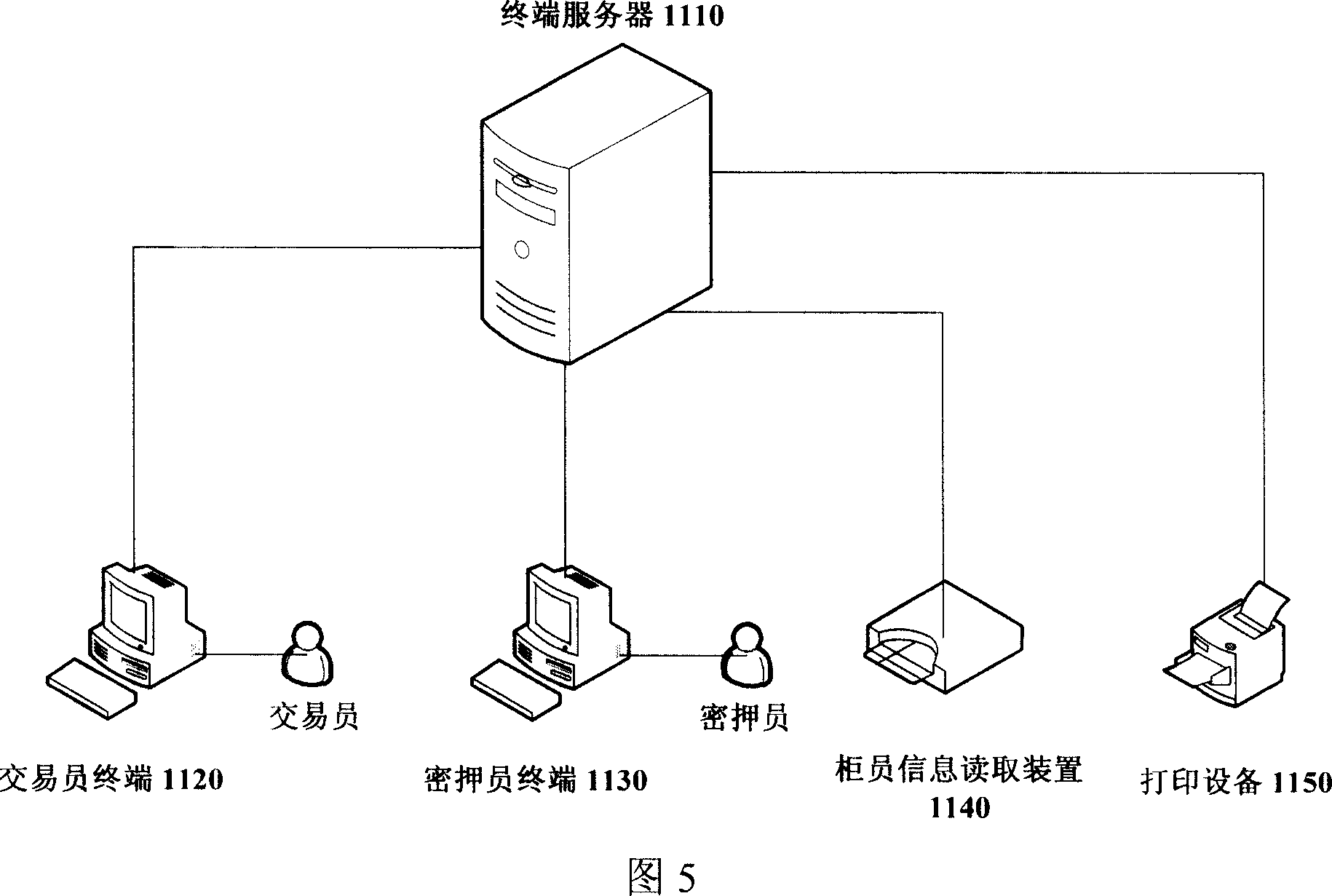
Patents
Literature
62results about How to "Achieve non-repudiation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
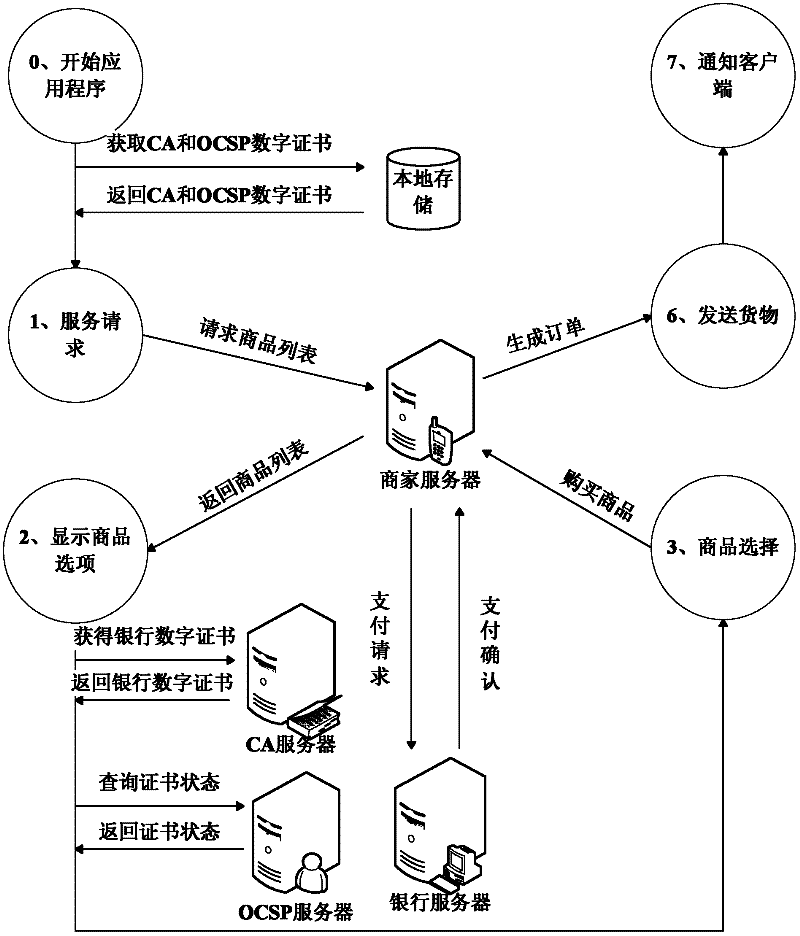
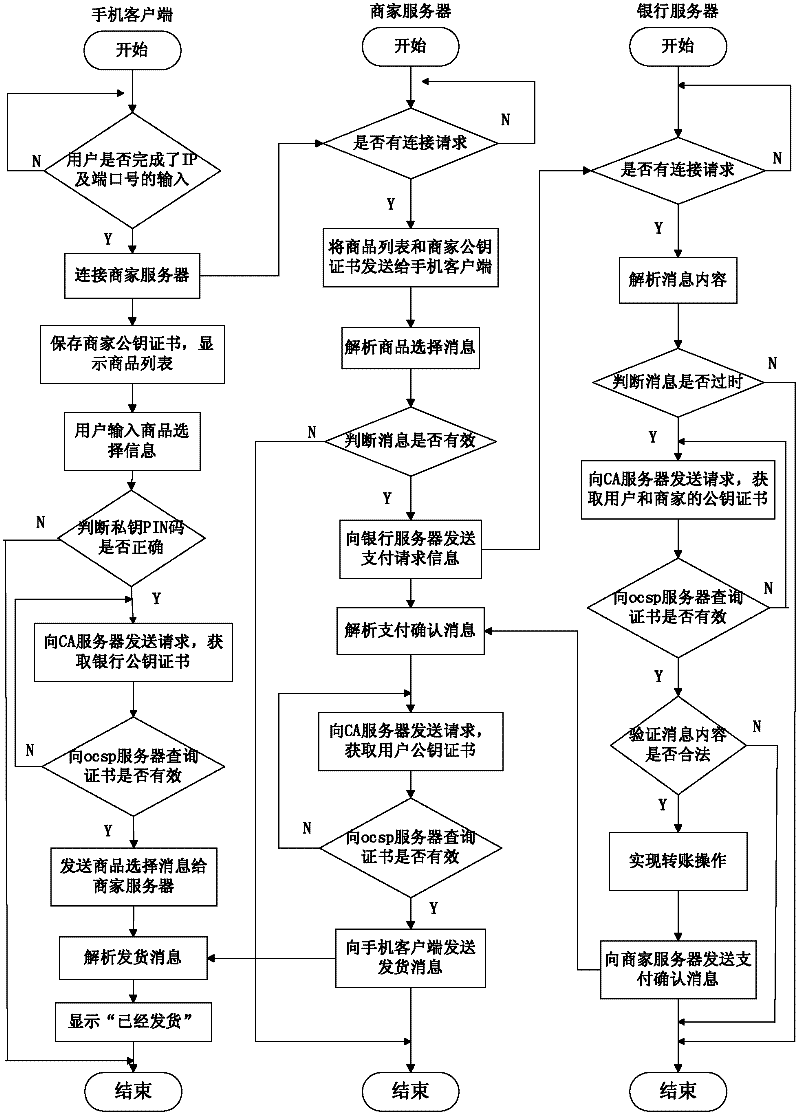
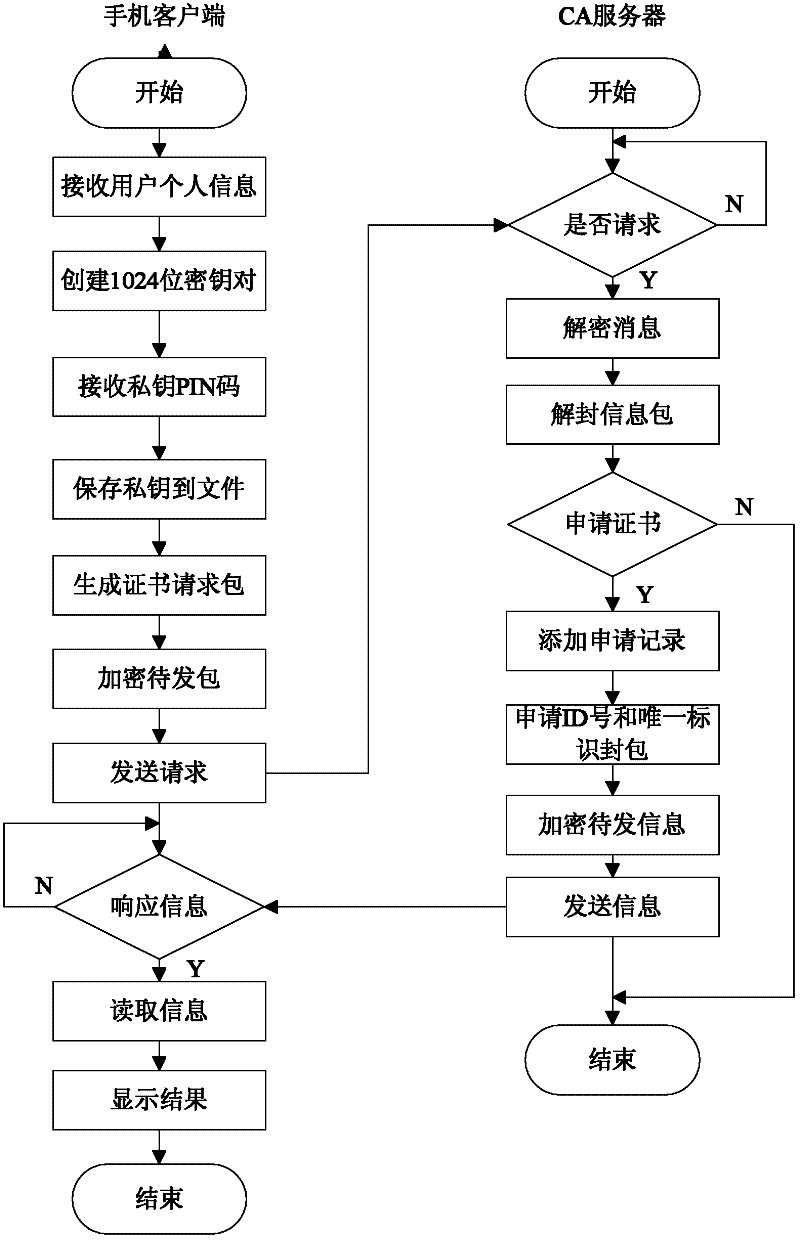
Remote mobile payment system based on digital certificate and payment method
InactiveCN102609841AGuaranteed confidentialityProtect transaction detailsProtocol authorisationConfidentialityDigital signature
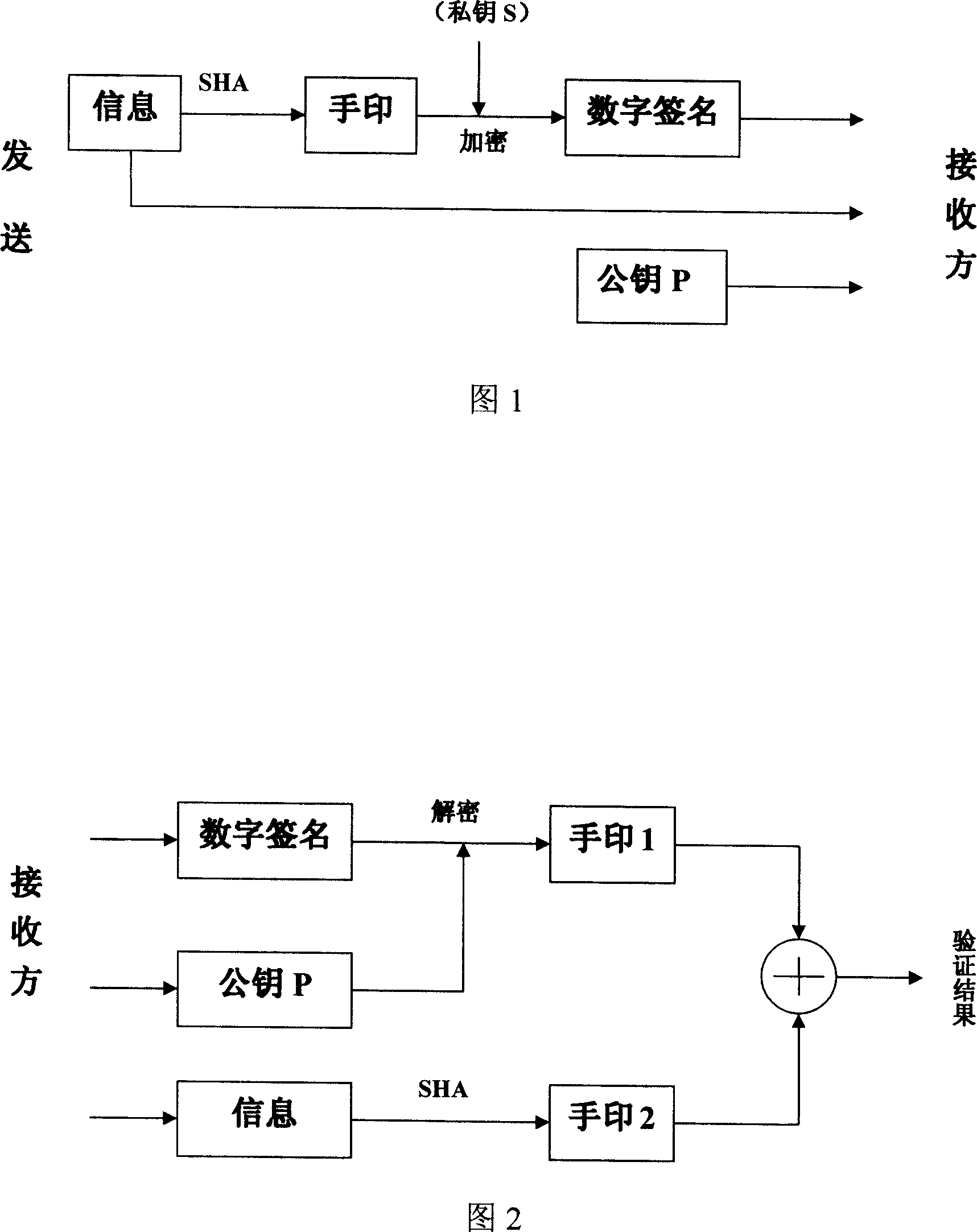
The invention relates to a remote mobile payment system based on a digital certificate and a payment method and belongs to the technical field of mobile payment. According to the invention, the digital certificate is used for binding an identity of a user with a public key of the user and the problem of difficulty in managing a secret key during a transaction process is solved. All communication information is encrypted by using the secret key, so that the confidentiality of the transaction information is ensured, the transaction details of the user are protected and the privacy is prevented from being revealed. Meanwhile, each piece of transaction information is digitally signed by using a private key of a sender; as long as a receiver successfully verifies the signature by using the public key of the sender, the sender cannot deny the performed operation of sending the information, so that the undeniable property of information is achieved; an abstract value of the information is calculated for each piece of transaction information; and the receiver firstly compares the abstract value of the information with the received information, so as to judge if the information is distorted and ensure the completeness of the information.
Owner:何文秀
Information security control system
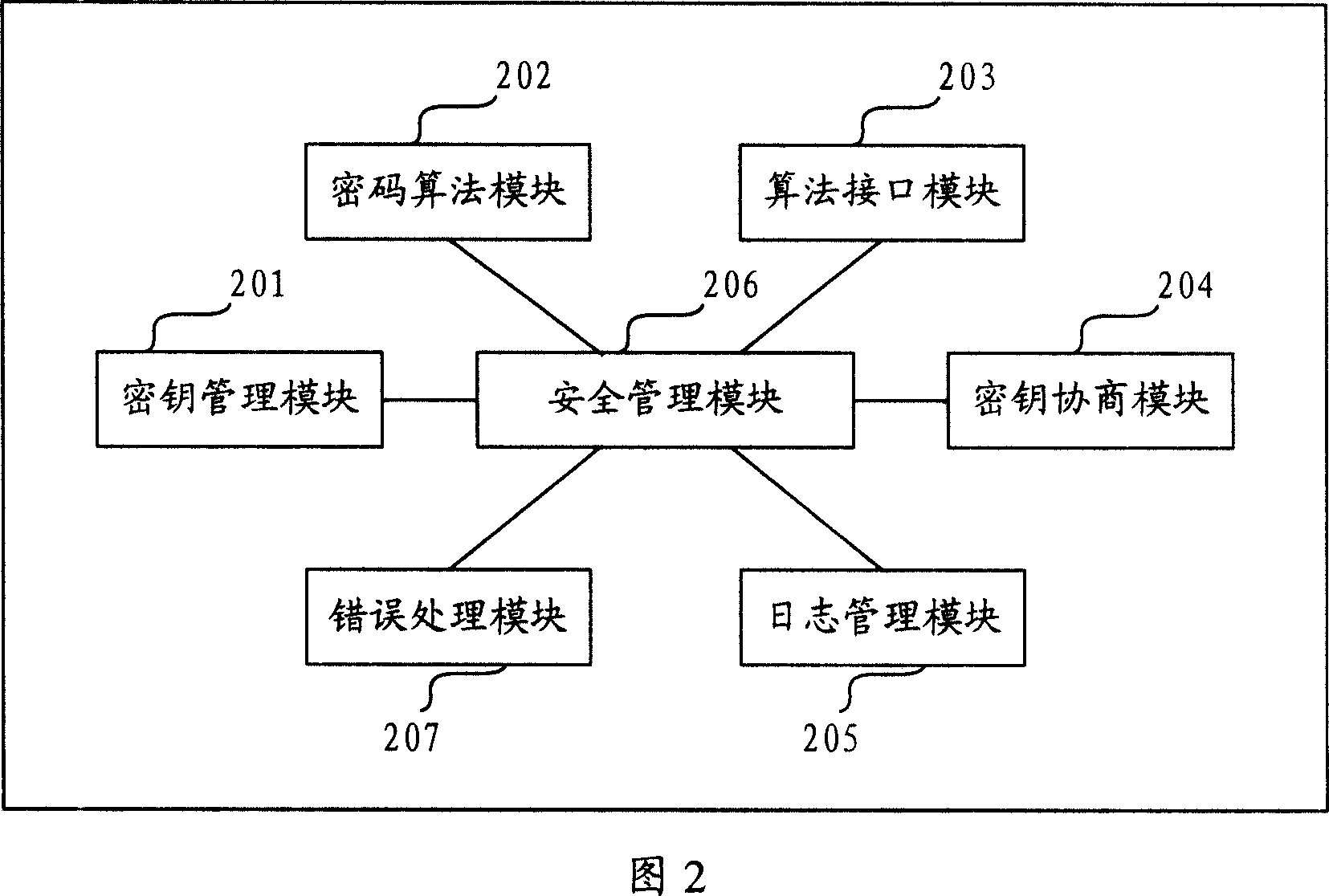
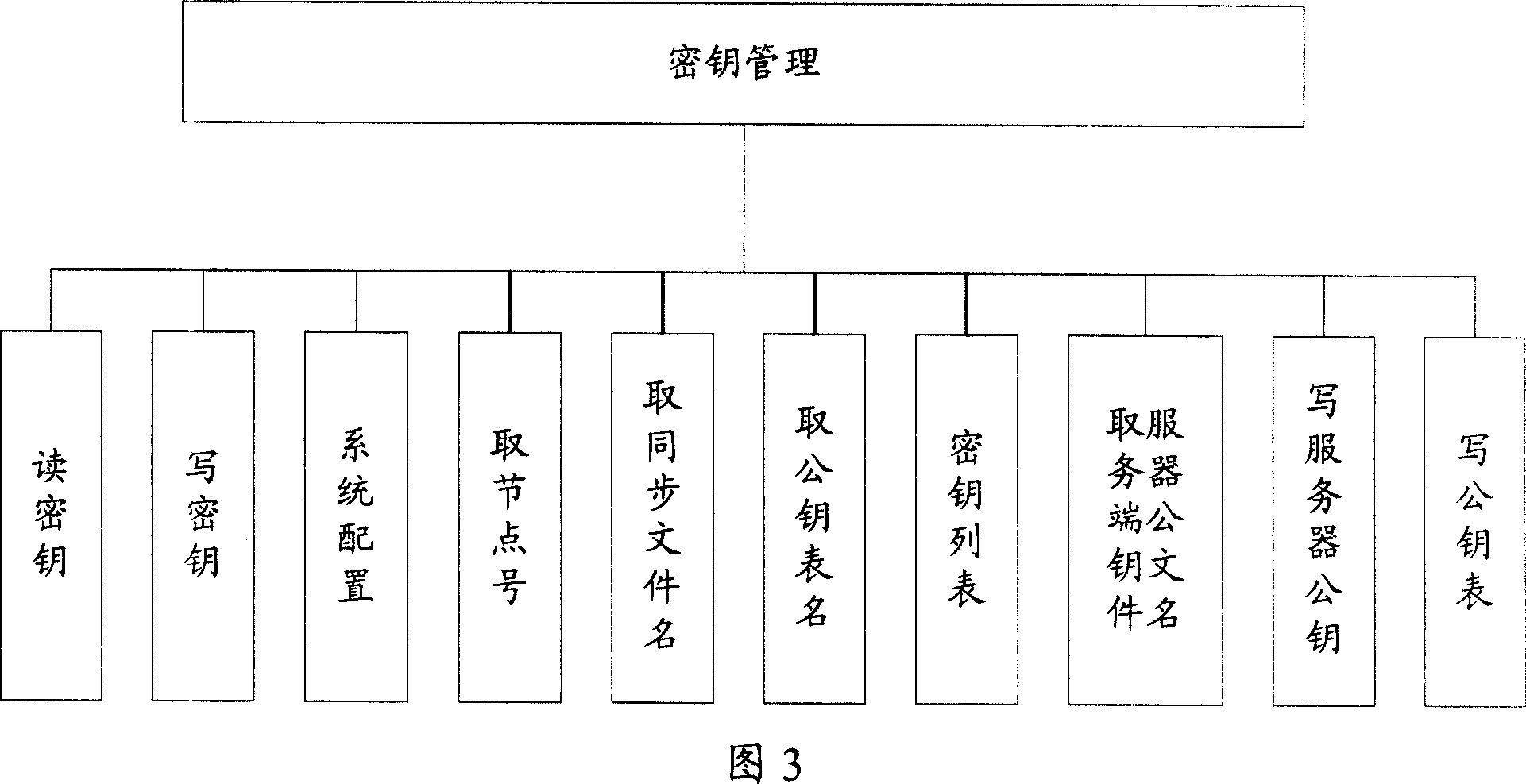
InactiveCN101043335AImplement encrypted transmissionAvoid illegal acquisitionUser identity/authority verificationError processingConfidentiality
The invention provides a control system for the information safety to solve the safe problems existed in the business system, and prevent the important data from leakage and illegal interpolation. The system includes: key management module, key negotiation module, code interface module, log management module, security management module and mistake processing module. The control system for the information safety provided by the invention can combine with the business system closely, and it is classified following the business system on the structure design, the business logic of every hierarchy has the corresponding security control to protect the every aspects of business, and the business safety technical measures cover the every aspect of business system that includes data transmission, data storage, database, files, logs and operation certification and so on, and it can assure the confidentiality, integrality, anti-aggression, usability, anti-repudiation, ID identify and authority control of business system.
