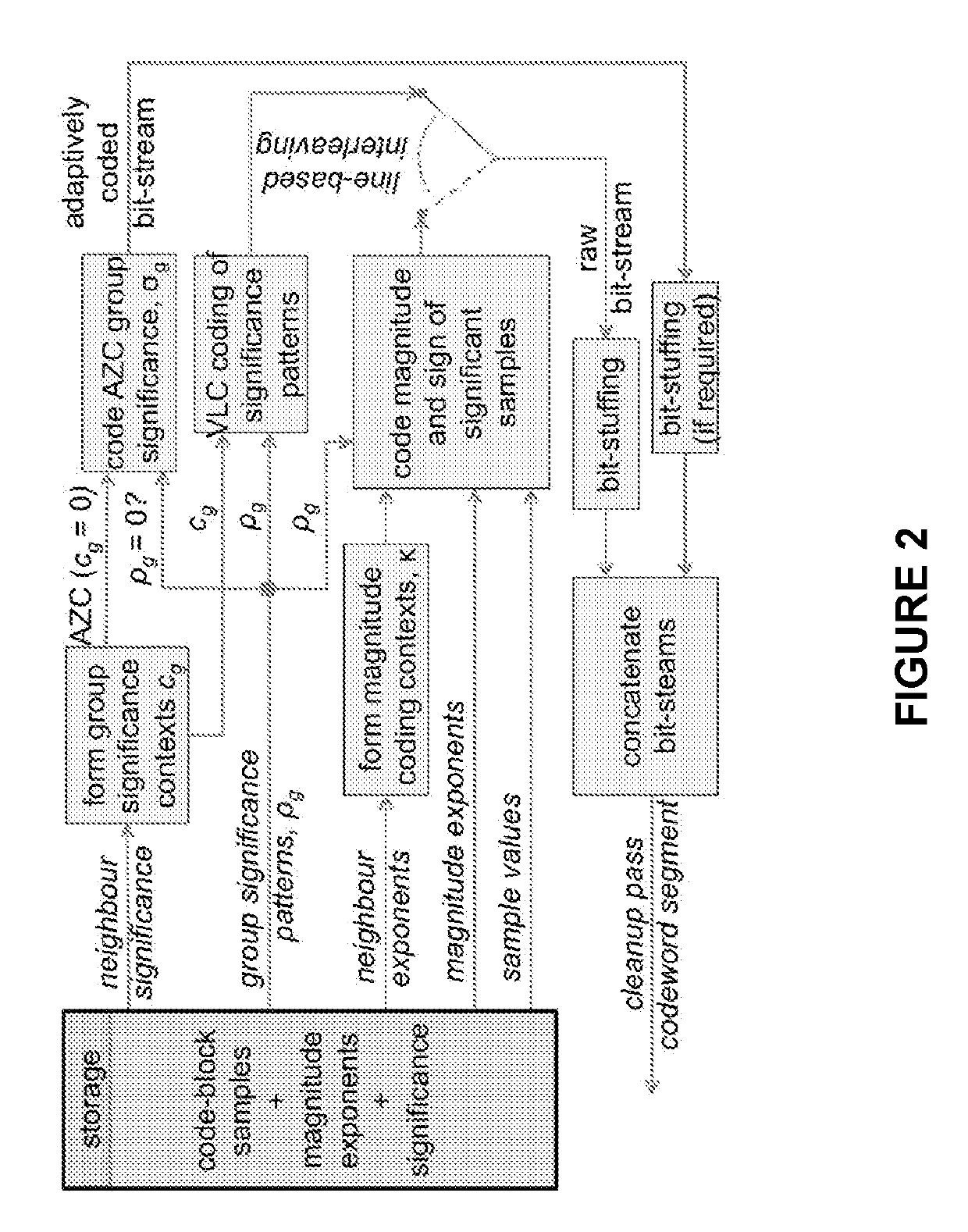
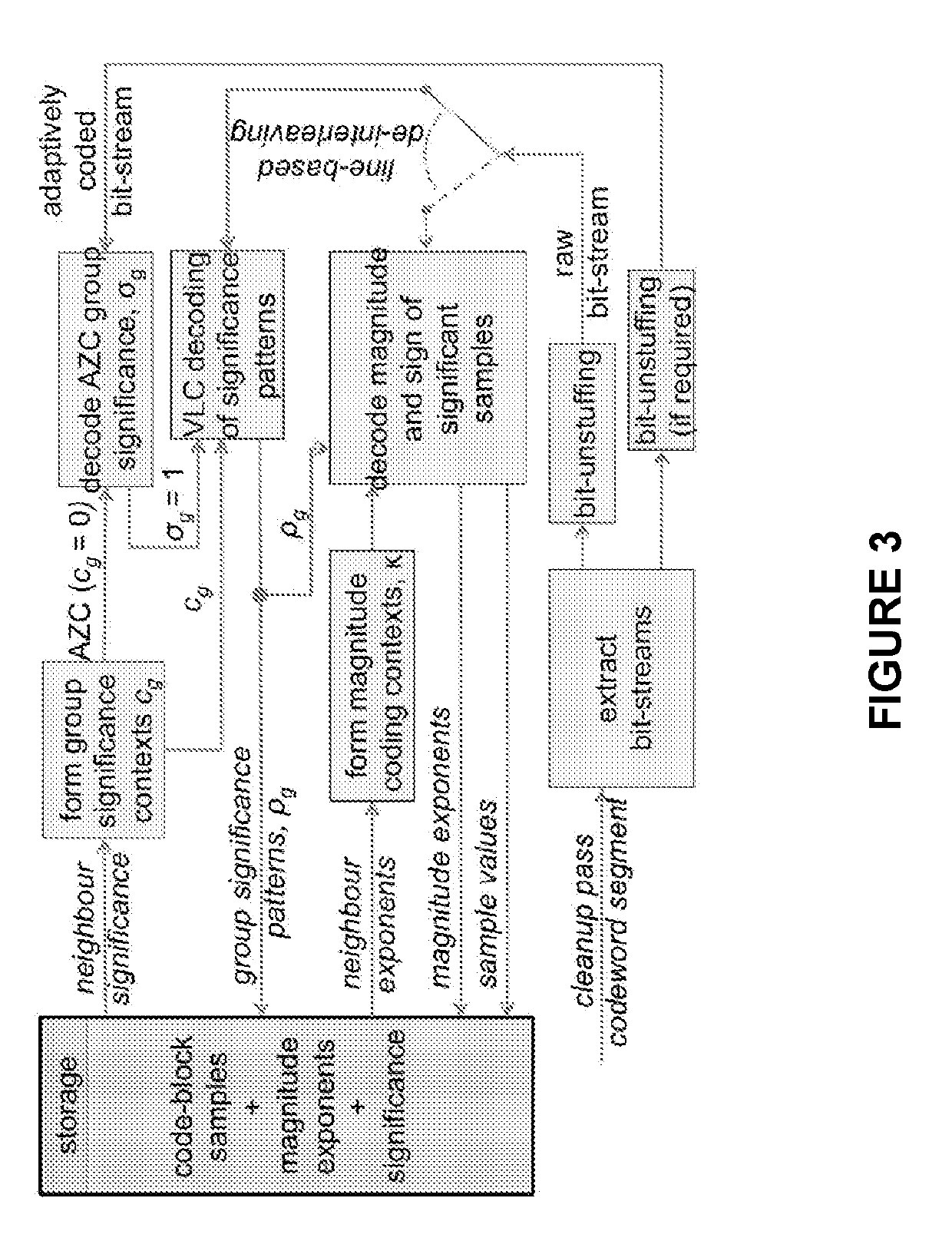
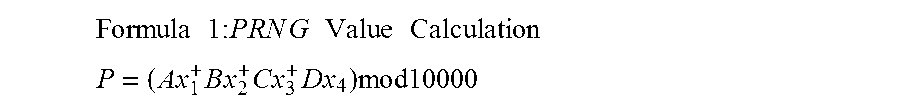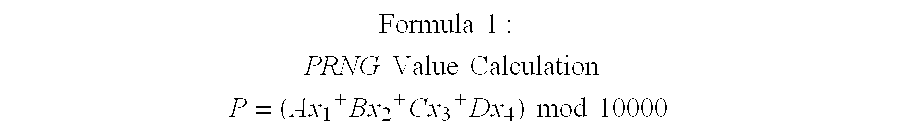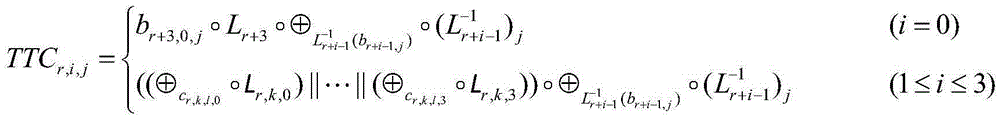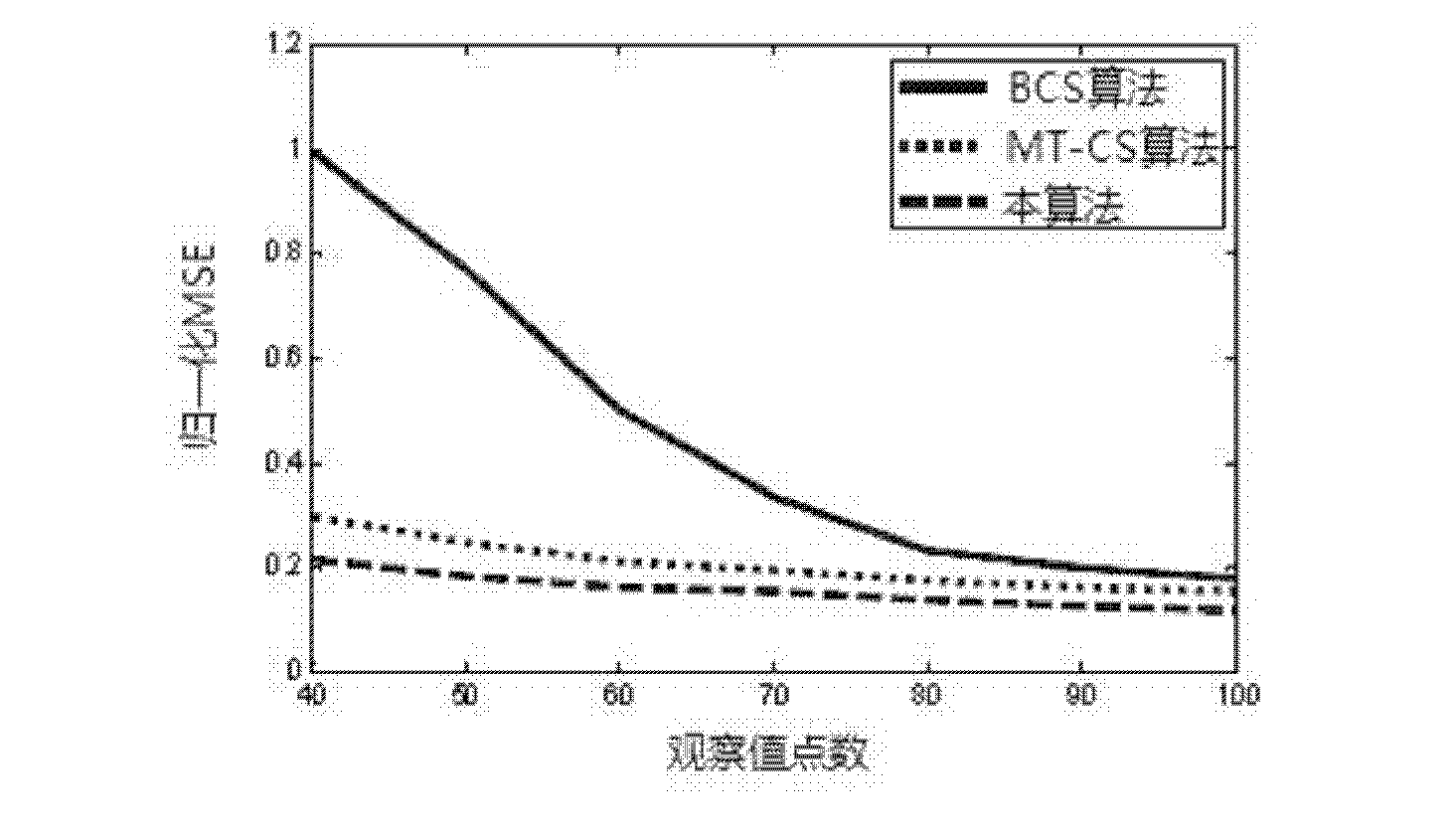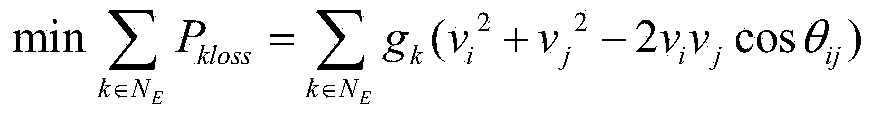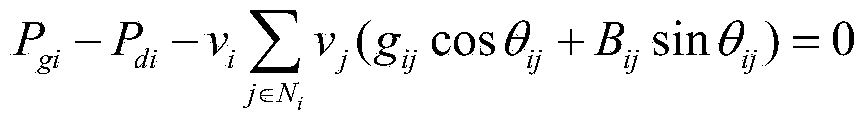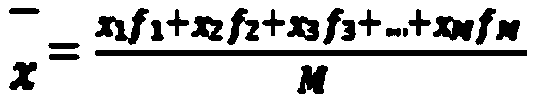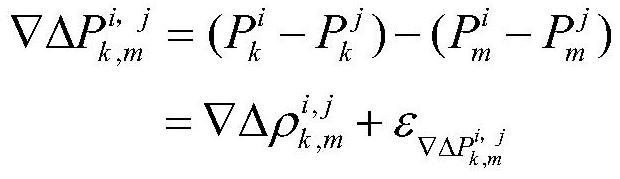Patents
Literature
135 results about "Standard algorithms" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In elementary arithmetic, a standard algorithm or method is a specific method of computation which is conventionally taught for solving particular mathematical problems. These methods vary somewhat by nation and time, but generally include exchanging, regrouping, long division, and long multiplication using a standard notation, and standard formulas for average, area, and volume. Similar methods also exist for procedures such as square root and even more sophisticated functions, but have fallen out of the general mathematics curriculum in favor of calculators (or tables and slide rules before them).
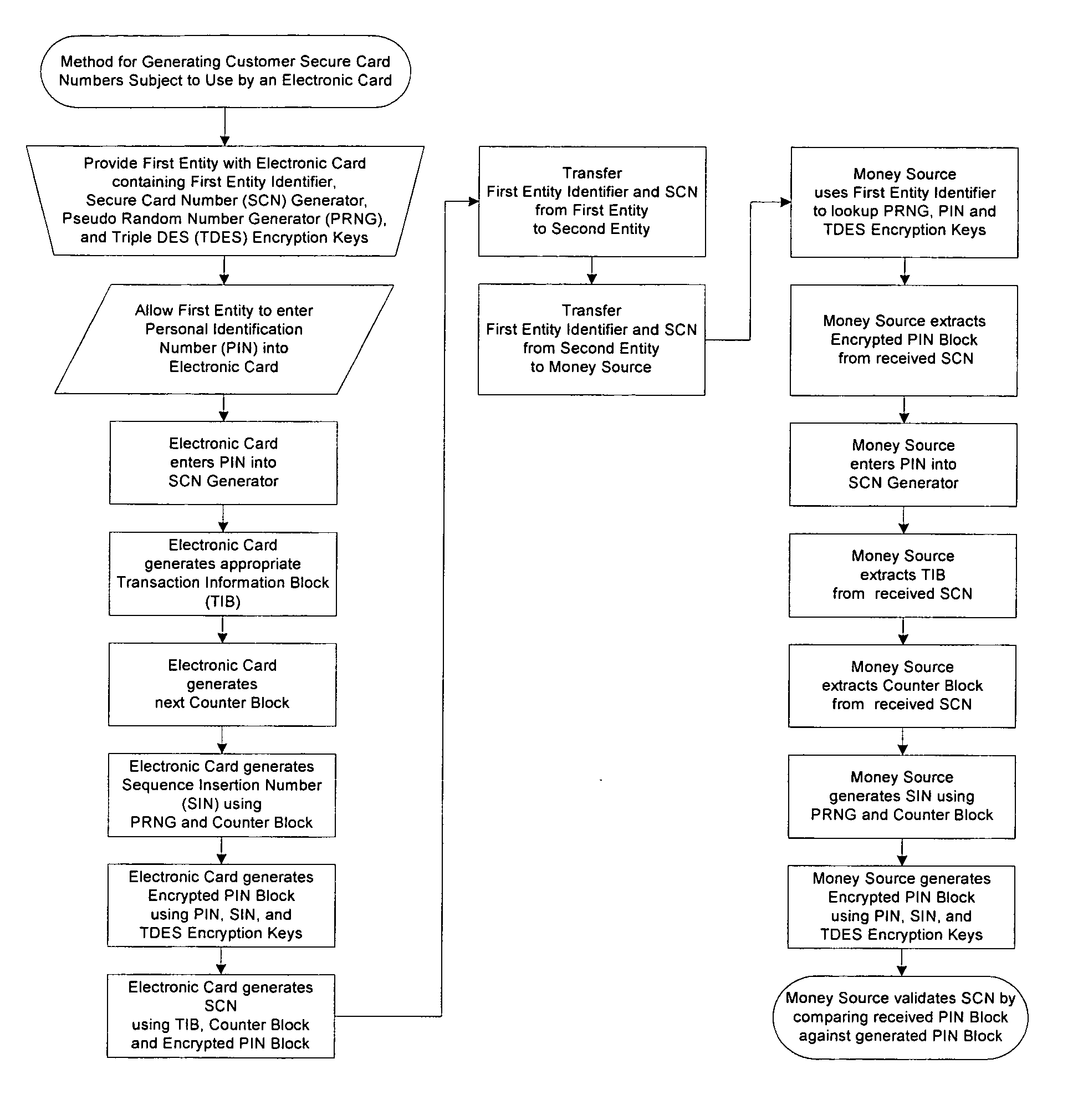
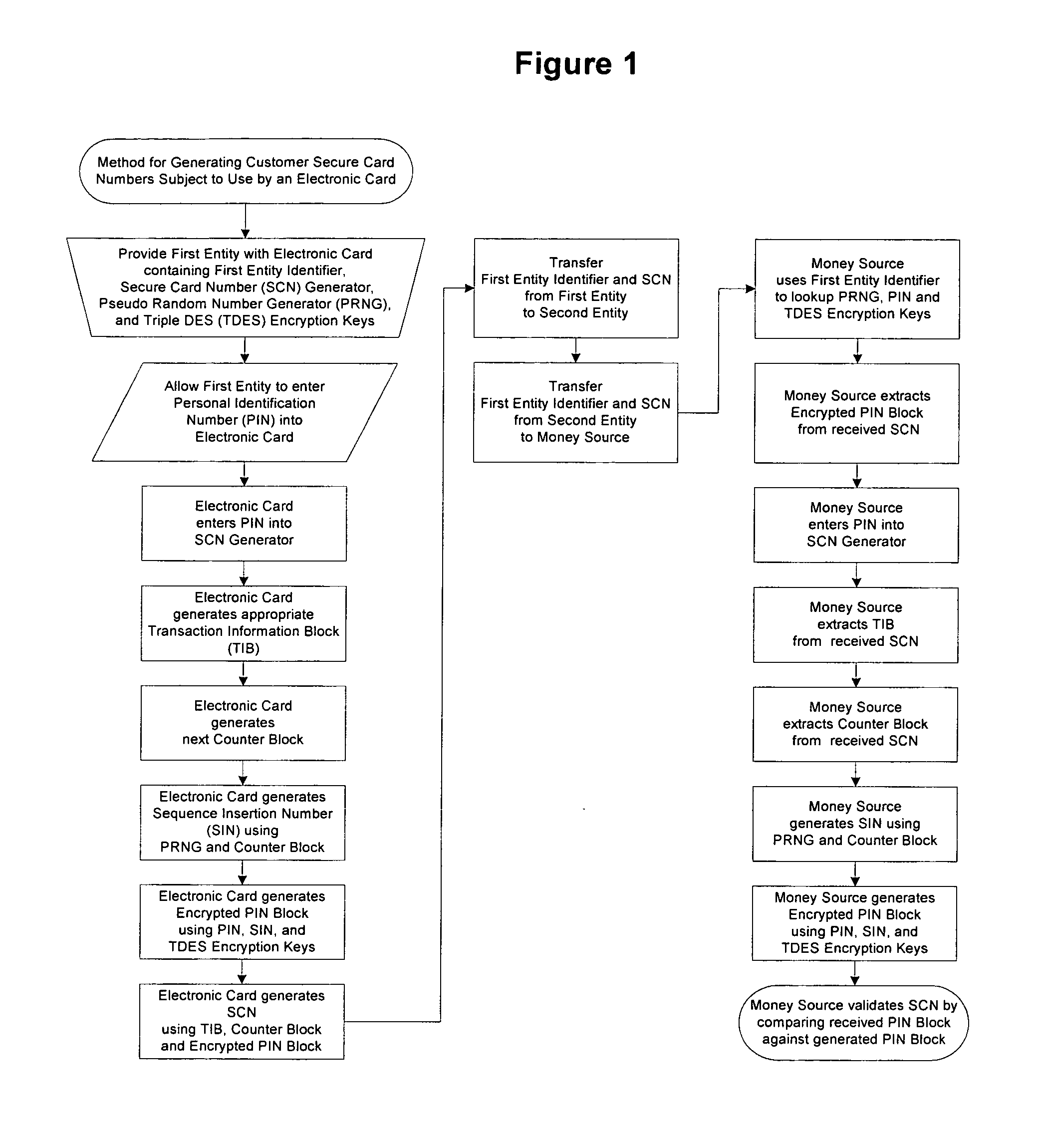
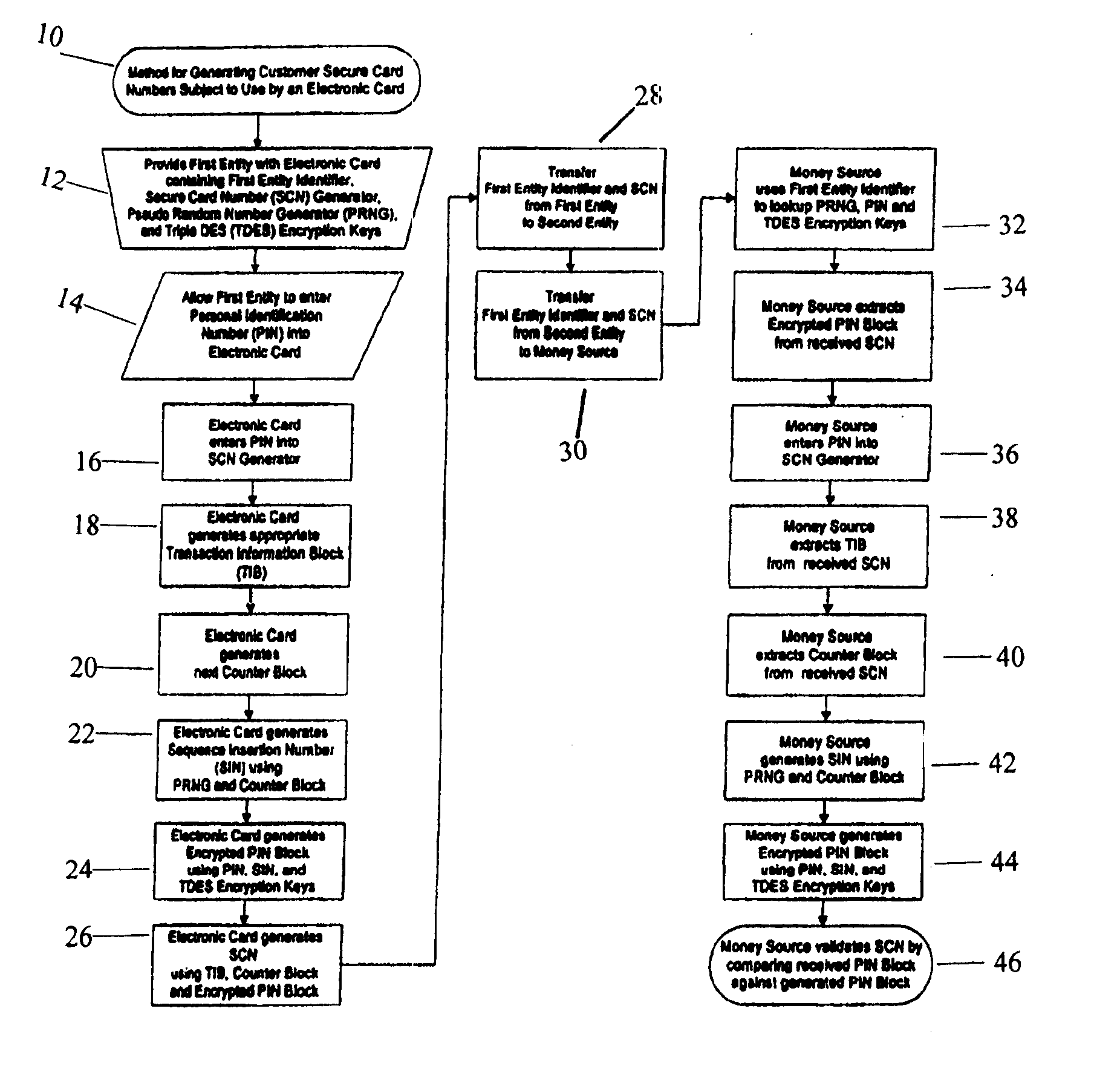
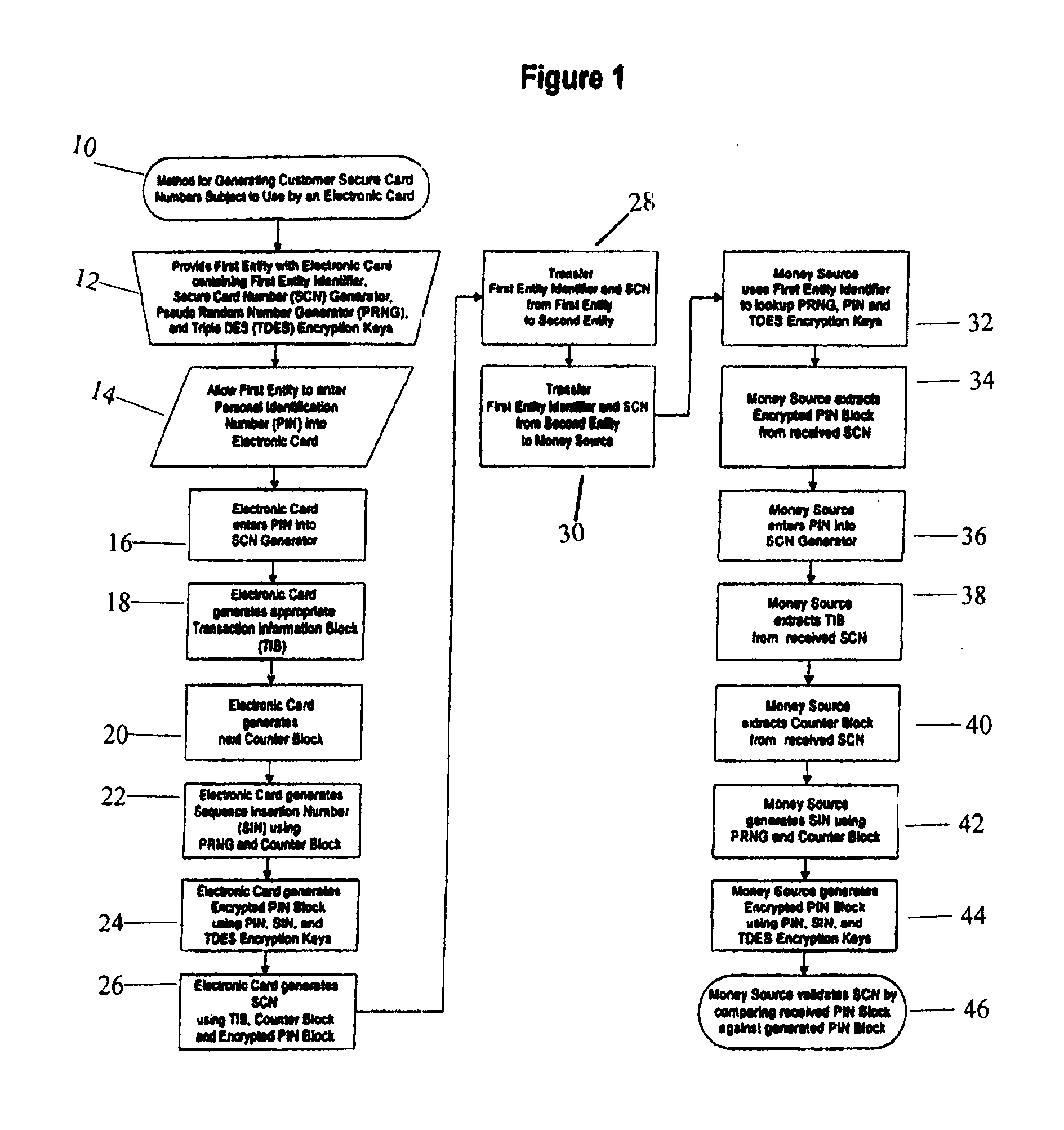
Method for generating customer secure card numbers
A method for providing secure transactions generates a Secure Card Number (“SCN”) for a first entity that is transferred with a first entity identifier to a second entity and then to a money source that verifies that the transaction is valid by use of the first entity identifier and the SCN. The SCN includes a 0Transaction Information Block (“TIB”), a Counter Block, and an encrypted Personal Identification Number (“PIN”) Block. The SCN is transferred to the money source in an account number or a non-account data field. The money source can use the TIB to determine whether the SCN should be used once or multiple times or to identify one of several physical devices, all of which are issued to the first entity, used to generate the SCN. The money source validates the SCN by duplicating the encryption process used to create an encrypted PIN Block and comparing the result to the encrypted PIN Block received with the transaction. A Triple Data Encryption Standard algorithm encrypts a PIN Block generated from a PIN, a Sequence Insertion Number (“SIN”) and a known starting value. The SIN can be a combination of three seed values and a random value generated by a Pseudo Random Number Generator (“PRNG”) initialized with the seed values. A Counter value is associated with the Counter Block and the seed values.
Owner:PRIVASYS
Method for Generating Customer Secure Card Numbers
InactiveUS20070215688A1Complete banking machinesFinancePersonal identification numberEntity identifier
A method for providing secure transactions generates a Secure Card Number (“SCN”) for a first entity that is transferred with a first entity identifier to a second entity and then to a money source that verifies that the transaction is valid by use of the first entity identifier and the SCN. The SCN includes a Transaction Information Block (“TIB”), a Counter Block, and an encrypted Personal Identification Number (“PIN”) Block. The SCN is transferred to the money source in an account number or a non-account data field. The money source can use the TIB to determine whether the SCN should be used once or multiple times or to identify one of several physical devices, all of which are issued to the first entity, used to generate the SCN. The money source validates the SCN by duplicating the encryption process used to create an encrypted PIN Block and comparing the result to the encrypted PIN Block received with the transaction. A Triple Data Encryption Standard algorithm encrypts a PIN Block generated from a PIN, a Sequence Insertion Number (“SIN”) and a known starting value. The SIN can be a combination of three seed values and a random value generated by a Pseudo Random Number Generator (“PRNG”) initialized with the seed values. A Counter value is associated with the Counter Block and the seed values.
