Side-channel attack protection method based on full-encryption algorithm pseudo-operation
An encryption algorithm, a technology of side-channel attack, applied in encryption device with shift register/memory, key distribution, can solve the problem that side-channel attack has no effect, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
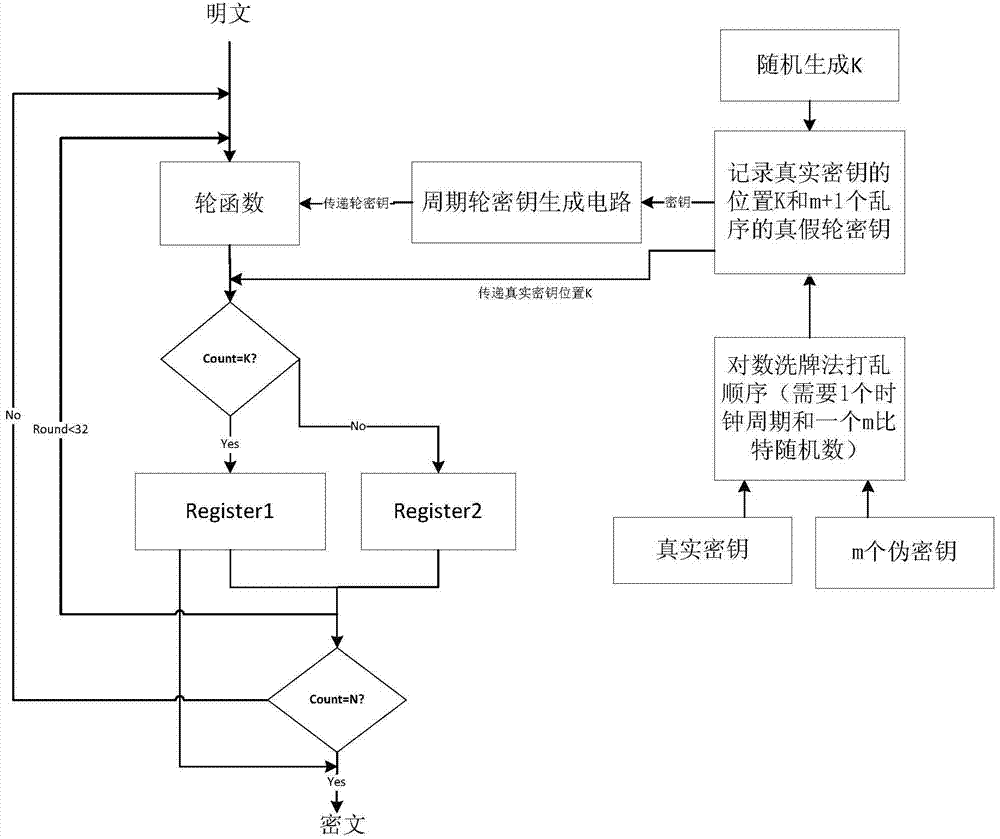
[0030] Such as figure 1 As shown, N=m+1 in this embodiment. N and m represent the execution times of the SMS4 algorithm and the number of pseudo-keys, respectively.
[0031] The implementation device of this embodiment includes: a round function generation module based on SMS4, 1 real key storage, m false key storages, a key storage random scrambling circuit, and a periodic round key generation circuit, wherein: SMS4 The round function is connected to the periodic round key generation circuit and transmitted, the key storage is connected to the key random scrambling circuit and transmitted, and the key random scrambling circuit is connected to the periodic round key generation circuit.
[0032] The SMS4-based round function generation module is: a normal SMS4 round function.
[0033]The one real key storage is: four 32-bit registers for storing 128-bit keys.
[0034] The m pseudo-key memories are: m 32-bit registers for storing m 32-bit pseudo-keys.
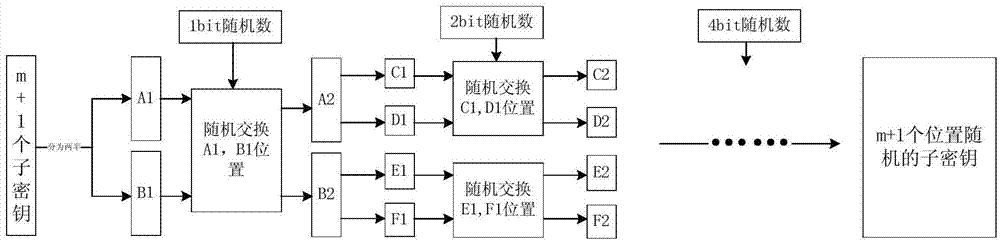
[0035] The random scr...