Owner:CHINA CONSTRUCTION BANK
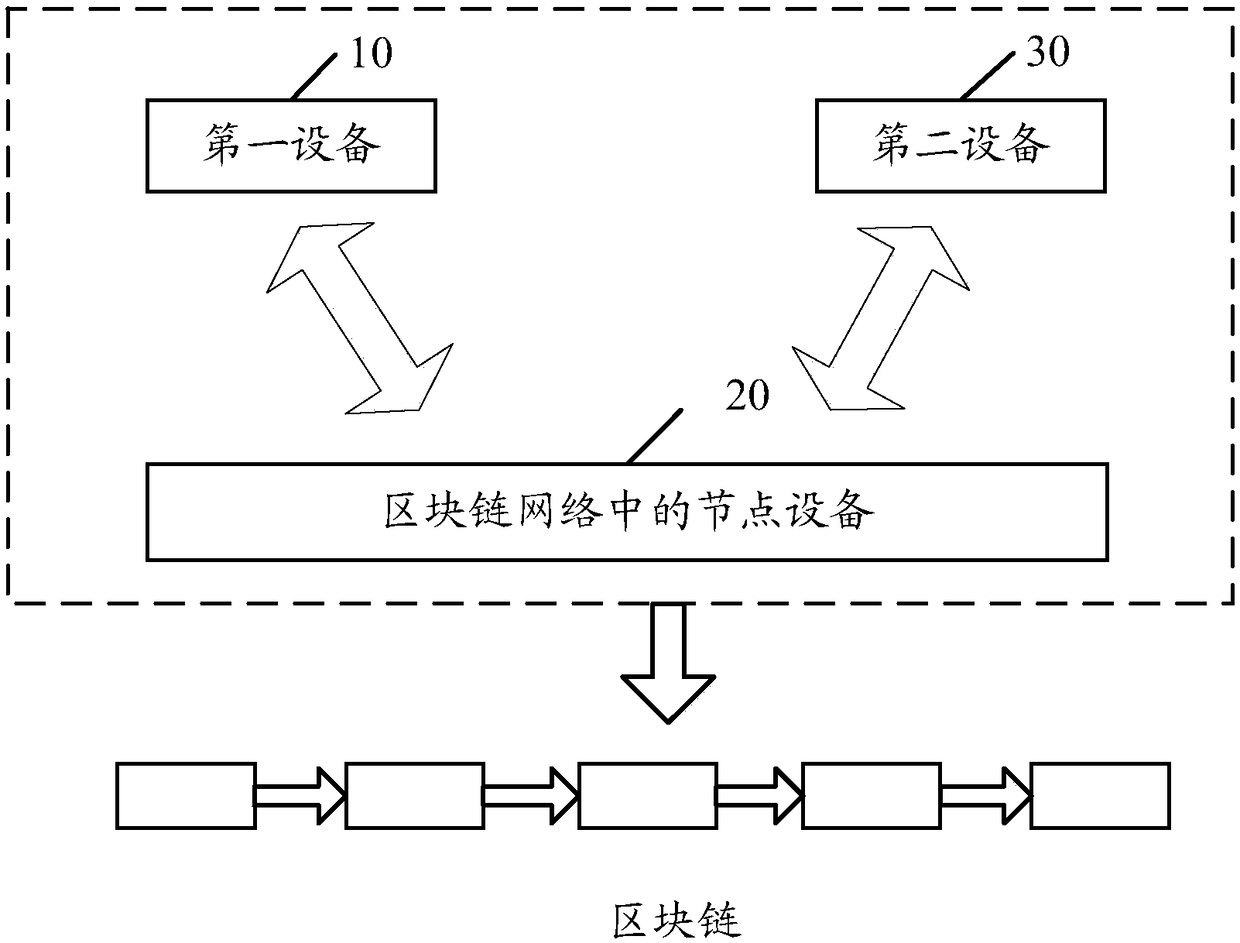
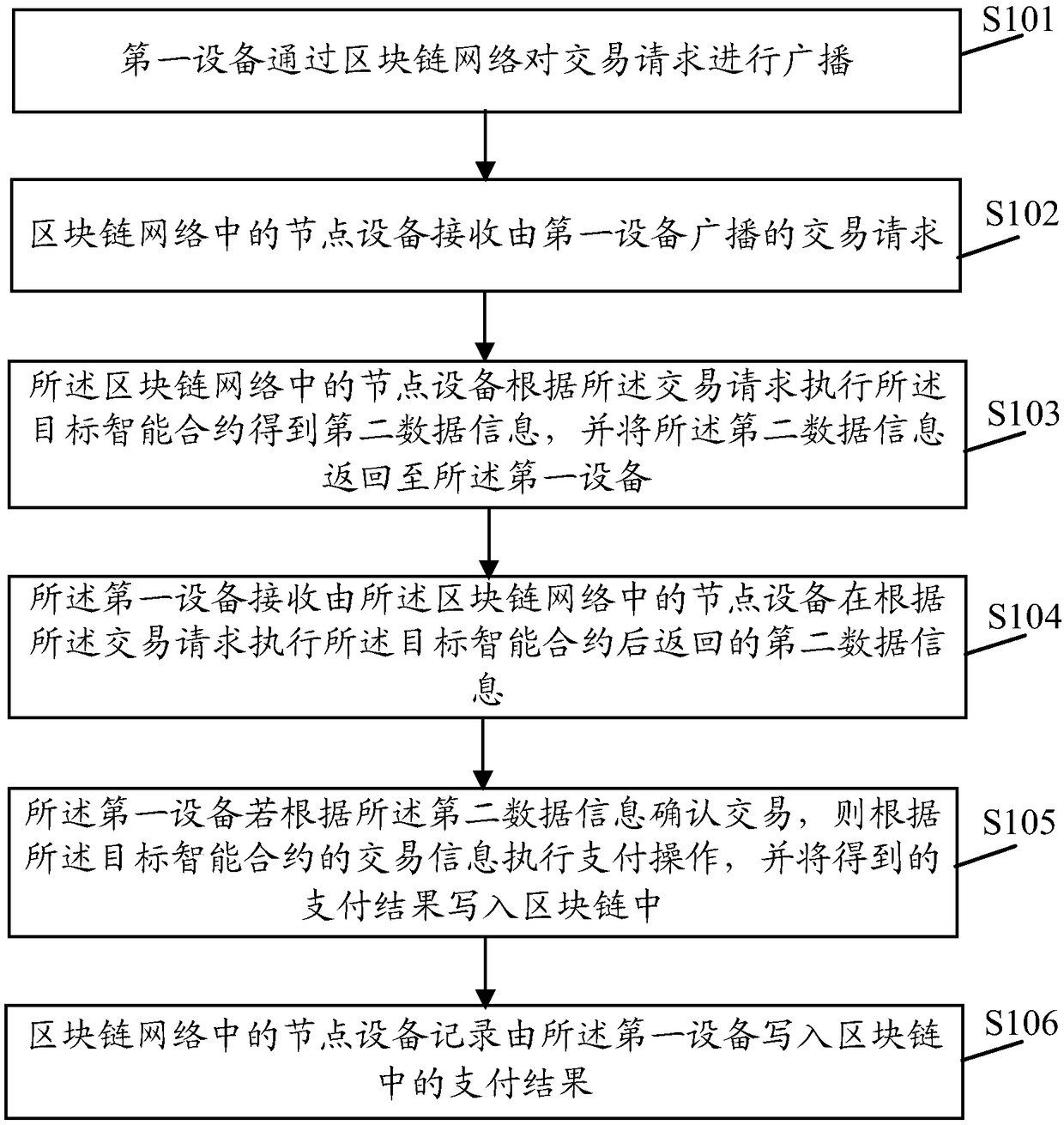
Data interaction method and device based on block chain
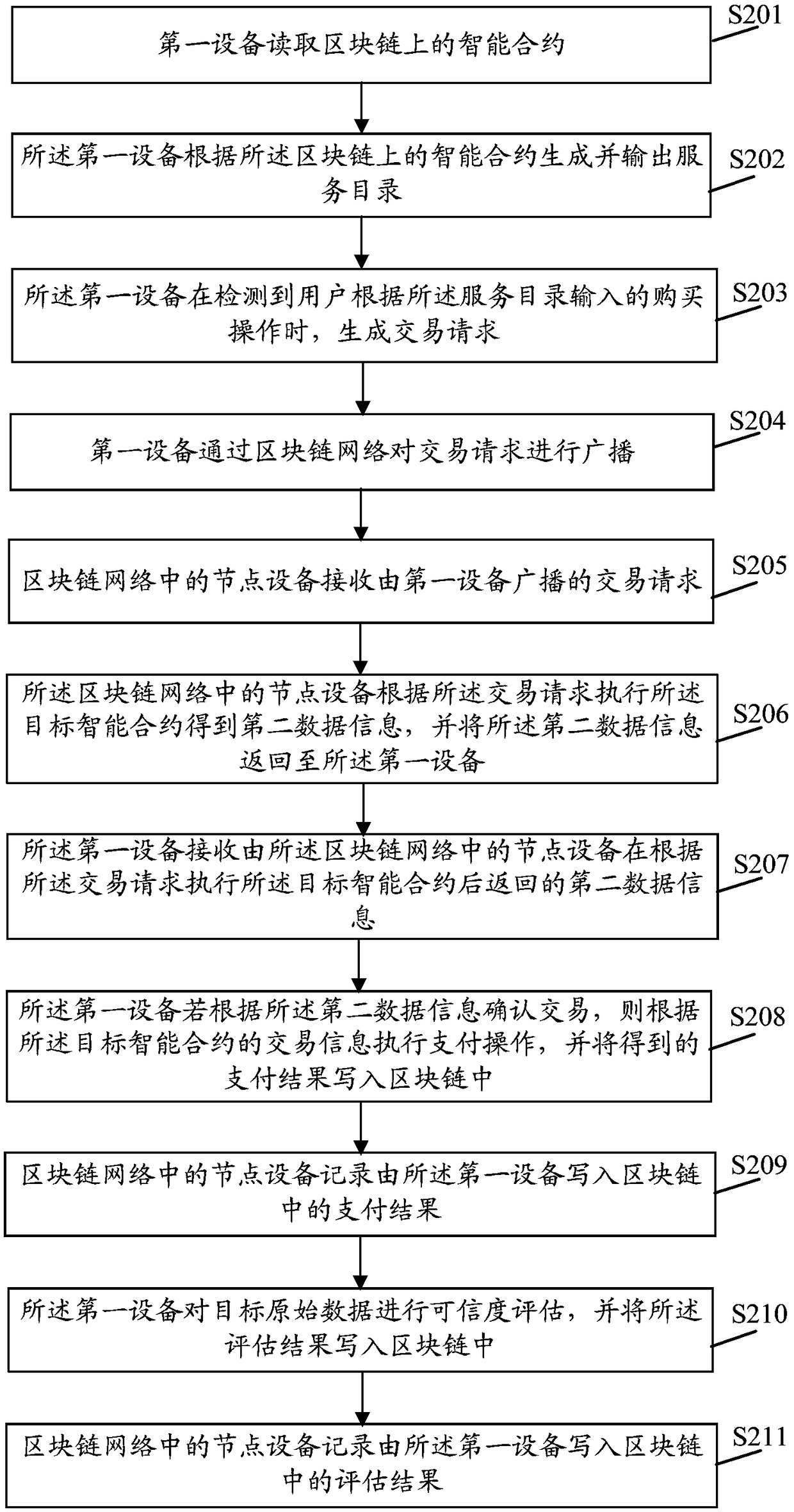
InactiveCN108647966AConvenient transactionEnsure safetyProtocol authorisationPaymentData information
The embodiment of the invention discloses a data interaction method and device based on a block chain. The method comprises the steps that a first device broadcasts a transaction request through a block chain network; the transaction request at least comprises an identifier of an address of a target intelligent protocol; the target intelligent protocol at least comprises first data information andtransaction information; the first device receives second data information returned by node devices in the block chain network after the target intelligent protocol is executed according to the transaction request; the second data information at least comprises the first data information and / or data information obtained after the first data information is processed; and if the first device confirms a transaction according to the second data information, payment operation is executed according to the transaction information in the target intelligent protocol, and the obtained payment result iswritten into the block chain. By the adoption of the data interaction method and device, the security and non-repudiation in the data transaction process can be effectively ensured.
Owner:深圳市融讯科技有限公司
Editable, linkable and non-repudiation ring signature method
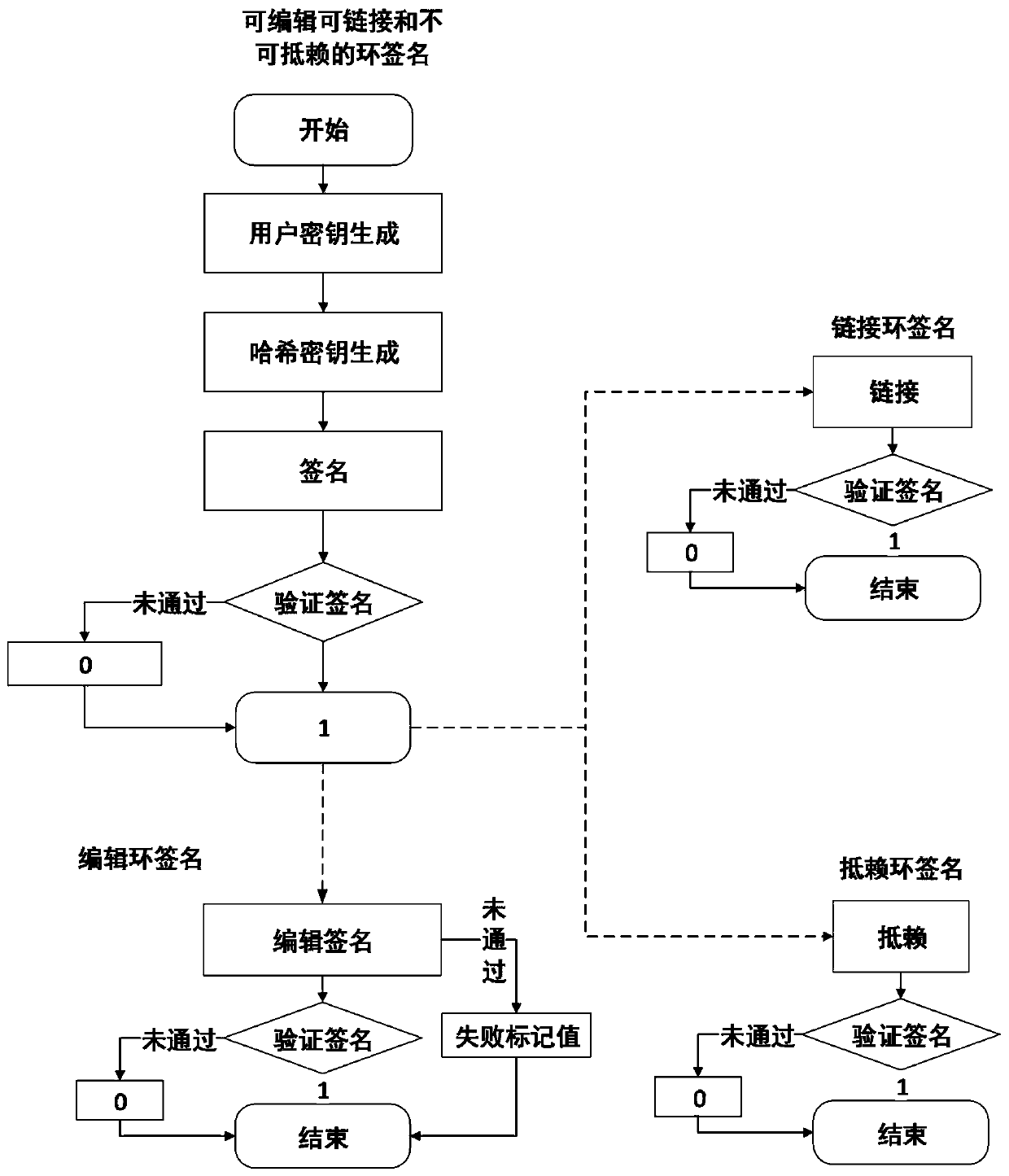
ActiveCN110071812APrivacy is not abusedAchieve traceabilityUser identity/authority verificationRing signaturePrivacy protection
The invention discloses an editable, linkable and non-repudiation ring signature method, belongs to the field of network security, and solves the problems of difficulty in revocation of a ring signature, difficulty in tracing identity information of a malicious user, capability of being authenticated by the signature after being edited, no privacy protection, no flexible authentication mechanism and the like in the prior art. The method is used for sequentially carrying out system initialization, user key generation, hash key generation and signature and providing conditional revocation identity privacy, editable and non-repudiation ring signatures. After the signature is edited, if the signature is required to be edited and whether the signature can be linked or repudiated is judged, thesignature is verified respectively, and after the verification is passed, the signature is edited and whether the signature can be linked or repudiated and the like is judged to be used for providingidentity privacy capable of being revoked, editable and non-repudiated ring signatures.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
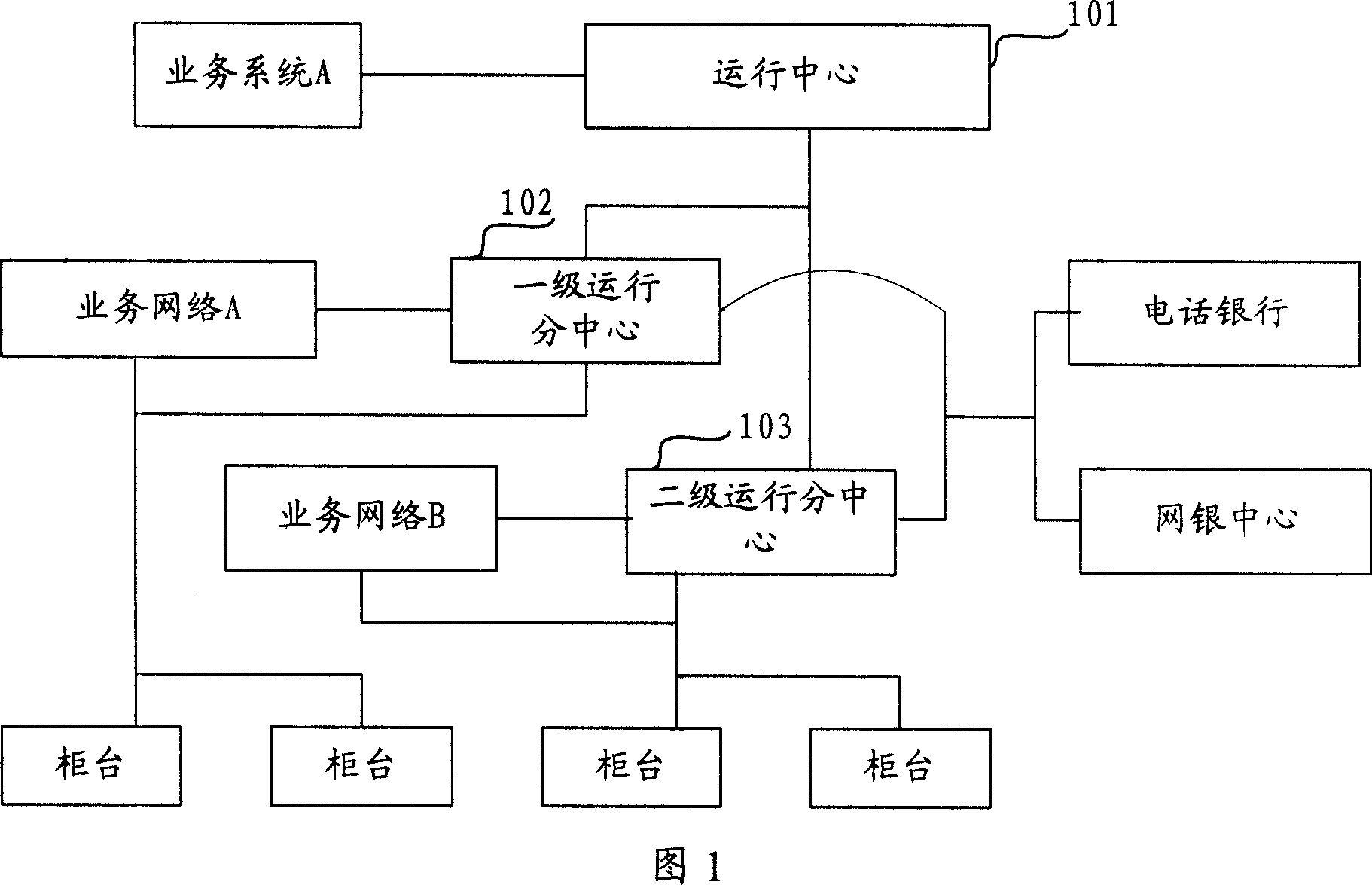
Data ciphered-mortgage transaction system, teller identification system, trans-center transaction system and method
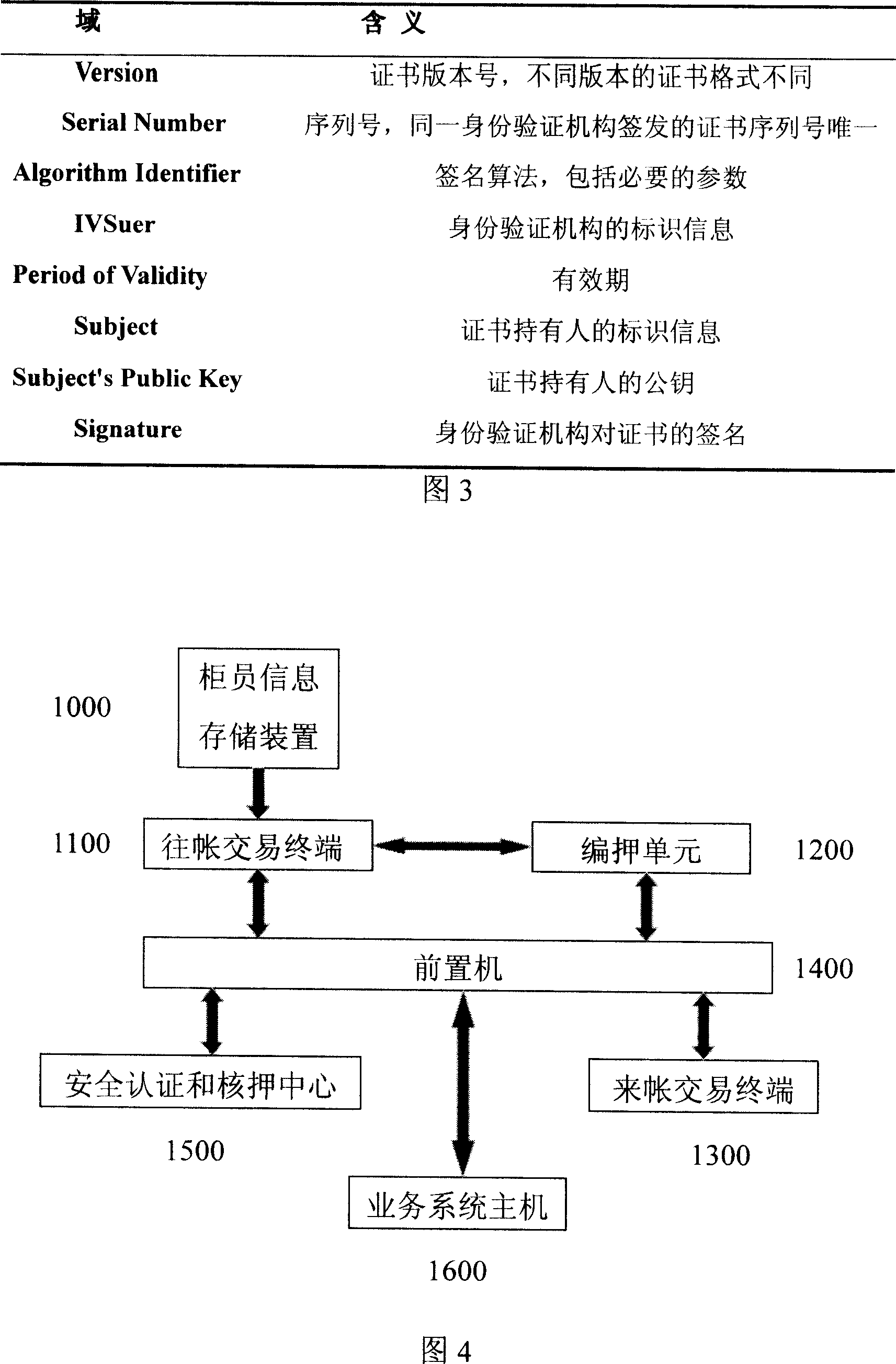
InactiveCN101145233AHigh degree of automationImprove transfer efficiencyComplete banking machinesFinanceInformation storageSecure authentication
The invention discloses a data cipher transaction system, which comprises a counter information storage device, a going-account transaction terminal, a cipher coding unit, a coming-account transaction terminal, a prepositive computer, a safety authentication and cipher check center, and a business system host. The data cipher transaction system performs authentication on the counter identity; if the authentication is passed, the invention carries out cipher coding on the transaction data; the coded cipher of the transaction data is checked in the safety authentication and cipher check center; if the cipher check is successfully done, the transaction data is sent to the coming account for treatment. The data cipher transaction system provided by the invention can improve the safety and reliability of banking transaction.