Owner:PRIVASYS
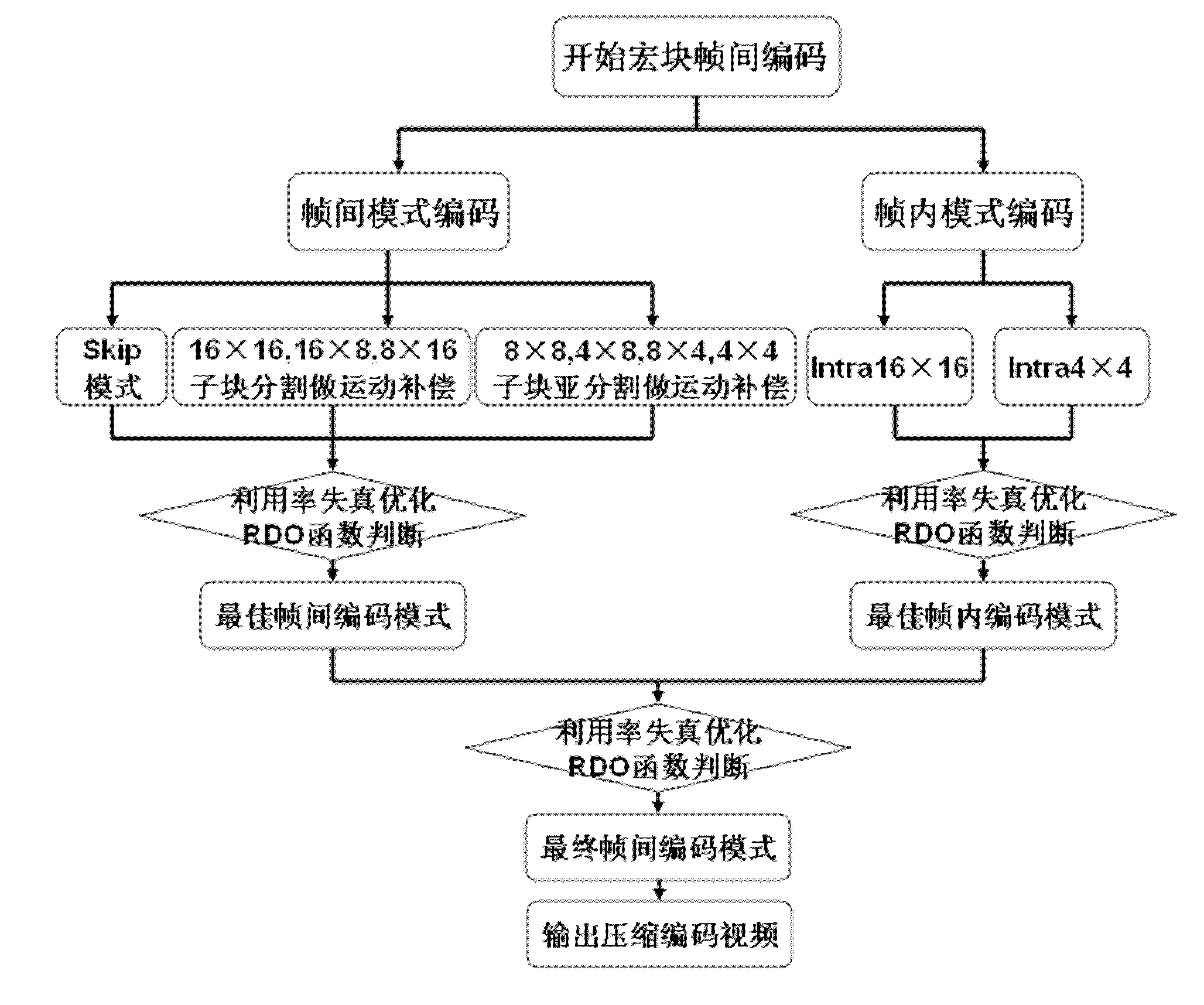
Method for realizing rapid video coding by adopting hierarchical structure anticipation
InactiveCN102186070AVersatileReduce coding timeTelevision systemsDigital video signal modificationComputer architectureVideo quality
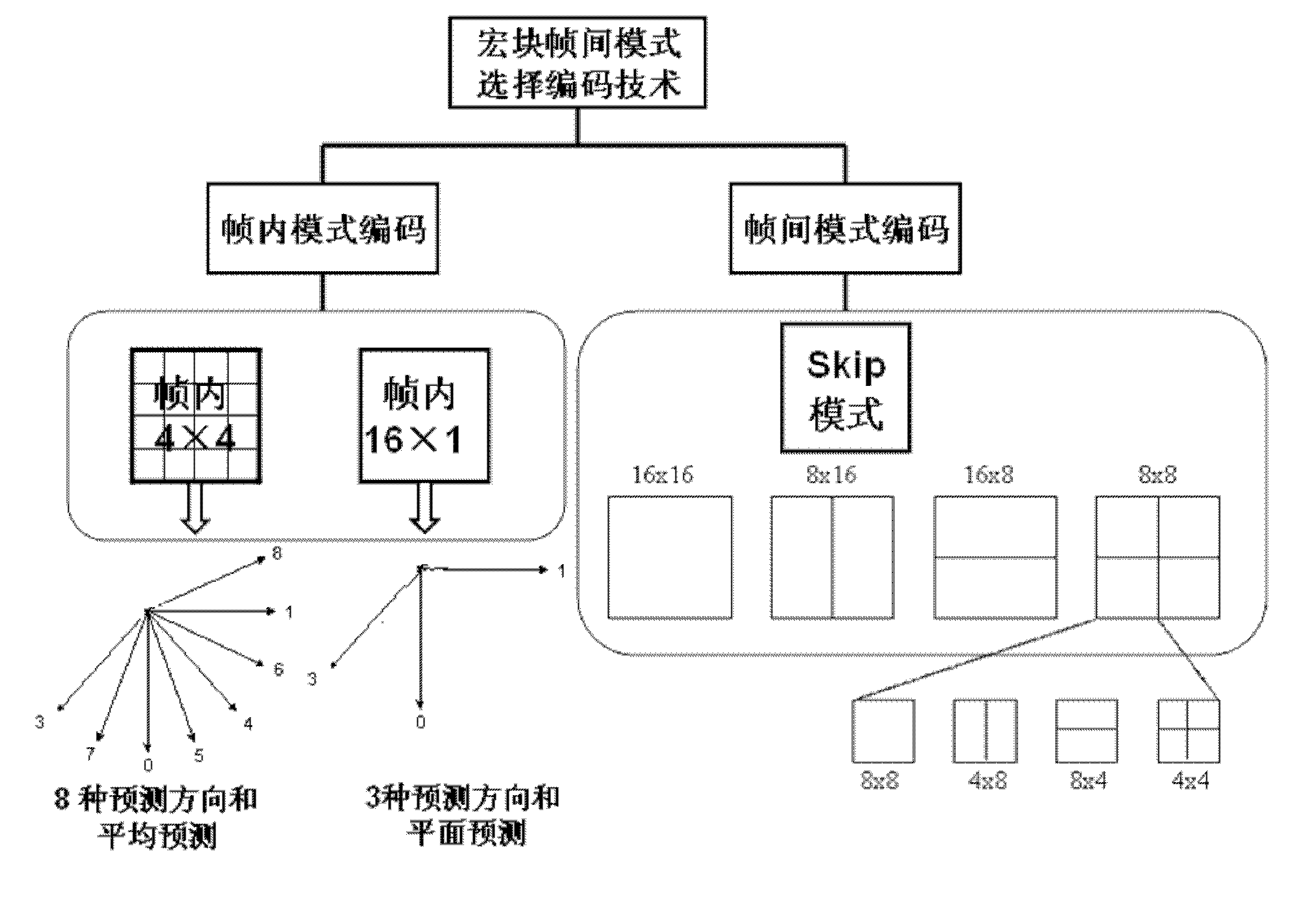
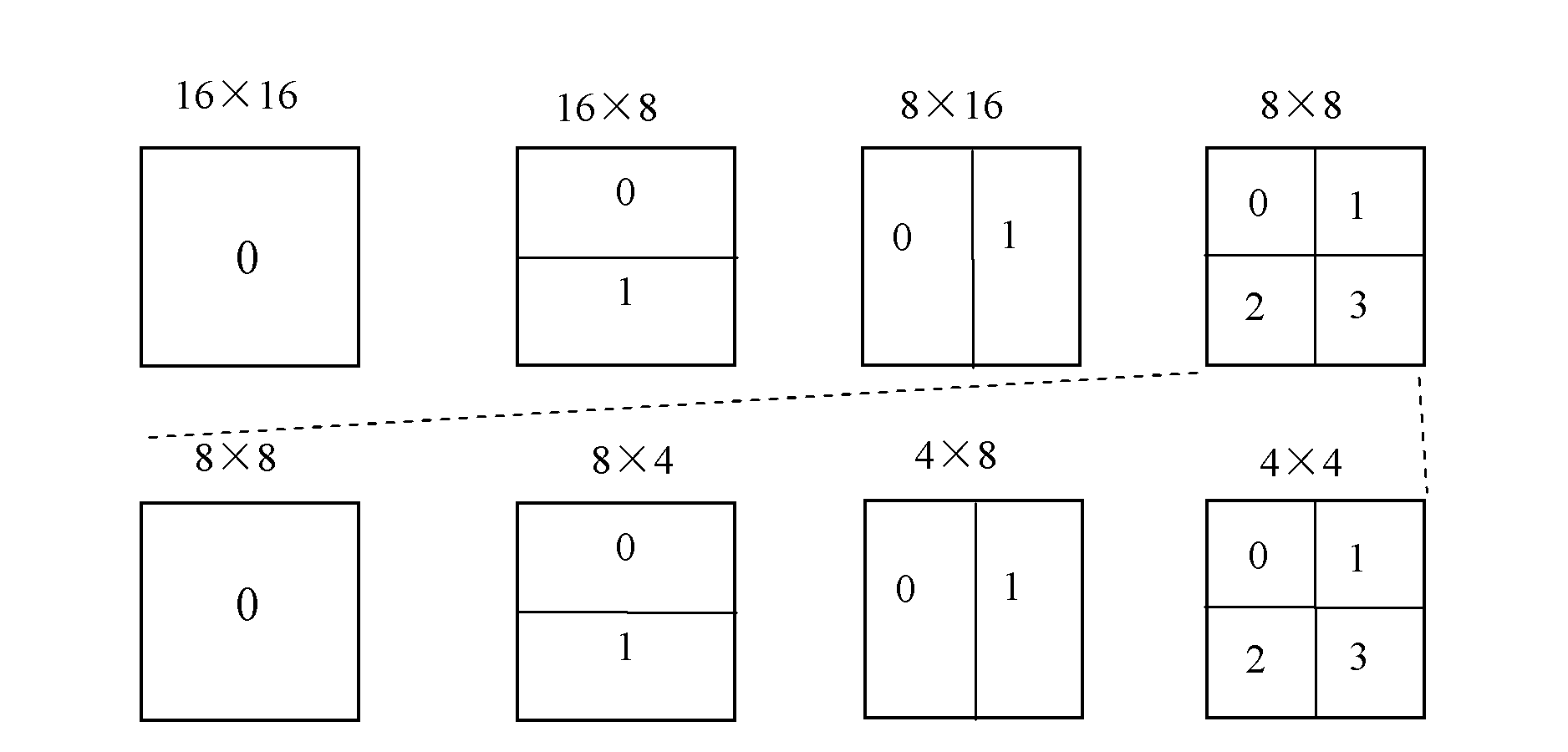
The invention discloses a method for realizing rapid video coding by adopting hierarchical structure anticipation, which relates to the field of video compression coding. The method comprises the following steps of: extracting the brightness information of a current coded macro block from original video data; defining, calculating and comparing time / space correlation characteristics of the current coded macro block, and anticipating whether the macro block may adopt inter-frame prediction or intra-frame prediction; and if the macro block adopts the inter-frame prediction, defining and calculating the flatness characteristic of the macro block, dividing the current coded macro block into one type of a flat macro block, a texture-rich macro block and a characteristic-unremarkable macro block according to the flatness characteristic, anticipating a set of inter-frame prediction mode to be adopted in a targeted way, determining an optimal inter-frame prediction mode in advance to realize rapid inter-frame compression coding. By the method provided by the invention, the inter-frame coding complexity and coding time are greatly reduced on the premise of ensuring lossless video quality, not increasing compression code rate and keeping an output code stream structure, and the high performance of high compression ratio of a conventional standard algorithm is maintained.
Owner:BEIJING UNIV OF TECH
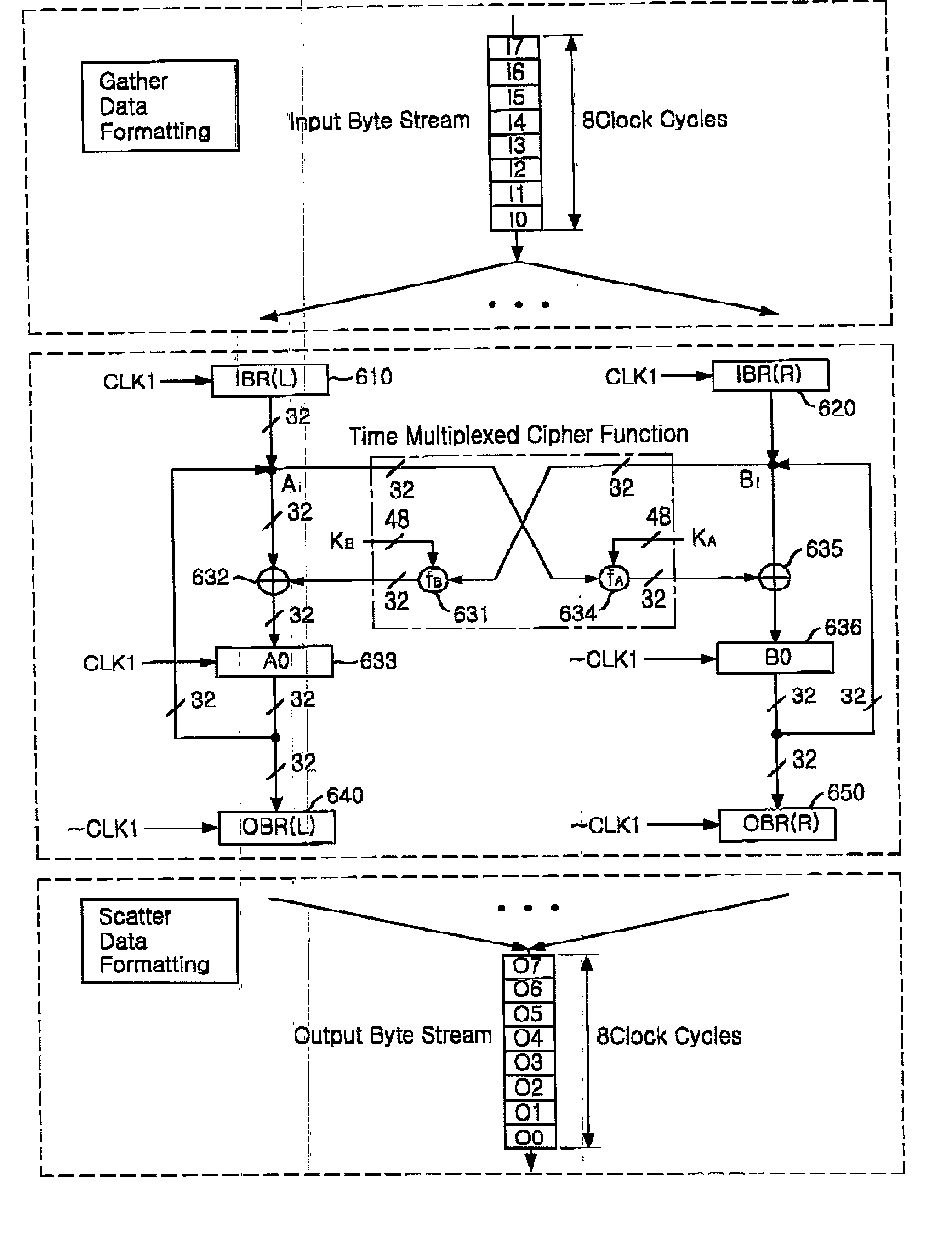
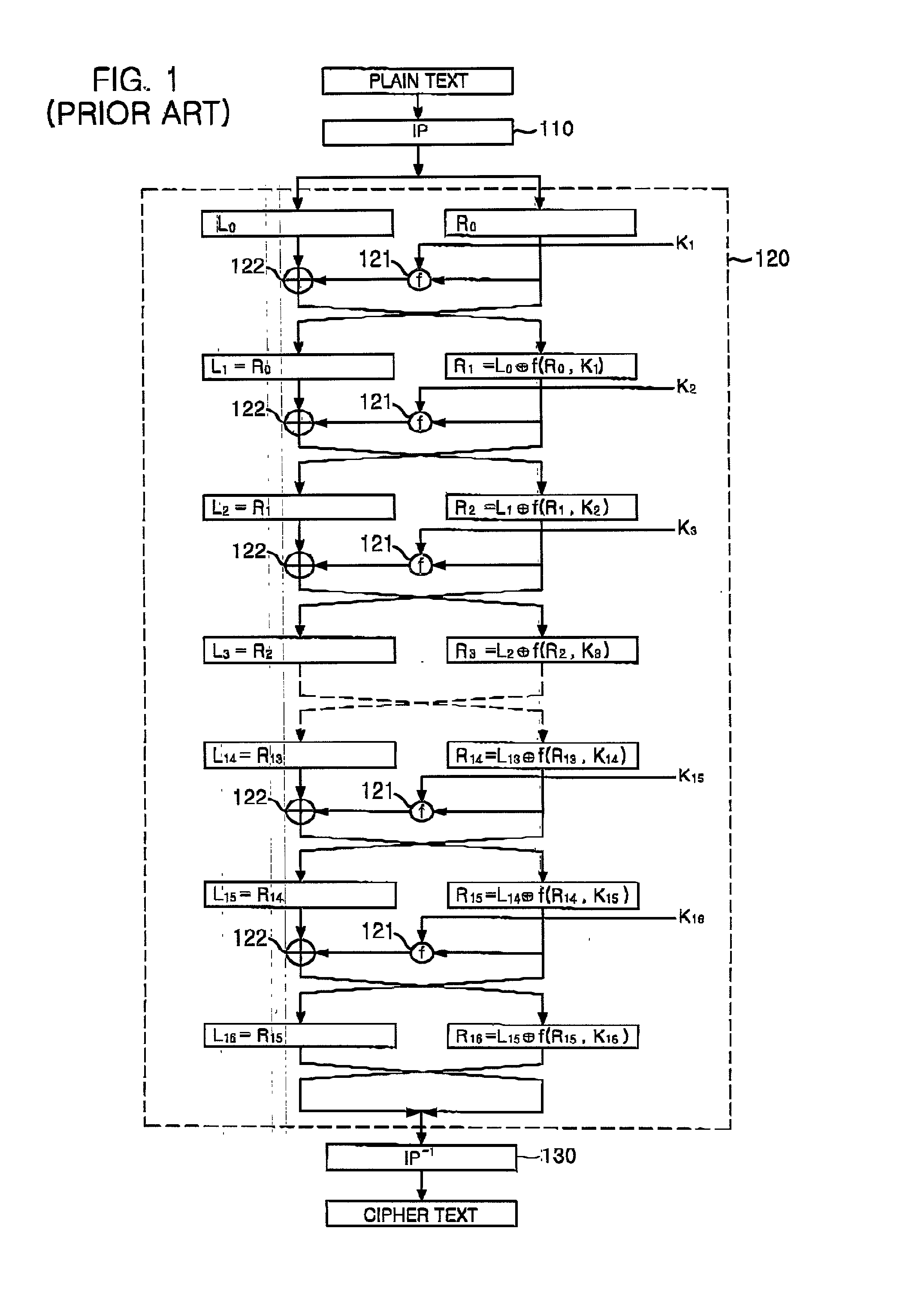
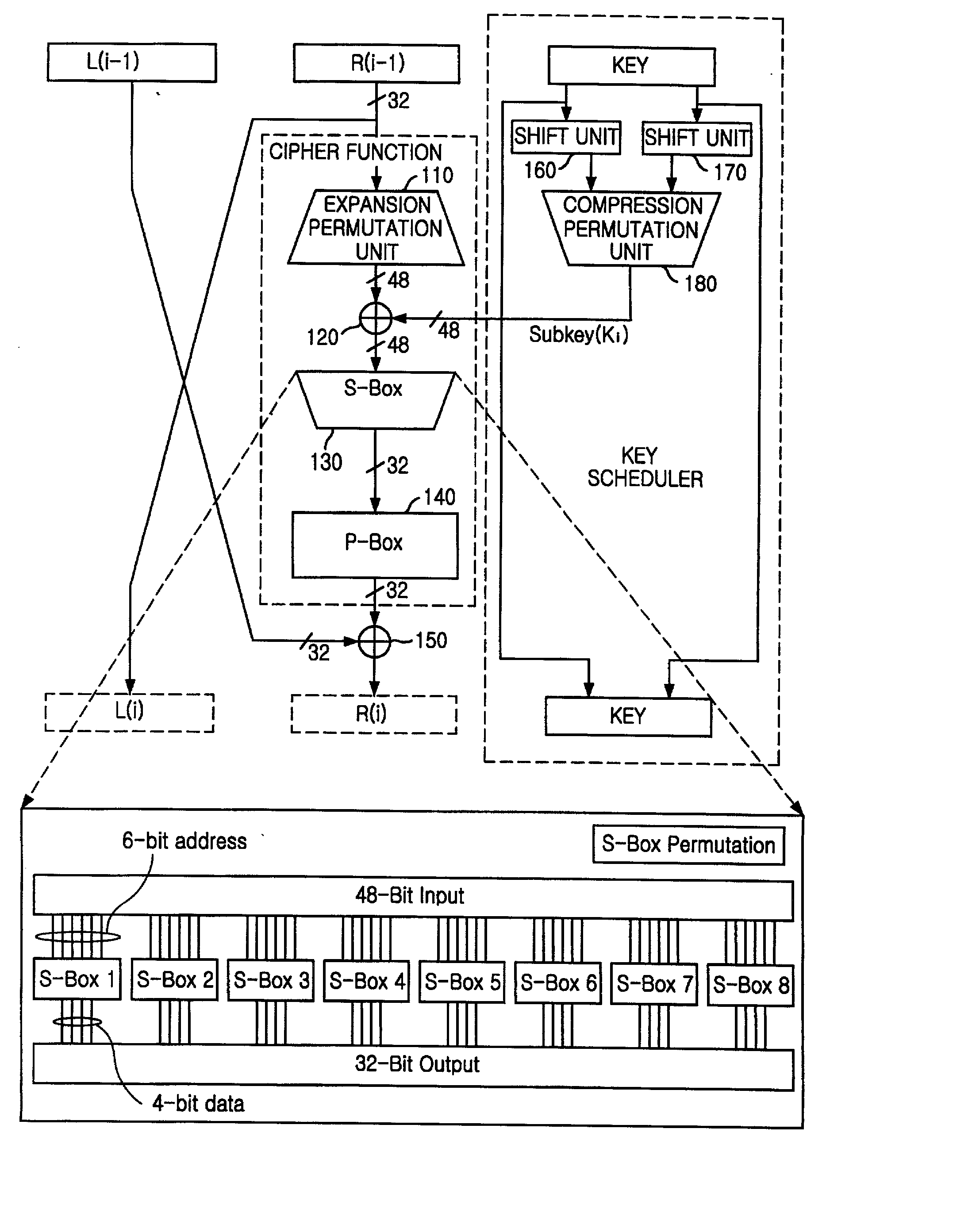
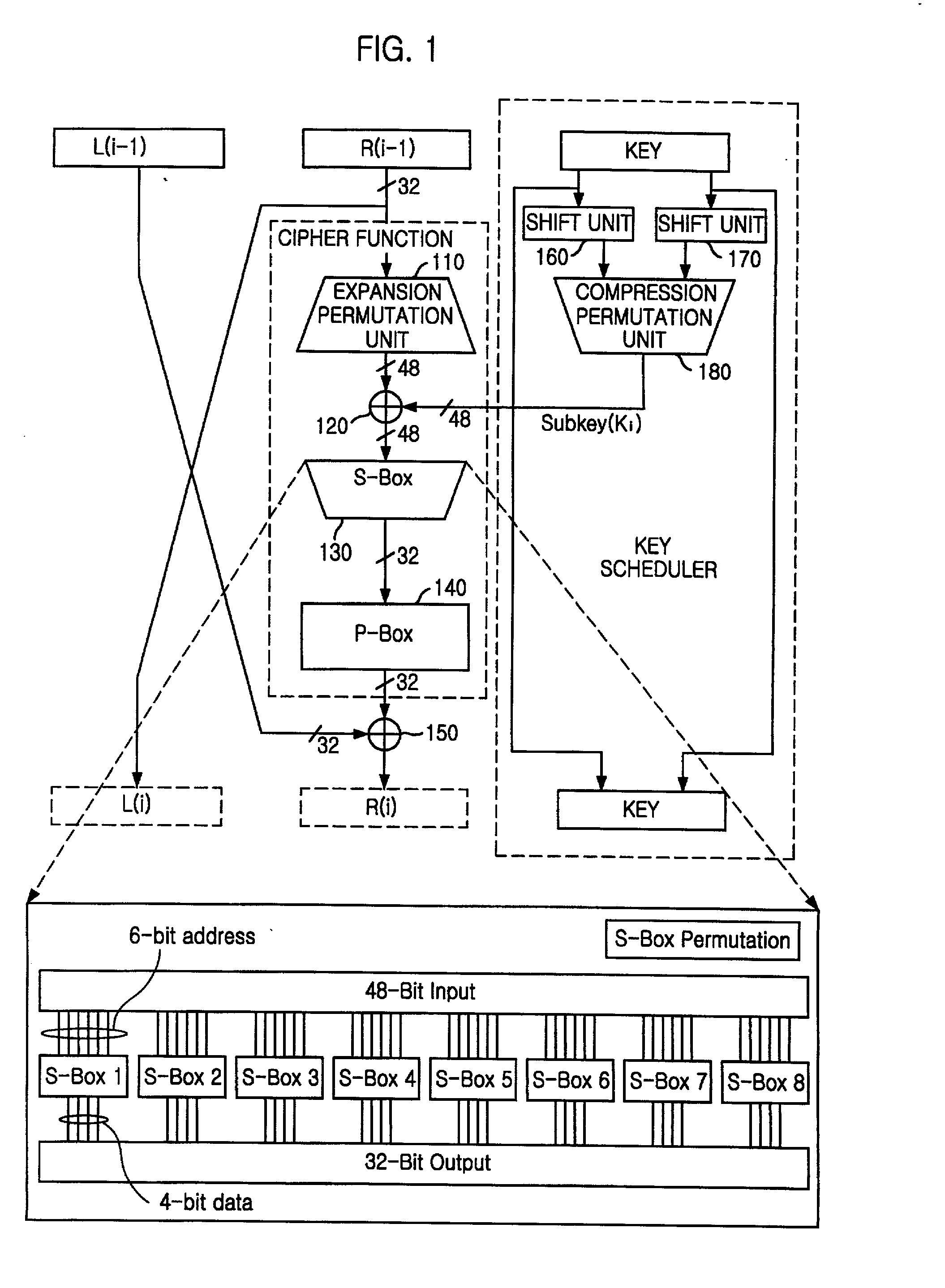
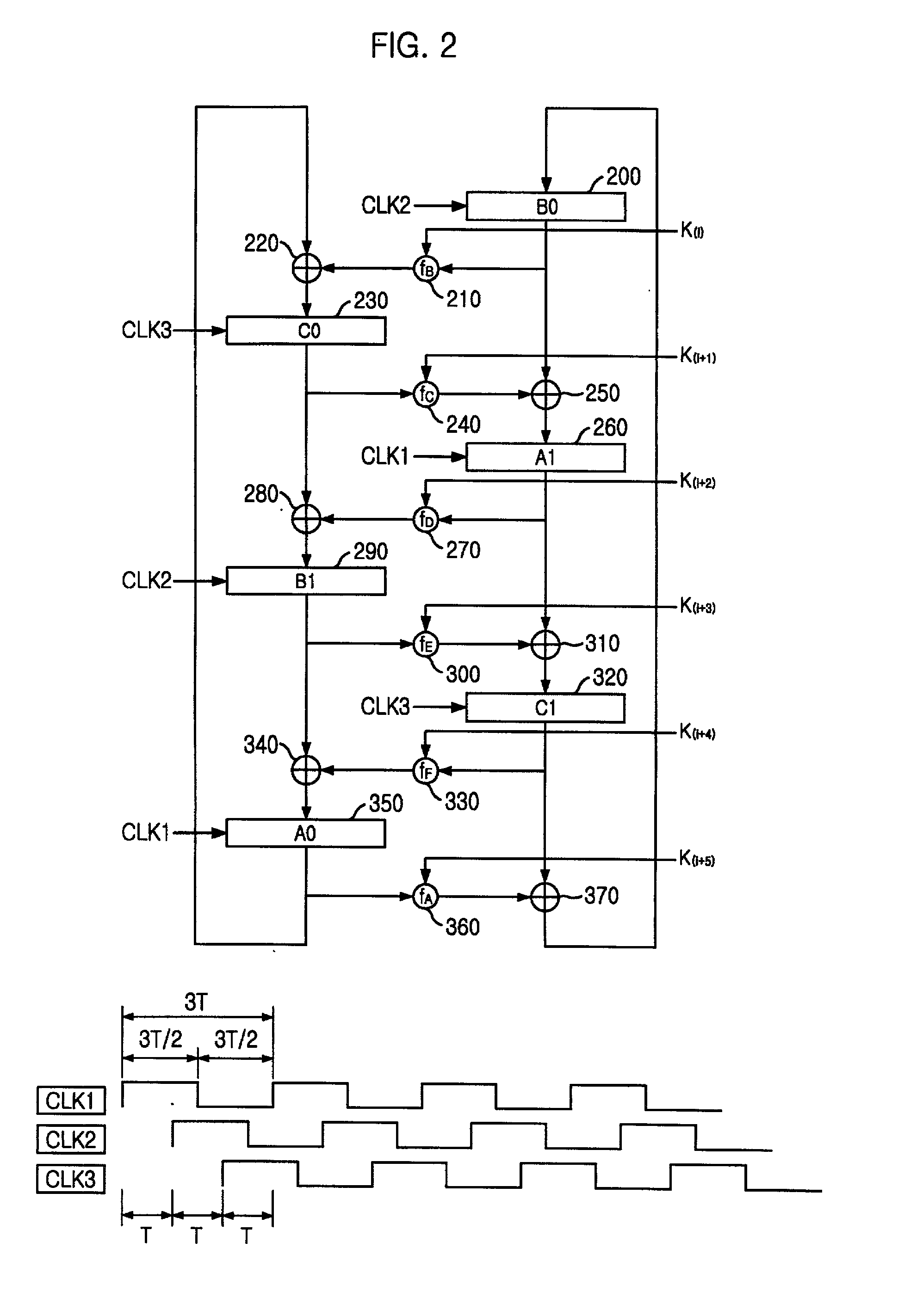
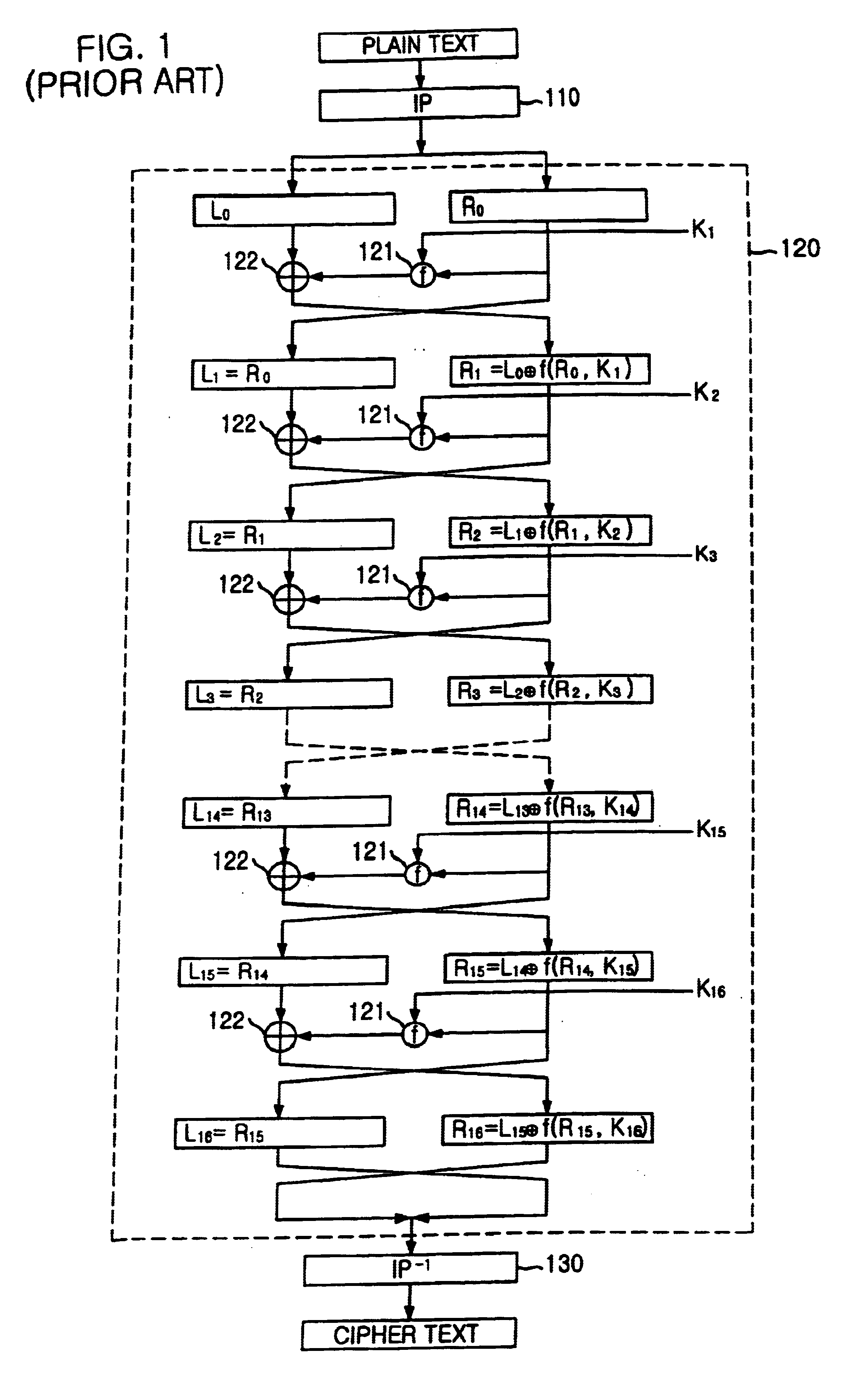
Encryption apparatus using data encryption standard algorithm
InactiveUS20020012430A1Encryption apparatus with shift registers/memoriesSecret communicationByteComputer science
An encryption apparatus using a DES encryption algorithm is disclosed. The apparatus for encrypting 64-bit plain text blocks includes: input buffering unit for receiving a plain text block byte-by-byte and outputting a first and a second 32-bit plain text blocks in response to a first clock; encryption unit for performing time multiplexed encryption of the first and the second 32-bit plain text blocks in response to the first clock and a second clock, thereby generating a first and a second 32-bit cipher text blocks; and output buffering unit for receiving the first and the second 32-bit cipher text blocks in response to the second clock and outputting eight 8-bit cipher text blocks.
