Patents
Literature
57 results about "Signature vector" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
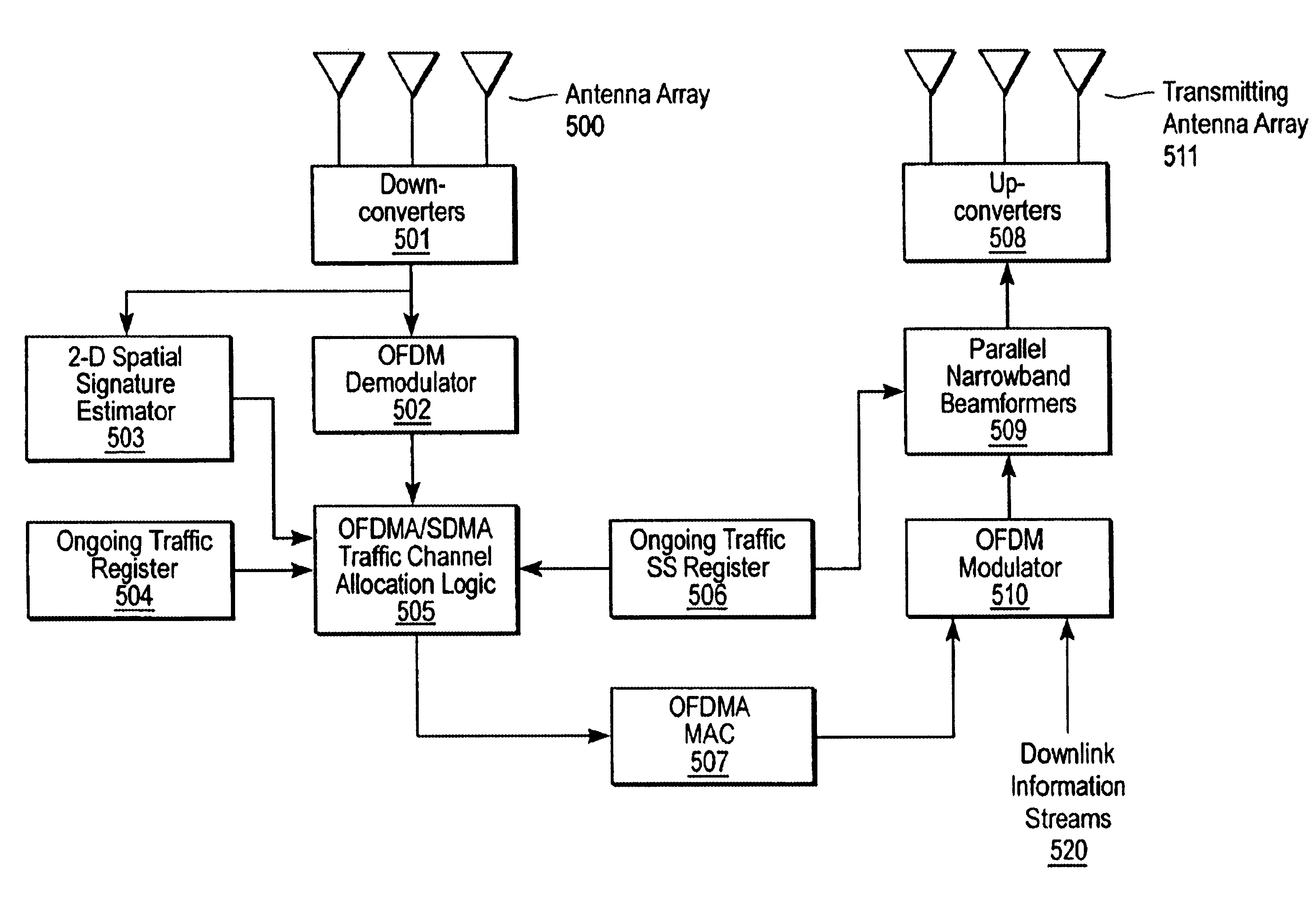
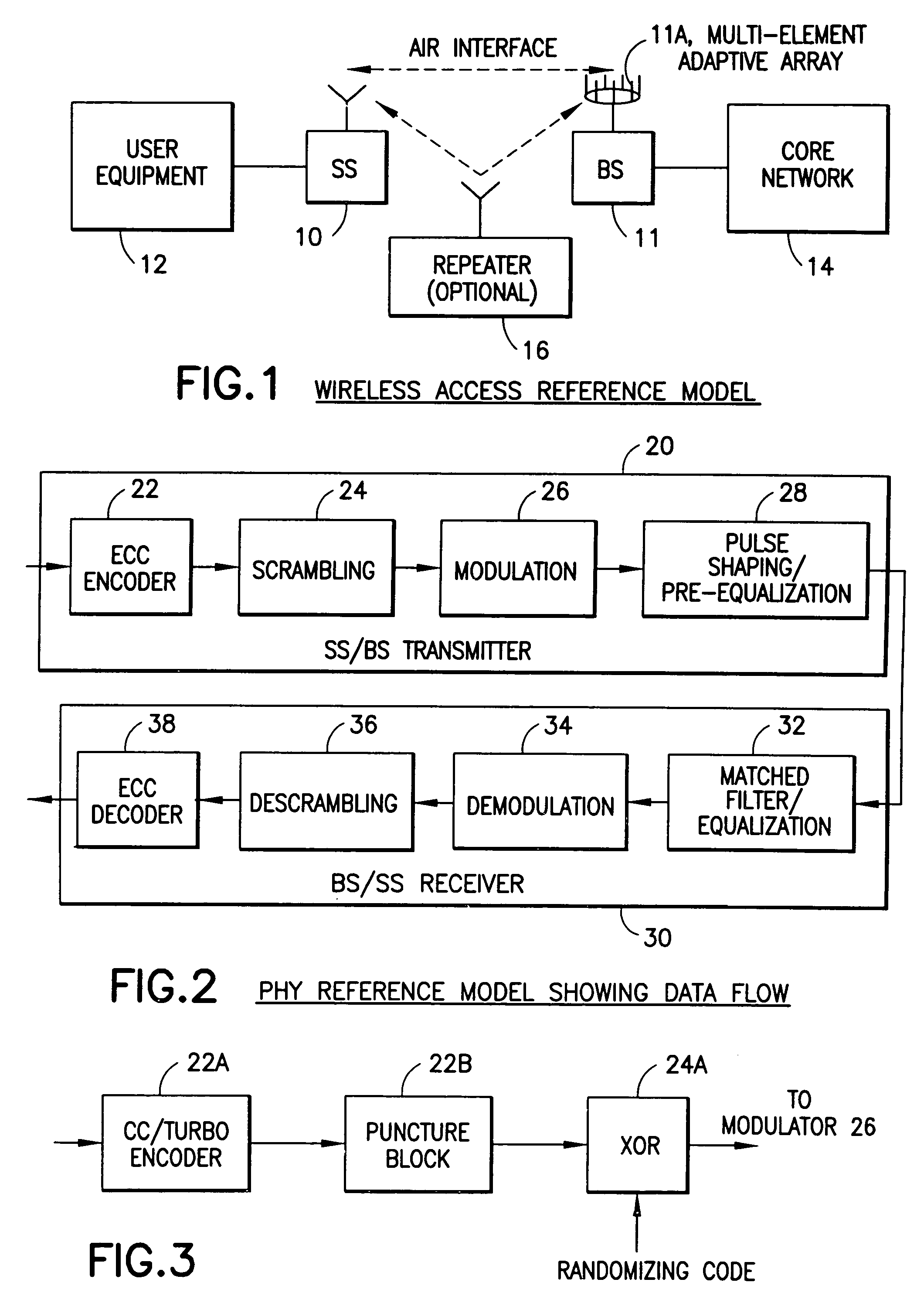
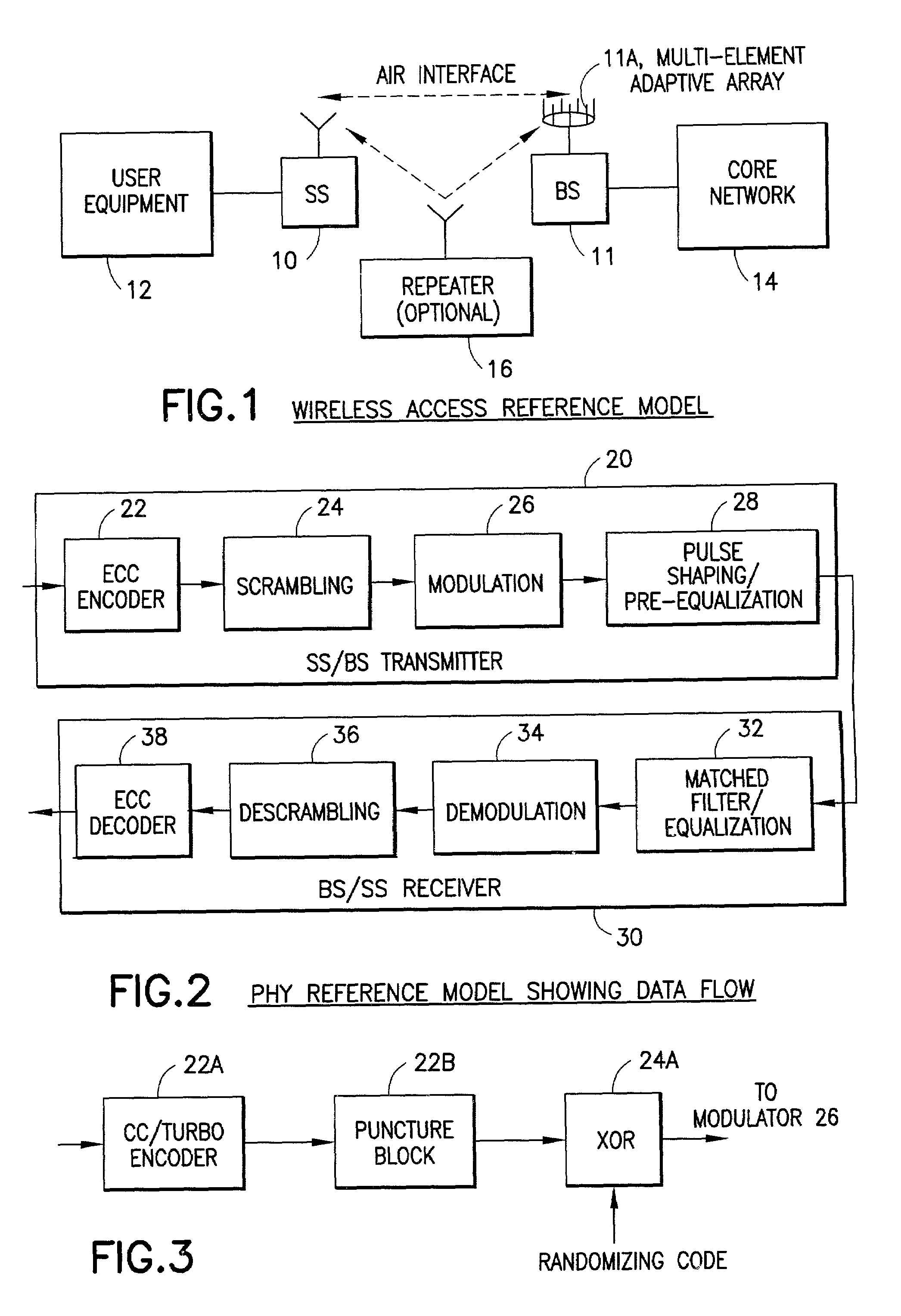
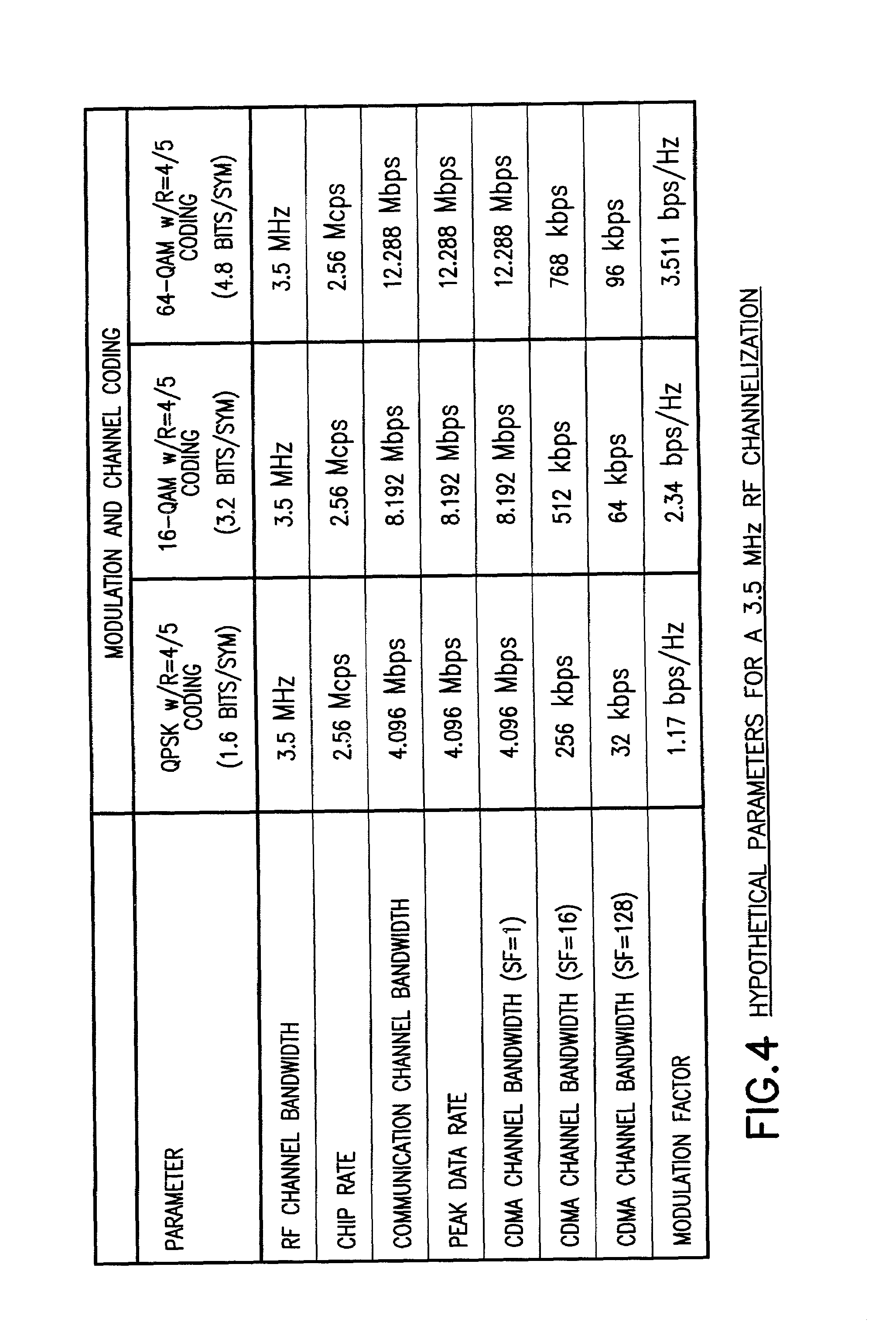
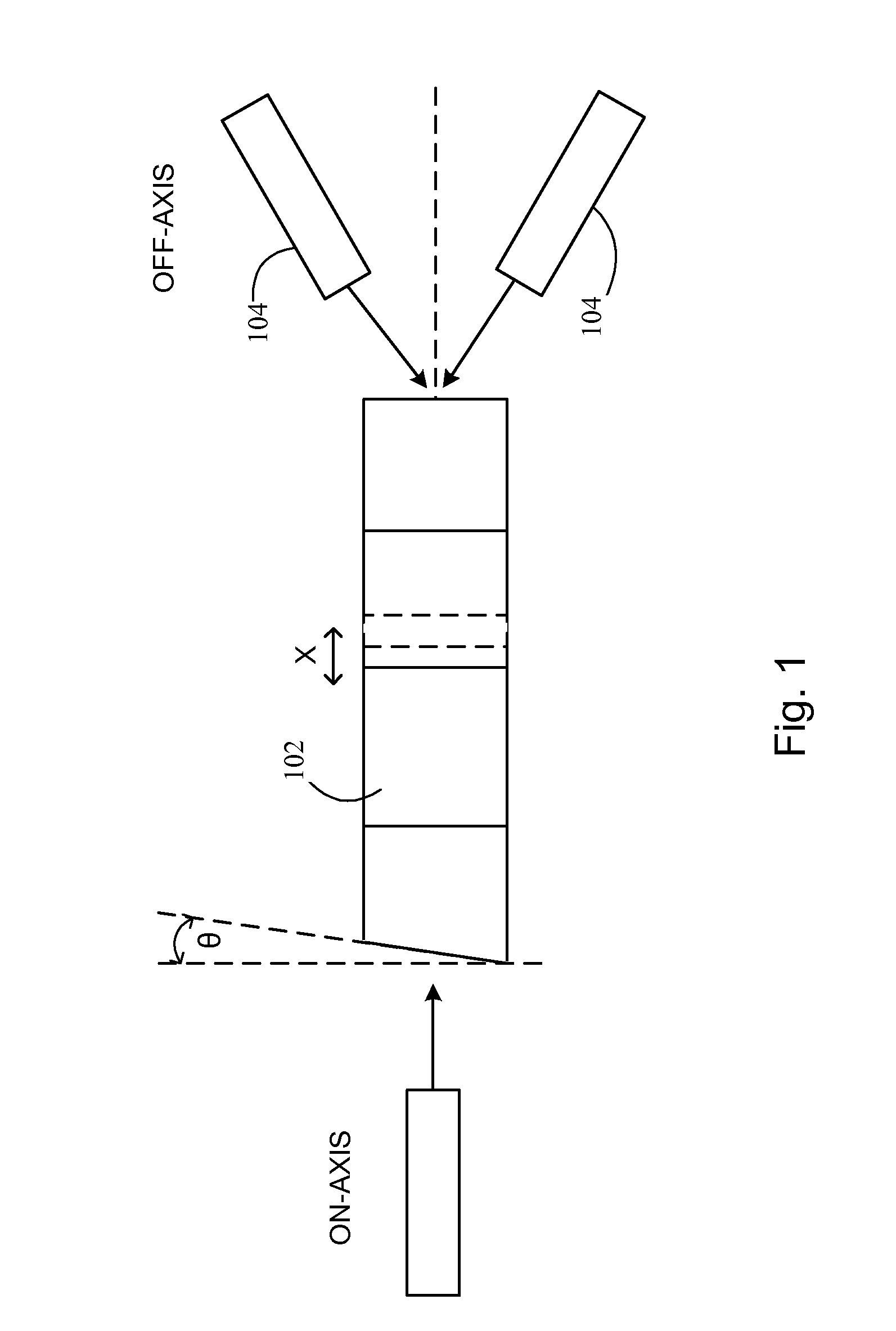
Channel allocation in broadband orthogonal frequency-division multiple-access/space-division multiple-access networks
A network is described. In one embodiment, the network comprises multiple subscriber units to communicate with the base station using an orthogonal frequency-division multiple-access (OFDMA) protocol, and a base station. The base-station includes a memory unit to store broadband spatial signature vectors associated with each subscriber and traffic channel allocation logic. The vectors are a function of frequency. The traffic channel allocation logic allocates OFDMA channels using the broadband spatial signature vectors of the subscribers.
Owner:ADAPTIX +1
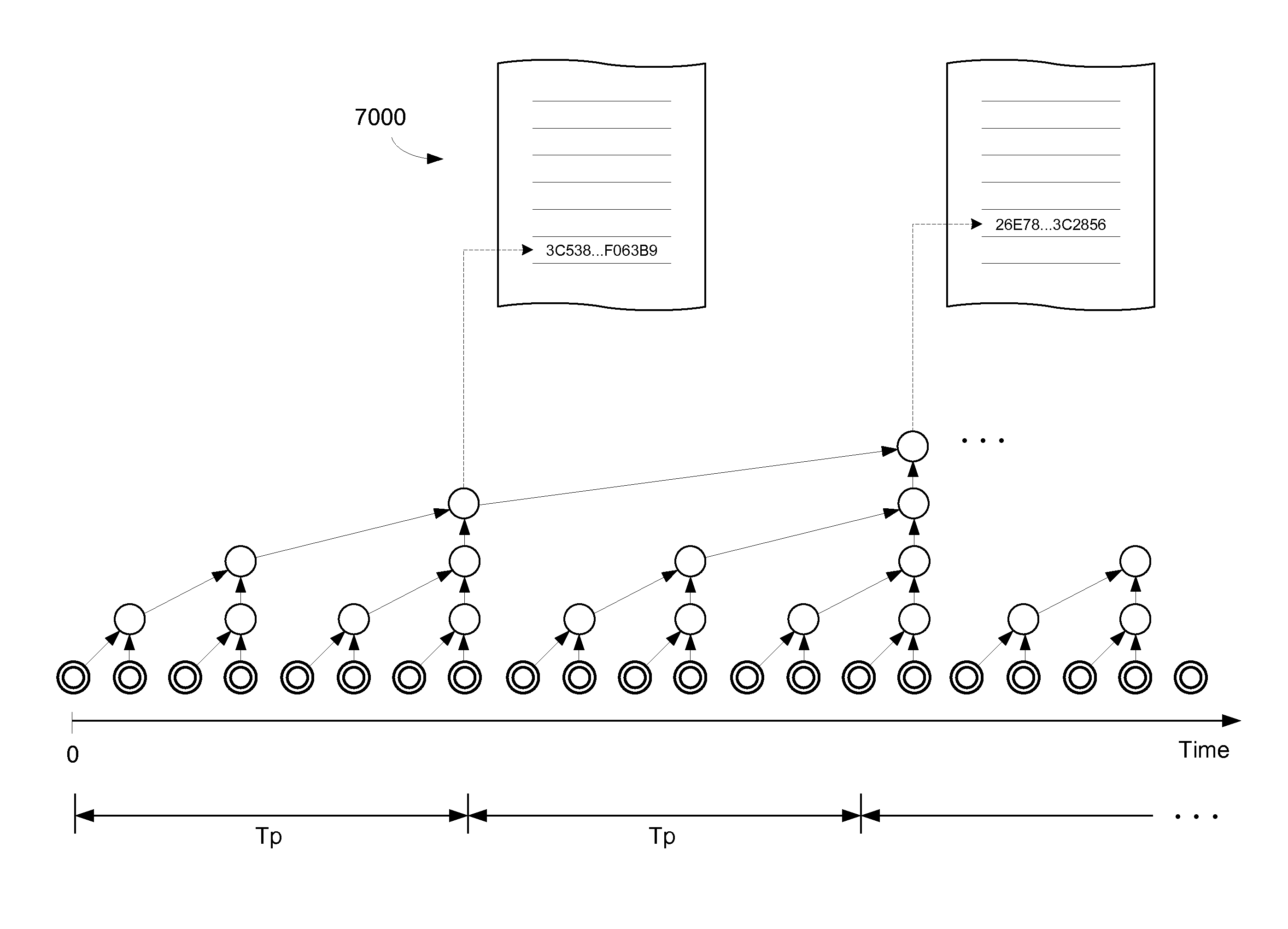
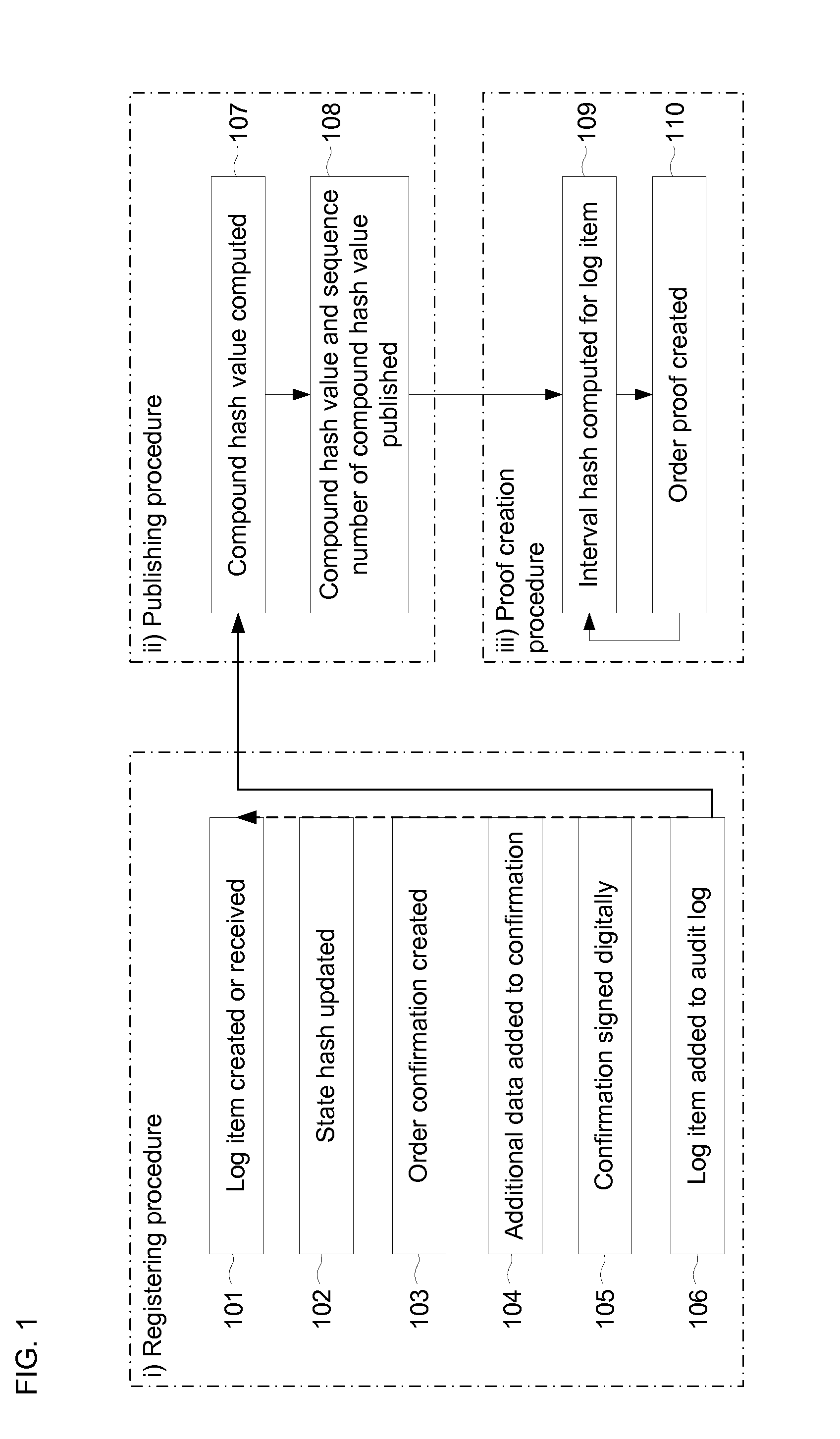
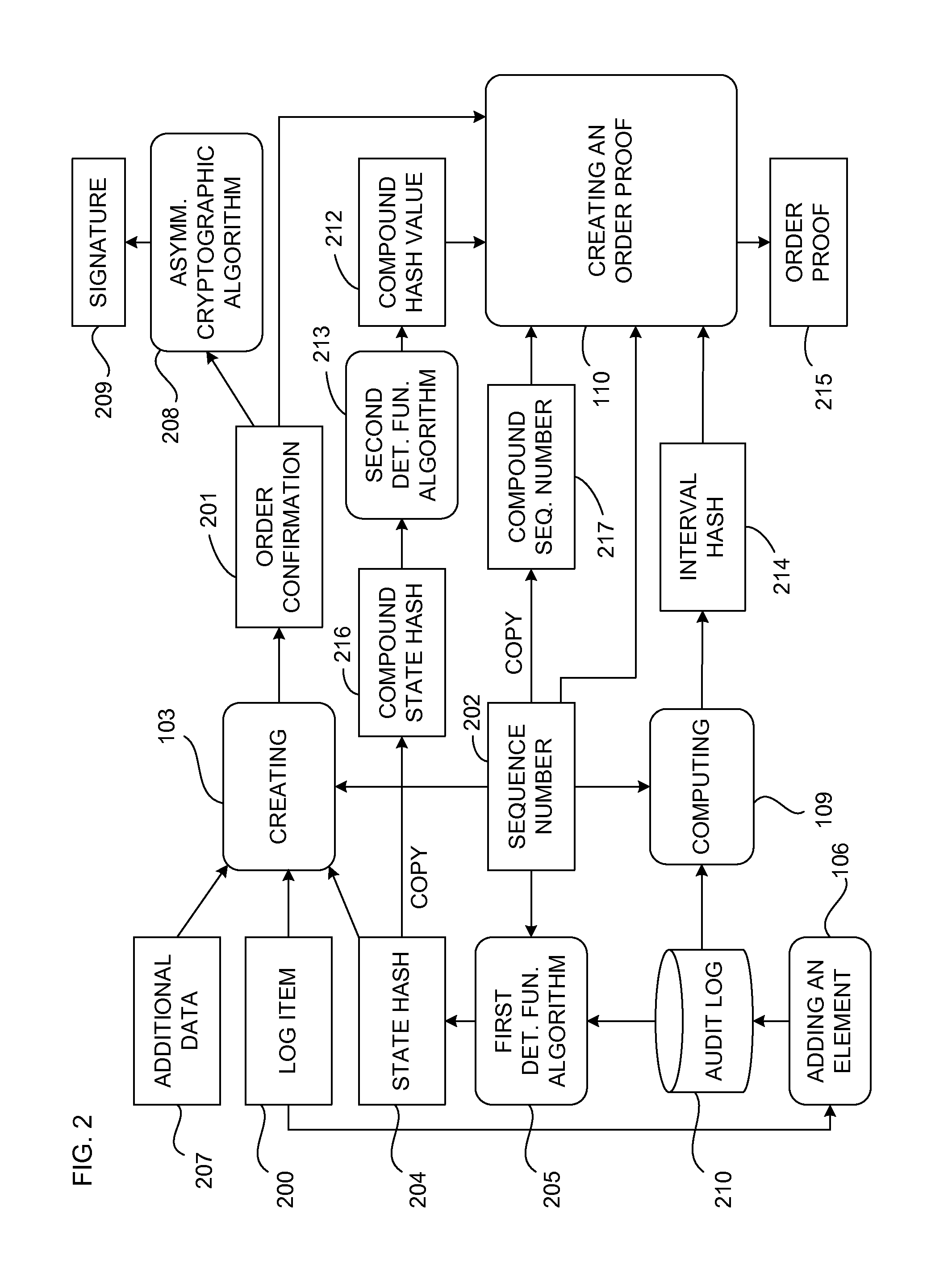
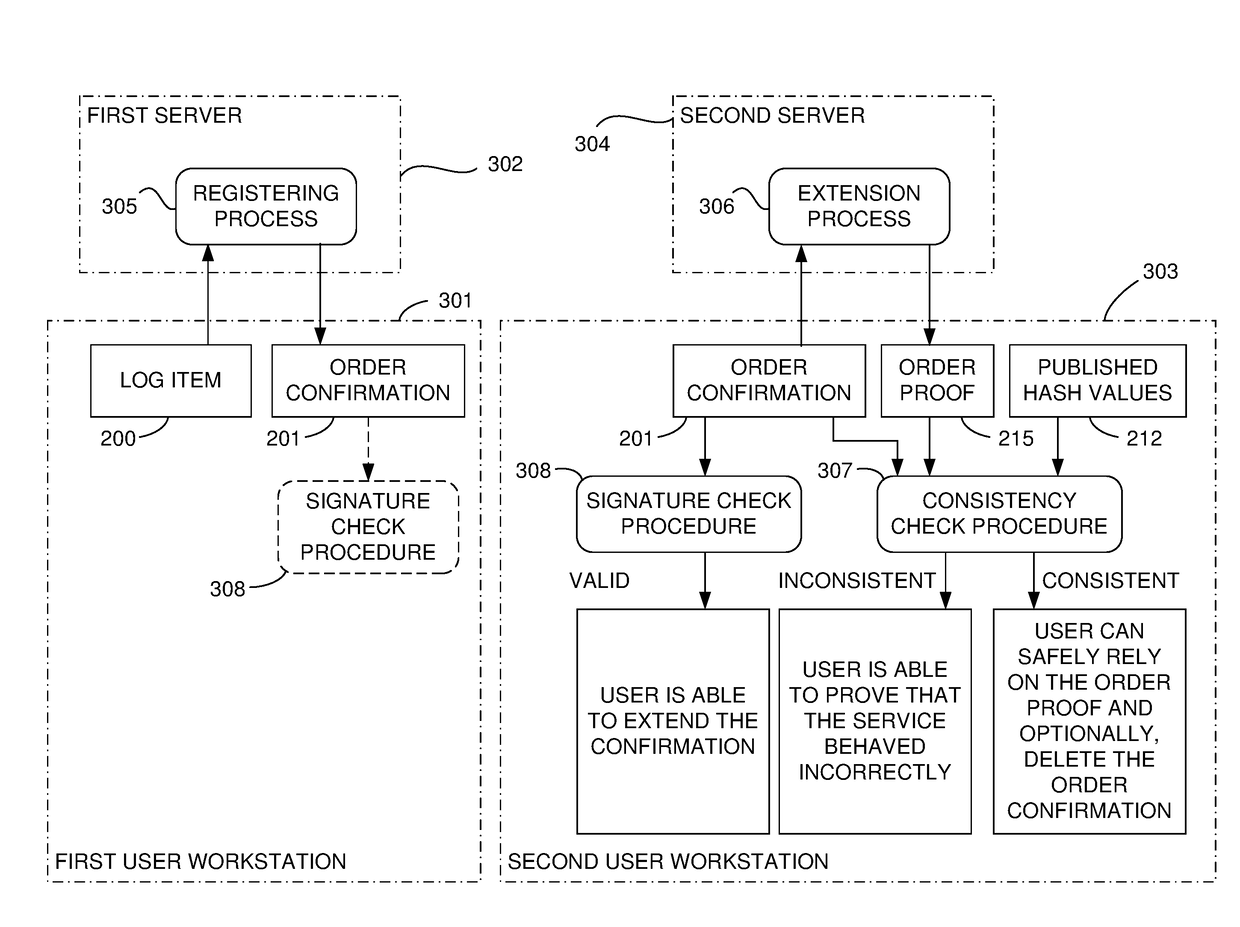
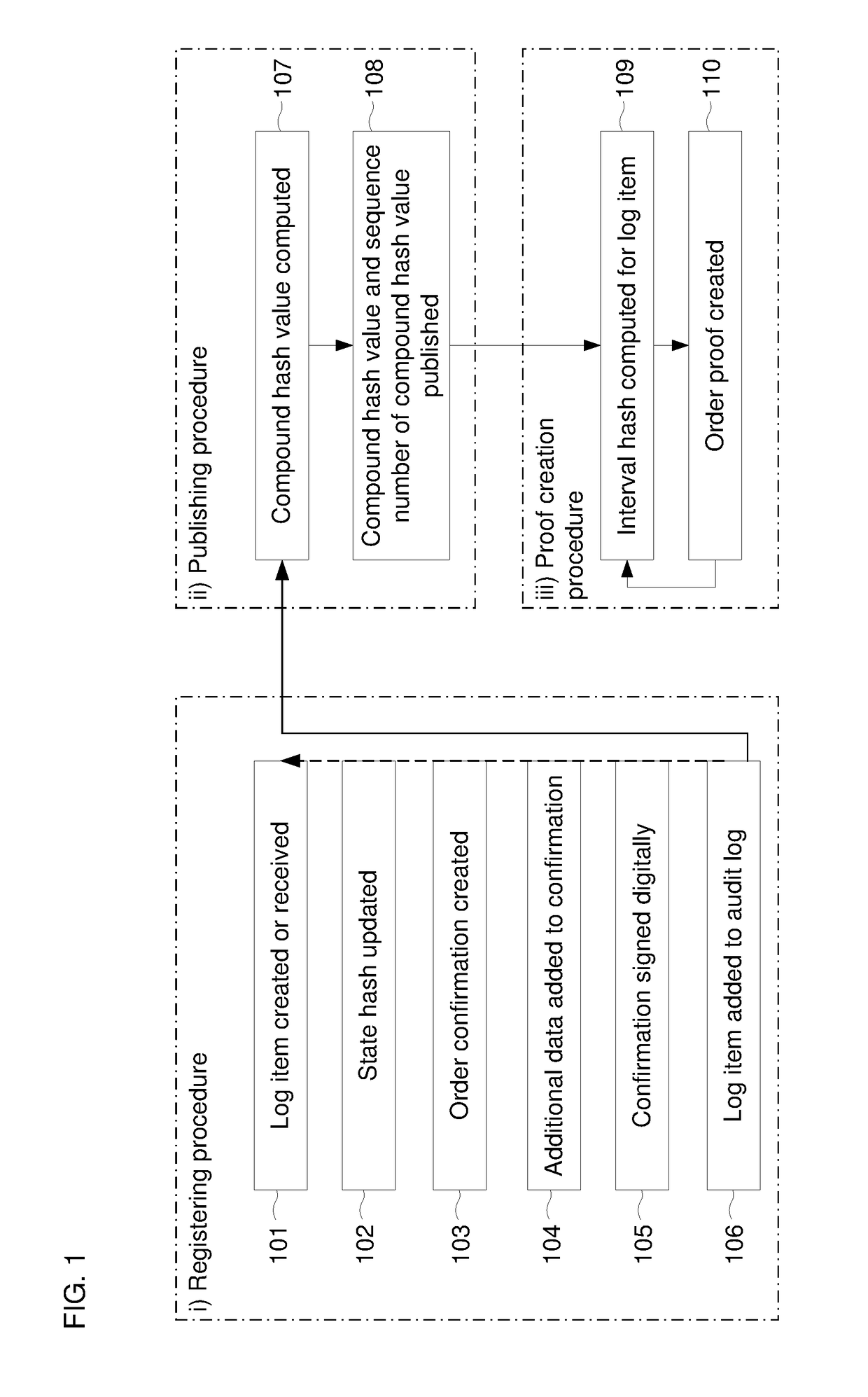
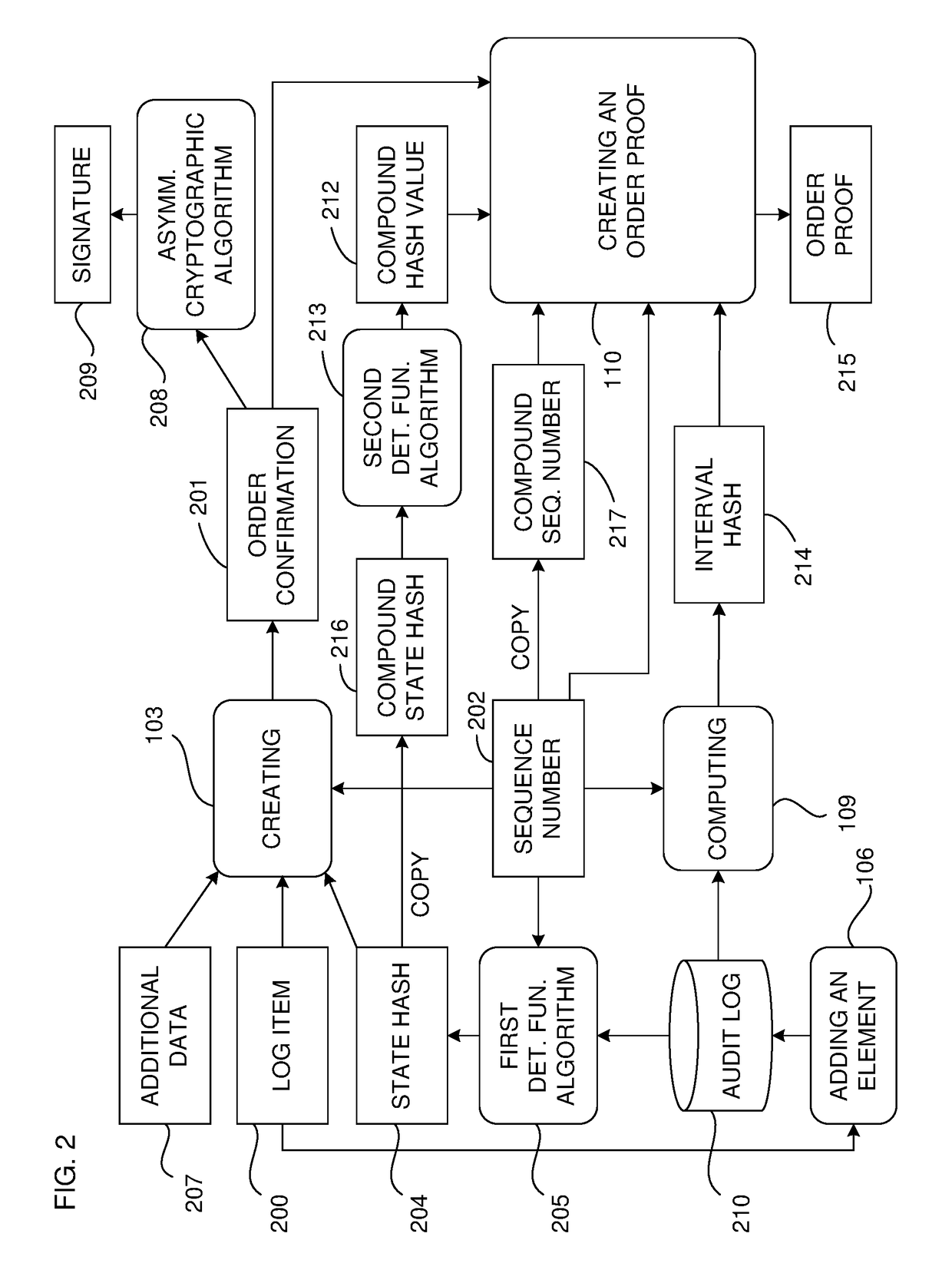
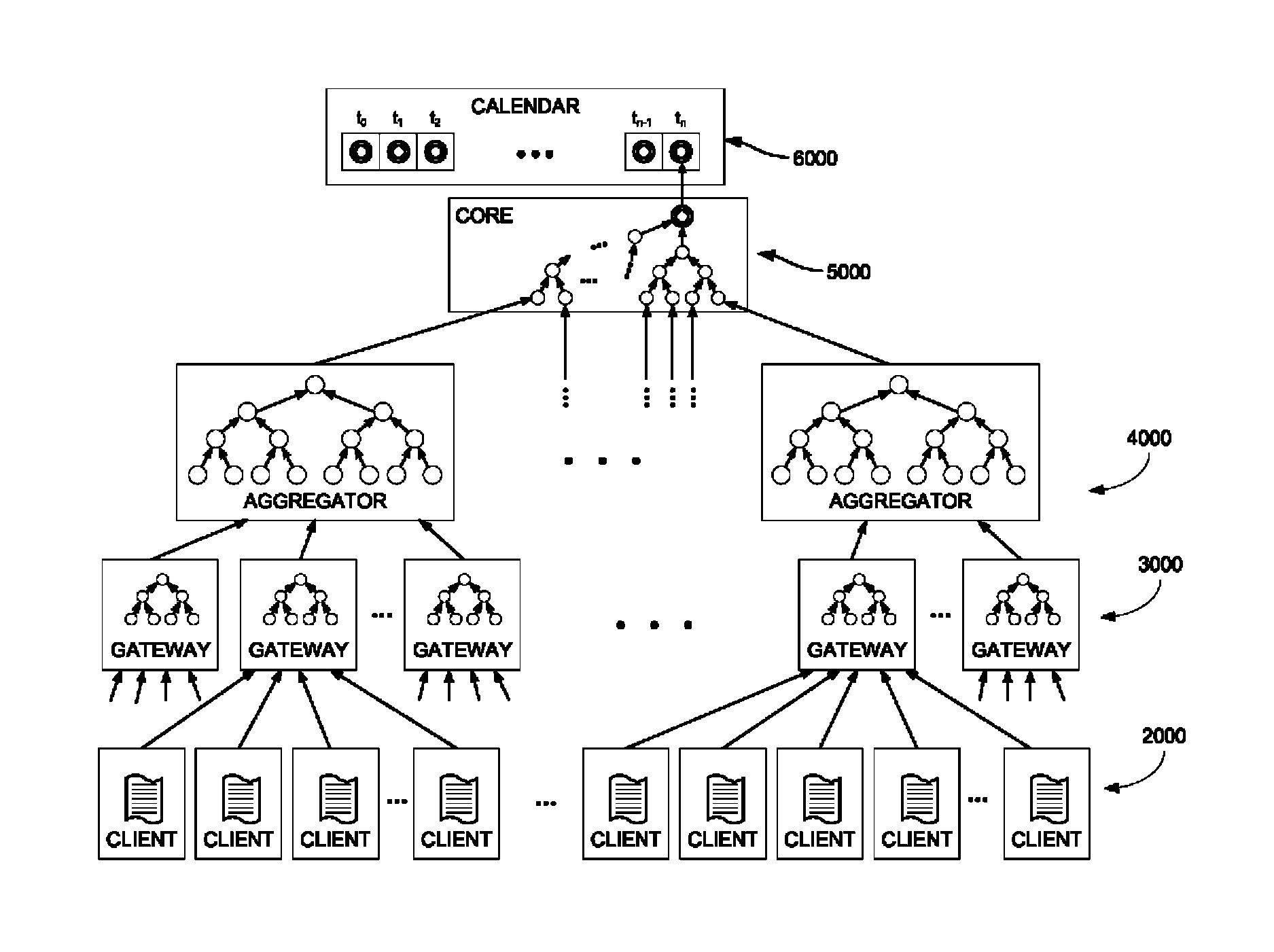
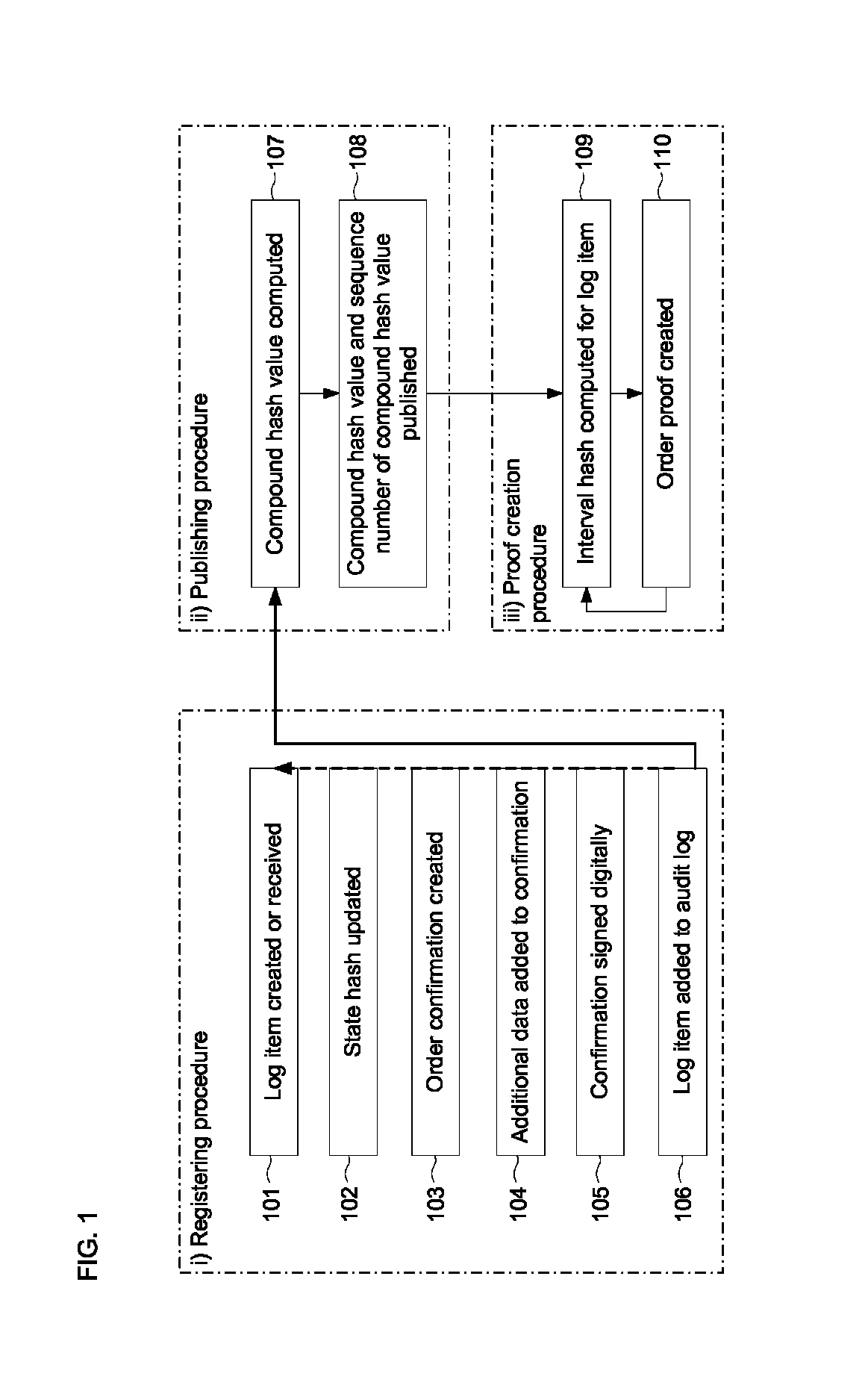
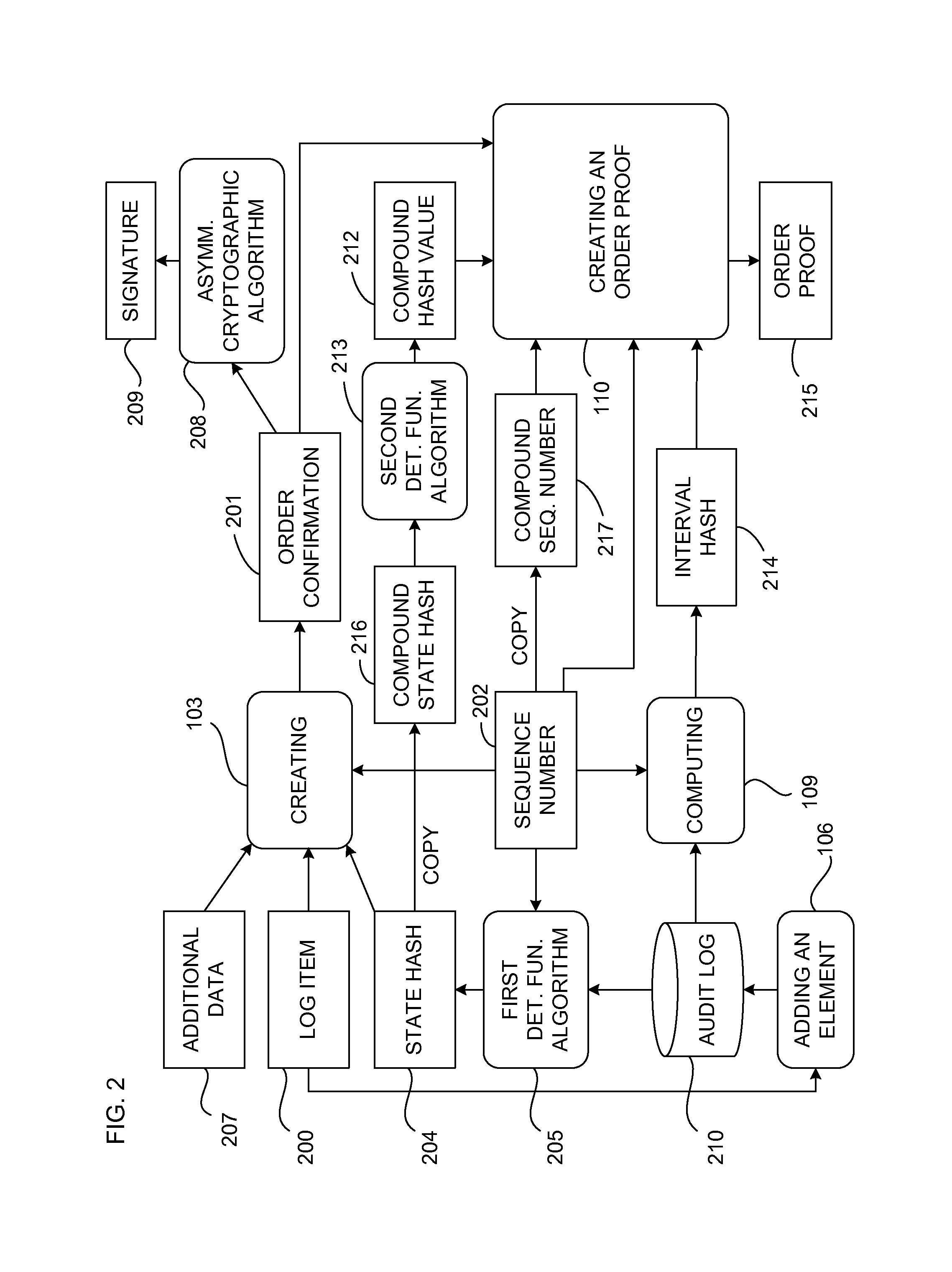
Document verification with distributed calendar infrastructure
ActiveUS20130276058A1Digital data processing detailsDigital data protectionTheoretical computer scienceDigital recording
Transformations of digital records are used as lowest level inputs to a tree data structure having a root in a core system and having nodes computed as digital combinations of child node values. A combination of root values is published in a permanent medium. Signature vectors are associated with the digital records and have parameters that enable recomputation upward through the tree data structure to either a current root value or to the published value. Recomputation yields the same value only if a candidate digital record is an exact version of the original digital record included in the original computation of the value.
Owner:GUARDTIME SA
Blockchain-supported, hash tree-based digital signature infrastructure
InactiveUS20180152442A1User identity/authority verificationDigital data protectionDigital signatureTree (data structure)
