Active network safety loophole detector
A network security, active technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problem of not well integrated visual display, shorten the detection running time, reduce the false alarm rate, detection accuracy high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be described in further detail below in conjunction with the accompanying drawings.
[0040] 1. The composition of the security vulnerability detector AVCS
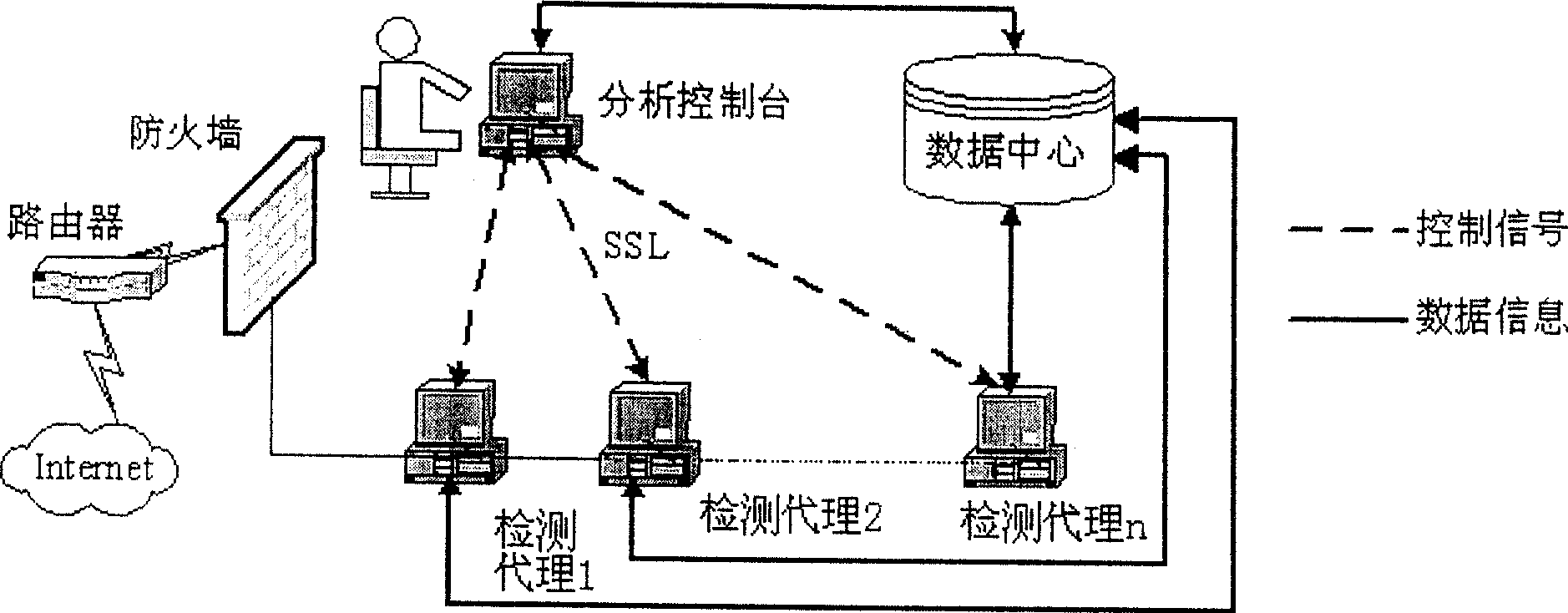
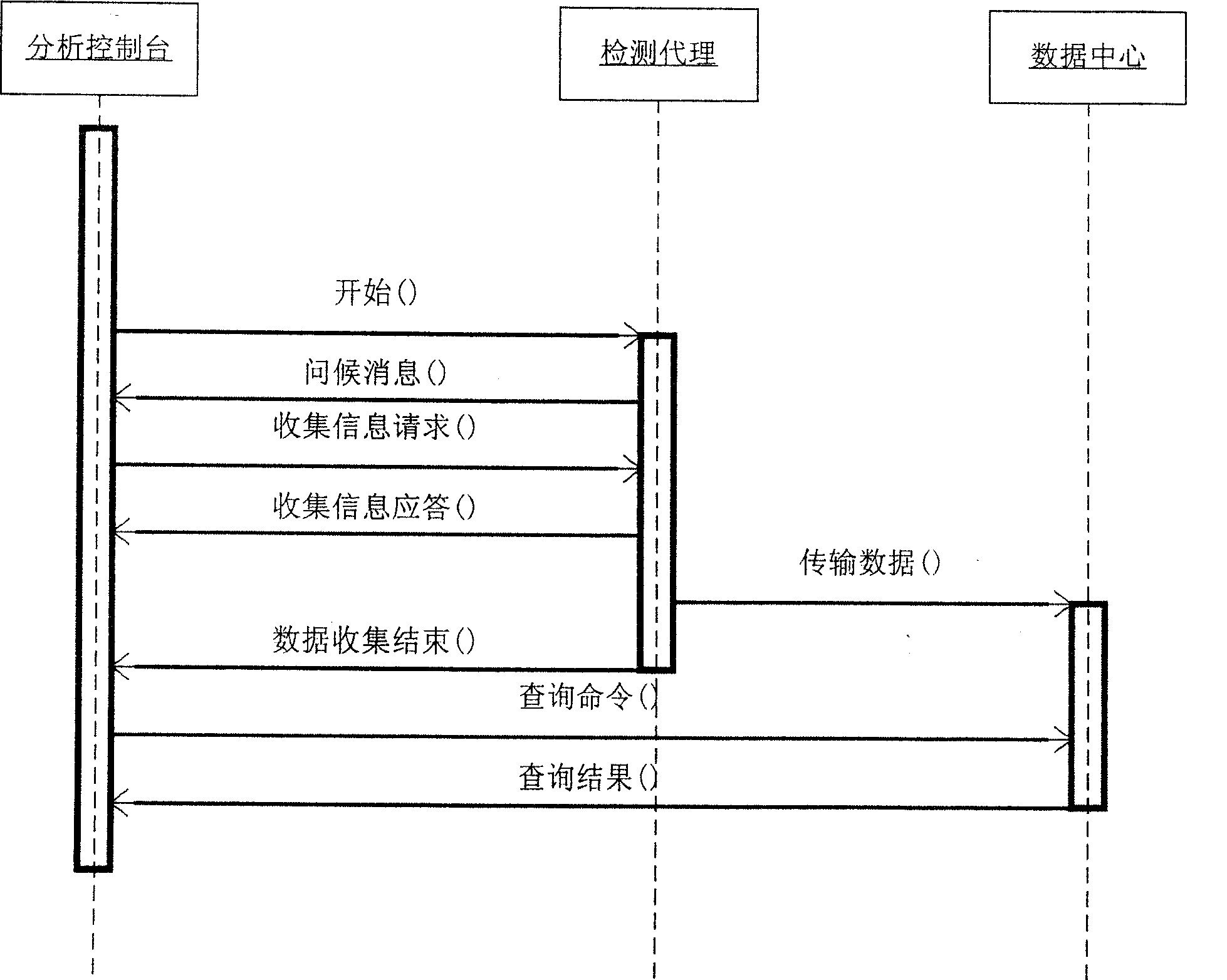
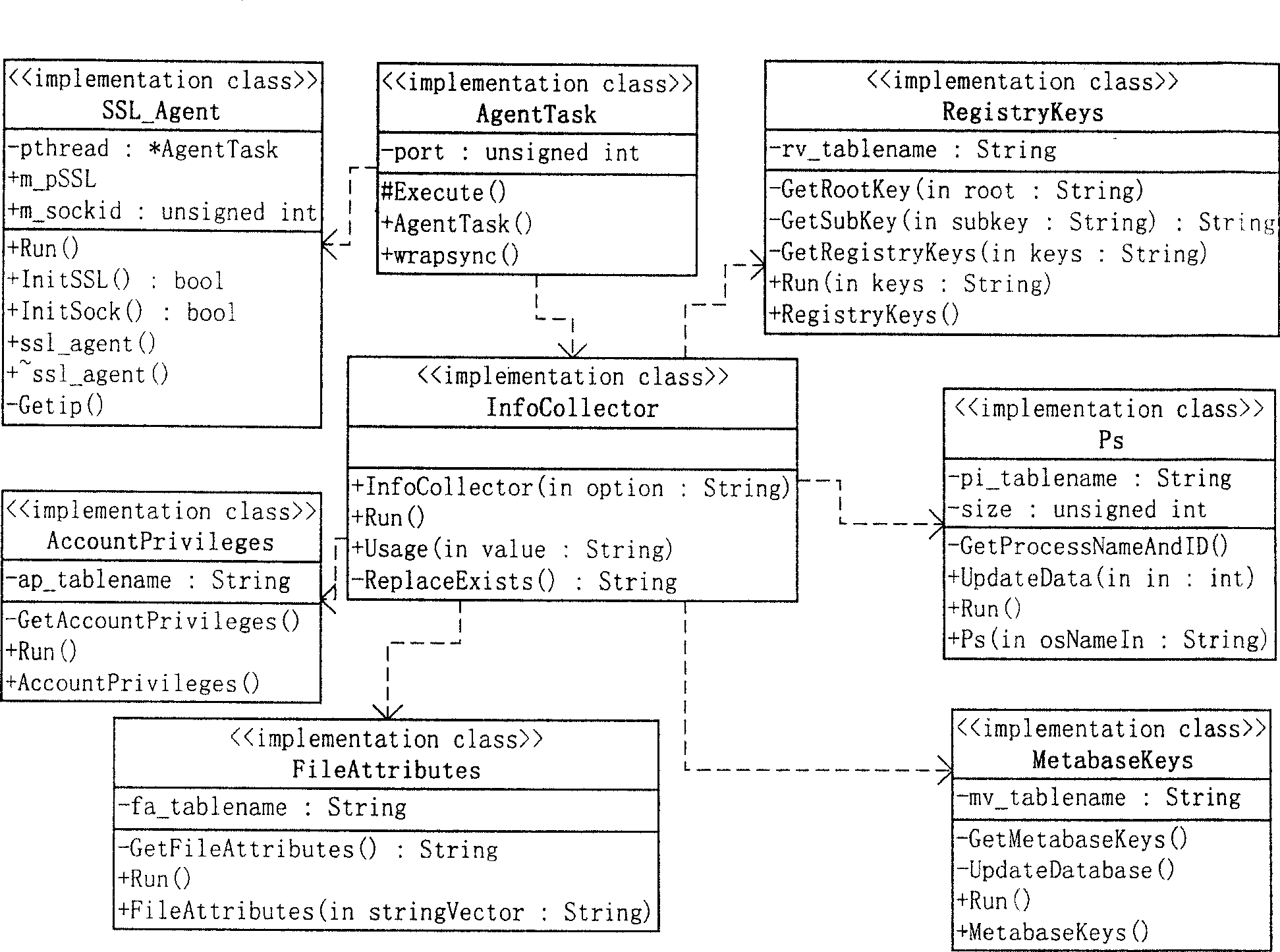
[0041] Such as figure 1 As shown, the composition of the active network security vulnerability detector AVCS is given, which is divided into three parts from the physical distribution: detection agent, data center and analysis console. Wherein, the detection agent is distributed on each host in the network and runs in the background mode. When a "data collection request" is received, OVAL is used to collect the system characteristic information of the machine, and the data is safely uploaded to the data center for later evaluation and analysis.
[0042] The analysis console is the graphical user interface of the system. The administrator can set the host to be evaluated, connect to the database, detection strategy, and evaluation conditions according to the evaluation needs. When the "...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com