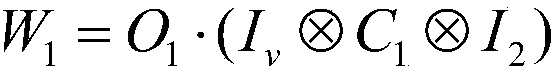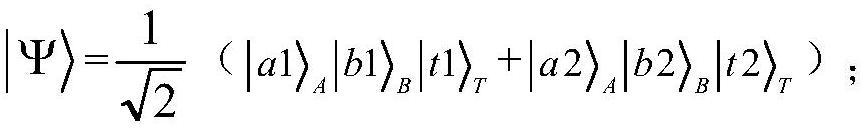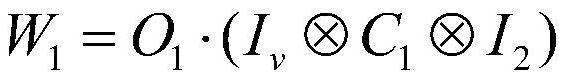Patents
Literature
31 results about "Quantum signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A quantum signature was the unique signature with which all matter in a universe resonated. It could not be changed by any known process, and was considered to be the basic foundation of existence.
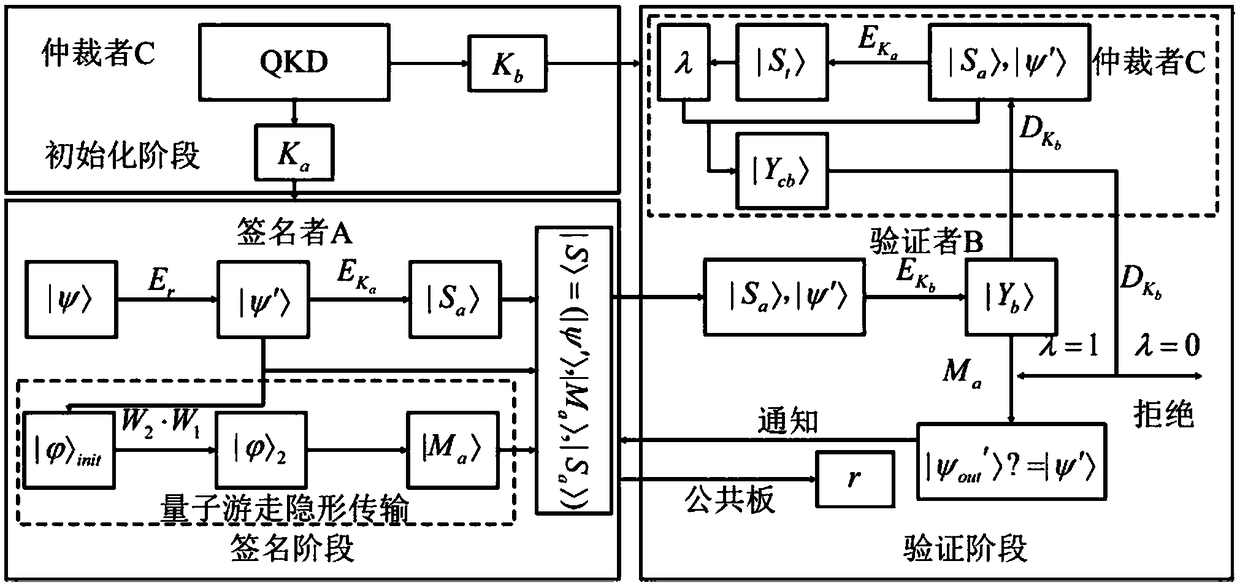
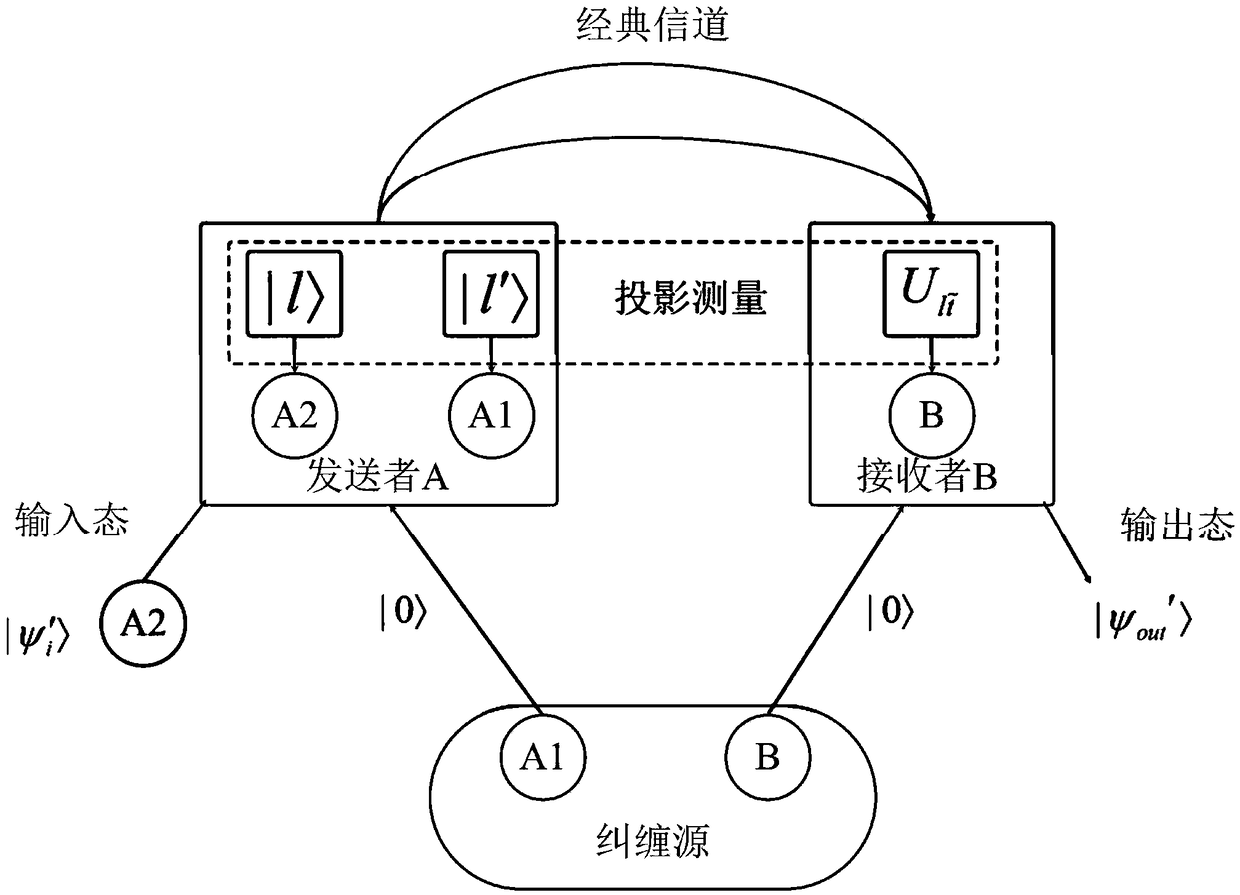
Arbitration quantum signature method based on quantum wandering stealth transmission
ActiveCN109257183AEasy signatureReduce overheadKey distribution for secure communicationUser identity/authority verificationRandom parametersLaboratory facility
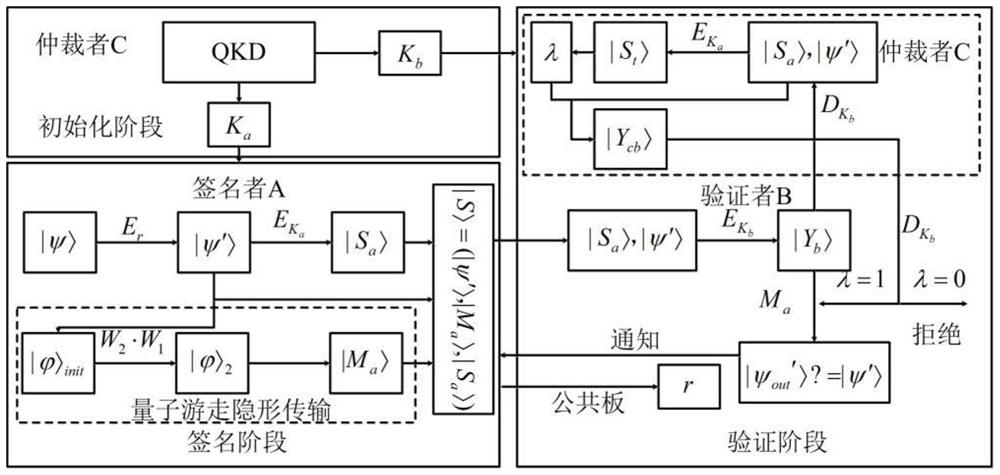
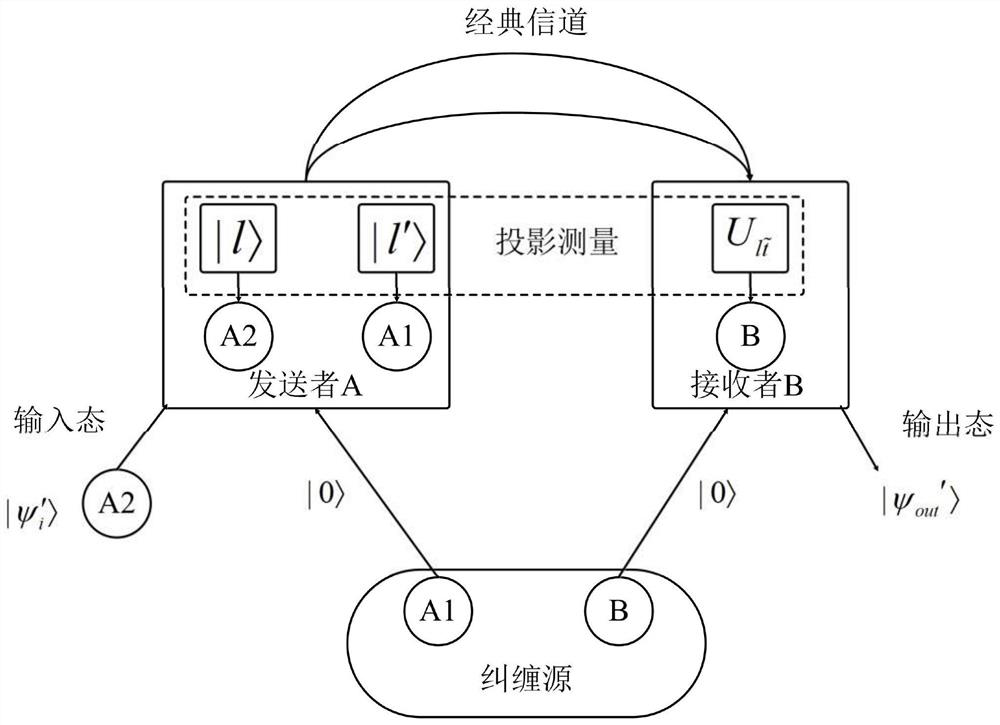
The invention discloses an arbitration quantum signature method based on quantum wandering stealth transmission, which comprisesan initialization phase for preparing a key and setting a system, a signature phase for constructing a signature of a transmission message, and a verification phase for verifying the validity of the signature, authenticity of the message source, and integrity of the message.The method of the invention adopts the stealth teleportation based on the quantum wandering to transmit the d-dimensional quantum state, and the entanglement source used for the stealth transmission does not need to be prepared in advance, thus saving the overhead of preparing the entangled state specially; Moreover, it is more efficient to measure with two projections of d elements. At the same time, the introduction of random parameters prevents the verifier from obtaining the content of the transmitted information and denying the signer's signature before accepting the signed information. In addition, the public board is used to publish the random parameters, and the verifier can obtain the information content of the signature after the verification is completed. Finally, the methodof the invention has the characteristics of saving resources, high measuring efficiency, easy realization of the laboratory and high signature security.
