File encryption and decryption method and device
A file encryption and file technology, applied in the field of data processing, can solve the problems of low efficiency and long processing time, and achieve the effect of reducing processing time and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
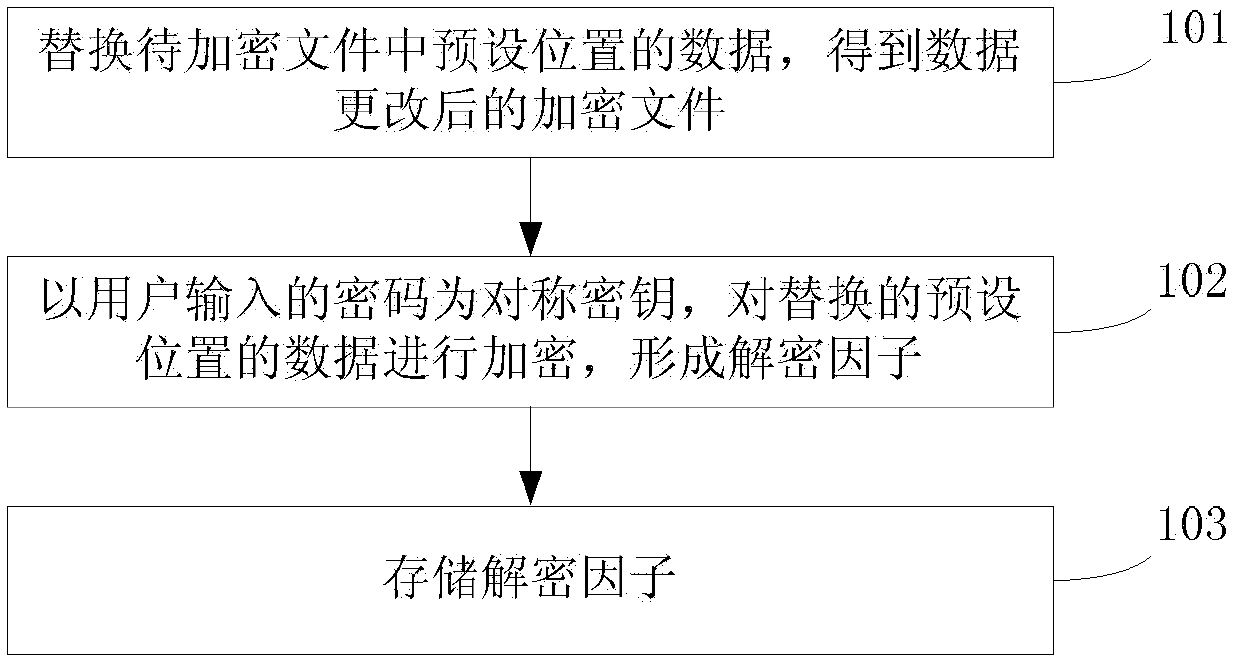
[0055] see figure 1 , the embodiment of the present invention provides a file encryption method, comprising:
[0056] 101: replace the data in the preset position in the file to be encrypted, and obtain the encrypted file after the data is changed;
[0057] Further, after obtaining the encrypted file after the data change, it also includes:
[0058] Set an encryption suffix for encrypted files to identify encrypted files based on their encryption suffix.
[0059] 102: Use the password input by the user as a symmetric key to encrypt the data at the replaced preset location to form a decryption factor;
[0060] 103: Store the decryption factor.
[0061] For this step, this embodiment does not limit the specific implementation of storing the decryption factor, including but not limited to the following methods:
[0062] Establish a corresponding relationship between the decryption factor and the encrypted file, and store the decryption factor locally according to the correspo...