Owner:AGRICULTURAL BANK OF CHINA
Digital signature and verification method, device and system
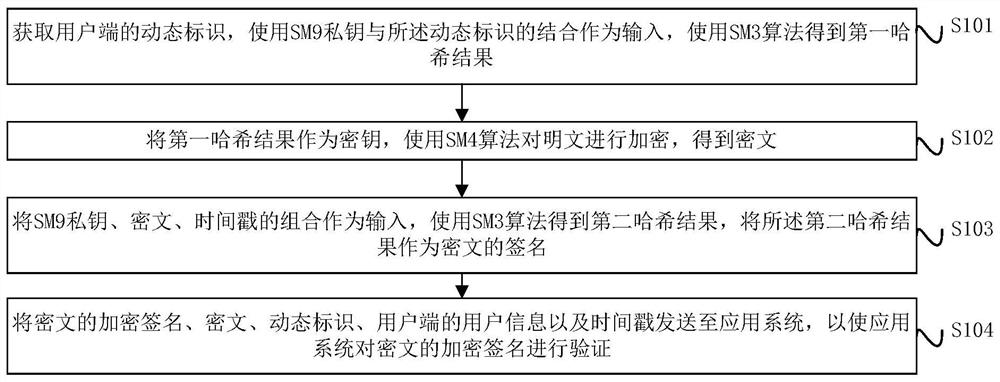
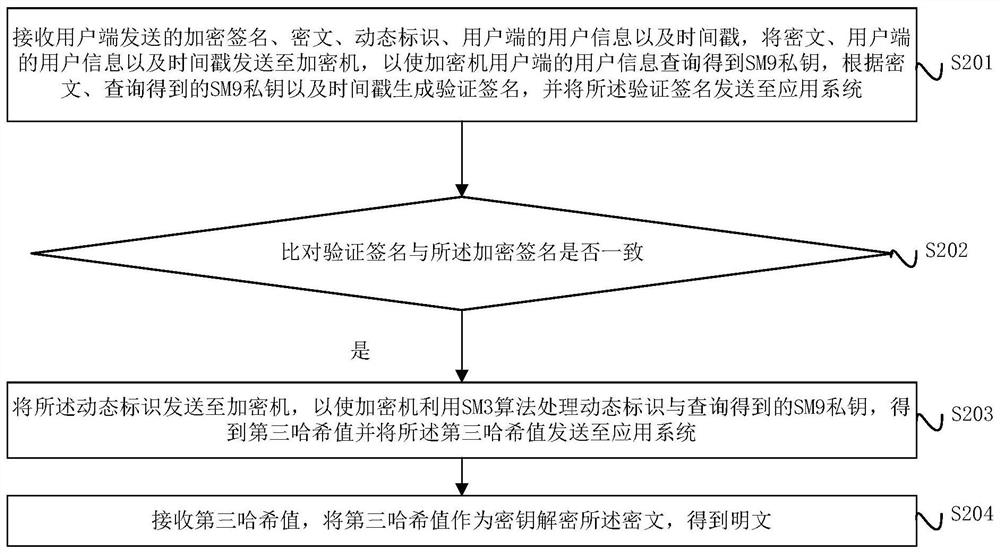
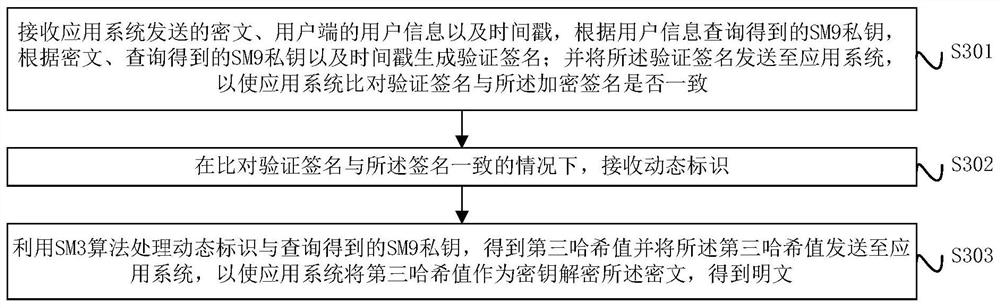
ActiveCN112688784AIncrease computing speedImprove signature efficiencyEncryption apparatus with shift registers/memoriesUser identity/authority verificationPlaintextTimestamp
The invention provides a digital signature and a verification method, device and system, and the method comprises the steps: obtaining a dynamic identification of a user side, taking the combination of an SM9 private key and the dynamic identification as an input, and obtaining a first hash result through an SM3 algorithm; taking the first hash result as a key, and encrypting the plaintext by using an SM4 algorithm to obtain a ciphertext; taking a combination of the SM9 private key, the ciphertext and the timestamp as input, obtaining a second hash result by using an SM3 algorithm, and taking the second hash result as an encrypted signature of the ciphertext; and sending the encrypted signature of the ciphertext, the ciphertext, the dynamic identifier, the user information of the user side and the timestamp to an application system, so that the application system verifies the encrypted signature of the ciphertext.
Owner:中科美络科技股份有限公司
Undeniable secure data transmission method based on block chain
ActiveCN110223064AAchieve non-repudiationUser identity/authority verificationDigital data protectionDigital signatureCiphertext
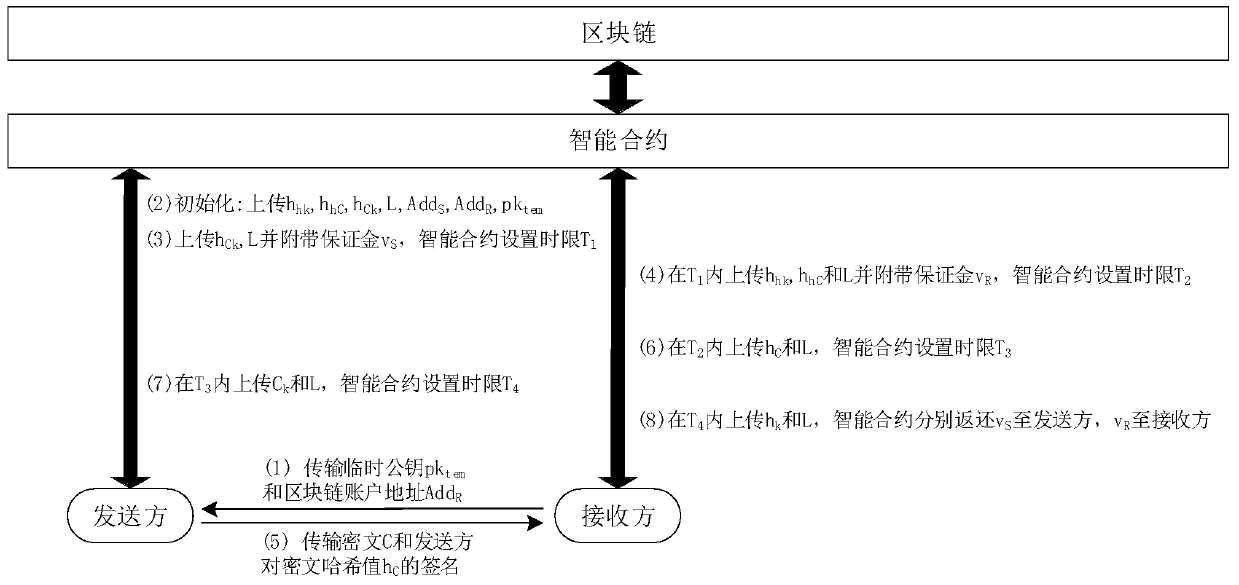
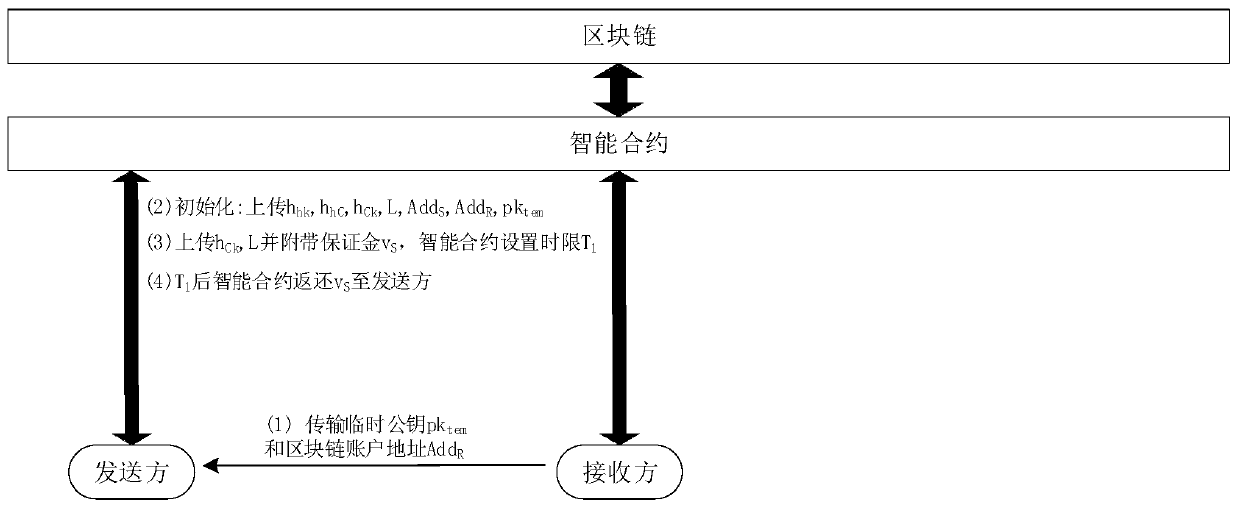
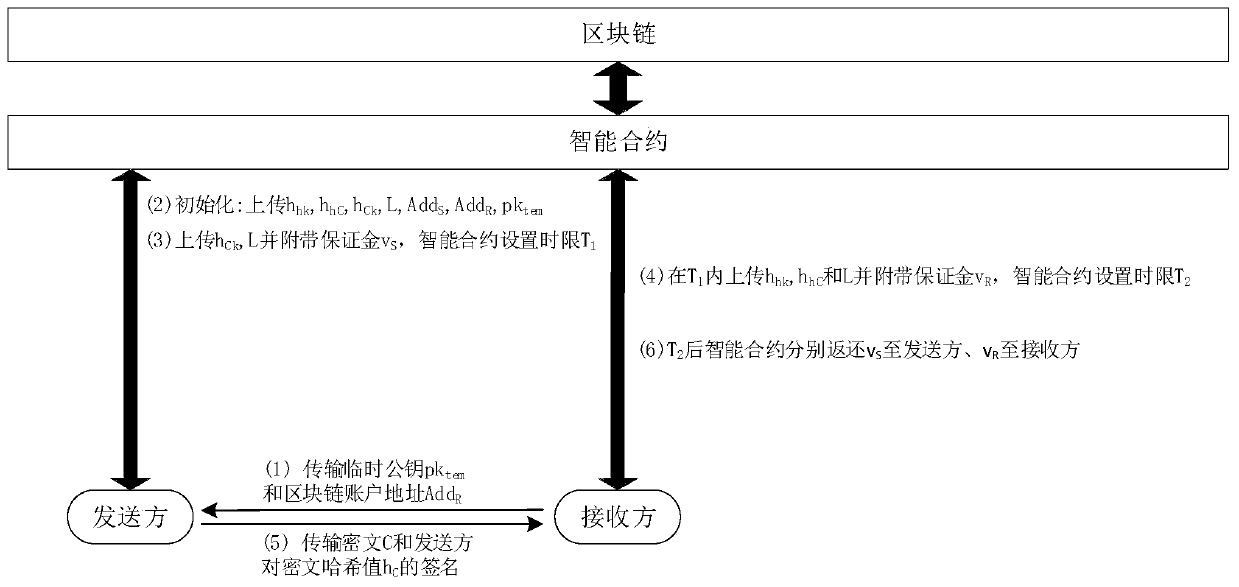
The invention discloses a non-deniable secure data transmission method based on a block chain. The method comprises the following steps that: (1) a receiver generates a temporary public and private key pair and sends a public key and a block chain account address thereof to a sender; (2) uploading initialization parameters to the intelligent contract in the sending direction; (3) the sending end pays the guarantee money to the intelligent contract; (4) receiving the deposit paid to the intelligent contract; (5) the sender sends the ciphertext and the digital signature of the ciphertext hash value to the receiver; (6) after the receiver obtains the ciphertext, a ciphertext hash value is disclosed to the intelligent contract; (7) the sending direction intelligent contract publicly uses the temporary public key to encrypt the ciphertext obtained by the secret key; and (8) the receiver obtains the ciphertext in the step (7) from the block chain, decrypts the original key by using the temporary private key and publishes the key hash value to the smart contract, and the smart contract returns the guarantee money of the two parties. The method and the device can be used for effectively realizing non-repudiation of a sender and a receiver on a transmission behavior in a secure data transmission process.
Owner:SICHUAN UNIV
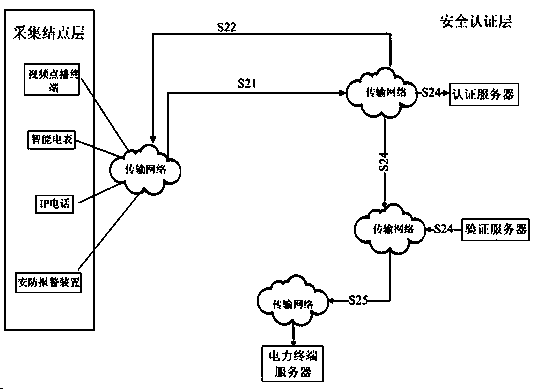
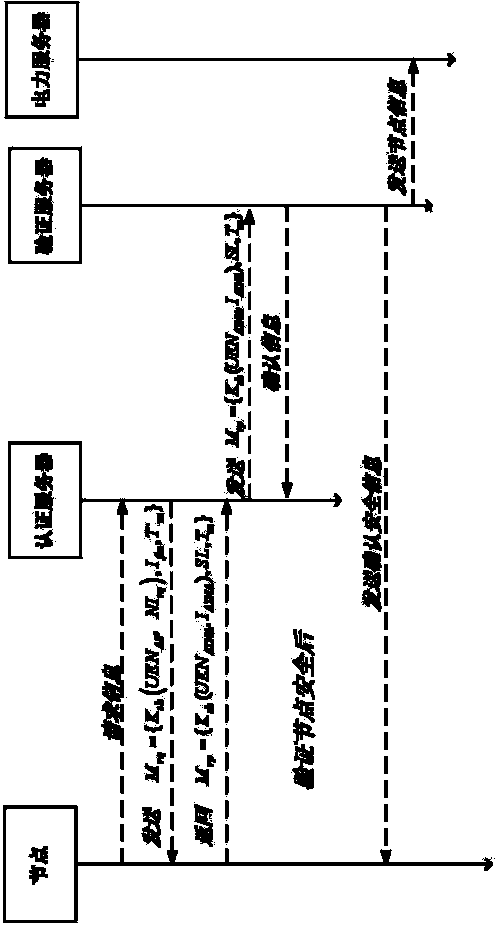
Node safety authentication method in smart grid
InactiveCN103647788AVerify accuracyAchieve non-repudiationUser identity/authority verificationNetwork deploymentExtensibility
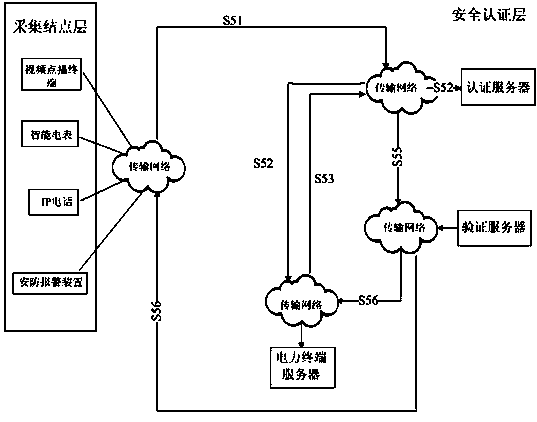
The invention provides a node safety authentication method in a smart grid. The node safety authentication method in the smart grid comprises the steps of: deploying each node in a smart grid node authentication system and presetting symmetrical private keys according to a hierarchical structure; initializing the smart grid node authentication system; authenticating nodes newly added in a sampling node layer; authenticating each server; performing information interaction on authenticated nodes and a power server and finishing node safety authentication. The node safety authentication method in the smart grid improves simplicity and extendibility of system network deployment as the smart grid node authentication system is structurally layered, reduces identity authentication frequentness of the nodes or the power server to a certain extent and increases efficiency of the whole system as a verification server is added in the system. Besides being able to verify identity of the nodes and the power server, the node safety authentication method in the smart grid also can guarantee the authentication process to be safe and efficient, and can enhance operation fluency of the whole system.
Owner:STATE GRID CHONGQING ELECTRIC POWER
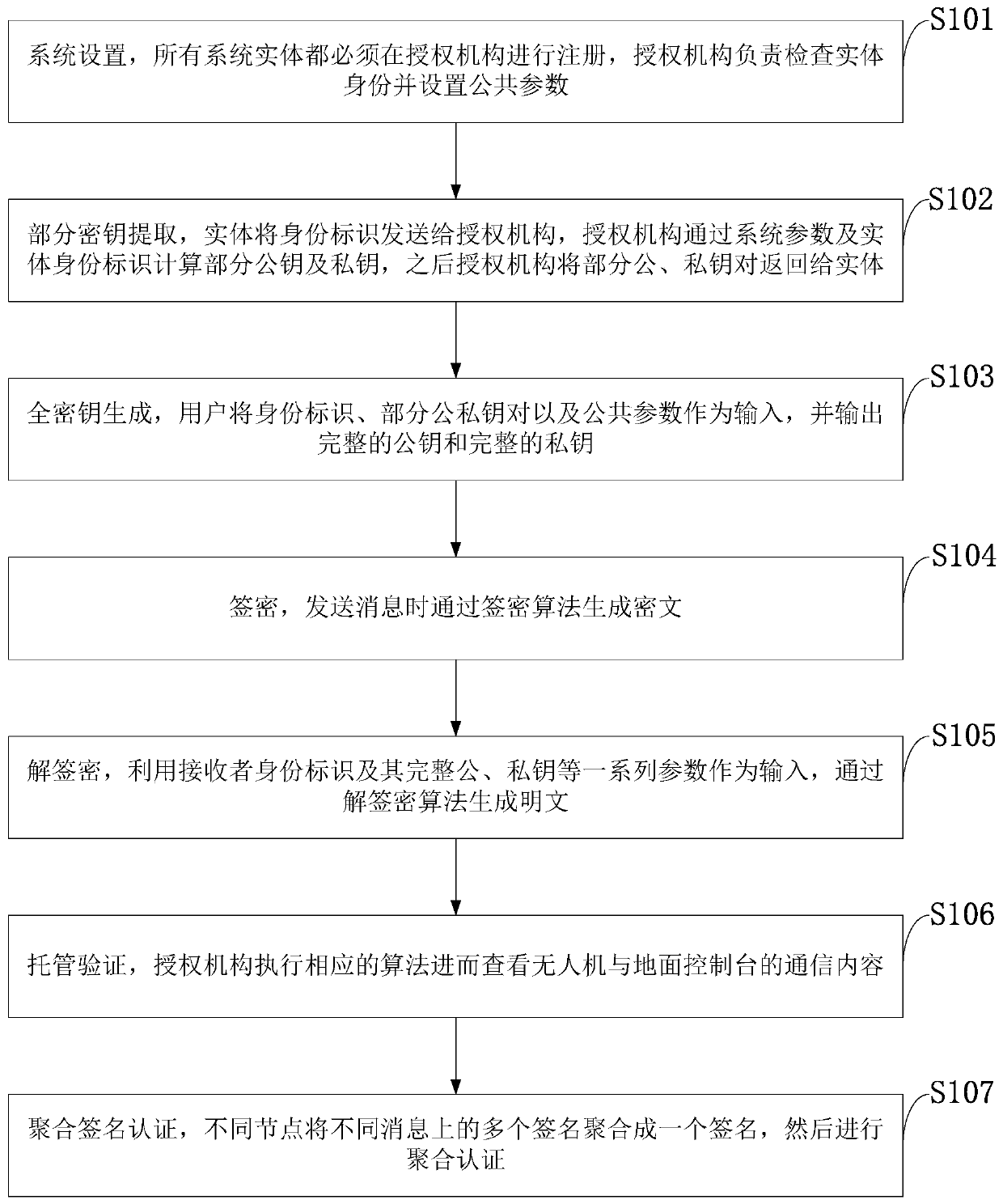
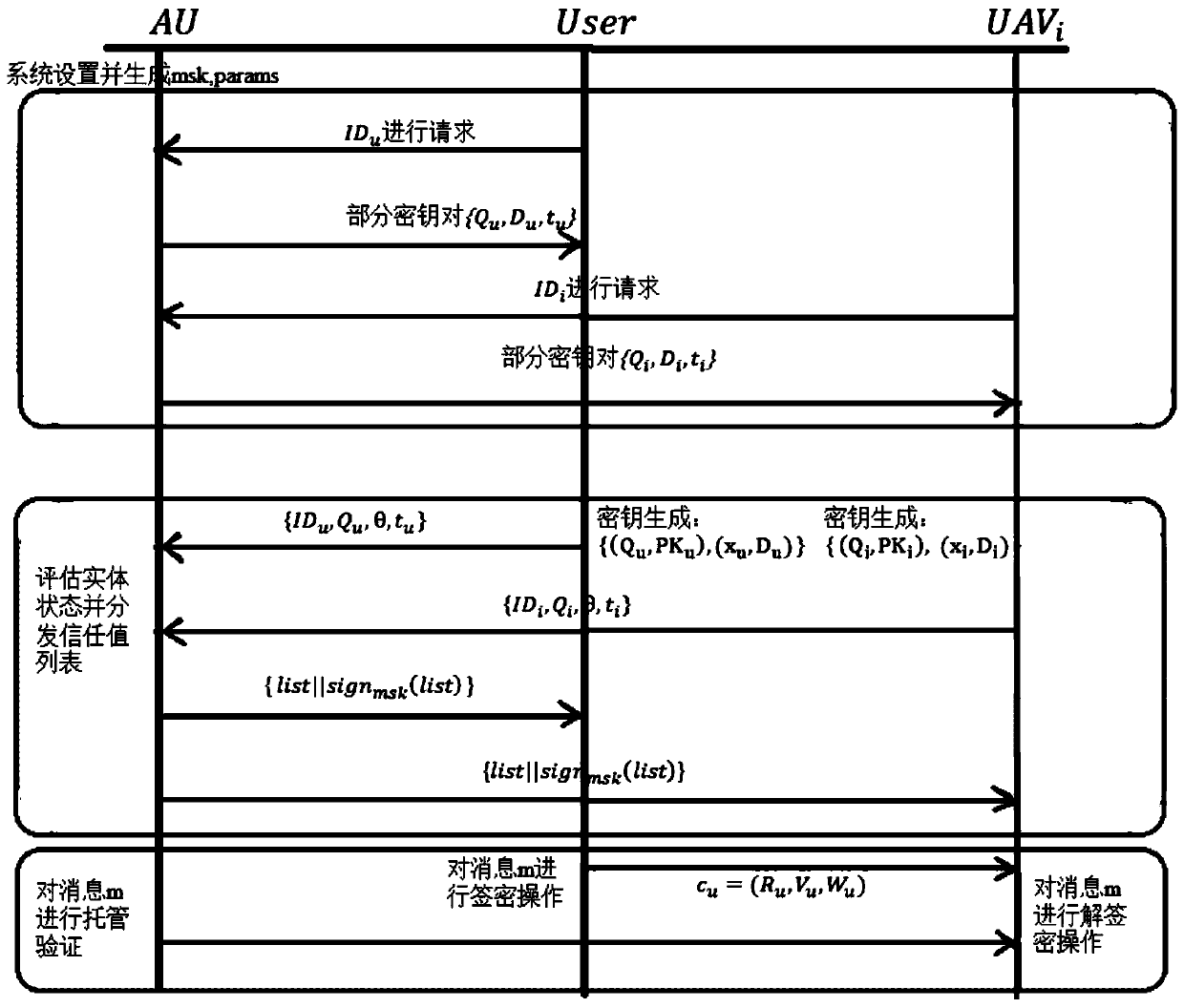
Unmanned aerial vehicle safety certifiable information communication processing method based on cloud platform
ActiveCN110690959AReduce overheadSolve redundancyKey distribution for secure communicationTransmission systemsPlaintextAlgorithm
The invention belongs to the technical field of unmanned aerial vehicle communication, and discloses an unmanned aerial vehicle safety certifiable information communication processing method and system setting based on a cloud platform. The method includes: setting a system; extracting a part of secret keys; generating a full key; generating a ciphertext through a signcryption algorithm when a message is sent; generating a plaintext through an unsigncryption algorithm by taking the receiver identity label and the parameters thereof as input; enabling the authorization mechanism to execute a corresponding algorithm so as to check and supervise the communication content of the unmanned aerial vehicle and the ground console; and enabling different nodes to aggregate a plurality of signatureson different messages into one signature for aggregation authentication, so as to reduce the authentication overhead. According to the invention, confidentiality, authentication, non-repudiation and unforgeability are realized; public key encryption and digital signature are combined, and confidentiality and identity authentication can be achieved at the same time. The authorization mechanism provides part of the key through the secure channel, and can check the access command and the location information. The control command and the position information cannot be forged under the condition ofno other part of private keys.