Owner:CENT SOUTH UNIV
Arbitration quantum signature method based on glass color sampling random unitary operation
ActiveCN111162913AReduce overheadImprove efficiencyKey distribution for secure communicationUser identity/authority verificationCommunications systemInformation design
The invention discloses an arbitration quantum signature method based on glass color sampling random unitary operation. The arbitration quantum signature method comprises an initialization stage, a signature stage and a verification stage. The initialization stage is used for preparing a secret key and establishing a communication system; the signature stage is used for selecting a proper signature algorithm to design the signature of the transmission information; and the verification stage is used for verifying the validity of the signer and the integrity and authenticity of original information. According to the invention, unitary operation encryption based on glass color sampling is adopted in the signature of transmission information designed in arbitration quantum signature; an m-modequantum state is transferred by adopting quantum walk invisible transmission based on a graph, a necessary entanglement state for invisible transmission does not need to be prepared in advance, the safety is higher by adopting a common channel and a random tuple, and a glass color sampling model and a quantum walk invisible transmission model are proved to be realized through a linear optical network; and therefore, the method disclosed by the invention is high in safety, resource-saving and easy to implement in experiment.
Owner:CENT SOUTH UNIV
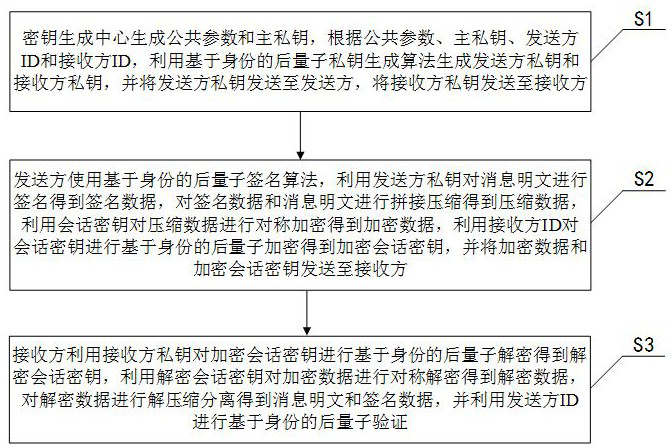
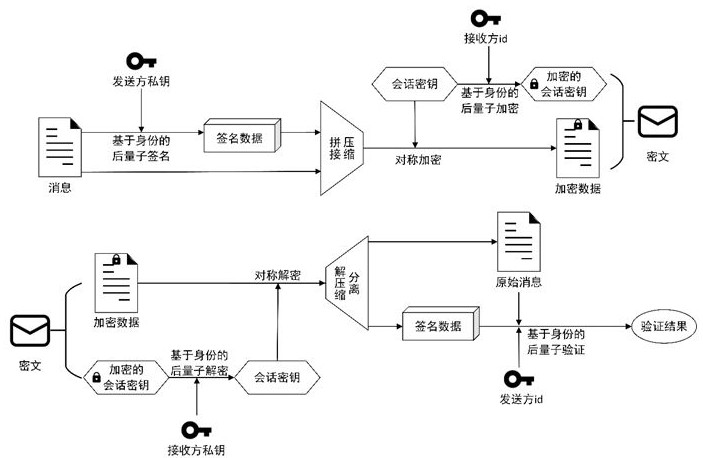
Post-quantum encryption and decryption method and system based on identity label, equipment and medium
ActiveCN114024676AEasy to managePost-quantum securityKey distribution for secure communicationPlaintextKey (cryptography)
The invention discloses a post-quantum encryption and decryption method and system based on an identity label, equipment and a medium, and belongs to the field of cryptography, and the method comprises the following steps: a key generation center generates a sender private key and a receiver private key by using an identity-based post-quantum private key generation algorithm; a sender signs a message plaintext by using a sender private key by using an identity-based post-quantum signature algorithm, sequentially performs splicing compression and symmetric encryption on signature data and the message plaintext, performs identity-based post-quantum encryption on a session key by using a receiver ID, and sends encrypted data and an encrypted session key to the receiver; and a receiver performs identity-based post quantum decryption on the encrypted session key by using the receiver private key, performs symmetric decryption on the encrypted data, performs decompression separation on the decrypted data to obtain a message plaintext and signature data, and performs identity-based post quantum verification by using the sender ID. The message encryption security is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
A public key arbitration quantum signature protocol based on quantum block encryption
ActiveCN109787770ASave resourcesEnsure safetyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey distributionProtocol for Carrying Authentication for Network Access
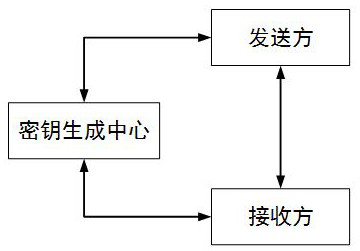
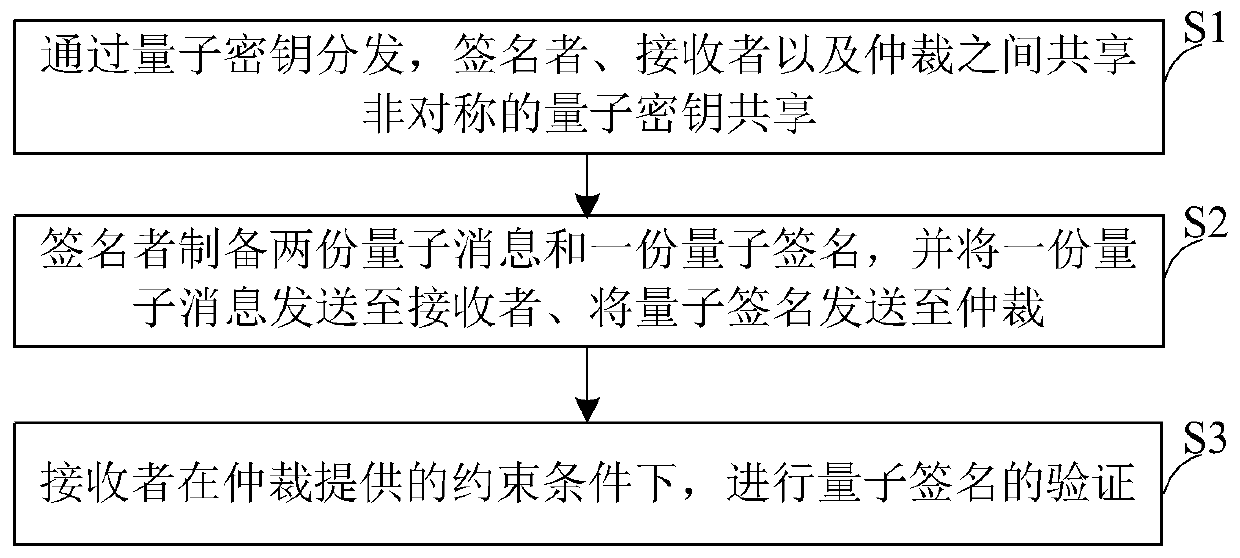
The invention discloses a public key arbitration quantum signature protocol based on quantum block encryption, which belongs to the technical field of quantum secret communication and comprises quantum key sharing among a signer, a receiver and arbitration through quantum key distribution. The signer prepares two parts of sub-messages and one part of sub-signature, sends one part of sub-message tothe receiver and sends the quantum signature to arbitration; And the receiver verifies the quantum signature under the constraint condition provided by arbitration. The protocol provided by the invention not only can ensure the security, but also has a better practical application value.