Transformations of digital records are used as lowest level inputs to a tree data structure having nodes computed as digital combinations of child node values up to a current calendar value. Signature vectors are generated for each of the digital records and have parameters that enable recomputation of the respective current calendar. Recomputation yields the same calendar value only if a candidate digital record is an exact version of the original digital record included in the original computation of the value. Either the current calendar value, or a function of a plurality of calendar values over a period, is encoded in a transaction value that is stored in a block of a blockchain.
Owner:GUARDTIME SA
Document verification with distributed calendar infrastructure
ActiveUS8719576B2Digital data processing detailsUser identity/authority verificationTheoretical computer scienceTree (data structure)
Transformations of digital records are used as lowest level inputs to a tree data structure having a root in a core system and having nodes computed as digital combinations of child node values. A combination of root values is published in a permanent medium. Signature vectors are associated with the digital records and have parameters that enable recomputation upward through the tree data structure to either a current root value or to the published value. Recomputation yields the same value only if a candidate digital record is an exact version of the original digital record included in the original computation of the value.
Owner:GUARDTIME SA
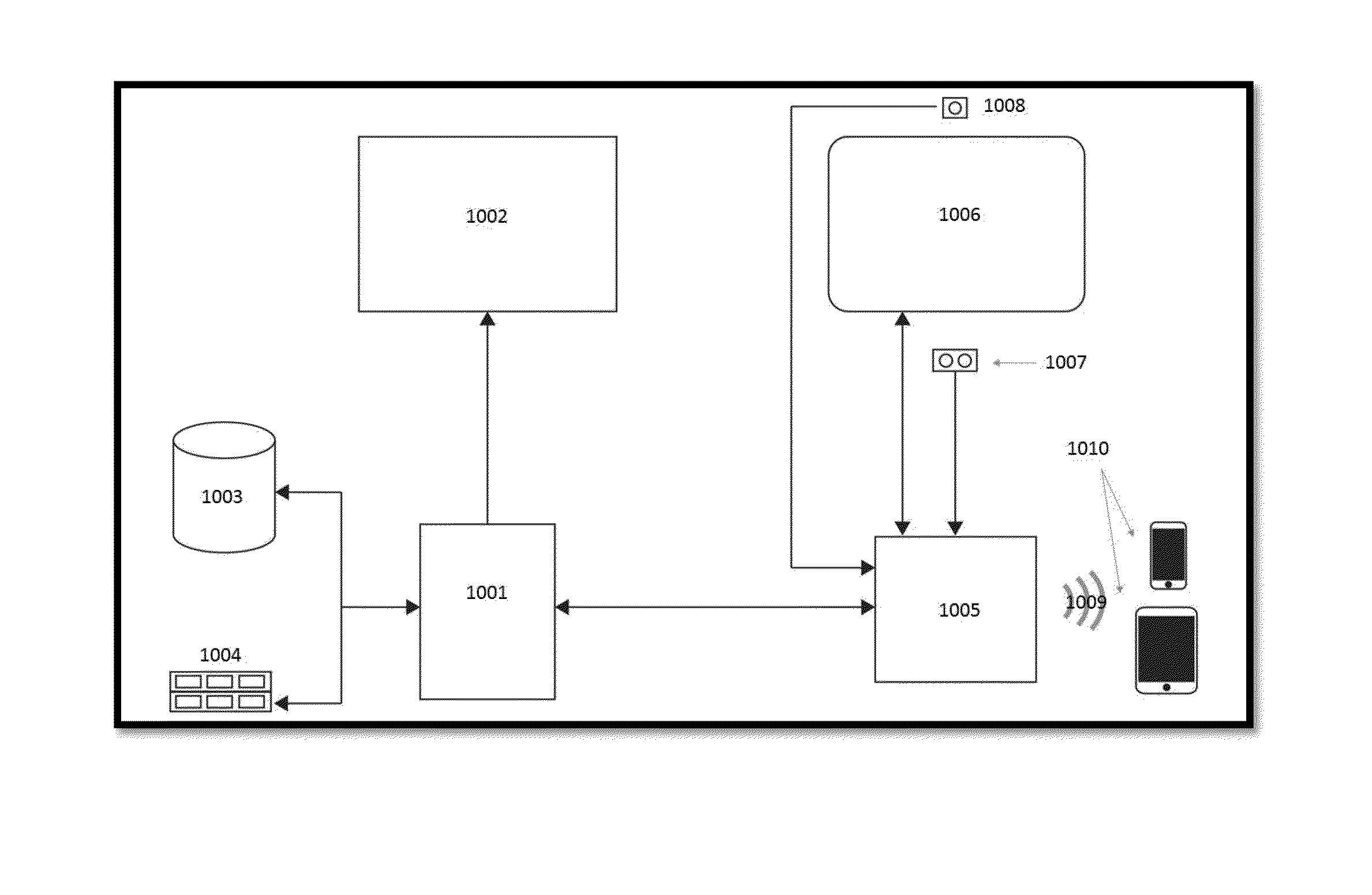
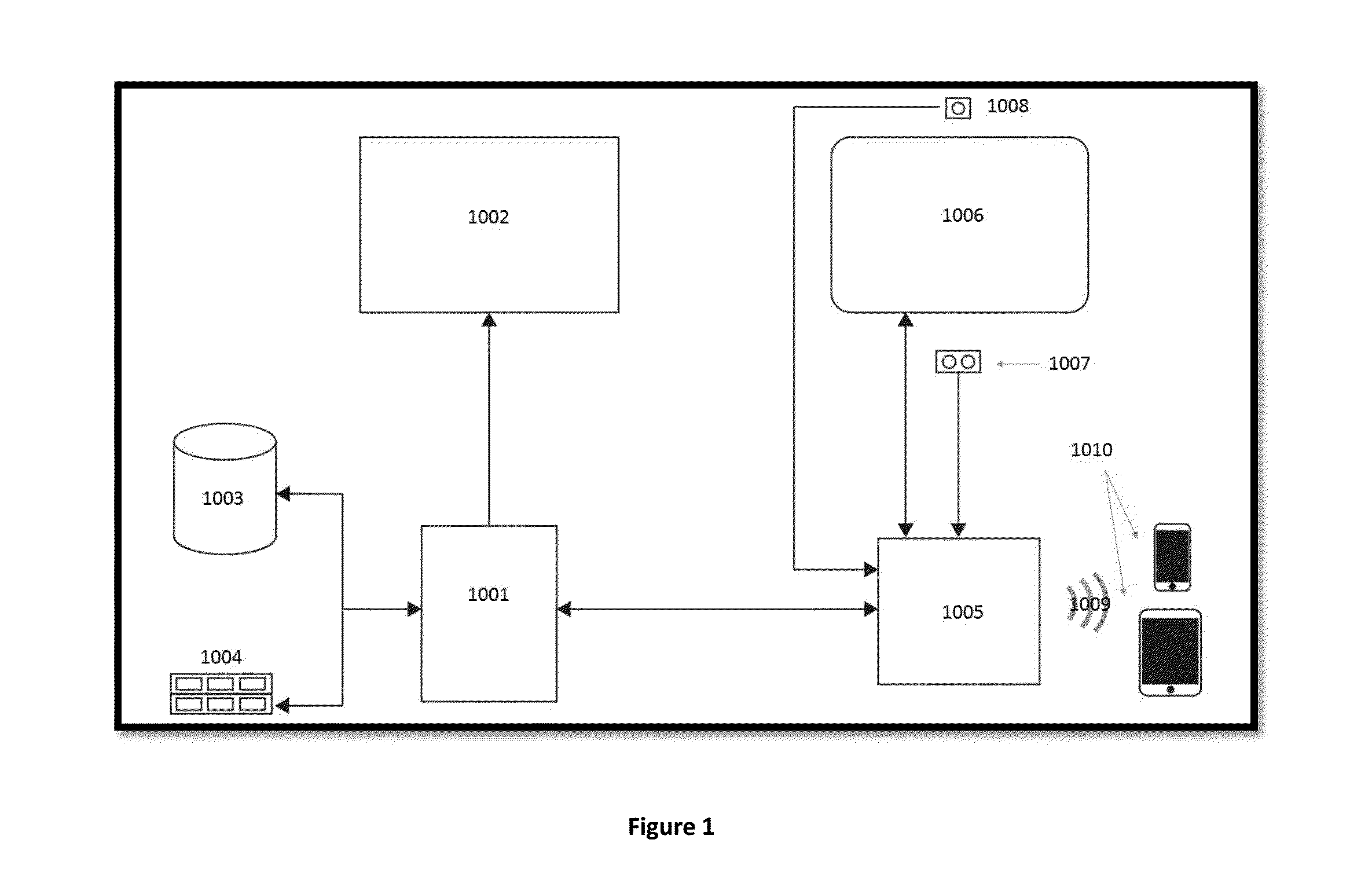
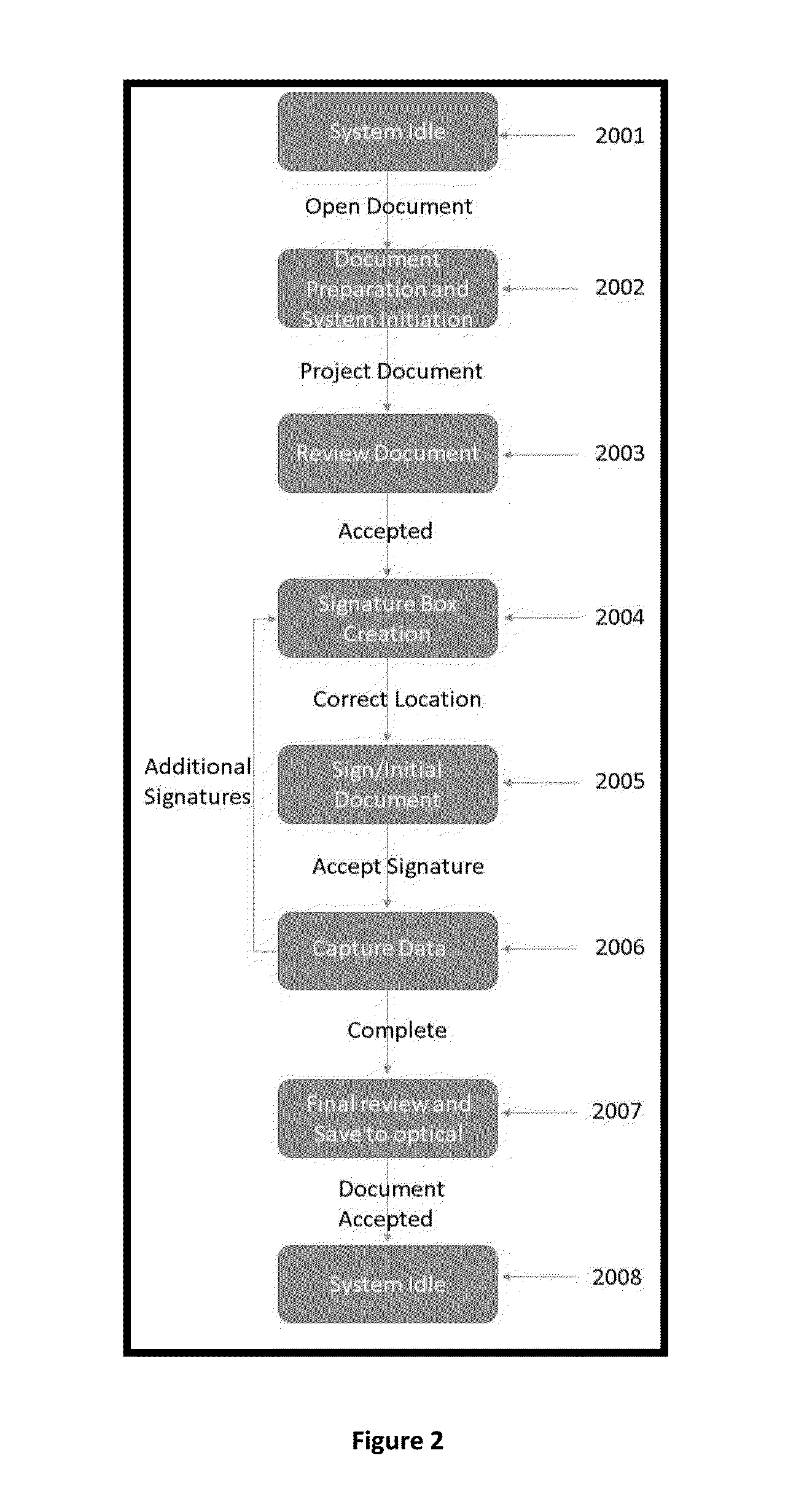
Method and System for Collaborative, Streaming Document Sharing with Verified, On-Demand, Freestyle Signature Process
InactiveUS20160224528A1Improve securitySignificant valueTelevision system detailsCustomer relationshipProcess systemsTouchscreen
Systems and methods for the sharing, collaborative reviewing and freestyle multiparty signing of an electronic document. The system and method to stream an electronic document from a CSR system onto a touchscreen device for real time and multiple signature placement anywhere within an electronic document. Placement of signature is determined by tapping and holding any point on a document to create a signature box which can be relocated and anchored anywhere on the electronic document. The electronic document is then signed via a touchscreen device and the system captures signature vector-based individual strokes and timing data of the signature strokes and stored with the document. The system uses a camera to take a picture of the signee and embeds the image, time stamp, location, and signature data in the electronic document.
