File encryption and decryption method and terminal
A file encryption and file technology, applied in the direction of digital data protection, etc., can solve the problem of low file security, and achieve the effect of avoiding low security, improving difficulty and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] In order to clearly describe the technical solutions of the embodiments of the present invention, in the embodiments of the present invention, words such as "first" and "second" are used to distinguish the same or similar items with basically the same functions and functions. Those skilled in the art can understand that words such as "first" and "second" do not limit the quantity and execution order.
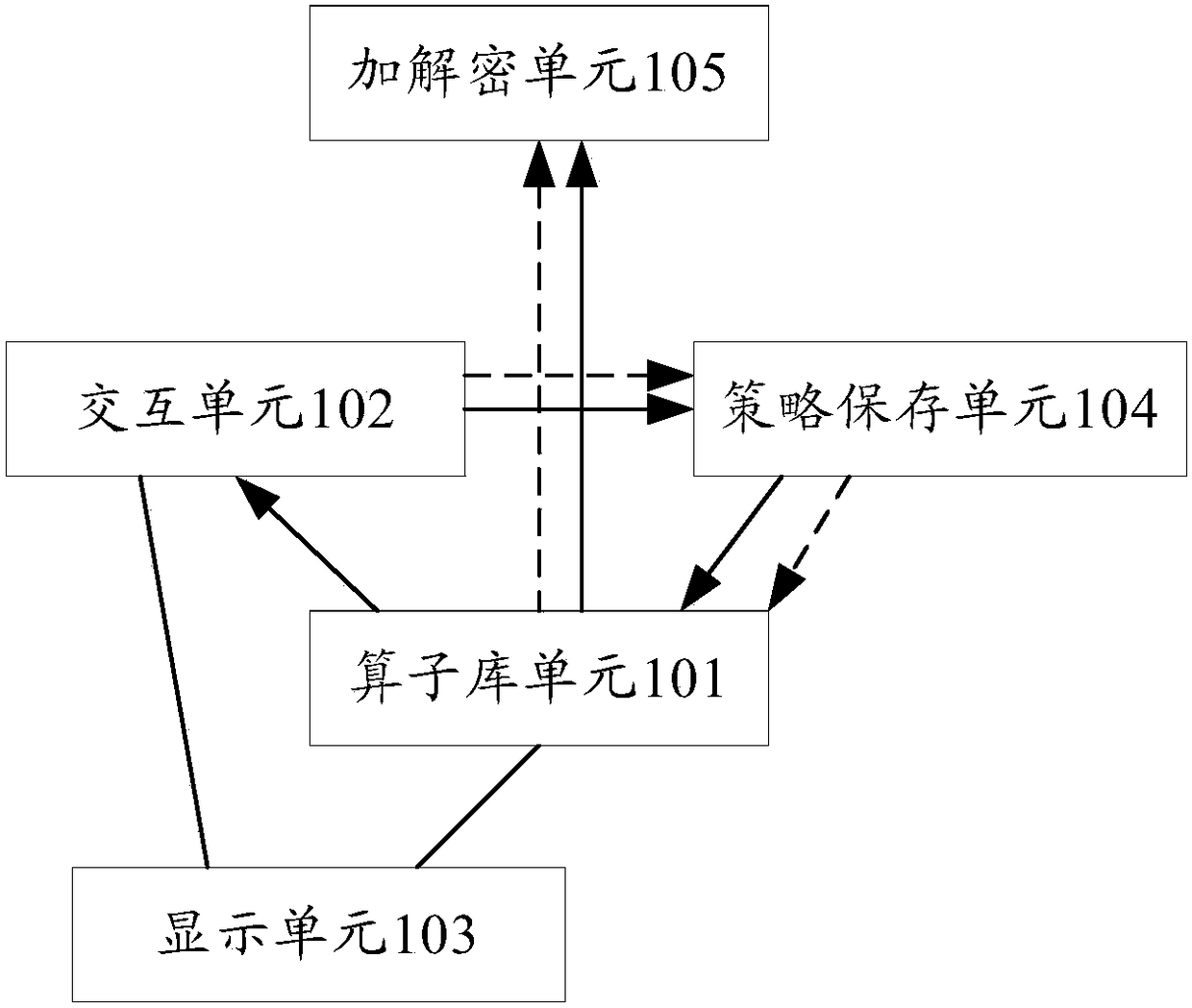
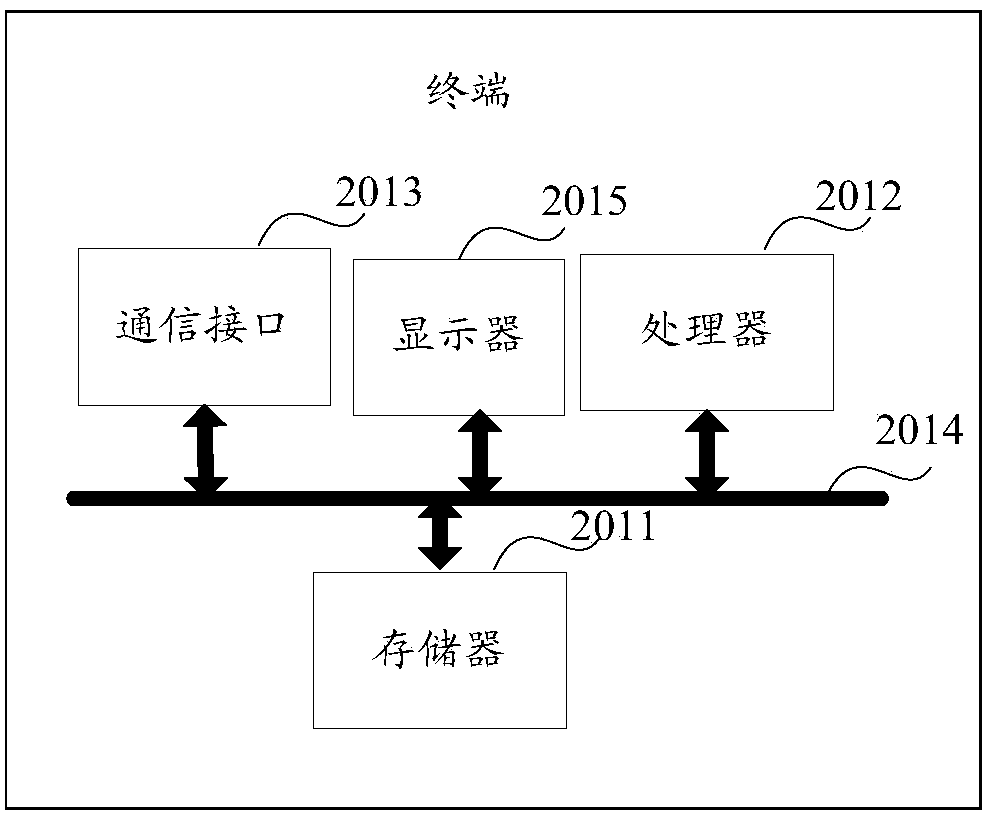
[0070] In the specific implementation process, the terminal in the embodiment of the present invention can be a mobile phone, a mobile computer, a tablet computer, a personal digital assistant (Personal Digital Assistant, PDA), a media player, a smart TV, a smart wearable device (such as a smart watch, Smart glasses and smart bracelets, etc.), electronic readers, handheld game consoles, vehicle-mounted electronic devices or cloud servers, etc., the terminal has the function of encrypting or decrypting files.
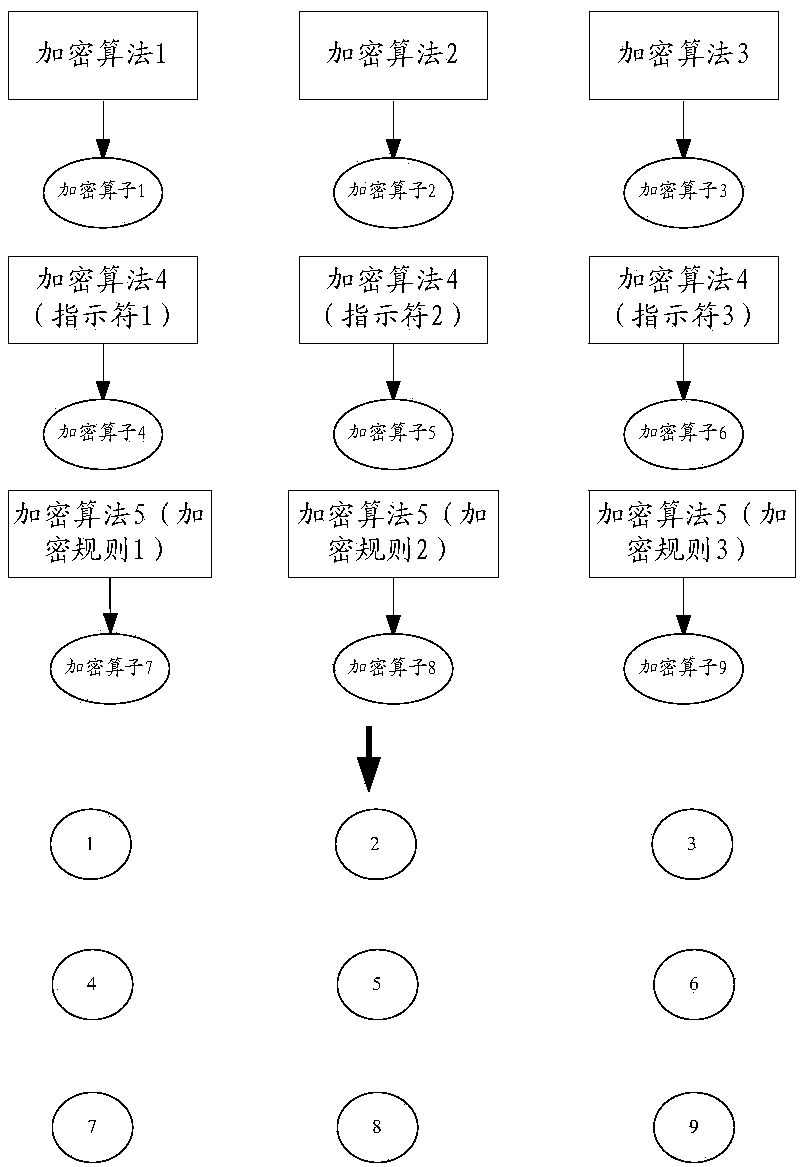
[0071] In the traditional cloud server storage technology, aft...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com