Owner:ANHUI JIYUAN SOFTWARE CO LTD +6
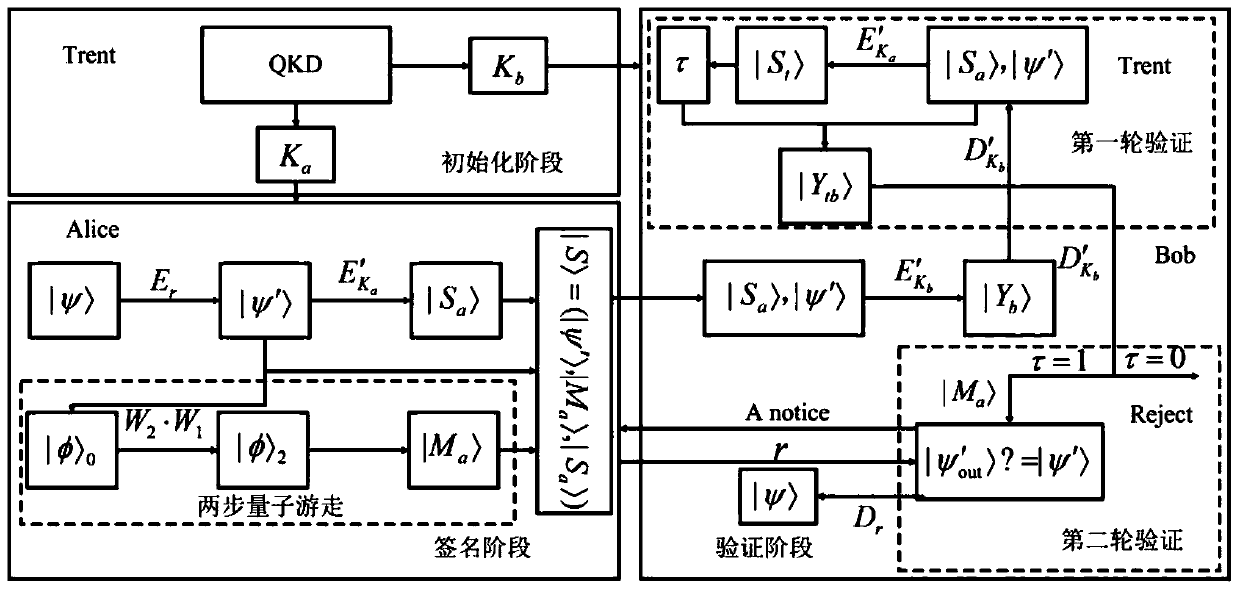
Arbitration quantum signature method based on XOR encryption
ActiveCN111224780ASimple processFulfillment requirementsKey distribution for secure communicationUser identity/authority verificationEngineeringArbiter
The invention discloses an arbitration quantum signature method based on XOR encryption. The method comprises a signer Alice, a receiver Bob, an arbiter Trent and a three-particle GHZ state quantum key shared by the three parties, the three-particle GHZ state is an entangled resource commonly used in quantum communication, and the signature method comprises the following steps: an initialization stage, a signature stage and a verification stage. The signer Alice, the receiver Bob and the arbiter Trent share the three-particle GHZ state and respectively keep own particle information secret; byusing a traditional XOR encryption and decryption method, a quantum message is encrypted and signed by sharing the GHZ state; by introducing a decoy photon state, the flow of a conventional arbitration quantum signature protocol is improved, the requirements of unforgeability and non-repudiation are met, and finally, it can be seen that encryption of the protocol does not involve a complex encryption method or complex quantum operation, so that the method is more practical than other methods.
Owner:GUANGDONG TECHN COLLEGE OF WATER RESOURCES & ELECTRIC ENG
Arbitration quantum signature design method based on Grover iteration flexible tracking
ActiveCN113242135AReduce occupancyImprove fairnessKey distribution for secure communicationUser identity/authority verificationTheoretical computer scienceEngineering
The invention discloses an arbitration quantum signature design method based on Grover iteration flexible tracking, and the method employs a Grover search algorithm to achieve the purpose that an arbitration management party can find a signer of a problem signature when a signature dispute occurs. In the arbitration process, the arbitration management system and each signature participant negotiate to obtain a final secret key and find a signer with a problem signature, so that a direct'disclosure 'mechanism of an arbitration group signature is avoided. The method is characterized in that a complete arbitration signature verification system is established, an arbitration management system can select whether to disclose the identity of a problem signature signer, and the method has flexible traceability and fairness.
