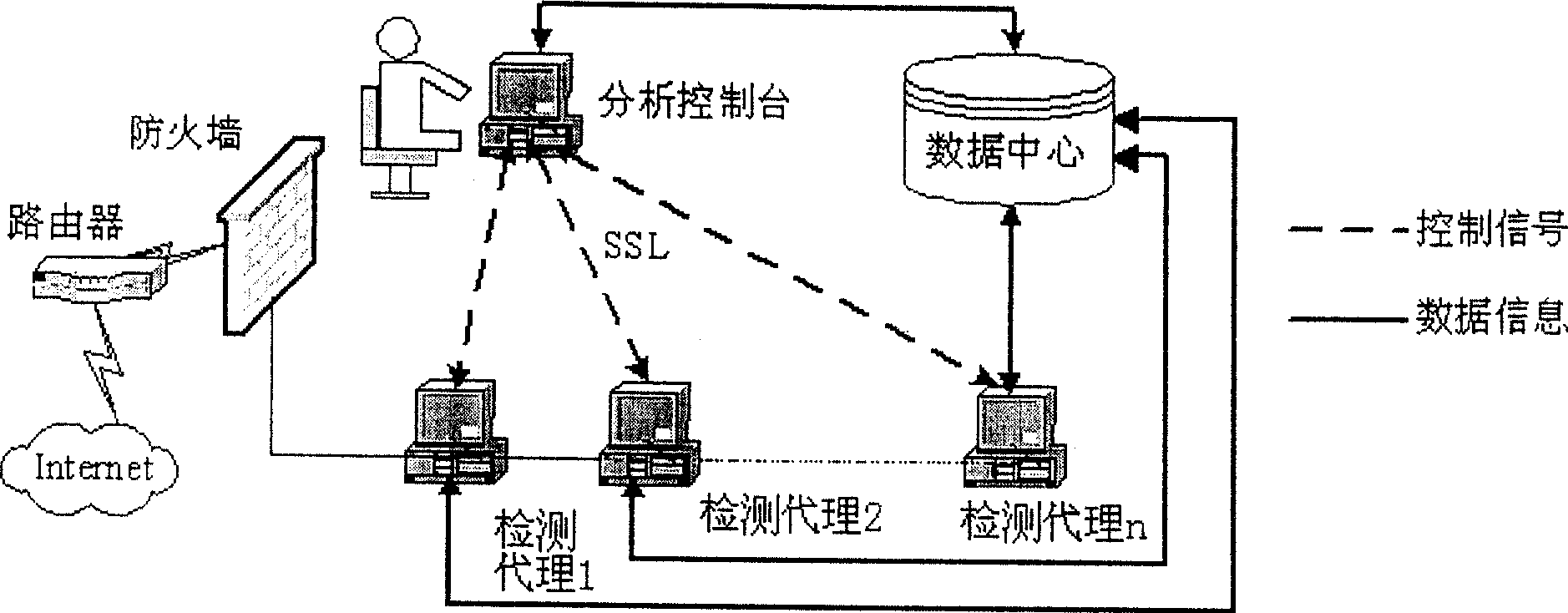
Active network safety loophole detector
InactiveCN1694454AImprove confidentialityReduce trafficData switching networksExtensibilityAnalysis data
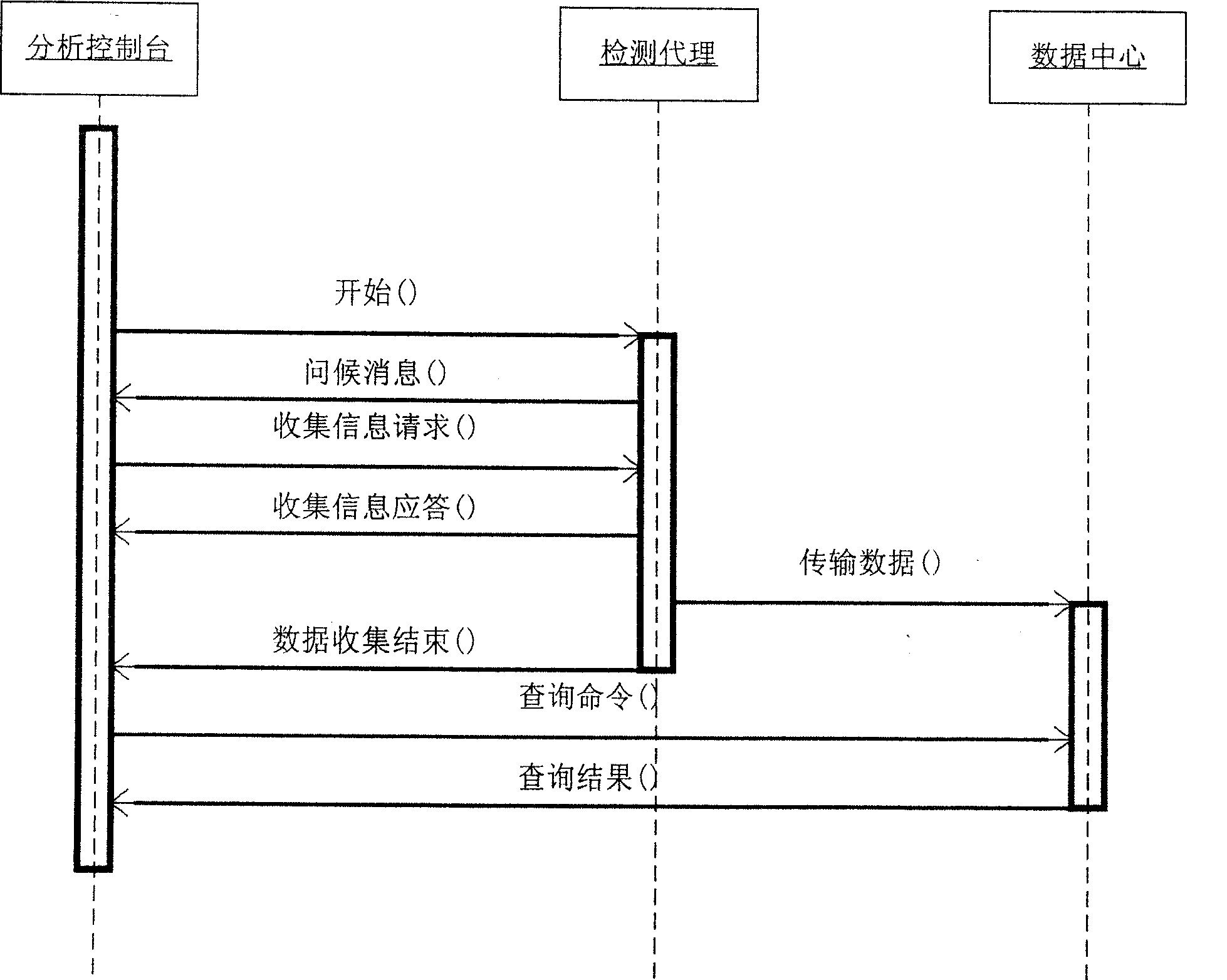
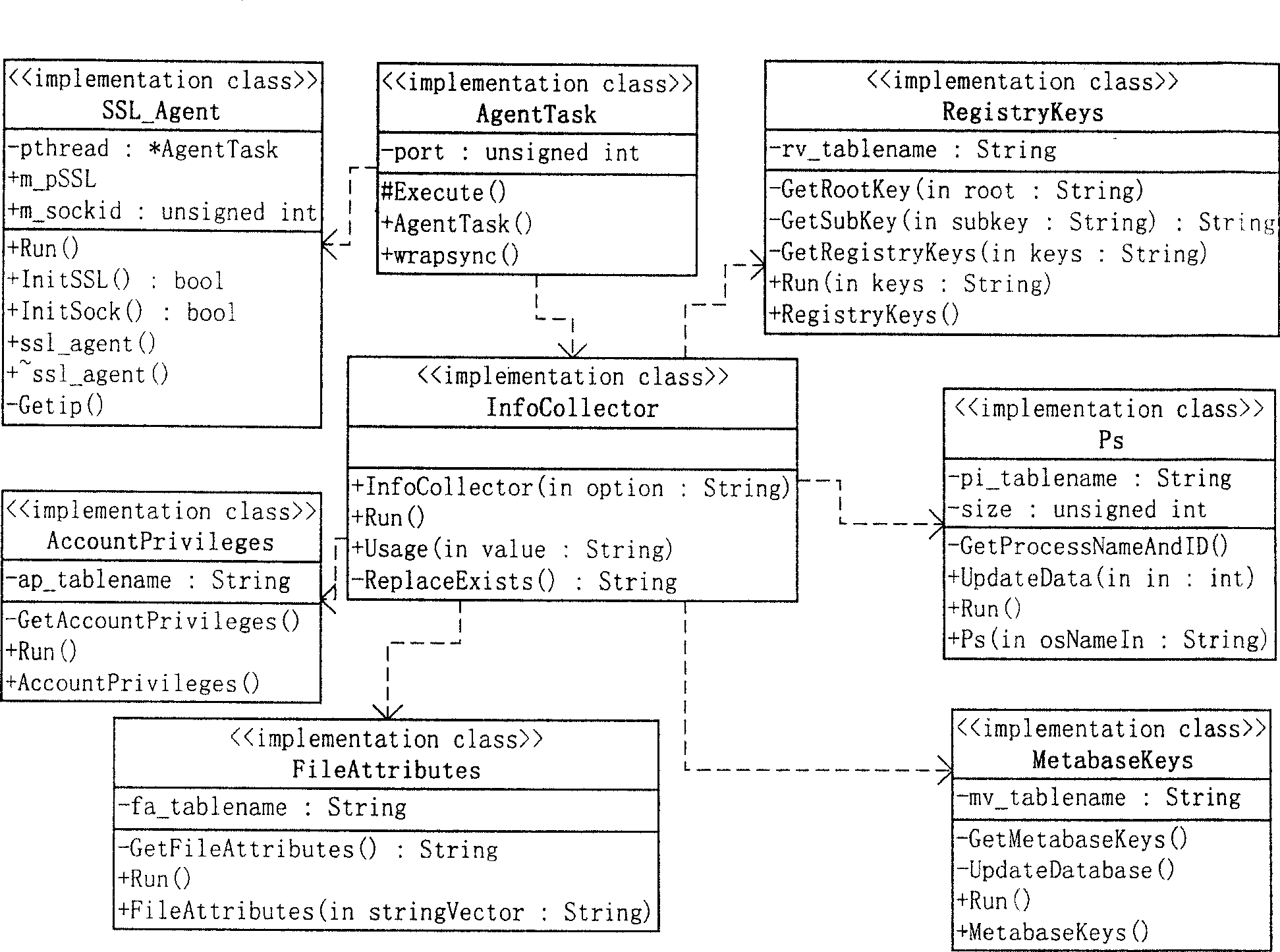
This invention discloses an active network safety leakage detector composed of three control modules of a detect agent, a data center and an analysis control stand, among which, the detection agent collection system matches the information and upwards it to the data center, the analysis control stand analyzes information stored in the data center to identify the host leakage by the OVAL leakage definition and carry out the associate analysis of attack / leakage by the predicate logic theory to find out the safety problem brought with the leakage combination to display potential attack paths in sight.
Owner:XI AN JIAOTONG UNIV
Network security risk evaluation system based on game theory
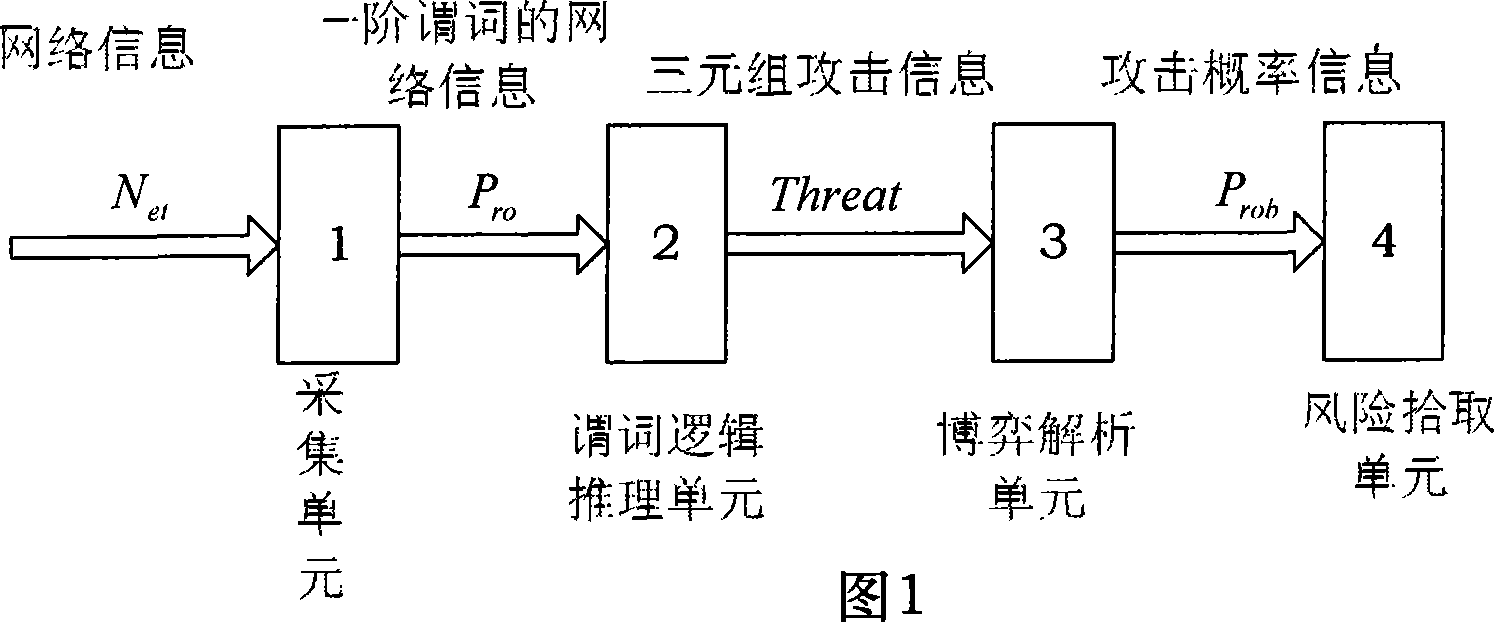
The present invention discloses a network safety risk evaluating system based on game theory. The system firstly collects network property data which comprises information of node address, service, application program, software leak, etc. from an evaluated network, describes with a first-order predicate logic, reasons with an XSB reasoning engine based on the description of first-order predicate logic, and obtaining the leak which is on the evaluated network system and can be used by an attacker, and a corresponding attack threat. Aiming at each attack threat, the system according to the invention establishes a game theoretical attack-defense model GTADM and calculates the game equilibrium point. The obtained attack probability is multiplied to the expected damage value of the attack to the attack target for obtaining the attack risk to the system. Thereby the risk level of nodes in the evaluated system is obtained and the security evaluating to the network is realized.
Owner:BEIHANG UNIV
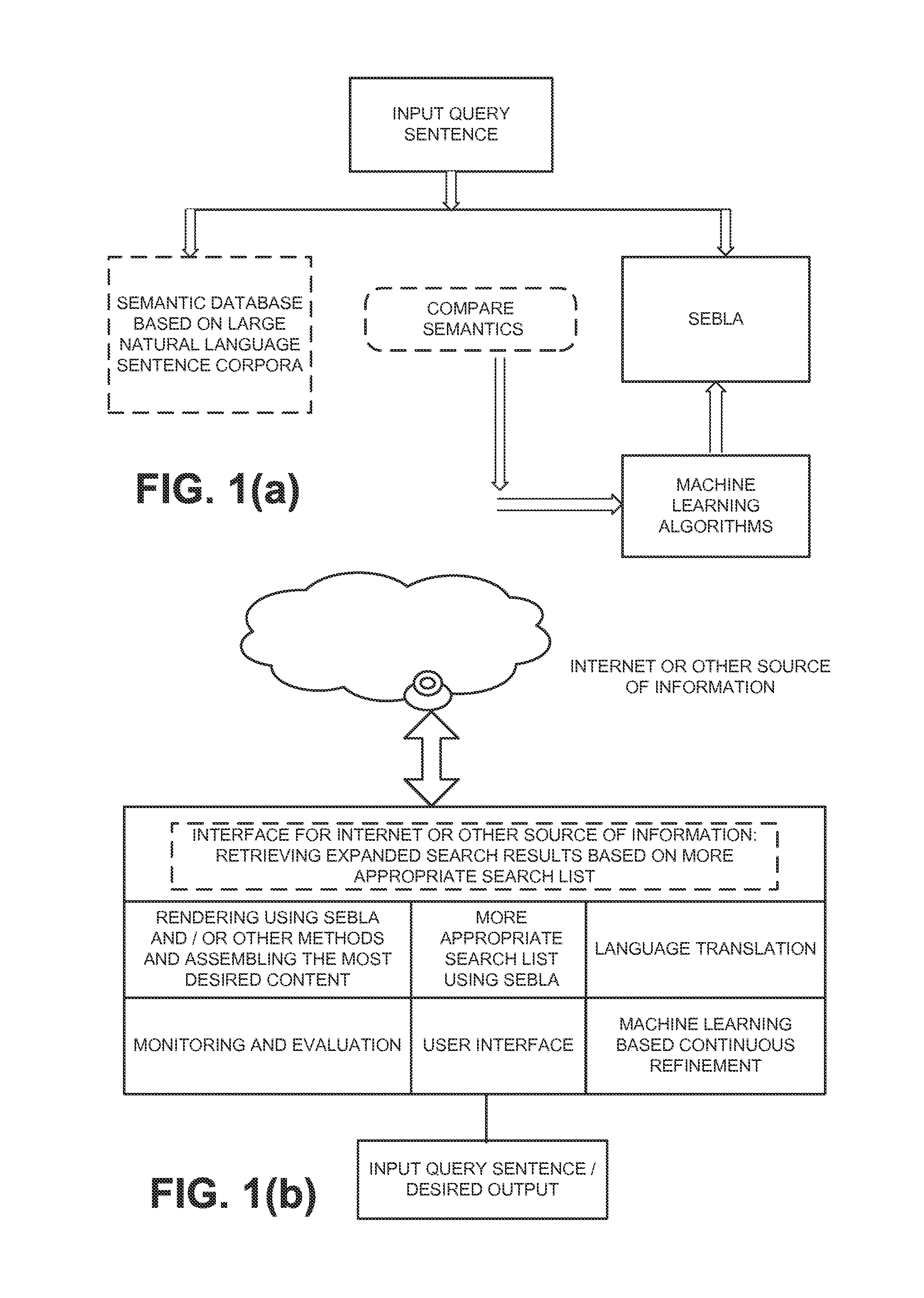
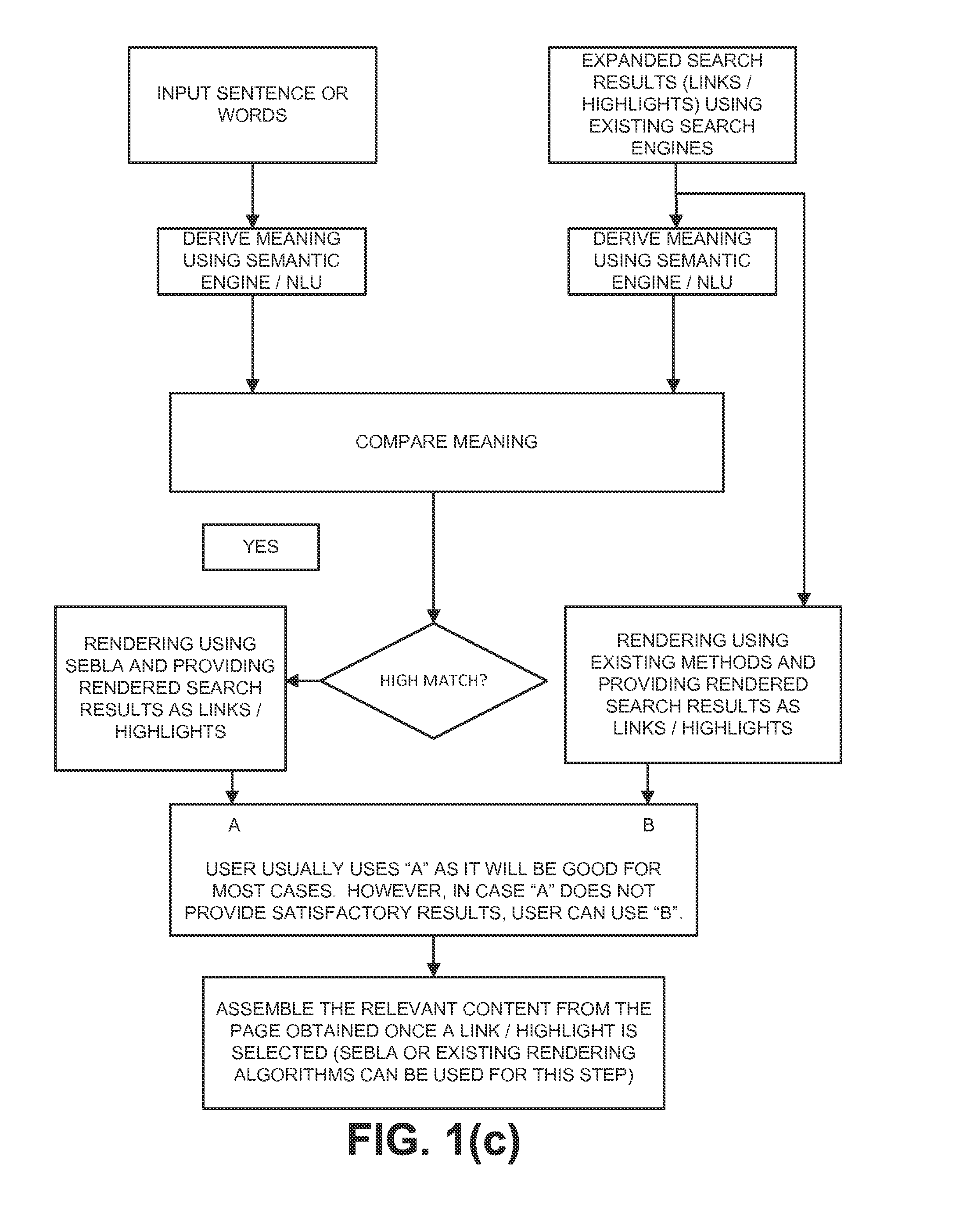
Natural language understanding using brain-like approach: semantic engine using brain-like approach (SEBLA) derives semantics of words and sentences
InactiveUS20140032574A1Digital data information retrievalDigital data processing detailsNatural language understandingSemantics
Natural Language Understanding (NLU) is a complex open problem. NLU complexity is mainly related to semantics: abstraction, representation, real meaning, and computational complexity. While existing approaches can solve some specific problems, they do not address Natural Language problems in a natural way. This invention describes a Semantic Engine using Brain-Like approach (SEBLA) that uses Brain-Like algorithms to solve the key NLU problem (semantics and its sub-problems).The main theme of SEBLA is to use each word as an object with all important features, most importantly the semantics. The next main theme is to use the semantics of each word to derive the meaning of a sentence as we do as humans. Similarly, the semantics of sentences are used to derive the meaning of a paragraph. The 3rd main theme is to use natural semantics as opposed to existing “mechanical semantics” used in Predicate logic, Ontology or the like.
