Mobile transaction privacy protection method based on bidirectional identity authentication of near field communication
A two-way identity authentication and near-field communication technology, applied in the field of two-way identity authentication, to reduce the burden, ensure security, and achieve the effects of anonymity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
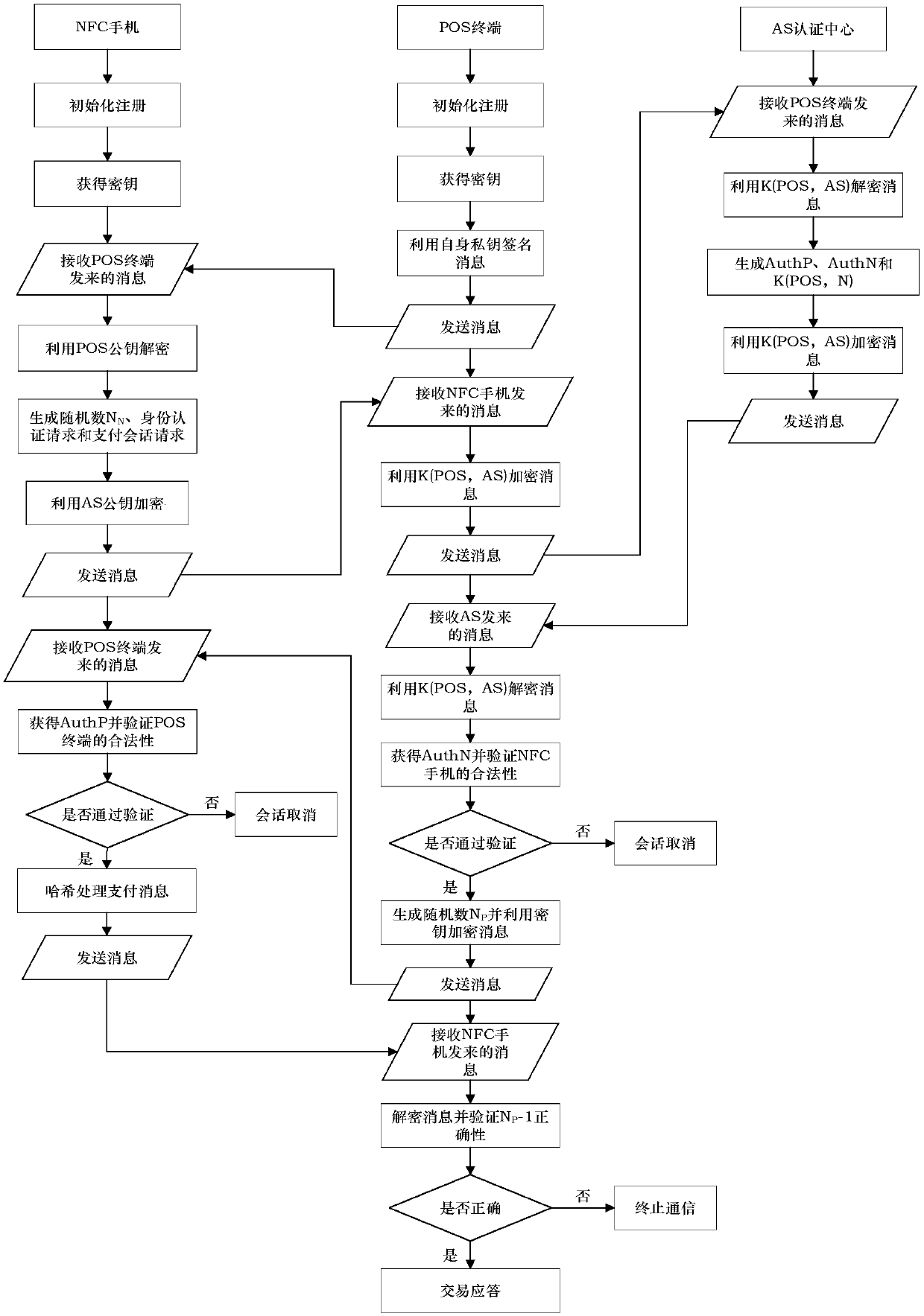
[0039] Initialization phase:
[0040] (1) Introduce a trusted third-party authentication agency AS, which is responsible for generating the session key K(a,b) between the NFC mobile phone and the POS terminal during the communication process, the authentication message AuthP of the AS to the POS terminal, and the AS to the NFC device The authentication message AuthN. AS generates system public-private key pair PK AS ||SK AS , contains a security application that allows verification of digital signatures, stores a list of trusted certificates and the hash function H needed to use in the communication process, etc. The AS discloses its public key and keeps its private key secret.