Owner:EAST CHINA JIAOTONG UNIVERSITY
Quantum signature method and quantum secret sharing method using quantum trapdoor one-way function
ActiveUS20200287714A1Key distribution for secure communicationPublic key for secure communicationQuantum secret sharingParticle physics
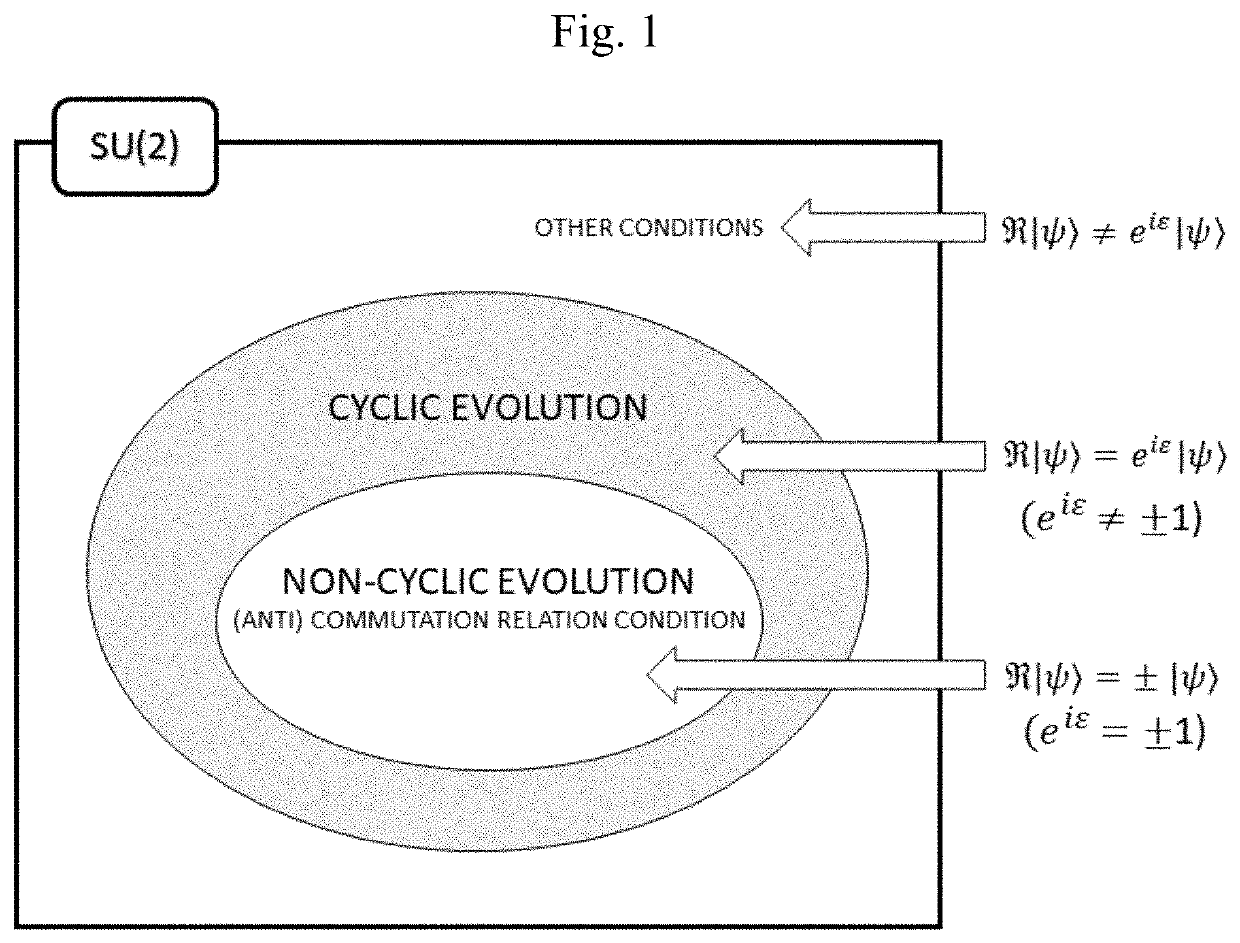
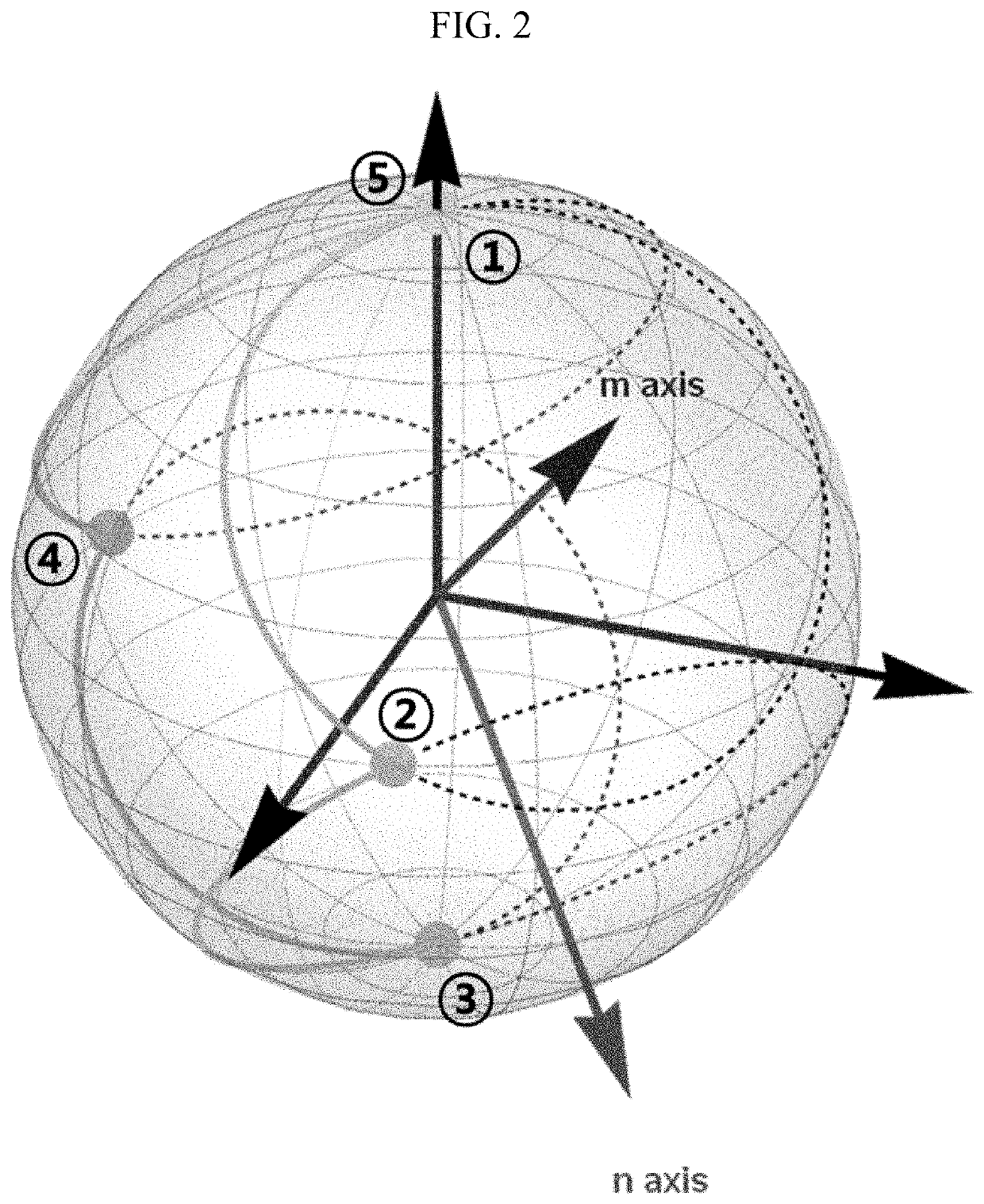
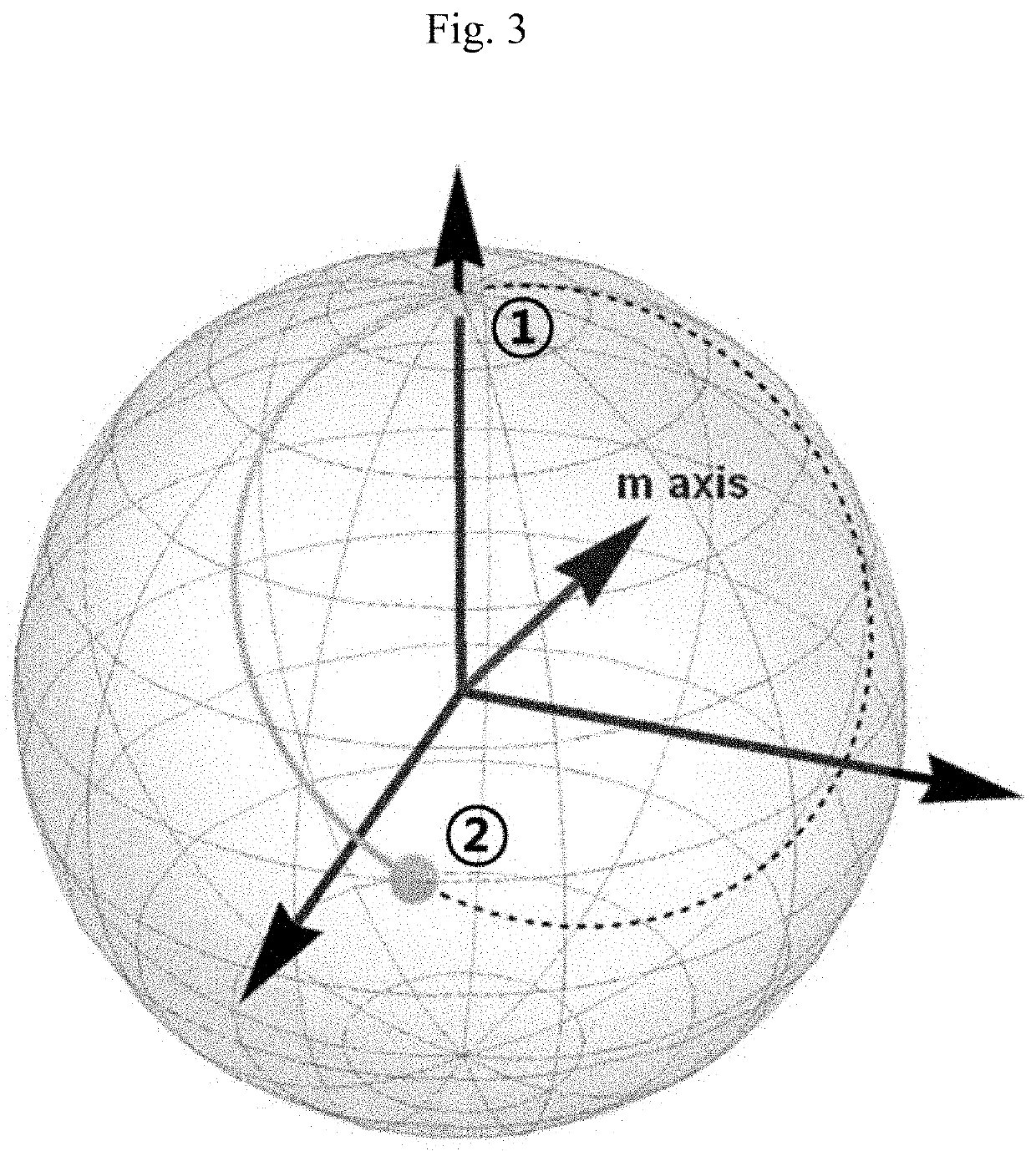
This specification discloses a quantum public-key cryptosystem. The quantum public-key cryptosystem may use two rotation operators R{circumflex over (n)}(θ) and R{circumflex over (m)}(φ) satisfying a cyclic evolution. The two rotation operators R{circumflex over (n)}(θ) and R{circumflex over (m)}(φ) do not have a commutation relation or an anti-commutation relation with each other. The commutation relation or the anti-commutation relation is established when either of the following conditions is satisfied: θ=2iπ, φ=2jπ, or {circumflex over (n)}·{circumflex over (m)}=1 (i, j=integer), and θ=(2k+1)π, φ=(2l+1)π, or {circumflex over (n)}·{circumflex over (m)}=0 (k, l=integer).
Owner:KOREA INST OF SCI & TECH
Quantum check transaction method based on block chain digital signature
PendingCN113744036AHas a decentralized architectureWith characteristicsFinanceDigital data protectionPaymentDigital signature
Provided is a quantum check transaction method based on a block chain digital signature. A quantum check generation module, a quantum check, a payment transfer module, a block chain, a block, a quantum key generation module, a quantum signature module, a digital signature and a quantum signature verification module are adopted. The method comprises the steps that: 1, the quantum key generation module distributes a quantum key for a quantum check; 2, a user A applies to the quantum check generation module for a quantum check; 3, the user A uses the quantum signature module to sign the quantum check; 4, a user B verifies the digital signature through the quantum signature verification module; 5, the payment transfer module completes quantum check payment; and 6, a quantum check payment account book is stored in the block chain. According to the method, the security and efficiency of check transaction can be ensured to the greatest extent in a trust-free network, the method has theoretical absolute security and quantum attack resistance, and the check account book stored in the block chain has traceability and tamper-proofing performance.
