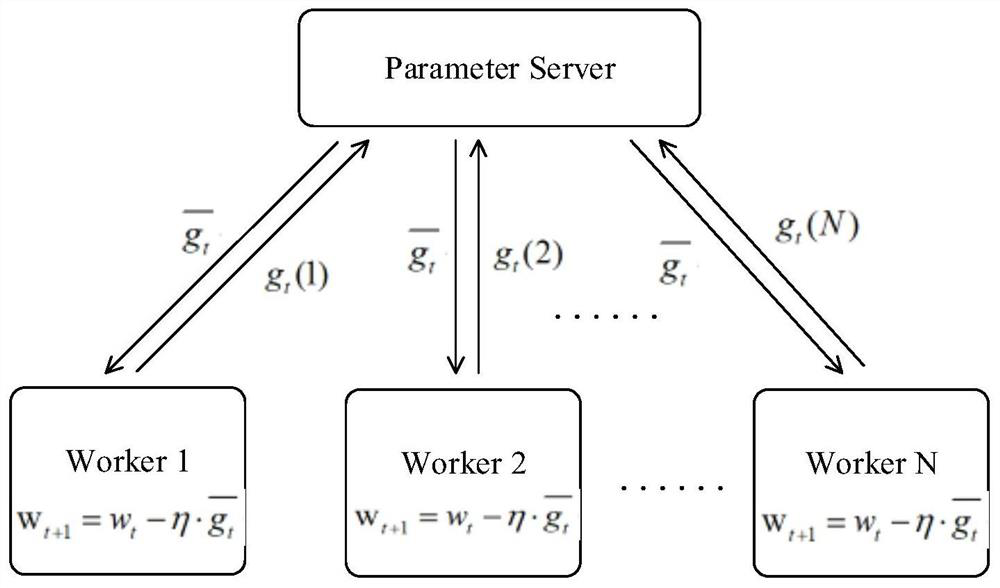
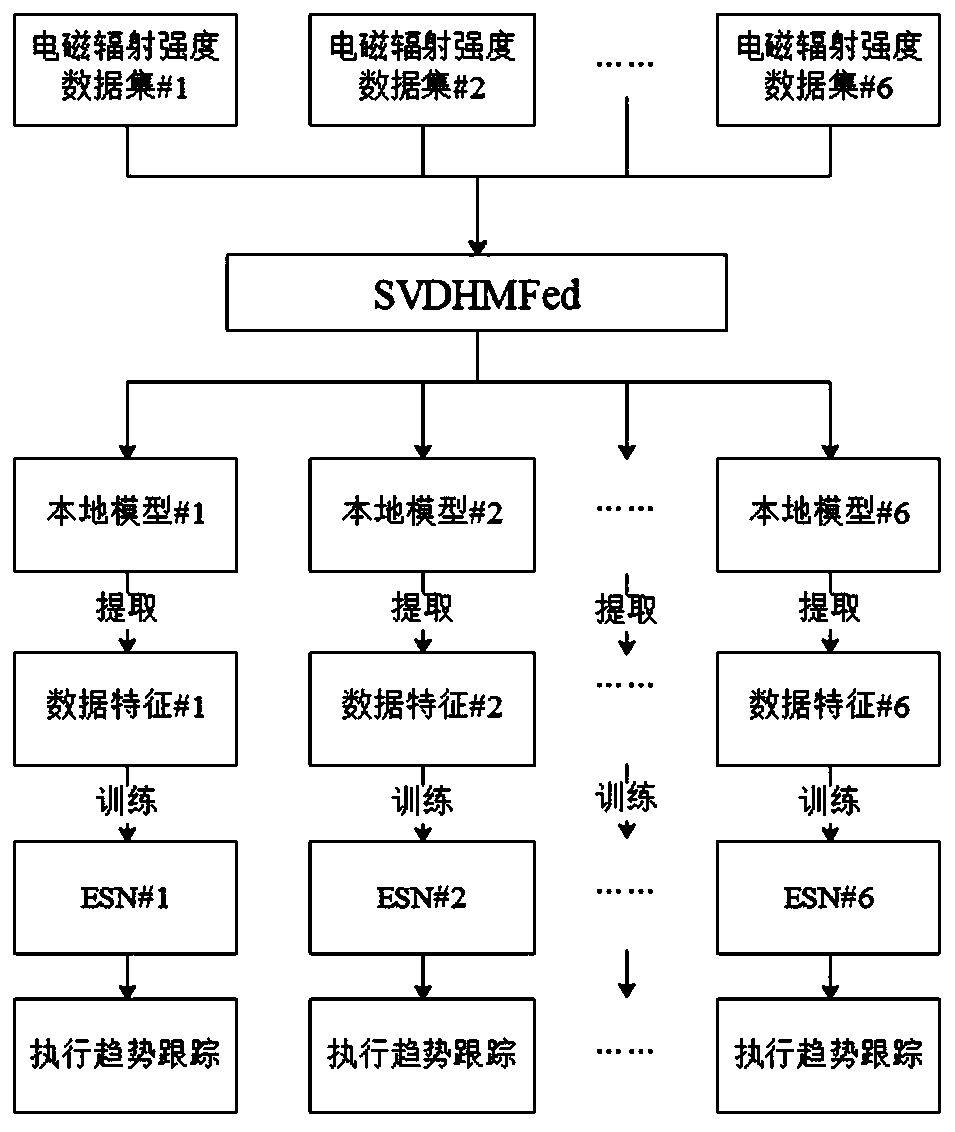
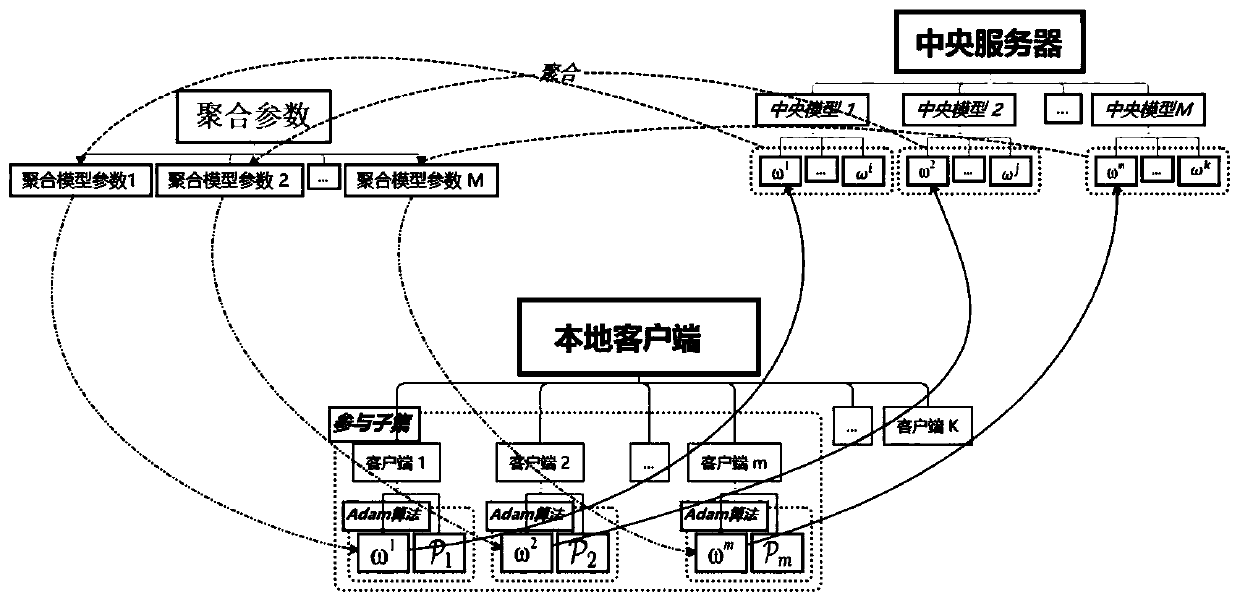
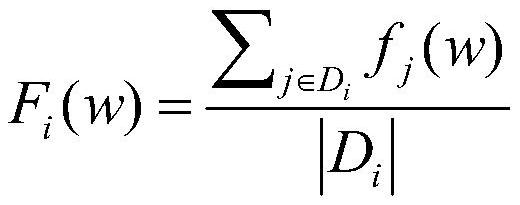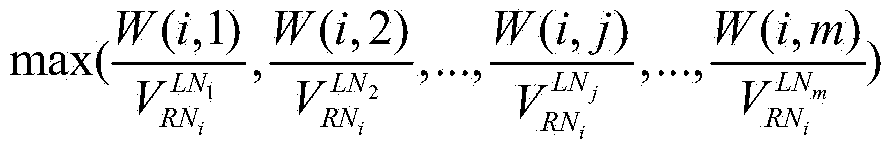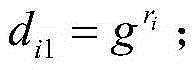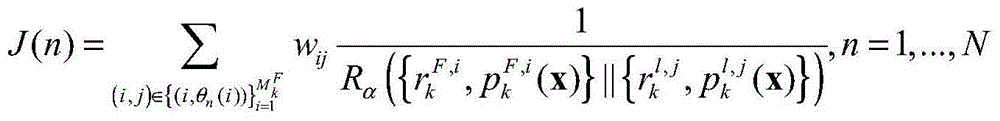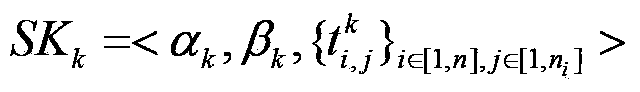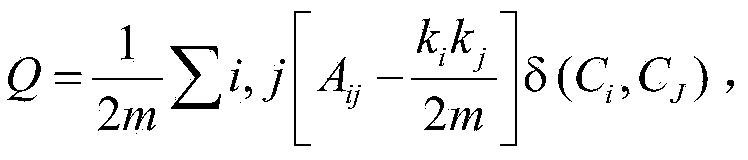Patents
Literature
218results about How to "Reduce communication cost" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
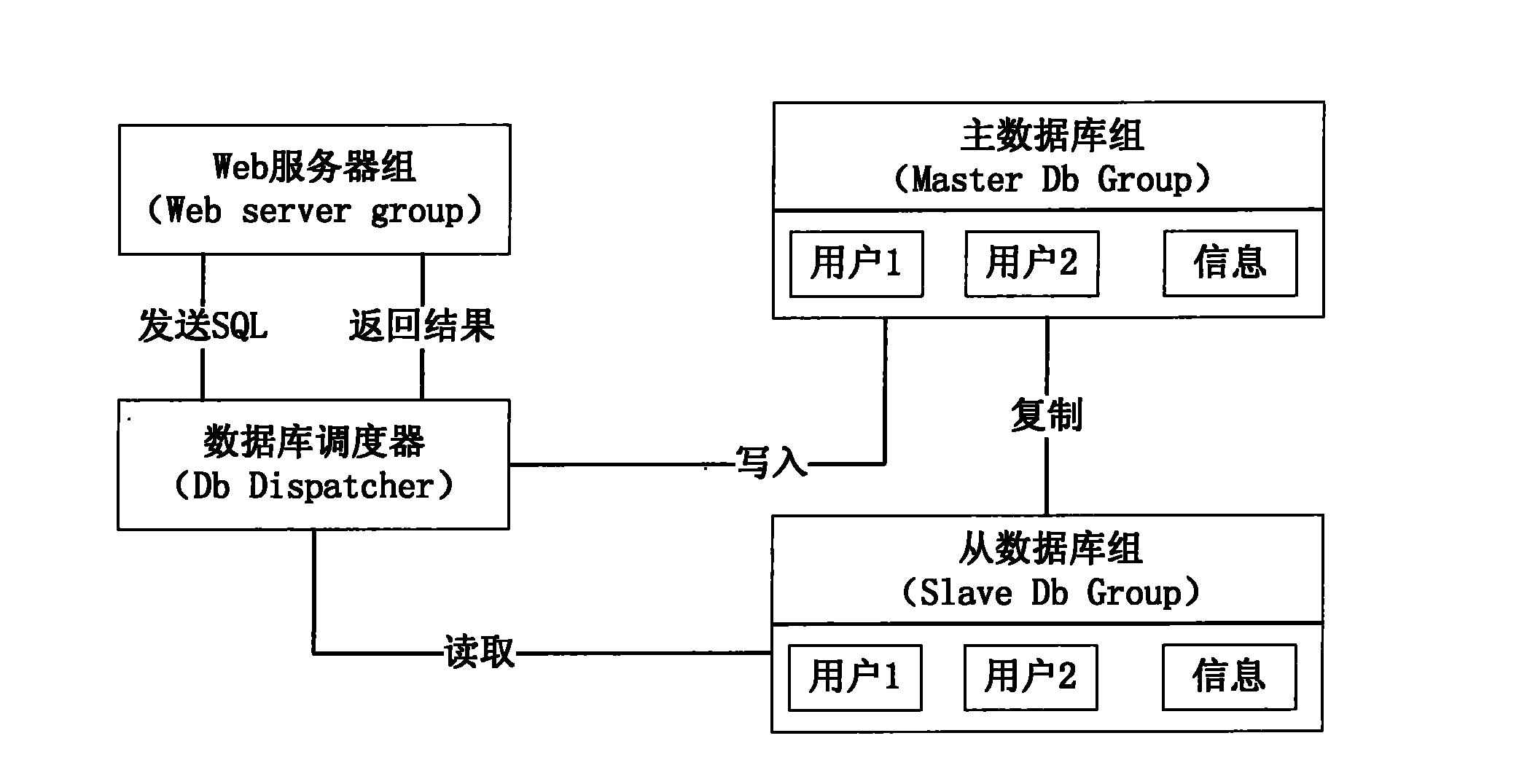
Distributed-type database access method and system
InactiveCN102033912AAvoid feesAvoid single database failure causing complete paralysisSpecial data processing applicationsLimited resourcesTraffic capacity
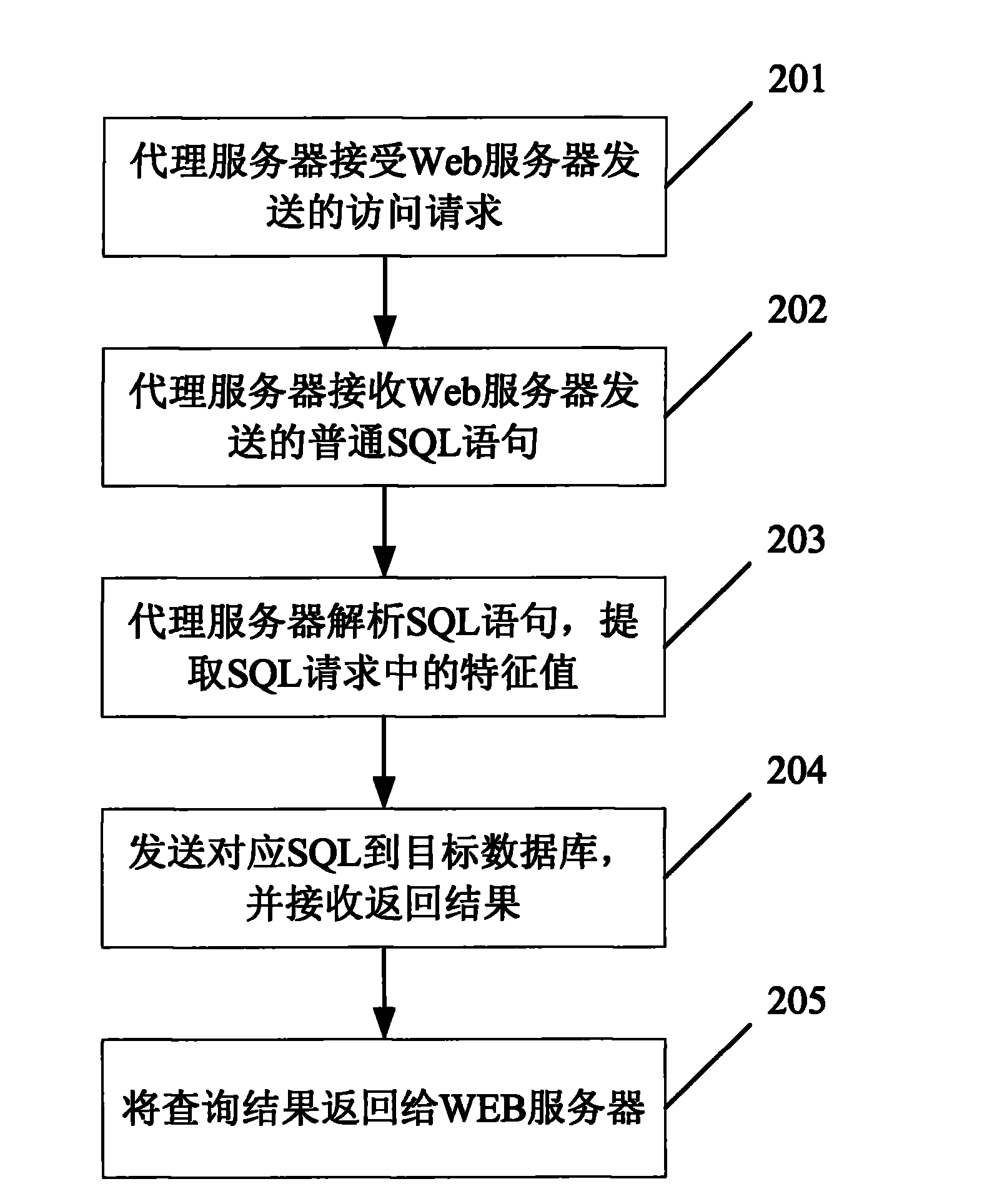
The invention relates to a distributed-type database access method and system. The distributed-type database access method comprises: 1. a Web server sends a database access request to a proxy server; 2. the proxy server analyzes the database access request according to a preset analysis rule, and sends the analyzed database access request to a corresponding target database; and 3. the proxy serve sends a result returned by the target database to the Web server. The invention avoids risk of high cost brought by the centralized management of the database and avoids the risks that the whole system fails because of the fault of the single database, the system scale has small possibility of expanding and is limited and the like. The invention effectively realizes the reasonable distribution of physical resources, lowers communication cost, has strong expansibility, can dynamically distribute data flow, and can separate reading from writing; and under the condition of limited resource, performance is maximized.
Owner:BEIJING BEWINNER DIANYI INFORMATION TECH CO LTD
Hierarchical federated learning method and device based on asynchronous communication, terminal equipment and storage medium
ActiveCN112532451AResolving heterogeneityImprove training efficiencyEnsemble learningData switching networksAsynchronous communicationEdge server
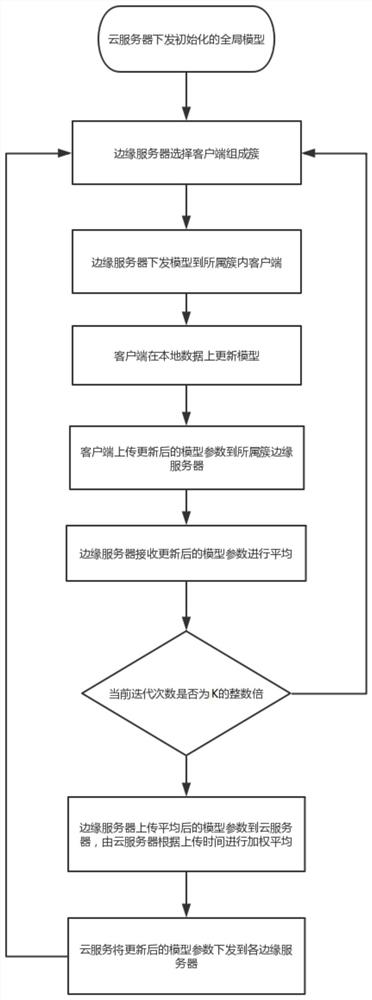
The invention provides a hierarchical federated learning method and device based on asynchronous communication, terminal equipment and a storage medium, and relates to the technical field of wirelesscommunication networks. The method comprises the following steps: an edge server issues a global model to an intra-cluster client to which the global model belongs; the client updates the model by using the local data and uploads the model to each belonging cluster edge server; the edge server determines to update the clients in the cluster according to the client update uploading time; the received model parameters are averaged by the edge server, and it is selected to asynchronously upload the model parameters to the central server or directly issue the model parameters to the client according to the updating times of the current client; and the central server performs weighted averaging on the parameters uploaded by the edge server, and issues the parameters to the client for training until the local model converges or reaches an expected standard. According to the method, the federated learning task can be efficiently executed, the communication cost required by the parameters of the federated learning model is reduced, the edge server butted with the client is dynamically selected, and the overall training efficiency of the federated learning is improved.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY
Outsourcing encrypted data-orientated verifiable intersection operation method and system
ActiveCN105812141AGuaranteed privacyReduce the number of interactionsUser identity/authority verificationPlaintextThird party
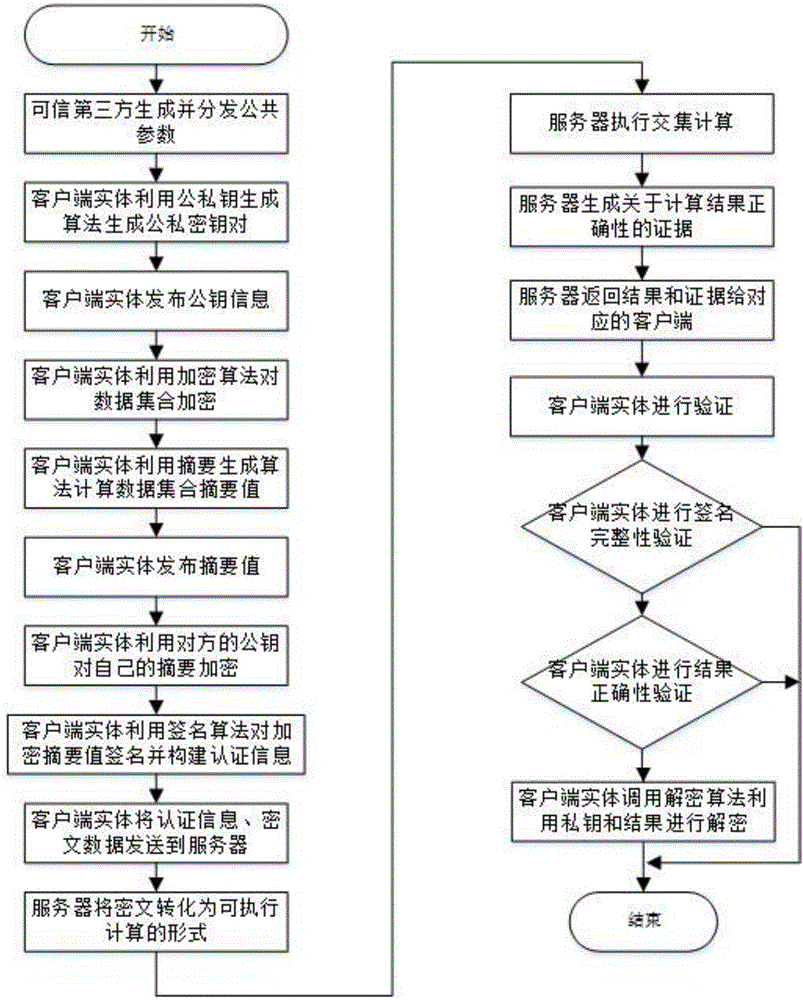
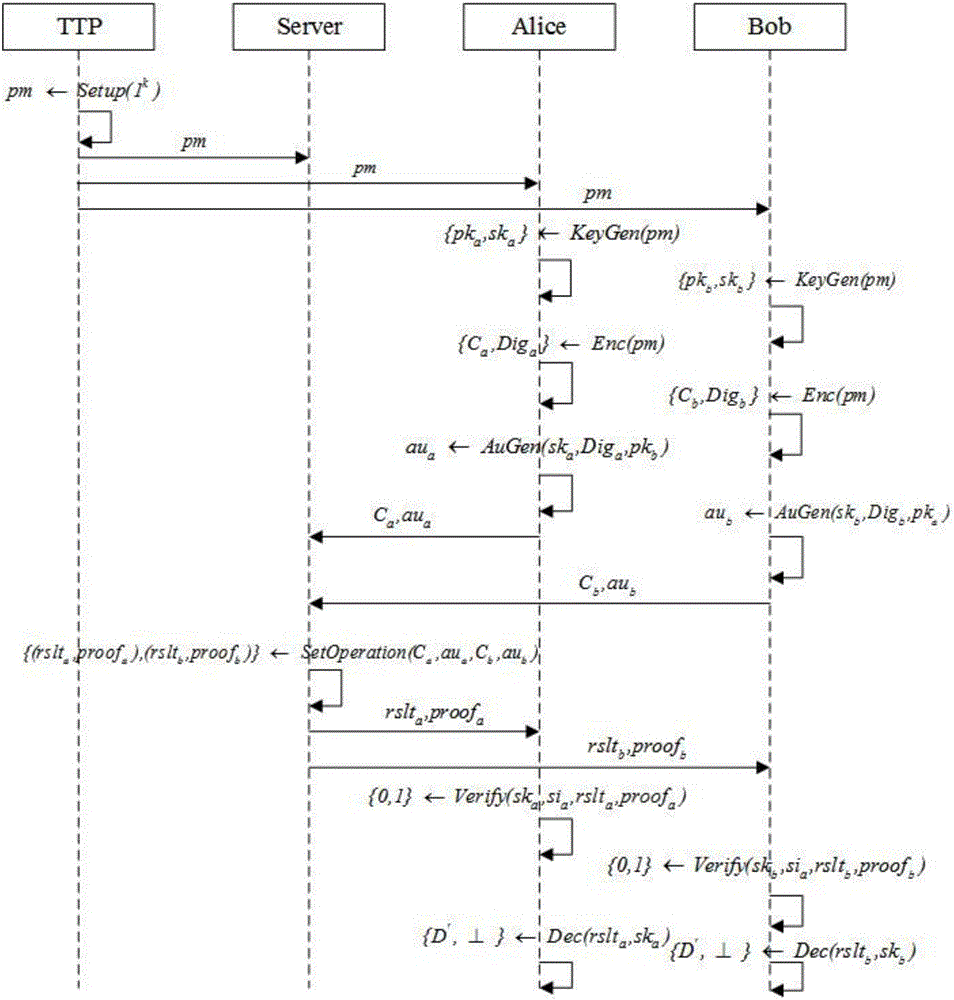
The invention relates to an outsourcing encrypted data-orientated verifiable intersection operation method and system and belongs to the verifiable outsourcing computation field. The method is carried out among a third-party trusted entity, at least two client entities and an outsourcing server side; the client entities are holders of data sets and requesters of data set intersection operation; the third-party entity is mainly responsible for the initialization and distribution of common parameters; the two client entities are mainly responsible for generating keys, encrypting data sets, calculating authentication information, verifying results and proofs returned by the outsourcing server side and decrypting an ciphertext data set returned by the outsourcing server side; the outsourcing server side is mainly responsible for performing data set intersection operation; and a plaintext data set is not required to be obtained through decryption when the outsourcing server side performs intersection operation, and the outsourcing server performs operation on a ciphertext, and therefore, the privacy of user data can be ensured. The method and system have the advantages of low frequency of interaction among the entities, low communication cost and efficient correctness verification of operation results.
