Digital signature and verification method, device and system
A digital signature and application system technology, which is applied in the direction of user identity/authority verification, encryption device with shift register/memory, etc., can solve the problems of high hardware requirements, low SM9 encryption efficiency, low signature efficiency, etc., and achieve improved signature Efficiency, ensuring data integrity, and achieving non-repudiation effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0064] The invention is applied to a digital signature and verification system, and the system includes: a user end, an application system and an encryption machine, wherein the user end communicates with the application system remotely; the application system and the encryption machine are deployed on the same side, and the two realize short-distance confidential communication.
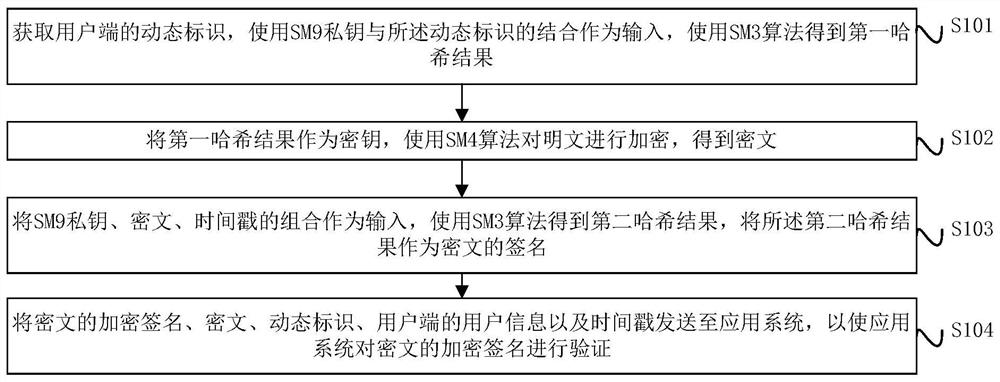
[0065] figure 1 A schematic flow diagram of a digital signature method provided by an embodiment of the present invention, such as figure 1 As shown, a digital signature method is applied to a client, and the client has an SM9 private key in advance, and the method includes:
[0066] S101: Obtain a dynamic identifier of the client, use the combination of the SM9 private key and the dynamic identifier as input, and use the SM3 algorithm to obtain a first hash result.
[0067] Exemplarily, a dynamically generated random number may be used as the dynamic identifier, and the length of the random number ...
Embodiment 2
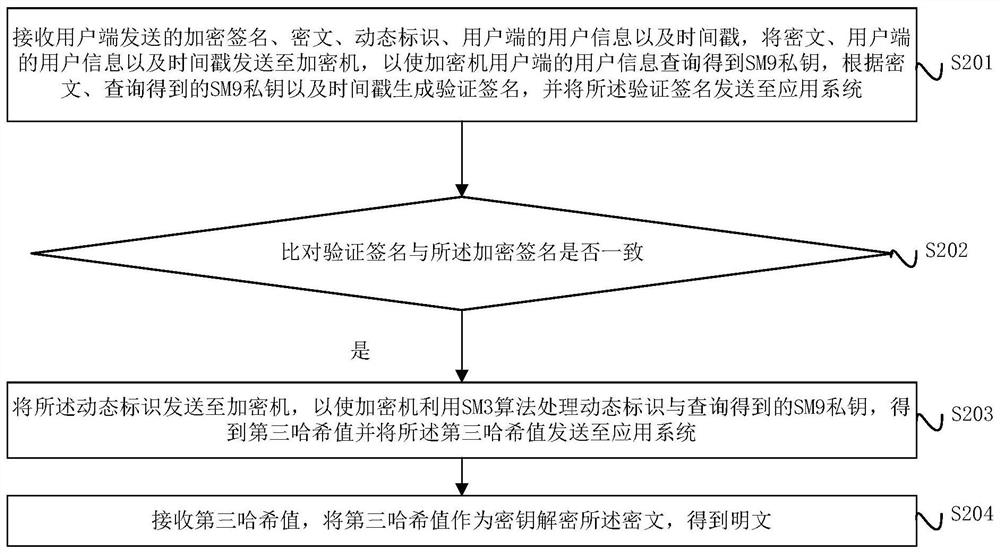
[0087] figure 2 A schematic flow diagram of a digital signature verification method provided by an embodiment of the present invention, such as figure 2 As shown, Embodiment 2 of the present invention is implemented based on Embodiment 1. Embodiment 2 of the present invention is applied to an application system, and the method includes:
[0088] S201: Receive the encrypted signature, ciphertext, dynamic identification, user information and time stamp sent by the client, and send the ciphertext, user information and time stamp to the encryption machine, so that the user information of the user end of the encryption machine can be queried The SM9 private key generates a verification signature according to the ciphertext, the SM9 private key obtained from the query and the time stamp, and sends the verification signature to the application system.
[0089] The client sends the signature of the ciphertext, that is, the second hash result; ciphertext; dynamic identification; tim...
Embodiment 3
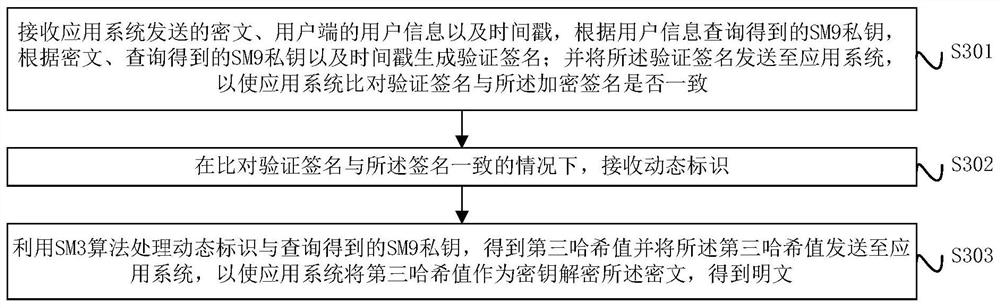
[0101] image 3A schematic flow diagram of a digital signature verification method provided by an embodiment of the present invention, such as image 3 As shown, Embodiment 3 of the present invention is realized based on Embodiment 1 and Embodiment 2. Embodiment 3 of the present invention is applied to an encryption machine, and several user information SM9 private key pairs are preset in the encryption machine. The method include:
[0102] S301: Receive the ciphertext sent by the application system, the user information of the client, and the timestamp, query the SM9 private key obtained according to the user information, and generate a verification signature according to the ciphertext, the SM9 private key obtained from the query, and the timestamp; The signature is sent to the application system, so that the application system compares and verifies whether the signature is consistent with the encrypted signature;
[0103] S302: Receive the dynamic identification when comp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com