Owner:CHINA THREE GORGES UNIV
Post-quantum signature scheme using biometrics or other fuzzy data
InactiveCN113647049AMultiple keys/algorithms usagePublic key for secure communicationAlgorithmDigital signature
Cryptographic methods and systems are described. An example cryptographic system may include a signature engine to digitally sign a message using fuzzy data associated with a signee. The signature engine is configured to generate a digital signature using a lattice instantiation and a linear sketch. The linear sketch is configured based on the lattice instantiation. The digital signature is a function of the fuzzy data and the message and uses a signature-time signing key residing within a signing key space. The signing key space is a space defined by the lattice instantiation. An example of a verification engine is also described. The verification engine is configured to receive the message and the digital signature and to verify the message as signed by the signee. The verification engine is configured to obtain key data for the signee comprising at least an initialisation-time verification key, to compute a distance metric based on the key data and the received digital signature, the distance metric indicating a measure of difference for the signature-time verification key, and to indicate a verification failure responsive to the distance metric being greater than a predefined homomorphic threshold. The methods and systems may be used as an authentication mechanism.
Owner:OXFORD UNIV INNOVATION LTD
Fault-tolerant quantum digital signature method capable of resisting collective noise
ActiveCN113300849AEasy to implementImprove practicalityKey distribution for secure communicationUser identity/authority verificationTelecommunicationsDigital signature
The invention discloses a fault-tolerant quantum digital signature method capable of resisting collective noise. The fault-tolerant quantum digital signature method specifically comprises the following steps: step 1, a sender Alice generating a quantum signature and sending the quantum signature to a receiver Bob and a receiver Charlie; step 11, Alice generating two same copy sequences; step 12, the sender Alice sending the quantum signature to the receiver Bob and the receiver Charlie respectively; step 13, the receiver Bob and the receiver Charlie randomly selecting half of the received quantum signatures and sending the quantum signatures to the receiver Bob and the receiver Charlie; step 14, for all signature elements in the hand at present, the receiver Bob and the receiver Charlie being measured; step 2, the sender Alice sending an information private key pair (k, PKk) to the receiver Bob, and when the Bob meets the receiving condition, forwarding the information private key pair (k, PKk) to the receiver Charlie. According to the method disclosed by the invention, the decoherence-free subspace is introduced, and the physical quantum states with the same noise factor are utilized to form the logic quantum state, so that the quantum information is not influenced by collective noise in the transmission process, and the fidelity of the communication process is improved.
Owner:NORTHWEST UNIV
Quantum cash settlement system and method based on block chain
PendingCN113516462AImprove securityAvoid crackingFinanceDatabase distribution/replicationBank accountOperations research
The invention discloses a quantum cash settlement system and method based on a block chain. The system comprises a quantum cash settlement system, a quantum cash key management system, a quantum cash bank and a quantum cash settlement block chain. The invention discloses a quantum cash settlement method based on a block chain. The quantum cash settlement method comprises a quantum cash extraction process, a quantum cash payment process and a quantum cash deposit process. A user can register in a quantum cash settlement system, and after the identity and legality are verified, a quantum cash bank account can be created; a user completes quantum signature through the quantum cash key management system, extraction and payment of quantum cash can be completed from a quantum cash bank account, or the quantum cash is stored in the quantum cash bank account, and all related data and settlement records of the user are stored in a quantum cash settlement block chain. According to the scheme, the reliability of quantum cash settlement is ensured by combining a block chain technology and a quantum encryption technology, and unconditional security is theoretically achieved.
Owner:CHINA THREE GORGES UNIV
Member revocable certificateless anti-quantum signature method based on cloud server
PendingCN114422136AKey distribution for secure communicationUser identity/authority verificationAlgorithmAttack
The invention provides a member revocable certificateless anti-quantum signature method based on a cloud server, which belongs to the field of information security, and mainly comprises five steps of a system initialization algorithm, a key SKID generation algorithm, a signature algorithm, a verification algorithm and a member revocation algorithm. According to the scheme, the revocable certificateless signature is established on a lattice cryptosystem, so that the scheme can resist quantum computer attacks, and higher security is achieved; a certificateless signature system is used in the scheme, and a key generation center is introduced, so that the certificate storage pressure is reduced, the risk is shared, and the system stability is improved; the revocation of the user is realized by means of the cloud server, and the secret key is divided into the partial secret key and the update secret key, so that the task of member revocation is completed by the cloud server, the computing pressure of the center is reduced, and the system is more reliable.
Owner:苏州鸿链信息科技有限公司
Identity-based post-quantum encryption and decryption method, system, device and medium
ActiveCN114024676BEasy to managePost-quantum securityKey distribution for secure communicationPasswordEngineering
The invention discloses an identity-based post-quantum encryption and decryption method, system, equipment and medium, which belong to the field of cryptography. The method includes: the key generation center uses the identity-based post-quantum private key generation algorithm to generate the sender's private key and Receiver's private key; the sender uses the identity-based post-quantum signature algorithm to sign the plaintext of the message with the sender's private key, concatenates, compresses and encrypts the signed data and the plaintext of the message in sequence, and uses the receiver's ID to encrypt the session key. Identity-based post-quantum encryption, and send the encrypted data and encrypted session key to the receiver; the receiver uses the receiver's private key to perform identity-based post-quantum decryption on the encrypted session key, symmetrically decrypt the encrypted data, and decrypt the decrypted The data is decompressed and separated to obtain the message plaintext and signature data, and the identity-based post-quantum verification is performed using the sender ID. Improve message encryption security.
Owner:HUAZHONG UNIV OF SCI & TECH
More efficient post-quantum signatures
ActiveCN113424492AKey distribution for secure communicationPublic key for secure communicationTheoretical computer scienceSignature vector
Techniques of generating a lattice-based verification matrix and signature vector are disclosed. The method enables a generating device to sample a gadget matrix and then generate a reduced gadget matrix. The generating device may then sample a trapdoor matrix and use the trapdoor matrix and the reduced gadget matrix to generate a verification matrix. A sending device may receive the trapdoor matrix and the verification matrix from the generating device, in addition to receiving a message. The sending device may then use the trapdoor matrix and the verification matrix to generate a signature vector for the message. A verification device can receive the verification matrix, the message, and the signature vector. The verification device may use the verification matrix and the signature vector to verify the message.
Owner:VISA INT SERVICE ASSOC
Anti-quantum signature verification method based on isolation witness
InactiveCN111541548AImprove verification efficiencyAverage signature shortKey distribution for secure communicationUser identity/authority verificationTheoretical computer scienceKey generation
The invention relates to an anti-quantum signature verification method based on isolation witness. A configuration module, a secret key module, an approval module, a verification module and a signature node are included. According to the method, defense measures of multiple side channel attacks are integrated, and a one-time signature scheme is adopted, so that the average signature is shorter, the secret key generation, signature and verification efficiency is higher, and the adaptability is higher than that of public key signature.
Owner:潘小胜
Decentralized quantum Byzantine consensus method
ActiveCN114553423AImprove fault toleranceUnconditional Security GuaranteedQuantum computersKey distribution for secure communicationEngineeringBroadcasting
The invention discloses a decentralized quantum Byzantine consensus method which comprises a message broadcasting stage and a message integration stage, the message broadcasting stage is composed of a plurality of message distribution wheels, and in each message distribution wheel, a main node distributes messages to other auxiliary nodes in the wheel; other auxiliary nodes verify and record the received messages, and message distribution is realized by using a three-party quantum signature technology, so that anti-counterfeiting performance and anti-repudiation performance are ensured; in the message integration stage, each node independently utilizes a major function to carry out multi-round statistical integration on a message statistical list in the node, and a finally output message is determined. According to the method, all good nodes, namely non-malicious nodes, are ensured to output consistent consensus conclusions finally; and under the condition that one good node serves as the initial main node, it can be ensured that finally, messages output by all the good nodes consistently are just the values distributed by the good initial main node in the initial message distribution round.