Owner:XIDIAN UNIV
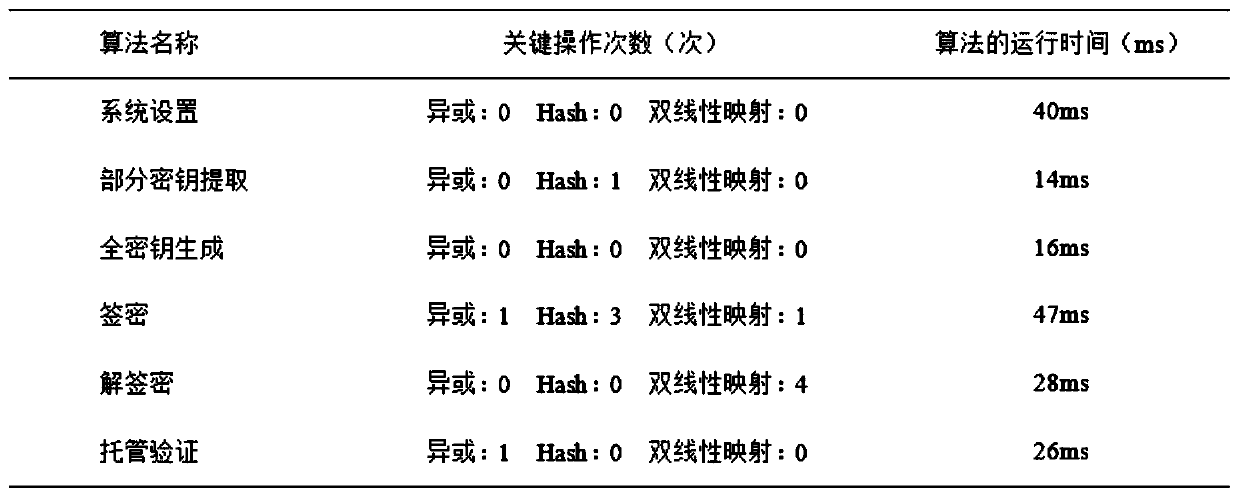
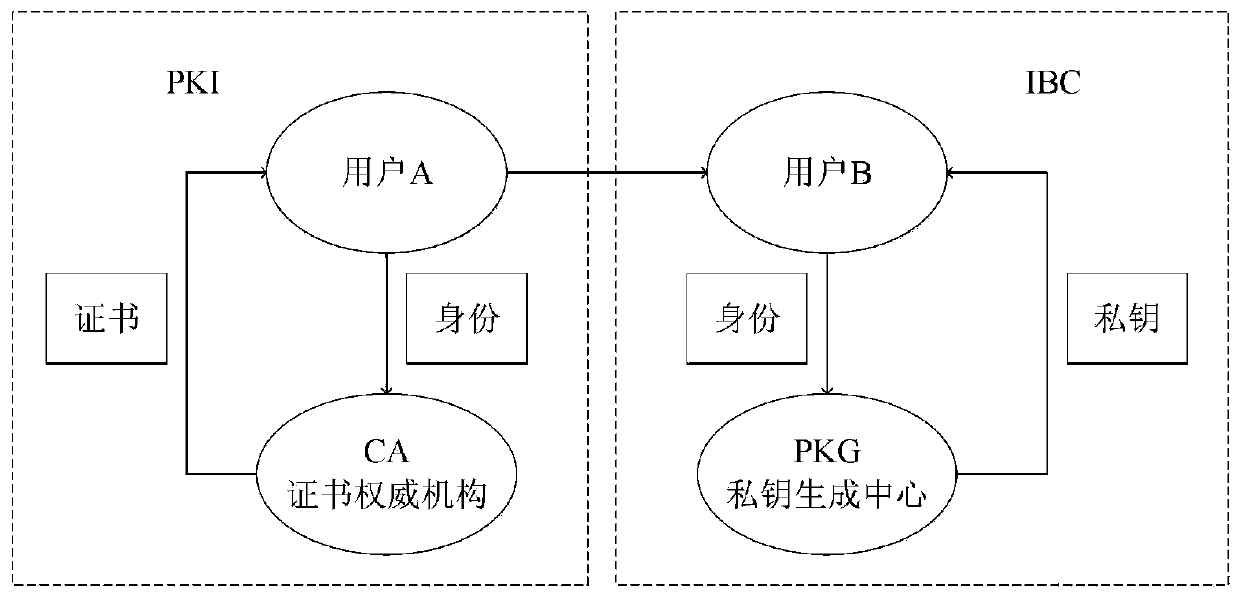
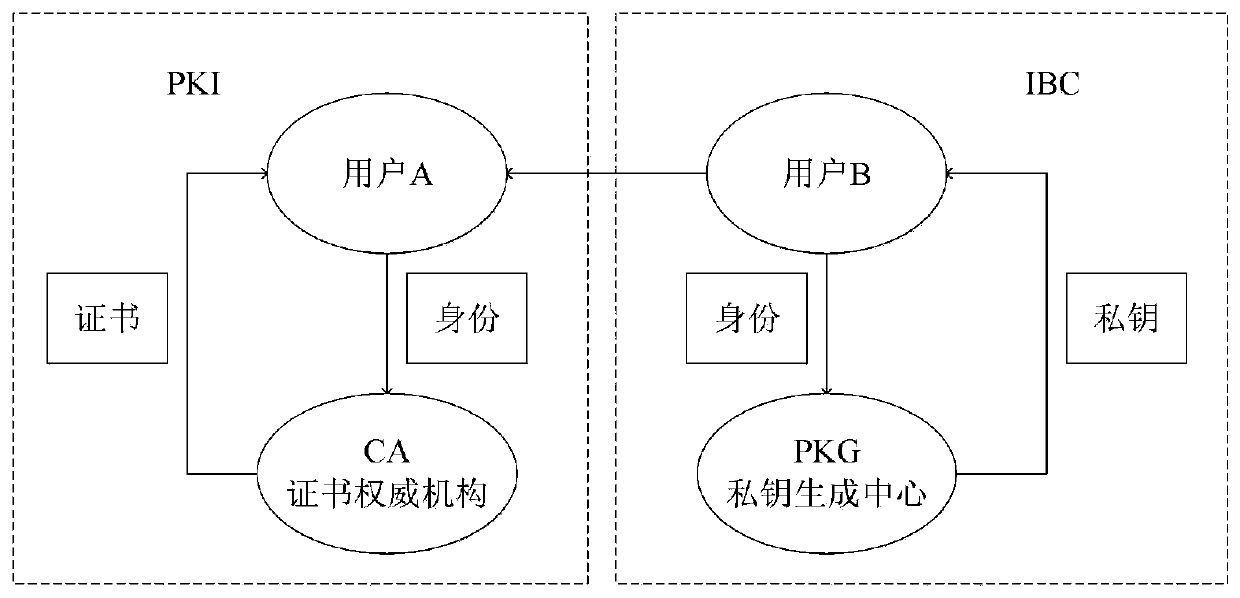
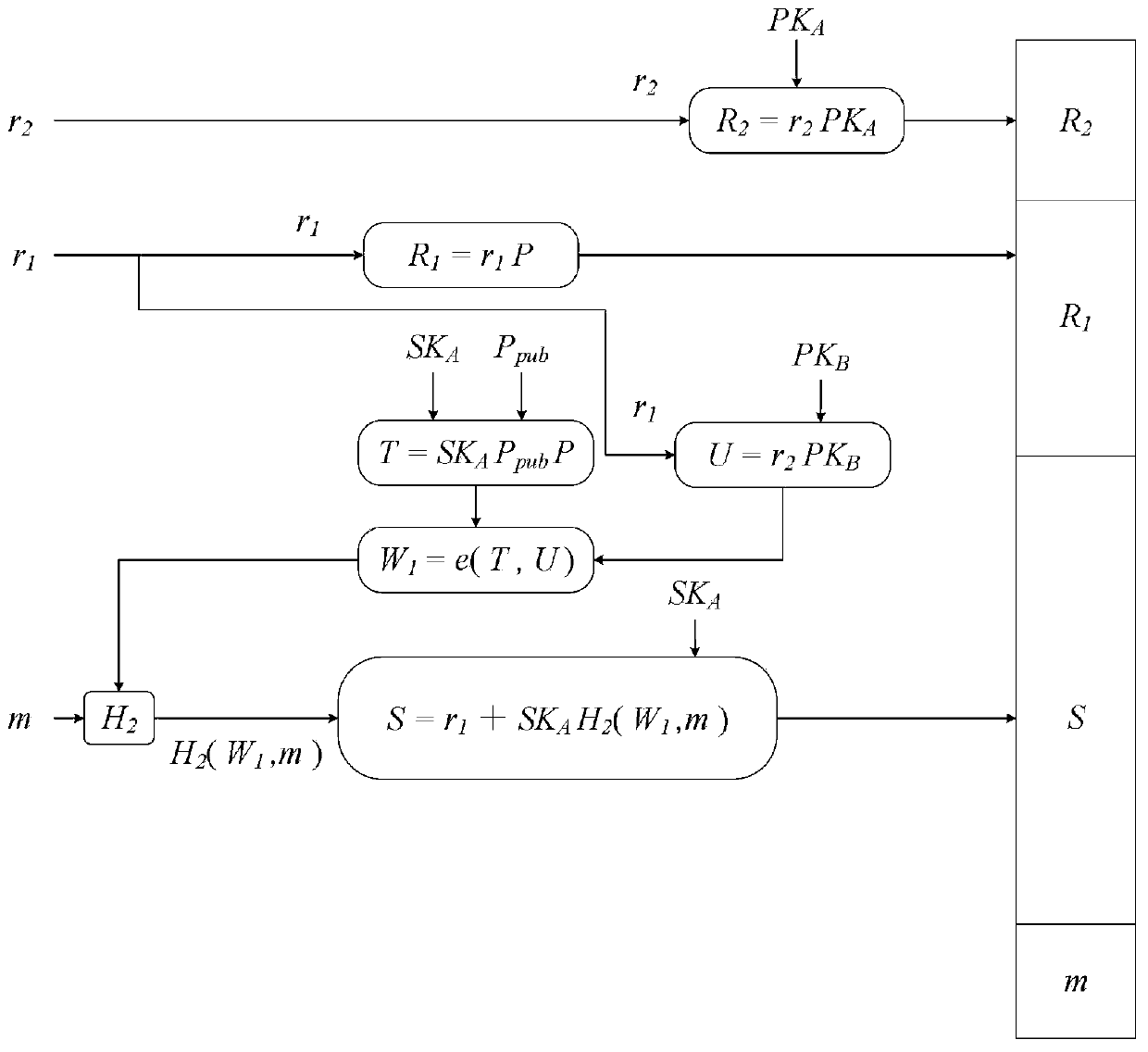
Secure bidirectional heterogeneous digital signature method between PKI and IBC
ActiveCN111342973AManagement issues do not existImplement digital signatureUser identity/authority verificationInternet privacyDigital signature
The invention discloses a secure bidirectional heterogeneous digital signature method between a PKI and an IBC. System parameters are generated through a private key generation center, and the systemparameters are disclosed; the user in the public key infrastructure environment and the user based on the identity encryption environment generate a public key and a private key respectively; whereinthe user in the public key infrastructure environment is a signer, the user based on the identity encryption environment is a verifier, the signer generates a signature and sends the signature to theverifier, and the verifier verifies the signature, passes the verification and accepts the message, otherwise, refuses to accept the message; wherein the user based on identity encryption is a signer,the user in the public key infrastructure environment is a verifier, the signer generates a signature and sends the signature to the verifier, and the verifier verifies the signature, passes the verification and accepts the message, otherwise, refuses to accept the message. According to the invention, the safety, correctness, non-repudiation and unforgeability of communication between the publickey infrastructure and the user based on the identity encryption environment are protected, and the safety and privacy requirements are met.
Owner:SOUTH CENTRAL UNIVERSITY FOR NATIONALITIES
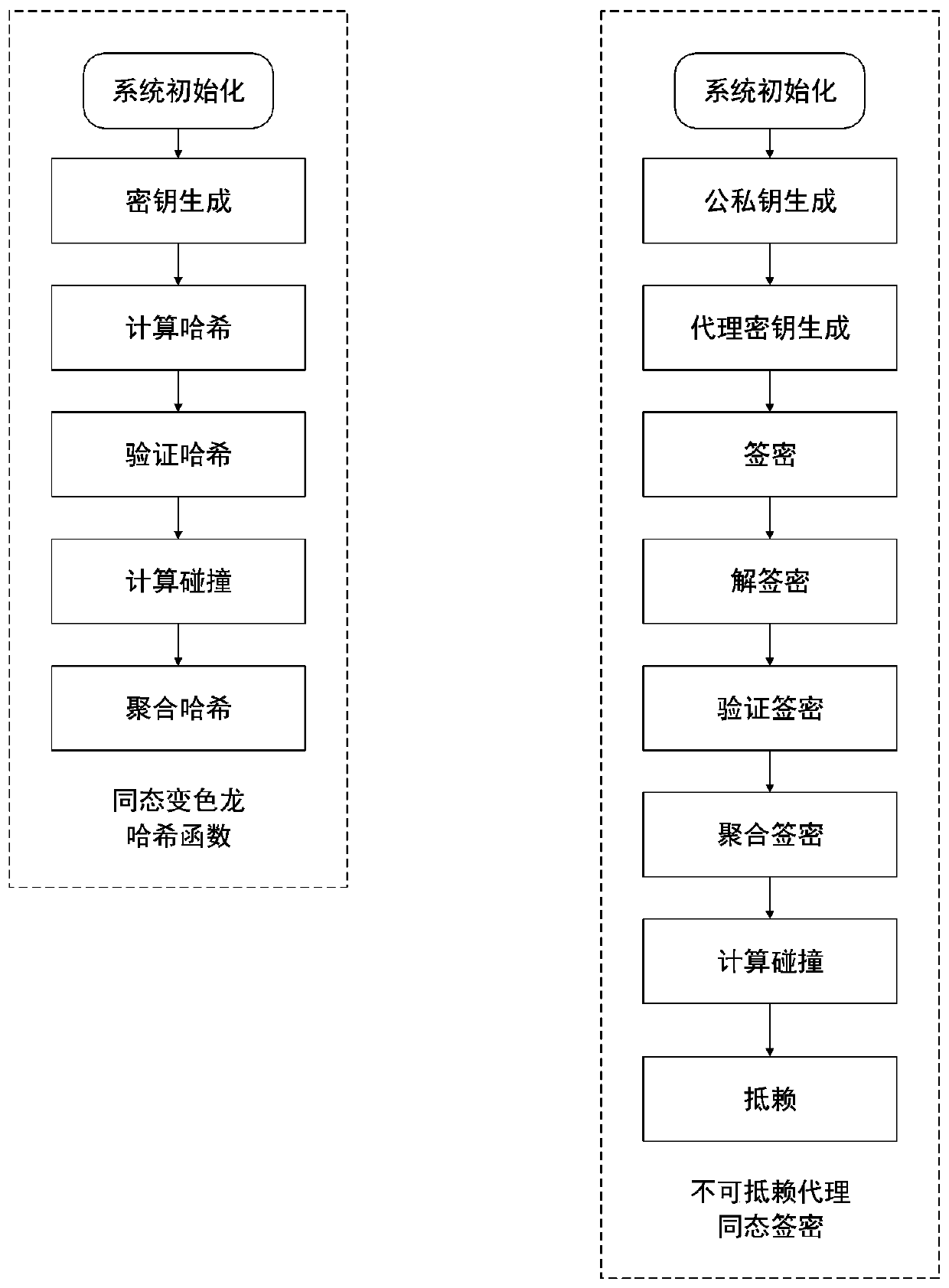
Hash calculation method and signcryption method based on homomorphic chameleon Hash function
ActiveCN110086599AComputationally efficientFunctionalKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionSurrogate key
The invention discloses a Hash calculation method and a signcryption method based on a homomorphic chameleon Hash function. According to the provided homomorphic chameleon hash function, a chameleon hash value result adopts a logarithm form, a signcryption result based on the hash in the signcryption method is also a logarithm form, so that the homomorphic property is achieved, the homomorphic aggregation can be conducted in hash calculation, hash is more efficiently calculated, and the homomorphic chameleon hash function has both the homomorphic state and the key leakage prevention characteristics. The signcryption method is realized on the basis of the homomorphic chameleon hash function, the homomorphic aggregation signcryption ensures the homomorphism, the system public parameters generated by the system initialization are used together by the chameleon hash function and the signcryption, and two password schemes share one set of system parameters, so that multiple function effectscan be realized under one set of shared system parameters, and multiple functions are supported under the same framework. Secondly, the proxy key generation and proxy re-signature steps realize the proxy re-signature, and the non-repudiation is realized through a repudiation step.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
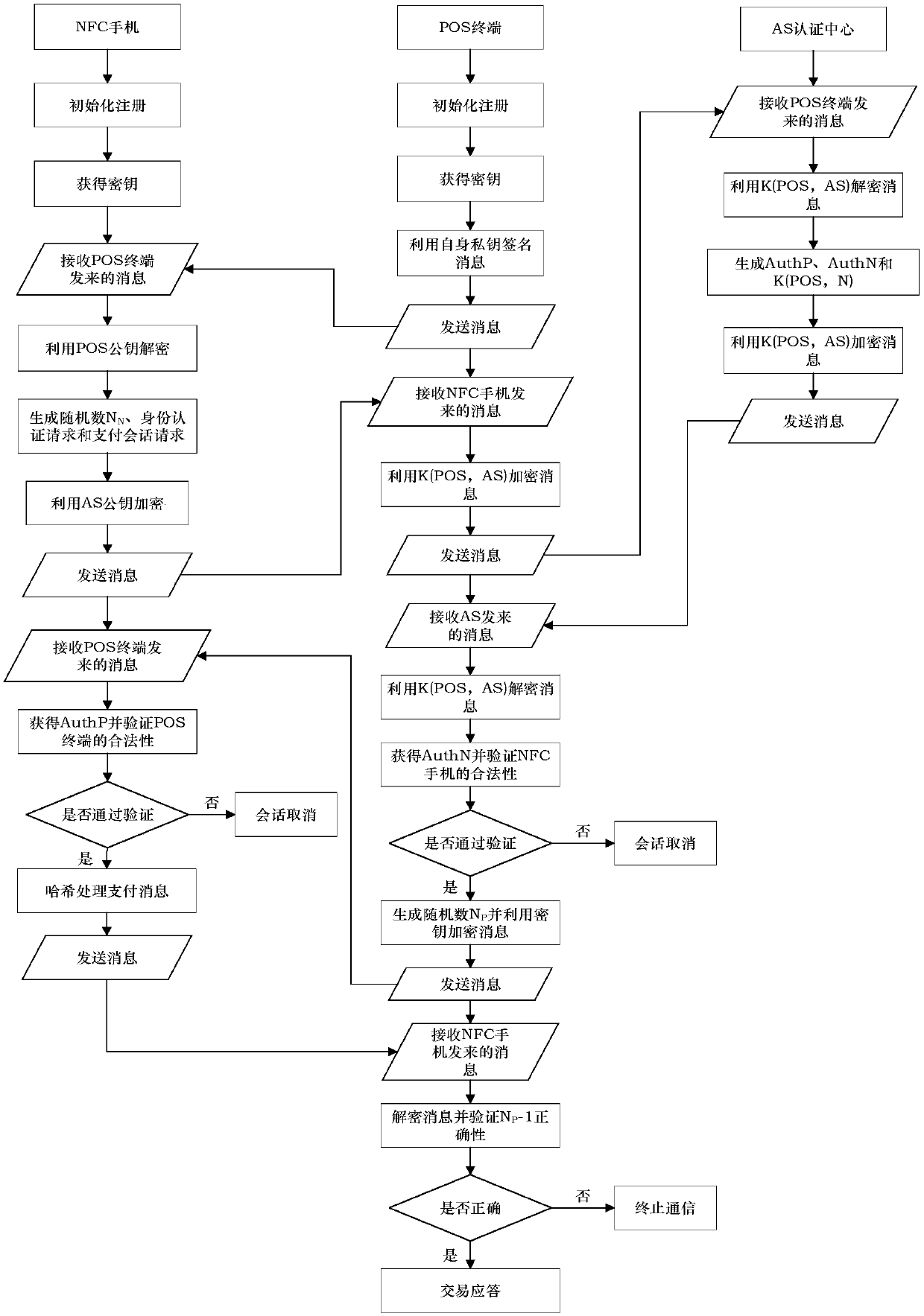
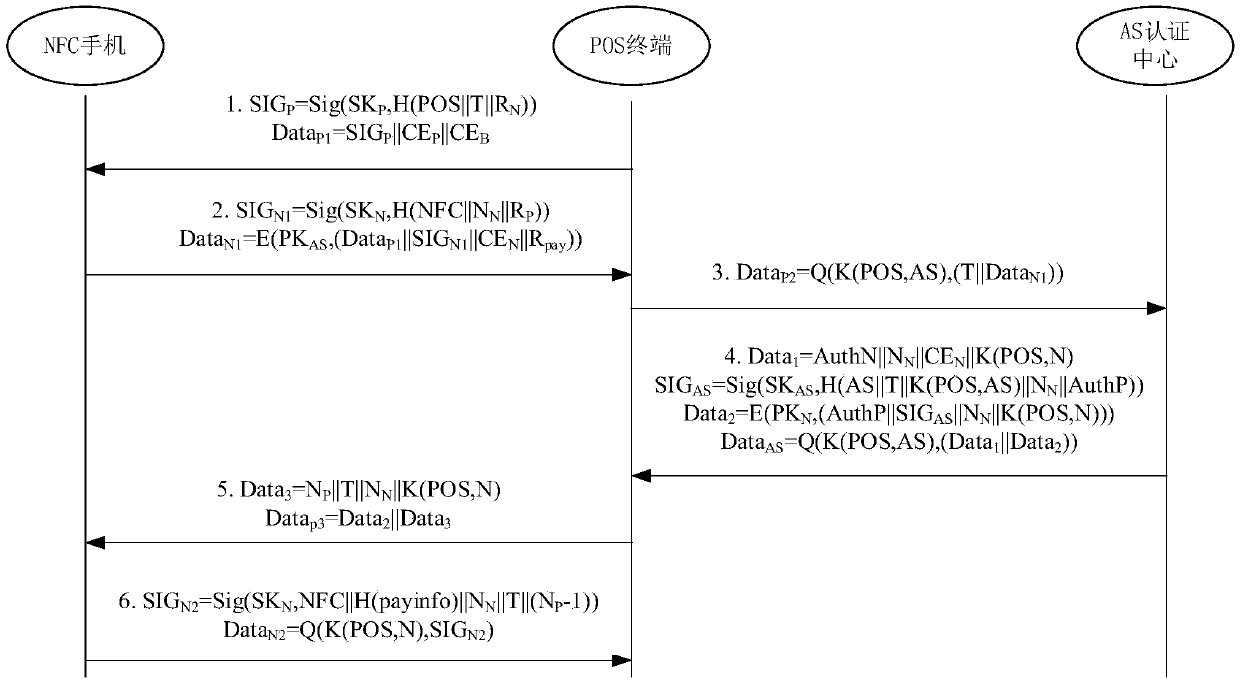
Mobile transaction privacy protection method based on bidirectional identity authentication of near field communication
ActiveCN107679847ALow hardware requirementsEnhanced anonymityUser identity/authority verificationPoint-of-sale network systemsPayment transactionPrivacy protection
The invention discloses a mobile transaction privacy protection method based on bidirectional identity authentication of near field communication (NFC). The method includes a first step and a second step. The first step is an initial registration stage in which an NFC mobile phone and a POS terminal request for registration by sending the identity information thereof to an authentication server AS, so as to get a public and private key pair and a related trusted certificate. The second step is bidirectional identity authentication between the NFC mobile phone device and the POS terminal. Identity authentication between the NFC mobile phone device and the POS terminal is carried out using a shared key generated by AS. Payment transaction can be conducted only after the two parties of communication are authenticated, and the legitimacy of the identity of the two parties is ensured. The method greatly guarantees the privacy of communication data between the two parties.
