Method for establishing channel in TLS1_3 protocol based on national cryptographic algorithm
A national secret algorithm and technology for establishing a channel, which is applied in the field of establishing a channel in the TLS1_3 protocol based on the national secret algorithm, can solve the problems of different key lengths, different iterative structures, and inability to apply the national secret algorithm, so as to increase security, The effect of avoiding packet content theft and improving security and performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
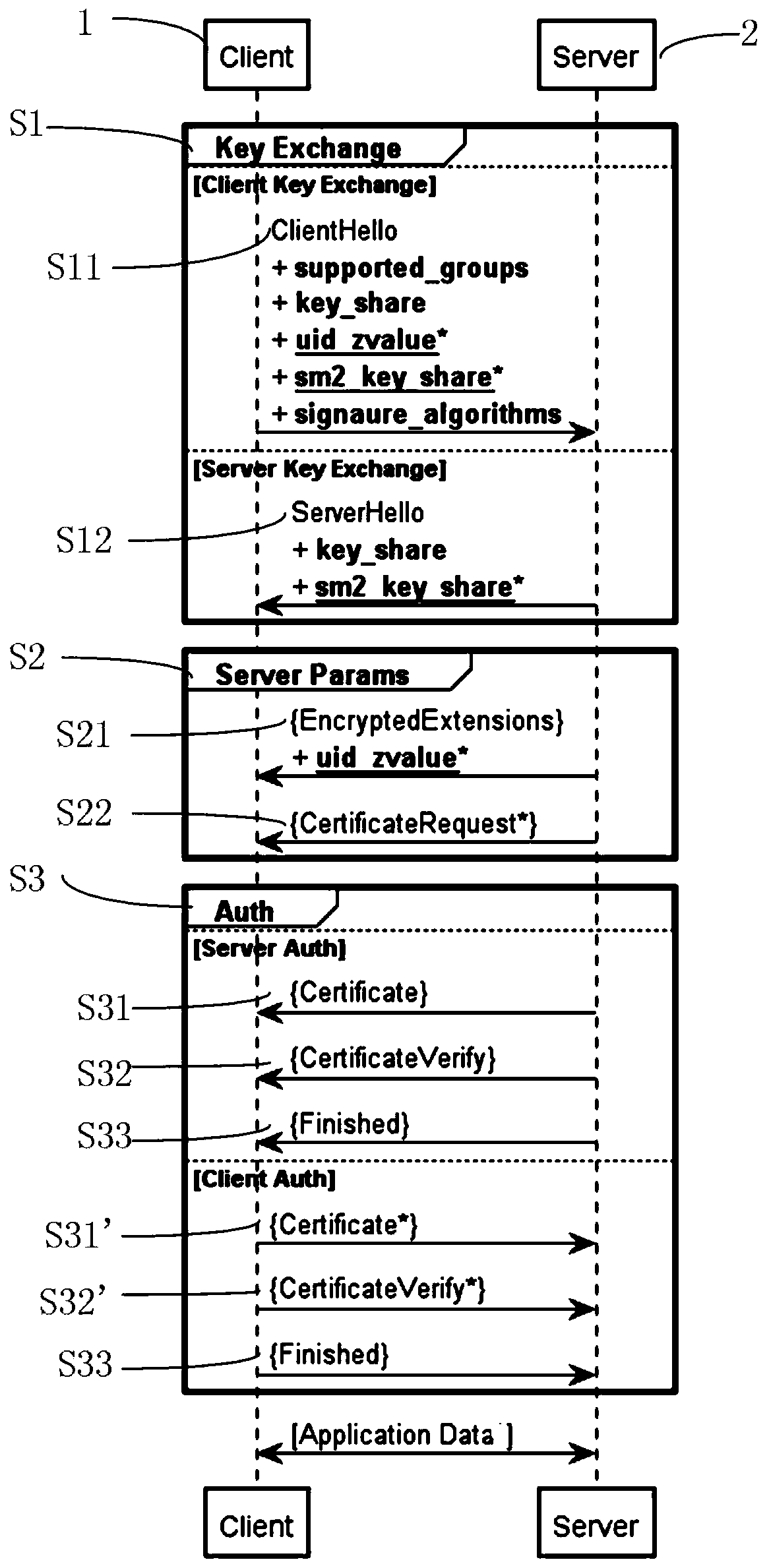
[0029] figure 1 It shows a sequence diagram of the message interaction process between the client and the server in the embodiment. In the figure, "+" indicates the extended message of the previous message (the bold indicates that this embodiment adds the original extension according to the extension rules); "*" indicates the optional extension (the bold and underlined indicates that this embodiment The newly added extension in ); "{}" indicates that these packets are protected using a key derived from [sender]_handshake_traffic_secret; "[]" indicates that these packets are protected using a key derived from traffic_secret_N.
