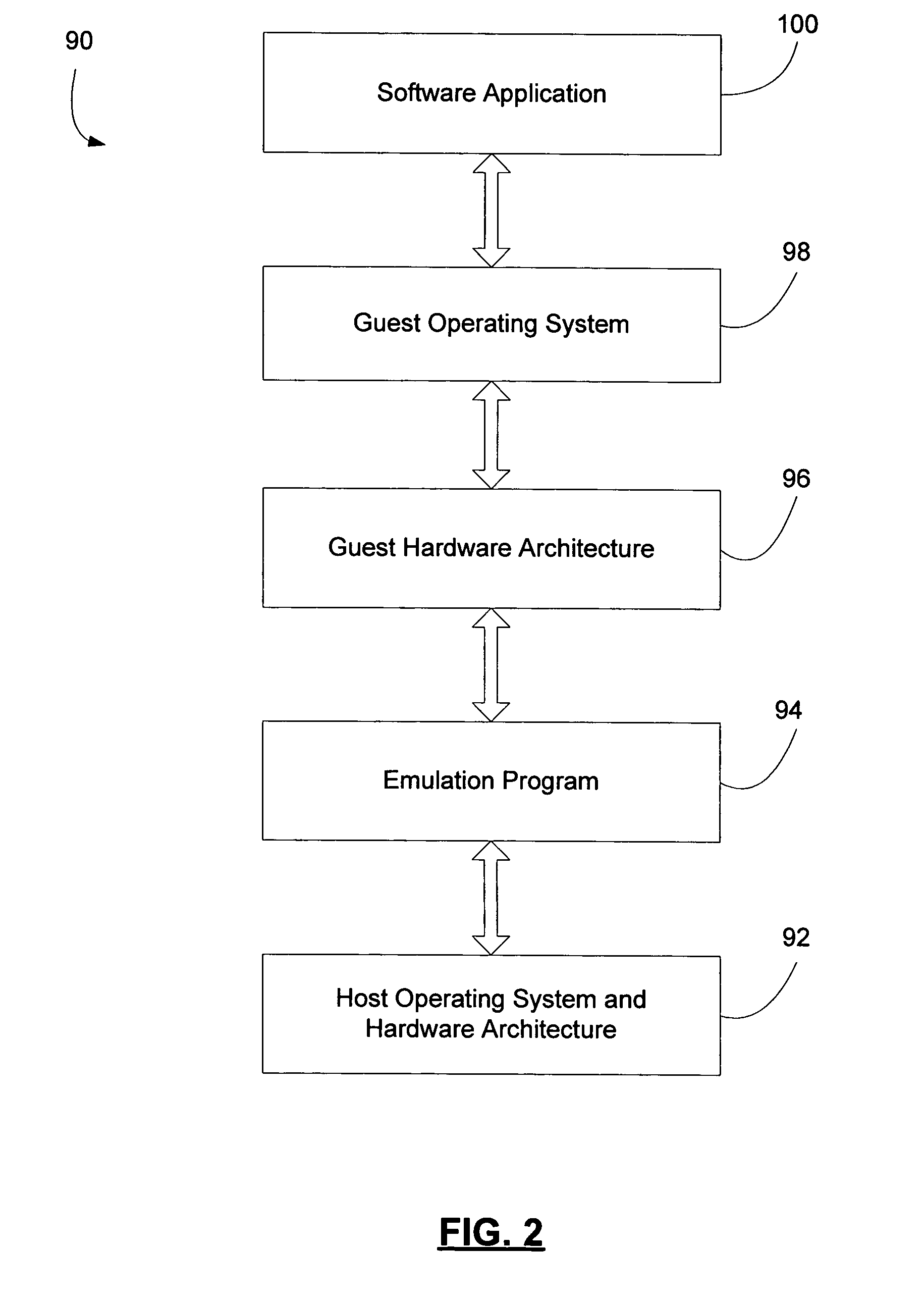
Patents
Literature
4038results about "Stamping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
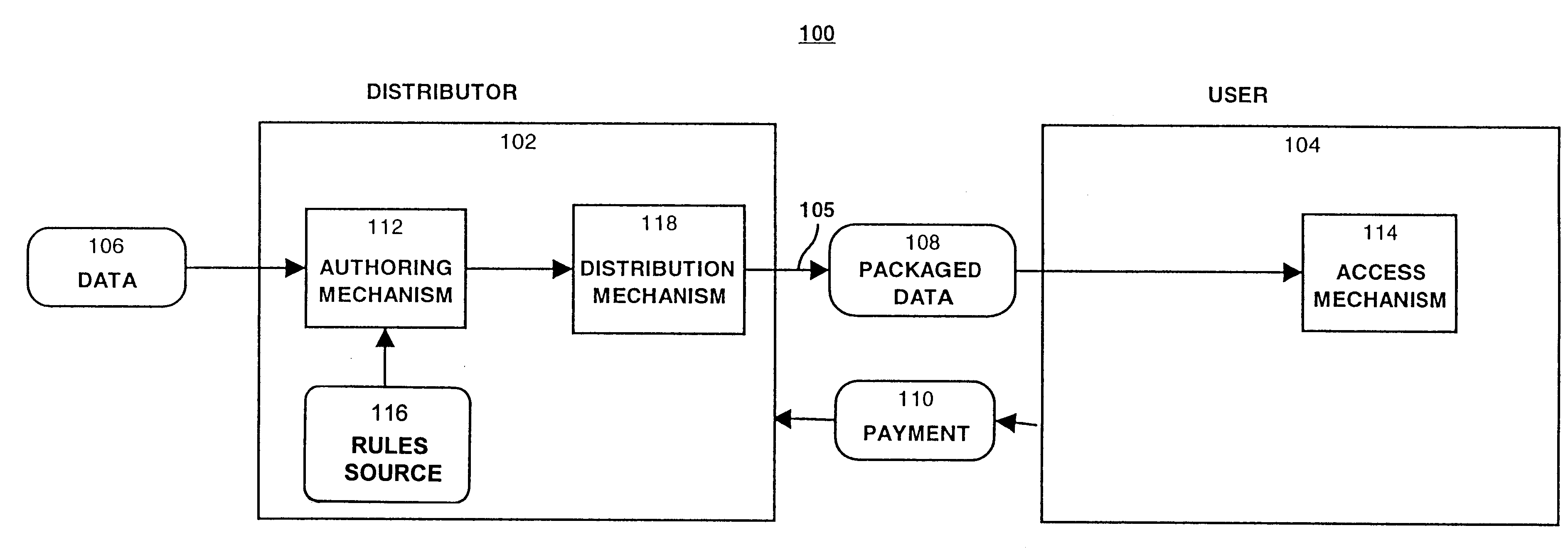
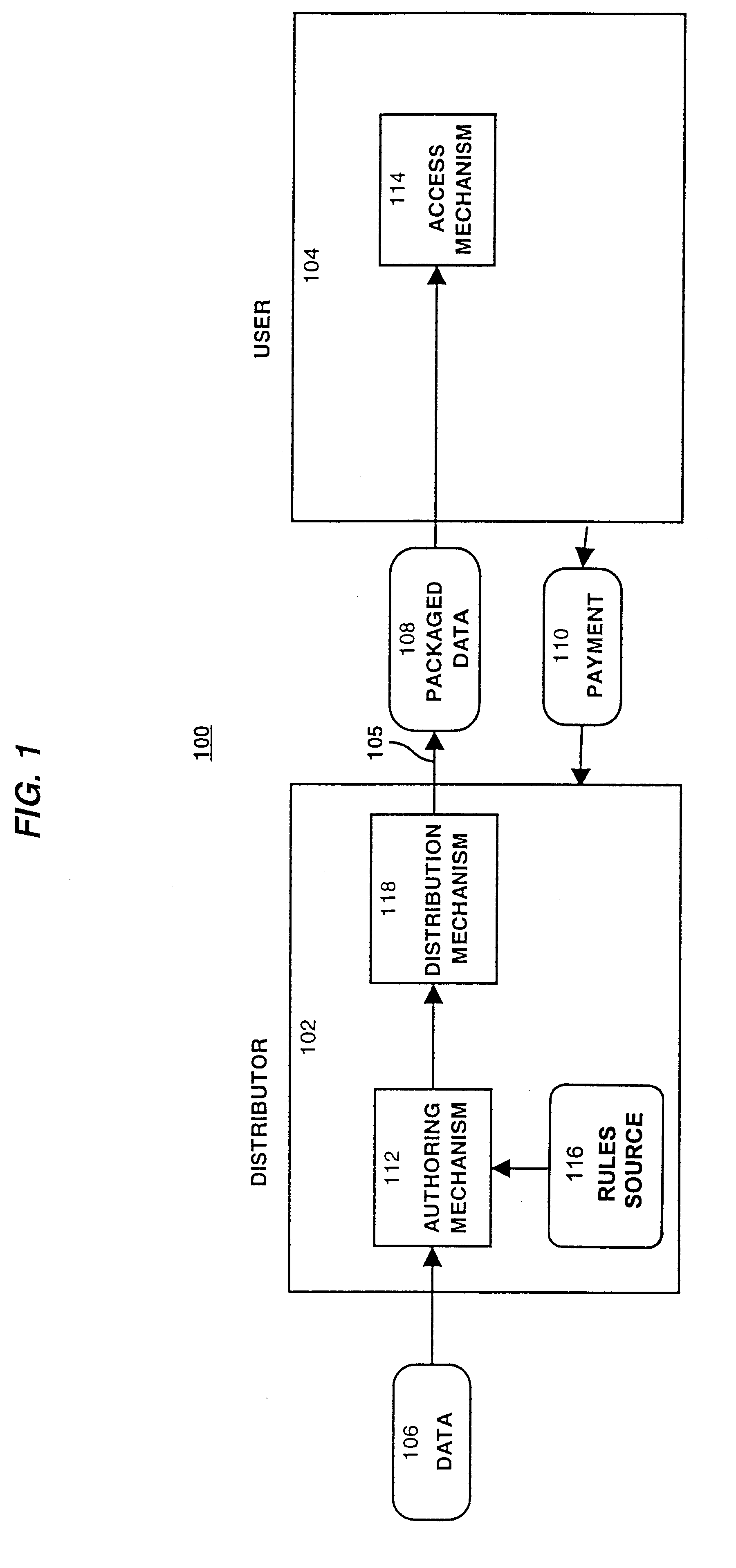
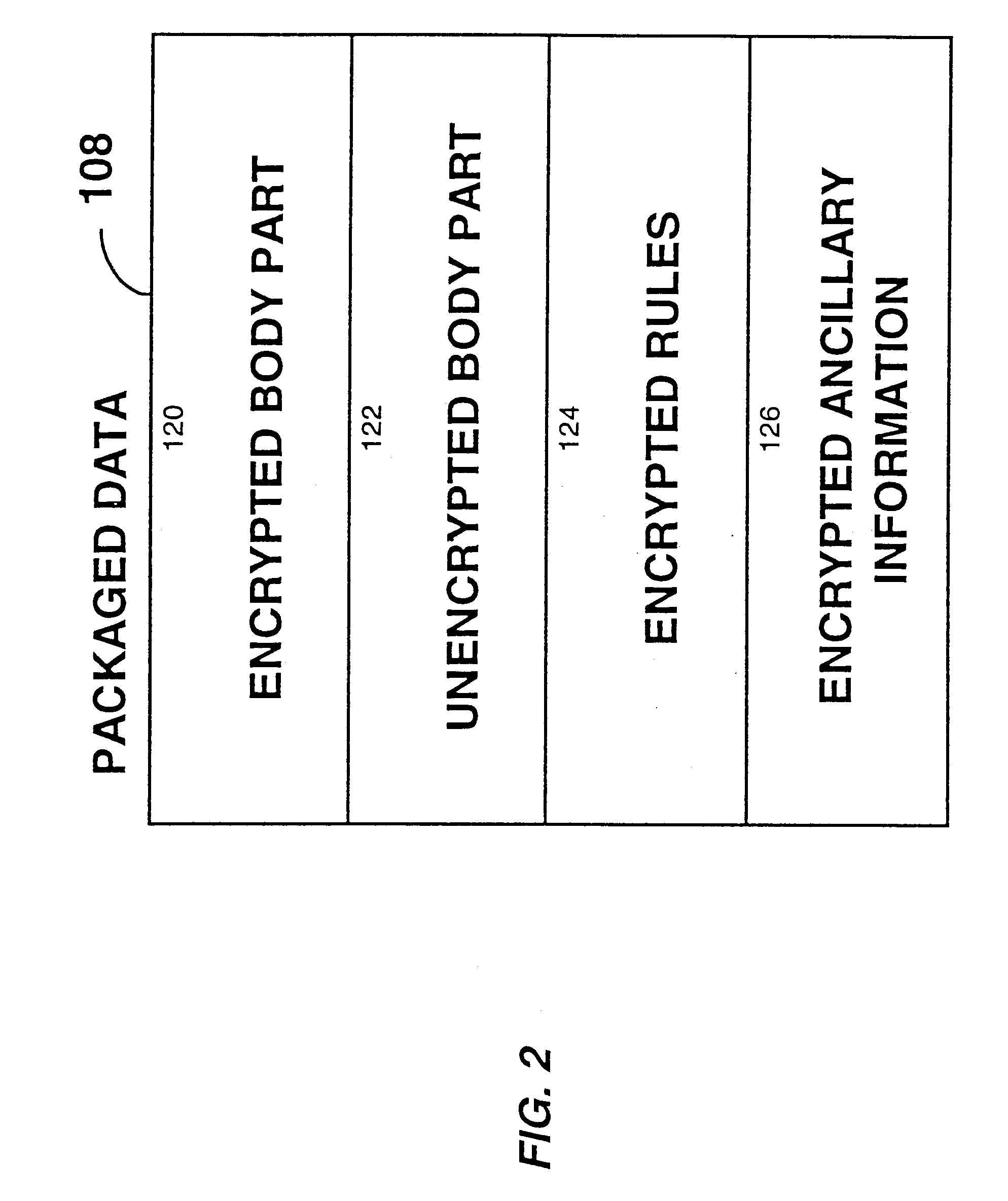
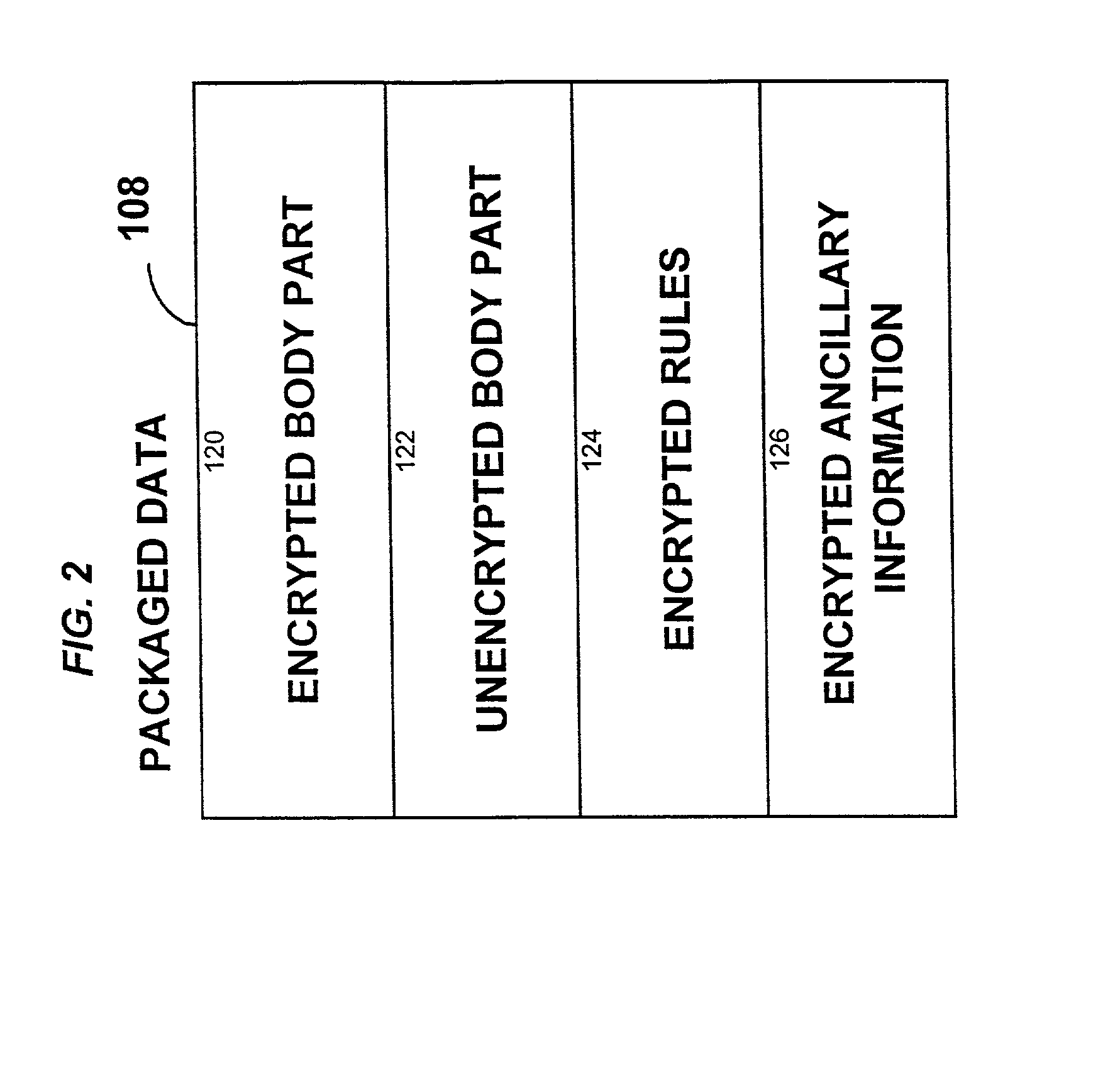
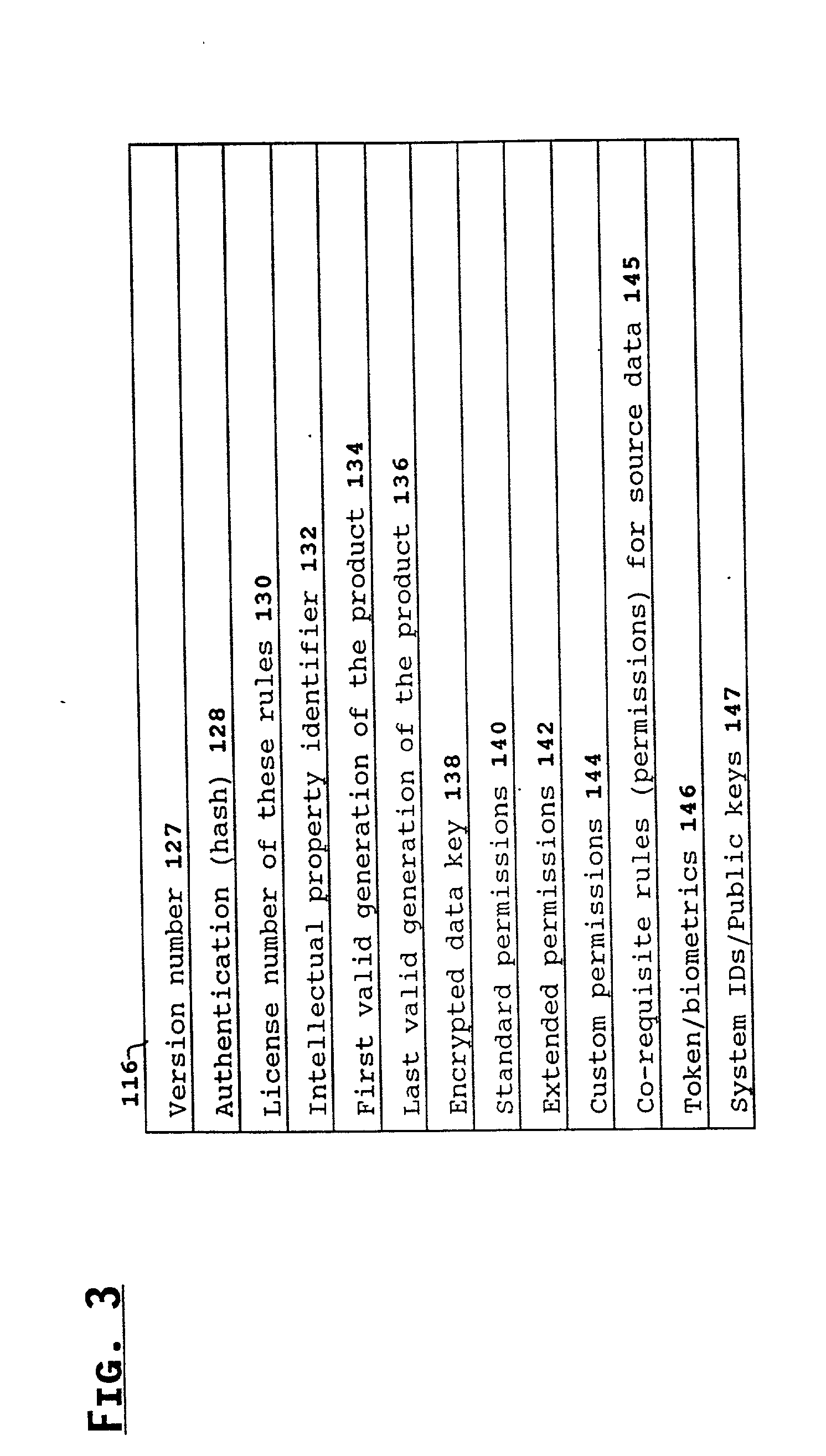
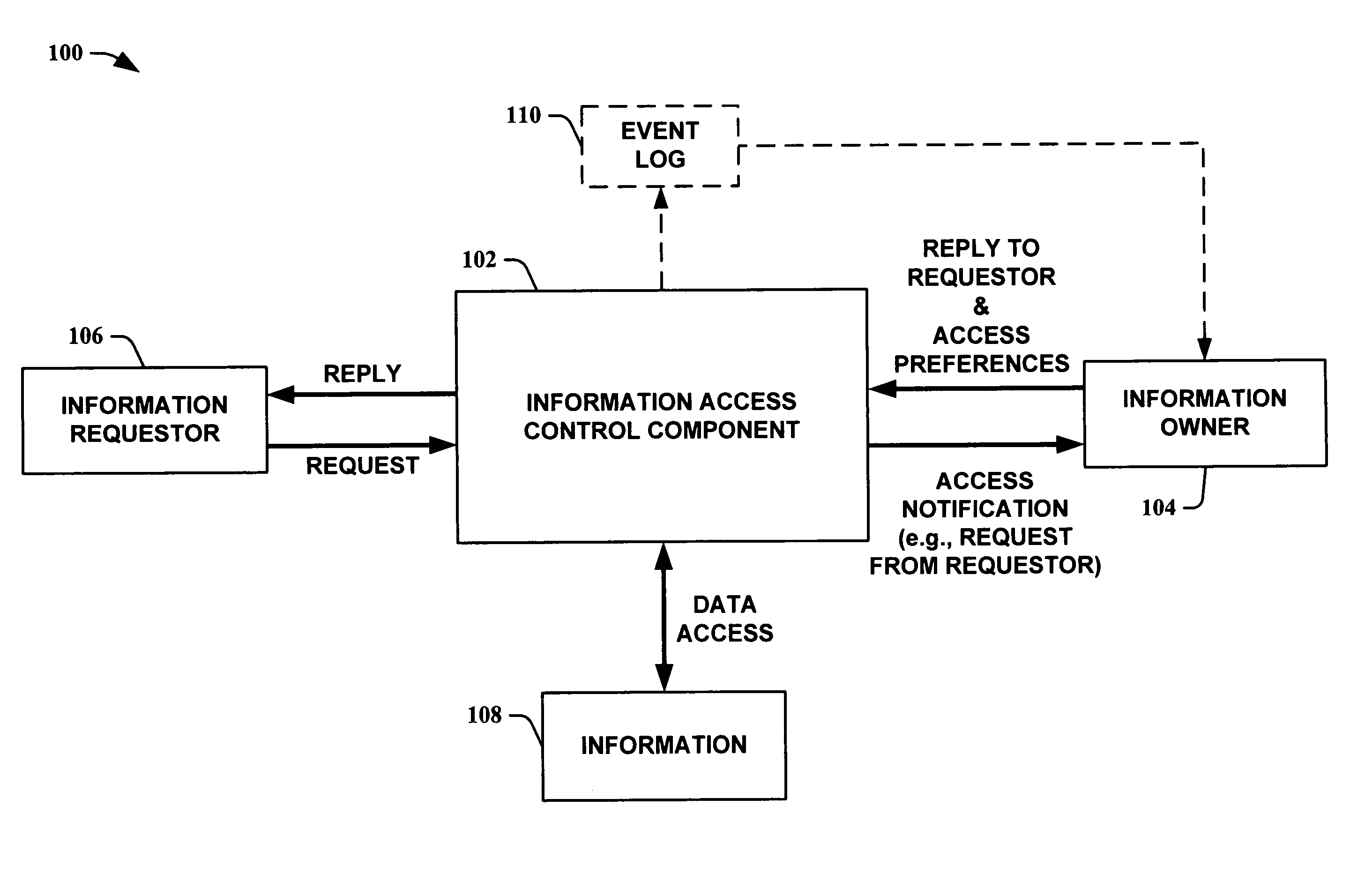
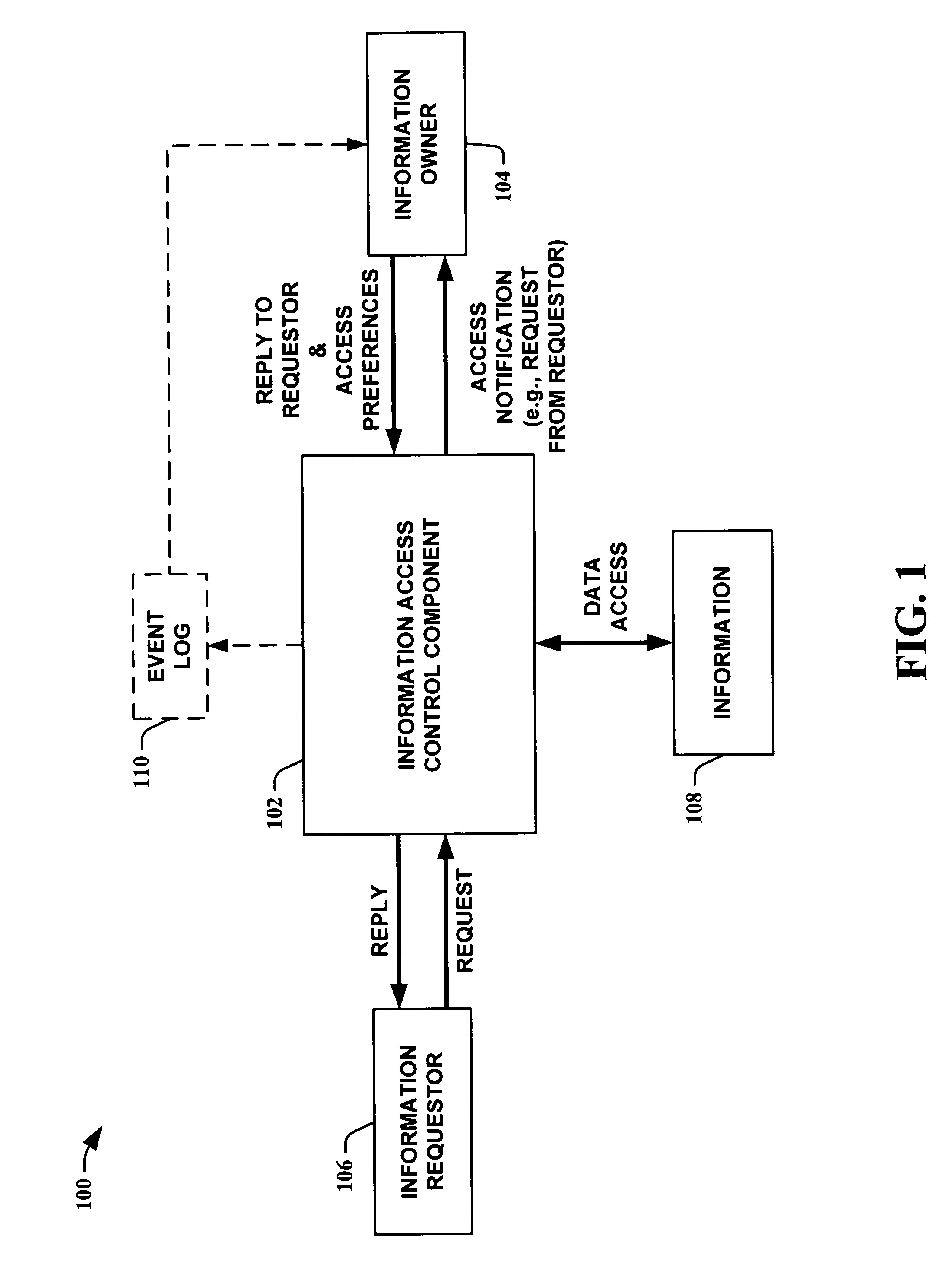
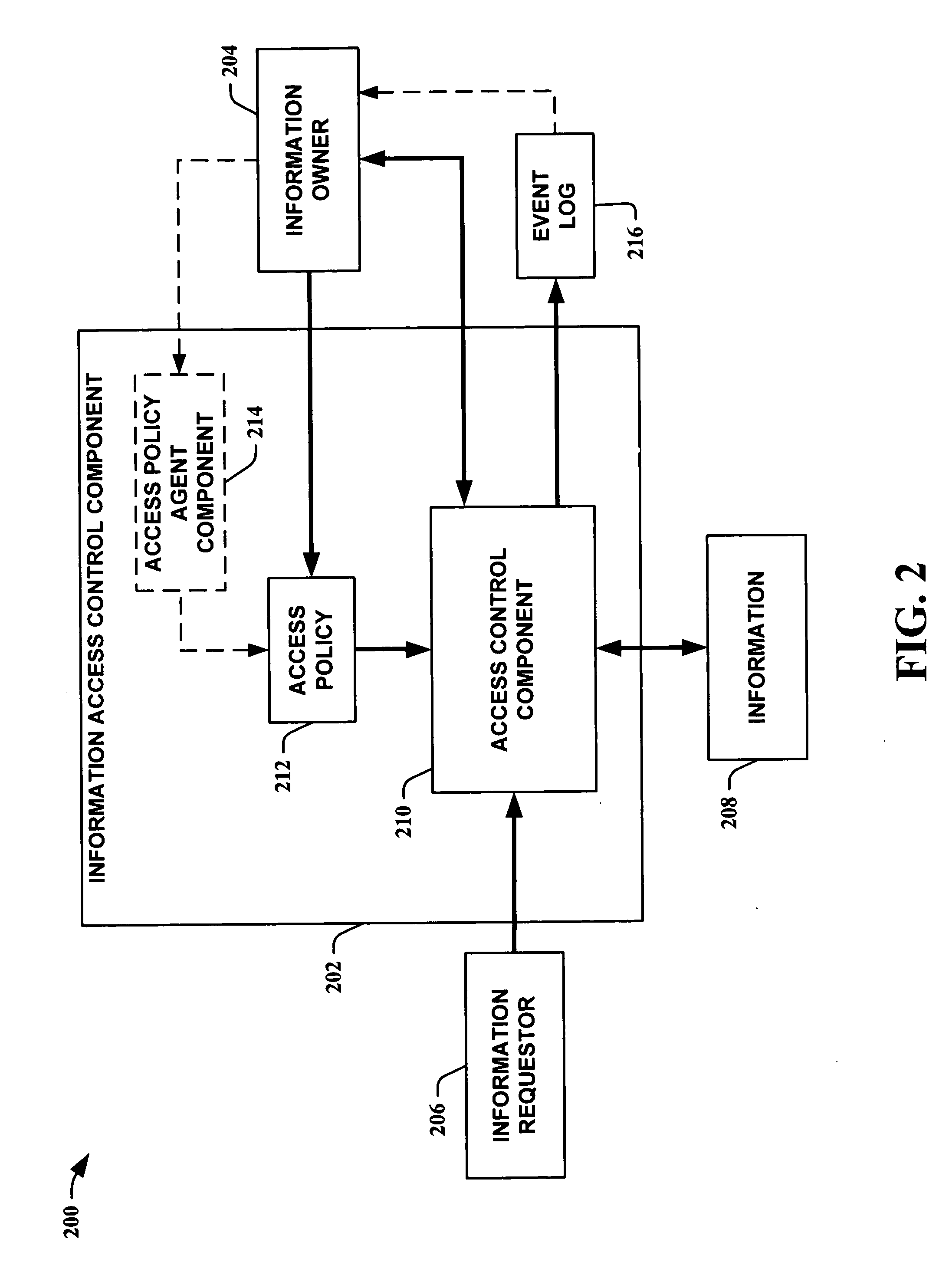
