Method for utilizing fingerprint to improve information transmission security
A technology of information transmission and fingerprint identification, which is applied in transmission systems, digital transmission systems, secure communication devices, etc., and can solve problems such as transaction security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
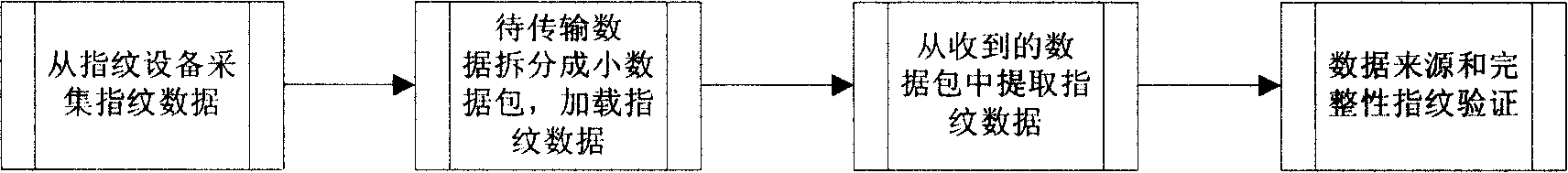
[0040] 1. Collect fingerprint data from the fingerprint device:
[0041] (1) Obtain personal fingerprint images through fingerprint collection equipment;
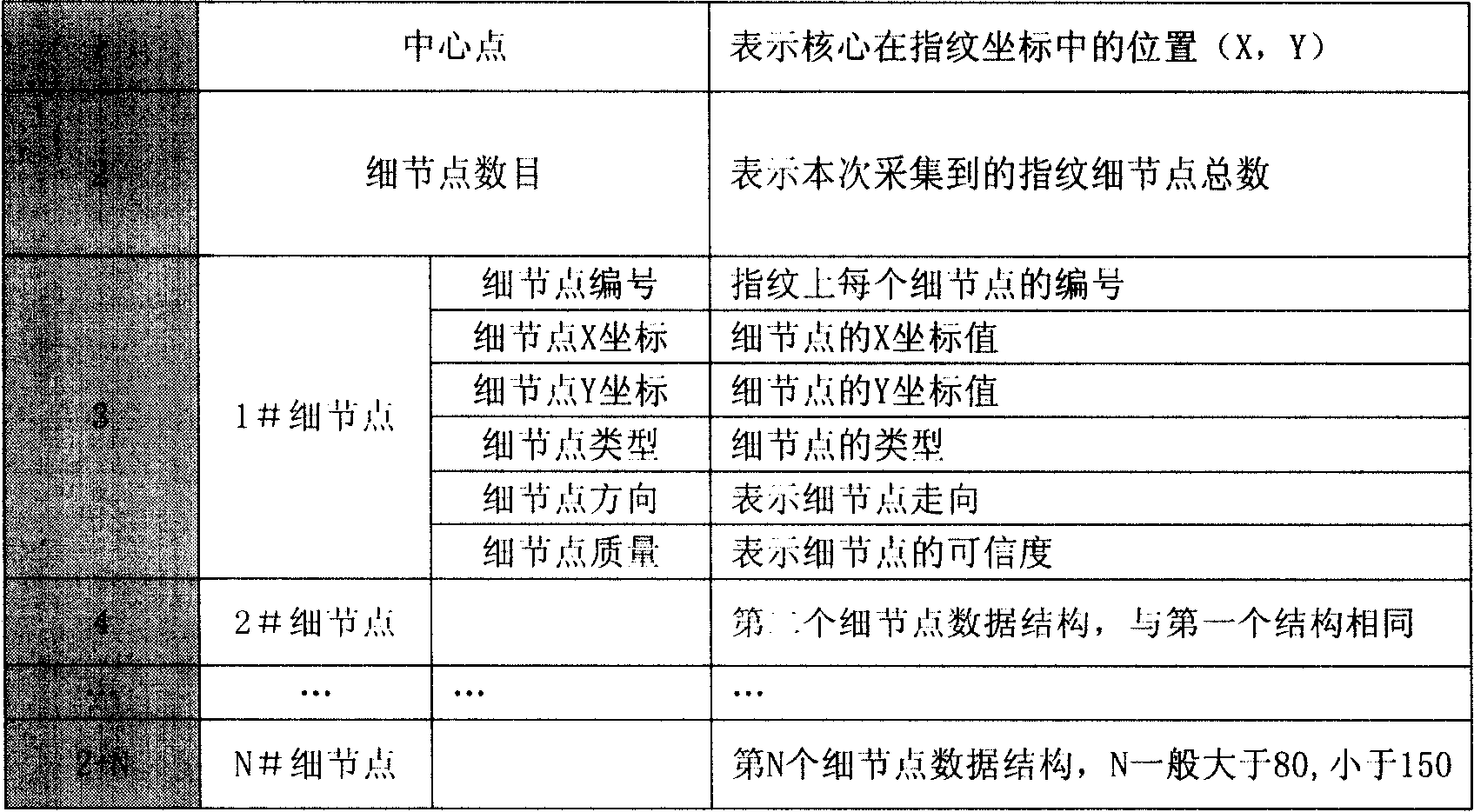
[0042] (2) Extract personal fingerprint feature values from the fingerprint image as fingerprint signature data, indicating the identity of the sender of the data, and there are no less than 7 fingerprint feature values (detail points). The fingerprint feature value (fingerprint minutiae) data composition is as follows: figure 2 .