Embodiment 2
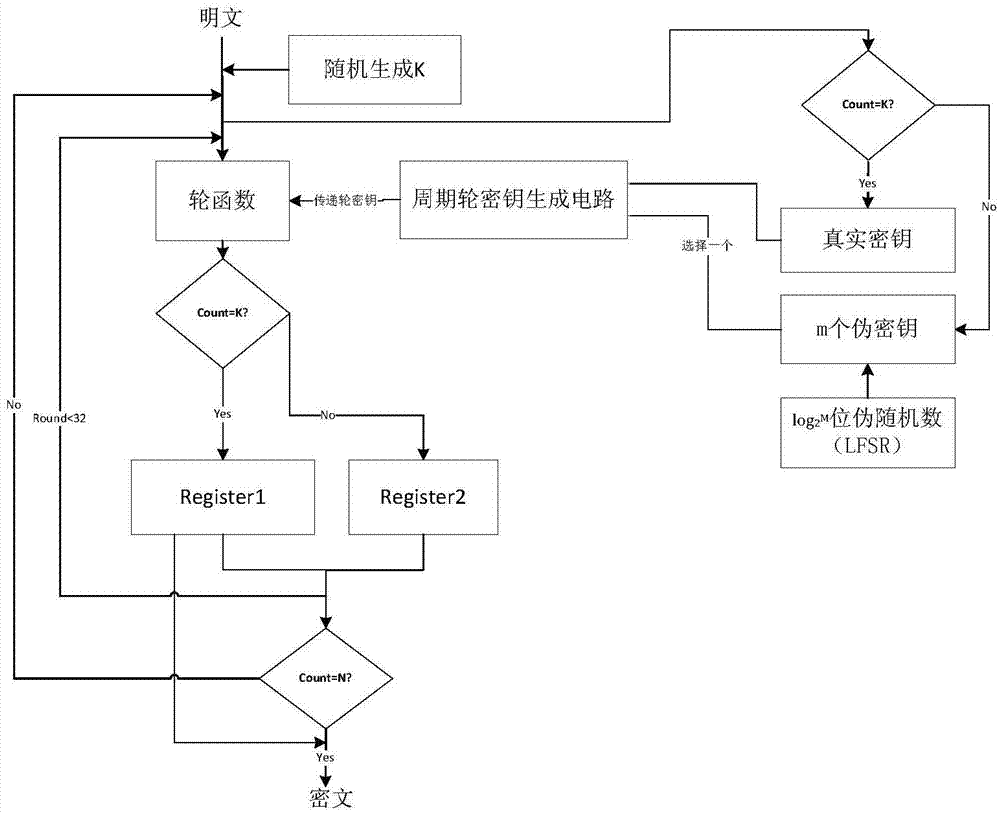
[0043] Such as image 3 As shown, N>m in this embodiment. N and m represent the execution times of the SMS4 algorithm and the number of pseudo-keys, respectively.
[0044] The implementation device of this embodiment includes: a round function generation module based on SMS4, (m+1) key storages, a periodic round key generation circuit, and a round key random selection circuit, wherein: the round function module of SMS4 is related to the periodic The round key generating circuit is connected and transmitted, the periodic round function generating module is connected and transmitted with the key storage, and the pseudo key storage is connected and transmitted with the periodic key random selection circuit.
[0045] The random selection circuit of the key is as follows: the moment when the real key is first positioned to execute the SMS4 algorithm, and the selection of other false keys is randomly and repeatedly selected from the optional false key, and the last 96 of the real k...
Embodiment 3
[0048] Embodiment 3 is a software calling method, and the selection method of its key is the same as that of Embodiment 1.
[0049] The application scenario of Embodiment 3 is that the hardware implementation cannot be changed, and the side-channel attack protection solution with the same effect as Embodiment 1 is implemented through software calling.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com