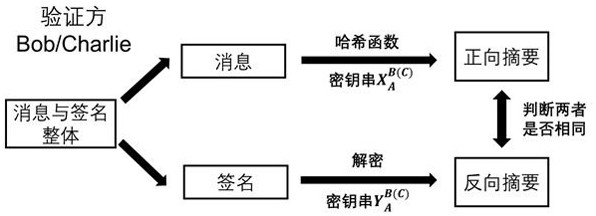
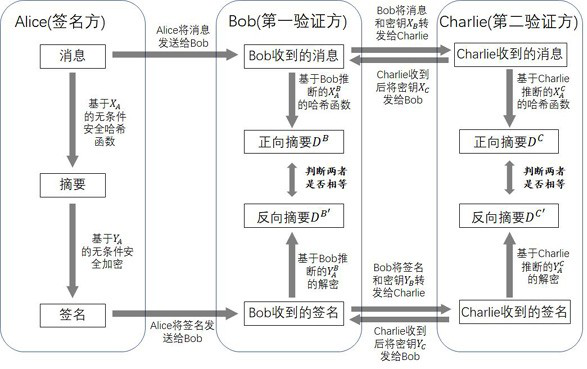
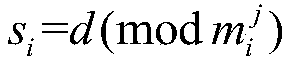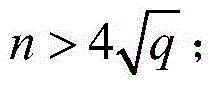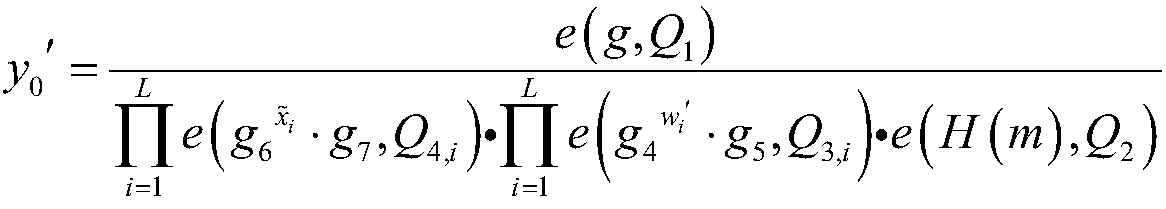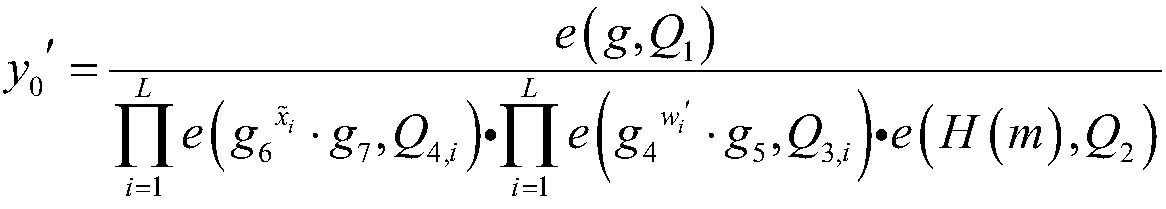Patents
Literature
60results about How to "Improve signature efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Block chain asset transaction transfer method based on weighted threshold signature algorithm
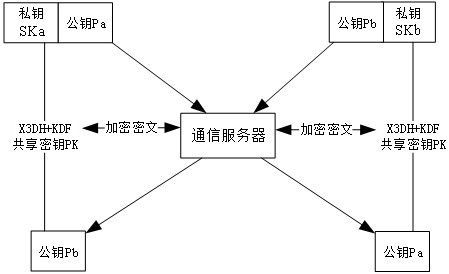
ActiveCN109377360AOvercoming the Disadvantages of LeakageImprove securityKey distribution for secure communicationFinanceChinese remainder theoremBlockchain
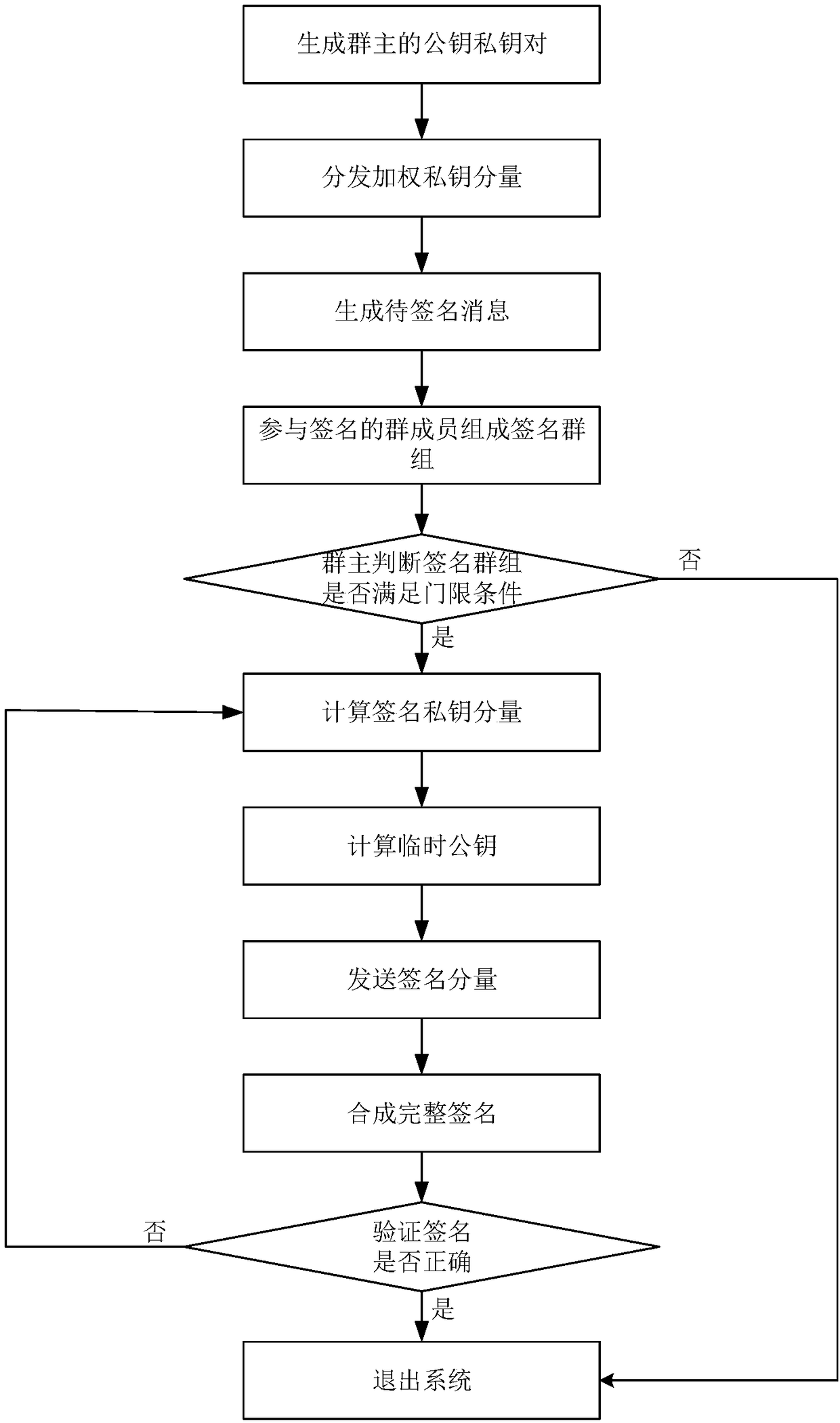
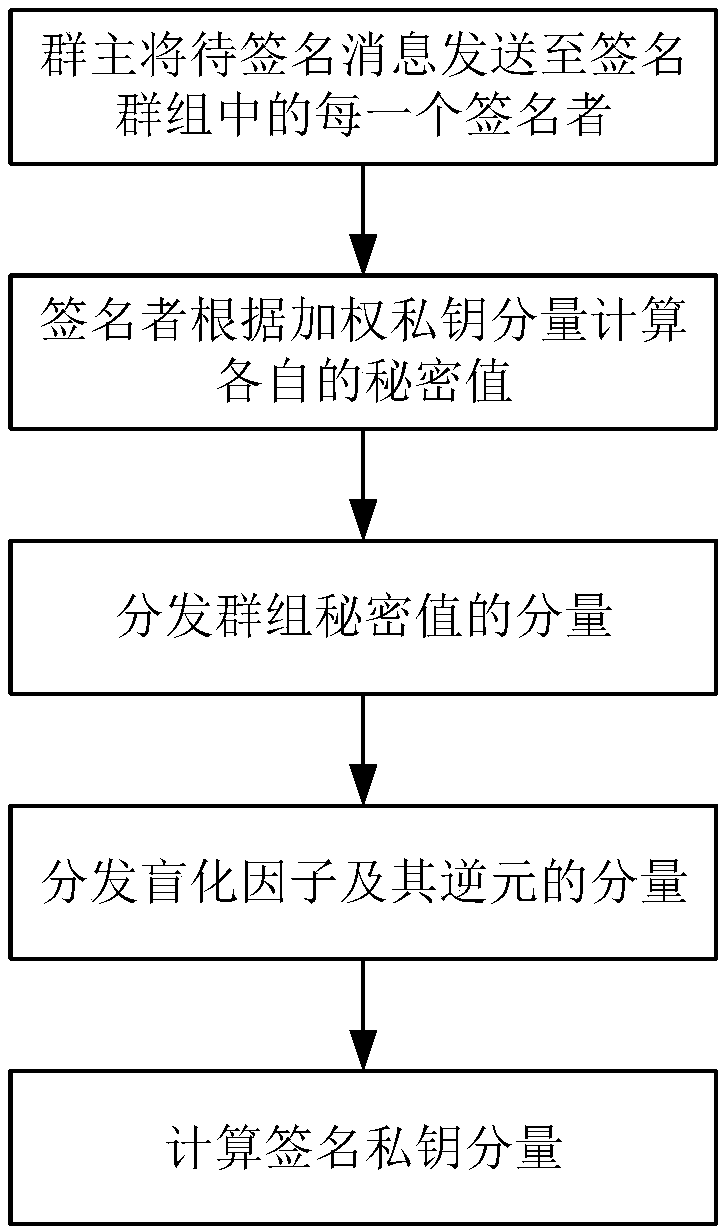
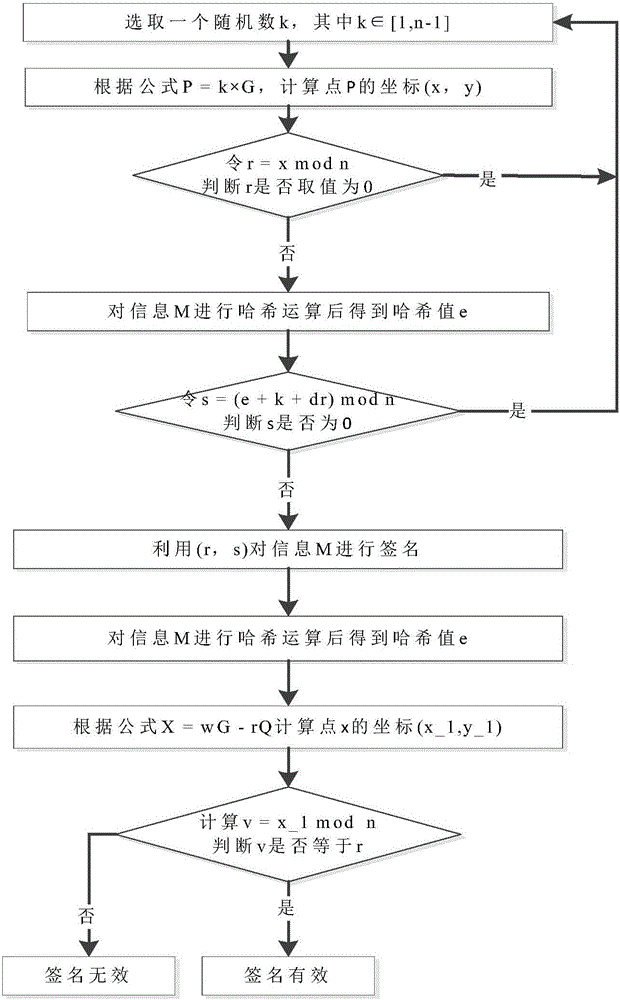
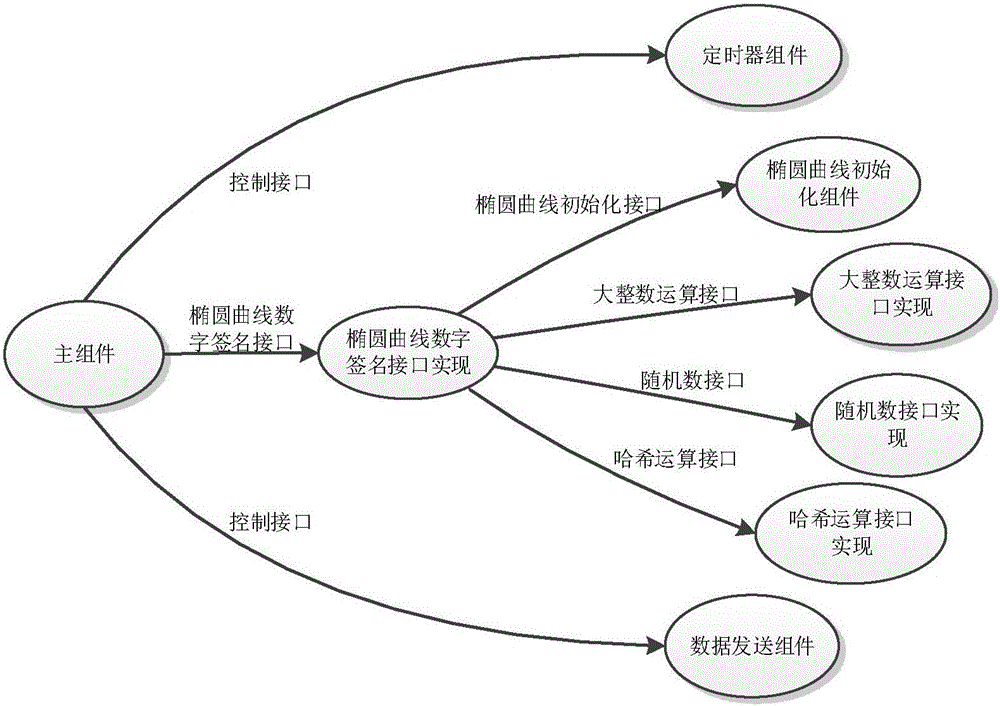
The invention discloses a block chain asset transaction transfer method based on a weighted threshold signature algorithm. The specific implementation steps include: 1, generating a public-key privatekey pair of a group master; 2, distributING a weighted private key component; 3, generatING a message to be signed; 4, a plurality of group memberS form a signature group; 5, that group mast judges whet the signature group satisfies the threshold condition; 6, calculatING a signature private key component; 7, calculatING a temporary public key; 8, sending a signature component; 9, synthesizing acomplete signature; 10, verifying that signature; 11. Exiting the system. The invention adopts threshold signature algorithm, reduces the risk of private key disclosure, and guarantees the security ofblock chain asset transaction transfer. A weighted secret sharing technique based on Chinese Residue Theorem (CRT) is used to improve the efficiency of signature generation algorithm.
Owner:XIDIAN UNIV
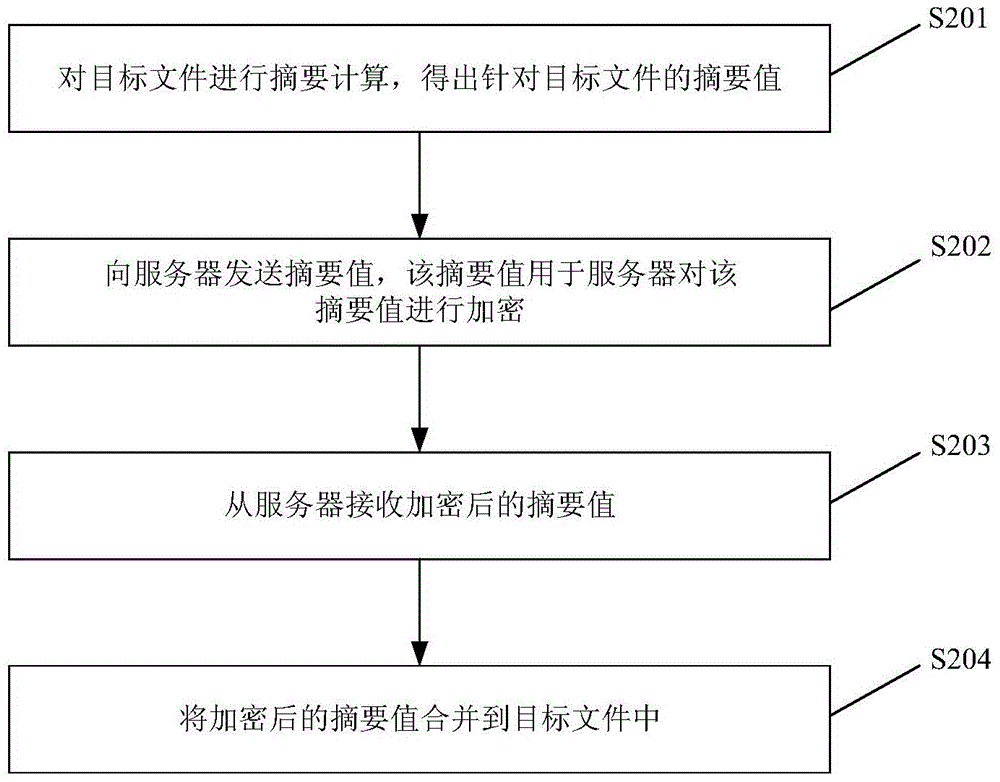
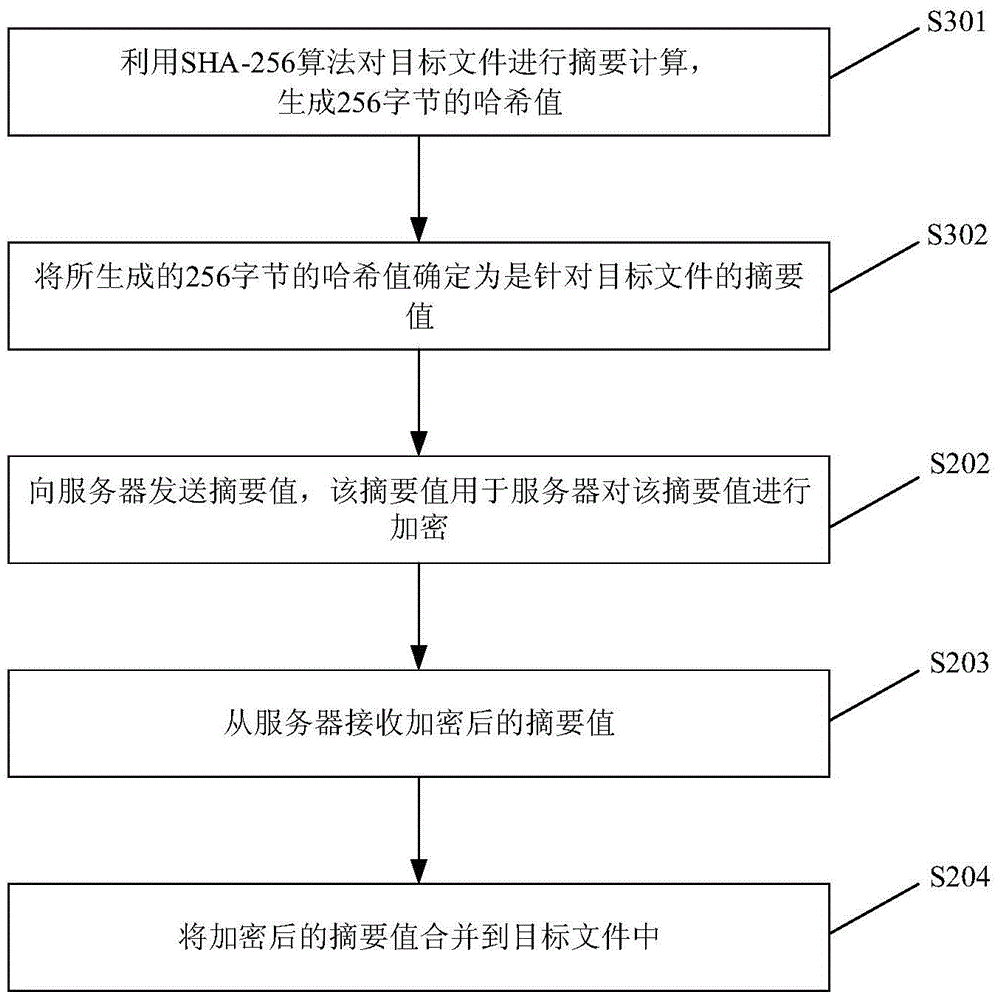
File signature method and device
InactiveCN105049213ATroubleshoot file signing issuesReduce message trafficUser identity/authority verificationInformation transmissionComputer science
The disclosure relates to a file signature method. The method is applied to a client and the method comprises the steps as follows: performing abstract calculation on a target file to obtain an abstract value of the target file; transmitting the abstract value to a server, wherein the abstract value is used by the server to encrypt the abstract value; receiving an encrypted abstract value from the server; and combining the encrypted abstract value into the target file. Therefore, the problem that the client needs to upload the whole target file to the server for file signature is solved, and the effects of reducing the information transmission amount between the client and the server and improving signature efficiency are achieved.