Owner:KHAN EMDADUR R
Predicate logic based image grammars for complex visual pattern recognition
InactiveUS8548231B2Improve performanceRegained much attention in computer visionCharacter and pattern recognitionChaos modelsAlgorithmFirst-order predicate
Owner:SIEMENS CORP
Method and device for discovering link layer network topology
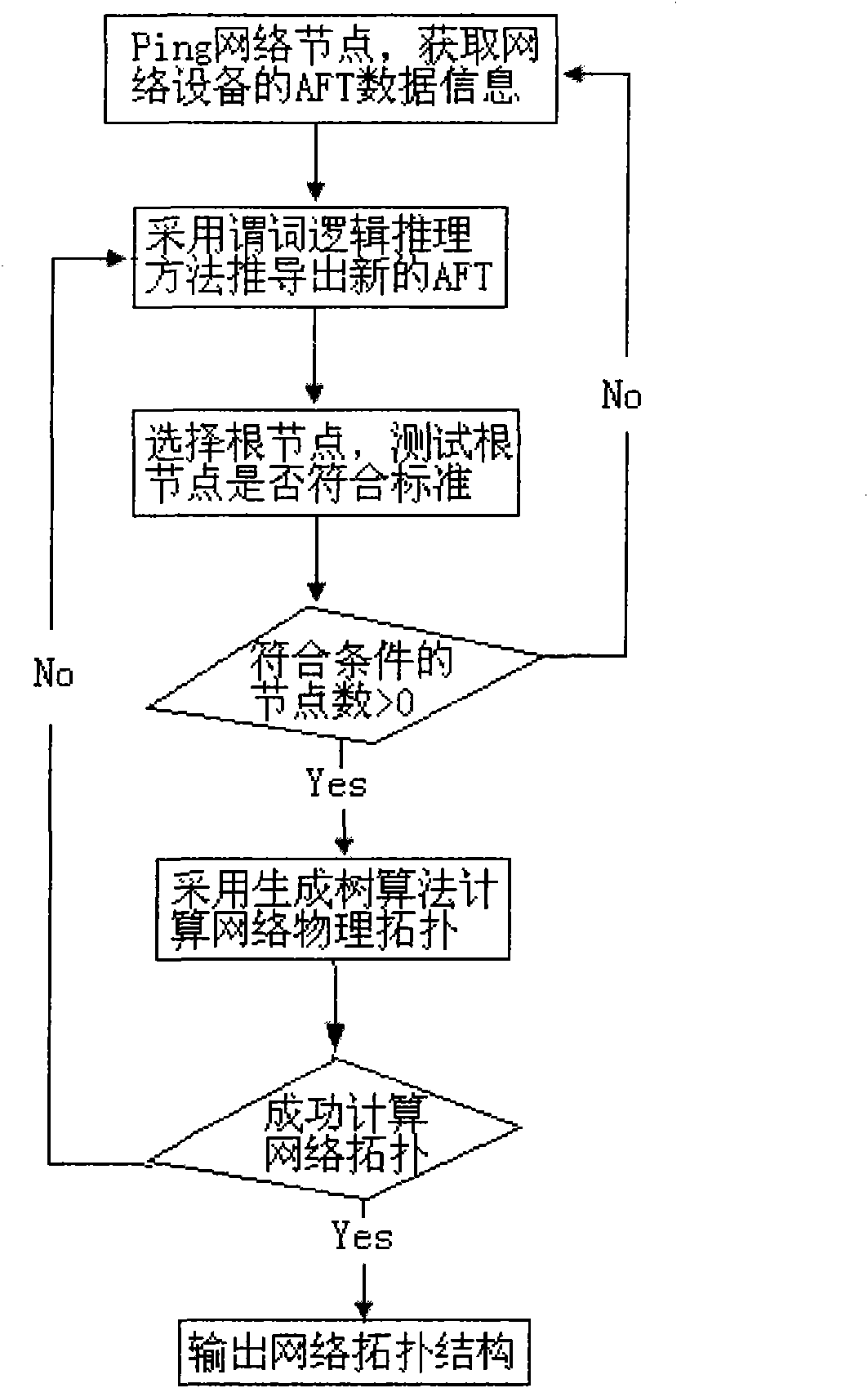
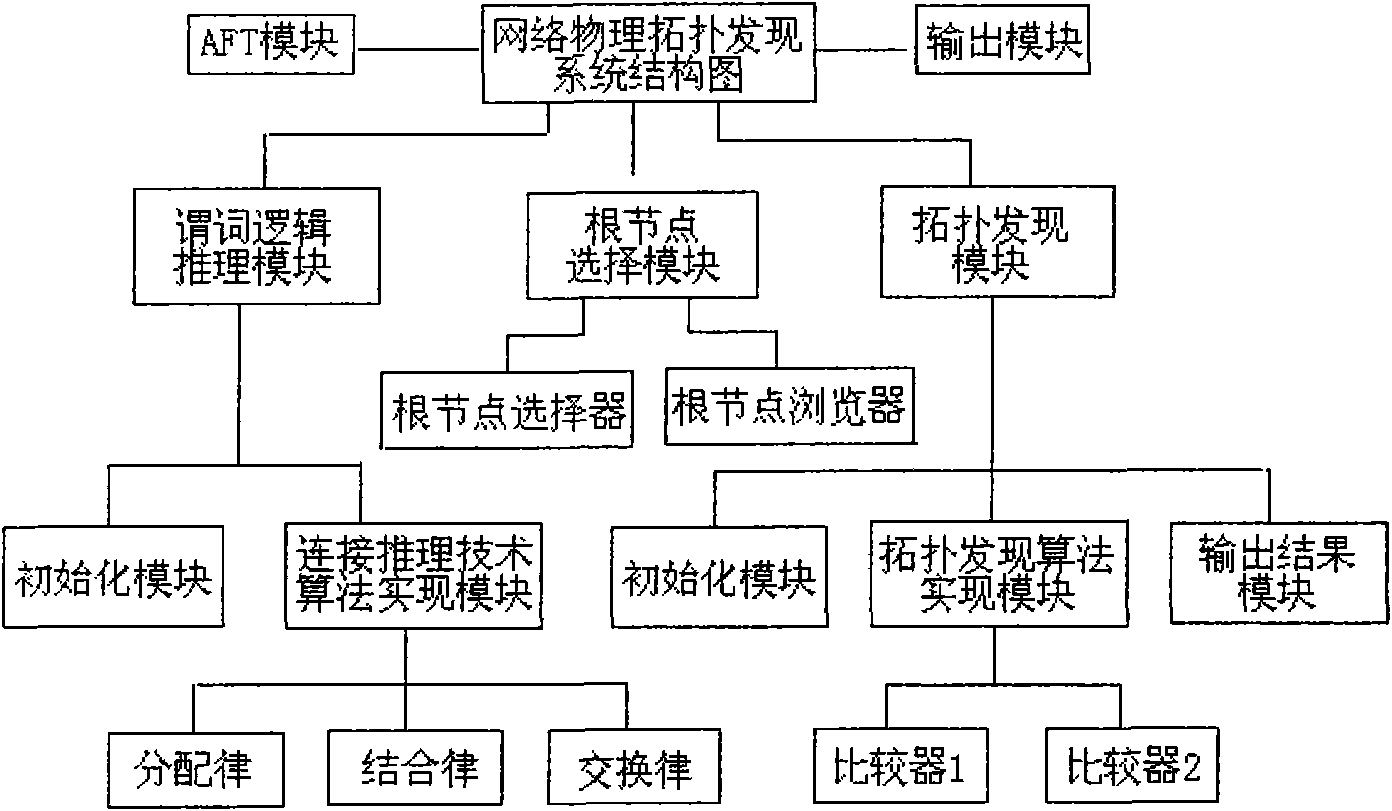
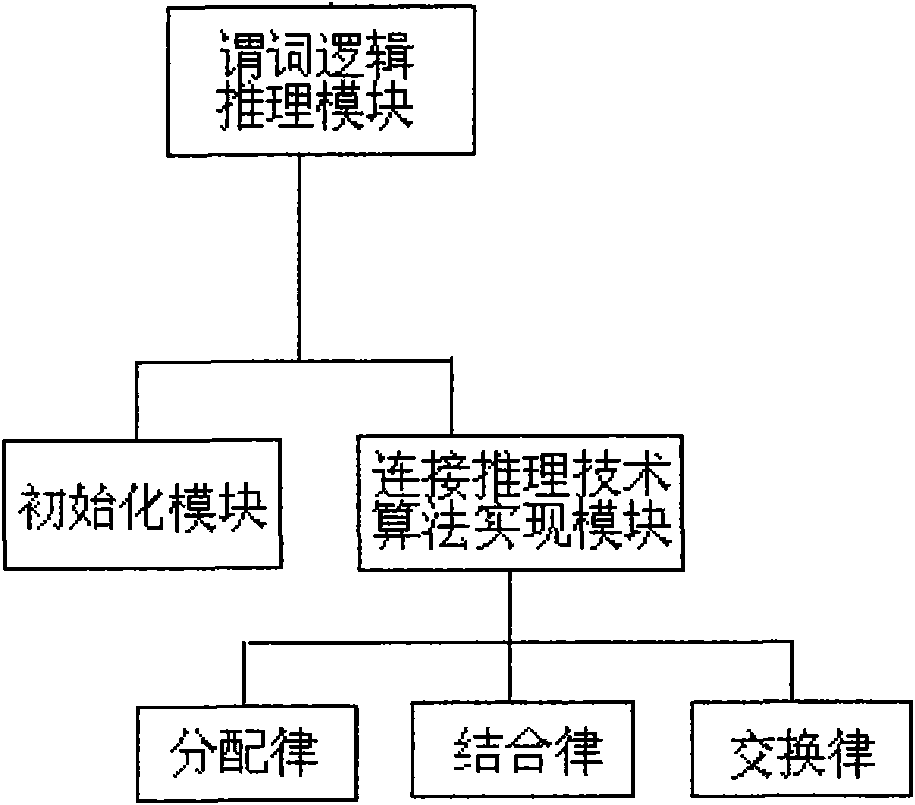
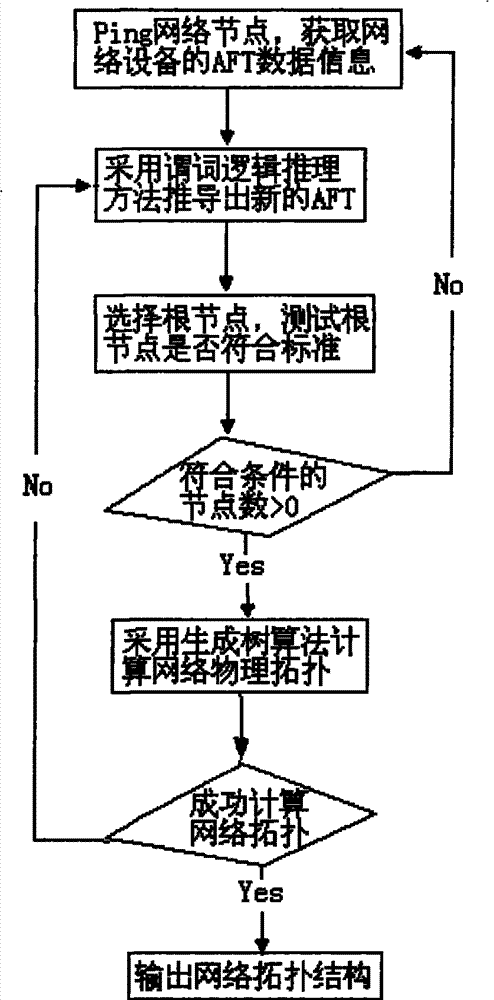
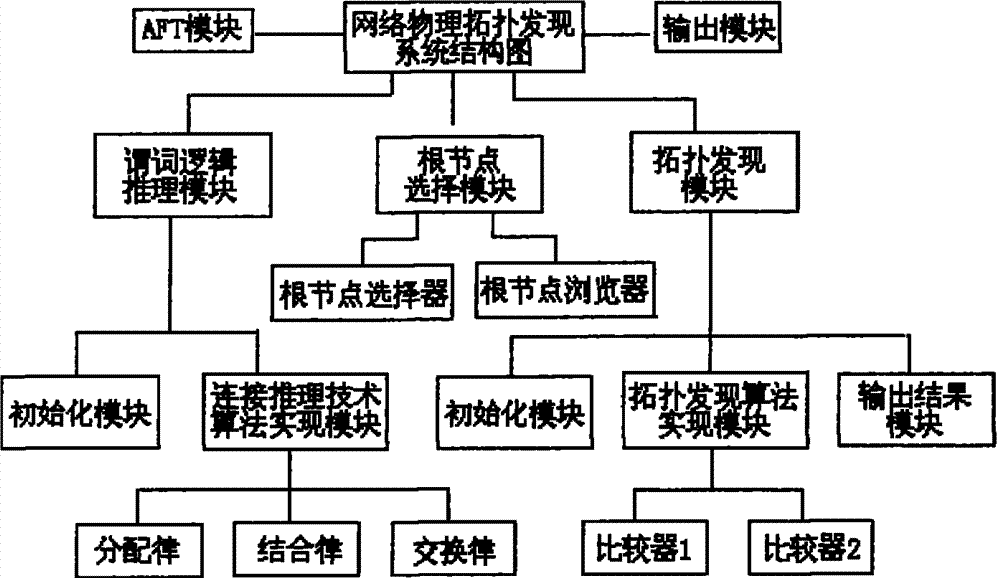
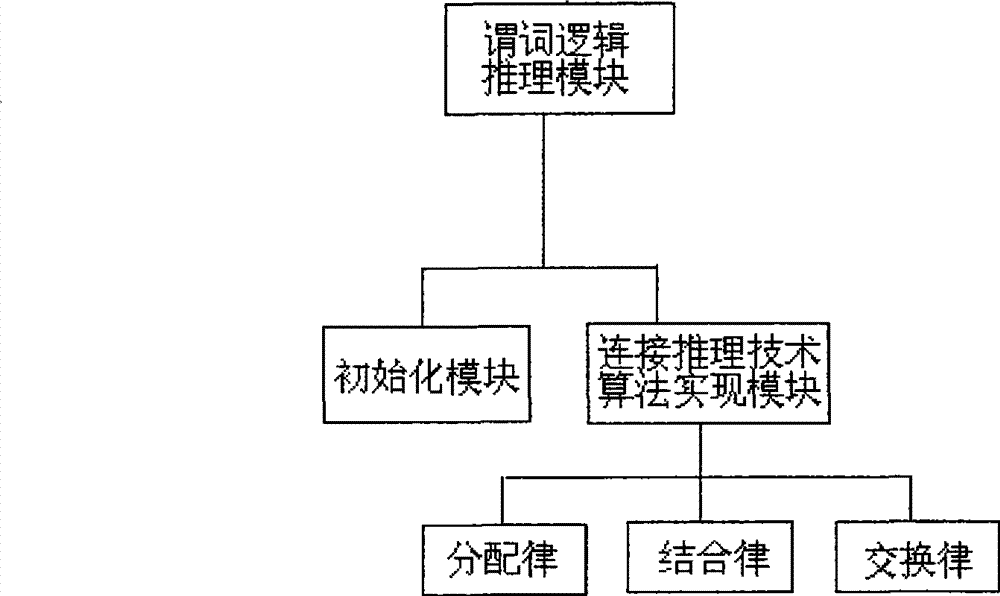
The invention discloses a method and a device for discovering link layer network topology. The method comprises the following steps: acquiring an address forwarding table (AFT table) of the network node by a pinging link layer network node; deriving the connection relation between network nodes by a predicate logic inference algorithm according to connection reasoning technology and repairing incomplete inverse root AFT data to acquire a complete AFT table; and utilizing a spanning tree protocol algorithm to calculate each network node according to the complete AFT table acquired according tothe predicate logic inference algorithm so as to discover a physical network topology structure of the link layer. The method provided by the invention combined with the predicate logic inference algorithm of the connection reasoning technology and a spanning tree protocol-based topology discovery algorithm can calculate the network node information effectively under the condition that the AFT data is incomplete, thereby overcoming the shortages of the prior method for discovering the link layer network topology and improving the probability of acquiring the physical network topology.
Owner:BEIJING VENUS INFORMATION TECH +1
Target domain knowledge base generation method and device and question answering method and device
ActiveCN111538844ARealization of logic operationsRealize logical derivationNatural language data processingSpecial data processing applicationsAlgorithmTheoretical computer science
The invention discloses a target domain knowledge base generation and question answering method and device, and the method comprises the steps: determining a concept graph, a reason graph and a predicate logic formula of target domain knowledge according to the knowledge type of the target domain knowledge; and generating a target domain knowledge base, wherein the concept map is used for representing a static relationship among the concept words, the factorial map is used for representing the sequence between the events and the factorial relationship between the events, and the predicate logic formula is used for representing business rules in the target domain knowledge. The question answering method comprises the steps that M events triggered by N word segmentation phrases of a questionare determined from an affair graph, and slot position values of slot positions of the M events are determined according to K word segmentation phrases, matched with a concept graph, in the N word segmentation phrases; a predicate logic formula corresponding to the consulting object of the question is calculated according to the M events and the slot values of the slots of the M events; an answerto the question is determined.