System for controlling access and distribution of digital property
InactiveUS6314409B2Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
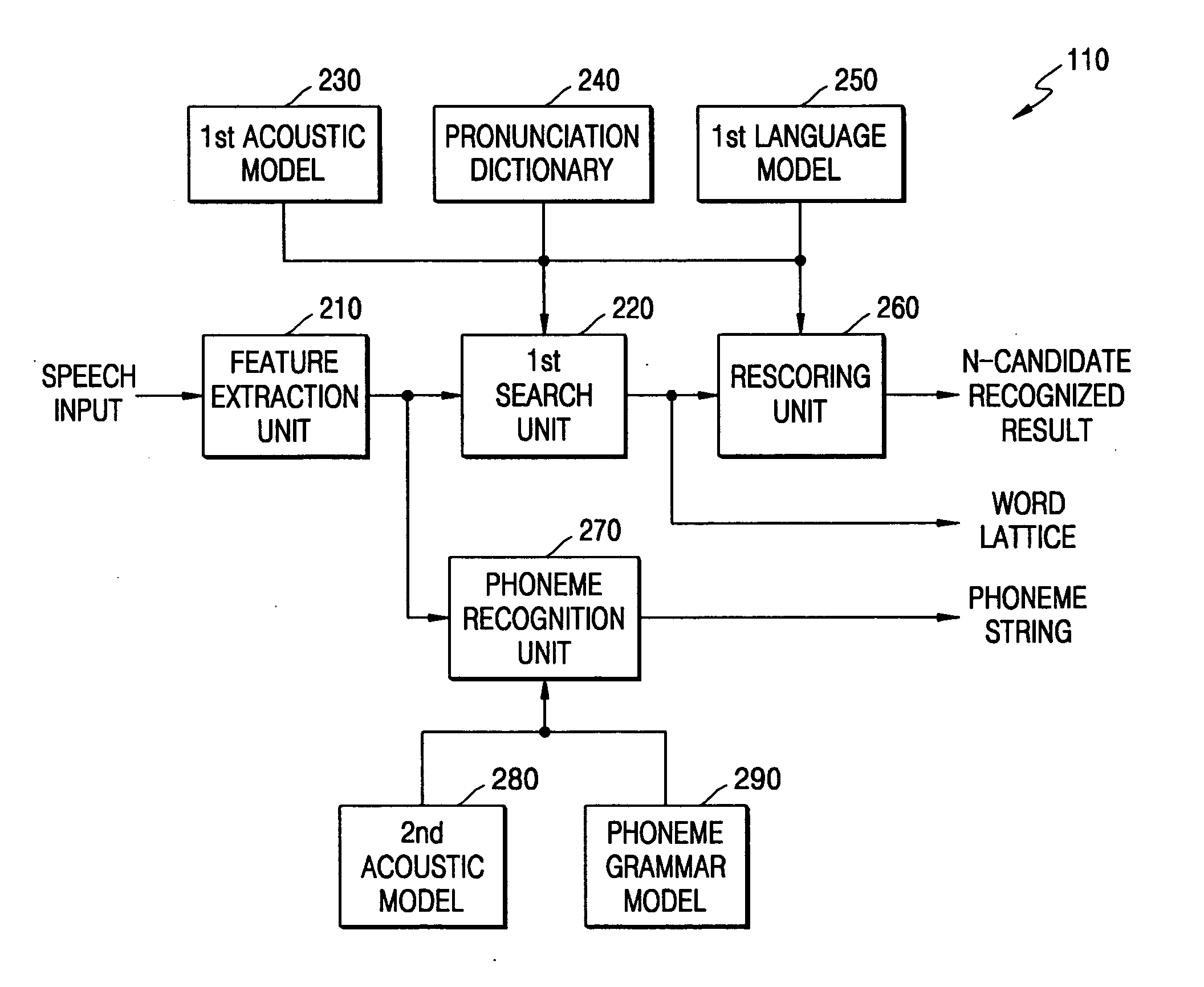
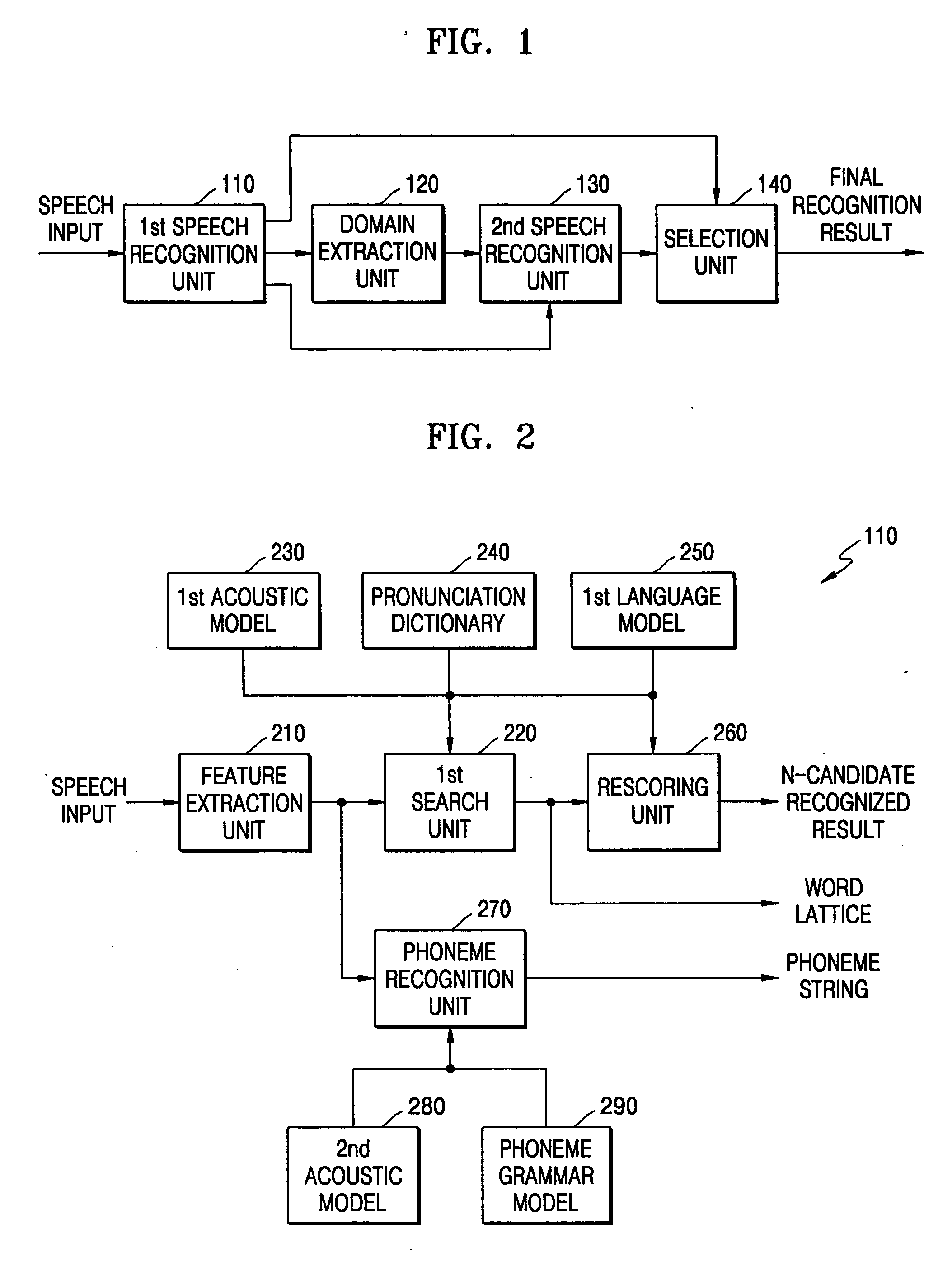
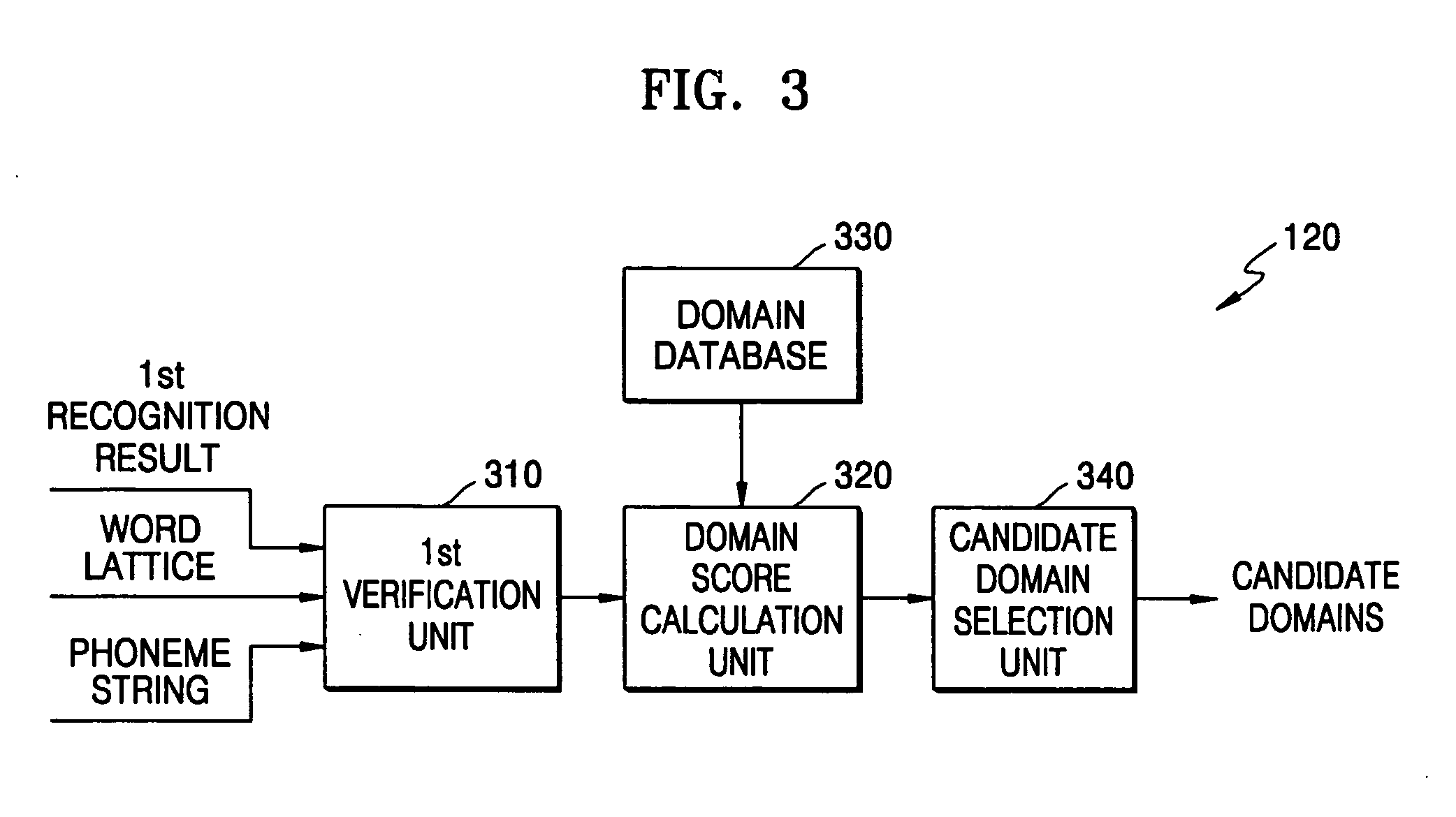
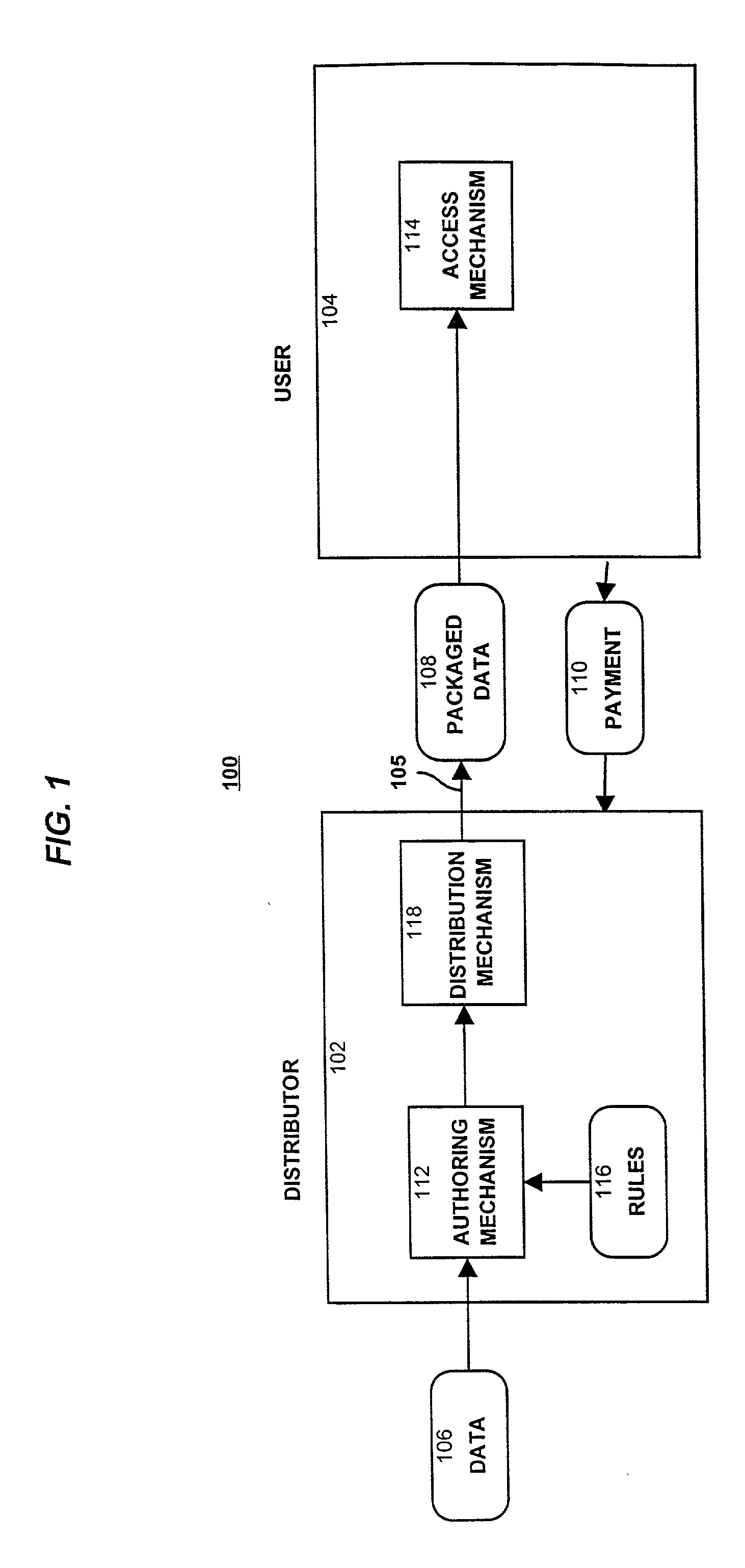
Domain-based dialog speech recognition method and apparatus
A domain-based speech recognition method and apparatus, the method including: performing speech recognition by using a first language model and generating a first recognition result including a plurality of first recognition sentences; selecting a plurality of candidate domains, by using a word included in each of the first recognition sentences and having a confidence score equal to or higher than a predetermined threshold, as a domain keyword; performing speech recognition with the first recognition result, by using an acoustic model specific to each of the candidate domains and a second language model and generating a plurality of second recognition sentences; and selecting at least one or more final recognition sentence from the first recognition sentences and the second recognition sentences. According to this method and apparatus, the effect of a domain extraction error by misrecognition of a word on selection of a final recognition result can be minimized.
