SM4 method capable of resisting energy analysis attack
An energy analysis attack and masking technology, applied in the direction of encryption devices with shift registers/memory, etc., can solve problems such as catastrophic effects, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
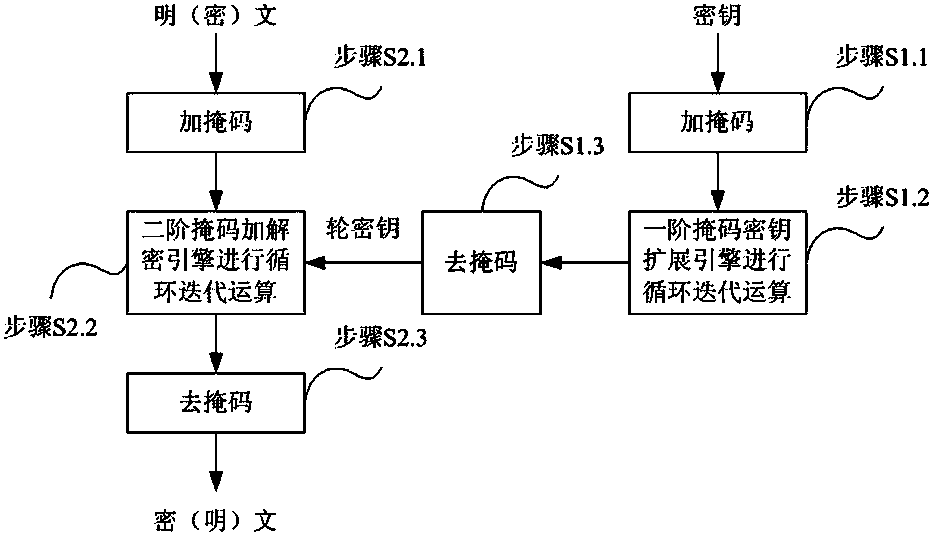
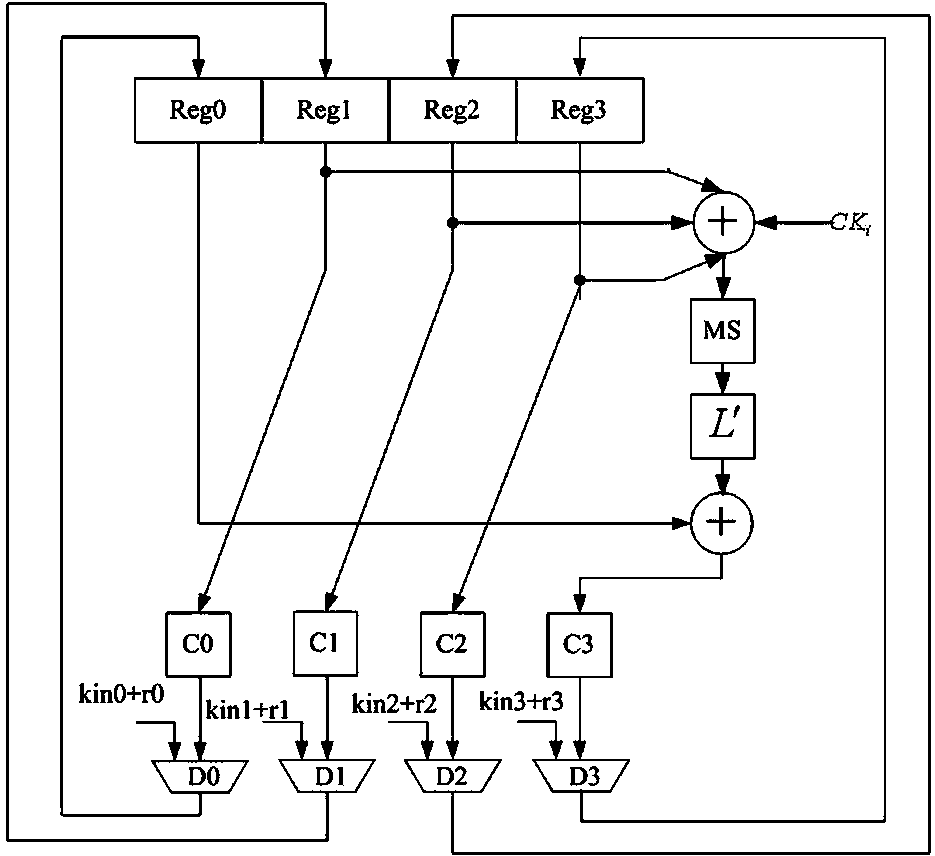
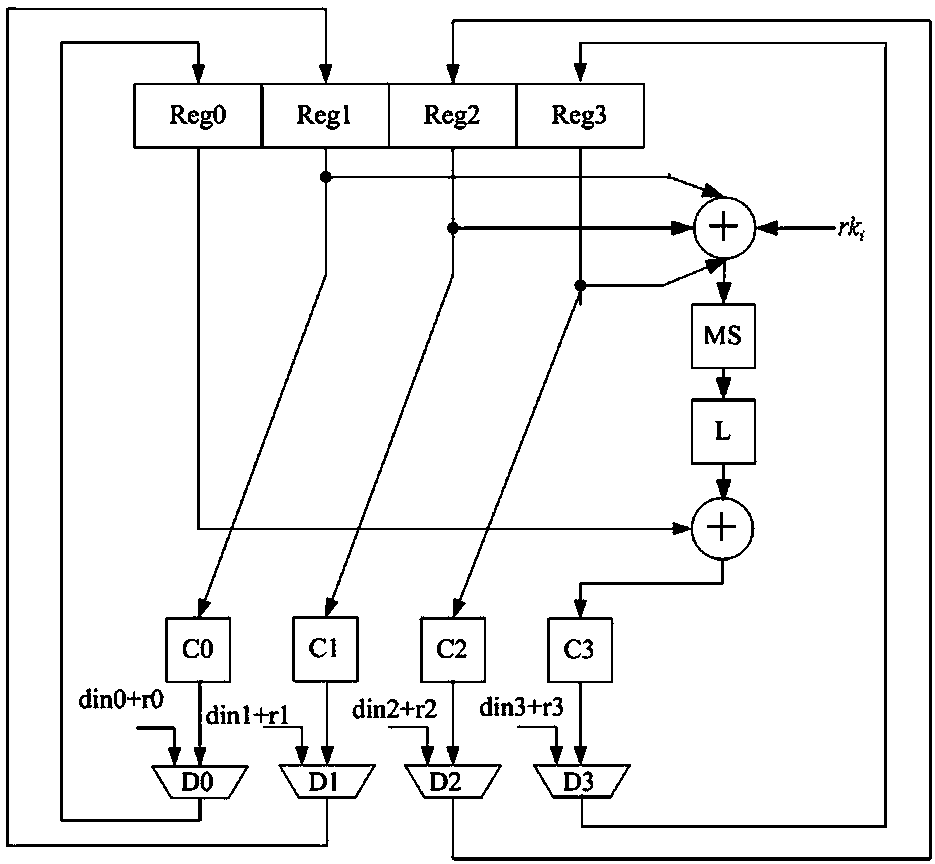
[0099] based on the following Figure 1 ~ Figure 3 , specifically explain the preferred embodiment of the present invention.
[0100] The SM4 algorithm is a grouping algorithm, which is a generalized Feistel structure, and its only nonlinear transformation is the S-box transformation.
[0101] The present invention provides an SM4 method capable of resisting energy analysis attacks. The method uses a first-order mask key expansion engine to perform a key expansion operation on an input key, and then outputs a round key to a second-order mask encryption and decryption engine. The second-order mask encryption and decryption engine performs 32 rounds of iterative operations on the input plain (cipher) text and round key, and then outputs the secret (plain) text.
[0102] The first-order mask key expansion engine and the second-order mask encryption and decryption engine work at the same time. The first-order mask key expansion engine generates a round key each round, and outputs...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com