Owner:GUANGDONG UNIV OF TECH
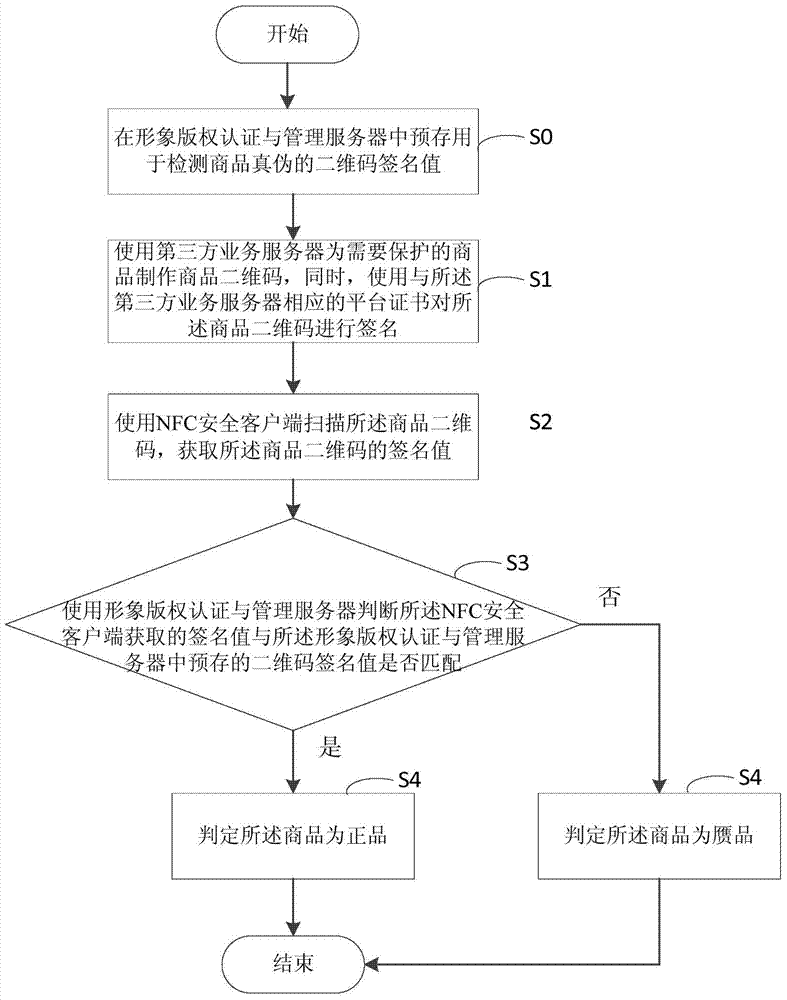
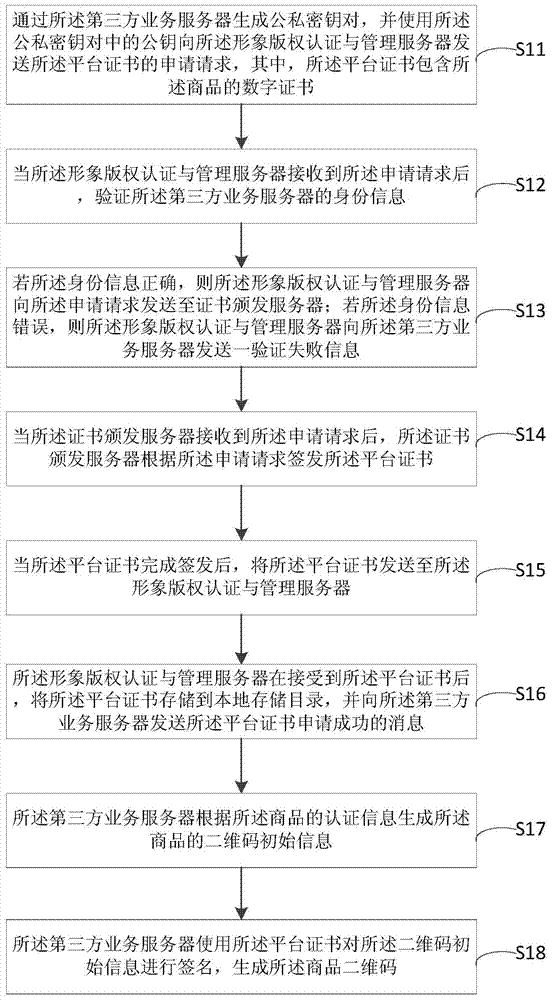
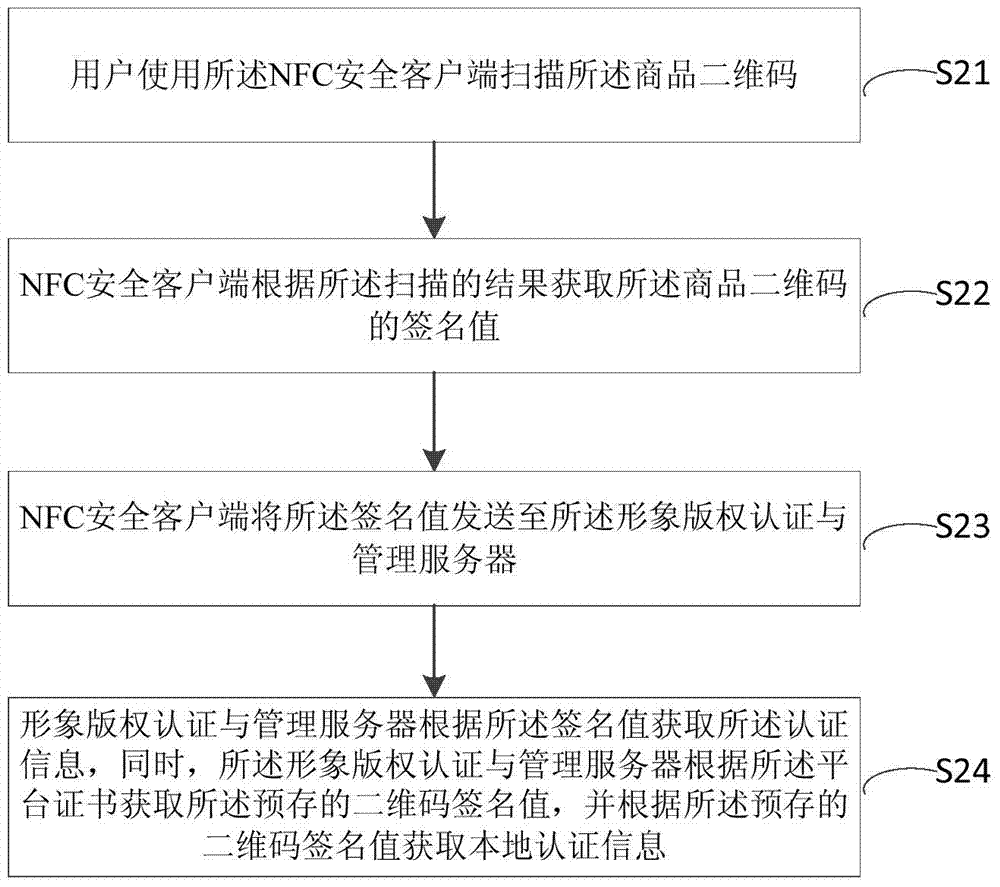
Commodity authenticity detecting method and system based on two-dimension code
ActiveCN104732400AProtection of legal rightsAchieve protectionDigital data authenticationCommerceThird partyData source
The invention discloses a commodity authenticity detecting method and system based a two-dimension code. The method comprises the steps that a third party service server is used for manufacturing the commodity two-dimension code for a commodity, and meanwhile the commodity two-dimension code is signed through a platform certificate corresponding to the third party service server; an NFC safety client side is used for scanning the commodity two-dimension code, and a signature value of the commodity two-dimension code is obtained; whether the signature value obtained by the NFC safety client side is matched with the two-dimension code signature value prestored in an image copyright authentication and management server or not is judged through the image copyright authentication and management server; if the signature value obtained by the NFC safety client side is matched with the two-dimension code signature value prestored in the image copyright authentication and management server, it is judged that the commodity is an authentic product. The legal right of commodity manufacturers is protected from a data source, data credibility and safety of data through the secret key technology, the NFC technology and the two-dimension code technology.
Owner:卓望数码技术(深圳)有限公司
Data encryption processing method for performing signature verification on application program interface
PendingCN114553416AStrengthen safe and orderly useAchieve non-repudiationKey distribution for secure communicationUser identity/authority verificationProgramming languageApplication procedure
A data encryption processing method for performing signature verification on an application program interface comprises the following steps: before a client of an application program sends a request to a corresponding server interface, firstly obtaining an exclusive asymmetric key through a server, thereby ensuring the security of the server accessing the client; when a client initiates an interface request to a corresponding server interface, a generated symmetric key is matched with a hash algorithm to encrypt data of a request body and generate a signature body of the request body, the server forms a signature verification body by using received request body parameters through the same encryption algorithm, and the signature body is verified through the signature and signature verification process. The anti-repudiation of the data original issuing behavior and the anti-repudiation of the data receiving behavior are realized; according to the invention, the non-repudiation of data request and transmission is realized by carrying out the encryption processing of signature verification on the data receiving and transmitting voucher; the safe and orderly use of the application program interface is enhanced, and the credibility, the safety and the traceability of the original request interface of the application program are ensured.
Owner:北京友普信息技术有限公司
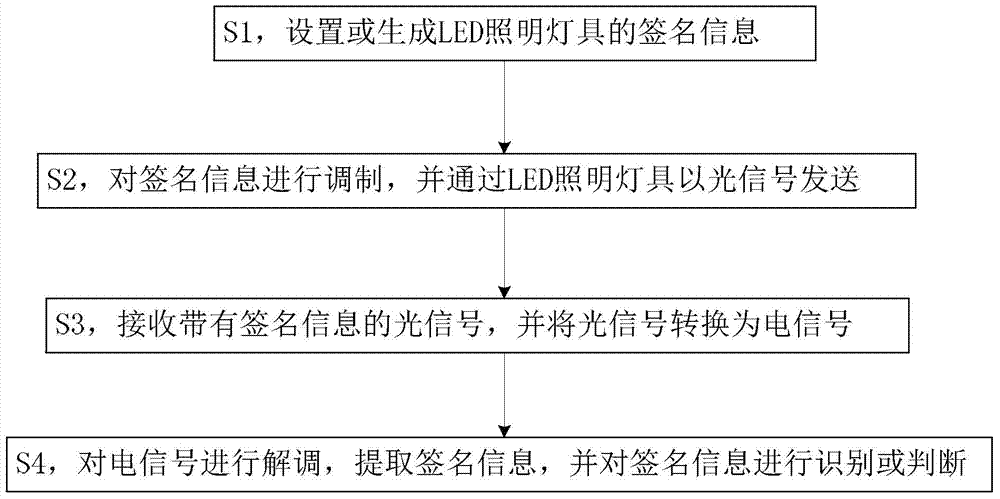
LED lighting lamp identification method, LED lamp, verification device and system
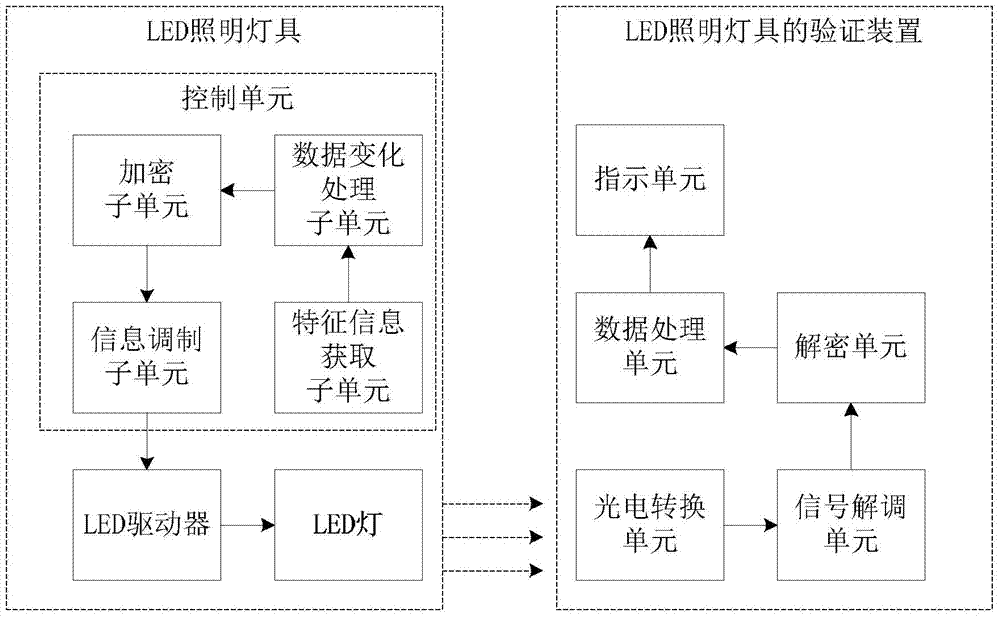
InactiveCN104506246AAchieving Security and ReliabilityGood economic and social benefitsClose-range type systemsElectromagnetic transmission optical aspectsLed driverVIT signals
The invention discloses an LED lighting lamp identification method, a lamp, a verification device and a system. The method comprises the steps that S1, signature information of the LED lighting lamp is generated; S2, the signature information is modulated and transmitted in the mode of an optical signal via the LED lighting lamp; S3, the optical signal with the signature information is received, and the optical signal is converted into an electric signal; and S4, the electric signal is demodulated, the signature information is extracted and the signature information is identified or judged. The lamp comprises a control unit, an LED driver and an LED lamp. The verification device comprises a photoelectric conversion unit, a signal demodulation unit and a digital processing unit. The system comprises the LED lighting lamp and the verification device of the LED lighting lamp. Judgment of authenticity of the lamp is realized, and characteristics that optical signal transmission is not affected by electromagnetic interference and has no penetrability are utilized so that reliability and security of signature information transmission are realized. Besides, additional cost is not increased or only a small part of cost is increased. The LED lighting lamp identification method can be widely applied to various LED lighting lamp identification systems.
Owner:SHENZHEN JIUZHOU OPTOELECTRONICS TECH
Method for utilizing fingerprint to improve information transmission security
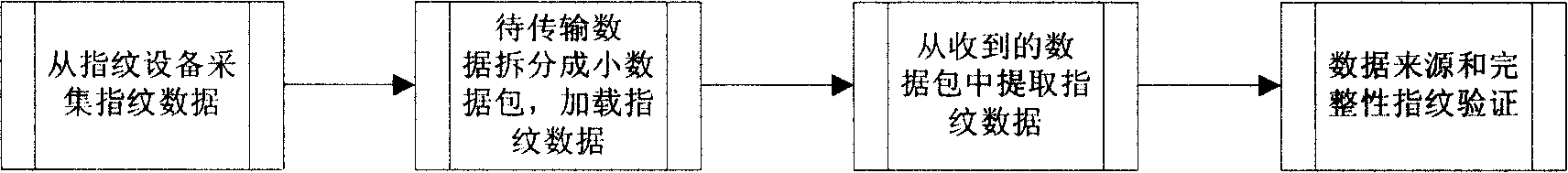
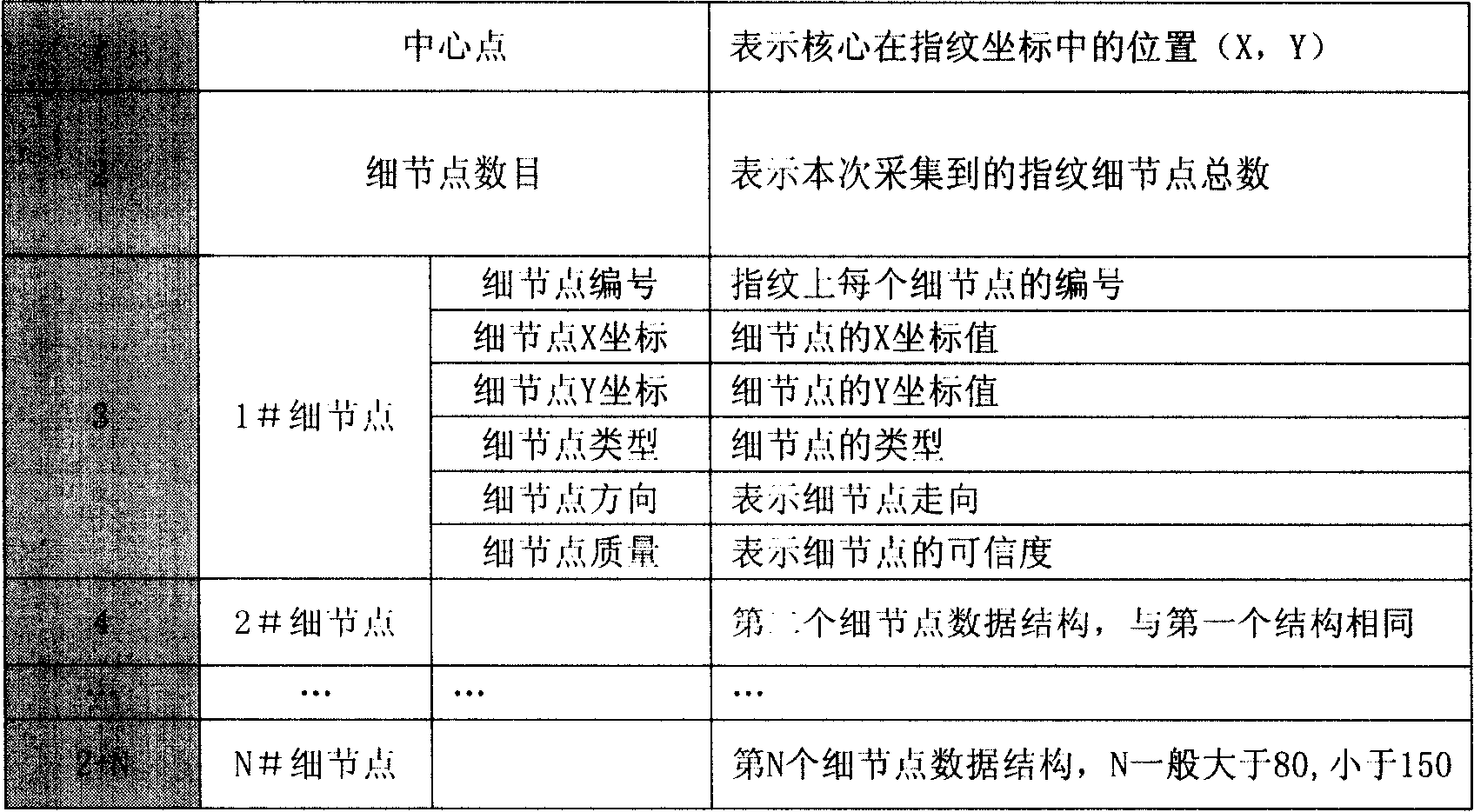
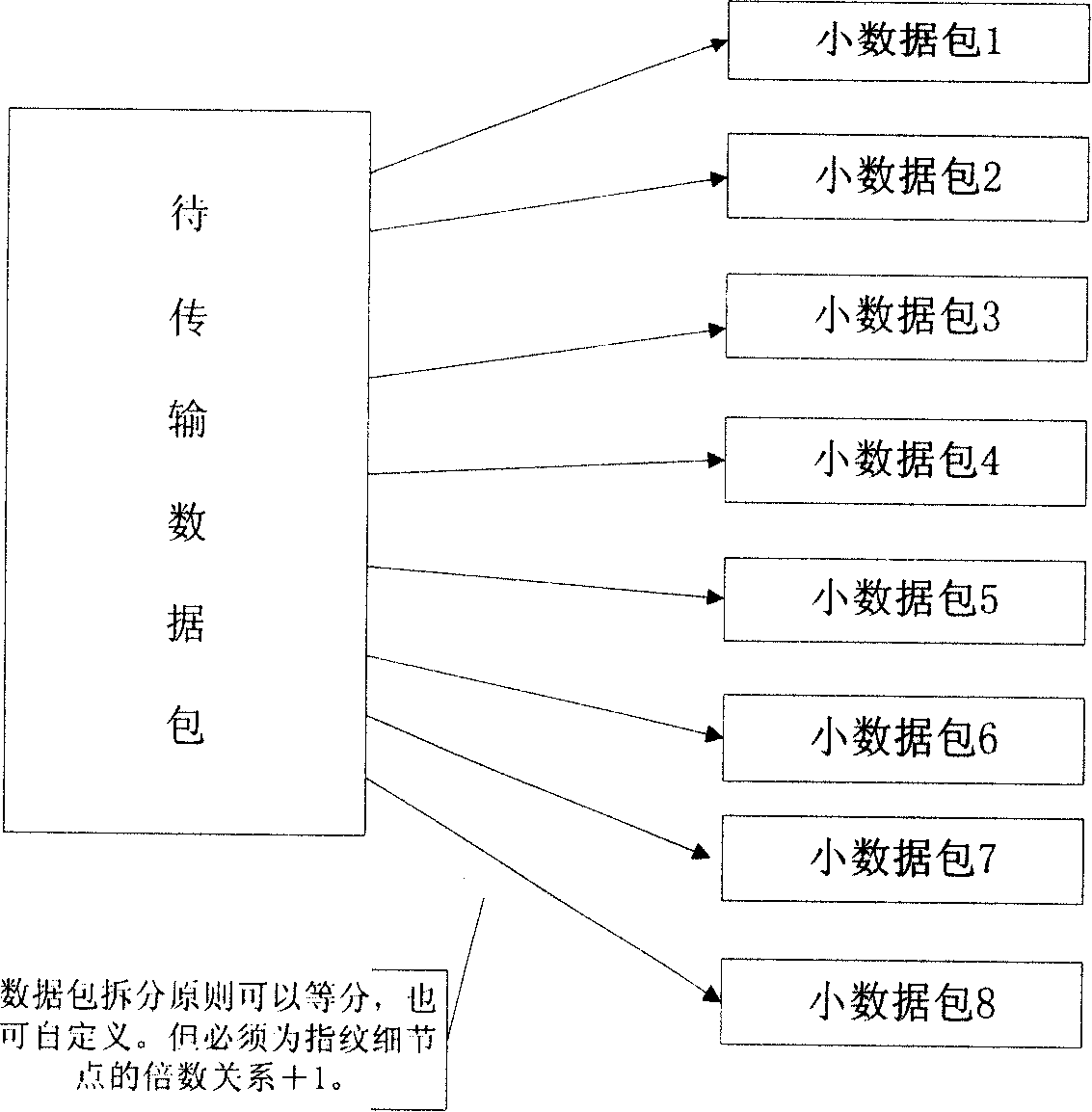
InactiveCN101166083AImprove integrityAchieve non-repudiationCharacter and pattern recognitionSecuring communicationInformation transmissionData transmission
This invention relates to a method for increasing safety of information transmission by fingerprint identification, which utilizes personal fingerprint data and identifying technology to inosculate personal fingerprint character in trade information and bind them together including the following steps: 1, collecting fingerprint data from a fingerprint device, 2, loading its data onto data to be transmitted, 3, picking up data from transmitted data, 4, determining source and integrality of data by fingerprint verification.