Owner:NANJING UNIV
Novel arbitration quantum signature method based on XOR encryption and GHZ state
PendingCN114553390AEasy to operateUnforgeableKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionTheoretical computer science
The invention provides a novel arbitration quantum signature method based on XOR encryption and a GHZ state. The novel arbitration quantum signature method comprises three steps of initialization, signature generation and signature verification. Firstly, an arbiter and a signer use a group of one-way hash functions and share a shared key; secondly, the signer performs quantum coding on the quantum message by using a key control hash function, and performs control NOT gate operation on the quantum message by using a control bit in a GHZ state to generate a quantum signature; and finally, a verifier performs similar XOR operation to verify the signature by using the control bit in the GHZ state. Compared with other arbitration quantum signature methods, key distribution and encryption of the method do not involve complex encryption methods or quantum operations, and forgery attacks and denial attacks can be effectively resisted; on the basis of meeting the requirements of safety, unforgeability and non-repudiation, the method disclosed by the invention is more practical and higher in efficiency.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Key generation hardware acceleration architecture and method based on Hash post-quantum signature
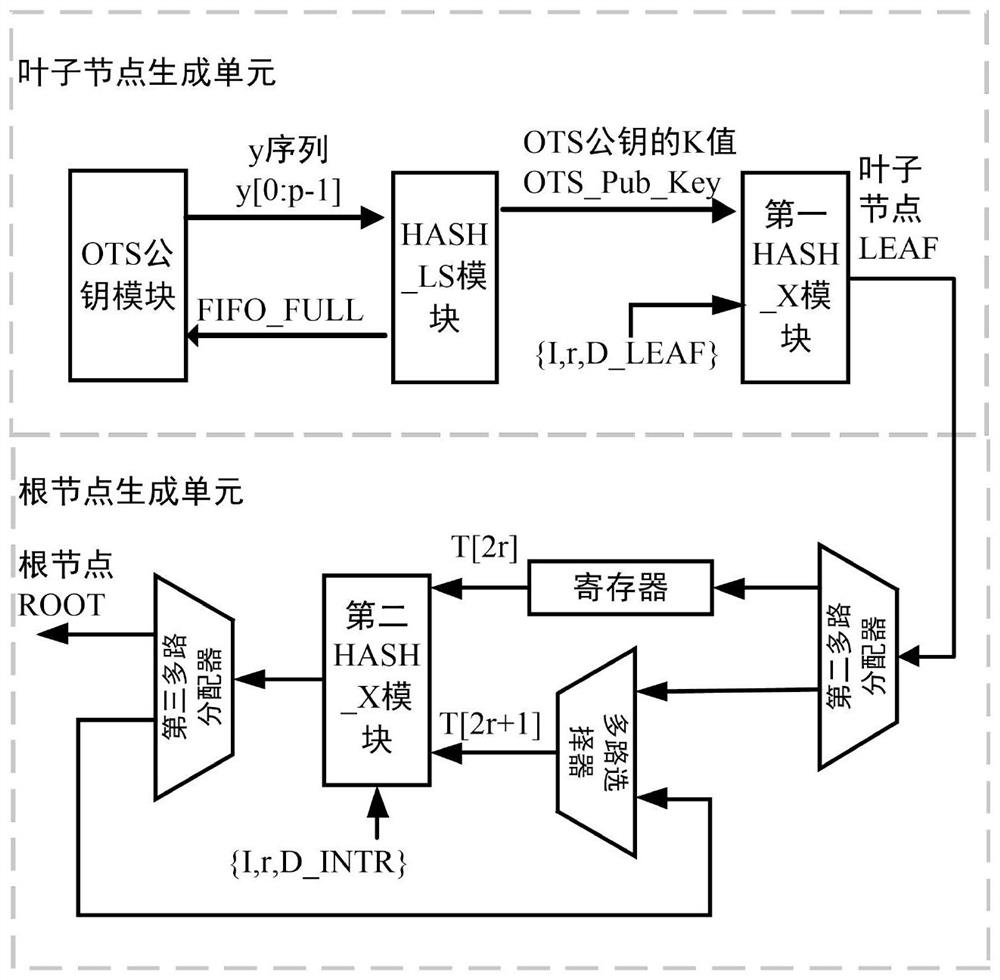
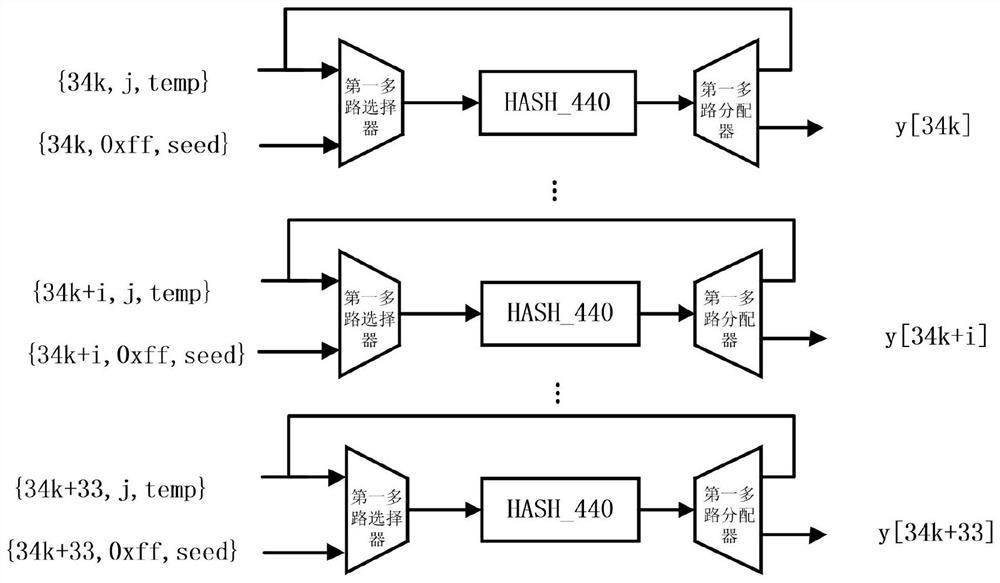
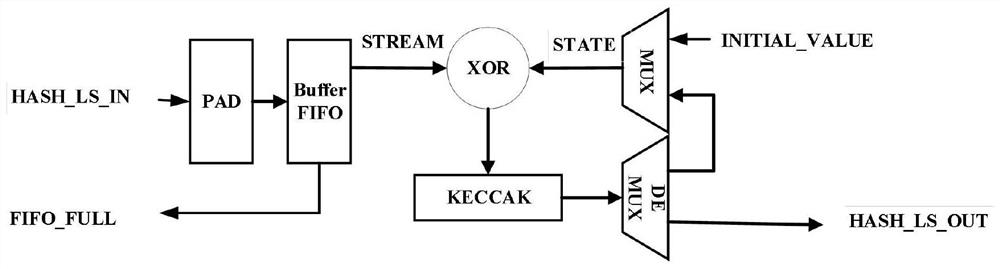
ActiveCN113225185AIncrease profitImprove hardware utilizationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareTime delays
The invention relates to the technical field of key generation, provides a key generation hardware acceleration architecture and method based on Hash post-quantum signature, and designs a high-speed and telescopic hardware acceleration architecture based on the characteristics of an algorithm and a parameter set in an LMS key generation process. The architecture is designed to be suitable for all parameter sets of an LMS scheme, low time delay and high hardware utilization rate can be achieved at the same time through appropriate parallel design, and the architecture keeps certain constant power when different parameters are achieved, and power attack can be helped to be resisted to a certain extent.