Owner:HUAWEI TECH CO LTD
Security policy validation for web services
Methods, apparatus, and products are disclosed for security policy validation for web services that include: transforming a security policy for a web service into a policy predicate logic representation; providing a profile predicate logic representation that represents one or more rules of a security policy profile; and determining whether the security policy satisfies the security policy profile in dependence upon the policy predicate logic representation and the profile predicate logic representation.
Owner:INT BUSINESS MASCH CORP
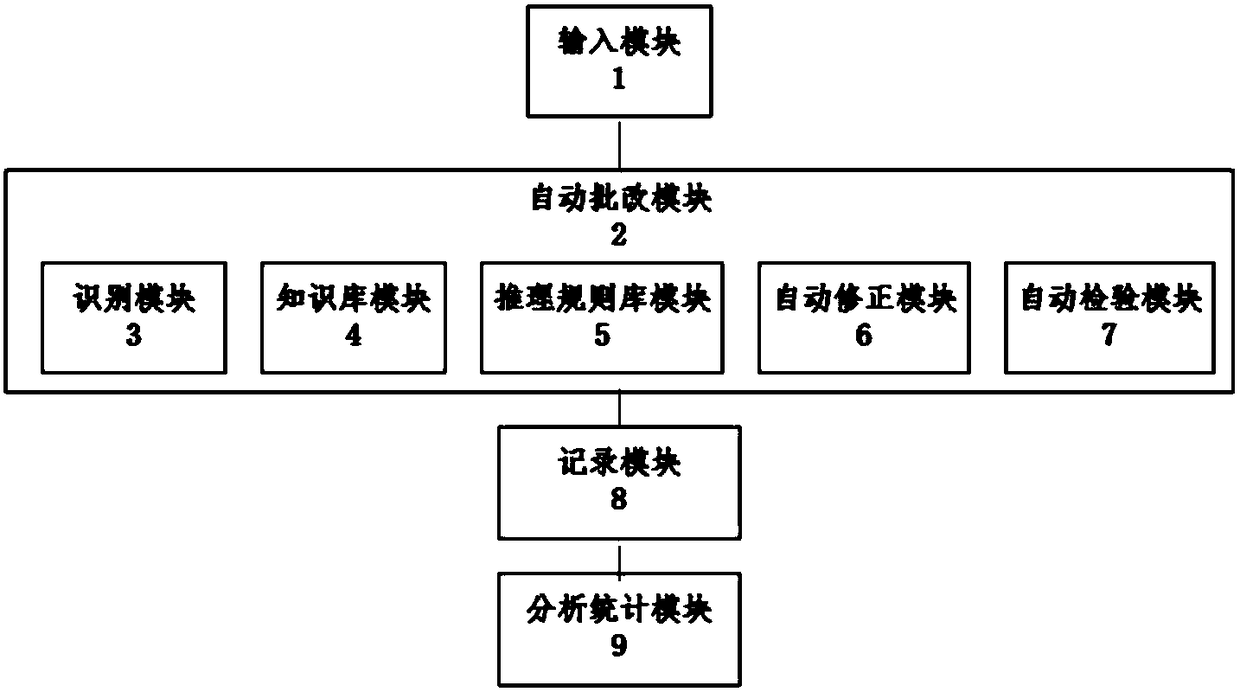
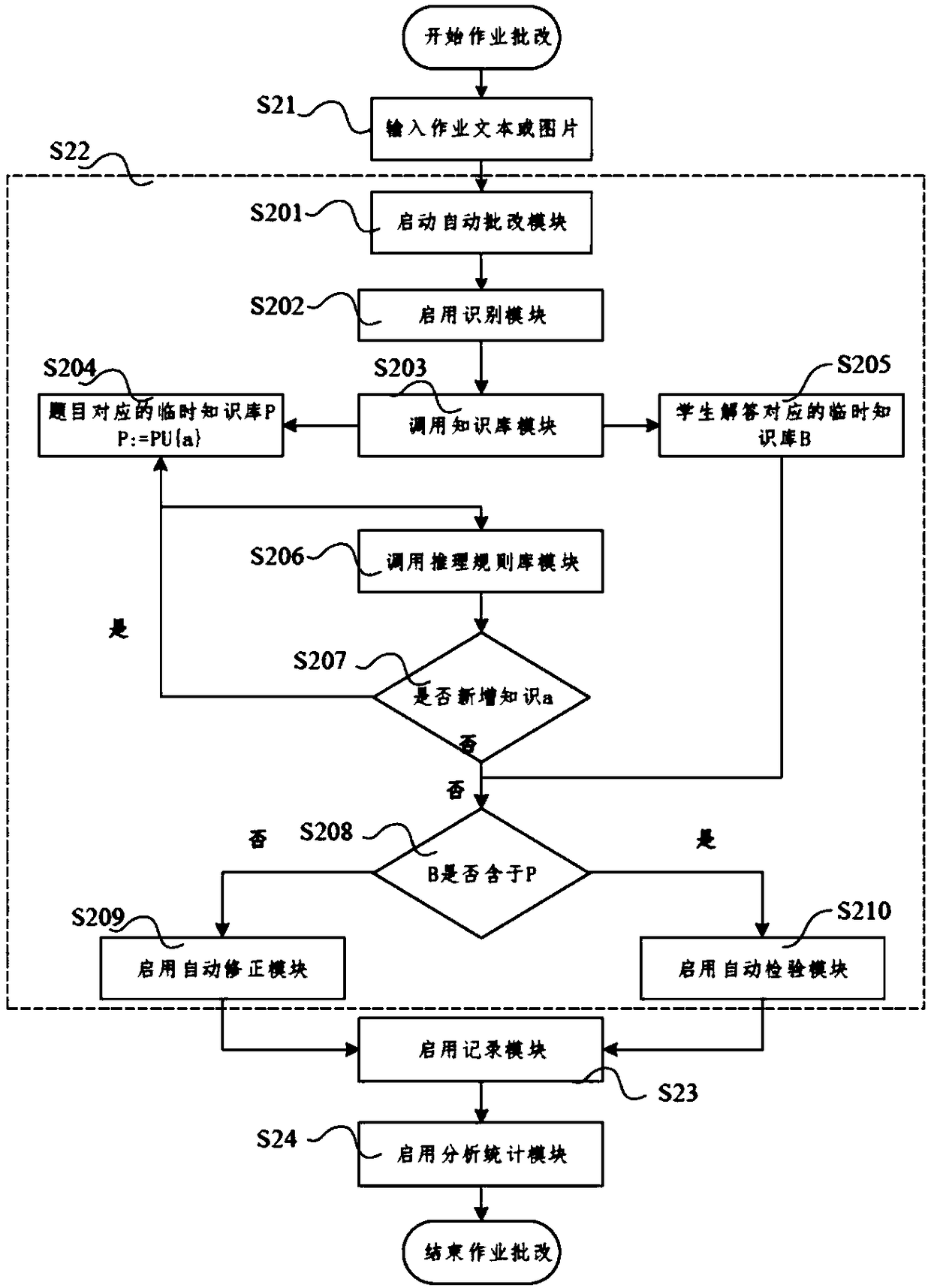
Homework correction device
InactiveCN108109453AAccurate feedbackReduce workloadElectrical appliancesAlgorithmTheoretical computer science
The invention discloses a homework correction device. The homework correction device comprises an input module, a recognition module, a knowledge base module, an inference rule base module, an automatic revising module, an automatic checking module, an automatic correction module and a recording module, wherein the input module is used for acquiring text information or picture information of homework to be corrected; the recognition module is used for recognizing the text information or picture information as knowledge points; the knowledge base module is used for expressing the knowledge points through predicate logic; the inference rule base module is used for establishing an inference rule according to the generally acknowledged truth, the theorem, the definition and the formula; the automatic revising module is used for discovering errors occurring in the solving process and obtaining the follow-up correct solving process