Remote data integrity verification method based on short signature
An integrity verification, remote data technology, applied in the field of data integrity verification, can solve problems such as user data threats, achieve high signature efficiency, prevent leakage or forgery, and reduce computational overhead and communication overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In order to make the purpose, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and the experimental conditions of the examples.
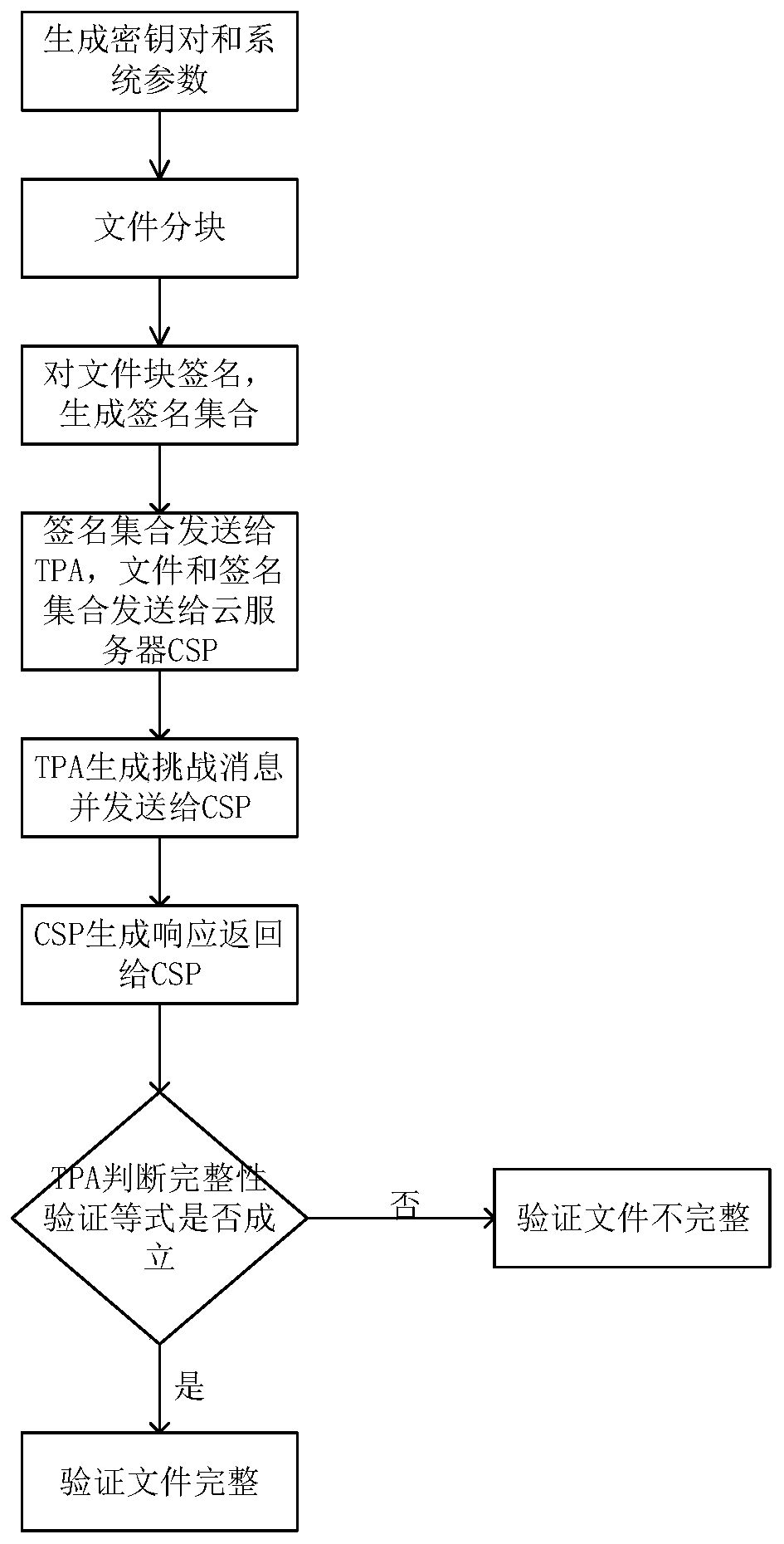
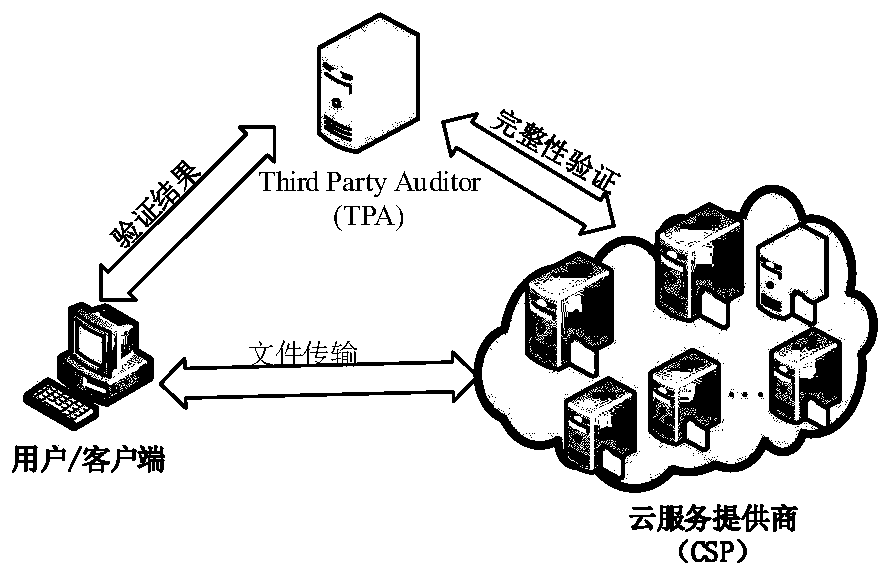
[0037] Please refer to figure 1 , the method includes the following five algorithms:
[0038] 1. When the user needs to store a large amount of data on the cloud storage server, it is necessary to initialize the system parameters and generate a secret key pair, KeyGen(k)→(pk,sk): the client inputs the security parameter k and outputs the user's public key pk, private key sk. Public pk, private key sk is kept by the user. This step can be pre-processed before signature verification, saving verification time.
[0039] 2. Then, the user executes the signature generation algorithm SigGen(sk,m)→σ, uses the private key generated in the previous step to sign the input file m, and generates the signature set σ of the dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com