Owner:SAMSUNG ELECTRONICS CO LTD
System for controlling access and distribution of digital property
InactiveUS20010021926A1Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
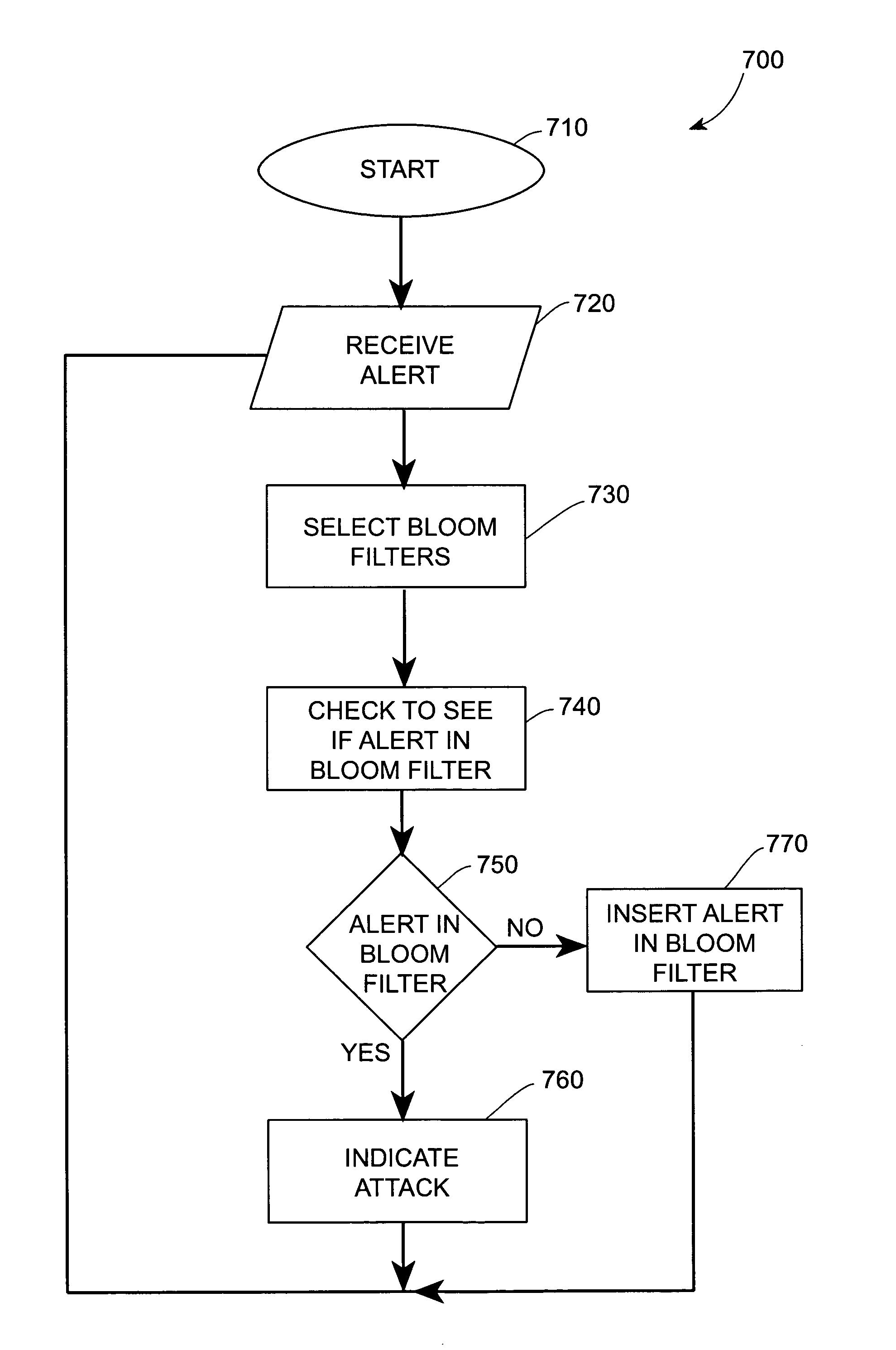
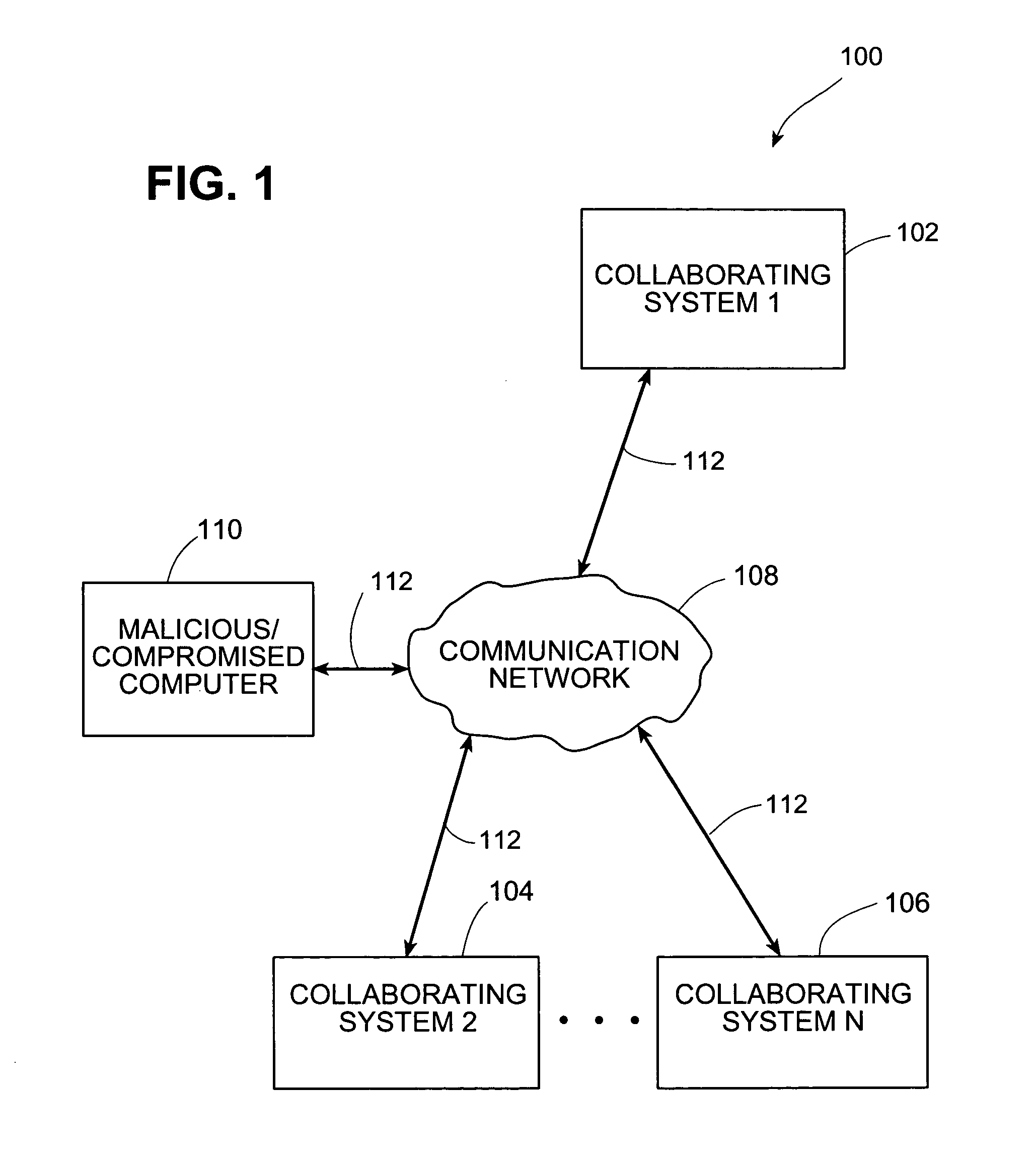
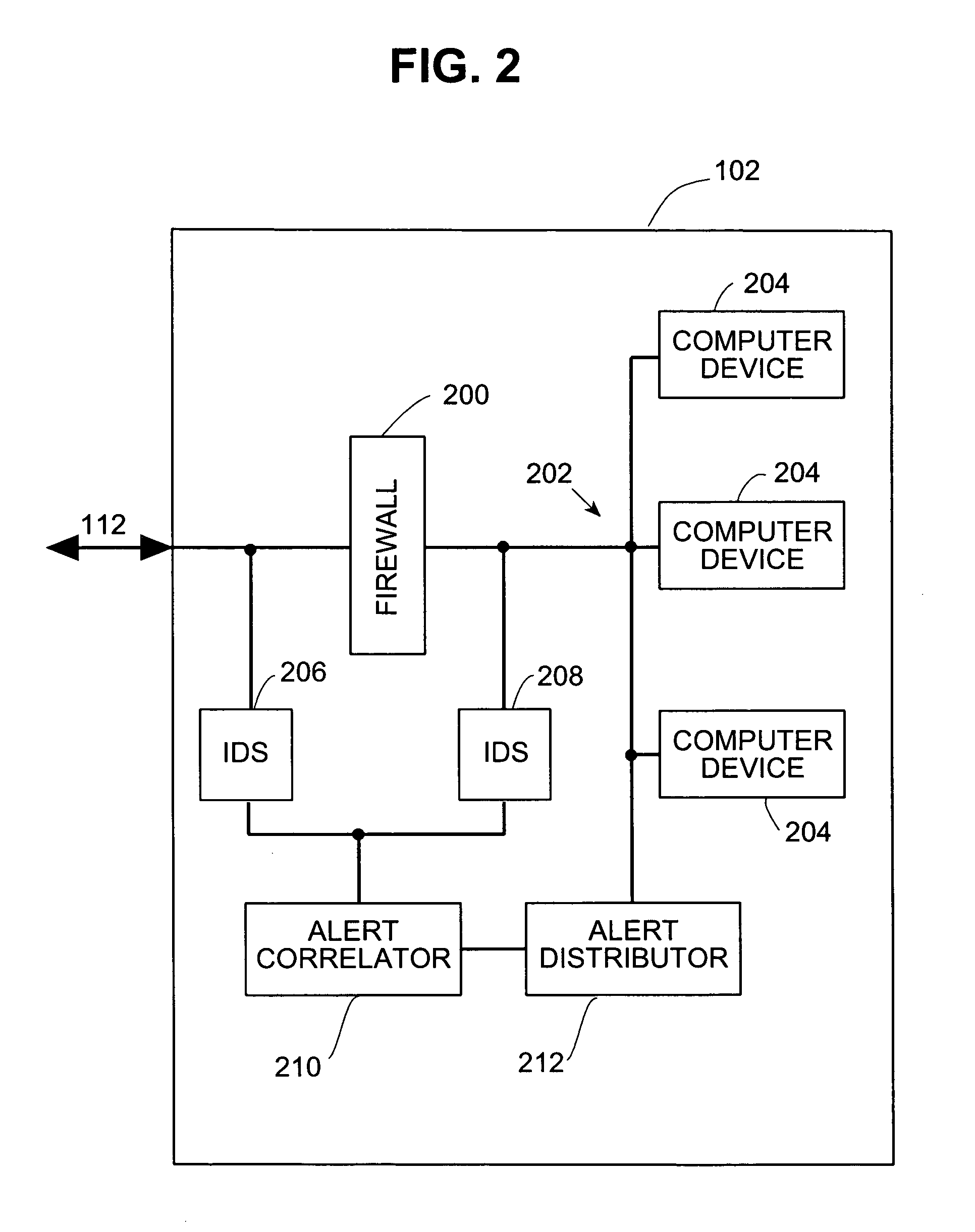
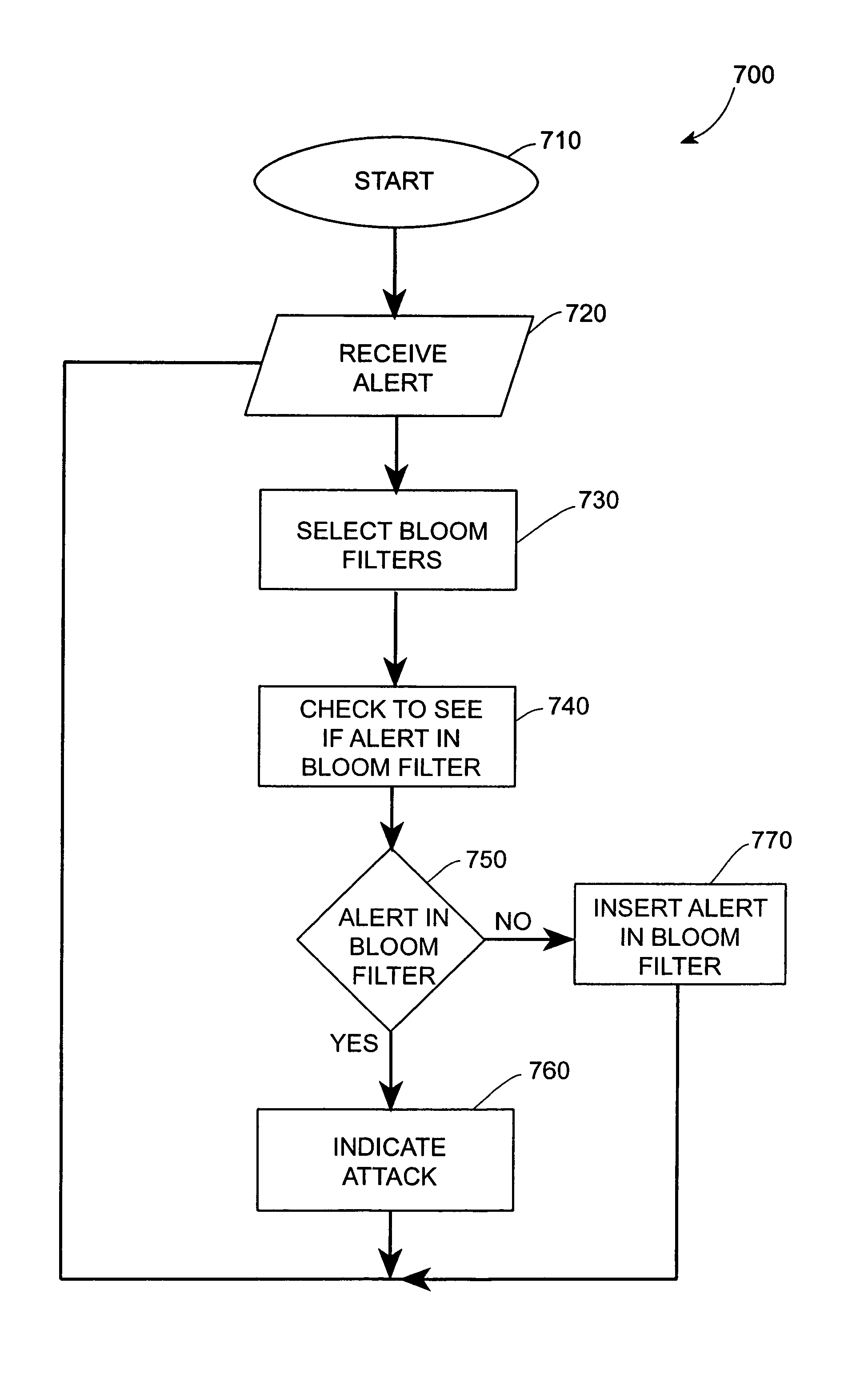
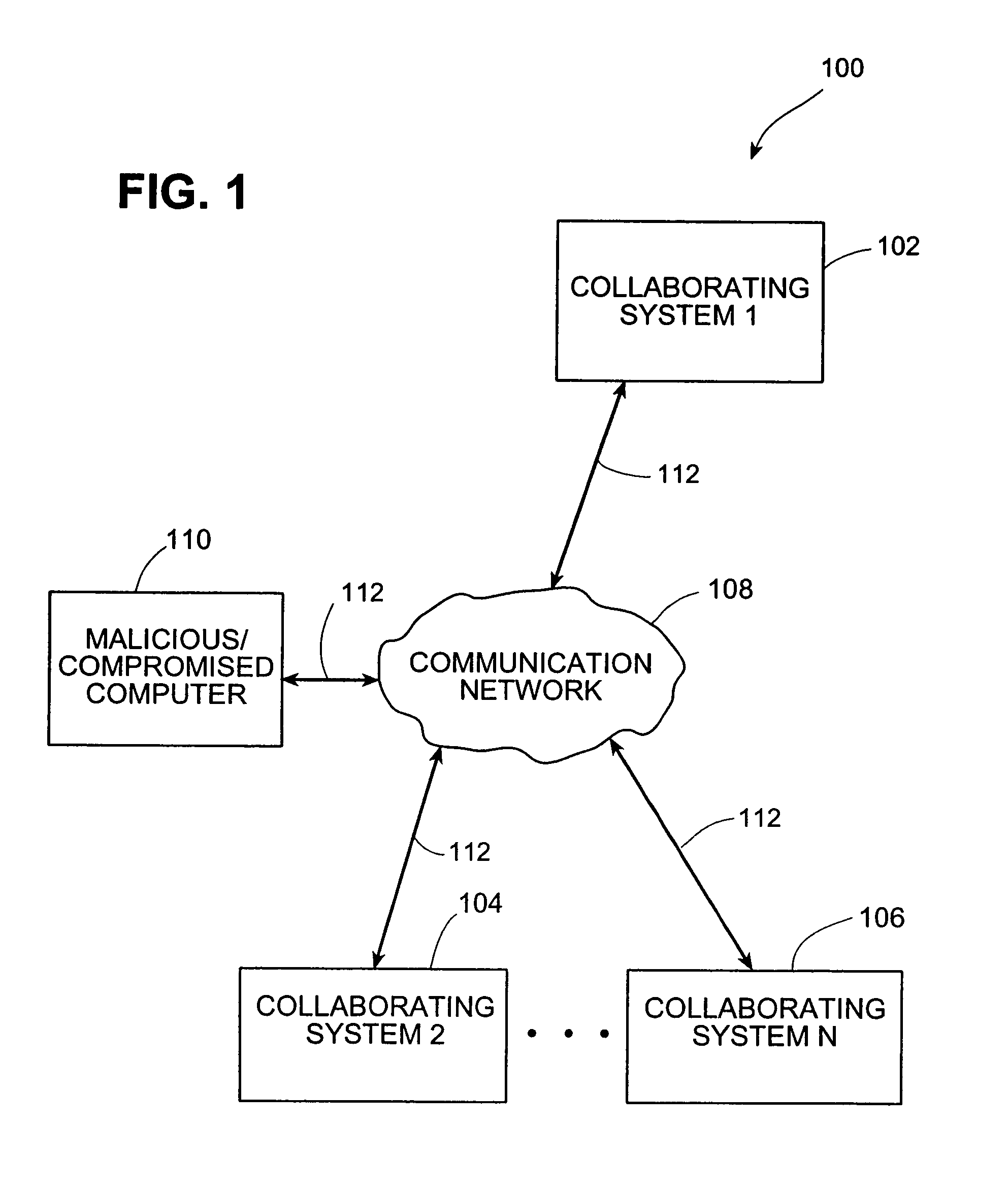
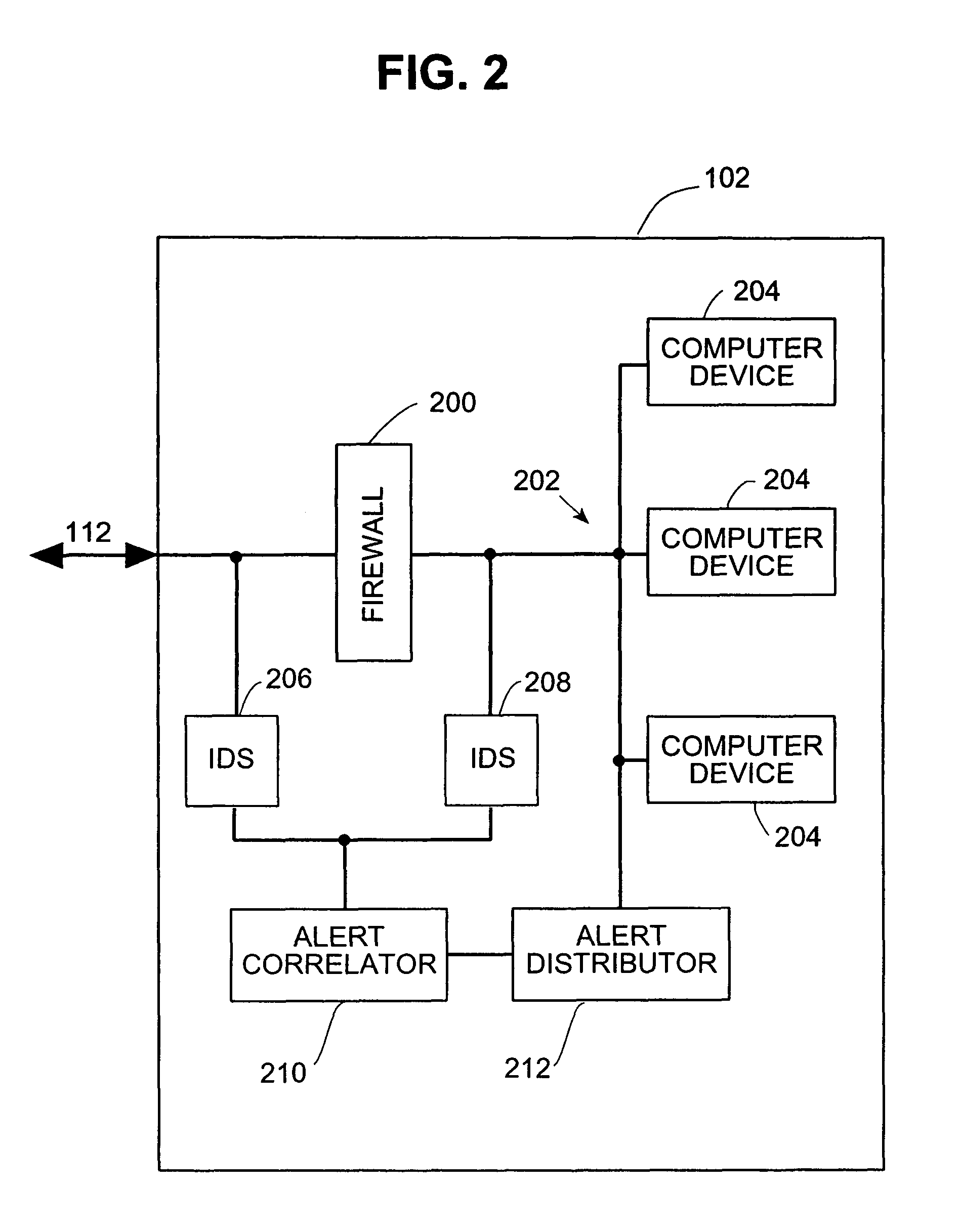
Systems and methods for correlating and distributing intrusion alert information among collaborating computer systems
ActiveUS7779463B2Technique is effectiveMemory loss protectionUser identity/authority verificationTraffic capacityEarly signs
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Systems and methods for correlating and distributing intrusion alert information among collaborating computer systems
ActiveUS7784097B1Technique is effectiveMemory loss protectionUnauthorized memory use protectionTraffic capacityCollaborative computing
Systems and methods for correlating and distributing intrusion alert information among collaborating computer systems are provided. These systems and methods provide an alert correlator and an alert distributor that enable early signs of an attack to be detected and rapidly disseminated to collaborating systems. The alert correlator utilizes data structures