Owner:XIAN ZINIU TECH OF INFORMATION
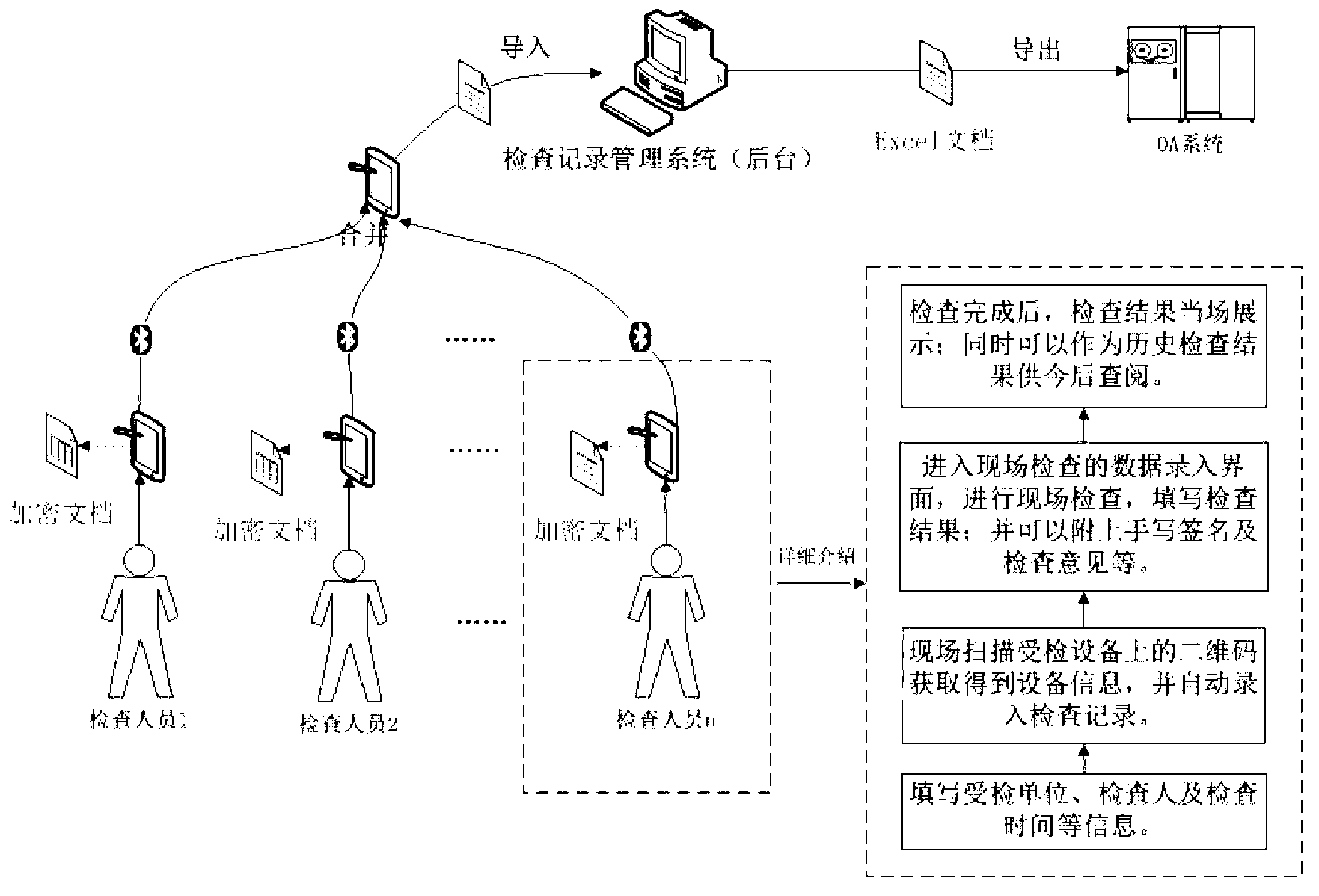
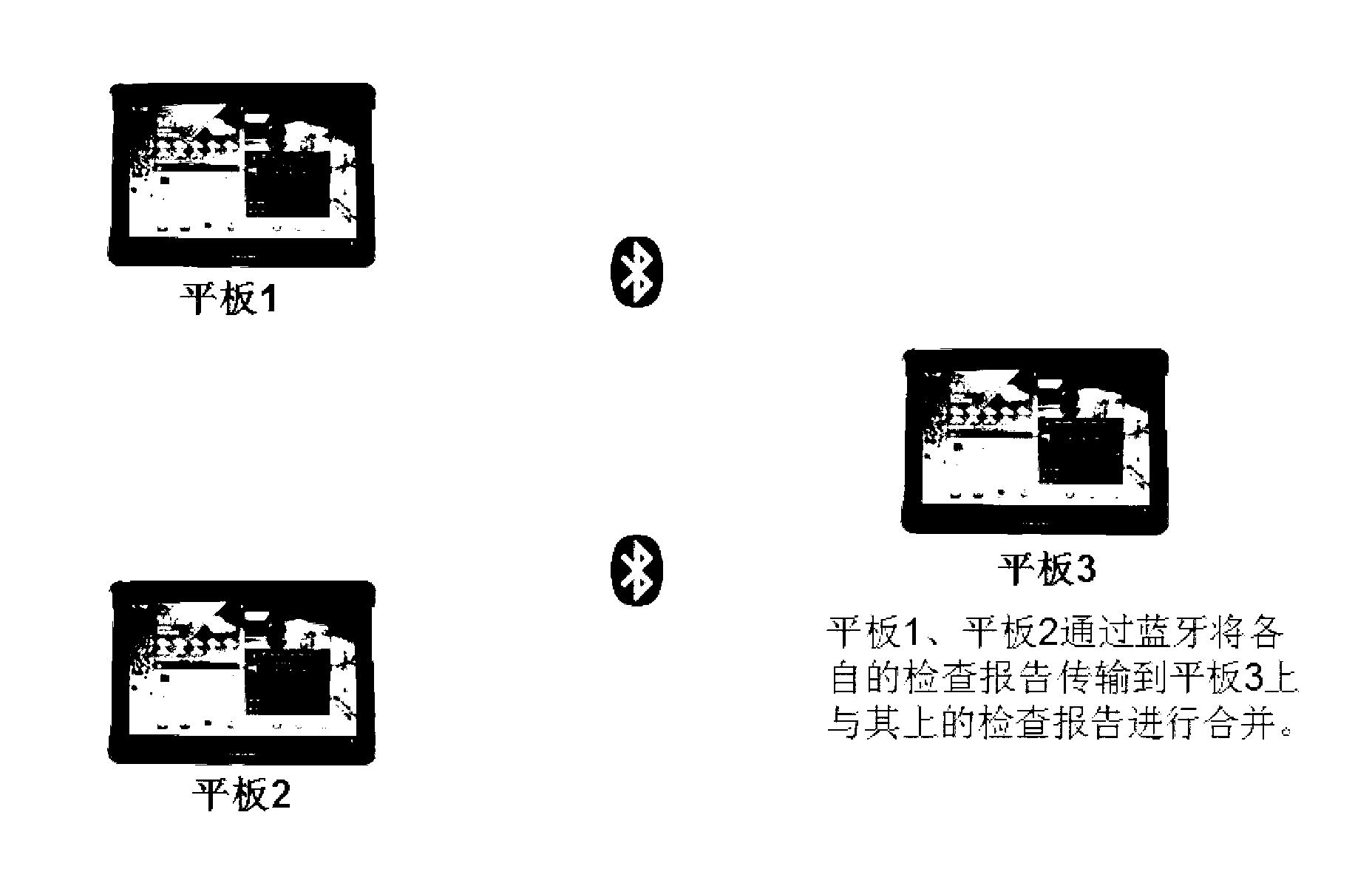
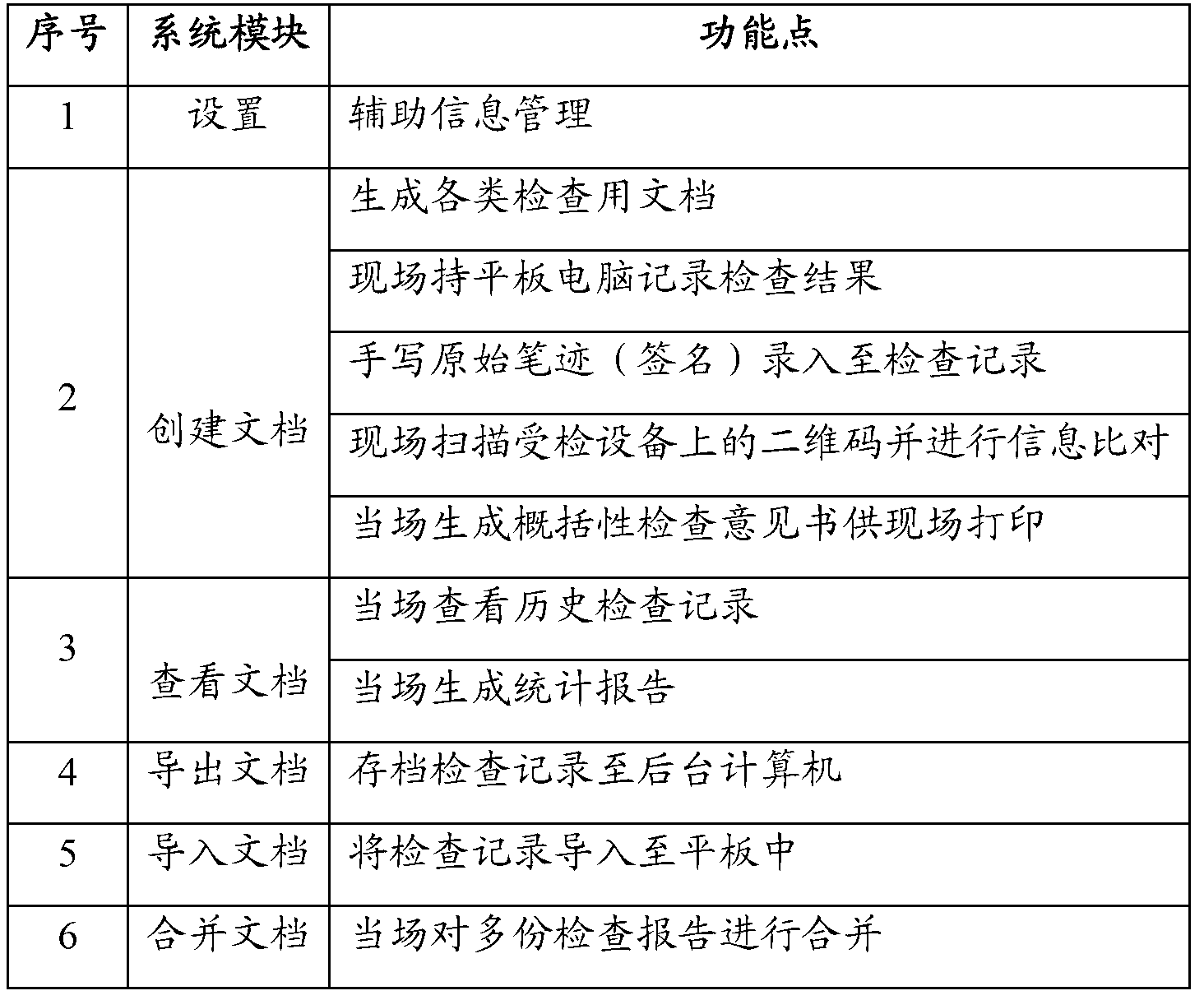
Tablet computer based on-site inspection recording system
The invention discloses a tablet computer based on-site inspection recording system. The system comprises a setting module, a document creating module, a document viewing module, a document exporting module, a document importing module and a merging module. Tablet computers are used for recording and managing on-site inspection results, and accordingly working efficiency of on-site inspection can be improved greatly; background importing is facilitated, workload of after-event data electronization is also reduced, and probable mistakes and omissions of the inspection results are decreased. Meanwhile, the system provides a handwritten signature function, non-repudiation the same as paper documents is realized, and a sufficient guarantee is provided for validity and identity of the inspection results.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
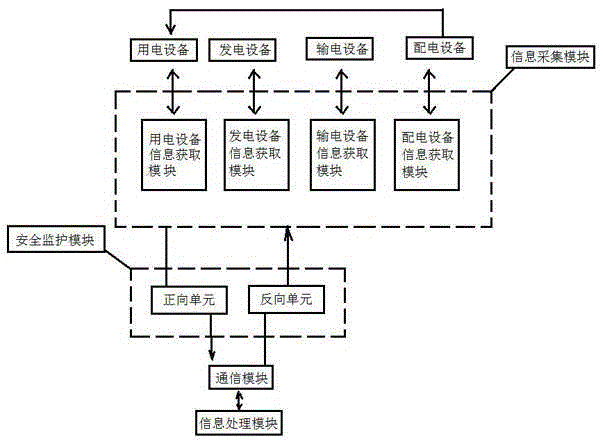
Intelligent power grid power information safety monitoring system and method
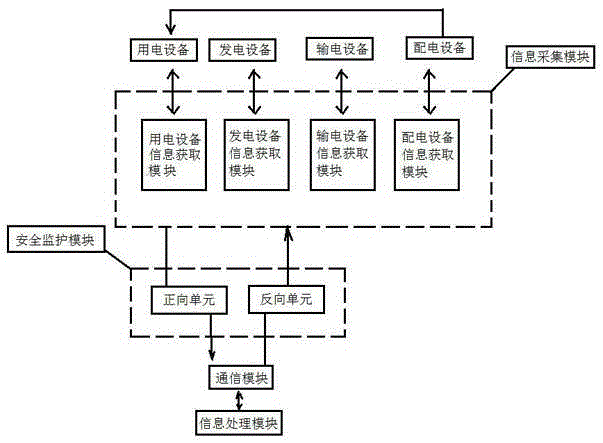
InactiveCN105305621AThe steps are well designedRegulatory control is simpleCircuit arrangementsPower gridSmart grid
The invention discloses an intelligent power grid power information safety monitoring system and a method. The system comprises an information acquisition module, an information processing module, a communication module and a safety monitoring module, and is characterized in that the information acquisition module comprises a power generation equipment information acquisition module, a power transmission equipment information acquisition module, a power distribution equipment information acquisition module and a power utilization equipment information acquisition module; the information processing module is used for storing and processing various power information in the intelligent power grid; the safety monitoring module comprises a forward unit and a backward unit; the information acquisition module adopts the forward unit when power information is transmitted to the communication module in a one-way mode; and the communication module adopts the backward unit when power information is transmitted to the information acquisition module in a one-way mode. Reliability, integrity, confidentiality and non repudiation of power information transmission can be realized.
Owner:STATE GRID CORP OF CHINA +1
Network identity authentication system and method
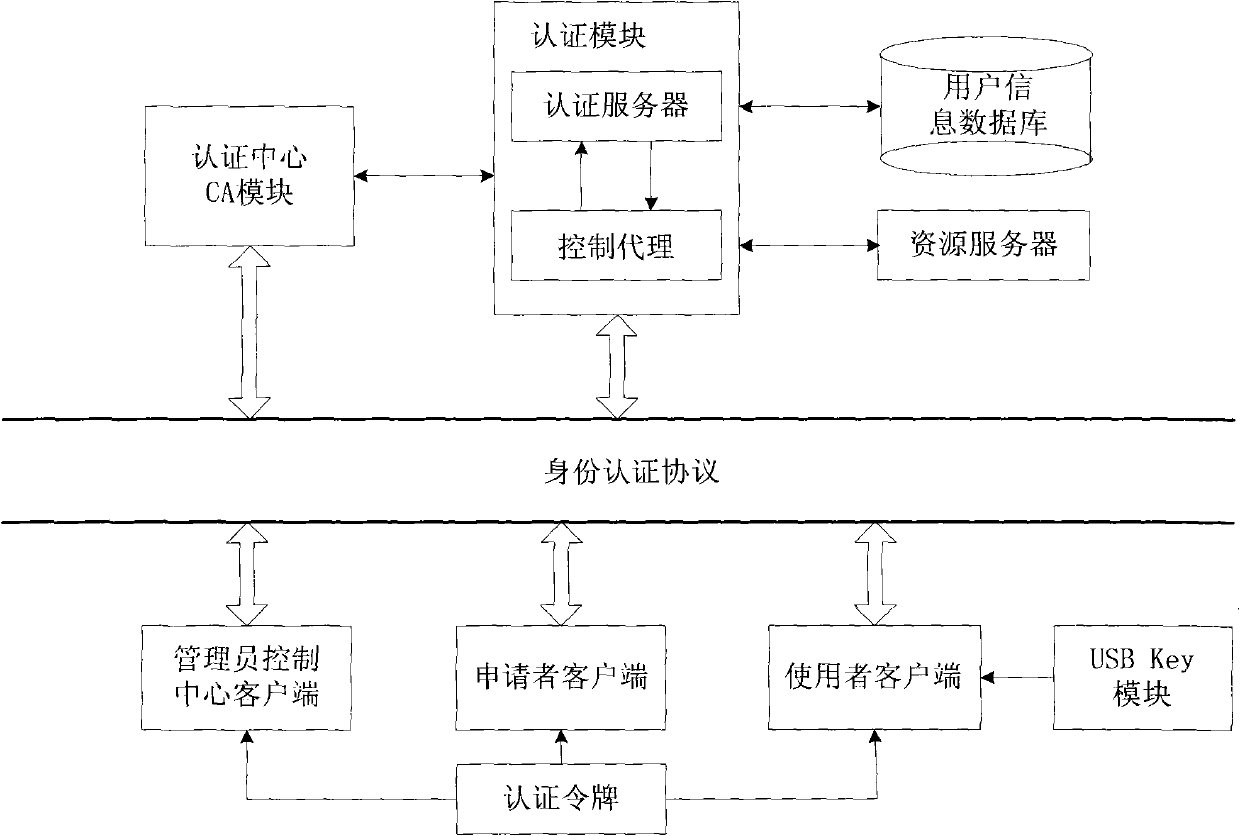
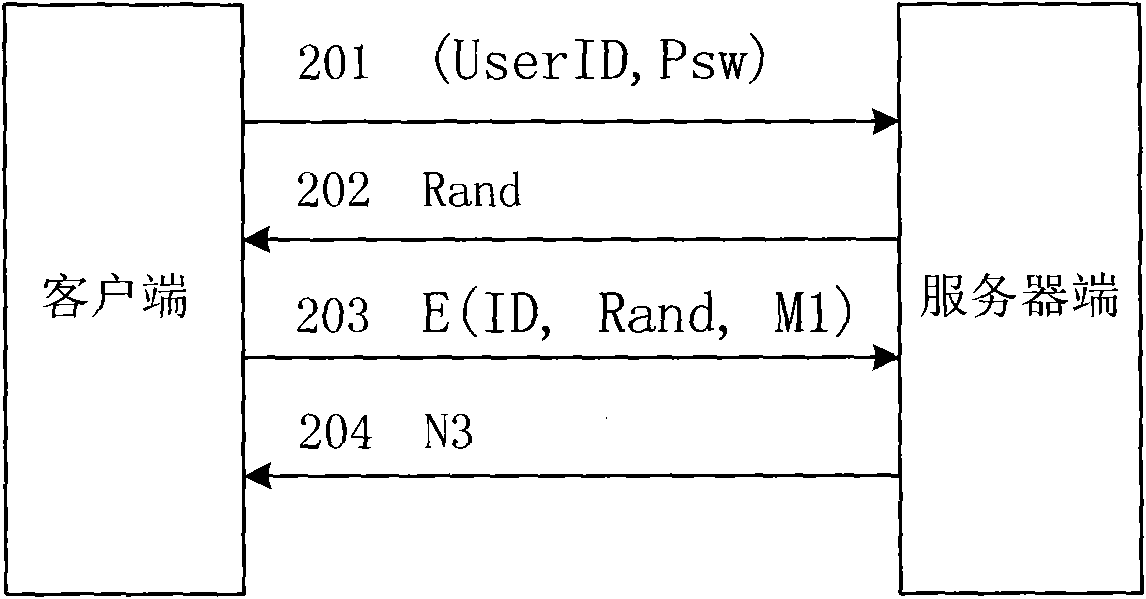
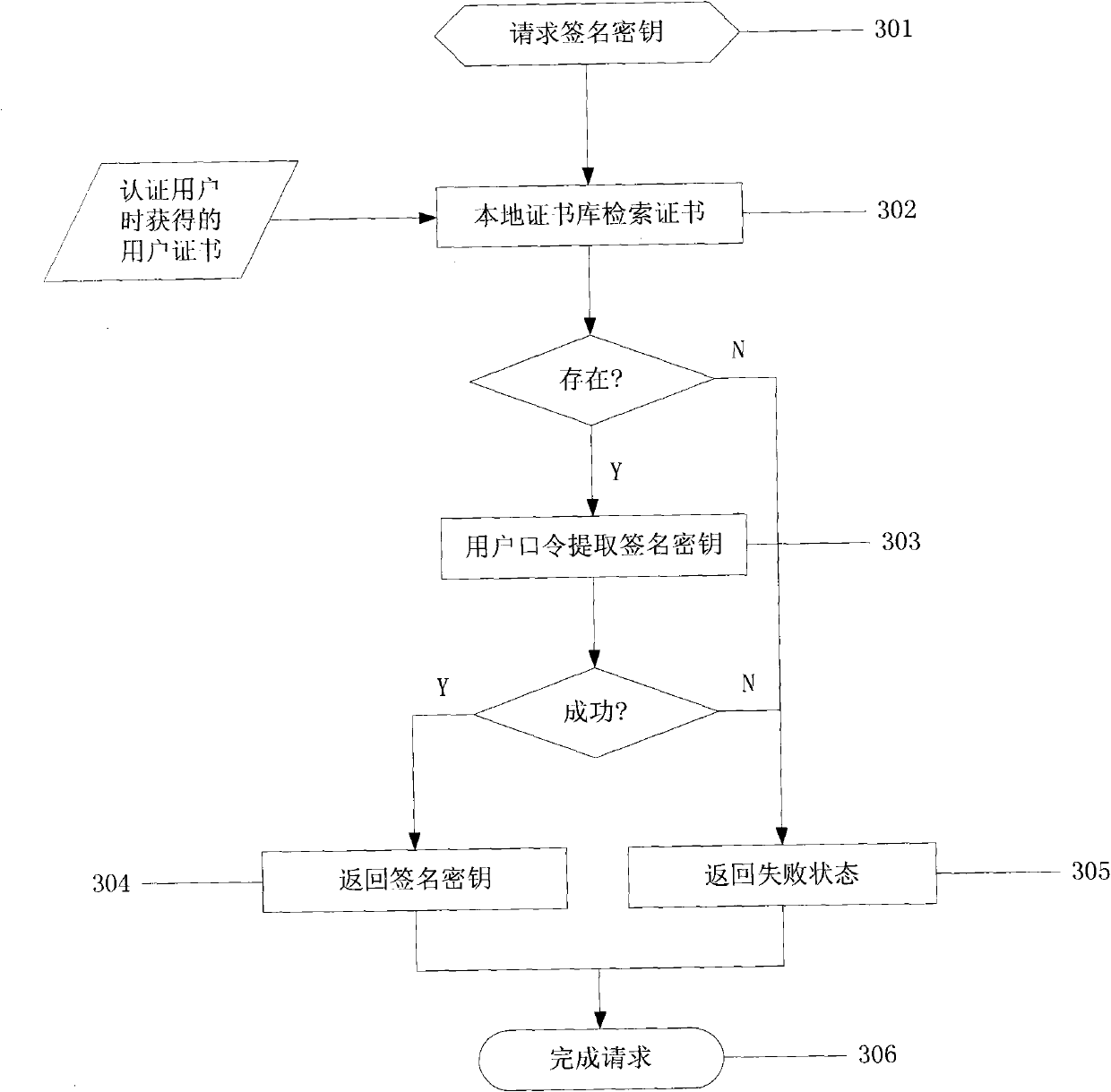
InactiveCN101674304BEnsure safetyAchieve separationUser identity/authority verificationConfidentialityAuthentication server
The invention relates to an identity authentication system and an authentication method. The identity authentication system comprises an authentication center CA module, an authentication module, a client side and a USB Key module, wherein the authentication center CA module is responsible for the functions of application, examination and approval, issuing, updating and revocation of a certificate; the authentication module respectively carries out the generation of a digital envelope and the authentication of a digital certificate to the client side and a server side; the client side mainly realizes the management of the system and the clients; and the USB Key module mainly provides a medium for storing the digital certificate and a user private key to the user. The invention adopts a digital envelope technology, and can meet the high-confidentiality requirement of data transmission; an authentication token is used for sending a request to the authentication server by the client sidefor authentication and realizing the security of the authentication process; and the client side and the authentication server respectively carry out the generation of the digital envelope and the digital certificate, thus being capable of realizing the mutual authentication between the client side and the authentication server.