Owner:NORTHEASTERN UNIV
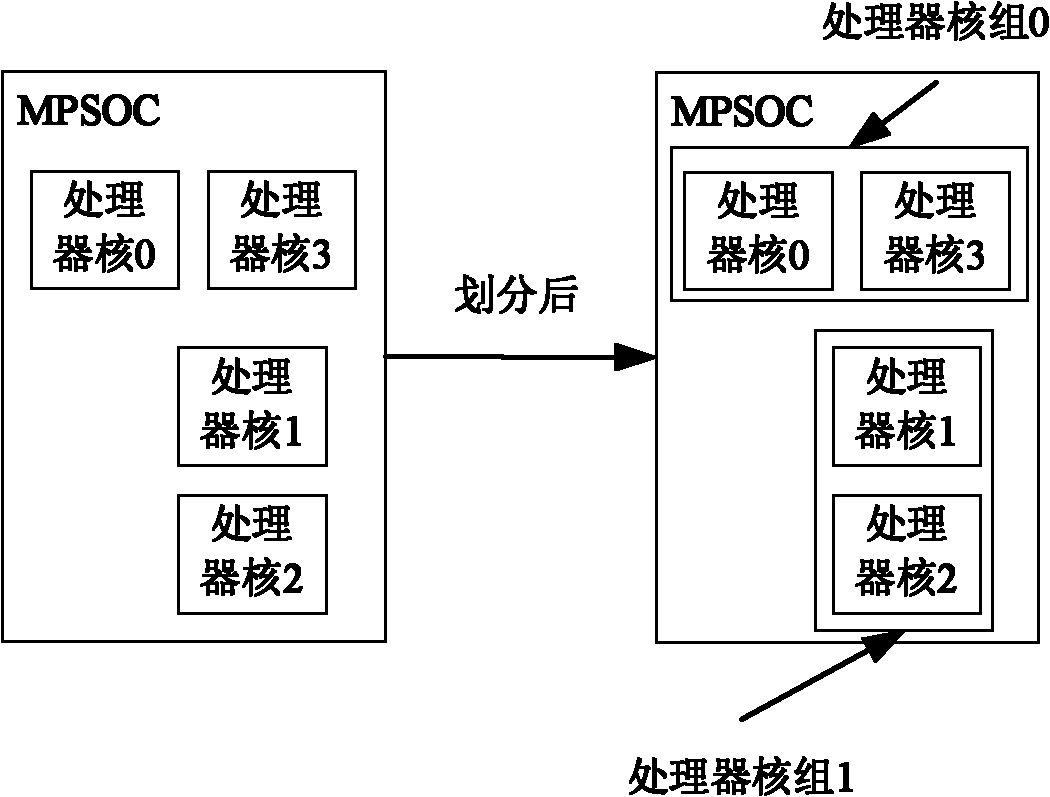
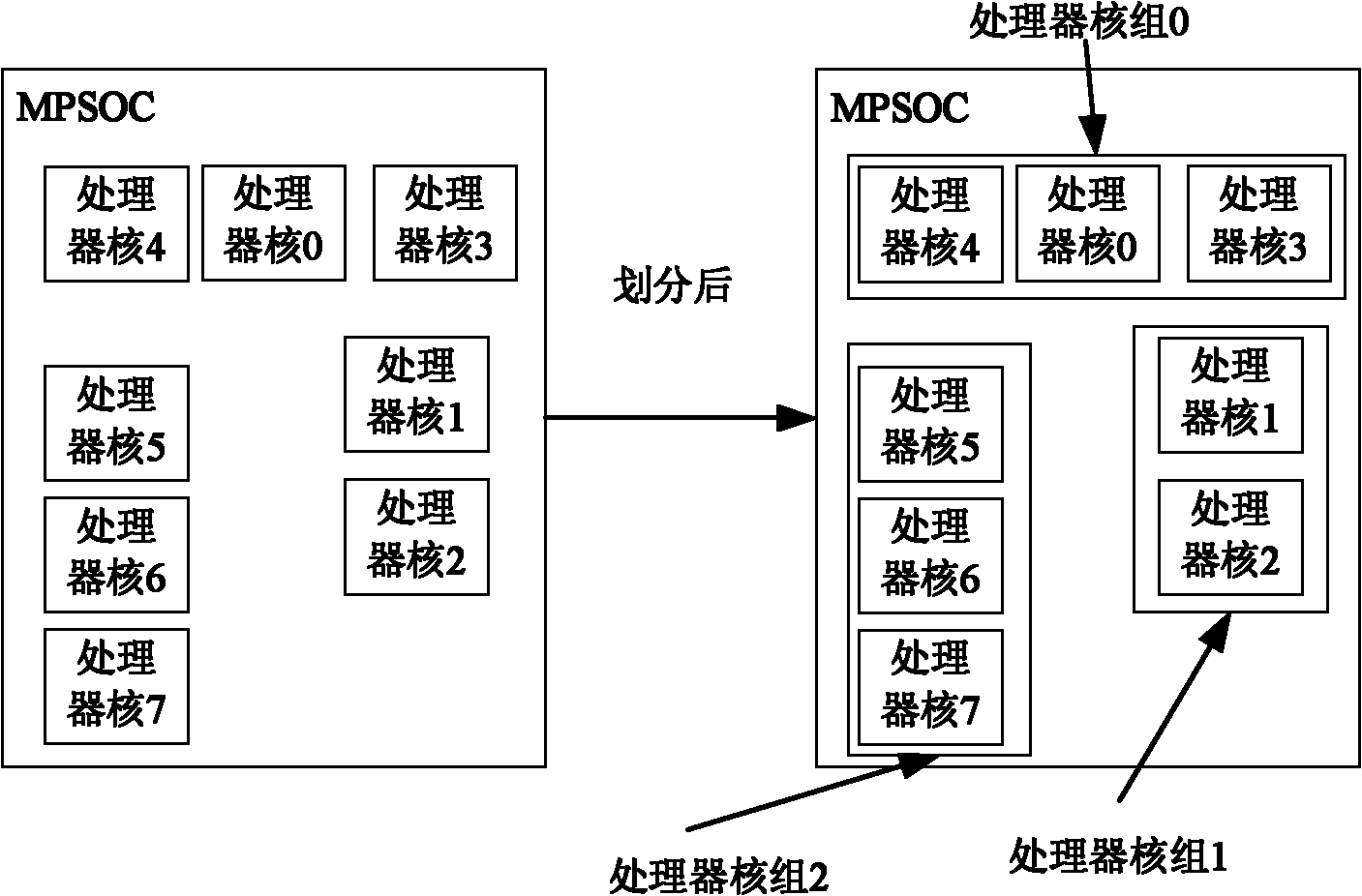
MPSoC (multi-processor system-on-chip)-oriented multithread scheduling method
InactiveCN102193779AImprove execution efficiencyReduce workloadMultiprogramming arrangementsConcurrent instruction executionMulti processorThread scheduling
The invention relates to an MPSoC (multi-processor system-on-chip)-oriented multithread scheduling method, which has the technical scheme comprising the following steps of: dividing a plurality of processor cores on the MPSoC into processor core sets according to a physical position relationship, and dividing adjacent processor cores into the same processor core set; dividing the threads in the same process into a same thread set; scheduling the thread set according to a configuration table of the processor core set; in the same processor core set, scheduling the threads by utilizing a time-share scheduling or rotating scheduling algorithm; and finally, optimizing the thread scheduling, namely moving the threads in the same process from the busy processor core set to the idle processor core set, wherein the number Mi of the moved threads is equal to the number Cs of the processor cores in the idle processor core set. According to the method, a plurality of threads are divided into different thread sets and the thread sets are scheduled on the core sets, thereby lowering the communication cost among the threads and increasing the scheduling efficiency.
Owner:WUHAN UNIV OF SCI & TECH
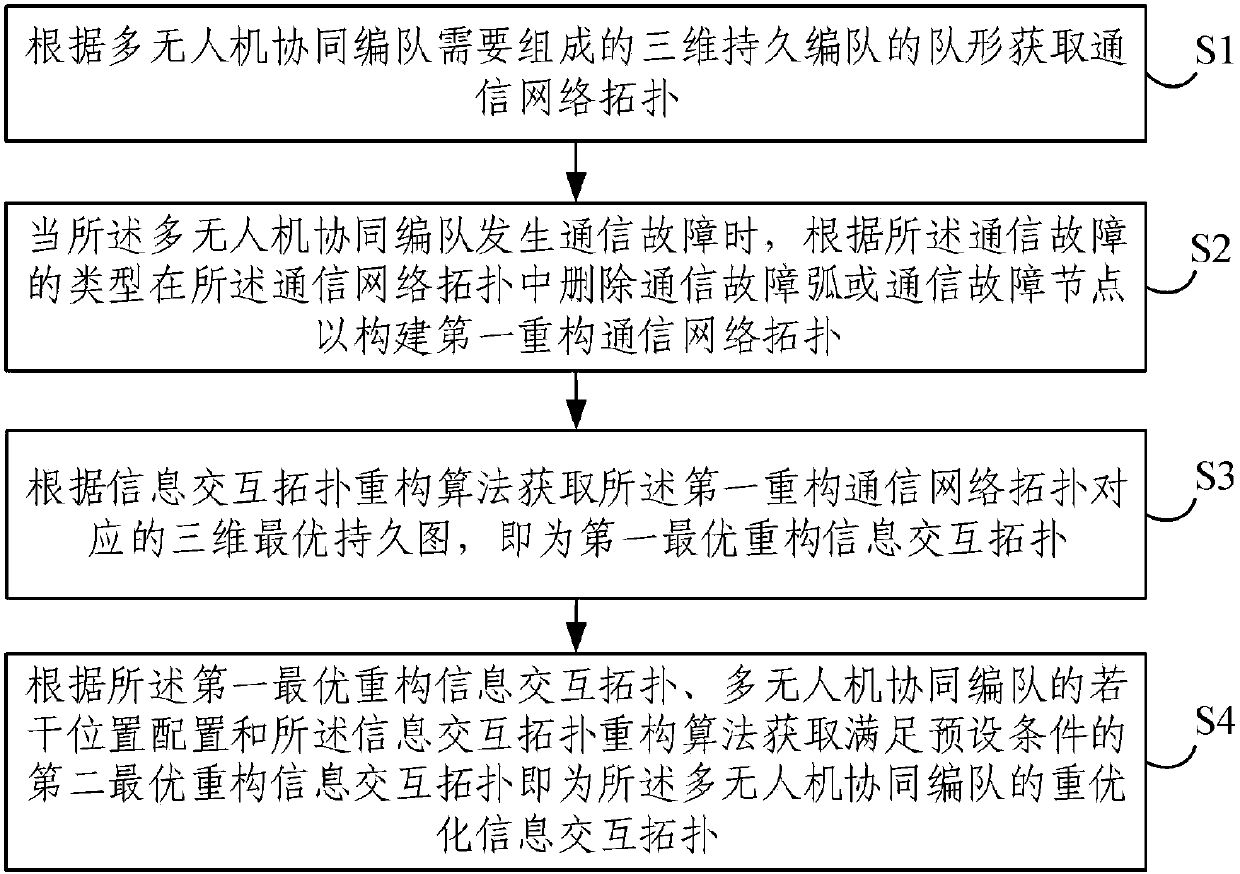
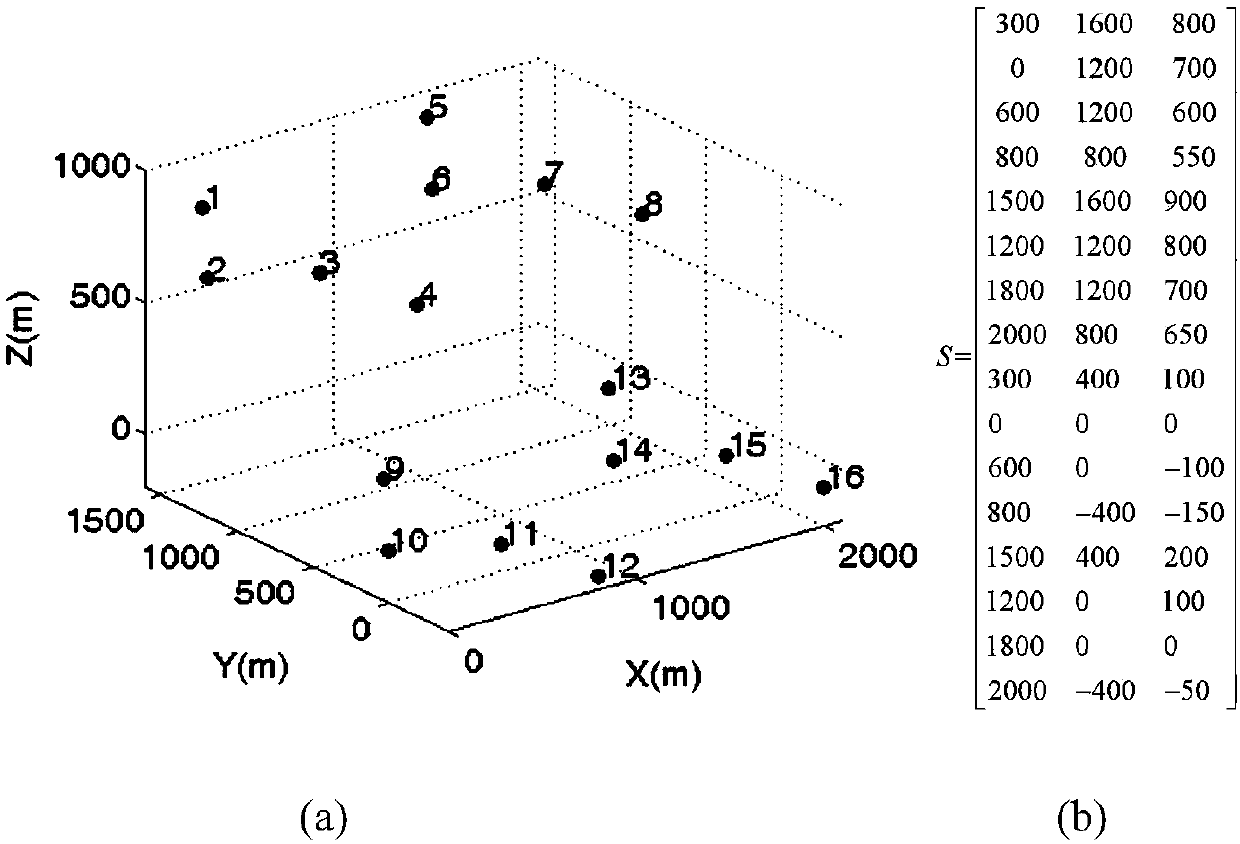
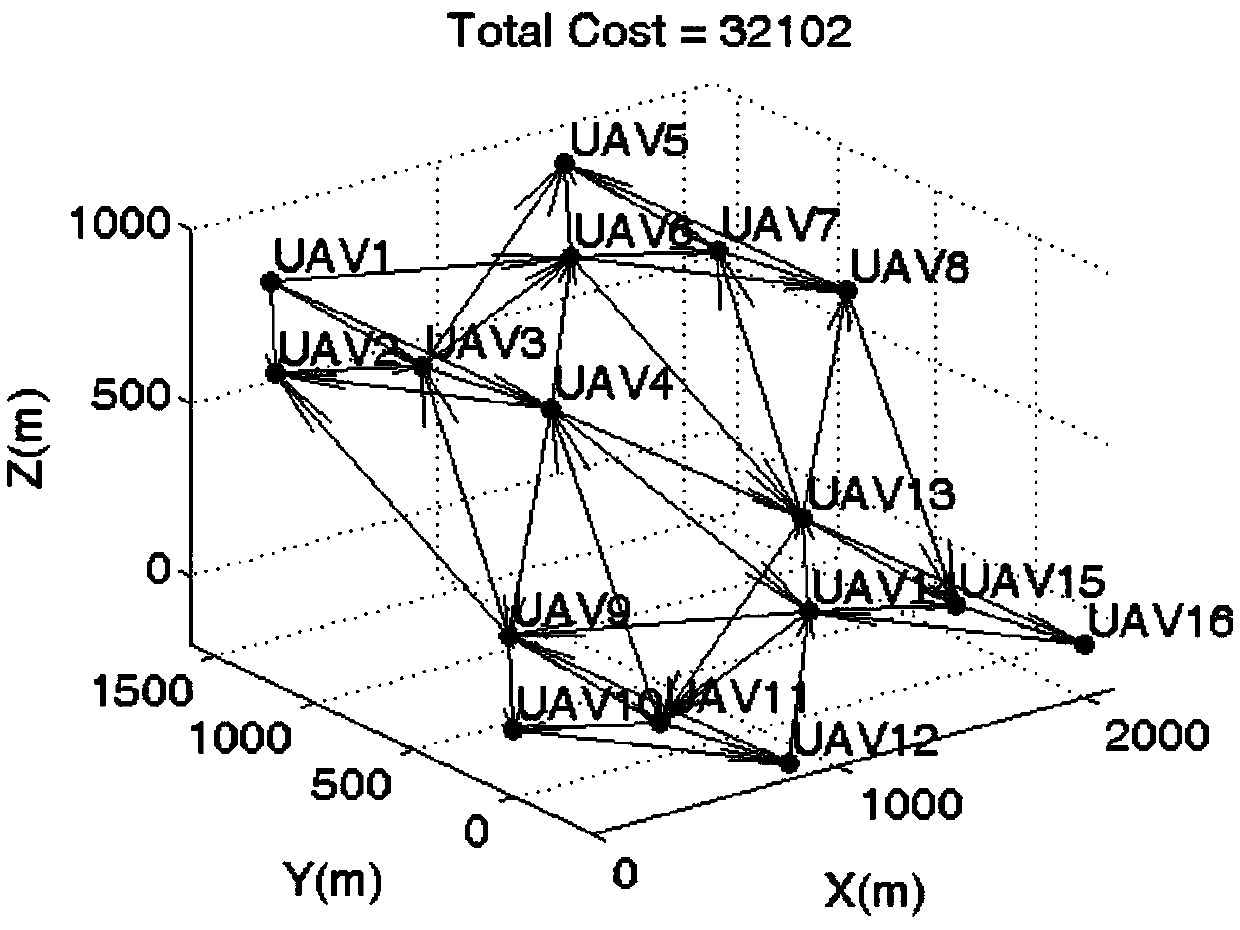
Heuristic optimization method and device for information exchange topology in multi-unmanned-aerial-vehicle coordinated formation
InactiveCN107797564AReduce communication costPosition/course control in three dimensionsReconstruction algorithmNetwork topology
The invention provides a heuristic optimization method and device for information exchange topology in a multi-unmanned-aerial-vehicle coordinated formation. The method comprises: S1, a communicationnetwork topology is obtained according to a three-dimensional persistent formation formed by the multi-unmanned-aerial-vehicle coordinated formation; S2, when a communication failure occurs in the multi-unmanned-aerial-vehicle coordinated formation, a communication failure arc or communication failure node is deleted in the communication network topology based on the type of the communication failure to construct a first reconfigured communication network topology; S3, according to an information exchange topology reconstruction algorithm, a three-dimensional optimal enduring map correspondingto the first reconfigured communication network topology being a first optimal reconstruction information exchange topology is obtained; and S4, according to the first optimal reconstruction information exchange topology, configuration of a plurality of position in the multi-unmanned-aerial-vehicle coordinated formation, and the information exchange topology reconstruction algorithm, a second optimal reconstruction information exchange topology meeting a preset condition is obtained, wherein the second optimal reconstruction information exchange topology is the re-optimization information exchange topology of the multi-unmanned-aerial-vehicle coordinated formation and the preset condition is as follows: n is larger than |V|*(|V|-1) / 2. According to the invention, an unmanned-aerial-vehiclecollision accident in the large-scale multi-unmanned-aerial-vehicle coordinated formation in a communication failure occurrence state is avoided and the formation is recovered; and the communicationcost of the formation is kept to be low.
