Encryption algorithm identification method based on deep learning graph network
An encryption algorithm and deep learning technology, applied in the field of computer software security, can solve problems such as various file formats, inability to identify encryption, and difficulty in judging whether the encryption mechanism is compliant, so as to facilitate research and reduce the difficulty of research
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] First of all, the applicant explains the technical terms involved in the present invention as follows:
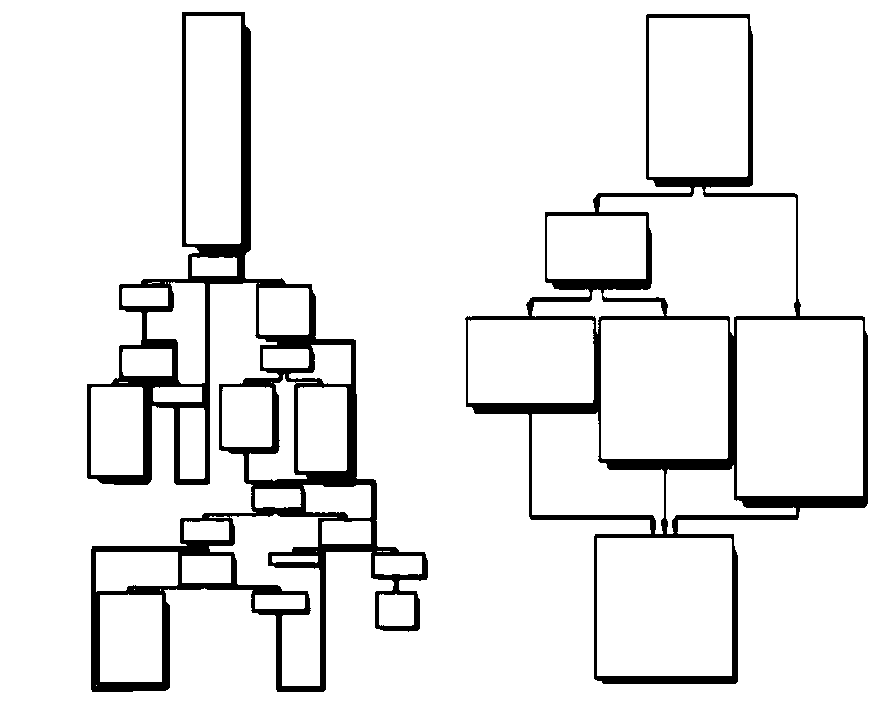
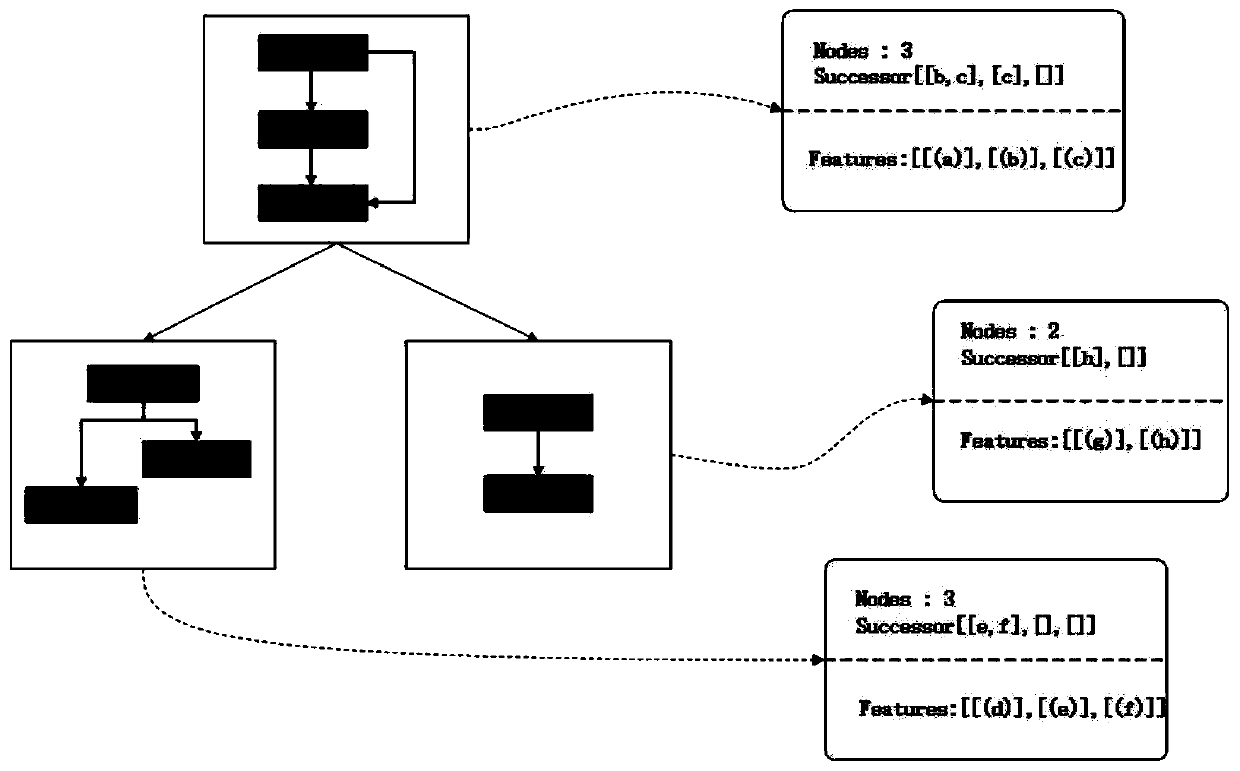
[0037] Basic block: refers to the sequence of statements executed sequentially in the program, in which there is only one entry and one exit, the entry is the first statement in it, and the exit is the last statement in it. A function in code consists of multiple basic blocks.