Owner:TECH HAPPENS LLC
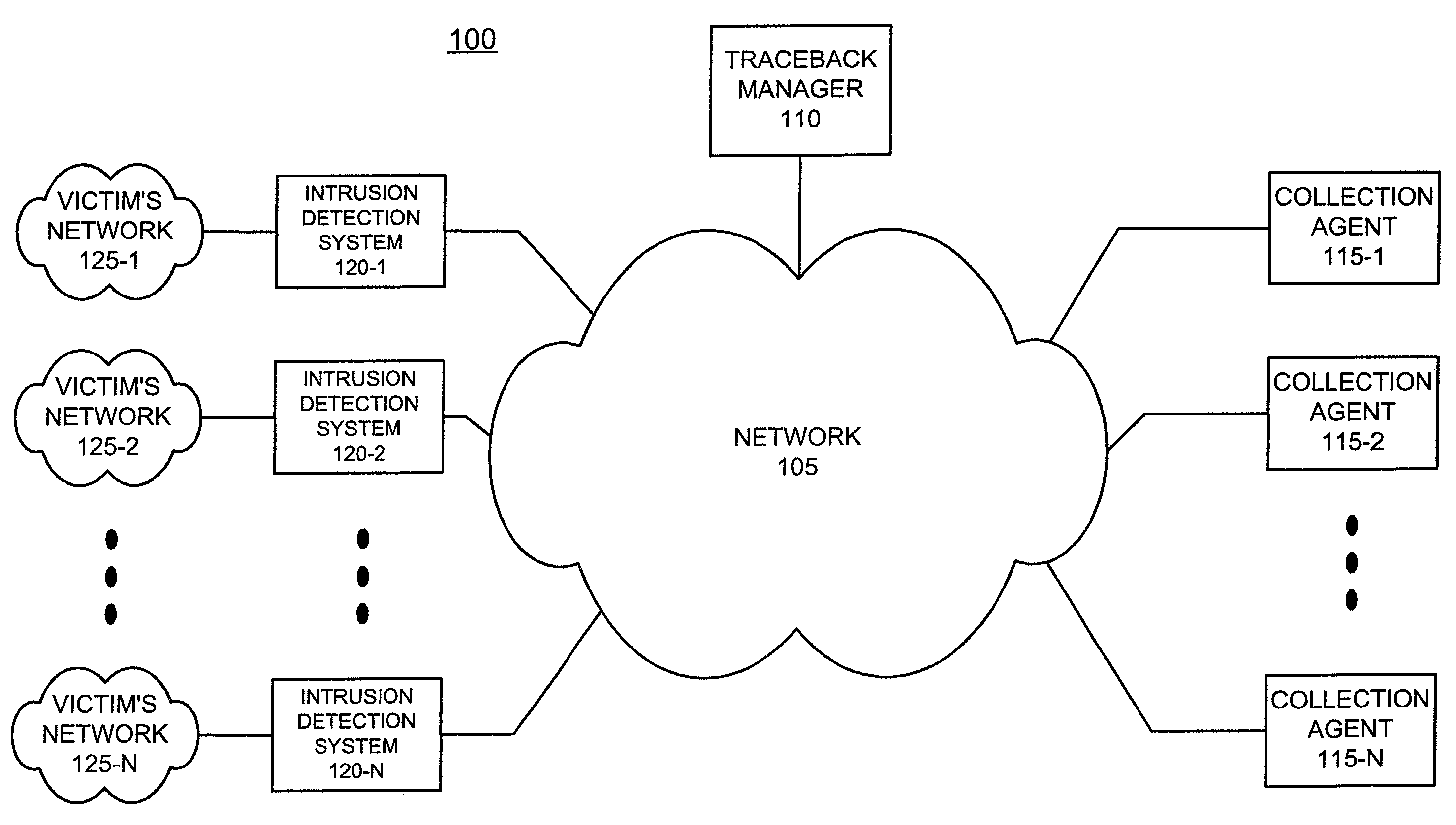
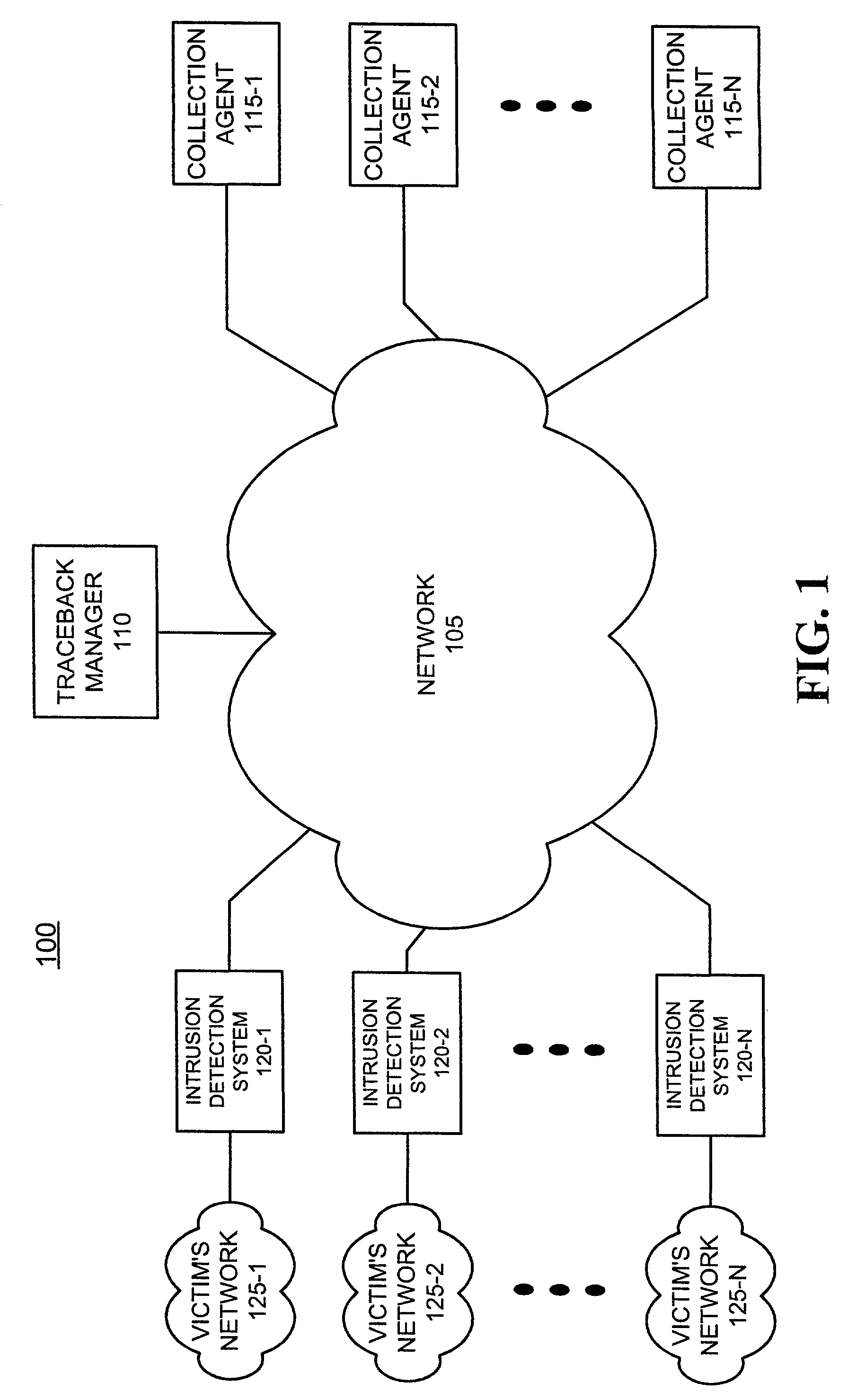
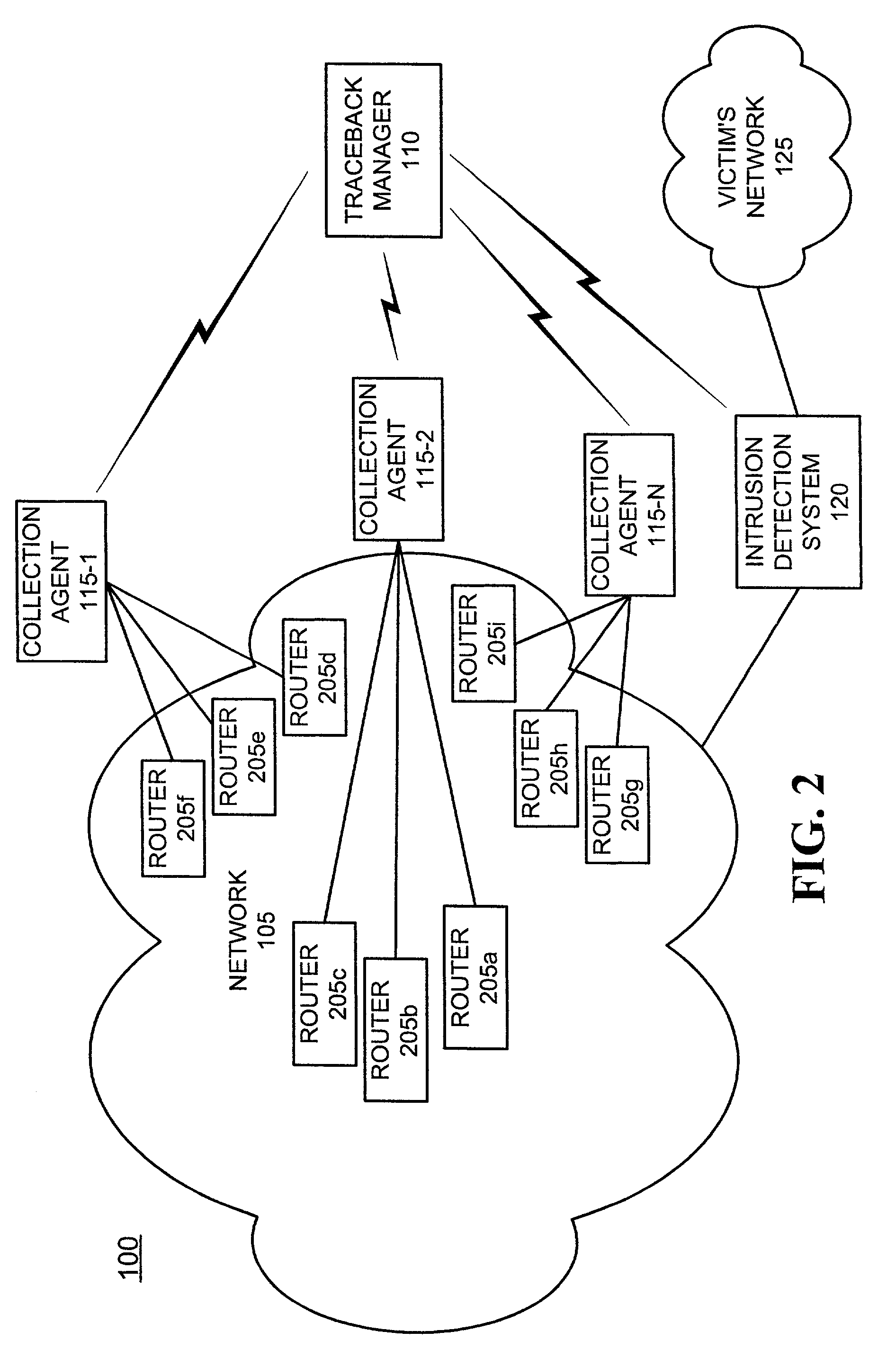
Systems and methods for point of ingress traceback of a network attack
An apparatus (520) for archiving signatures associated with packets received at a node in a network includes a first memory (620), a second memory (625), a signature tap (610), a multiplexer (615), and a controller (630). The signature tap (610) receives packets at the node and computes one or more signatures for each of the received packets. The multiplexer (615) aggregates the computed one or more signatures in the first memory (620) to produce one or more signature vectors. The controller (630) archives the one or more signature vectors in the second memory (625).
Owner:TRI COUNTY EXCELSIOR FOUND +1
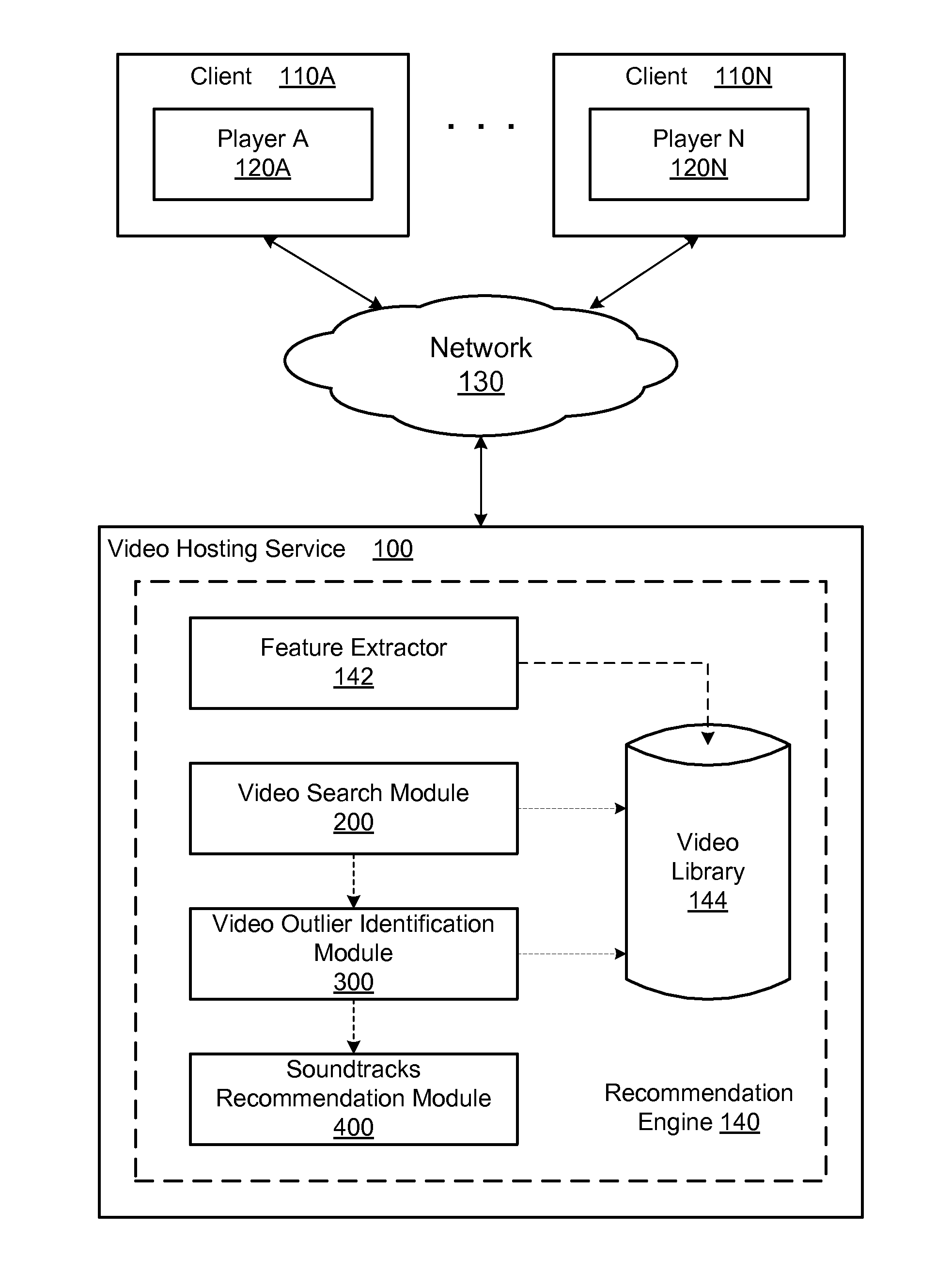
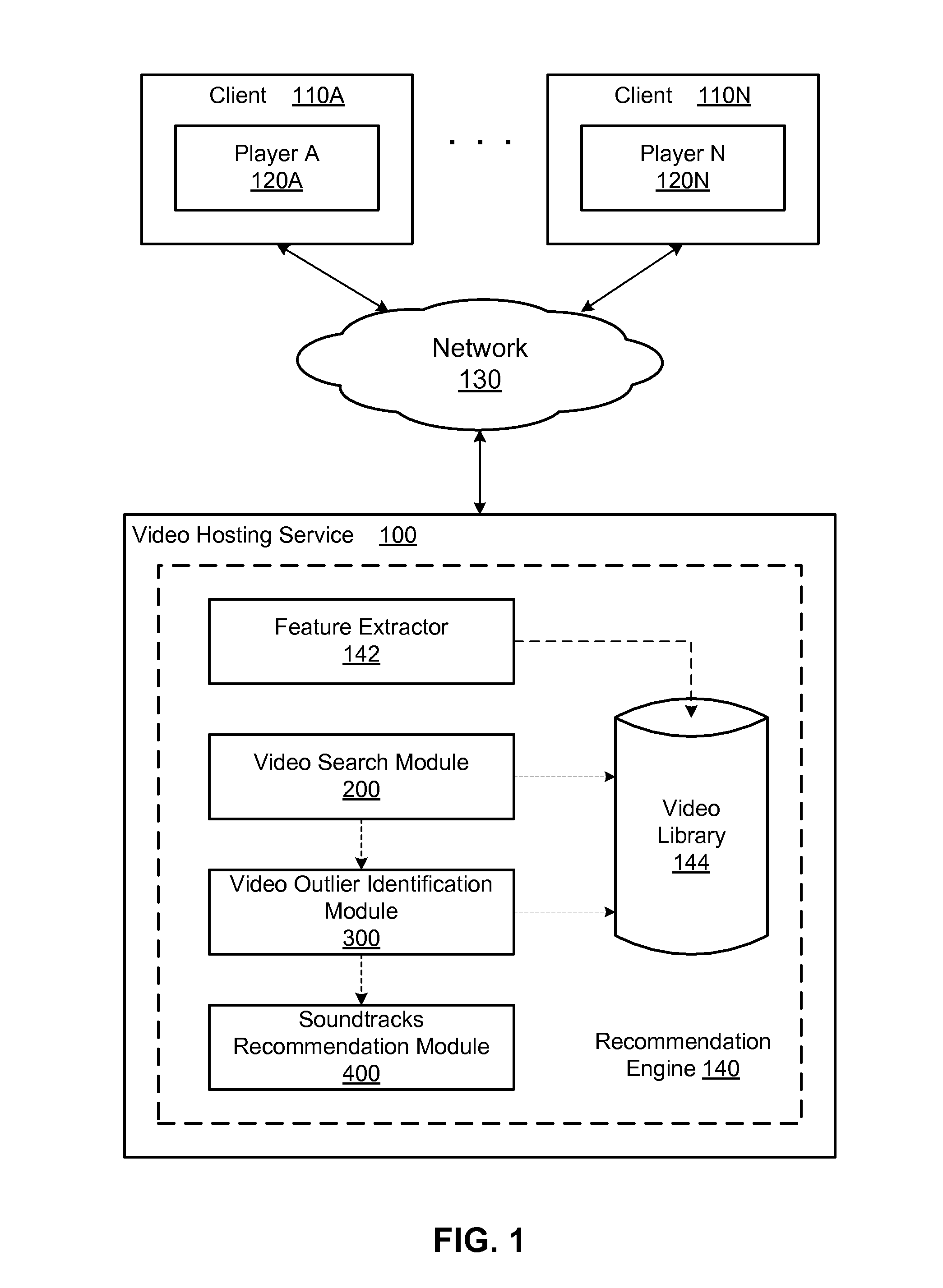
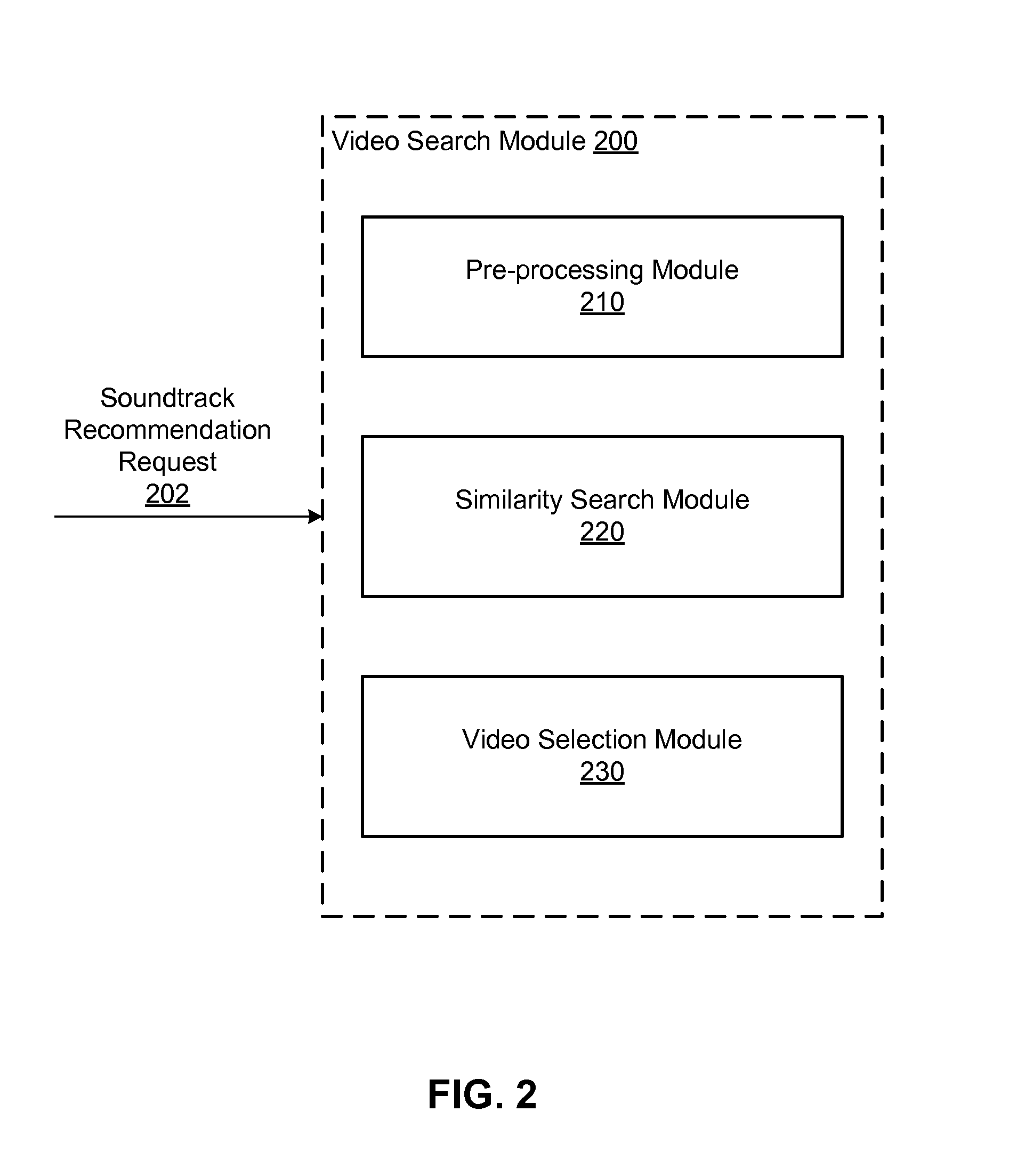
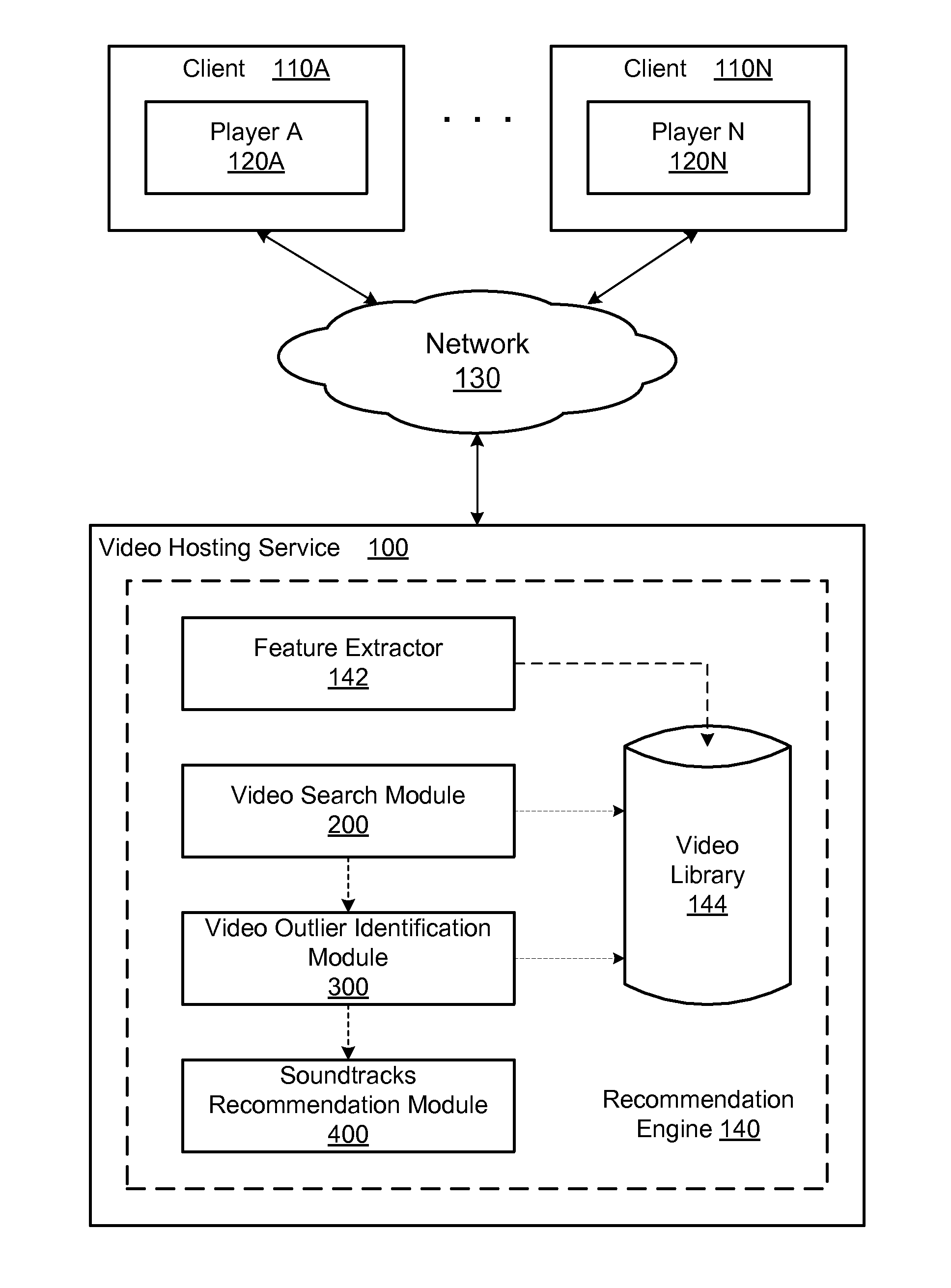
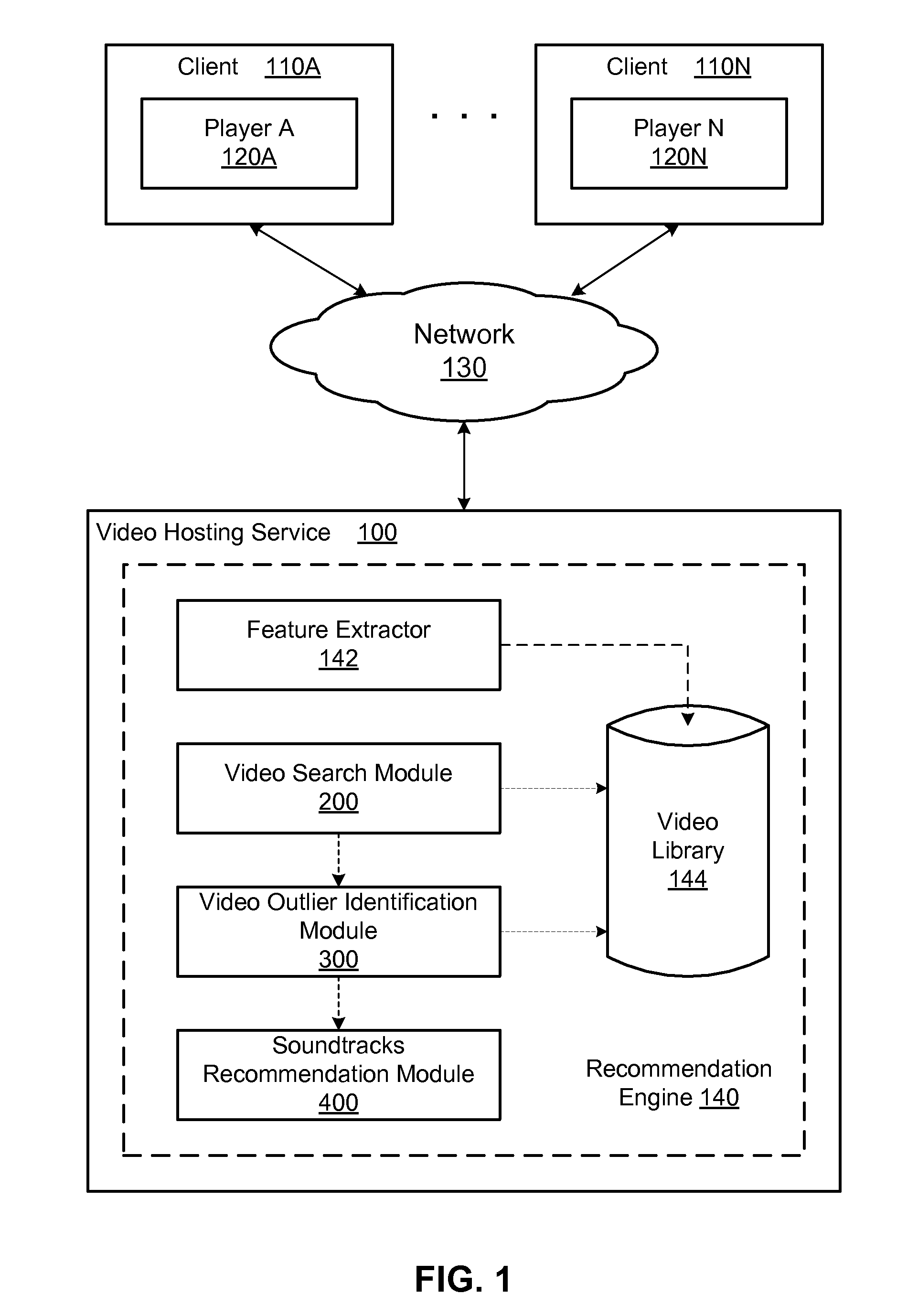
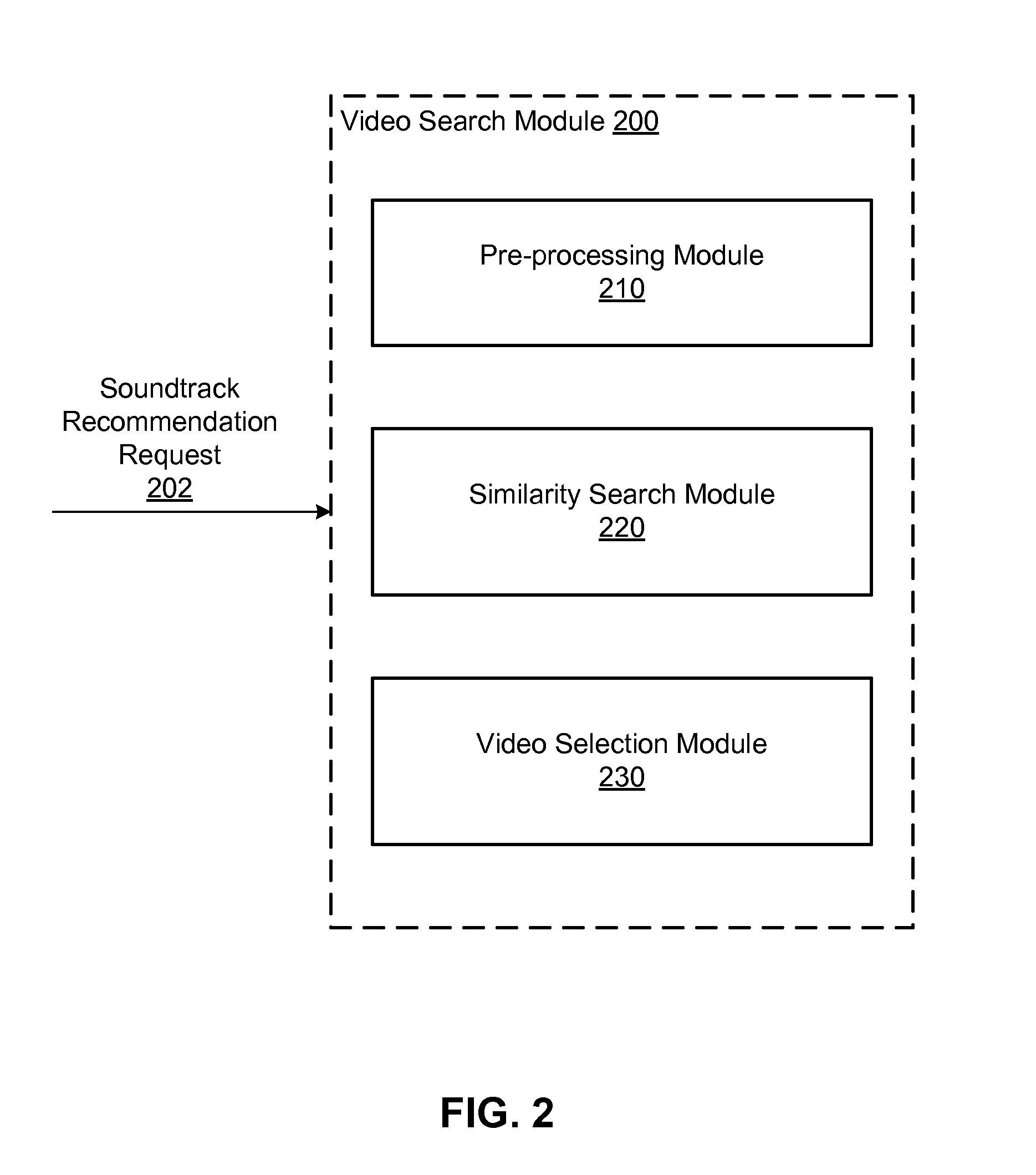
Music soundtrack recommendation engine for videos
A system and method provide a soundtrack recommendation service for recommending one or more soundtrack for a video (i.e., a probe video). A feature extractor of the recommendation service extracts a set of content features of the probe video and generates a set of semantic features represented by a signature vector of the probe video. A video search module of the recommendation service is configured to search for a number of video candidates, each of which is semantically similar to the probe video and has an associated soundtrack. A video outlier identification module of the recommendation service identifies video candidates having an atypical use of their soundtracks and ranks the video candidates based on the typicality of their soundtrack usage. A soundtrack recommendation module selects the soundtracks of the top ranked video candidates as the soundtrack recommendations to the probe video.
