Undeniable secure data transmission method based on block chain
A technology for secure data and transmission methods, applied in the field of undeniable secure data transmission based on blockchain, which can solve the problems of cost, low efficiency, and the difficulty of long-term safe preservation of evidence.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
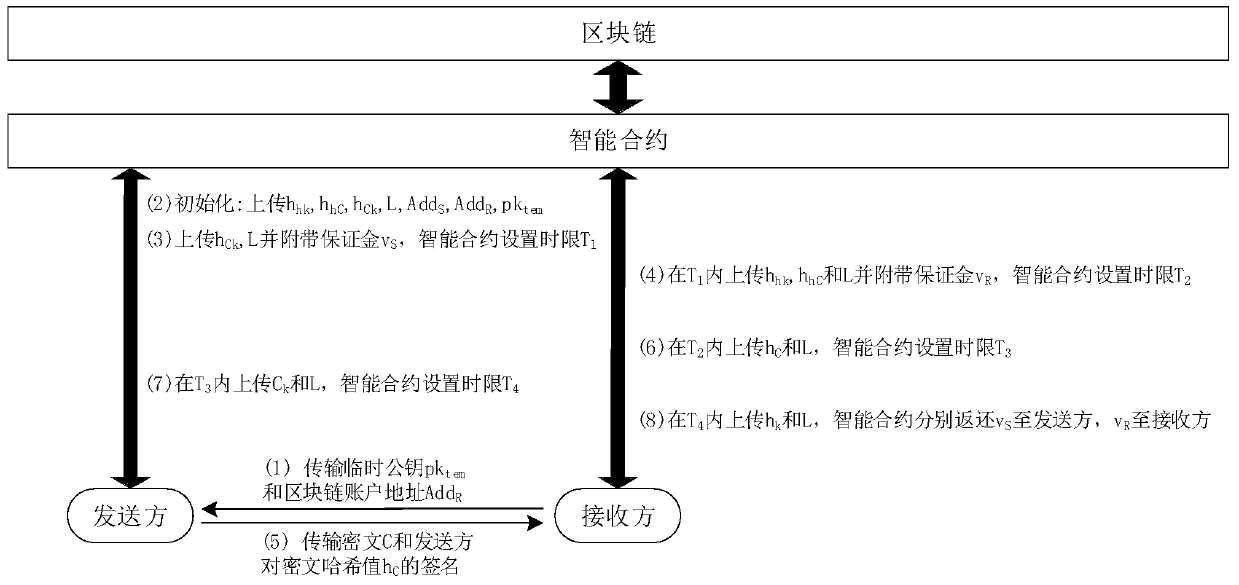
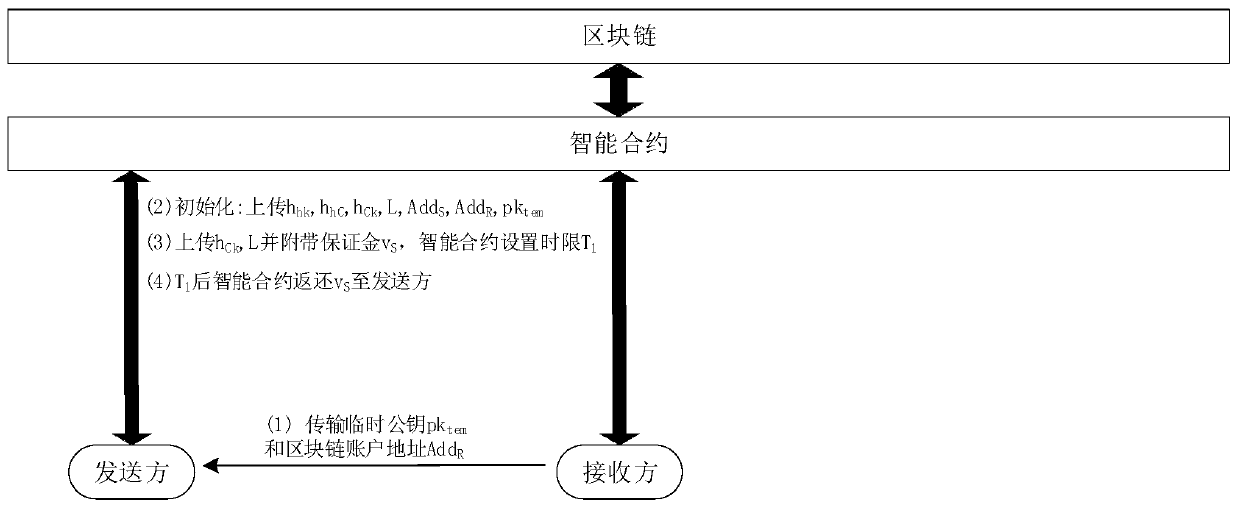
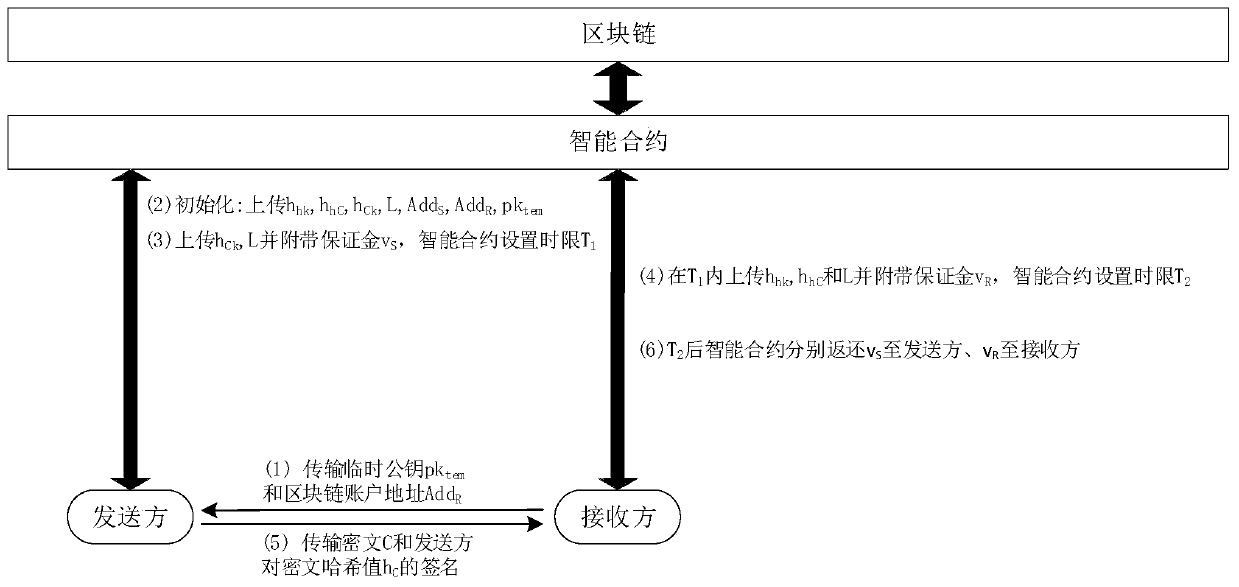
[0035] Deploy the smart contract first and disclose the contract address. Participants who need to transfer data undeniably can call any function in the smart contract through this address. Smart contracts can be applied to multiple transmission instances, and different instances are identified with different random numbers L. Considering the existence of malicious parties, a blockchain-based undeniable secure data transmission method includes the following steps:
[0036] (1) The recipient locally generates a temporary public-private key pair (sk tem ,pk tem ), and the temporary public key pk tem and your own blockchain account address Add R Sent to the sender via a normal channel independent of the blockchain.
[0037] (2) After receiving the receiver's temporary public key and blockchain account address, the data sender genera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com