to correlate alert detections and provide a mechanism through which threat information can be revealed to other collaborating systems. The alert distributor uses an efficient technique to group collaborating systems and then pass data between certain members of those groups according to a schedule. In this way data can be routinely distributed without generating excess traffic loads.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
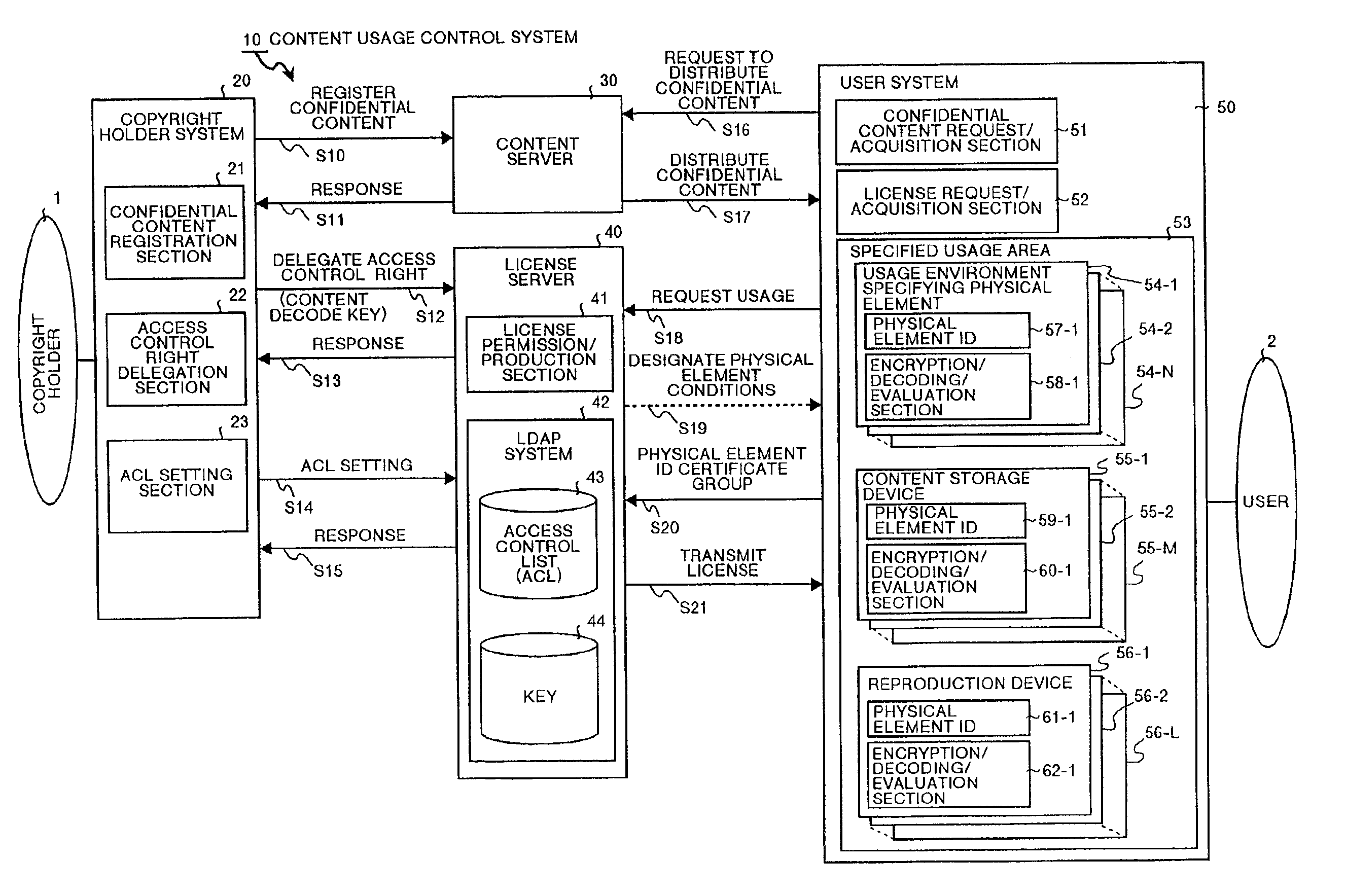
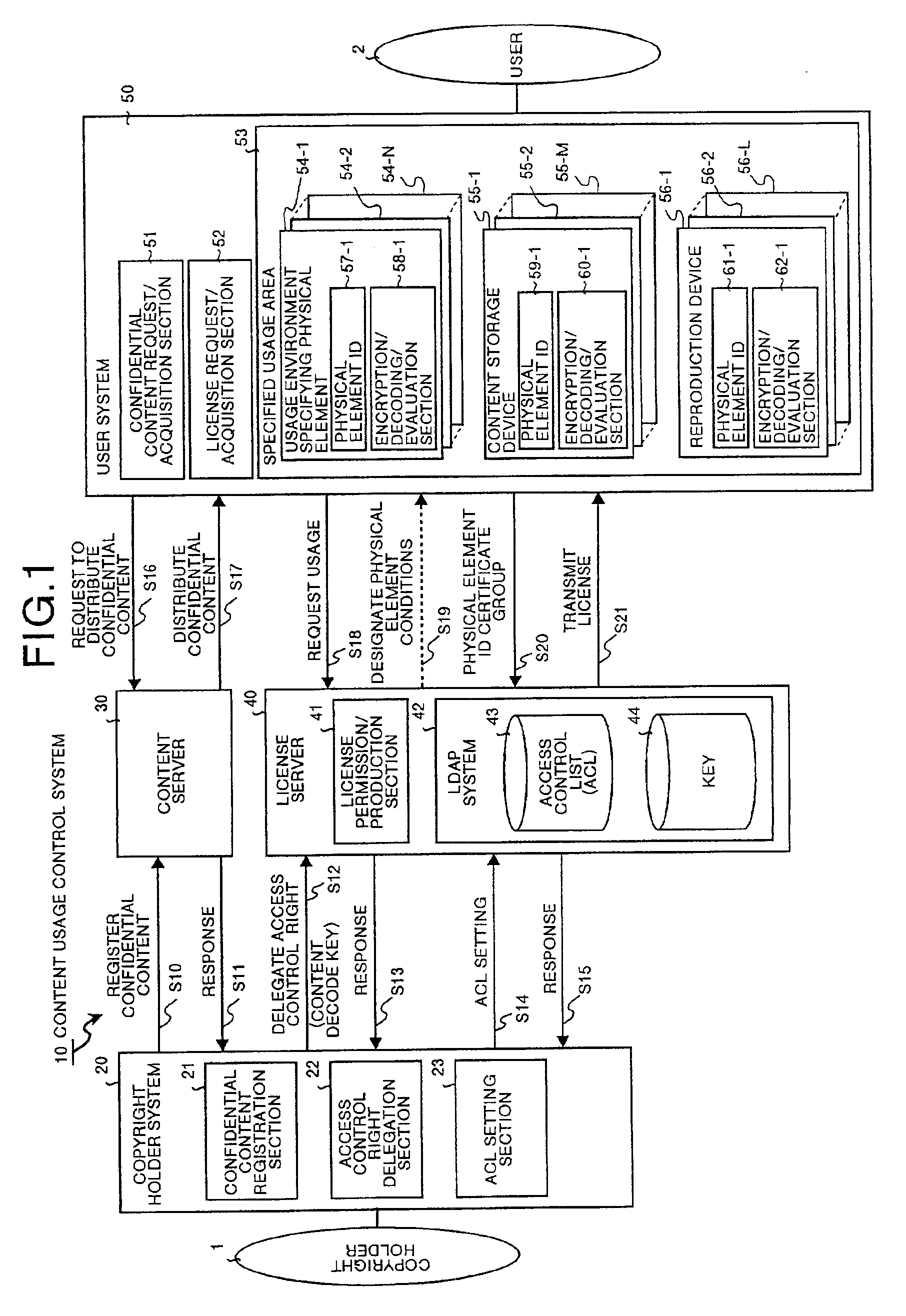
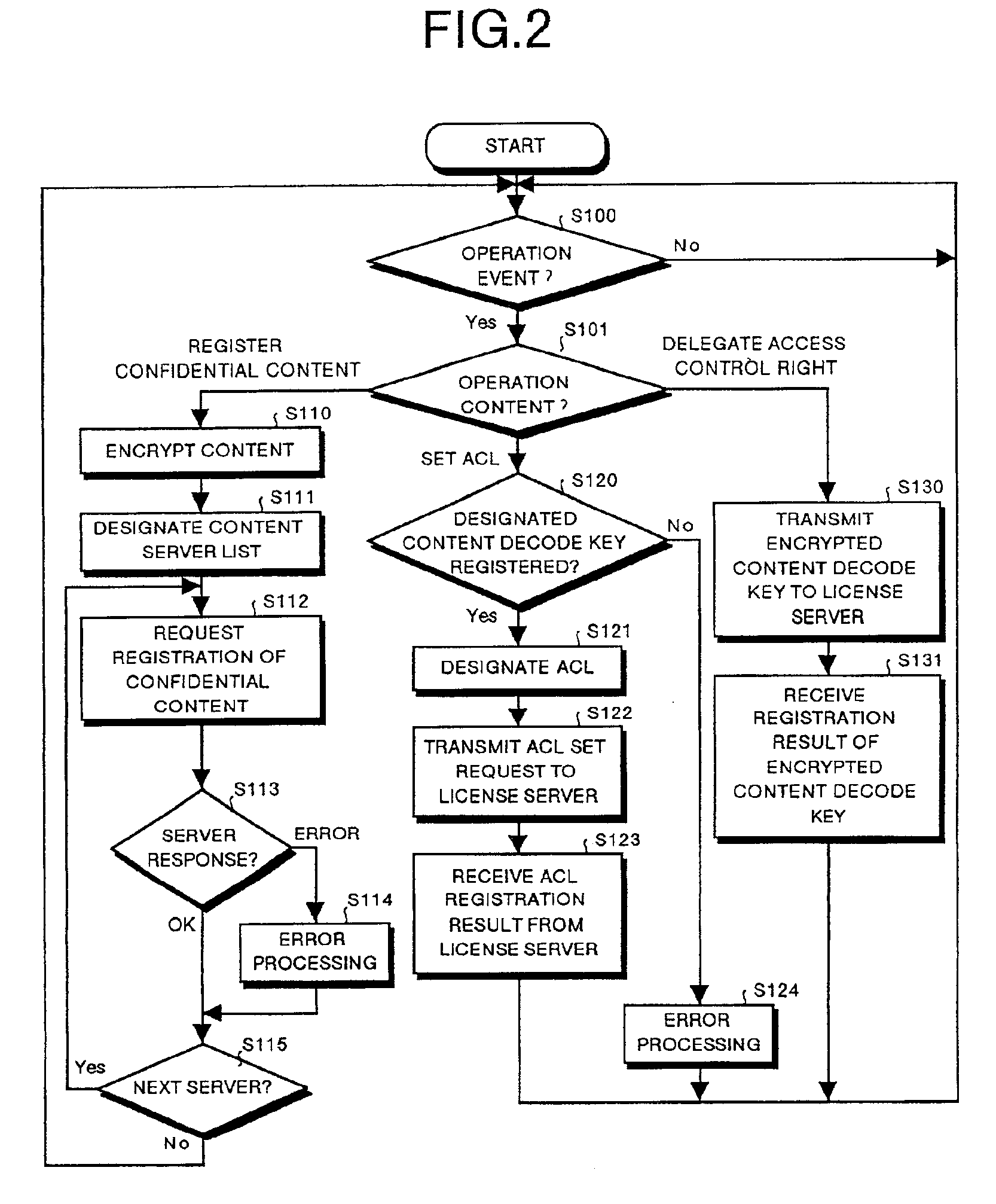
Content usage control system, content usage apparatus, computer readable recording medium with program recorded for computer to execute usage method
InactiveUS6873975B1Prevent illegal useImprove accuracyDigital data processing detailsAnalogue secracy/subscription systemsControl systemStructure of Management Information
A content usage control system comprises a copyright holder system, content server, license server and user system. The ACL setting section of the copyright holder system sets a license ACL expressed as a structure by a combination of logic sums and logic products of a plurality of partial licenses for the content, based on the user ID and a plurality of physical element IDs including media used in the user system, and stores the license ACL in an access control list. The license server controls the usage of the content by the user utilizing the access control list.
Owner:FUJITSU LTD
System for implementing security on telecommunications terminals
ActiveUS20090254993A1Improve securityOvercome problemsUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunications linkComputer terminal
A system includes at least one telecommunications terminal having data processing capabilities, the telecommunications terminal being susceptible of having installed thereon software applications, wherein each software application has associated therewith a respective indicator adapted to indicate a level of security of the software application, the level of security being susceptible of varying in time; a software agent executed by the at least one telecommunications terminal, the software agent being adapted to conditionally allow the installation of software applications on the telecommunications terminal based on the respective level of security; a server in communications relationship with the software agent, the server being adapted to dynamically calculate the level of security of the software applications, and to communicate to the software agent the calculated level of security of the software applications to be installed on the telecommunications terminal.
