Long key-based realization system and method for SM4 key extending algorithm
A key expansion and implementation system technology, which is applied in the implementation system field of SM4 key expansion algorithm, can solve the problem of small key space, achieve the effect of strengthening randomness, solving potential safety hazards, and increasing key space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
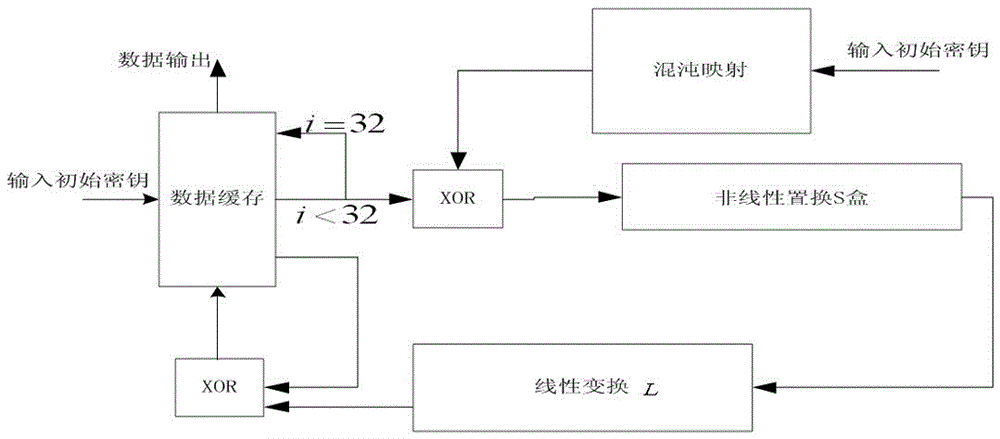
[0020] Such as figure 1 Shown, a kind of implementation system of SM4 key expansion algorithm based on long key, including chaotic mapping module, data cache module, XOR module, non-linear permutation S box module and linear transformation L module, described chaotic mapping module input As part of the initial key, by using multiple iterations of the chaotic map, a pseudo-random sequence with good randomness is generated as the input of the original SM4 key expansion algorithm. By considering the chaotic performance and hardware resource consumption, the chaotic map module selection Logistic mapping;
[0021] The XOR module is a multi-input XOR logic gate circuit;
[0022] The non-linear permutation S-box module uses four parallel 8-input S-boxes in total, each parallel S-box addresses the input 8-bit number address, and outputs 8-bit data stored in the S-box;
[0023] The linear transformation L module is simply a shift and XOR operation.
Embodiment 2
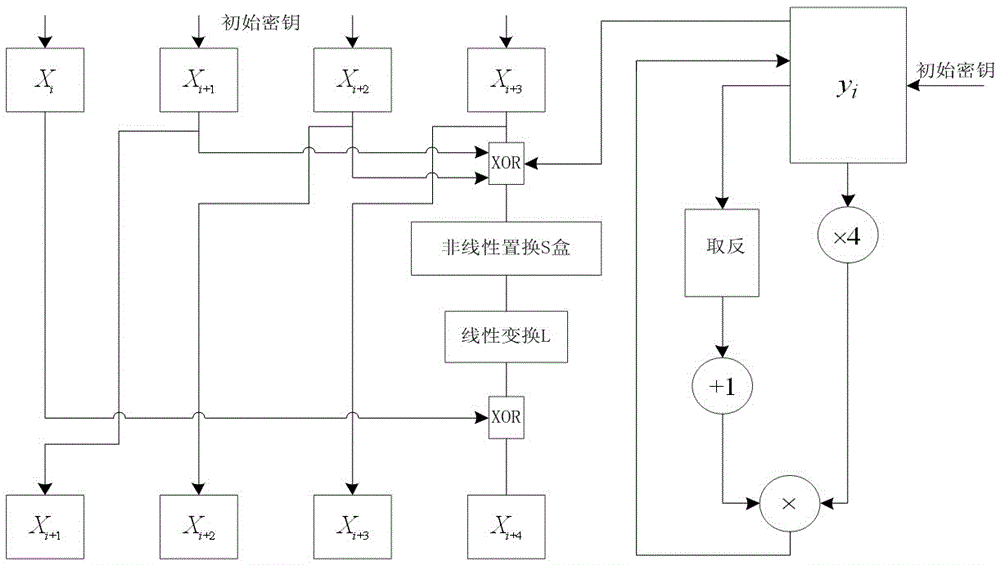
[0025] Such as image 3 As shown, the implementation method of a long-key based SM4 key expansion algorithm obtained by the system of Embodiment 1 comprises the following steps:
[0026] Step 1001: Divide the initial key into two parts. One part is a fixed-size 128-bit k 1 , the remaining initial key is another part k 2 . k 2 The number of bits needs to be greater than or equal to 32 bits. Therefore, the number of bits of the entire initial key needs to be greater than or equal to 160 bits.
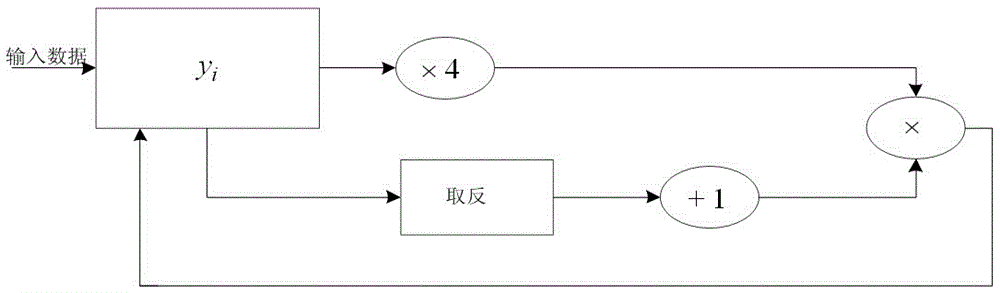
[0027] Step 1002: set the fixed 128-bit key k 1 Divide into 4 32-bit data sequentially from high bit to low bit, and store in X i 、X i+1 、X i+2 and x i+3 middle. The remaining initial key k 2 As the initial value of the Logistic chaos map, and stored in y i middle.
[0028] Step 1003: put X i+1 、X i+2 and x i+3 XOR, finally with k 2 The low 32-bit data XOR is extracted to obtain the final 32-bit number V.
[0029] Step 1004: Divide the 32-bit number V into four 8-bit nu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com