Owner:ZHEJIANG NORMAL UNIVERSITY
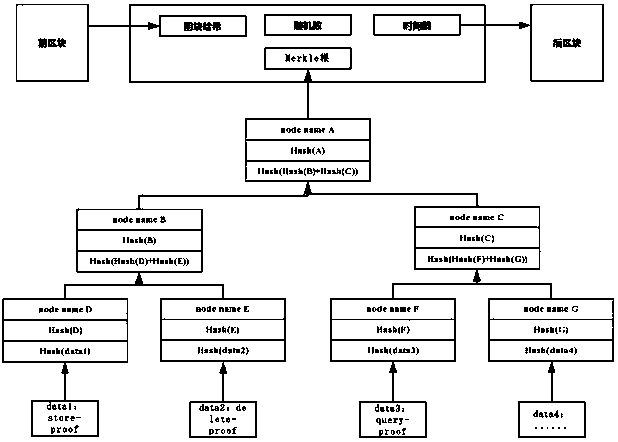
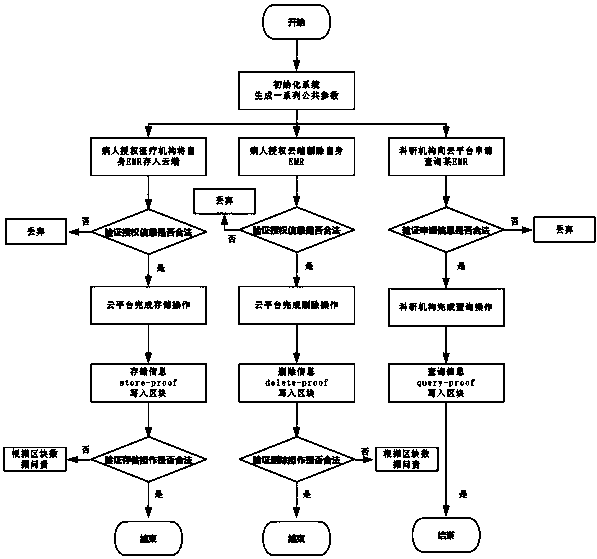
Accountable medical data storage method based on block chain
ActiveCN110851878AProtect personal privacyAchieve non-repudiationMedical data miningDigital data protectionBlockchainCloud storage
The invention discloses an accountable medical data storage method based on a block chain. According to the system, a system framework different from an existing medical block chain is provided by combining a block chain technology and a cloud storage technology, and all operations, such as deleting medical data, storing medical data and querying medical data, carried out on the medical data are written into blocks through a consensus mechanism. Meanwhile, the system realizes non-repudiation of related users on data operation through a cryptography method, and illegal operation of any user isresponded by taking data stored in the block chain as evidence.
Owner:NANJING UNIV OF POSTS & TELECOMM
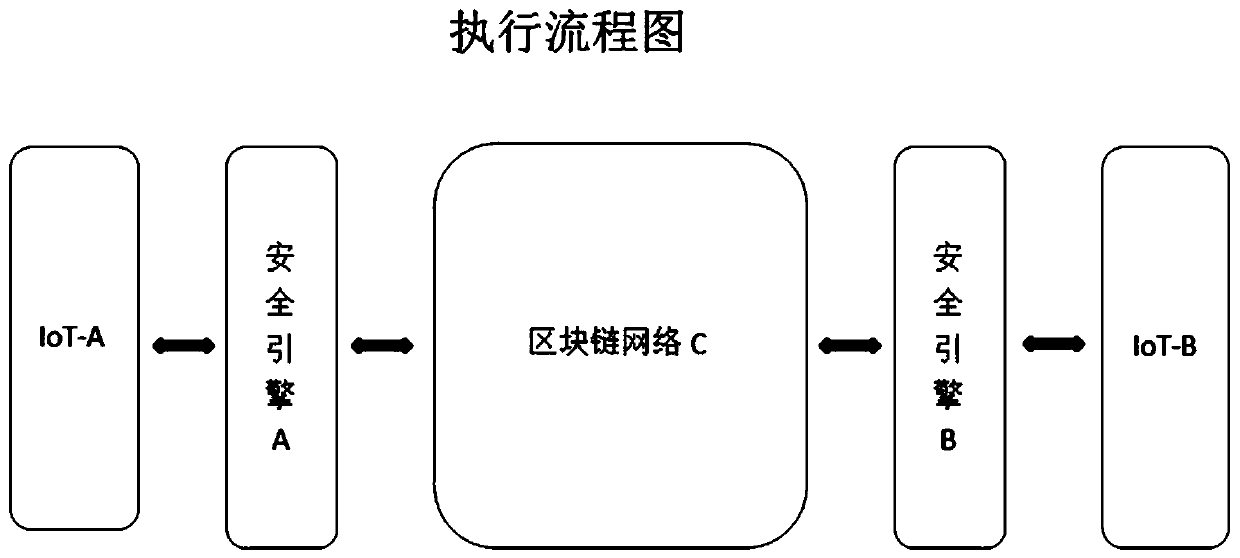
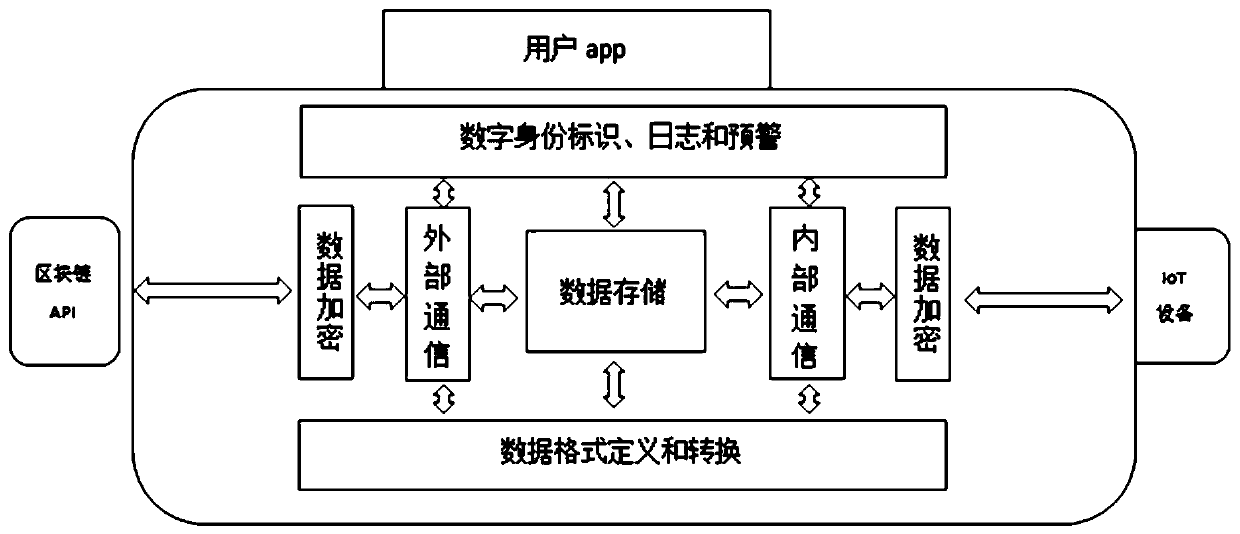
IoT security and data privacy protection system based on blockchain
ActiveCN108306887BImplement a unified key distribution mechanismAchieve non-repudiationTransmissionData privacy protectionThe Internet
The invention discloses a block chain-based internet of things safety and data privacy protection system. The system comprises an internet of things safety engine corresponding to internet of things equipment, and a block chain network communicated with the internet of things safety engine. The establishment of an access session channel with the internet of things equipment of an accessed party isrealized through the block chain network by the application program or the internet of things equipment of an access initiator. Meanwhile, the paid acquisition of the data usage right and the node accounting are completed through the block chain network according to data stored by the internet of things safety engine and corresponding digital right requirements. The internet of things safety engine can automatically carry out the data encryption and decryption operation and the data transaction packaging operation. According to the invention, a block chain network-based internet of things equipment unified key distribution mechanism is realized, so that the authorized use of the internet of things equipment and the establishment of a trust mechanism are effectively realized. Meanwhile, based on the block chain network, the data privacy and the data rights are protected. Therefore, the privacy protection safety of the data of the internet of things equipment is greatly improved.
Owner:徐正伟 +2
Intelligent power grid safety communication method based on combined password
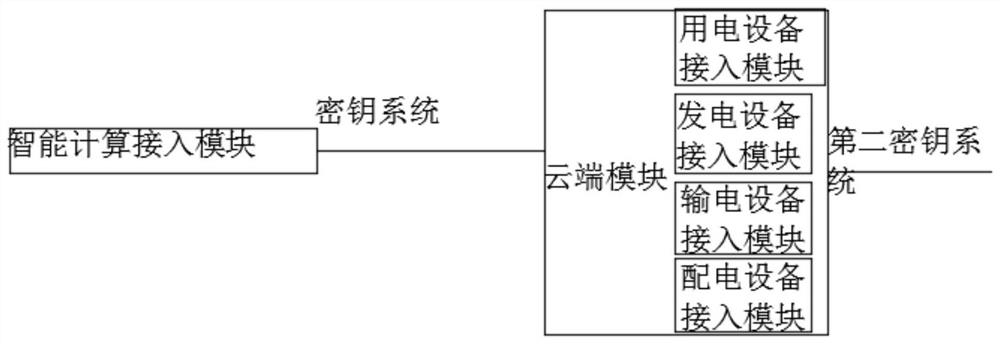
PendingCN112511490ASecure transmissionAchieve reliabilityKey distribution for secure communicationCircuit arrangementsSmart grid communicationConfidentiality
The invention relates to the technical field of telecommunication, in particular to an intelligent power grid safety communication method based on a combined password. The system comprises a pluralityof transfer stations, each transfer station is provided with an intelligent computing access module and a cloud module connected with the intelligent computing access module, and the intelligent computing access modules are used for acquiring information of power generation equipment, power transmission equipment, power distribution equipment and power utilization equipment and interacting the acquired information with the cloud modules. Each intelligent computing access module is correspondingly provided with a secret key system, and the cloud module is further connected with a second secretkey system. The method has the beneficial effects that the reliability, integrity, confidentiality and non-repudiation of information transmission are realized; the public key cryptosystem is used inthe smart power grid, so that the authentication and confidentiality of smart power grid communication are ensured, and the number of secret keys stored in the smart power grid is effectively reduced.
Owner:苏州达塔库自动化科技有限公司
Distributed secure communication method and system based on block chain
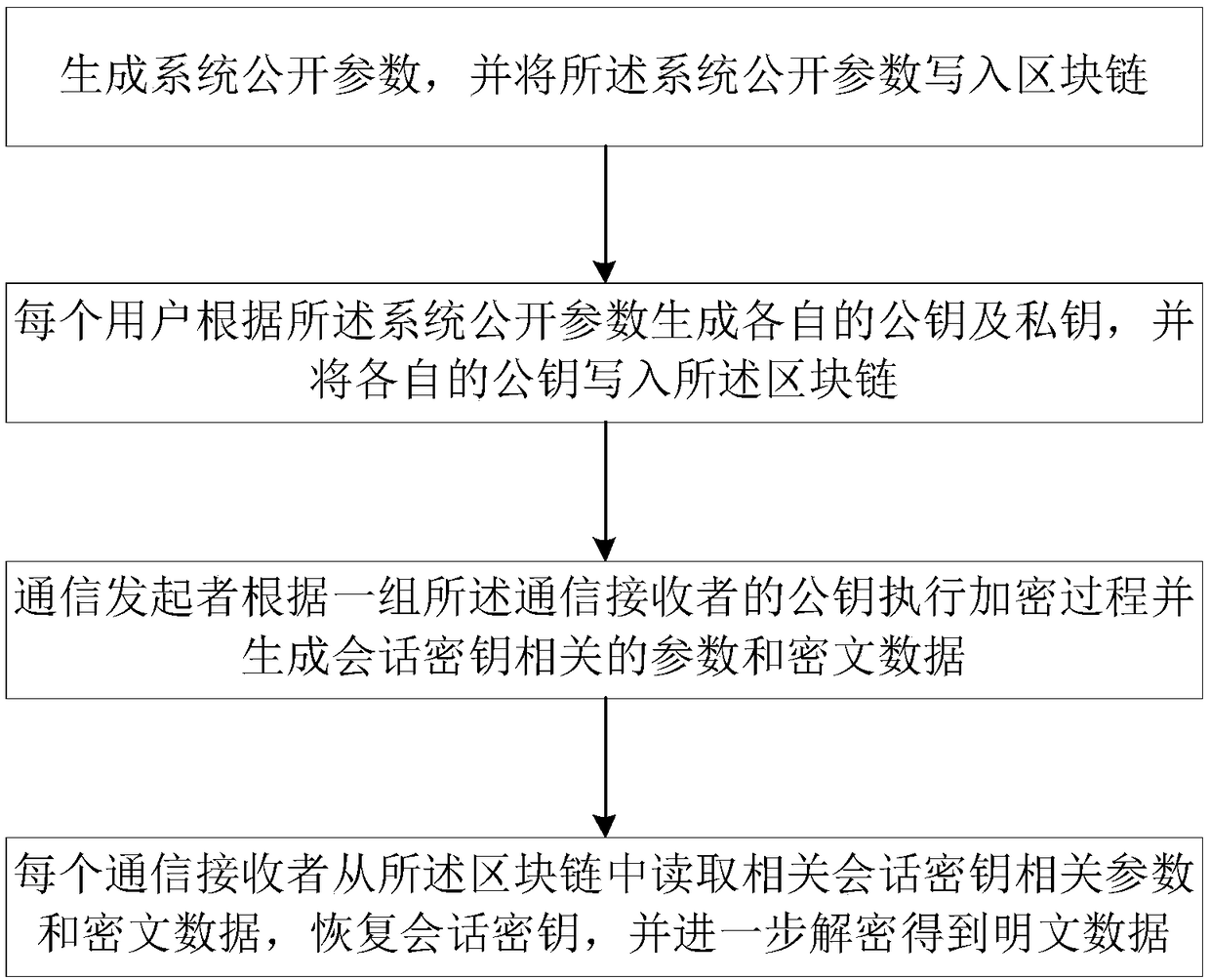
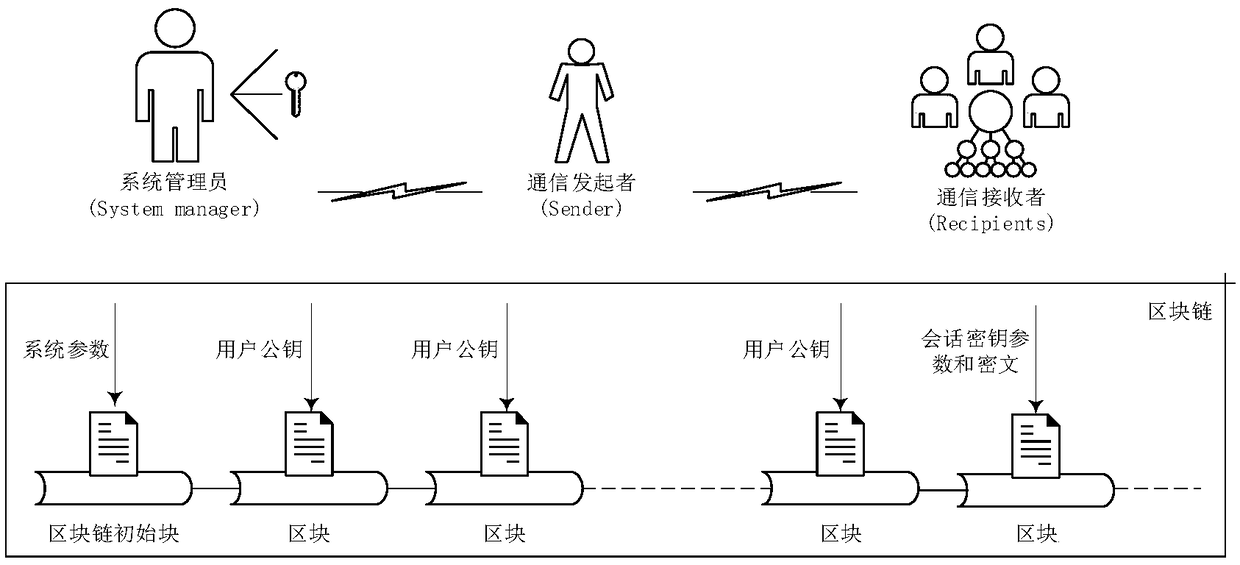
ActiveCN109495478APrivacy protectionAchieve non-repudiationTransmissionSecure communicationBlockchain
The invention provides a distributed secure communication method based on a block chain. The distributed secure communication method based on the block chain comprises the steps that system public parameters are generated and written in the block chain; each user generates a public key and a private key according to the system public parameters, and writes the public key into the block chain, wherein the users include communication initiators and communication receivers; the communication initiators perform encryption processes according to the public keys of a group of the communication receivers and generate session key-related parameters and ciphertext data, and the session key-related parameters and ciphertext data are written into the block chain; and each communication receiver readsthe relevant session key-related parameters and ciphertext data from the block chain to restore session keys, and further performs decryption to obtain plaintext data. By use of the method, the session keys are processed, distributed and restored in a distributed environment, and the data is encrypted and decrypted, so that the privacy of the session keys and the user data in a transmission process can be guaranteed.
Owner:GUILIN UNIV OF ELECTRONIC TECH
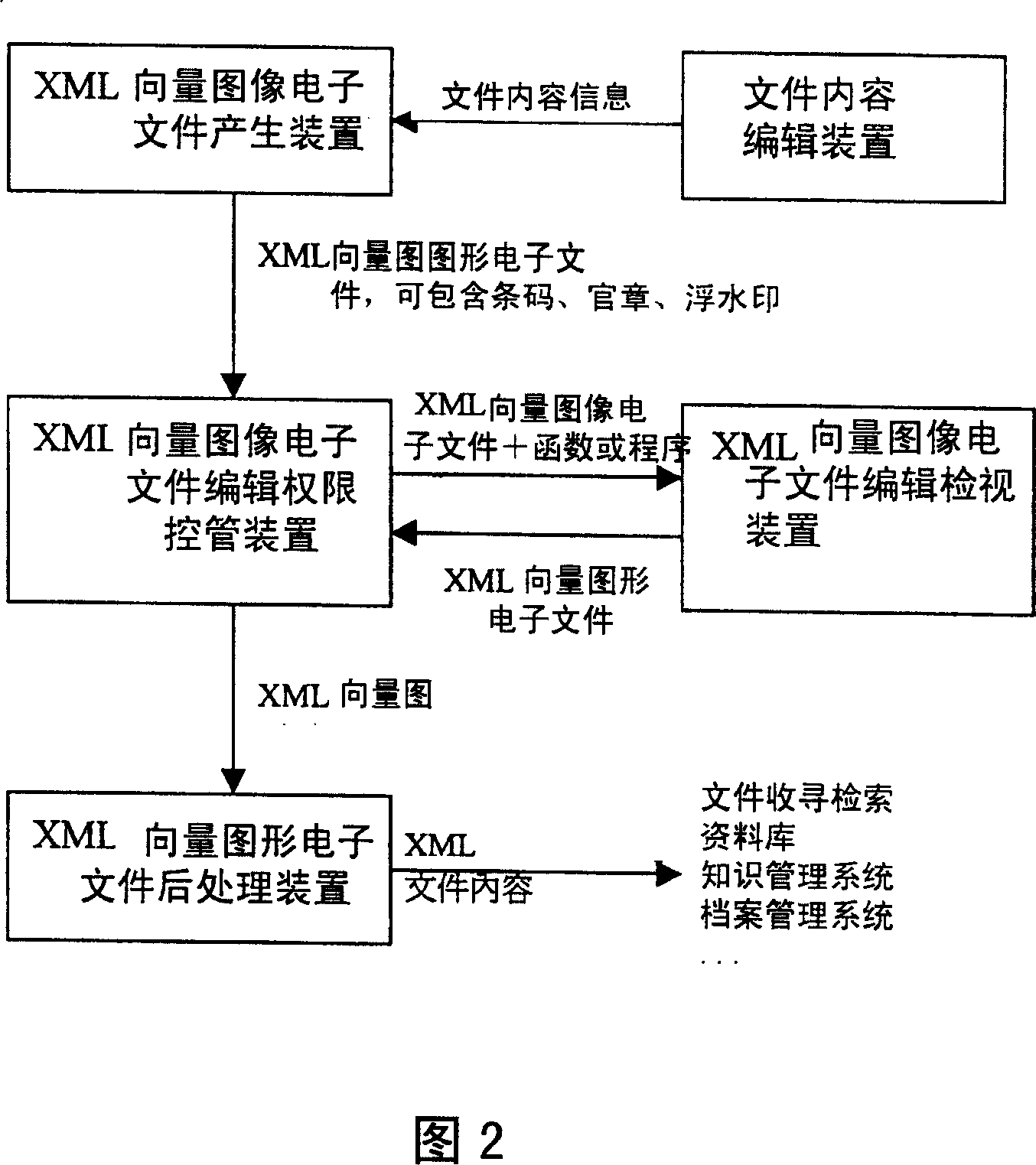
XML vector graphics technology based electron file and window online signing method
InactiveCN1967575AAchieve non-repudiationRealize immutabilityOffice automationElectronic documentScripting language
The invention is the electronic document and windows online signed method based on XML vector graphics technology, and it is a document format that conforming XML (eXtensible Markup Language) international standards, and takes on the electronic document or electronic window with the main body of digital contents, and adds the programs written in scripting languages or other programming languages by the means of include or link, to achieve the electronic document and windows online signed relevant jobs.