through the backtracking technology; the automatic checkingmodule is used for checking the completeness of the solving process of students; the automatic correction module is used for calling the recognition module, the knowledge base module, the inference rule base module, the automatic revising module and the automatic checking module for automatically correcting and revising the homework, and storing the correction result; the recording module is usedfor recording the automatically revised part of the homework or the incomplete part in automatic checking, and the knowledge points and the inference rule relevant to the parts.
Owner:GUANGZHOU UNIVERSITY
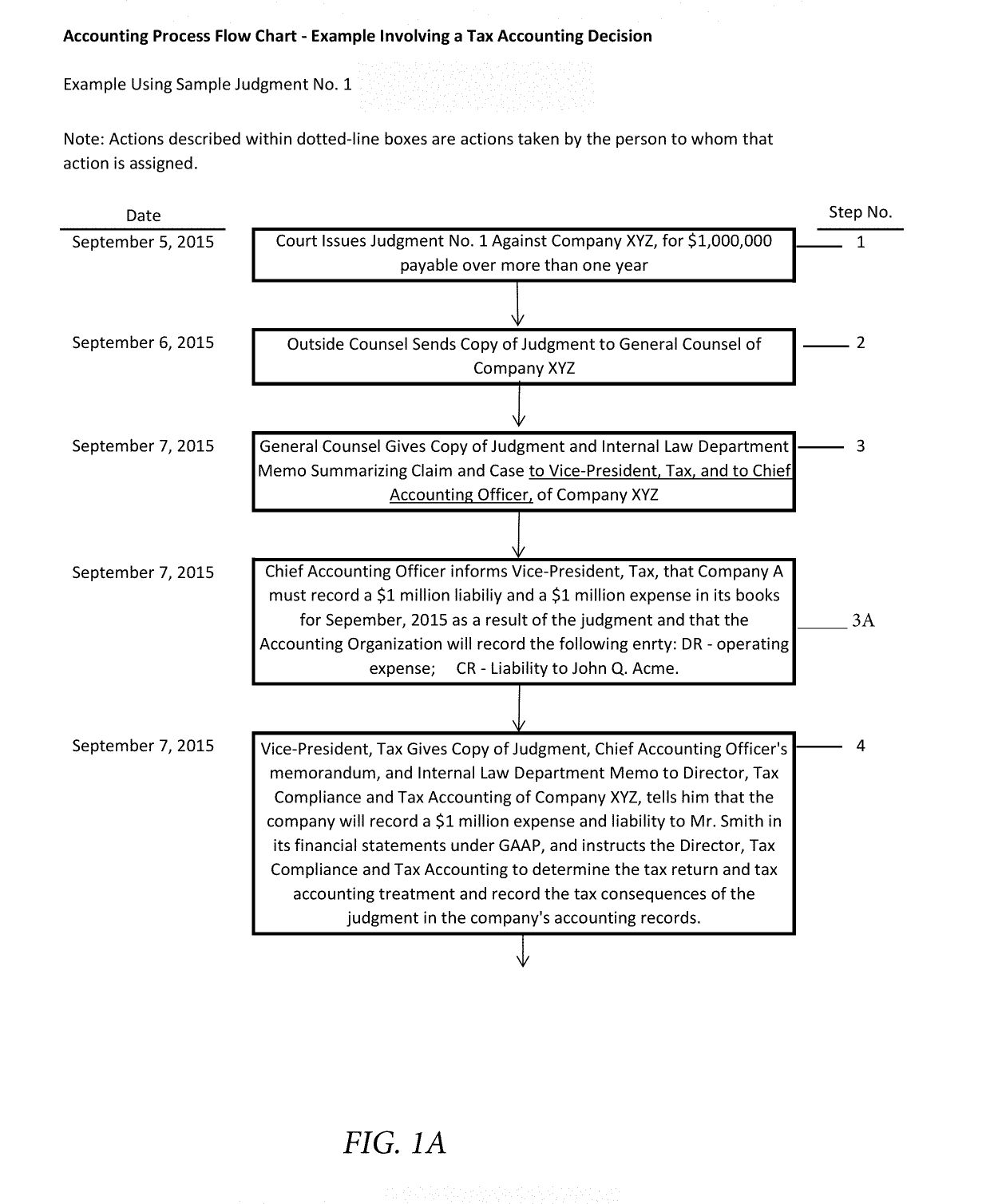
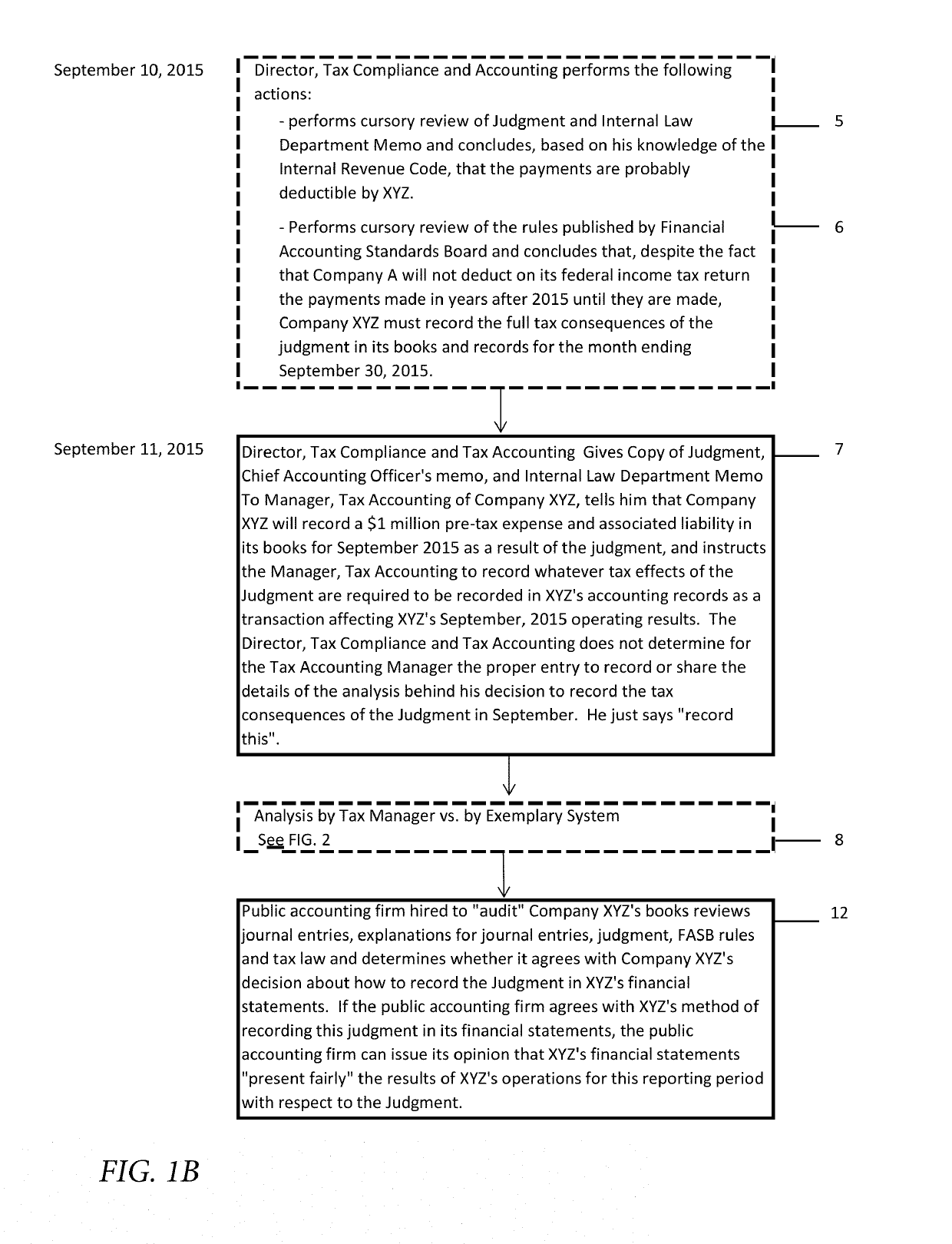
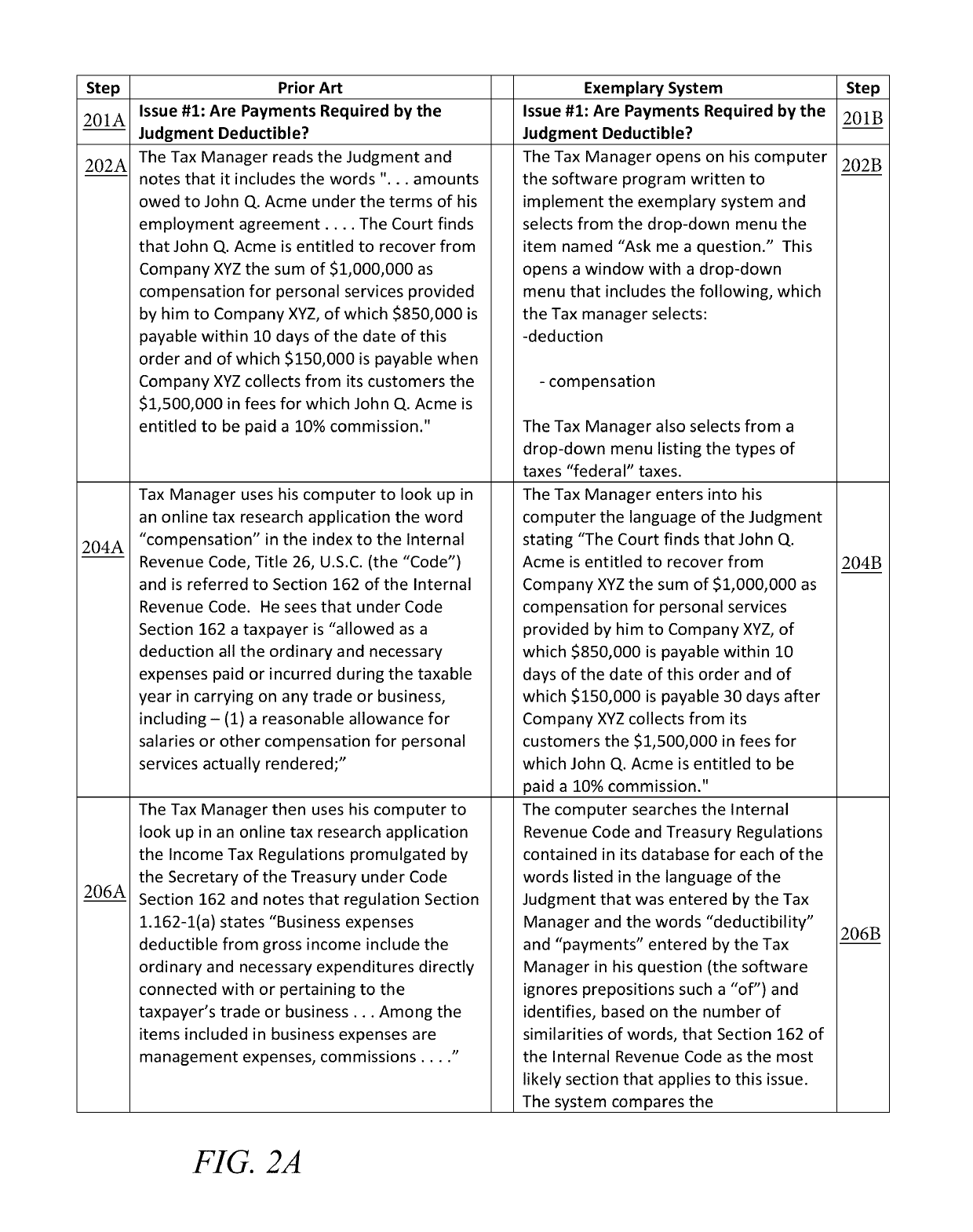
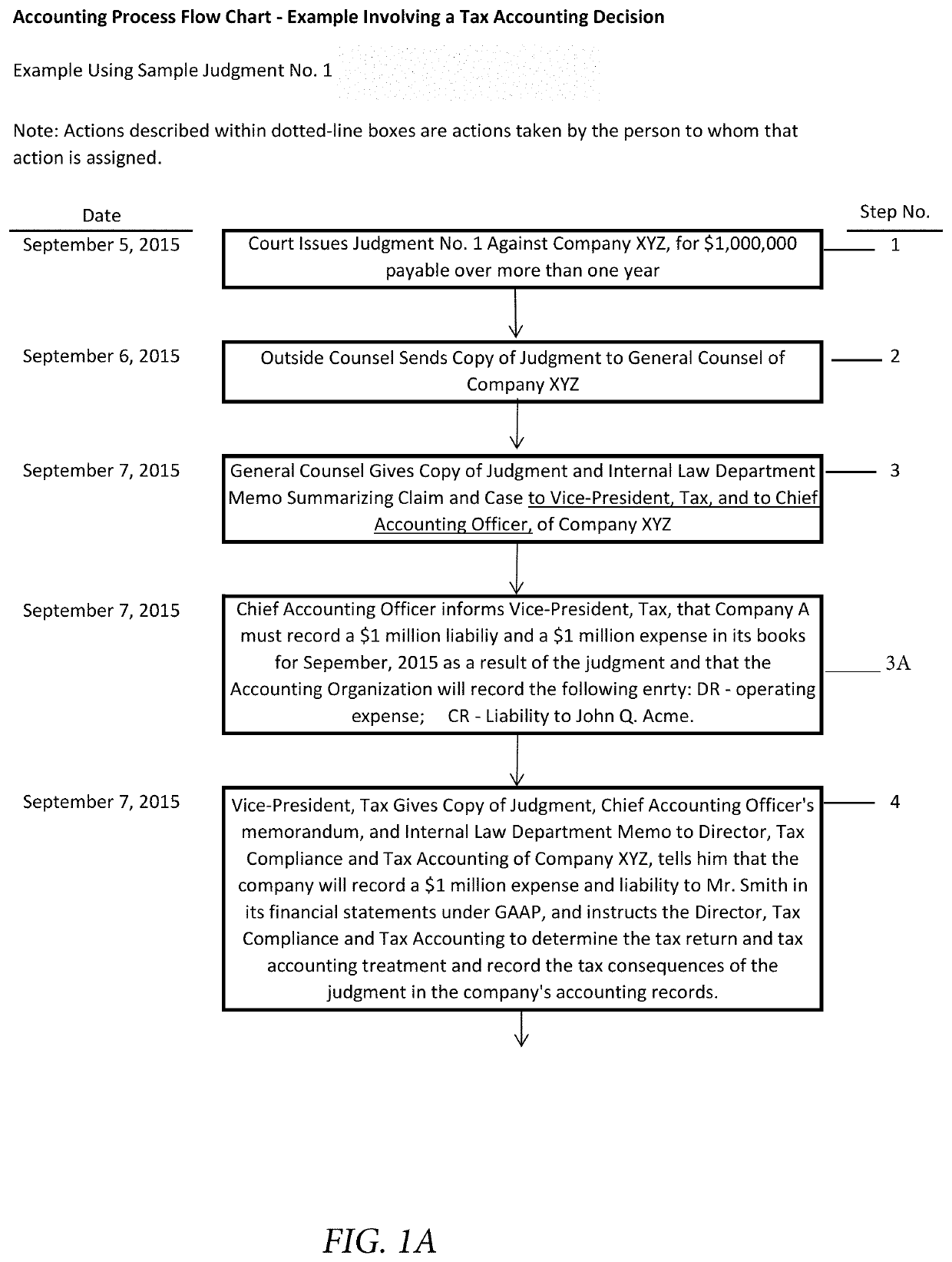
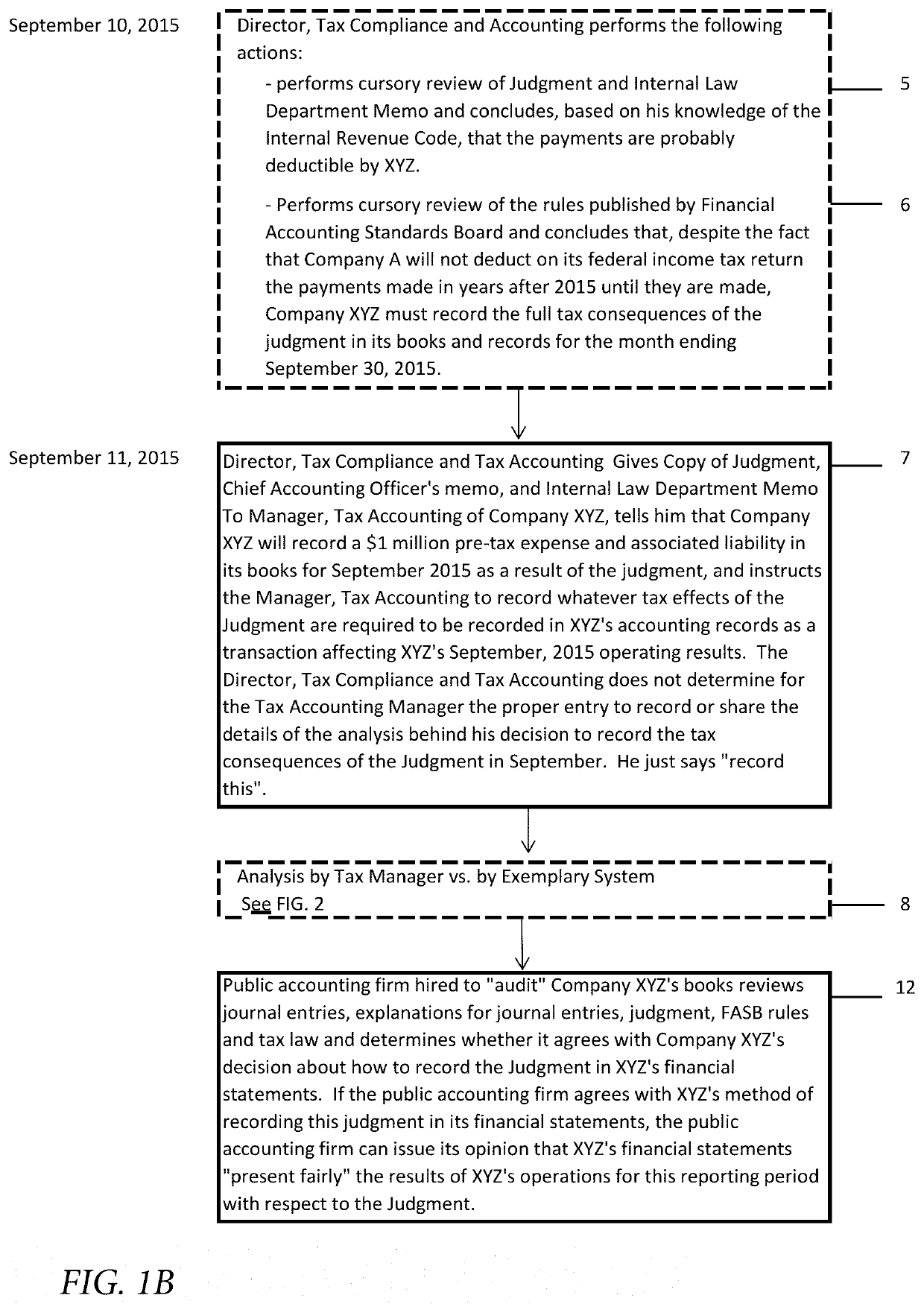
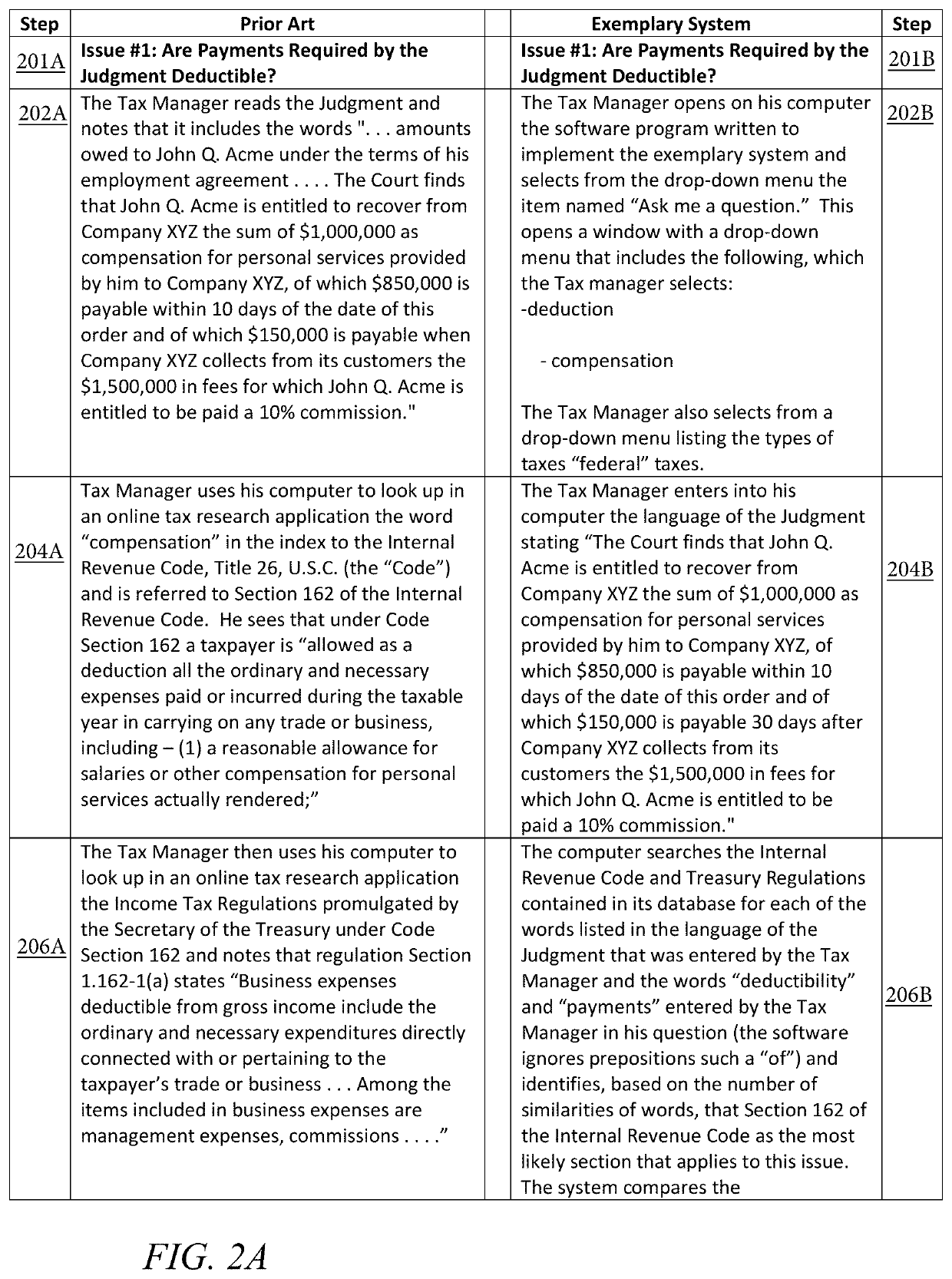
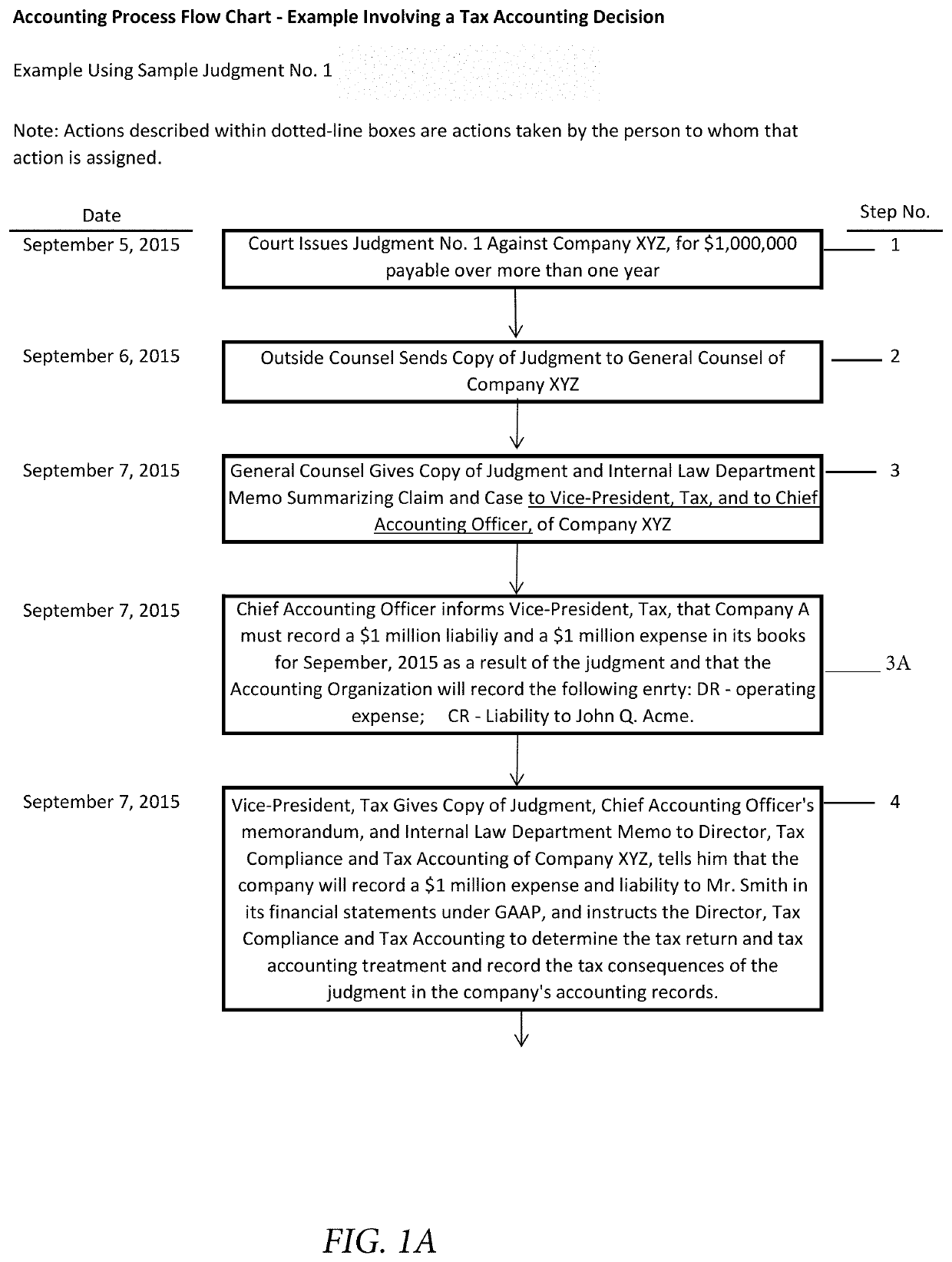
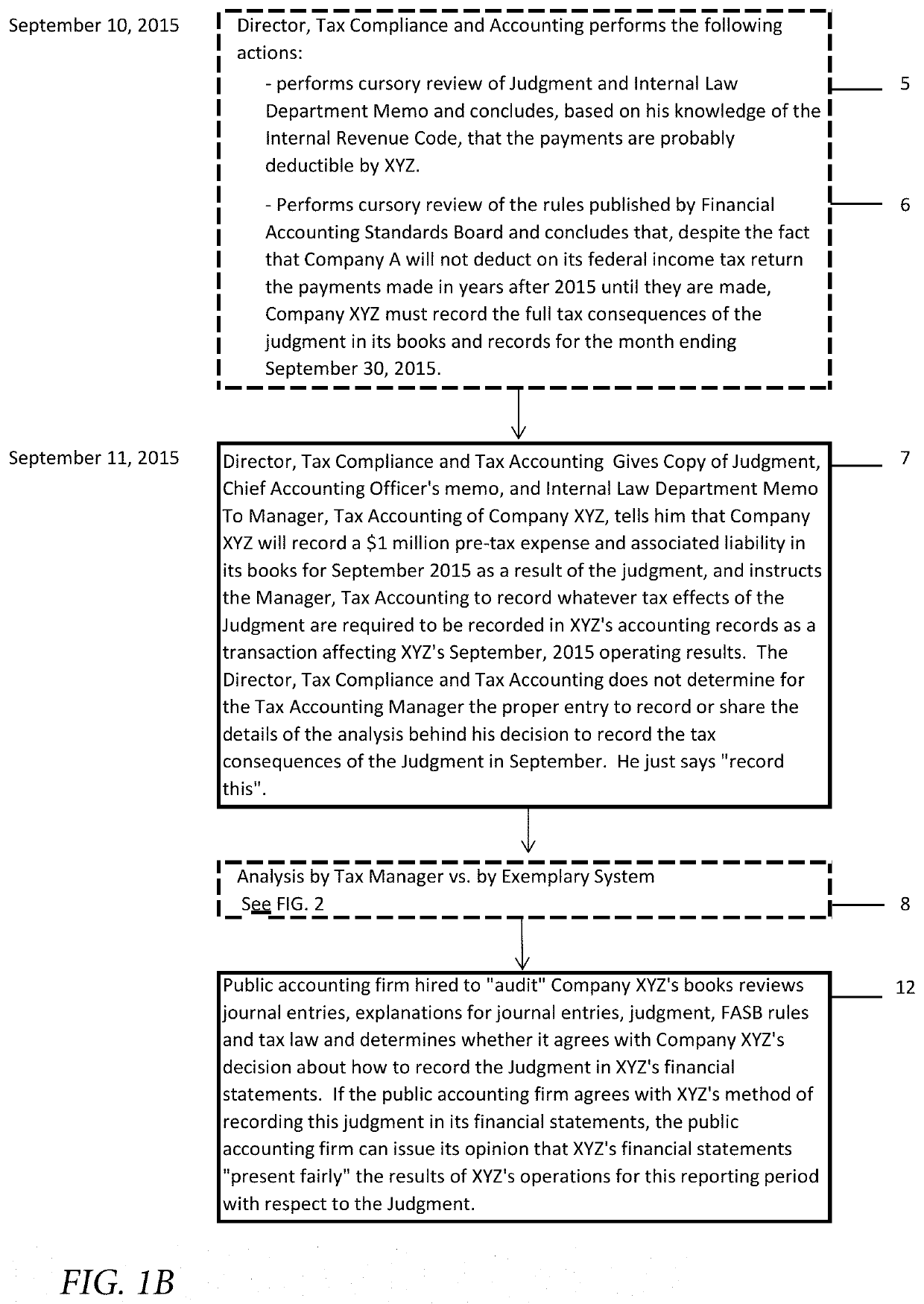
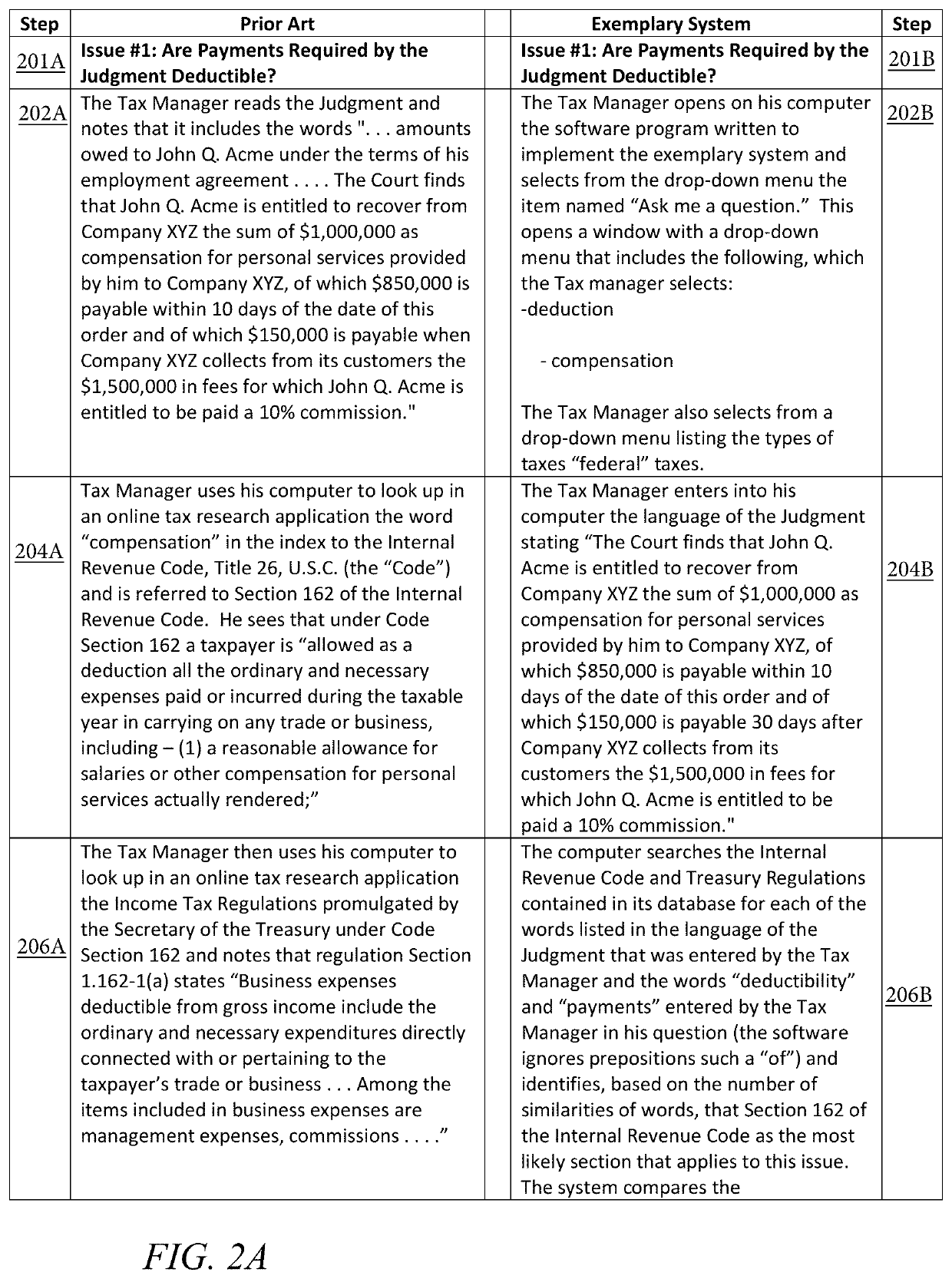
Determining correct answers to tax and accounting issues arising from business transactions and generating accounting entries to record those transactions using a computerized predicate logic implementation
ActiveUS10373268B1Facilitate actionSimple actionFinanceSpecial data processing applicationsLogic programmingIntermediate form
At least one pertinent authority, in ordinary English language, is paraphrased into a series of intermediate forms. The at least one pertinent authority is at least one of a tax authority and an accounting authority. The series of intermediate forms are rendered into a corresponding series of logical statements. The series of logical statements are encoded into relations in a logic programming language.