Owner:HEFEI UNIV OF TECH
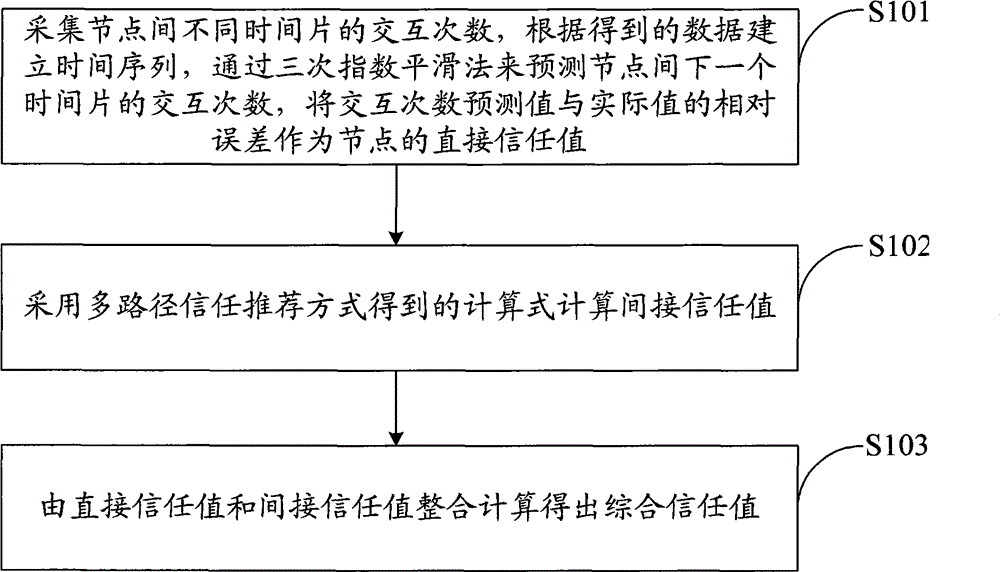
Method for calculating trust values of wireless Mesh network nodes
InactiveCN104038928AReduce computational complexityReduce communication costTransmissionSecurity arrangementWireless mesh networkComputation complexity
The invention discloses a method for calculating the trust values of wireless Mesh network nodes. The method comprises direct trust value calculation, indirect trust value calculation and comprehensive trust value calculation, wherein the direct trust value calculation is carried out for acquiring the interaction times of different time slices among the nodes and establishing a time sequence according to the obtained data at first, and then predicating the interaction times of the next time slice among the nodes by virtue of three times of an exponential smoothing method, and taking the relative errors of the interaction times predicated values and the actual values as the direct trust values of the nodes; the calculation formula of indirect trust values is obtained in a multi-path trust recommendation mode; comprehensive trust values are obtained by virtue of integrated computation for the direct trust values and the indirect trust values. The invention provides a method for calculating the trust values of the nodes, according to the specific condition of a network, adaptive smoothing factor alpha, credibility threshold value Phi, the value of a direct trust value weight beta are selected, the time attenuation characteristic and objectivity of the trust values are guaranteed, the credibility of the nodes is objectively and accurately described, the computation complexity is low, and the method is suitable for a wireless Mesh network.
Owner:LANZHOU JIAOTONG UNIV
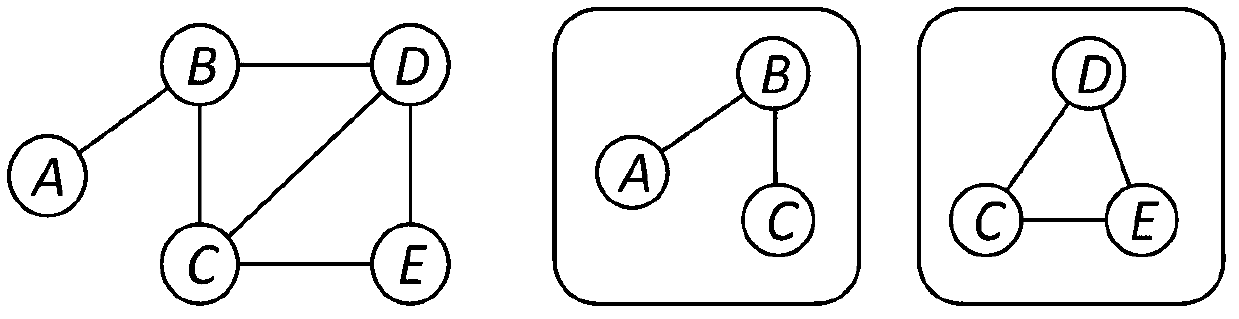
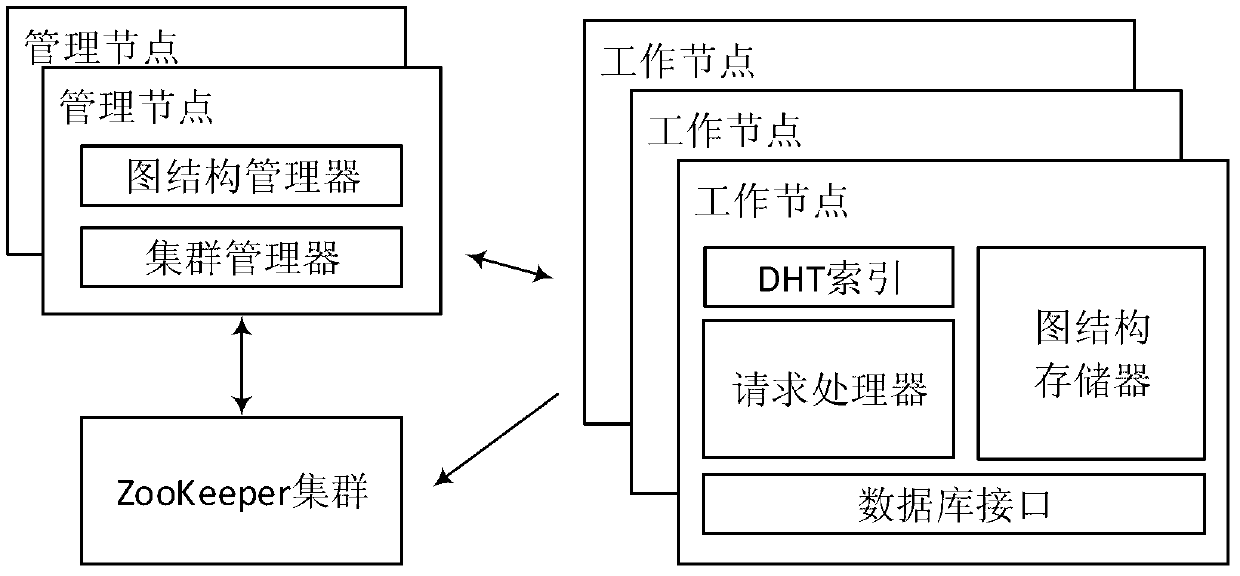
Data storage method and system suitable for social network graph
InactiveCN103345508AReduce RPC costReduce the number of cluster RPC requestsSpecial data processing applicationsDatabase interfaceSocial graph
The invention relates to a data storage method and system suitable for a social network graph. The method includes the steps that graph structure information of the social network graph is read in a side list or an adjacency list mode; a peak is separated into a plurality of sub peaks, and each sub peak has all the peak data and data on corresponding sides of the peak; with regard to sides, which are not distributed in partitions, in the graph, firstly the sides are distributed to one partition, and at the moment sides spanning the partitions are not generated; if the distribution is not succeed, one side spanning the partitions is generated. The system comprises a plurality of management nodes, a plurality of work nodes, and ZooKeeper clusters. Only one management node is in the working state at a same moment, and each work node comprises a PHT index, a graph structure storage, a request processor and a database interface. The data storage method and system suitable for the social network graph can be increased to reflect the change of a social network graph structure, reduces communication cost among servers, increases overall throughput of the servers, and improves user experience.
Owner:PEKING UNIV
Data distribution method based on access frequency variable-length logic section
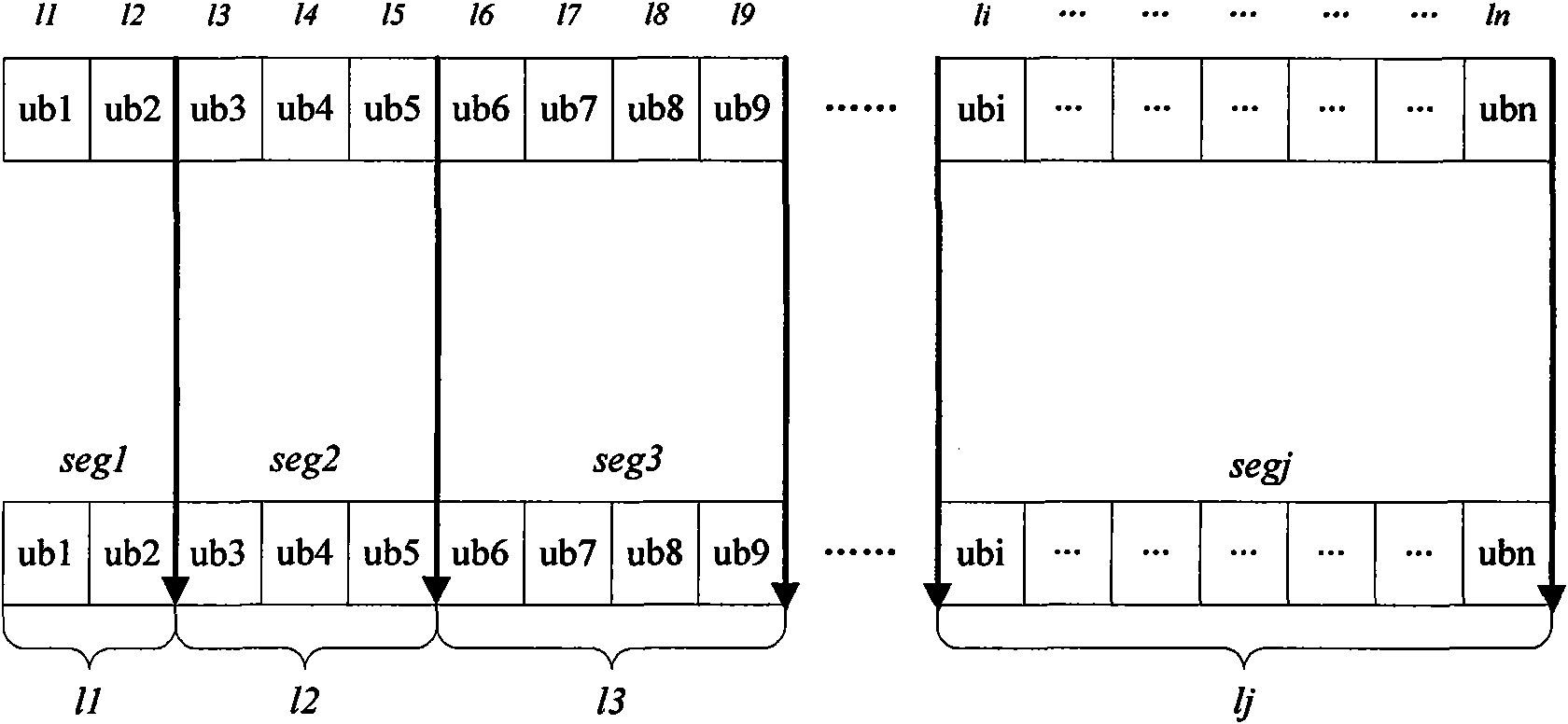
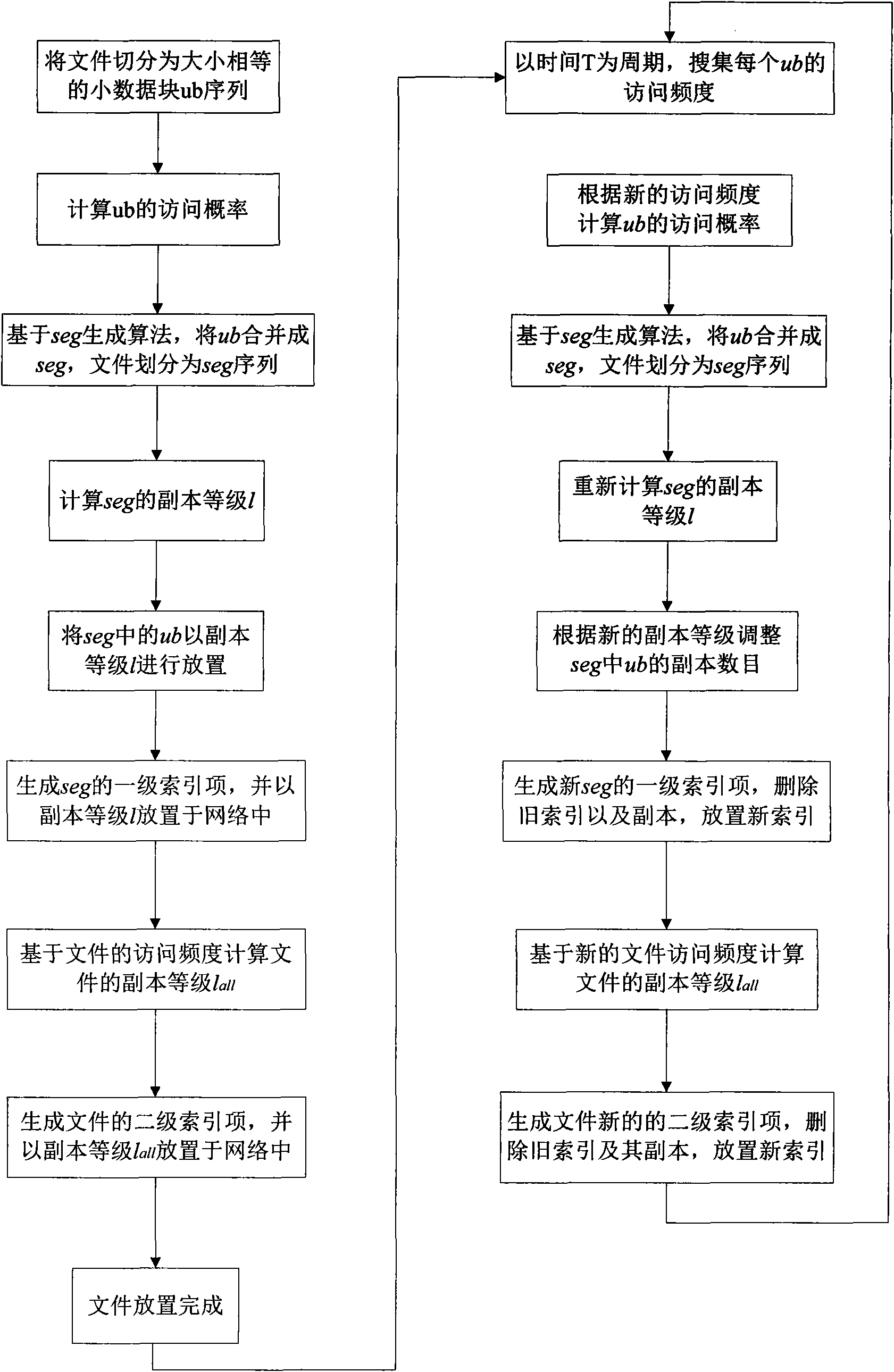
ActiveCN101645888AMeet needsImprove experienceError preventionData switching networksContent distributionDistribution method
The invention provides a data distribution method based on access frequency variable-length logic sections. The method comprises the following steps: segmenting a file into a fine particle size unit,generating variable-length logic sections for the file based on the access frequency difference at different time periods of the file of a user, respectively carrying out popularity-based multiple-copy placement according to different logic sections, generating multistage index entries for each logic section; and meanwhile adjusting the index entries of the updated file according to the copy levelof the file so that copy distribution of data in a CDN network better conforms to the practical access habit of the user. File slices in the fine particle size form more accurate statistics of the access habit of the user, which facilitates updating the access frequency characteristics of the user based on time change, and the slices are applied to copy generation for content distribution so thatdata distribution in the system is self-adaptively adjusted with time. In addition, application of the multistage index effectively reduces communication expenditure in the case of copy level adjustment of the data, and improves the system performance.