Owner:MAGNACHIP SEMICONDUCTOR LTD
Electronic medical record realization method and device based on blockchain
InactiveCN107368750AGuaranteed precisionPrevent tamperingDigital data protectionSpecial data processing applicationsMedical recordPassword
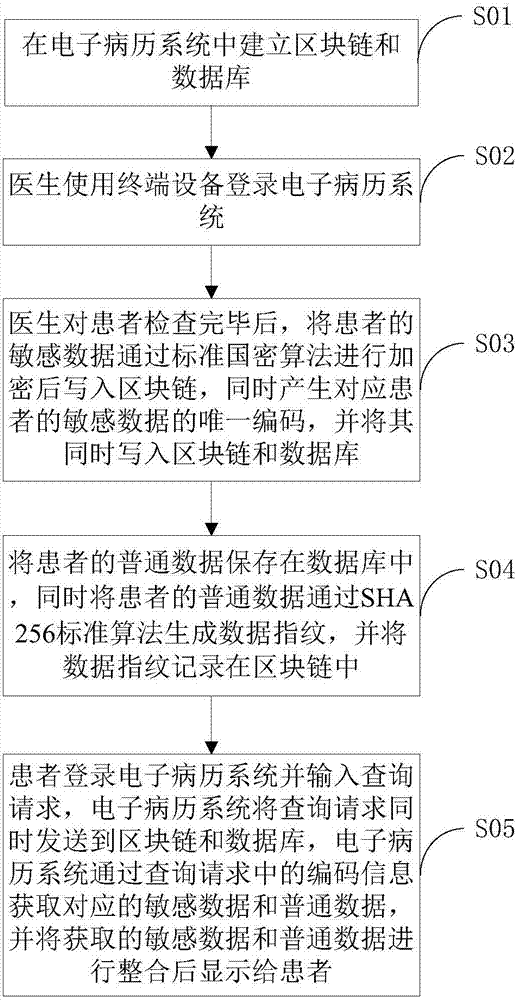
The invention discloses an electronic medical record realization method and device based on a blockchain. The method comprises the following steps that: a doctor uses terminal equipment to log in an electronic medical record system; after the doctor finishes checking a patient, the sensitive data of the patient is encrypted through a standard domestic password algorithm, then, the sensitive data of the patient is written into the blockchain, and the unique code of the sensitive data of the corresponding patient is generated and written into the blockchain and a database; the common data of the patient is stored in the database, meanwhile, the common data of the patient is generated into a data fingerprint through an SHA256 standard algorithm, and the data fingerprint is recorded in the blockchain; and the patient logs in the electronic medical record system and inputs a query request, the query request is sent to the blockchain and the database, and the electronic medical record system obtains the corresponding sensitive data and common data through coding information in the query request, carries out integration on the obtained sensitive data and common data and displays the integrated data to the patient. When the method is implemented, the information of the patient can be shared and is convenient in obtaining, the information of the patient can be prevented from being tampered, and the rights of the patient can be guaranteed.
Owner:雷虹
Security white box realizing method and device for national cipher standard algorithm SM4
InactiveCN105681025AEnsure safetySecurity advantageEncryption apparatus with shift registers/memoriesPasswordComputer terminal
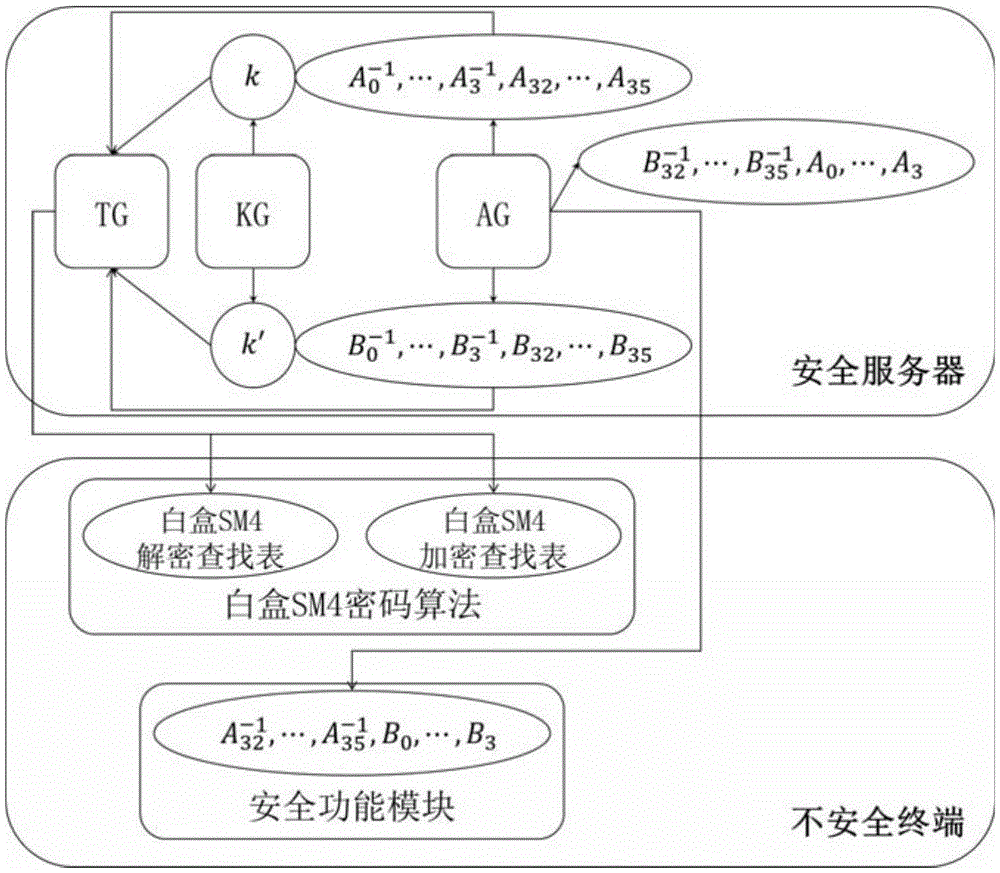
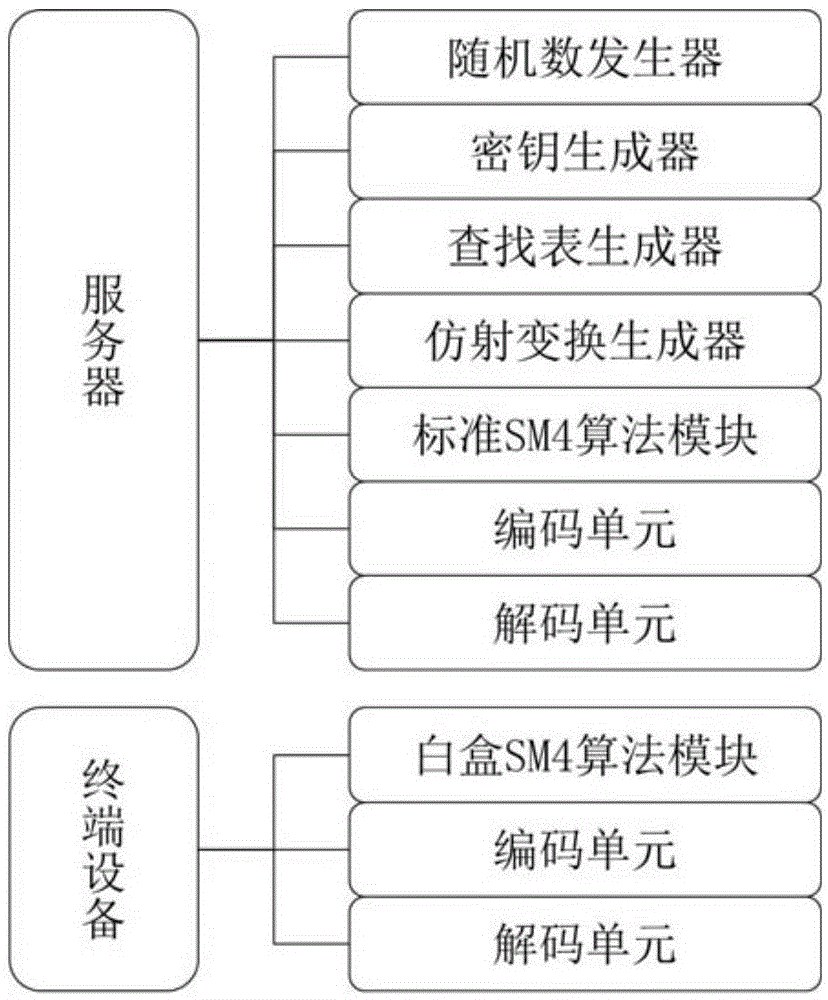
The present invention discloses a security white box realizing method and device for the national cipher standard algorithm SM4, discloses essential components of equipment required by the white box SM4 algorithm, and belongs to the technical field of information security. With adoption of the method and the device, secret keys embedded into cipher software can be effectively protected in untrusted computer terminals. The white box SM4 password algorithm provided by the present invention achieves safe realization of the China commercial block cipher standard SM4. Secret keys are embedded into lookup tables, randomly selected affine codes are used for protecting the lookup tables, and thus the secret keys embedded in the lookup tables are protected. A TTC lookup table and a TRT lookup table are used in the algorithm, the last xor operation of output data of the TTC lookup table is embedded into the TRT lookup table, and output data of the TRT lookup table is protected by new 32-bit affine codes, so the situation of offsetting 32-bit affine codes embedded in the lookup tables by combining lookup tables can be prevented, thereby preventing reduction of code cracking difficulty, and realizing the protection aim.
Owner:INST OF INFORMATION ENG CAS
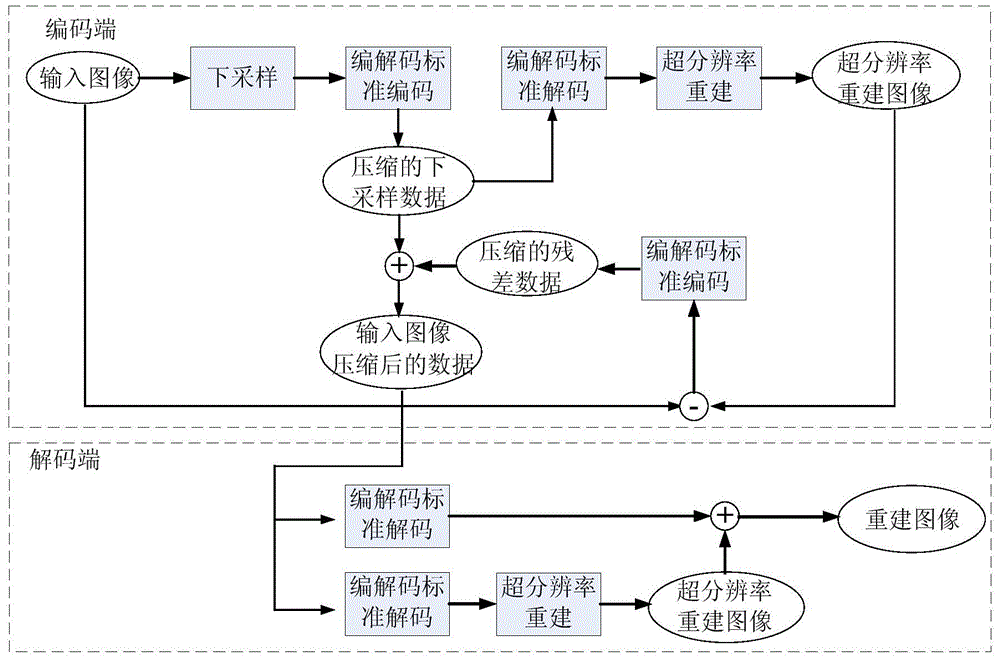
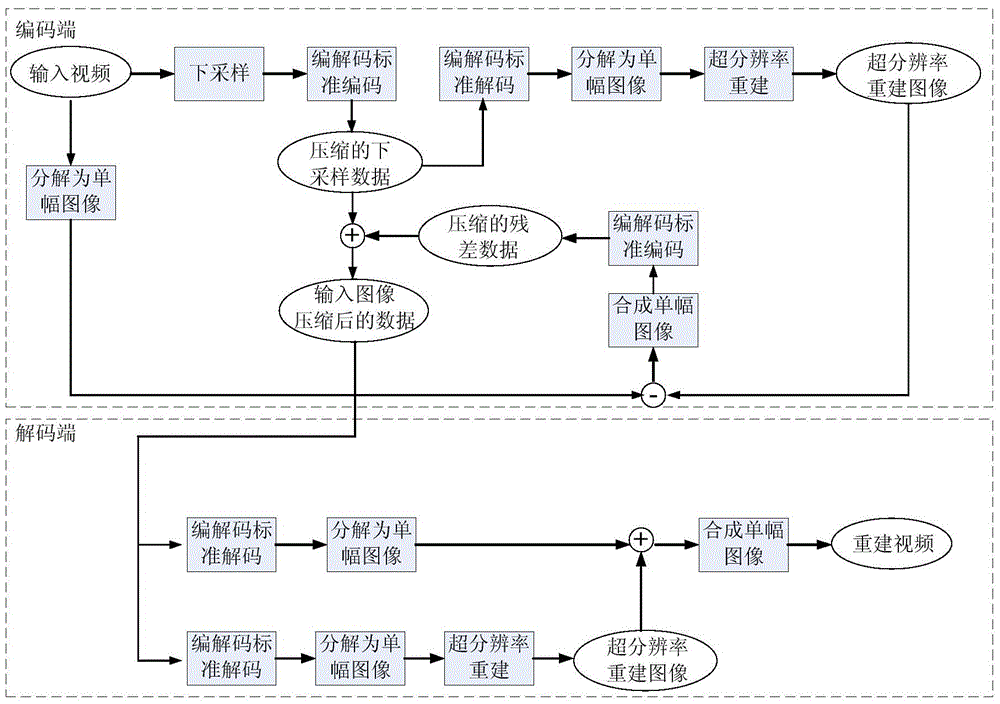
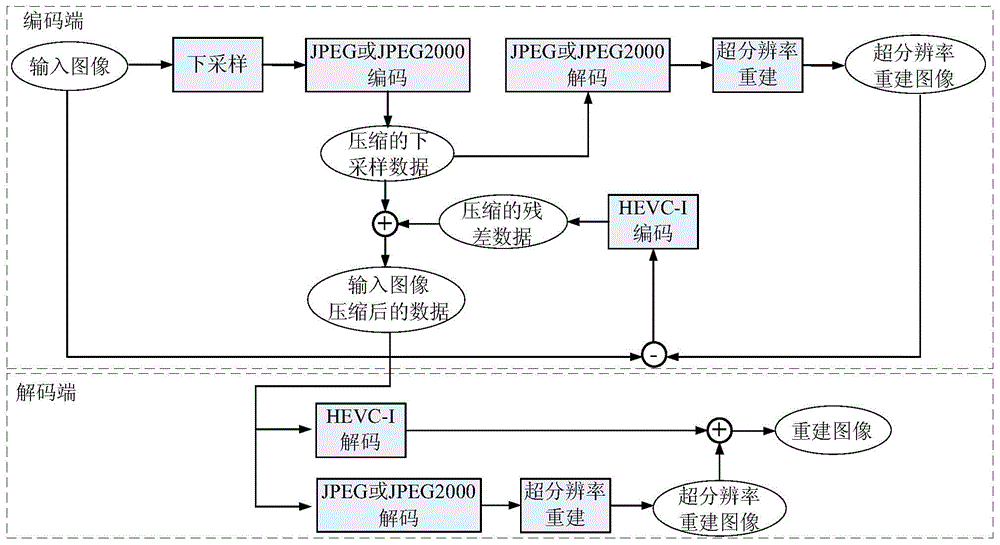
Image compression method combining super-resolution reconstruction
ActiveCN103607591AImprove subjective visual qualityReduce code rateImage enhancementDigital video signal modificationNegative feedbackImaging quality
The invention discloses a video and image lossy compression method for image coding. The method combines traditional JPEG, JPEG2000, H.264 and HEVC-code standard algorithms with super-resolution image reconstruction and designs an image compression method combining the super-resolution reconstruction on the basis. Downsampling is carried out on an input video and image, wherein a downsampling method adopts a Bicubic algorithm and a downsampling multiple is 2. The number of dot arrays of a downsampling image is only 1 / 4 of that of an original image. The encoding rate of the downsampling image is far lower than that of an original input image so that the encoding rate is reduced. At the same time, on the basis that robustness differences of a residual image and a general image are analyzed, a negative-feedback step is introduced in the design so that part of high-frequency detail information lost in a super-resolution image reconstruction step is remedied and reconstructed video or image quality is improved. Compared with the JPEG and the H.264 standard algorithms, the compression method reduces the encoding rate greatly under a situation that image quality is the same.
Owner:SICHUAN UNIV
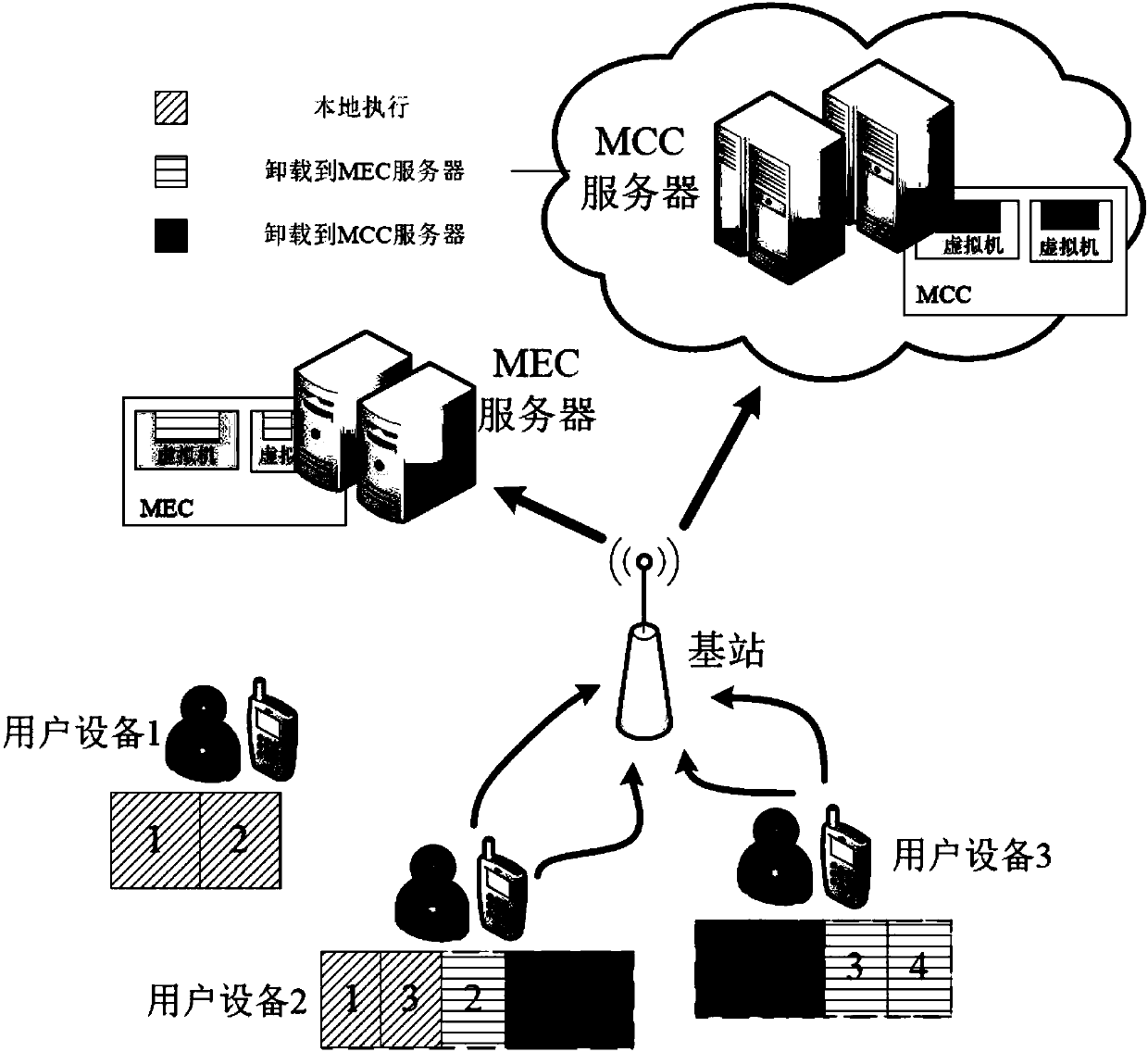
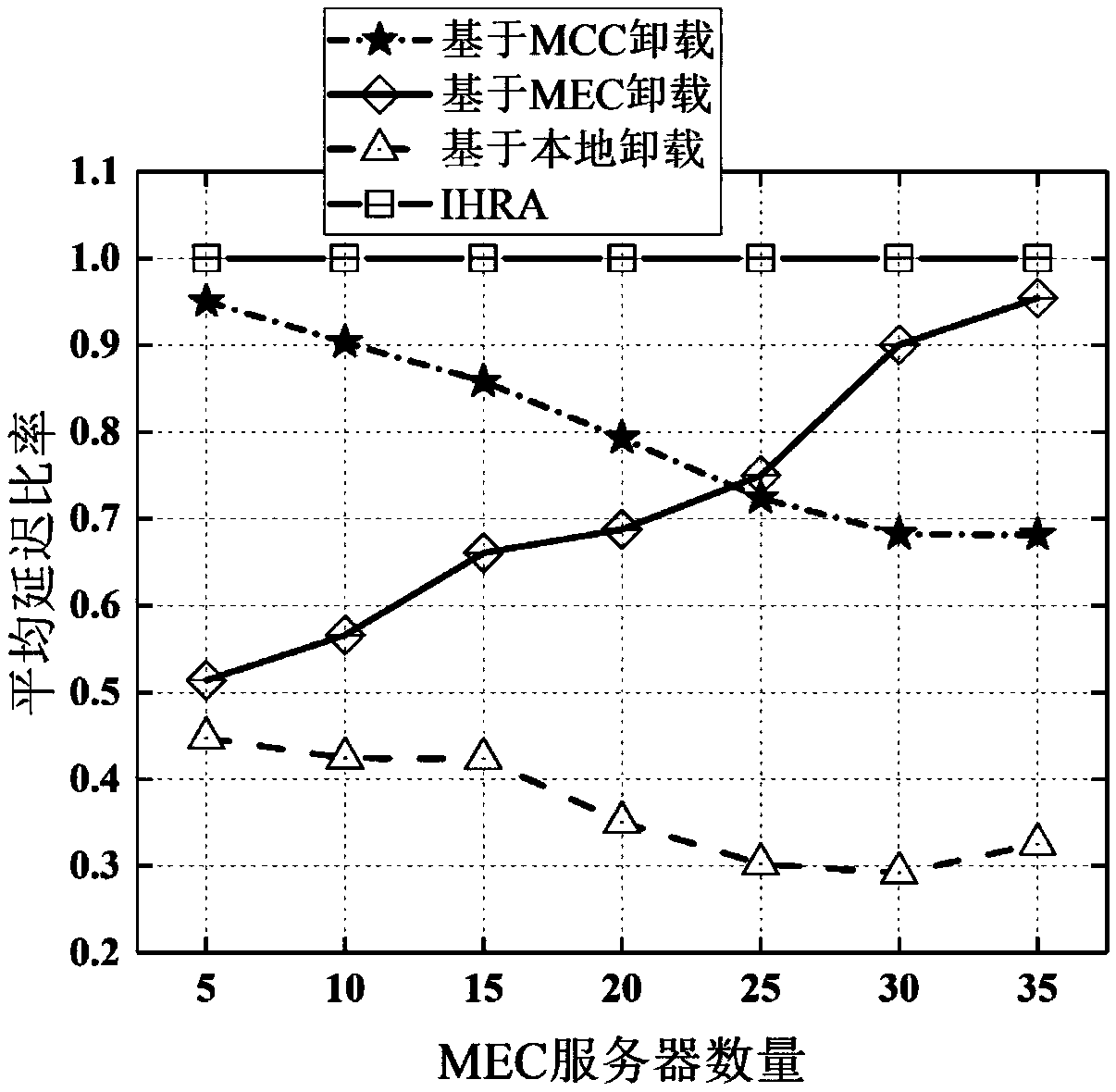
Network unloading method based on mixed cloud computation
The invention provides a network unloading method based on mixed cloud computation. The model defines transmission delay, processing delay and total delay for computing unloading computation beginningfrom the single-user unloading computation problem, and a single-user optimal solution is obtained by using a branch-bound algorithm. The boundary computing resource limitation and the transmission interference between the users are considered on this basis, the multi-user computing unloading problem is modelled as a hybrid integer linear planning MILP problem; due to the high computation complexity of the MILP problem, the model designs an iterative heuristic moving boundary computation resource allocation IHRA algorithm to solve the MILP problem and makes the unloading decision. A simulation result shows that the IHRA algorithm designed by the invention is superior to the standard algorithm in the application program running delay and unloading efficiency, and a new solution scheme is provided for the resource allocation problem of the hybrid cloud computation network unloading model.
Owner:DALIAN UNIV OF TECH
Encryption apparatus using data encryption standard algorithm
InactiveUS20020003876A1Improve process capabilityEncryption apparatus with shift registers/memoriesSecret communicationS-boxMultiplexer
An encryption device eliminates data contention and minimizes area by accessing twice data for a given time by using a memory device of two times faster access time. The encryption device for performing encryption of plain text blocks using data encryption standard algorithm, wherein the encryption device includes an initial permutation unit, a data encryption unit having n-stage (n is an even number) pipeline structure using a first clock, a second clock and a third clock, and an inverse initial permutation unit, the encryption device includes: a multiplexer for selecting one of n / 3 48-bit inputs; 8 S-Boxes, each for receiving 6-bit address among the selected 48-bit and outputting 4-bit data; a demultiplexer for distributing 32-bit data from the S-Boxes to n / 3 outputs; and a controller for control the multiplexer and the demultiplexer with a fourth clock and a fifth clock, wherein the fourth and the fifth clock are faster than the first, the second and the third clocks by n / 3 times.