Owner:XIAOMI INC
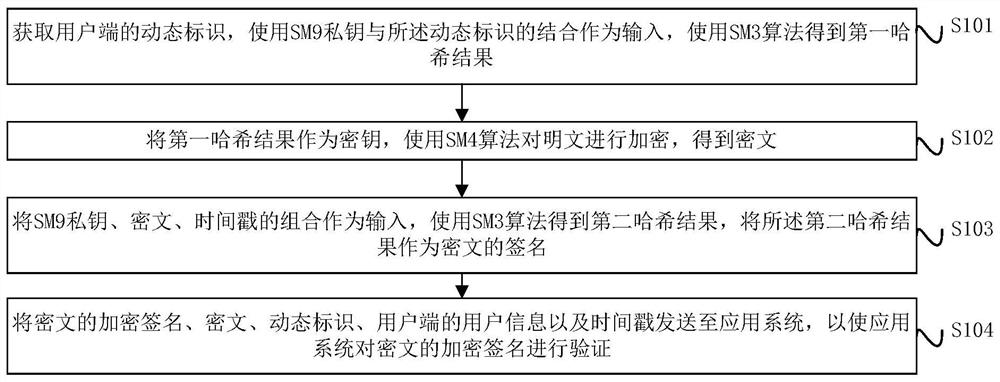
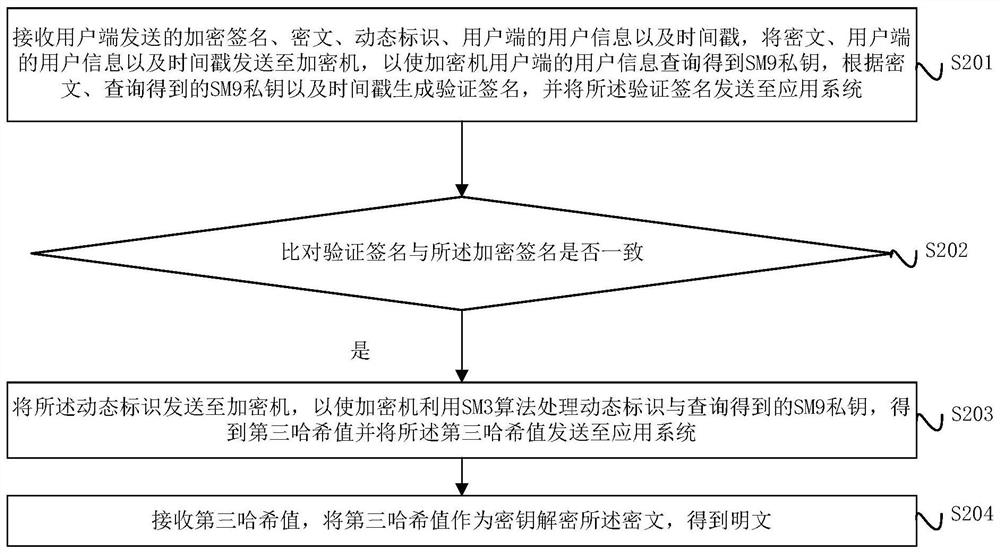
Digital signature and verification method, device and system
ActiveCN112688784AIncrease computing speedImprove signature efficiencyEncryption apparatus with shift registers/memoriesUser identity/authority verificationPlaintextTimestamp
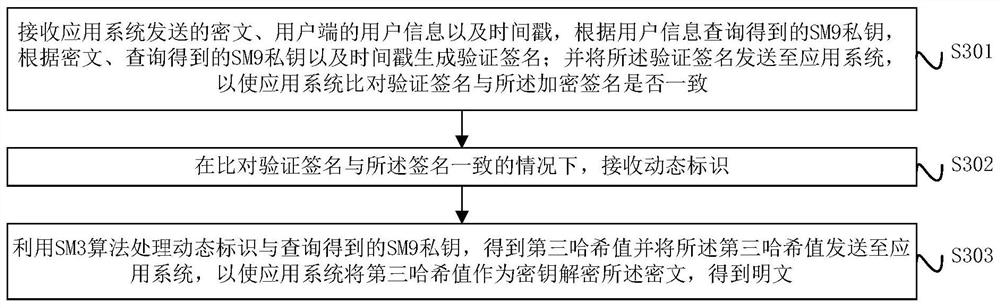
The invention provides a digital signature and a verification method, device and system, and the method comprises the steps: obtaining a dynamic identification of a user side, taking the combination of an SM9 private key and the dynamic identification as an input, and obtaining a first hash result through an SM3 algorithm; taking the first hash result as a key, and encrypting the plaintext by using an SM4 algorithm to obtain a ciphertext; taking a combination of the SM9 private key, the ciphertext and the timestamp as input, obtaining a second hash result by using an SM3 algorithm, and taking the second hash result as an encrypted signature of the ciphertext; and sending the encrypted signature of the ciphertext, the ciphertext, the dynamic identifier, the user information of the user side and the timestamp to an application system, so that the application system verifies the encrypted signature of the ciphertext.
Owner:中科美络科技股份有限公司
Multiple signature generation and verification system and method thereof
InactiveCN103095697AReduce communication costImprove signature efficiencyUser identity/authority verificationSignature fileValidation methods
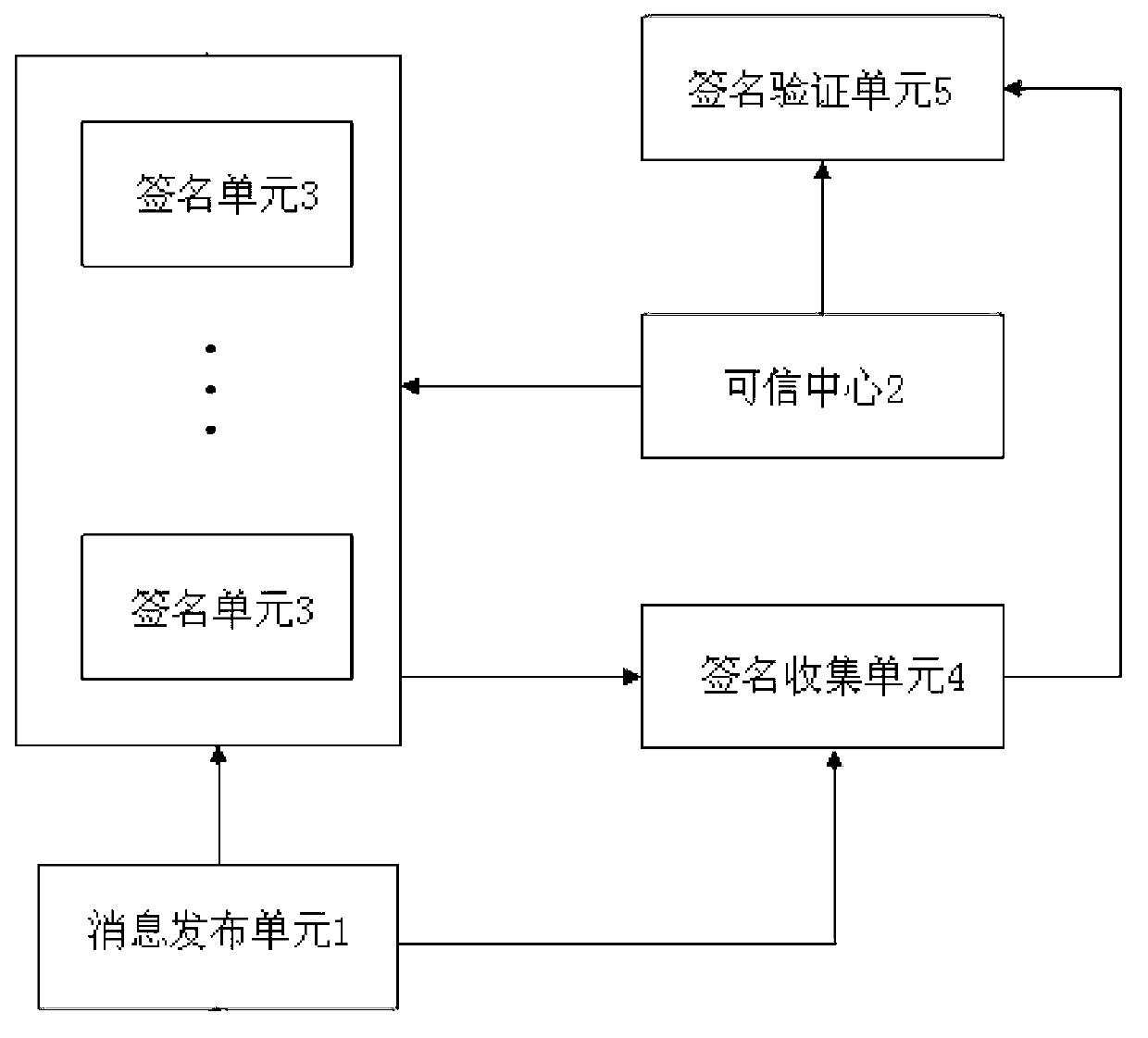
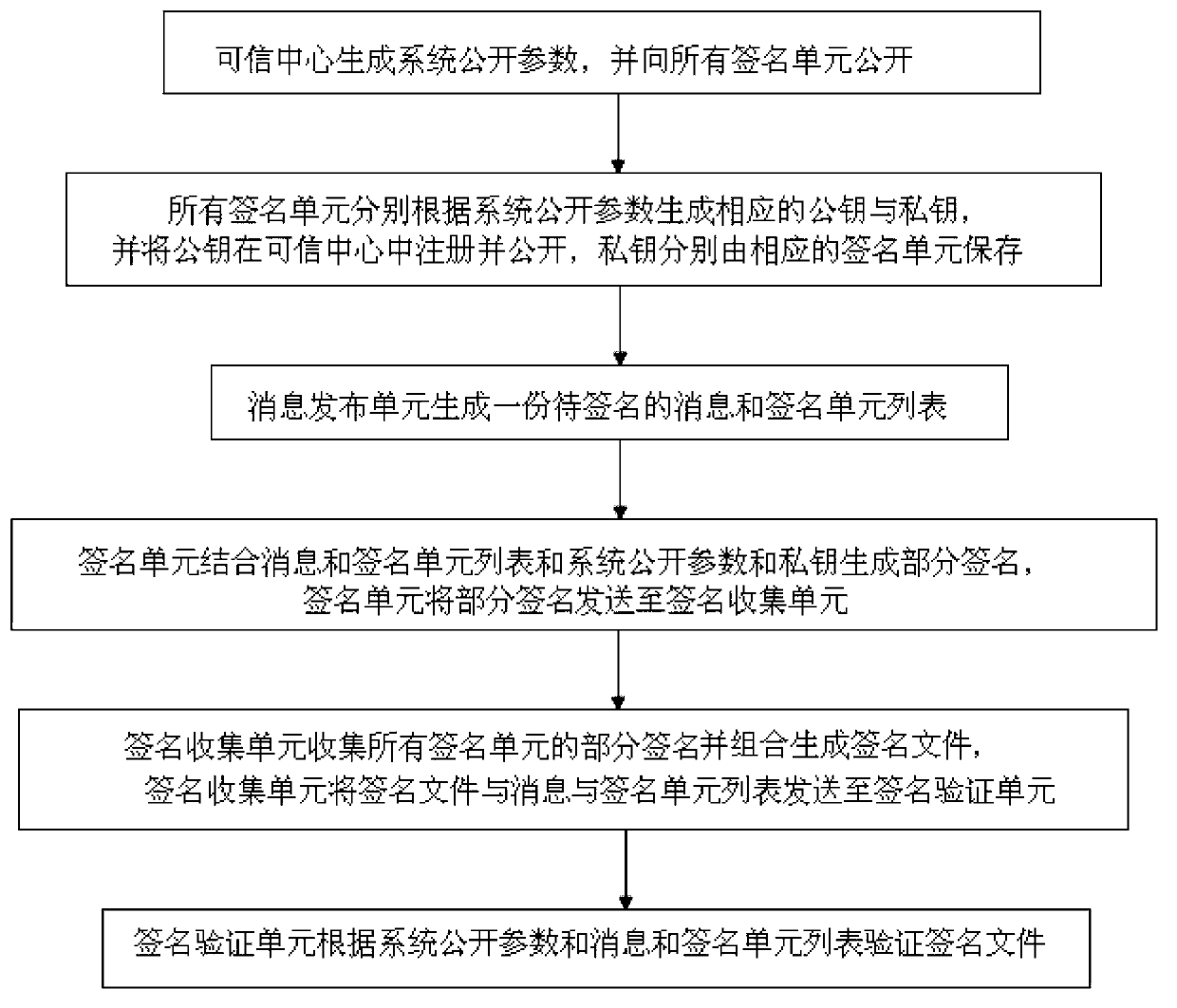
The invention discloses a multiple signature generation and verification system and a method thereof. The multiple signature generation and verification system comprises an information releasing unit, a credible center, at least one signature unit, a signature collection unit and a signature verification unit. The information releasing unit generates information to be signed, and a signature unit listing used for signing. The credible center generates system public parameters. At least one signature unit is connected with the information releasing unit and the credible center in a communication mode and is used for generating a public key and a private key and generating corresponding partial signatures. The signature collection unit is connected with the information releasing unit, the signature unit and the signature verification unit in a communication mode. The signature verification unit is connected with the credible center and the signature collection unit in a communication mode and is used for verifying signature files according to the public parameters, the signature unit listing and the information. According to the multiple signature generation and verification system, each signature unit independently generates the partial signatures of the each signature unit, and the system is free from interaction, low in communication cost, and high in signing efficiency. The invention further discloses the multiple signature generation and verification method.
