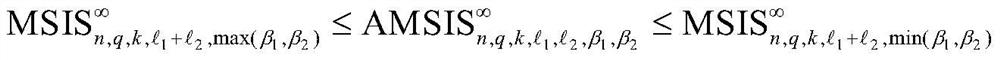A Lattice-Based Digital Signature Method
A digital signature and mathematical technology, applied in digital transmission systems, user identity/authority verification, secure communication devices, etc., to achieve the effects of fast calculation speed, short signature length and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
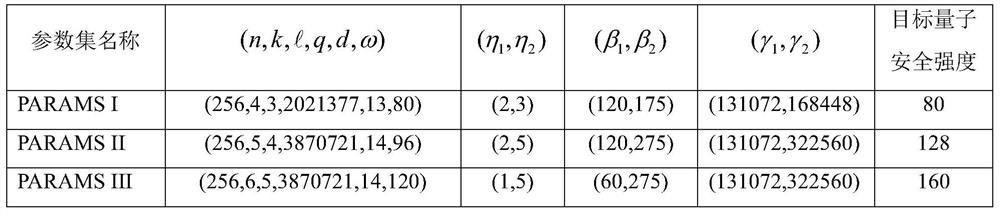
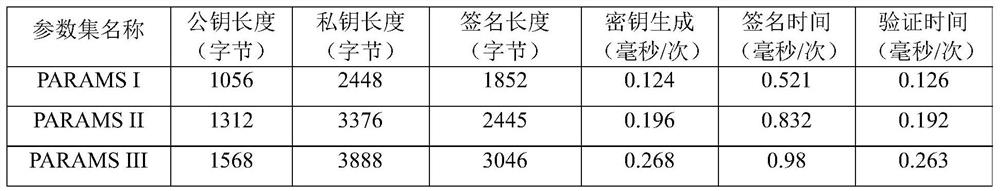
[0048] In order to embody the above-mentioned features and advantages of the present invention, the present invention will be further described below through a digital signature method on a lattice based on AMSIS and AMLWE mathematical difficulty problems as a specific embodiment.
[0049] This example involves the use of the hash function Used to generate a matrix A, and anti-collision hash function CRH:{0,1} * →{0,1} 384 . This embodiment also needs to use the hash function where B 60 Indicates ring R q There are exactly 60 elements in which the coefficients are -1 or 1, and the other coefficients are all 0 elements. The hash function H uses the extended output function to generate a random byte stream, and then uses the Fisher-Yates shuffling algorithm to map the random byte stream to B 60 Random elements in .
[0050] This embodiment will use Power2Round q (square power rounding function), Decompose q (decomposition function), HighBits q (take high bit function...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com