Owner:NANJING UNIV
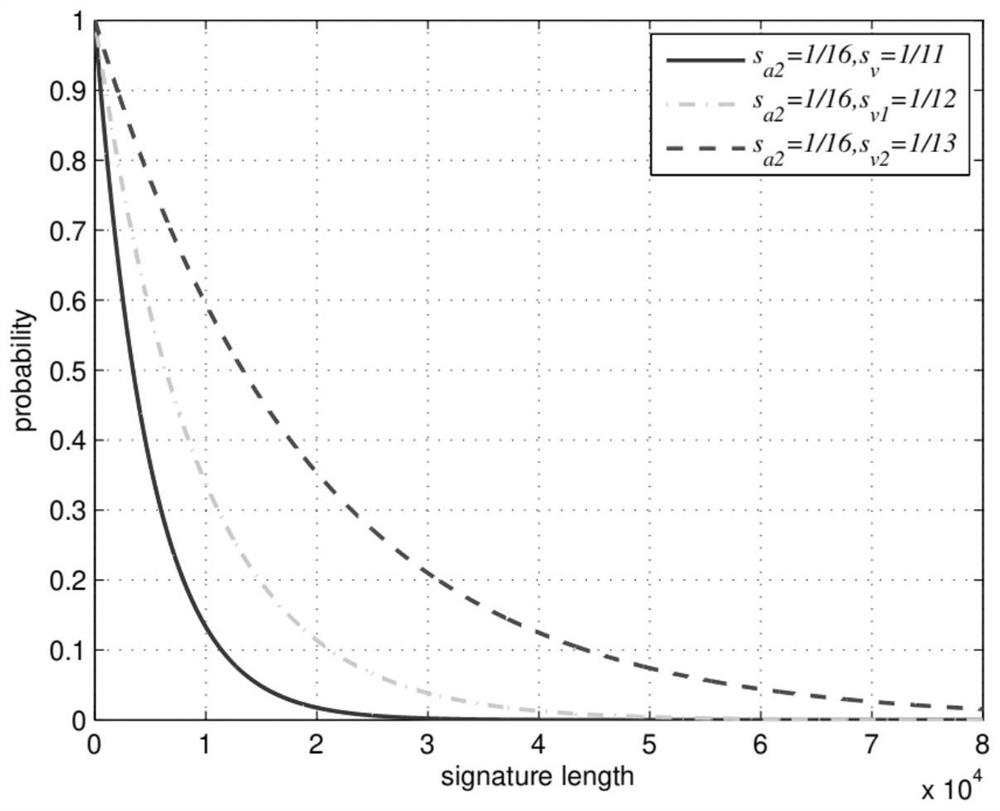
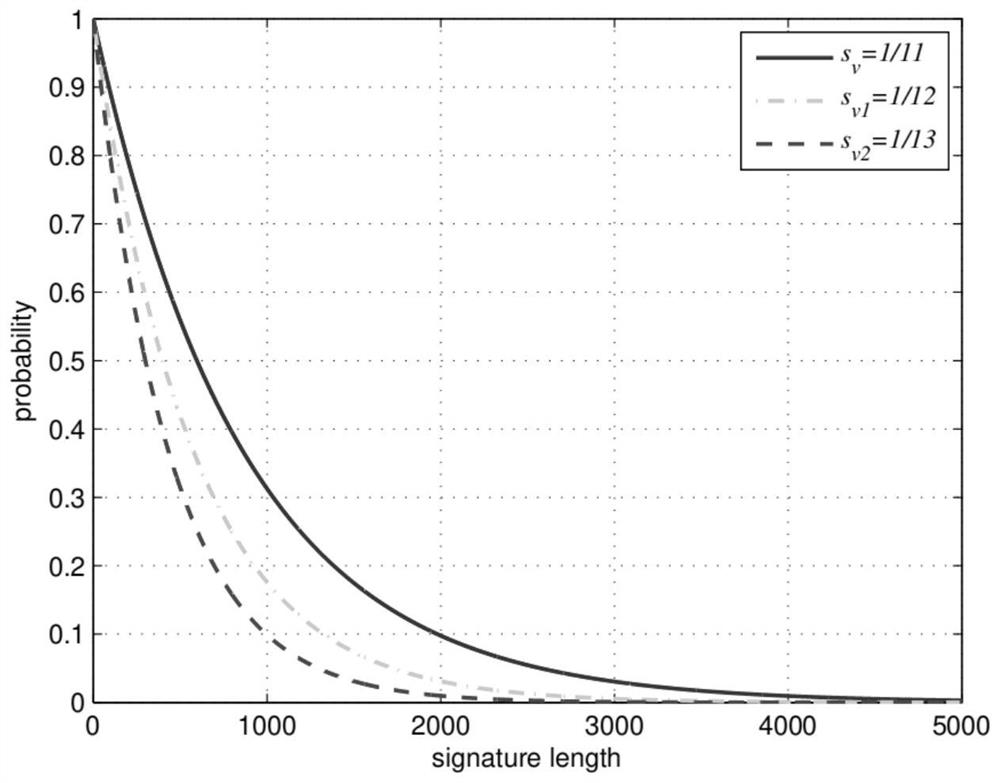
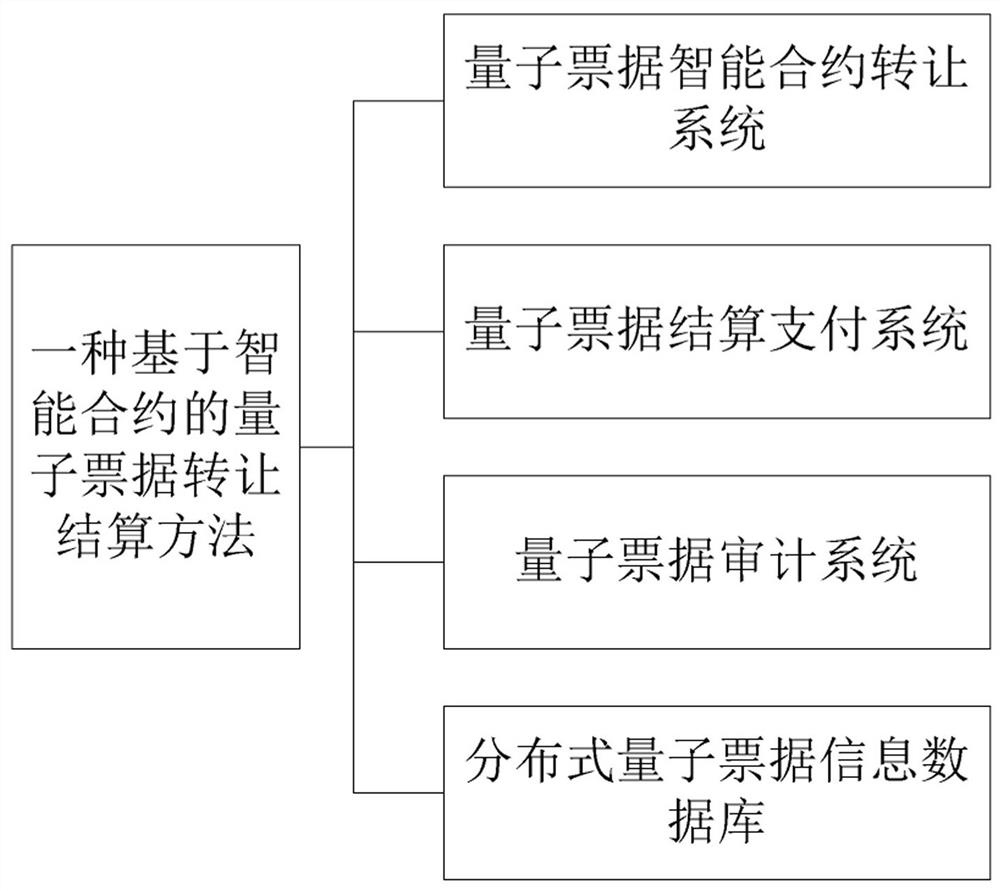
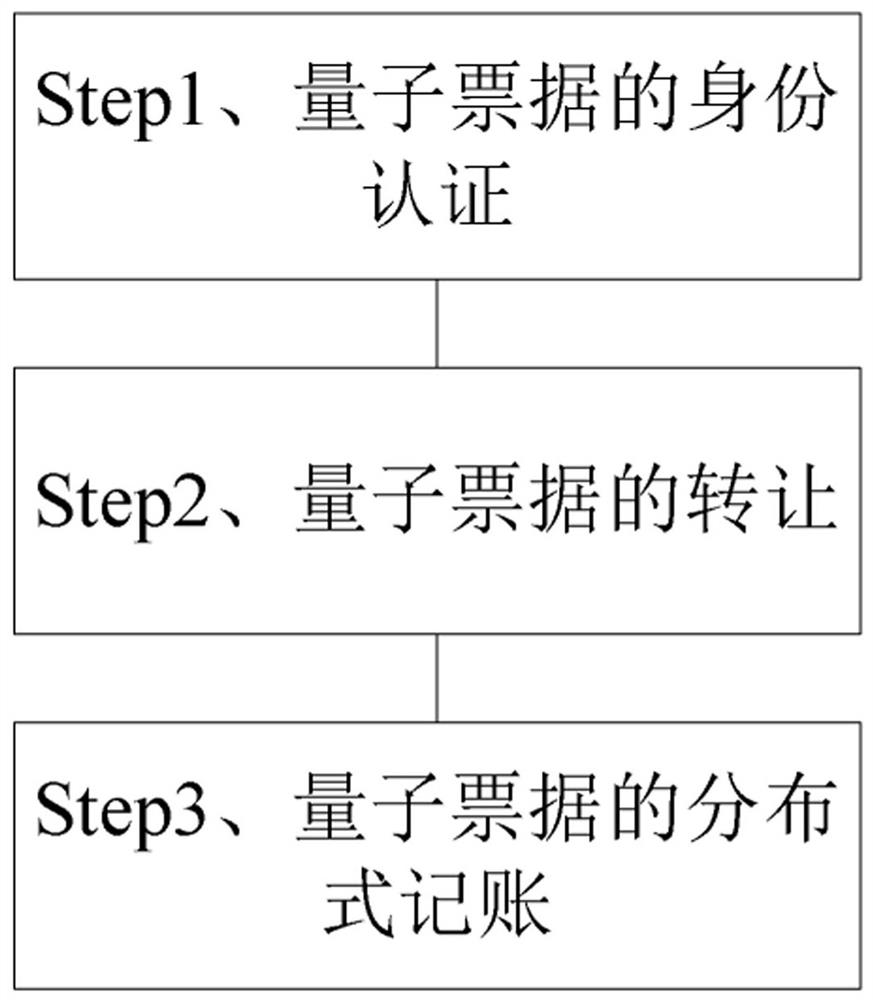
Quantum bill transfer settlement method based on smart contract
PendingCN113516467AImprove securityAvoid crackingFinanceDatabase distribution/replicationPaymentTransfer system
A quantum bill transfer settlement method based on a smart contract comprises the following steps: authenticating the identity of a quantum bill, registering the bill in a quantum bill smart contract transfer system when transfer or a transferee needs to transfer the bill, so that after the identity and legality are registered and verified, the transfer or transferee can transfer various quantum bills in the quantum bill intelligent contract transfer system; the transferring the quantum bill, concretely selecting a proper transfer mode for payment by the transfer or the transferee according to the characteristics of the quantum bill, taking the transfer as a bill debtor, performing quantum signature on the bill according to an intelligent contract, and transferring the quantum bill to the transferee after the signature succeeds; and implementing distributed bookkeeping of the quantum bill, wherein the quantum bill intelligent contract transfer system records of transfer and accepting records which comprise corresponding intelligent contract protocols, quantum bill transfer timestamps, block chain hash values and transferor and transferee information, so that the security of quantum bill transfer can be guaranteed.