Owner:ZHENGZHOU SEANET TECH CO LTD
Method for acquiring road network matching track of mobile object
InactiveCN101866545AImprove the accuracy of statistical analysisImprove trajectory accuracyDetection of traffic movementRoad networksComputer science
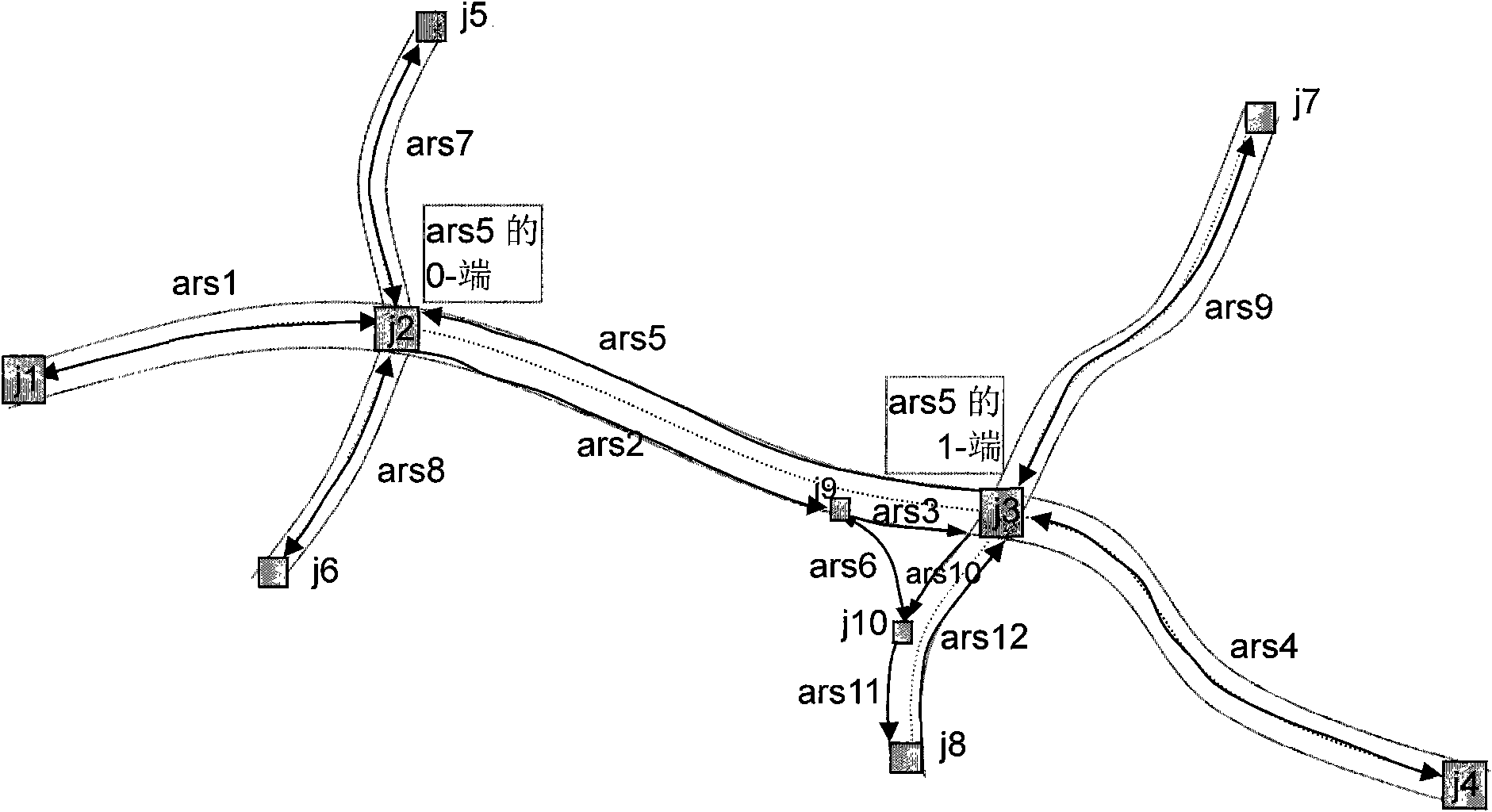
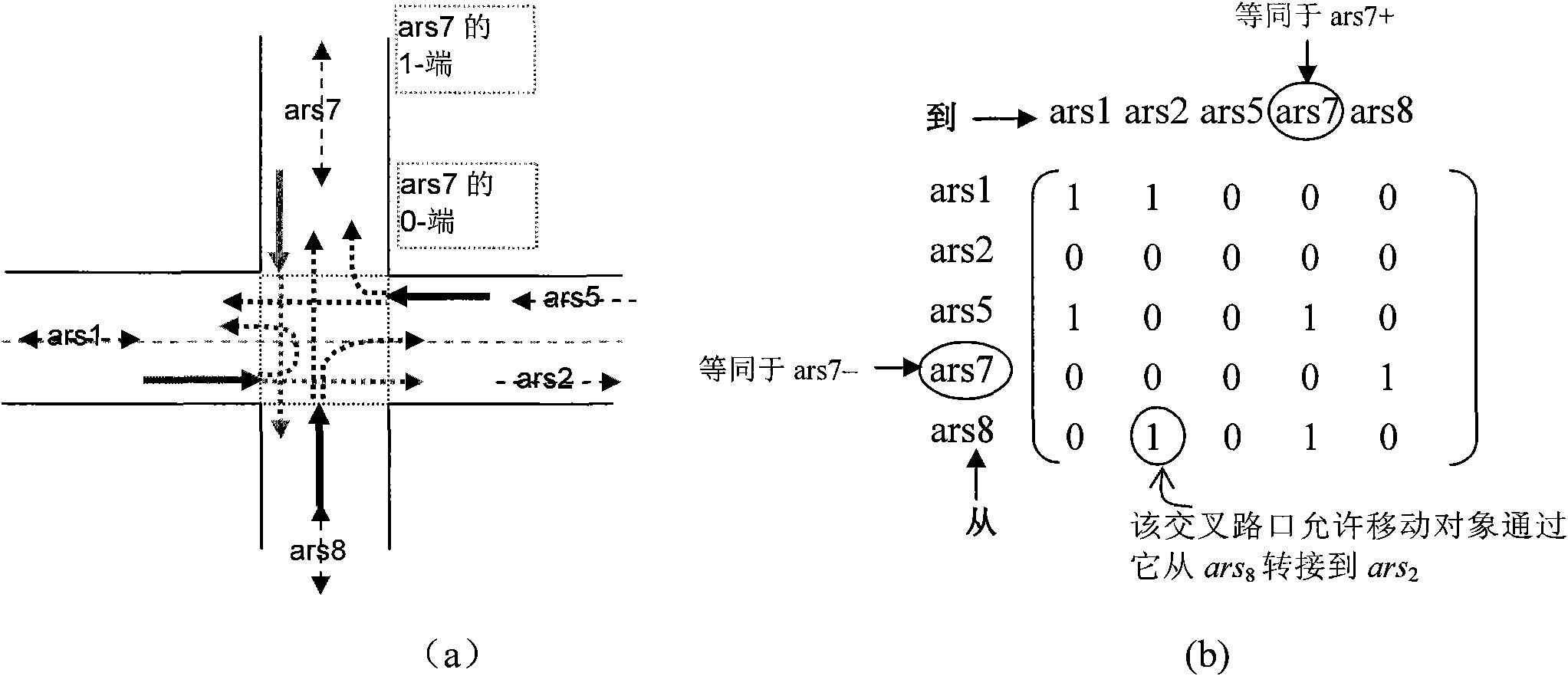
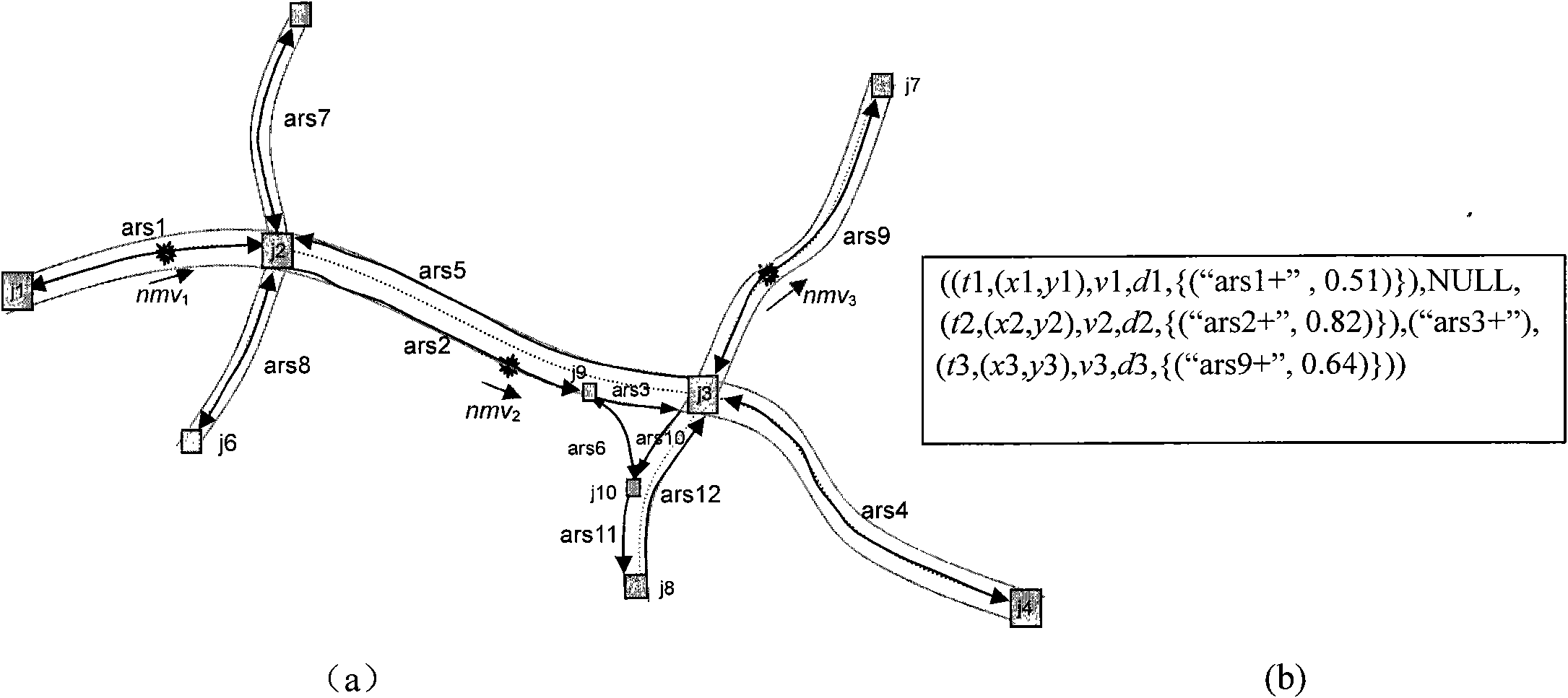
The invention discloses a method for acquiring a road network matching track of a mobile object, and belongs to the fields of spatiotemporal databases and intelligent transportation systems. The method comprises that: a) the mobile object acquires mv sequences and sends the mv sequences to a server in batches, wherein mv refers to a mobile vector; b) the server performs road network matching on each mv in the mv sequences to obtain nmv sequences, wherein the nmv refers to the road network matched mobile vector; and c) the server performs path matching on each nmv in the nmv sequences to obtain and store the road network matching track. The method can be used for the intelligent transportation systems.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Federation prediction method based on federation learning
ActiveCN112364943AImprove performanceIncrease aggregation weightForecastingCharacter and pattern recognitionDifferential privacyNetwork model
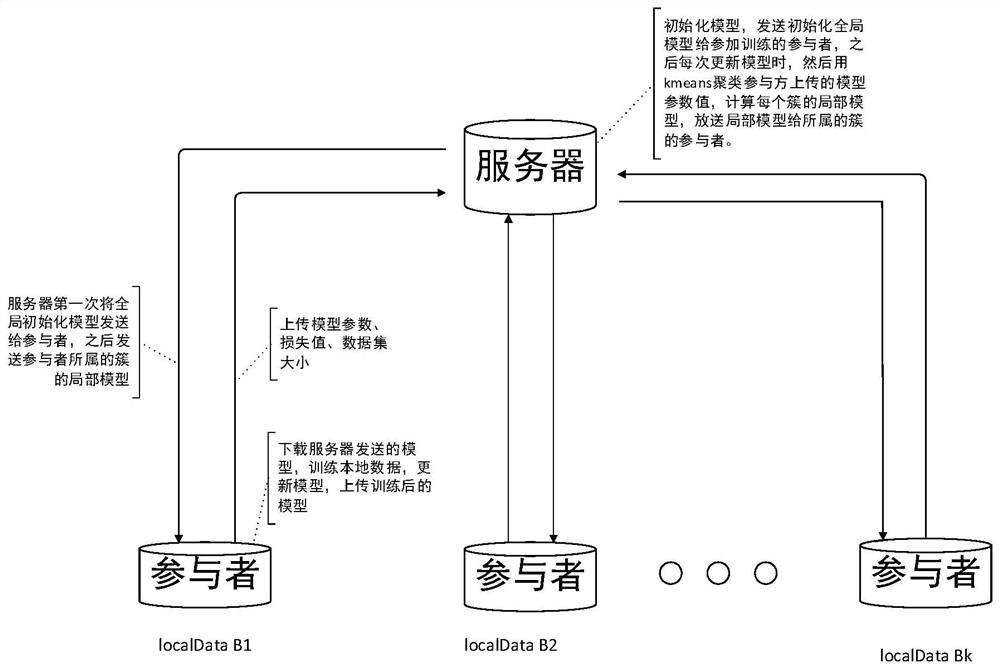
The invention discloses a federation prediction method based on federation learning, and the method enables the parameter change of a neural network model updated by a single participant to have onlydirection difference and no size difference through the unitization of a locally updated gradient vector, thereby protecting the data privacy, and avoiding the use of homomorphic and differential privacy or other encryption technologies. Under the condition of not losing data precision, the communication cost between the equipment and the server is greatly reduced. Besides, considering that the difference of data in a federated learning scene is large, the performance of a local participant can be improved by increasing the local information of the data, the uploaded neural network model parameters are clustered by utilizing a k-means algorithm to obtain similar neural network model parameters, the neural network model parameter aggregation weight is improved. The method is more suitable for the data scene of the participant.
Owner:GUANGXI NORMAL UNIV
Update method of mobile object location based on traffic network and GPS
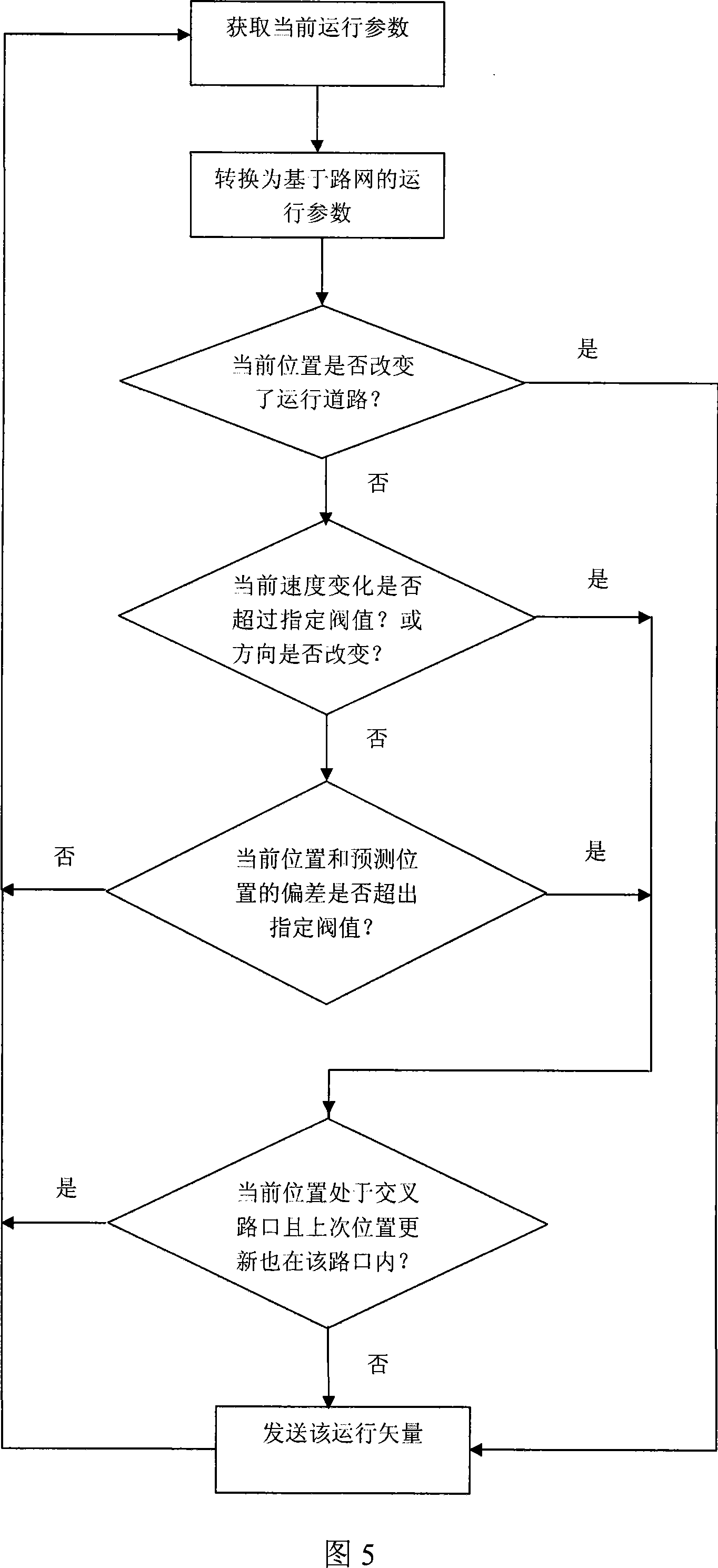
InactiveCN101128051AGuaranteed accuracyReduce calculation errorsBeacon systems using radio wavesPosition fixationObject basedTraffic network
The utility model discloses an updating method for a moving object based on the road transportation network and GPS, aiming at enabling a central server to trace the former and current position of the moving objects. The utility model is characterized in that the moving object uses GPS to measure the latest running data continuously, through matching with the transportation network, the coordinate of the latitude and the longitude and the direction data are converted into the data format based on the road network, then the current running vector is compared with the running data submitted by the updating on the last position according to the principle of the inertia, and the position updating condition is determined, the current running vector of the moving object is reported to the central server only when the moving object does not keep running as the principle of the inertia. Additionally, the utility model optimizes the updating of the position in the road crossing, only one time position updating of the moving object is performed at most in the road crossing. The utility model has advantages of reducing the communication frequency and improving the data processing efficiency under the premises of securing the processing precision compared with the prior art.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Key management method based on wireless Mesh netword
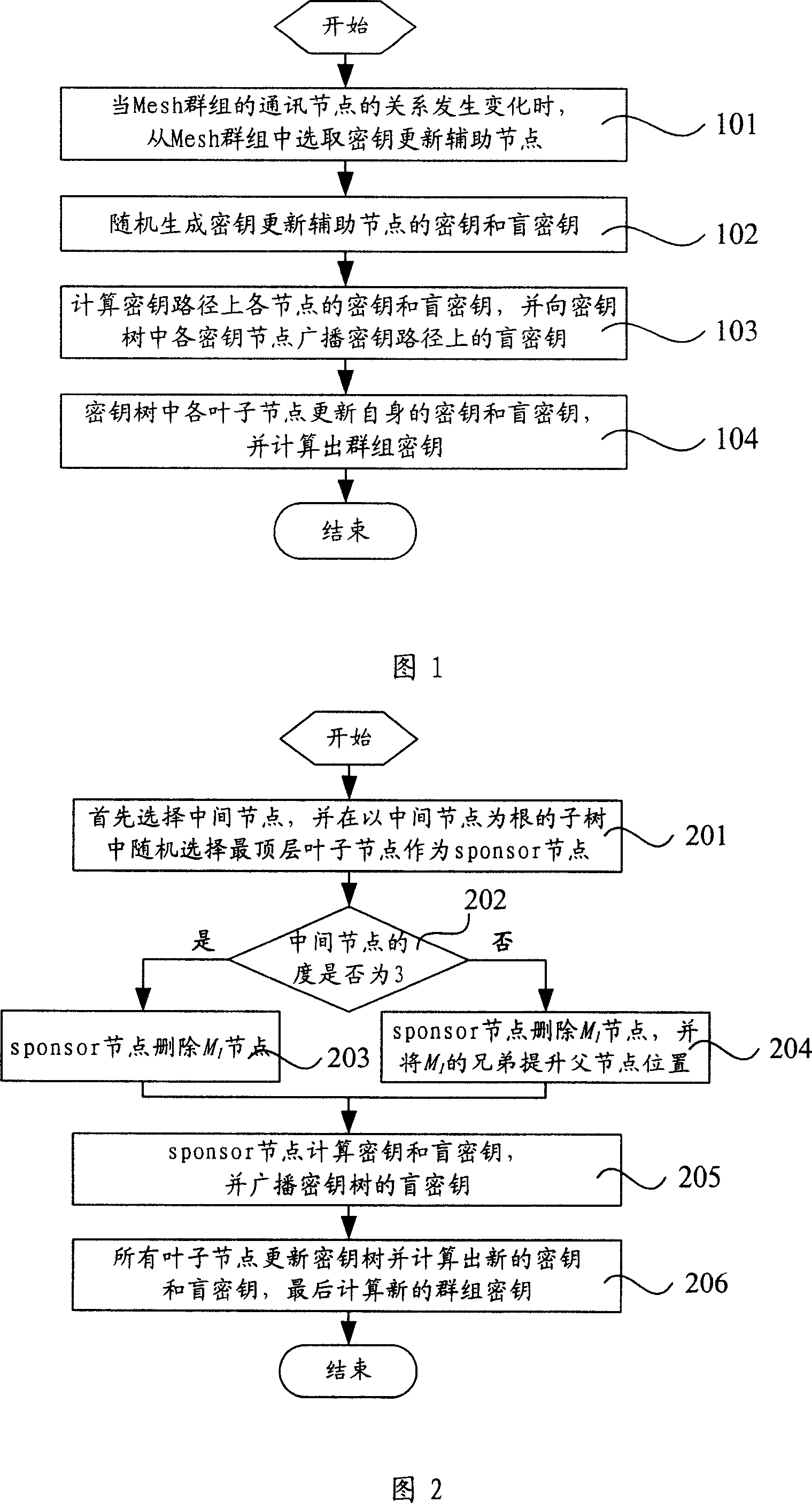
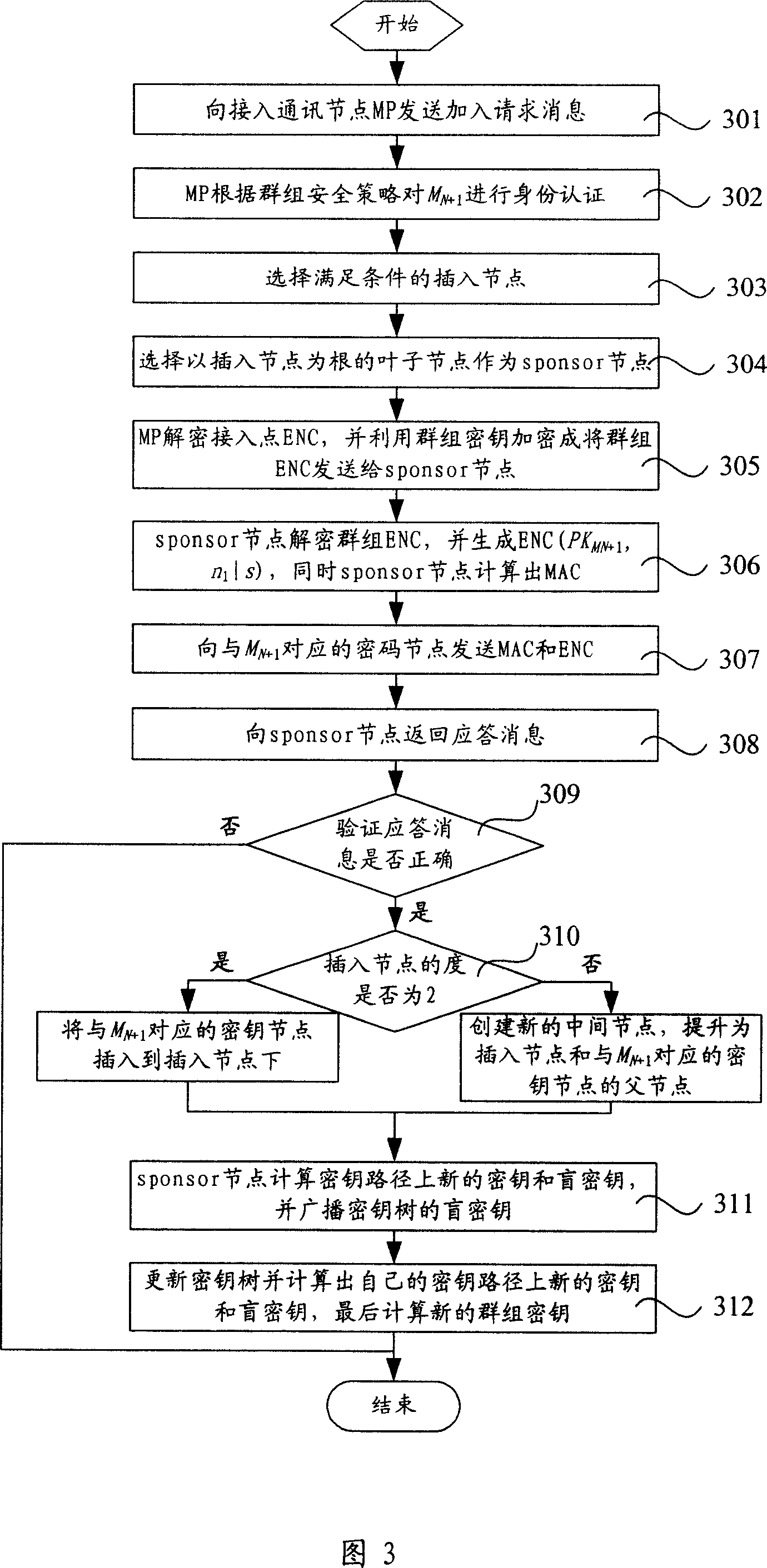
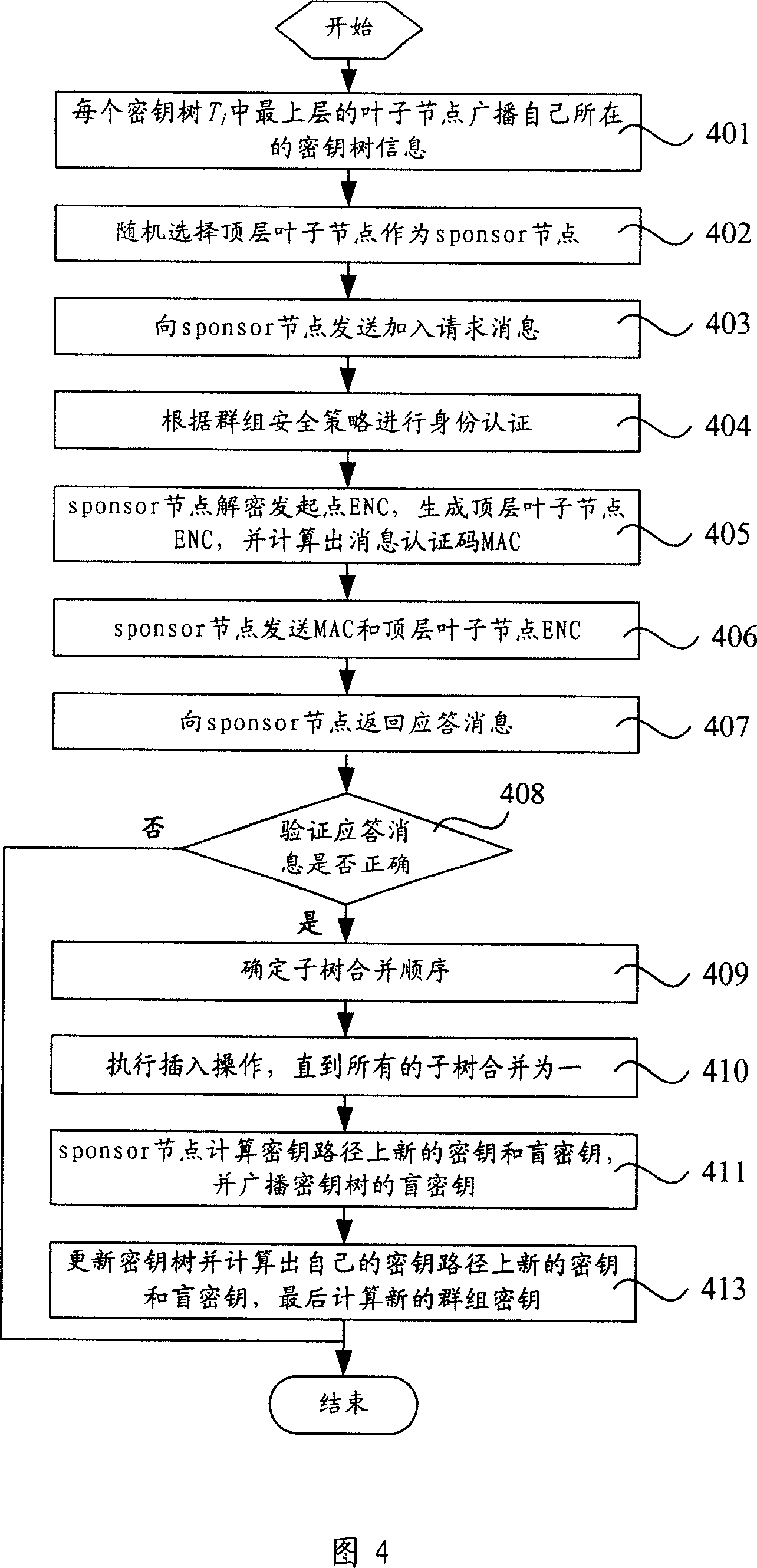
InactiveCN101110670AReduce communication costReduce computational costKey distribution for secure communicationExtensibilityWireless mesh network
The present invention relates to a key management method based on wireless Mesh network, which is characterized in that the method includes procedures below: As relation amongst communication nodes of a mesh cluster varies, an auxiliary updating node is selected from a key tree in correspondence with the Mesh cluster. Wherein, the key tree is provided with a ternary tree structure. A key and a blind key of the auxiliary updating node are created at random. Keys and blind keys at all key nodes in a key path of the key tree are calculated for the auxiliary updating node. Besides, all key nodes of the key tree broadcast to blind keys of all key nodes on the key path. Each leaf node of the key tree updates its own keys and blind keys and works out cluster keys. The technic proposal of the present invention provides parameters of total information length while nodes are added and leaves, password calculation quantity, total combined cluster information length and so on lower than those of prior arts, thus eliminating conflicts of safety demands of prior arts with expansibility and QoS demands.
