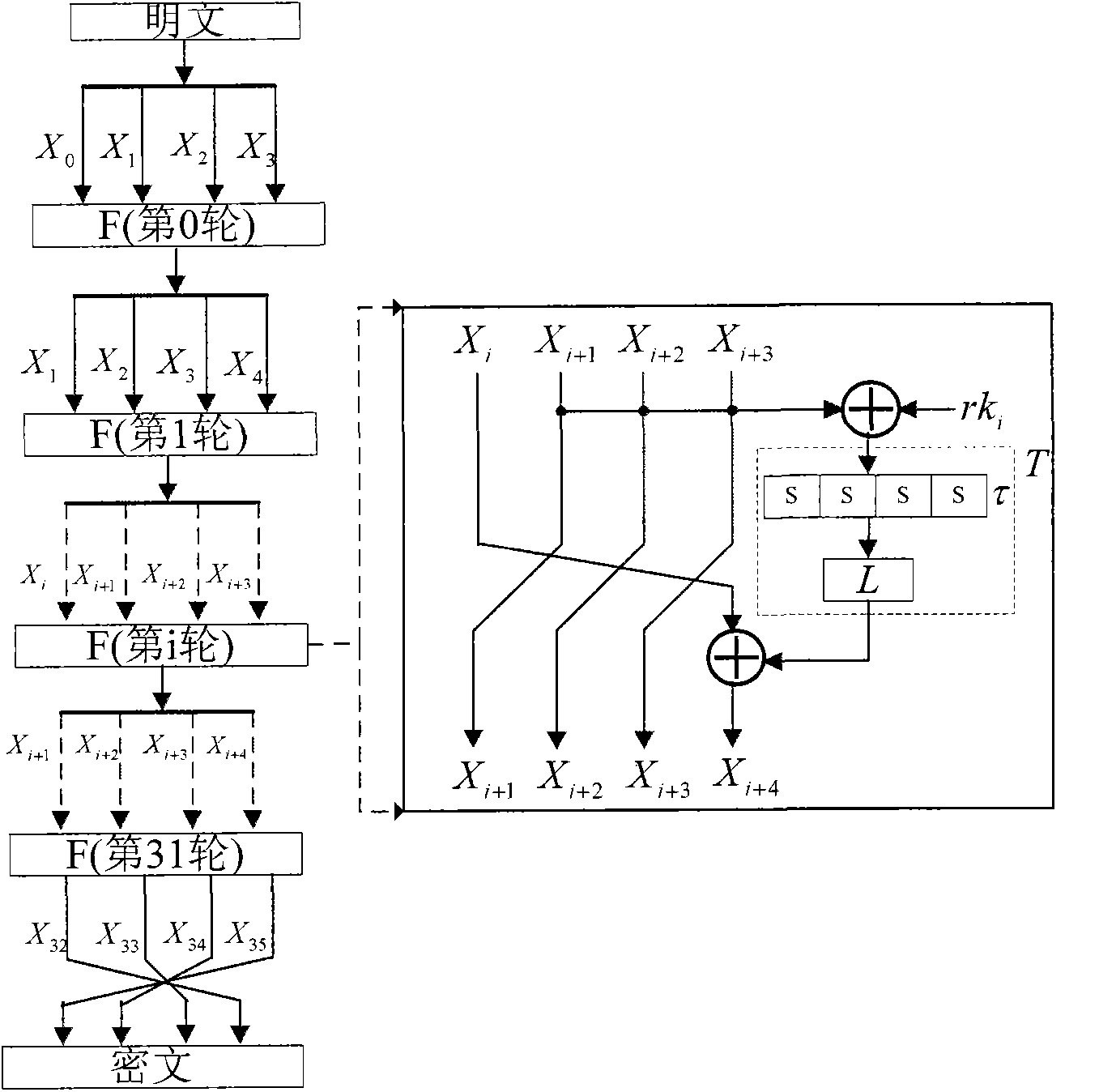
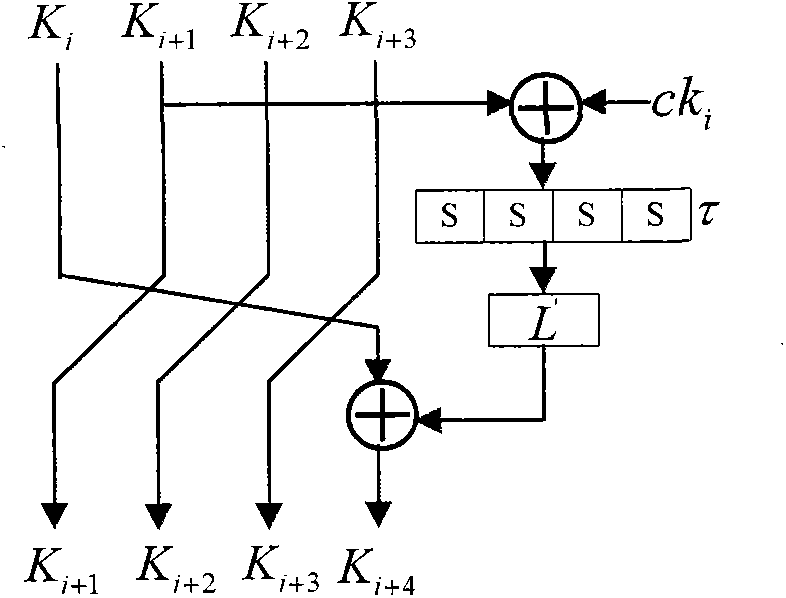
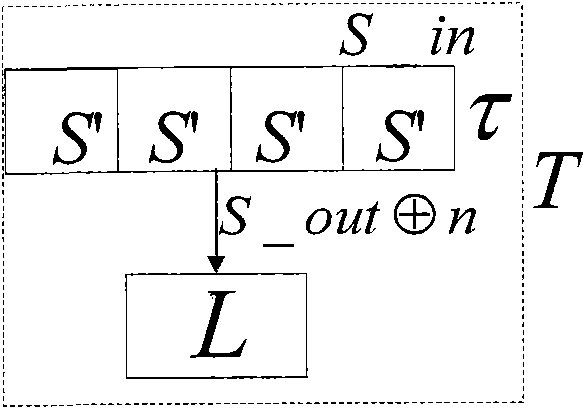
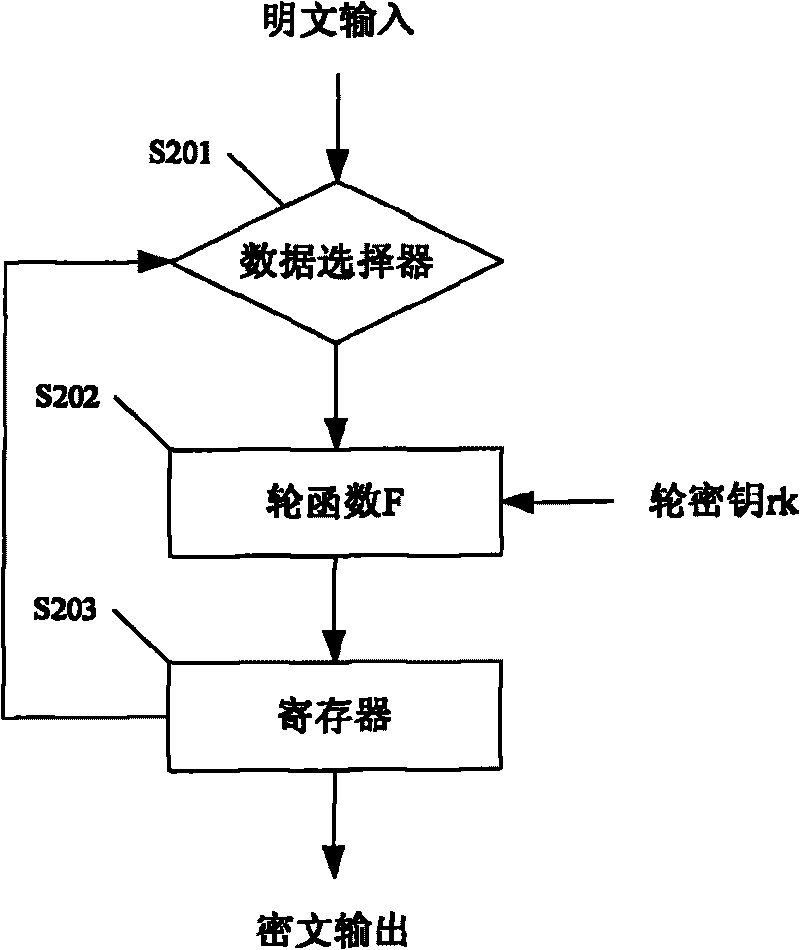
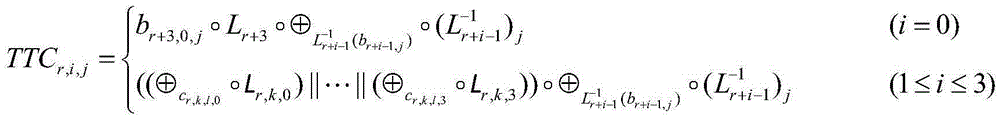Patents
Literature
124 results about "SM4 Algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
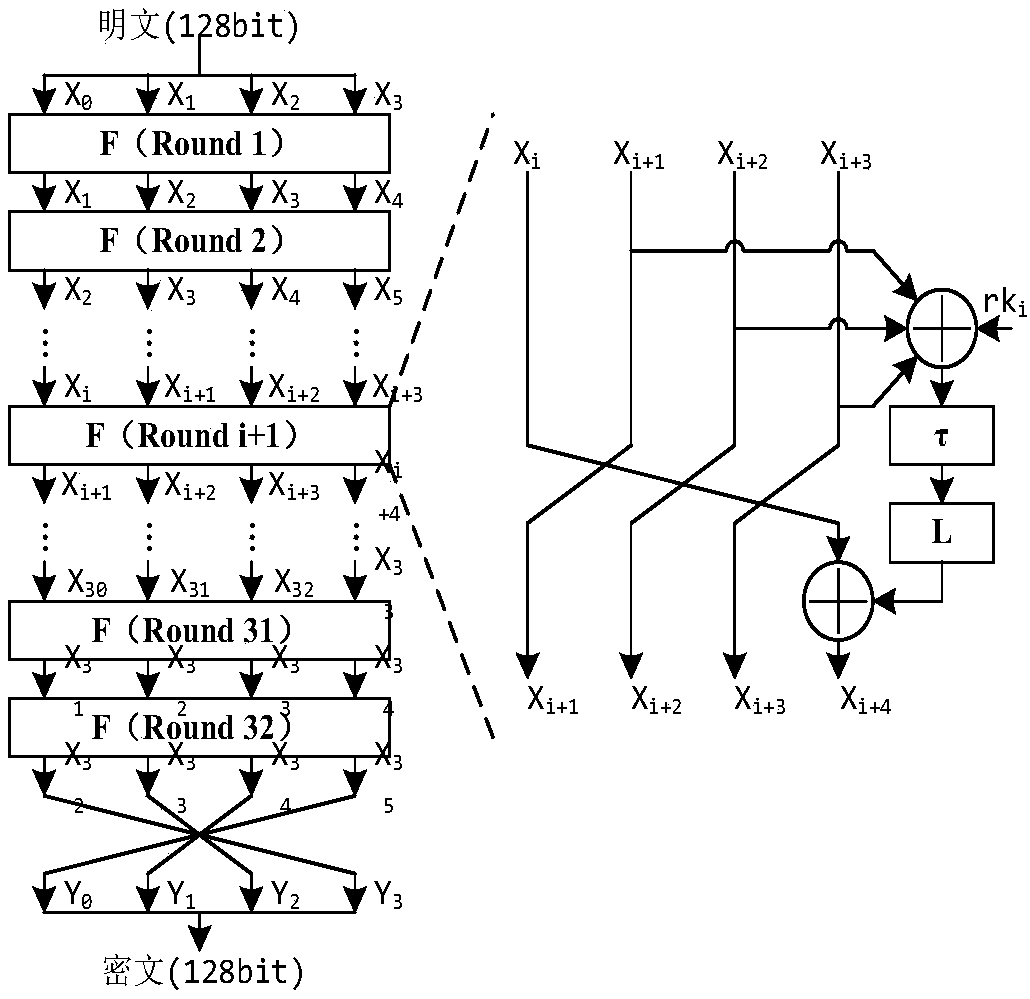
SM4 (formerly SMS4) is a block cipher used in the Chinese National Standard for Wireless LAN WAPI (Wired Authentication and Privacy Infrastructure). SM4 was a cipher proposed to for the IEEE 802.11i standard, but has so far been rejected by ISO. One of the reasons for the rejection has been opposition to the WAPI fast-track proposal by the IEEE.
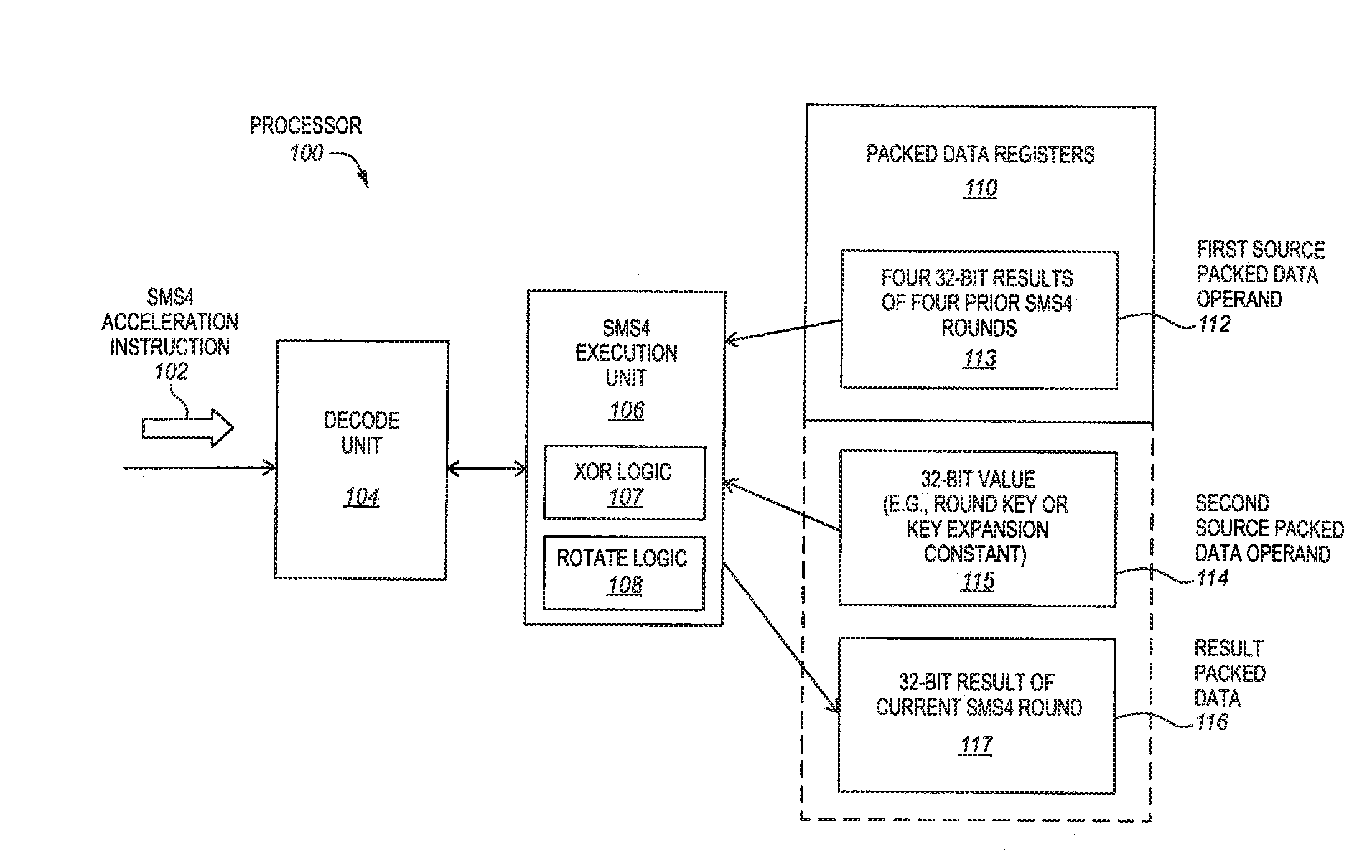
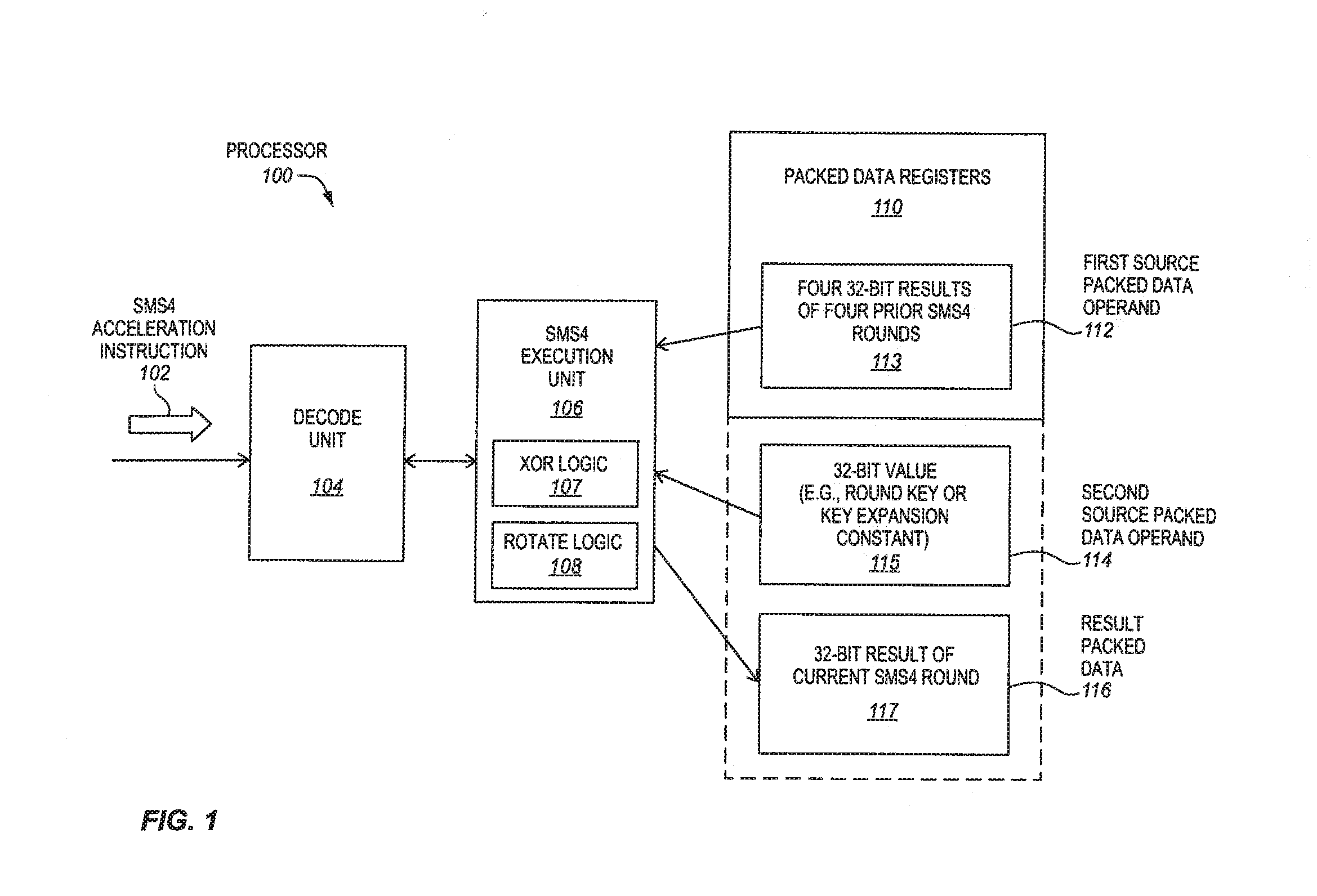
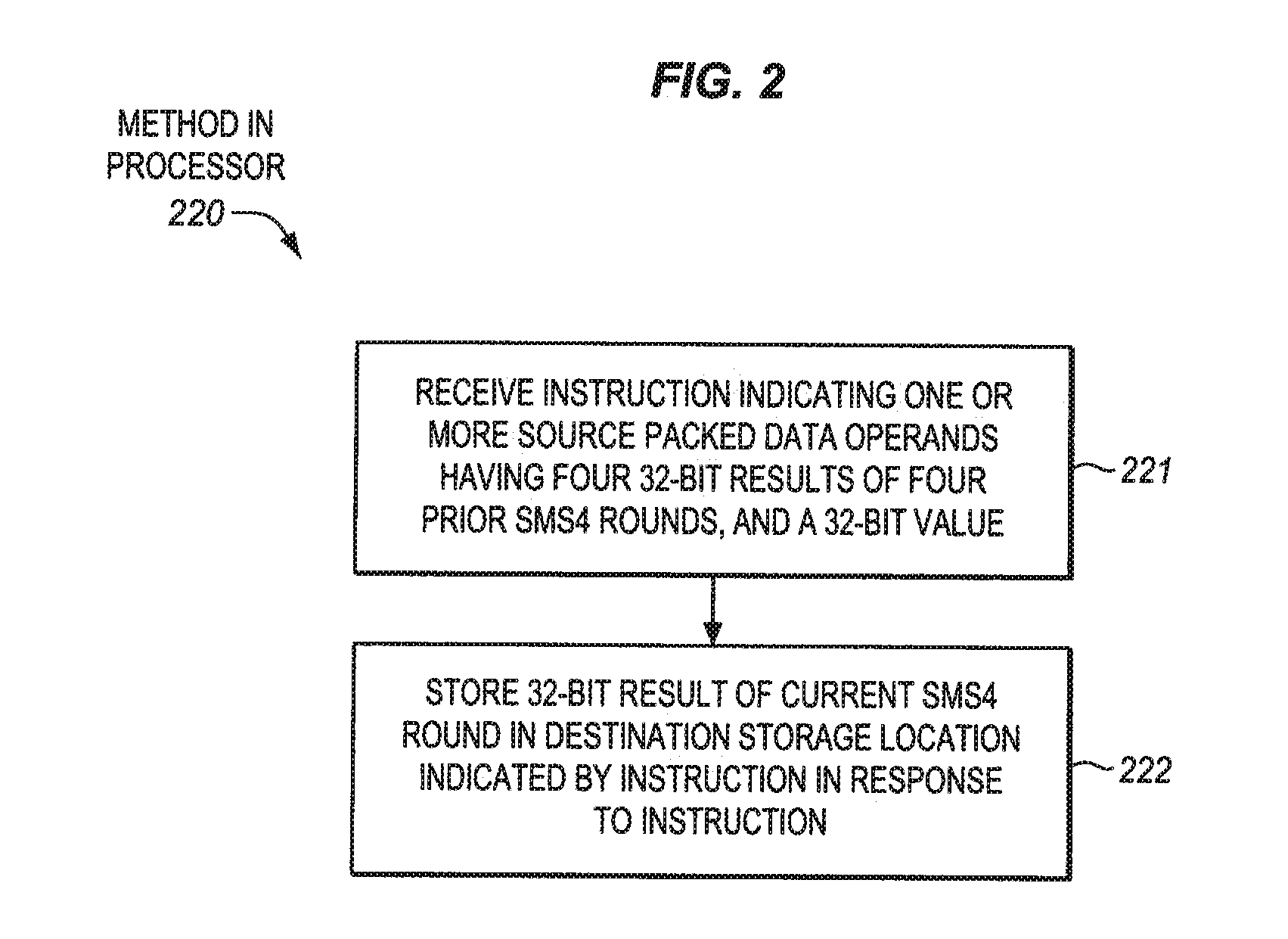
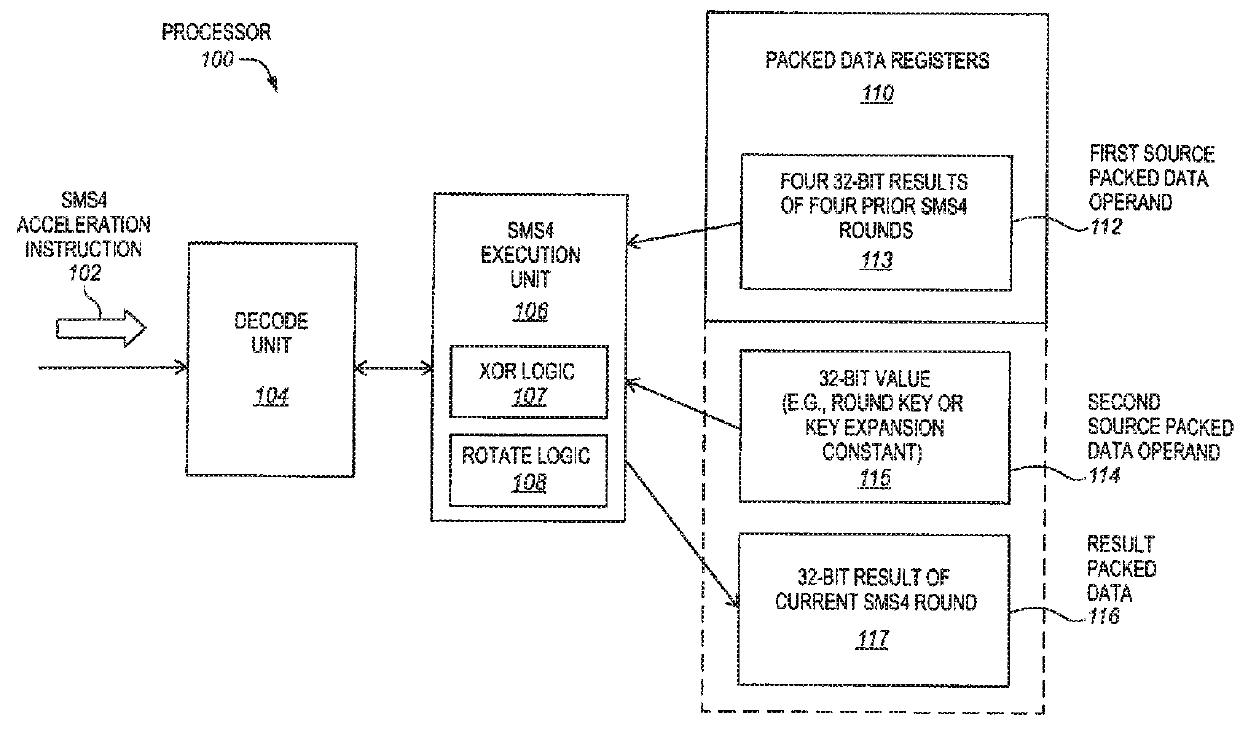
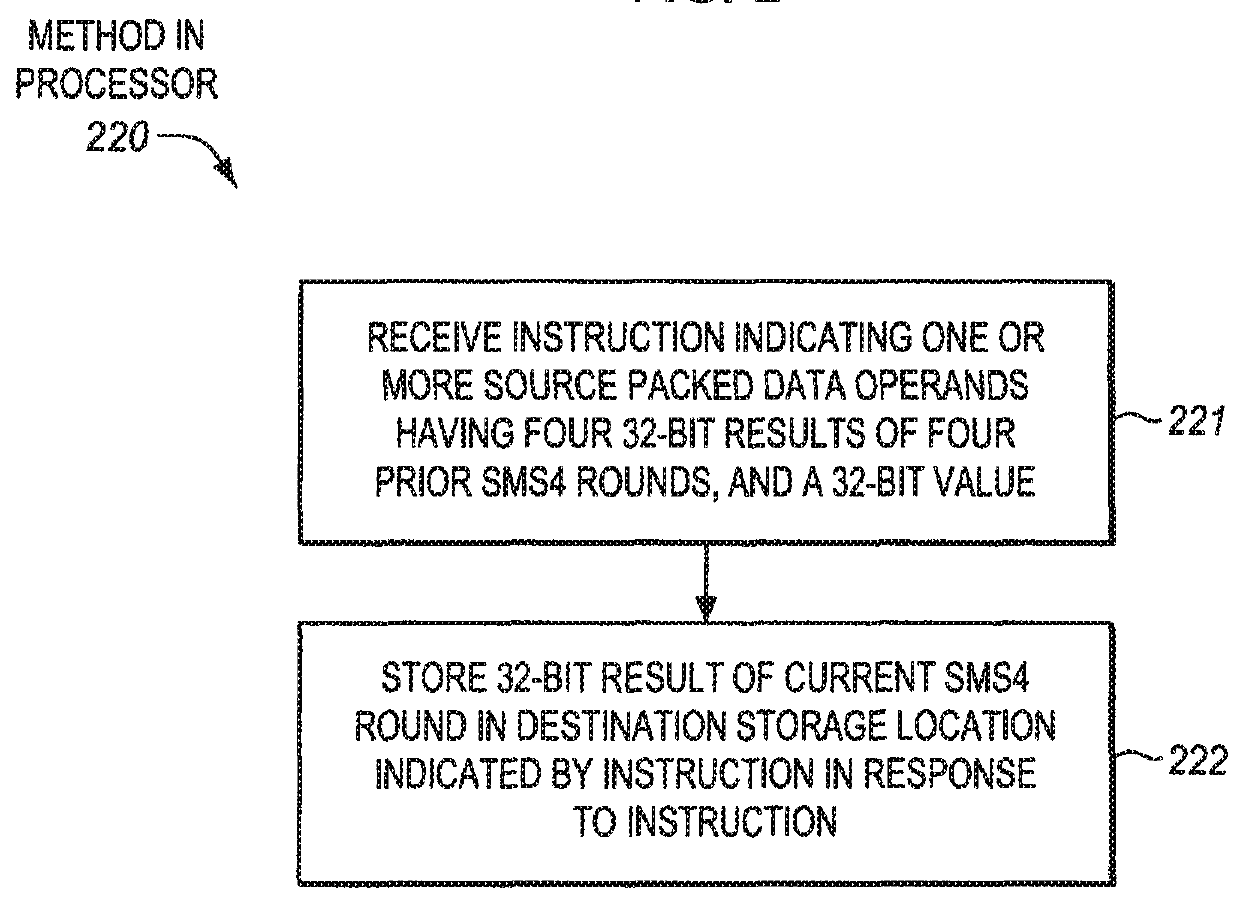
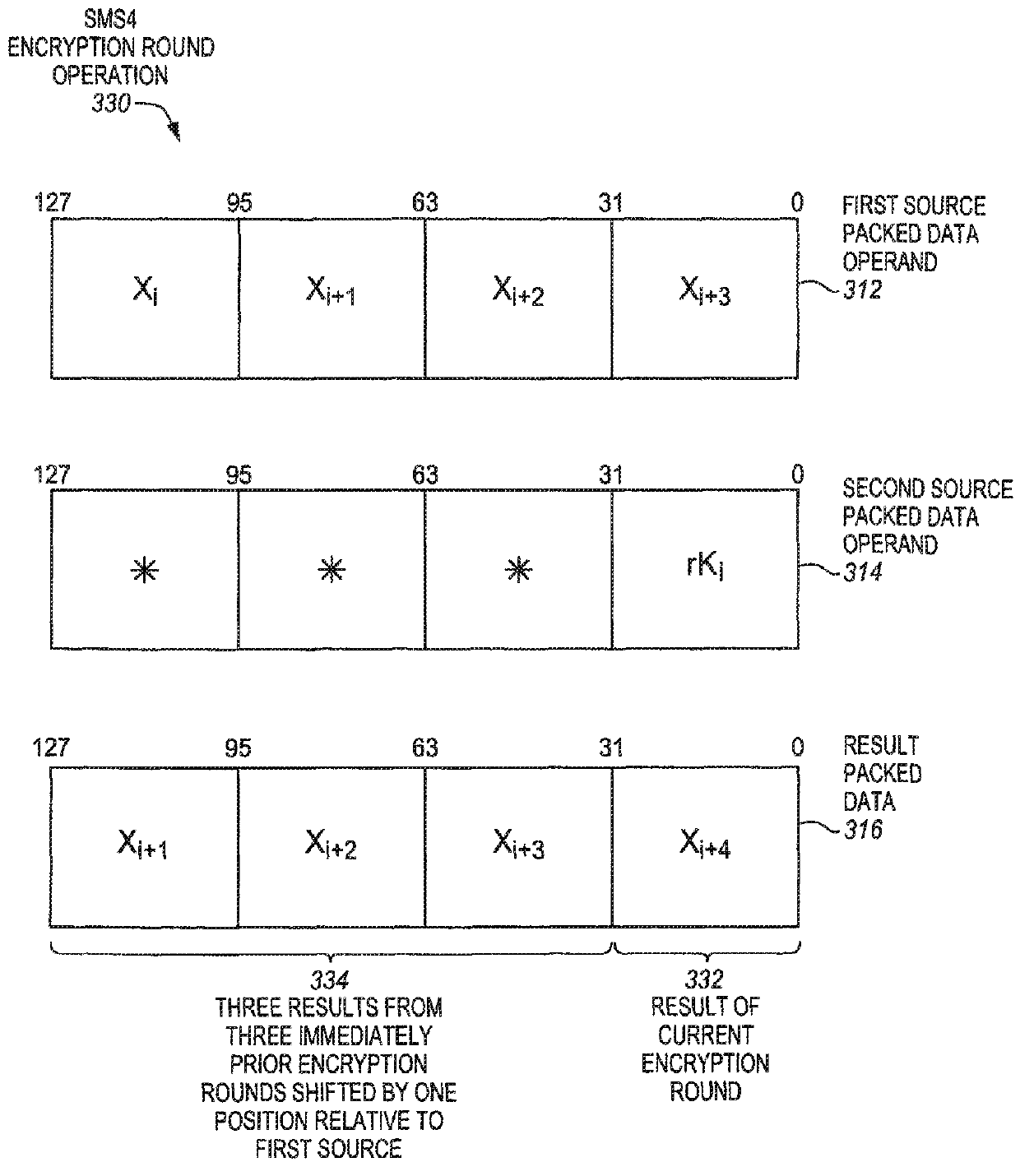
Sms4 acceleration processors, methods, systems, and instructions
A processor of an aspect includes a plurality of packed data registers and a decode unit to decode an instruction. The instruction is to indicate one or more source packed data operands. The one or more source packed data operands are to have four 32-bit results of four prior SMS4 rounds. The one or more source operands are also to have a 32-bit value. An execution unit is coupled with the decode unit and the plurality of the packed data registers. The execution unit, in response to the instruction, is to store a 32-bit result of a current SMS4 round in a destination storage location that is to be indicated by the instruction.
Owner:INTEL CORP
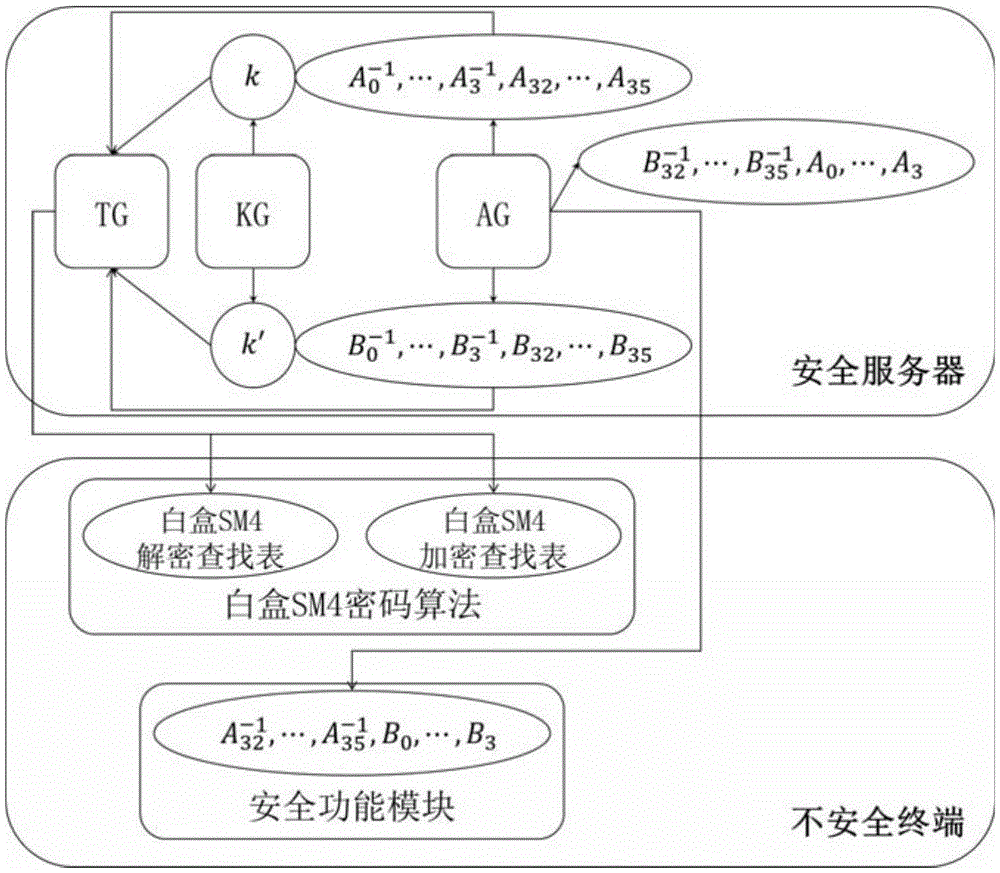
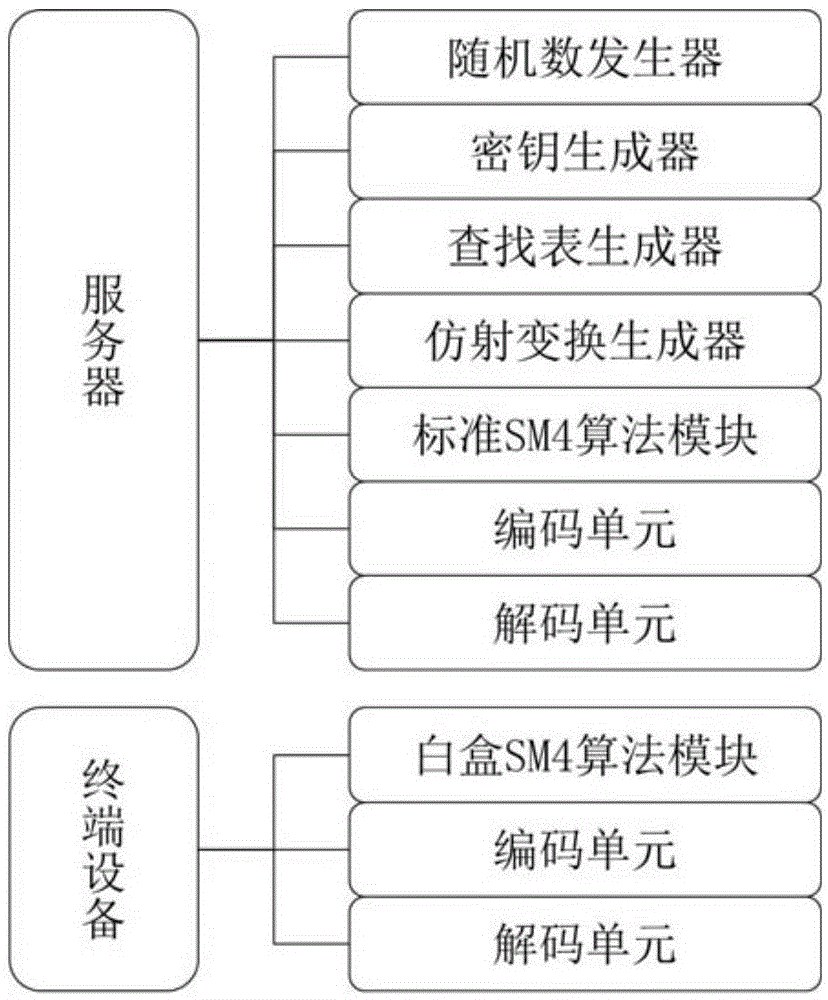
Security white box realizing method and device for national cipher standard algorithm SM4
InactiveCN105681025AEnsure safetySecurity advantageEncryption apparatus with shift registers/memoriesPasswordComputer terminal
The present invention discloses a security white box realizing method and device for the national cipher standard algorithm SM4, discloses essential components of equipment required by the white box SM4 algorithm, and belongs to the technical field of information security. With adoption of the method and the device, secret keys embedded into cipher software can be effectively protected in untrusted computer terminals. The white box SM4 password algorithm provided by the present invention achieves safe realization of the China commercial block cipher standard SM4. Secret keys are embedded into lookup tables, randomly selected affine codes are used for protecting the lookup tables, and thus the secret keys embedded in the lookup tables are protected. A TTC lookup table and a TRT lookup table are used in the algorithm, the last xor operation of output data of the TTC lookup table is embedded into the TRT lookup table, and output data of the TRT lookup table is protected by new 32-bit affine codes, so the situation of offsetting 32-bit affine codes embedded in the lookup tables by combining lookup tables can be prevented, thereby preventing reduction of code cracking difficulty, and realizing the protection aim.
Owner:INST OF INFORMATION ENG CAS
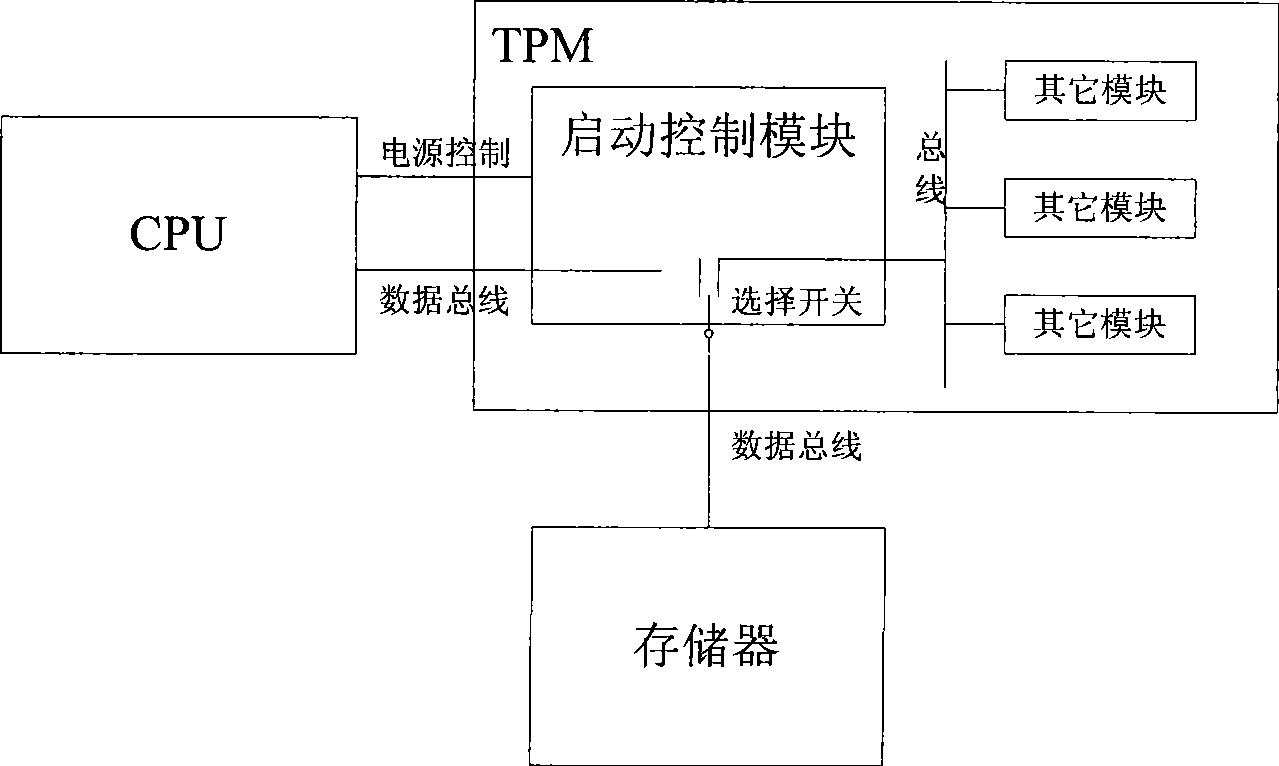
Trusted platform module and its computer starting control method
InactiveCN101504705AWith power controlFunctionalPlatform integrity maintainanceProgram loading/initiatingElectricityTrusted Platform Module