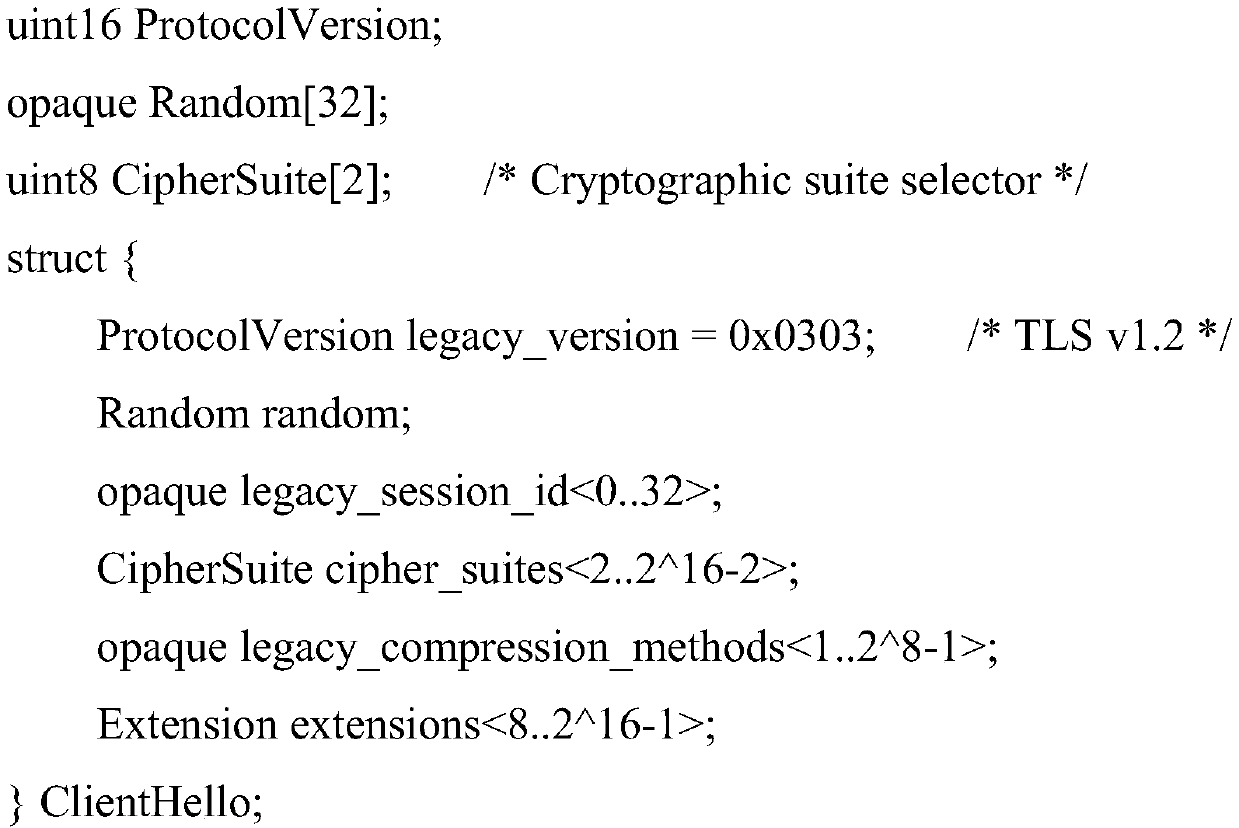
[0030] The key parameters used in the secure channel are generated by the TLS1_3 handshake protocol. The TLS1_3 handshake protocol is used when the client 1 (Client) and the server 2 (Server) communicate for the first time. T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com