Owner:GOOGLE LLC
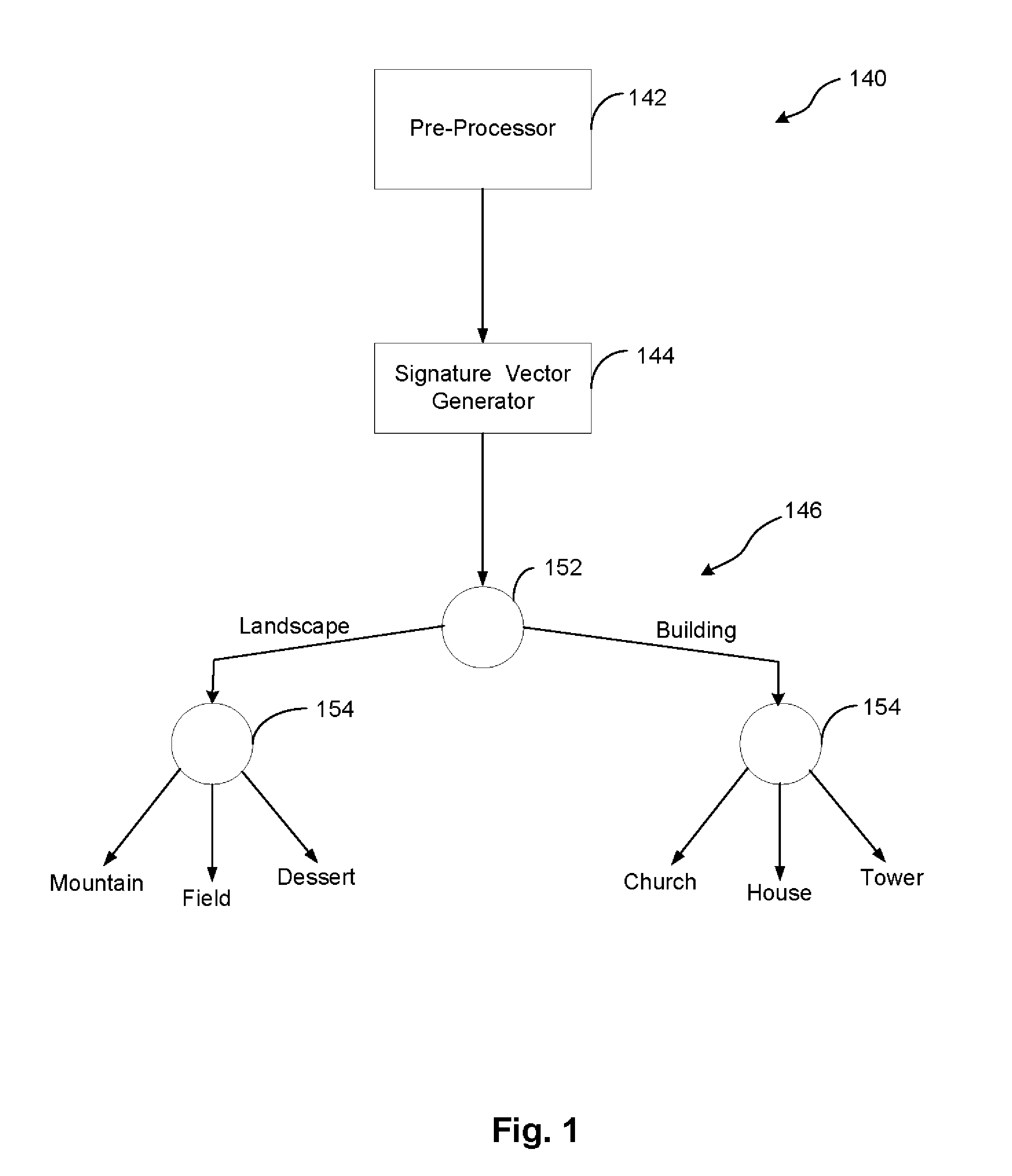
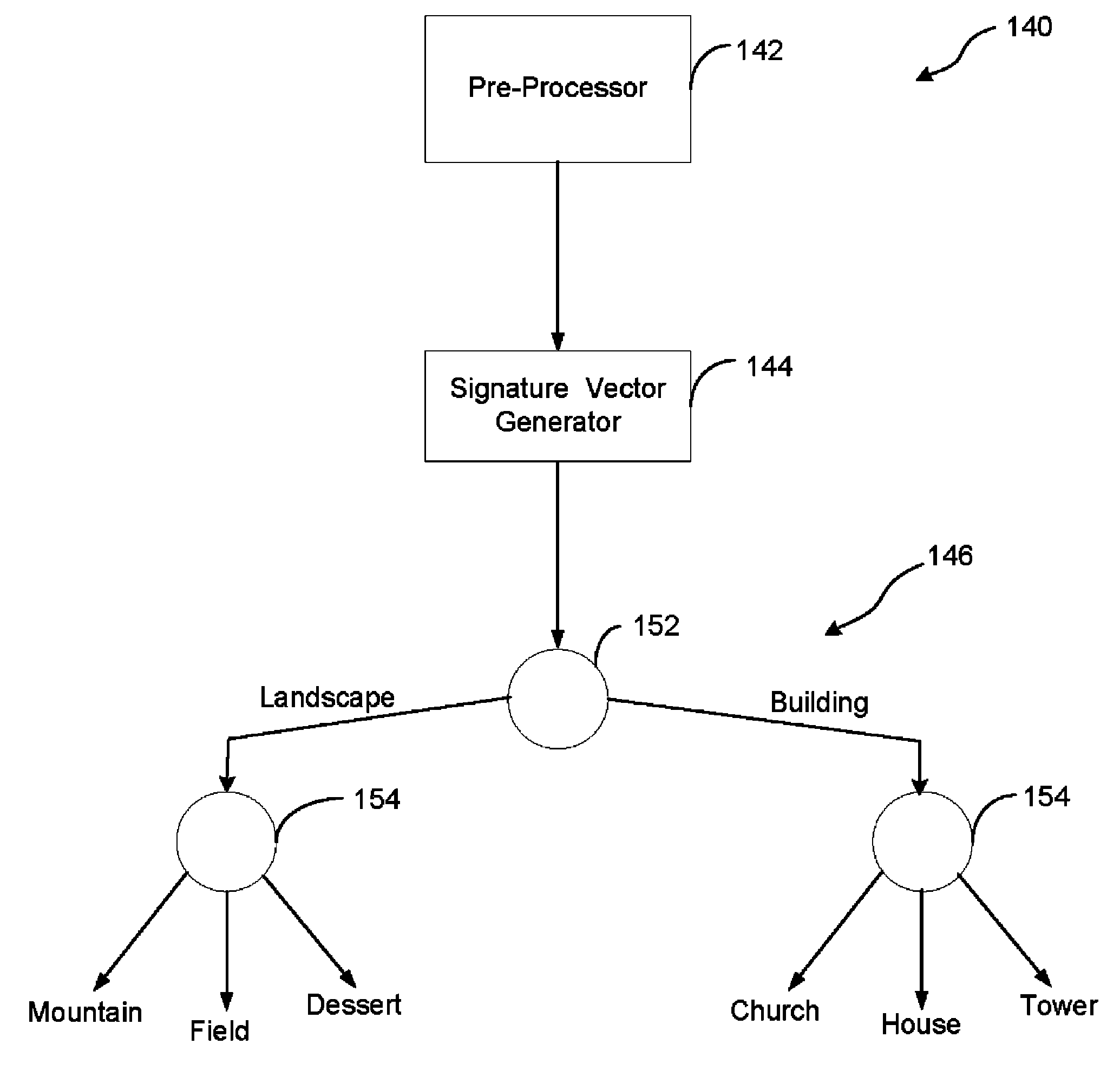
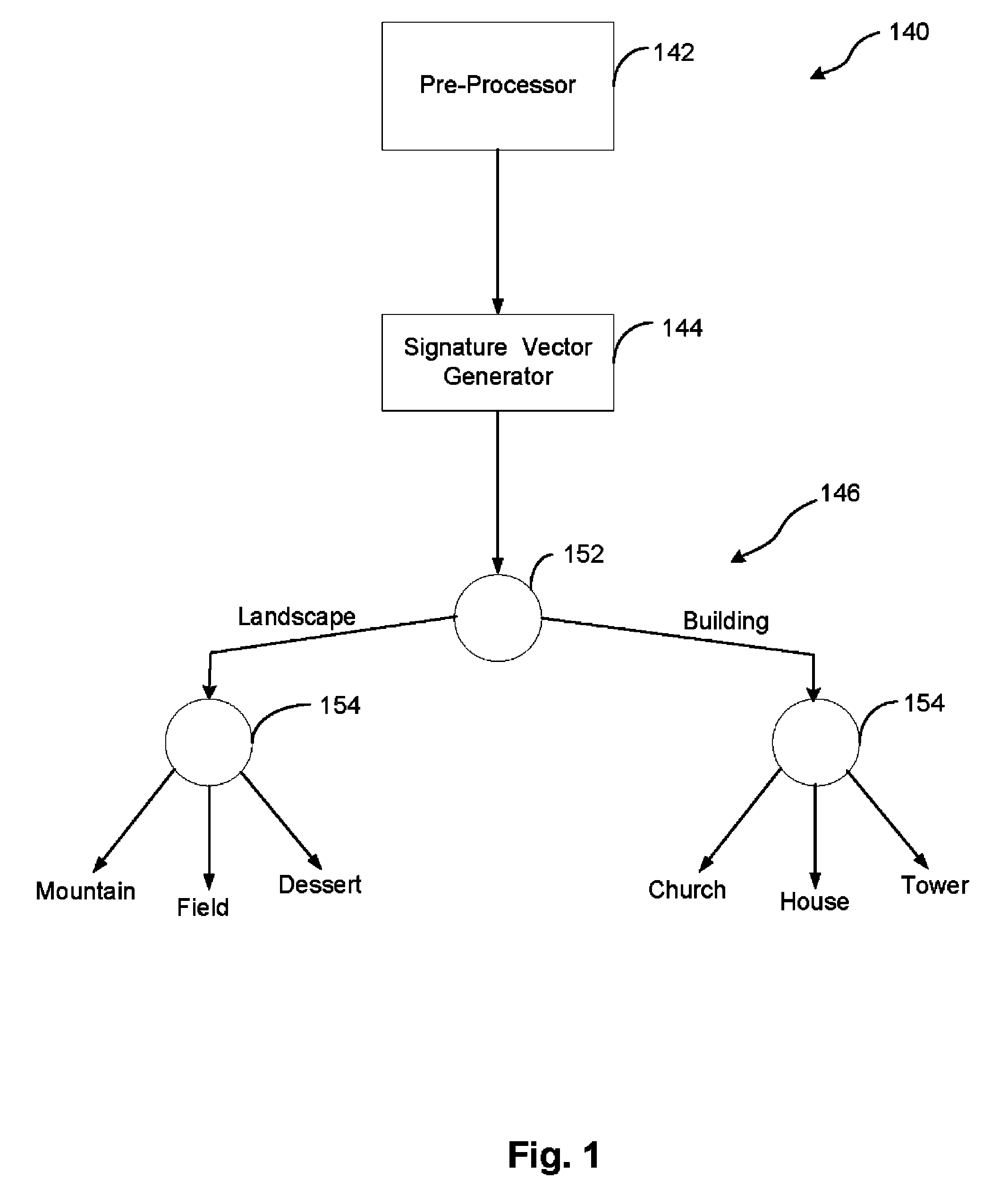
Method And Apparatus For Automatic Image Categorization Using Image Texture
InactiveUS20090060340A1Improve accuracyReduce significant processing overheadImage enhancementImage analysisSignature vectorTexture feature
A method of automatically categorizing an input image comprises extracting texture features of the input image and generating a signature vector based on extracted texture features. The generated signature vector is processed using at least one classifier to classify the input image.
Owner:SEIKO EPSON CORP
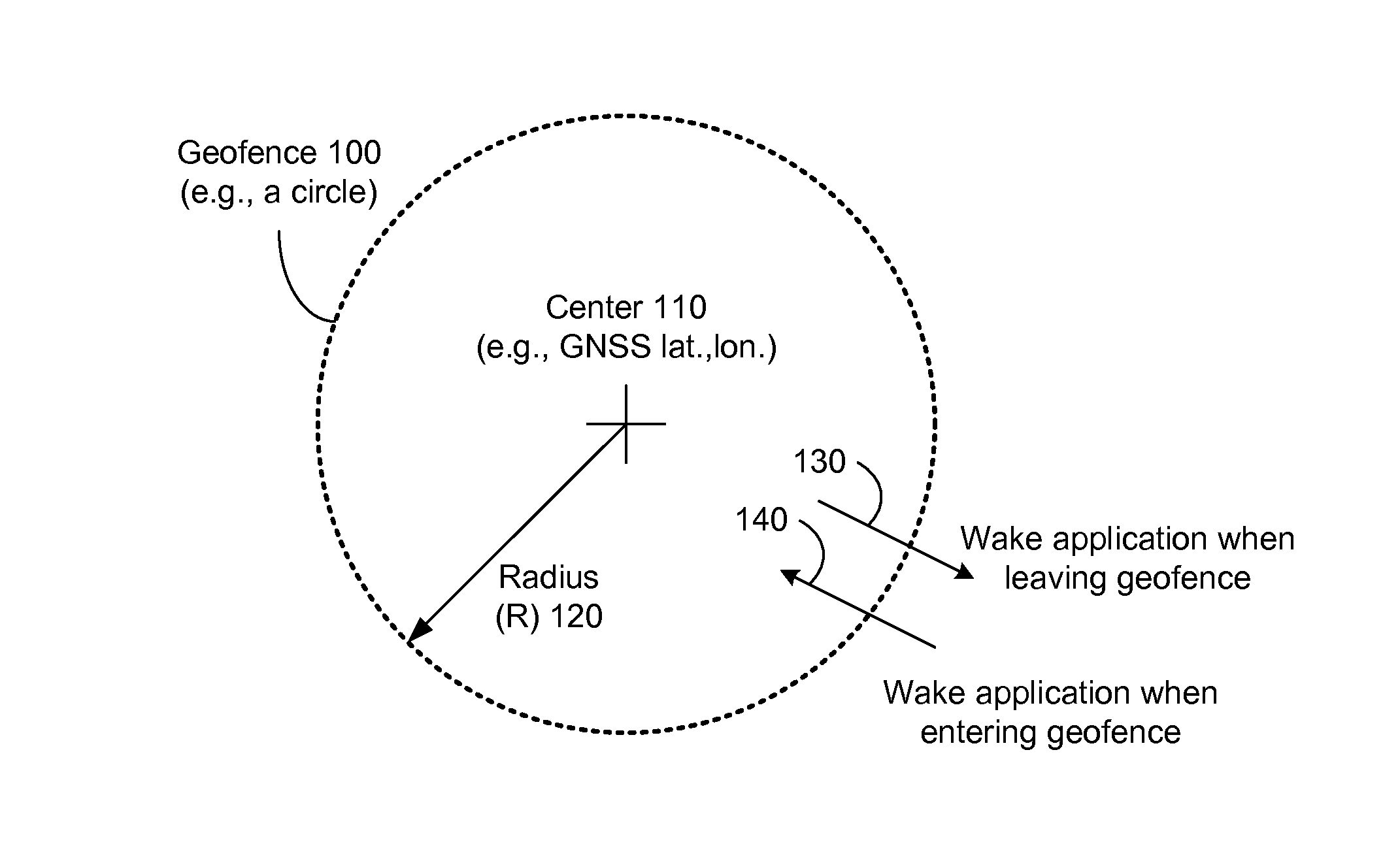
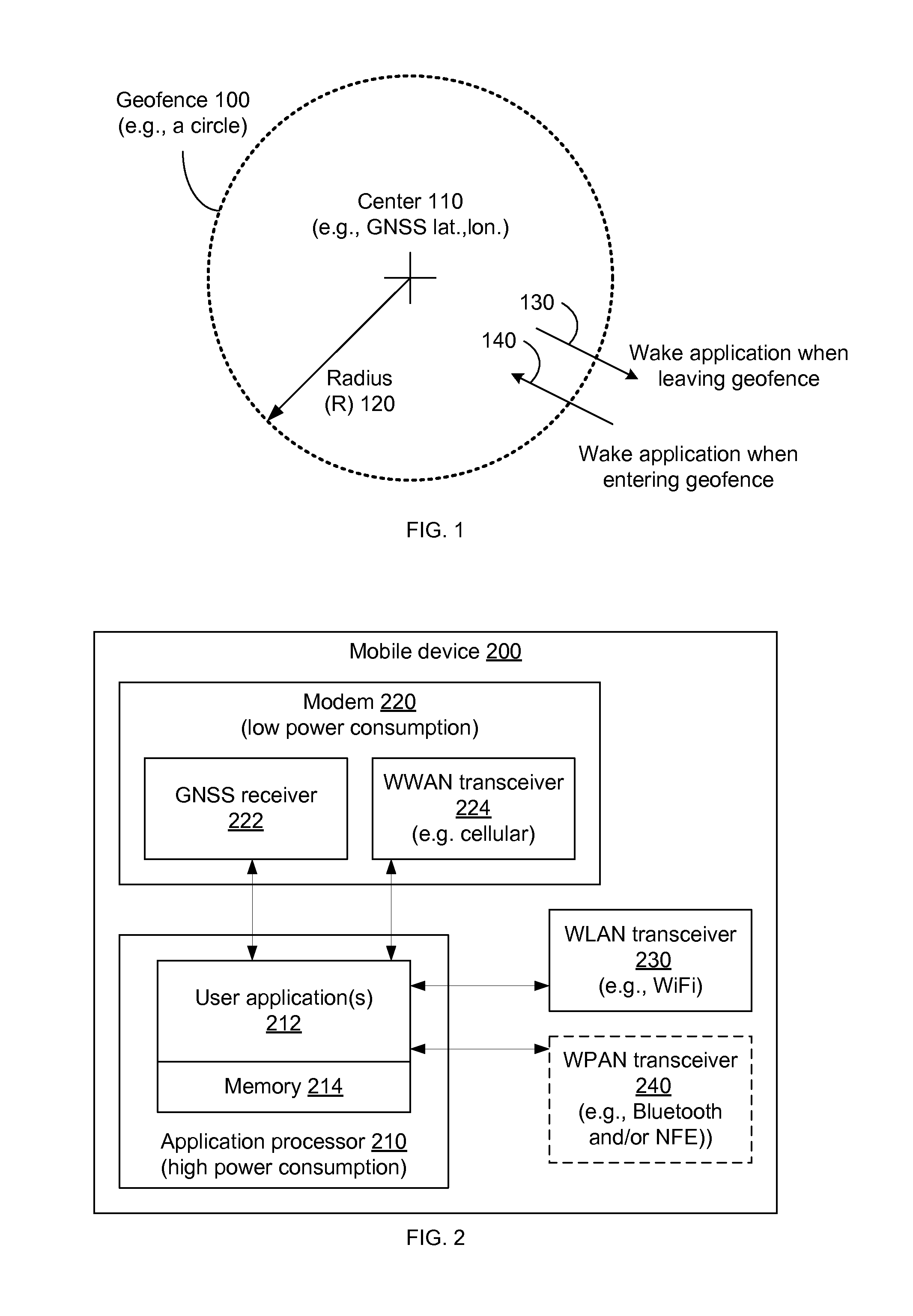
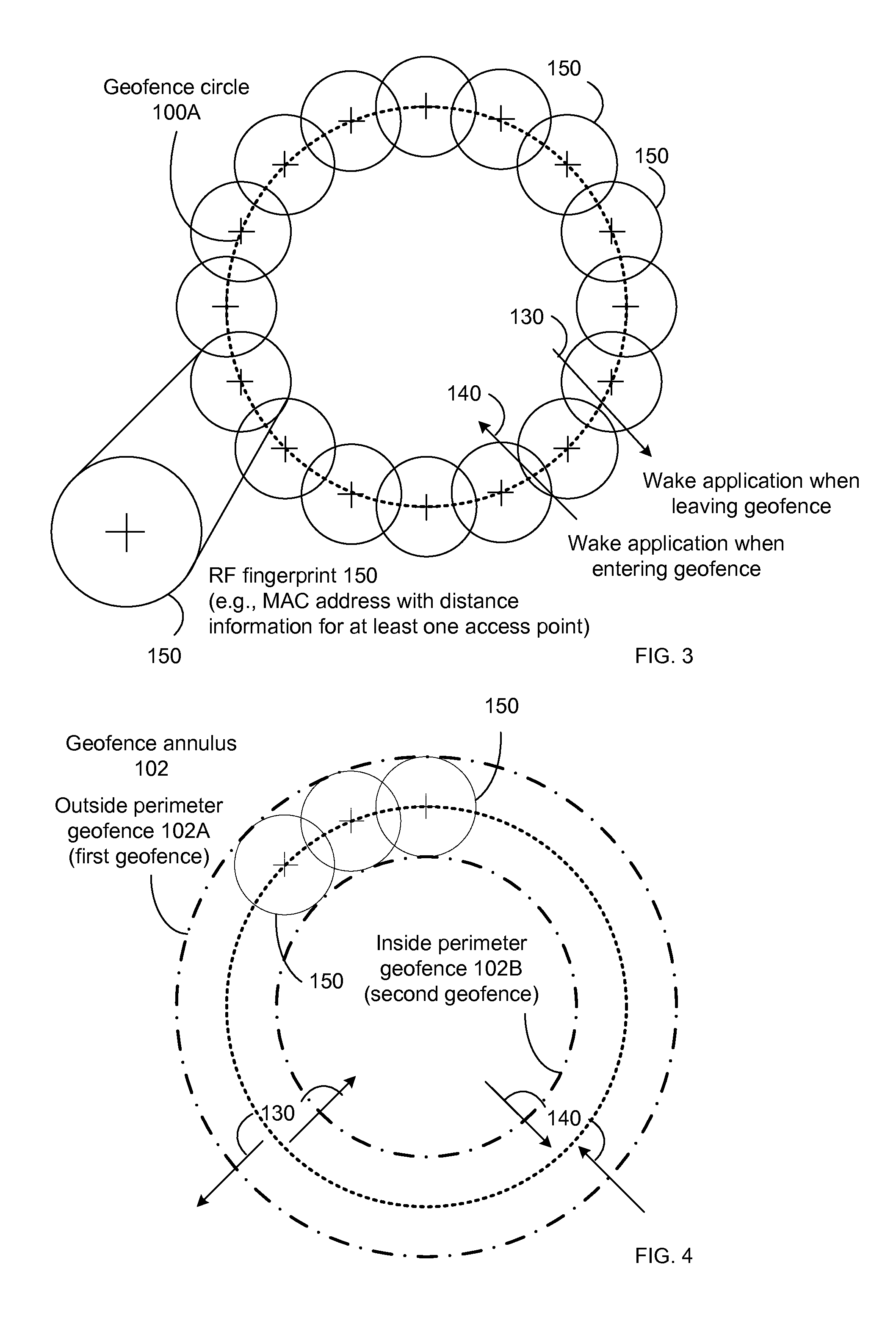
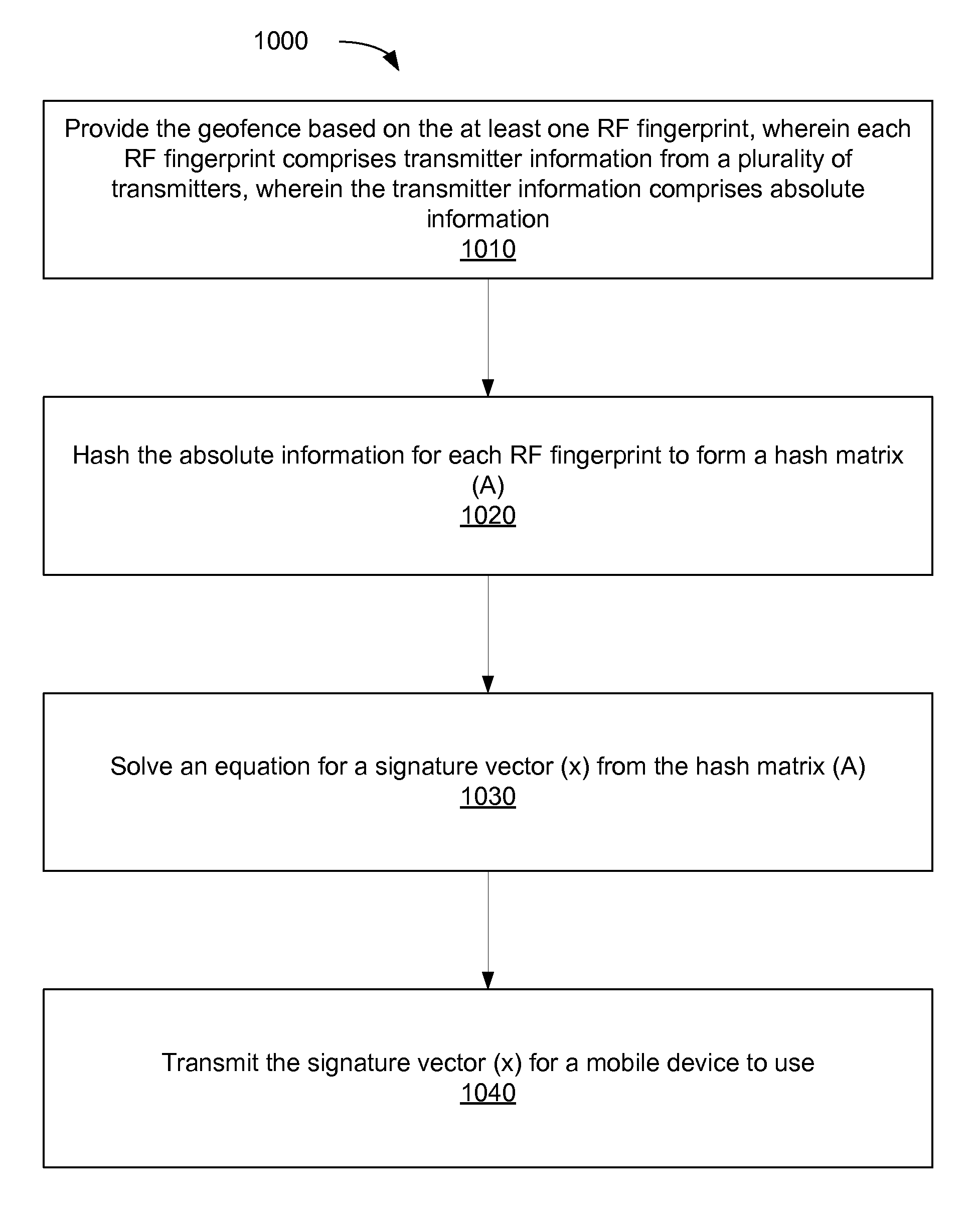
Communicating RF fingerprint-based geofences
Systems, apparatus and methods for communicating and using a geofence while maintaining privacy are presented. A geofence is based on at least one RF fingerprint. The RF fingerprints include absolute information that is transformed into a one-way matrix (A) by application of a one-way function. The absolute information may identify a transmitter (e.g., by location, address or the like). An equation 0=Ax (where 0 is a zero vector, A is the one-way matrix and x is a signature vector) is solved to reveal one possible solution for the signature vector (x). This signature vector (x) is communicated rather than the RF fingerprints themselves, thus obscuring the absolute information and maintaining privacy.
Owner:QUALCOMM INC
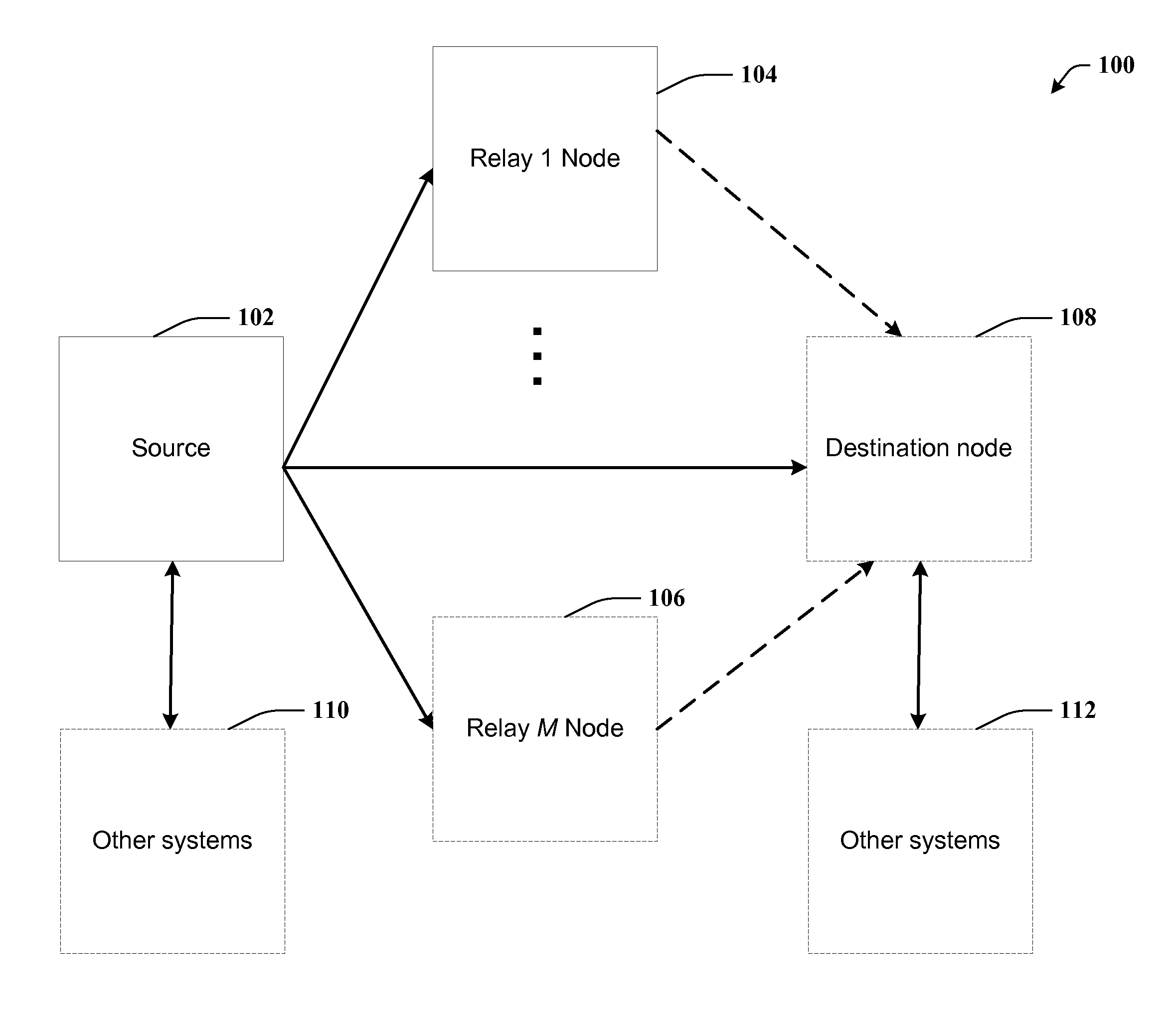
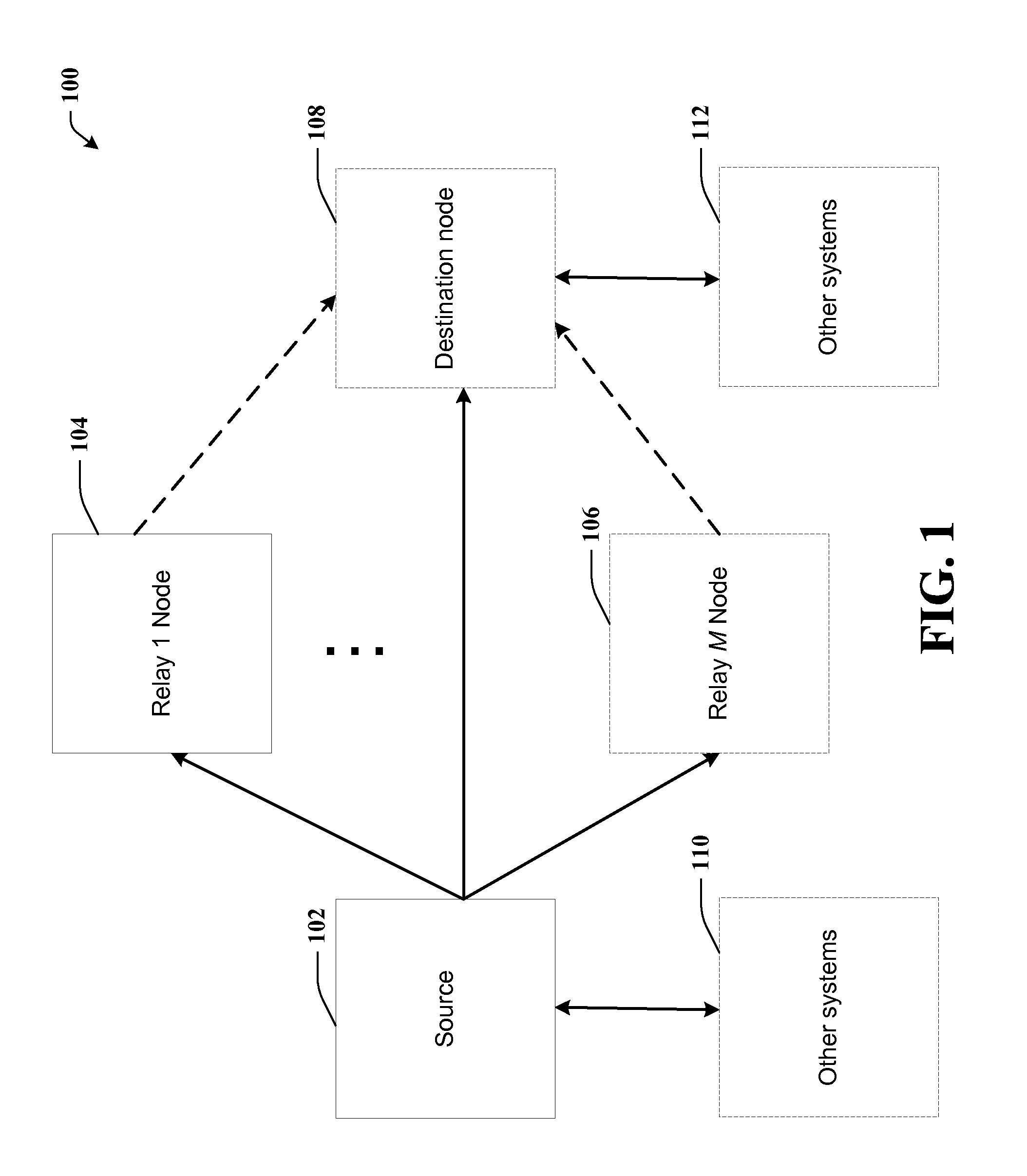
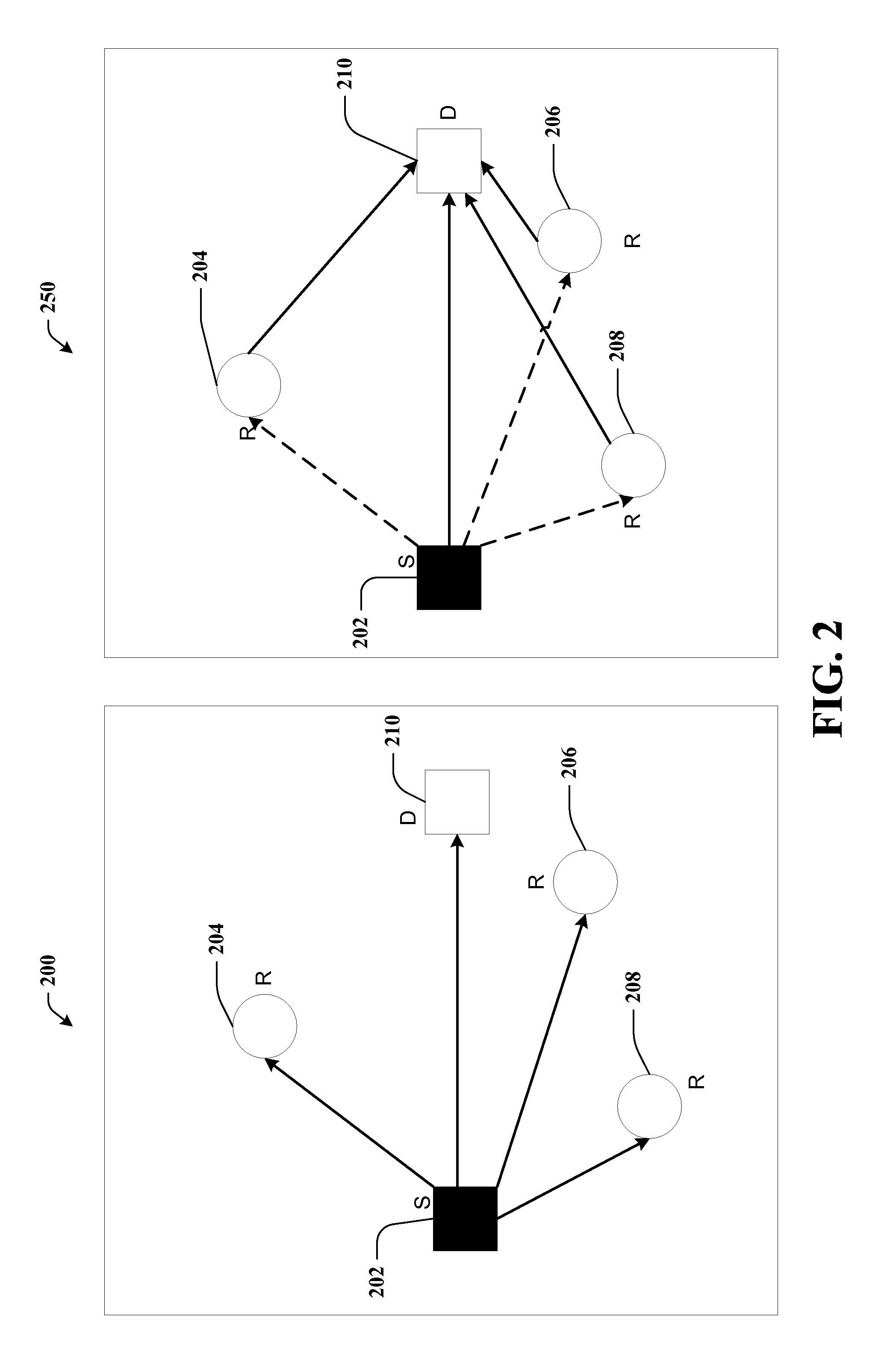
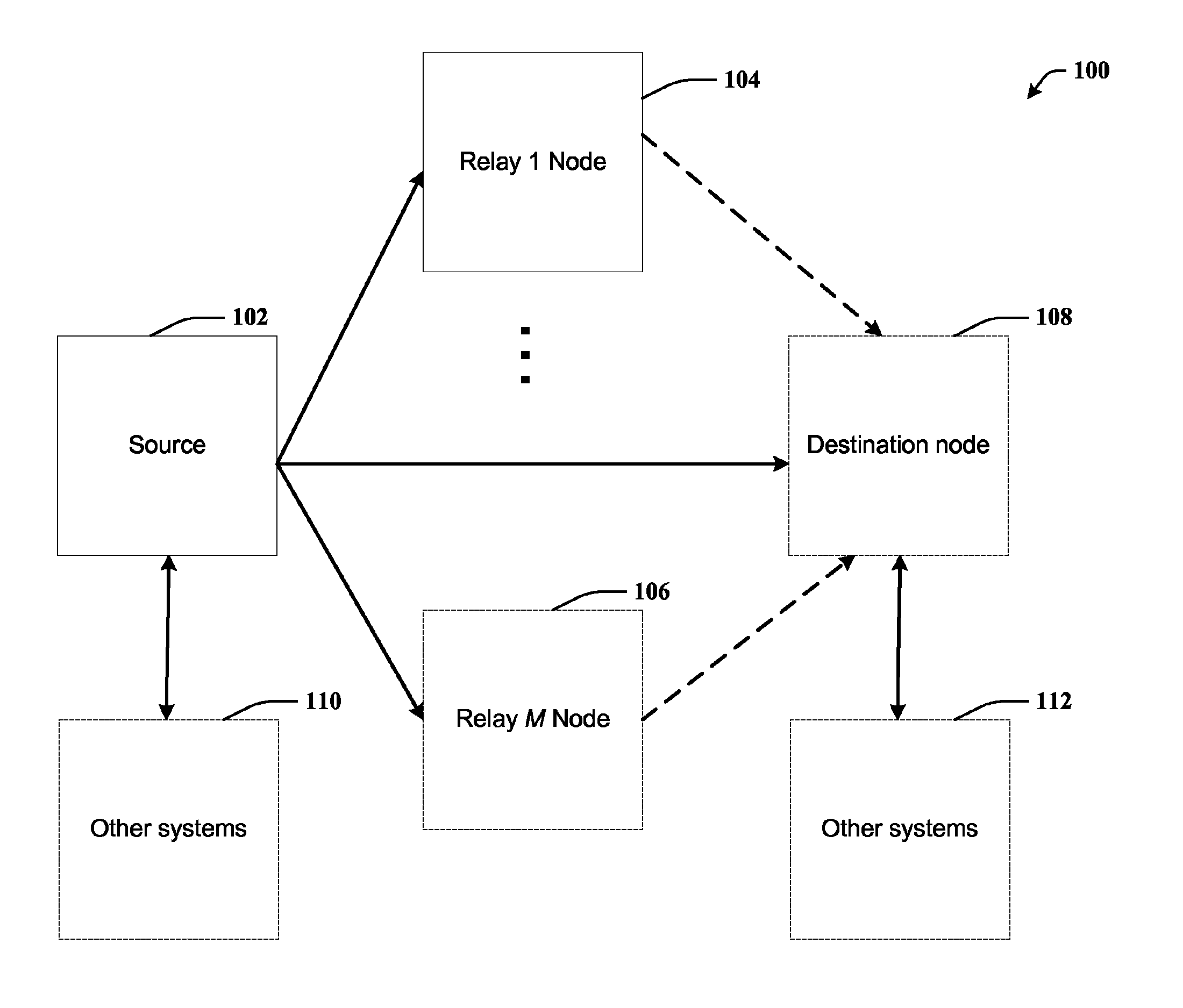
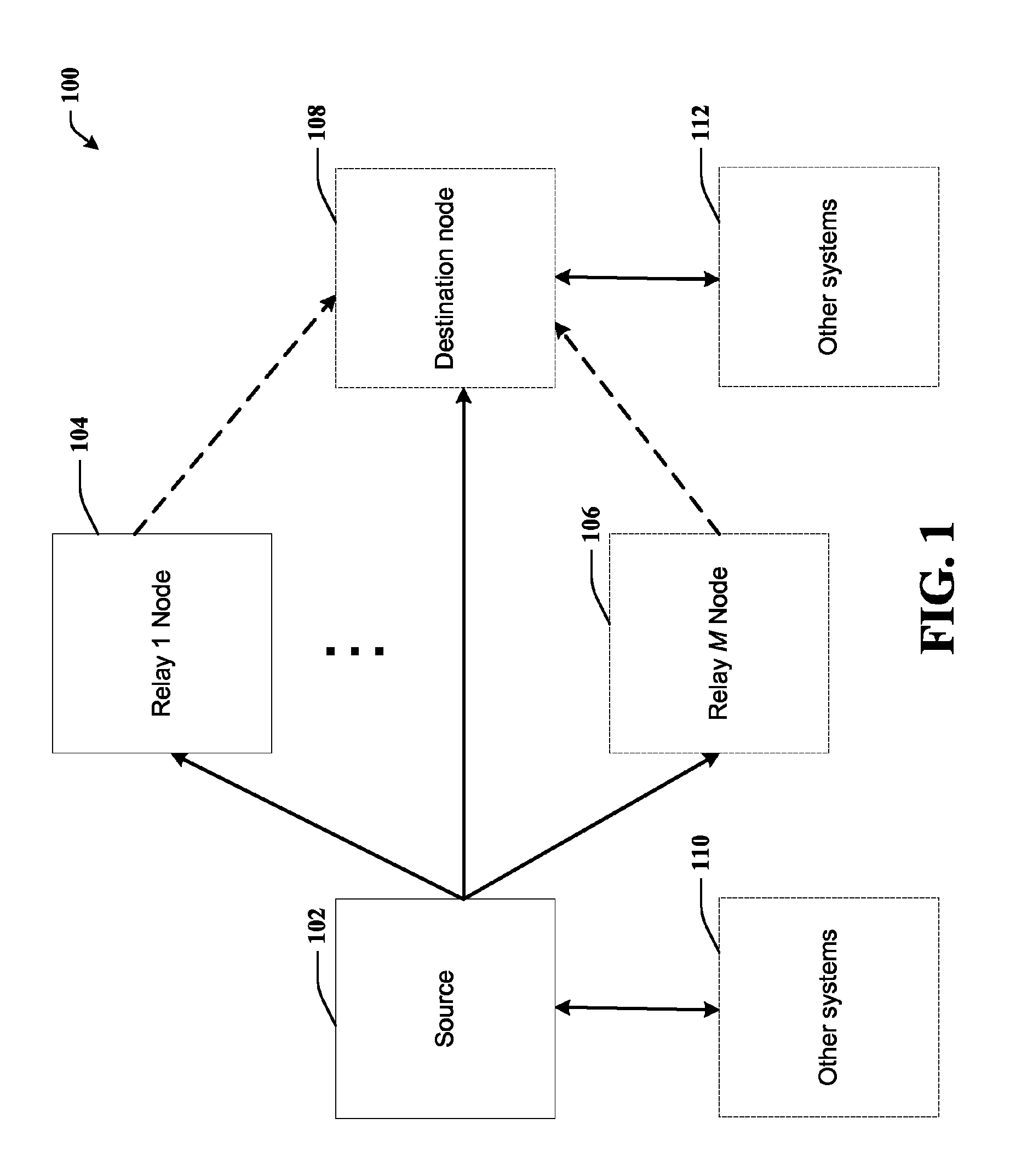
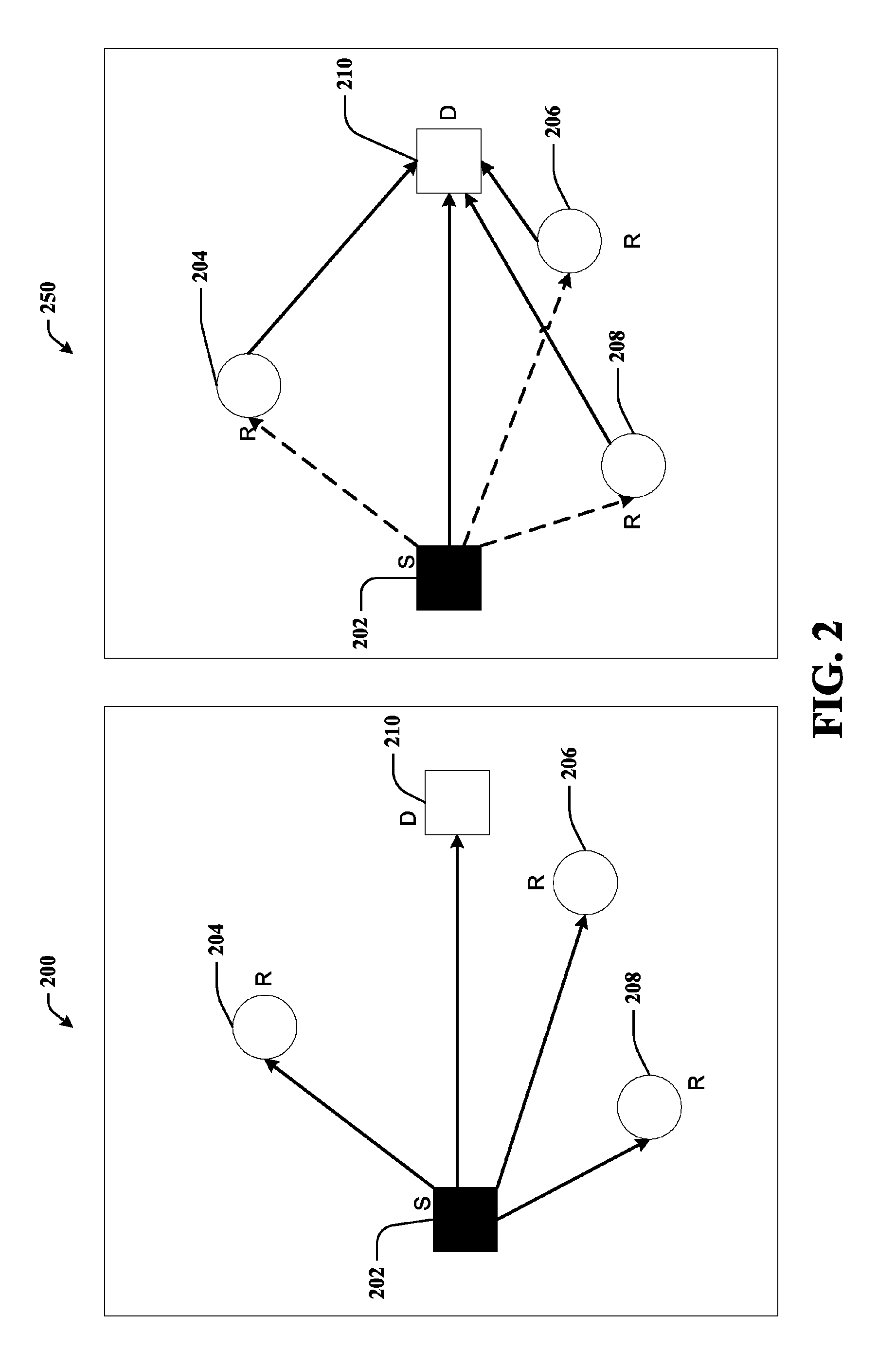
Full-rate distributed space-time codes for cooperative communications
ActiveUS20090129496A1Improve maximizationEasy transferRepeater circuitsAmplitude-modulated carrier systemsFull RateDiversity scheme
A full-rate distributed space-time (ST) code design is provided for amplify-and-forward cooperative wireless channels. A signal space diversity technique is employed at the source node and a unique signature vector at each relay node. The distributed space-time (ST) codes can achieve full cooperative diversity and full rate. The achievable diversity gain is M+1, where M is the number of relay nodes. Optimal power allocation can be used to maximize the coding gain under a total power constraint.