The invention provides a trusted platform module and a method for controlling computer starting by adopting the same. The novel trusted platform module with control function is formed by adding a starting control module into the prior trusted platform module to be combined with the prior trusted platform module. The novel trusted platform module is the first to be started when a computer is electrified and controls a starting flow so as to change the position that usually the trusted platform module is only slave equipment and ensure that the trusted platform module becomes main control equipment. The novel trusted platform module begins to work before the computer starts, provides bottom security, comprises a power supply for controlling a CPU of the computer and a data bus between the CPU of the computer and a storage of the computer, and performs integrity verification on a starting component of the computer. The trusted platform module and the method also use hardware to realize SMS4 symmetric cryptographic algorithm and remedy the advantages of the prior trusted platform module. The trusted platform module can fully control the starting flow of the computer, and has the advantages of high security, quick encryption / decryption operation, reliable operation and the like.
Owner:WUHAN UNIV
Gait bio-feature based mobile device identity recognition method
The invention provides a gait bio-feature based mobile device identity recognition method. The method is combined with a mobile terminal and is perfection and expansion of an existing bio-identification technology. The method consists of two parts of a training module and an identification module. The training module comprises three steps of data acquisition, feature extraction and model establishment; and the identification module comprises to-be-identified user data collection, model matching and notification response. According to the method, by utilizing self functions and convenience of the mobile terminal, data is completely acquired, a scientific mathematic basic model is constructed, and gait information of a user is obtained, so that user uniqueness is ensured. A system adopts a national SMS4 symmetric encryption algorithm to perform encryption, so that the data transmission security is well ensured. The method has the advantages that rich sensor and network functions of the mobile device are fully utilized, a modeling process is combined with daily gaits of the user, and the bio-identification technology can be continuously perfected without the need for a deliberate operation. Compared with other identification modes, the security system is relatively high in concealing property and difficult to target. Meanwhile, no contact is required, the concealing is difficult, and remote identification can be performed, so that the user security guarantee is greatly improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
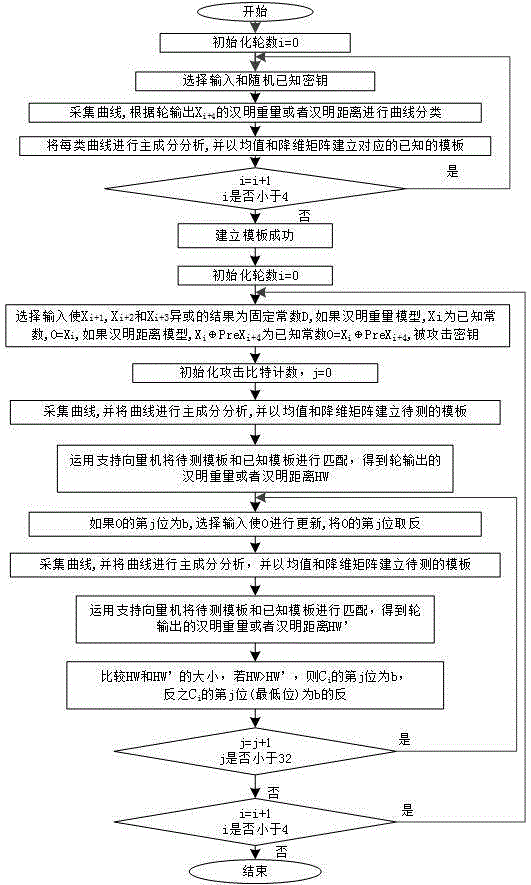
Second-order side channel energy analysis method for SM4 algorithm of simple mask
ActiveCN103647637ABreaking new ground for attackExtended side channel energy analysis methodEncryption apparatus with shift registers/memoriesPower analysisS-box
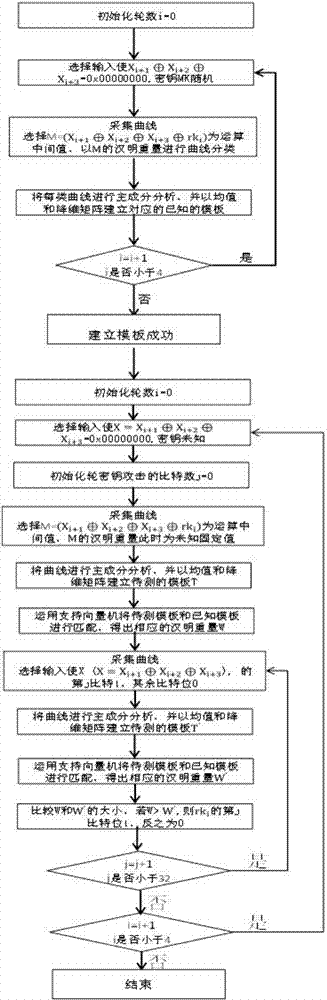
The invention discloses a second-order side channel energy analysis method for an SM4 algorithm of a simple mask. To achieve mask protection for the SM4 algorithm with the output of four S boxes carrying the same mask value, the method comprises the steps of (1) acquiring energy traces and establishing a sampling energy consumption matrix; (2) preprocessing the energy consumption matrix in the previous step; (3) selecting attack points to conduct CPA or DPA to obtain rki, 0; (4) re-selecting an S-box operation part and following the steps (2) and (3) to obtain rki, u through analysis; and (5) carrying out the steps (2), (3) and (4) on previous / next four rounds to obtain a round key and obtaining an initial key through a key inverse expansion operation. The technical scheme of the invention innovatively provides the new second-order energy analysis method, develops a new situation of SM4 cryptographic algorithm attack, extends the side channel power analysis method for the SM4 algorithm, and can fully and effectively conducts side channel energy analysis on the SM4 cryptographic algorithm; and the method of the technical scheme is highly practical for common mask protection measures.
