Symmetric searchable encryption method, device, equipment and medium
An encryption method and symmetric technology, applied in the field of data search, can solve the problems of not being able to verify the latest results of the search results, not being able to realize the complete verifiability of forward-safe search results at the same time, and reducing the security of searching data stored in the cloud.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
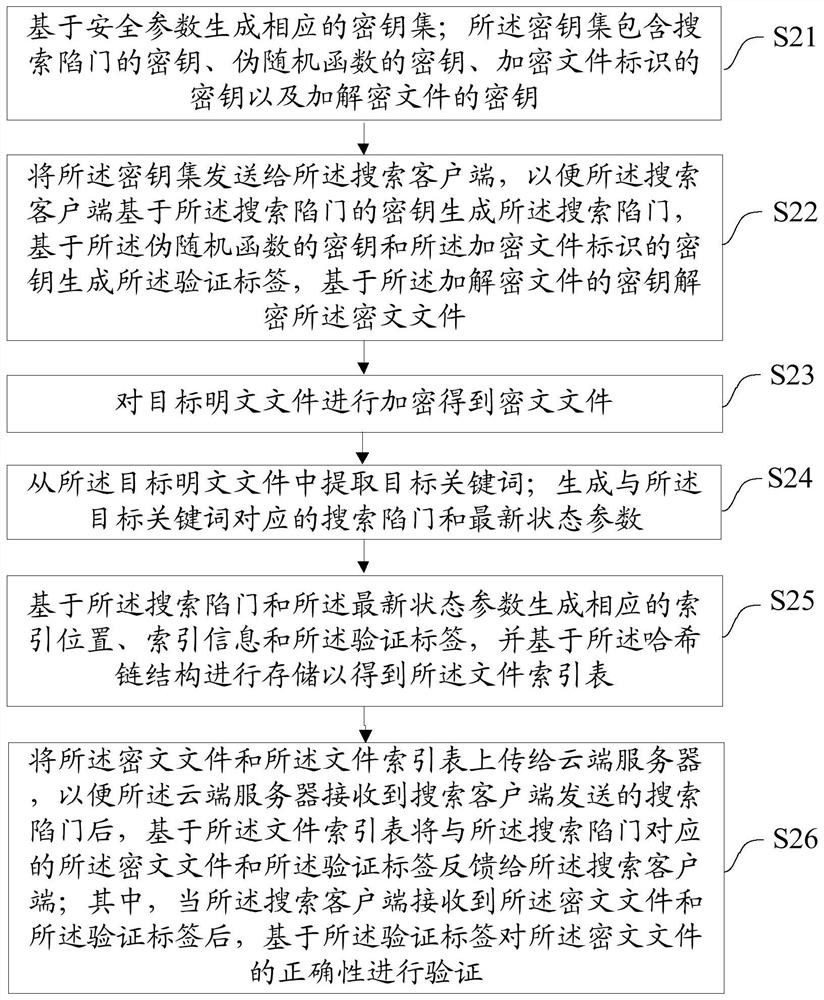
[0044] In the prior art, the complete verification of the search results through the MAC verification mechanism cannot verify whether the search results are the latest results. In addition, the verification of the search results based on the construction of verification evidence based on multiple hash functions cannot verify the correctness of the returned files. Moreover, forward security and complete verifiability of search results cannot be achieved simultaneously in the prior art. In order to overcome the above problems, this application proposes a fully verifiable forward-secure symmetric searchable encryption method, which can realize complete verification of search results on the basis of ensuring forward security.
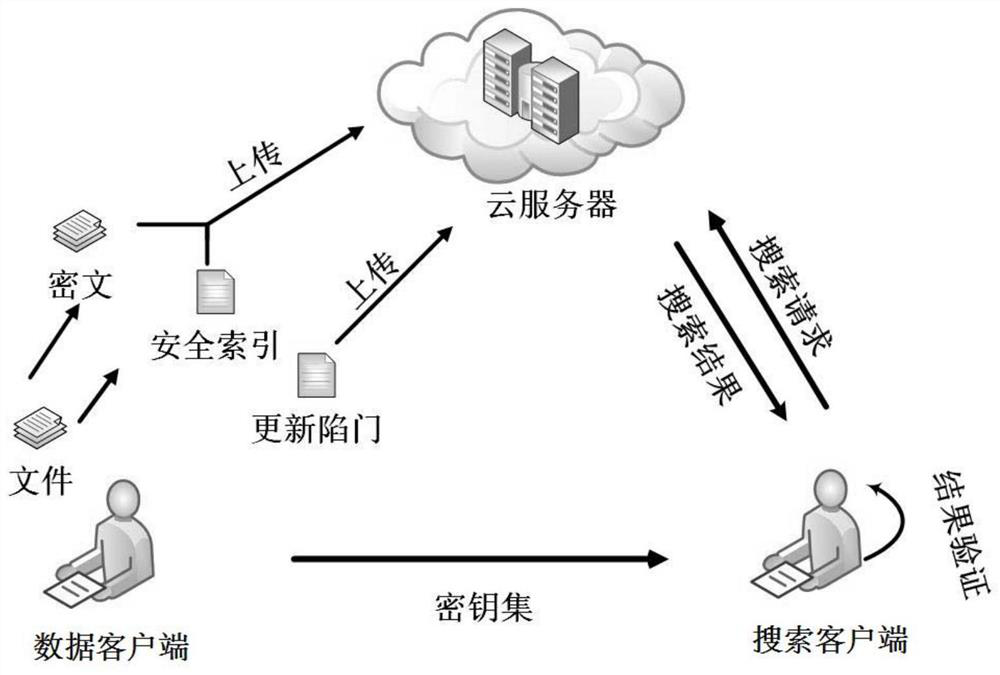
[0045]The embodiment of this application discloses a symmetric searchable encryption method, which is applied to the data client, see figure 1 As shown, the method may include the following steps:
[0046] Step S11: Encrypt the target plaintext file to obt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com