Owner:XIDIAN UNIV +1
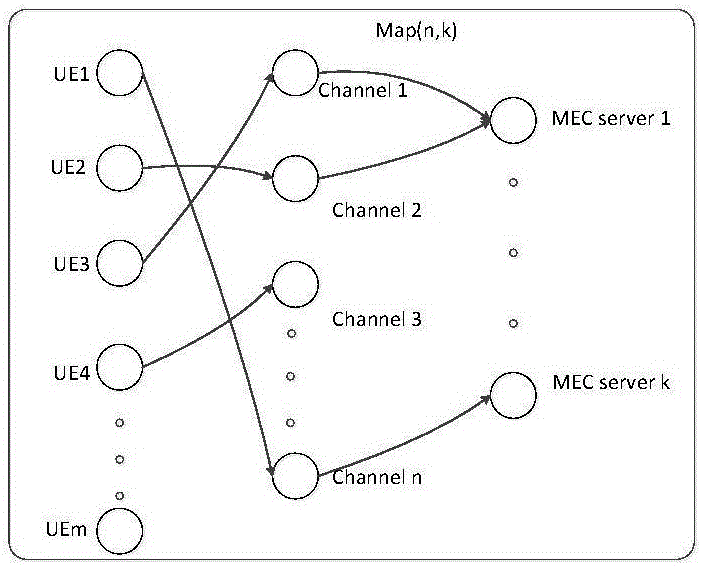
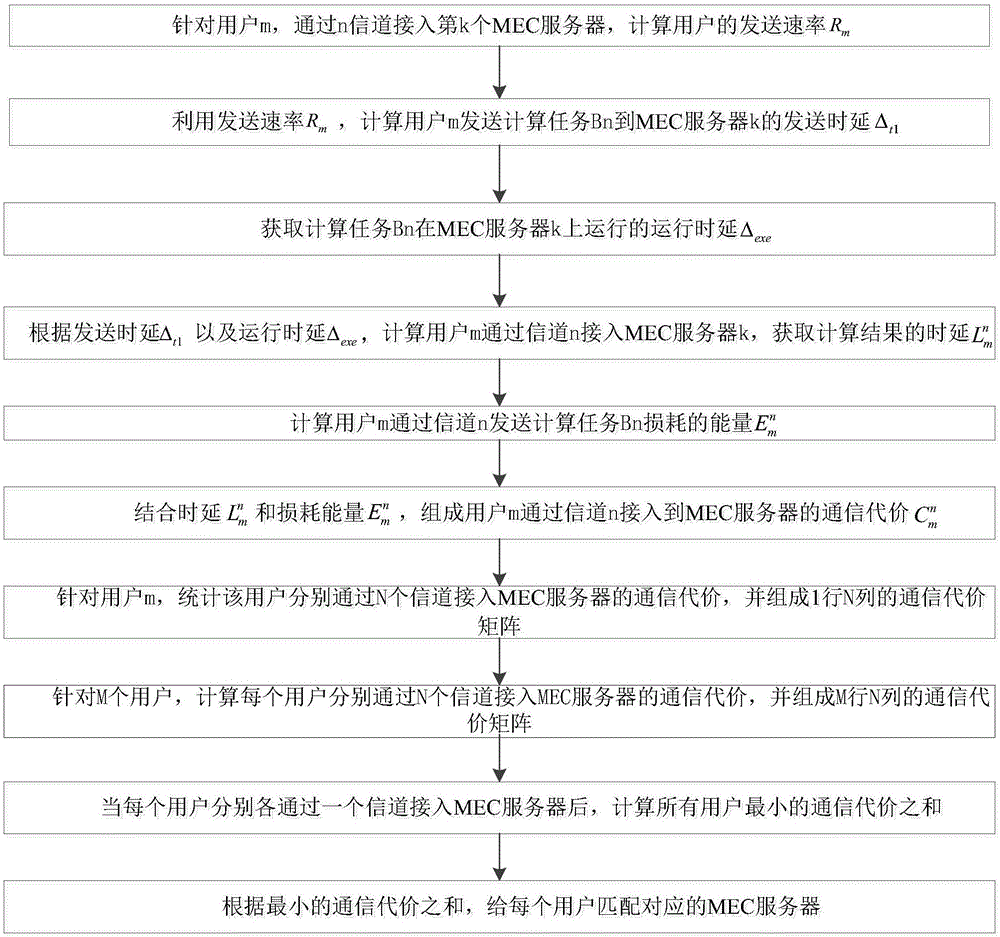
MEC server selection algorithm based on fairness
ActiveCN106100907AEasy to analyzeImprove scene adaptabilityData switching networksControl communicationsEnergy consumption
The invention discloses an MEC server selection algorithm based on fairness, and belongs to the field of mobile communication. The algorithm comprises the steps of establishing a system model among users, channels and MEC servers; randomly selecting the users to be connected with the MEC servers by an initial system; sending calculation tasks in time t by the selected users, and matching the MEC servers for the users according to communication cost; uploading the calculation tasks by the users, and calculating the throughput of each user; sorting the throughput of all users in a descending mode, selecting former N users with the low throughput, and calculating the communication cost of the users; and for the users with the low throughput, selecting the MEC serves by the users for next time calculation. The algorithm has the advantages that the influences of delay and energy consumption on selection of the users to the MEC servers are taken into combined consideration, and a communication model is introduced into the system; and when the users are in different application scenes, different weight parameters are selected, the communication cost is controlled, and the algorithm has better scene adaptability.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Correcting method and application of multi-size router for extensible large-scale sensor network
InactiveCN1719803AReduce communication costCutting costsData switching networksHigh level techniquesNetwork generationEnergy balanced
This invention relates to a multi-dimension route correction method and application for scalable large-scale sensor network. The method includes combining cluster and flooding routes containing a route system based on cluster and flood, a sleep system based on time dispatch and a route correction method based on the optimum covered restriction, fault nodes and network energy balance. The realization process includes: generation of network organization and initial head node and distributed network generation and route correction. This method is used in route correction of large-scale expansion sensor dynamic network and autonomous intermediated piece service agent, autonomous manage intermediate service and energy balance, the optimum cover restriction and fault node judgment, time dispatch energy-save system, the uncertainty test of non-experienced knowledge and distributed coordinated algorithm data.
Owner:WUHAN UNIV
VoIP safety meeting session key transmission method
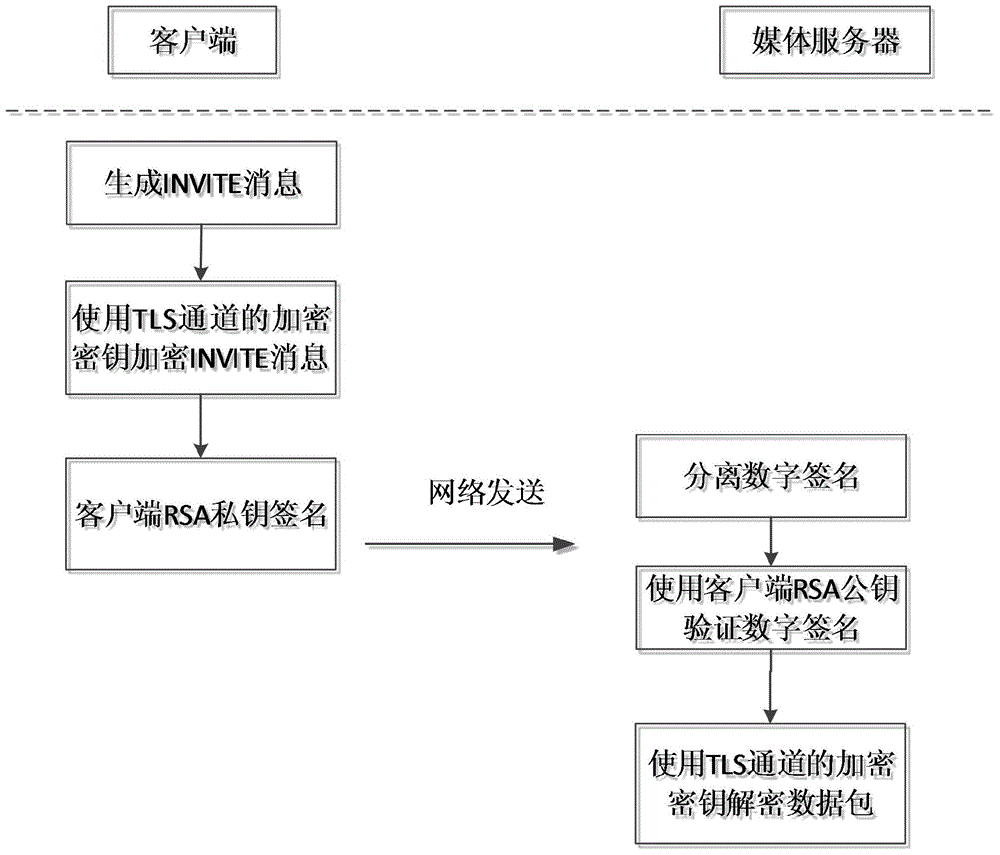
InactiveCN104618110AGuaranteed confidentialityIntegrity guaranteedKey distribution for secure communicationUser identity/authority verificationInformation transmissionClient-side
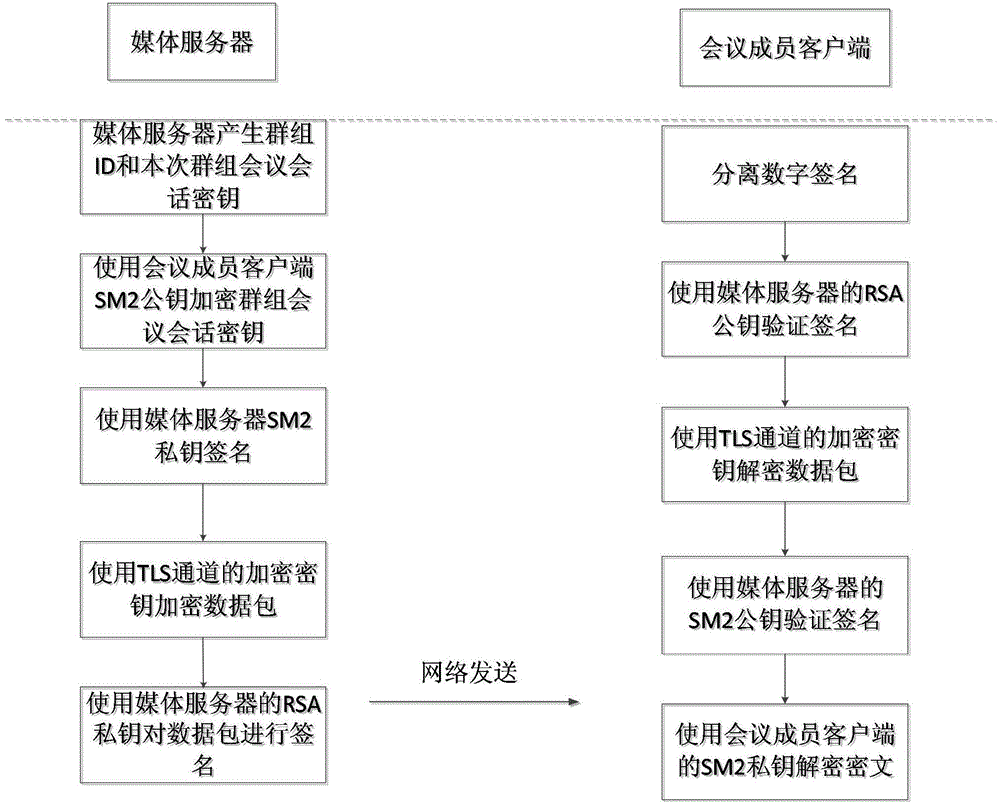
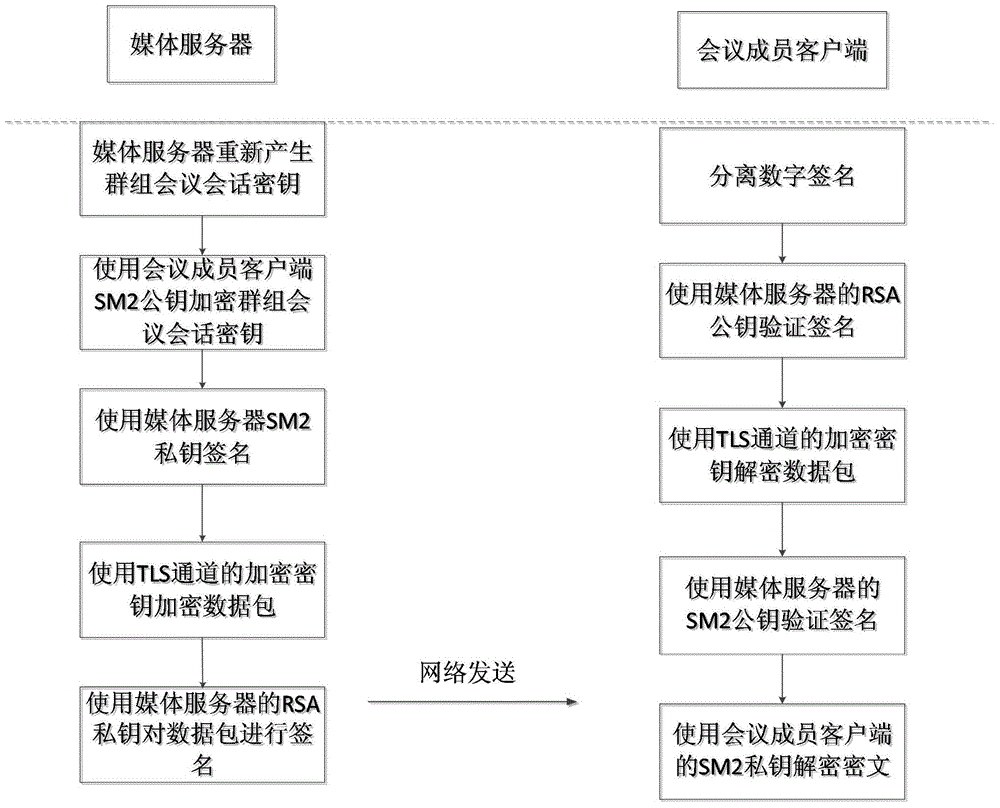
The invention discloses a VoIP safety meeting session key transmission method. The VoIP safety meeting session key transmission method includes that 1) a meeting initiator generates communication request information for building a group, encrypts the communication request information through an encryption key of a TLS passage, signs through an RSA signature key of the meeting initiator and sends to the server; the server uses a corresponding RSA signature public key to verify the information and decodes the information through an encryption key of the TLS passage to obtain the communication request information; 2) the server generates a group ID and a group meeting session key, builds the group and sends invitation information to a client to be invited; 3) the client uses an RSA signature public key of the server to verify the invitation information, decodes the invitation information through an encryption key of the TLS passage, uses an SM2 public key of the server to verify the information and uses an SM2 key thereof to decode the cipher-text to obtain the group ID and group meeting session key. The VoIP safety meeting session key transmission method greatly improves the information transmission safety.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Cloud storage system and file copy deployment method based on cloud storage system
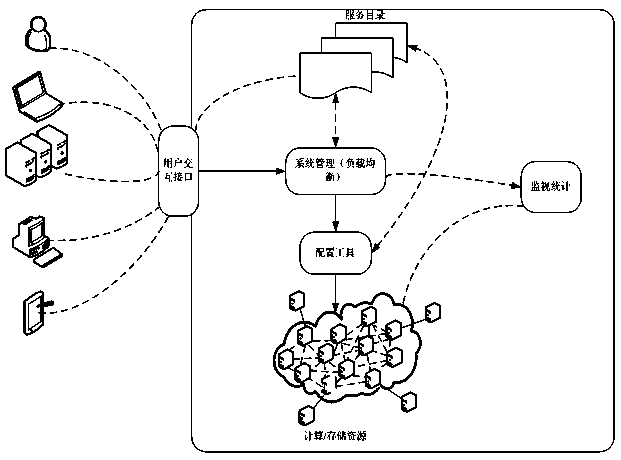
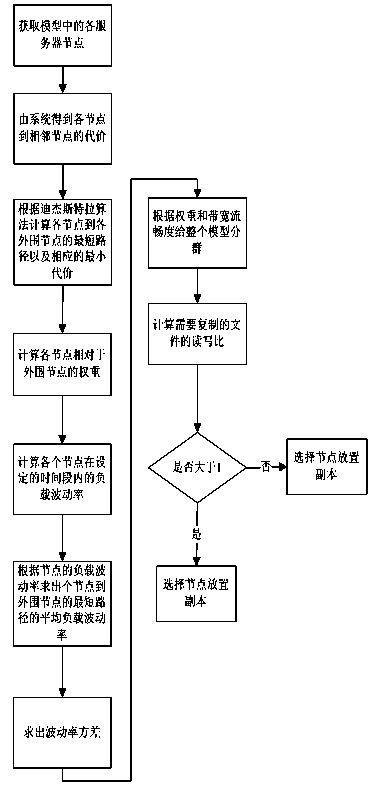
ActiveCN103763363AImprove usabilityReduce communication costInput/output to record carriersTransmissionNetwork communicationDependability
The invention discloses a cloud storage system and a file copy deployment method based on the cloud storage system. The cloud storage system and the file copy deployment method are used for improving the reliability and the availability of data under cloud storage and belong to the technical fields of distributed computation and cloud storage. By means of the cloud storage system and the file copy deployment method, a whole cloud computing model is grouped according to inlet server nodes of the distributed cloud computing model, the minimum communication cost from server nodes to the inlet nodes and the bandwidth fluency degree of the optimal path obtained by the self load fluctuation rate; a copy is reasonably arranged according to the read-write ratio of the copy. According to the cloud storage system and the file copy deployment method, the network communication cost is wholly reduced, and meanwhile the availability of the copy is improved. Compared with a traditional copy arranging scheme, the technical scheme has the larger advantages on both the utility rate of storage space and the communication cost.