Owner:ABOV SEMICON
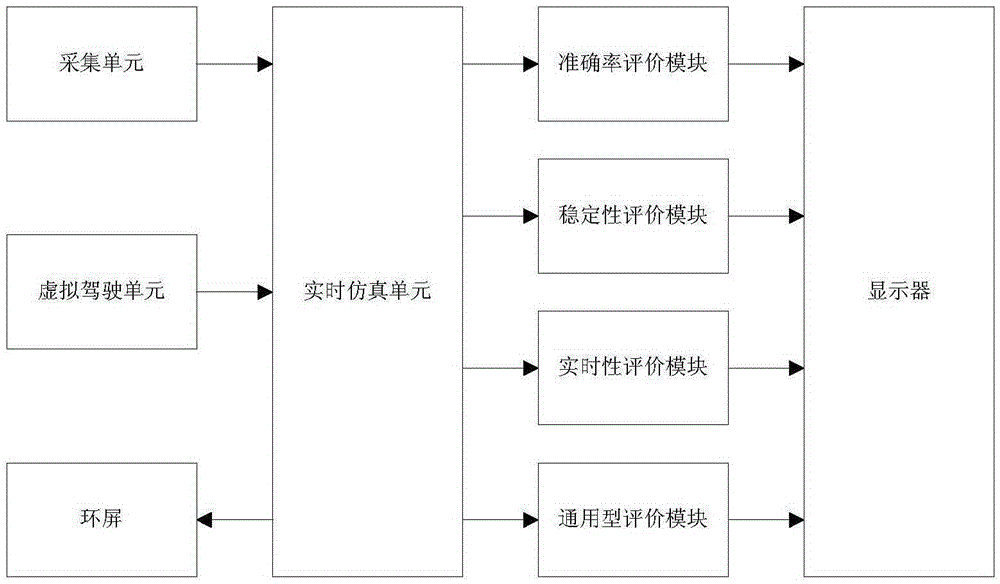
ADAS virtual development and test system
InactiveCN105388021ACredible assessmentTrusted developmentVehicle testingReal-time simulationUnexpected events
The invention provides an ADAS virtual development and test system, which comprises an acquisition unit used for acquiring a real traffic environment, a virtual driving unit used for simulating real driving behaviors, a real-time simulation unit used for simulating a real or virtual environment and vehicle driving attitude, and a display unit used for displaying information. The ADAS virtual development and test system regards a real traffic scene which is shot by a real vehicle in advance and projected to an annular screen as input of road information of a real-time simulation machine, can reflect the driving behaviors of a driver in the real environment, comprises various kinds of interference, noise and sudden incidents in the real environment, so that the assessment and development of an ADAS product are more credible, reliable and true; and through the assessment of comparing test results of the tested ADAS product with a standard algorithm stored in the real-time simulation machine, the ADAS virtual development and test system can obtain digital assessment results while testing is performed.
Owner:CHONGQING JIAOTONG UNIVERSITY
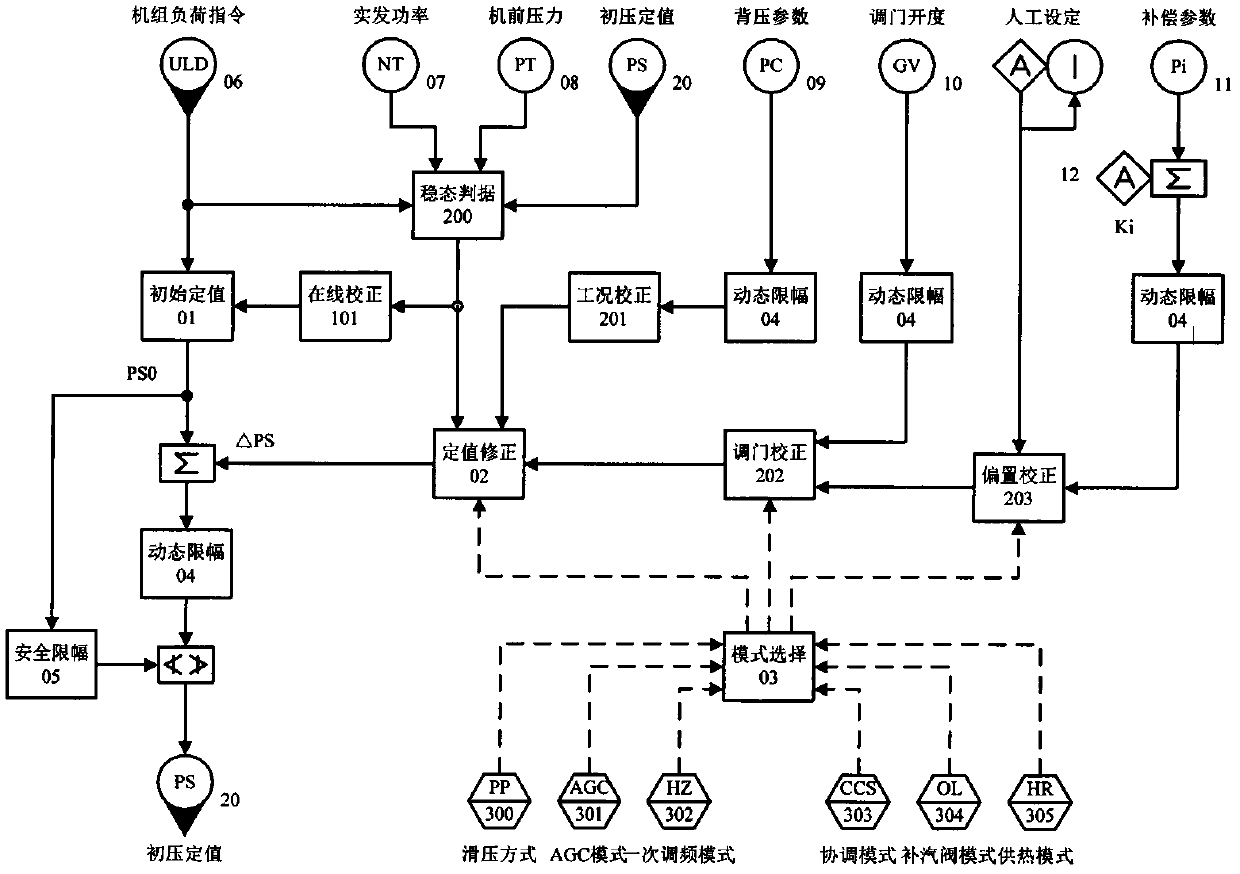
Multi-objective optimization method of initial pressure fixed value of uniform-admission turbine
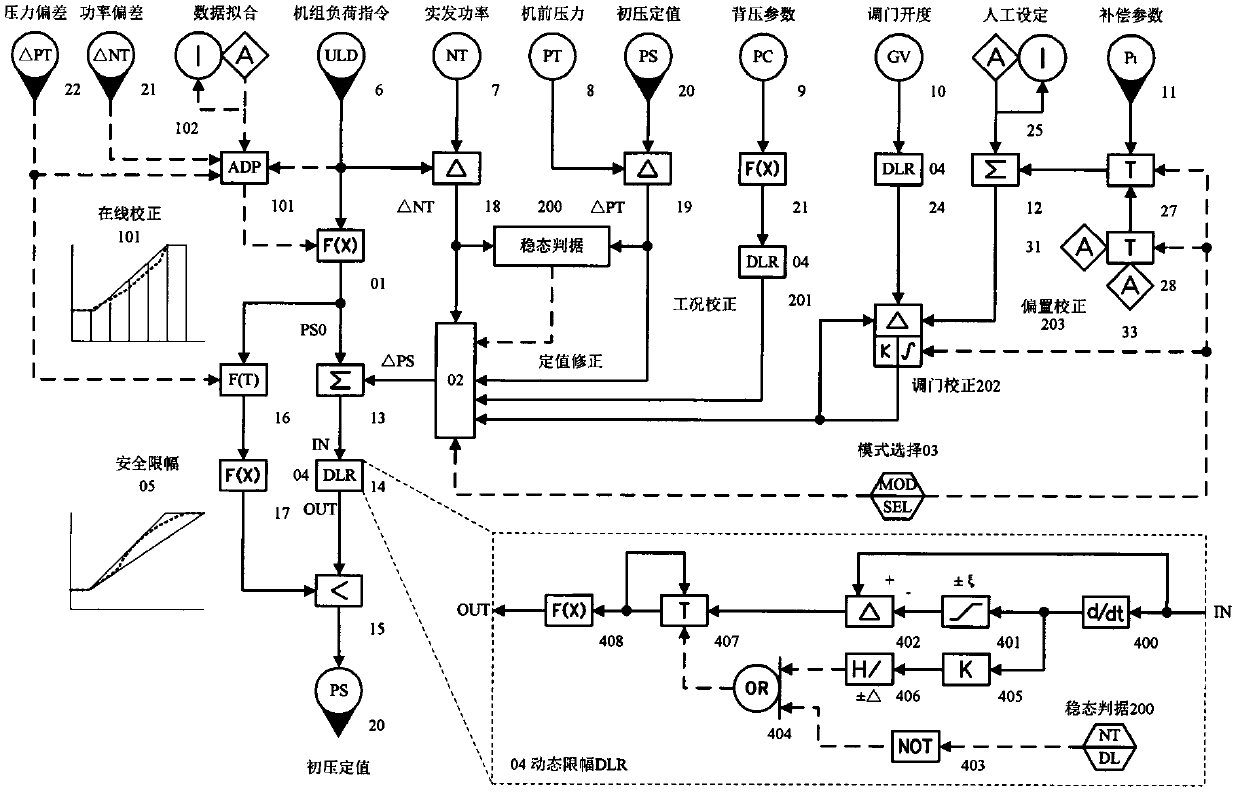
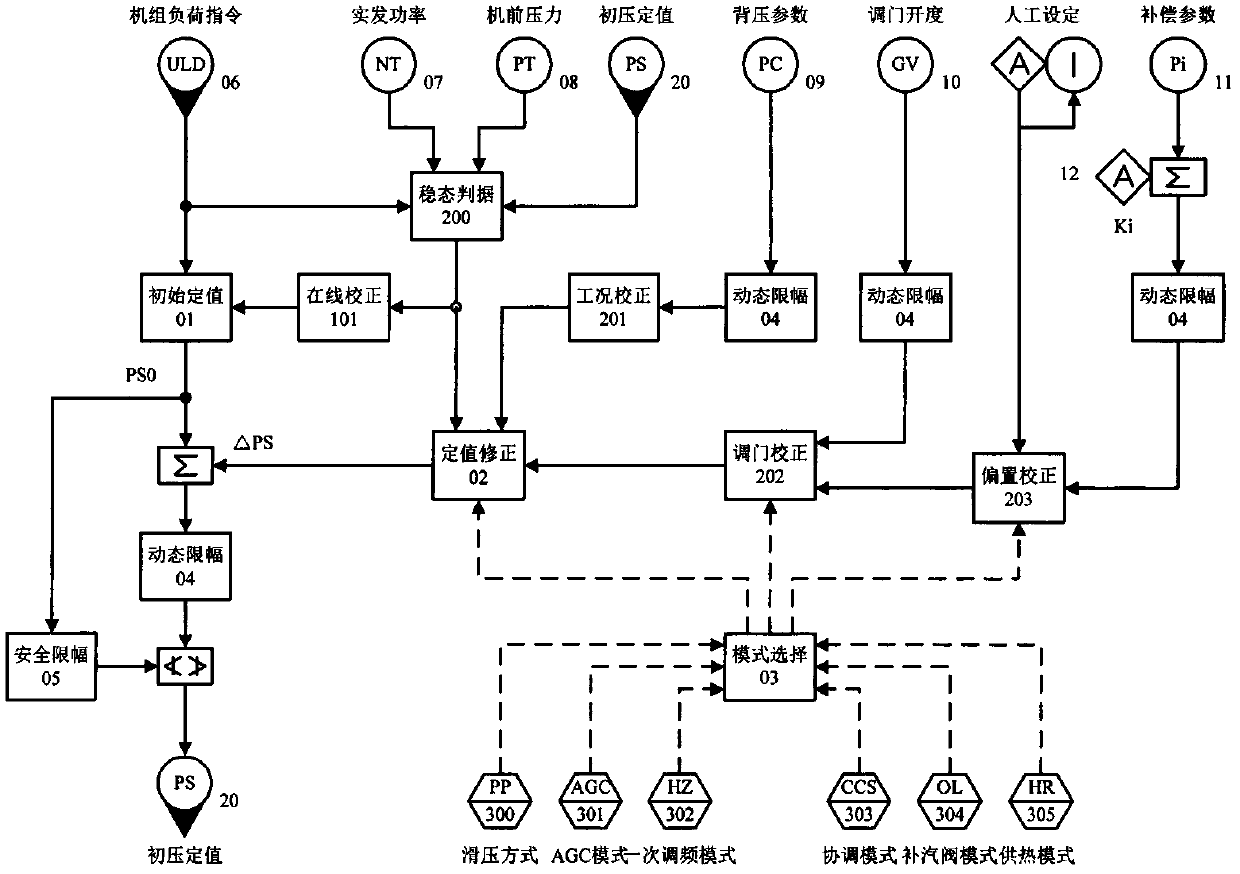
InactiveCN102606227AImprove adaptabilityImprove securityMachines/enginesEngine componentsCommunications systemComputer module
The invention discloses a multi-objective optimization method aiming at the initial pressure fixed value of a uniform-admission turbine and a DCS (Data Communication System) implementation method of the multi-objective optimization. The method synchronous considers the corrections of the working state of the turbine and the change of the running mode of a unit assembly to the initial pressure fixed value; the method is specifically composed of five control logical modules implemented by the DCS standard algorithm configuration; the five control logical modules consist of an initial value fixing module, a fixed value correcting module, a mode selecting module, a dynamic limiting module and a safety limiting module; wherein the fixed value correcting module is overlapped by a working state correcting part, an adjustment threshold correcting part and an offset correcting part respectively. At the same time, the adaptability and the safety of the optimization control strategy are improved by the asymmetric constraint of each unstable working state.
Owner:上海迪吉特控制系统有限公司
A self-adapted code rate control method based on relevancy
InactiveCN101188752ATelevision systemsDigital video signal modificationComputation complexityRound complexity
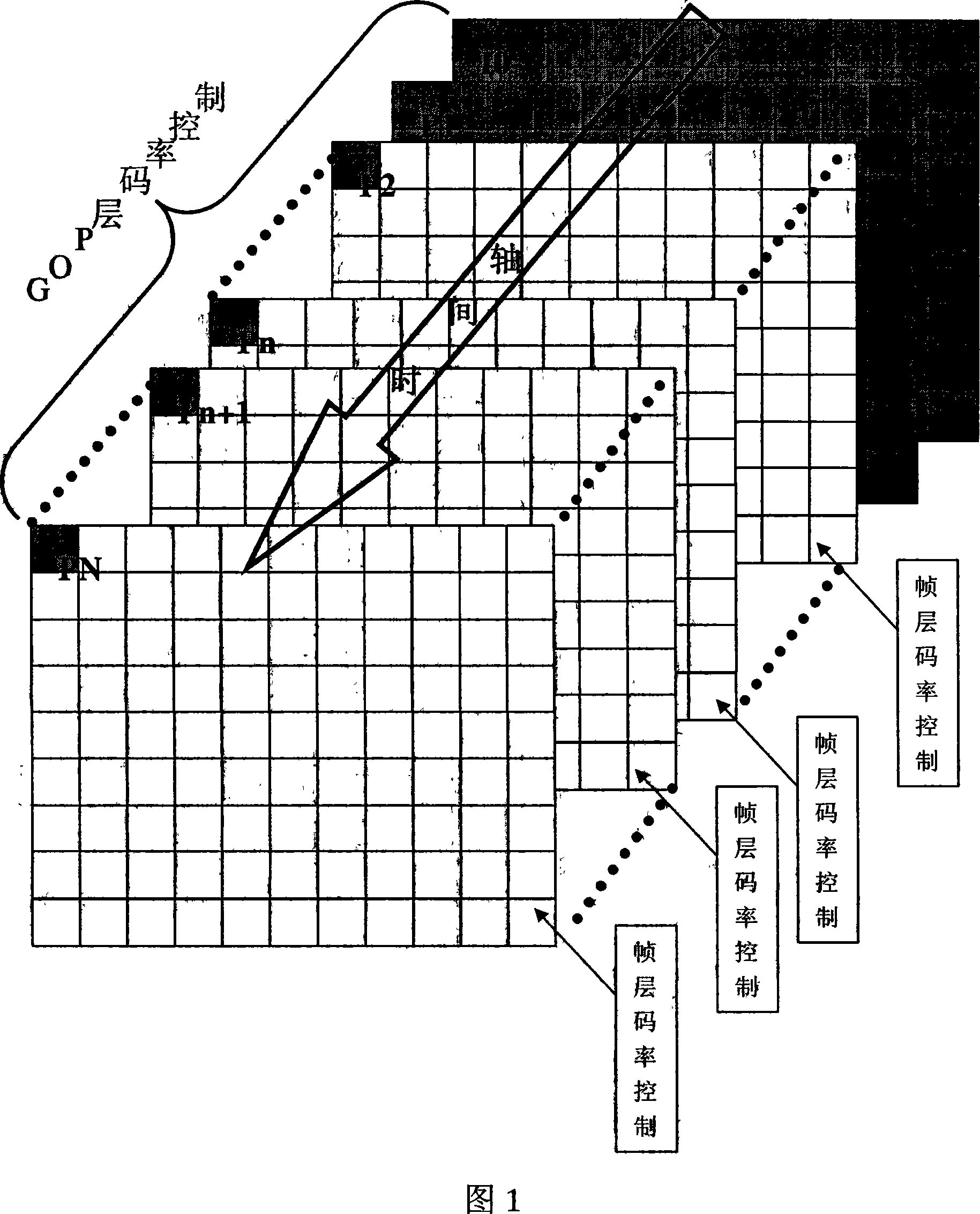
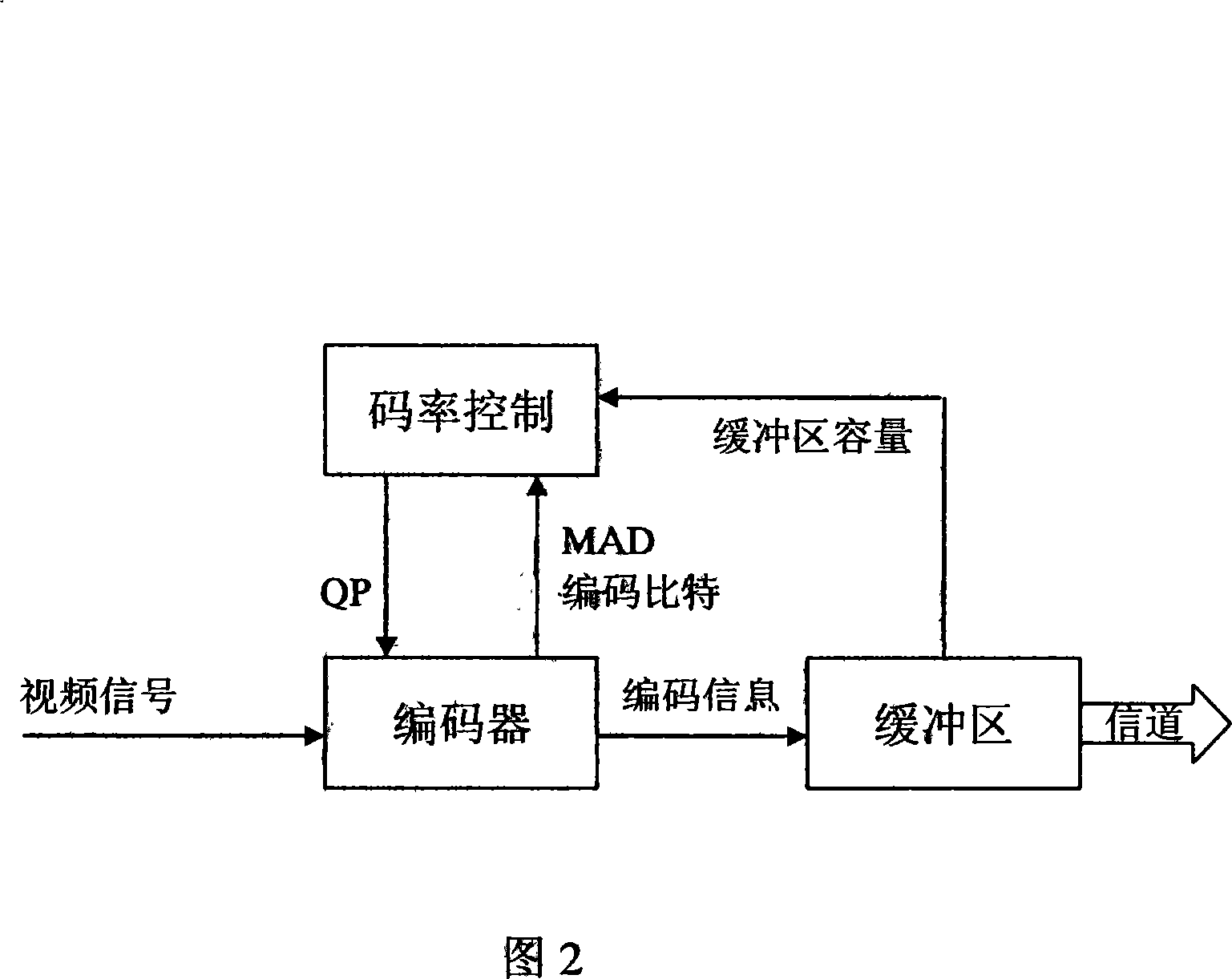
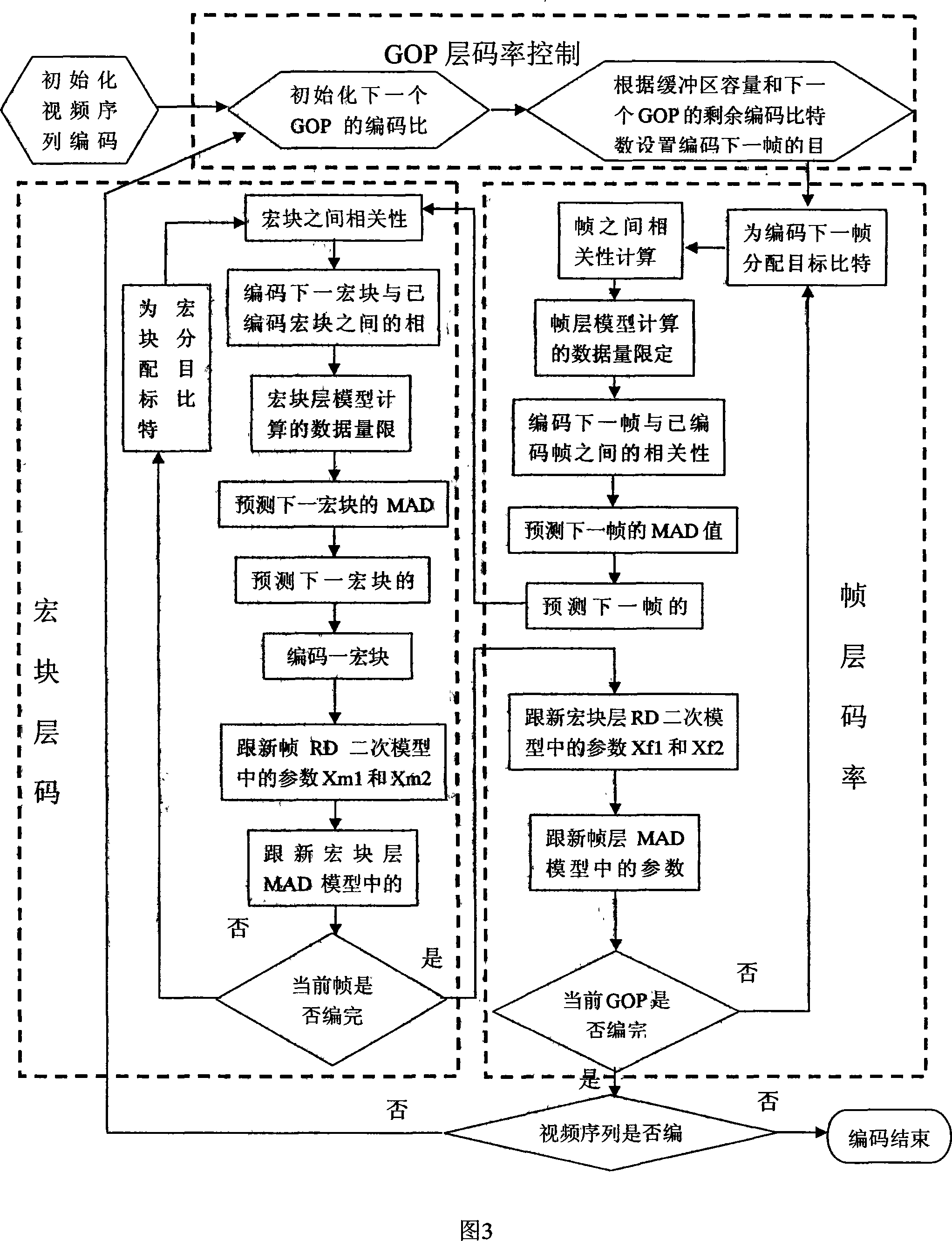
The invention relates to a relevant self-adaptive bit rate control method based on H.264 / AVC. A data quantity used for forecasting a model parameter is self-adaptively adjusted by utilizing the relevance between video frames or macro blocks in the method to ensure that the average data quantity of the model computation is decreased, thereby the computation complexity is decreased. The combination of the frame layer control and the macro block layer control is adopted in the bit rate control method, the variation range of the quantification grade of the macro block in the video frame is contracted, a new MAD model is established on the frame layer, and the weighting solution is operated by adopting the relevance during the process of the model solution and the RD solution; a new MAD forecasting model is established on the macro block layer. According to the correlated characteristic of a space time between the macro blocks, the solution proposal of the MAD model and the RD model is designed. The testing indicates that compared with the G012 standard algorithm, the invention has the advantages that the complexity of the algorithm is low, the bit rate control precision is improved, a buffering area is smoothed, and the PSNR value of the coding video is improved averagely by 0.4dB.
Owner:方春
Hierarchical cooperative combined spectrum sensing algorithm
InactiveCN102638802AReduce Spectrum Sensing OverheadNetwork planningFrequency spectrumData information
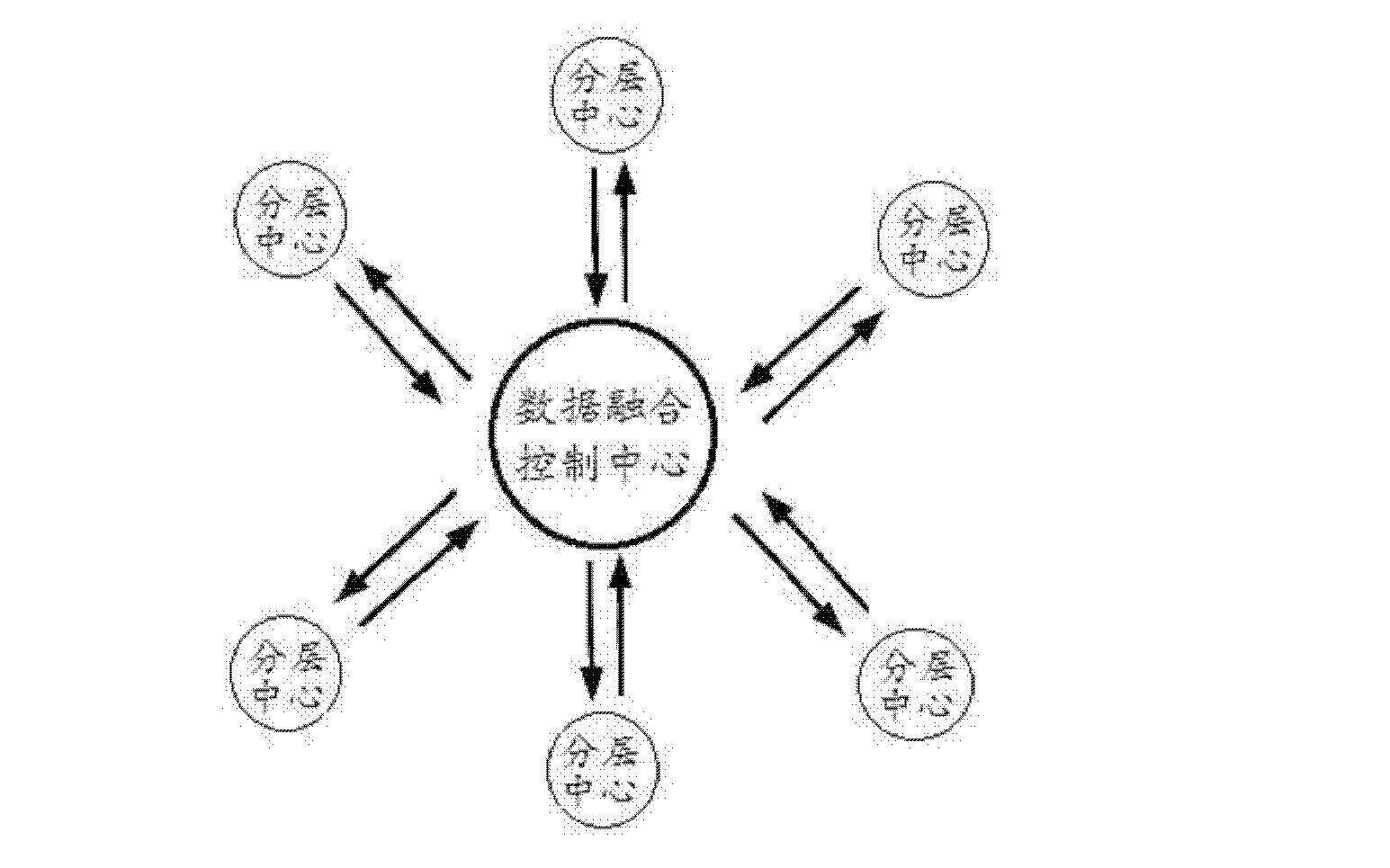
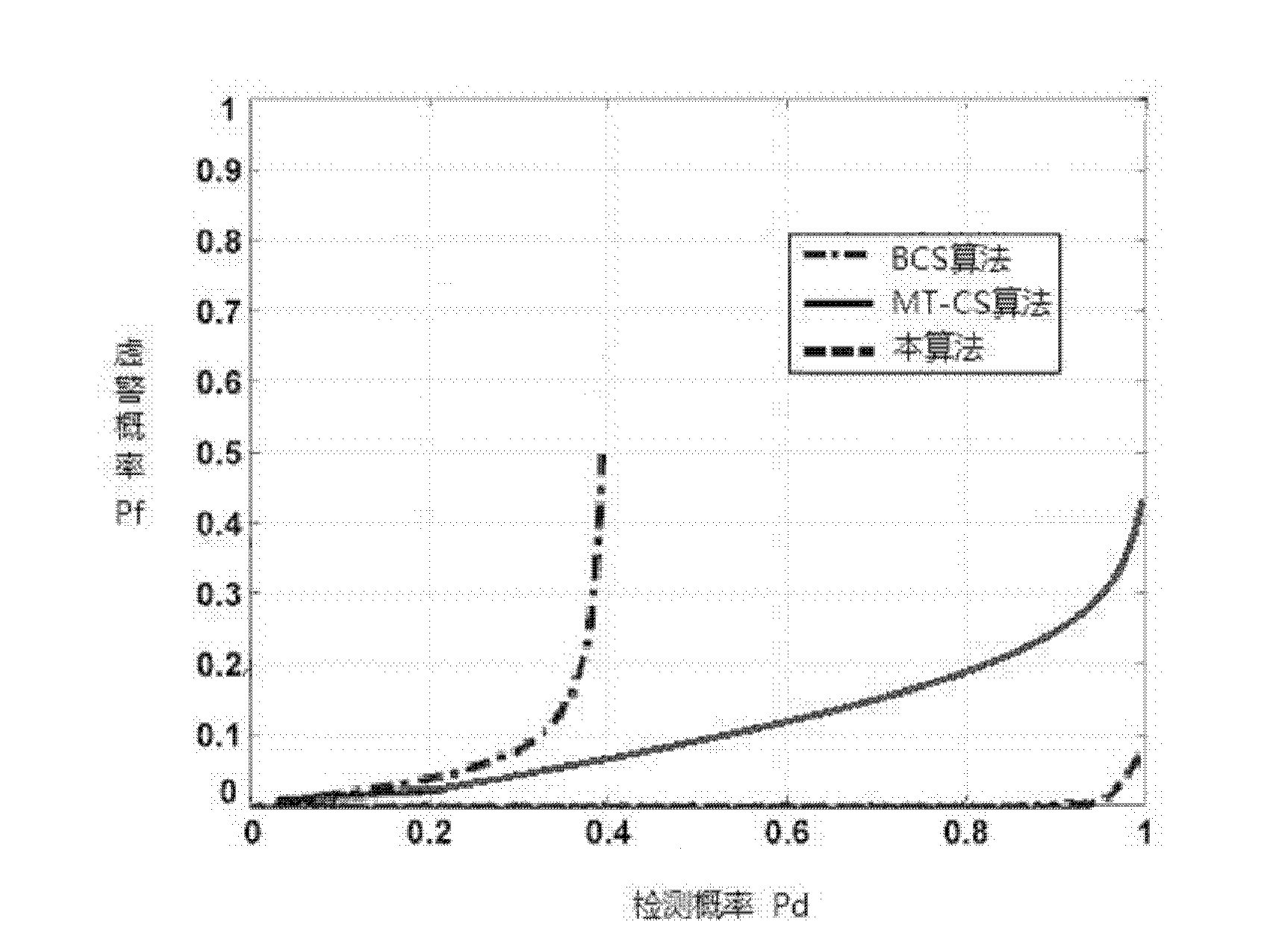
The invention relates to the field of cognitive radio communication and provides a multi-layer distributed combined spectrum sensing algorithm based on a Dirichlet process so as to realize dynamic spectrum sensing. The sensing data acquired by secondary users in a plurality of hierarchical centers is fused to search the optimized sensing information. The automatic data packet is realized by employing the Dirichlet process, a shared hyper-parameter and a corresponding divergent probability in each packet are estimated by a bayesian model, the hyper-parameter is acquired by employing a standard Viterbi algorithm, and the hyper-parameter is compared with a decision threshold value to acquire a final spectrum decision result so as to determine whether a channel is available. Due to the design, the space diversity information of the compressed sensing data is fully considered, and the uncertainty of an individual secondary user on the compressed sensing data is reduced, so that the normalized mean squared error performance is high, the compressed sensing data information in each hierarchical center can be effectively obtained through the algorithm, high accurate detection probability and low false alarm probability are acquired, and the spectrum sensing performance is improved.