Owner:LINGNA HLDG PTE
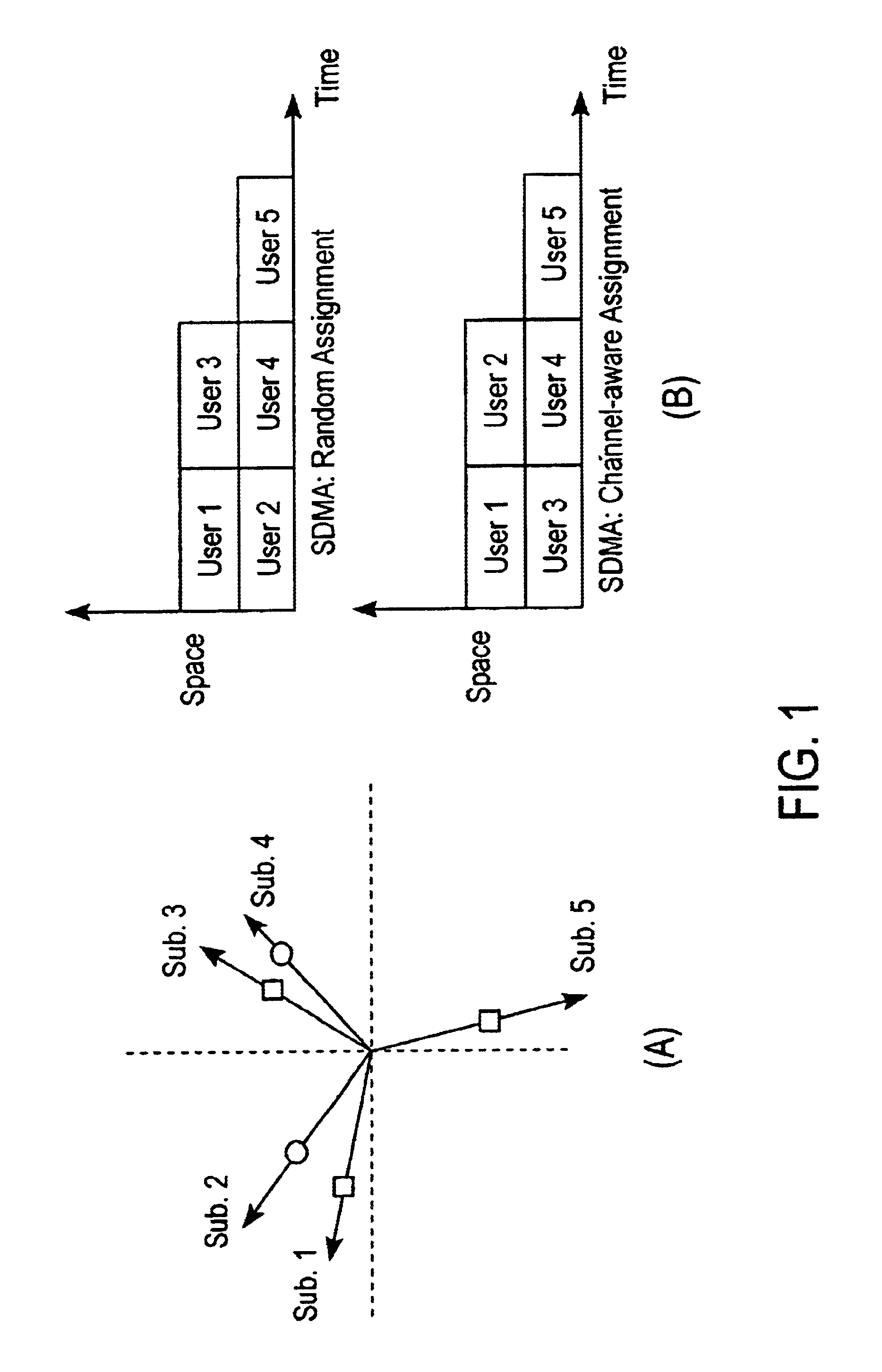
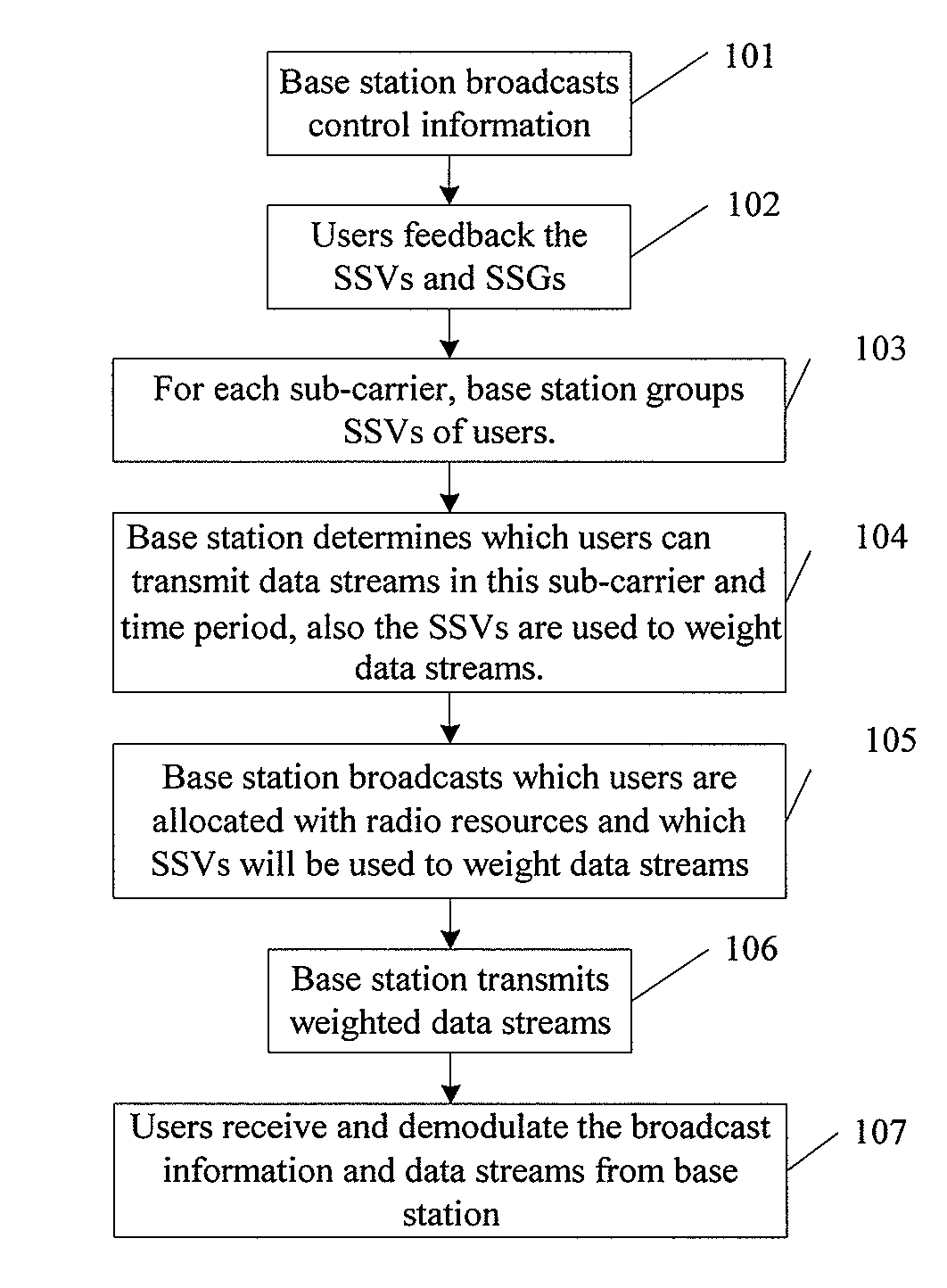
Resource allocation method for mimo-ofdm of multi-user access systems
ActiveUS20080165883A1Reduce complexityQuality improvementModulated-carrier systemsDiversity/multi-antenna systemsMulti inputCo-channel interference
A resource allocation method for MIMO (multi-input multi-output-OFDM (orthogonal frequency-division multiplex) of multi-user access systems includes A) for each sub-carrier or group of sub-carriers of OFDM, grouping signature vectors of users at a time period according to correlations of the signature vectors; B) from the grouping results, selecting the signature vectors according to a scheduling rule; assigning the sub-carrier frequency and time resource to users of which simultaneously the selected signature vectors have low correlations; and assigning spatial resource to the users corresponding to the selected signature vectors. By minimizing the spatial co-channel interference to an acceptable low level, the complexity significantly in the joint multi-user optimization is reduced.
Owner:NOKIA TECHNOLOGLES OY
Method and apparatus for automatic image categorization using image texture
InactiveUS7983486B2Simple technologySignificant processing overheadImage enhancementImage analysisAutomatic image annotationSignature vector
A method of automatically categorizing an input image comprises extracting texture features of the input image and generating a signature vector based on extracted texture features. The generated signature vector is processed using at least one classifier to classify the input image.
Owner:SEIKO EPSON CORP
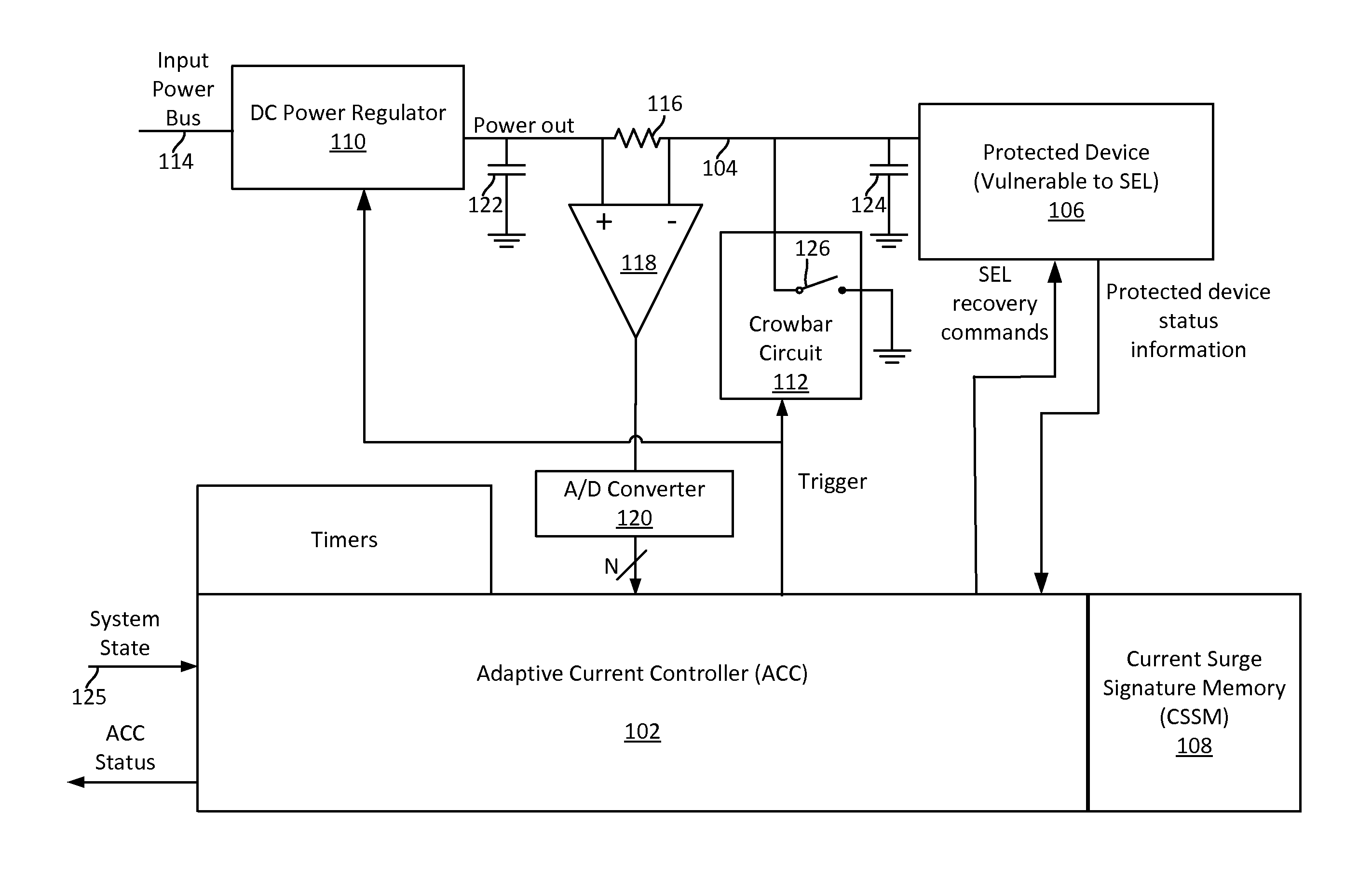
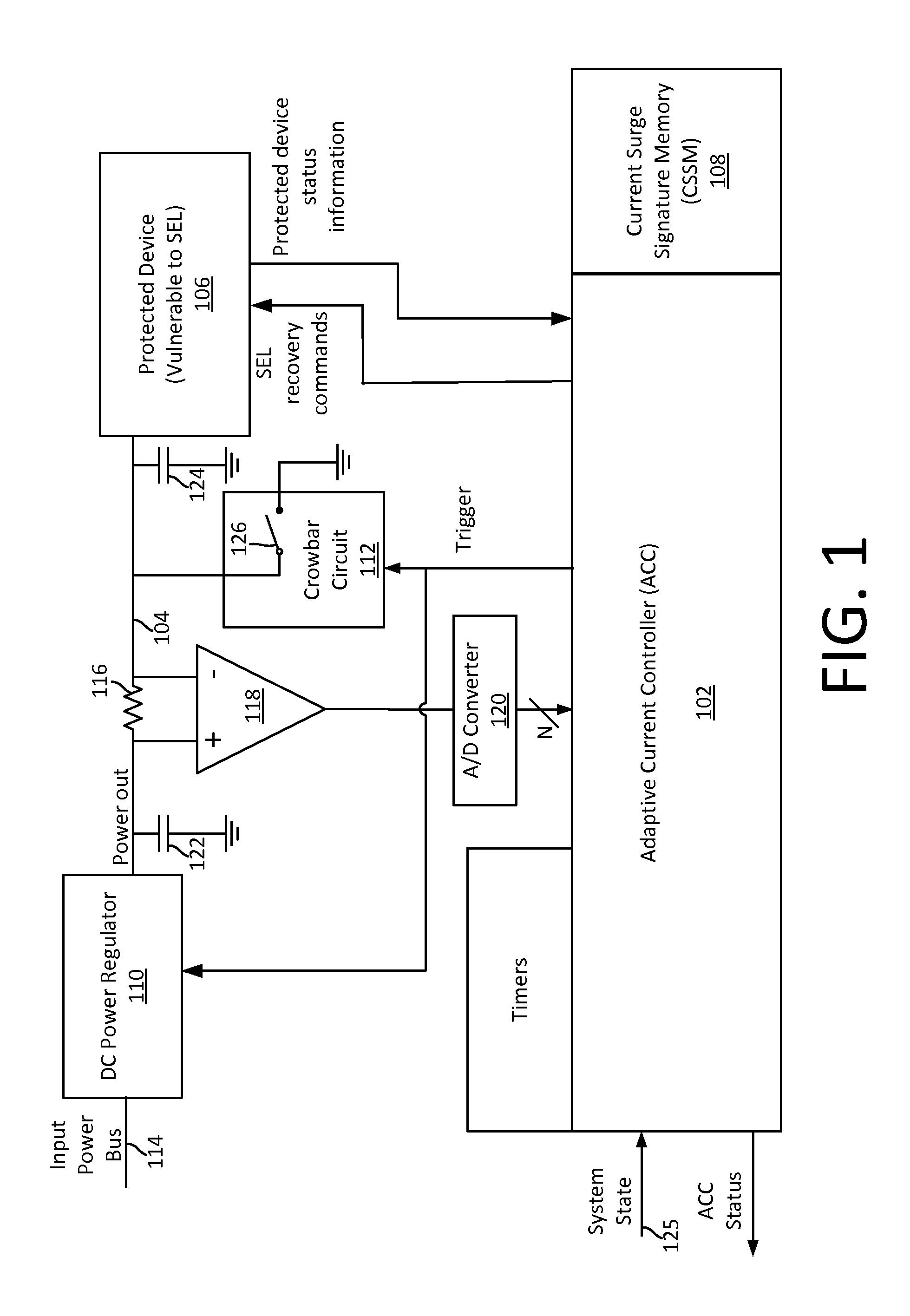
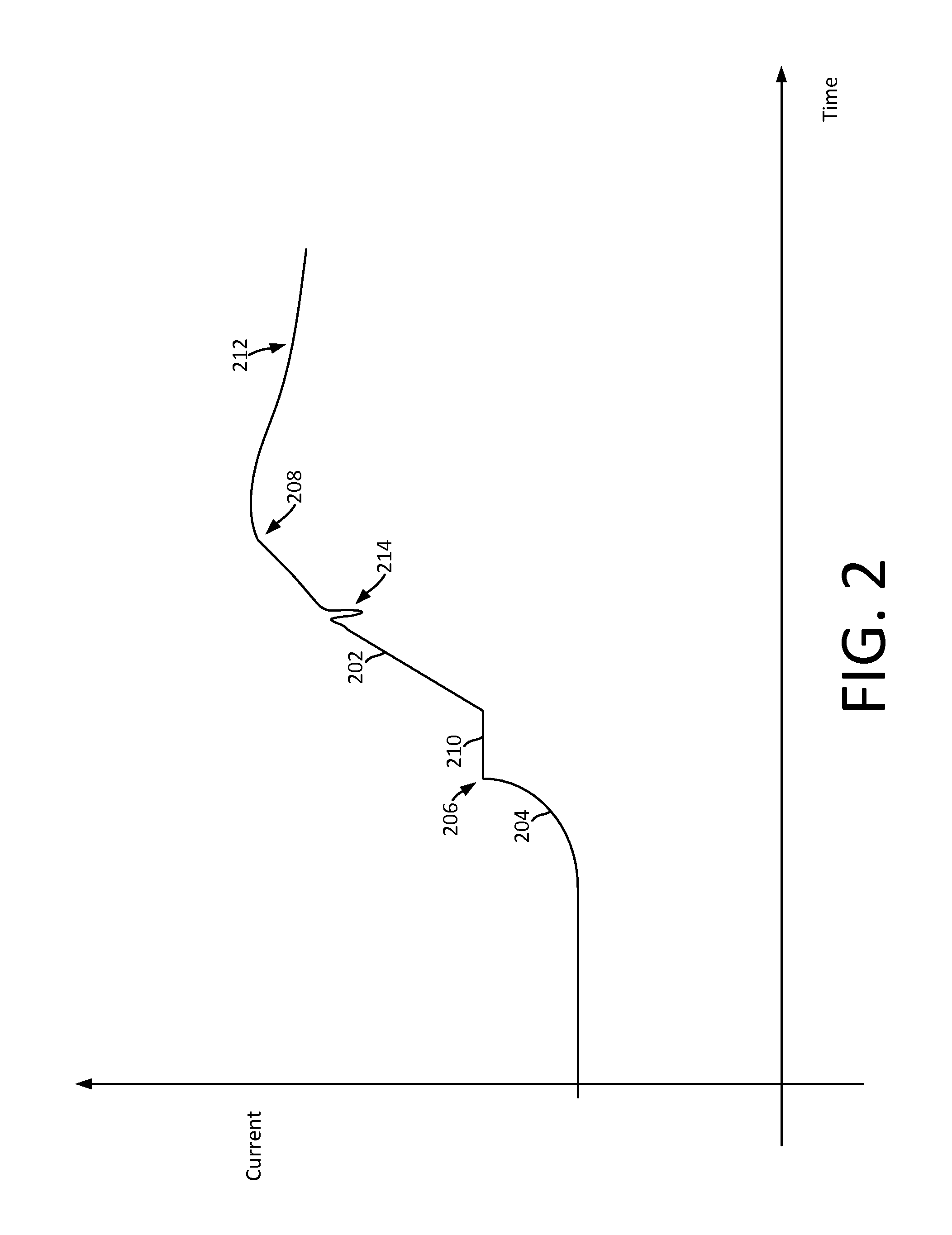
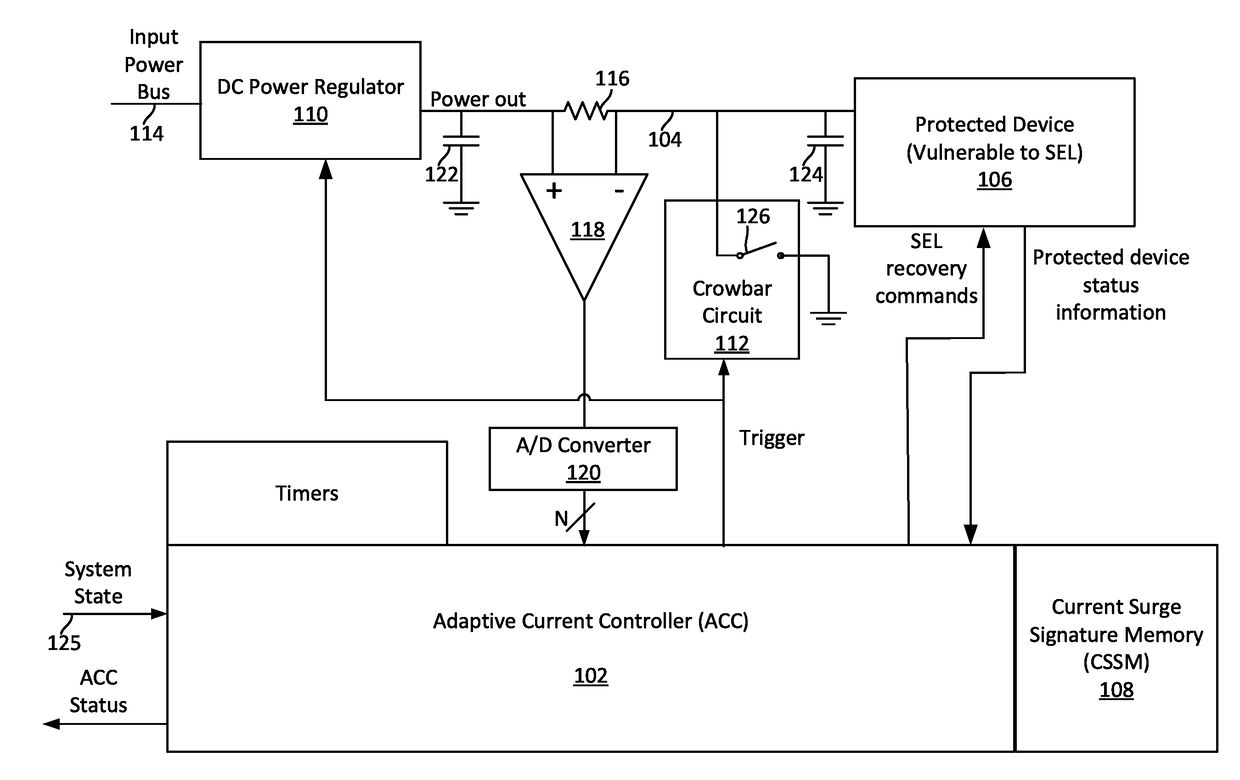
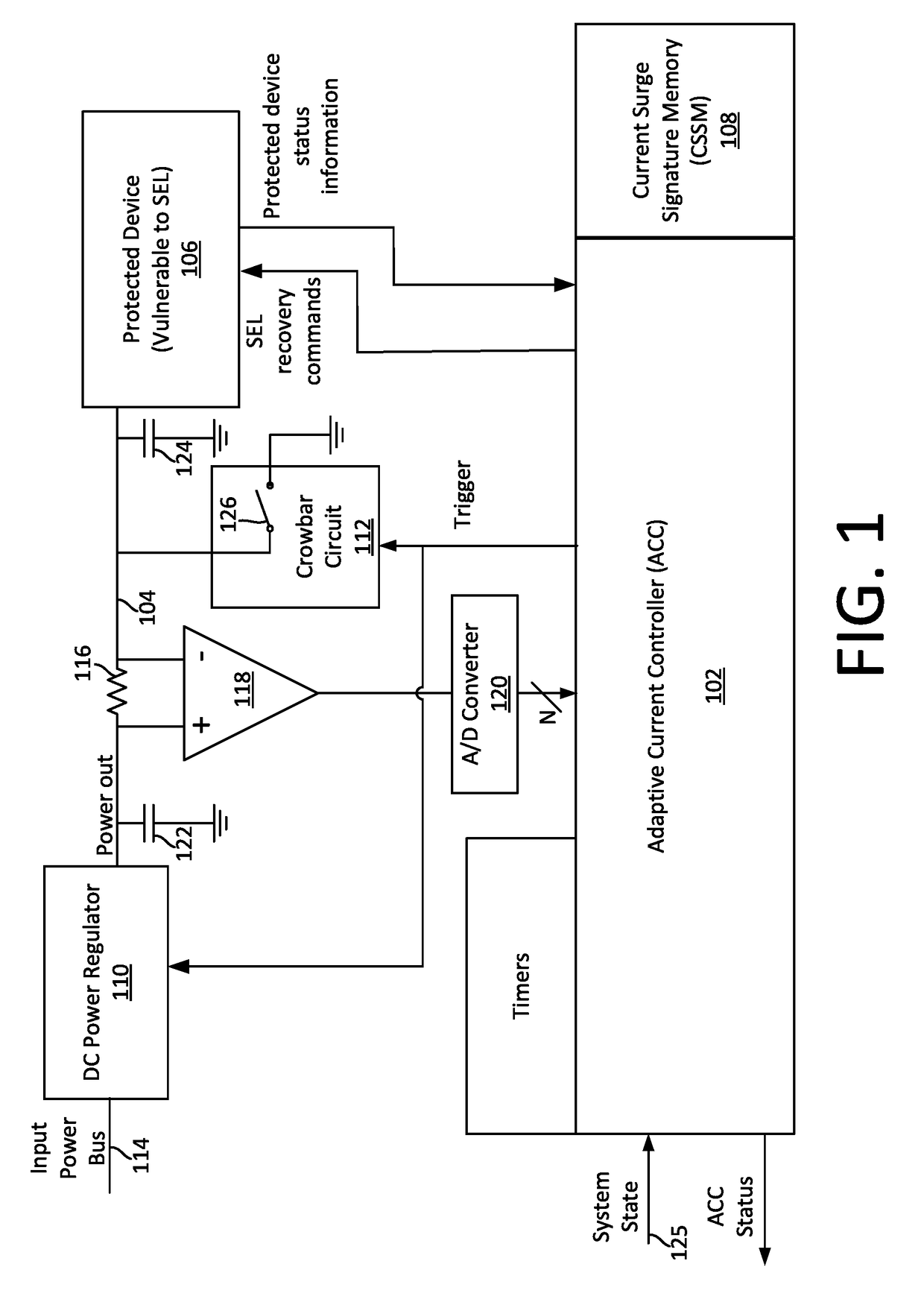
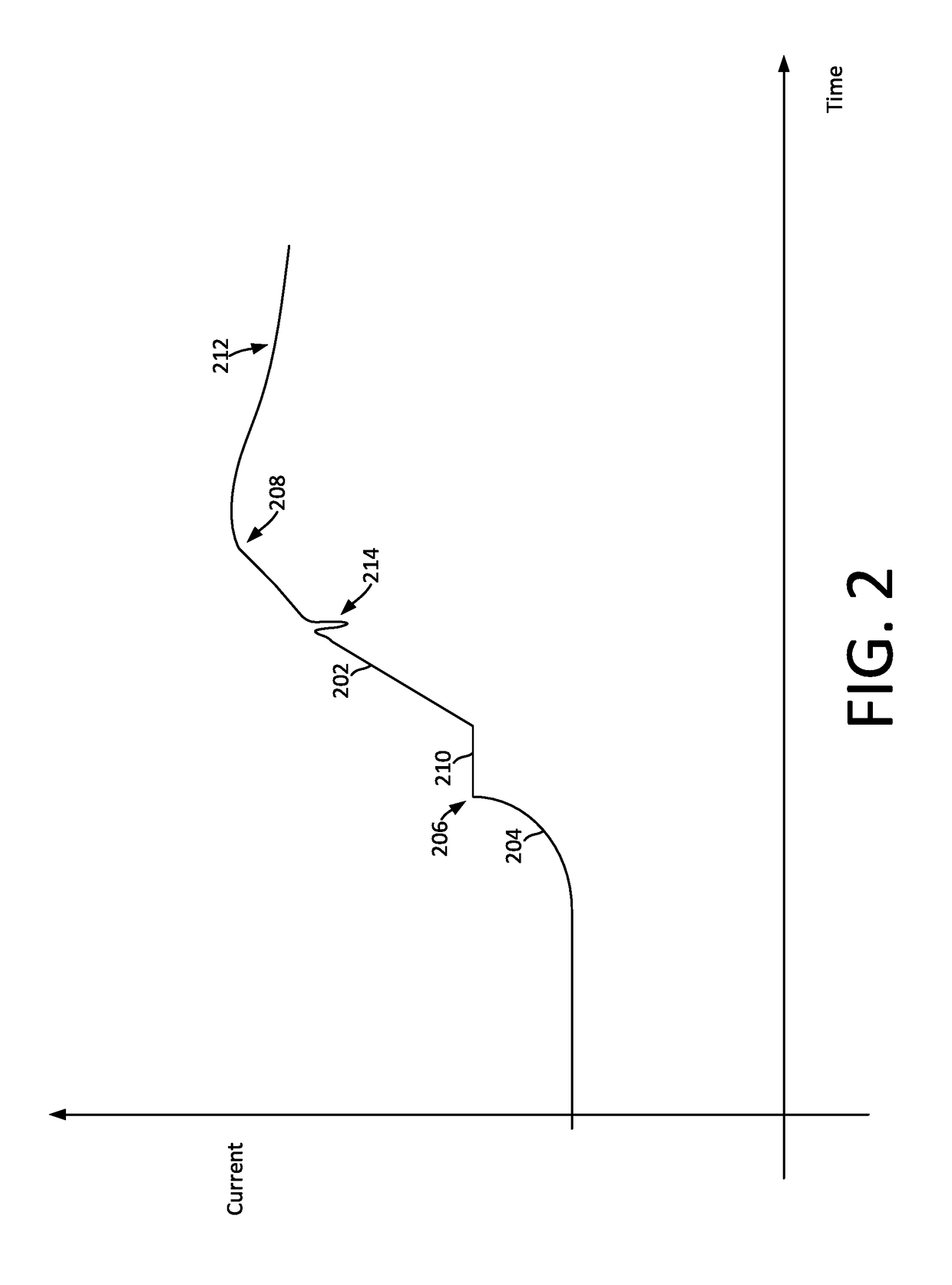
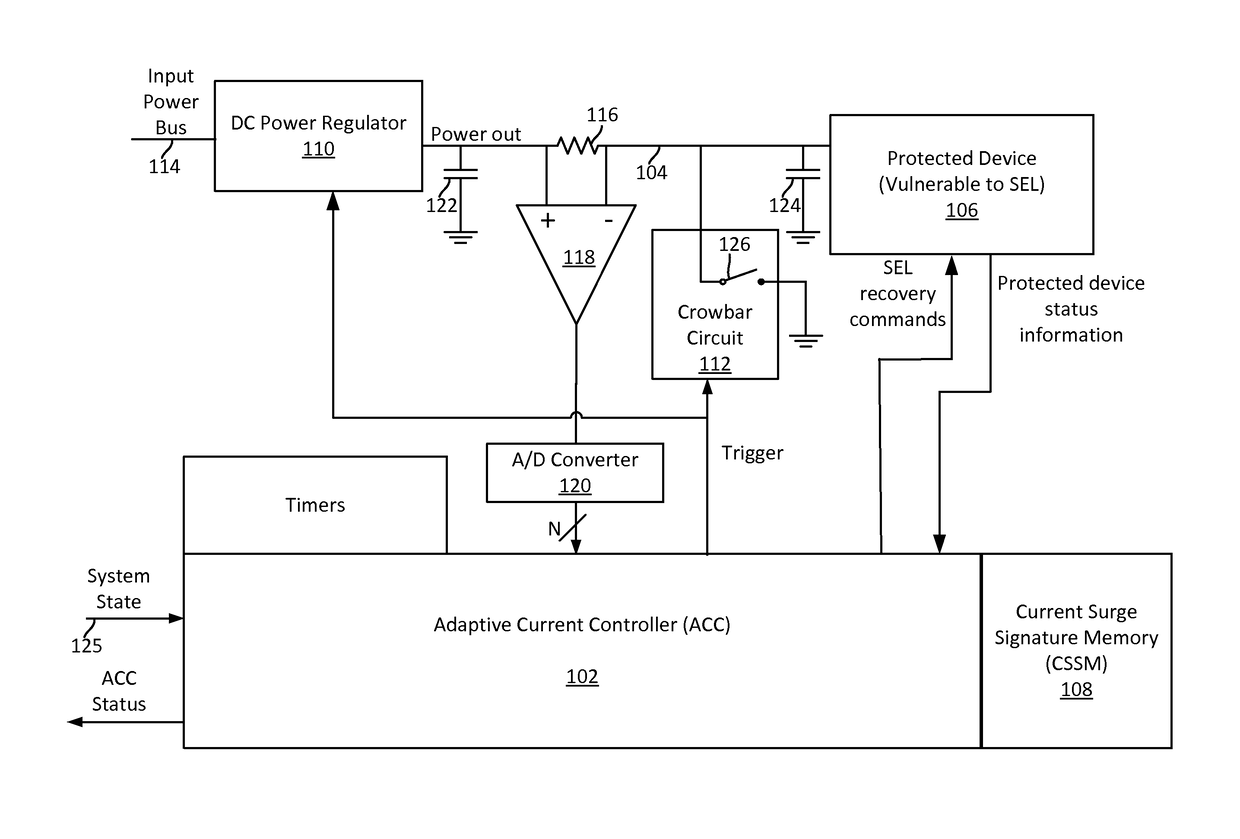
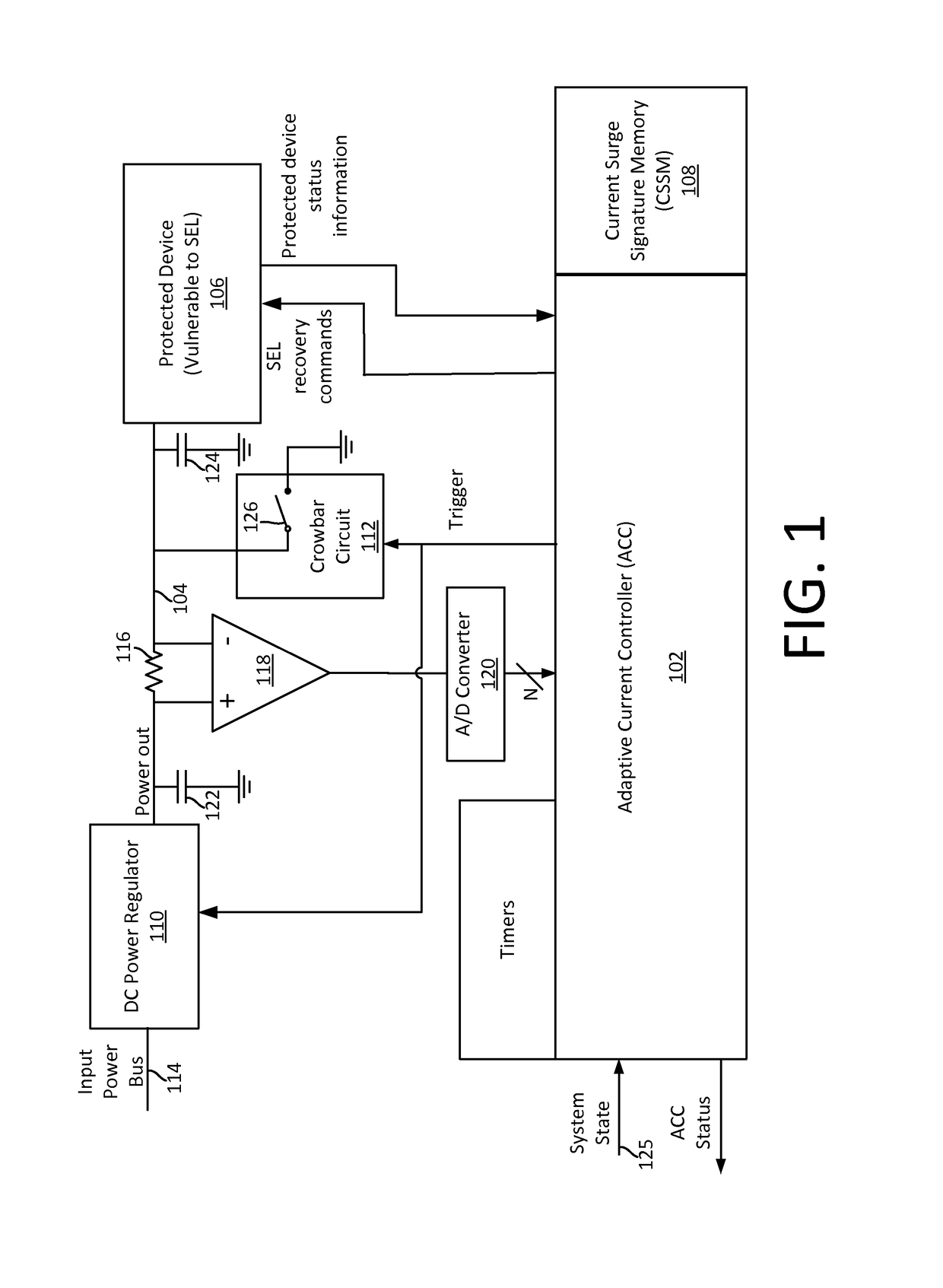
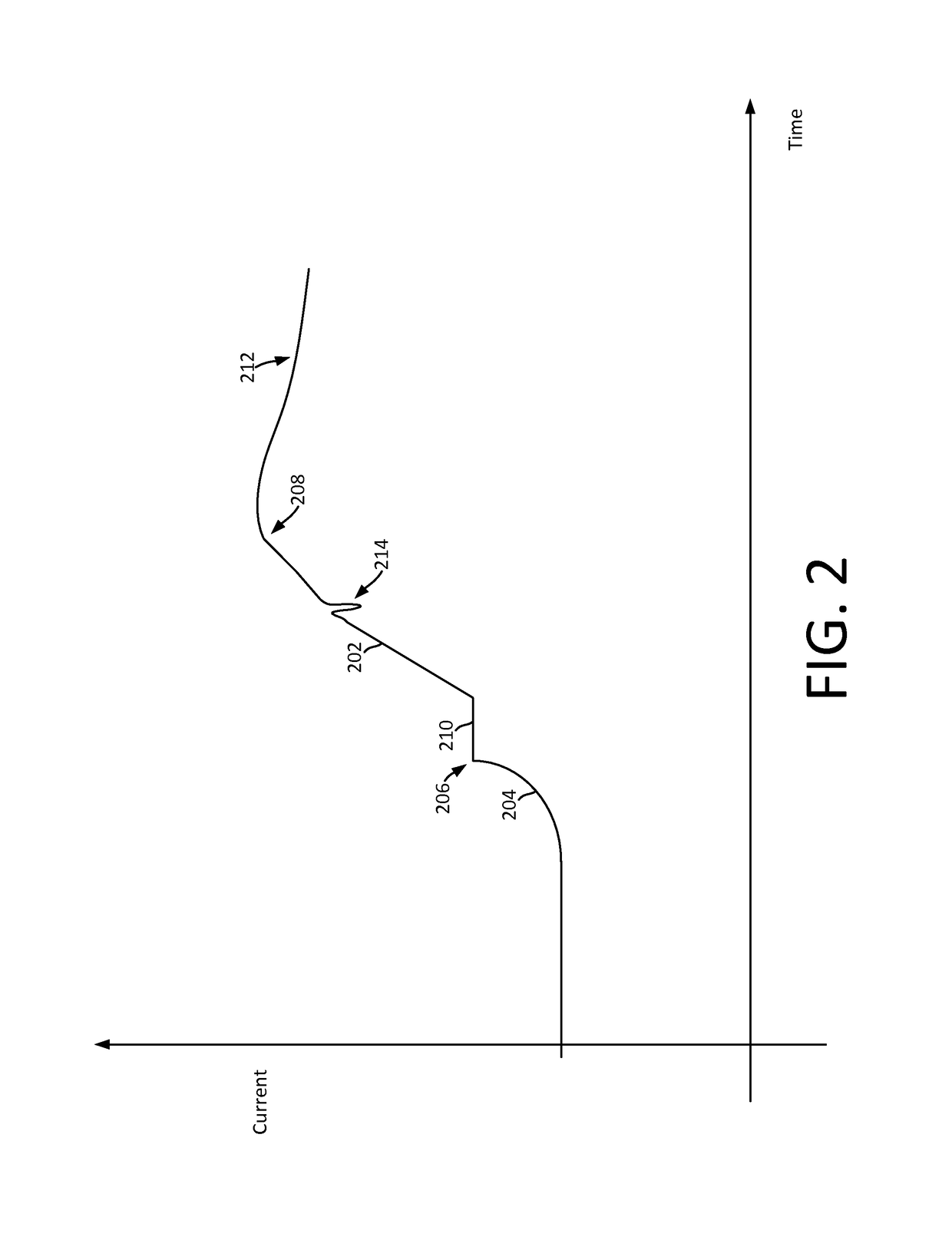
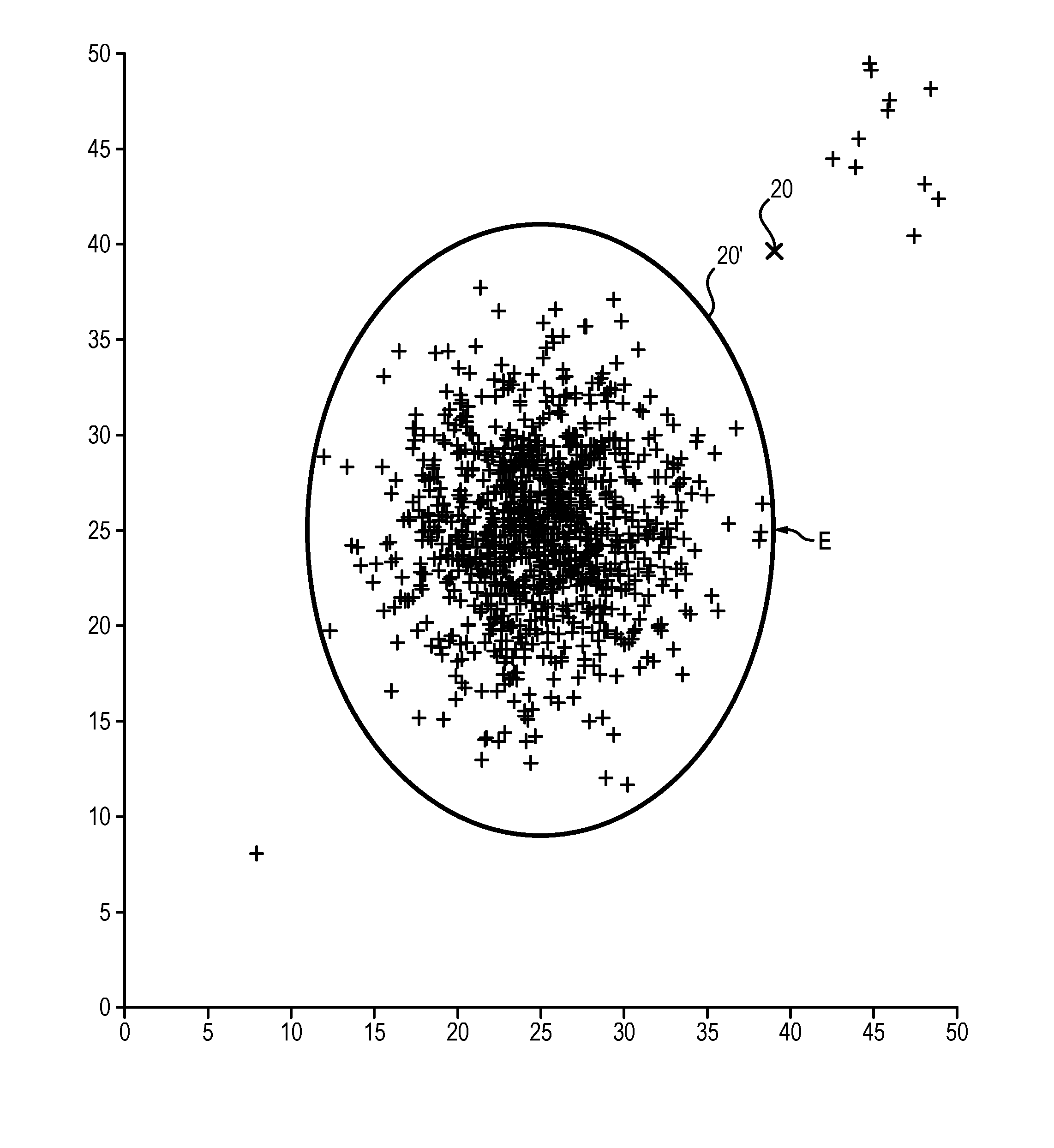
Single event latchup (SEL) current surge mitigation
ActiveUS20170033554A1Electrical testingEmergency protective arrangements for automatic disconnectionSingle event latchupData signal
Method and system for Single Event Latchup (SEL) current surge mitigation involves monitoring data signals for a protected device and deriving from them a detected signature comprised of one or more detected signature vector components. The detected signature vector components are compared to previously stored signature vector components. Based on the comparing, the system selectively differentiates between the occurrence of standard power surges associated with normal operation of the protected device, and a non-standard current surge which requires cycling power of the protected device for continued proper functioning of the protected device.
Owner:HARRIS CORP
Music soundtrack recommendation engine for videos
ActiveUS20140212106A1Television system detailsDigital data information retrievalFeature extractionVocal tract
Owner:GOOGLE LLC
Device, system and method for extracting physiological information
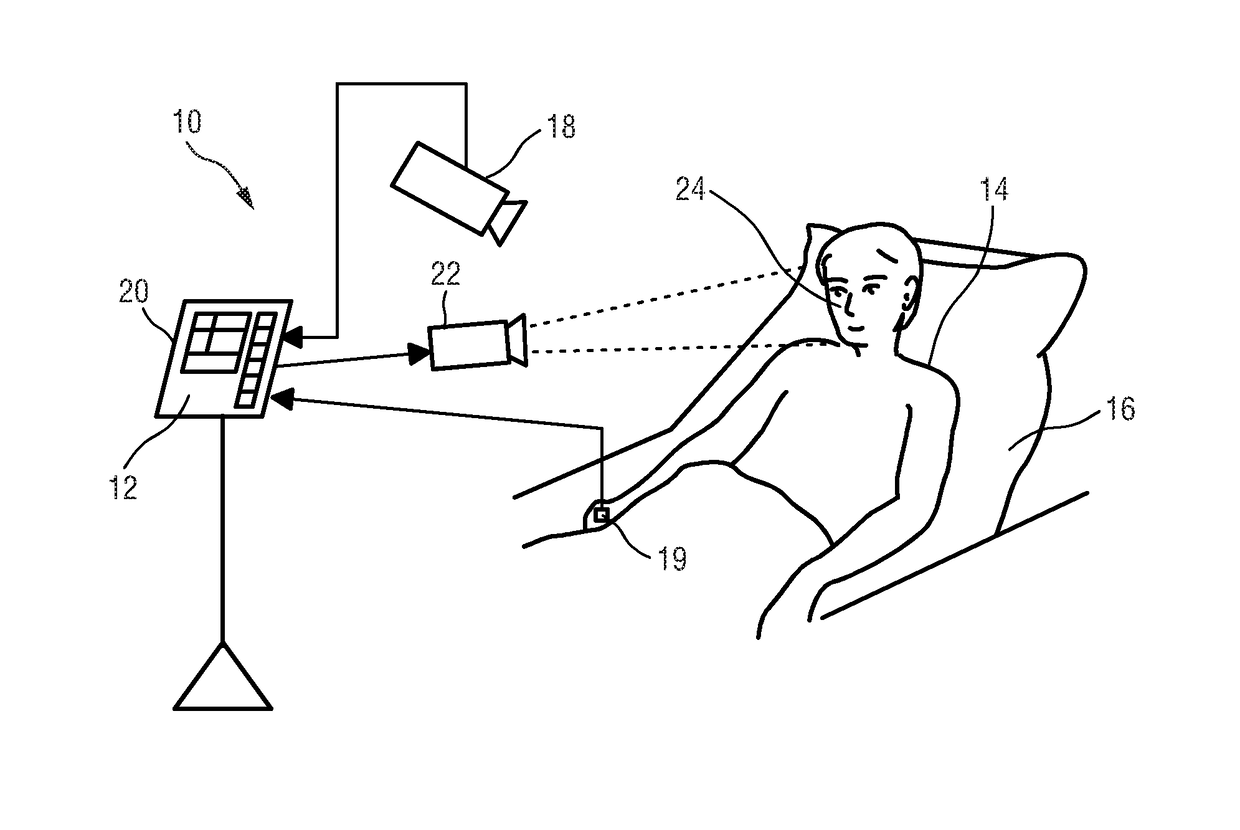
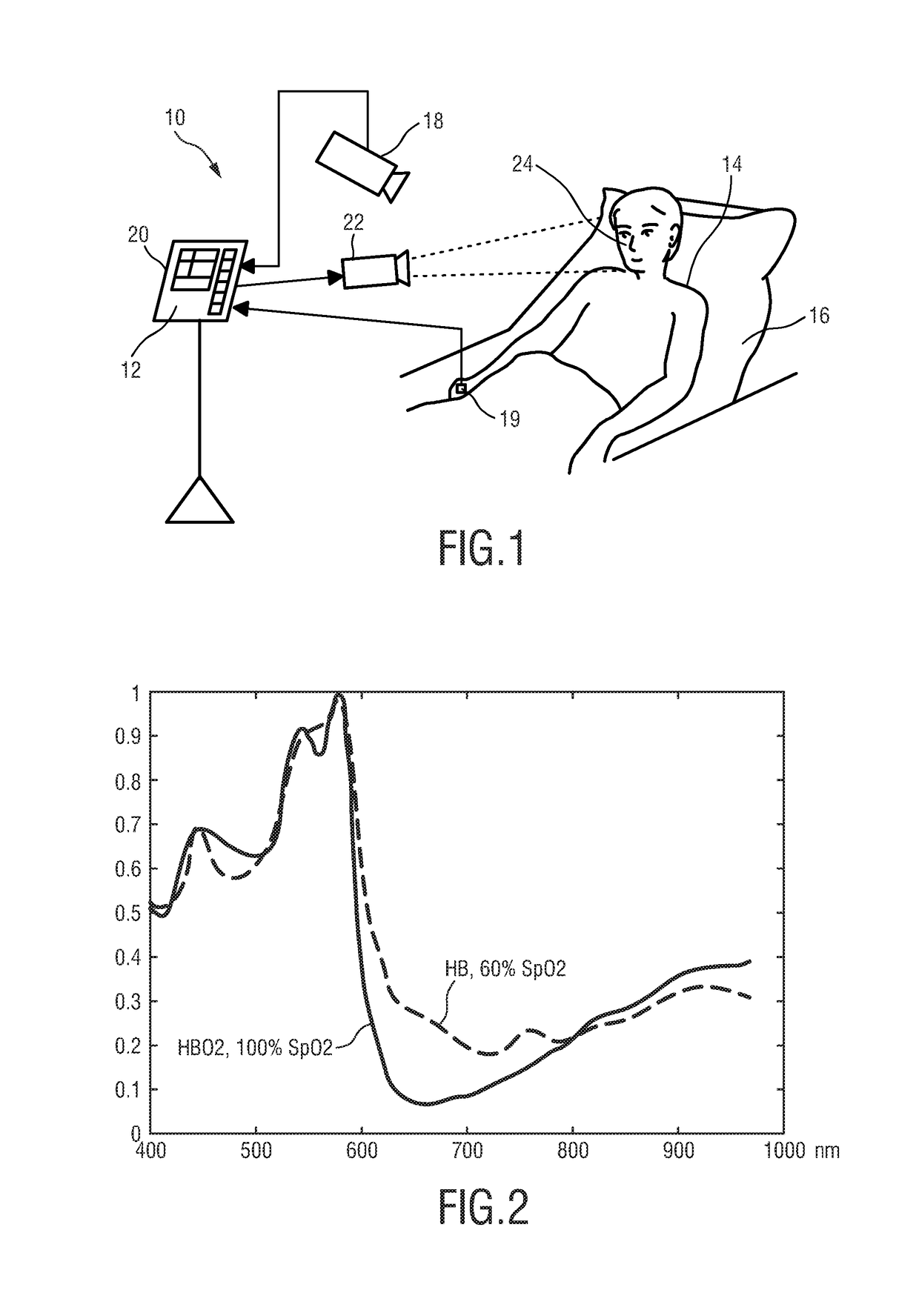
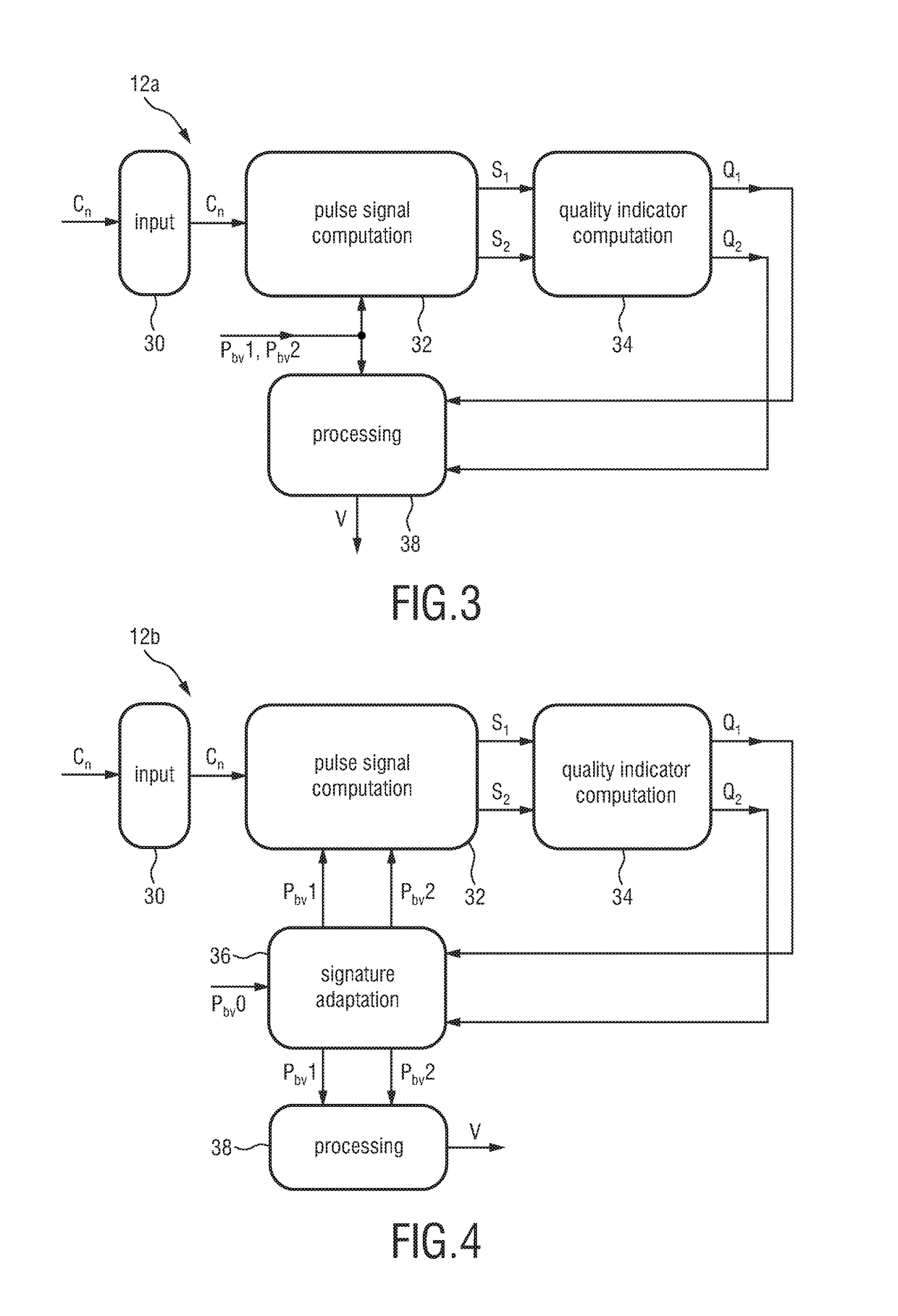
ActiveUS20170086755A1Increase relative motionImprove Noise RobustnessDiagnostics using spectroscopyEvaluation of blood vesselsElectromagnetic radiationLength wave
