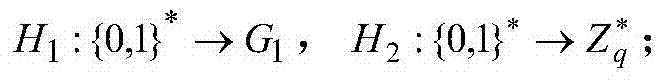Certificateless verifiable encrypted signature method with forward security
A forward-secure, certificate-free technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as security hazards in signing contracts, and ensure forward security, high security and fairness , the effect of high computational efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
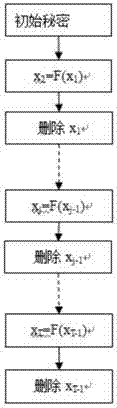
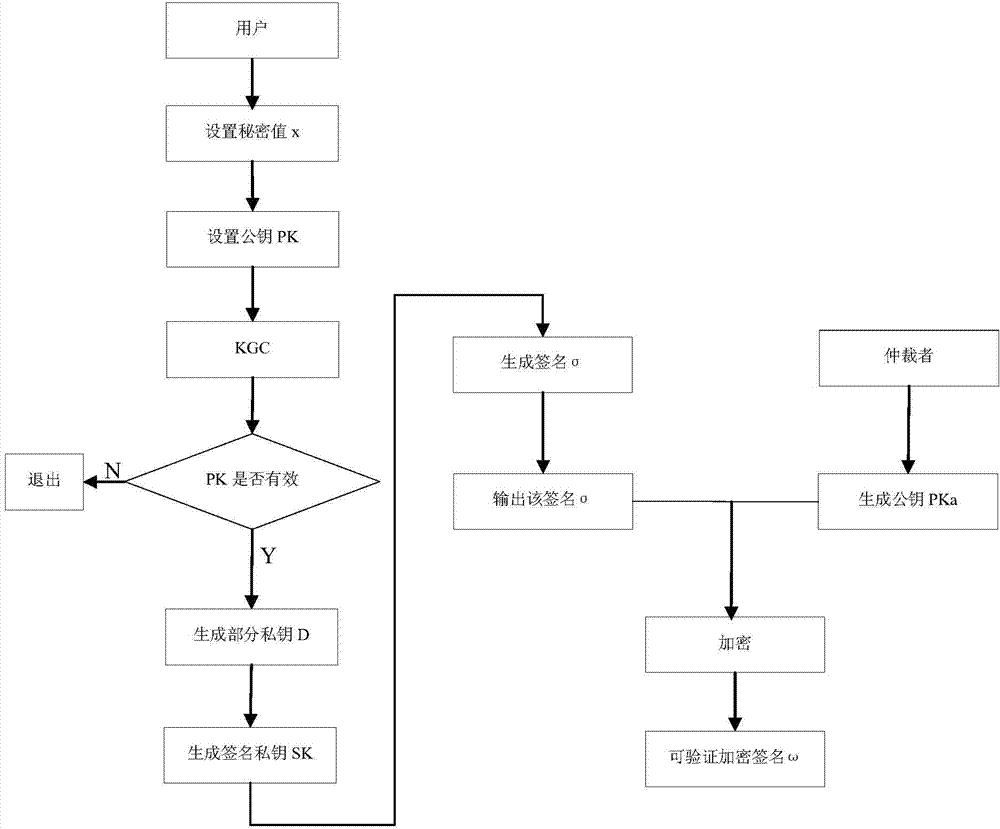
[0035] Such as figure 1 , 2 As shown, the present invention discloses a forward secure non-certificate verifiable encrypted signature method, setting the private key of the actual signature as a constant related to a specific time period, and safely deleting the unused key; at the same time, A trusted third party is added as an arbitrator, and when a dispute occurs, the arbitrator will rule.
[0036] Concrete steps are as follows: (1) generate system parameter; Establish KGC public parameter params={G 1 ,G 2 ,e,q,P,P pub ,g,H 1 ,H 2}, where G1, G2 are additive cyclic groups and multiplicative cyclic groups with order q and generator P; e is bilinear pairing G 1 ×G 1 →G 2 , P pub =sP is the system public key, g=e(P,P); the Hash function is
[0037] H 1 { { 0,1 } * → G 1 , H ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com