Owner:HARBIN INST OF TECH
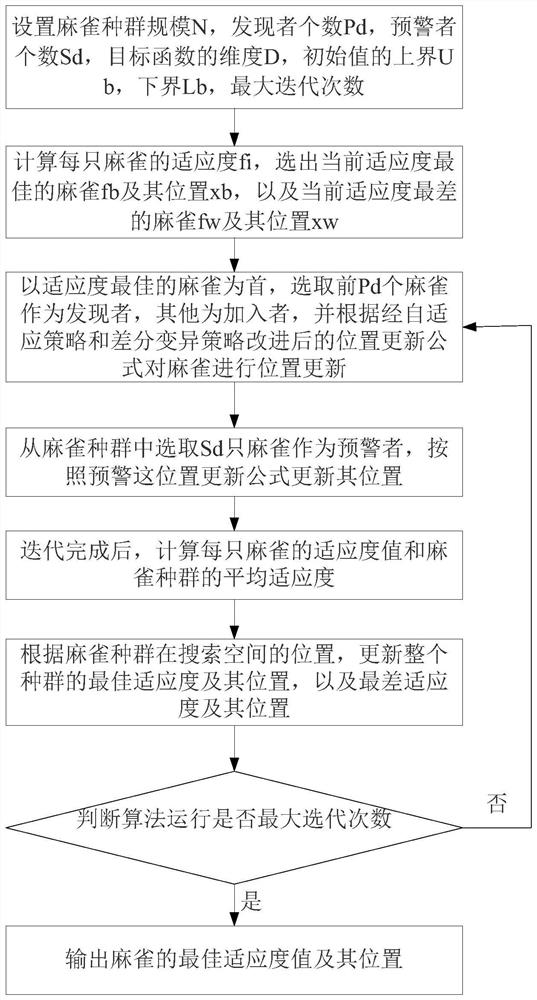
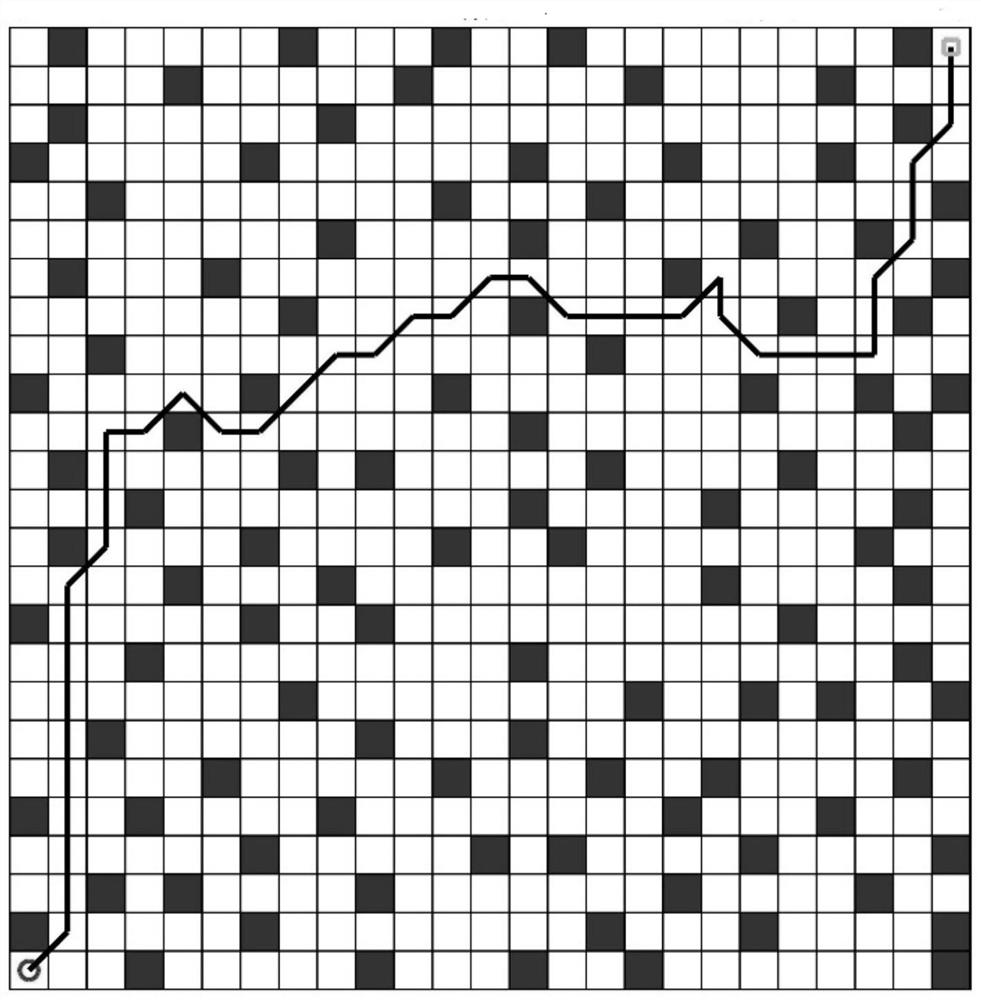
Robot path planning method based on self-adaptive sparrow search algorithm
ActiveCN112461247AIncrease population diversityFast convergenceNavigational calculation instrumentsPosition/course control in two dimensionsLocal optimumDifferential mutation
The invention discloses a robot path planning method based on an adaptive sparrow search algorithm. The method comprises the following steps: S1, introducing an adaptive weight and a differential variation strategy to propose the adaptive sparrow search algorithm; and S2, planning the path of the robot by adopting an adaptive sparrow algorithm. According to the method, the capacity of the standardSSA algorithm for large-scale optimization and local precise optimization in the early stage is improved through the self-adaptive strategy, the population diversity of the SSA algorithm is improvedthrough the differential mutation strategy, the problem that the SSA algorithm is prone to falling into local optimum in the later stage of search is solved, and therefore the search performance and development performance of the algorithm are improved; and meanwhile, the algorithm has relatively high convergence rate and relatively strong optimization capability.
Owner:GUANGZHOU UNIVERSITY
Method and apparatus for image compression
ActiveUS20190222845A1Limited setFast block coding algorithmDigital video signal modificationPattern recognitionBlock code
The invention relates to a method and apparatus for image compression, particularly to an improved block-coding apparatus and method for image compression. Image compression systems such as JPEG and JPEG2000 are known and popular standards for image compression. Many of the advantageous features of JPEG2000 derive from the use of the EBCOT algorithm (Embedded Block-Coding with Optimized Truncation). One drawback of the JPEG2000 standards is computational complexity. This application discloses a relatively fast block-coding algorithm, particularly as compared with the standard JPEG2000 EBCOT algorithm. Computational complexity is reduced.
Owner:KAKADU R & D PTY LTD
Reactive power grid capacity configuration method for random inertia factor particle swarm optimization algorithm
ActiveCN104037776ARealize online static voltage support capability evaluationImprove local search capabilitiesForecastingSystems intergating technologiesCapacity provisioningPower grid
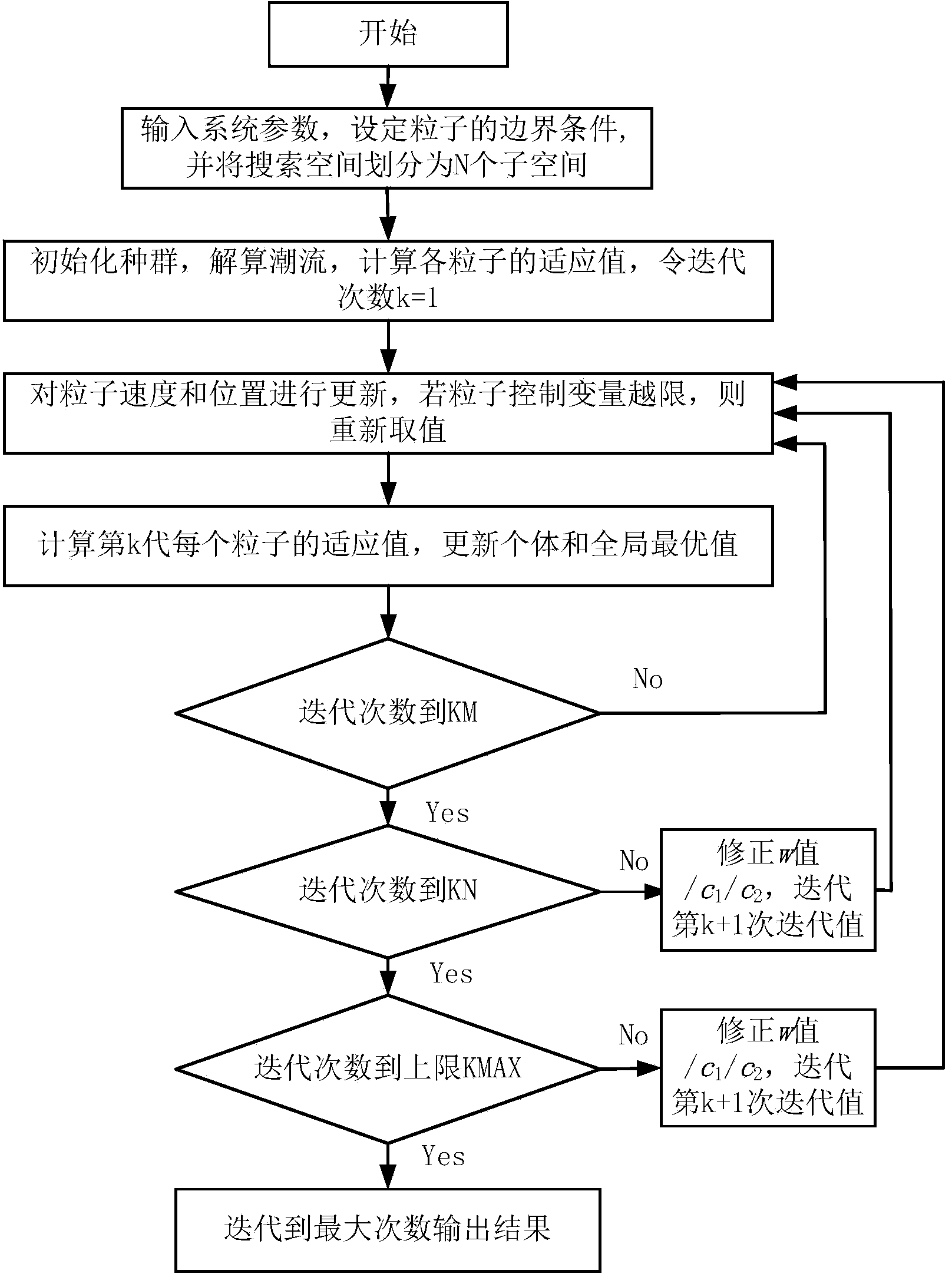
The invention discloses a reactive power grid capacity configuration method for a random inertia factor particle swarm optimization algorithm. The reactive power grid capacity configuration method includes steps that I, acquiring system parameters of a WAMS system in real time and setting particle boundary conditions; II, initializing a swarm and determining an adaptive value of the particle; III, dividing iterative stages; IV, updating the speed and position of the particle; V, judging whether the iteration times arrives at the maximum iteration times of a global search stage; VI, judging whether the iteration times arrives at the maximum iteration times of a primary solution stabilization stage; VII, judging whether the iteration times arrives at the upper iteration limit; VIII, iterating till arriving at the maximum times, and outputting an online reactive capacity configuration method. Compared with a standard algorithm and an adaptive mutation algorithm, the reactive power grid capacity configuration method for the random inertia factor particle swarm optimization algorithm enables the optimization precision to be improved and realizes to improve the early global search capability and the late local search precision based on guaranteeing a convergence rate through combining with actual situations of reactive optimization, and the global optimal solution is ultimately obtained.
Owner:STATE GRID CORP OF CHINA +2
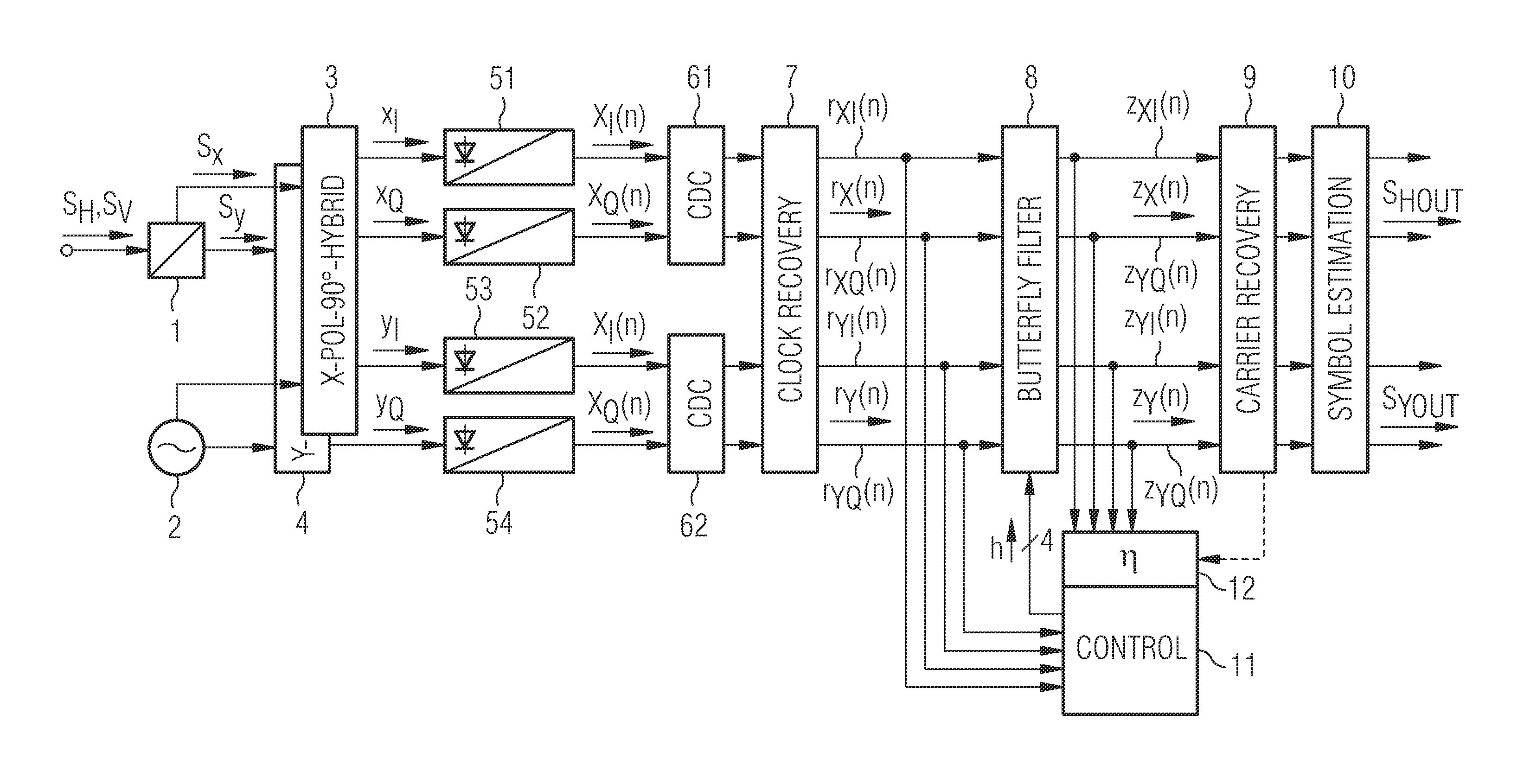
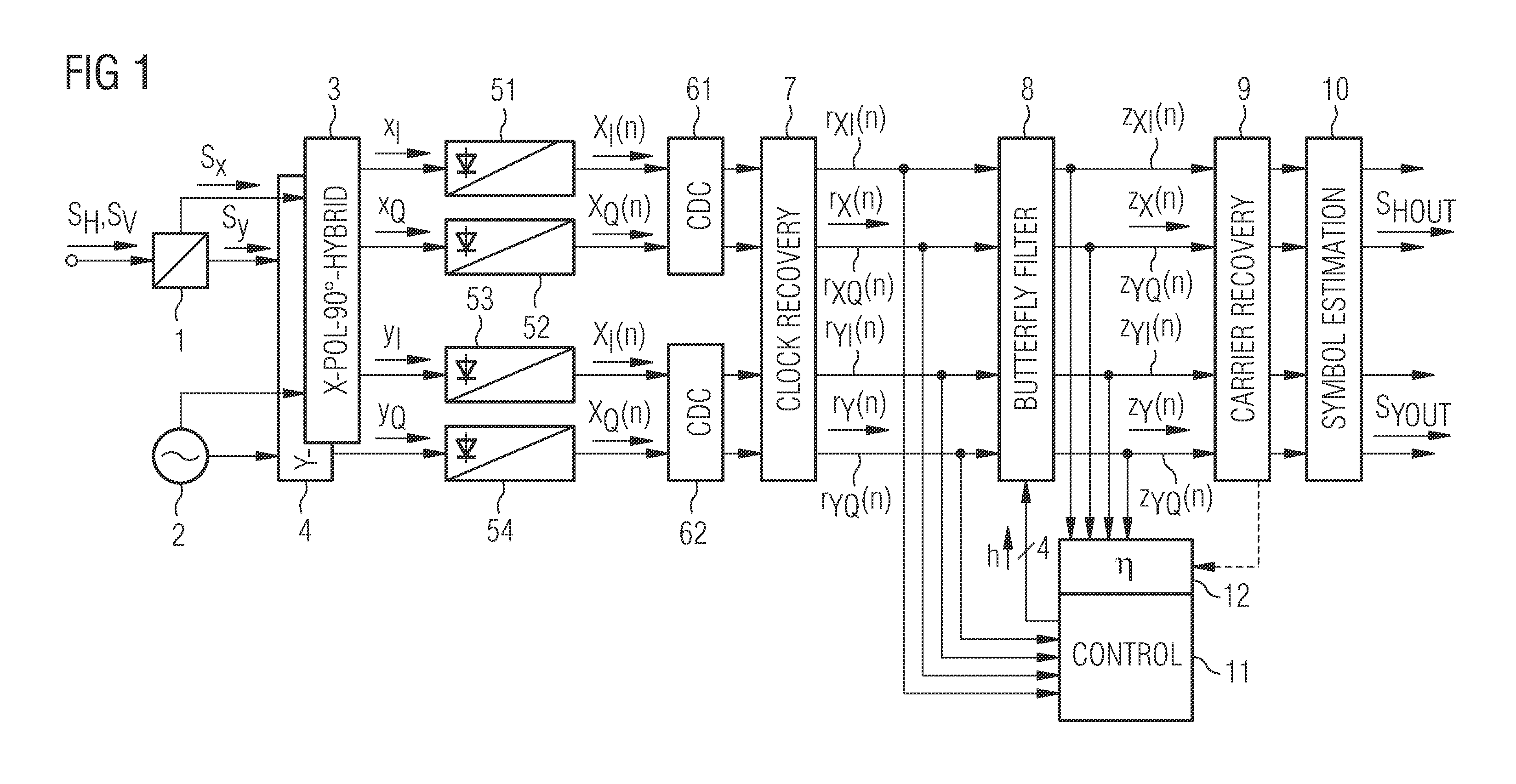
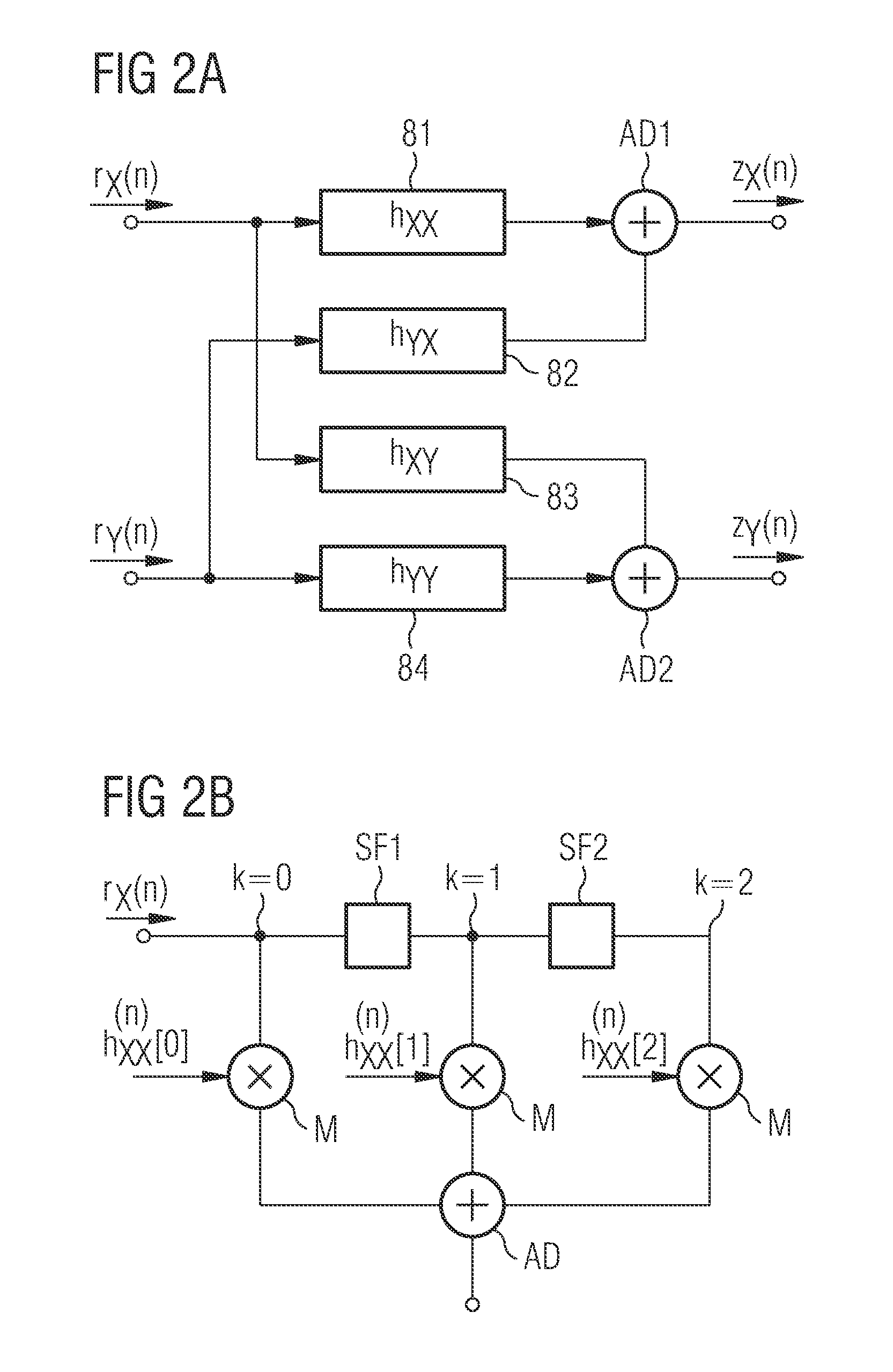
Method and arrangement for blind demultiplexing a polarisation diversity multiplex signal
ActiveUS20120084619A1Polarisation multiplex systemsModulated-carrier systemsPolarization diversityStandard algorithms
A received optical signal (SH, Sv) is coherently demodulated and converted into orthogonal x-polarisation samples (rx(n)), and y-polarisation samples (ry(n)). These samples are converted into signal x-samples zx(n) and signal y-samples zy(n) by an FIR butterfly filter (8). Correction values are calculated in an error calculating circuit (12) of a control unit (11) and added to filter transfer functions derived by a standard algorithm to determine corrected filter coefficients. Degenerate convergences calculating the transfer functions are avoided.
Owner:XIEON NETWORKS SARL
Robot path planning method in complex narrow environment
ActiveCN110083165ASolve the problem of local path dynamic replanningEfficientPosition/course control in two dimensionsSimulationReinforcement learning algorithm
The invention discloses a robot path planning method in a complex narrow environment. An RRT-Connect algorithm is combined with a reinforcement learning algorithm, and certain randomness of a random tree is reserved. According to a degree of obstacle density, an appropriate step size is selected so that a robot can realize rapid and random exploration in an obstacle-dense environment, can quicklypass through in a sparse obstacle environment; orientation of random tree distribution is increased, and a convergence speed is improved; and planning performance can be increased in the process of interaction with the environment so that a planned path is close to an optimal path and a local minimum can be avoided. An improved algorithm is compared with an original standard algorithm, the plannedpath is better and consumed time is less.