Owner:国家密码管理局商用密码检测中心
Encrypting and deciphering system for realizing SMS4 algorithm
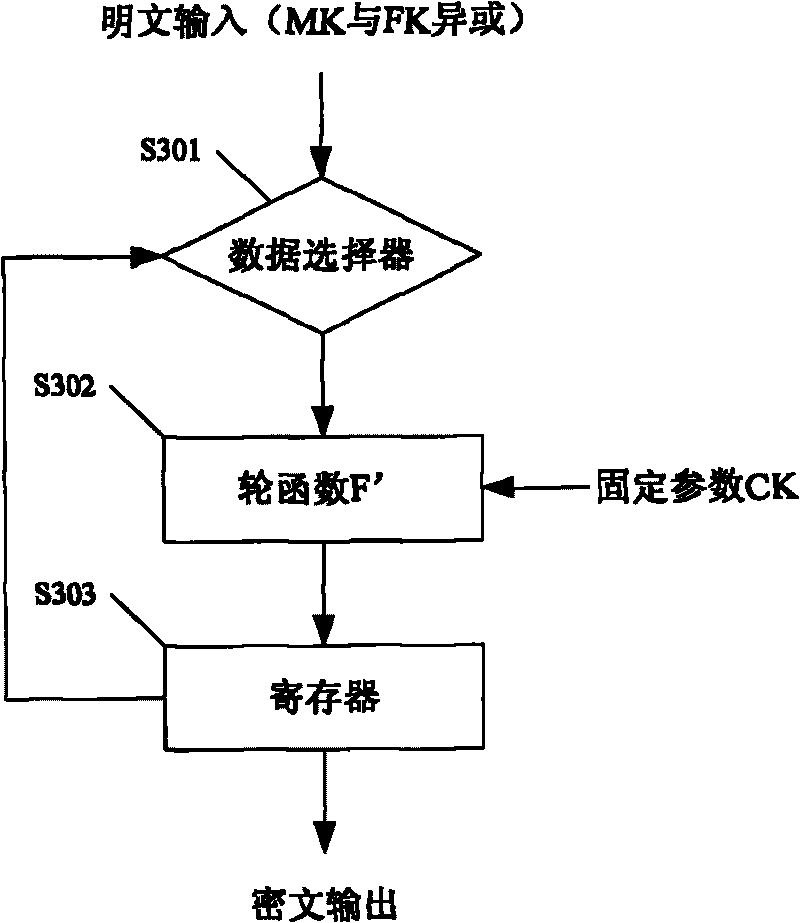
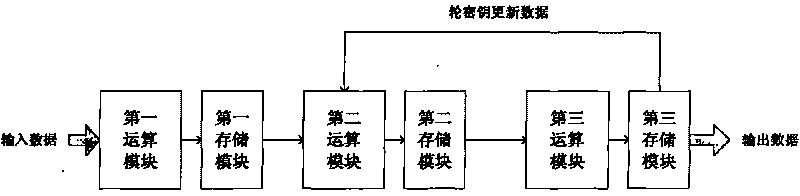
InactiveCN101764685AReduce redundancyEncryption apparatus with shift registers/memoriesProduction lineThree stage
The invention relates to the field of block cipher algorithm of wireless local network, and provides an encrypting and deciphering system for realizing SMS4 algorithm; the encrypting and deciphering system comprises a first operation module and a first-stage production line of a first storing module, a second operation module and a second -stage production line of a second storing module and a third operation module and a third -stage production line of a third storing module. The three operation modules in the technical scheme of the invention realize functional reuse for encryption and decryption operation and round key spreading operation, thereby directly reducing component redundancy and reducing the occupied area of the system. Moreover, the invention adopts three-stage production line structure to deal with three groups of data simultaneously, and in which any group of data can be the encryption and decryption operation or the round key spreading operation, so as to improve system efficiency.
Owner:GCI SCI & TECH
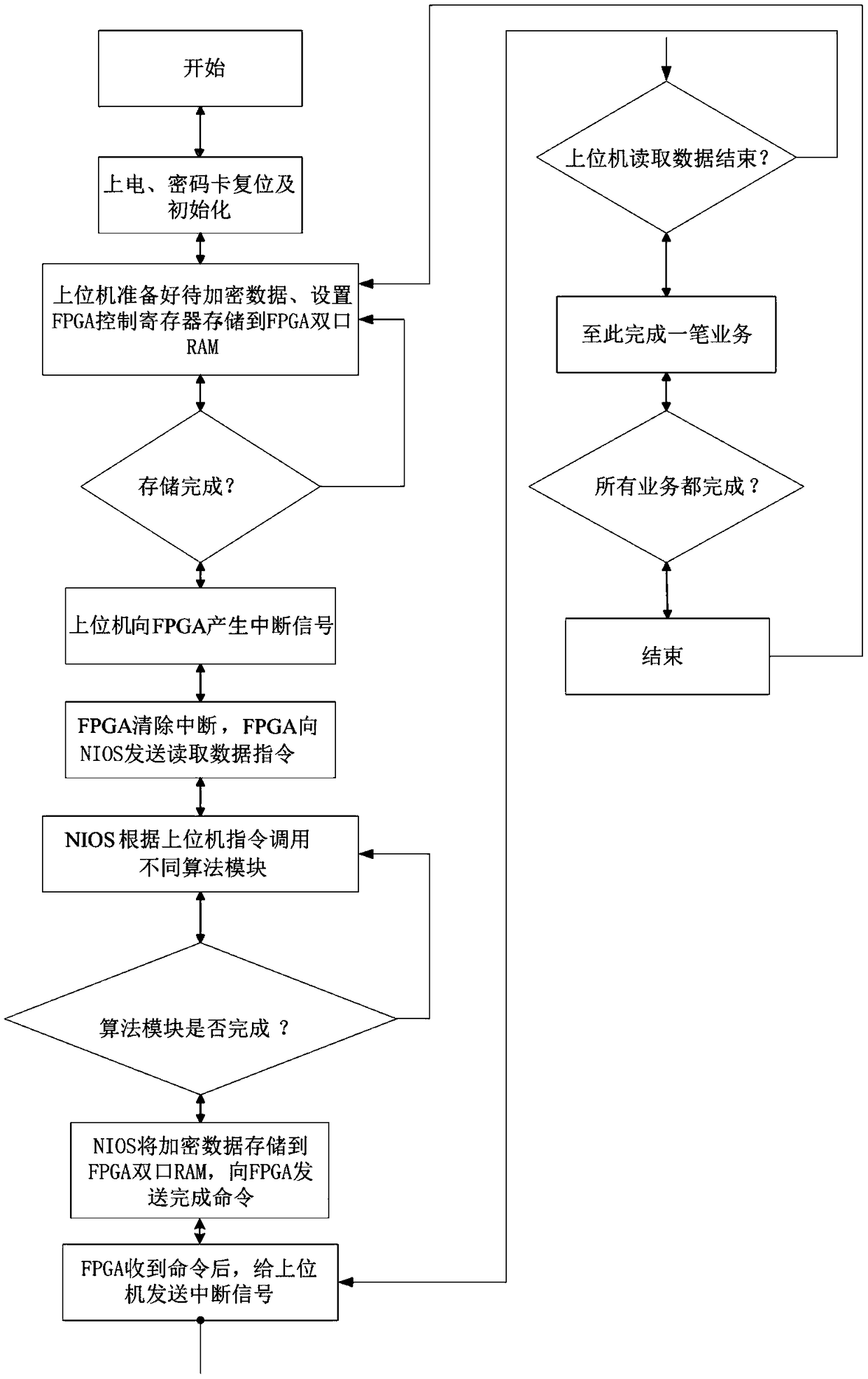
A full algorithm cryptographic card based on PCI-E interface and an encryption method thereof
InactiveCN109145568AImprove security strengthImprove securityDigital data authenticationEnergy efficient computingAlgorithmic State MachineSERCOS interface
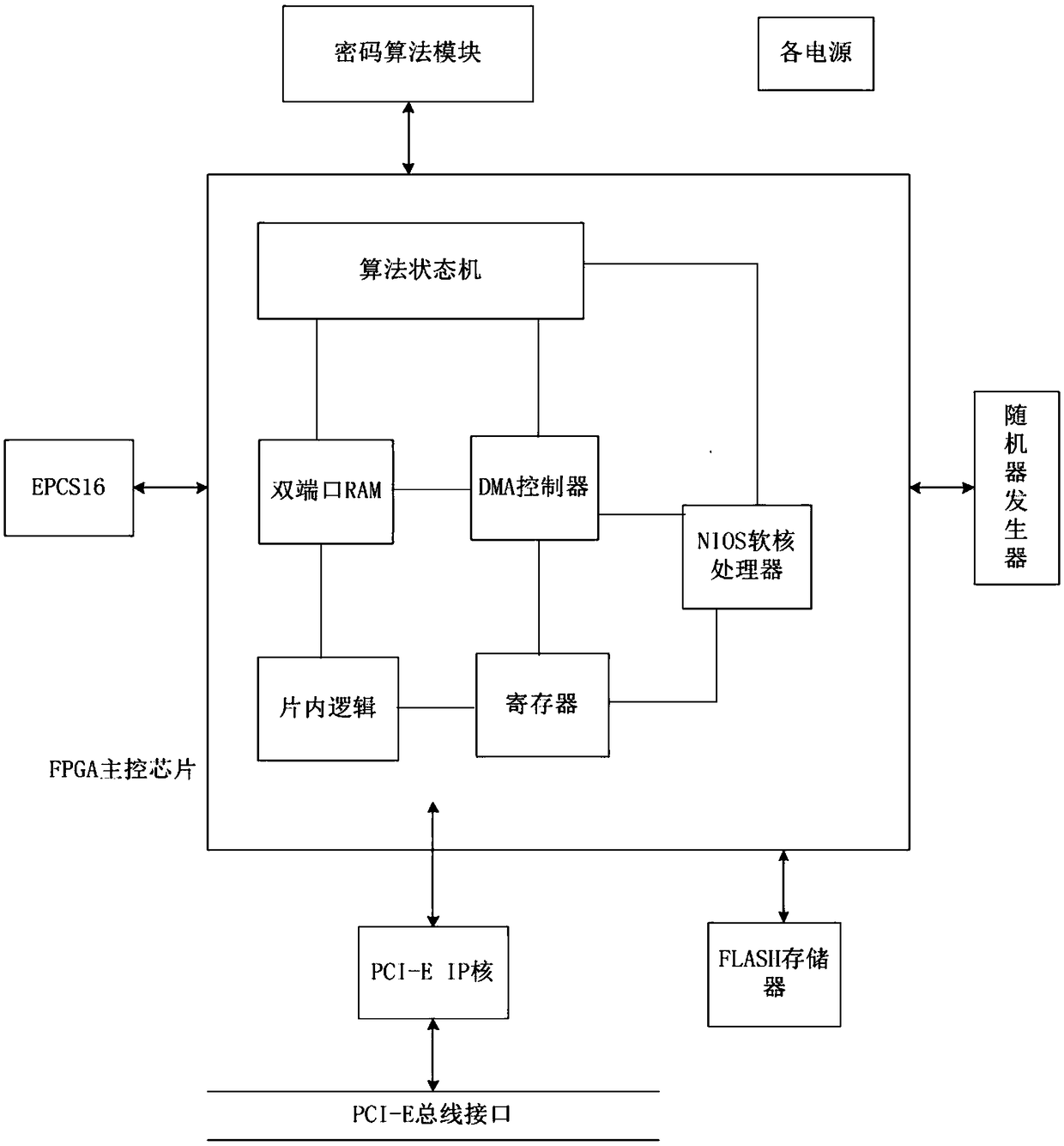
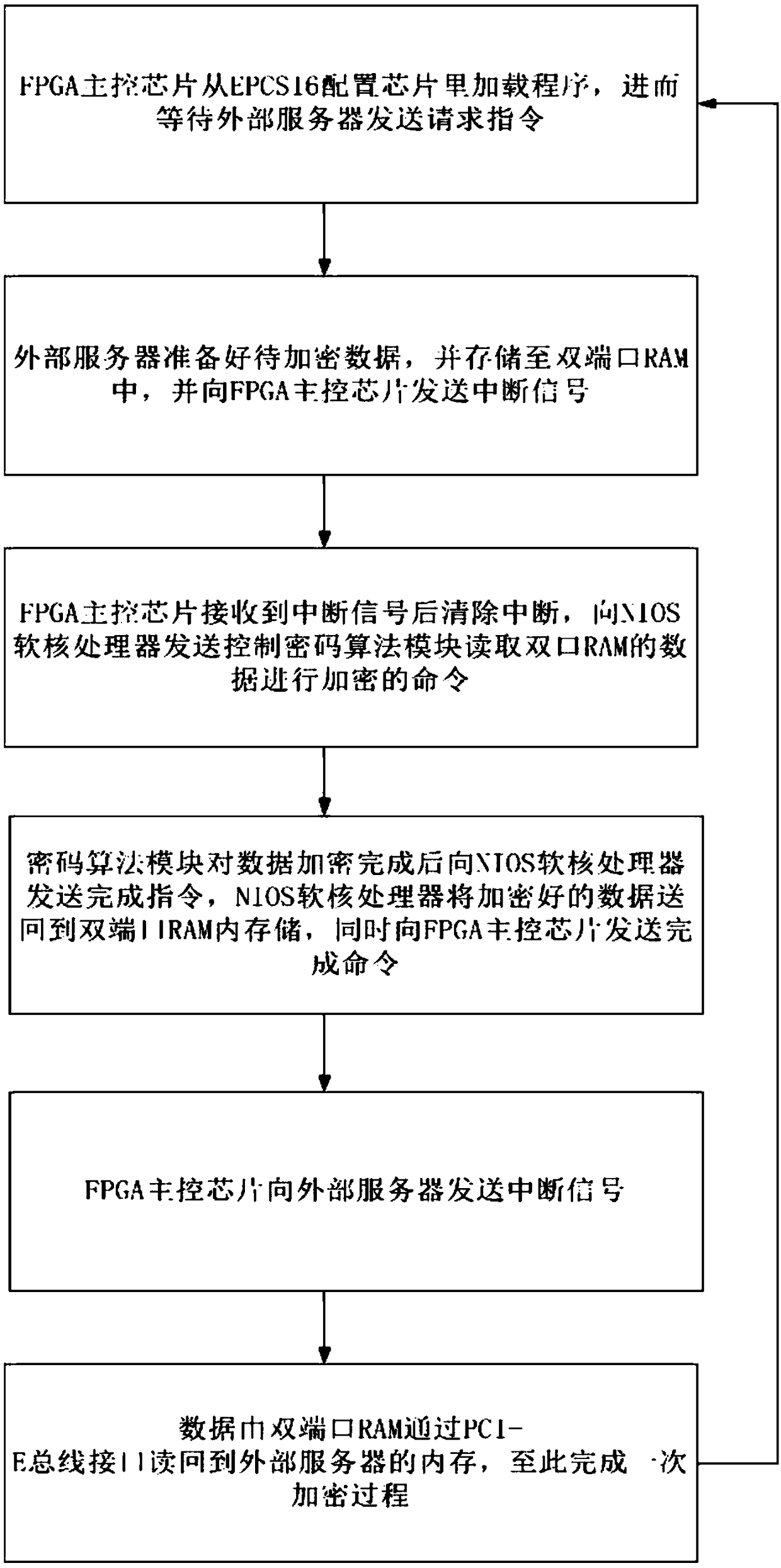
The invention discloses a method based on PCI-E interface full algorithm cryptographic card, including: a cryptographic algorithm module, a FLASH memory, a PCI-E bus interface, a random numb generator, and an FPGA master control chip with NIOS soft core processor, wherein a PCI-E IP core and an algorithm state machine are integrated in the FPGA master control chip. The cryptographic algorithm module comprises a symmetric key encryption SM4 algorithm chip, a symmetric key encryption SM1 algorithm chip and an asymmetric key encryption SM2 algorithm chip. The invention also discloses an encryption method of the cipher card. The invention provides a high-performance full-algorithm cryptographic card, which simultaneously reduces the complexity of hardware circuit and energy consumption, improves the key operation speed, and the cryptographic card adopts a home-made cryptographic algorithm, so that the user's key is most securely protected.