Owner:CHINA THREE GORGES UNIV
A Public Key Arbitration Quantum Signature Protocol Based on Quantum Block Encryption
ActiveCN109787770BSave resourcesEnsure safetyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEngineeringKey distribution
The invention discloses a public key arbitration quantum signature protocol based on quantum block encryption, which belongs to the technical field of quantum security communication, including quantum key sharing among signers, receivers and arbitrations through quantum key distribution; signers Prepare two quantum messages and a quantum signature, send a quantum message to the receiver, and send the quantum signature to the arbitration; the receiver performs quantum signature verification under the constraints provided by the arbitration. The protocol provided by the invention can not only guarantee safety, but also has better practical application value.
Owner:ANHUI JIYUAN SOFTWARE CO LTD +6
Arbitrated Quantum Signature Method Based on Quantum Walk Teleportation
ActiveCN109257183BEasy signatureReduce overheadKey distribution for secure communicationUser identity/authority verificationTelecommunicationsEngineering
The invention discloses an arbitration quantum signature method based on quantum wandering stealth transmission, which comprisesan initialization phase for preparing a key and setting a system, a signature phase for constructing a signature of a transmission message, and a verification phase for verifying the validity of the signature, authenticity of the message source, and integrity of the message.The method of the invention adopts the stealth teleportation based on the quantum wandering to transmit the d-dimensional quantum state, and the entanglement source used for the stealth transmission does not need to be prepared in advance, thus saving the overhead of preparing the entangled state specially; Moreover, it is more efficient to measure with two projections of d elements. At the same time, the introduction of random parameters prevents the verifier from obtaining the content of the transmitted information and denying the signer's signature before accepting the signed information. In addition, the public board is used to publish the random parameters, and the verifier can obtain the information content of the signature after the verification is completed. Finally, the methodof the invention has the characteristics of saving resources, high measuring efficiency, easy realization of the laboratory and high signature security.
Owner:国科蓝盾(北京)科技有限公司
Quantum signature method based on secret sharing
PendingCN113849862AImprove securitySmall amount of calculationQuantum computersDigital data protectionThird partyAlgorithm
The invention discloses a quantum signature method based on secret sharing, which comprises three steps of initialization, signature generation and signature verification, and in the whole process, distribution of secret keys and partial verification and arrangement of signatures are carried out according to a reliable third party. Compared with other quantum signature schemes, the key distribution and encryption of the method do not involve complex encryption methods or complex quantum operations, and the method is more practical and higher in efficiency on the basis of meeting security, unforgeability and non-repudiation.
Owner:BEIJING INSTITUTE OF GRAPHIC COMMUNICATION
Arbitrated Quantum Signature Method Based on Bose Sampling Random Unitary Operation
ActiveCN111162913BReduce overheadImprove efficiencyKey distribution for secure communicationUser identity/authority verificationCommunications systemTheoretical computer science
The invention discloses an arbitration quantum signature method based on Bose sampling random unitary operation, including an initialization stage, a signature stage and a verification stage; the initialization stage is used to prepare a key and establish a communication system; the signature stage is used to select a suitable signature The algorithm designs the signature of the transmitted information; the verification phase is used to verify the validity of the signer and the integrity and authenticity of the original information. The present invention adopts the unitary operation encryption based on Bose sampling in the signature of the transmission information in the arbitration quantum signature, adopts the quantum walk teleportation based on the graph to transfer the m-mode quantum state, and the necessary entanglement state for teleportation does not need Prepared in advance, the employment of public channels and random tuples makes the security higher, and the teleportation model using the Bose sampling model and the quantum walk has been proven to be realized through a linear optical network; therefore, the method of the present invention has high security and saves resource and easy to implement experimentally.
Owner:CENT SOUTH UNIV
A Design Method of Arbitrated Quantum Signature Based on Grover Iterative Flexible Tracing
ActiveCN113242135BImprove fairnessEasy to operateKey distribution for secure communicationUser identity/authority verificationVerification systemManagement system
The invention discloses an arbitration quantum signature design method based on Grover iterative and flexible tracking. The design uses a Grover search algorithm to realize that when a signature dispute occurs, the arbitration management party can find the signer of the problematic signature. During the arbitration process, the arbitration management system negotiates with each signature participant to obtain the final key, find the signer of the problem signature, and avoid the direct "public" mechanism of the arbitration group signature. The present invention is characterized in that a complete arbitration signature verification system is established, and the arbitration management system can choose whether to disclose the identity of the signature signer of the problem, which has flexible traceability and fairness.
Owner:EAST CHINA JIAOTONG UNIVERSITY
Quantum computing-resistant signature method and signature system based on public key pool
ActiveCN109600228BUser identity/authority verificationCryptographic attack countermeasuresEngineeringQuantum computer
The invention discloses a quantum computing-resistant signing method based on a public key pool, and a signing system, wherein the signing method includes: the signing direction seal server requests to obtain an encrypted seal public key; The party uses the electronic seal to sign the document to generate a document with the electronic signature; the electronic signature includes at least the seal signature generated by the public key of the seal, and the anti-quantum signature containing the encrypted public key of the seal Calculate the public key; when verifying the seal, the seal verification direction seal server requests to obtain the public key key for the seal public key extracted from the anti-quantum computing public key, and uses the extracted seal public key to verify the seal signature.
Owner:RUBAN QUANTUM TECH CO LTD
Quantum digital signature method independent of reference system
ActiveCN114745129AReduce communication cost lossReduce technical difficultyKey distribution for secure communicationUser identity/authority verificationComputer hardwareDigital signature
The invention provides a quantum digital signature method independent of a reference system, which is applied to a quantum signature system. The quantum digital signature system comprises three participants of a user side Alice, a Bob and a Charlie, the Alice belongs to a signer, and the Bob and the Charlie belong to signed persons. The method comprises a key distribution stage and a message stage, in the key distribution stage, a key is generated by using a reference system independent quantum key distribution protocol, and then in the message stage, the quantum digital signature is completed by using the key generated in the above process. According to the protocol, a relatively high signature rate can still be kept under the condition that a relatively large deflection angle exists between user reference frames, and the performance of the protocol is superior to that of an existing BB84 quantum digital signature protocol.
Owner:NANJING UNIV OF POSTS & TELECOMM
A Hardware Acceleration Architecture and Method for Key Generation Based on Hash Post-Quantum Signature
ActiveCN113225185BIncrease profitImprove hardware utilizationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwarePower attack
Owner:NANJING UNIV
A block chain digital signature method, device and system based on quantum cryptography
ActiveCN113422681BEnsure safetyImprove securityKey distribution for secure communicationUser identity/authority verificationKey (cryptography)Digital signature
The invention discloses a block chain digital signature method, device and system based on quantum cryptography, which is applied to the entrusting party in the block chain, and the entrusting party is generated based on an election mechanism. The method includes: the receiver and the entrusting party receive Quantum signature and signature information; if the recipient passes the quantum signature verification, receive the quantum entrustment sent by the recipient; the entrusting party verifies the signature information based on the quantum entrustment; if the verification is passed, receive the private key pair sent by the recipient , verify the quantum signature based on the private key pair. In the above process, the quantum signature, quantum entrustment and private key pair are constructed based on the quantum key technology, and the entrusting party is selected based on the election mechanism, and the entrusting party uses the quantum key technology to verify the quantum signature. The party can fully guarantee its impartiality in message verification. Due to the high security of the quantum key, the security can be guaranteed without complex keys, and the efficiency of the signature is improved.
Owner:STATE GRID E COMMERCE CO LTD +2
More efficient post-quantum signatures
ActiveUS20220045865A1Public key for secure communicationUser identity/authority verificationTheoretical computer scienceSignature vector
Techniques of generating a lattice-based verification matrix and signature vector are disclosed. The method enables generating device to sample a gadget matrix and then generate a reduced gadget matrix. The generating device may then sample a trapdoor matrix and use the trapdoor matrix and the reduced gadget matrix to generate a verification matrix. A sending device may receive the trapdoor matrix and the verification matrix from the generating device, in addition to receiving a message. The sending device may then use the trapdoor matrix and the verification matrix to generate a signature vector for the message. A verification device can receive the verification matrix, the message, and the signature vector. The verification device may use the verification matrix and the signature vector to verify the message.
Owner:VISA INT SERVICE ASSOC
Nanoscale electrochemical interface for detection of analytes
A sensor can selectively detect quantum signatures in charge transfer processes via a tunneling current. The sensor can be designed to preferentially detect certain modulations in the tunneling current that can be indicative of a polarization mode or a range of polarization modes of a predetermined analyte. In one aspect, the sensor can include a metal electrode having a first surface and a secondsurface. The sensor can also include an insulator film having a first thickness, a first surface area and a first surface chemistry. The insulator film can be coupled to the metal electrode via the first surface. The sensor can also include a functionalization film having a second thickness, a second surface area and a second surface chemistry. The functionalization film can be coupled to the metal electrode via the second surface.
Owner:PROBIUSDX +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com