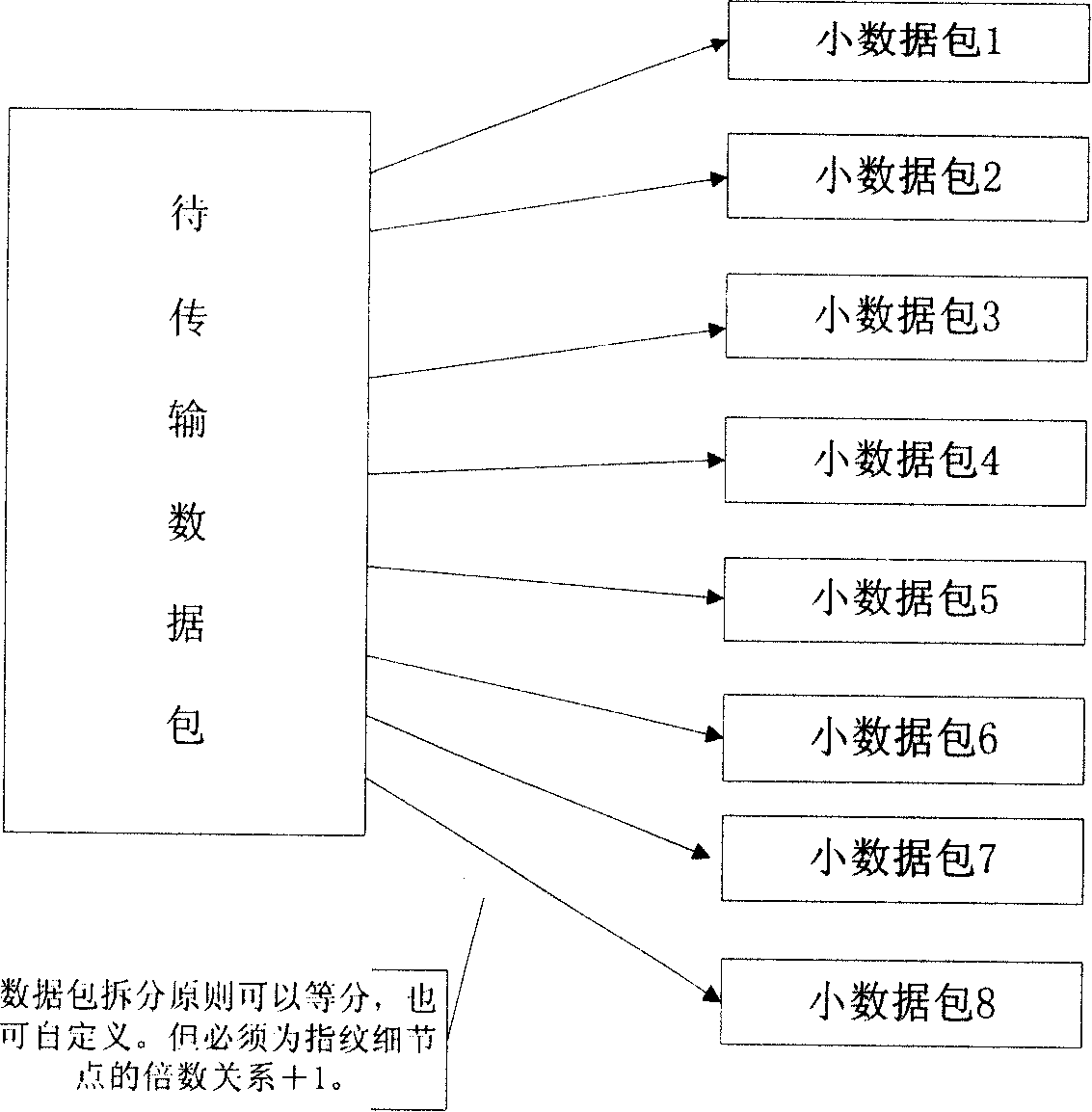
[0043] 2. Load fingerprint data in the data packet to be transmitted:
[0044] (1) see image 3 , Divide the data packet to be transmitted into several small data packets. The number of small data packets is equal to or multiplied by the number of fingerprint detail points +1; the principle of data packet splitting can be divided into equal parts or customized, but it must be the multiple relationship of fingerprint detail points +1.
[0045] (2) The fingerprint feature value data is d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com