Owner:西安得安信息技术有限公司
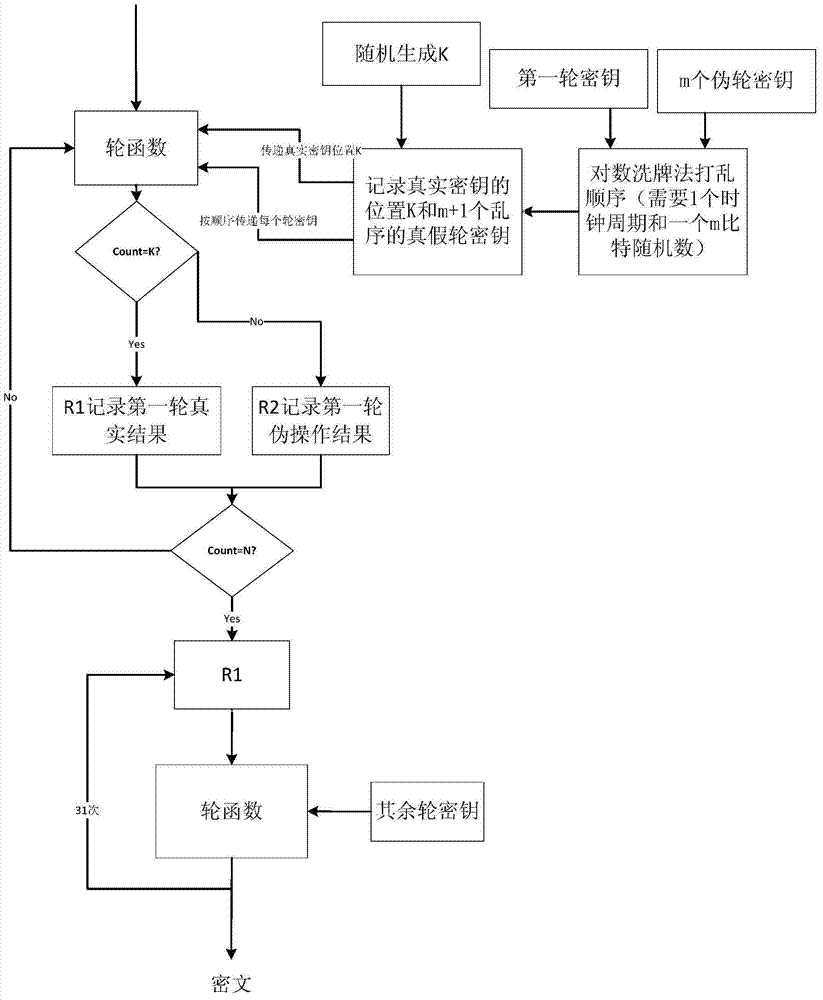
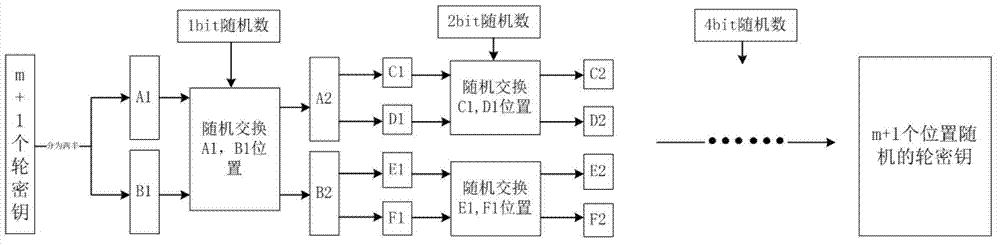
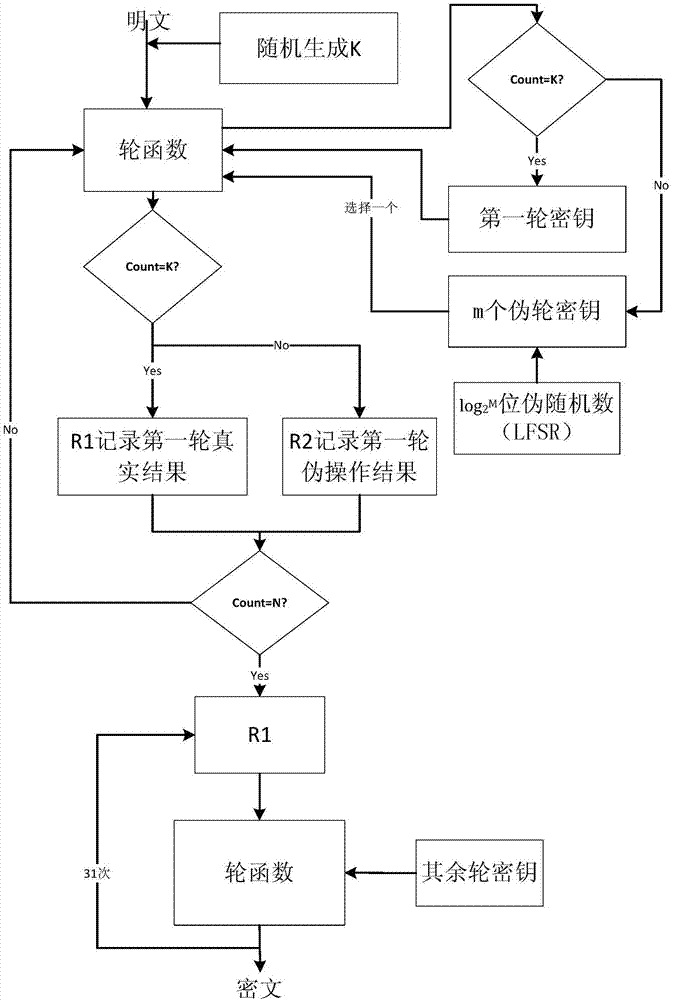
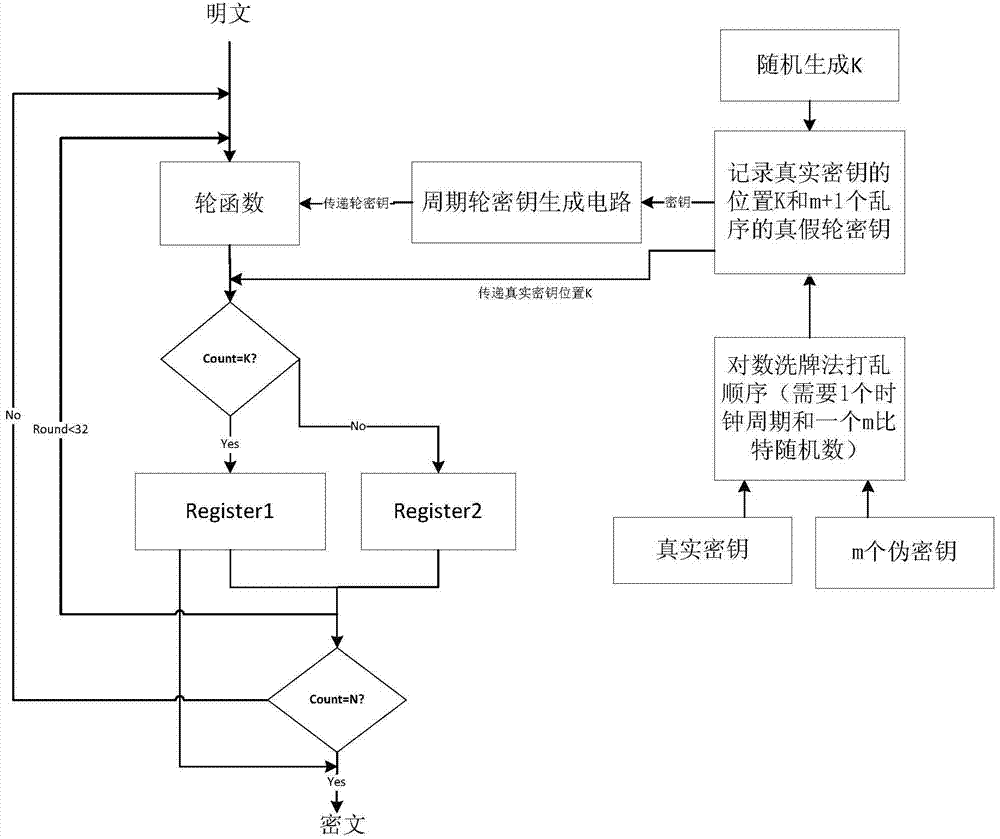
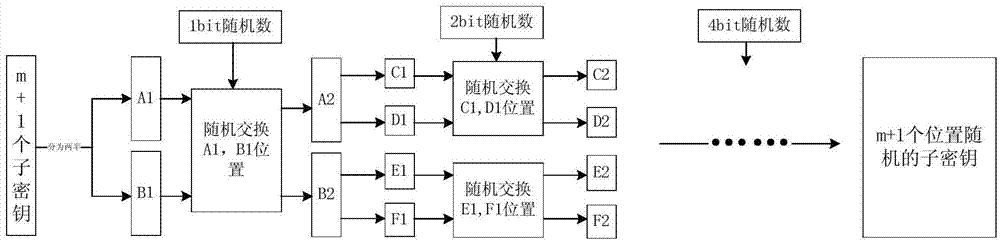
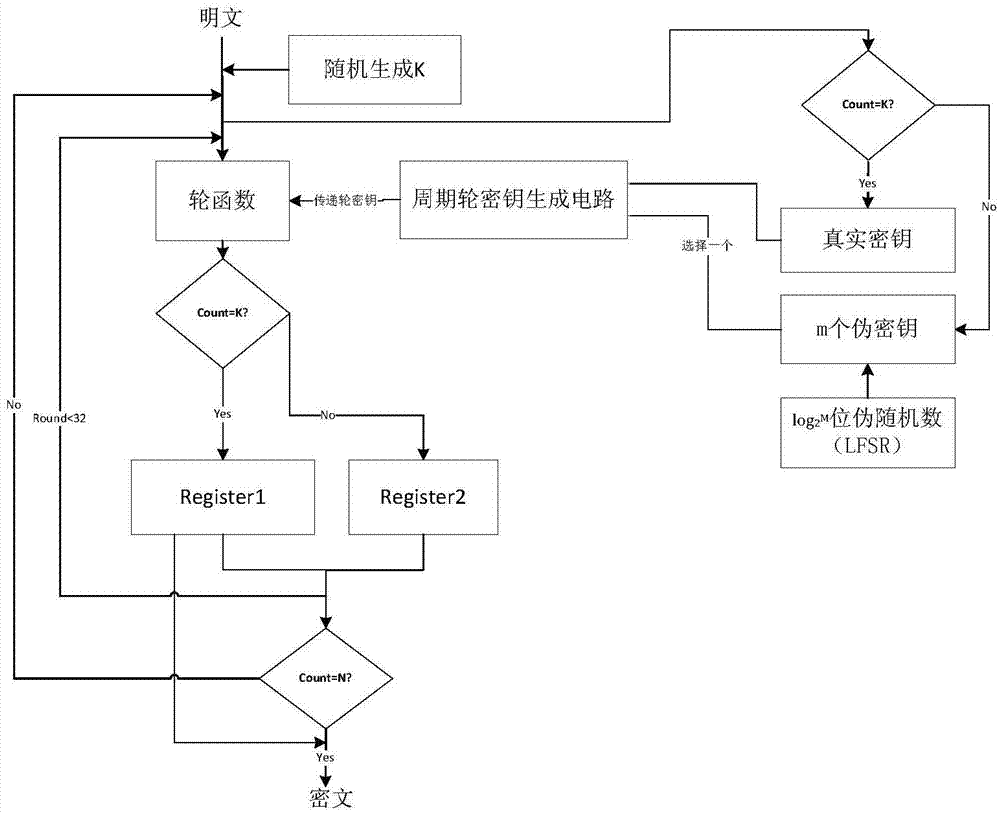
Resisting method of circuit on side channel attack based on pseudo-operation
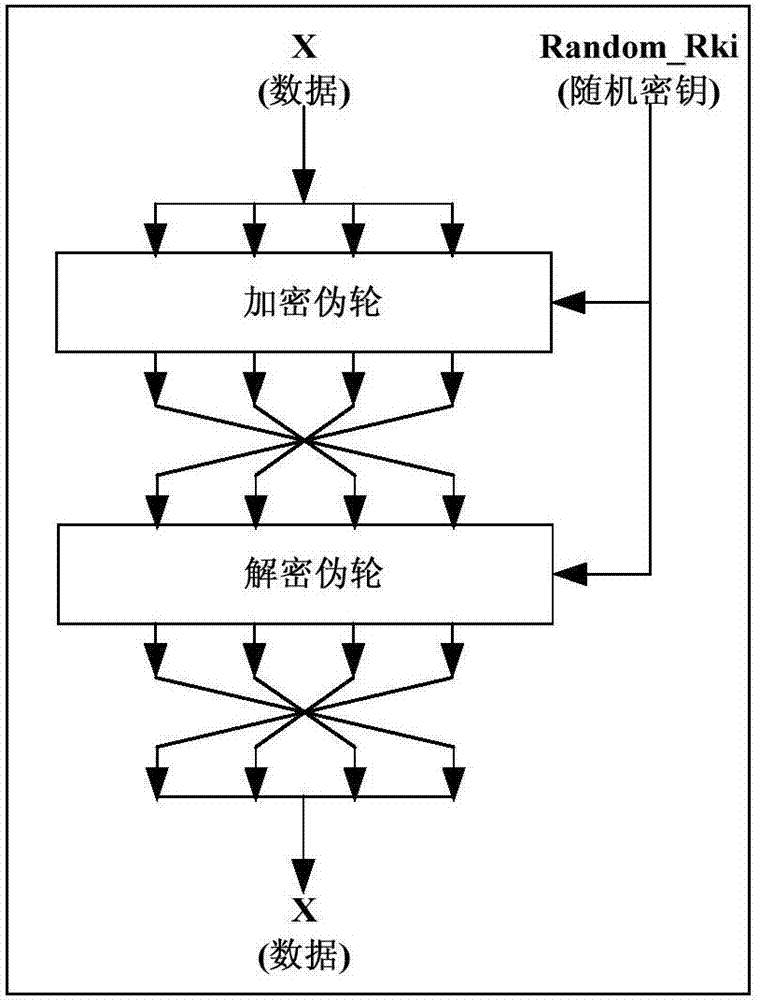
The invention discloses a resisting method of a circuit on the side channel attack based on the pseudo-operation, and belongs to the technical field of computer security. A round secret key sequence is composed by m pseudo-round secret keys and one real-round secret key to conduct the first round SMS4 encrypting calculation, a second round SMS4 encrypting calculation is conducted on the result of the first round SMS4 encrypting calculation with the participation of the real-round secret key, and a ciphertext is acquired. According to the resisting method of the circuit on the side channel attack based on the pseudo-operation, the position of the generated first round SMS4 encrypting calculation is random, and an attacker cannot align with a power-consumption curve, so that the attack cannot be realized; in addition, compared with an unprotected circuit, the energy consumption cannot exceed the two times of the original energy consumption.
Owner:SHANGHAI JIAO TONG UNIV +2
SM4 method capable of resisting energy analysis attack
ActiveCN104333447AGood for unmaskingEasy to implementEncryption apparatus with shift registers/memoriesPower analysisComputer hardware
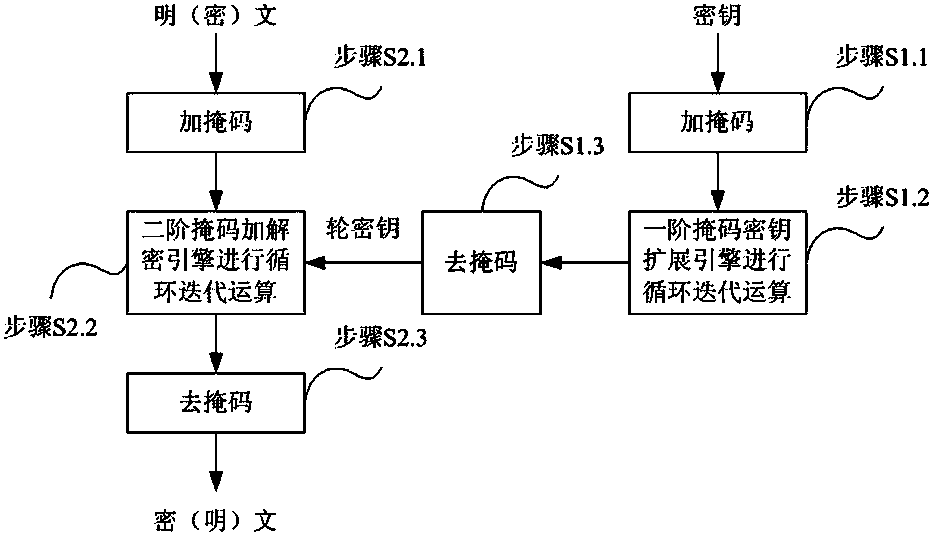
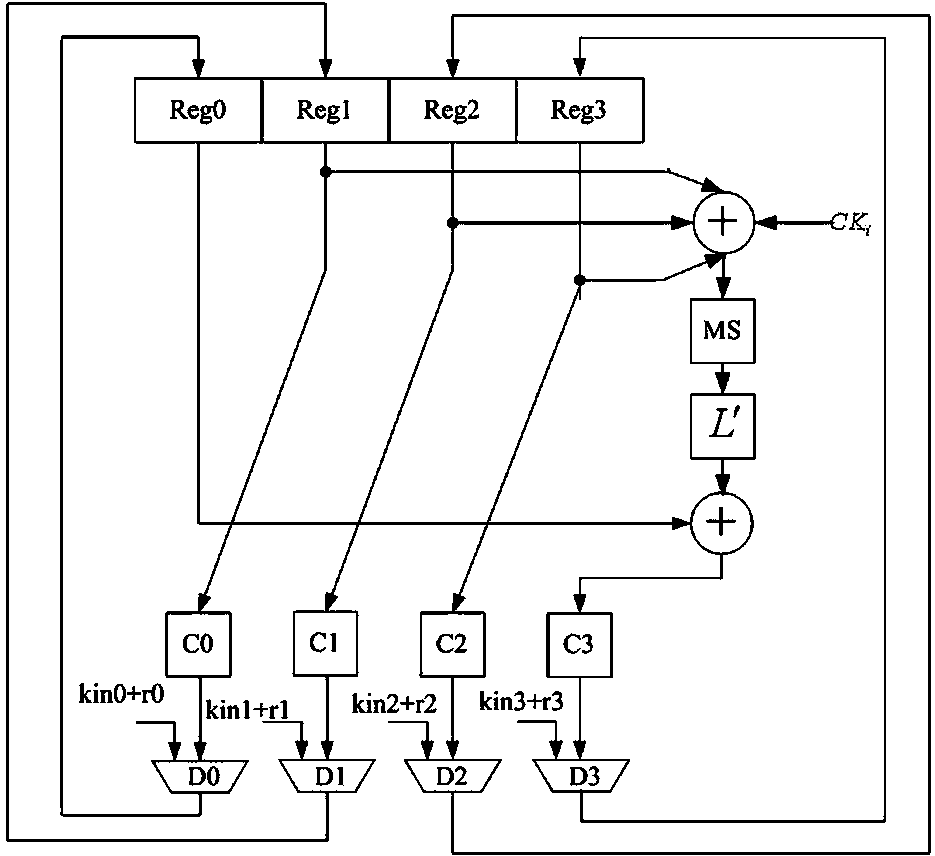
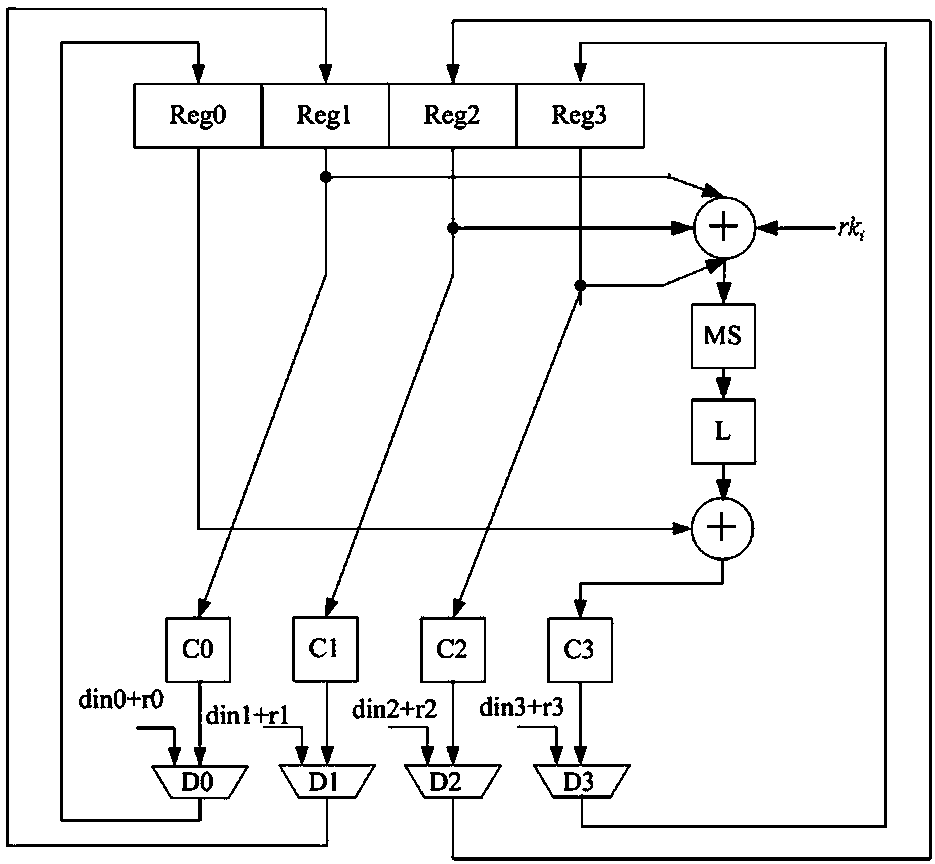
The invention relates to an SM4 method capable of resisting energy analysis attack. The method comprises the following steps: carrying out secret key expansion operation on an input secret key by a first-order mask secret key expansion engine, outputting a round key to a second-order mask encryption / decryption engine, carrying out 32-round loop iteration operation on input plaintext / ciphertext and the round key by the second-order mask encryption / decryption engine, and outputting the plaintext / ciphertext. According to the SM4 method, the encryption / decryption engine for SM4 is realized by use of a second-order mask, the secret key expansion engine for the SM4 algorithm is realized by use of a first-order mask, the method can be used for resisting the high-order energy analysis attack in an encryption / decryption process, resisting template attack in a secrete key expansion process, and effectively improving the hardware implementation safety of the SM4 algorithm.
Owner:SHANGHAI AISINOCHIP ELECTRONICS TECH
Template attack method in allusion to SM4 cipher algorithm round output
ActiveCN104868990AEncryption apparatus with shift registers/memoriesTemplate matchingSupport vector machine
The invention discloses a template attack method in allusion to SM4 cipher algorithm round output. According to the method disclosed by the invention, special channel input is taken as a premise, the SM4 algorithm round output is used as an attack point, the hamming weight or the hamming distance of the round output is selected to establish a template, and template attack in allusion to the SM4 cipher algorithm round output can be realized by a small number of templates. Meanwhile, selective input is taken as a basis in a template matching stage, a support vector machine is used to act as a tool for judgment and analysis, a bit of linear transformation output can be broken by only two times of matching, and then a round sub-key is reversely derived by inverse transformation of nonlinear transformation and linear transformation. The method disclosed by the invention effectively solves a problem that template attack in allusion to the SM4 cipher algorithm round number is infeasible at the present stage.
Owner:CHENGDU UNIV OF INFORMATION TECH +3
System for realizing SM4 algorithm at super-speed as well as operating method of system
ActiveCN104579636ASolve the speed bottleneckRealize collaborative flowEncryption apparatus with shift registers/memoriesData channelSingle task
The invention relates to a system for realizing SM4 algorithm at a super-speed. The system comprises a control module, a cipher-expanding / ciphering / deciphering module, a ciphering / deciphering module, a ciphering / deciphering module, a data channel subdivider, a cipher-expanding / ciphering and deciphering selector, a round cipher / result channel subdivider and a result selector. The system provided by the invention solves the problem that the speed is low in the existing hardware system as 32 round keys are computed to cipher, and during single task operation, the treatment speed can reach nearly two folds of the existing hardware system. Based on the thought of module reusability, three tasks are synchronously ciphered and deciphered, and the problem that a deciphering module is idle during frequent ciphering tasks in conventional design is solved, so that the utilization ratio and operating speed of the system are effectively improved; during multi-task operation without changing the keys, the processing speed reaches three times that of the single-task operation, the fastest six times that of the existing hardware system.
Owner:BINZHOU POLYTECHNIC
SM4 algorithm encryption unit based on FPGA chip and USB interface chip
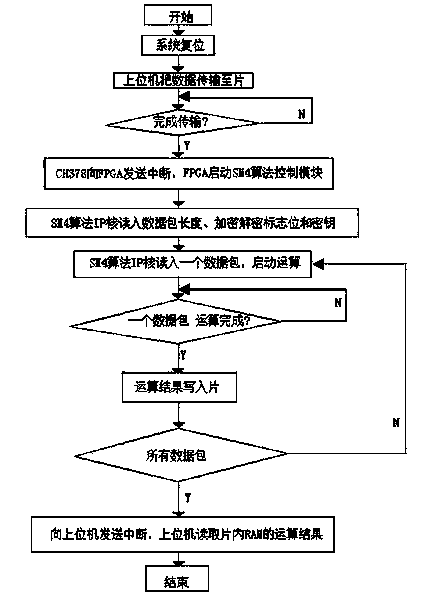
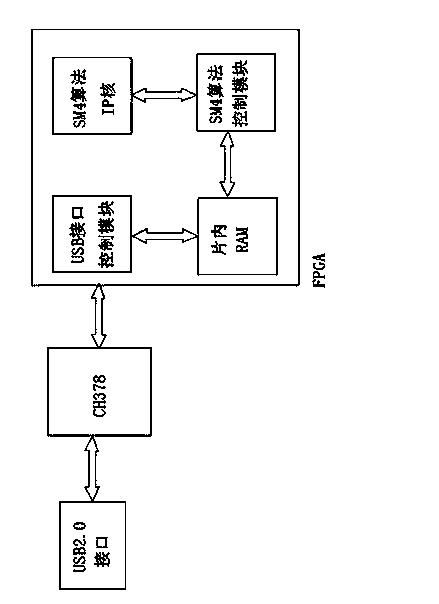
InactiveCN103973432AFast data encryption and decryptionImprove securityEncryption apparatus with shift registers/memoriesComputer hardwareFpga implementations
The invention discloses an SM4 algorithm encryption unit based on an FPGA chip and a USB interface chip. The SM4 algorithm encryption unit based on the FPGA chip and the USB interface chip comprises the USB interface chip, the FPGA chip, a USB interface control module, an SM4 algorithm IP core, an SM4 algorithm control module and an on-chip RAM, wherein the USB interface control module, the SM4 algorithm IP core, the SM4 algorithm control module and the on-chip RAM are realized through the FPGA chip. In the SM4 algorithm encryption unit, the FPGA chip serves as a control core, and the SM4 algorithm IP core and the related control module are realized through the VHDL design; the SM4 algorithm encryption unit is connected to a user terminal through a USB interface, it is guaranteed that important data of a user are transmitted in a ciphertext mode in the network, and consequently quick operation and secure transmission of the data are achieved. The SM4 algorithm encryption unit based on the FPGA chip and the USB interface chip has the advantages of being high in data encryption and decryption speed, high in security, convenient to use and the like.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Side-channel attack protection method based on full-encryption algorithm pseudo-operation
ActiveCN104734845AKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareCiphertext
The invention provides a side-channel attack protection method based on full-encryption algorithm pseudo-operation in the technical field of computer security. Multiple times of SMS4 encryption calculation is conducted through a secret key sequence composed of m pseudo secret keys and a true secret key, and required ciphertext is obtained through the SMS4 encryption calculation result which the true secret key participates in. The position of generated true operation is random, an attacker can not align with a power consumption curve, and therefore attacks can not be achieved. In addition, no interference effect on side-channel attacks can be achieved when the pseudo secret keys are used, and the side-channel attacks can lose efficacy. The scheme can be achieved through a full-hardware mode or a software calling mode, and by means of the software calling method, password circuits where hardware can not be modified and side-channel attacks can not be prevented can be protected.