Owner:ORPHYS HENRY A
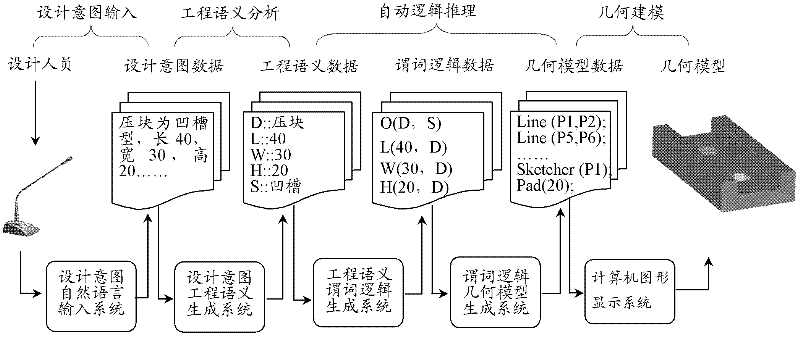
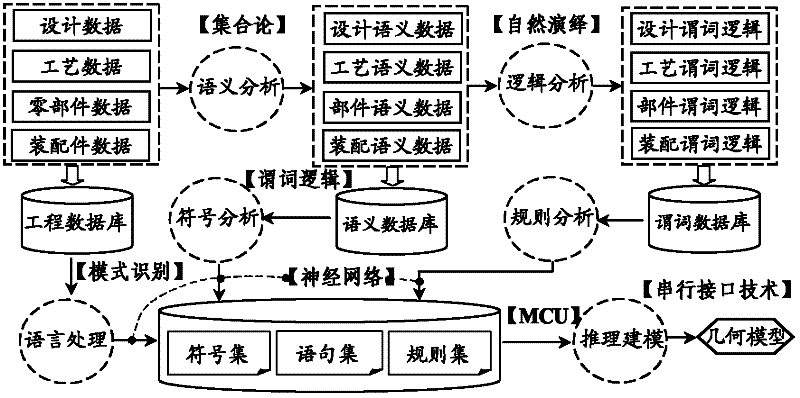
Design-idea-driven natural language geometric modeling method
InactiveCN102509351AReduce manual interventionImprove modeling efficiencySpecial data processing applications3D modellingPattern matchingGeometric modeling
The invention relates to a design-idea-driven natural language geometric modeling method which comprises the following steps: step 1: design idea analysis: inputting a design idea in a natural language mode according to the design task by a designer, thereby forming a design idea file stored in the form of binary data; step 2: engineering semantic analysis: analyzing a binary statement in the design idea file, and carrying out mode matching operation on the binary statement and a preset binary field in an engineering database to form an engineering semantic file; step 3: automatic logical reasoning: transforming the engineering semantic data generated in the step 2 into predicate logic data and geometric model data according to a predicate logic transformation rule; and step 4: geometric modeling. The whole modeling process can be automatically completed by the system, thereby reducing the manual intervention and enhancing the modeling efficiency.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Determining correct answers to tax and accounting issues arising from business transactions and generating accounting entries to record those transactions using a computerized logic implementation
ActiveUS11295393B1Easy searchSimple actionNatural language translationDigital data information retrievalEngineeringFinancial transaction
Pertinent natural language authority documents are translated into corresponding statements in a system of predicate logic which statements are encoded into relations in a programming language. The authority documents are indexed into an electronic database to facilitate subsequent searching. User-entered query terms and / or query terms derived from pertinent prose are obtained, specifying at least one of a tax problem and an accounting problem; based on same, the electronic database is searched to locate applicable authority(ies). A comparison and inference engine executing on at least one hardware processor is activated to apply applicable relations in the programming language to a problem ascertainable from the query, to obtain a conclusion by applying derivation rules in the system of predicate logic. The conclusion is presented to a decision maker.
Owner:ORPHYS HENRY A
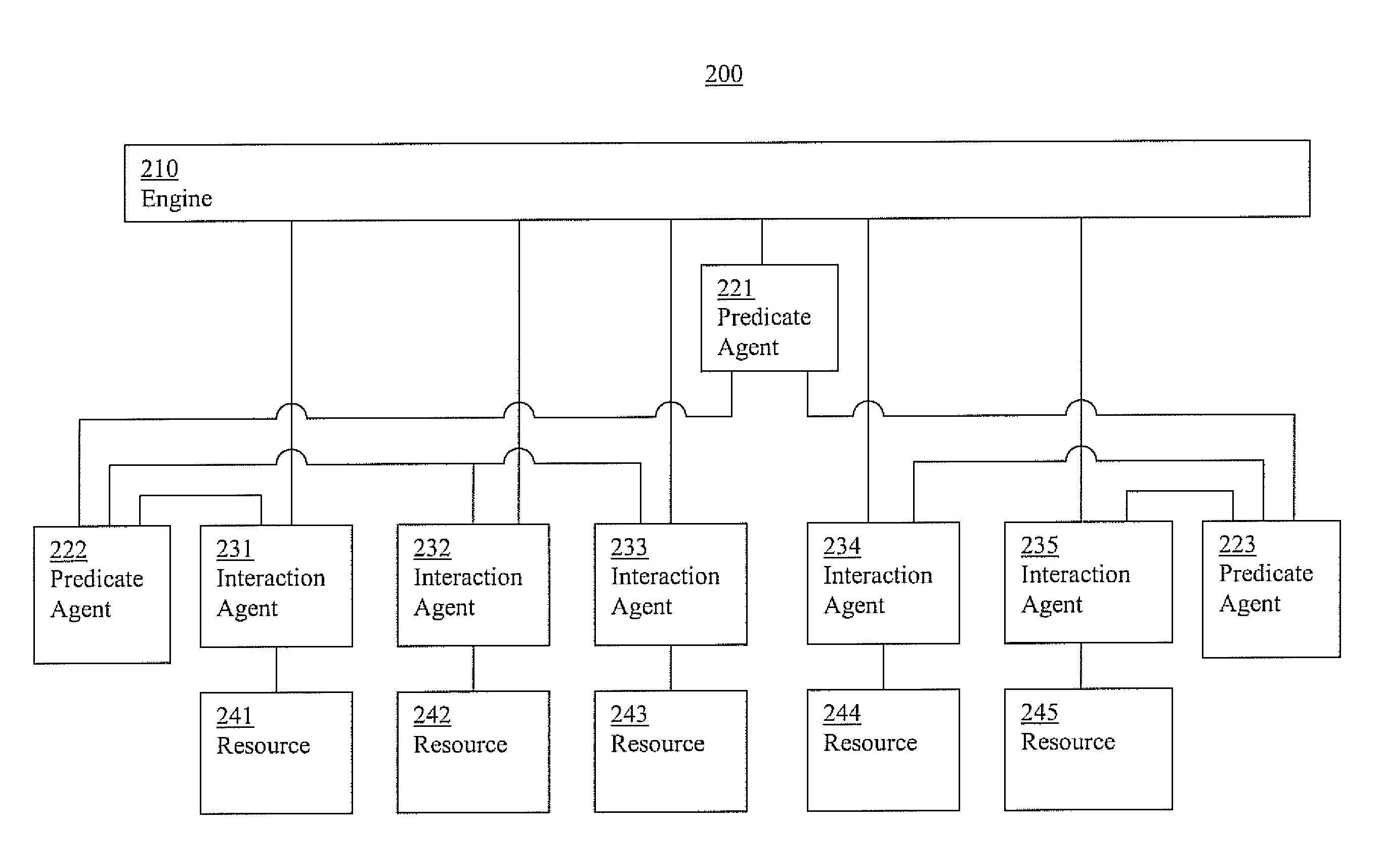
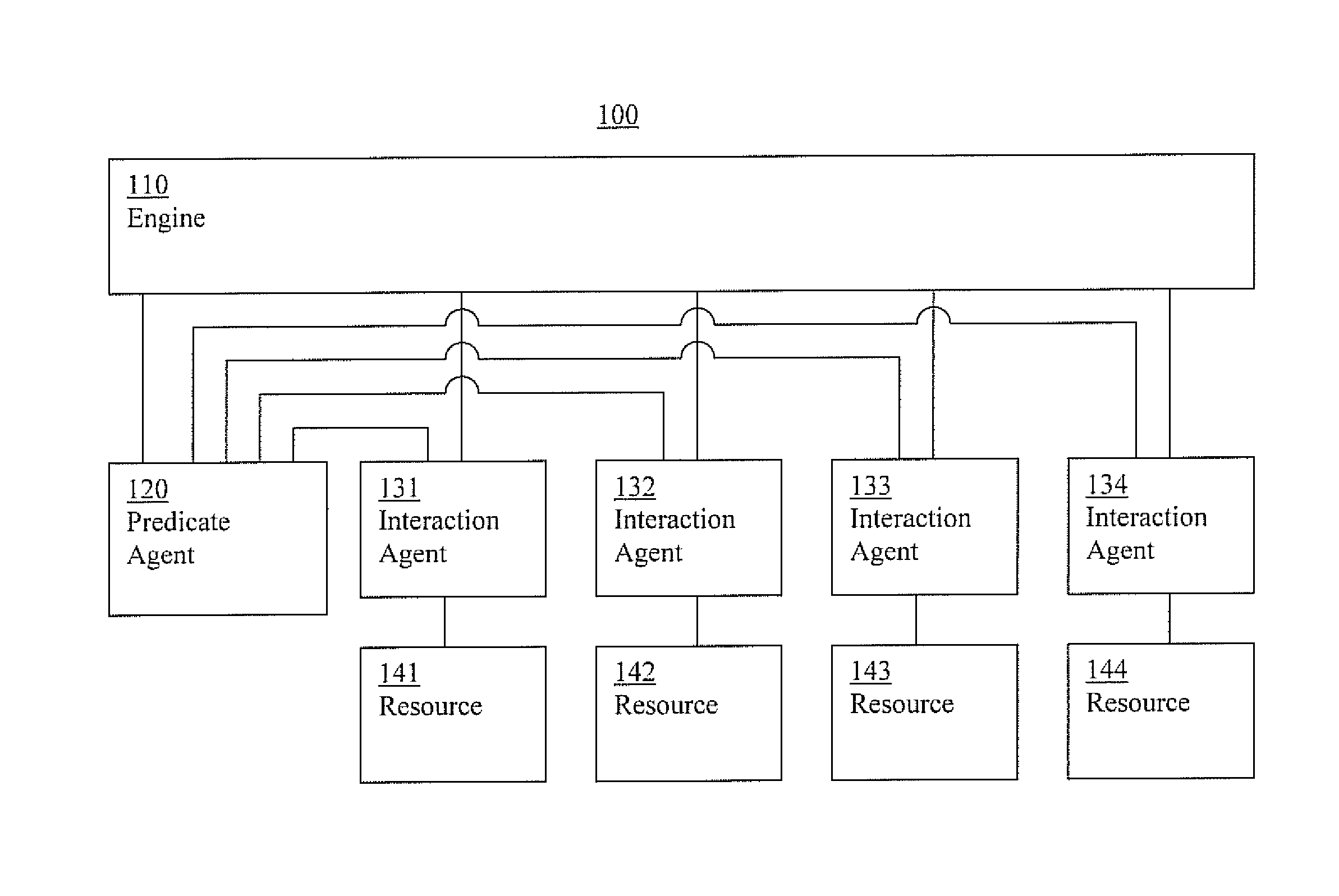
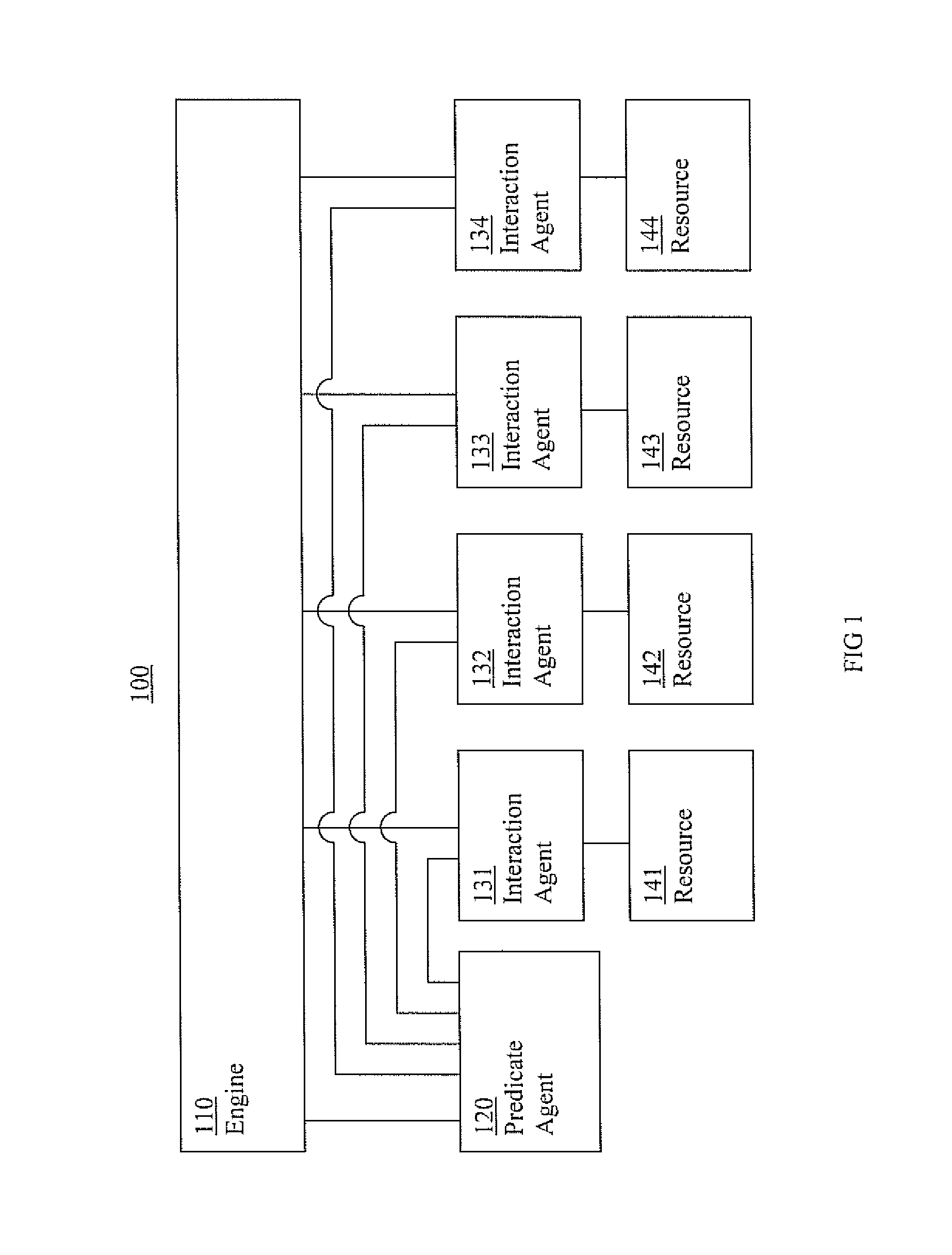
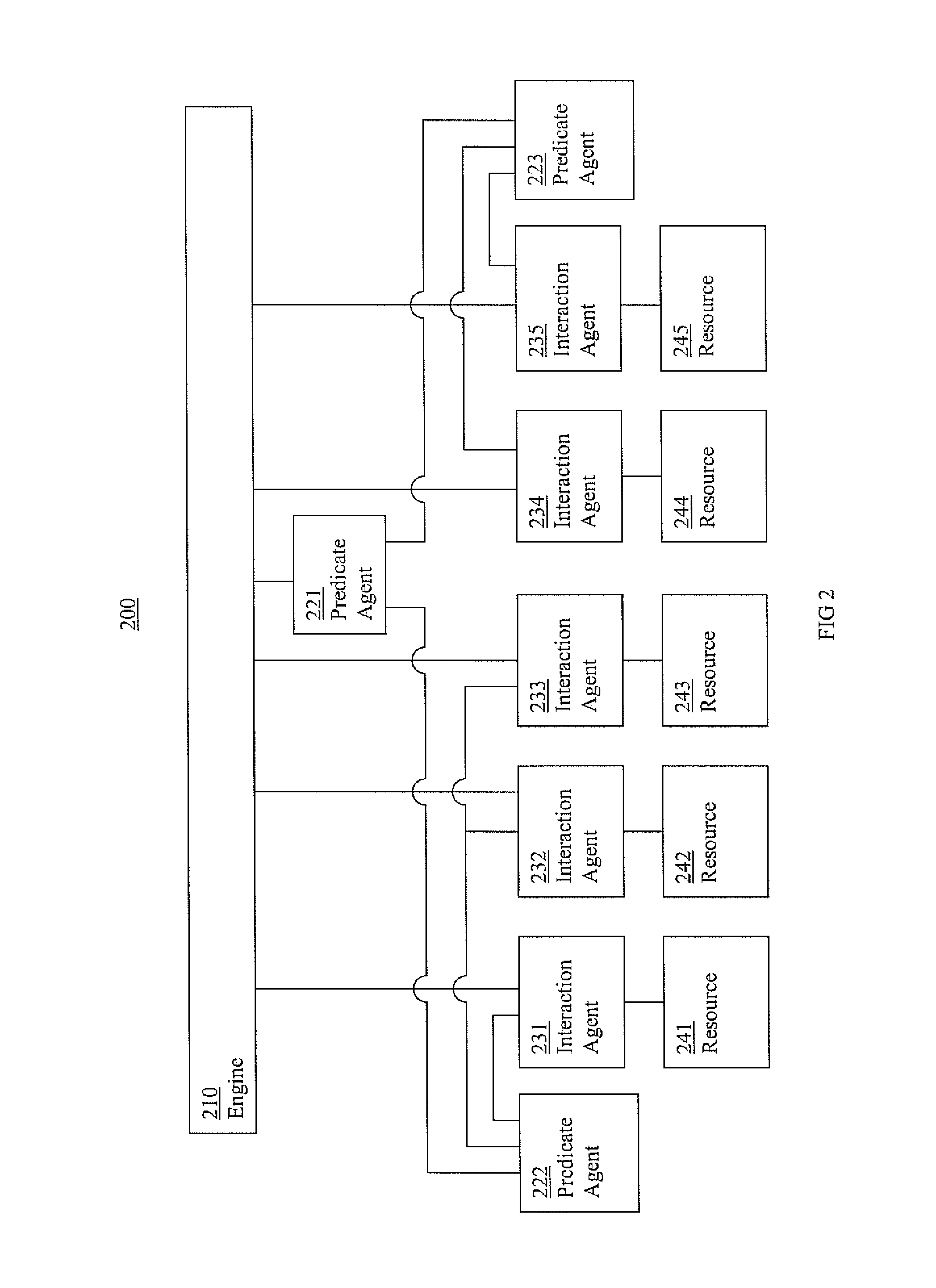
Cluster systems and methods
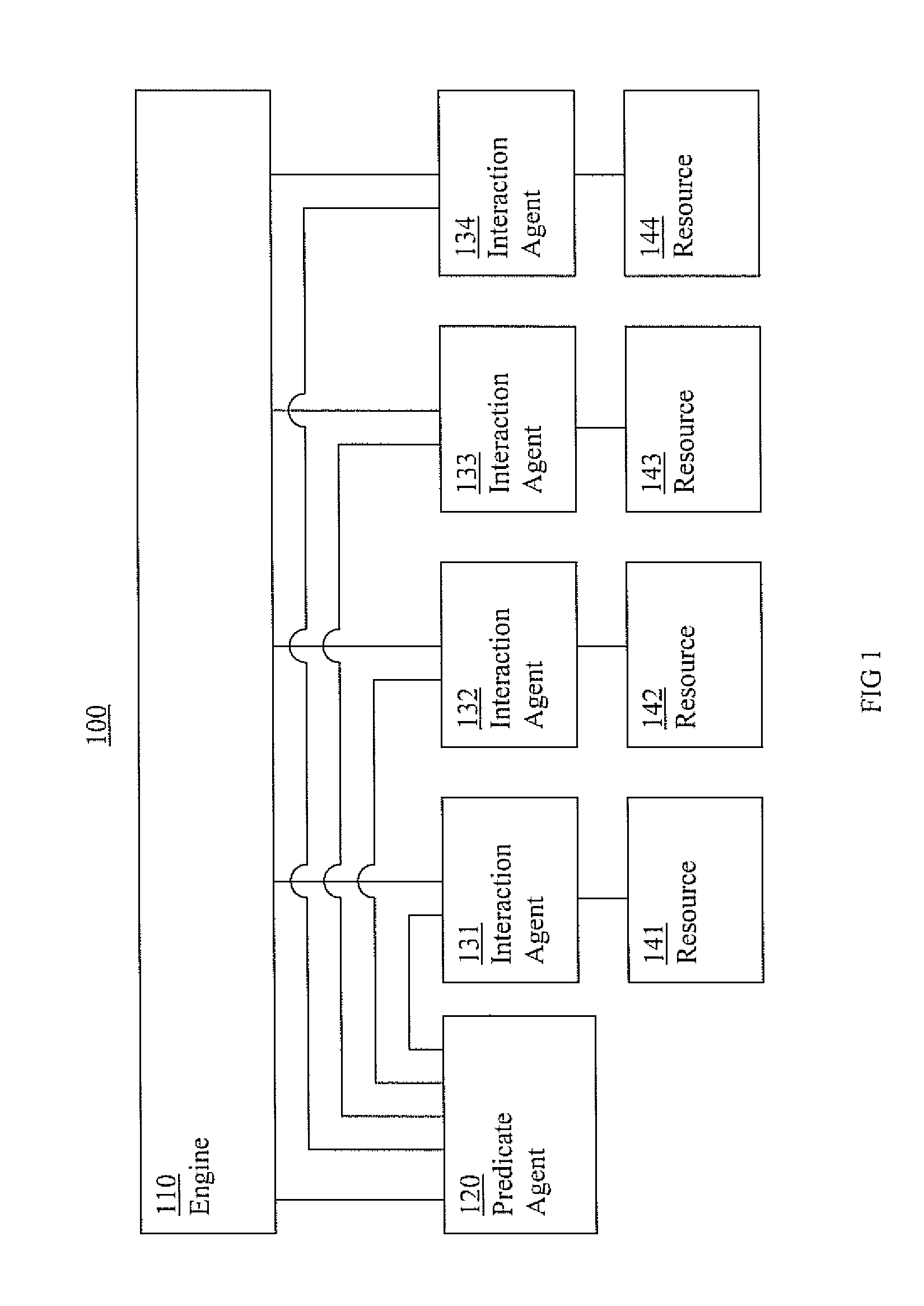
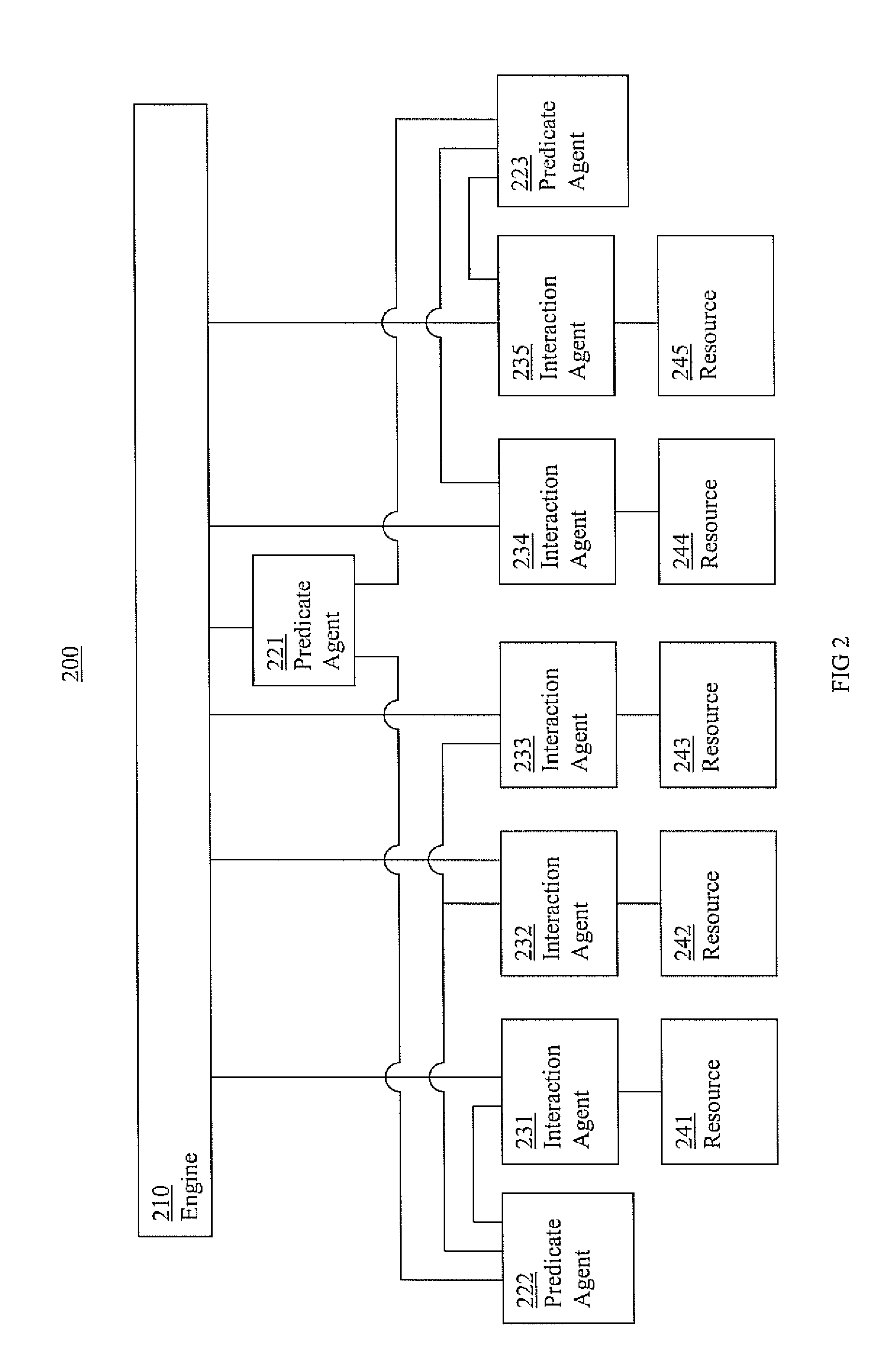