The present invention relates to a device, system and a method for extracting physiological information indicative of at least one vital sign of a subject. To provide a high motion robustness, the proposed device comprises an input interface configured to obtain at least two detection signals derived from detected electromagnetic radiation transmitted through or reflected from a skin region of a subject, wherein each detection signal comprises wavelength-dependent reflection or transmission information in a different wavelength channel, a pulse signal computation unit configured to compute at least two pulse signals from said at least two detection signals using different signature vectors for the computation of each pulse signal, a quality indicator computation unit configured to compute quality indicator values for said pulse signals indicating a characteristic of the respective pulse signal, and a processing unit configured to derive physiological information indicative of at least one vital sign from the signature vector that results in the pulse signal with the best quality indicator value and / or from said pulse signal.
Owner:KONINKLJIJKE PHILIPS NV
Code assignment algorithm for synchronous DS-CDMA links with SDMA using estimated spatial signature vectors
InactiveUS7050480B2Increase system capacityAntenna supports/mountingsSubstation equipmentCommunications systemParallel computing
A method is disclosed for operating a synchronous space division multiple access, code division multiple access communications system. The method operates, within a coverage area of a base station (BS) or radio base unit (RBU) having a multi-element antenna array, for estimating a SSV for individual ones of a plurality of active subscriber stations (SSs) and assigns a spreading code to a subscriber station (SS) that minimizes the similarity of the determined SSVs of the SSs in a spreading code set. A metric used to measure the similarity of the spatial signature vectors of the SSs comprises the squared sum of the inner products of same code SSs' SSV with a current SS's SSV. The step of assigning includes calculating the magnitude of the squared inner product of the SSVs of all pairs of active SSs; using the calculated values for determining ξn(c) for each spreading code that is not already used some specified maximum number of times; and assigning to a SS the spreading code with a minimum ξn(c).
Owner:L 3 COMM CORP
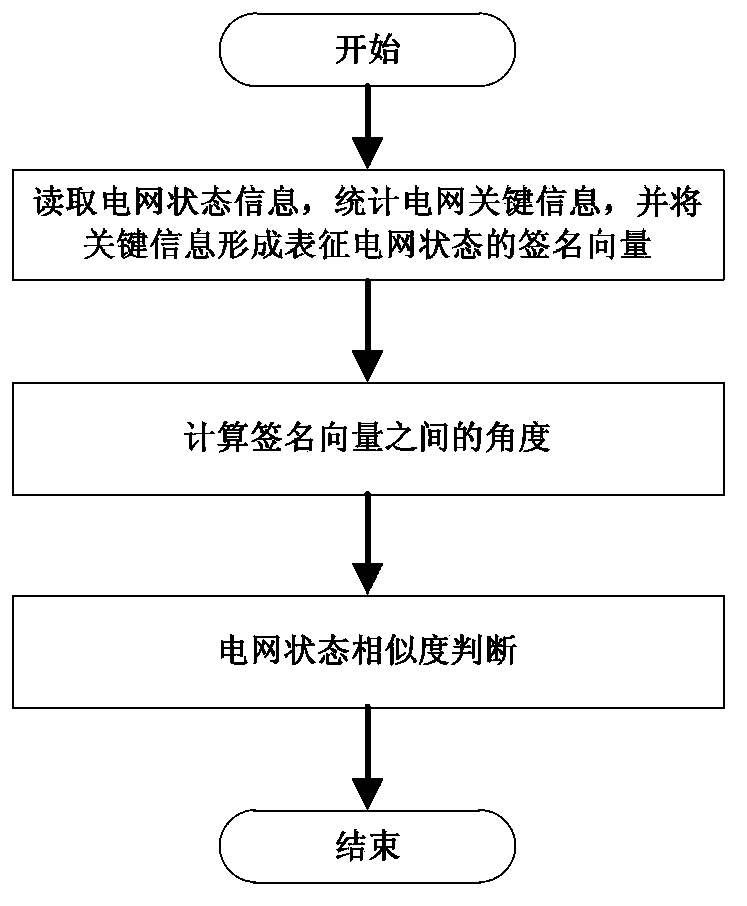
Power grid state similarity quantitative analyzing method based on locality sensitive hashing
ActiveCN103530812AAvoid analysisQuick classificationData processing applicationsElectric power systemPower grid
The invention provides a power grid state similarity quantitative analyzing method based on locality sensitive hashing. The method comprises the following steps: power grid state information is read, power grid key information is counted, and key information is formed into signature vectors representing power grid states; angles among the signature vectors are computed; and power grid state similarity is judged. The method is applicable to the locality sensitive hashing (LSH in short) technology of an electrical power system. Power grid original state data are converted into the corresponding signature vectors, and the power grid states of corresponding moments are expressed via the signature vectors. On the aforementioned basis, computation of degree of similarity of the power grid states is realized by utilizing similarity of the signature vectors. Large data of power grid state information are converted into the signature vectors of small data so that analysis of overall data is avoided.