Owner:SHANGHAI JIAO TONG UNIV +2
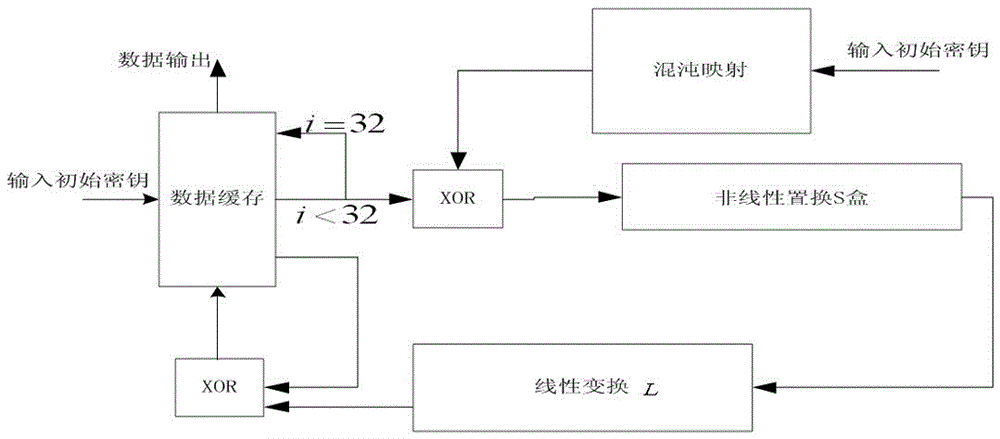
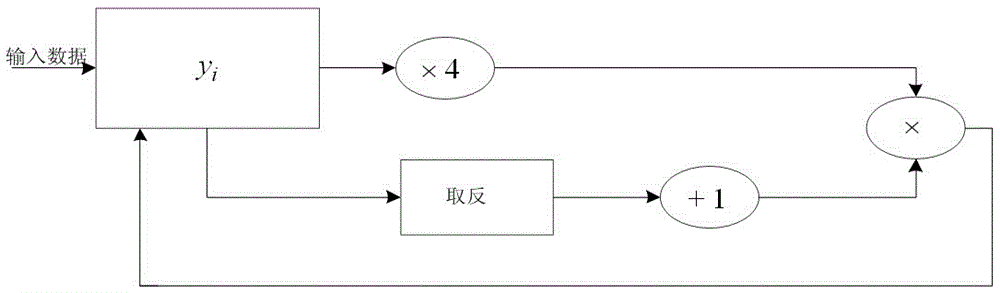
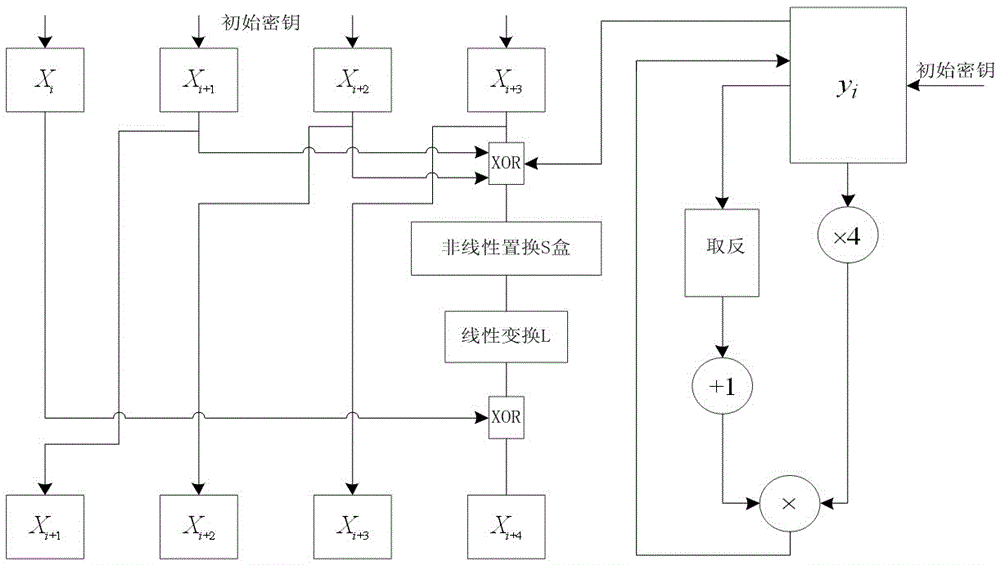
Long key-based realization system and method for SM4 key extending algorithm
ActiveCN106209358AIncrease randomnessLarge key spaceKey distribution for secure communicationSecuring communication by chaotic signalsS-boxTheoretical computer science
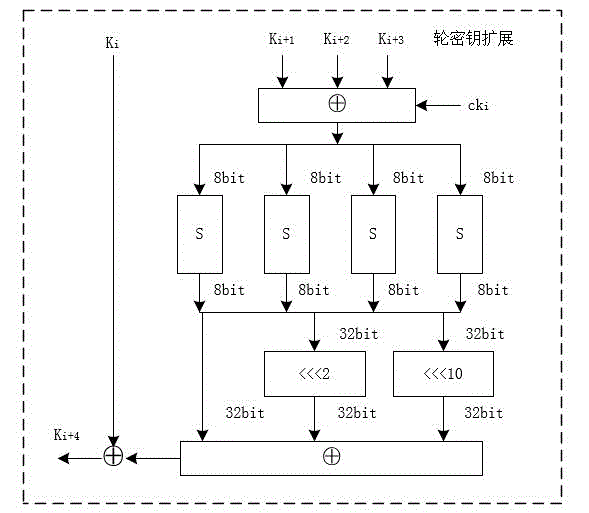
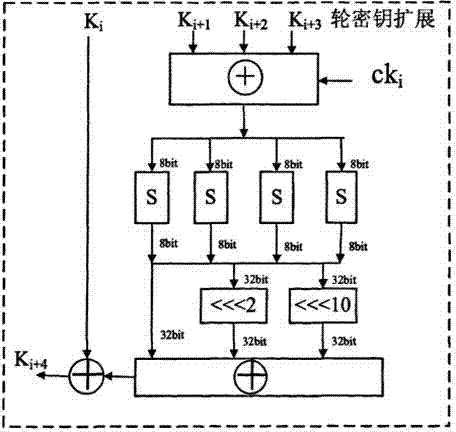
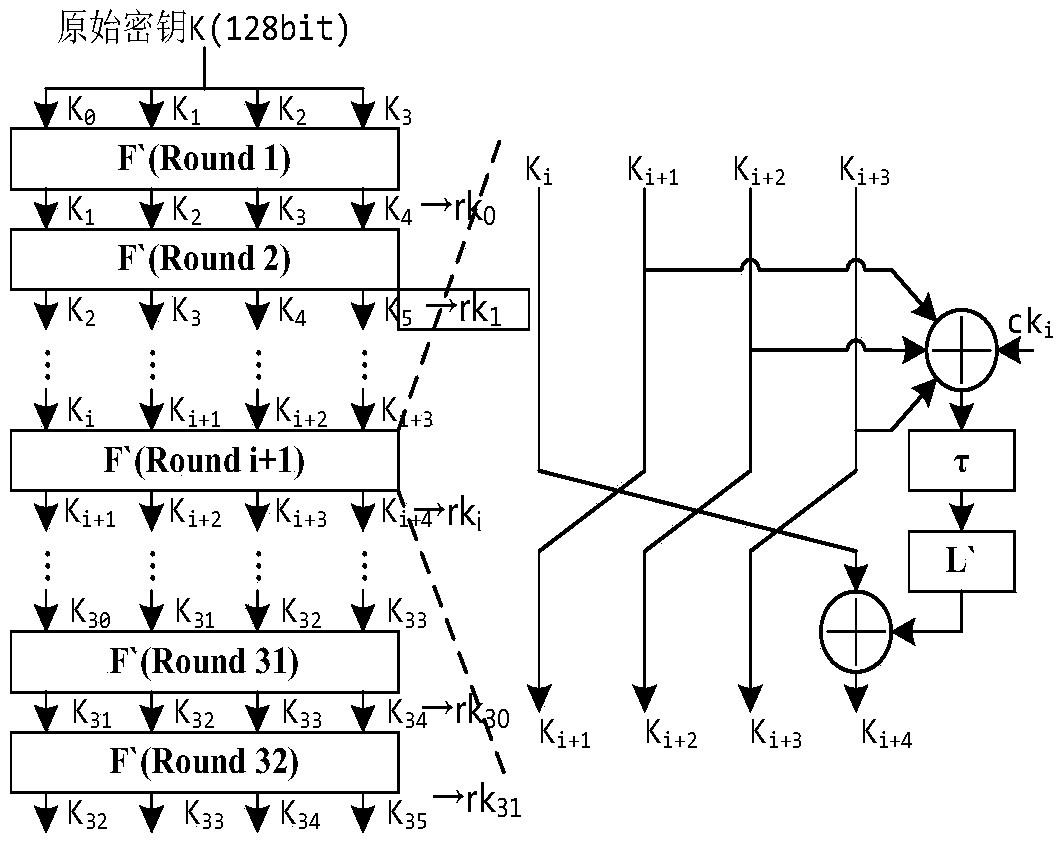
The invention discloses a long key-based realization system and method for an SM4 key extending algorithm. The system comprises a chaotic mapping module, a data caching module, an xor module, a nonlinear permutation S box module and a linear transformation L module, wherein an input of the chaotic mapping module is a partial initial key, a pseudorandom sequence with good randomness is generated as an input of an original SM4 key extending algorithm by utilizing multi-time iterations of chaotic mapping, and the chaotic mapping module selects Logistic mapping through considering chaotic performance and hardware implementation resource consumption; and the chaotic mapping is fused in the SM4 key extending algorithm. By optimizing the SM4 key extending algorithm, the key space of the SM4 algorithm is expanded and the randomness of sub-keys in each round is enhanced.
Owner:HEILONGJIANG UNIV
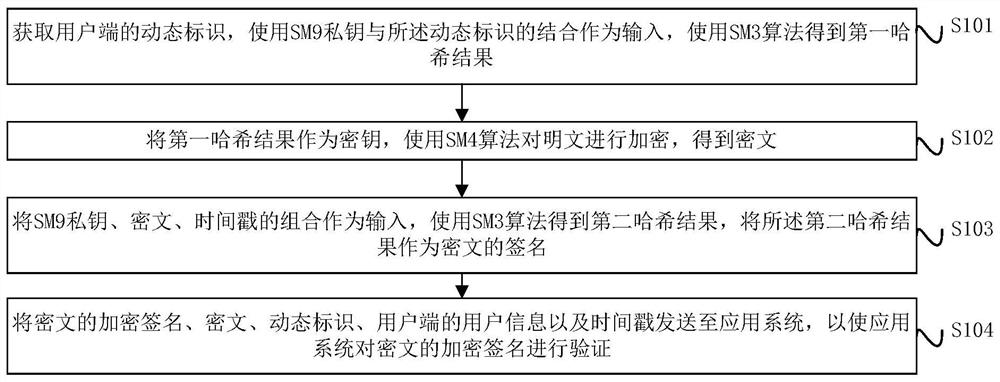
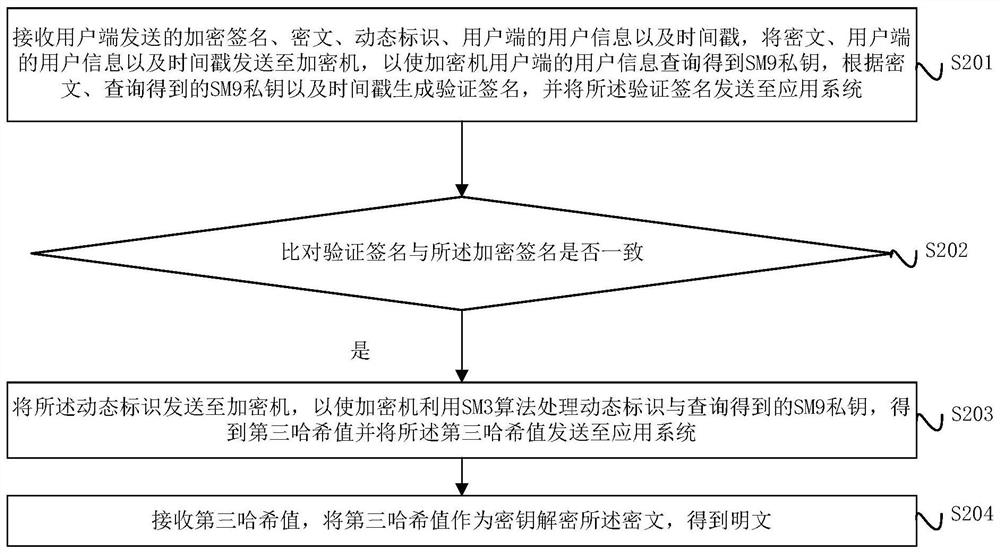
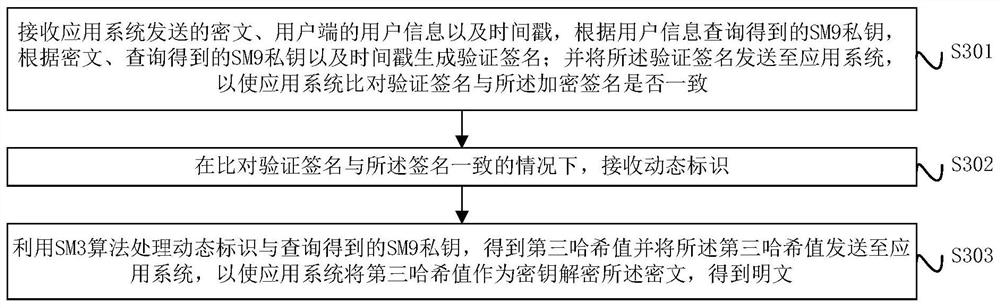
Digital signature and verification method, device and system
ActiveCN112688784AIncrease computing speedImprove signature efficiencyEncryption apparatus with shift registers/memoriesUser identity/authority verificationPlaintextTimestamp
The invention provides a digital signature and a verification method, device and system, and the method comprises the steps: obtaining a dynamic identification of a user side, taking the combination of an SM9 private key and the dynamic identification as an input, and obtaining a first hash result through an SM3 algorithm; taking the first hash result as a key, and encrypting the plaintext by using an SM4 algorithm to obtain a ciphertext; taking a combination of the SM9 private key, the ciphertext and the timestamp as input, obtaining a second hash result by using an SM3 algorithm, and taking the second hash result as an encrypted signature of the ciphertext; and sending the encrypted signature of the ciphertext, the ciphertext, the dynamic identifier, the user information of the user side and the timestamp to an application system, so that the application system verifies the encrypted signature of the ciphertext.
Owner:中科美络科技股份有限公司
Secure transmission method of private cloud medical data
InactiveCN107026859ASatisfy real-timeFast operationUser identity/authority verificationSecure transmissionPrivacy protection
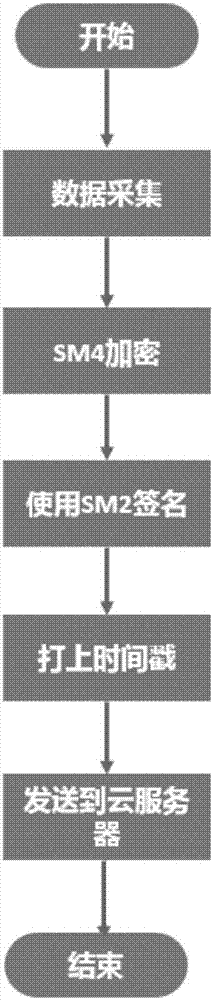
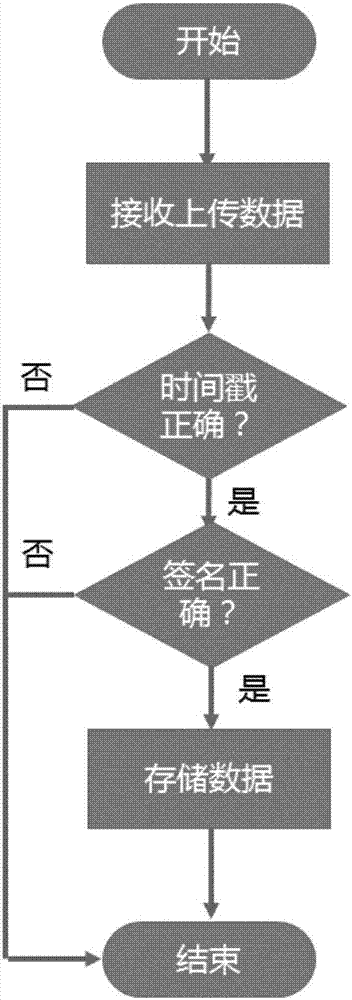
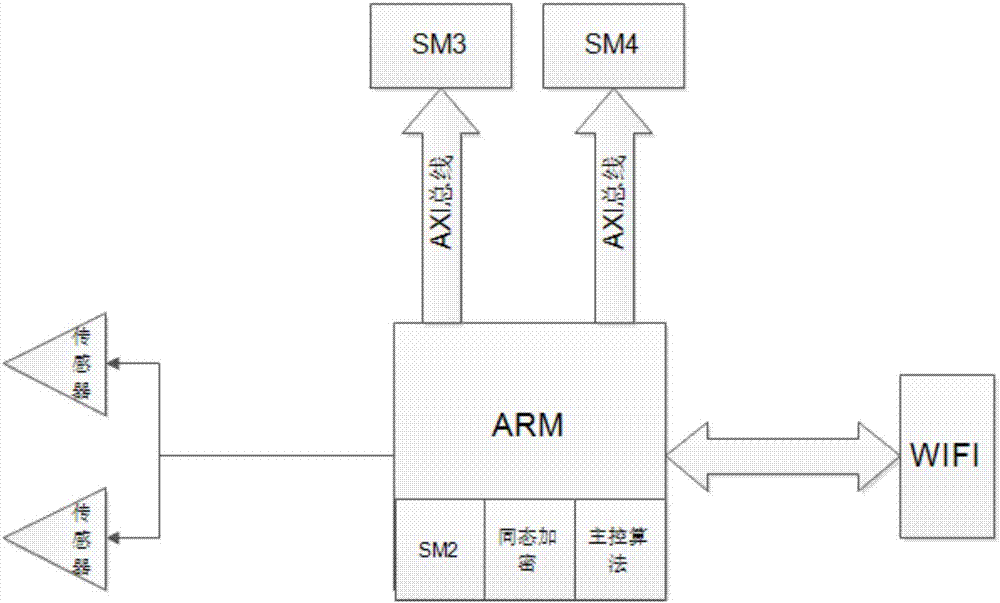
The invention discloses a secure transmission method of private cloud medical data. The method comprises the following steps: encrypting collected data by calling an IP core of an SM4 algorithm by an ARM through an AXI bus, performing digital signature on the encrypted data by the ARM by using an SM2 algorithm after the data are encrypted, calling the IP core of an SM3 algorithm to perform operation acceleration in the signature process, and sending the data to the cloud by using WIFI. By adoption of the secure transmission method disclosed by the invention, the following problem is solved: before the existing personal private cloud medical data need to be encrypted to ensure the security before being sent to a cloud server, however the data bandwidth required for high-precision medical data is very large, and the computing ability of the traditional software cannot satisfy the real-time encryption demand, the security of the data is guaranteed by the SM4 algorithm in the secure transmission method disclosed by the invention, the reliability of the data is guaranteed by the SM2 digital signature algorithm, and the privacy protection of the personal medical data in the transmission process is accomplished efficiently in real time by means of the parallel processing ability of hardware.
Owner:XIDIAN UNIV
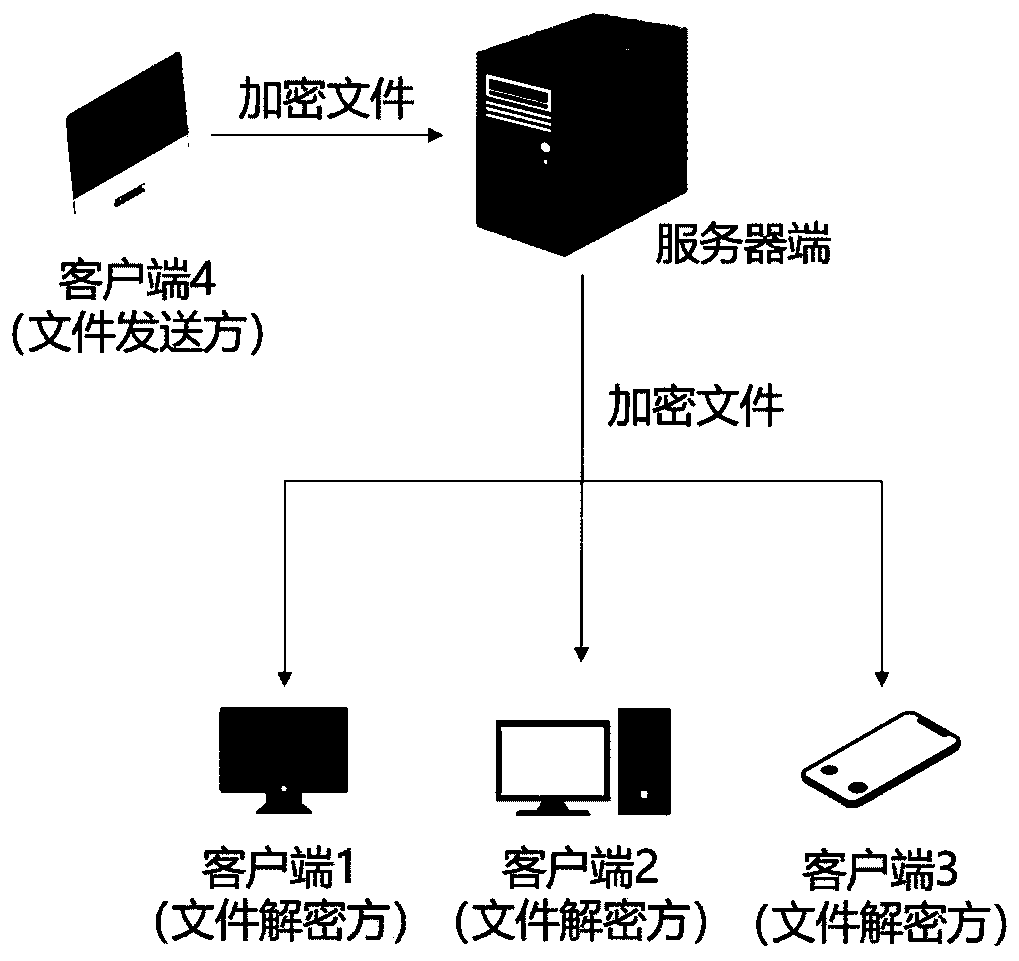
Anti-leakage file security sharing method
ActiveCN110190962AEasy to uploadKey distribution for secure communicationMultiple keys/algorithms usageFile transmissionSecure transmission
The invention discloses an anti-leakage file security sharing method. According to the invention, the SM4 algorithm and the SM2 algorithm are used for respectively realizing file encryption and file key secure transmission. In terms of algorithm selection of encrypted files, symmetric encryption is more efficient, and therefore SM4 is selected as an encryption algorithm of a file body. And an SM2algorithm is selected to encrypt and transmit the encrypted key of the file. And meanwhile, file authority management after secret key distribution is realized. In addition, the abstract generated bythe SM3 algorithm and the SM2 signature are utilized to ensure that the file and the browsing record are not tampered. According to the method, the browsing record and the file are creatively fused together, file transmission and decryption are improved to a certain extent, and the generation of the file browsing record recognized by the components of the whole system is facilitated.