Information cluster systems and methods are presented. In one embodiment, a cluster method comprises: performing an engine process including issuing requests to bring a resource online, offline, and monitor the resources, wherein the engine process is performed by an engine; performing a resource interaction process including interacting with a resource and directing a resource to comply with the request from the engine process, wherein the resource interaction process is performed by a resource interaction agent; performing a predicate logic process including performing predicate logic operations to determine if a predicate logic condition associated with the resource is satisfied and forwarding an indication of the results of the predicate logic operations to the engine process, wherein the predicate logic process is performed by a predicate logic agent that is separate from the engine performing the engine process.
Owner:VERITAS TECH
Control instruction classification method based on semantic network
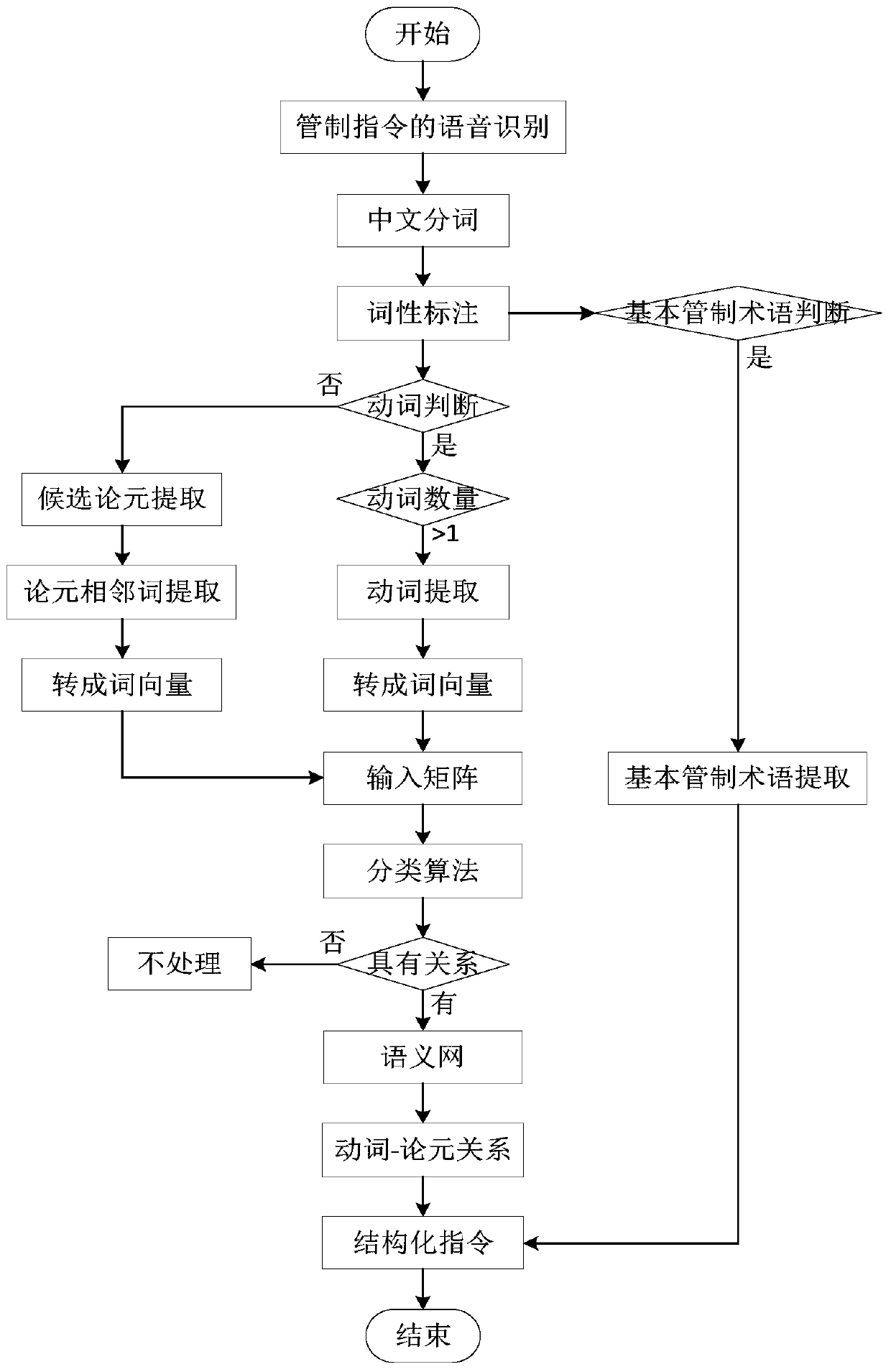
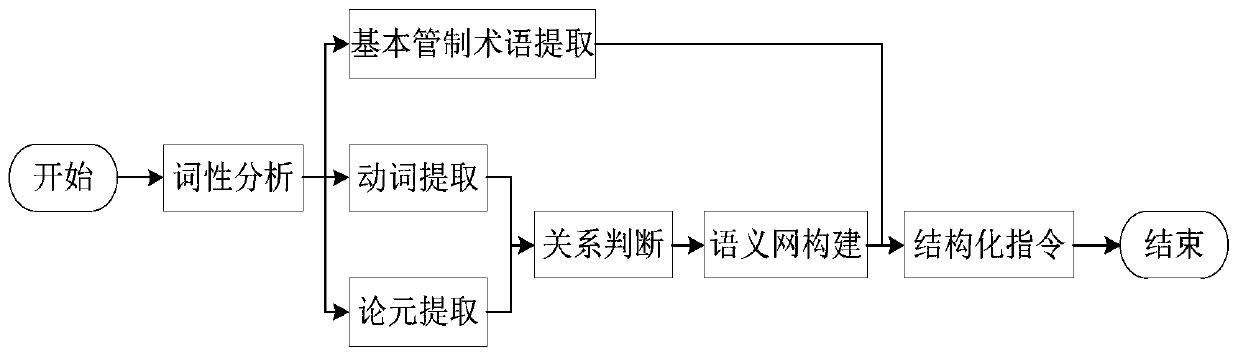
ActiveCN110232121AEasy to parseGuaranteed to workData processing applicationsSemantic analysisClassification methodsReasoning system
The invention discloses a control instruction classification method based on a semantic network, and aims to construct a computer readable structured control instruction and provide a basis for automatic processing of the control instruction, and form a predicate logic structure to provide a basis for realizing a knowledge reasoning system. By processing an unstructured control instruction, the method can realize the following auxiliary functions: extracting information carried by a basic control term appearing in the control instruction; extracting action, state and other information of the aircraft and performing analog simulation; and forming computer readable structured information to provide data for knowledge reasoning. According to the method, aiming at the condition that a complexcontrol instruction comprises a plurality of control intentions, whether different arguments in the control instruction are associated with verbs of the different control intentions or not is judged through a deep neural network, and the associated verbs and argument words are brought into a semantic network for semantic role marking.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
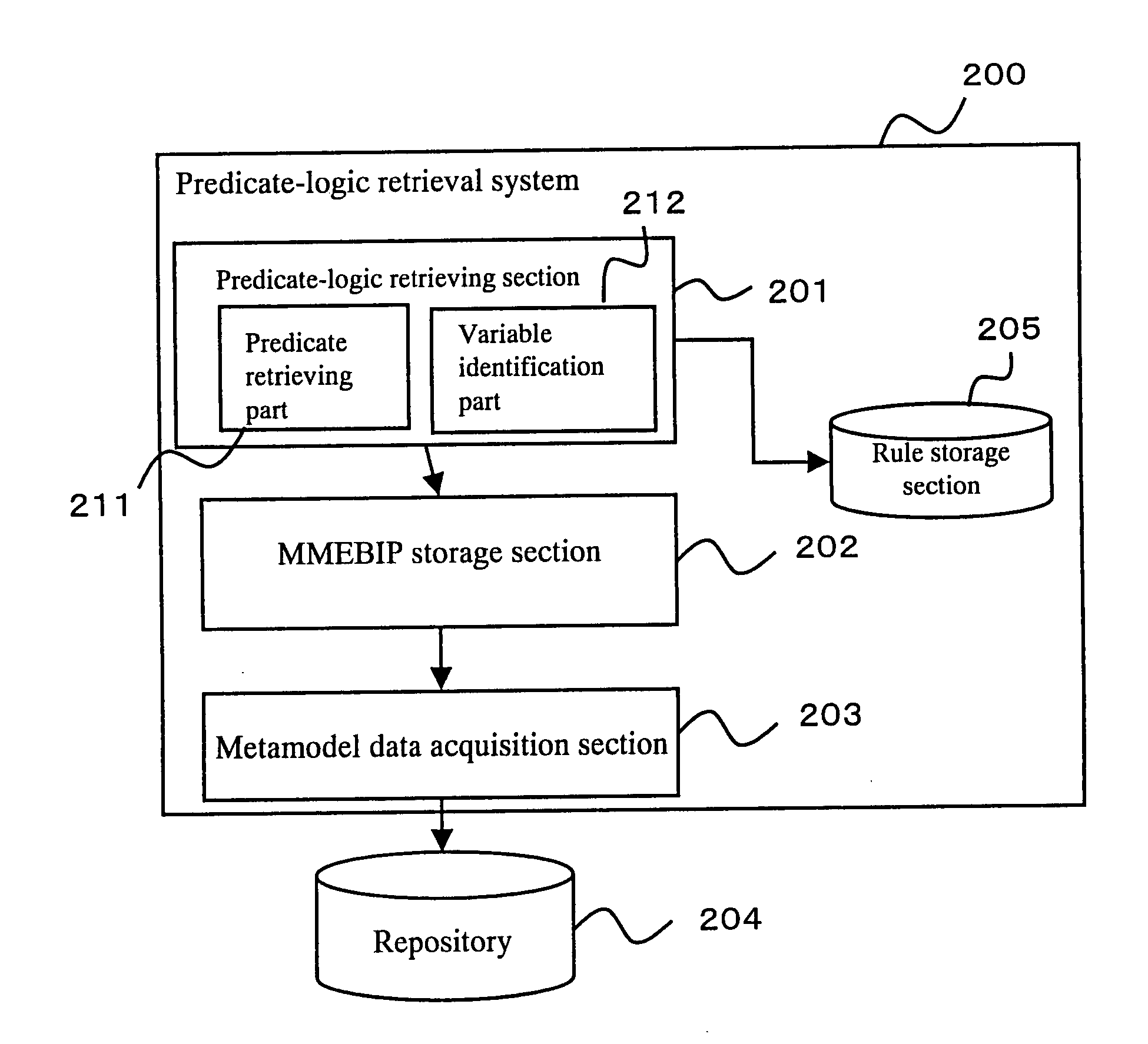
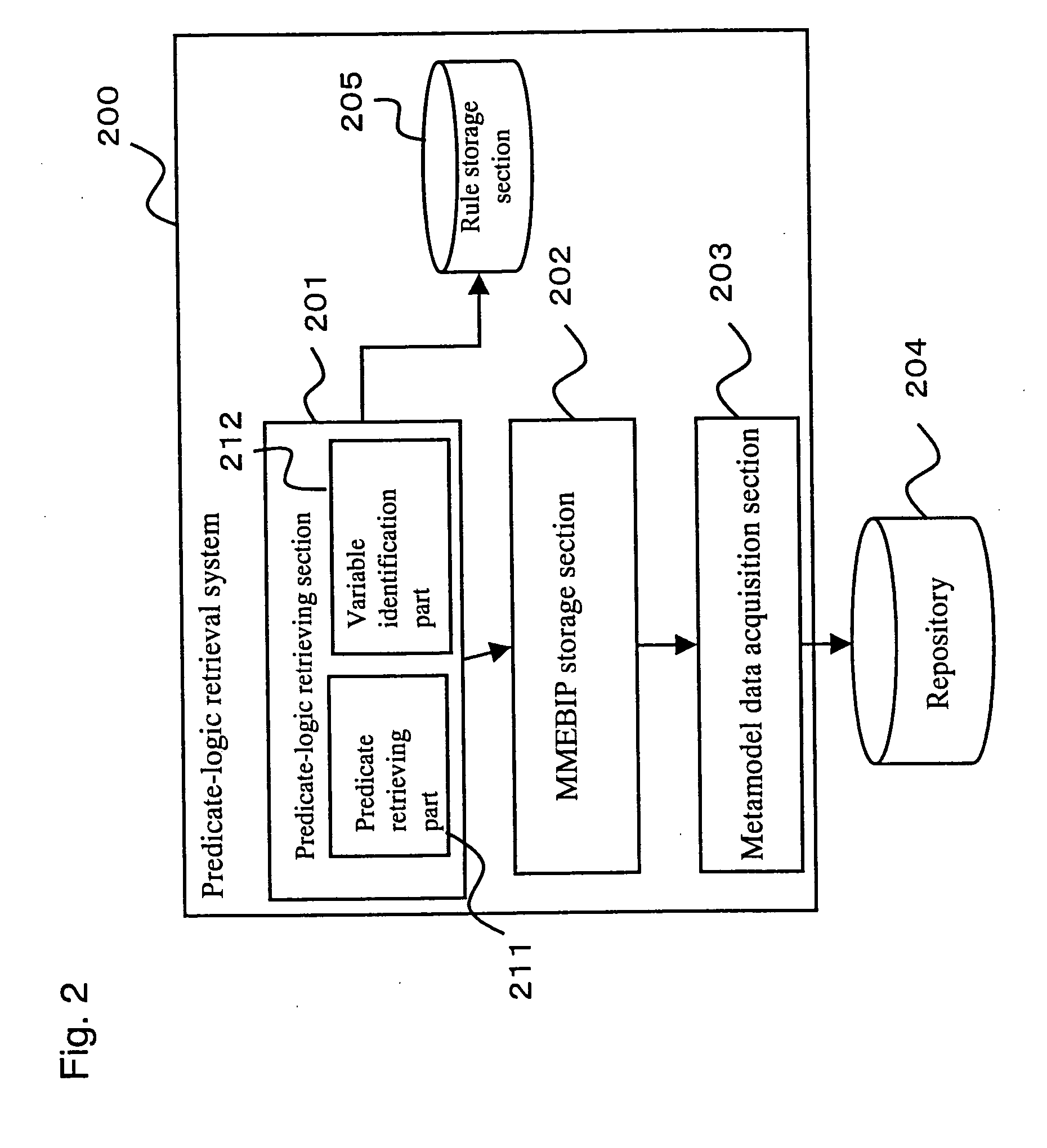
Predicate-logic retrieval system
InactiveUS20070022108A1Complicates data storageDigital data information retrievalSpecial data processing applicationsDatabasePredicate logic
A predicate-logic retrieval system includes a predicate-logic retrieving section for receiving a predicate query and a metamodel-element built-in predicate (MMEBIP) storage section storing therein MMBEIPs and get-functions in association. If a predicate query includes a MMEBIP, the predicate-logic retrieval system retrieves a get-function from the MMBIP storage section, uses the get-function to retrieve predicate data from a repository storing therein data in a metamodel format, and executes variable identification for the predicate thus retrieved.