Owner:EAST CHINA NORMAL UNIV +1
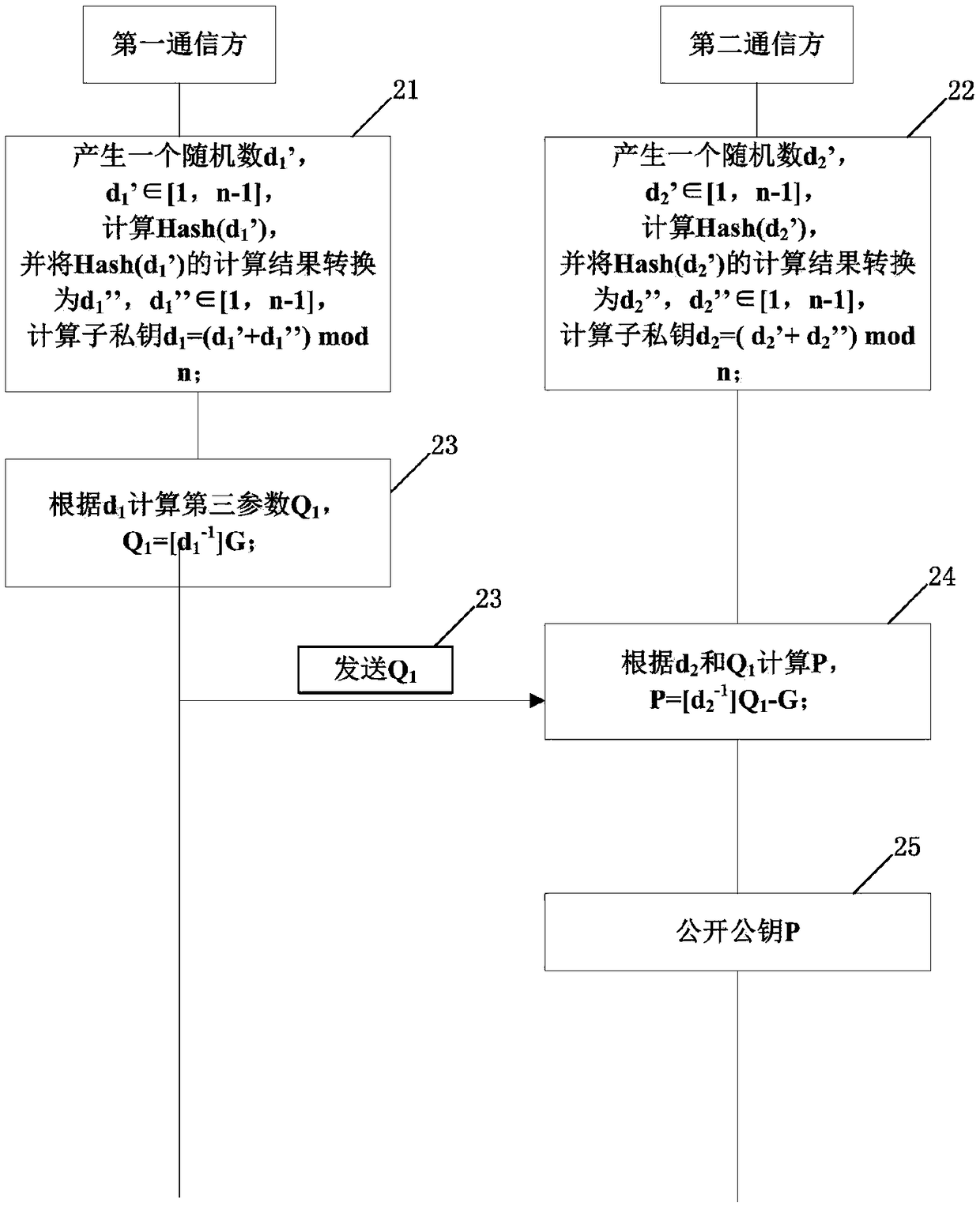
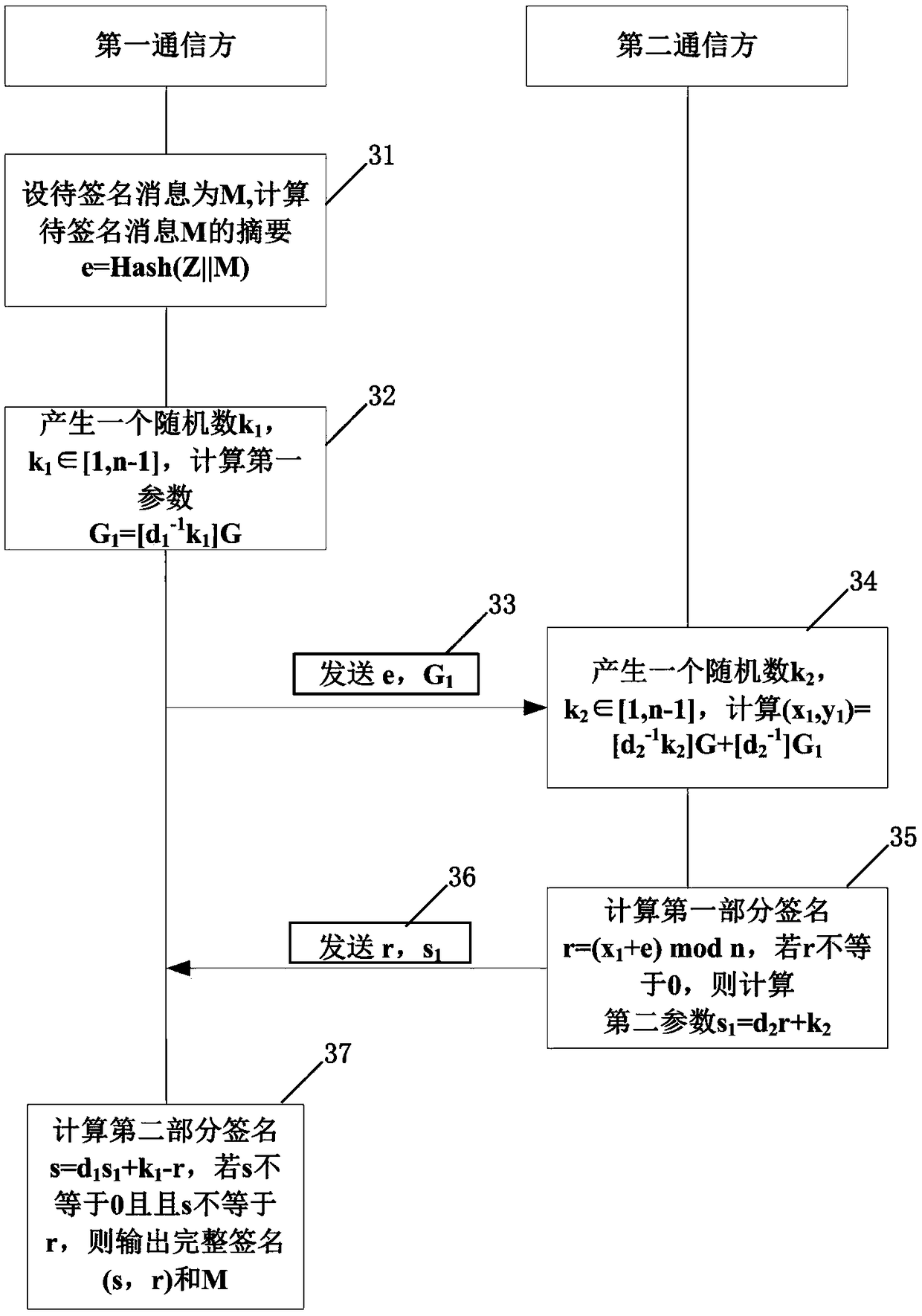
SM2-based both side signature method and system
ActiveCN109450640AReduce data trafficReduce the amount of data calculationPublic key for secure communicationUser identity/authority verificationCiphertextInformation security
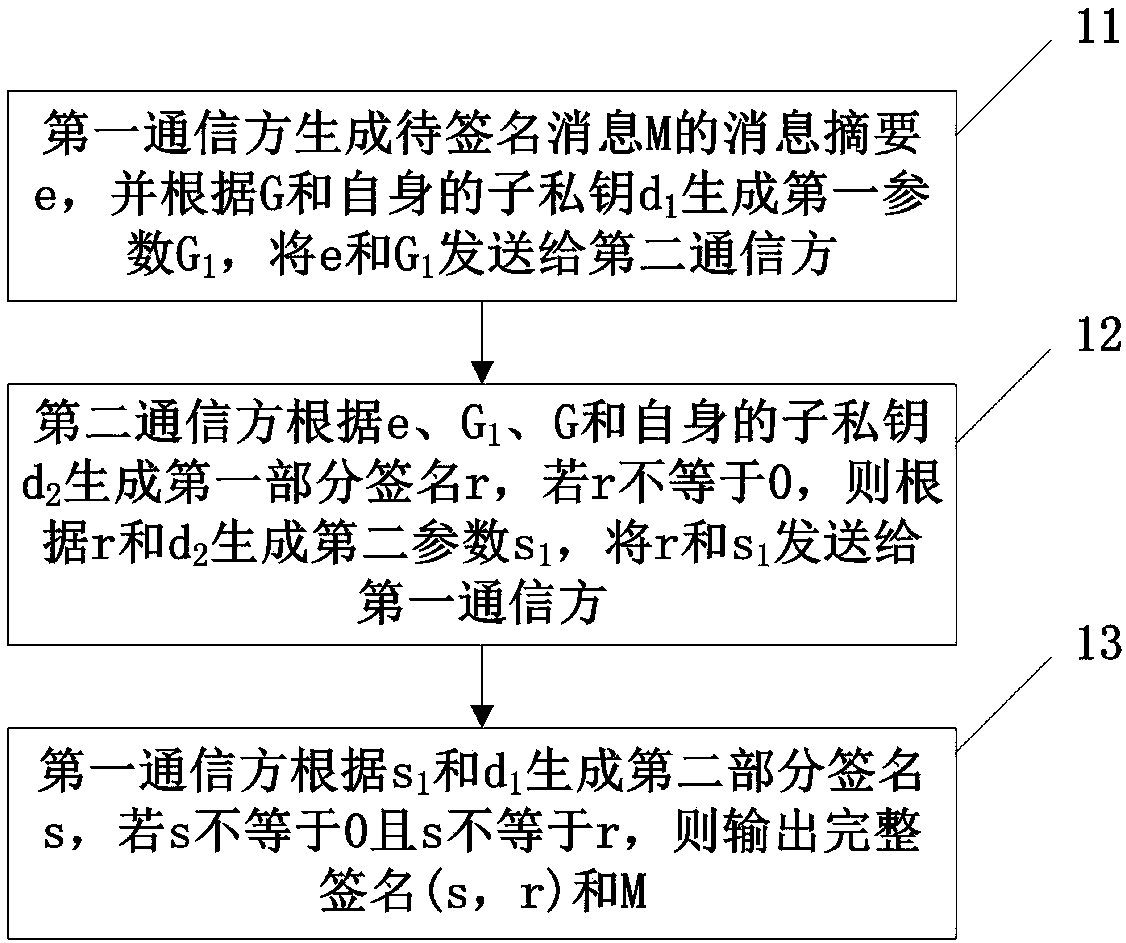
The invention relates to the technical field of information security, and the embodiment discloses an SM2-based both side signature method and system. By adoption of the technical scheme provided by the invention, a part of private key can be separately stored in both communication sides, a signature or decryption and other operations can only be performed on a message by the cooperation of the both sides, neither of the both communication sides can obtain any information of the private key of the other side, therefore an attacker cannot forge the signature or decrypt the ciphertext if invading any of the both sides, and the both communication sides need to transmit two data to the opposite side in the signature interaction, so that the data communication traffic and the data calculation amount are low, and the signature efficiency is higher.
Owner:中电科网络安全科技股份有限公司
Remote data integrity verification method based on short signature
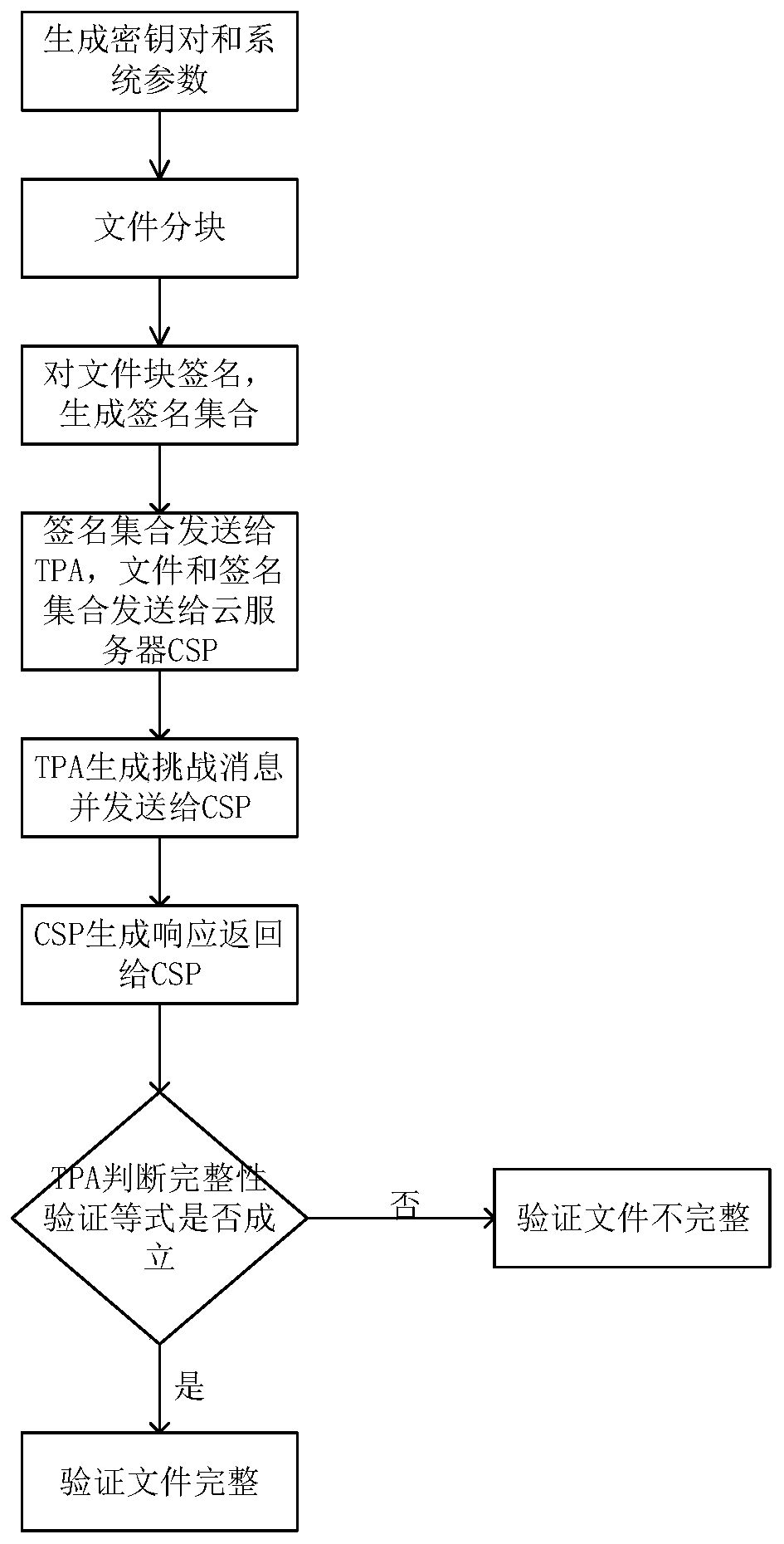
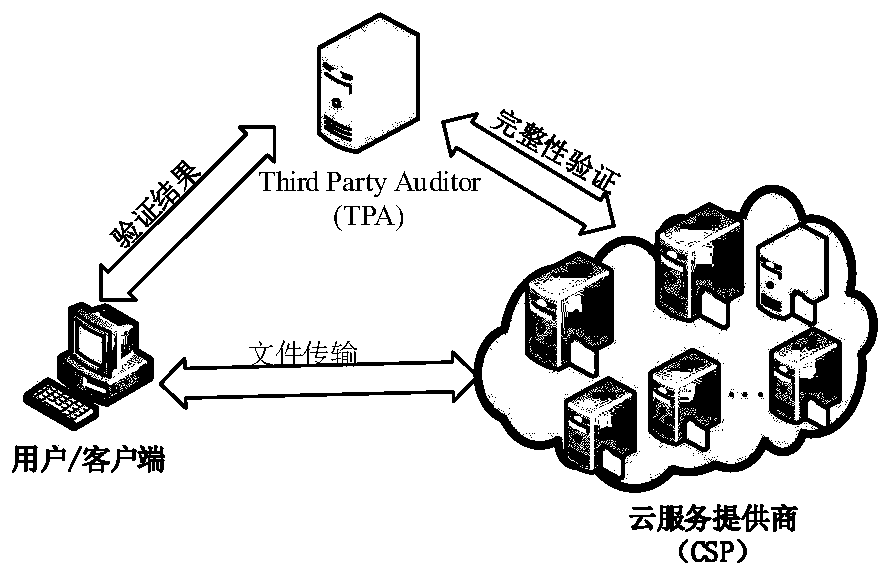
InactiveCN109951296AImprove signature efficiencyReduce computational overhead and communication overheadUser identity/authority verificationDigital data protectionPhases of clinical researchChallenge response
The invention provides a remote data integrity verification method based on a short signature. The method comprises the following steps: in a preprocessing stage, a client generates public and privatekey pairs and system parameters, and carries out blocking processing on a file to be uploaded to a cloud storage server; signing each file block by using a short signature algorithm; uploading the file and the signature set to a cloud storage server, and sending the signature set to a trusted third party; and in a challenge-response stage, the third party generates challenge information and sendsthe challenge information to the cloud server, and the server generates data holding evidences and returns the data holding evidences to the third party; and in a verification stage, the third partyverifies whether the data holding evidence is correct or not by using a verification algorithm, if so, the TRUE explains that the file is stored completely, or else, the FLSE explains that the storedfile is damaged. In order to solve the problems of low signature efficiency and low security in the prior art, a short signature and a trusted third party are used to reduce the calculation overhead of a client, an anti-collision hash function and a random masking technology are adopted to protect data privacy in a verification process, and analysis shows that the method can resist an adaptive selection message attack.
Owner:BEIJING UNIV OF POSTS & TELECOMM +2
Digital signature method, device and cipher device
ActiveCN106712965AReduce correlationResistance to linear attacksUser identity/authority verificationLow speedDigital signature
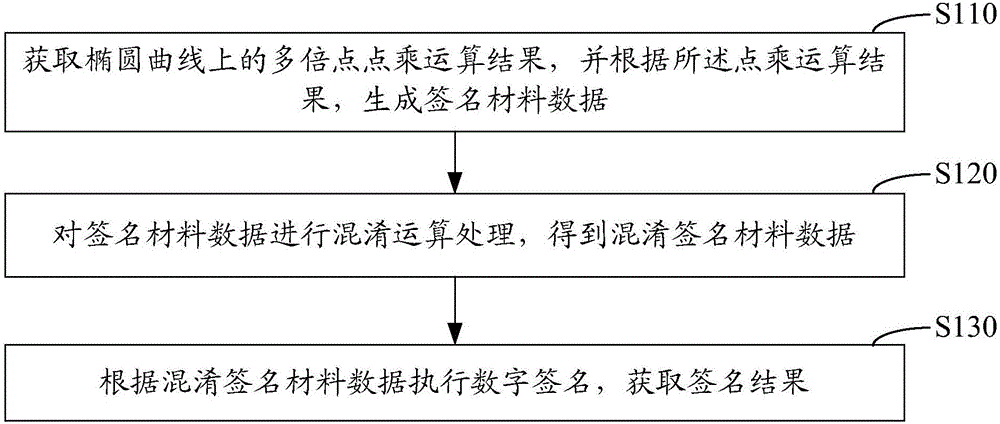
The invention relates to a digital signature method, device and cipher device. The digital signature method comprises the steps of obtaining multi-point multiplication operation results on an elliptic curve and generating signature material data according to the multi-point multiplication operation results; carrying out mixing operation processing on the signature material data, thereby obtaining mixed signature material data; and carrying out digital signature according to the mixed signature material data, thereby obtaining a signature result. According to the method and the devices, the mixed operation based on point addition is carried out on the known multi-point operation results, thereby resisting a linear attack and obtaining high enough operation efficiency. On the basis of random numbers generated by a low-speed hardware device and the multi-point multiplication operation results, more multi-point operation results are generated through adoption of the mixing algorithm, and the signature efficiency is improved. Through adoption of the mixing algorithm, the correlation among the mixing output results is relatively low, and the linear attack can be effectively resisted.
Owner:GUANGDONG CERTIFICATE AUTHORITY
Lightweight digital signature method facing wireless sensing network
ActiveCN105025474AGood choiceImprove securityNetwork topologiesSecurity arrangementDigital signatureSecret code
The invention discloses a lightweight digital signature method facing a wireless sensing network based on an elliptic curve cryptography mechanism. The method comprises the following steps: initializing a parameter, establishing a public and private key pair, generating a digital signature, and verifying the signature. By utilizing a deformation of a signature equation in a digital signature verification step for the elliptic curve cryptography mechanism, time-consuming modular inversion operation in original signature generation and verification is changed into additive operation, and a TinyECC 2.0 function library after multiple optimization is introduced at the same time, so operation for ECCs is simple and is easy to understand, the lightweight digital signature method has high safety performance, and generation and verification processes of the digital signature has the advantages of the small computation amount and the fast speed.