Owner:DALIAN UNIV
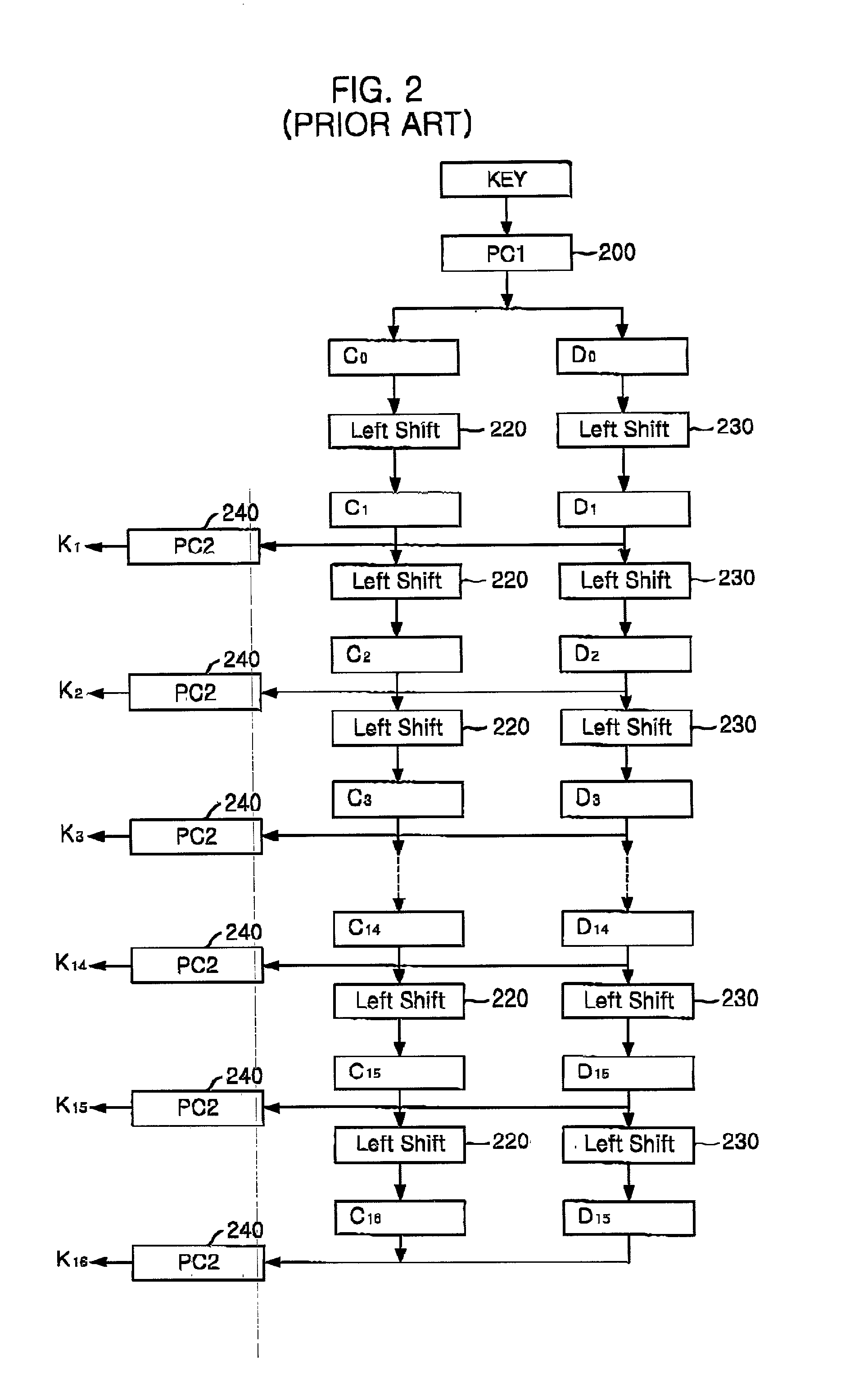
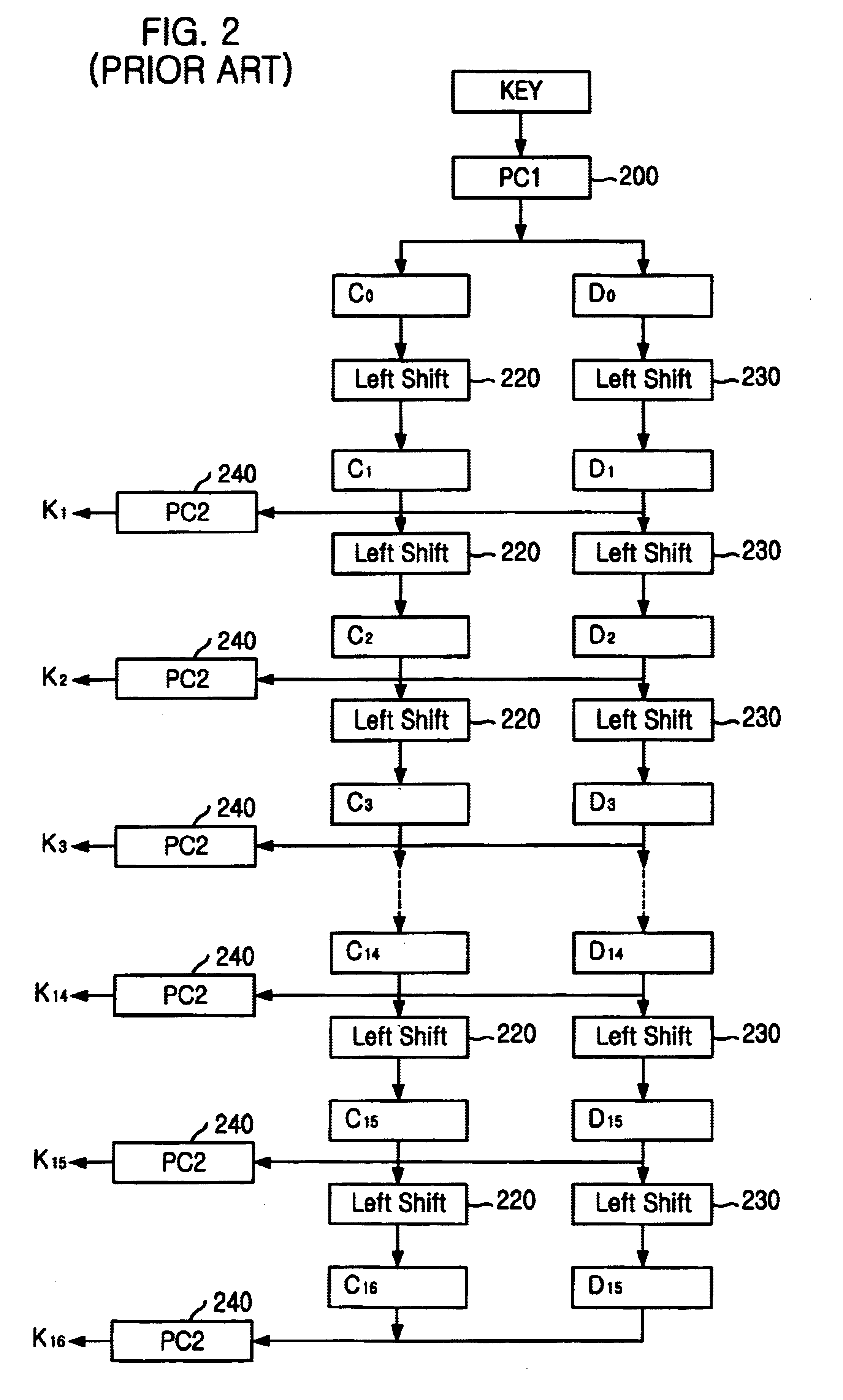
Key scheduler for encryption apparatus using data encryption standard algorithm
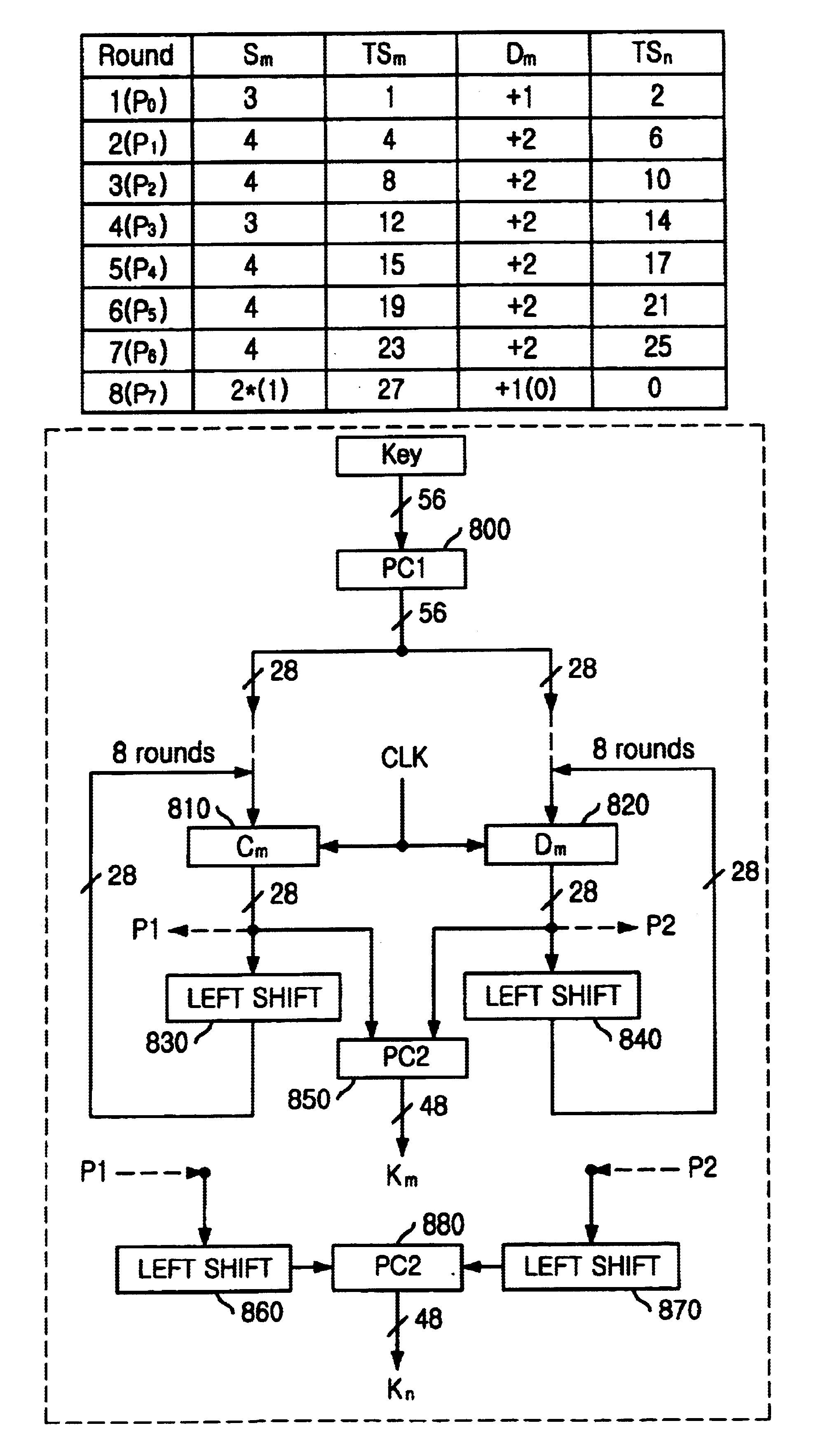
ActiveUS7123720B2Small sizeEncryption apparatus with shift registers/memoriesSecret communicationProcessor registerStandard algorithms
A key scheduler for an encryption apparatus using a DES encryption algorithm is disclosed. The key scheduler includes: a first permutation choice unit for permuting a 56-bit block; a first register for storing left 28 bits among the 56-bit block from the first permutation choice unit in accordance with a clock signal; a second register for storing right 28 bits among the 56-bit block from the first permutation choices unit in accordance with the clock signal; a first and a second shift units for shifting the 28-bit blocks stored in the first and the second registers to the left by a first predetermined number of bits and outputting shifted 28-bit blocks to the first and the second registers respectively; a second permutation choice unit for permuting the 28 bits stored in the first and the second registers, thereby generating a first subkey; a third and a fourth shift units, each for shifting the 28 bits stored in the first and the second registers to left by a second predetermined number of bits; and a third permutation choice unit for permuting the 28 hits stored in the third and the fourth shifters, thereby generating a second subkey.
Owner:ABOV SEMICON
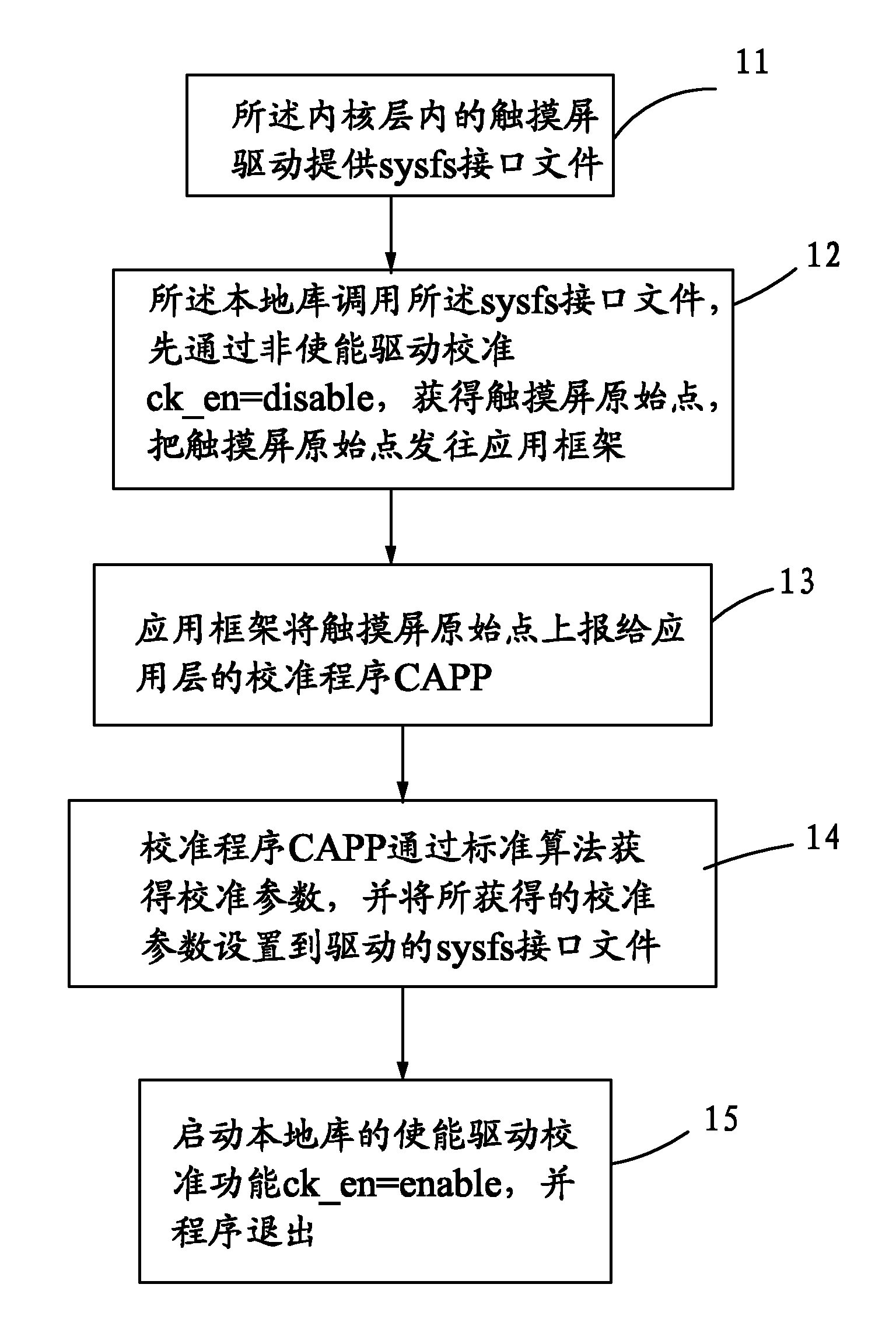
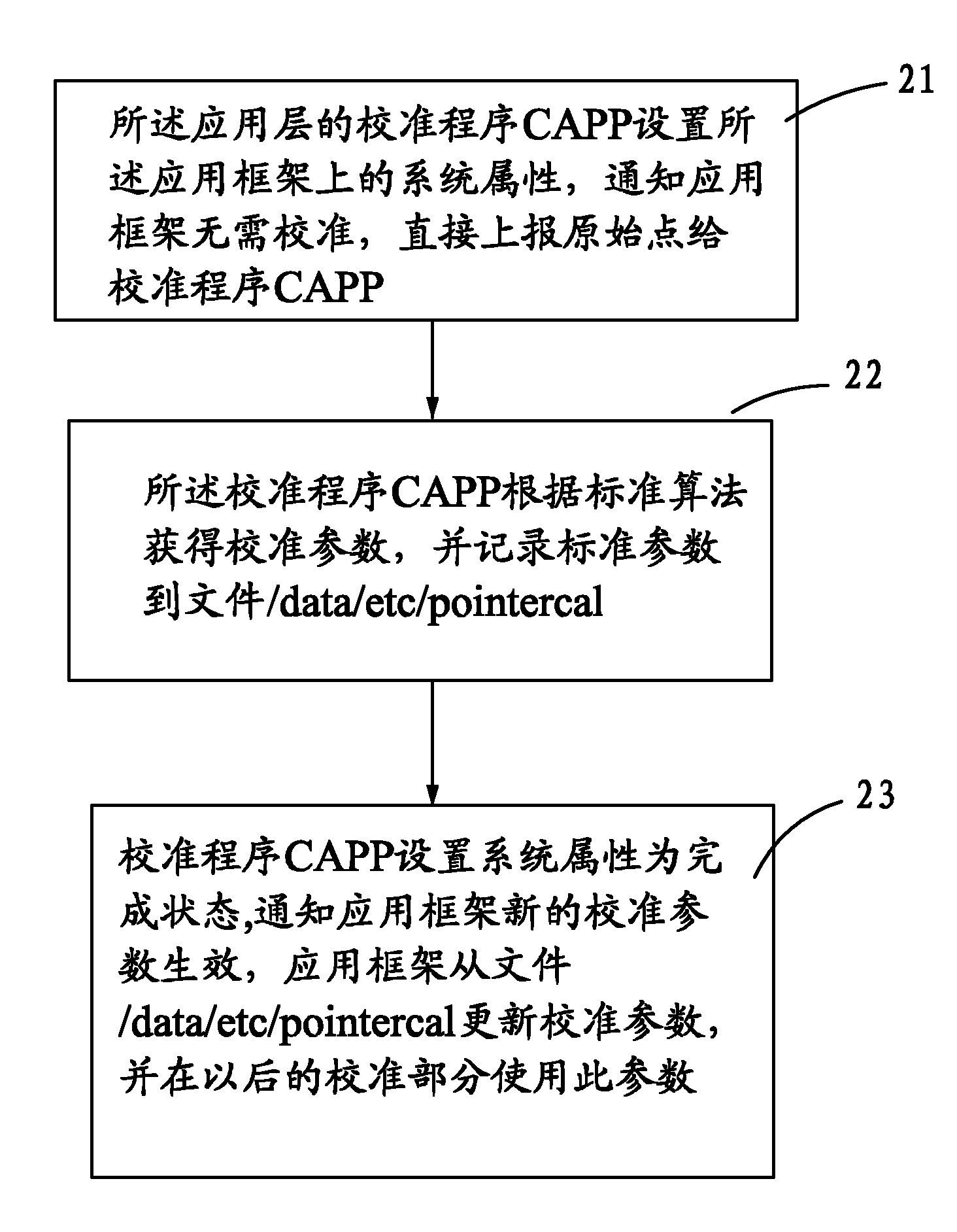
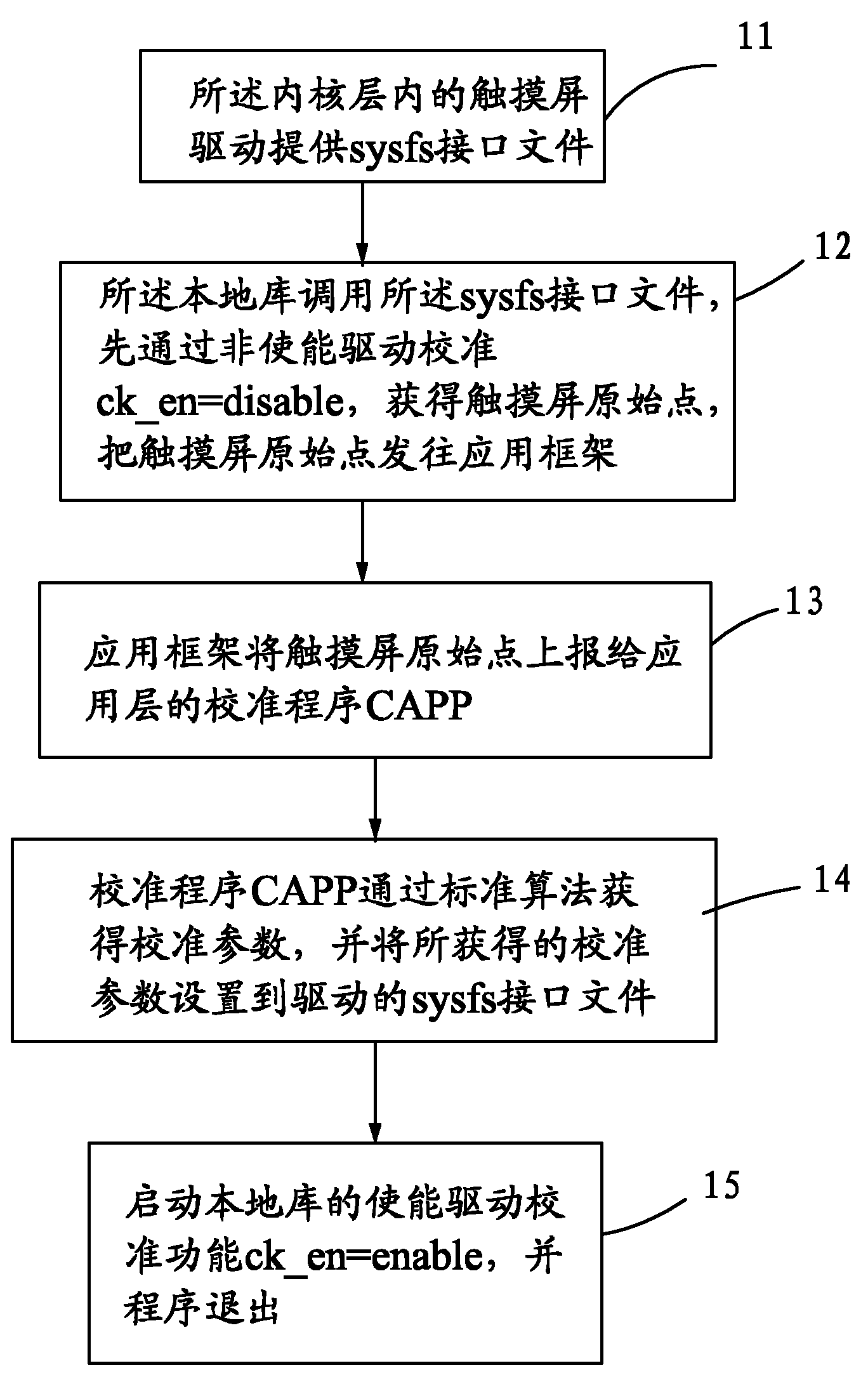
Method for calibrating touch screen in Android platform
InactiveCN101980118ACalibration parameter adjustmentProgram loading/initiatingInput/output processes for data processingTouchscreenProtocol Application
The invention provides a method for calibrating a touch screen in an Android platform. An Android framework comprises a kernel layer, a local repository, an application framework and an application layer. The method comprises the following steps that: 11, the touch screen is driven to provide a sysfs interface file; 12, the local repository acquires an original point by disable drive calibration and sends the original point to the application framework; 13, the application framework reports the original point to computer-aided process planning (CAPP); 14, the CAPP acquires calibration parameters by a standard algorithm and then set the calibration parameters to the sysfs interface file; 15, enable drive calibration is started and then a program quits; the second method comprises the following steps that: 21, the CAPP sets a system attribute and informs the application framework of reporting the original point; 22, the CAPP acquires the calibration parameters by the standard algorithm; and 23, the CAPP sets the system attribute, and informs the application framework of making the novel calibration parameters take effect, and the application framework updates the calibration parameters. By the method, the calibration parameters of the touch screen can be dynamically regulated according to user experience of different users.
Owner:FUJIAN XINO COMM TECH
System and method for managing and monitoring multiple workflows
A criteria-based system and method is provided for performing workload management. Unlike conventional systems, the invention provides a system and method that includes a core workload management entity for performing workload management for multiple process lines. Each process line is defined based on the criteria for a workload, such as a product line or service based task. The method may include providing initial information related to components supply, then developing workflow processes and workflow exit criteria algorithms for individual workflow steps. The exit criteria may produce a common thread among multiple product lines, allowing the process to extend to create a diverse master workflow system to manage and monitor the workflow of an organization. The system and method are adaptable to product supply chain workflow management, project management, service provision management, and any other scenario where some level of concurrent management of multiple workflows is desired.
Owner:AGILE SOFTWARE CORPORATION
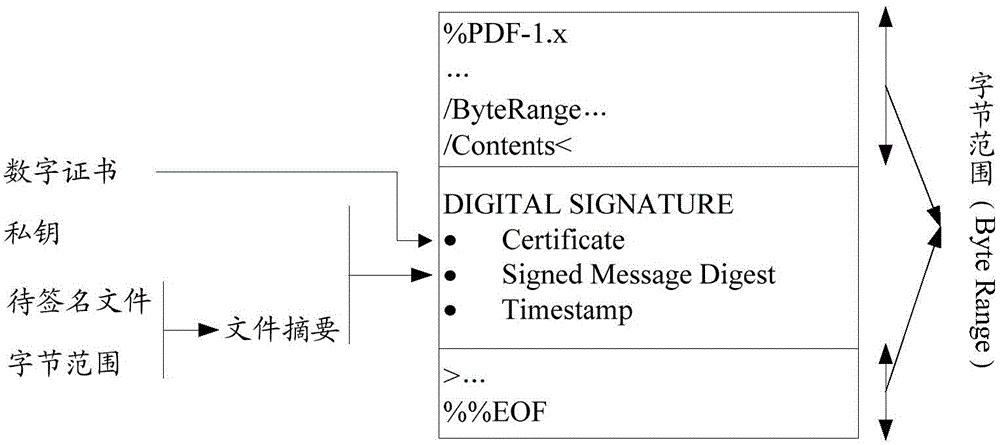
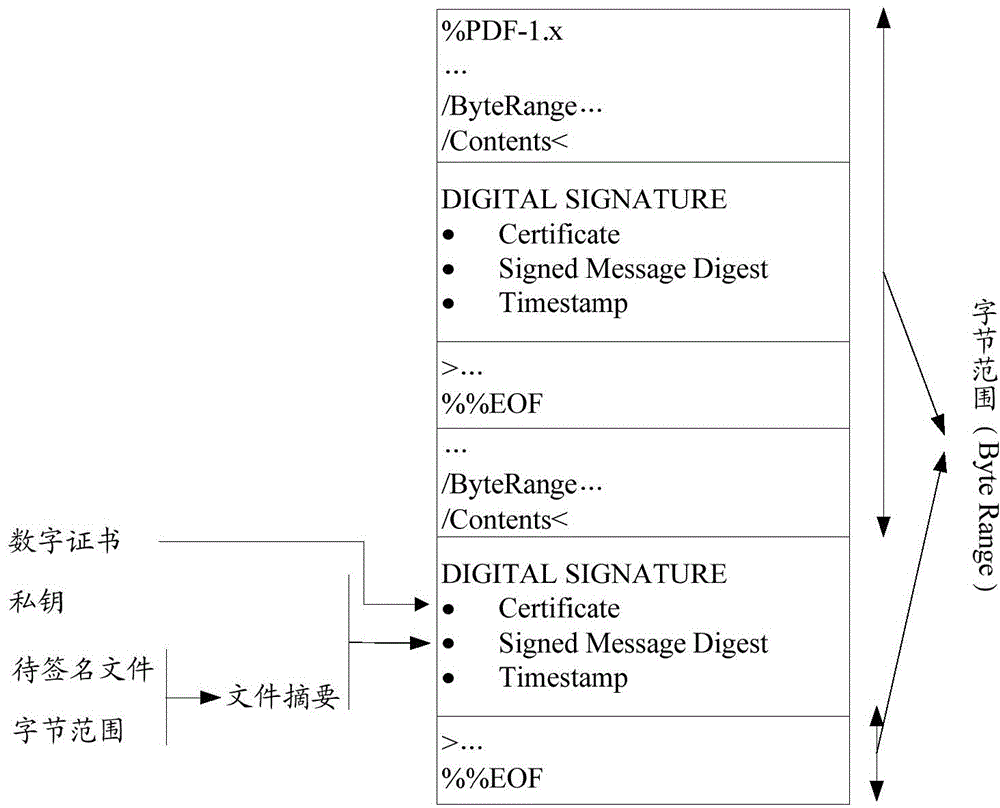
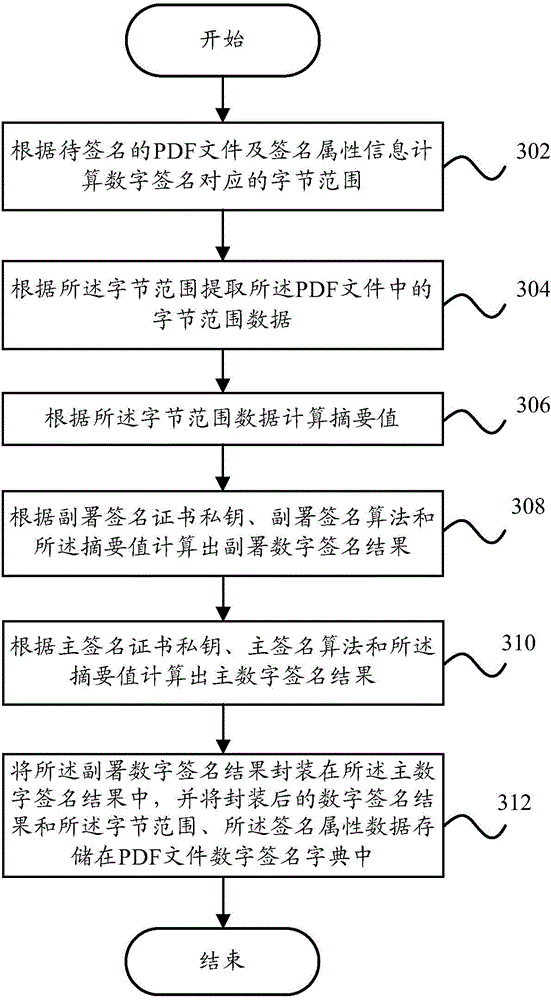
PDF digital signature method and system and PDF digital signature verification method and system
ActiveCN105320900AReduce complexityImprove performanceUser identity/authority verificationDigital data protectionDigital signaturePortable document format
The invention provides a PDF digital signature method. The PDF digital signature method includes the steps that byte range data corresponding to a digital signature are calculated according to a PDF file to be signed and attribute information of the digital signature; an abstract value is calculated according to the byte range data, and a countersignature digital signature result is calculated according to the abstract value; a main digital signature result is calculated according to the abstract value; the countersignature digital signature result is packaged in the main digital signature result, and the digital signature result obtained after packaging is stored in a PDF file digital signature dictionary. Correspondingly, the invention further provides a PDF digital signature system and a PDF digital signature verification method and system. By means of the PDF digital signature method and system and the PDF digital signature verification method and system in the technical scheme, the same version of the PDF file can be subjected to digital signing for multiple times, and the shared signature of the content of the same file is achieved; as the countersignature signature result of a user-defined algorithm is packaged into the main signature result of a standard algorithm, the compatibility between the PDF file signed with the user-defined algorithm and a universal PDF reader is achieved.
