Template attack method in allusion to SM4 cipher algorithm round output
A template attack and cryptographic algorithm technology, applied in the field of cryptographic algorithm analysis and detection, can solve the problems of template attack, increase the difficulty of processing data and computational complexity, and infeasible template attack.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0086] The specific embodiments of the present invention are described below so that those skilled in the art can understand the present invention, but it should be clear that the present invention is not limited to the scope of the specific embodiments. For those of ordinary skill in the art, as long as various changes Within the spirit and scope of the present invention defined and determined by the appended claims, these changes are obvious, and all inventions and creations using the concept of the present invention are included in the protection list.
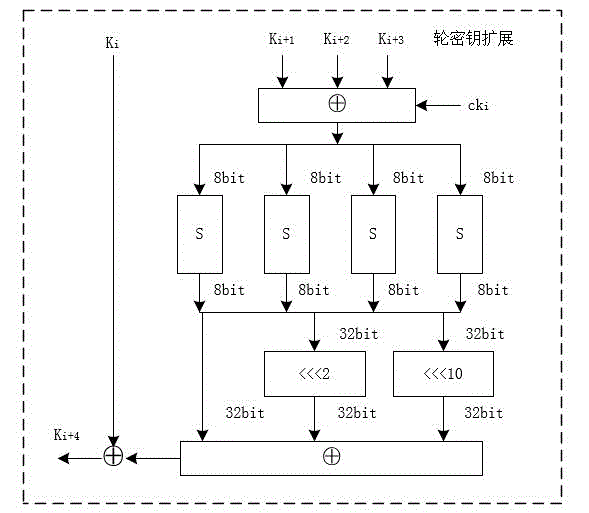
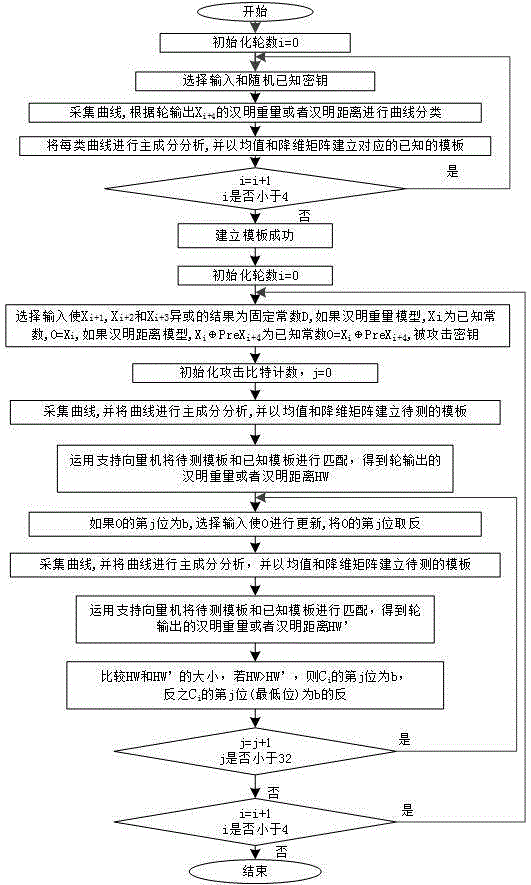
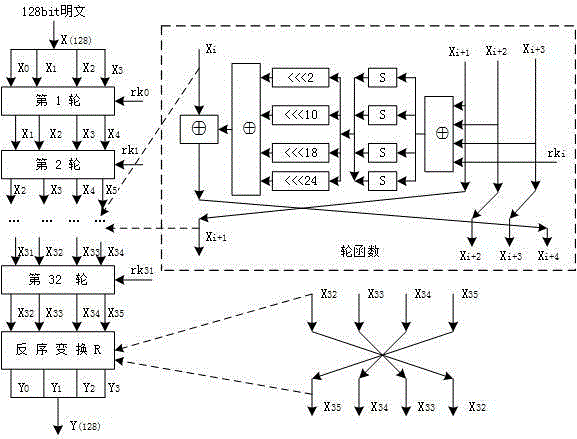
[0087] The method for the template attack aimed at the SM4 cipher algorithm round output specifically comprises the following steps:
[0088] S1: Optionally input plaintext or ciphertext and a random known key, and establish a round output X i+4 (i=0,1,2,3) is the template for calculating the intermediate value of the Hamming weight / Hamming distance, and a total of 33 templates are established for each round of output. The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com