Owner:NEC CORP
Cloud service functional attribute filtering method based on domain ontology
The invention provides a cloud service functional attribute filtering method based on domain ontology, relating to the field of service-oriented collaboration. The method includes the following steps:matching a category of a service requested by a cloud service requester with a category of a specific cloud service, and determining whether the cloud service makes all predicate logics included in the cloud service request true, if true, performing filtering on value attributes, calculating the set similarity and comprehensive similarity of input / output ontology, and then adopting a relaxation matching strategy to filter the cloud services. According to the scheme of the invention, an ontology technology is applied to the cloud collaboration, the cloud service functional attribute filteringmethod based on the domain ontology is proposed, and compared with a traditional UDDI-based service discovery mechanism, semantic information described by cloud service functions are fully used, so that the cloud services required by users can be discovered more accurately.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Cluster systems and methods
Information cluster systems and methods are presented. In one embodiment, a cluster method comprises: performing an engine process including issuing requests to bring a resource online, offline, and monitor the resources, wherein the engine process is performed by an engine; performing a resource interaction process including interacting with a resource and directing a resource to comply with the request from the engine process, wherein the resource interaction process is performed by a resource interaction agent; performing a predicate logic process including performing predicate logic operations to determine if a predicate logic condition associated with the resource is satisfied and forwarding an indication of the results of the predicate logic operations to the engine process, wherein the predicate logic process is performed by a predicate logic agent that is separate from the engine performing the engine process.
Owner:VERITAS TECH
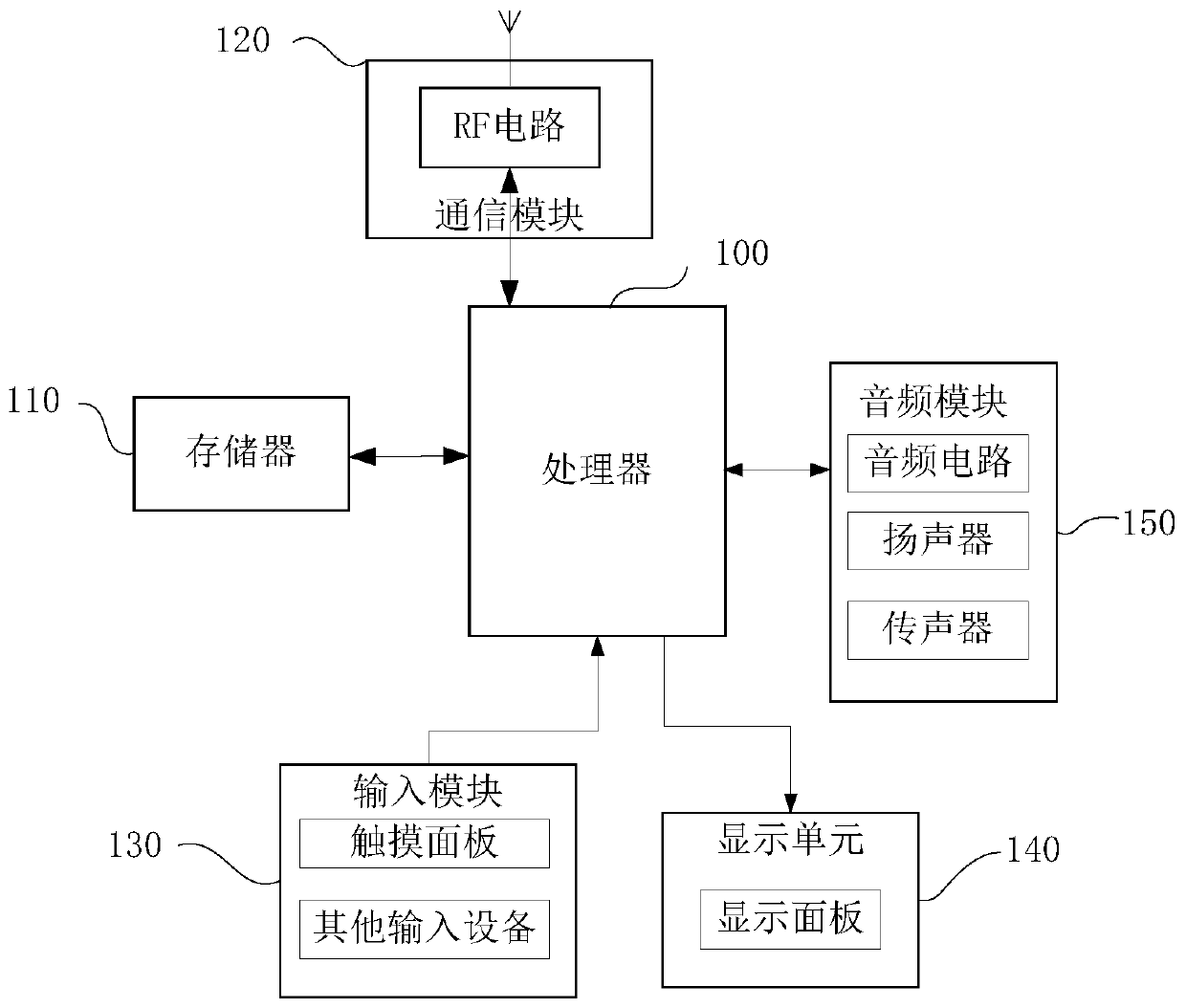
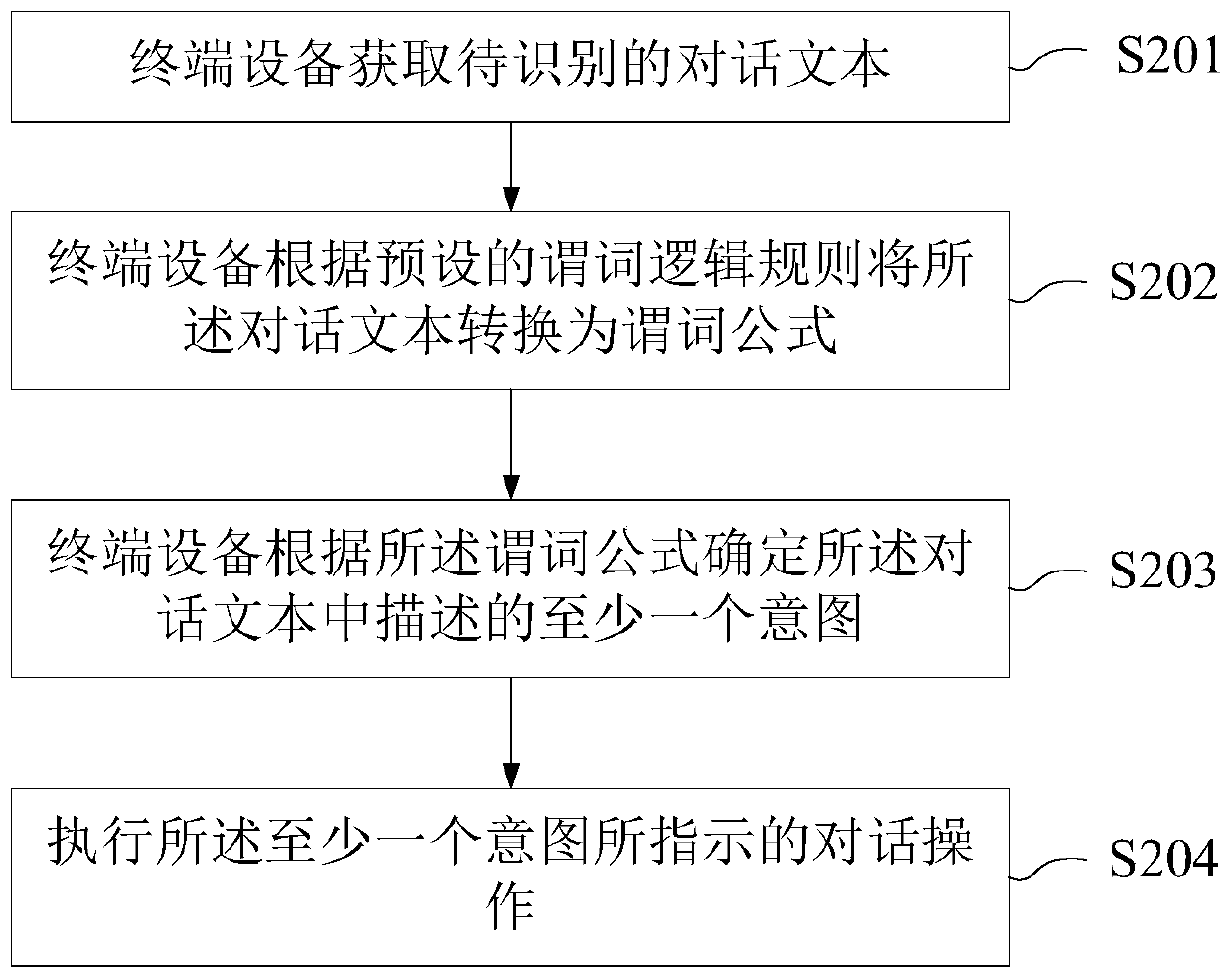
Dialogue response method and device
InactiveCN110888969AReduce failure rateAccurate descriptionDigital data information retrievalSemantic analysisTransformation of textTheoretical computer science
The invention provides a dialogue response method and device, and relates to the field of terminal artificial intelligence (AI), in particular to the field of voice recognition. The method comprises the steps of obtaining a to-be-recognized dialogue text; converting the dialogue text into a predicate formula according to a preset predicate logic rule, wherein the predicate formula is used for describing semantics of the dialogue text; determining at least one intention described in the dialogue text according to the predicate formula; and executing a dialogue operation indicated by the at least one intention.
Owner:HUAWEI TECH CO LTD
Predicate logic-based standard reconstruction representation method
ActiveCN108416124ASolve storage problemsResolve identifiabilityGeometric CADDesign optimisation/simulationDesign standardSymbolic processing
The invention discloses a predicate logic-based standard reconstruction representation method. The method specifically comprises the following steps of 1, segmenting a standard entry into multiple clauses; 2, performing normalization processing on the clauses obtained in the step 1; and 3, performing symbolic processing on clause components processed in the step 2, and storing a processing resultin a computer. The Chinese building standard entry can be subjected to digital expression, so that the problems of computer storage and identification of design standards at present are solved.
Owner:XIAN UNIV OF TECH
Automatic malicious code behavior analysis system
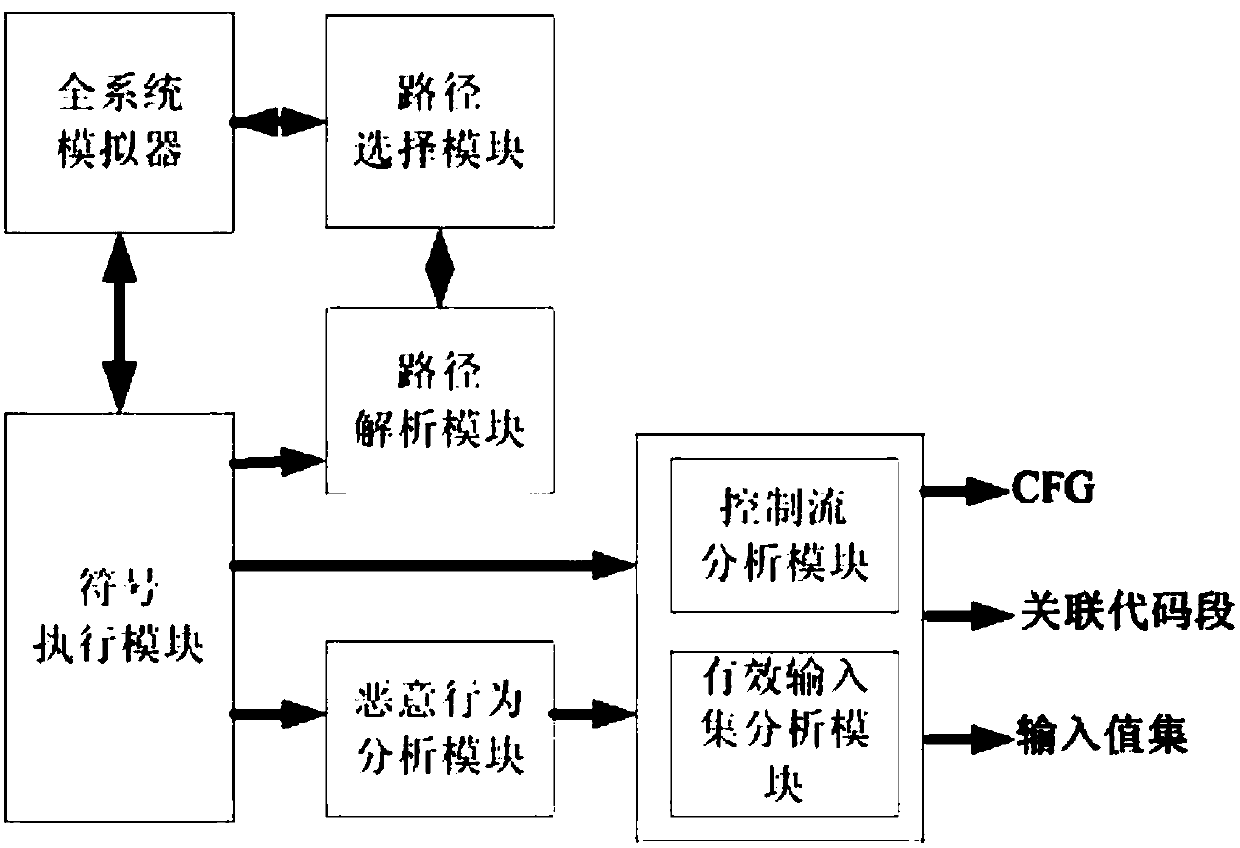
InactiveCN109840416AImprove analysis efficiencyUnderstanding Attack CapabilitiesPlatform integrity maintainanceValue setPriority setting
The invention relates to an automatic analysis system for malicious code behaviors. The system comprises a full-system simulator, a symbol execution module, a path analysis module, a path selection module, a malicious behavior analysis module, a control flow analysis module and an effective input set analysis module, wherein the symbol execution module finds a branch dependent on a symbol variablein a binary malicious code and then generates path judgment predicate logic. The path analysis module analyzes the path judgment predicate logic, generates a new execution path and adds the new execution path into the path storage pool; the path selection module carries out priority setting on paths in the path storage pool; the control flow analysis module generates and continuously updates a control flow graph CFG; the malicious behavior analysis module extracts malicious behavior characteristics and structural characteristics realized by the associated code segment; the effective input setanalysis module finds out an input value set which enables the malicious behavior program to execute according to a specific path. The invention provides an efficient malicious code behavior automatic analysis system.
Owner:西安玖诚玖谊实业有限公司
Determining correct answers to tax and accounting issues arising from business transactions and generating accounting entries to record those transactions using a computerized predicate logic implementation
ActiveUS10706480B1Easy to find laterFacilitate actionNatural language translationDigital data information retrievalEngineeringFinancial transaction
Pertinent natural language authority documents are translated into corresponding statements in a system of predicate logic which statements are encoded into relations in a programming language. The authority documents are indexed into an electronic database to facilitate subsequent searching. User-entered query terms and / or query terms derived from pertinent prose are obtained, specifying at least one of a tax problem and an accounting problem; based on same, the electronic database is searched to locate applicable authority(ies). A comparison and inference engine executing on at least one hardware processor is activated to apply applicable relations in the programming language to a problem ascertainable from the query, to obtain a conclusion by applying derivation rules in the system of predicate logic. The conclusion is presented to a decision maker.
Owner:ORPHYS HENRY A
Active network safety loophole detector
InactiveCN100463461CImprove confidentialityReduce trafficData switching networksAnalysis dataData center
This invention discloses an active network safety leakage detector composed of three control modules of a detect agent, a data center and an analysis control stand, among which, the detection agent collection system matches the information and upwards it to the data center, the analysis control stand analyzes information stored in the data center to identify the host leakage by the OVAL leakage definition and carry out the associate analysis of attack / leakage by the predicate logic theory to find out the safety problem brought with the leakage combination to display potential attack paths in sight.