Owner:BEIJING ZETTASTONE TECH CO LTD
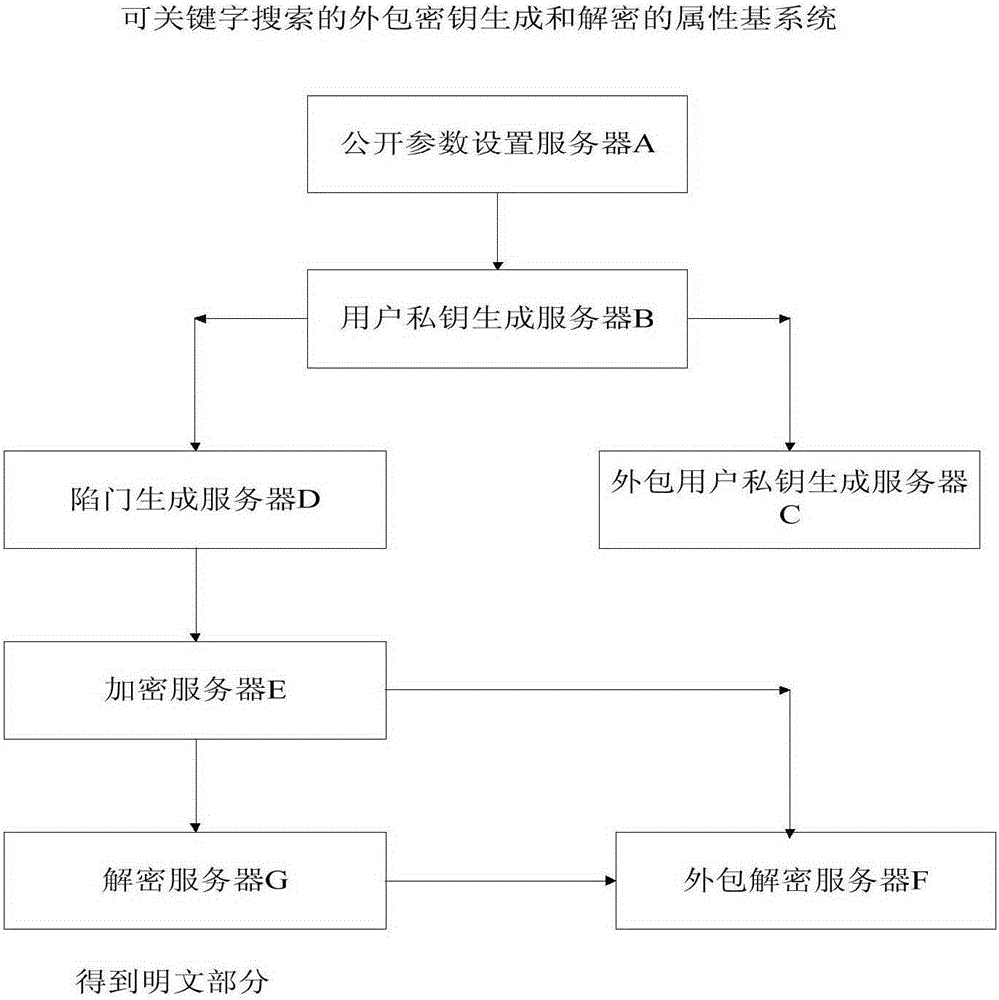
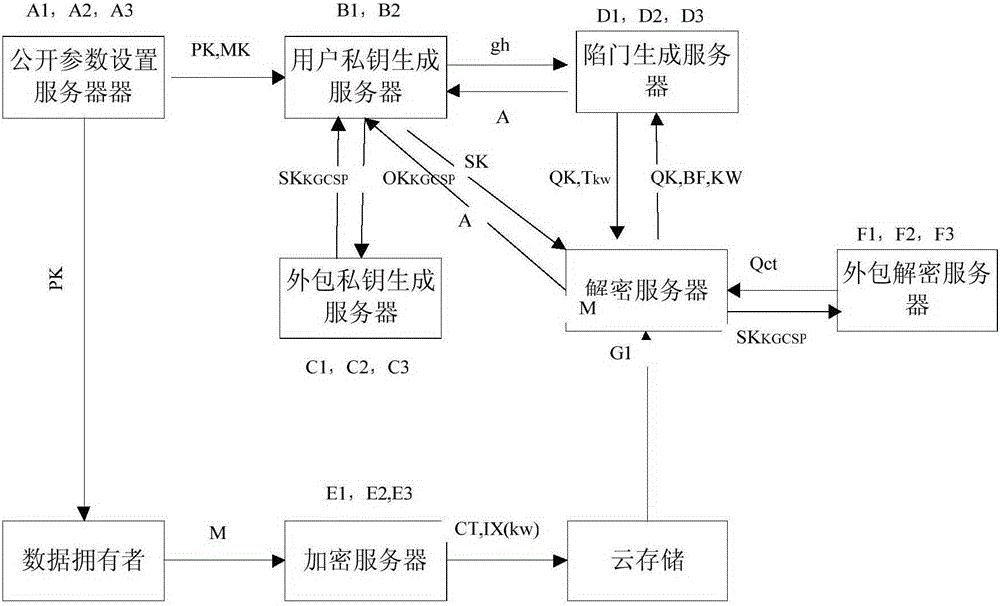
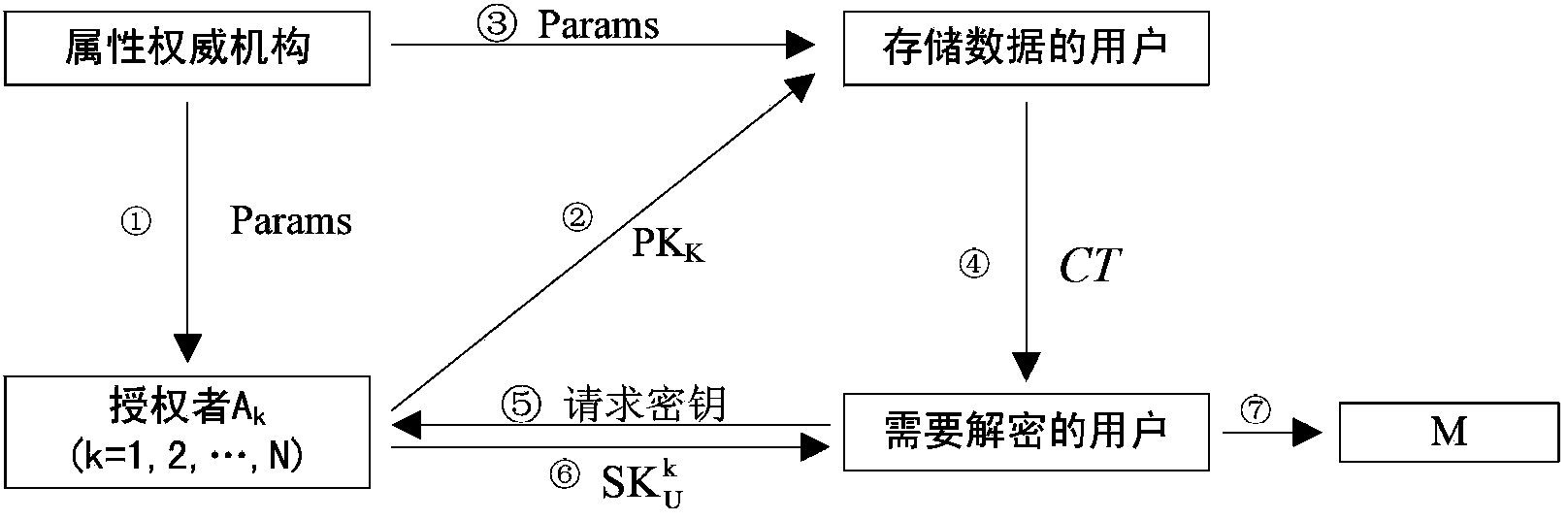
Outsourced key generation and decryption property-based system capable of realizing keyword search and decryption method
ActiveCN105323061AEfficient and more accurate acquisitionReduce communication costPublic key for secure communicationKey generationUser Privilege
The invention provides an outsourced key generation and decryption property-based system capable of realizing keyword search. The outsourced key generation and decryption property-based system capable of realizing the keyword search comprises a public parameter setting server, a user private key generation server, an outsourced user private key generation server, a trap door generation server, an encryption server, an outsourced decryption server and a decryption server, wherein the public parameter setting server is in charge of generating a system master key and public parameters; the user private key generation server is in charge of generating a private key pair and a local user private key; the outsourced user private key generation server is in charge of generating an outsourced user private key; the trap door generation server is in charge of assisting a user to generate an inquiry password and a trap door; the encryption server is in charge of encrypting a message and generating corresponding ciphertext and keyword indexes; the outsourced decryption server is in charge of decrypting an outsourced part of the ciphertext according with user right and searching for matching ciphertext by adopting the trap door submitted by the user; and the decryption server decrypts partially decrypted ciphertext, so that the message is restored. The invention provides a method for searching ciphertext matched with keywords.
Owner:HOHAI UNIV
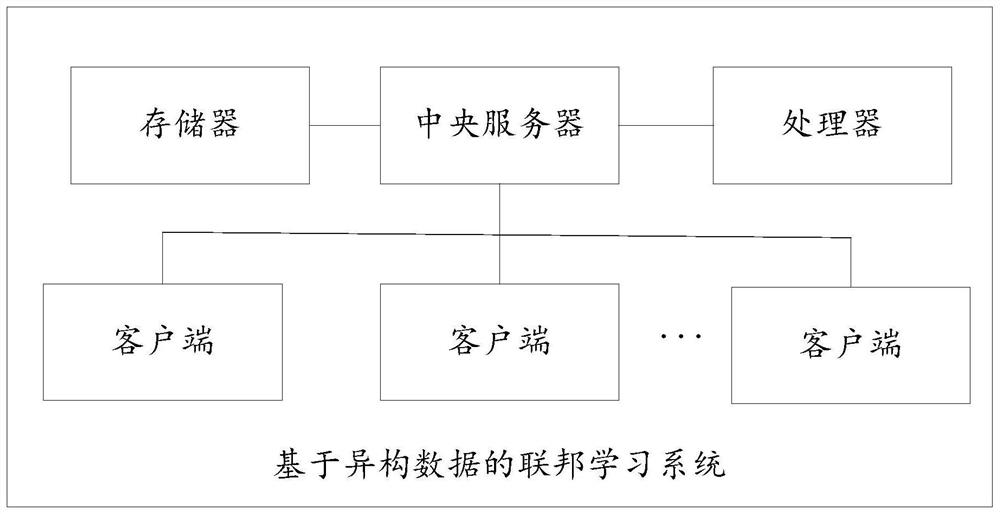
Federated learning system based on heterogeneous data
The invention relates to a federated learning system based on heterogeneous data, which comprises a central server, K clients, a memory in which a computer program is stored and a processor, and is characterized in that the central server stores a global control variable S and a global model parameter W obtained by each round of federated learning; the global control variable S is used for recording the global model updating direction of the round; the client stores a local control variable Si obtained by each participating client by participating in federated learning every time, the local control variable Si is used for recording the updating direction of a local model of the client participating in federated learning training this time, and the value of i is 1-K.Communication cost of federated learning based on heterogeneous data is reduced, and the convergence speed and the convergence stability of federated learning are improved.
Owner:上海嗨普智能信息科技股份有限公司 +1
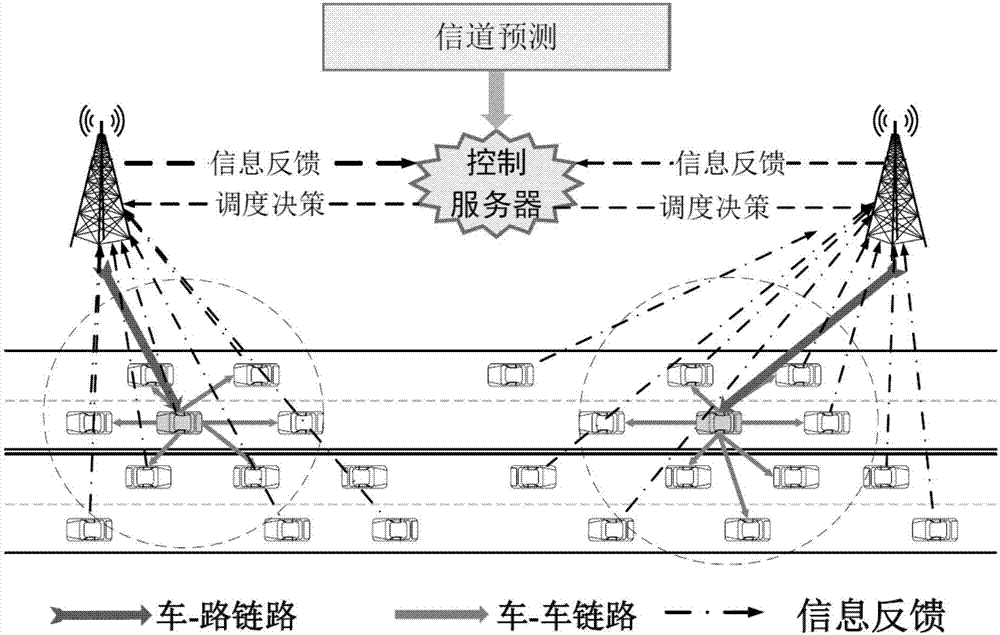
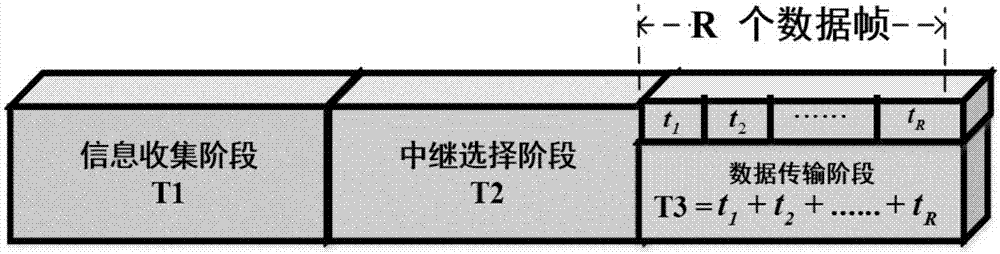
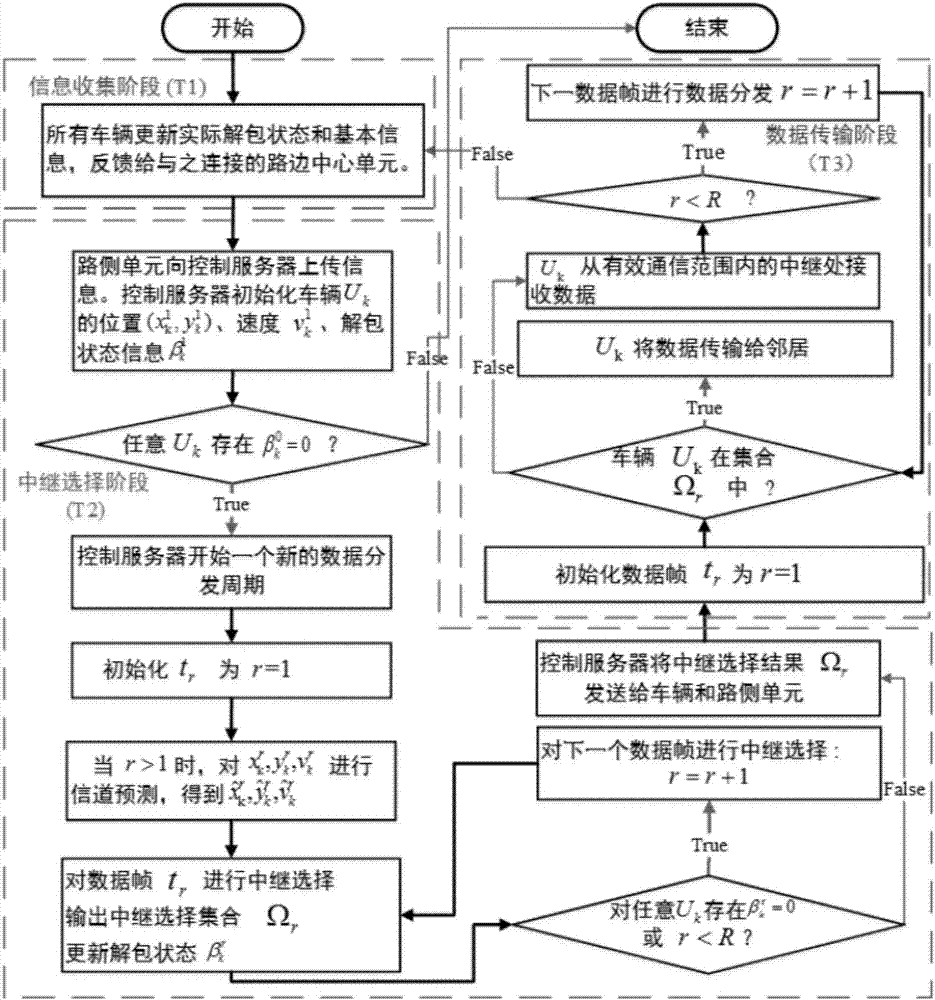
Internet of vehicles (IoV) data transmission scheduling method based on channel prediction
InactiveCN106972898AImprove performanceGreat Communication BenefitTransmission monitoringHigh level techniquesPrediction algorithmsTelecommunications link
The invention discloses an Internet of vehicles (IoV) data transmission scheduling method based on channel prediction. Large-scale channel information between vehicles and roadside enter units and between vehicles is predicted by using a channel prediction algorithm according to collected vehicle state information, a signal to noise ratio and communication benefit of a potential communication link are computed, and a relay vehicle node set is selected to scheduling data distribution by using a greedy algorithm. According to the method, an effective vehicle node is selected as a relay node for distributing data by predicting the channel fading in large scale to achieve the maximum communication benefit; and in a central data distribution scene having the vehicles and the roadside center units, a throughput rate of the system is improved, and data distribution delay is reduced by reasonably allocating time resources.
Owner:PEKING UNIV
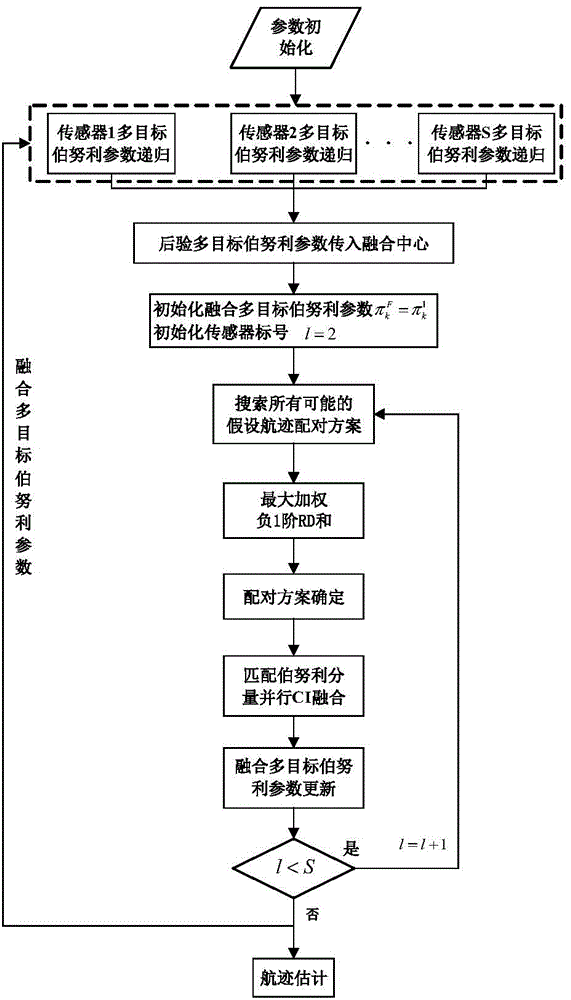
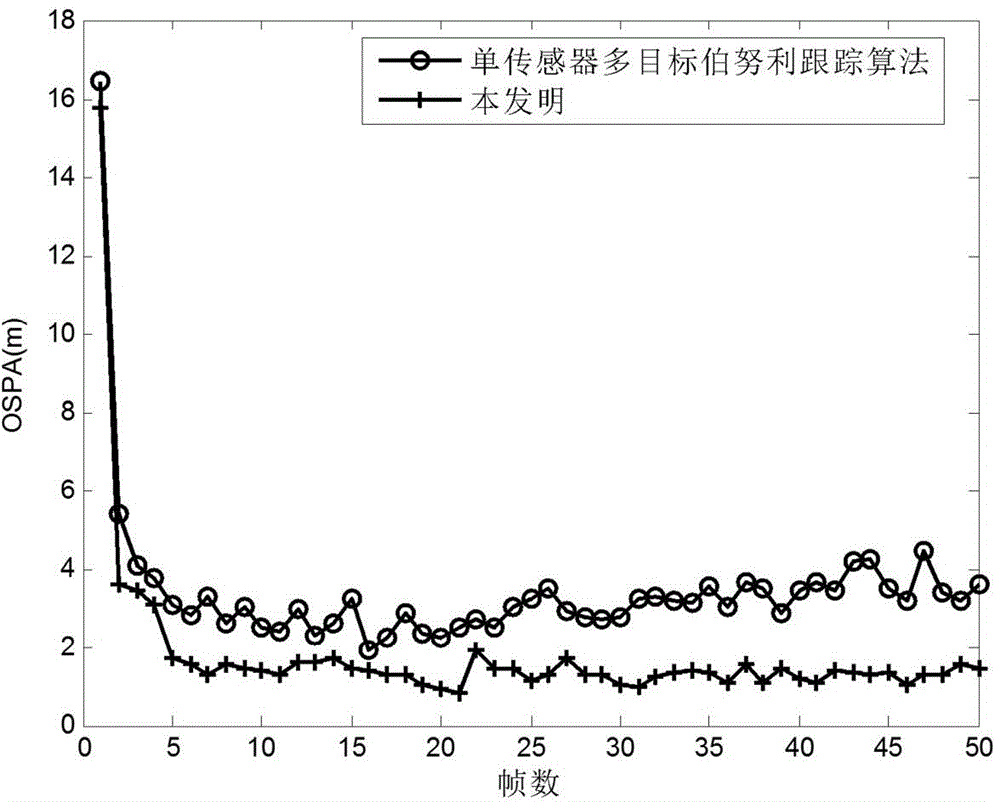
Multiple-target Bernoulli distribution type fusion method based on weighting negative first-order RD (Renyi Divergence)
ActiveCN104133983AImprove tracking accuracyImprove reliabilitySpecial data processing applicationsFusion centerRadar signal processing
The invention discloses a multiple-target Bernoulli distribution type fusion method based on weighting negative first-order RD (Renyi Divergence), and belongs to the field of radar signal processing. The same frame of posteriori multiple-target Bernoulli parameters of a plurality of sensors is transmitted to a fusion center, and the posteriori multiple-target Bernoulli parameters of all sensors are fused in the fusion center. The fusion method comprises the following steps: decomposing the multiple-target Bernoulli parameter into a plurality of Bernoulli components; constructing a cost function based on a weighting negative first-order RD sum to find an optimal matching scheme of the Bernoulli parameters of different sensors; fusing a plurality of matched Bernoulli components in parallel by adopting a CI (Covariance Intersection) fusion rule; approximately realizing the fusion of the multiple-target Bernoulli parameters of different sensors; selecting a plurality of most likely targets from a fusion result; and returning the fused result to each sensor. Therefore, the invention has the effects of being high in tracking precision, low in false alarm rate, strong in robustness, high in reliability, small in communication cost and strong in antijamming capability.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Encryption method for multiple authorization centers
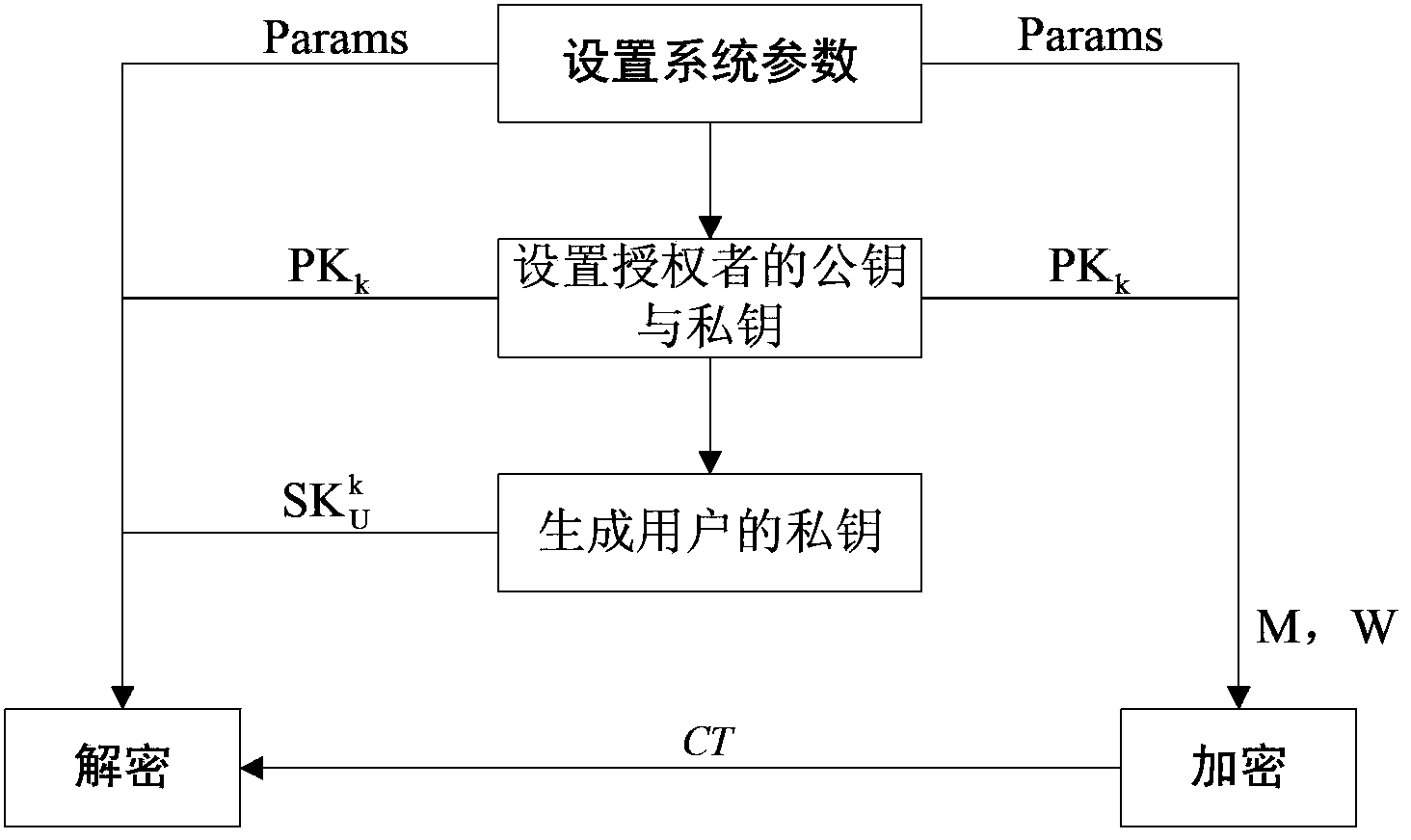
InactiveCN103457725AReduce computational costReduce communication costPublic key for secure communicationAttribute-based encryptionCloud computing
The invention provides an encryption method for multiple authorization centers. The method includes the steps that system parameters are firstly set; a public key and private keys of an authorizer are set according to the system parameters, the public key is used for encrypting data, and the private keys are used for generating a private key of a user; the private key of the user is used for decrypting an encrypted message. Through the encryption method which fixes the length of the encrypted message, includes the multiple authorization centers and is based on attributes, a center authorizer is removed, each authorization center independently manages the attribute and distributes the private keys, meanwhile, calculation cost and communication cost of the authorization centers and the user are reduced through the method, the encryption method is used for solving problems of access control and safety in cloud calculation, the efficiency of system operation is improved, and expenditure is saved.