Owner:HANGZHOU DIANZI UNIV
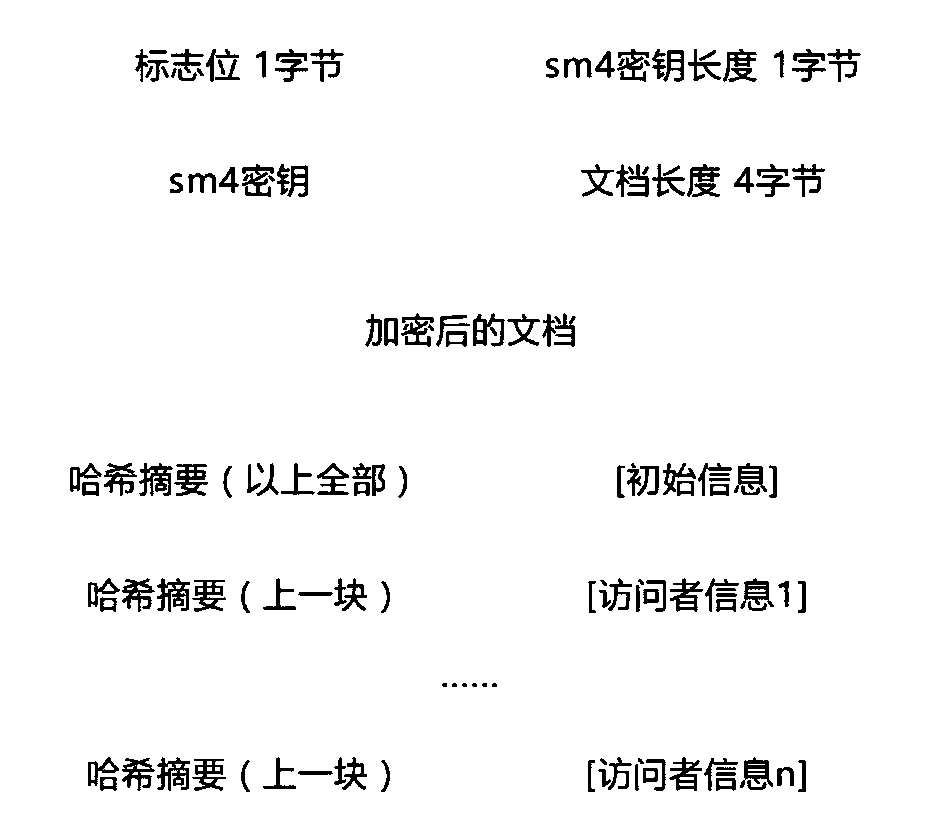
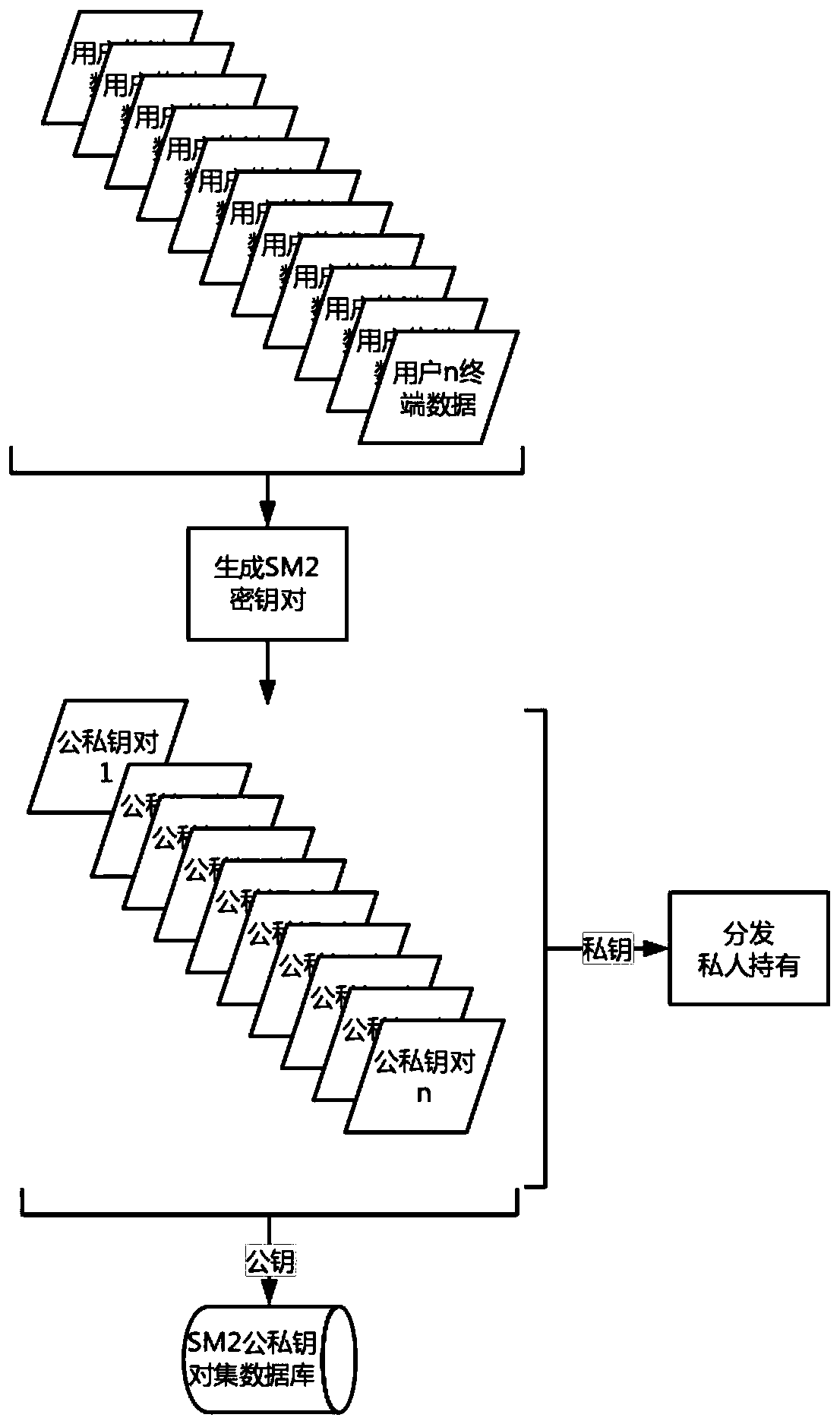
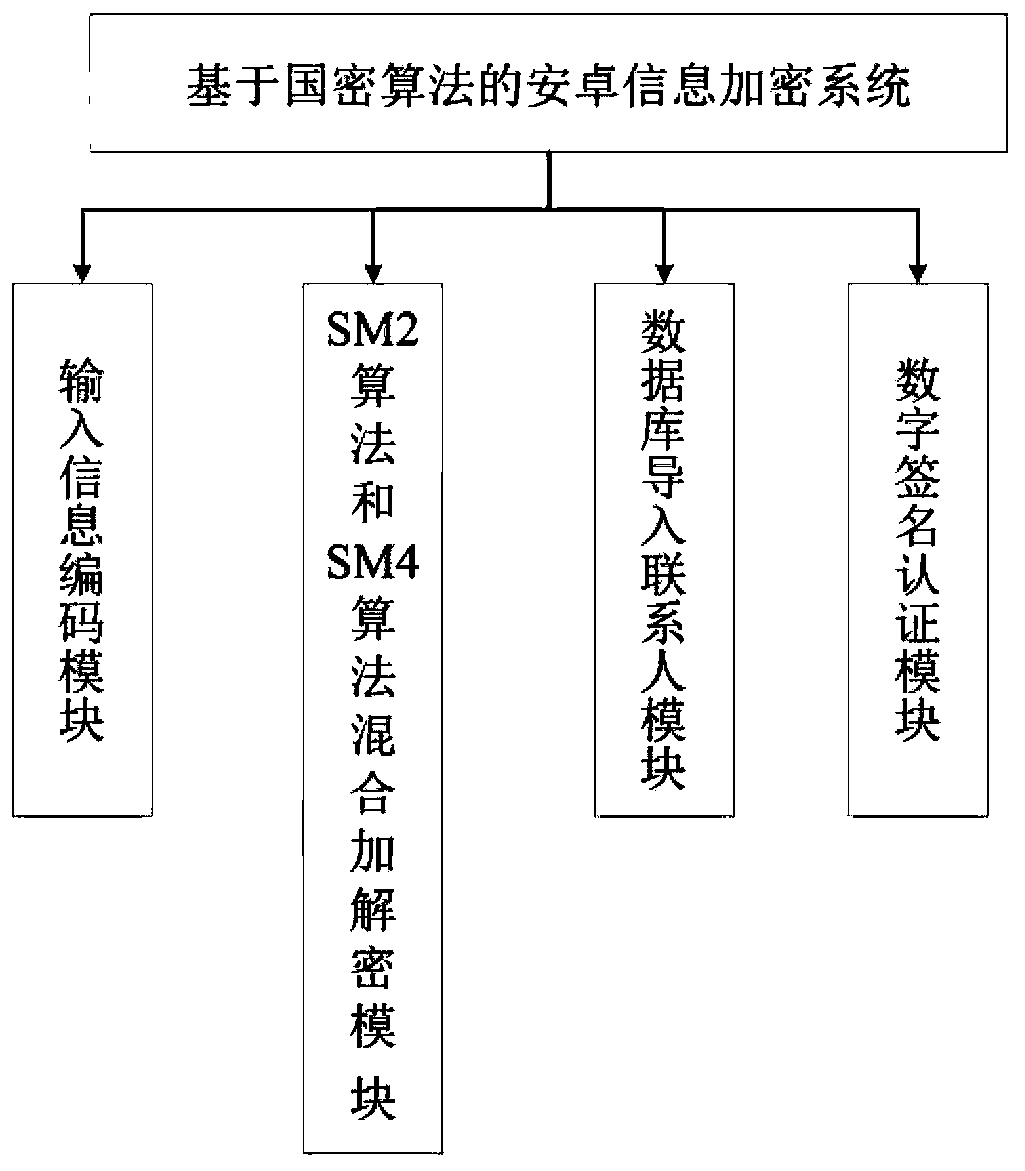
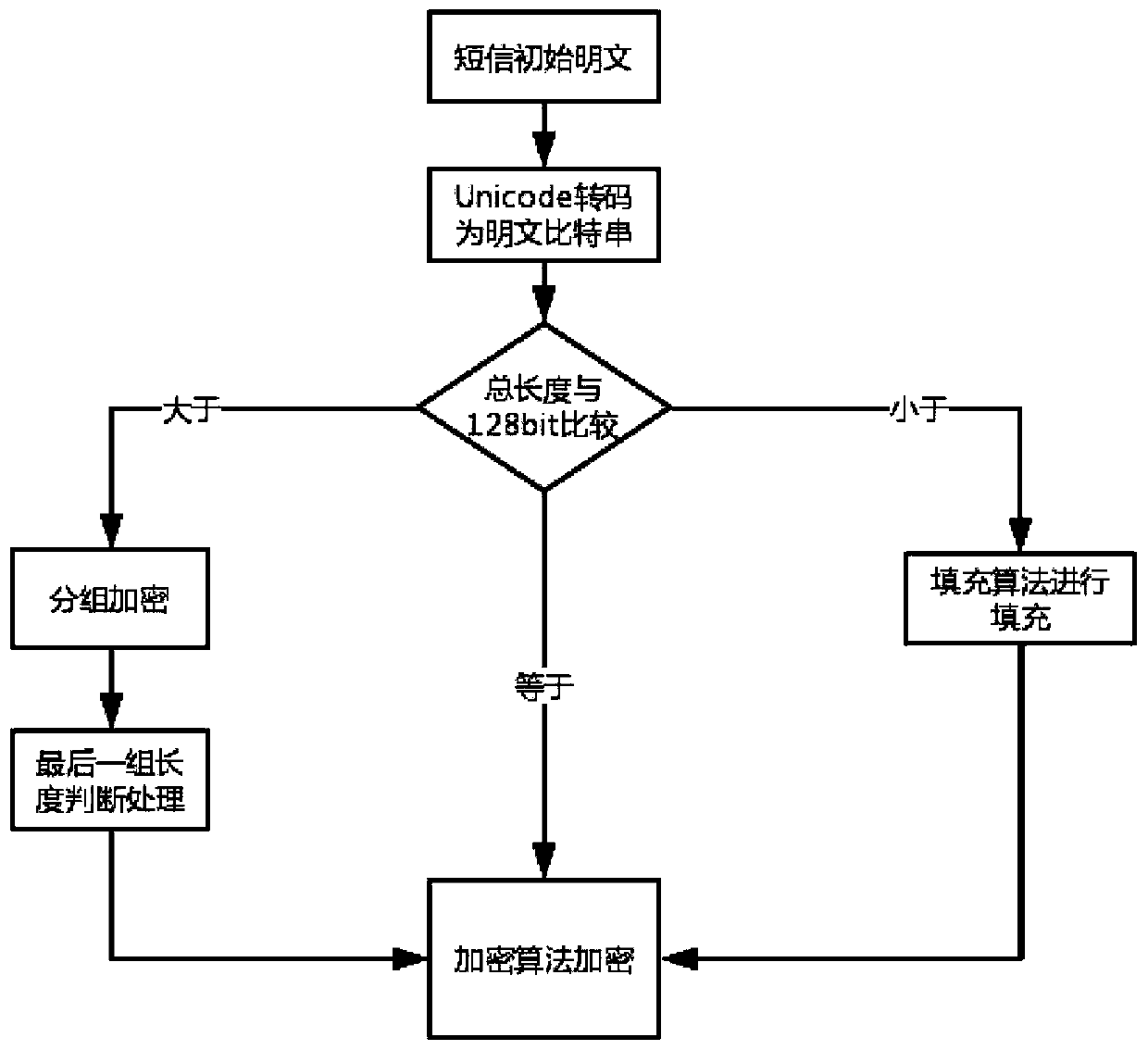
Android information encryption system and method based on national cryptographic algorithm
InactiveCN110505050ASolve the problem of data transmission between sender and senderImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPlaintextResource consumption
The invention relates to an Android information encryption system and method based on a national cryptographic algorithm. The method is based on a hybrid cryptosystem combining an SM4 algorithm and anSM2 algorithm; the SM4 algorithm is adopted to encrypt the plaintext, the encryption efficiency is improved, the resource consumption is reduced, the elliptic curve encryption algorithm is adopted toencrypt the secret key for information encryption to ensure the security of the plaintext in the transmission process, and meanwhile, the security hash algorithm is adopted to perform hash comparisonon the plaintext before and after receiving and transmitting to verify the information integrity.
Owner:BEIJING ELECTRONICS SCI & TECH INST +1
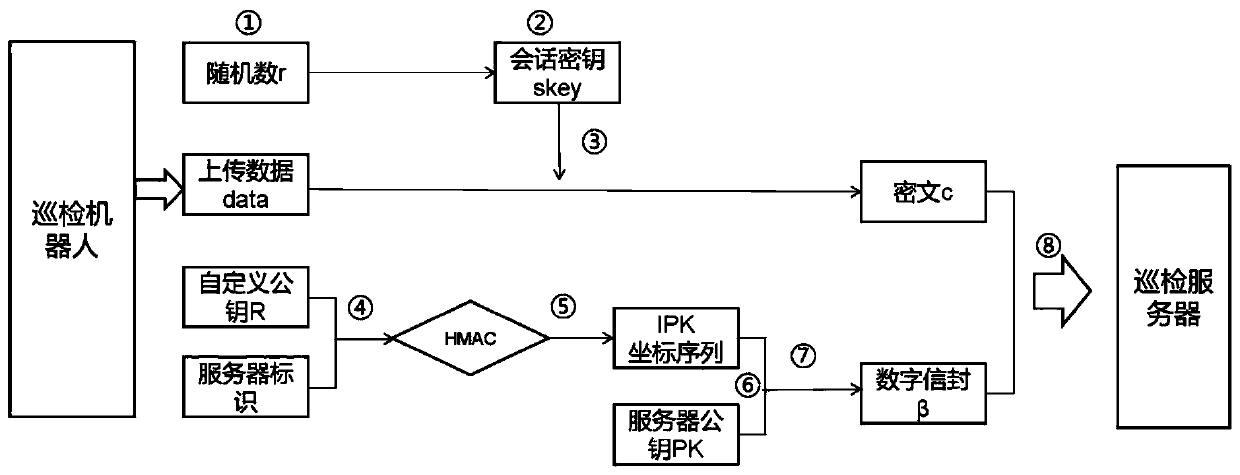
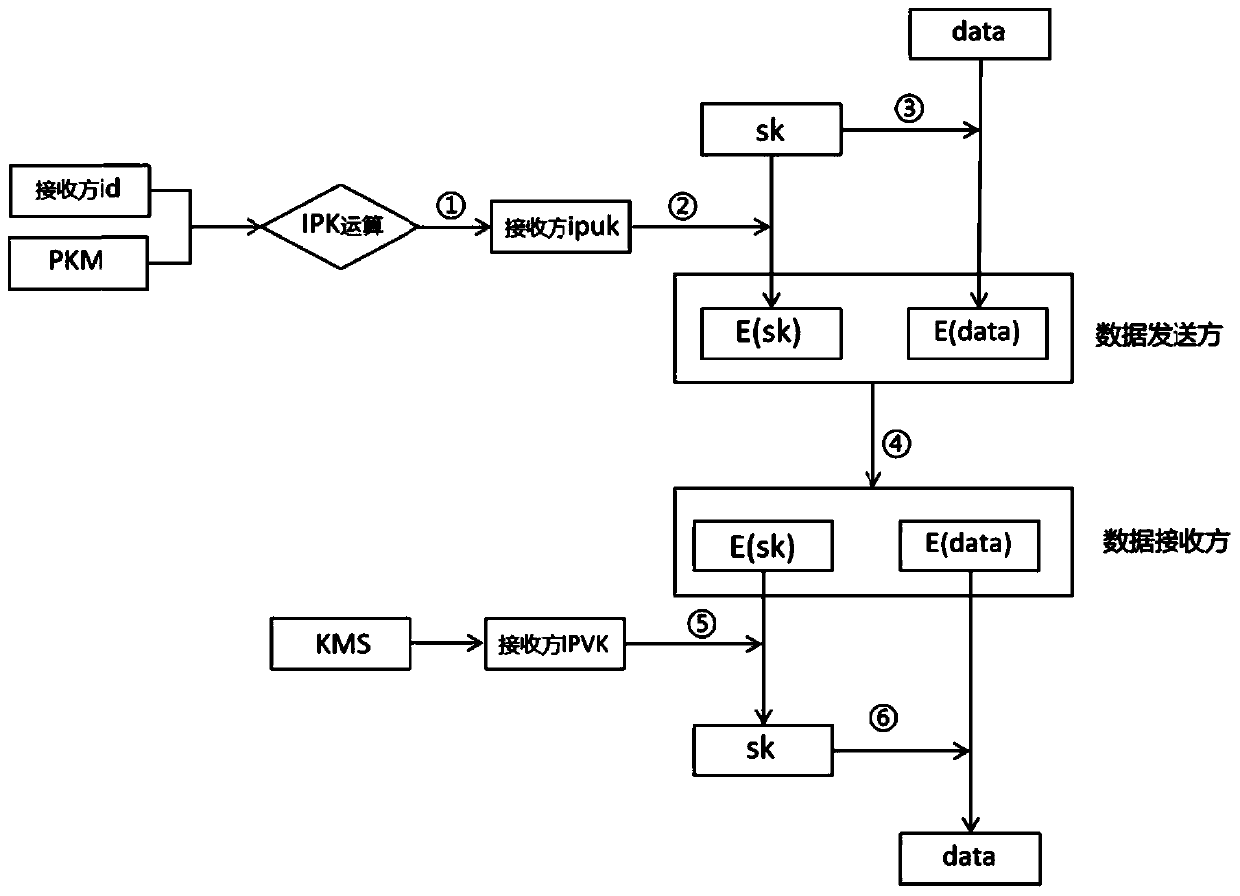
Substation inspection robot data transmission encryption and decryption method and system
ActiveCN110995716AProtection from being leakedSolve management problemsKey distribution for secure communicationRegistering/indicating time of eventsAlgorithmCiphertext
The invention discloses a data transmission encryption and decryption method and system of a transformer substation inspection robot. The method provided by the invention comprises the following steps: when an inspection robot is used as a data sender to upload data to an information management system, the uploaded data is encrypted by adopting an SM4 encryption algorithm, and encrypted transmission of a session key is realized by adopting a digital envelope technology of IPK; the information management system serves as a data receiver, receives ciphertext data C and a digital envelope beta sent by the inspection robot, calls a pre-configured private key sk to open the digital envelope beta to obtain a session key, and decrypts the ciphertext C by using the session key through an SM4 algorithm to obtain original data data. According to the invention, the public key management problem is solved through an IPK recognition public key system, and direct point-to-point data transmission encryption can be realized. According to the invention, efficient and safe inspection robot data transmission is realized.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +1
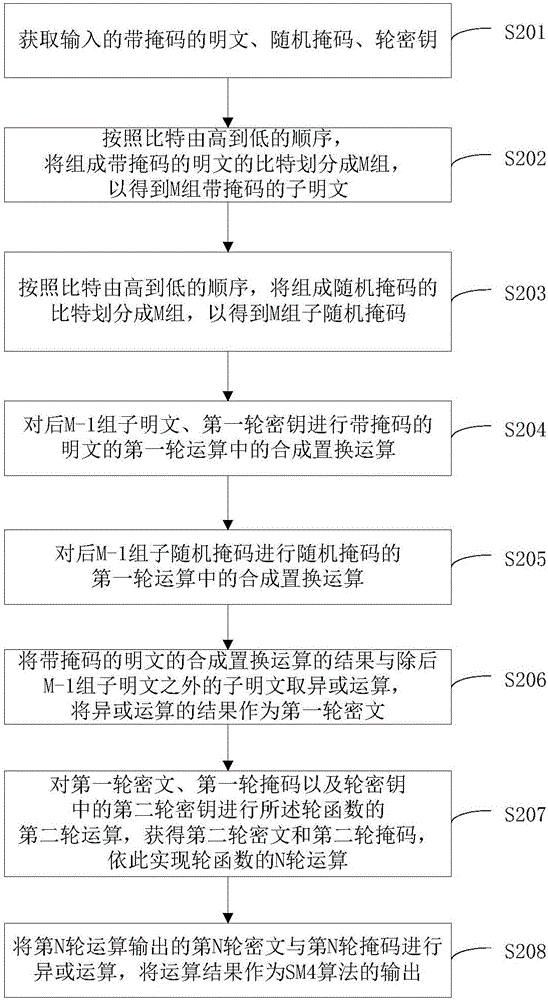
Mask method and mask device for SM4 algorithm
The invention discloses a mask method and a mask device for an SM4 algorithm. The mask method comprises the following steps: acquiring an inputted masked plain text, a random mask and round keys; carrying out a first round operation of a round function on the masked plain text, the random mask and a first round key in the round keys, to obtain a first round ciphertext and a first round mask; carrying out a second round operation of the round function on the first round ciphertext, the first round mask and a second round key in the round keys, to obtain a second round ciphertext and a second round mask, so as to realize N rounds of operation of the round function in turn; and carrying out an XOR operation an N round ciphertext and an N round mask outputted from the N round operation, wherein the operation result is taken as an output of the SM4 algorithm. Namely, except for the first round operation in the N rounds of operation of the round function, masks required for each round operation are all obtained by the output of the last round operation next to the current round operation, and therefore a demask on an intermediate value of the N rounds of operation is not required by adopting the technical solution disclosed by the invention, so that a resistance to an energy attack is realized.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT
Template attacking method for SM4 password algorithm selective input on basis of Hamming weight
The invention discloses a template attacking method for an SM4 password algorithm. In the method, the SM4 algorithm selective input serves as an attacking point, and the Hamming weight is selected to establish templates, and the complete SM4 template attacking can be achieved with a small number of templates; meanwhile, selective plaintext input serves as a basis at the template matching stage, a support vector machine serves as a tool for judgment and analysis, and a bit of a subkey can be decrypted through only two times of matching. The method effectively solves the problems that through other methods at a current stage, for template attacking, too many template data exist and the calculation amount is too large.