Owner:XI AN JIAOTONG UNIV
Verification system, verification method, and recording medium for storing verification program
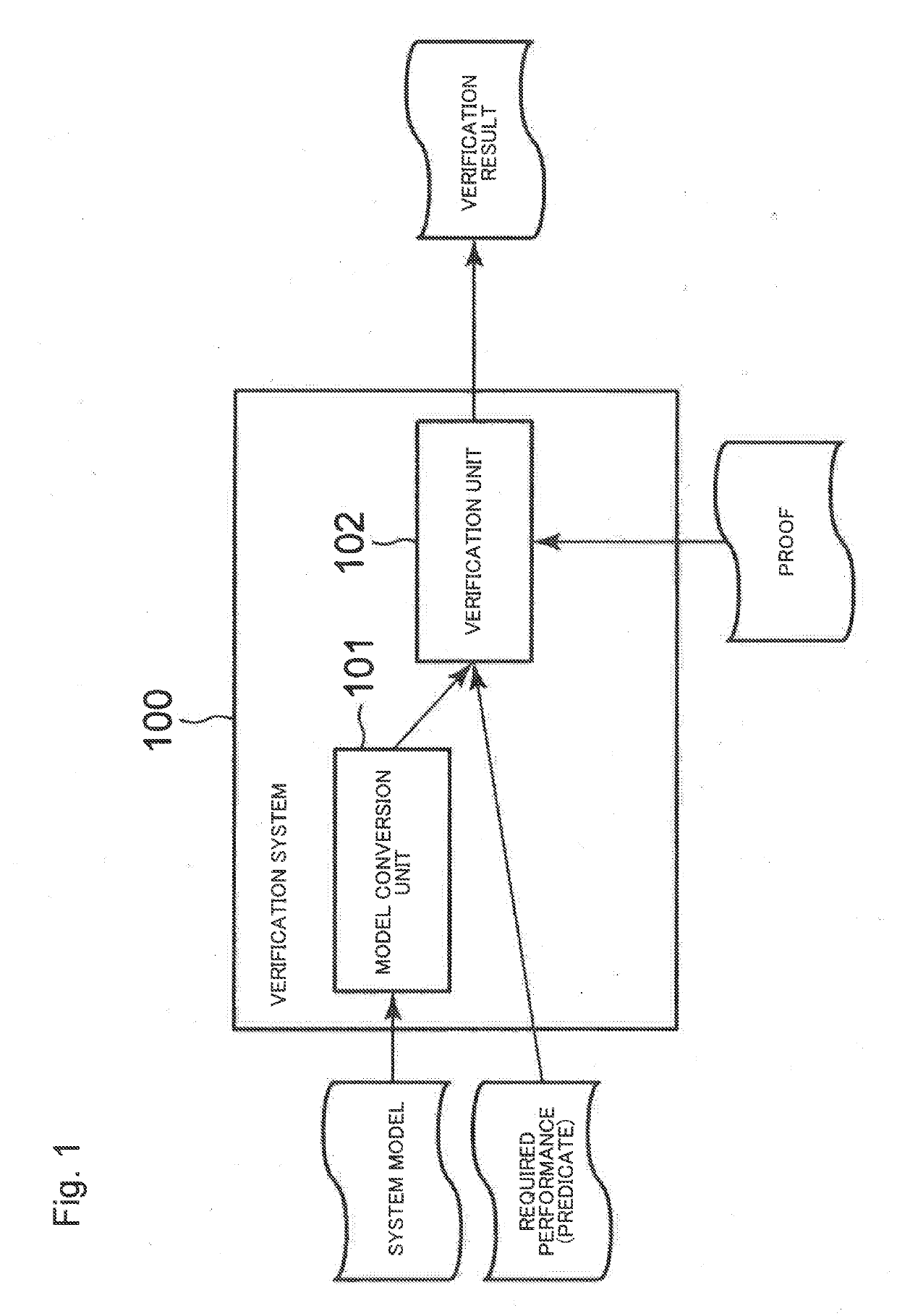
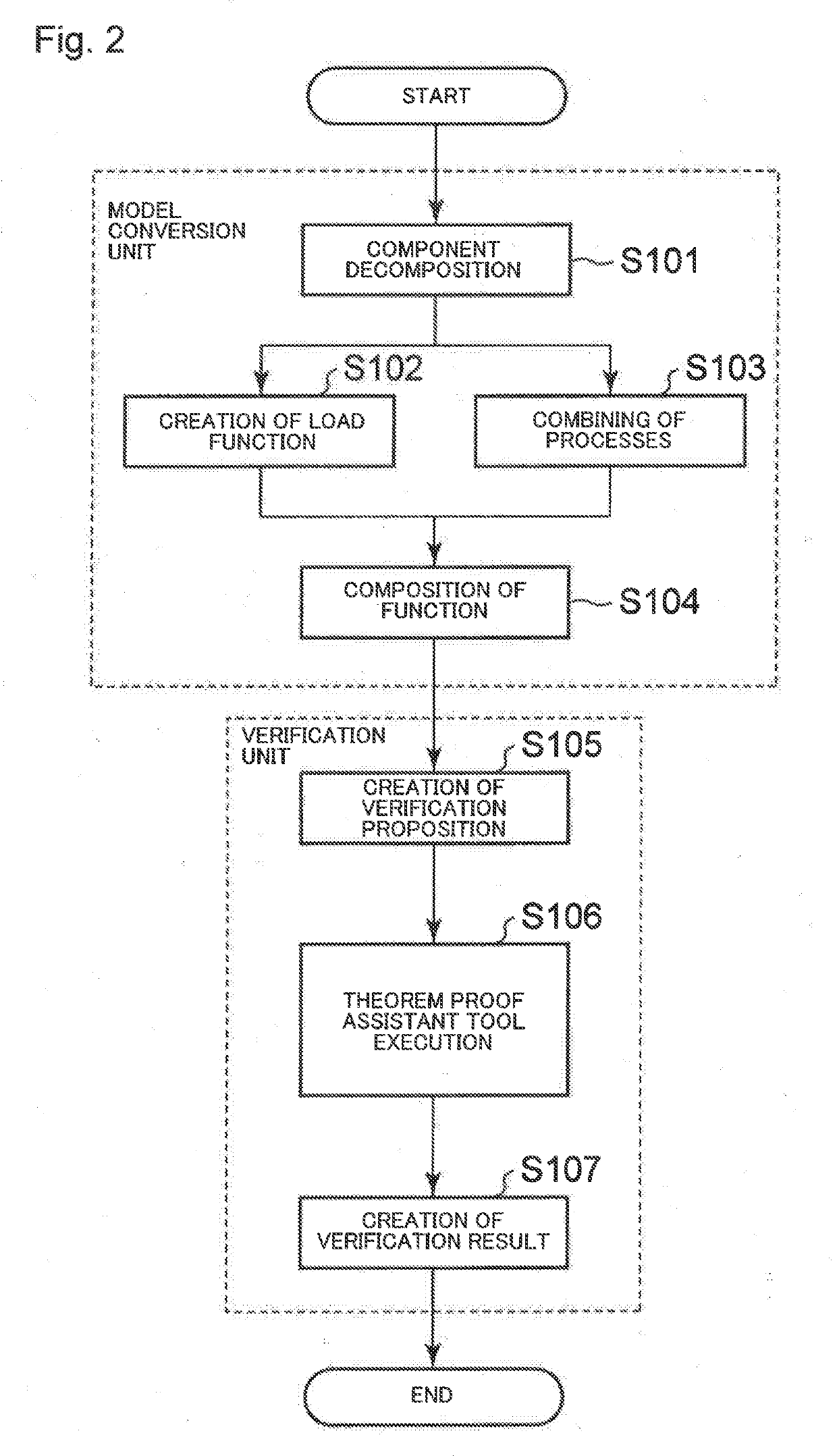
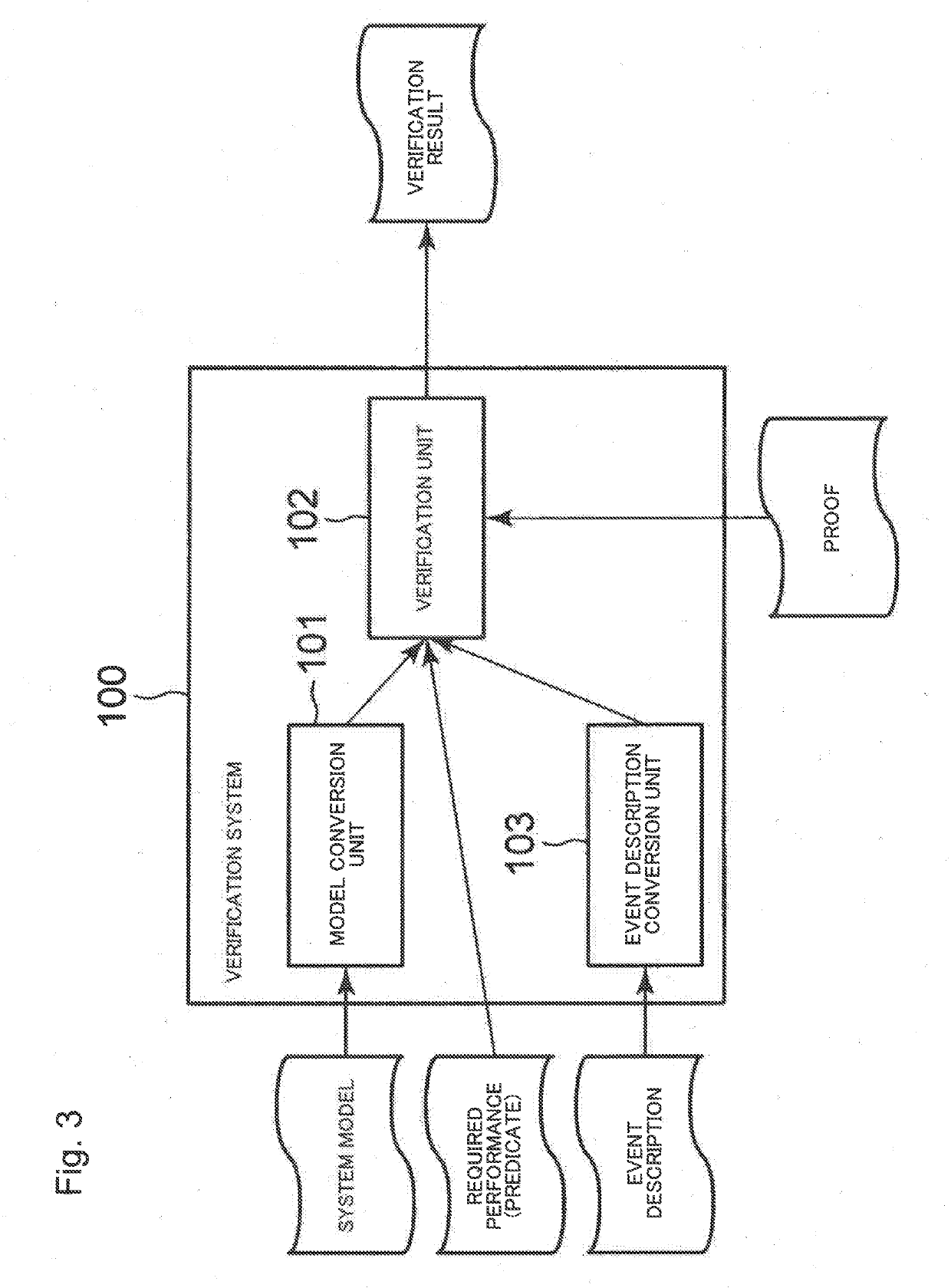
InactiveUS20190171956A1Guaranteed system performanceGuaranteed performanceMathematical modelsHardware monitoringMathematical modelValidation methods
A verification system includes at least one memory configured to store instructions; and at least one processor configured to execute the instructions to: receive, as input, a mathematical model obtained by converting a model indicating a configuration of a test object system into a predicate in predicate logic and create a proposition indicating that the test object system satisfies a performance requirement represented by the predicate; and verify whether or not a proof of the proposition having been created is true.
Owner:NEC CORP
Method and device for generating knowledge base in target domain and answering questions
ActiveCN111538844BNatural language data processingSpecial data processing applicationsEvent triggerTheoretical computer science
This application discloses a method and device for generating a knowledge base in the target field and answering questions. According to the knowledge type of the target field knowledge, the application determines the concept map, the event map and the predicate logic formula of the target field knowledge; and then generates the target field knowledge base. The concept graph is used to represent the static relationship between concept words; the event graph is used to represent the order of events and the relationship between events; the predicate logic formula is used to represent the business rules in the target domain knowledge. The problem-solving method includes: determining the M events triggered by the N word-segment phrases in the problem from the reasoning map, and determining the slots of the M event slots according to the K word-segment phrases matching the concept map in the N word-segment phrases value; according to the M events and the slot values of the slots of the M events, the predicate logic formula corresponding to the query object of the question is calculated; and then the answer to the question is determined.
Owner:HUAWEI TECH CO LTD
Semantic solidification and derivation method based on public predicate logic
PendingCN114372471AGuaranteed uptimeGood spreadability of multiplexed setsSemantic analysisText database indexingFeature setAlgorithm
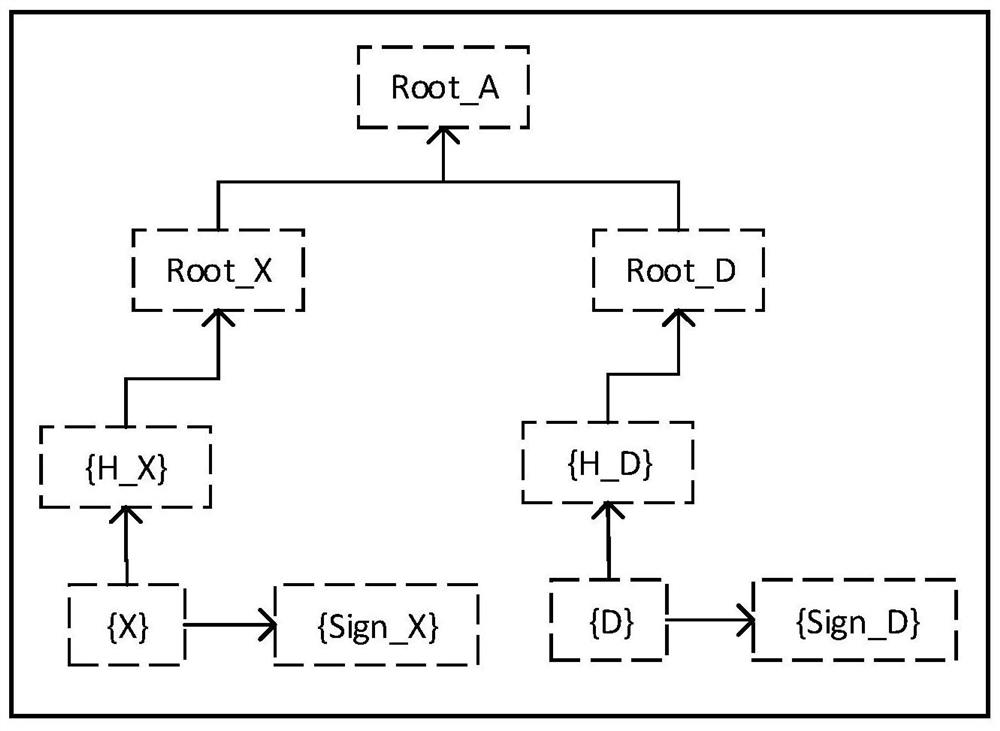
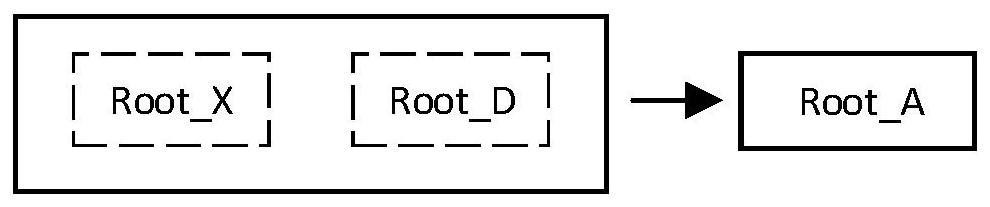
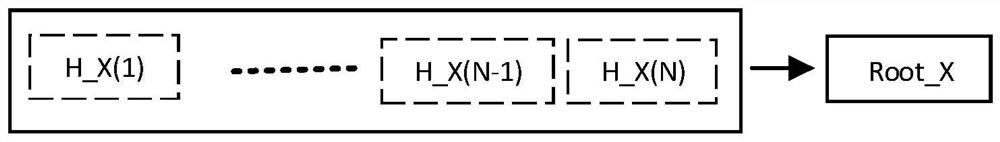
The invention discloses a semantic solidification and derivation method based on public predicate logic, which comprises the following steps of: 1) selecting or designing a semantic unit X for an automaton A to form a semantic unit set {X} and a corresponding data state set {D}; 2) performing digital feature acquisition on each semantic unit in {X} and calculating an index value of each semantic unit to obtain a semantic unit index set {HX} and a digital feature set {SignX}; performing digital feature acquisition on each data state in the data state {D} and calculating an index value of each data state to obtain a data state index set {HD} and a digital feature set {SignD}; (3) respectively taking {HX} and {HD} as input to carry out a calculation mode so as to obtain a root RootA of the automaton A; and (4) the A'starts the automaton A through the RootA, all semantic units and data states of the automaton A are obtained for driving, and therefore the requirement for the automaton A is obtained.
Owner:SUZHOU SUPERBLOCK CHAIN INFORMATION SCI & TECH CO LTD
Method and device for discovering link layer network topology
The invention discloses a method and a device for discovering link layer network topology. The method comprises the following steps: acquiring an address forwarding table (AFT table) of the network node by a pinging link layer network node; deriving the connection relation between network nodes by a predicate logic inference algorithm according to connection reasoning technology and repairing incomplete inverse root AFT data to acquire a complete AFT table; and utilizing a spanning tree protocol algorithm to calculate each network node according to the complete AFT table acquired according tothe predicate logic inference algorithm so as to discover a physical network topology structure of the link layer. The method provided by the invention combined with the predicate logic inference algorithm of the connection reasoning technology and a spanning tree protocol-based topology discovery algorithm can calculate the network node information effectively under the condition that the AFT data is incomplete, thereby overcoming the shortages of the prior method for discovering the link layer network topology and improving the probability of acquiring the physical network topology.
Owner:BEIJING VENUS INFORMATION TECH +1
A Method for Multi-robot Cooperative Exploration
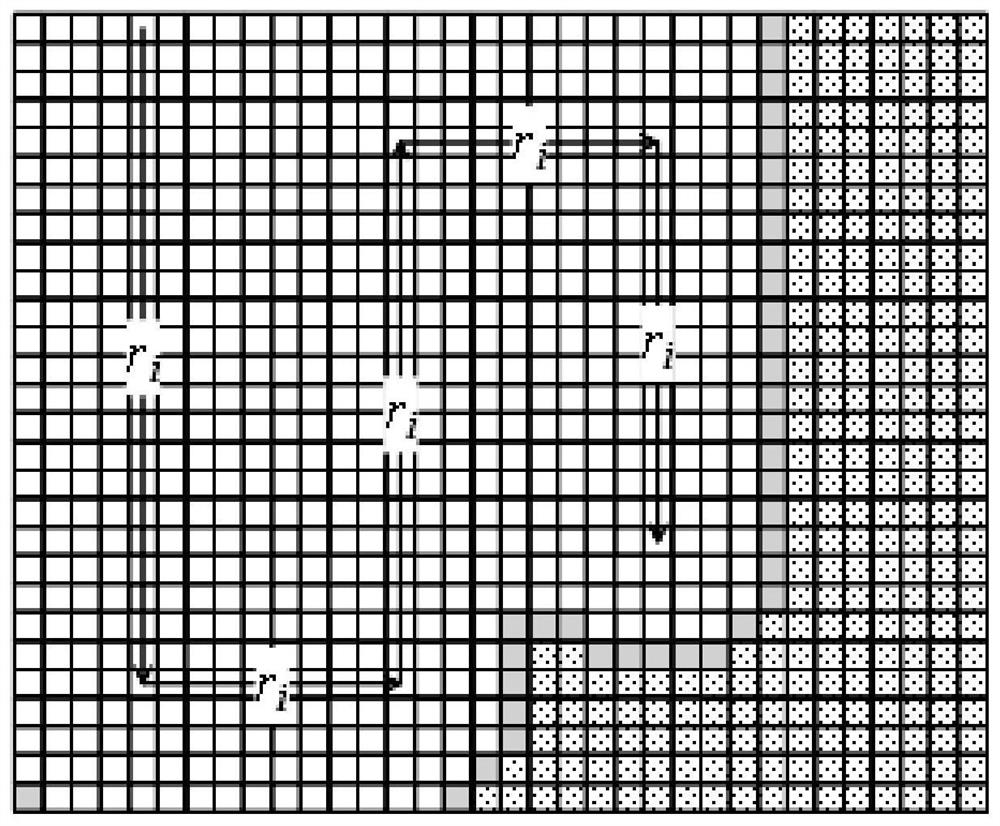
InactiveCN108958202BImprove coordinationSimplify Collaborative ComputingTotal factory controlProgramme total factory controlRobotic systemsMultirobot systems
The invention discloses a multi-robot coordinated exploration method, and relates to the multi-intelligent robot system technical field; the method comprises the following steps: a robot system comprises at least two robots, employs a zig-zag type mobile track to scan a to-be-explored area according to a predicate logical reasoning rule, and builds an environment model according to the scan information. The method uses the logical reasoning rule to realize coordinated control of the robots, uses the zig-zag type mobile track auxiliary direction for realizing exploration, and uses the main direction for selecting an exploration task and coordinating the robots, thus converting coordination in the 2D space into coordination in the one-dimensional space; the robot system is divided into a plurality of subsystems, thus using less rules to realize a bigger scale of multi-robot system coordination, simplifying the coordination work computing, and reducing the field coordination strategy modification difficulty.
Owner:QIQIHAR UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com