[0041] (2) The user's NFC mobile phone requests registration by sending its own ID to the AS. The user performs a hash algorithm on the ID, and the generated H(ID) is used as the public key, and then sends the public key to the AS to generate the private key of the NFC mobile phone. , so as to obt...
Embodiment 2
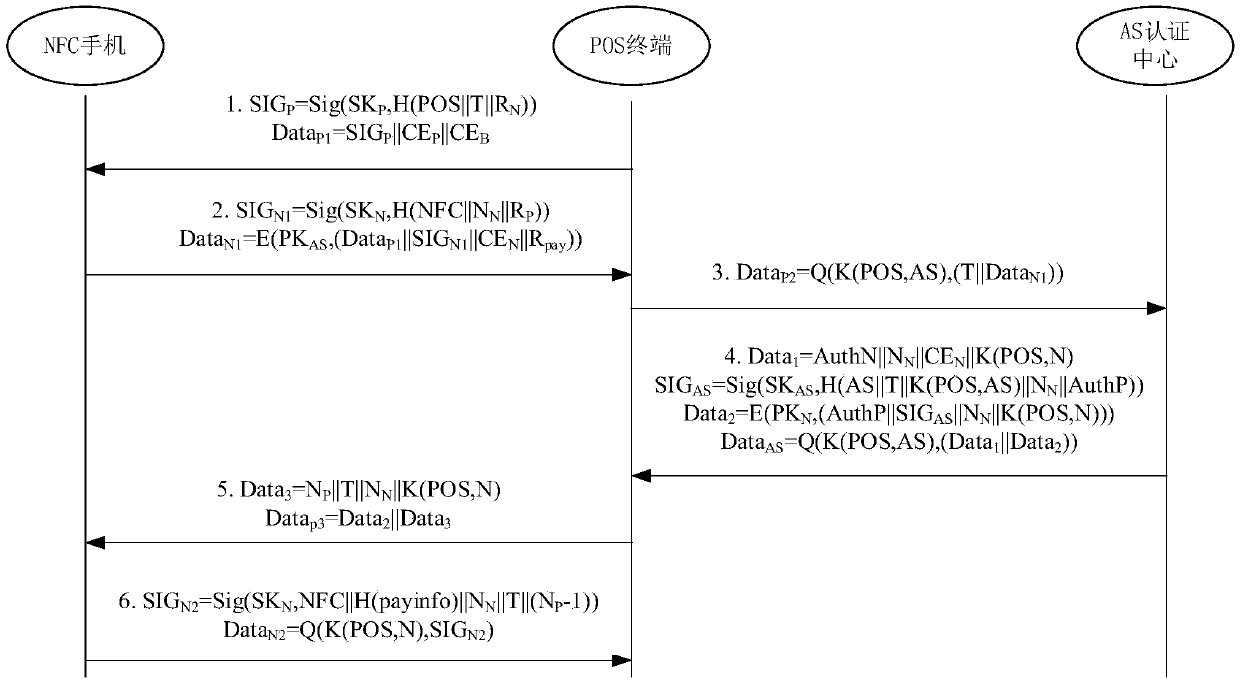
[0043] Two-way identity authentication process between NFC mobile phone device and POS terminal:
[0044] (1) POS→NFC: The POS terminal sends a request message to the NFC mobile phone, including the current unique transaction timestamp T generated by the POS terminal, and the identity authentication request R of the POS terminal to the NFC mobile phone N , trusted security certificate CE for POS terminals P , Acquiring bank trusted security certificate CE B , and the signature SIG of the POS terminal P . SIG P is to use the private key SK of the POS terminal P For messages POS, TD and R N The hash value signature obtained, SIG P =Sig(SK P ,H(POS||T||R N )). Message packet Data P1 including SIG P 、CE P and CE B , Data P1 =SIG P ||CE P ||CE B . POS terminal will Data P1 Send to NFC mobile phone device. SIG P 、CE P and CE P Allows authentication of POS terminals, guaranteeing T and R N The integrity of the message is transmitted, and it can ensure that the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com