Combined attack method for SM4 algorithm
A joint attack and algorithm technology, applied in the countermeasures of attack encryption mechanism, digital transmission system, electrical components, etc., can solve the problems of unfavorable attack analysis and achieve the effect of improving attack efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
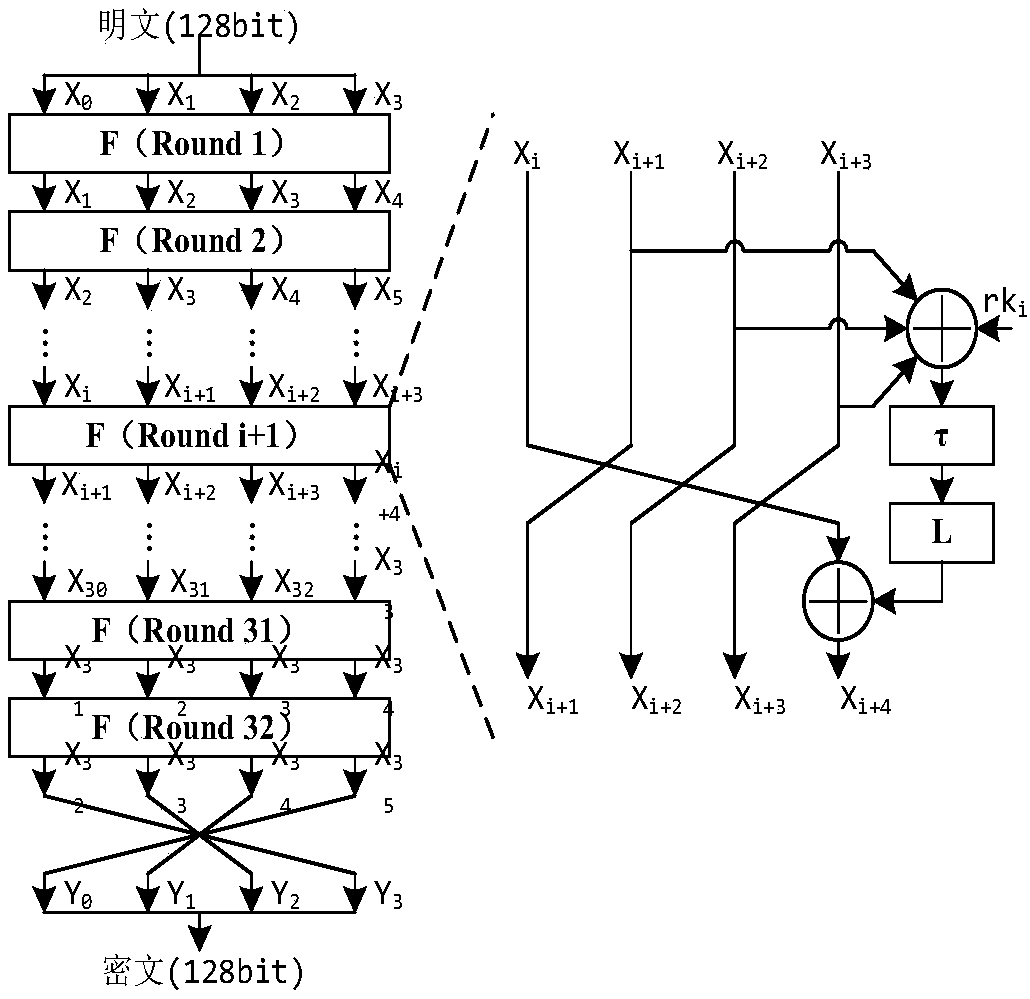
[0038] The present invention proposes a method combining cross-round attack and differential analysis. This method only needs to select plaintext input for the first round and the third round. The basic idea is as follows:
[0039] Let X 4 Enter A for the first round of selection 1 =(a 0,1 , a 1,1 , a 2,1 , a 3,1 ,) the output result of the time wheel, at this time, the constraints for selecting the input are:
[0040] random
[0041] Then there are:
[0042] At this time T(A 1) is an unknown fixed value, X 0 is a random value, let the corresponding input of the second round be set to A 2 , the output of box S is B 2 , then there is
[0043]
[0044]
[0045] make
[0046] key 1 is a fixed value, so you can choose the key 1 To analyze the attack target for energy, the intermediate value of the attack is selected at this time as the output of the second round of S-box nonlinear transformation. key in attack 1 Afterwards, due to the key 1 There are t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com