Anti-leakage file security sharing method
An anti-leak, file technology, applied in the field of password applications, can solve the problems of reduced file transmission efficiency, difficulty in taking into account file security transmission speed, file sharing security, and inability to well reflect the immediacy of information sharing.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The present invention will be further described below in conjunction with drawings and embodiments.
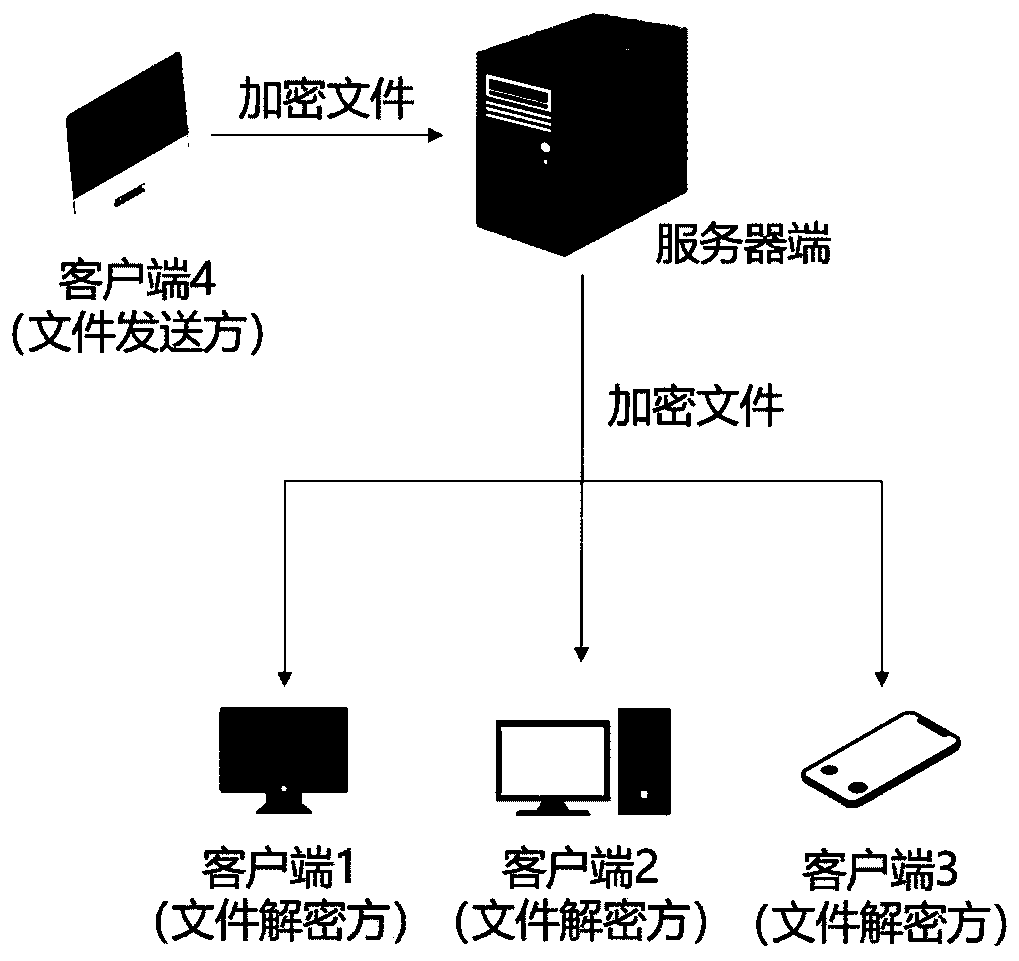
[0063] In order to distribute work to all components and ensure security, first determine that for each shared file, the implementation process involves four components: the file publisher, the encrypted file, the server and the file decryptor, such as figure 1 Shown: Among them, the file publisher is the person who wants to share the file; the encrypted file is the file currently being shared; the server side, that is, the central server, manages the file and the identity of all participants; the file decryption party, that is, the file acquirer, has Qualified people to access this file.
[0064] The file publisher only needs to upload the file to the server, and obtain the file decryption key returned by the server to distribute to qualified persons. Or delegate server-side distribution. It is worth noting that in the system, the identities of the file issuer and th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com