A Hardware Acceleration Architecture and Method for Key Generation Based on Hash Post-Quantum Signature
A key generation and hardware acceleration technology, which is applied in the field of key generation hardware acceleration architecture based on post-hash quantum signatures, can solve the problems of low key efficiency and speed, long time consumption, etc., and achieve low latency and high hardware utilization rate, the effect of resisting power attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] In order to improve the key generation speed of LMS signature and reduce the time consumption of key generation, the embodiment of the present application provides a hardware acceleration architecture and method for key generation based on post-hashing quantum signature.
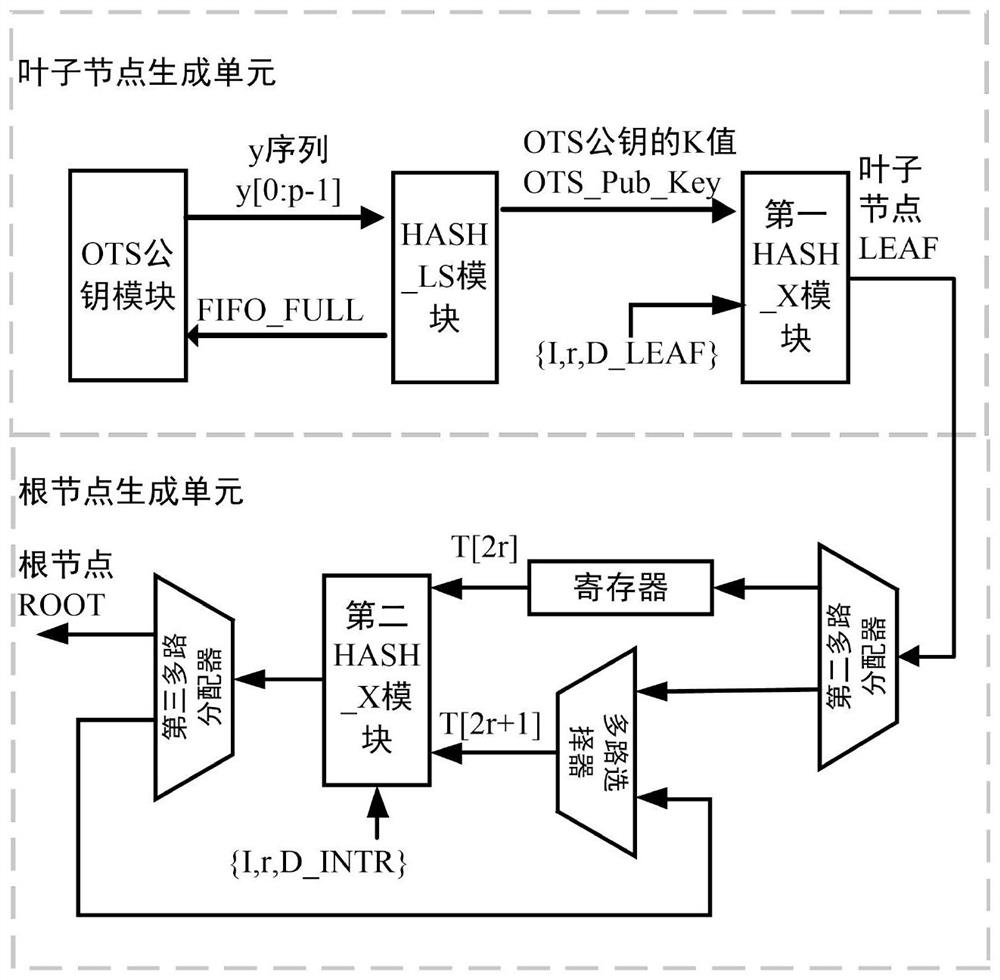
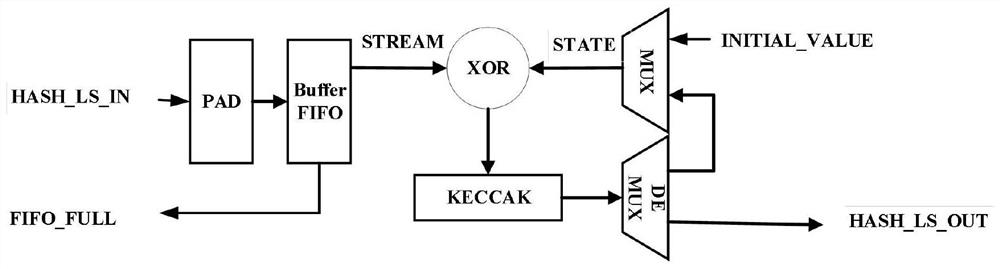
[0044] Such as figure 1 As shown, the first aspect of the embodiment of the present application provides a key generation hardware acceleration architecture based on post-hash quantum signature, the key generation hardware acceleration architecture includes a leaf node generation unit and a root node generation unit, and the leaf node The generating module includes an OTS public key module, a HASH_LS module and a first HASH_X module.
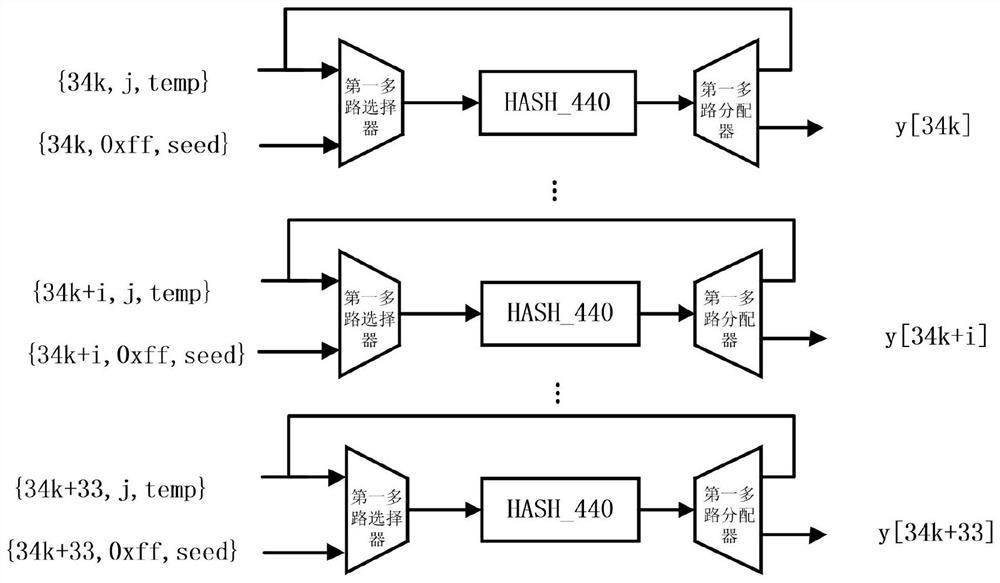
[0045] Such as figure 2 As shown, it is a schematic diagram of the overall structure of the hardware acceleration architecture provided by the embodiment of the present application. The OTS public key module includes p groups of parallel OTS key submodules, and p is t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com