Owner:ANHUI UNIVERSITY
System for approving electronic contract and method therefor
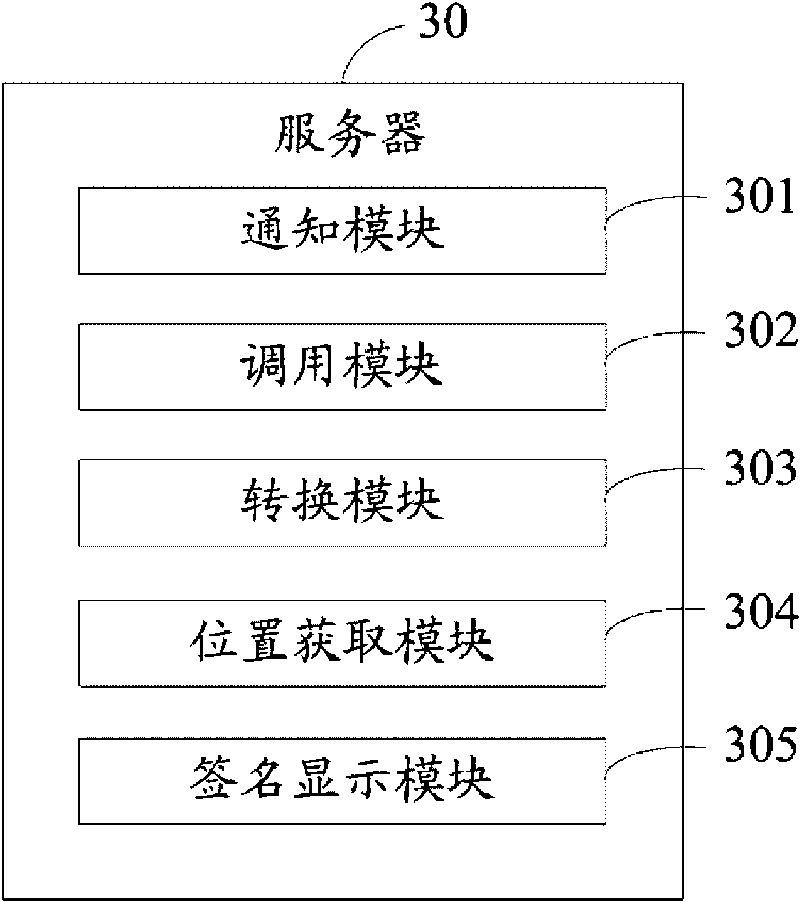
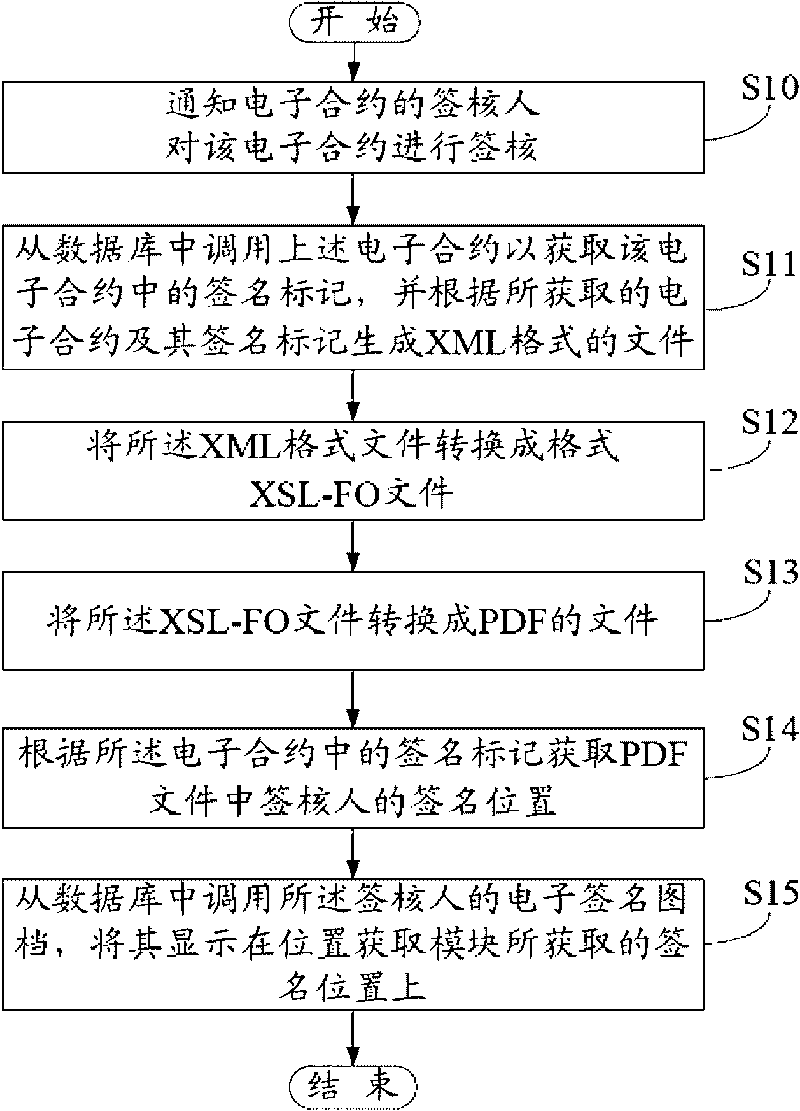
InactiveCN101751612AFlexible signatureImprove signature efficiencySemi-structured data mapping/conversionSpecial data processing applicationsElectronic contractsDatabase
A method for approving an electronic contract comprises the steps as follows: when in request of approving the electronic contract, the approver of the electronic contract is notified of approving the electronic contract, when the approver receives the above notification, the electronic contract is retrieved from a database so as to obtain the signature in the electronic contract, an XML file is generated according to the obtained electronic contract and the signature, the XML file is converted into an XSL-FO file which is then converted into a PDF file, and the PDF file is a PDF contract. The signature location of the approver in the PDF contract can be obtained according to the signature in the electronic contract, and the electronic signature drawing of the approver is retrieved from the database and is displayed at the signature location.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
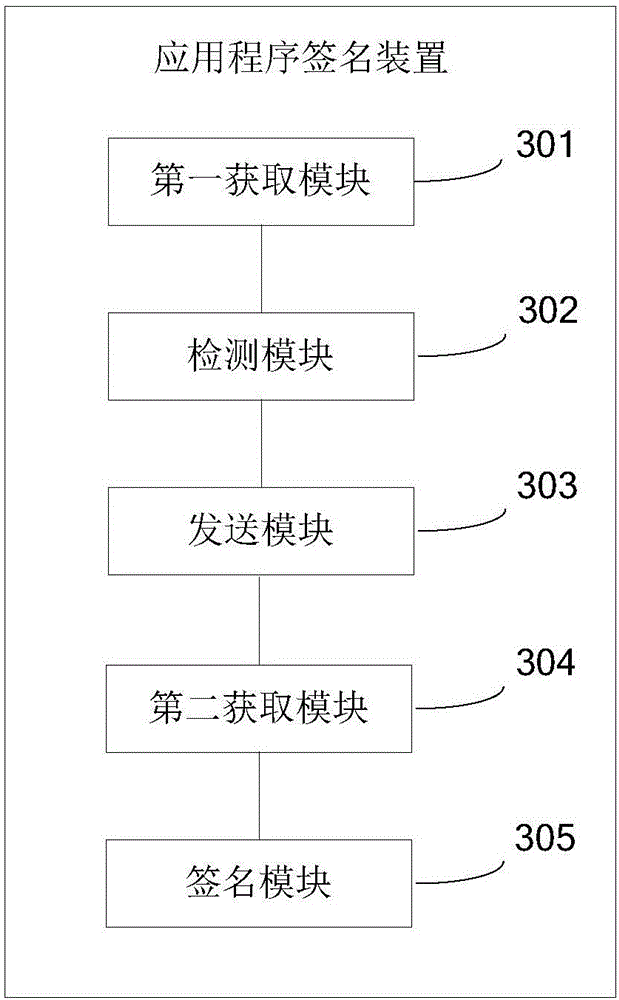
Application program signing method and application program signing device
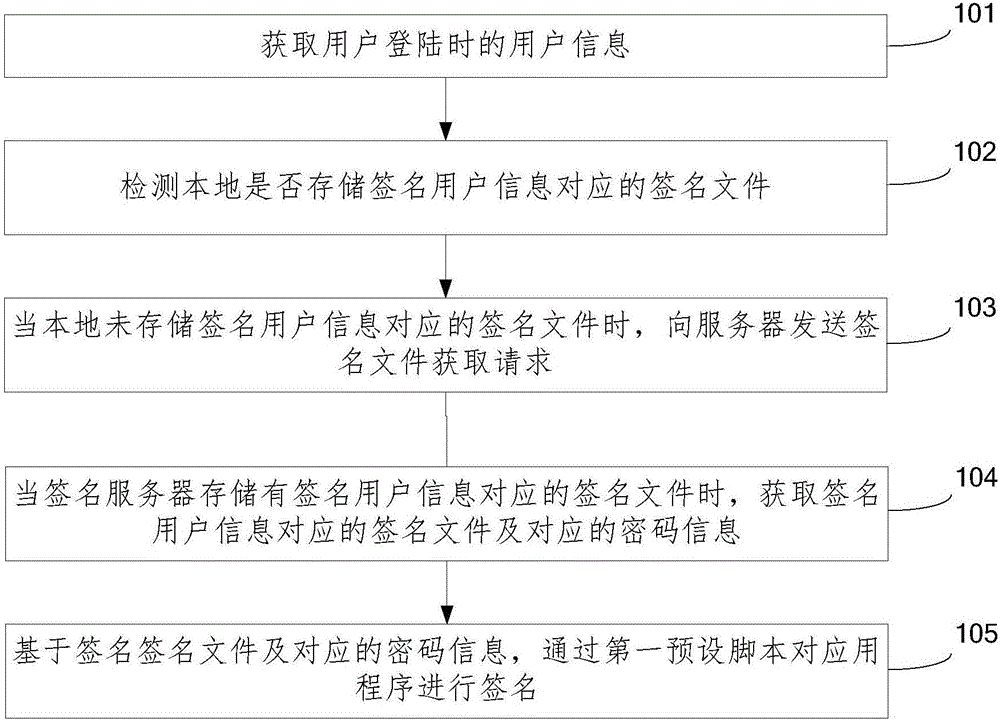
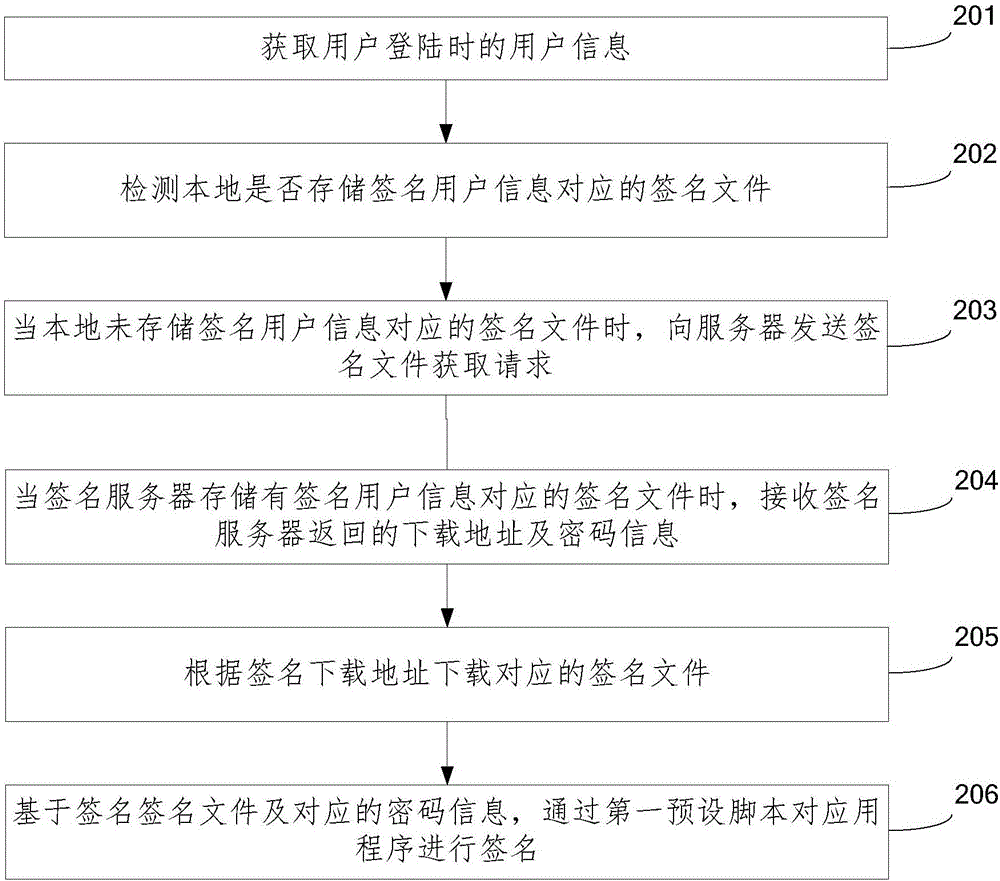
ActiveCN106559223AImprove execution efficiencyImprove securityUser identity/authority verificationSignature filePassword
The invention provides an application program signing method and an application program signing device, which belong to the technical field of computers. The method comprises steps: user information when a user logs in is acquired; whether a signature file corresponding to the signature user information is stored locally is detected; when the signature file corresponding to the signature user information is not locally stored, a signature file acquisition request is transmitted to the server; when the signature file corresponding to the signature user information is stored in the server, the signature file corresponding to the signature user information and corresponding password information are acquired; and based on the signature file and the corresponding password information, the application program is signed through a first preset script. As the whole signature process is packaged, the signature process is thus simple and the signature efficiency is high. Besides, as the signature file and the corresponding password information are backed up to the server, the safety of the signature file and the safety of the password information are thus improved. Finally, through carrying out alignment optimization on the signed application program, the application program execution efficiency can be improved.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Quantum digital signature method
ActiveCN113297633AUnconditional Security GuaranteedImprove signature efficiencyQuantum computersDigital data protectionComputer hardwareDigital signature
The invention discloses a quantum digital signature method, and belongs to the technical field of quantum security. In order to solve the problem that in the prior art, the security of a digital signature protocol and the efficiency of signing a message are generally not high, the invention provides a quantum digital signature method which comprises the following three steps: preparing a secret key, generating a signature and verifying the signature. The technical scheme provided by the invention is a real unconditional security scheme, solves the problem of low efficiency of the existing unconditional security digital signature protocol, has strong compatibility, can be realized by using various systems, can be realized in the current system, can be harmonious and free in the future quantum internet system, and has very strong application range and prospect in the present stage and in the future.
Owner:NANJING UNIV +1
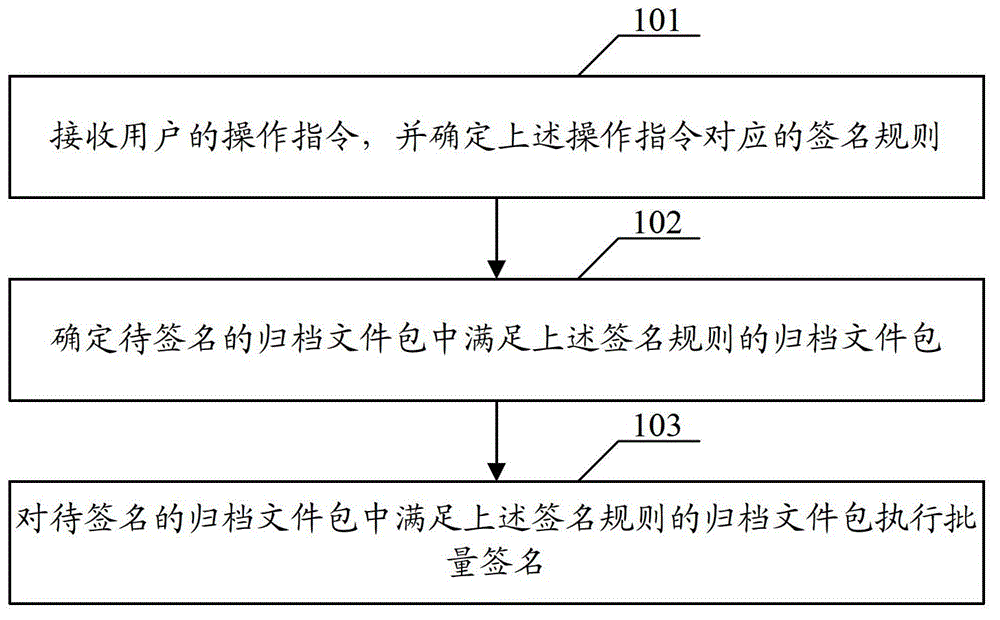
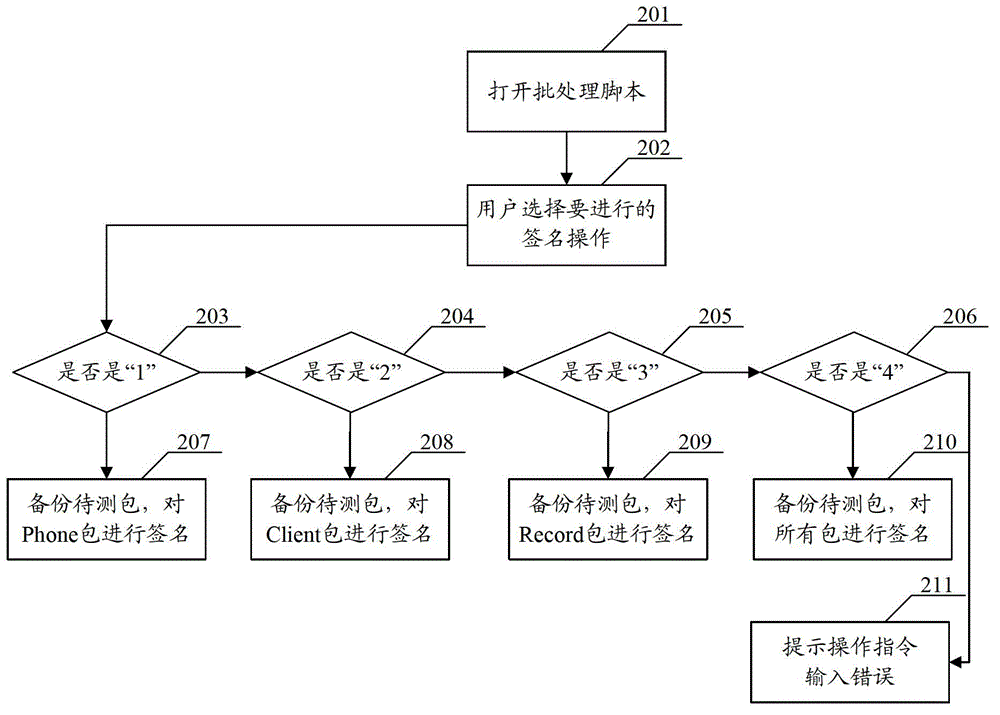
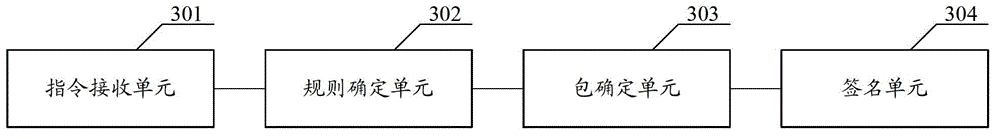
Archived file package signing method and device
InactiveCN104376235AImprove signature efficiencyProgram/content distribution protectionSpecific program execution arrangementsArchive fileUser input
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data processing method, device and equipment and storage medium
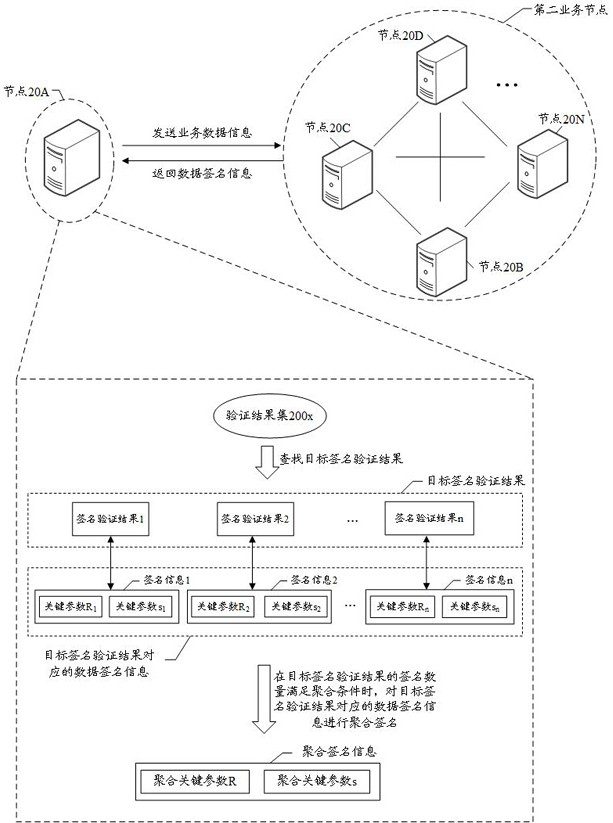
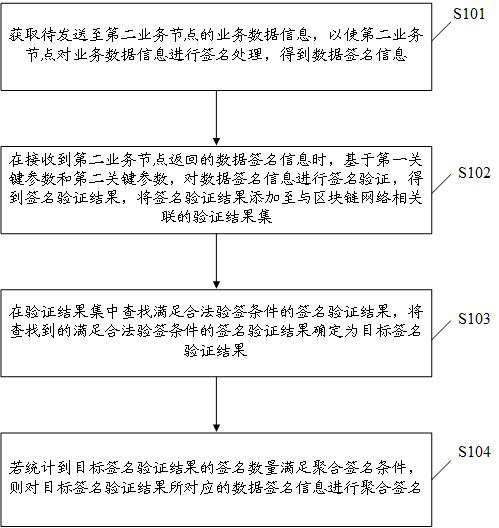
ActiveCN112600671AReduce interactionImprove signature efficiencyKey distribution for secure communicationUser identity/authority verificationBusiness dataTarget signature
The embodiment of the invention discloses a data processing method and device, equipment and a storage medium; the data processing method comprises the steps: transmitting, by a first business node, business data information to a second business node, so as to enable the second business node to obtain data signature information, wherein a first key parameter and a second key parameter in the datasignature information are related to the random parameter, and the random parameter is jointly determined by the second service node based on the node private key and the service data information; performing signature verification on the received data signature information based on the first key parameter and the second key parameter, and adding a signature verification result obtained by signature verification to a verification result set; searching a target signature verification result meeting a legal signature verification condition in the verification result set; and if the number of signatures of the target signature verification result meets the aggregation signature condition, performing aggregation signature on the counted data signature information. By adopting the embodiment ofthe invention, the network complexity of the aggregation signature can be reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Attribute base network signature method supporting dynamic attractive space
InactiveCN108777626AAvoid problems reinitializing the systemSave resourcesKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAccess structureGranularity
The invention discloses an attribute base network signature method supporting the dynamic attractive space, and belongs to the field of information security. The method is mainly characterized in thata layering technology (including an attribute layer and a secret shearing layer) is used for realizing the dynamic attribute space structure; in the attribute layer, an attribute authorizing center AA uses a random perturbance method for performing fuzzification processing on user attributes; when a new attribute needs to be added, the attribute authorizing center AA only needs to select a randomnumber for the attribute; the corresponding commitment is calculated and is used as a sub secret key of the attribute; the problem of initializing the system again is avoided; in the secret sharing layer, the linear secret sharing method is used for defining the visit structure for signing the message; the visit strategy supporting the fine granularity can be supported; high signature efficiencyis realized. The method has the advantages of high anonymity performance and high security; the access control functions and anonymity identity identification of cloud calculation, electronic medicinecare and the like can be effectively realized.