Owner:STATE GRID CORP OF CHINA +2
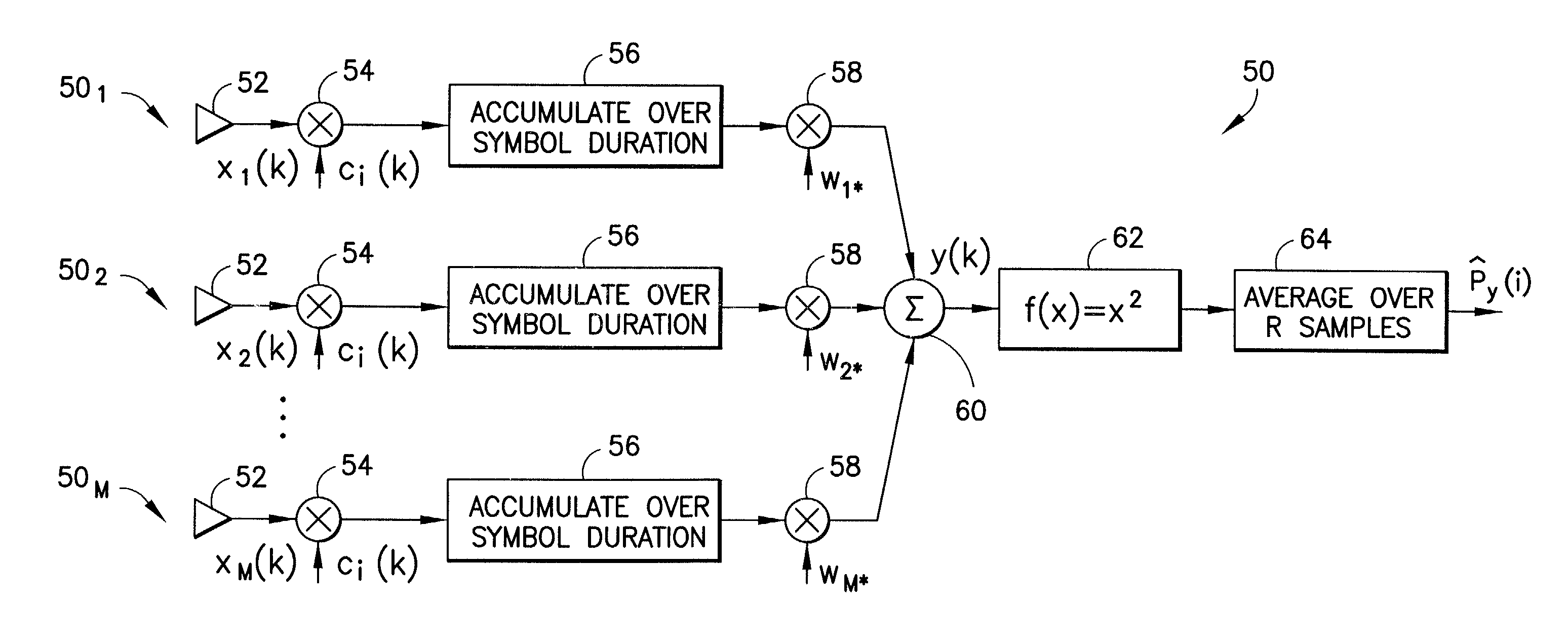
Code assignment algorithm for synchronous DS-CDMA links with SDMA using channel scanning
InactiveUS7031290B2Increase system capacityAntenna supports/mountingsSecret communicationCommunications systemSpace-division multiple access
A method is disclosed for operating a synchronous space division multiple access, code division multiple access communications system. The method operates, within a coverage area of a base station (BS) or radio base unit (RBU) having a multi-element antenna array, to assign spreading codes to users. The method estimates a spatial signature vector (SSV) for a current subscriber station; uses the estimated SSV as a weight vector when determining the output power that is correlated with each of a plurality of spreading code sequences and assigns a spreading code to the current subscriber station that is determined to have the minimum output power. The step of determining the output power includes steering a beamformer toward the current subscriber station by setting the weight vector equal to the SSV, and also determines the average squared value of the antenna array output that has been despread using a code i. The multi-element antenna array has M elements, and the step of determining the output power operates an M-branch receiver to despread a signal received on each element with a spreading code i, to accumulate the despread signal over a symbol duration, to scale the accumulated signal by the weight vector, to sum all of the scaled values and to square the result, and to average the squared result over R samples to determine the output power for code i for the current subscriber station. R may have a value in the range of about 16 symbols to about 64 symbols, and may be fixed or variable.
Owner:L 3 COMM CORP
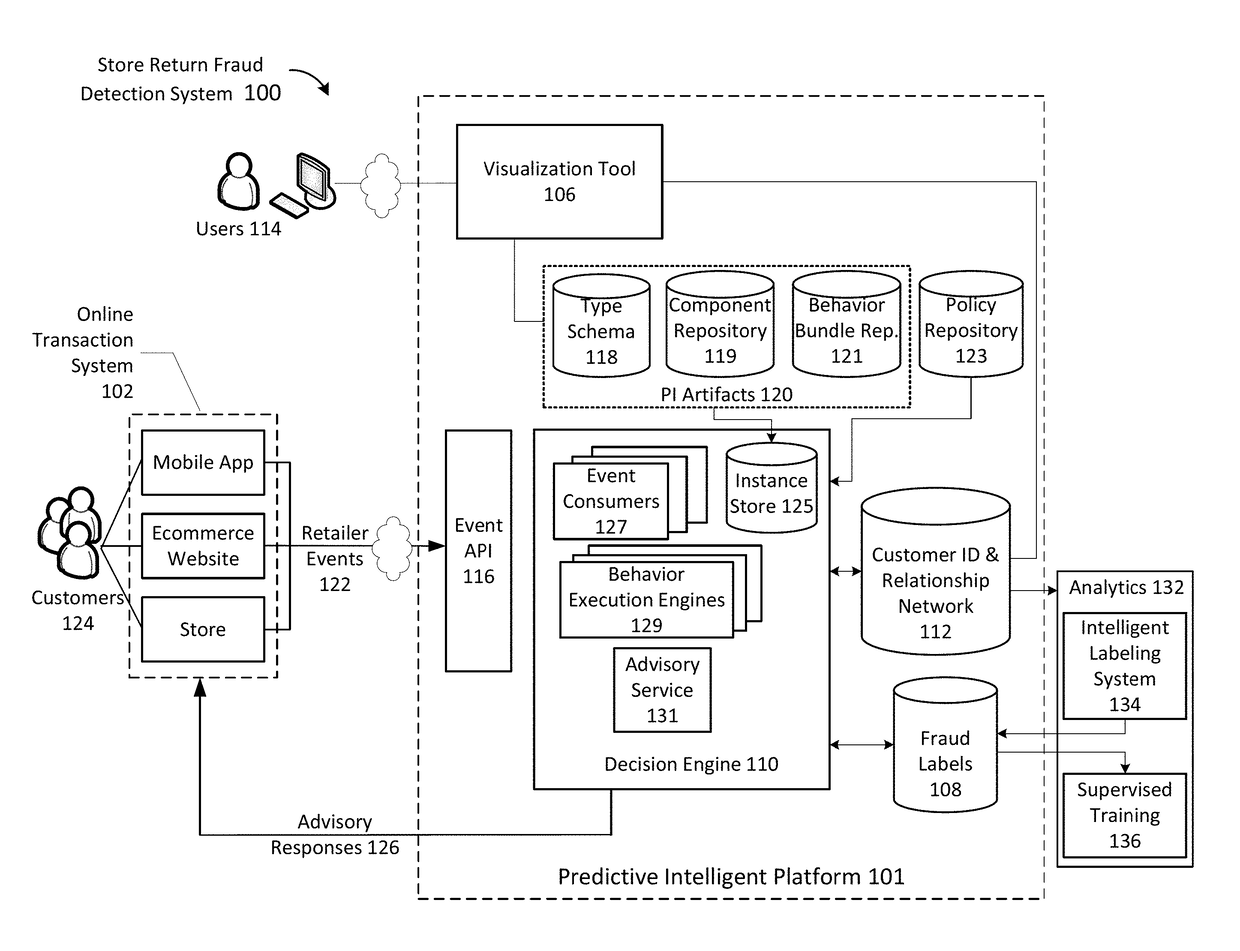
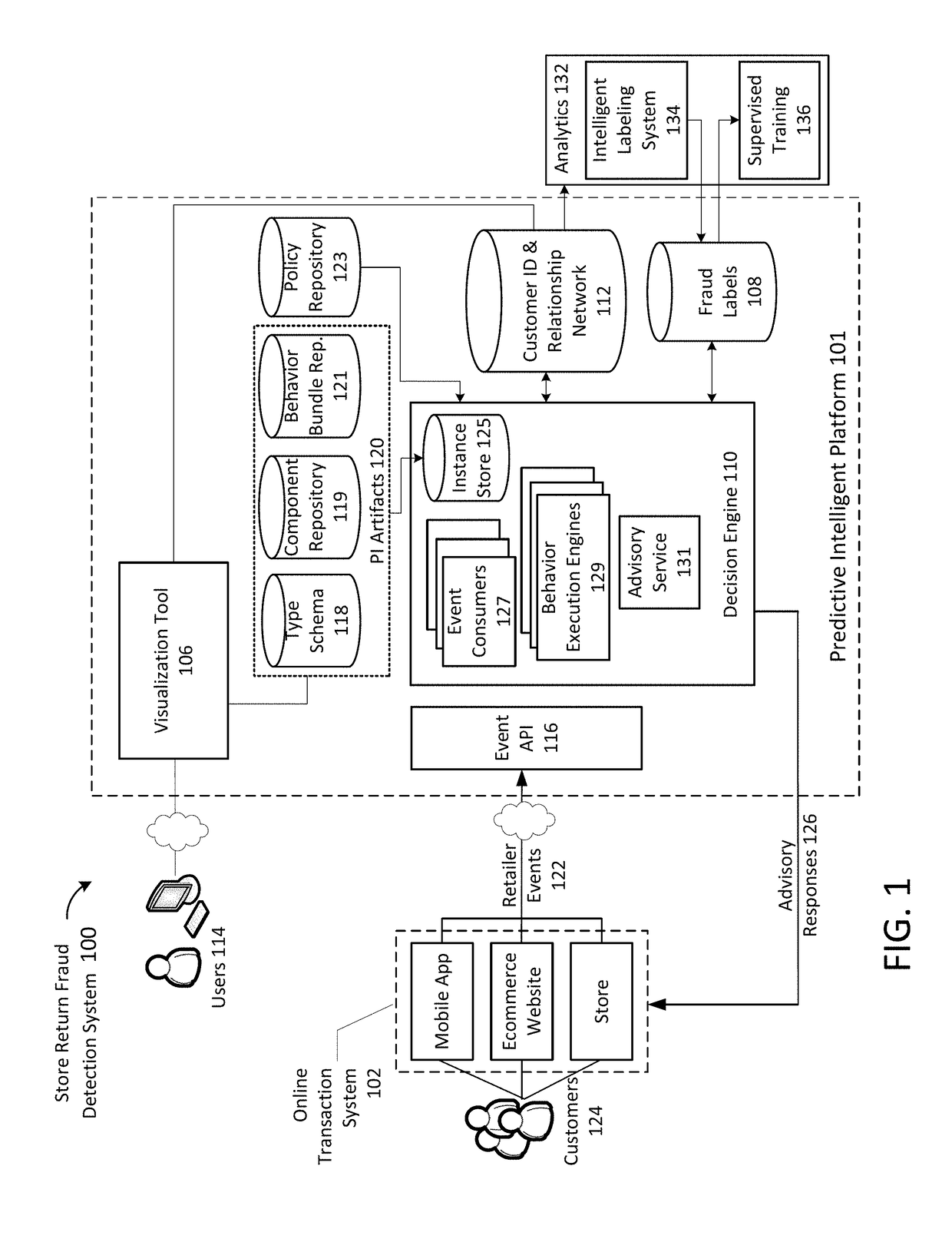
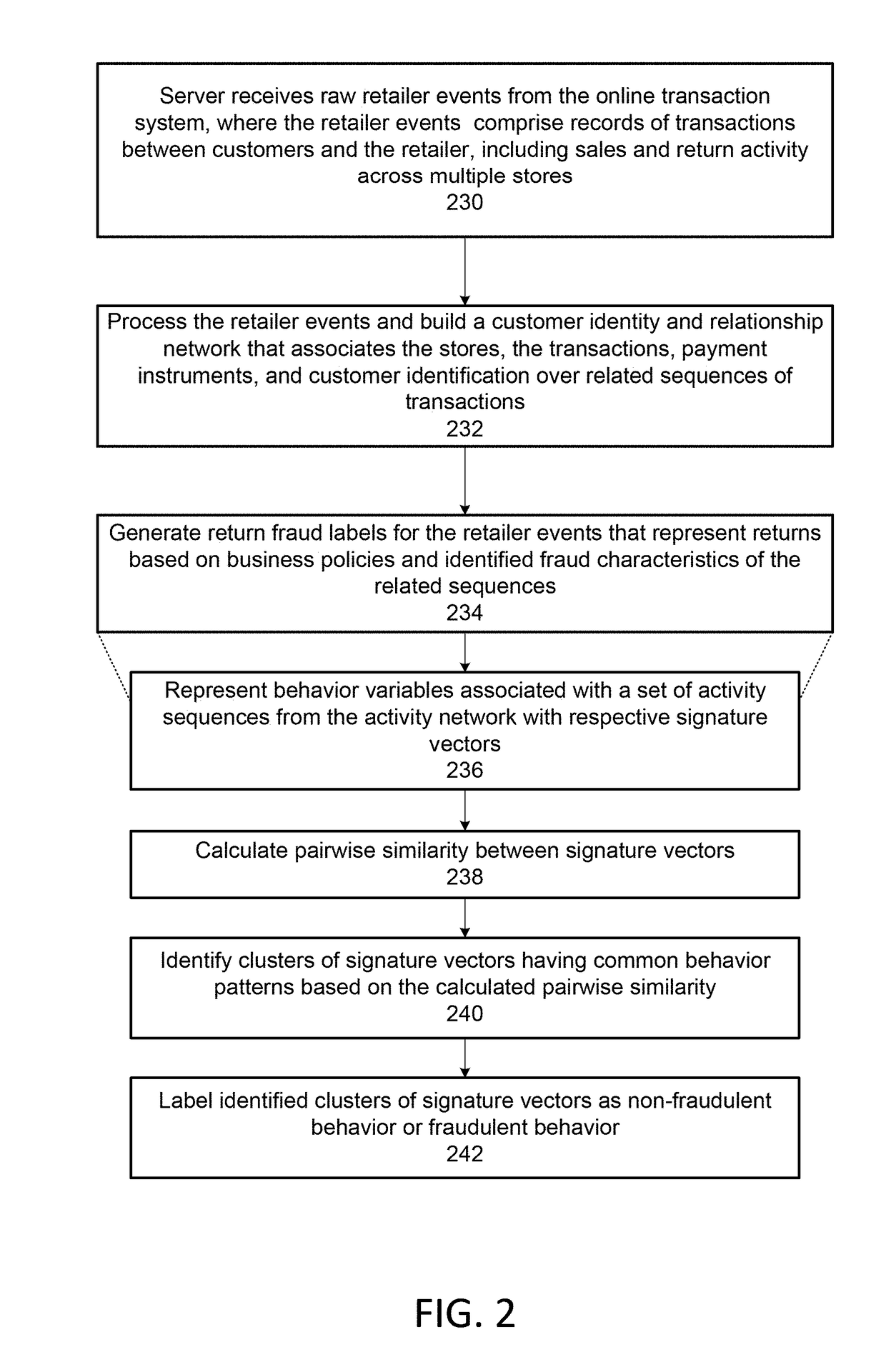
Identifying and labeling fraudulent store return activities
ActiveUS20180130071A1Reduce probabilityMinimize impactCharacter and pattern recognitionCommercePaymentData mining
A method and system for identifying and labeling fraudulent store return activities includes receiving, by a server, retailer events from an online transaction system of a retailer, the retailer events comprising records of transactions between customers and the retailer, including sale, exchange and return activities across multiple stores. The retailer events are processed to build a network that associates stores, transactions, payment instruments, and customer identification over related activity sequences of transactions. Return fraud labels are generated for the retailer events representing returns based on identified fraud characteristics of the related activity sequences by: representing behavior variables extracted from activity sequences by respective signature vectors; calculating pairwise similarity between the signature vectors; identifying clusters of the signature vectors having common behavior patterns based on the calculated pairwise similarity; and labeling the identified clusters of signature vectors as non-fraudulent behavior or fraudulent behavior.
Owner:WALMART APOLLO LLC
Communicating RF fingerprint-based geofences
Systems, apparatus and methods for communicating and using a geofence while maintaining privacy are presented. A geofence is based on at least one RF fingerprint. The RF fingerprints include absolute information that is transformed into a one-way matrix (A) by application of a one-way function. The absolute information may identify a transmitter (e.g., by location, address or the like). An equation 0=Ax (where 0 is a zero vector, A is the one-way matrix and x is a signature vector) is solved to reveal one possible solution for the signature vector (x). This signature vector (x) is communicated rather than the RF fingerprints themselves, thus obscuring the absolute information and maintaining privacy.
Owner:QUALCOMM INC
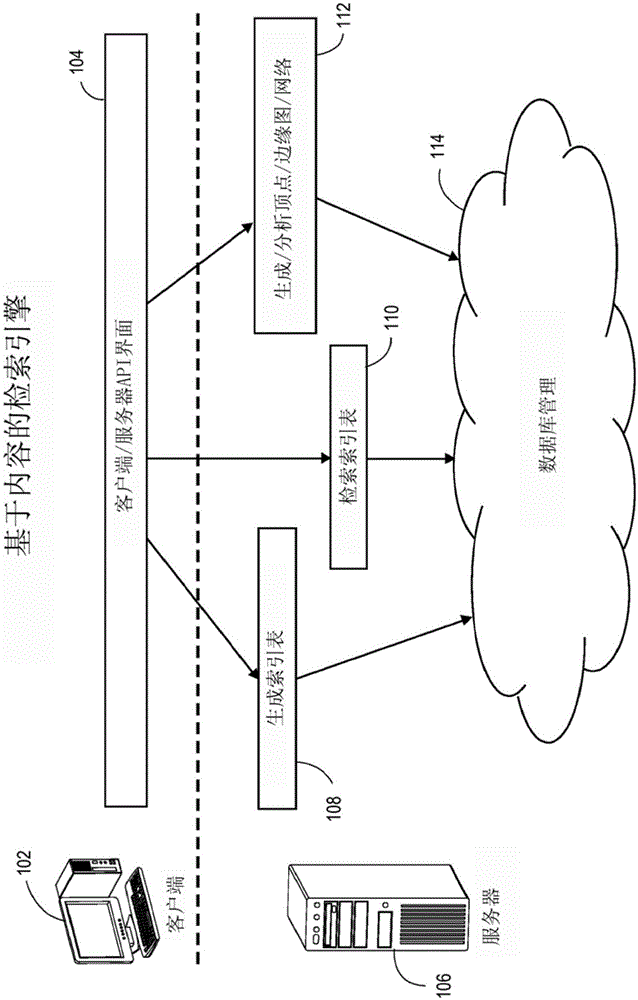
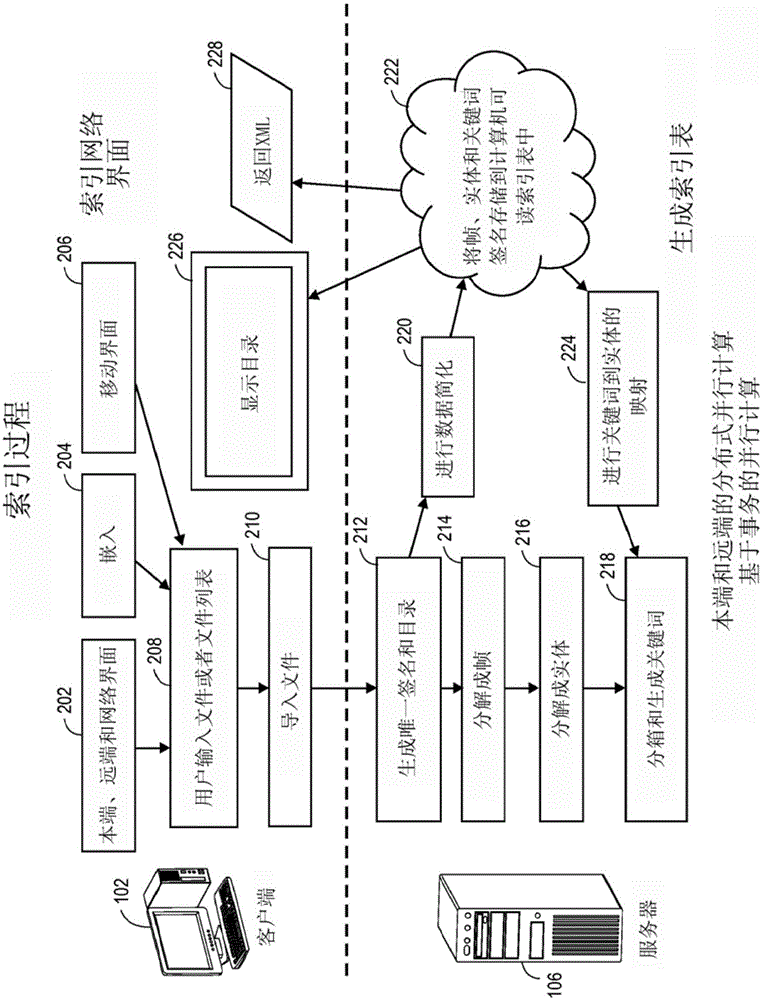
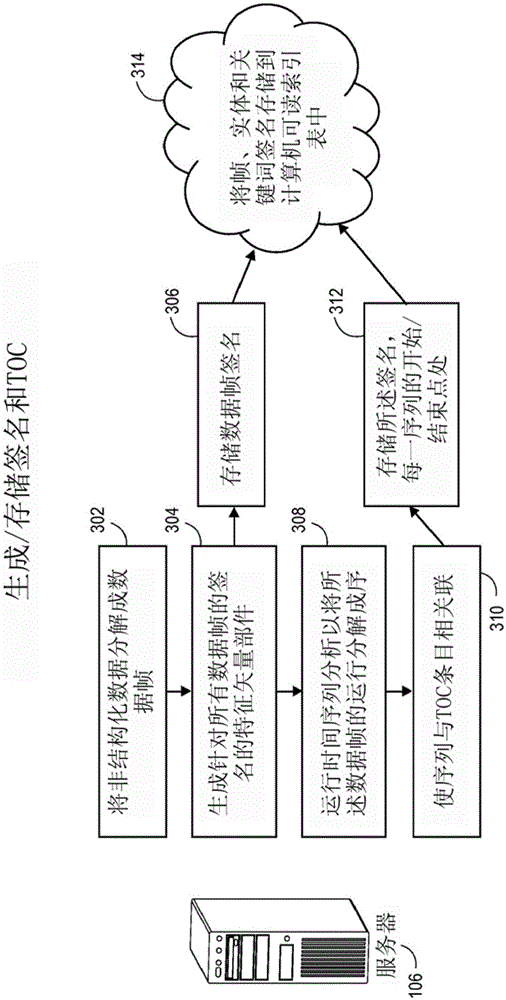
Content based search engine for processing unstructurd digital
Systems and methods for receiving and indexing native digital data and generating signature vectors for subsequent storage and searching for such native digital data in a database of digital data are disclosed. Native digital data may be transformed into associated transform data sets. Such transformation may comprise entropy-like transforms and / or spatial frequency transforms. The native and associated transform data sets may then be partitioned in to spectral components and those spectral components may have statistical moments applied to them to create a signature vector. Other systems and methods for processing non-image digital data are disclosed. Non-image digital data may be transformed into an amplitude vs time data set and a spectrogram may then be applied to such data sets. Such transformed data sets may then be processed as described.
Owner:DATAFISSION
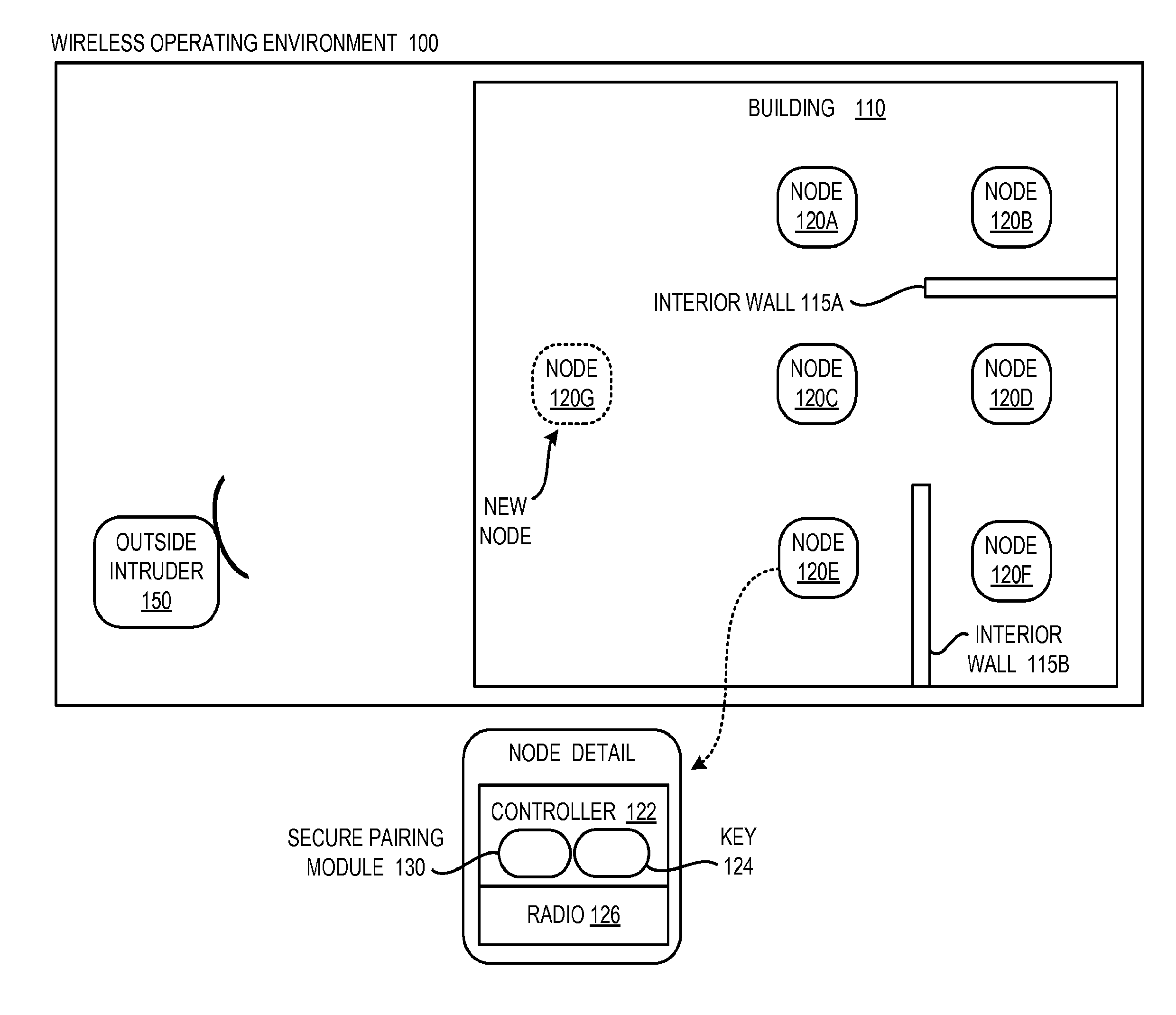
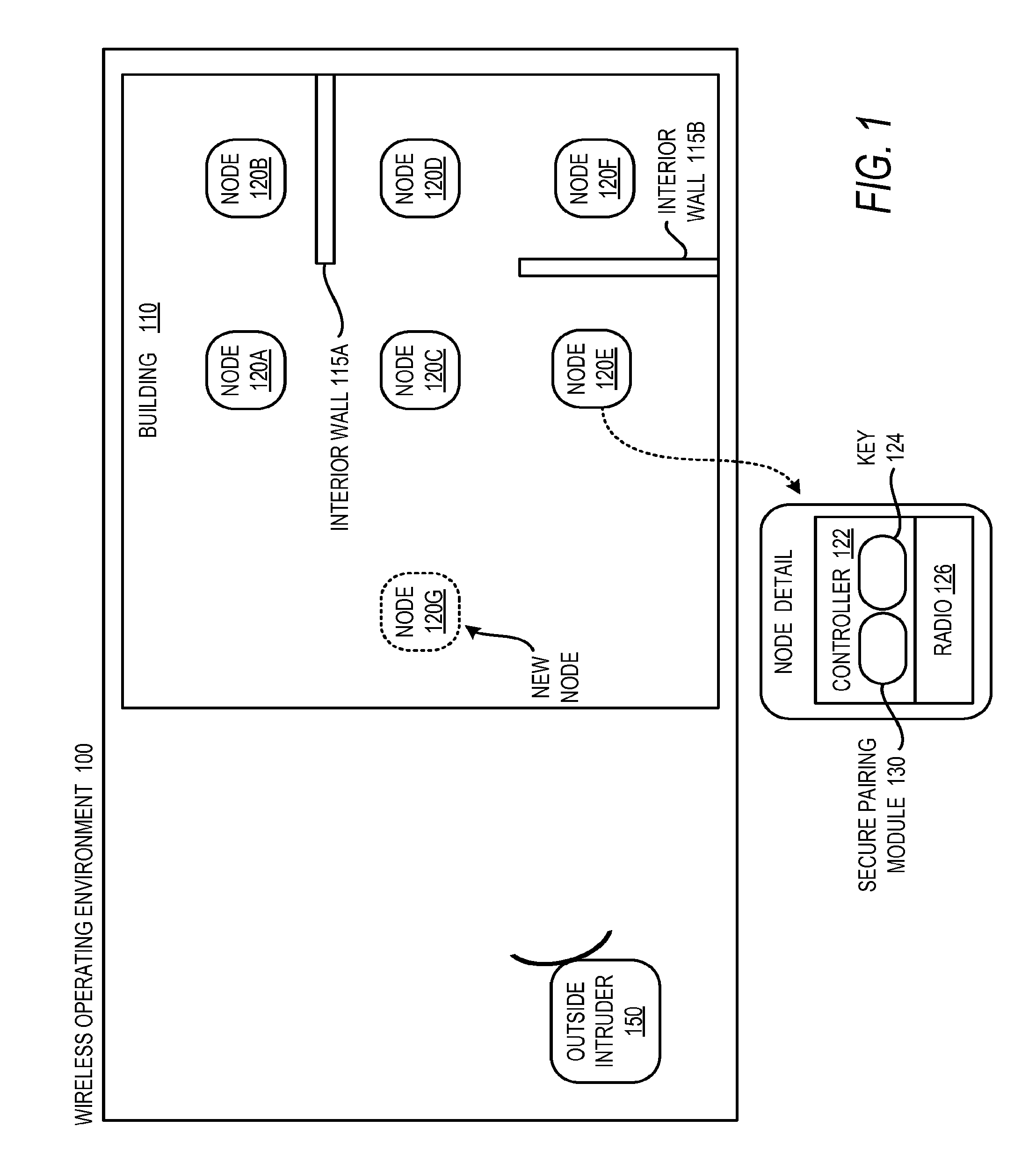
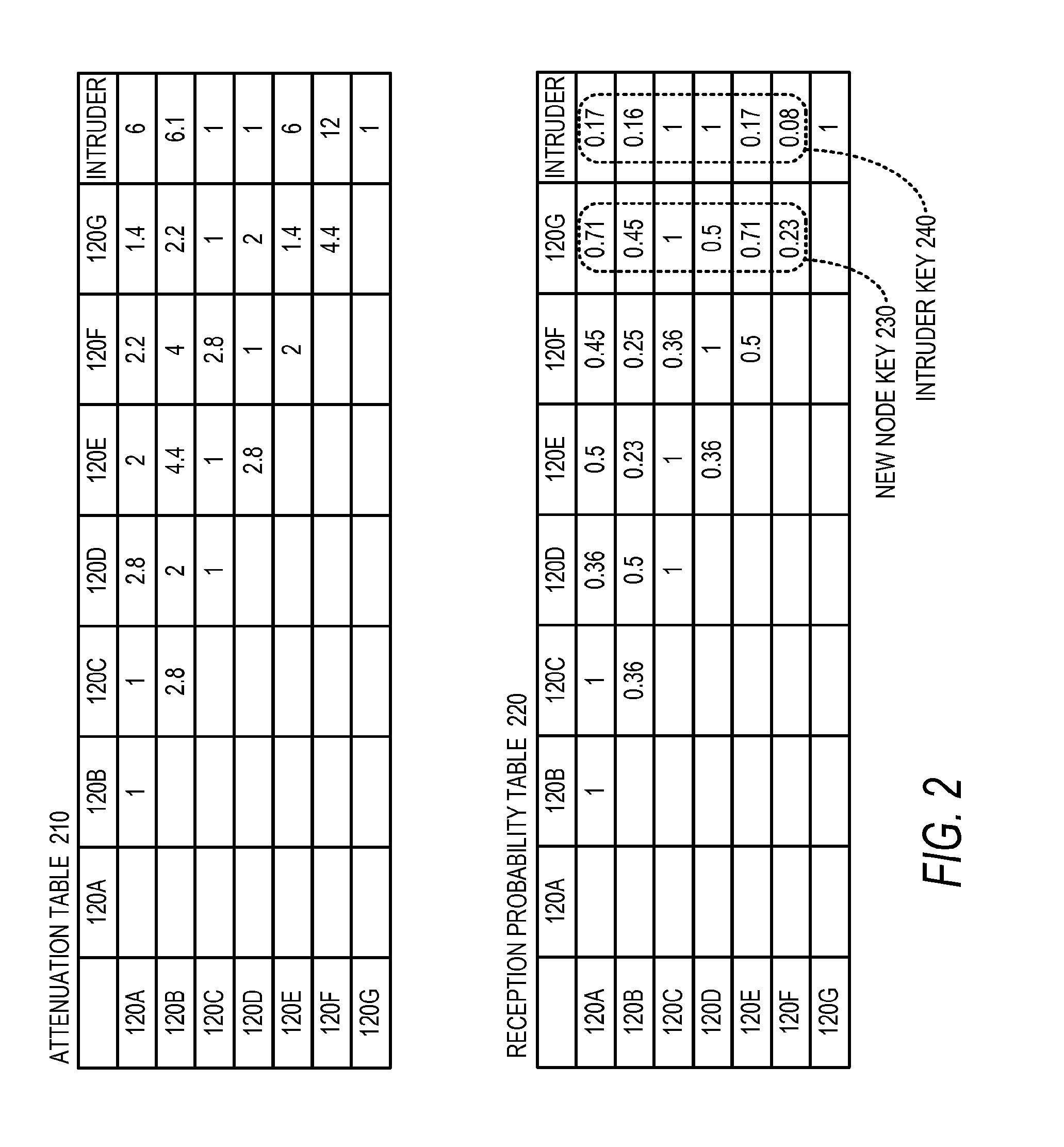
Radio Channel Metrics for Secure Wireless Network Pairing
InactiveUS20110307953A1Communication securityMemory loss protectionError detection/correctionComputer networkRadio channel
Technologies are generally described for using metrics of radio path characteristics within a wireless network to establish signal signature vectors. These signal signature vectors may be used as a shared secret between network nodes to establish affirmative identification. For example, a signal signature vector may be established when a new node sends a fixed number of packets to the existing nodes and the existing nodes send a fixed number of other packets back to the new node. The number of properly received packets can be counted to establish a success probability between the new node and each existing node. These probabilities can be normalized and quantized to generate signal signature vectors at each node. Without every transmitting any of the vectors, the vector at the new node should be highly correlated to the vectors at existing nodes since the pair-wise channels between each of the nodes should be reasonably symmetrical.