Owner:CHENGDU UNIV OF INFORMATION TECH +3
SM4 algorithm white box implementation method and device, electronic equipment and computer medium
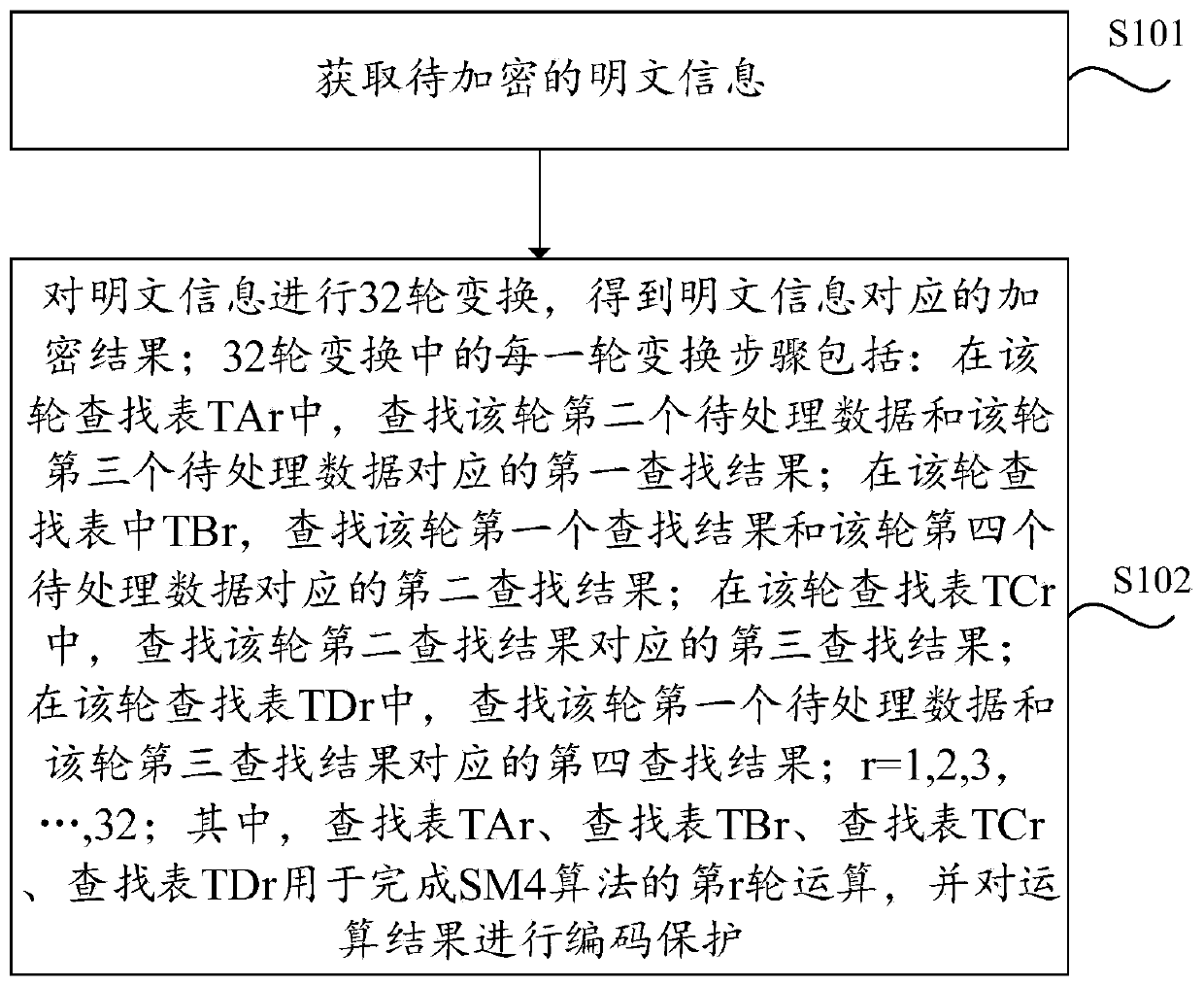
PendingCN110784306AImprove smoothness of interactionImprove securityEncryption apparatus with shift registers/memoriesAlgorithmParallel computing
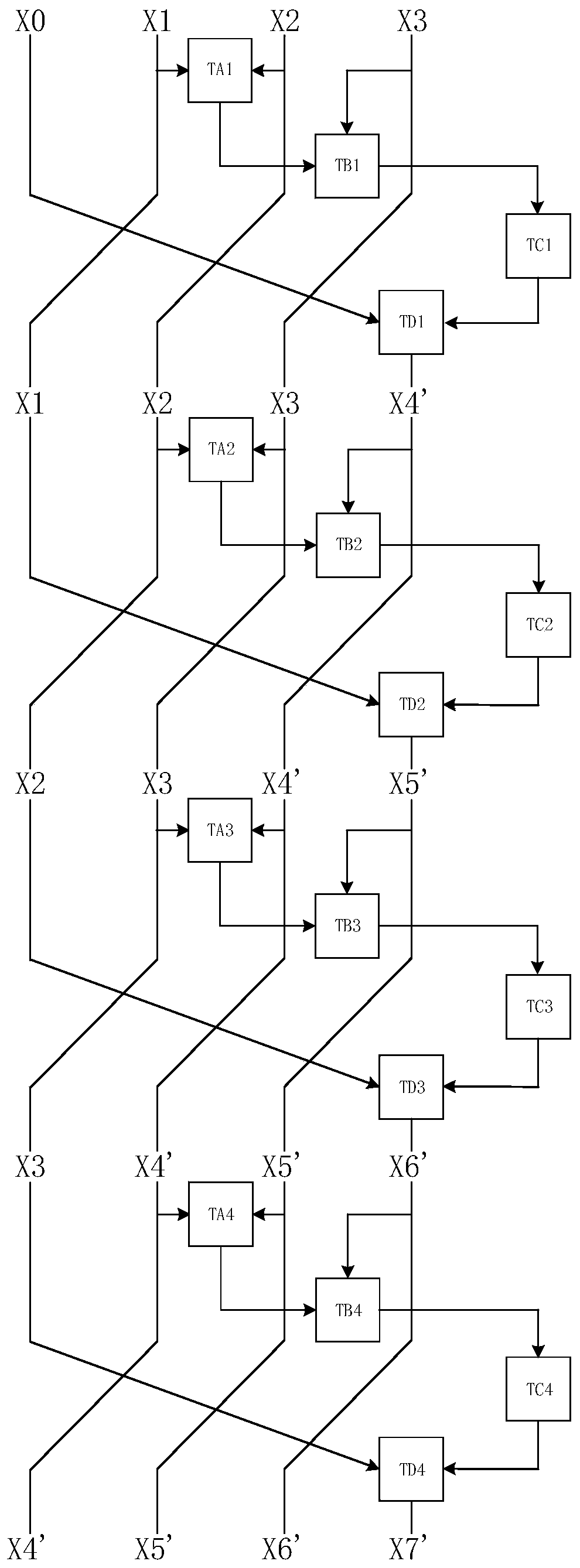
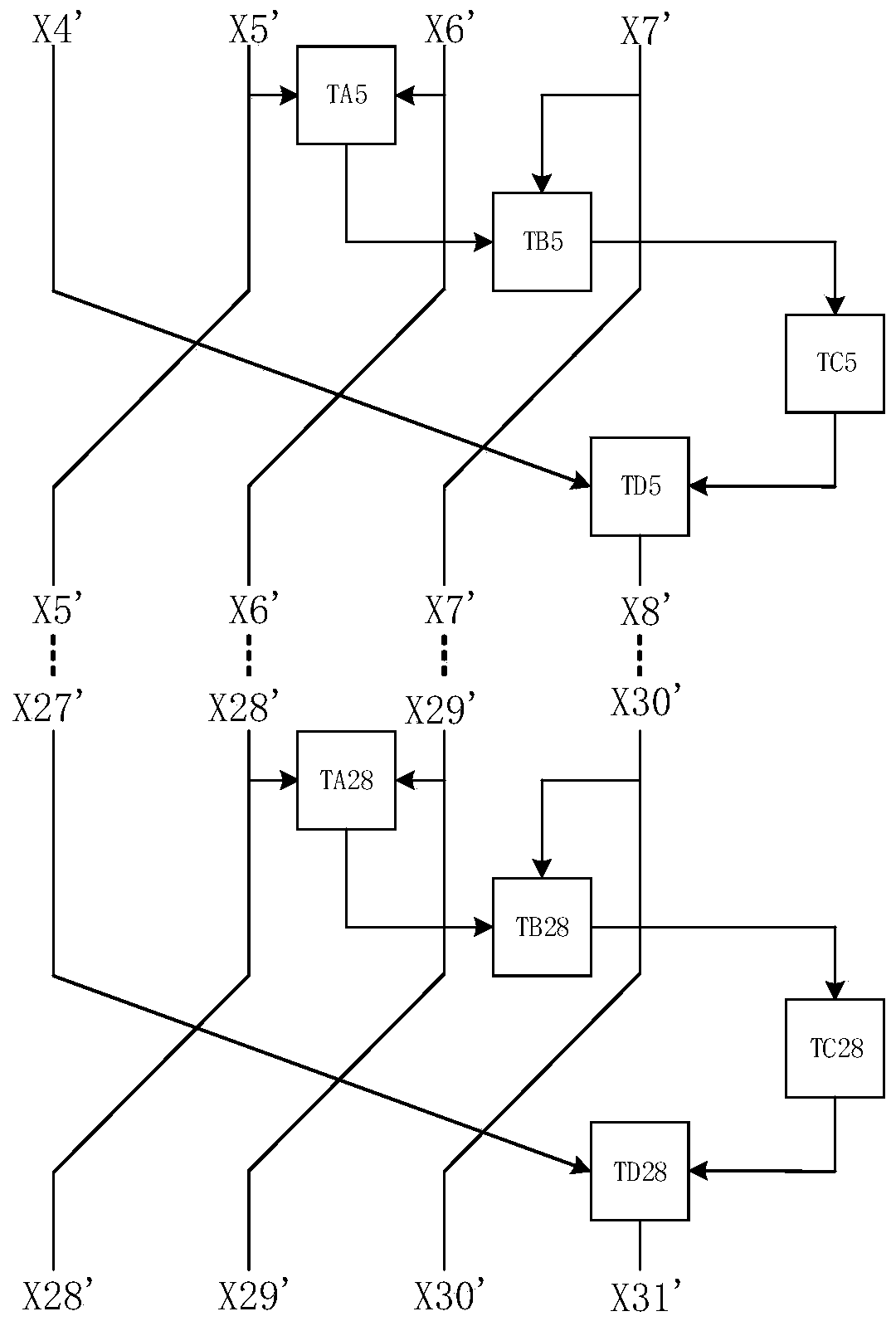
The invention provides an SM4 algorithm white box implementation method and device, electronic equipment and a computer medium. The method comprises the steps of obtaining plaintext information to beencrypted; performing 32 rounds of transformation on the plaintext information to obtain an encryption result corresponding to the plaintext information, wherein each round of transformation in the 32rounds of transformation comprises the following steps: in the round of lookup table TAr, searching a first lookup result corresponding to the second round of data to be processed and the third roundof data to be processed; searching a first search result of the round and a second search result corresponding to fourth to-be-processed data of the round in the round search table TBr; searching a third search result corresponding to the second search result in the round of lookup table TCr; in the round of lookup table TDr, searching a fourth lookup result corresponding to the first round of data to be processed and the third round of lookup result, wherein r is equal to 1, 2, 3,..., 32, the lookup table TAr, the lookup table TBr, the lookup table TCr and the lookup table TDr are used for completing the rth round of operation of the SM4 algorithm, and encoding protection is carried out on an operation result; and the key has high security.
Owner:中电科网络安全科技股份有限公司
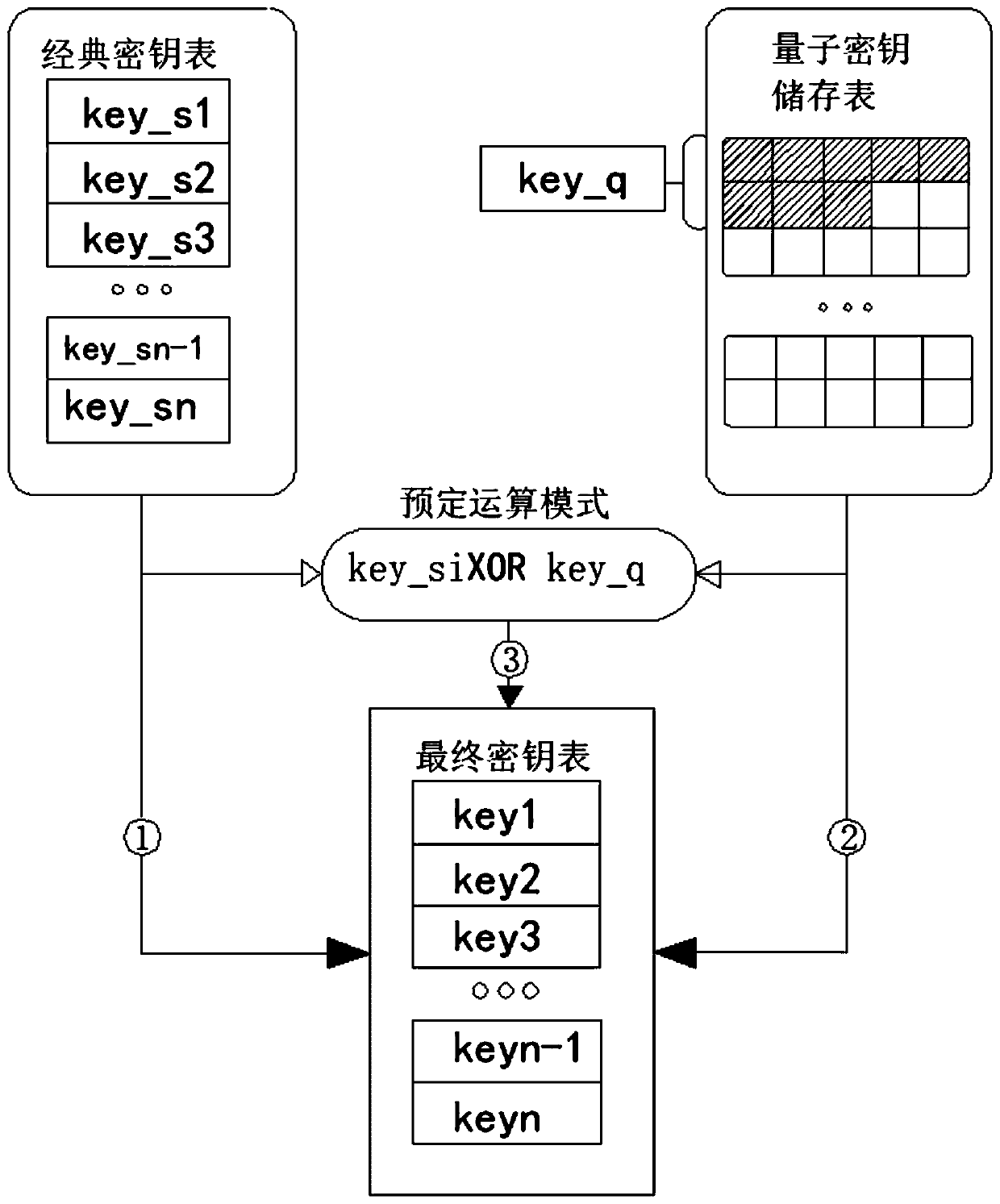
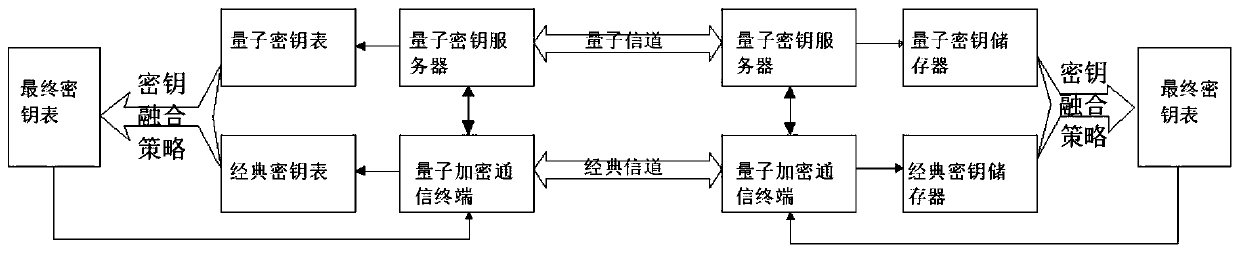
Self-adaptive key distribution mechanism based on QKD network
InactiveCN109889340AImprove real-time performanceIncrease speedKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareRC4
The invention discloses a self-adaptive key distribution mechanism based on a QKD network, and the mechanism comprises three key strategies: 1, using a classic key independently; 2, independently using a quantum key; and 3, the quantum key and the classic key are used in a fusion manner, so that the condition that the requirement on the key quantity cannot be met due to low quantum key generationrate is avoided. According to the invention, a playing type video is downloaded; Audio information, assigning a candidate packet encryption algorithm for it; AES, 3DES, IDEA, SM1, SMS4, Twofish. The method is used for an RTSP streaming video. Audio information, High real-time performance needs to be guaranteed, The method comprises the following steps: aiming at RTSP streaming video / audio information; assigning a candidate encryption algorithm for it; AES, SM1, SMS4, RC4, Rabbit, ChaCha20, The method has the advantages that the requirements on real-time performance of text information such aselectronic mails and control information are low, a symmetric encryption algorithm is distributed for the application of the type mainly according to the security level required by the application, and accordingly candidate encryption algorithms such as DES, AES, SM1, SMS4 and Twofish can be designated for the application of the type;
Owner:BEIJING INFORMATION SCI & TECH UNIV +1
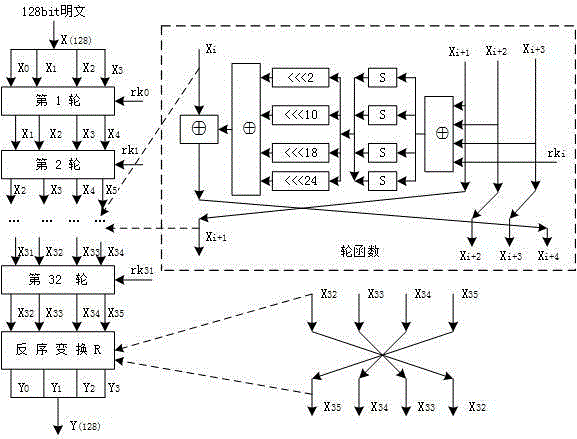
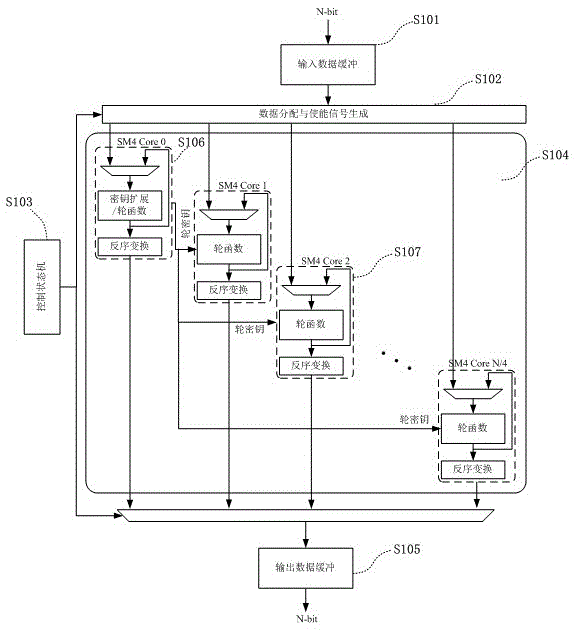
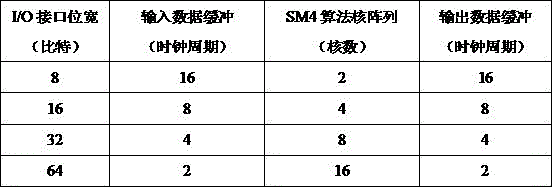
Extensible pipelined circuit aiming at SM4 cryptographic algorithm and implementation method thereof
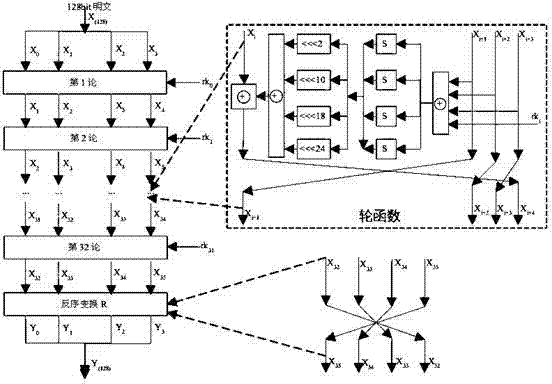
ActiveCN105577363AImprove throughputDoes not incur large area overheadEncryption apparatus with shift registers/memoriesComputer scienceSM4 Algorithm
The invention discloses an extensible pipelined circuit aiming at an SM4 cryptographic algorithm and an implementation method thereof. According to the invention, an encryption and decryption iterative operation and a key extending algorithm are implemented through an SM4 algorithm core array, the SM4 algorithm core array comprises N / 4 SM4 algorithm cores, each SM4 algorithm core performs loop iteration 32 times to finish encryption / decryption of 128 bits of data, the N / 4 SM4 algorithm cores perform parallel execution, the number of the SM4 algorithm cores is regulated according to I / O bit width, and given that the I / O bit width is N, so the number of the algorithm cores in the structure is N / 4. According to the invention, encryption / decryption of the SM4 algorithm can be executed in a pipelined form, and a circuit structure can be regulated according to I / O interfaces with different bit widths.
Owner:NANJING QINHENG MICROELECTRONICS CO LTD
SMS4 acceleration processors, methods, systems, and instructions
A processor of an aspect includes a plurality of packed data registers and a decode unit to decode an instruction. The instruction is to indicate one or more source packed data operands. The one or more source packed data operands are to have four 32-bit results of four prior SMS4 rounds. The one or more source operands are also to have a 32-bit value. An execution unit is coupled with the decode unit and the plurality of the packed data registers. The execution unit, in response to the instruction, is to store a 32-bit result of a current SMS4 round in a destination storage location that is to be indicated by the instruction.
Owner:INTEL CORP
Combined attack method for SM4 algorithm
ActiveCN108880783AQuick calculationImprove attack efficiencyCryptographic attack countermeasuresPlaintextS-box
The invention discloses a combined attack method for SM4 algorithm, combines the energy analysis attack and the differential analysis attack, and provides a combined attack method of energy analysis and differential analysis aiming for the SM4 algorithm. An S-box nonlinear output is selected as an attack intermediate value, and the sensitive intermediate values of the second round and the fourthround are attacked by selecting a plaintext to realize cross-round energy analysis and attack. A round secret key can be quickly calculated through differential analysis of the S box, and the attack efficiency is improved. In addition, the method can also be extended to joint attacks of all symmetric cryptographic algorithms.