Owner:SOUTHWEST JIAOTONG UNIV
Medical data encryption method based on block chain
InactiveCN112635009AGuaranteed safe sharingHigh feasibilityCo-operative working arrangementsDigital data protectionMedical recordCiphertext
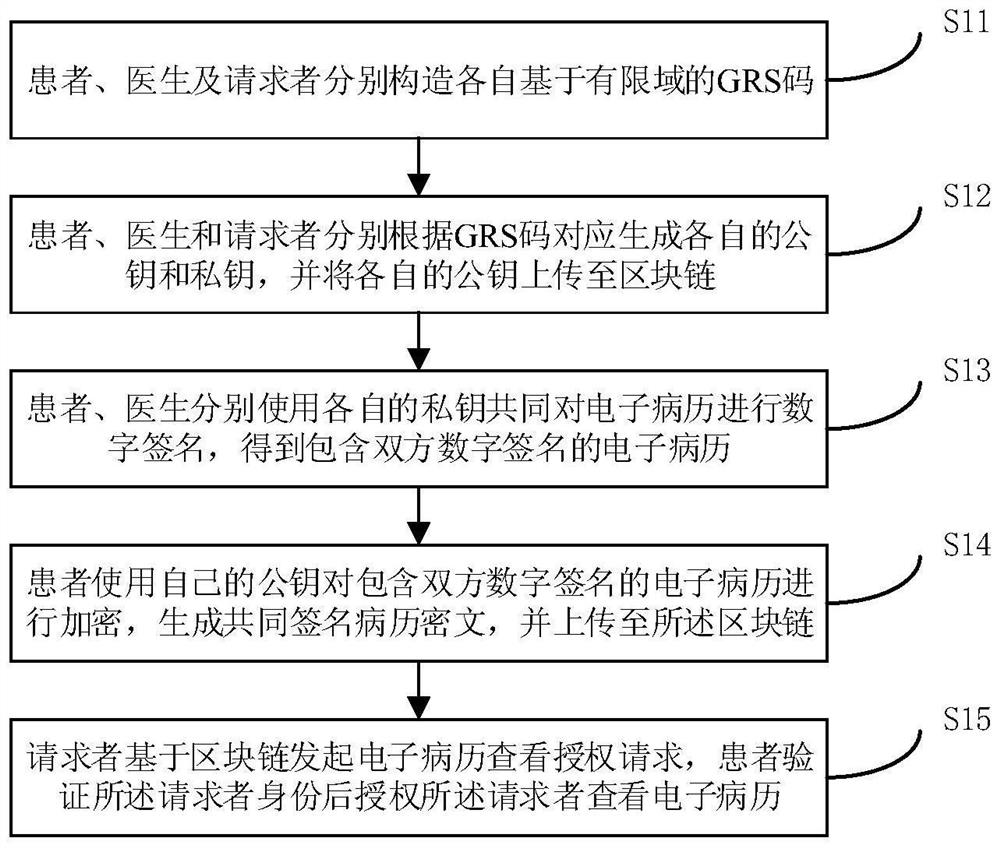
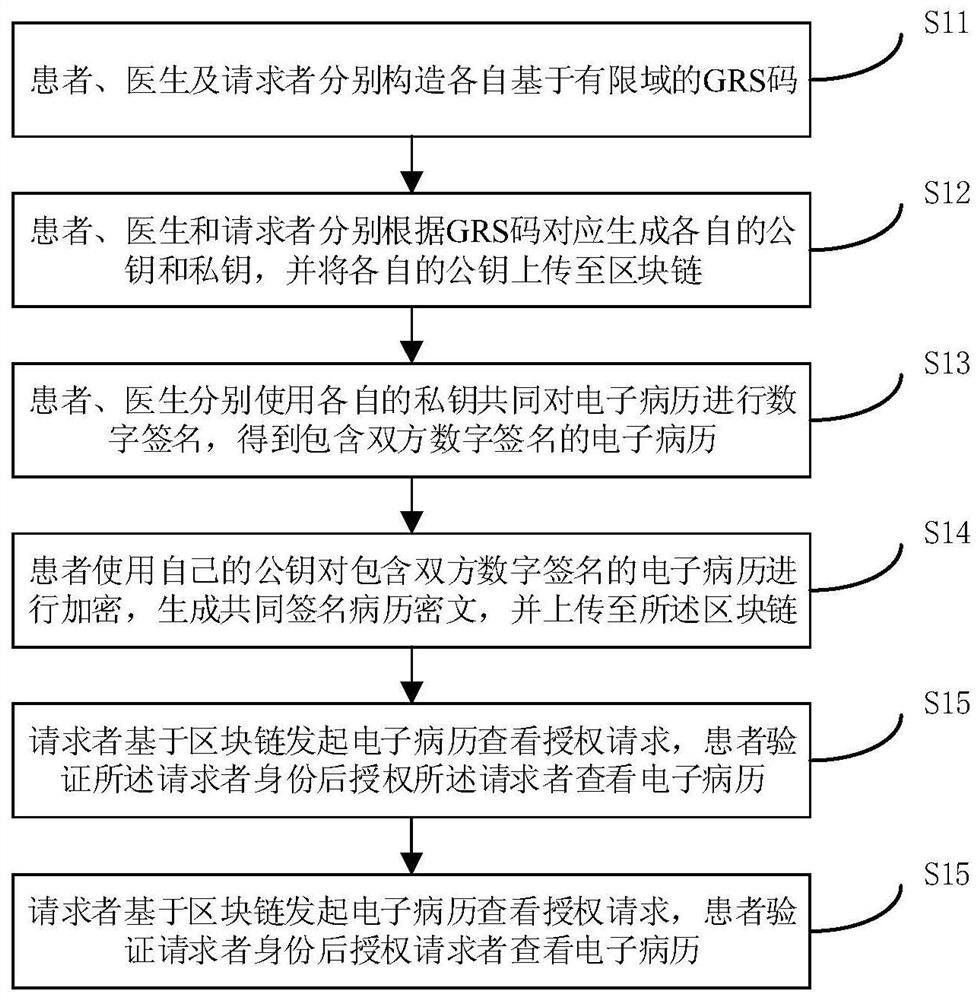
The invention discloses a medical data encryption method based on a block chain. The method comprises the steps that a patient, a doctor and a requester construct GRS codes based on finite fields respectively; the patient, the doctor and the requester correspondingly generate respective public keys and private keys according to the GRS codes, and upload the respective public keys to the blockchain; the patient and the doctor perform digital signature on the electronic medical record by using respective private keys to obtain the electronic medical record containing digital signatures of the patient and the doctor; the patient encrypts the electronic medical record containing the digital signatures of the two parties by using the own public key to generate a common signature medical record ciphertext, and uploads the common signature medical record ciphertext to the blockchain; and the requester initiates an electronic medical record viewing authorization request based on the blockchain, and the requester is authorized to view the electronic medical record after the patient verifies the identity of the requester. Based on the blockchain technology and the digital signature encryption technology, safe sharing of the medical information among different medical institutions and different doctors can be effectively ensured, and therefore, whether the medical information is tampered or leaked can be verified.
Owner:XIAN CREATION KEJI CO LTD
Improved linkable ring signature method and device, and improved linkable ring signature verification method and device
ActiveCN112118100AReduce the number of operationsImprove signature efficiencyKey distribution for secure communicationPublic key for secure communicationComputer networkRing signature
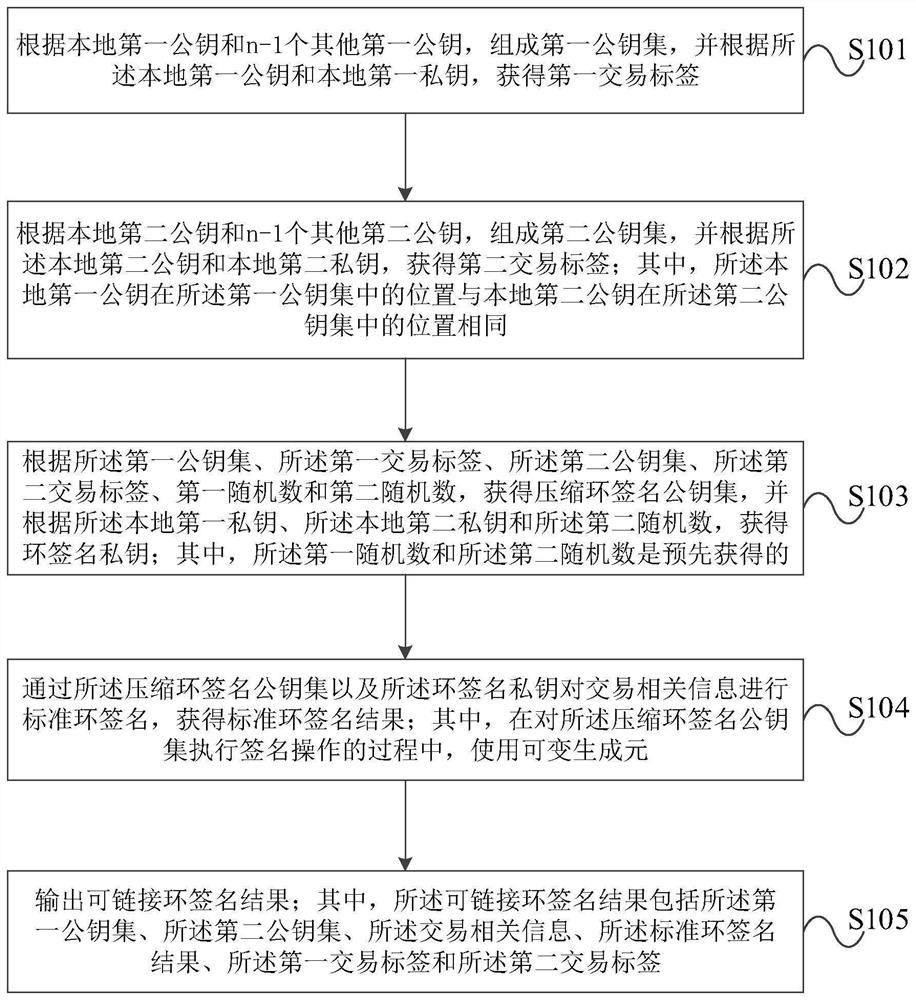
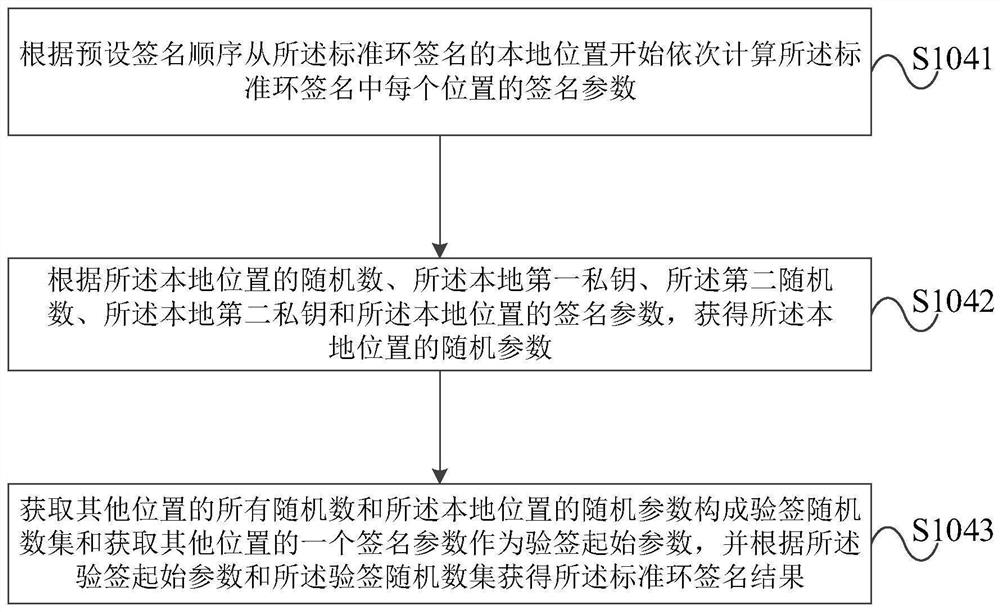
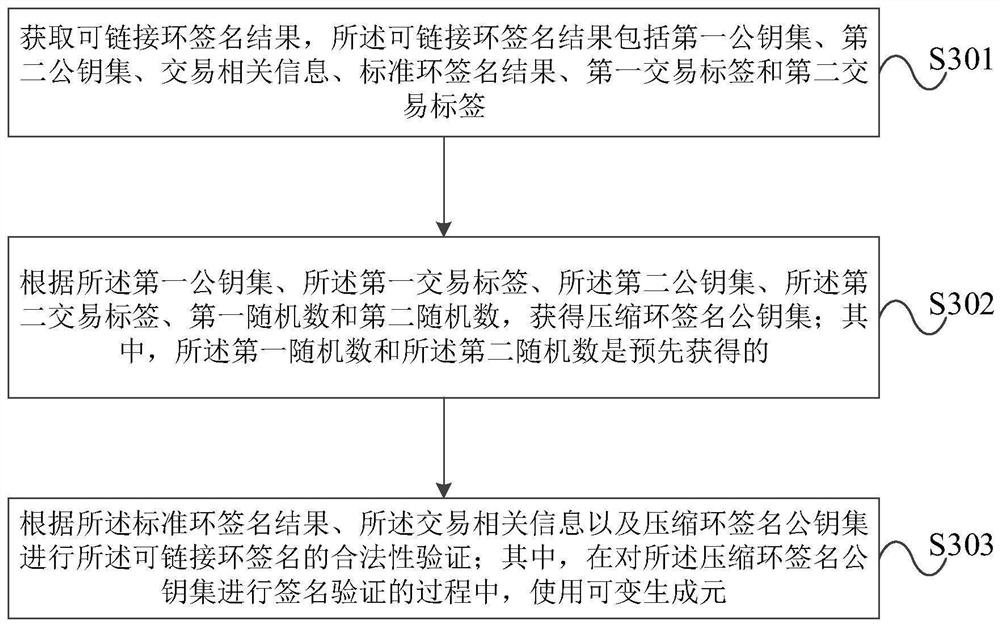
The invention provides an improved linkable ring signature method and device, and an improved linkable ring signature verification method and device. The improved linkable ring signature method comprises the steps: forming a first public key set according to a local first public key and n-1 other first public keys, and obtaining a first transaction label according to the local first public key anda local first private key; forming a second public key set according to a local second public key and n-1 other second public keys, and obtaining a second transaction label according to the local second public key and a local second private key; obtaining a compression ring signature public key set, and obtaining a ring signature private key according to the local first private key, the local second private key and a second random number; performing standard ring signature on the transaction related information by the compression ring signature public key set and the ring signature private key to obtain a standard ring signature result; and outputting a linkable ring signature result. The device is used for executing the method. According to the improved linkable ring signature method anddevice, the improved linkable ring signature verification method and device provided by the embodiment of the invention, the signature efficiency is improved, and the signature size is effectively compressed.
Owner:CCB FINTECH CO LTD
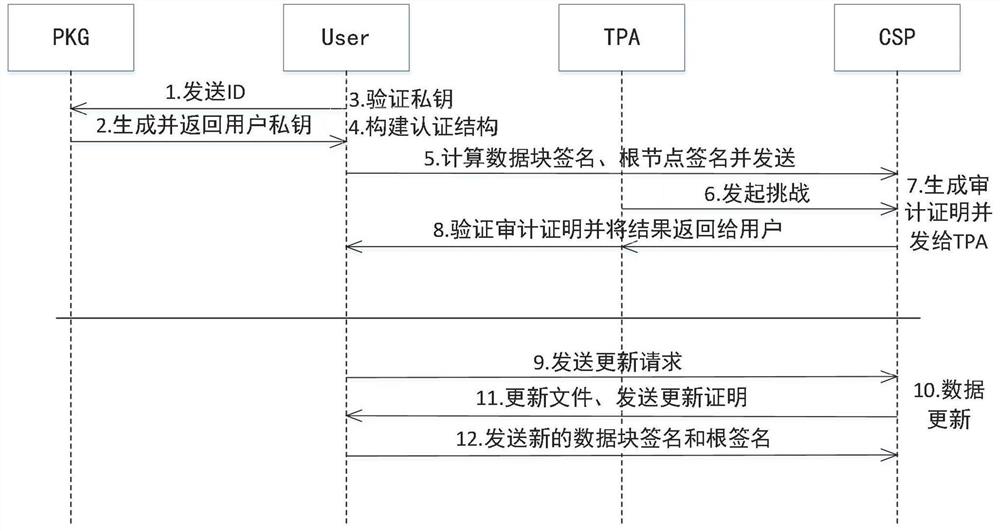
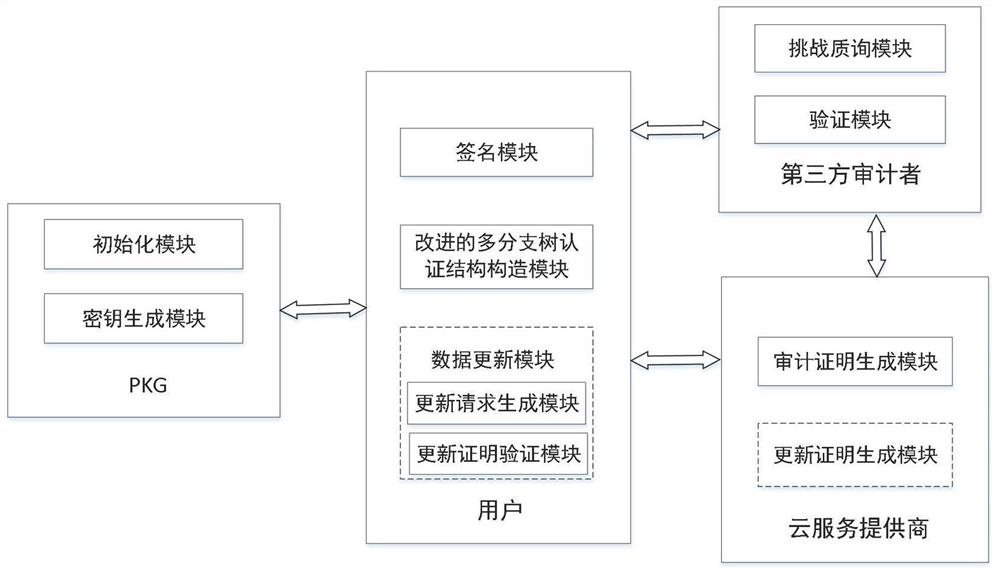
Integrity dynamic auditing method based on improved multi-branch tree in cloud environment
PendingCN113094335ARealize dynamic updateIntegrity Audit SupportDigital data protectionFile access structuresAccess frequencyEngineering
The invention discloses an integrity dynamic auditing method based on an improved multi-branch tree in a cloud environment, which comprises two parts of an identity-based dynamic integrity auditing method and an improved multi-branch tree construction method, adopts an identity-based integrity auditing architecture, and provides an improved multi-branch tree authentication structure. Data block information is stored on non-leaf nodes of an authentication tree to improve the node utilization rate, an auxiliary root node is selected to describe the integrity of the node and all descendant nodes below the node, the concept of the locality principle is introduced into construction of a multi-branch tree, and the access frequency is added to the node to record the access frequency of the data block. When the cloud service provider carries out data block query on the verification request sent by the TPA, the authentication tree is traversed according to the access frequency, the whole authentication tree does not need to be traversed, searching is only carried out at the corresponding auxiliary root node, and then the length of an authentication path is shortened. And the communication overhead in the verification process is reduced while dynamic auditing is realized.