Owner:EMPIRE TECH DEV LLC
Exchange method and exchange node of metadata in opportunity network
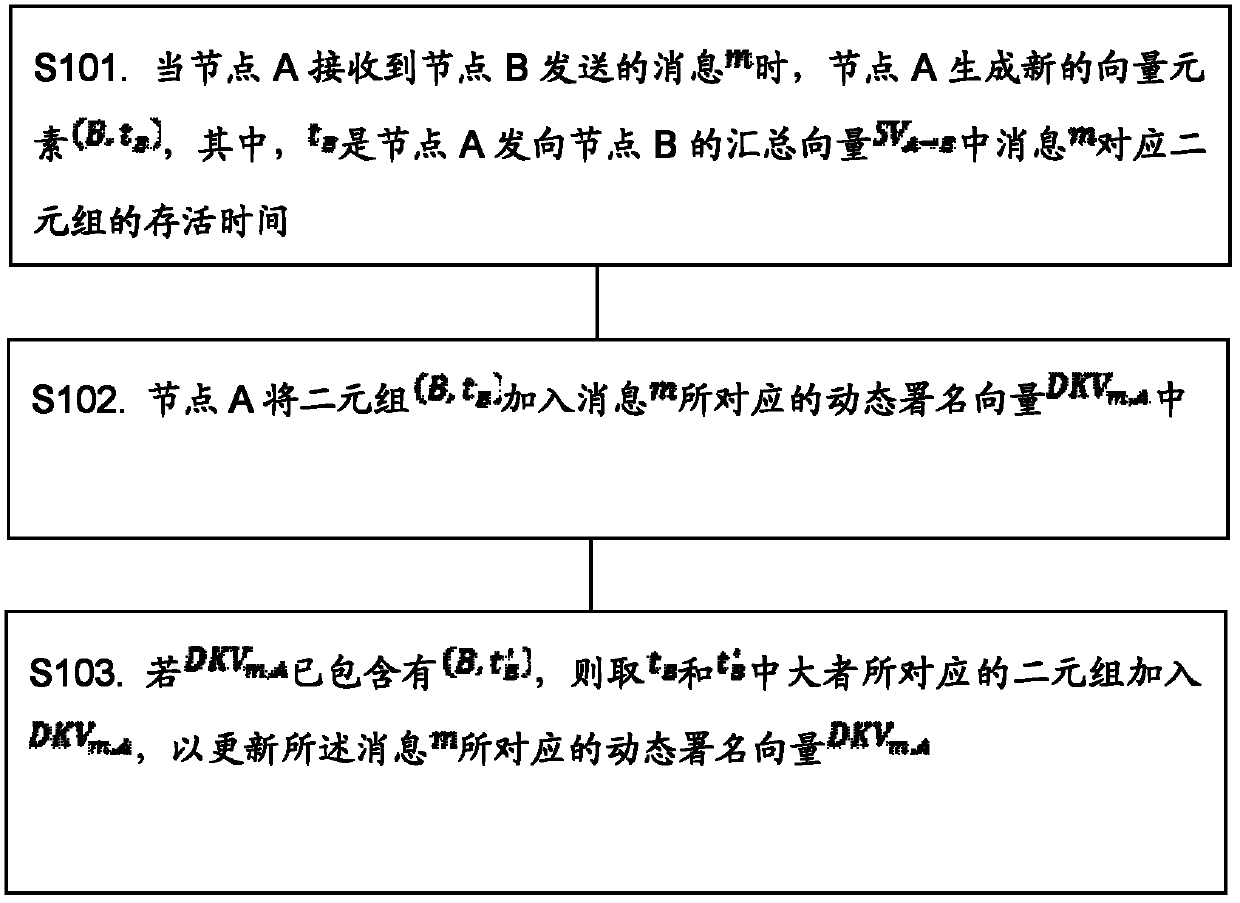
ActiveCN102791046AImprove synchronicityNetwork topologiesWireless network protocolsVector elementData mining
An embodiment of the invention discloses an exchange method and an exchange node of metadata in an opportunity network. The exchange method and the exchange node are used for the technical field of information to provide an improvement mode of dynamic signature vector aiming at resolving the problem in the prior art that solutions of metadata exchange in the opportunity network are insufficient, and especially a signature vector method has shortcomings. A node A generates a new vector element when the node A receives news transmitted by a node B, and the new vector element is survival time of two-tuples that information transmitted to the node B from the node A corresponds to. The node A adds the two-tuples into the dynamic signature vector that the information corresponds to. If the dynamic signature vector contains the two-tuples, two-tuples that larger ones in the sum correspond to are added in to update the dynamic signature vector that the information corresponds to. The exchange method and the exchange node add overtime processing and node elimination prediction mechanisms on the basis of the prior signature vector and improve synchronism of metadata between the nodes.
Owner:TONGJI UNIV
Adaptive single event latchup (SEL) current surge mitigation
ActiveUS20180248351A1Guaranteed uptimeFalse alarm rateEmergency protective arrangement detailsEmergency protective arrangements for automatic disconnectionSingle event latchupDevice status
Method for SEL mitigation involves determining one or more base sets of signature vector components for each of a plurality of signal loading conditions experienced by a protected device in an operating state, each set of base signature vector components together comprising a base signature vector. The method further involves monitoring signature vector components for the protected device to determine a detected signature vector which is comprised of a set of detected signature vector components. The detected signature vector is compared to a dynamically selected base signature vector which is associated with the device state and signal loading condition which are currently active to differentiate between the occurrence of standard current surges associated with normal operation of the protected device and a non-standard current surge.
Owner:HARRIS CORP
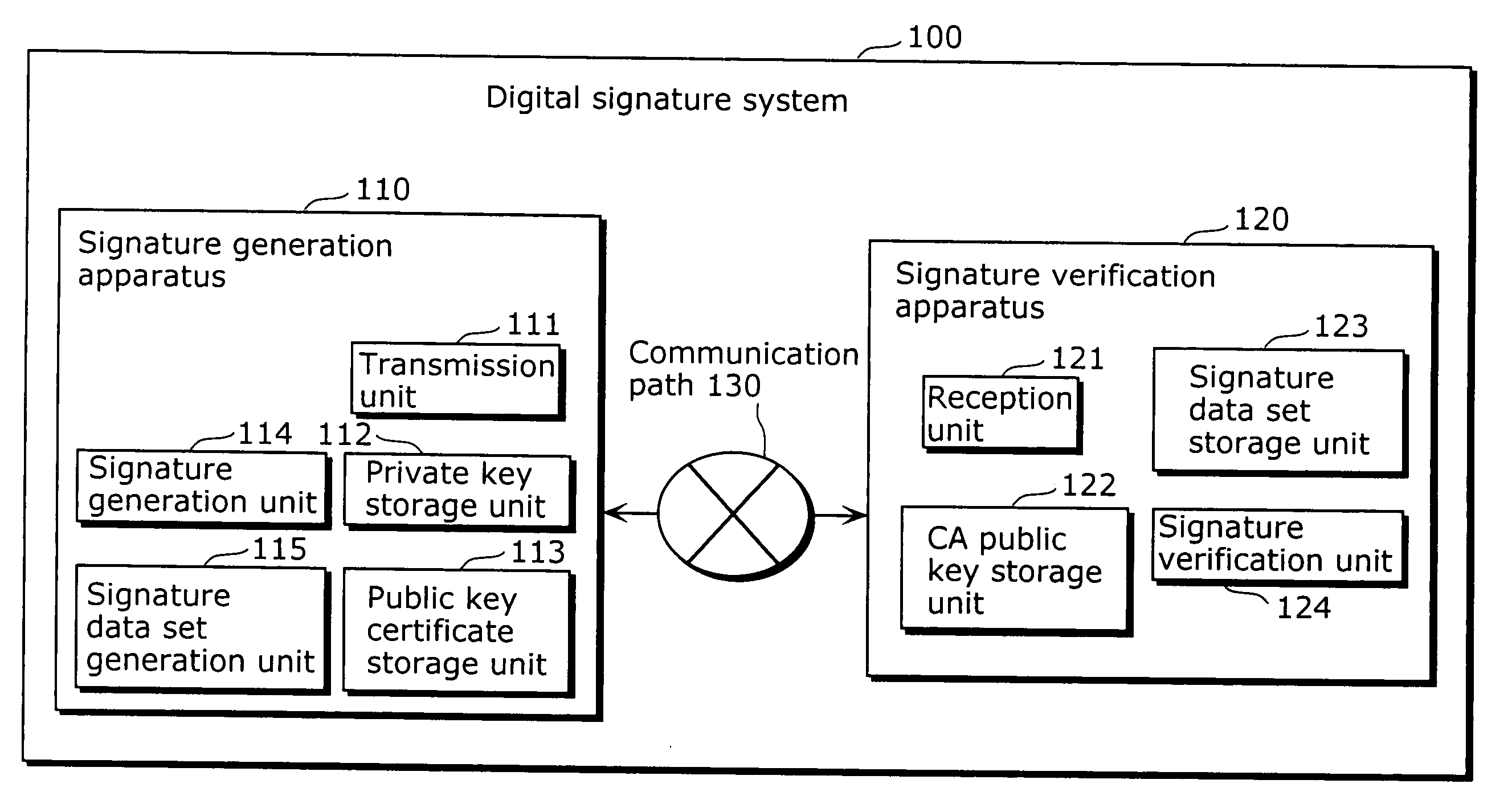
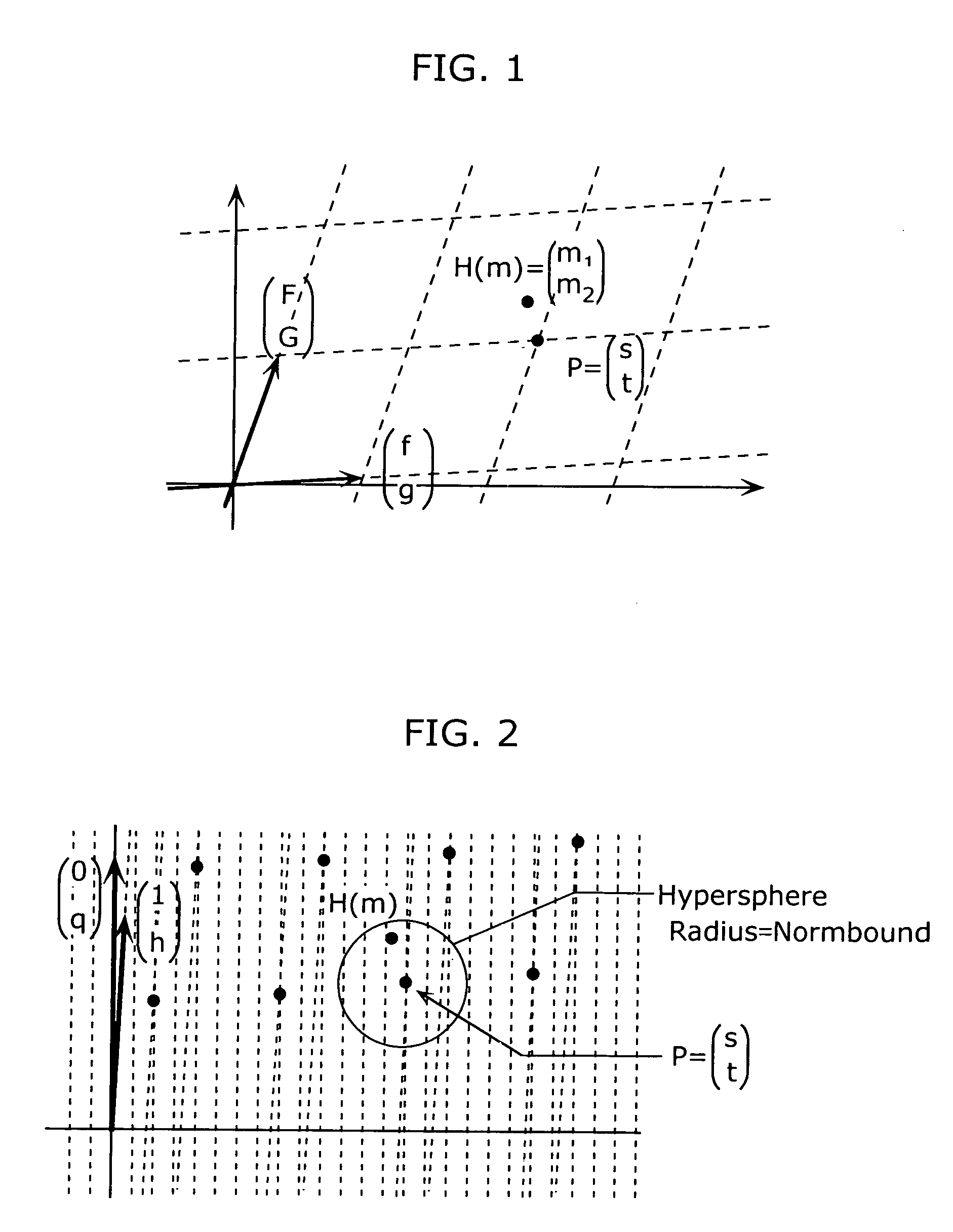
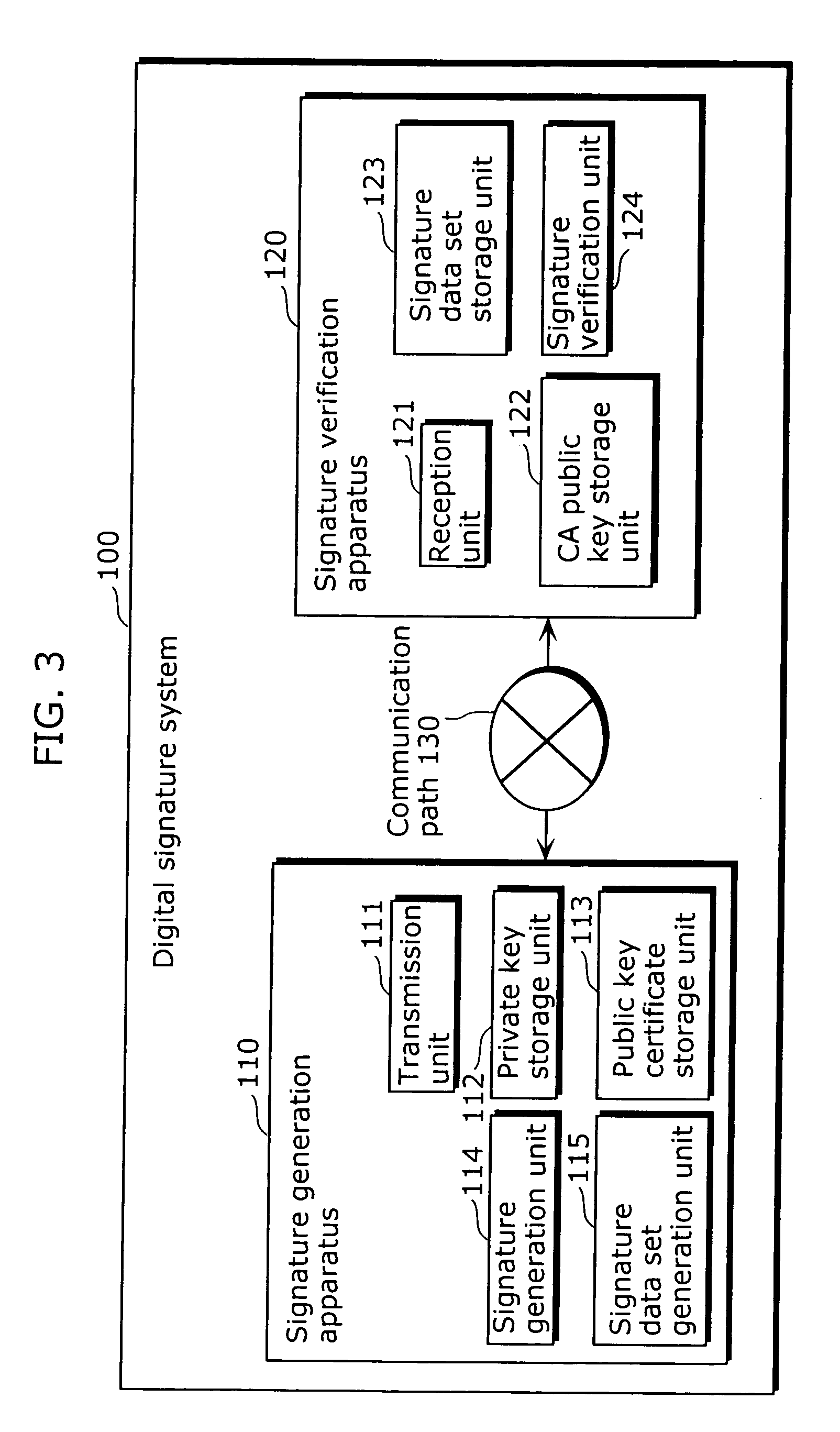
Signature generation apparatus and signature verification apparatus
ActiveUS20090235078A1Increase valueAvoid it happening againKey distribution for secure communicationMultiple keys/algorithms usageComputer scienceSignature vector
A signature generation apparatus and a signature verification which can surely prevent occurrence of inappropriate signature verification error are providedA signature generation apparatus (110) includes a signature generation unit (114) which calculates a signature vector (s, t) for a message m using a private key, and generates signature data S indicating polynomials sl and sh that can specify the polynomial s and a polynomial th which is a quotient when the polynomial t is divided by q.
Owner:PANASONIC CORP
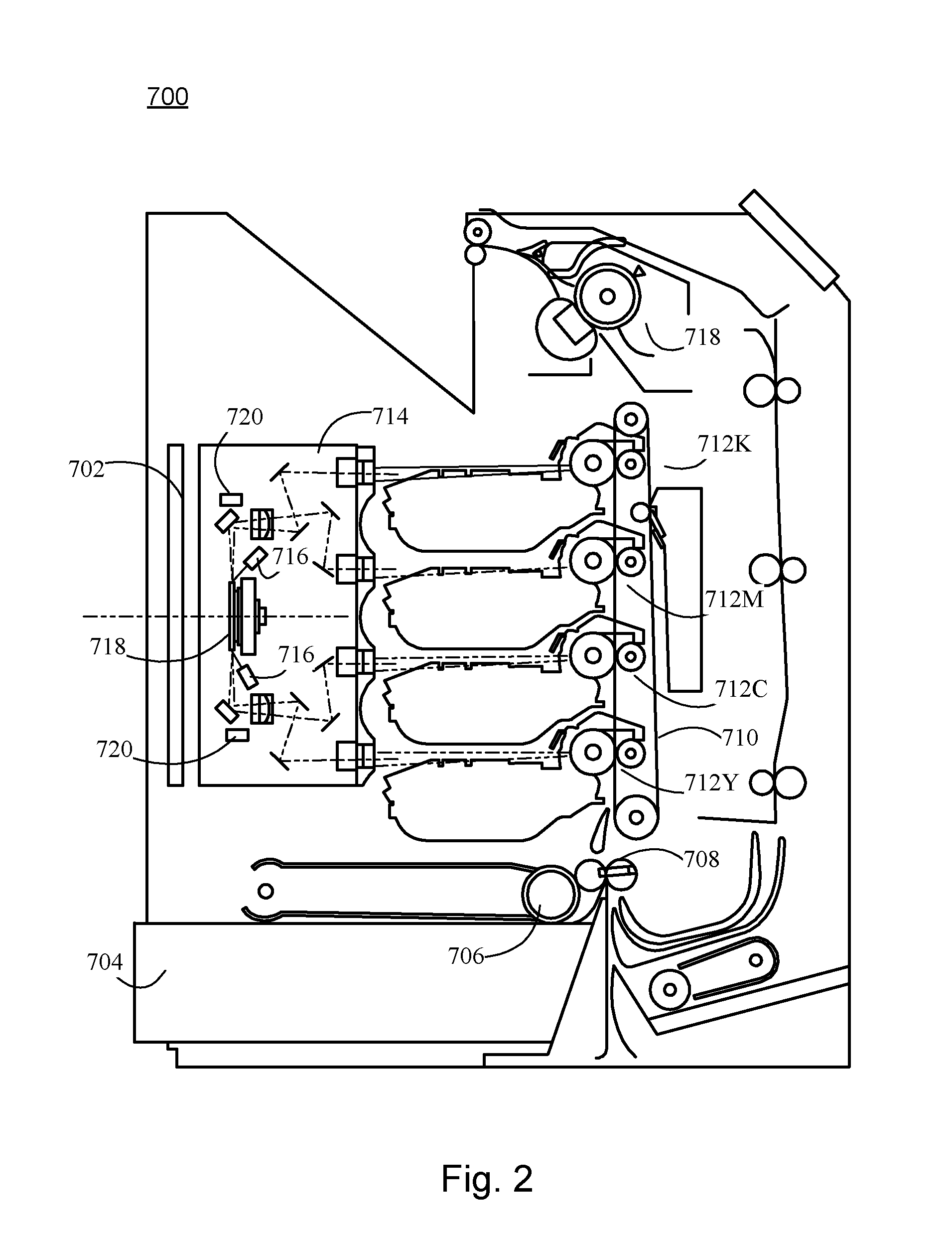
Laser scan unit for an imaging device
ActiveUS20120281996A1Reduces scan jitter scanReduces scan scan line variabilityElectrographic process apparatusElectrographic processes using charge patternFeature vectorScan line
A system and method for reducing scan line jitter in laser scan systems employing a rotating mirror, including a controller for determining a unique time delay for each mirror facet and controlling laser sources so that video provided by each laser source is delayed in a scan line by the unique time delay corresponding to the mirror facet used in creating the scan line. The controller computes a facet map signature vector corresponding to each mirror facet matches the signature to a previously stored signature and assigns distance offset data to the mirror facets based upon the matching.
Owner:LEXMARK INT INC
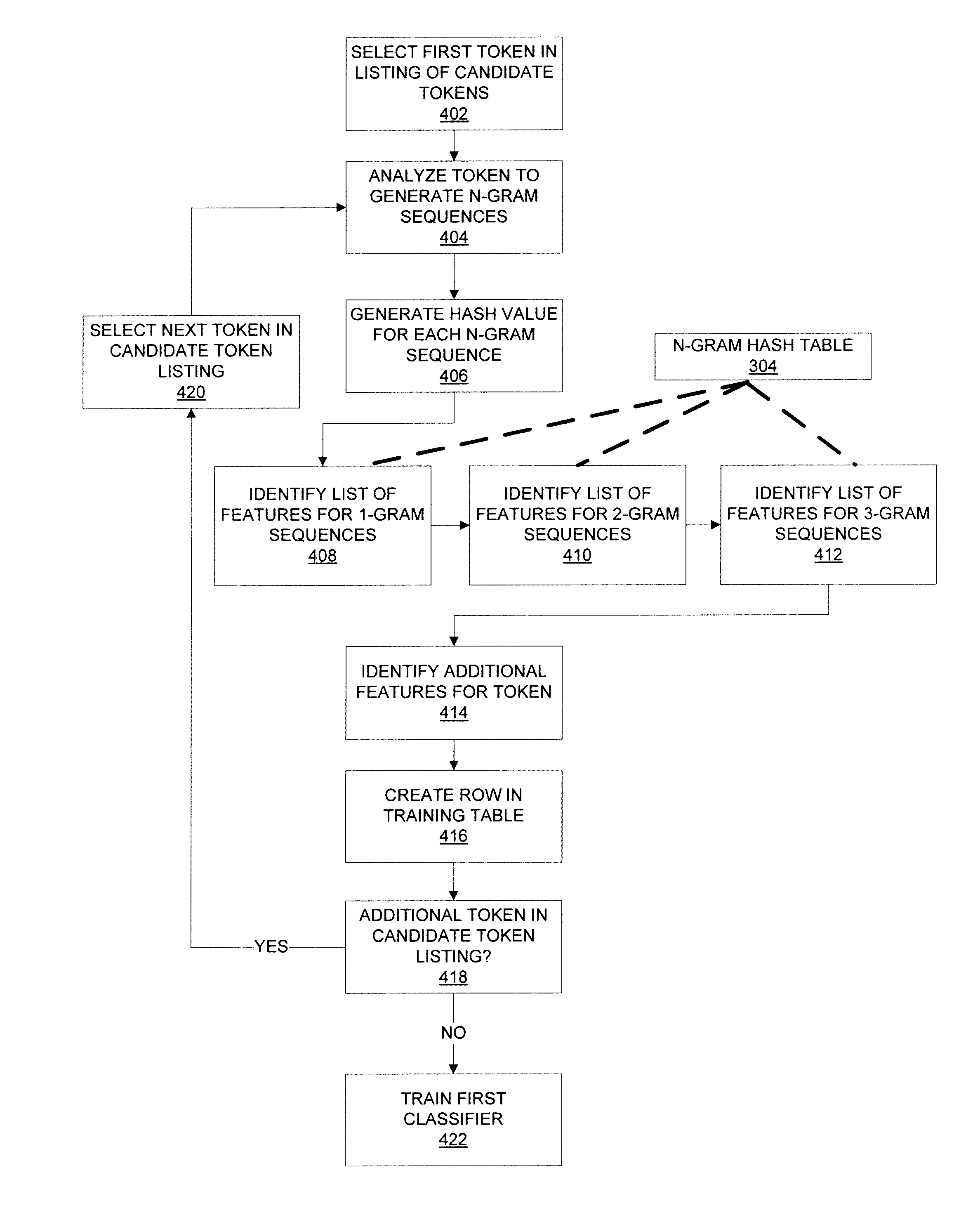
Identifying and processing a number of features identified in a document to determine a type of the document
A system and method for document classification are presented. An input document is received (e.g., by at least one server communicatively coupled to a network). A plurality of features are identified in the input document. The plurality of features include sequences of text extracted from the input document. A feature vector of the input document is generated based upon the sequences of text, and the feature vector of the input document is compared to each of a plurality of signature vectors to determine a primary type of the input document. The primary type of the input document is stored into a storage system in communication with the at least one server.
Owner:LOCU
Full-rate distributed space-time codes for cooperative communications
ActiveUS8542760B2Easy transferMaximize coding gainRepeater circuitsAmplitude-modulated carrier systemsFull RateDiversity scheme
Owner:LINGNA HLDG PTE
Single event latchup (SEL) current surge mitigation
ActiveUS9960593B2Electrical testingEmergency protective arrangements for automatic disconnectionSingle event latchupSignature vector
Method and system for Single Event Latchup (SEL) current surge mitigation involves monitoring data signals for a protected device and deriving from them a detected signature comprised of one or more detected signature vector components. The detected signature vector components are compared to previously stored signature vector components. Based on the comparing, the system selectively differentiates between the occurrence of standard power surges associated with normal operation of the protected device, and a non-standard current surge which requires cycling power of the protected device for continued proper functioning of the protected device.
Owner:HARRIS CORP
Method of analysing flight data
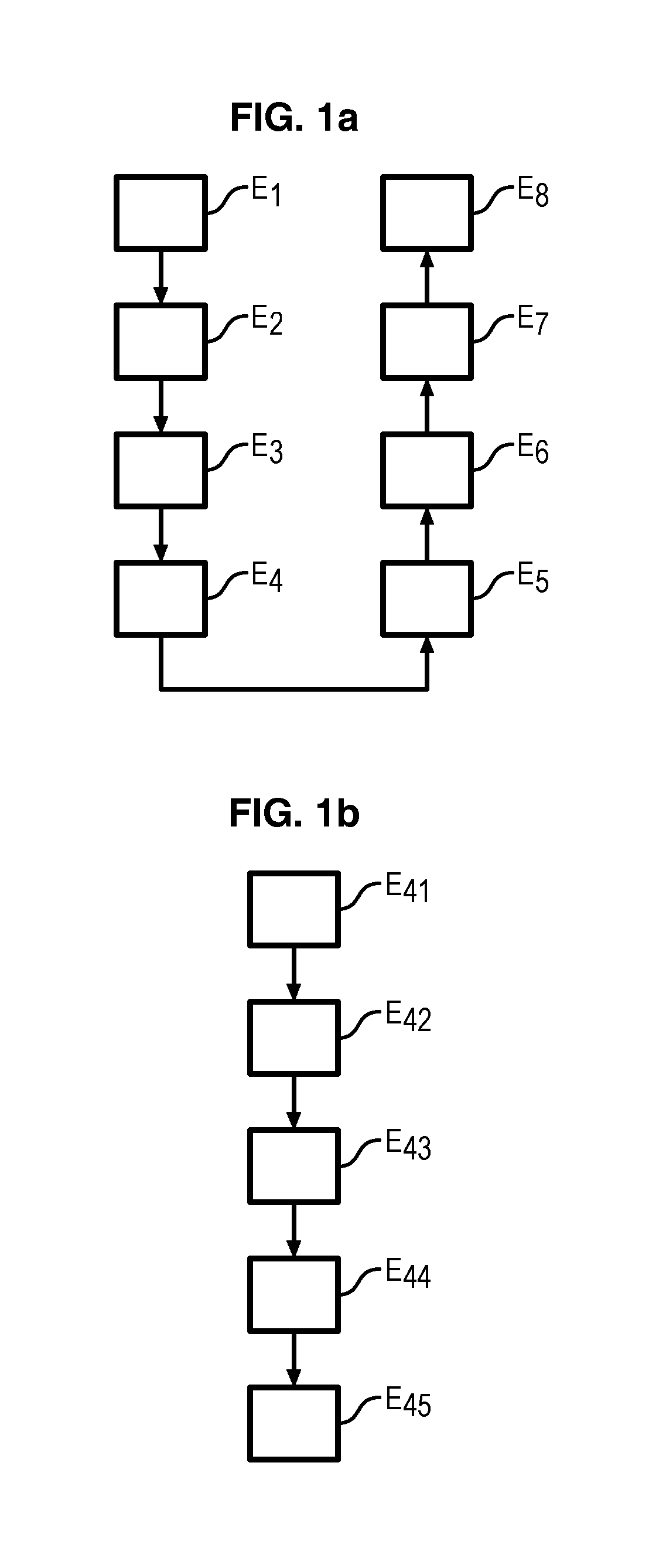
ActiveUS20150019070A1Diagnosis of abnormal is simpleSimplify the diagnostic processVehicle testingRegistering/indicating working of vehiclesComputer scienceKernel entropy component analysis
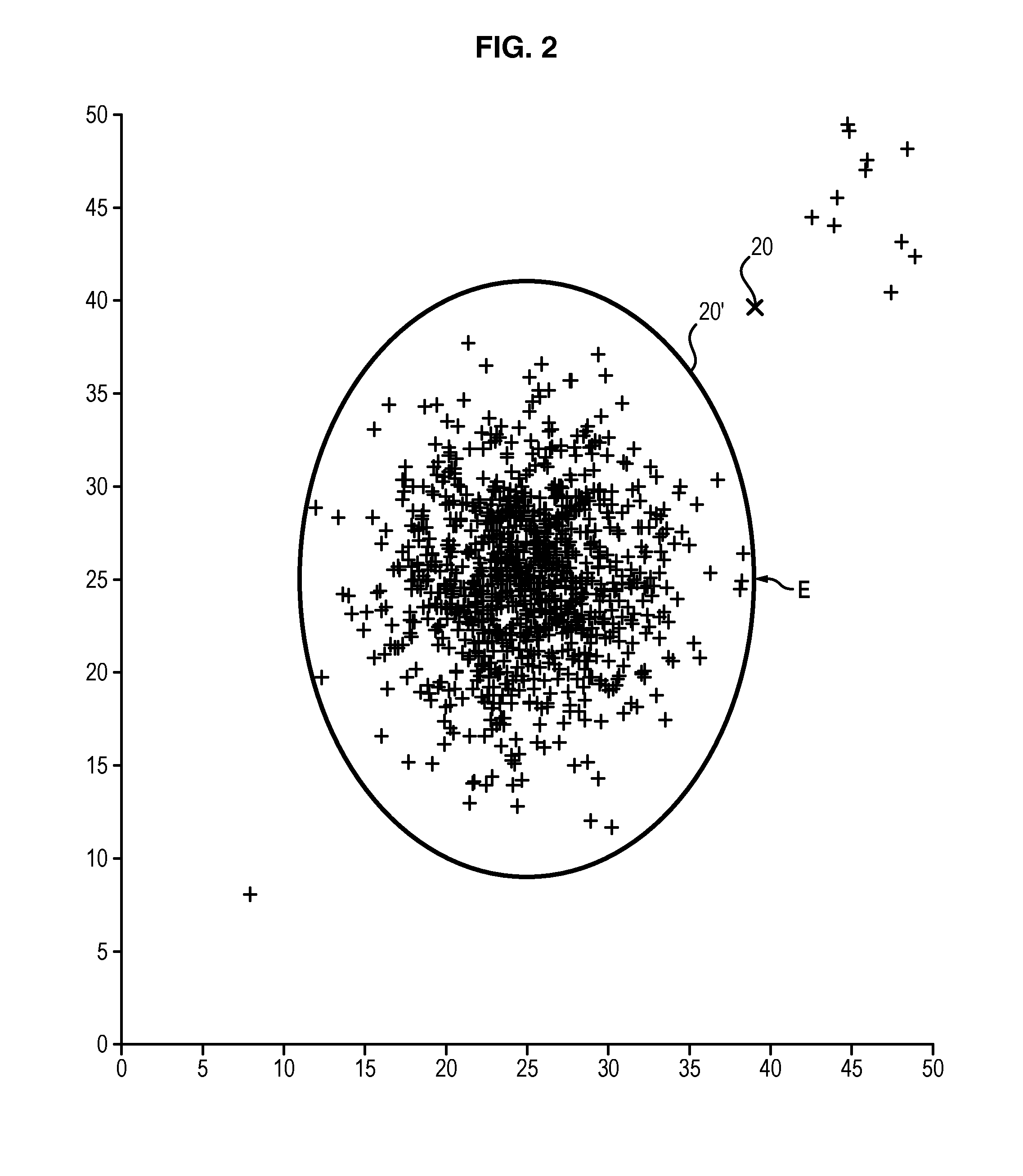
The invention relates to a method of analysing flight data recorded during N flights of at least one aircraft, by means of a flight data recorder of an aircraft, the data being grouped together by flight i in a signature vector of the flight Xi of size d, the components of which correspond to data recorded during said flight i of the aircraft, a flight i being thus defined by the signature vector Xi, the method comprising the following steps: Gaussian kernel entropy component analysis of the flight signatures Xi to obtain a zone of normal flights and classifying the flight signatures Xi with respect to their distance to said zone; determining, for each flight i, an abnormality score zi defined by the distance of a flight signature Xi with respect to the zone of normal flights; detecting, as a function of the abnormality score zi, at least one abnormal flight.
Owner:SAFRAN ELECTRONICS & DEFENSE +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com