Method and system for realizing cross-domain secure communication
A secure communication, cross-domain technology, applied in the field of cross-domain secure communication, can solve the problem of not being able to resist the security of temporary keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The technical method of the present invention will be further described below in conjunction with the accompanying drawings and through specific implementation methods.
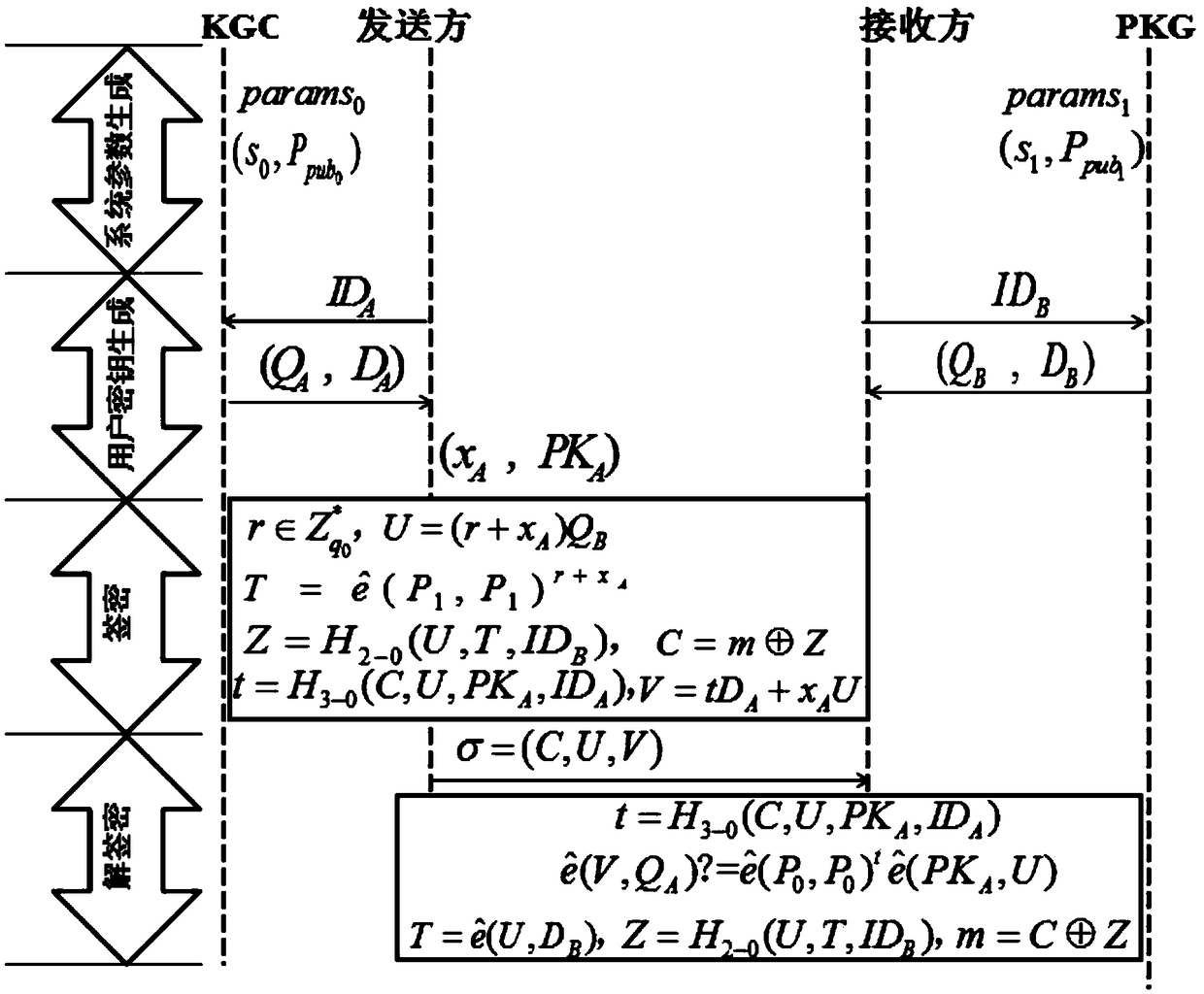
[0064] Such as figure 1 with figure 2 As shown, a method for realizing cross-domain secure communication provided in this embodiment is implemented according to the following steps:
[0065] System parameter generation phase:
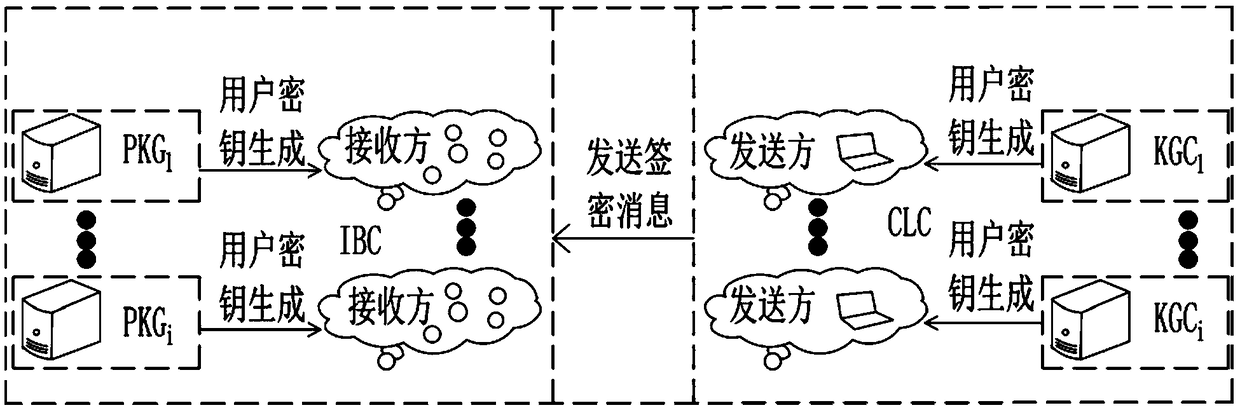
[0066] In order to ensure the versatility of this method, the sender chooses any matching KGC, and the receiver chooses any matching PKG. Both the sender and KGC are in the CLC environment, and the receiver and PKG are both in the IBC environment. KGC exposes its system parameters params 0 , and randomly select a master key s 0 , PKG exposes its system parameters params 1 , and randomly select a master key s 1 , KGC system parameter params 0 And the system parameter params of PKG 1 Are not the same.
[0067] Specifically, the KGC system parameter params 0 The generati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com