[0038] Crawling: Refers to the online-to-local copying process of source codes such as web pages, open source libraries, and code hosting platforms using reptile tools such as Octoparse.
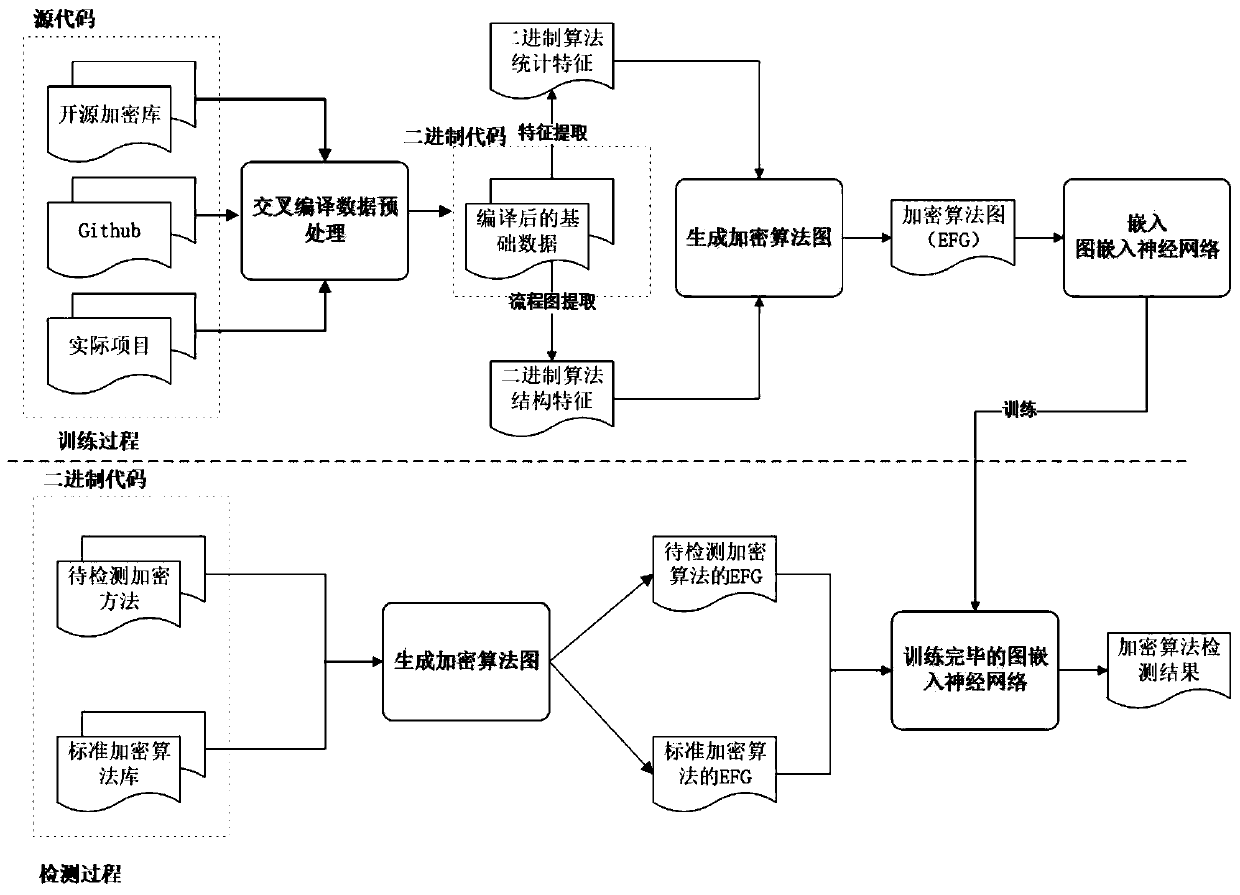
[0039]The encryption algorithm identification method based on the deep learning graph network of the present invention is designed with the idea of converting the traditional "binary encryption algorithm identification problem" into a "binary similarity detection problem".
[0040] see figure 1 , the present embodiment provides an encryption algorithm identification method based on a deep learning graph...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com