Owner:BEIJING UNIV OF TECH
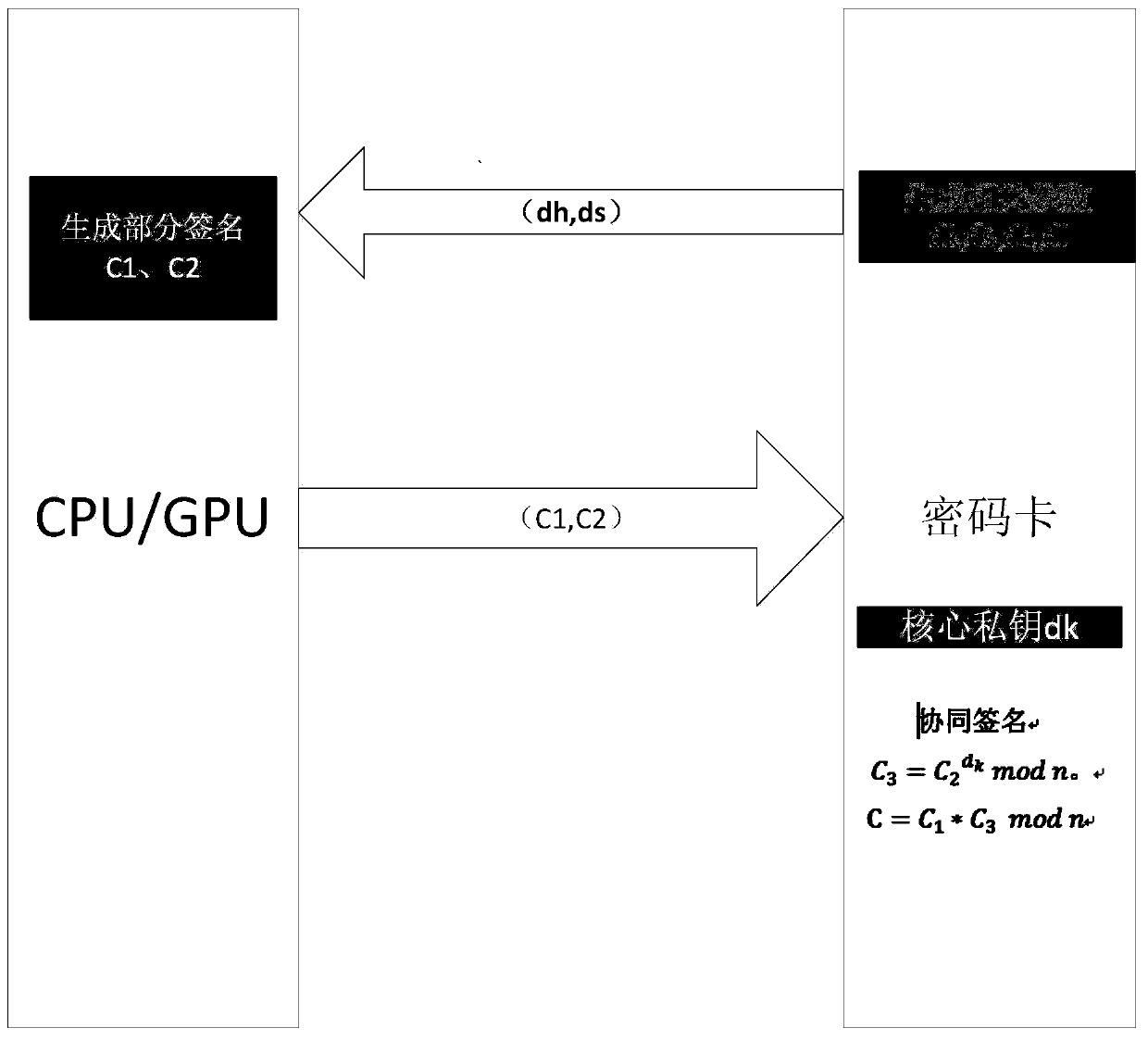
Cooperative digital signature method and device based on RSA and electronic equipment
ActiveCN110113169AEnsure safetyImprove signature efficiencyKey distribution for secure communicationUser identity/authority verificationComputer securityDigital signature
The invention relates to a cooperative digital signature method and device based on RSA and electronic equipment. The method comprises the following steps: an RSA-based digital signature is realized through cooperation of a first signature entity and a second signature entity, wherein the RSA signature operation is divided into time-consuming operation and safety operation, the first signature entity executes the time-consuming operation, and the second signature entity executes the safety operation, wherein the operation performance of the first signature entity is higher than that of the second signature entity, and the safety performance of the second signature entity is higher than that of the first signature entity; and the user is stored in the second signature entity privately. According to the invention, the user private key is stored in the second signature entity with high security performance, so that the security of the private key is ensured; the time-consuming operation with low security requirement is completed by the first signature entity with high performance, the signature efficiency is improved, and the complete coordinated digital signature can be realized onlyby two entities, so that the realization is simple and convenient. The invention also relates to an RSA-based collaborative digital signature device and electronic equipment.
Owner:BEIJING SANSEC TECH DEV
Signature method and device, computer equipment and computer readable storage medium
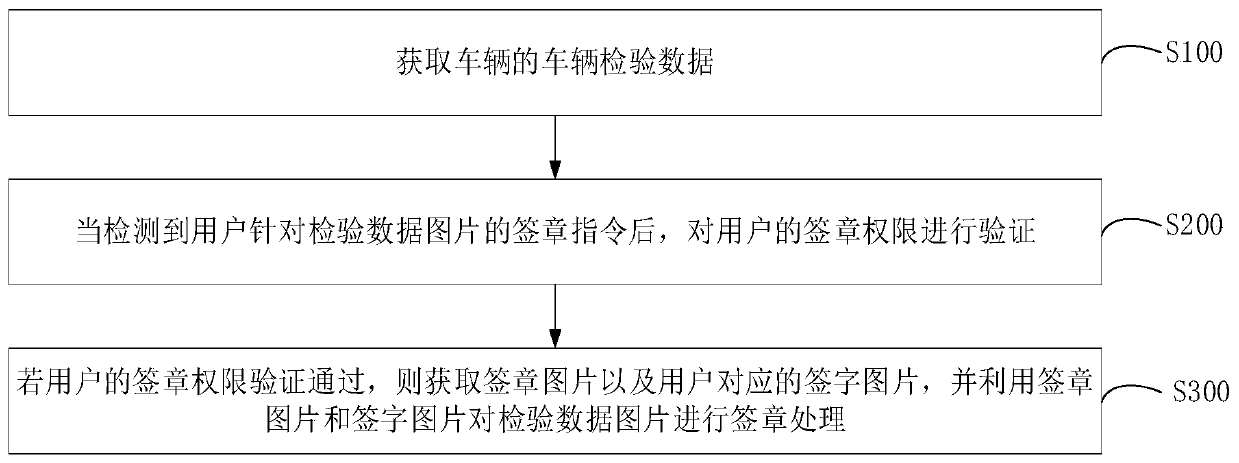
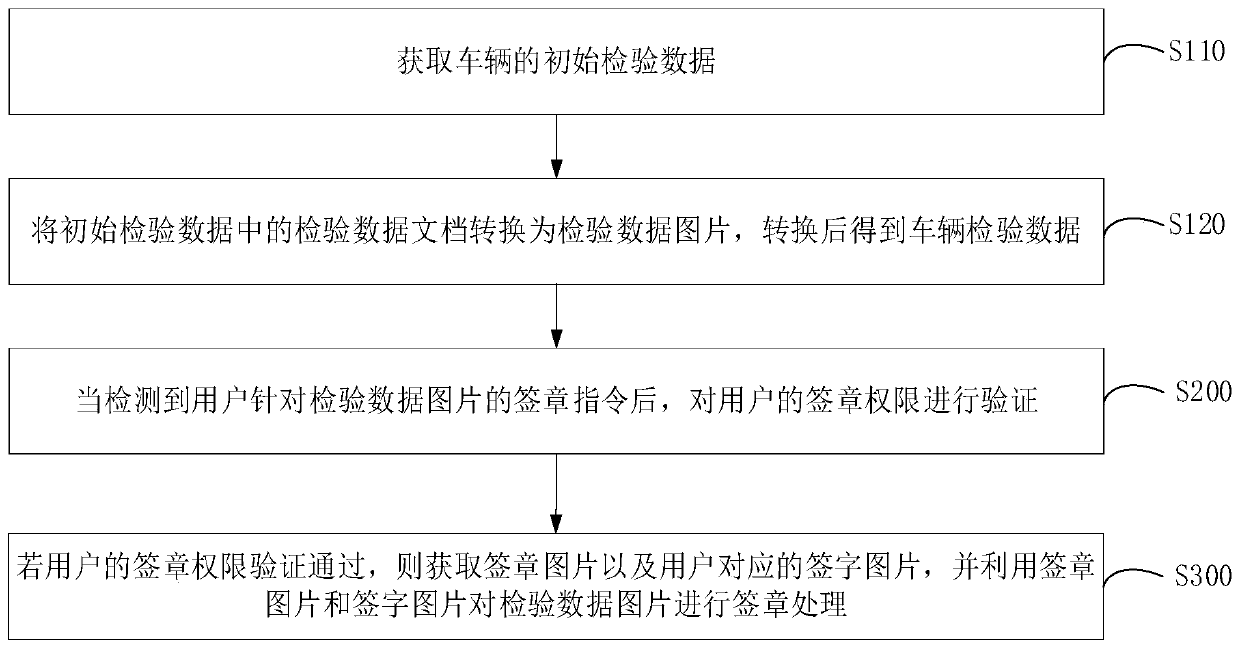
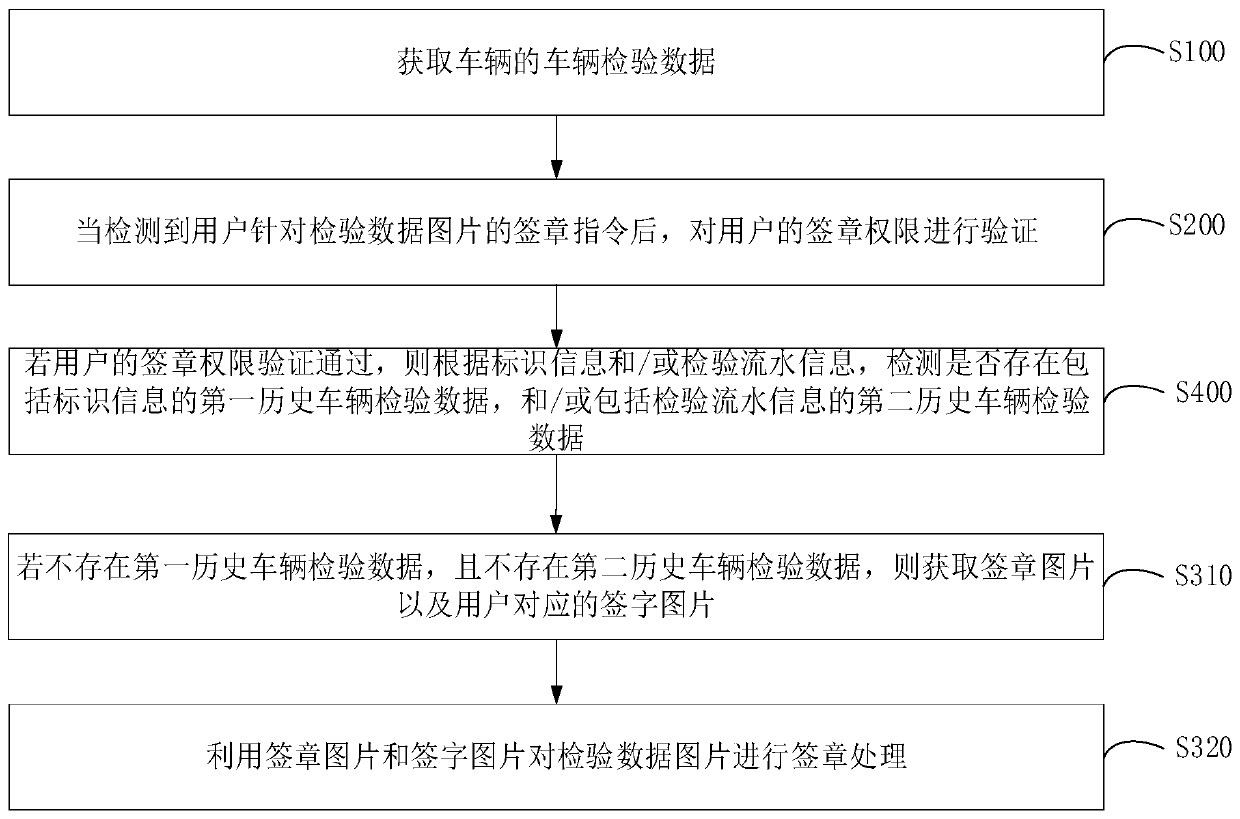
InactiveCN111541828AAvoid the problem of low signature efficiencyImprove signature efficiencyData processing applicationsTransmissionProgramming languageData graph
The invention relates to a signature method and device, computer equipment and a computer readable storage medium. The signature method comprises the following steps: acquiring vehicle inspection dataof a vehicle, wherein the vehicle inspection data comprises an inspection data picture to be signed; when a signature instruction of the user for the inspection data picture is detected, verifying the signature permission of the user; and if the signature permission of the user passes the verification, obtaining a signature picture and a signature picture corresponding to the user, and performingsignature processing on the inspection data picture by using the signature picture and the signature picture. By adopting the method, the signature efficiency of the to-be-signed inspection data picture can be improved.
Owner:上海眼控科技股份有限公司
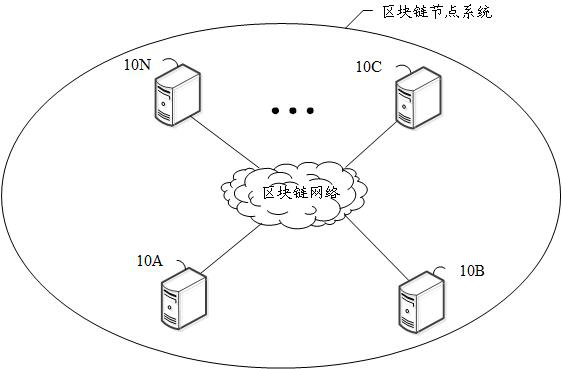
Signature method and system applied to block chain and storage medium
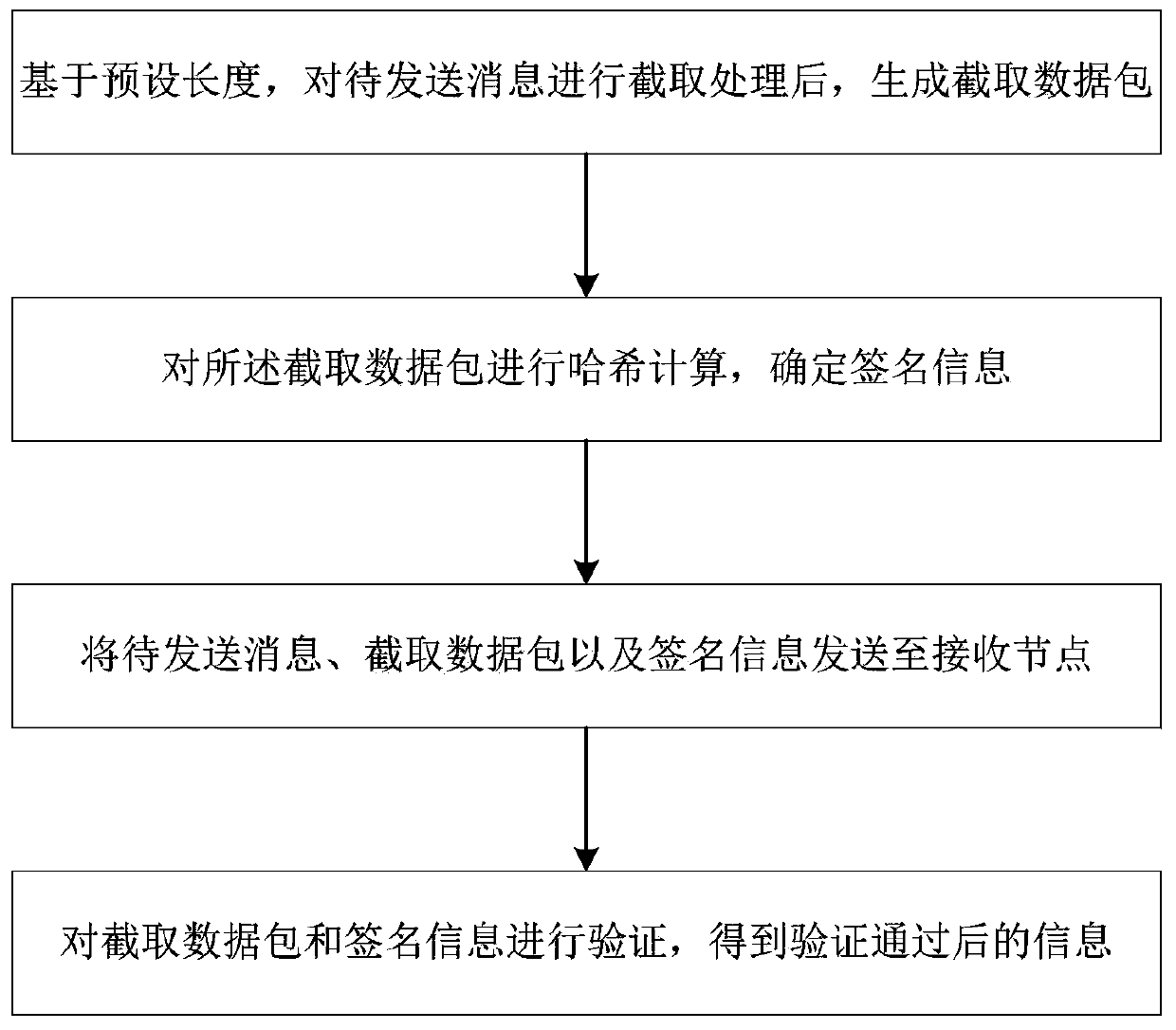
PendingCN111062721AReduce resource consumptionImprove efficiencyPayment protocolsBlockchainEngineering
The invention discloses a signature method and system applied to a block chain and a storage medium, and the method comprises the steps: carrying out the interception of a to-be-transmitted message based on a preset length, and generating an interception data packet; performing hash calculation on the intercepted data packet, and determining signature information; sending the message to be sent, the intercepted data packet and the signature information to a receiving node; and verifying the intercepted data packet and the signature information to obtain information after the verification is passed. According to the invention, after the to-be-sent message is intercepted based on the preset length, hash calculation is carried out on the intercepted data packet, and verification is carried out according to the intercepted data packet, so that the resource consumption during message signature between nodes can be reduced, the message signature efficiency is improved, and the method can bewidely applied to the technical field of block chains.
Owner:南京金宁汇科技有限公司
A Quantum Digital Signature Method
ActiveCN113297633BUnconditional Security GuaranteedImprove signature efficiencyQuantum computersDigital data protectionDigital signatureTheoretical computer science
The invention discloses a quantum digital signature method, which belongs to the technical field of quantum security. Aiming at the problem that the security of the digital signature protocol and the efficiency of signing messages are generally not high in the prior art, the present invention provides a quantum digital signature method, which includes the following three steps: preparing a key, generating a signature, Verify the signature. The technical solution of the present invention is a real unconditional security solution, which solves the problem of low efficiency of the existing unconditional security digital signature protocol. This solution also has strong compatibility and can be realized by using various systems. It can be realized in the system, and it can also be harmonious and comfortable in the future quantum Internet system. It has a strong application scope and prospect at this stage and in the future.