Owner:HOHAI UNIV
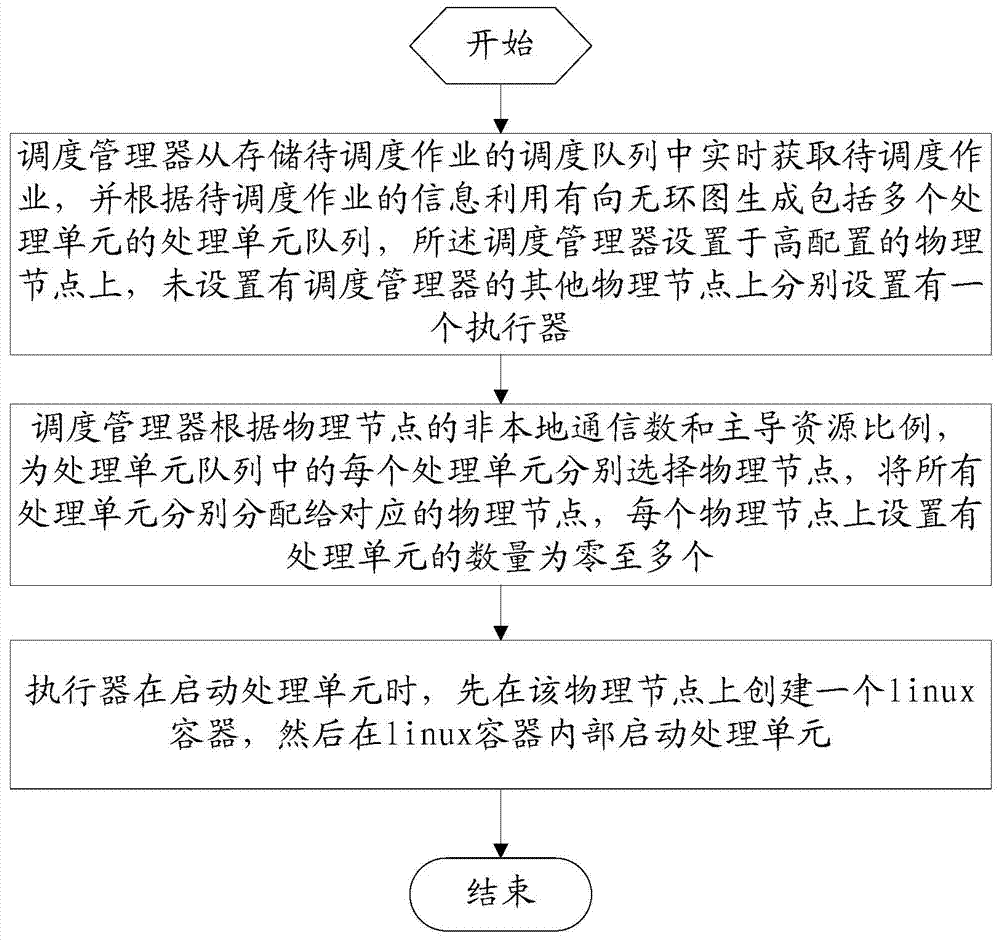
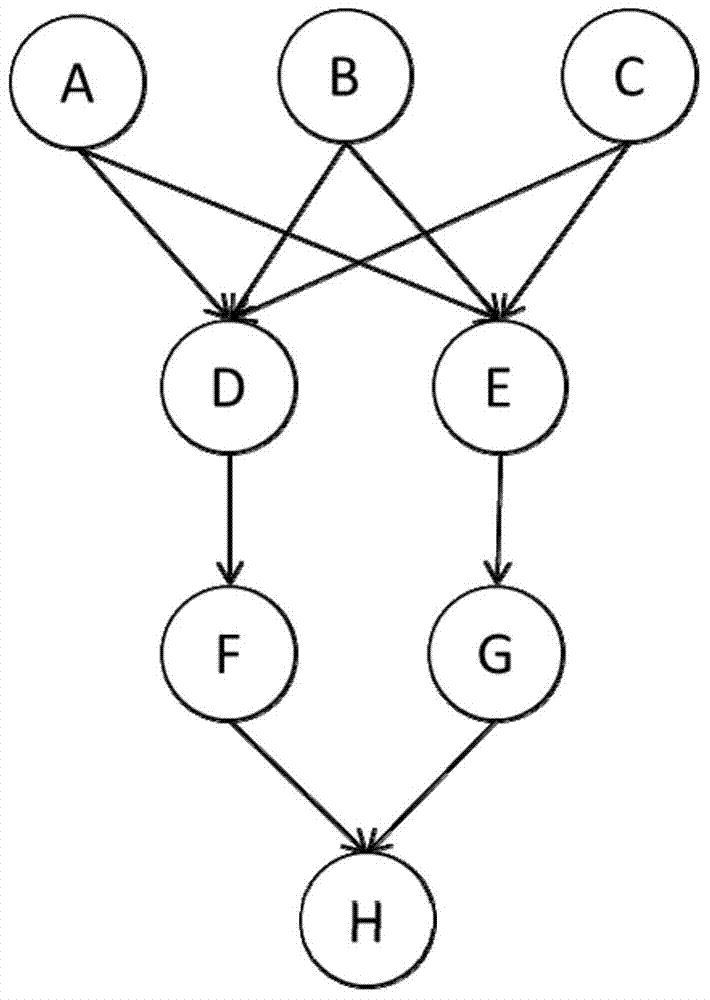
Job scheduling method and device for streaming data
ActiveCN103491024AReduce communication costReduce network latencyData switching networksGNU/LinuxStream data
The invention relates to a job scheduling method for streaming data. The job scheduling method for the streaming data comprises the following steps: a scheduling manager acquires jobs to be scheduled from a scheduling queue in real time, and utilizes a directed acyclic graph for generating a processing unit queue according to information of the jobs to be scheduled; according to the ratio of the non-local communication number of physical nodes to dominant resources, the scheduling manager selects one physical node for each processing unit in the processing unit queue and distributes all the processing units to the corresponding physical nodes respectively; when an actuator starts one processing unit, a linux container is established on the physical node of the processing unit, and then the processing unit is started inside the linux container. According to the job scheduling method for the streaming data, the processing units are scheduled to the physical nodes which are small in non-local communication number and low in load, the processing units which need communication frequently can be concentrated to the same physical node, and therefore network communication across the physical nodes is reduced.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Management method and management system of centralized mobile agent server
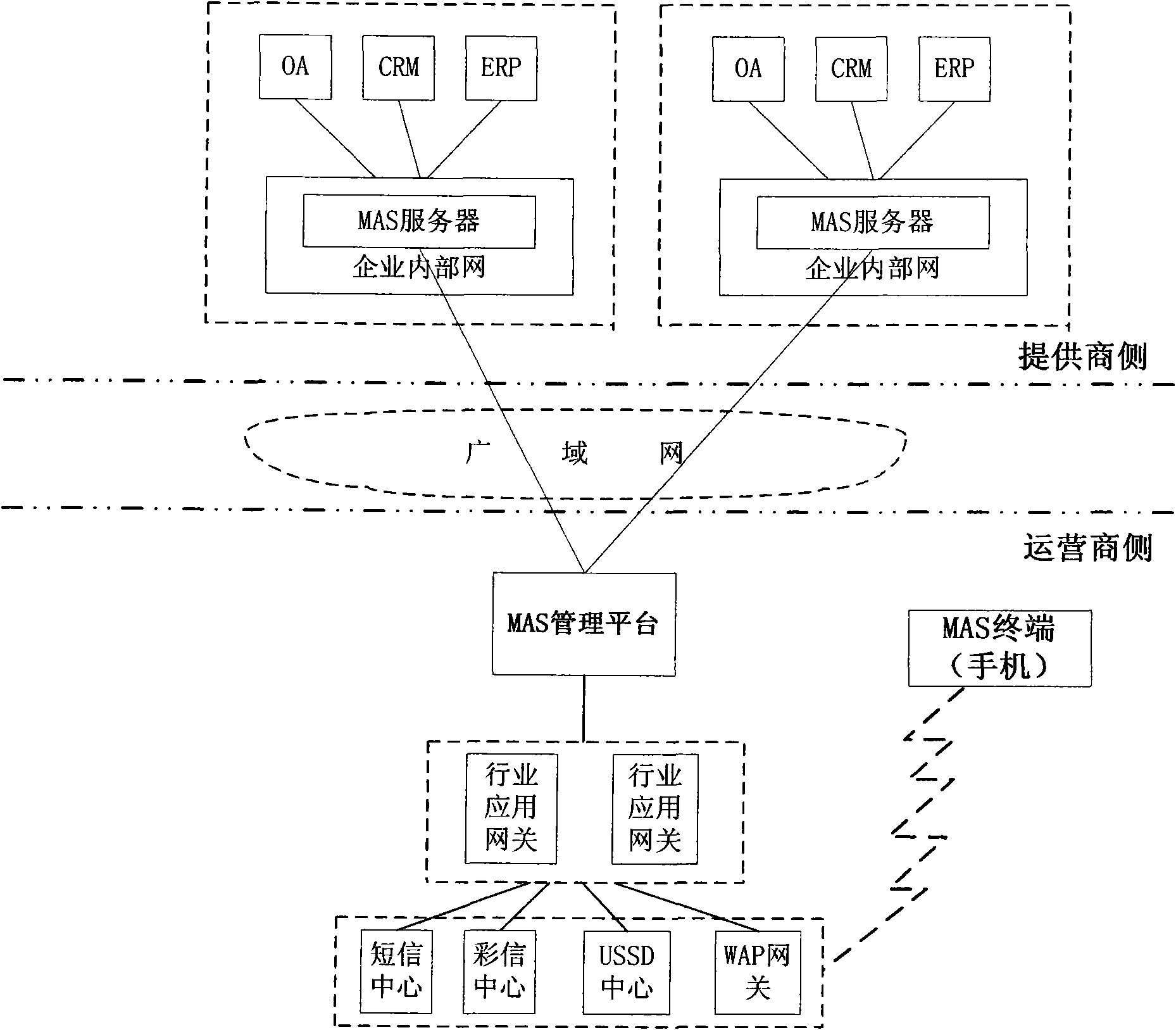
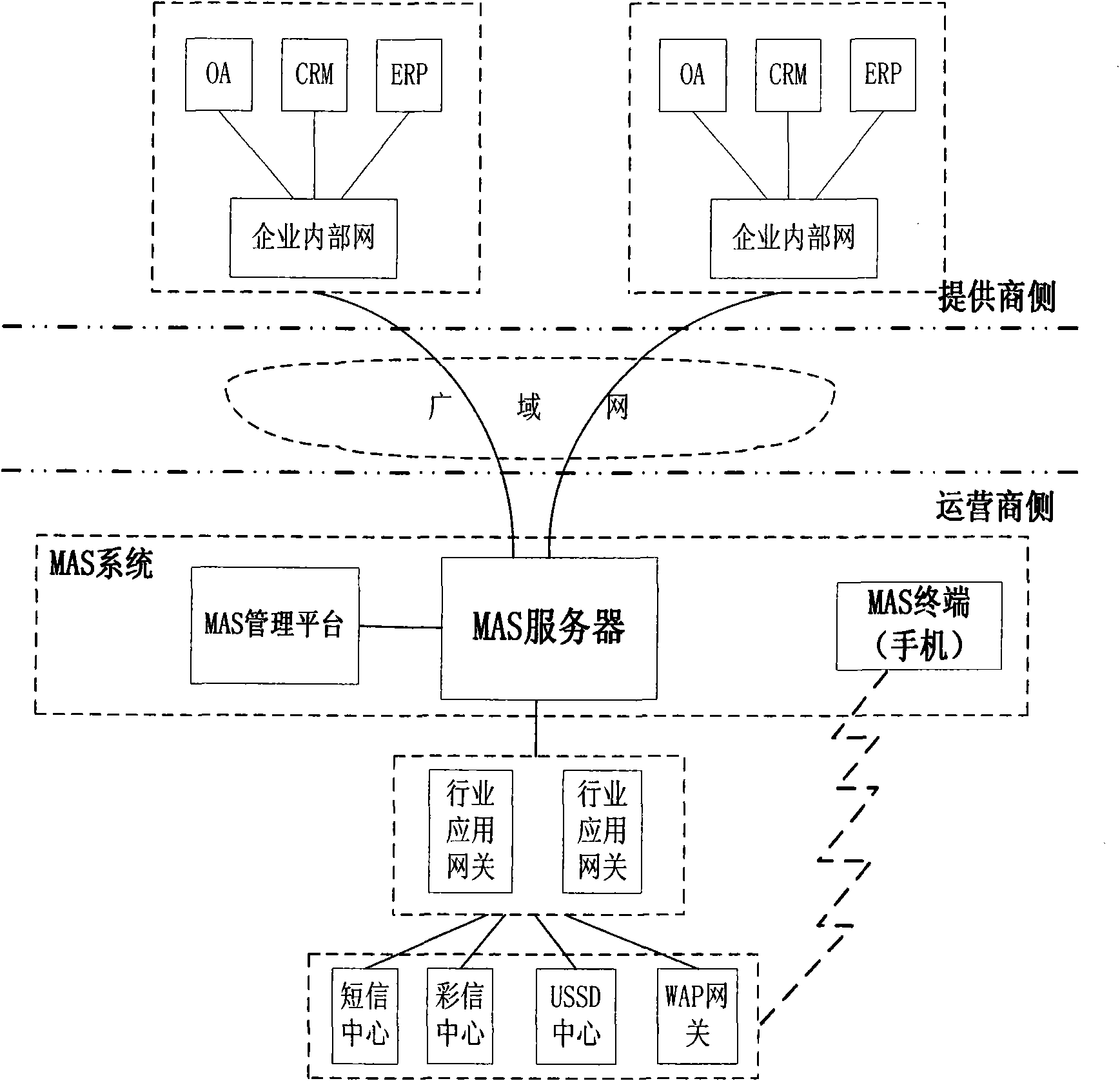
InactiveCN101959220ALower acquisition costsEasy to manageNetwork traffic/resource managementNetwork architectureStructure of Management Information
The invention provides a management method and a management system of a centralized mobile agent server. The system comprises a mobile agent server and a mobile agent server management platform, wherein the mobile agent server is positioned on the side of an operator, directly connected with the mobile agent server management platform and connected with one or more enterprise application systems on the side of the operator through a wide area network; the mobile agent server is used for finishing the transmission of service data between the enterprise application server and the mobile terminal and performing controlling; and the mobile agent server management platform is used for performing unified management on the service data of the mobile agent server. By arranging an MAS server on the side of the operator in a centralized way, the method and the system ensure simple network architecture, contribute to management and maintenance of the operator, reduce the operation maintenance cost, and effectively reduce the data transmission redundancy of network element equipment, such as the MAS server, industry application gateways and the like, thereby reducing the communication cost and improving the system response speed.
Owner:ZTE CORP
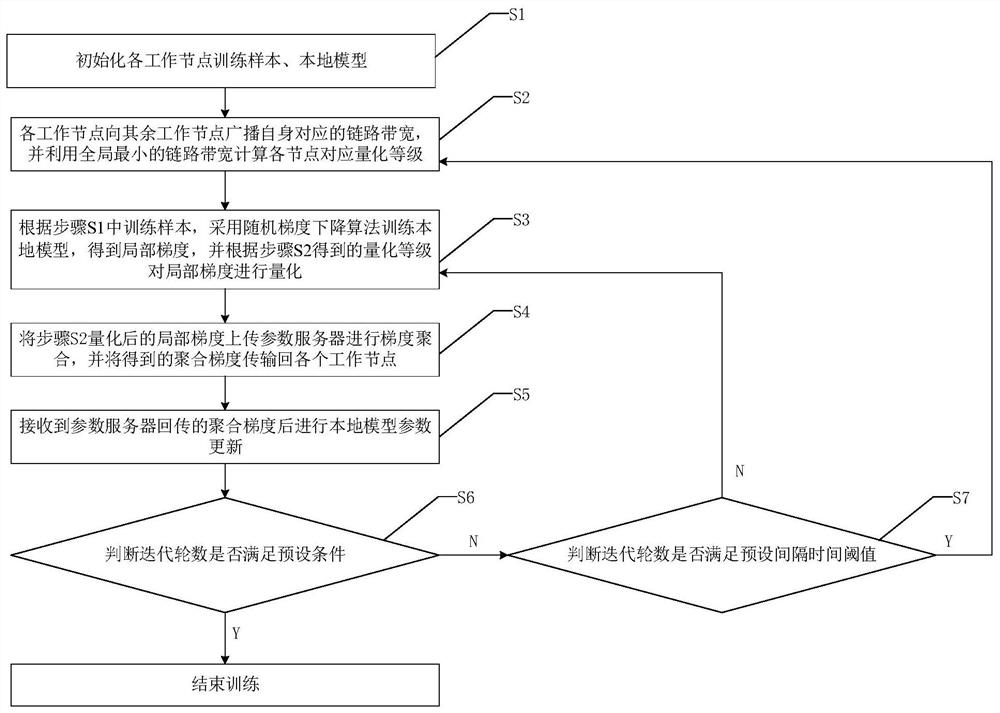
Federal learning adaptive gradient quantification method
ActiveCN113315604AEfficient learning and trainingHigh precisionNetwork traffic/resource managementEnsemble learningEngineeringArtificial intelligence
The invention discloses a federal learning adaptive gradient quantification method, which comprises the following steps of: initializing a training sample and a local model of each working node, training the local model by using the training sample to obtain a local gradient, and quantifying the local gradient according to a quantification level obtained by each working node; uploading the local gradient to a parameter server for gradient aggregation, and transmitting an aggregation result back to each working node; each working node updating local model parameters by using the quantized aggregation gradient; judging whether the number of iterations meets a preset interval time threshold, if so, broadcasting the link state of each working node and timely adjusting the self quantization level, otherwise, entering an iterative training process, and ending training until a preset condition is met. According to the method, the quantized bits of the gradient are adaptively adjusted according to the real-time bandwidth of the node link, the stragler problem is effectively relieved, the bandwidth resource utilization rate is improved on the basis that the communication overhead task is reduced through a traditional quantization method, and more efficient federal learning training is completed.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
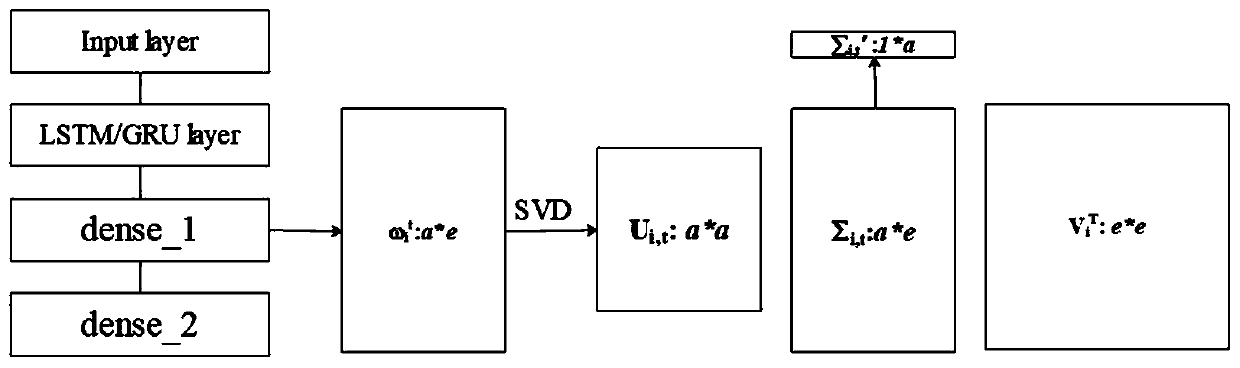
Heterogeneous federated learning mine electromagnetic radiation trend tracking method based on SVD algorithm
ActiveCN111079977APlay the role of noise reductionReduce the amount of communication in a single roundForecastingCharacter and pattern recognitionData imbalanceModel extraction
The invention discloses a heterogeneous federated learning mine electromagnetic radiation intensity trend tracking method based on an SVD algorithm, and the method comprises: firstly proposing a heterogeneous model federated learning algorithm for the problem of data imbalance in a federated learning client, and setting a heterogeneous central model in a server for the client to select, so as to improve the precision of a local model; aiming at the problem of uploading communication cost of local model parameters, providing an efficient communication algorithm that an SVD algorithm is firstlyused for decomposing a parameter matrix to obtain a corresponding singular value matrix, and then the singular value matrix is uploaded to a central server for aggregation updating; and finally, usingthe updated local model by each client to extract local data features, and using the features and real data values by each client to train the ESN and then to execute trend tracking. According to theinvention, trend tracking of electromagnetic radiation intensity acquired by multiple sensors can be realized on the premise of protecting data privacy, the trend tracking precision of each client can be improved, and the communication cost required by a framework is reduced.