Owner:成都三零嘉微电子有限公司
Data desensitization method and device, computer equipment and storage medium
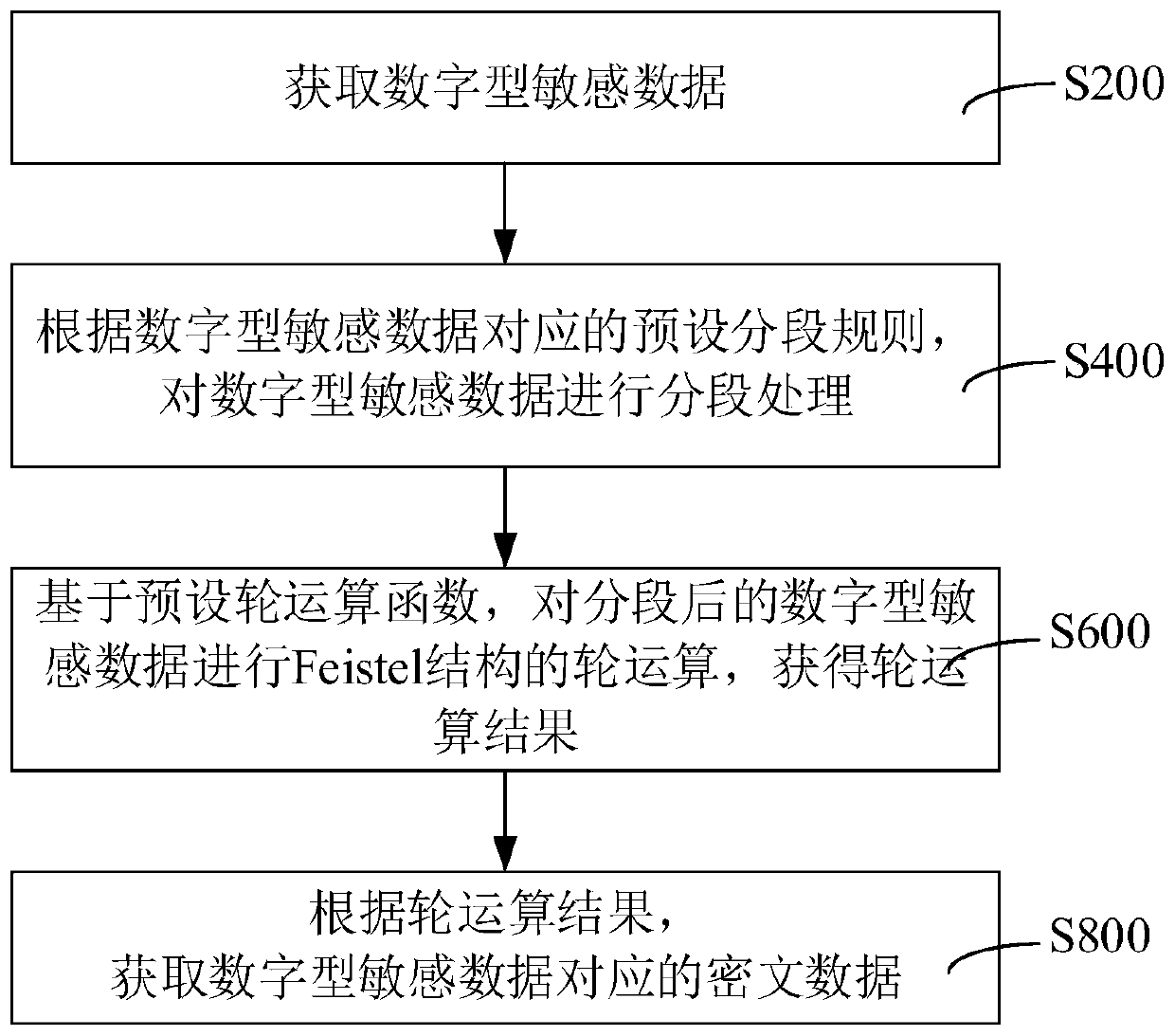
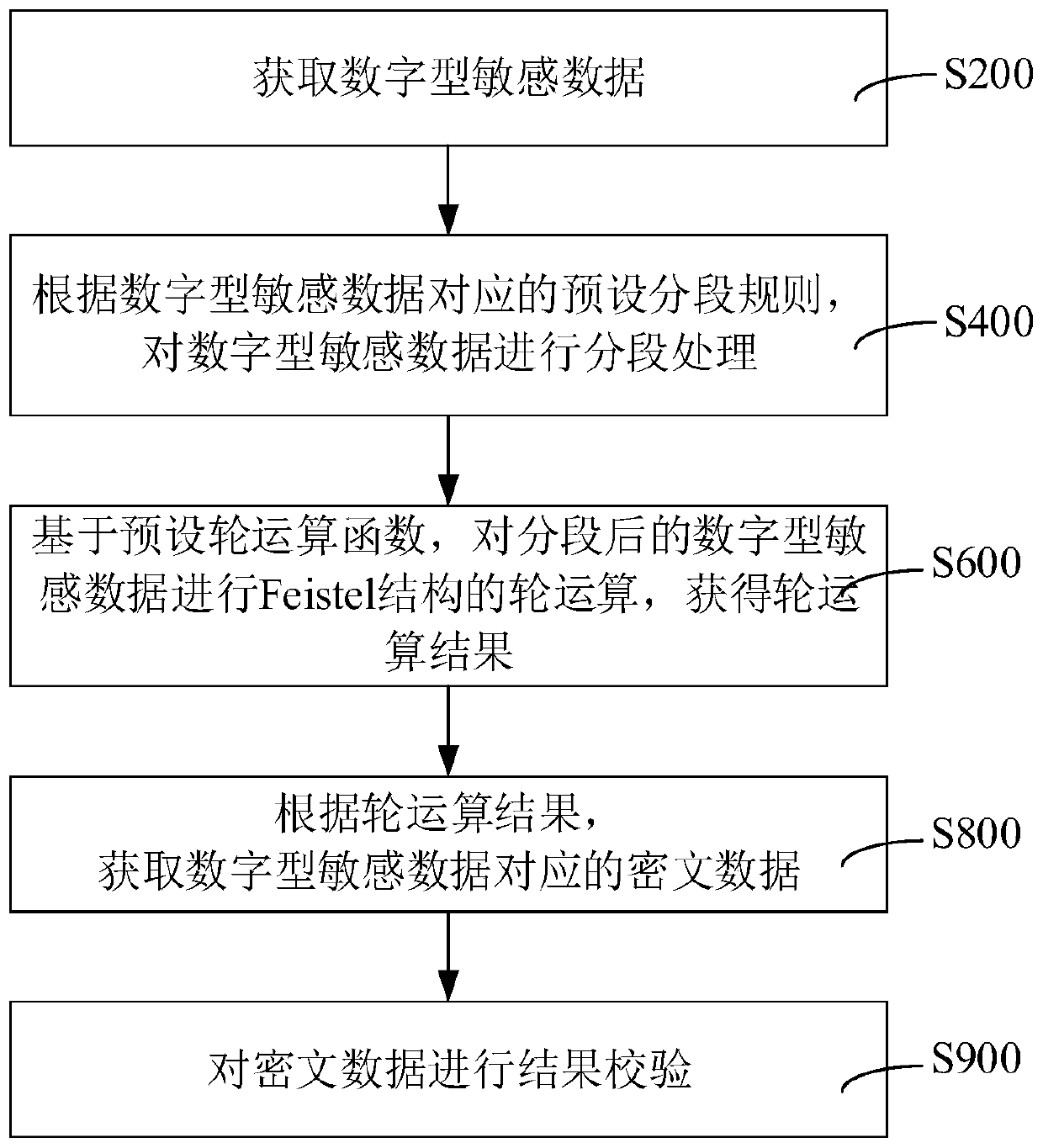
InactiveCN110750810AGood application effectEnsure consistencyDigital data protectionData classAlgorithm
The invention relates to a data desensitization method and device, computer equipment and a storage medium. The method comprises the following steps: acquiring digital sensitive data; according to a preset segmentation rule corresponding to the digital sensitive data, performing segmentation processing on the digital sensitive data; based on a preset round operation function, performing round operation of a Feistel structure on the segmented digital sensitive data to obtain a round operation result; and acquiring ciphertext data corresponding to the digital sensitive data according to a roundoperation result. According to the data desensitization method, a round function is constructed through SM4 encryption; round operation is carried out based on a round function to carry out data desensitization; the format consistency of the digital characteristic data before and after desensitization is effectively ensured; the data length, the data type and the like are not changed, so that theoriginal database storage unit can directly store the ciphertext result, the utilization rate of the encryption result is effectively improved, meanwhile, the SM4 algorithm is expanded to a reserved format encryption algorithm, and the applicability of SM4 is enhanced.
Owner:卓尔智联(武汉)研究院有限公司
Power-attack-resistant SM4 algorithm hardware implementation system
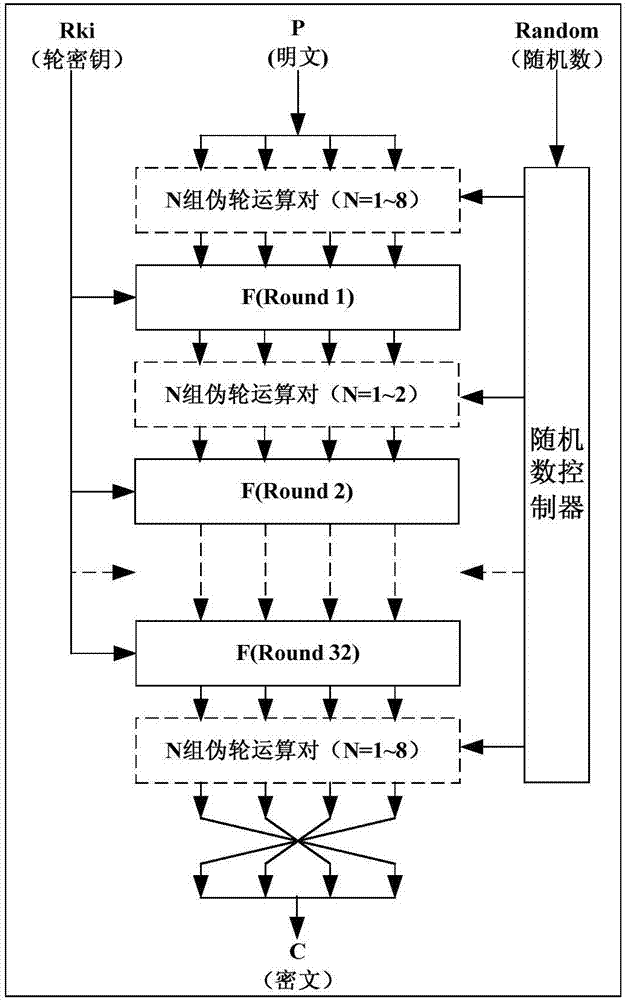
InactiveCN107154843ADestroy associationPower consumption attack defenseEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresSmart cardHardware implementations
The invention discloses a power-attack-resistant SM4 algorithm hardware implementation system, and relates to the technical field of information safety. According to the system, a pseudo wheel operation pair module and a random number controller are added to an SM4 algorithm hardware circuit, thereby achieving the random insertion of a pseudo wheel operation pair between the wheel operations in the SM4 encryption process. The value of data passing through the pseudo wheel operation pair will not change, but the power consumption features of a circuit and the execution time sequence features of the circuit are disturbed. The correlation between the data and the power consumption is broken, and the power attack is effectively prevented. The system can be used in a safety chip of an intelligent card and a USBKey, and also can be suitable for various types of safety chips which need to prevent the power attack for the SM4.
Owner:北京万协通信息技术有限公司
Hard copy control system based on national commercial cipher algorithm
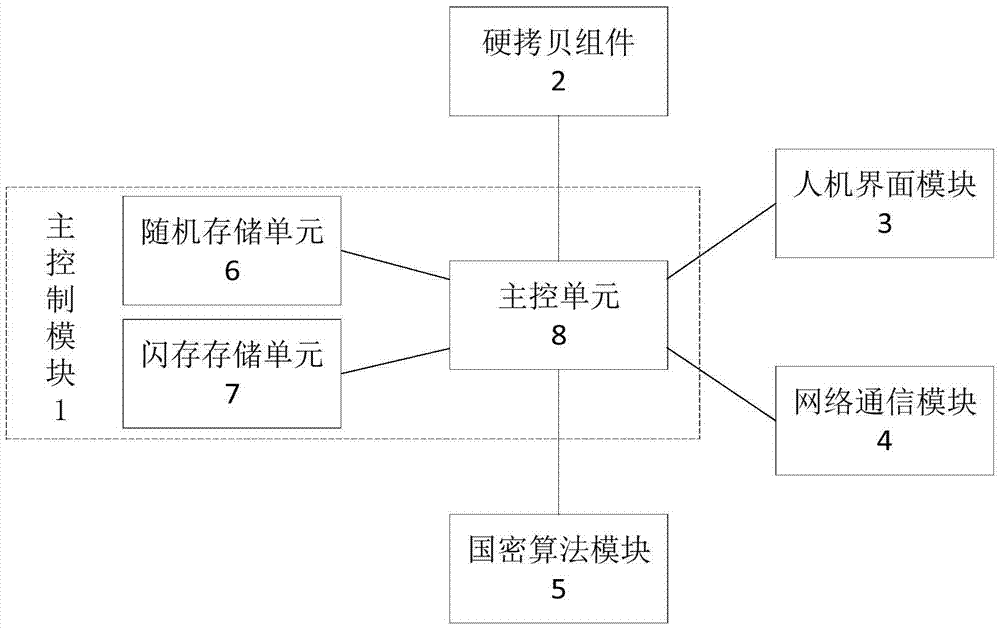
ActiveCN107124277AAvoid safety hazardsIntegrity guaranteedUser identity/authority verificationInternal/peripheral component protectionHuman–machine interfaceAlgorithm
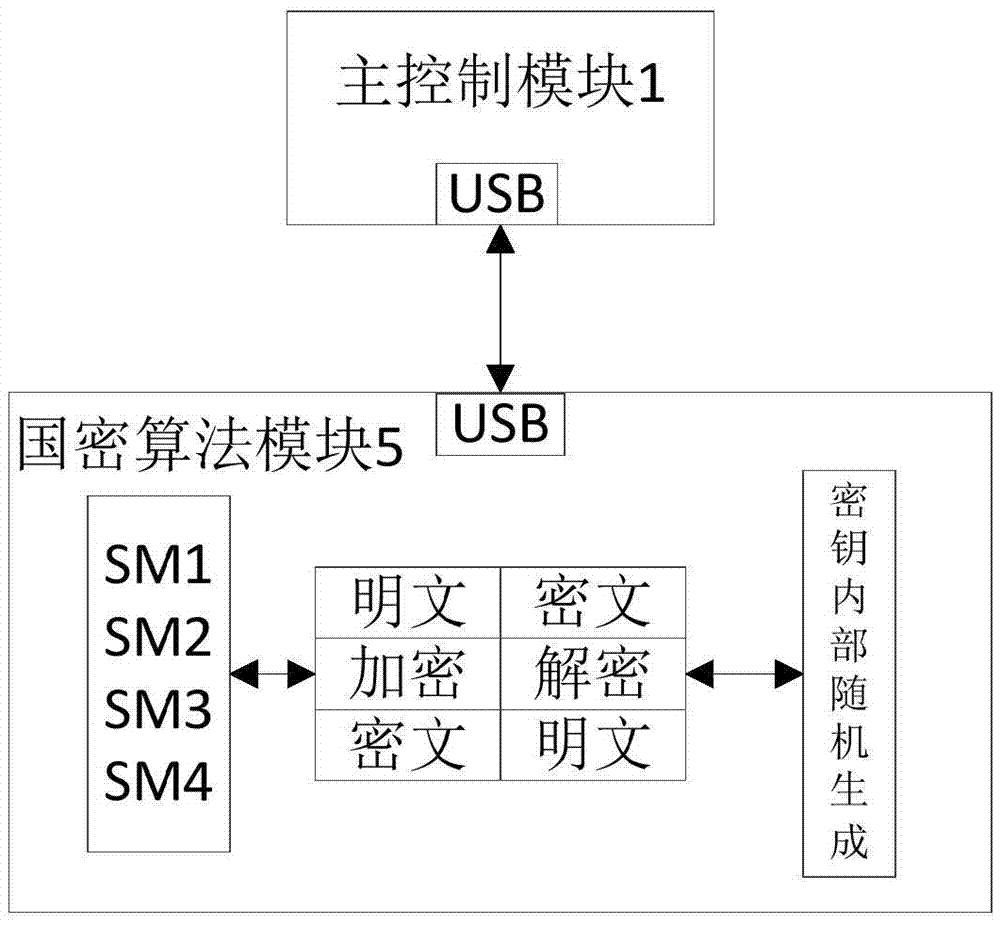
The invention relates to a hard copy control system based on a national commercial cipher algorithm, comprising a main control module, a hard copy component, a human-computer interface module, and a network communication module. The main control module comprises a random access memory unit, a flash memory unit, and a main control unit. The main control unit is connected with the hard copy component, the human-computer interface module, the network communication module, the random access memory unit and the flash memory unit. The system further comprises a national cipher algorithm module used for providing an SM1 / SM2 / SM3 / SM4 algorithm and connected with the main control unit. Compared with the prior art, the confidentiality of the work information of the hard copy component is ensured and information leakage is prevented while the integrity and correctness of the work information are ensured, and the information security risk of the existing hard copy component is solved.
Owner:上海航天智能装备有限公司
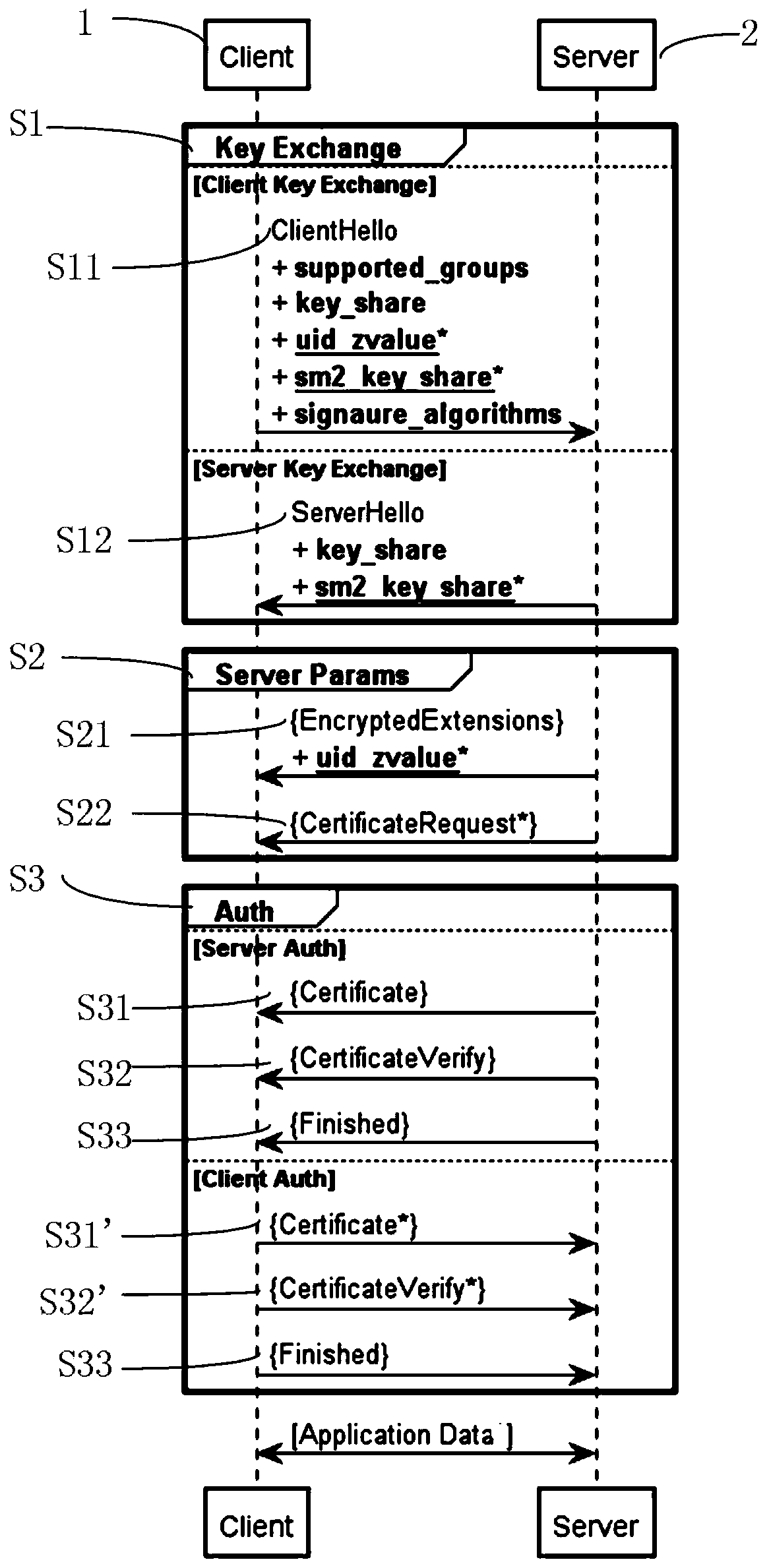
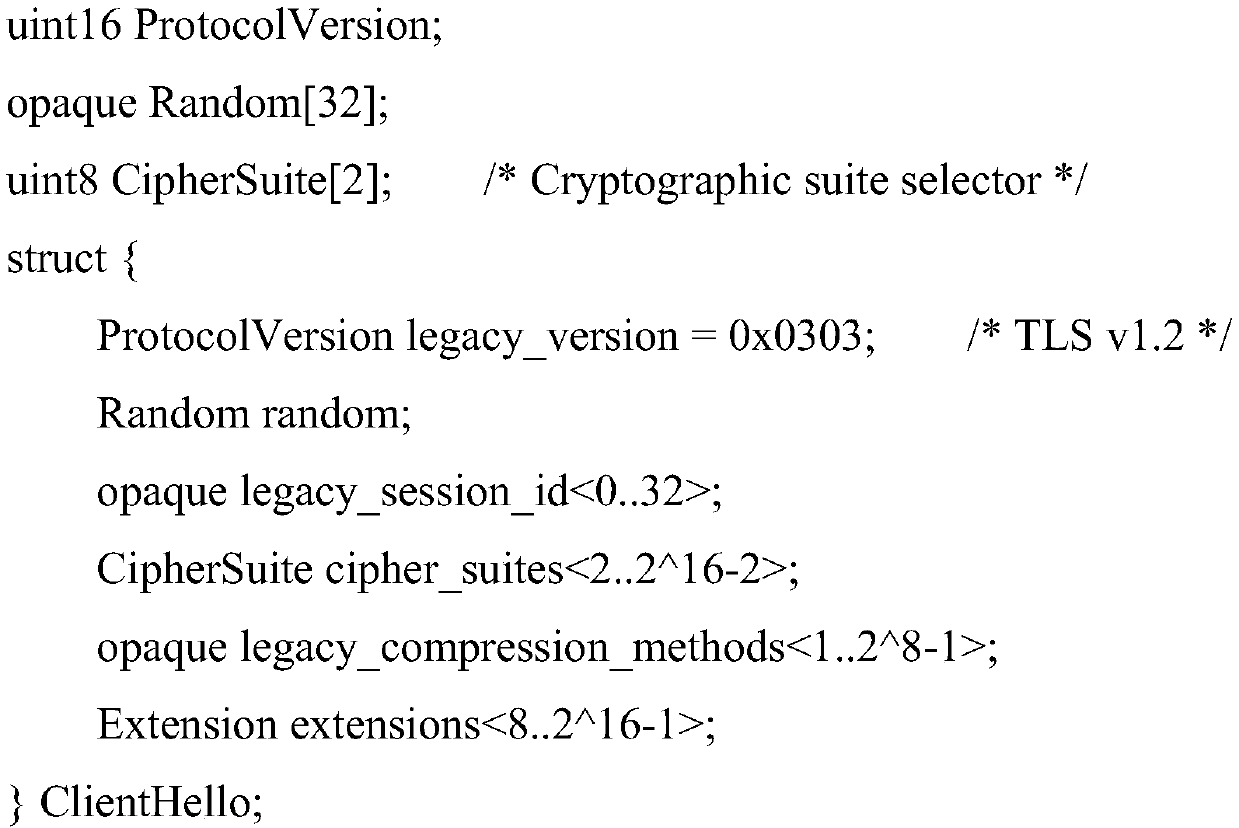
Method for establishing channel in TLS1_3 protocol based on national cryptographic algorithm
ActiveCN110995414AShorten the lengthPrevent theftEncryption apparatus with shift registers/memoriesPublic key for secure communicationKey exchangeKey size
The invention discloses a method for establishing a channel in a TLS1_3 protocol based on a national cryptographic algorithm. The method comprises a key exchange stage, a server parameter stage and anidentity authentication stage. In the key exchange phase, an SM2 key exchange algorithm is introduced to negotiate a shared key, and compared with international algorithms such as ECDH and ECDSA, a safer mechanism is adopted; in the identity authentication stage, compared with an RSA algorithm, the SM2 algorithm has the advantages that the encryption strength is similar to the safety performanceof a 3072-bit RSA algorithm when the key length of the SM2 algorithm is 256 bits, two message words are used in each round of a compression function of the SM3 algorithm, and the SM3 algorithm has higher word completeness than an existing SHA256 algorithm. In a symmetric encryption algorithm, an SM4 algorithm is introduced, a 32-round nonlinear iterative structure is adopted, the number of roundsof calculation is far larger than that of an AES algorithm, and safety is higher. According to the method, by improving the encryption algorithm serving as a data transmission safety core, secret keyleakage in the transmission process is avoided, and the safety of establishing a TLS1_3 channel is improved to a great extent.
Owner:CHINA FINANCIAL CERTIFICATION AUTHORITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com