Owner:NANJING UNIV +1
Service system of multiple digital certificate authentication mechanisms
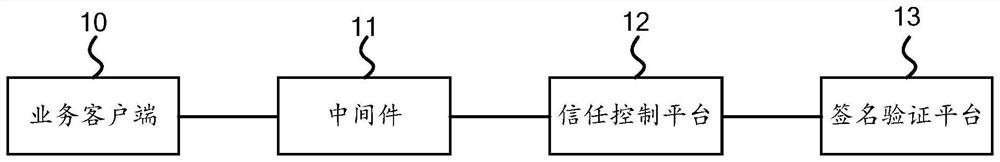
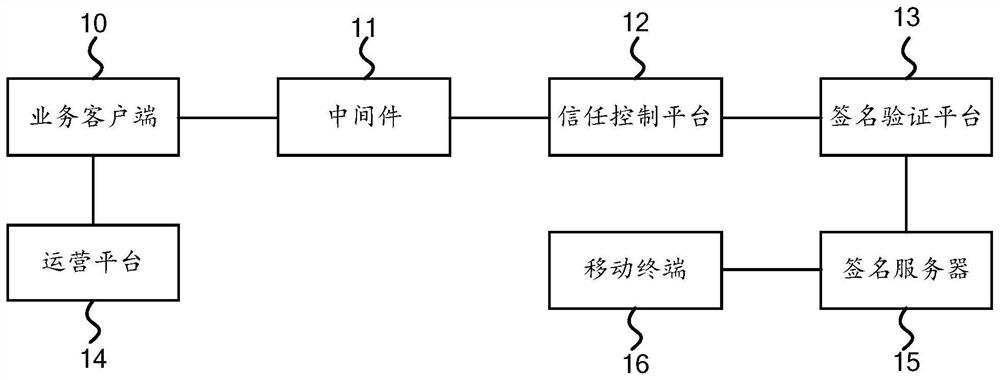
PendingCN111831996AAvoid monopolyPhenomena affecting normal useDigital data protectionDigital data authenticationService systemInternet privacy
The invention provides a service system of multiple digital certificate authentication mechanisms. The service system comprises a service client, middleware, a trust control platform and a signature verification platform, the service client sends a signature request carrying the to-be-signed service identifier to the trust control platform to request the trust control platform, and selects at least one digital certification institution corresponding to the to-be-signed service identifier, so that a user selects a digital certificate of a target digital certification institution to sign; the middleware reads certificate information of a digital certificate of a target digital certification authority and signs the to-be-signed service to obtain signature information of the to-be-signed service; the trust control platform detects certificate information of the digital certificate of the target digital certification authority and sends signature information to the signature verification platform after the certificate information passes the detection; and the signature verification platform verifies the signature information and sends a verification result to the service client. Therefore, the phenomenon that the normal use of a business system is influenced due to service interruption of a certain CA can be prevented, and the signature efficiency is improved.
Owner:BEIJING GUODIANTONG NETWORK TECH CO LTD +1
Remote note signing machine
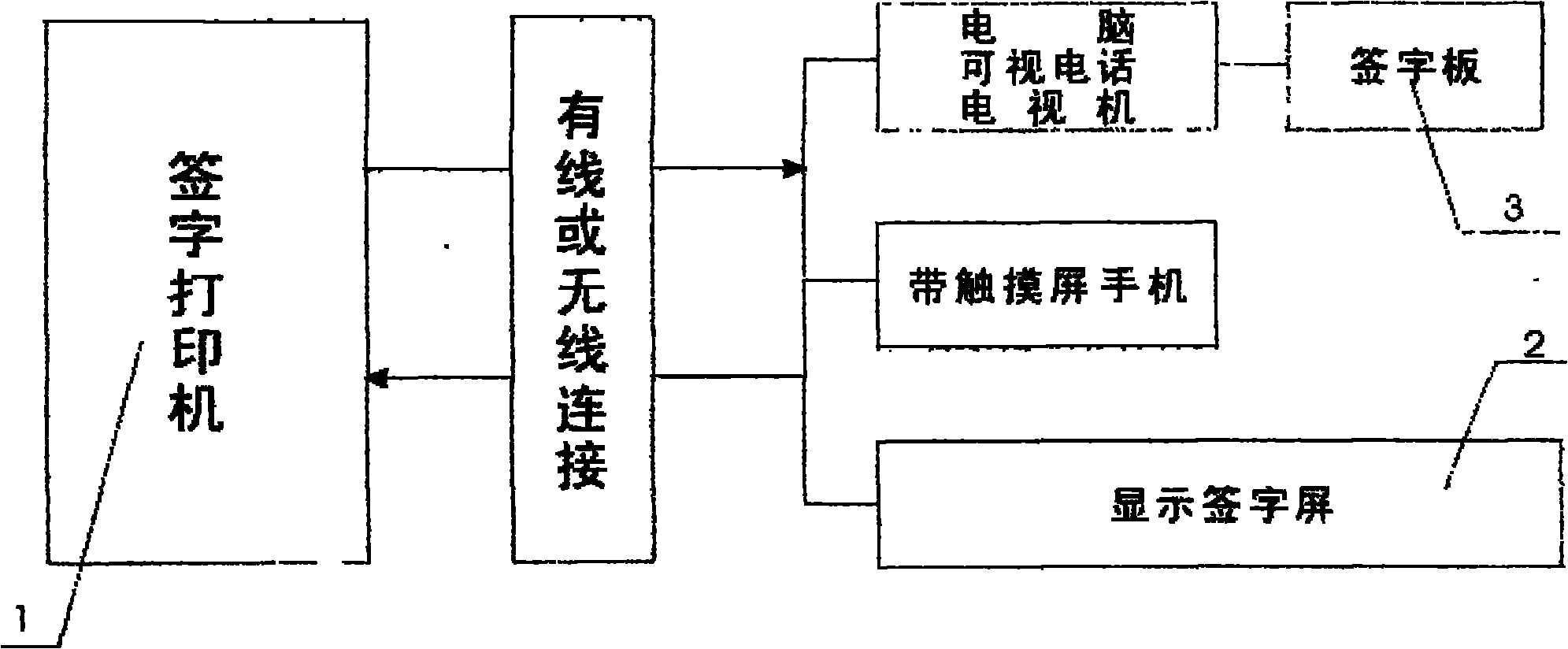
InactiveCN101827183AImprove signature efficiencyEasy to operatePictoral communicationComputer science
The invention discloses a remote note signing machine, which comprises a signing printer 1 and a display signing screen 2 which are connected in a wired or wireless manner. After documents or notes to be signed are placed into a signing printer 1, an operator presses a signing person menu 6 on the signing printer 1 to transmit a signal required to be signed to a signer; a signal device transmits the signal to the display signing screen 2 owned by the signer in a wired dialing or wireless dialing manner; and the signer clicks a signing menu 28 after seeing prompt information of a prompt 26, signs own name on a signing area 24 by using a special signing pen and clicks a signing confirm menu 16 and transmits the signing. The signing printer 1 receives signing information which is processed by a processor; and then singing contents are printed on the documents or the notes by using a printing head. The invention has the beneficial effects that the remote note signing machine has simple operation and convenient use and can effectively improve the office efficiency of singing notes.
Owner:唐善科
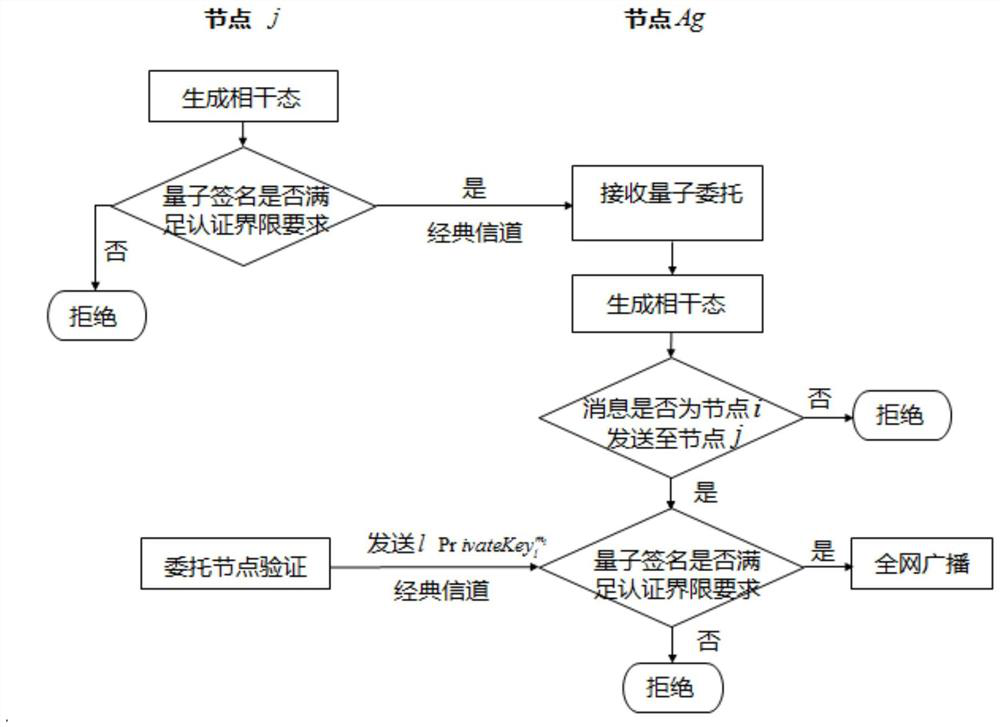
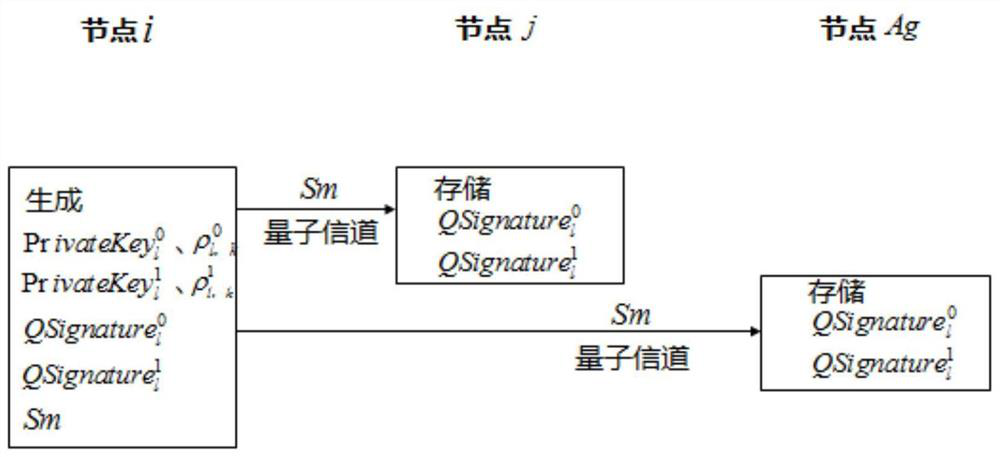
Blockchain digital signature method, device and system based on quantum cryptography
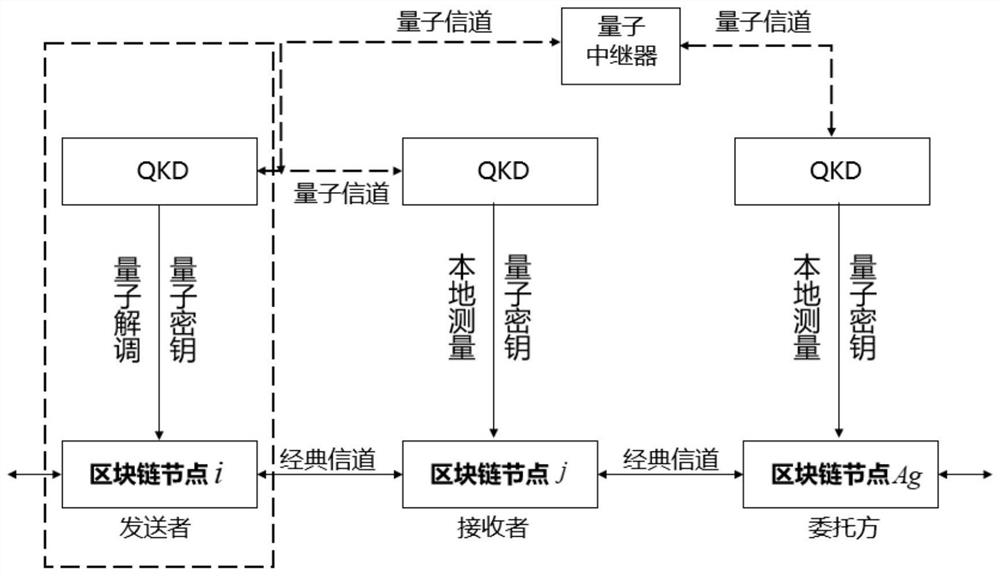
ActiveCN113422681AGuarantee fairnessImprove securityKey distribution for secure communicationUser identity/authority verificationBlockchainEngineering
The invention discloses a blockchain digital signature method, device and system based on quantum cryptography, applied to a consignor in a blockchain, the consignor being generated based on an election mechanism. The method comprises the following steps: a receiver and the consignor receive a quantum signature and signature information sent by a sender; under the condition that the quantum signature passes the verification by the receiver, a quantum commission sent by the receiver is received; the consignor verifies the signature information based on quantum commission; and under the condition that the verification is passed, a private key pair sent by the receiver is received, and the quantum signature is verified based on the private key pair. In the above process, the quantum signature, the quantum commission and the private key pair are constructed based on the quantum key technology, the consignor is selected based on the election mechanism, the quantum signature is verified by the consignor by using the quantum key technology, and the consignor determined based on the election mechanism can fully ensure the fairness of the consignor in message verification. As the security of the quantum key is high, the security can be ensured without a complex key, and the signature efficiency is improved.
Owner:STATE GRID E COMMERCE CO LTD +2
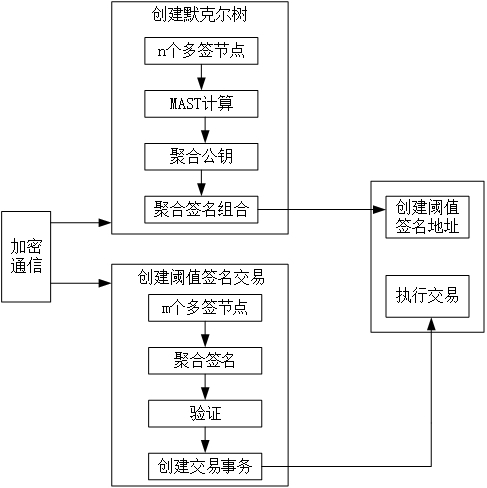
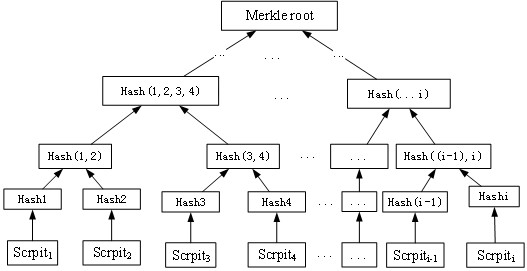
Threshold signature method, system, device and storage medium based on aggregated multi-signature
ActiveCN113556237BAvoid cumbersomeImprove signature efficiencyUser identity/authority verificationComputer networkEngineering
The invention discloses a threshold signature method, system, device and storage medium based on aggregated multi-signature. The method includes the following steps: selecting m signature nodes based on n signature nodes of the block chain network, and generating an aggregated public key based on the m signature nodes And the aggregated temporary public key, gather all the aggregated public keys to form an aggregated public key combination; create a Merkle tree structure based on the aggregated public key combination, and obtain the Merkle root; generate the second aggregated public key through n signature nodes, and combine the default Kergen derives a threshold signature address; generates a transaction in the threshold signature address, signs the transaction at m signature nodes, aggregates all signatures and combines the aggregated temporary public key to generate an aggregate signature, and executes the transaction based on the aggregate signature. Through this method, verifiable aggregated multi-signatures are provided for threshold signatures, privacy is protected through unified script coding of the MAST structure, and encrypted communication is used to increase the security of the aggregated signature process, and finally a safe and efficient threshold signature extension is realized.
Owner:杭州链网科技有限公司
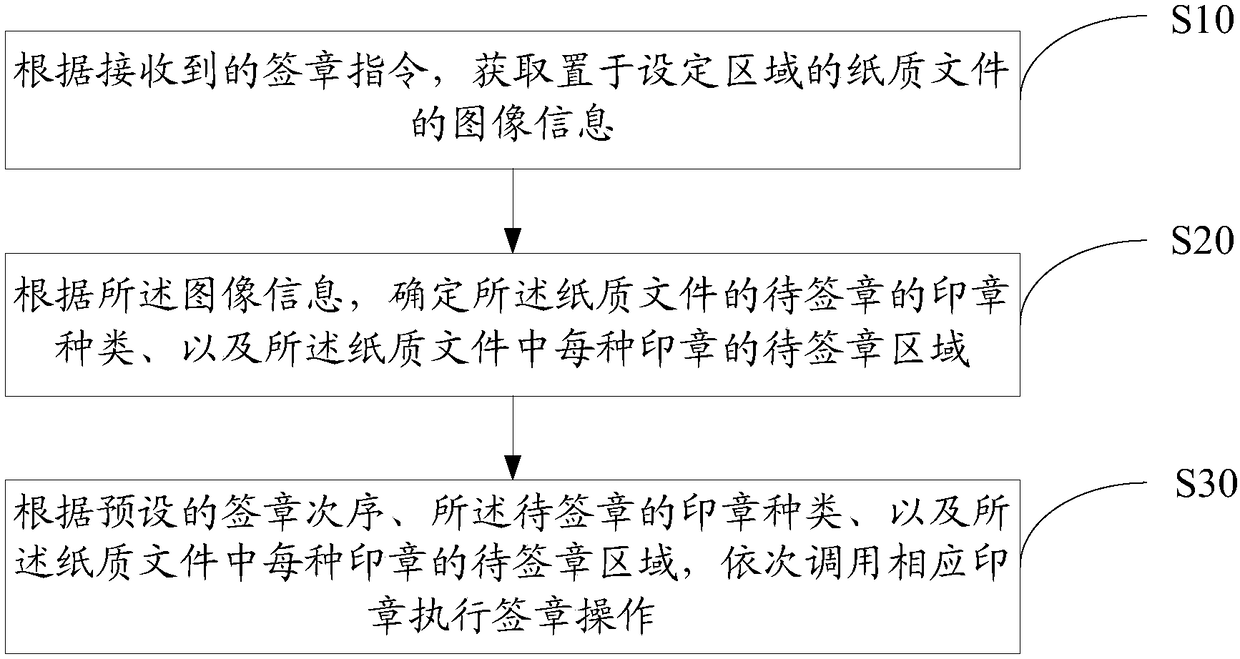
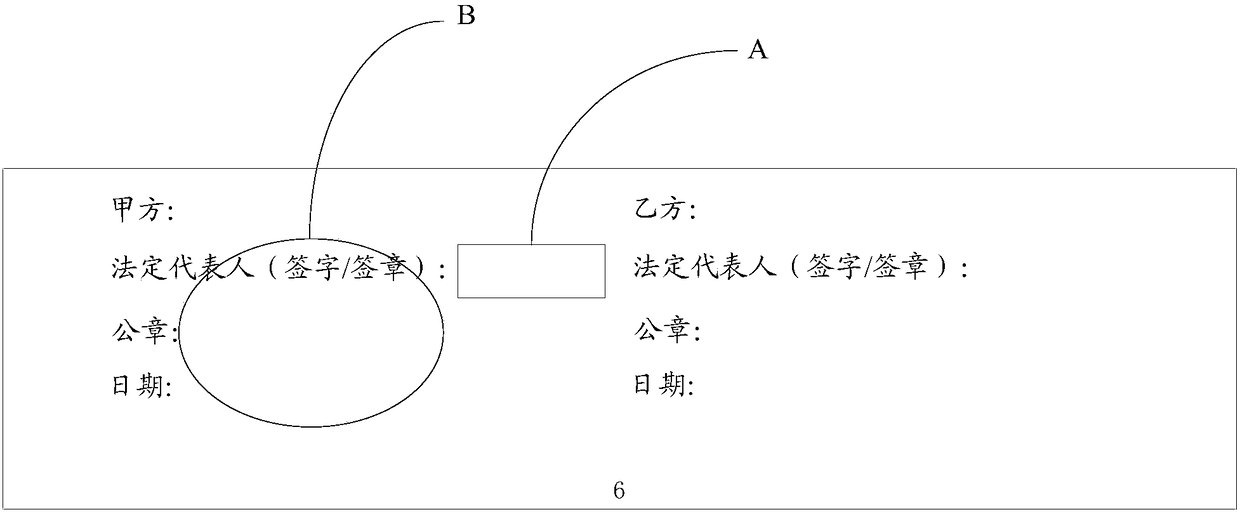
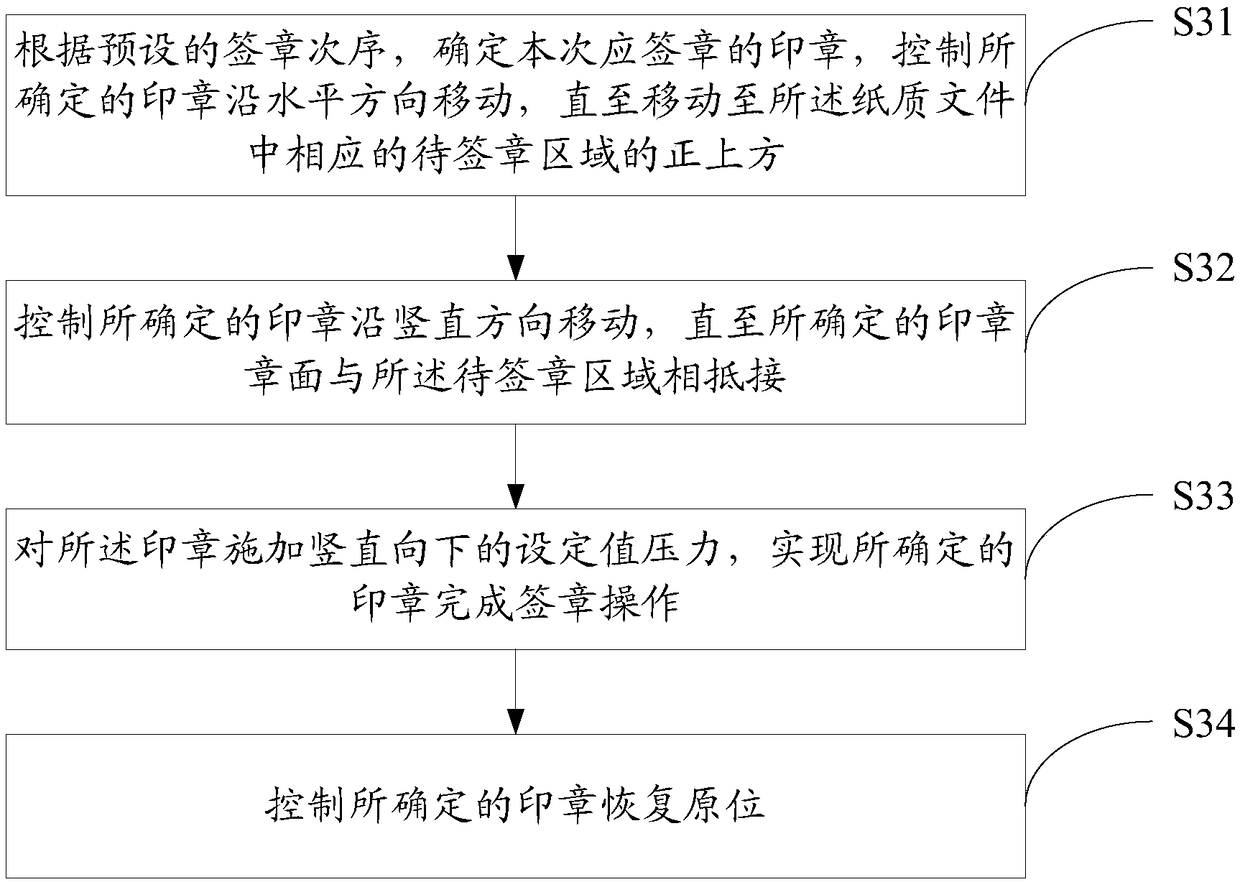
Realization method and device for signature of paper documents
The invention discloses a realization method for signature of paper documents. The method comprises the following steps: obtaining image information of paper documents in a set area according to a received signature instruction; according to the image information, determining to-be-signed stamp types of paper documents and a to-be-signed area of each stamp in each paper document; and orderly calling corresponding stamps to perform signature operation according to a pre-set signature sequence, a to-be-signed stamp type and a to-be-signed area of each stamp in each paper document. The inventionalso provides a realization device for signature of paper documents. The technical scheme of the method and the device has the following beneficial effects: without human signature required, signaturefailure caused by a man-made cause is avoided and high signature efficiency is obtained; meanwhile, control over an intelligent stamp out of sight is carried out by a stamp manager; for instance, thestamp is borrowed; therefore, an actual user of the intelligent stamp is a user authorized by the manager; and misuse of the intelligent stamp is prevented, thereby ensuring safety use of the intelligent stamp.
