An ultra-lightweight RFID two-way authentication method
A two-way authentication and ultra-lightweight technology, applied in the field of ultra-lightweight RFID two-way authentication, can solve problems such as asynchronous attacks and full-leakage attacks, potential safety hazards, asynchronous attacks, etc., and achieve resistance to asynchronous attacks and Replay attack, ensure forward security, and ensure the effect of difference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
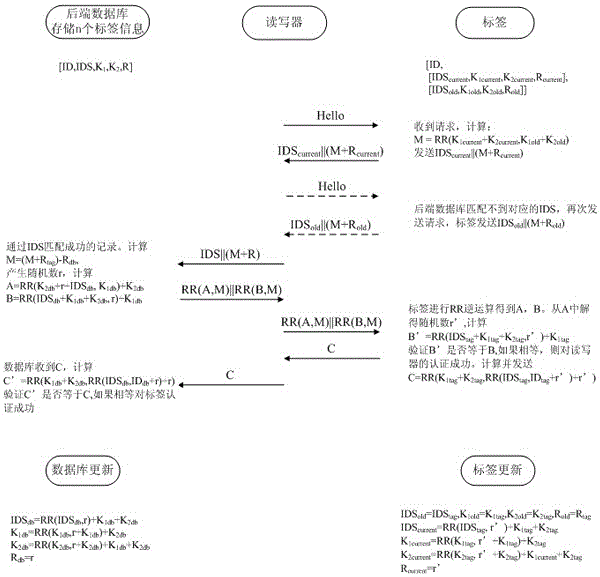
[0051] Below in conjunction with accompanying drawing, the technical scheme of invention is described in detail:
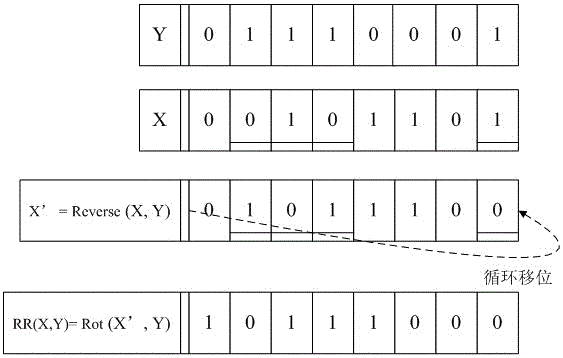
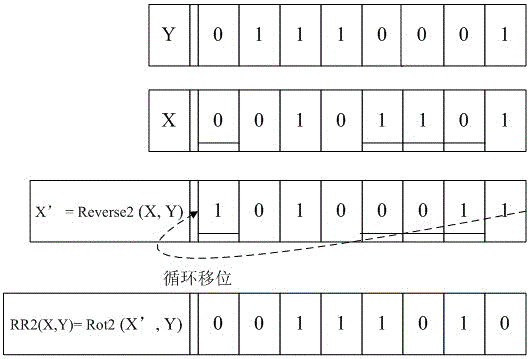
[0052] The bitwise operation RR(X, Y) involved in the present invention is aimed at hiding secret data, and after negating X, the displacement operation is performed on the negated X according to the displacement number determined by Y. Two examples of bitwise operation RR(X, Y) that can be used in the present invention are given below.
[0053] (1) Bitwise operation RR(X, Y): record the bit number n of each bit of Y with a value of 1 1 ,n 2 ,...,n k , compare the operand X with the recorded bit number n 1 ,n 2 ,...,n k Corresponding bit ,..., To invert the value, remember that the operand X after bitwise inversion is X’:
[0054] X'=Reverse(X,Y);
[0055] Then use the value of the operand Y modulo its data length as the number of left shift digits, and perform a left shift operation on X':
[0056] RR(X,Y)=Rot(X',Y).
[0057] Take two 8bit data X=001...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com