IoT security and data privacy protection system based on blockchain
A data privacy and protection system technology, applied in the field of Internet of Things, can solve the security risks of the Internet of Things, data abuse and privacy violations of Internet of Things devices have not found universality, and failed to provide a unified key distribution mechanism, etc. problems, to achieve the effect of improving privacy protection security, realizing authorized use, and realizing non-repudiation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
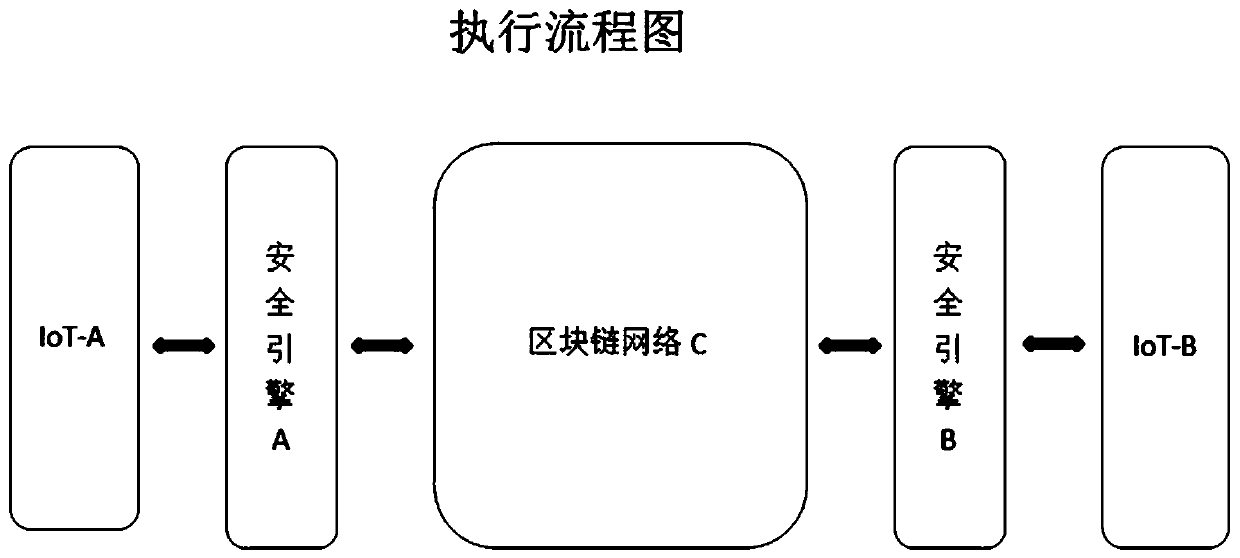
[0036] refer to figure 1 , is a schematic diagram of an optional application environment of a specific embodiment of the present invention.
[0037] In this embodiment, the blockchain-based Internet of Things security and data privacy protection system includes an Internet of Things security engine and a blockchain network communicating with the Internet of Things security engine. like figure 1 As shown, the present invention can be applied to application environments including, but not limited to, IoT security engine A, IoT security engine B, and blockchain C. Among them, the IoT security engines A and B are hardware devices at the communication boundary of IoT devices that can be designed according to predetermined security rules, automatically encrypt and decrypt data, and encapsulate data transactions.
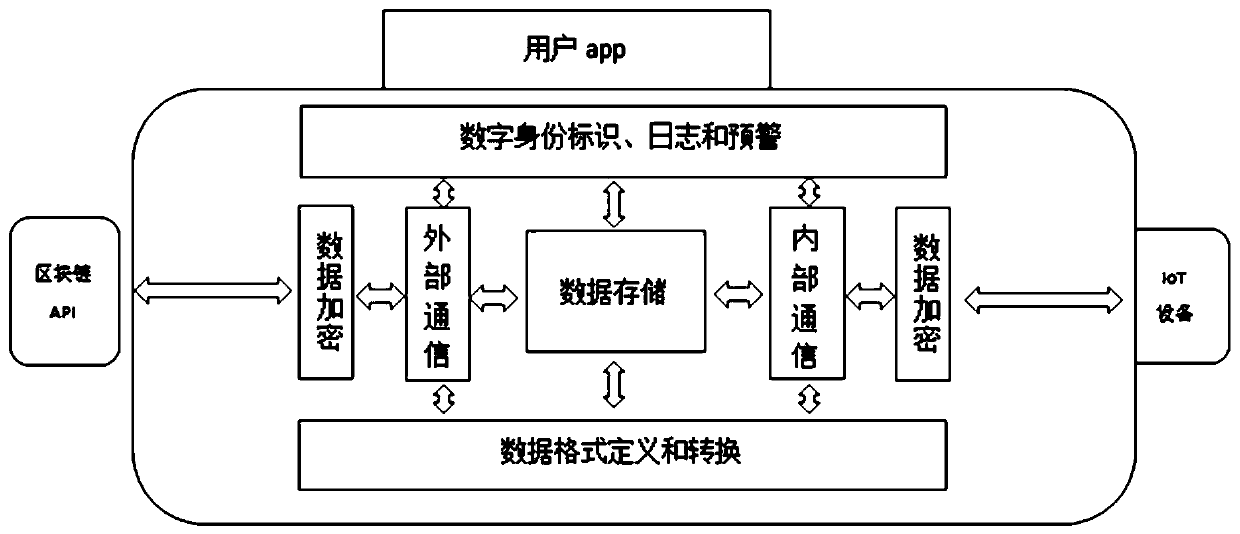
[0038] IoT security engines A and B are used for digital identity identification of IoT devices, device data encryption and demystification, and data transaction encapsu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com