Embodiment 2
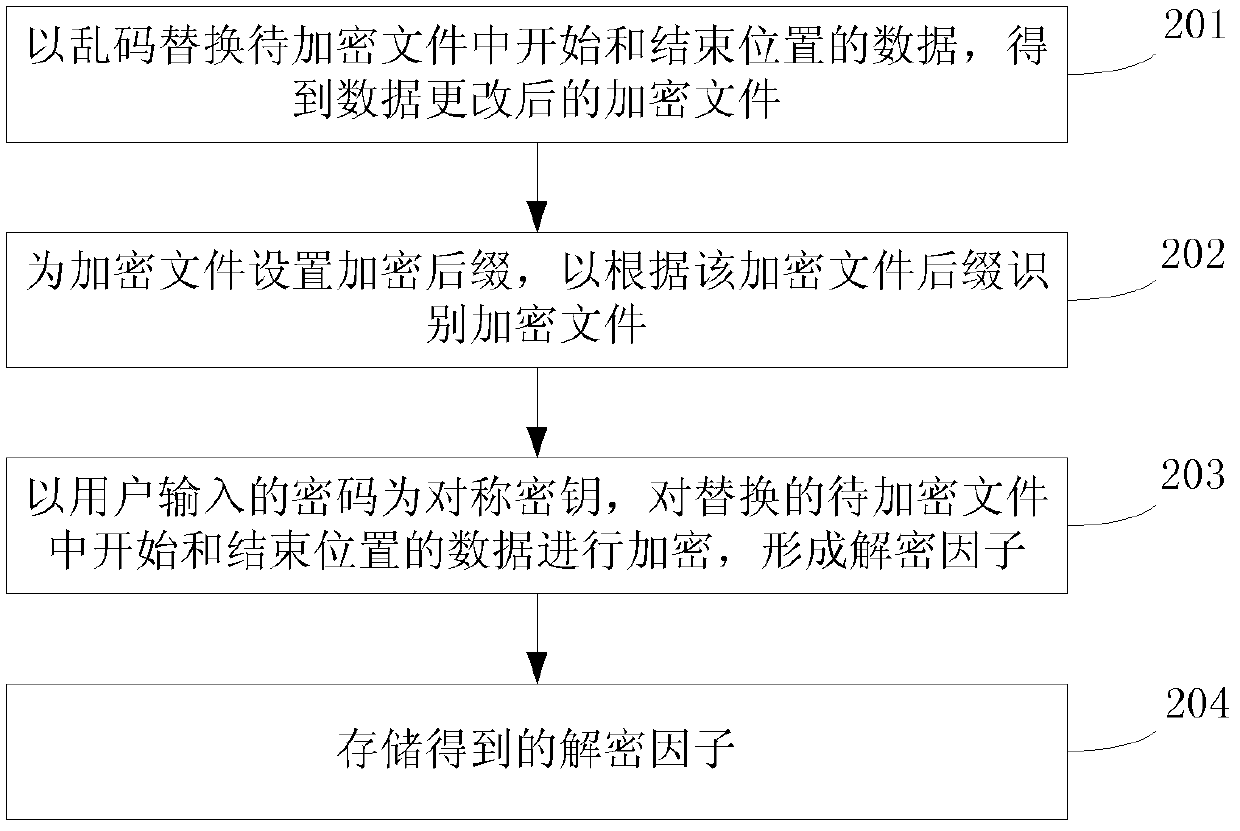
[0065] see figure 2, this embodiment provides a file encryption method. For the convenience of description, in combination with the content of the first embodiment above, this embodiment replaces the data at the preset position in the file to be encrypted with the data at the start and end positions of the file to be encrypted as As an example, the method provided in this embodiment is illustrated. see figure 2 , the method flow provided by this embodiment is specifically as follows:
[0066] 201: replace the data at the start and end positions in the file to be encrypted with garbled characters, and obtain the encrypted file after data modification;
[0067] Wherein, garbled characters are the chaotic characters that cannot be read normally because the system or software lacks support for a certain character encoding. The purpose of browsing the file to be encrypted normally is to achieve the effect of encryption. For the data at the start position and the end position ...
Embodiment 3
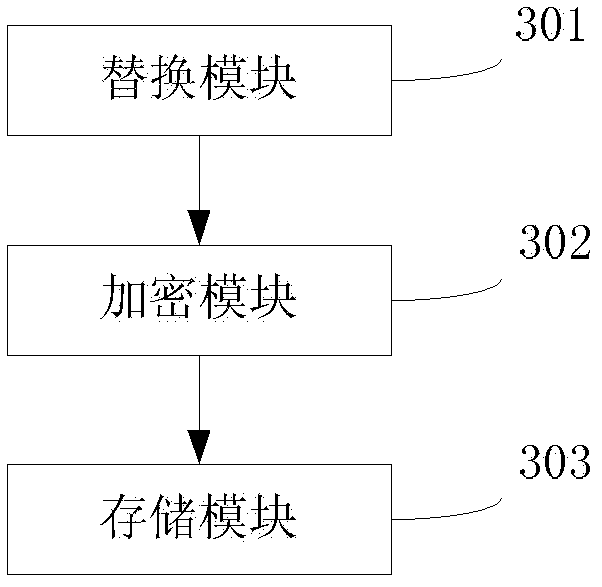
[0079] This embodiment provides a file encryption device, which is used to implement the file encryption methods provided in the first and second embodiments above. see image 3 , the device consists of:
[0080] Replacement module 301, is used for replacing the data of preset position in the file to be encrypted, obtains the encrypted file after data change;
[0081] An encryption module 302, configured to use the password input by the user as a symmetric key to encrypt the data at the preset position replaced by the replacement module 301 to form a decryption factor;
[0082] The storage module 303 is configured to store the decryption factor obtained by the encryption module 302 .
[0083] Wherein, when the replacement module 301 replaces the data in the preset position in the file to be encrypted, its specific implementation method can refer to the relevant description of step 201 in the second embodiment above, and will not be repeated here. The process of encrypting t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com