Owner:INFODOC TECH CORP
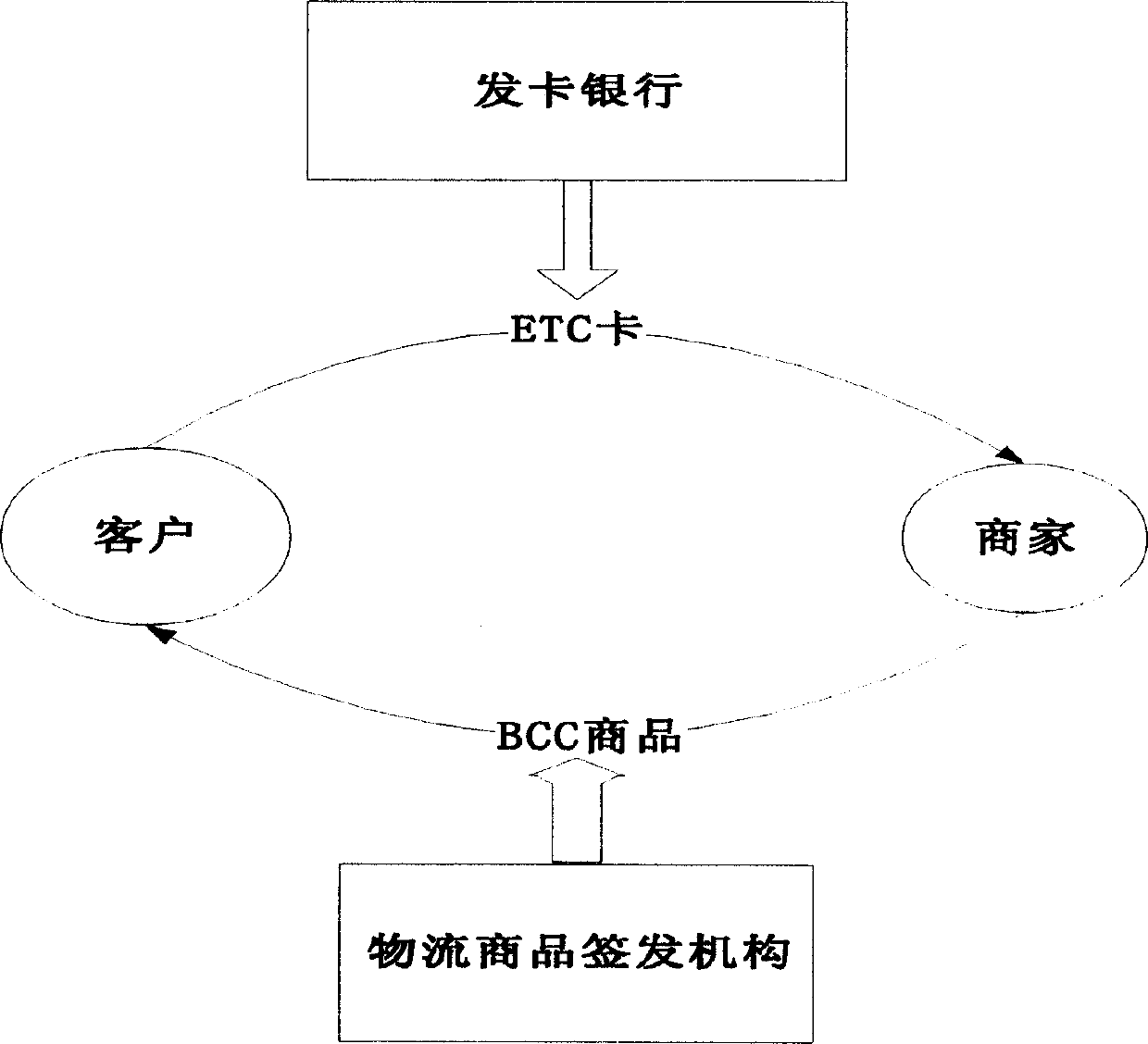
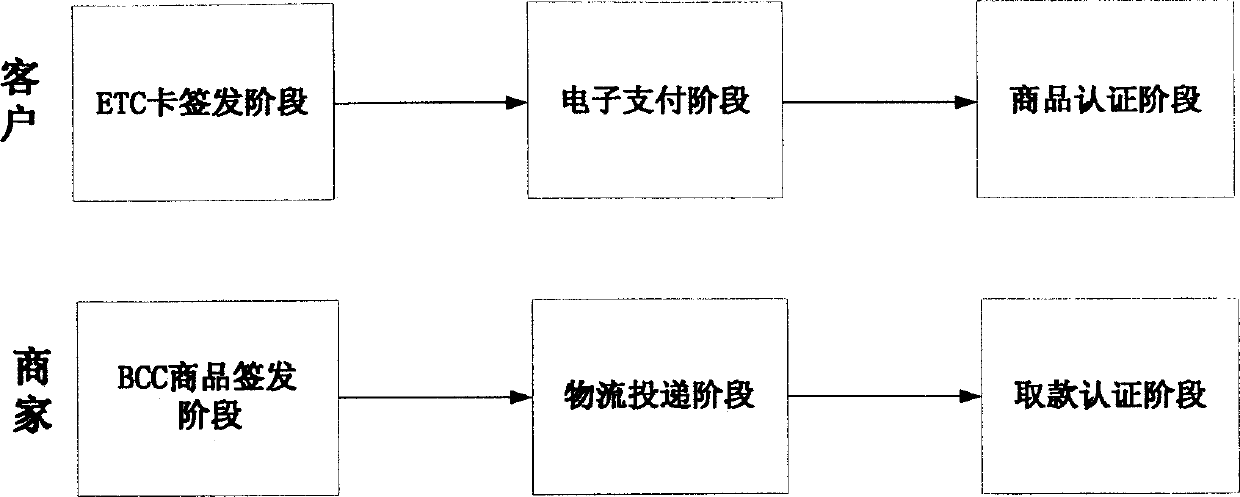
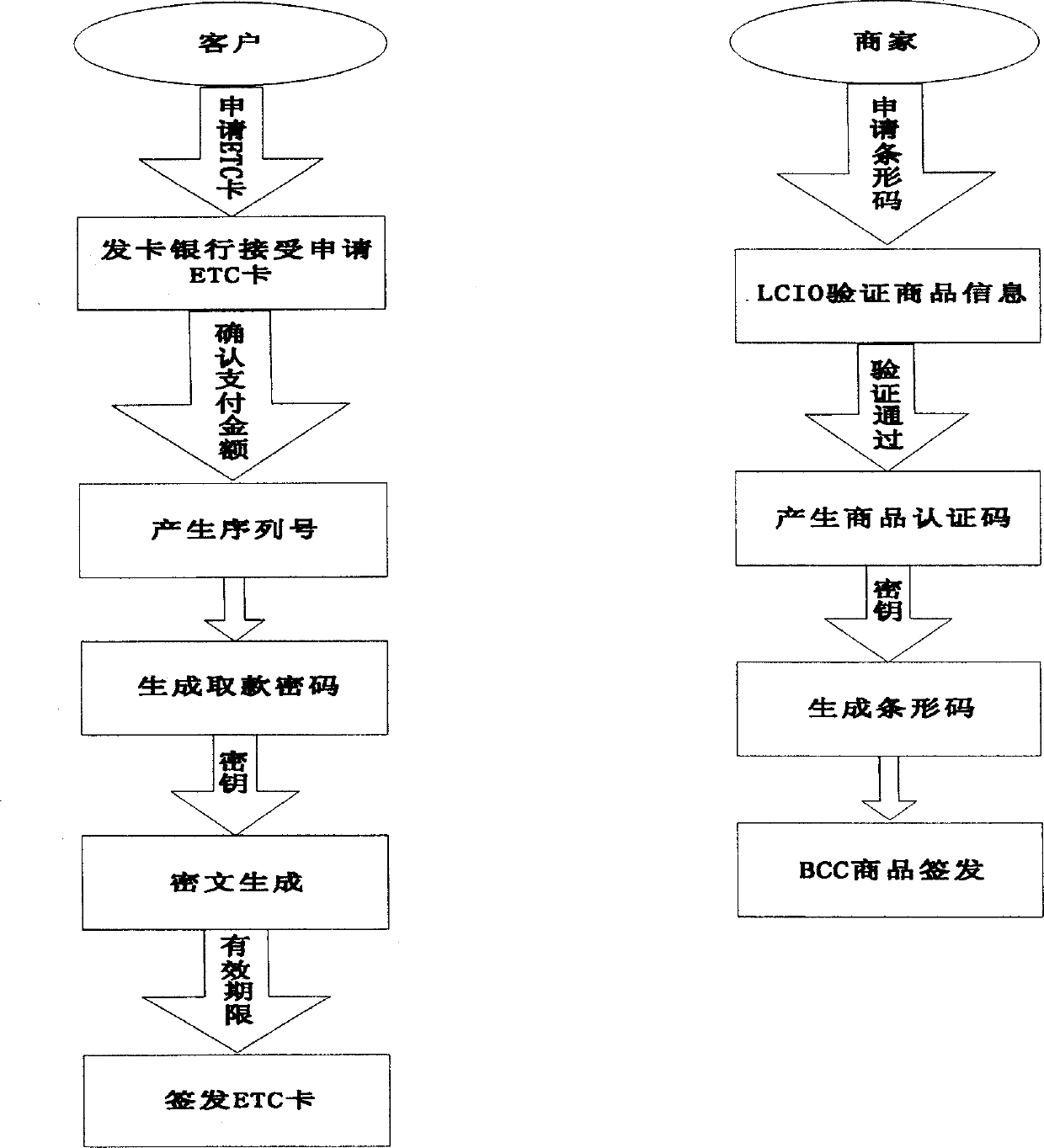
Plan to realize safe electronic transaction system
InactiveCN1741058AGuaranteed correctnessQuality assurancePayment architectureCommerceSecurity solutionIssuing bank
The scheme for implementing safety electronic transaction system by utilizing public key cryptosystem adopts the following main measures: customer makes an application for issuing enciphered cash-transposing card (ETC card) to card-issuing bank, and the shop can make an application to logistics commodity issue organization (LCID) for issuing bar code commodity (BCC), so that ETC card can be substituted for cash, and the BCC commodity can be substituted for general commodity. Said invented electronic transaction scheme process is composed of customer's ETC card-issuing stage, electronic payment stage, commodity authentication stage, shop's BCC commodity issuing stage, logistics delivery stage and drawing authentication stage.
Owner:NANJING UNIV OF POSTS & TELECOMM
Security protection system and method based on network multimedia equipment data transmission
ActiveCN111901301AImprove confidentialityImprove integrityTransmissionInformation technology support systemConfidentialityTransmission technology
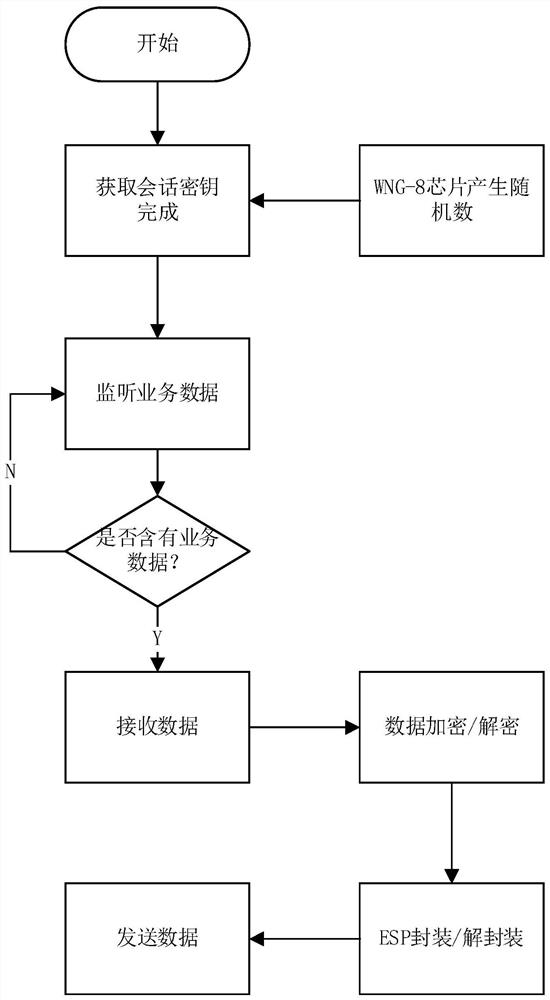
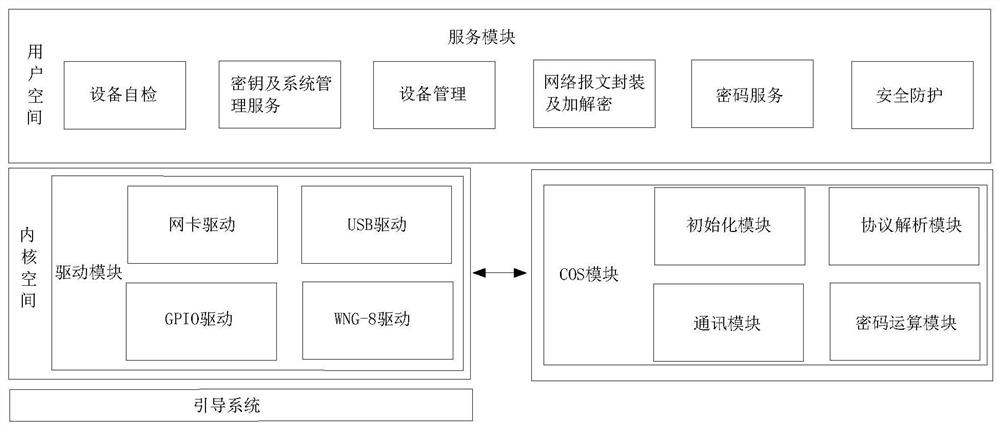
The invention discloses a security protection system and method based on network multimedia equipment data transmission, which belongs to the technical field of network security, and comprises a service module, a driving module and a COS module, and is characterized in that the service module provides a function module for a user to use; the driving module is used for providing bottom-layer driving and providing support for the service module; the COS module is used for providing underlying algorithm implementation; according to the security protection system based on network multimedia equipment data transmission, a certificate-based identity authentication technology, a key security distribution and management technology and an ESP tunnel security transmission technology are adopted, thepassword functions of confidentiality, integrity, authenticity, non-repudiation and the like of the network message are realized, and the purposes of interception prevention, counterfeiting prevention, replacement prevention and intrusion attack prevention of the multimedia system of the multimedia data stream are achieved by combining a network protection technology, so that the multimedia datatransmission safety and the multimedia system use safety are ensured.
Owner:乾讯信息技术(无锡)有限公司
A private file management system and method based on finger vein authentication
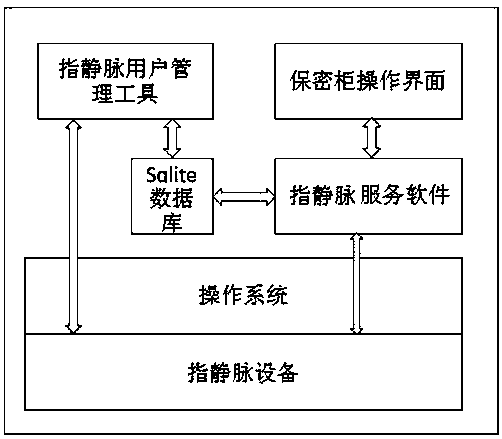
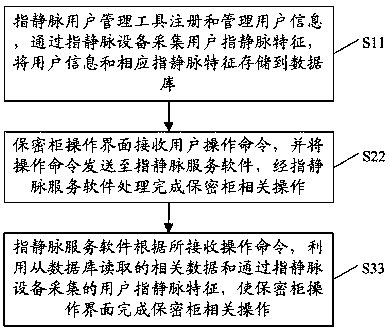
PendingCN109697373AImprove confidentialityImprove integrityDigital data protectionDigital data authenticationManagement toolConfidentiality
The invention discloses a private file management system and method based on finger vein authentication, and the system comprises a finger vein user management tool which is used for registering and managing user information, collecting the finger vein characteristics of a user through a finger vein device, and storing the user information and the corresponding finger vein characteristics in a database; a confidential cabinet operation interface which is used for receiving a user operation command and sending the operation command to the finger vein service software, and relevant operation ofthe confidential cabinet is completed through processing of the finger vein service software; and the finger vein service software enabling the confidential cabinet operation interface to complete theconfidential cabinet related operation by utilizing the related data read from the database and the user finger vein characteristics collected by the finger vein equipment according to the received operation command. The digital vein authentication is combined with the file confidentiality cabinet system, and confidentiality, integrity, identifiability and non-repudiation of file storage are achieved.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
Credible identity recognition method and system based on block chain
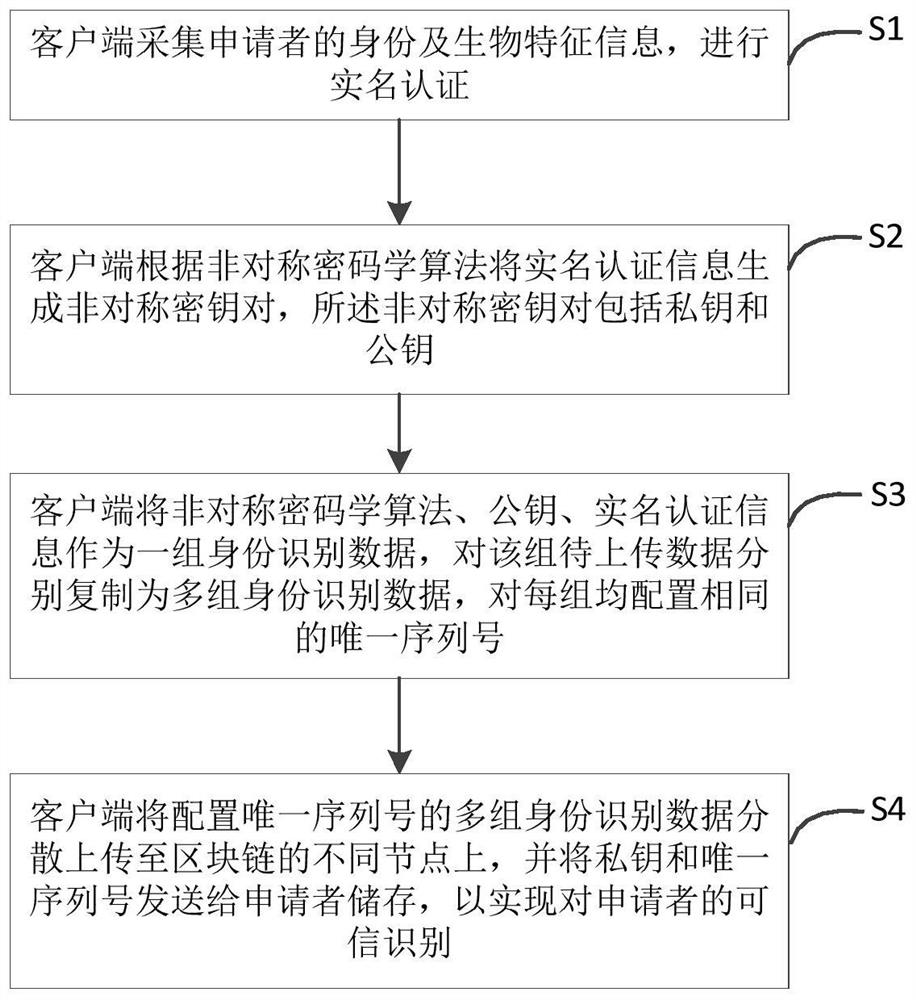
PendingCN112328997ATrusted Identity ImplementationRealize immutableDatabase distribution/replicationDigital data protectionKey (cryptography)Identity recognition
The invention discloses a trusted identity recognition method and system based on a block chain. The method comprises the steps: collecting the identity and biological feature information of an applicant, and carrying out the real-name authentication; generating an asymmetric key pair from the real-name authentication information according to an asymmetric cryptography algorithm, wherein the asymmetric key pair comprises a private key and a public key; gathering the asymmetric cryptography algorithm, the public key and the real-name authentication information as a group of identity recognitiondata, respectively copying the group of to-be-uploaded data into multiple groups of identity recognition data, and configuring the same unique serial number for each group; uploading, in a dispersedmanner, the multiple groups of identity recognition data configured with the unique serial numberd to different nodes of the blockchain, and the private key and the unique serial number are sent to anapplicant for storage, so that credible recognition of the applicant is realized. The credible identity recognition method and system based on the block chain has the advantages of being higher in credibility and higher in safety.
Owner:ANHUI JIYUAN SOFTWARE CO LTD +1
Method and system for realizing cross-domain secure communication
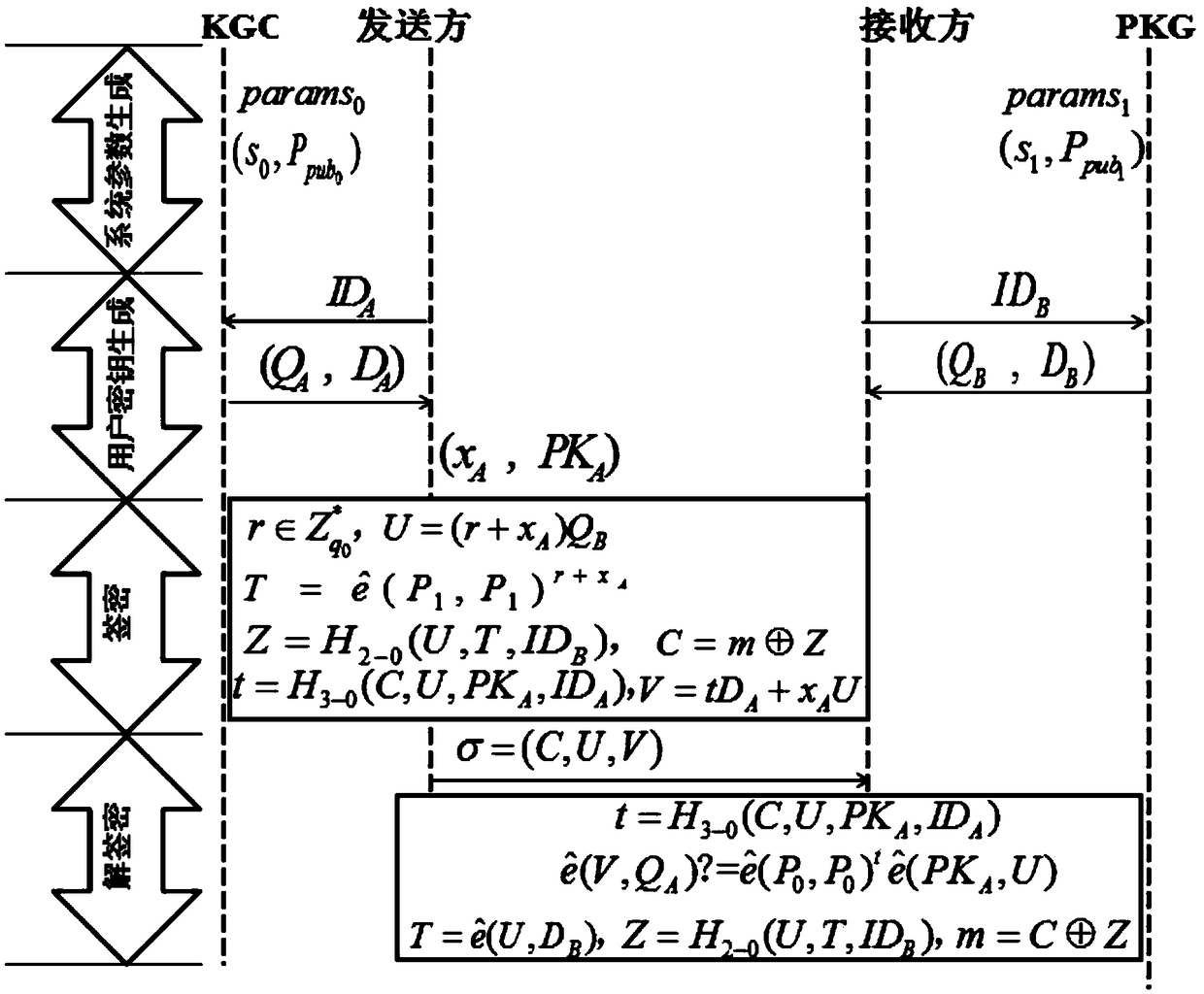
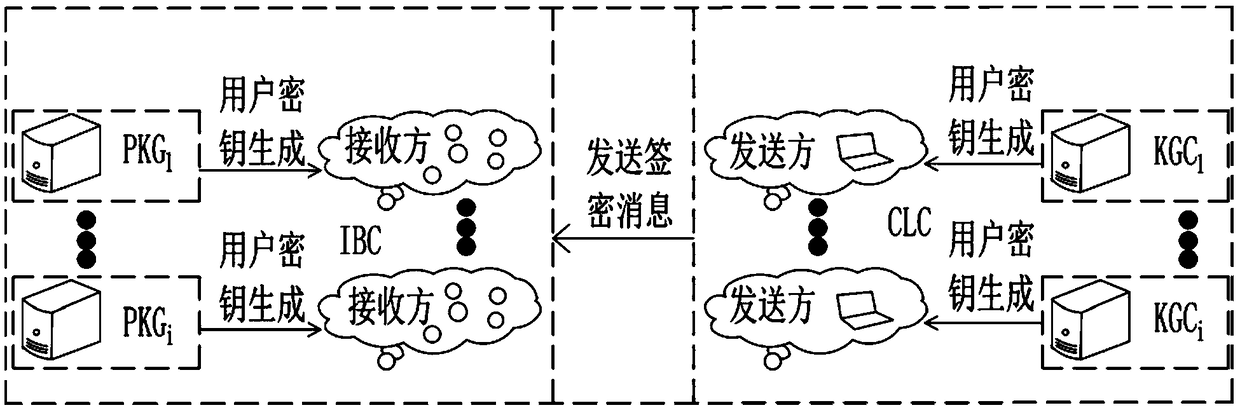
ActiveCN109412815AImplement ephemeral key securityImplement cross-domain featuresKey distribution for secure communicationPublic key for secure communicationSecure communicationKey generation
The invention discloses a method and a system for realizing cross-domain secure communication, and belongs to the field of secure communication. The method for realizing the cross-domain secure communication is implemented according to the following steps: a system parameter generation phase: a KGC discloses its system parameter params0 and randomly selects a master key s0, and a PKG discloses itssystem parameter params1 and randomly selects a master key s1; a user key generation phase: a partial public key QA and a partial private key DA of a sender are calculated, the sender selects a random number xA, another partial public key PKA and another partial private key A are calculated, and public keys QB and DB of a receiver are generated; a signcryption phase: the sender performs signcryption on a plaintext m to form a signcryption message sigma, and sends the signcryption message sigma to the receiver; and a de-signcryption phase: the receiver obtains the plaintext m by using the signcryption message sigma and the private key DB of the receiver. By adoption of the method and the system for realizing the cross-domain secure communication disclosed by the invention, temporary key security and cross-domain functional characteristics are achieved.
Owner:NANCHANG UNIV
Smart grid electric power information safety monitoring system and method
InactiveCN105262218AAchieve reliabilityImprove integrityCircuit arrangementsInformation processingSmart grid
The present invention discloses a smart grid electric power information safety monitoring system and a smart grid electric power information safety monitoring method. The smart grid electric power information safety monitoring system comprises an information acquisition module, an information processing module, a communication module and a safety monitoring module, and is characterized in that: the information acquisition module comprises a power generation equipment information acquisition module, a power transmission equipment information acquisition module, a distribution equipment information acquisition module and an electric equipment information acquisition module; the information processing module is used for storing and processing various electric power information in a smart grid; the safety monitoring module comprises a forward unit and a reverse unit; when the information acquisition module unidirectionally transmits the electric power information to the communication module, the forward unit is adopted, and when the communication module unidirectionally transmits the electric power information to the information acquisition module, the reverse unit is adopted. The smart grid electric power information safety monitoring system of the present invention achieves reliability, integrity, security and non-repudiation of transmission of the electric power information.
Owner:STATE GRID CORP OF CHINA +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com