Owner:方正国际软件(北京)有限公司 +1
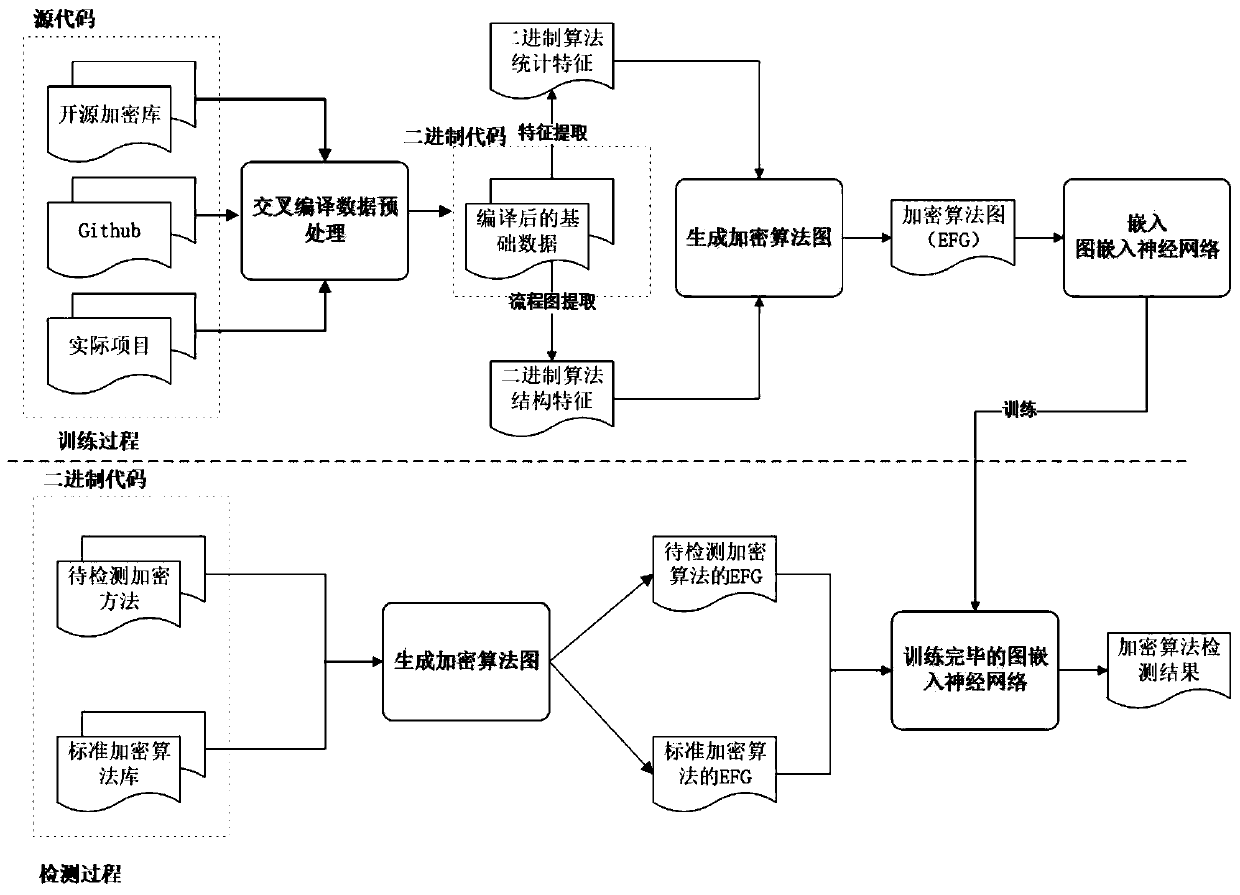
Encryption algorithm identification method based on deep learning graph network
ActiveCN111460472AReduce research difficultyConvenient researchCharacter and pattern recognitionDigital data protectionPattern recognitionSource code
An encryption algorithm identification method based on a deep learning graph network is composed of a training process and an inspection process, and comprises the following steps: training: constructing a basic source code library for crawled source code data related to encryption; carrying out cross-compiled preprocessing, obtaining a binary code library, respectively extracting statistical characteristics and structural characteristics of a binary encryption algorithm, integrating the statistical characteristics and the structural characteristics to generate an encryption algorithm graph, embedding the encryption algorithm graph into a neural network to become vectors, judging whether codes are similar or not by comparing distances among the vectors, and obtaining a model for judging whether embedded vectors of the encryption algorithm graph are similar or not through training; checking: generating a standard encryption algorithm library, selecting one copy of encryption algorithm which is standardized and has been determined in type; generating an encryption algorithm graph, generating an encryption algorithm graph for the to-be-detected encryption algorithms of unknown types,embedding the encryption algorithm graph into the trained model, sequentially comparing the vector distances with the embedding of the standard encryption algorithm library, and taking the standard algorithm type with the shortest vector distance to the to-be-detected encryption algorithms as the type of the to-be-detected encryption algorithms.
Owner:NORTHWEST UNIV(CN)
Self-adaptation method for back-propagation (BP) nerve cell with multilayer structure
The invention relates to the field of nerve network hardware realization, in particular to a self-adaptation method for the computation of a single nerve cell node in a BP nerve network with a multilayer structure in different computation stages to realize different learning algorithm. A nerve cell processor is used for executing the computation of the single node on each layer of the BP nerve network. By programming a control register, a microcontroller can control an arithmetic device to execute the computation of three different kinds of BP nerve networks at the nerve cell node, wherein BP nerve network learning algorithm includes three kinds of typical learning algorithms, namely BP standard algorithm, additional momentum item algorithm and learning speed self-adaptation adjustment algorithm. A plurality of nerve cell processors can be connected in series to realize pipeline algorithm, so that the self-adaptation method has the characteristics of high flexibility and high practicability and is applicable in the application field of embedded hardware BP hardware nerve networks.
Owner:FUJIAN NORMAL UNIV
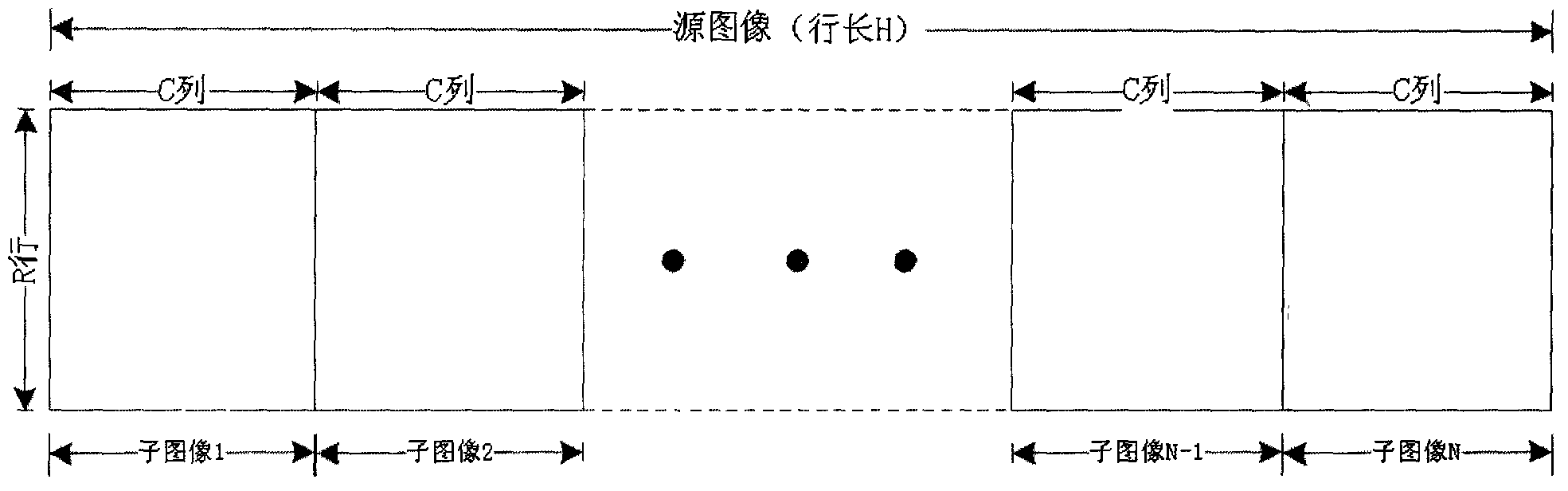
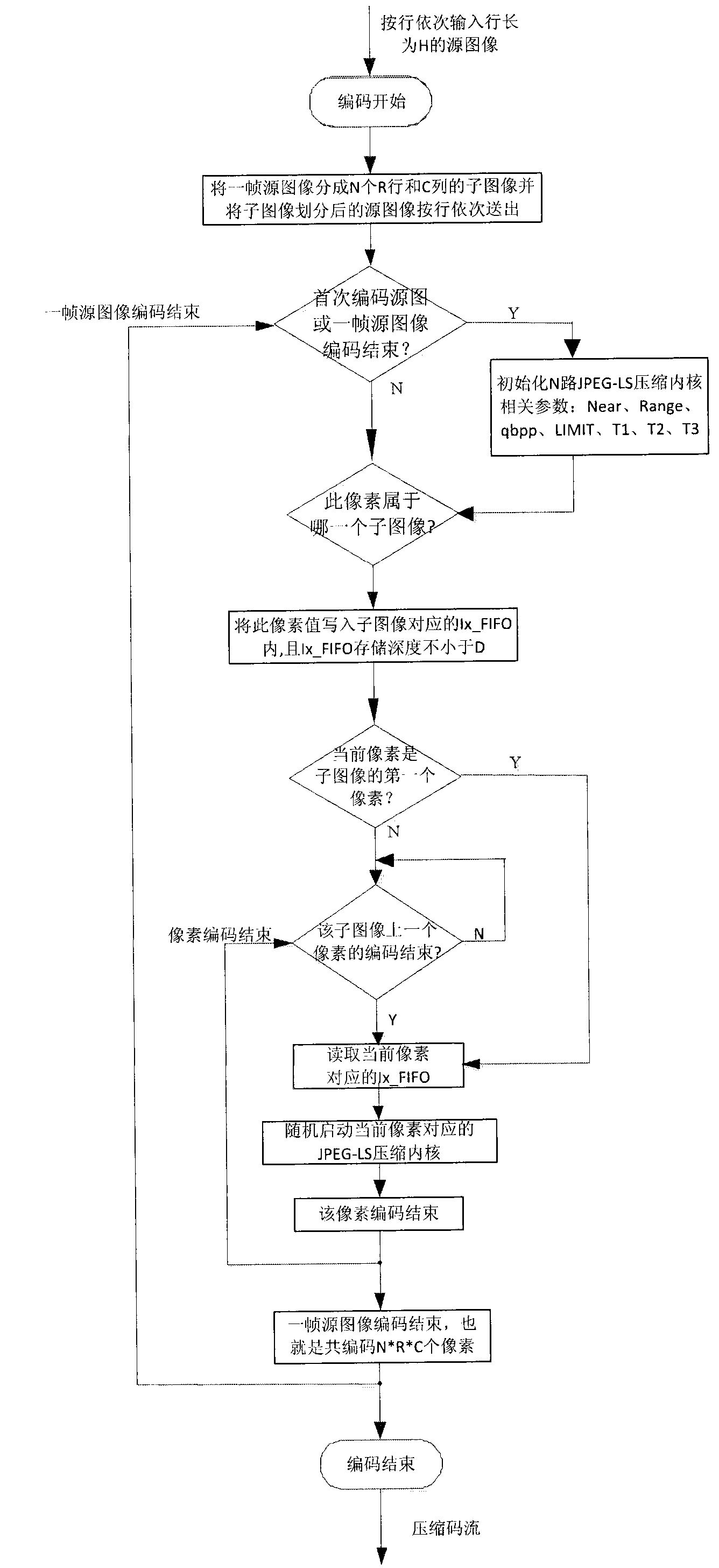
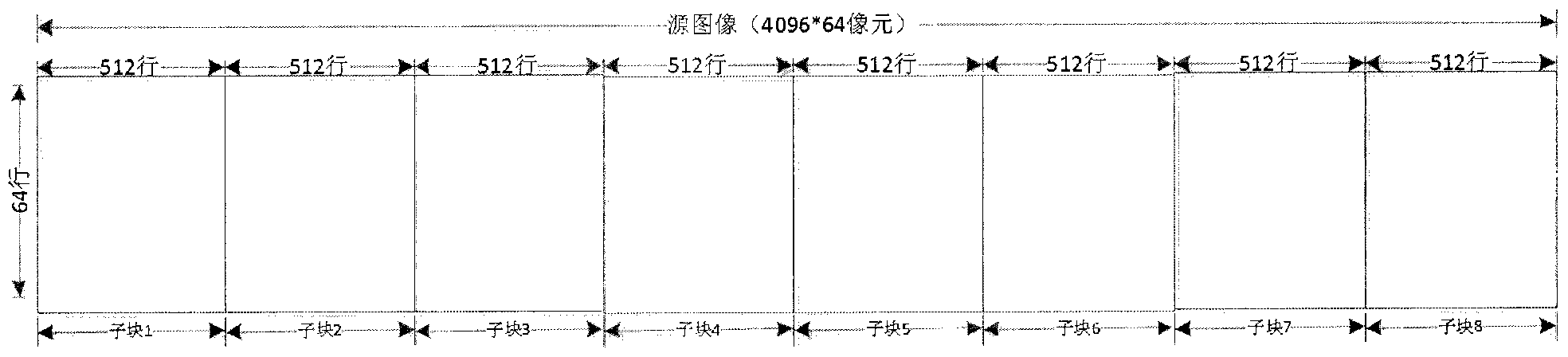
Multipath compressed kernel parallel encoding control method on basis of JPEG-LS (Joint Pho-tographic Experts Group-Lossless Standard) algorithm
ActiveCN102801981AImprove scalabilityQuick compressionTelevision systemsDigital video signal modificationParallel encodingJPEG
The invention relates to a multipath compressed kernel parallel encoding control method on the basis of a JPEG-LS (Joint Pho-tographic Experts Group-Lossless Standard) algorithm. According to the method, a compressed kernel implemented on the basis of the JPEG-LS standard algorithm is adopted to form an N-path compressed kernel parallel encoding control method to complete the image compression by the following steps: (1) dividing a source image into N sub-images which are arranged in R rows and in C lines; (2) completing initializing related parameters of N paths of JPEG-LS compressed kernels in time and preparing to encode; (3) by carrying out write control and read control on N Ix_FIFO (First In First Out), randomly starting the N paths of JPEG-LS compressed kernels so as to uninterruptedly encode the source image; and (4) encoding the source image by a parallel encoding system implemented by the control method. The processing effect of the method is nearly equivalent to the effect of utilizing one compressed kernel implemented on the basis of the JPEG-LS standard algorithm to complete encoding the source image, but the throughput rate and the processing rate of the method are nearly improved by N times.
Owner:XIAN INSTITUE OF SPACE RADIO TECH
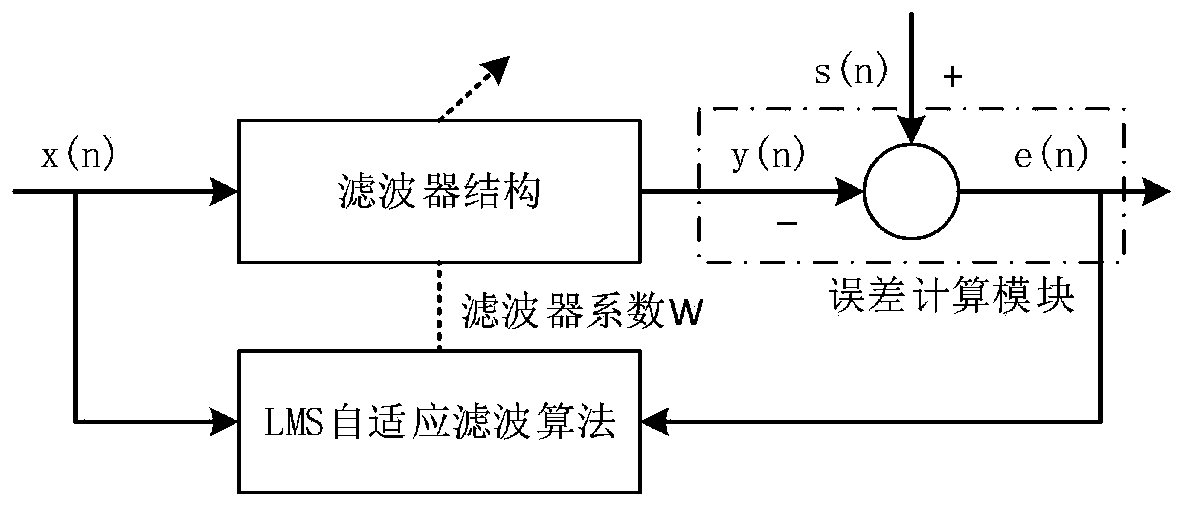
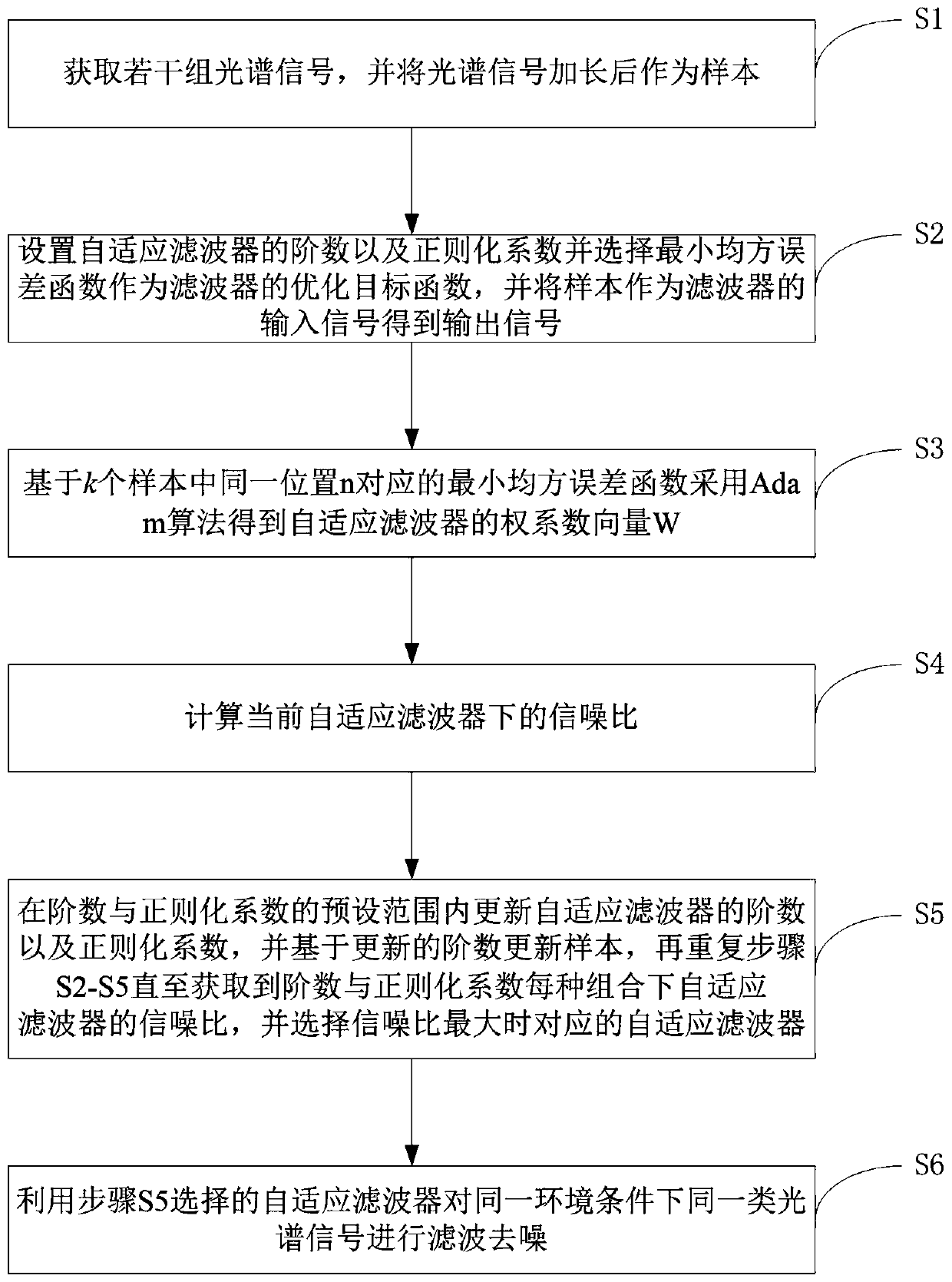
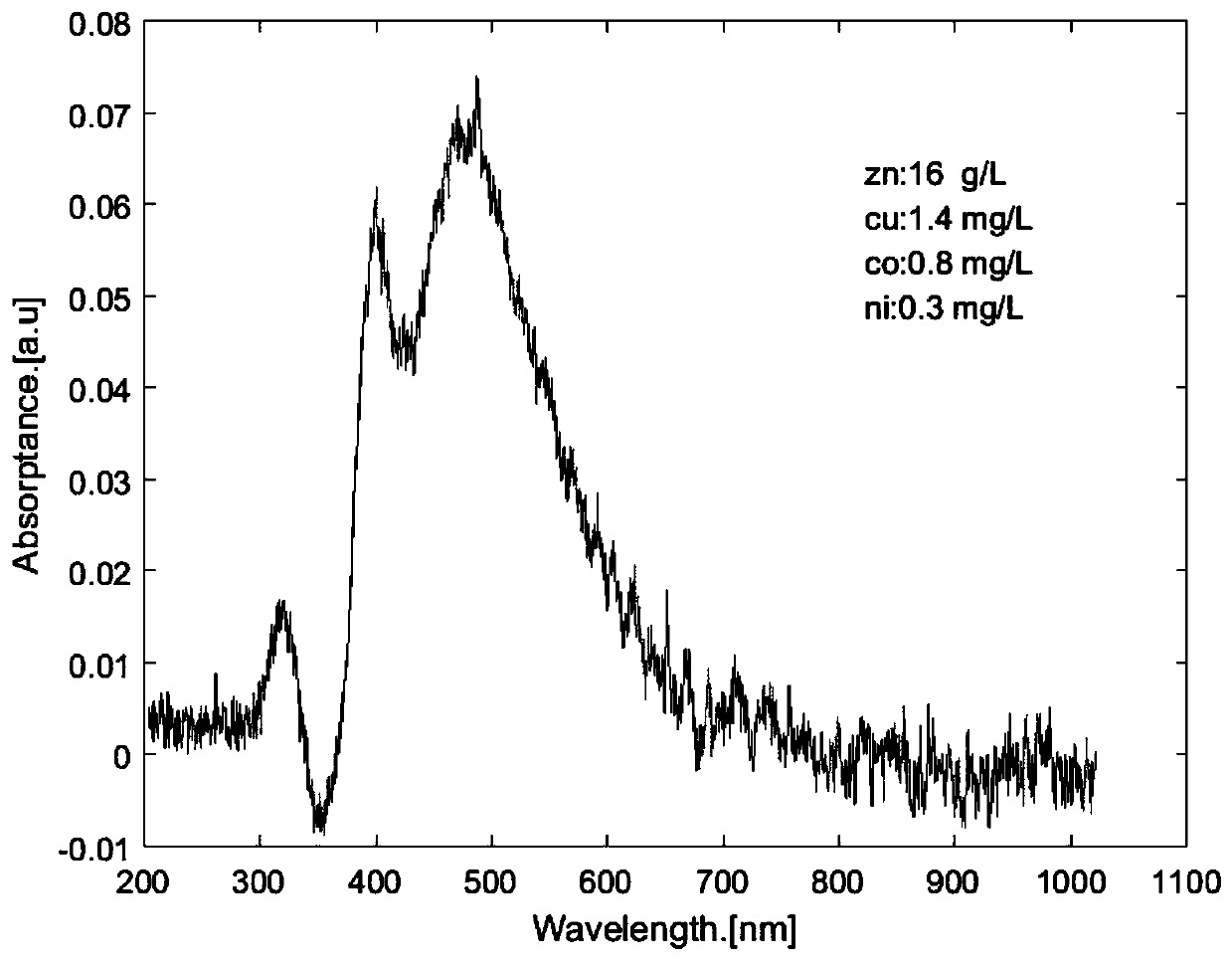
Spectrum denoising method
ActiveCN109946253AImprove noise immunityImprove generalization abilityColor/spectral properties measurementsPattern recognitionAdaptive filter
The invention discloses a spectrum denoising method which comprises the following steps: acquiring a plurality of groups of spectrum signal samples; setting an order number and a regularization coefficient of a self-adaptive filter, selecting a minimum mean square error function as an optimal target function of the filter, and taking the samples as input signals of the filter so as to obtain output signals; based on a minimum mean square error function corresponding to a same position n of k samples, acquiring a weight coefficient vector W of the self-adaptive filter according to an Adam algorithm; calculating a signal to noise ratio of the self-adaptive filter; within a preset range of the order number and the regularization coefficient, updating the order number and the regularization coefficient of the self-adaptive filter, repeating the step of acquiring the signal to noise ratio of each self-adaptive filter, and selecting a self-adaptive filter corresponding to the maximum singleto noise ratio; performing filtering denoising on a same type of spectrum signals under a same environment condition by using the selected self-adaptive filter. Compared with a conventional standard LMS algorithm, the method disclosed by the invention is optimal in denoising effect, and rapid in convergence rate.
Owner:CENT SOUTH UNIV
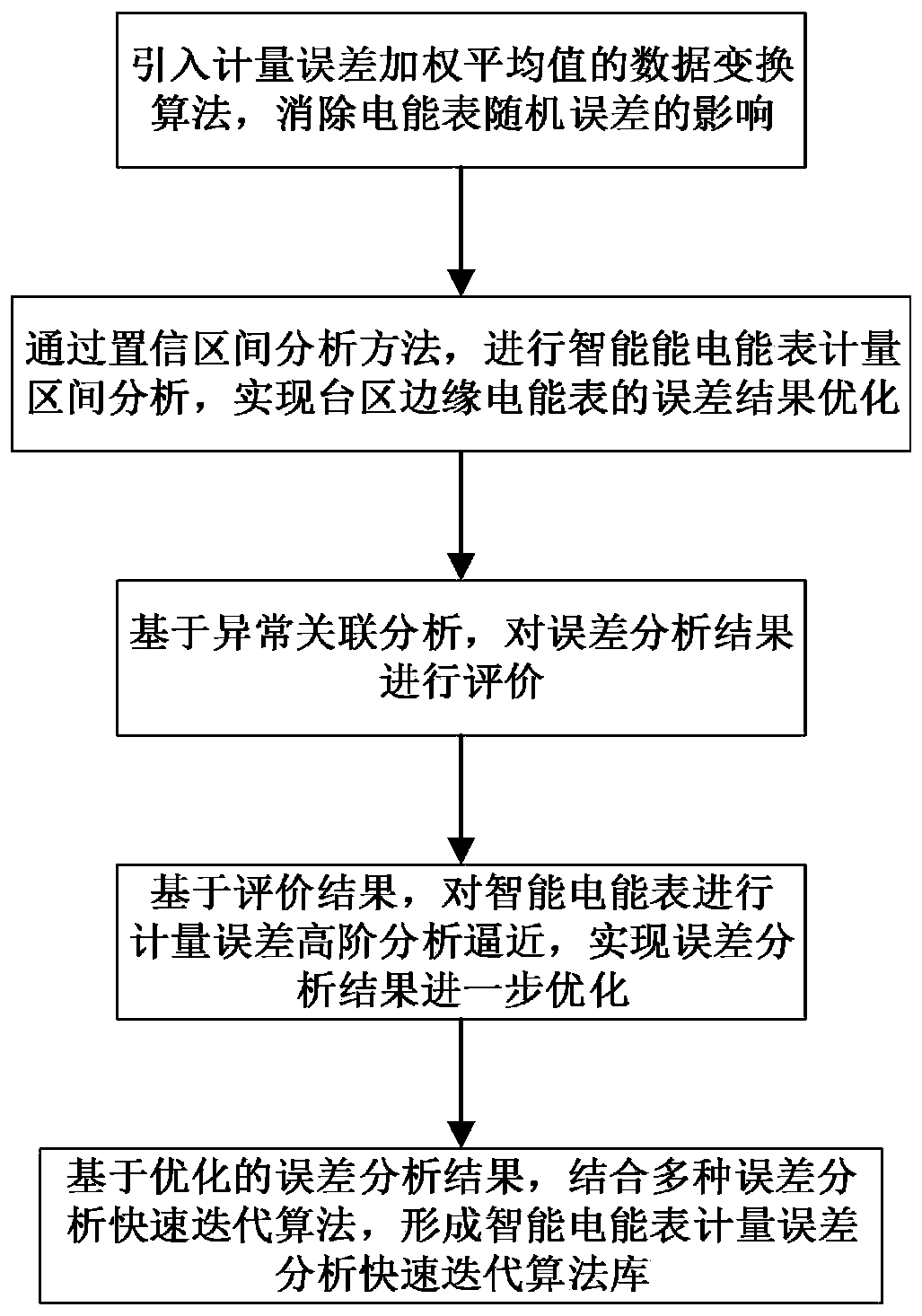
Data conversion method and system based on intelligent electric energy meter metering error analysis
ActiveCN111103565AEliminate the effects of random errorsError result optimizationElectrical measurementsData transformationTransformer
The invention relates to a data conversion method based on intelligent electric energy meter metering error analysis. The concept of metering relative error weighted average is introduced through multiple data transformation algorithms, then intelligent electric energy meter metering interval analysis is performed through a confidence interval analysis method, and error result evaluation and optimization of error result optimization, abnormal correlation analysis, metering error high-order analysis approximation and the like of the transformer area edge electric energy meter are realized. A standard algorithm knowledge base for metering error analysis of the intelligent electric energy meter is established so that relative errors of the electric energy meter are accurately calculated, andmaintenance, service life and the like of the electric energy meter are effectively and accurately guided.