Owner:CHINA UNIV OF MINING & TECH
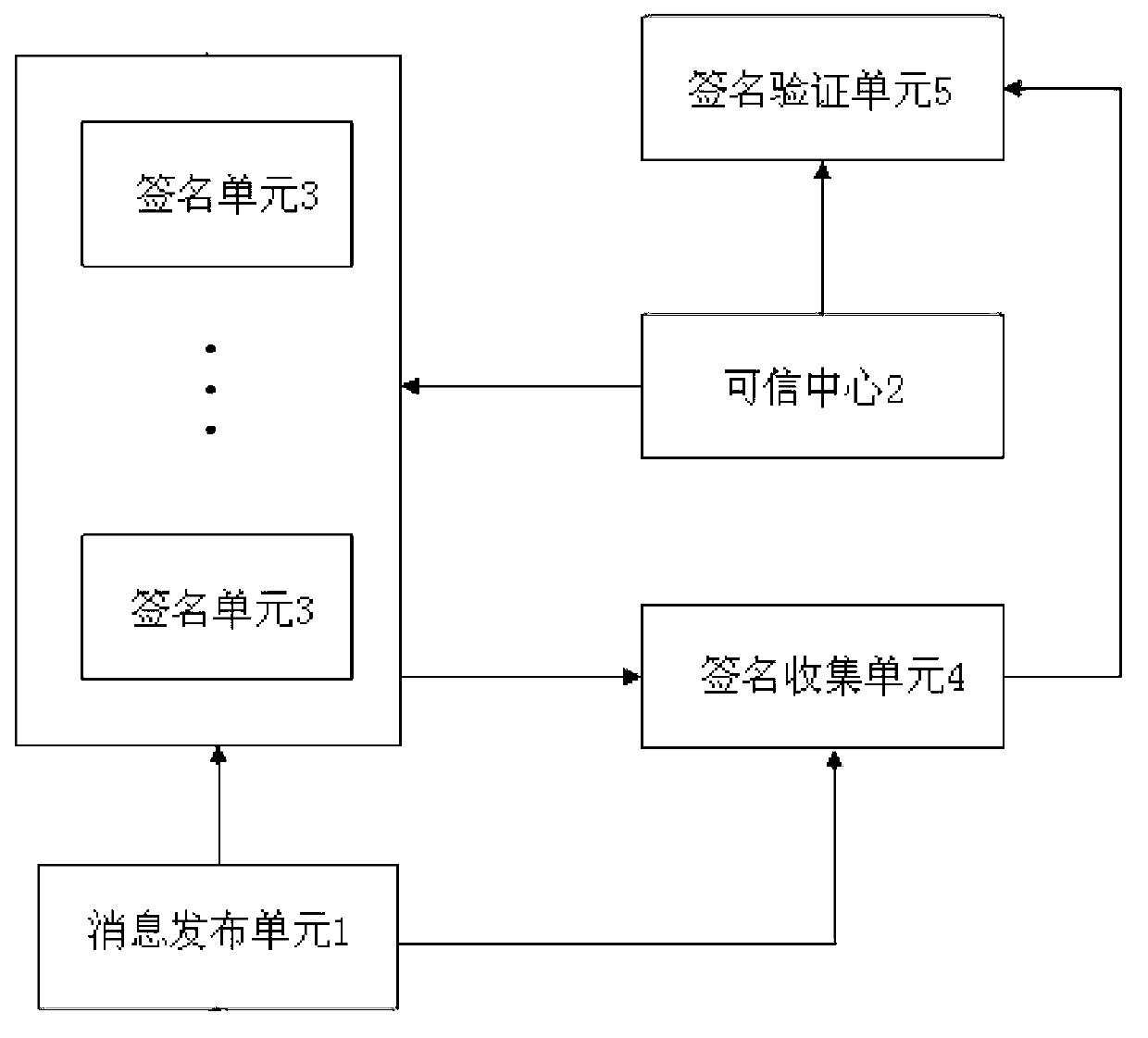
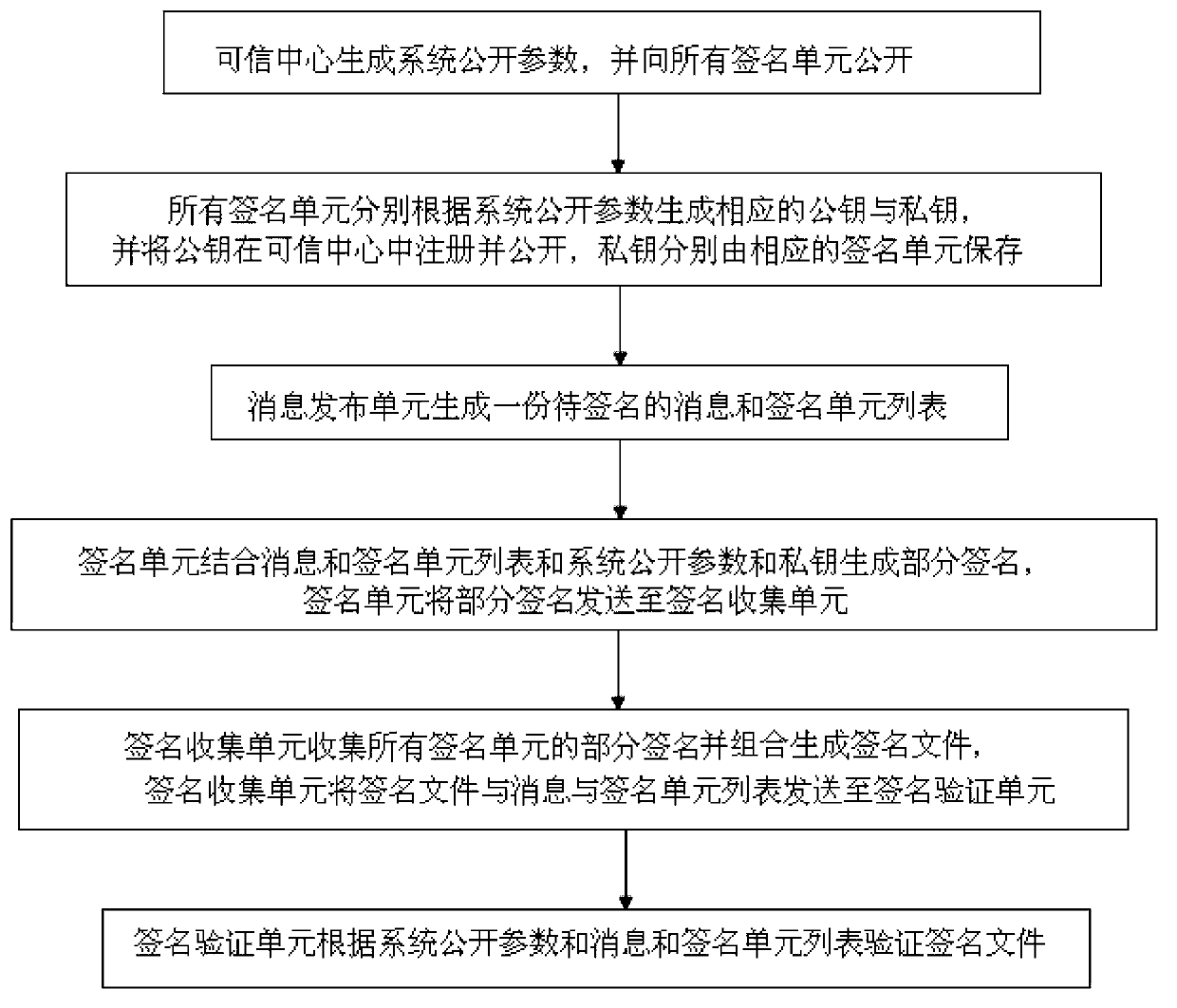
Multiple signature generation and verification system and method thereof
InactiveCN103095697AReduce communication costImprove signature efficiencyUser identity/authority verificationSignature fileValidation methods
The invention discloses a multiple signature generation and verification system and a method thereof. The multiple signature generation and verification system comprises an information releasing unit, a credible center, at least one signature unit, a signature collection unit and a signature verification unit. The information releasing unit generates information to be signed, and a signature unit listing used for signing. The credible center generates system public parameters. At least one signature unit is connected with the information releasing unit and the credible center in a communication mode and is used for generating a public key and a private key and generating corresponding partial signatures. The signature collection unit is connected with the information releasing unit, the signature unit and the signature verification unit in a communication mode. The signature verification unit is connected with the credible center and the signature collection unit in a communication mode and is used for verifying signature files according to the public parameters, the signature unit listing and the information. According to the multiple signature generation and verification system, each signature unit independently generates the partial signatures of the each signature unit, and the system is free from interaction, low in communication cost, and high in signing efficiency. The invention further discloses the multiple signature generation and verification method.
Owner:EAST CHINA NORMAL UNIV +1
Network telephony processing method for smart mobile terminal
InactiveCN103796282AFully account for complexityReduce communication costInterconnection arrangementsAssess restrictionVoice communicationNetwork conditions
The invention relates to the field of mobile communication and mobile internet, and provides a network telephony processing method integrated with a voice call based on a public mobile communication network and a network call based on the mobile internet. The network telephony processing method is applied to a smart mobile terminal with a voice communication function. When a user conducts telephone dial-up, the smart mobile terminal can detect the network condition of the smart mobile terminal, a common call mode or a network call mode can be automatically chosen according to the detecting result to conduct dialing and communicating by telephone, and network access modes are automatically chosen. According to the network telephony processing method for the smart mobile terminal, the advantages of the network call are fully performed to lower the communication cost, the complexity of network users, network coverage, network quality and network charges is also completely considered at the present stage, application schemes which are simpler and more convenient to use are provided for the user, and conditions are created for establishing further converged communication.
Owner:黄晓峰
Trusted energy-saving data convergence method for wireless sensor network
InactiveCN102438298ASave energyProlong survival timePower managementEnergy efficient ICTMobile wireless sensor networkWireless mesh network
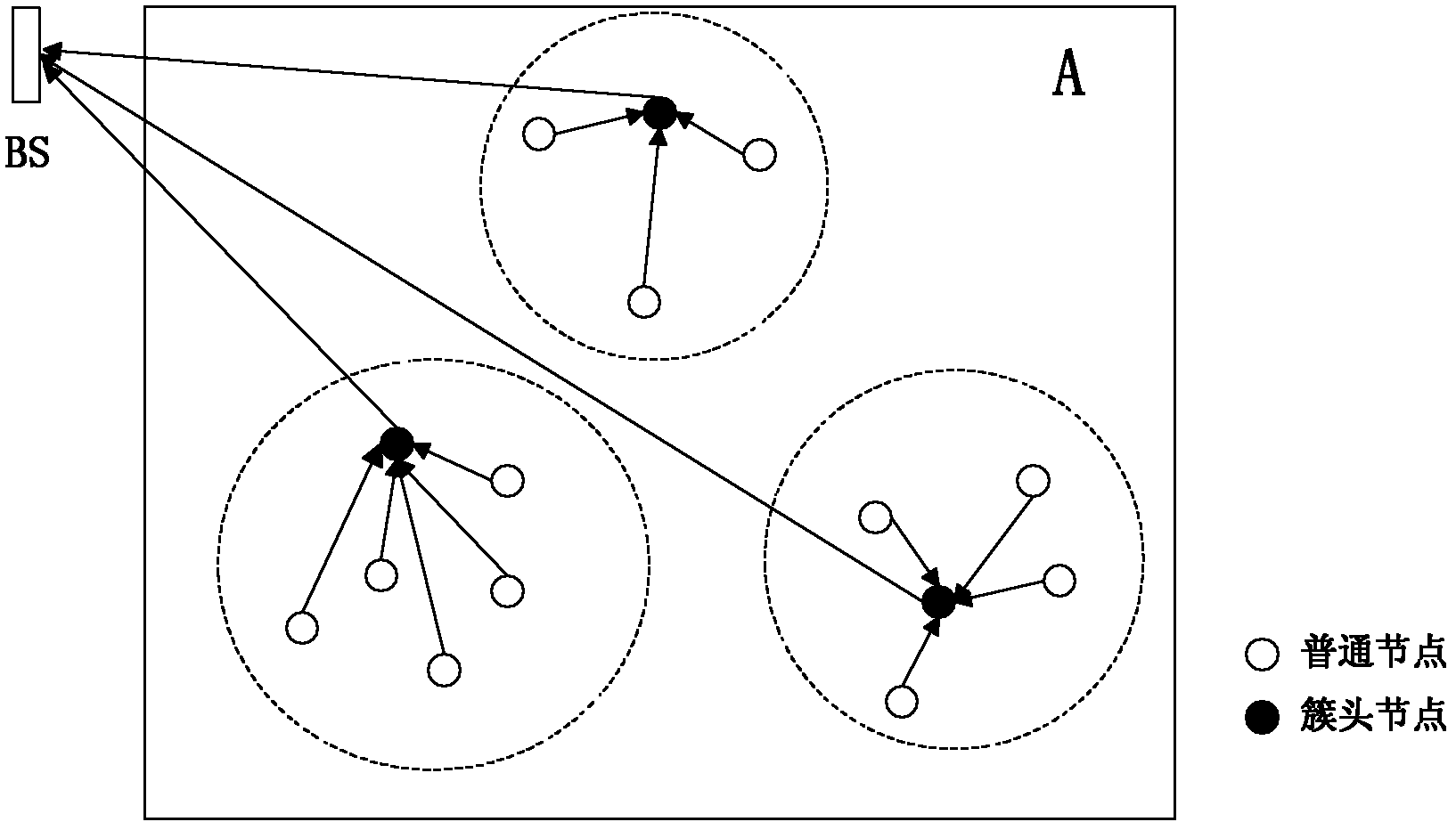
The invention discloses a trusted energy-saving data convergence method for a wireless sensor network. The method comprises the following steps of: cluster head election, cluster migration and sensor node clearing-up, wherein all uncovered nodes are taken as cluster head nodes or become multi-hop member nodes of other clusters through neighbor nodes to finish node convergence. By the energy-saving data convergence method, the energy load of the whole network is equally allocated to each sensor node, and simultaneously, a data convergence technology is utilized to reduce energy consumption, eliminate data redundancy and increase available information streams from a source node to a base station, thereby fulfilling the aim of prolonging the service life of the whole network.
Owner:李千目
Two-tiered wireless sensor network range query method capable of verifying privacy protection
ActiveCN104717644AGuaranteed privacy and securityAchieving verifiabilityNetwork traffic/resource managementData switching networksPrivacy protectionNetwork communication
The invention discloses a two-tiered wireless sensor network range query method capable of verifying privacy protection. The two-tiered wireless sensor network range query method capable of verifying privacy protection includes the data collection protocol step and the query execution and verification protocol step. The data collection protocol step includes the procedures that sensor data are periodically collected by sensor nodes and subjected to bucket partitioning, data buckets are encrypted, verification code information of redundant buckets is worked out, corresponding data messages are constructed and uploaded to storage nodes, and the data messages are collected and then stored through the storage nodes. The query execution and verification protocol step includes the procedures that query instructions containing minimum tag sets corresponding to target zones are constructed by a base station and sent to the storage nodes, the storage nodes execute query processing and return corresponding query feedback messages, the base station decrypts the feedback messages and works out final query results, and finally query result consistency is verified. The protocol steps of the method are simple, privacy security of sensitive data can be guaranteed, and the query results can be verified; the in-network communication cost of the sensor nodes is low, and prolonging of the life cycle of a whole network is facilitated.
Owner:NANJING UNIV OF POSTS & TELECOMM
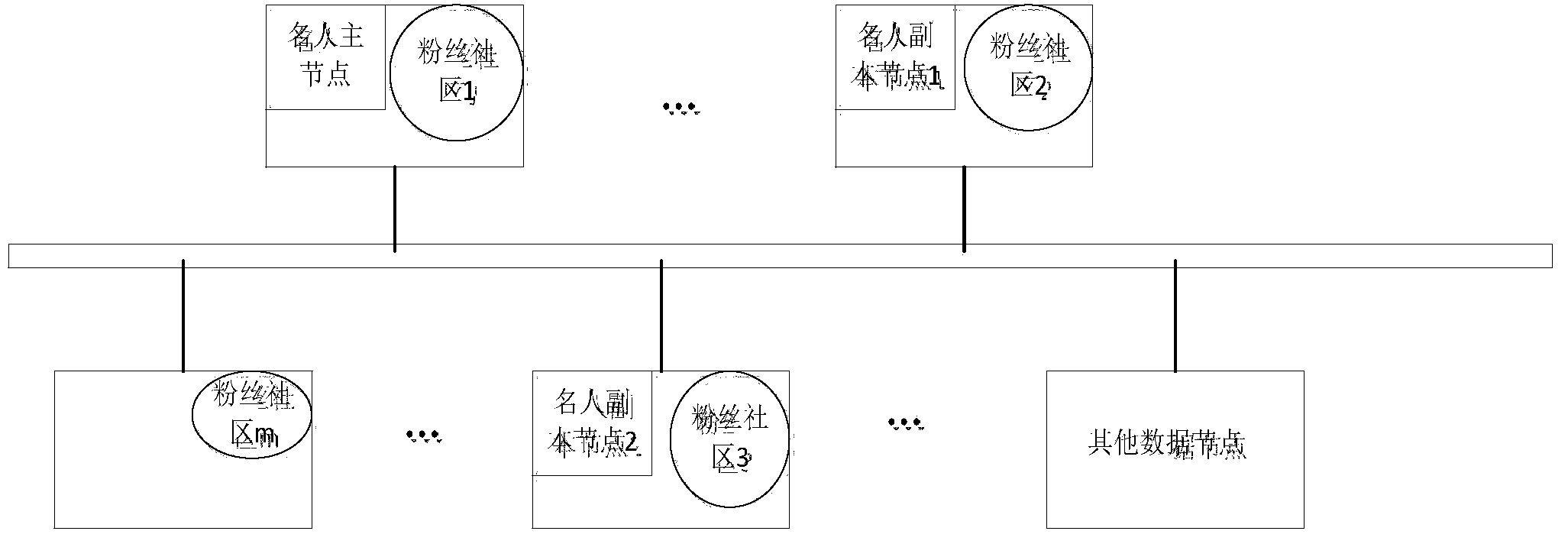
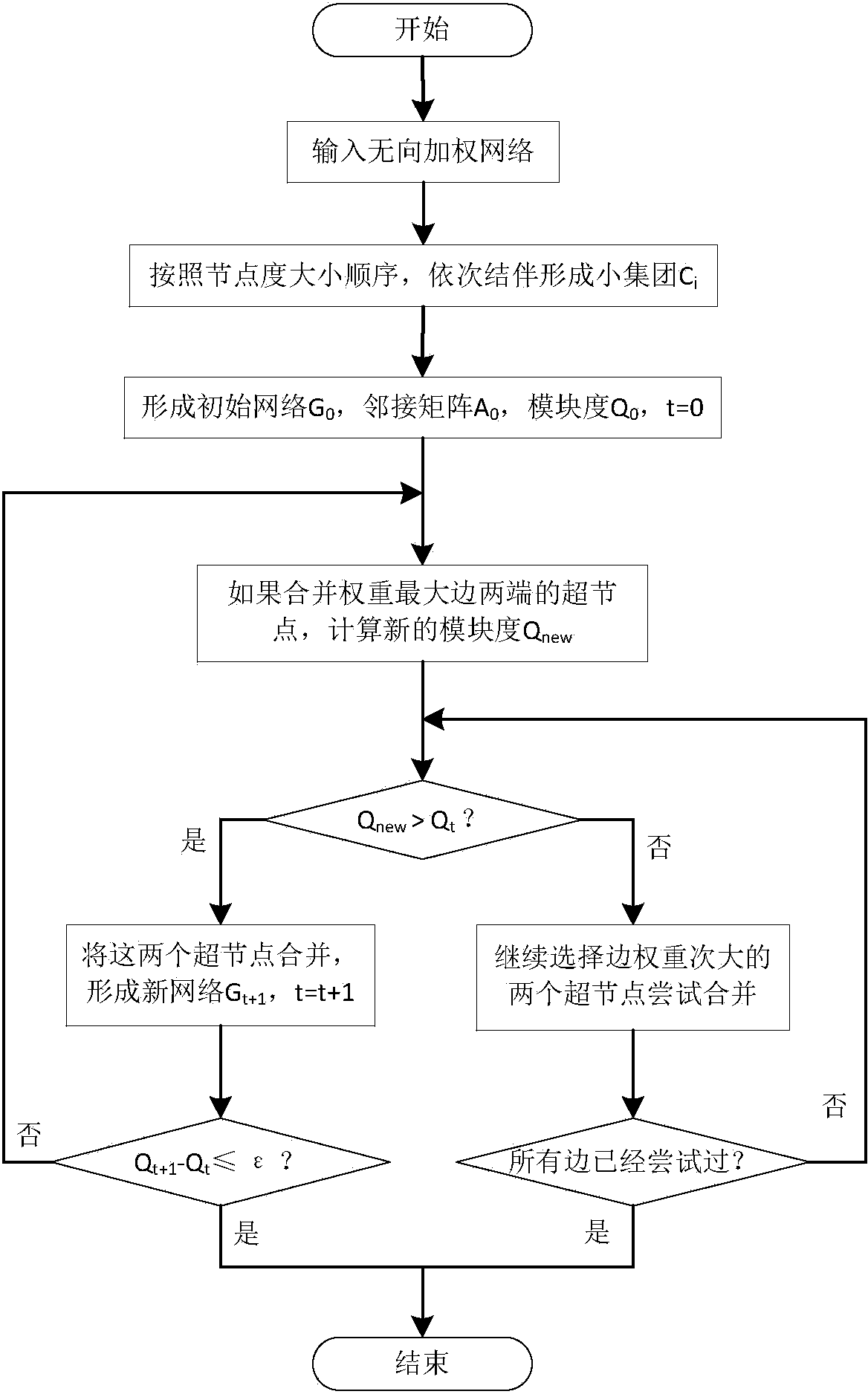
On-line social network mass data storage method based on community division
InactiveCN103838831AReduce communication costRelieve pressureData processing applicationsTransmissionCommunity basedModularity
The invention discloses an on-line social network mass data storage method based on community division. With a graph structure of a social network serving as the starting point, firstly, the social network is divided into a celebrity user layer and a common user layer according to node degrees, and then the community division is conducted on each layer through a modularity optimization method. A small group forming strategy is designed to preprocess an initial network, a supernet is formed, and an edge weight optimization scheme is adopted for merging super nodes step by step so as to improve the modularity. After the community division is completed, common user data are stored preferentially, user data of the same community are stored in the same server node, celebrity user data are preferentially considered to be stored in the server with the most fans, and then the celebrity user data are secondly considered to be stored in the server node where the community of the celebrity user data are located. By the design that the celebrity user data are stored in a multi-replication mode, the load of a single server is reduced; since social network data are stored through the community division method, the locality of access can be improved, and communication expenditure can be reduced.
Owner:SOUTHEAST UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com