Owner:SHENZHEN SAIYI TECH DEV
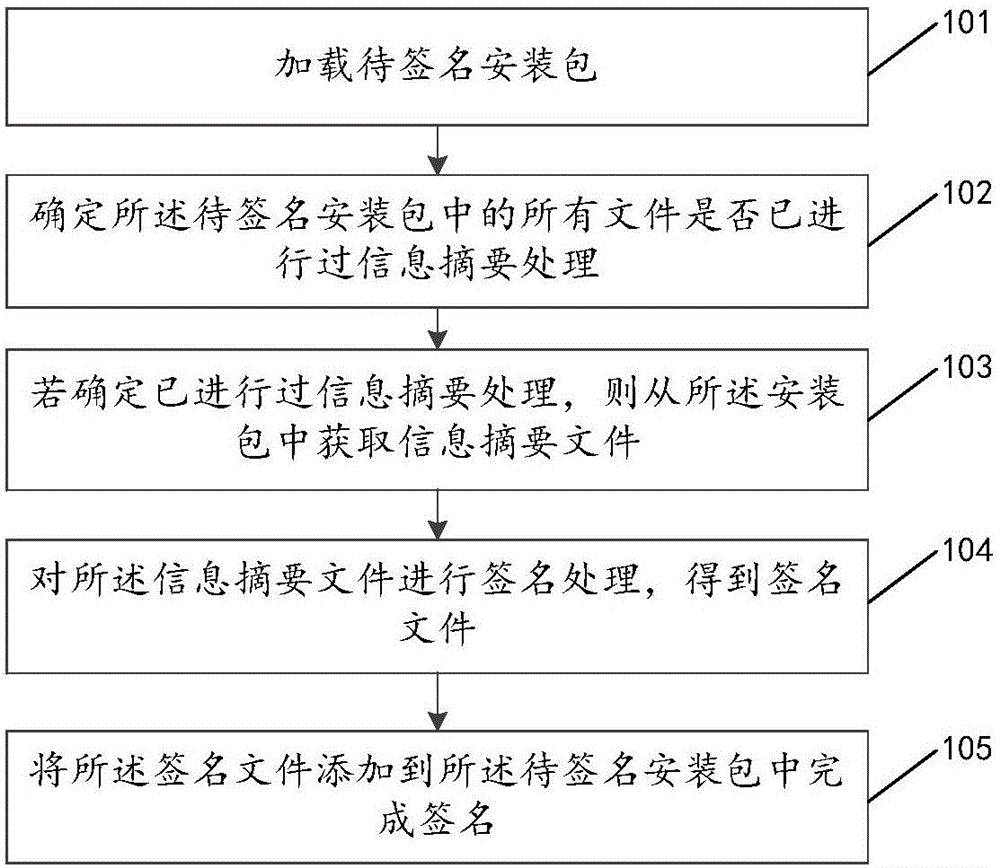
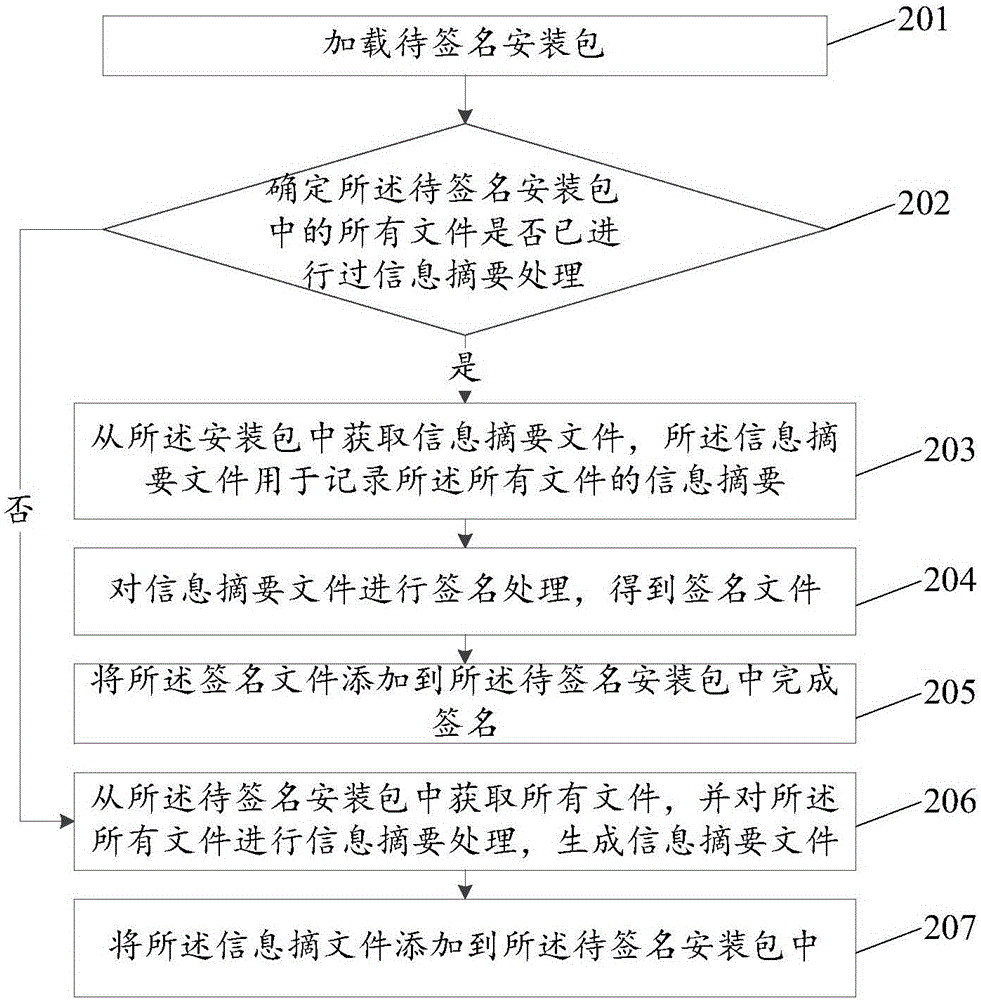
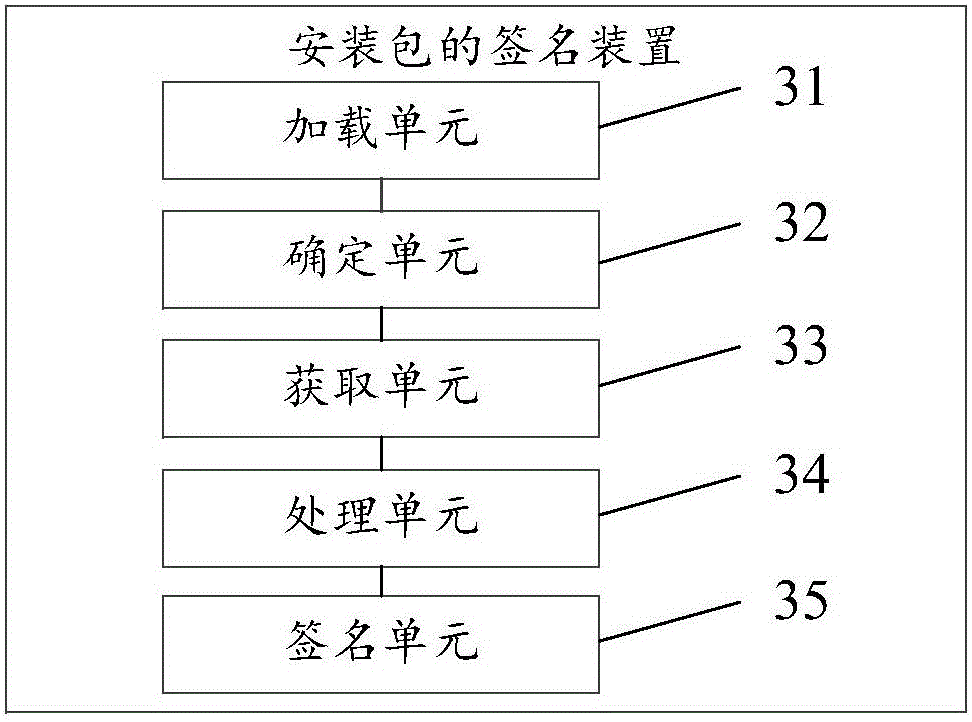
Installation package signature method and device
InactiveCN106685641AImprove signature efficiencyImprove efficiencyEncryption apparatus with shift registers/memoriesUser identity/authority verificationSignature fileInformation technology
The invention discloses an installation package signature method and device, relates to the field of information technology, and solves the problem of large amount of time consumption in installation package signature in the prior art and the resulting low efficiency of installation package signature. The method of the invention comprises the steps of loading an installation package to be signed; determining whether or not a file in the installation package to be signed has been subjected to message digest processing; if determining that the message digest processing has been performed, obtaining a message digest file from the installation package, the message digest file being for recording a message digest of the file; performing signature for the message digest file to obtain a signature file; and adding the signature file to the installation package to be signed to complete the signature. The invention is mainly used for the signature of the installation package.
Owner:光锐恒宇(北京)科技有限公司
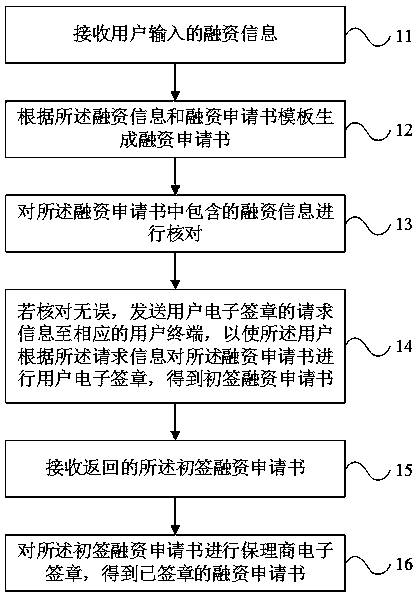
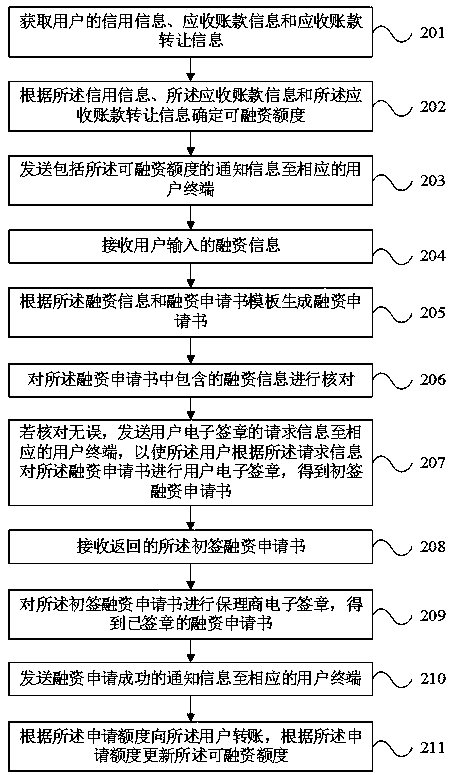
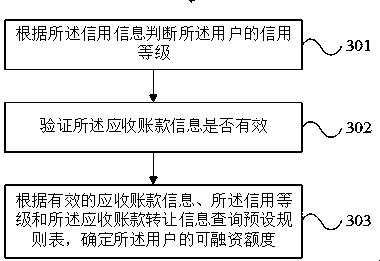
Service factoring management method and system
InactiveCN111091463AImprove signature efficiencySave the cost of signing and stampingFinanceOffice automationManagement systemOperations research
The invention discloses a service factoring management method. The method comprises the steps of receiving financing information input by a user, generating a financing application form according to the financing information and the financing application form template, checking financing information contained in the financing application form; error-free check, sending request information of the user electronic signature to a corresponding user terminal, the user performs user electronic signature on the financing application form according to the request information; obtaining an initial financing application form; receiving a returned initial financing application form, carrying out factoring agent electronic signature on the preliminary signing financing application form; obtaining a signed financing application form; online electronic signature is realized; according to the technical scheme, the signature efficiency is greatly improved, the signature cost is saved, the problems that in the prior art, in the file signature process of commercial factoring, paper stamping parts are adopted for transferring and stamping among all parties, the transferring efficiency is low, the cost is high, and the safety is low are solved, and in addition, the invention further provides a commercial factoring management system, terminal equipment and a storage medium.
Owner:盛业信息科技服务(深圳)有限公司
Quantum digital signature system and method based on time phase coding
PendingCN113961954AEnsure safetyGuarantee unconditional securityQuantum computersRandom number generatorsHash functionDigital signature
The invention discloses a quantum digital signature system and method based on time phase coding, and the quantum digital signature system can have the security in information theory, thereby avoiding the problem that the security cannot be guaranteed along with the development of a quantum computing technology. The method comprises the following steps: generating a secure key in a signature process, after the key is generated, selecting a random number obtained in a random number generator to generate an irreducible polynomial, generating a hash function by the irreducible polynomial and part of the key, and inputting a message into the hash function to generate a hash value, where the Hash function used each time needs to be updated, and the remaining secret key for generating the Hash function is used for encryption; converting messages with any length into fixed-length hash values by means of the generated hash function. According to the invention, the digital signature involved in the method has no limitation on the length of the messages, and the signature efficiency is very high.
Owner:NANJING UNIV +1
EV code signature realizing method and device
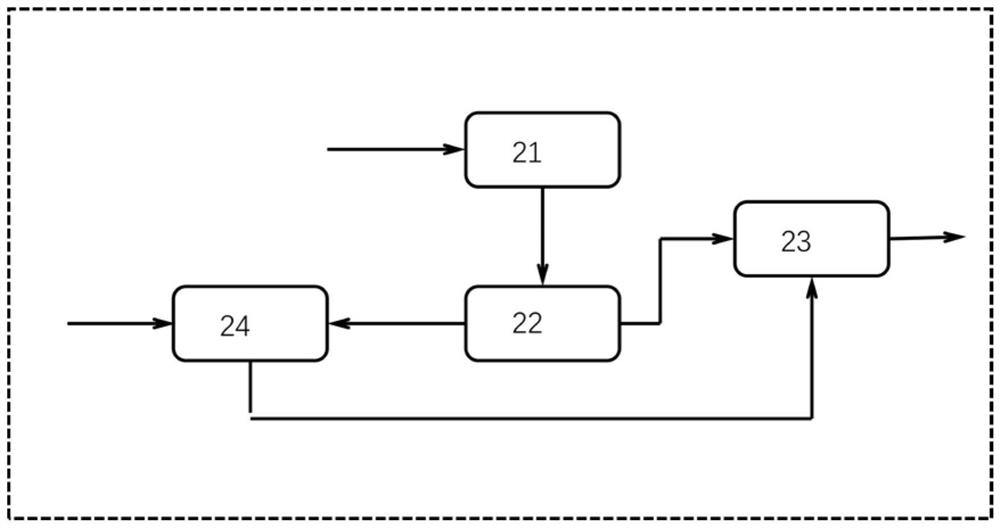
ActiveCN106066949AImprove signature efficiencyProgram/content distribution protectionSignature fileUSB
The invention discloses an EV code signature realizing method and device; the method comprises the following steps: receiving a signature request sent to an assigned host, and sending the signature request to a virtual machine on the assigned host, wherein the signature request comprises a to-be-signed file; receiving a signature result file returned by the virtual machine, wherein the virtual machine uses an EV signature certificate in a USB device inserted into the assigned host to carry out EV code signature for the to-be-signed file, thus obtaining the signature result file; sending the signature result file to the signature request sender. The method and device do not need the user to manually perform EV code signature, and can concurrently execute a plurality of EV code signature operations, thus improving EV code signature efficiency.
Owner:北京鸿享技术服务有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com