Verifiably encrypted signature generation method and system
A signature value and encrypted public key technology, which is applied in the field of cryptography and information security, can solve problems such as impact, and achieve the effect of high portability and easy deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] Embodiments of the verifiable encrypted signature generation method and system of the present invention will be described below in conjunction with the accompanying drawings.
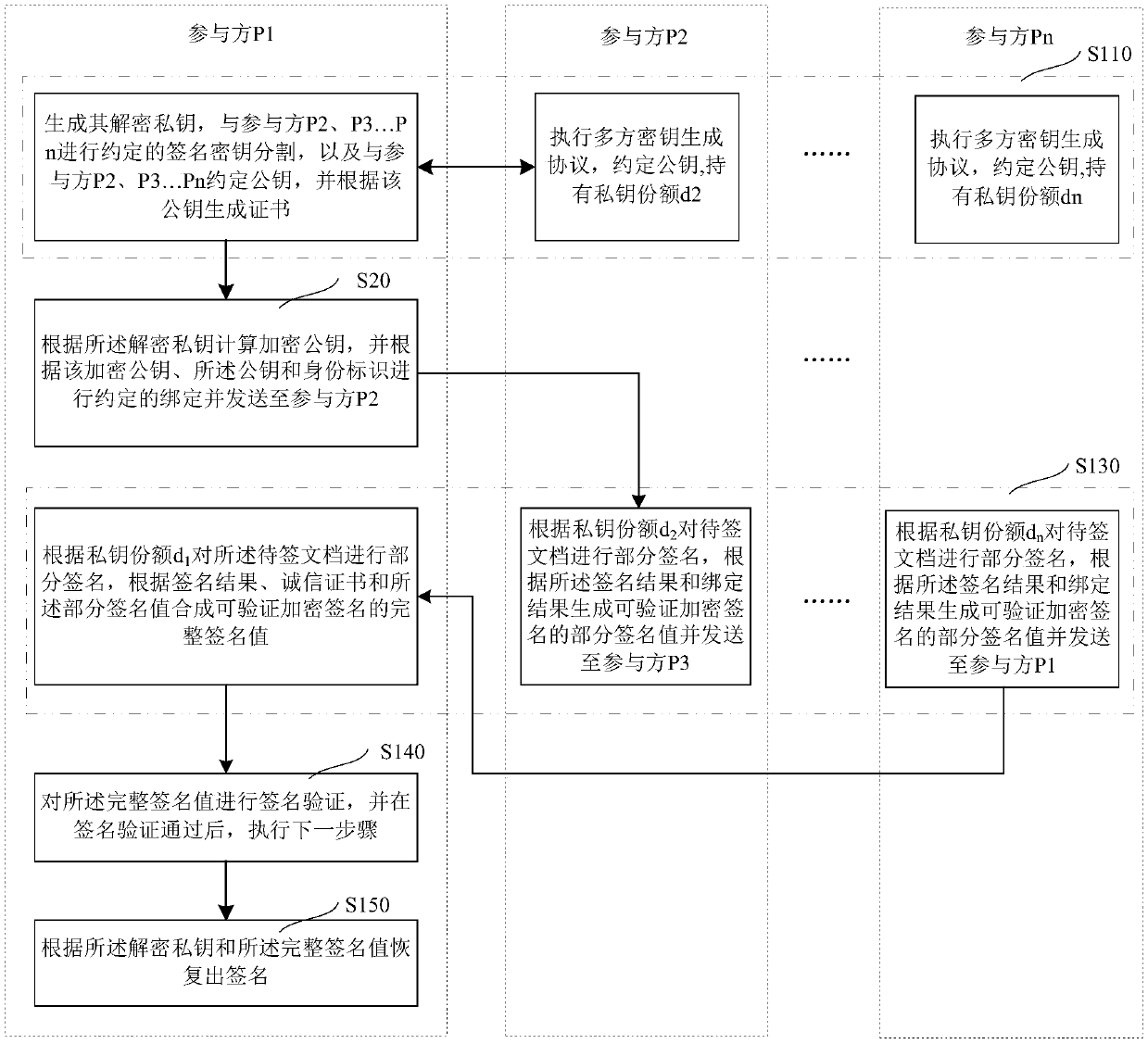
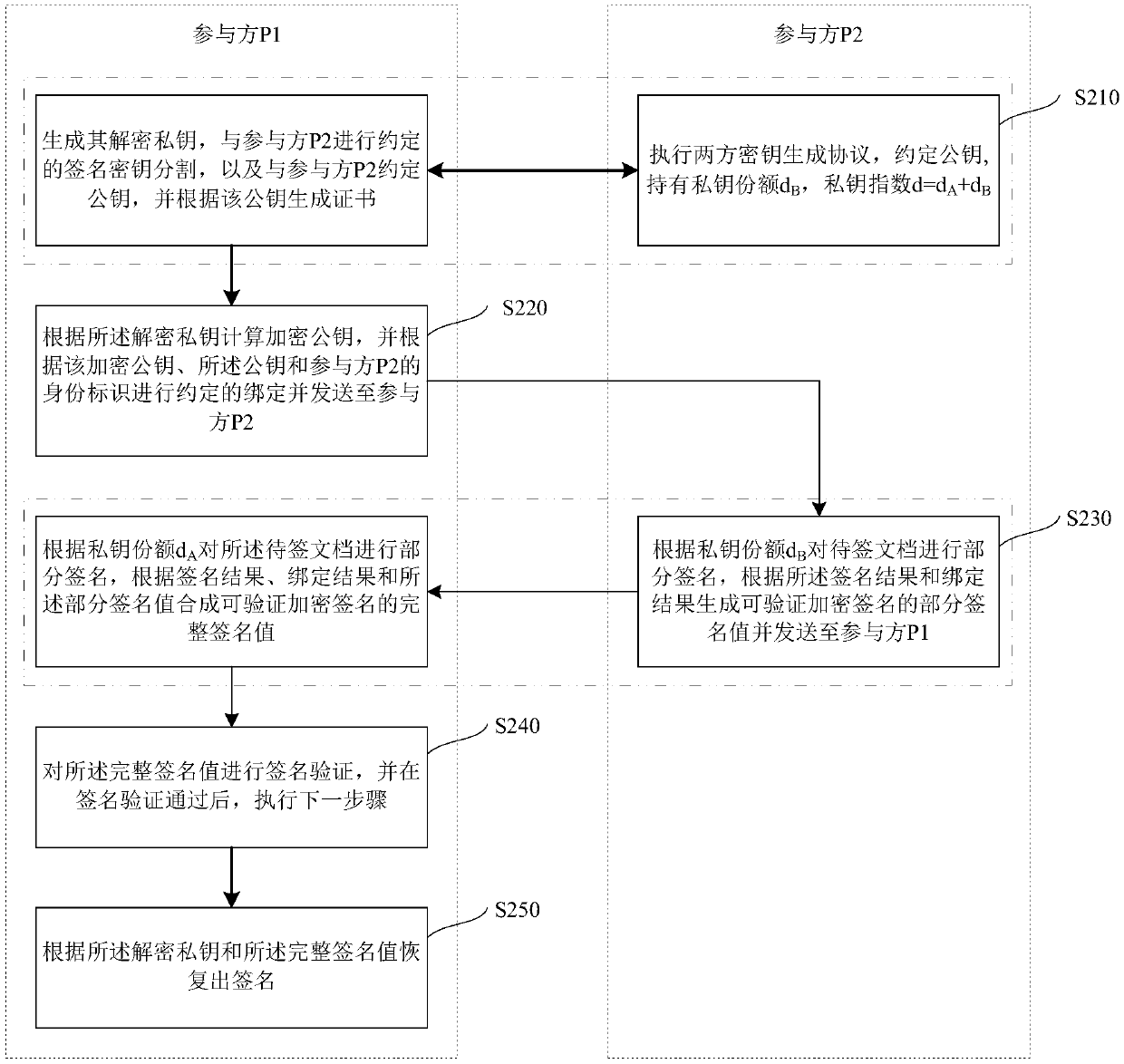
[0036] In the following embodiments, a scenario in which multiple participants collaborate to generate verifiable encrypted signatures is considered. Suppose there are n parties P 1 , P 2 ...,P n , n>2. Participants P1, P2...Pn correspond to an identity ID1,..., IDn respectively; then, n participants participate in the process of generating verifiable encrypted signatures in turn in the form of a ring. Of course, in practical applications, the participant P 2 ...,P n It is also possible to agree on a group mark as a common identity ID.
[0037] refer to figure 1 as shown, figure 1 It is a flowchart of a method for generating a verifiable encrypted signature according to an embodiment, including:
[0038] Step S110: Participant P1 generates its decryption private key, splits the agreed si...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com