Owner:ELECTRIC POWER SCI & RES INST OF STATE GRID TIANJIN ELECTRIC POWER CO +2
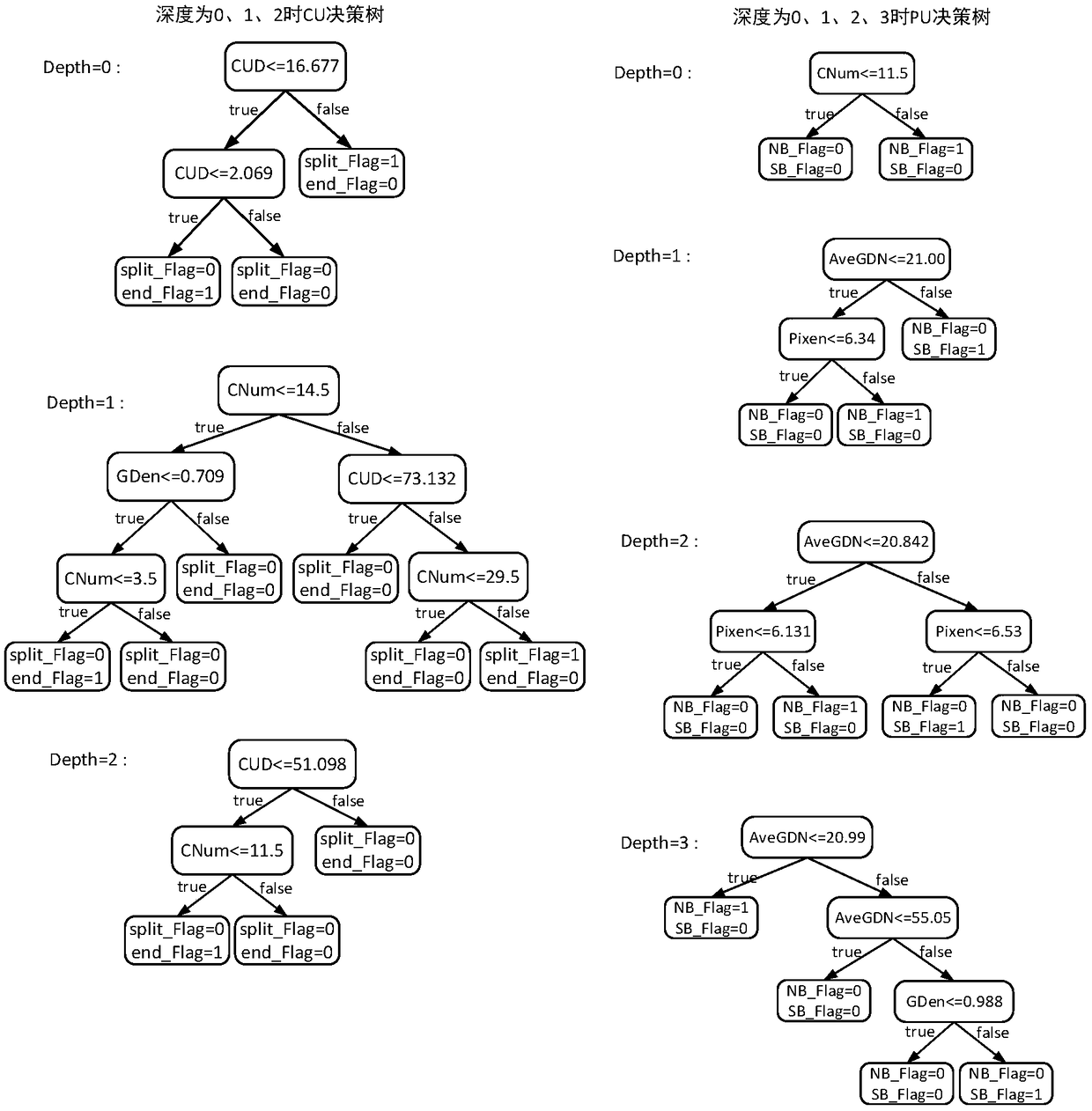
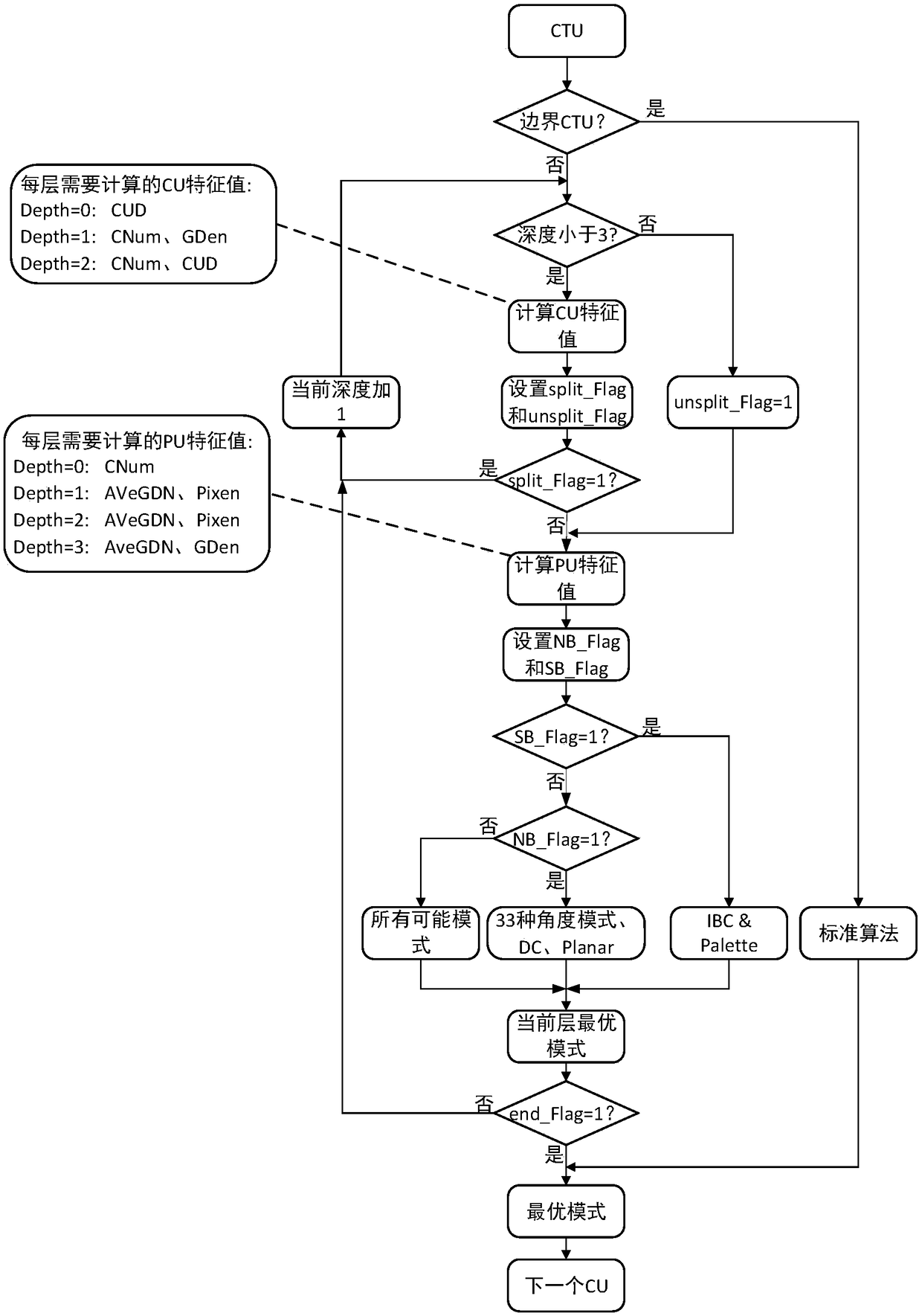
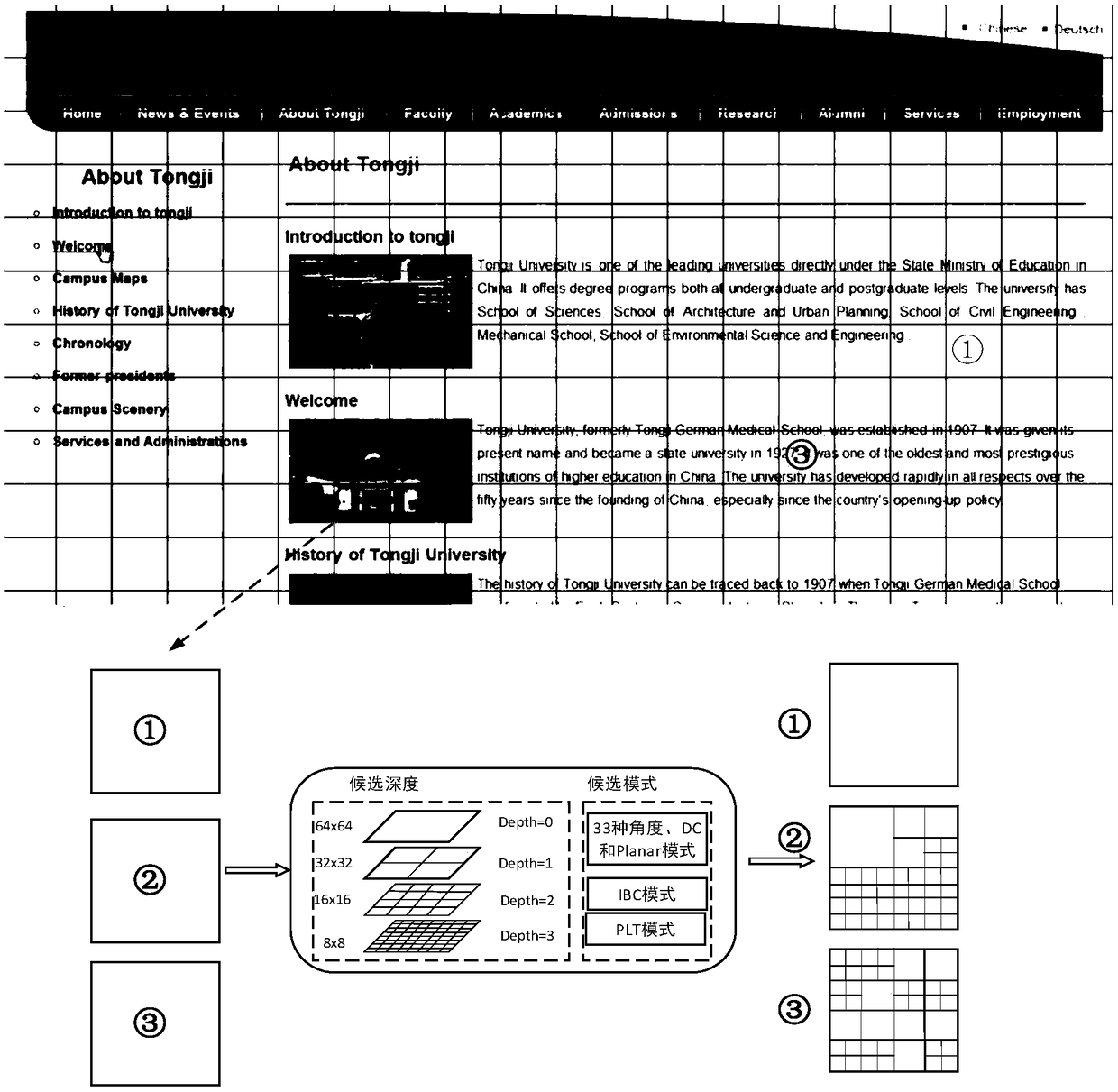
A HEVC screen content intra-frame fast encoding algorithm based on decision tree
ActiveCN109040764AReduce coding timeReduce coding complexityDigital video signal modificationData setOriginal data
The invention provides a HEVC screen content intra-frame fast encoding algorithm based on a decision tree, belonging to the technical field of video encoding and decoding. The algorithm includes: 1) extracting effective eigenvalues; 2) generating an original data set as a training set, and on the basis, training to complete a decision tree comprising a CU decision tree and a PU decision tree; 3) dividing the image into a plurality of CTUs, judging whether the current CU is a boundary CTU in the process of executing intra-frame encoding, if so, executing a standard algorithm to complete encoding, otherwise, carrying out step 4); 4) Performing fast coding, that is, completing the partition of current CU and the selection of PU mode by calculating the eigenvalue of the layer in a certain depth decision tree. The invention reduces the coding complexity by reducing the depth of CU and the mode traversal of PU through the algorithm of decision tree. Finally, it is ensured that the coding time can be effectively reduced and the effect of fast intra-frame coding can be achieved under the condition that the bit rate and peak signal-to-noise ratio are basically unchanged.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
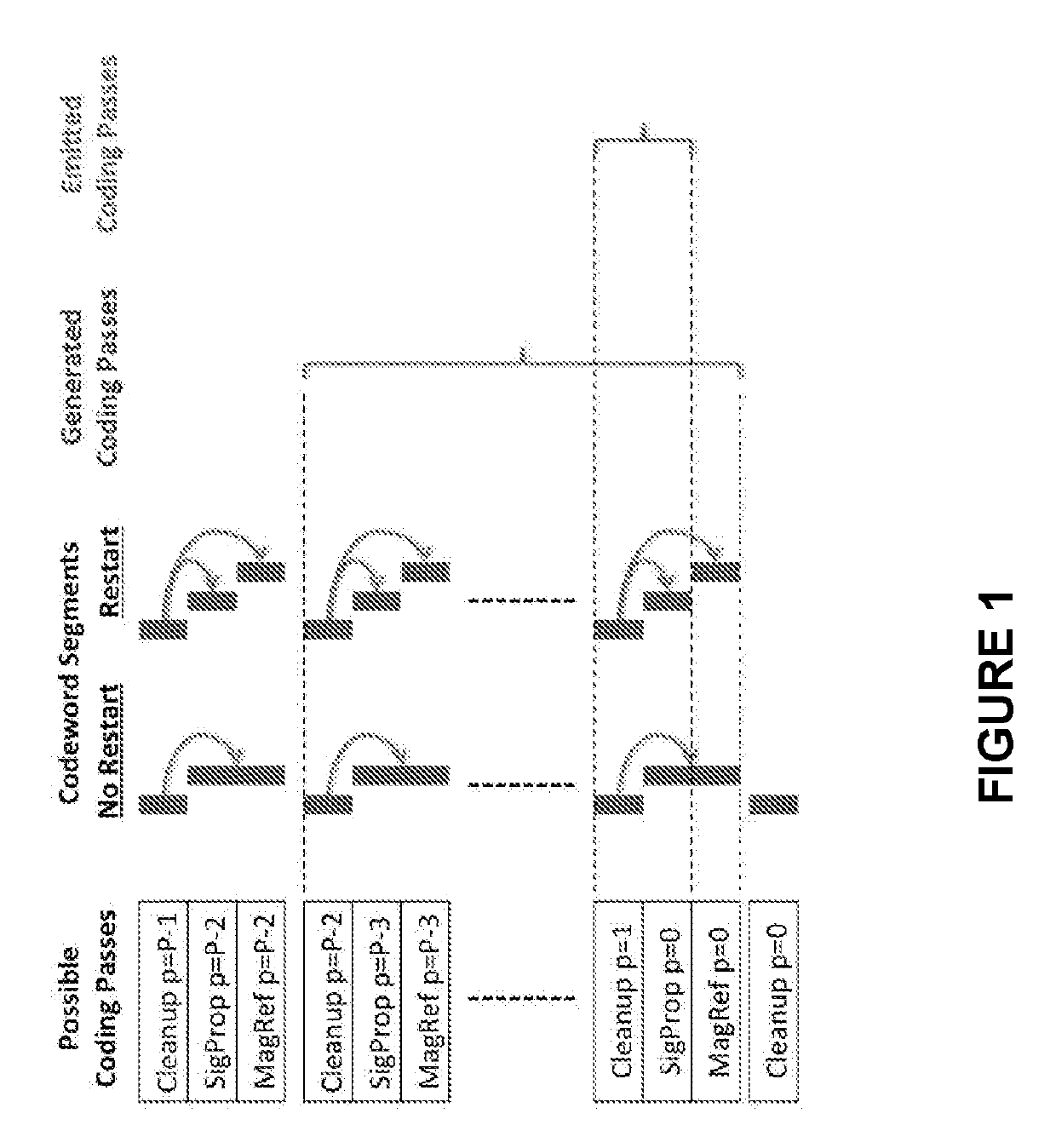
Two Low Complexity Decoding Algorithms for LDPC Codes
InactiveUS20130055043A1Simple processImprove performanceError correction/detection using multiple parity bitsCode conversionComputation complexityRound complexity
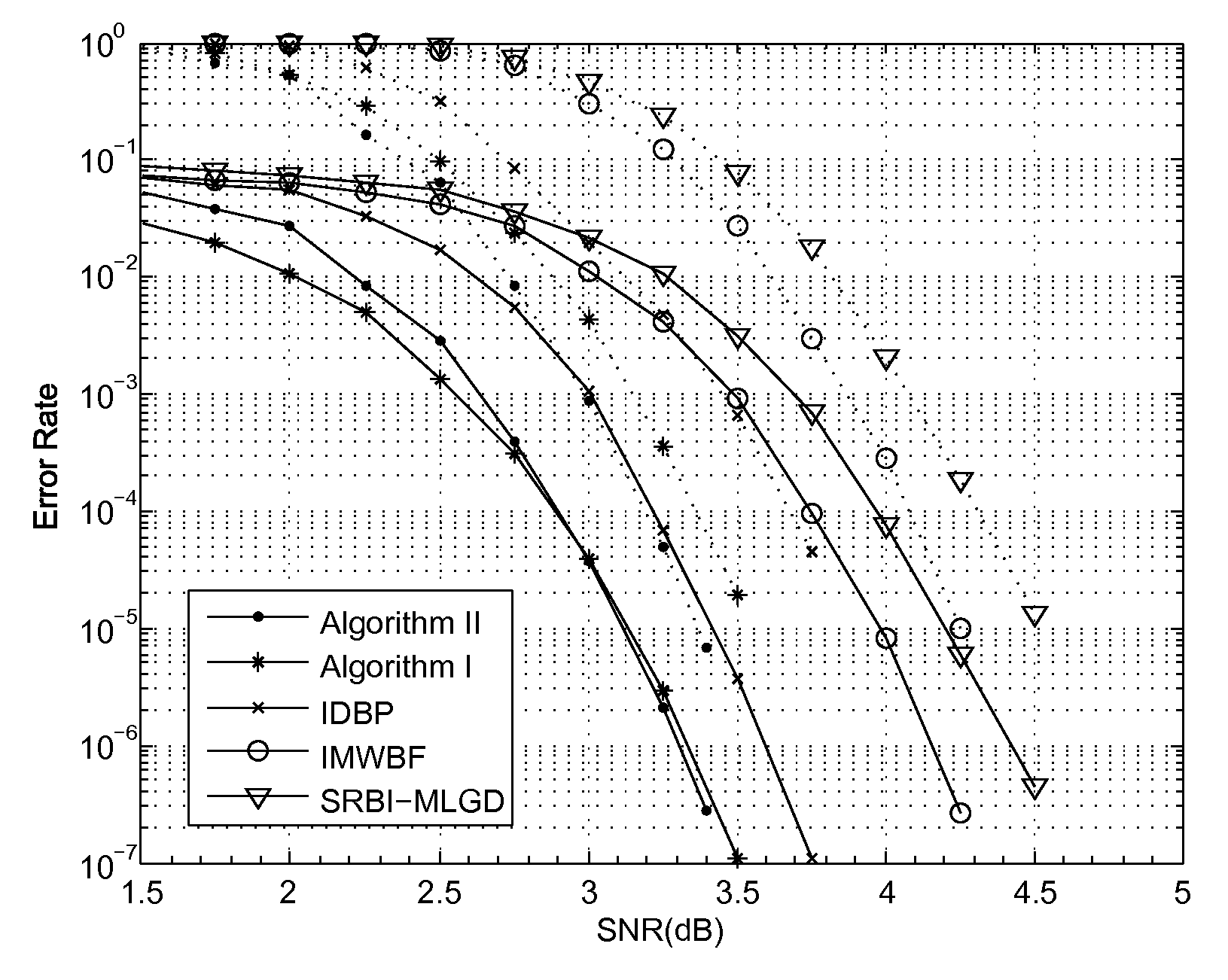
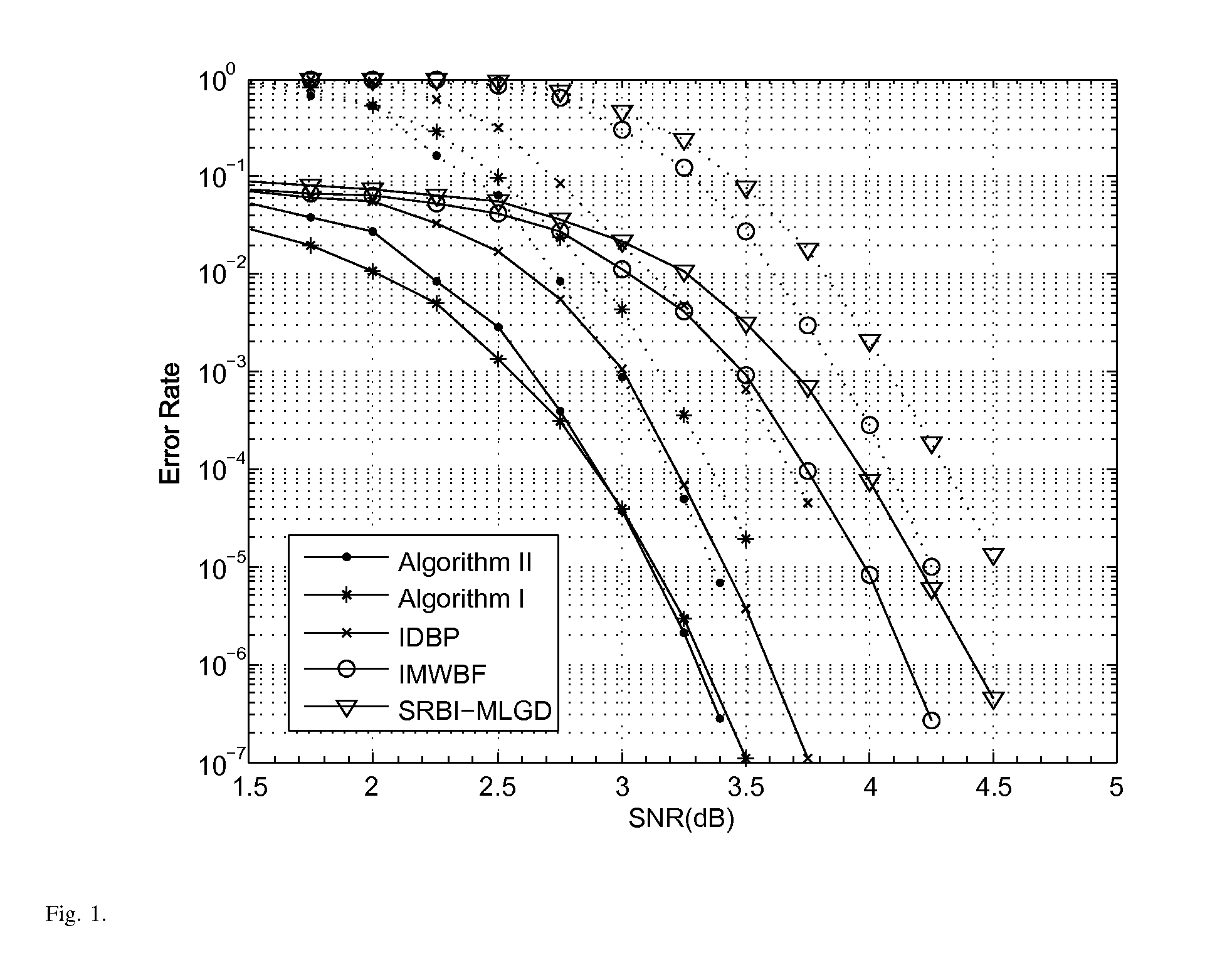
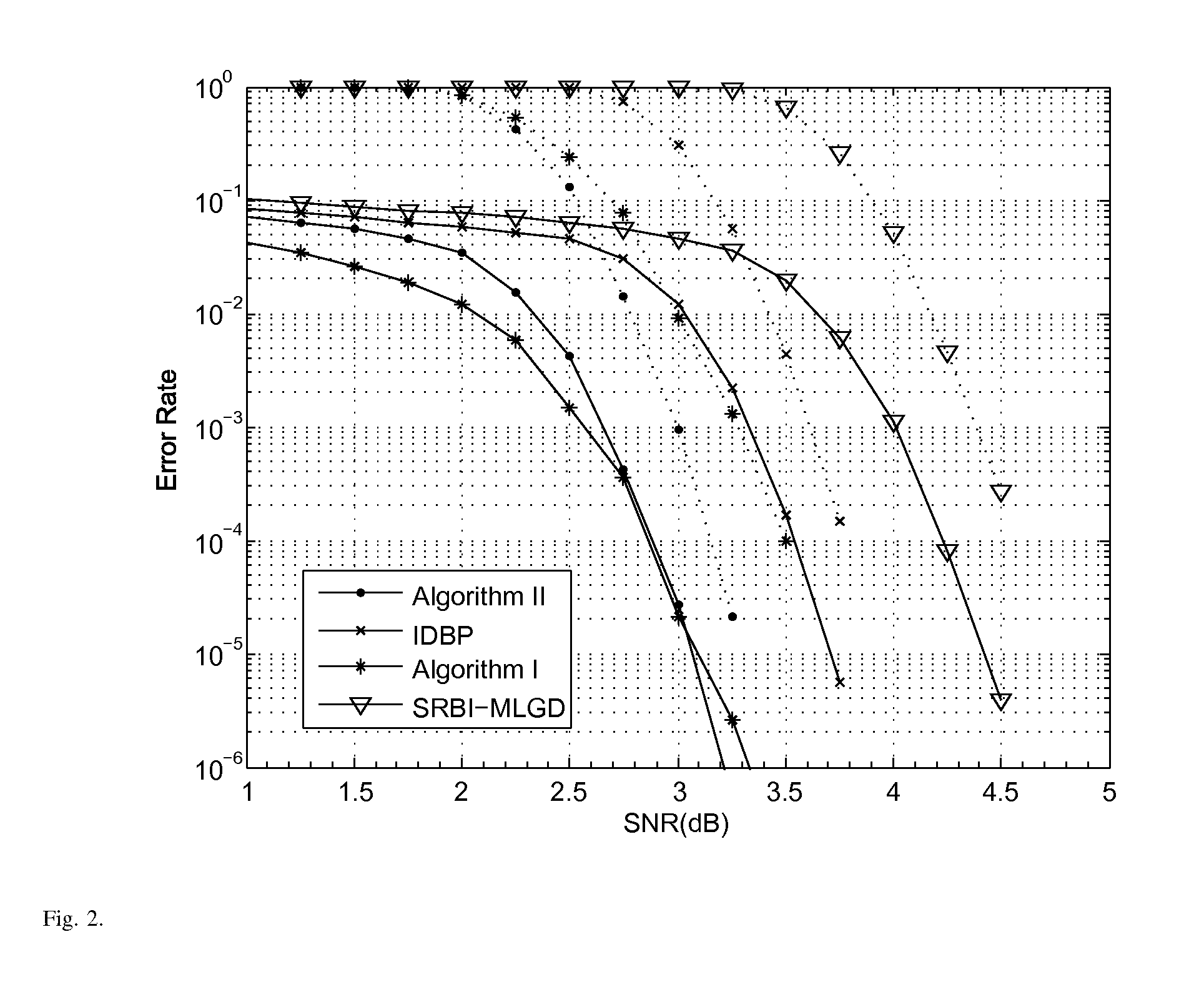
In the present invention, two improved variants of the reliability-based iterative majority-logic decoding algorithm for regular low-density parity-check (LDPC) codes are presented. The new algorithms are obtained by introducing a different reliability measure for each check-sum of the parity-check matrix, and taking it into account in the computation of the extrinsic information that is used to update the reliability measure of each received bit in each iteration. In contrast to the first algorithm, the second algorithm includes check reliability that changes at each iteration. For the tested random and structured LDPC codes, both algorithms, while requiring very little additional computational complexities, achieve a considerable error performance gain over the standard one. More importantly, for short and medium block length LDPC codes of relatively large column weight, both algorithms outperform or perform just as well as the iterative decoding based on belief propagation (IDBP) with less decoding complexity.
Owner:NGATCHED NKOUATCHAH TELEX MAGLORIE +2
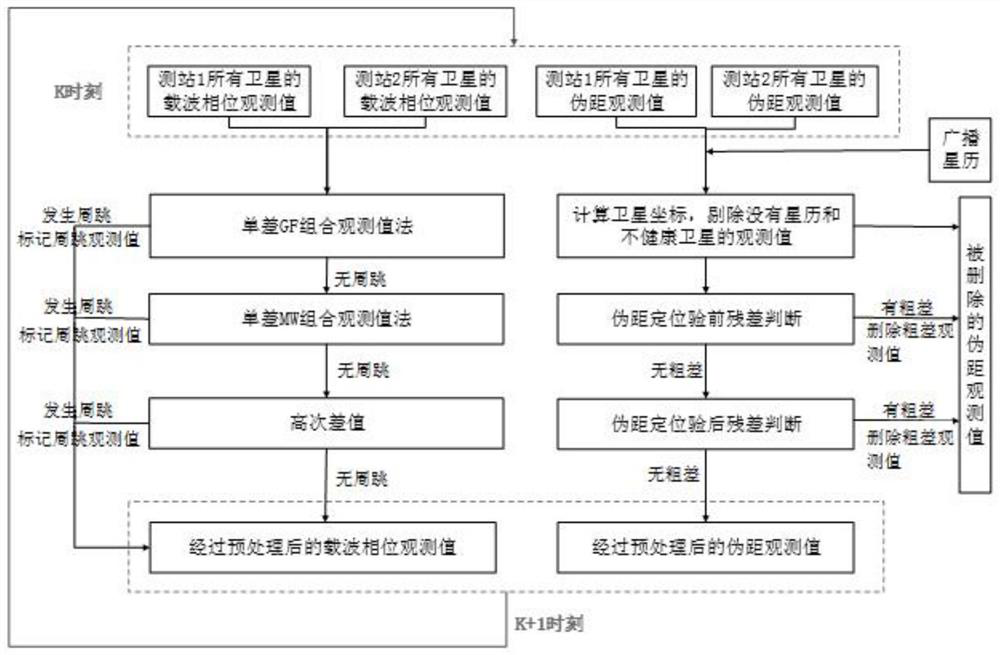
Beidou GNSS satellite real-time positioning and orientation data preprocessing system and method
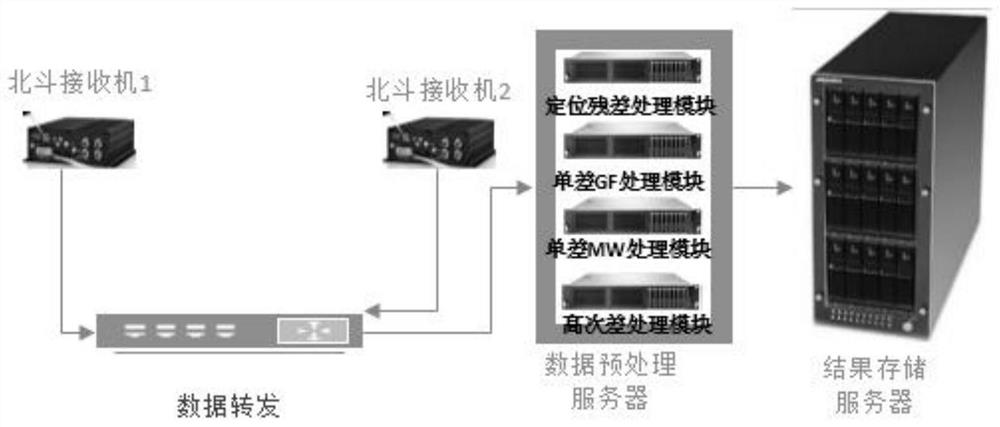
PendingCN112305574AImprove reliabilityImprove effectivenessSatellite radio beaconingObservation dataCarrier signal
The invention relates to a Beidou GNSS satellite real-time positioning and orientation data preprocessing system and method. The method comprises the following steps of inputting carrier phase observation values, pseudo-range observation values and broadcast ephemeris of a plurality of Beidou / GNSS satellites of an observation station 1 and an observation station 2, utilizing a satellite position calculation standard algorithm to respectively calculate each satellite coordinate and a clock error correction number, comprehensively using a pseudo-range positioning residual analysis method, an inter-station single-difference GF and MW combined observation value method and a high-order difference method for detecting pseudo-range gross errors and carrier phase cycle slips, acquiring all data through calculation, conducting cycle slip judgment and residual judgment before and after pseudo-range positioning verification, and finally acquiring observation data high in effectiveness and reliability. The pseudo-range positioning residual analysis method, the inter-station single-difference GF and MW combined observation value method and the high-order difference method are comprehensively used for detecting pseudo-range gross errors and carrier phase cycle slips, and the effectiveness and reliability of detection are improved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +5
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com