Owner:TELECOM ITALIA SPA
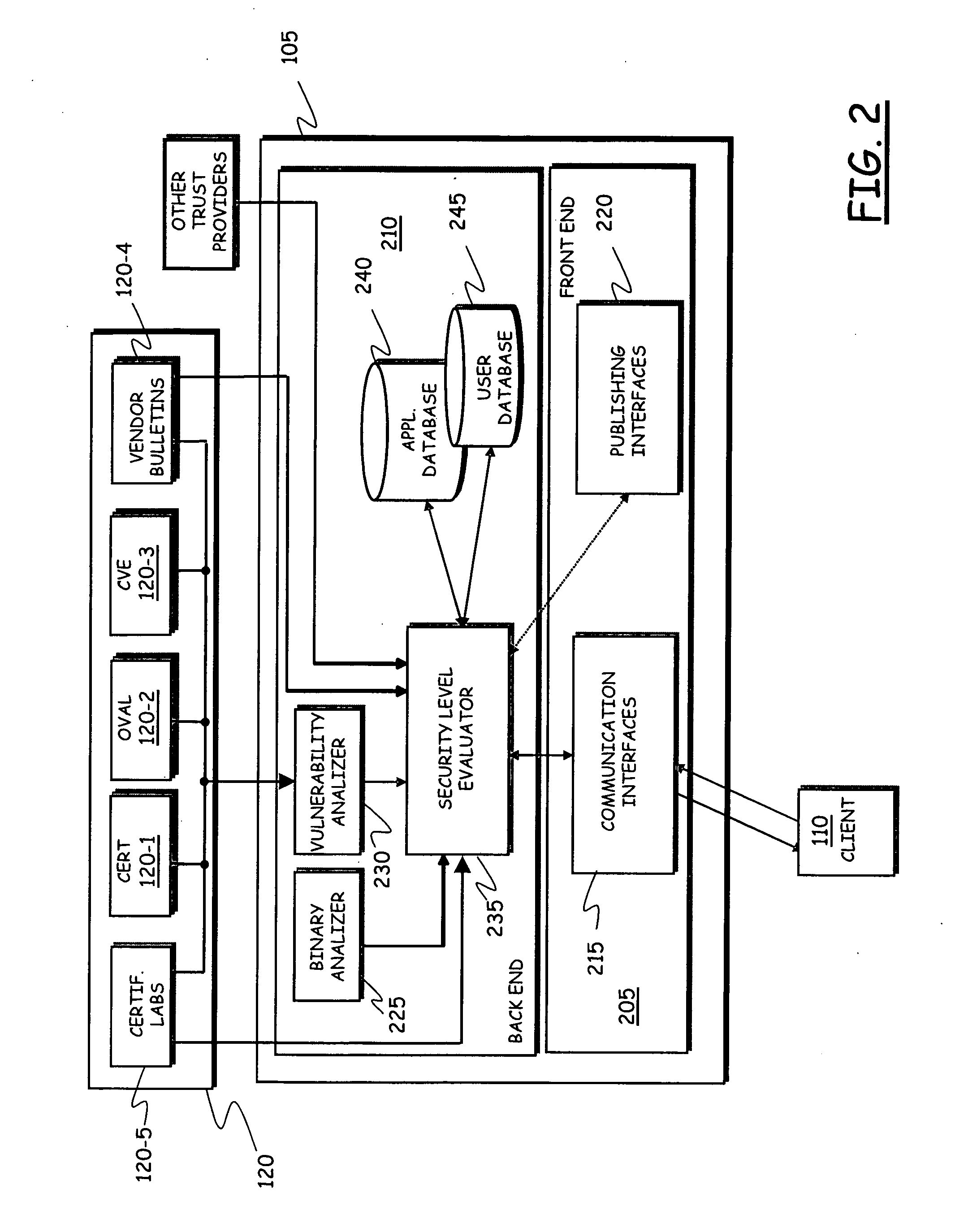
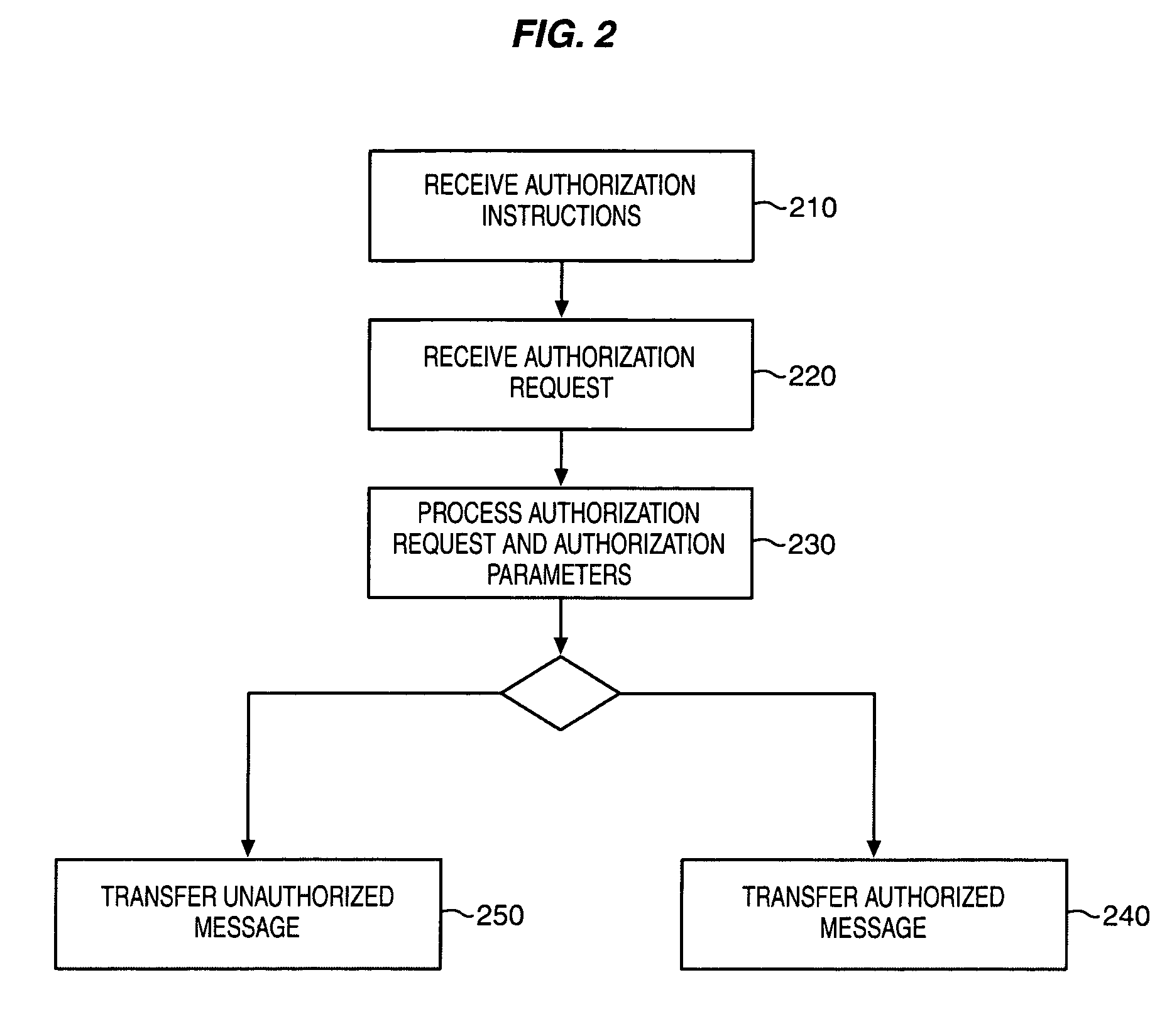
Software license authorization system
ActiveUS7703142B1Digital data processing detailsUser identity/authority verificationUser deviceSoftware license
An authorization system is described that includes a first interface, a processing system, and a second interface. The first interface is configured to receive an authorization instruction from an enterprise and receive an authorization request from a user device. The authorization instructions indicate authorization parameters. The user device transfers the authorization request each time the application is selected for execution. The authorization instructions are based on a license obtained by the enterprise for an application and wherein a user device operated by a user has the application. The processing system is configured to process the authorization request and authorization parameters to determine if the execution of the application is authorized. The second interface is configured to transfer an authorized message to the user device if the execution of the application is authorized and transfer an unauthorized message to the user device if the execution of the application is not authorized.
Owner:T MOBILE INNOVATIONS LLC
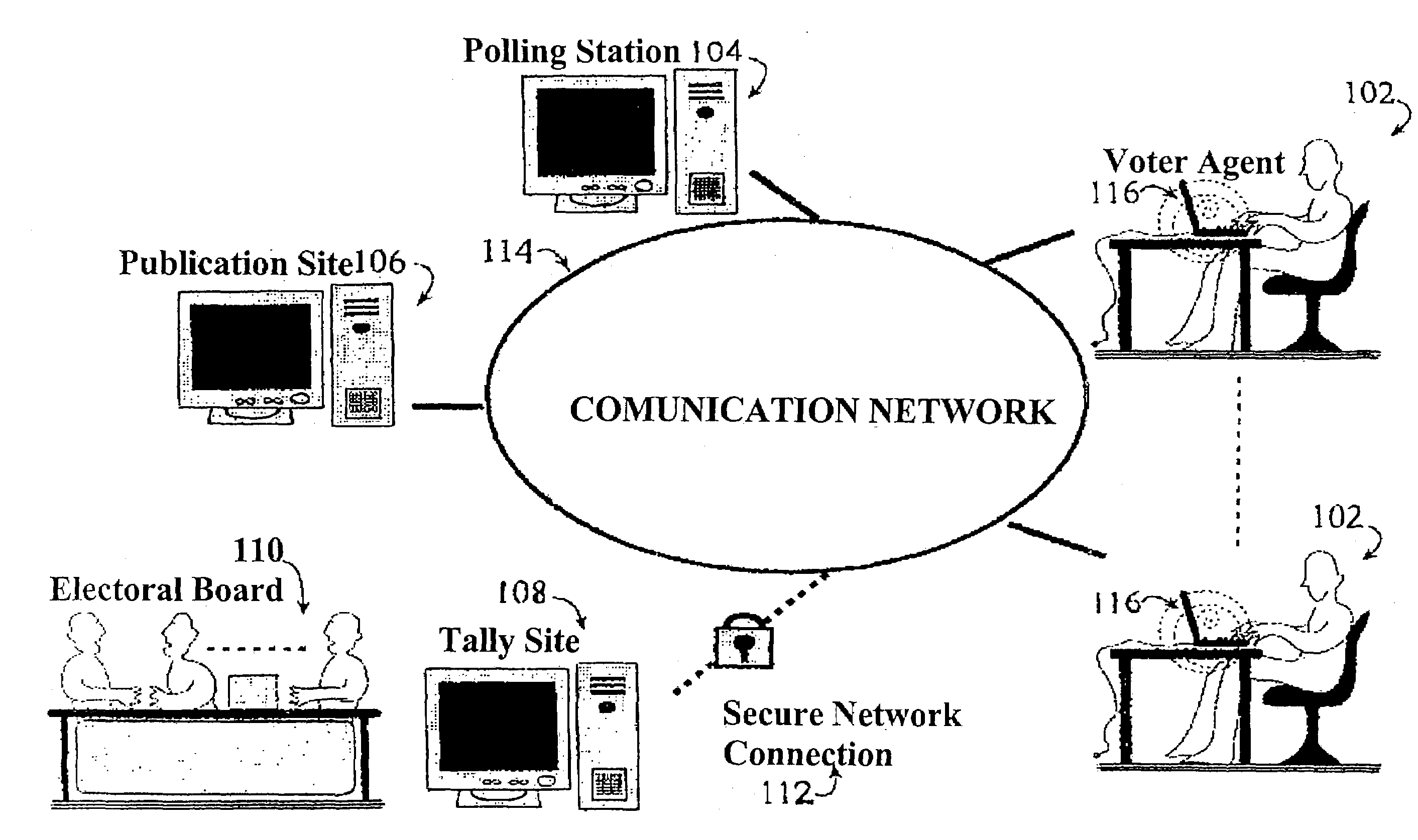
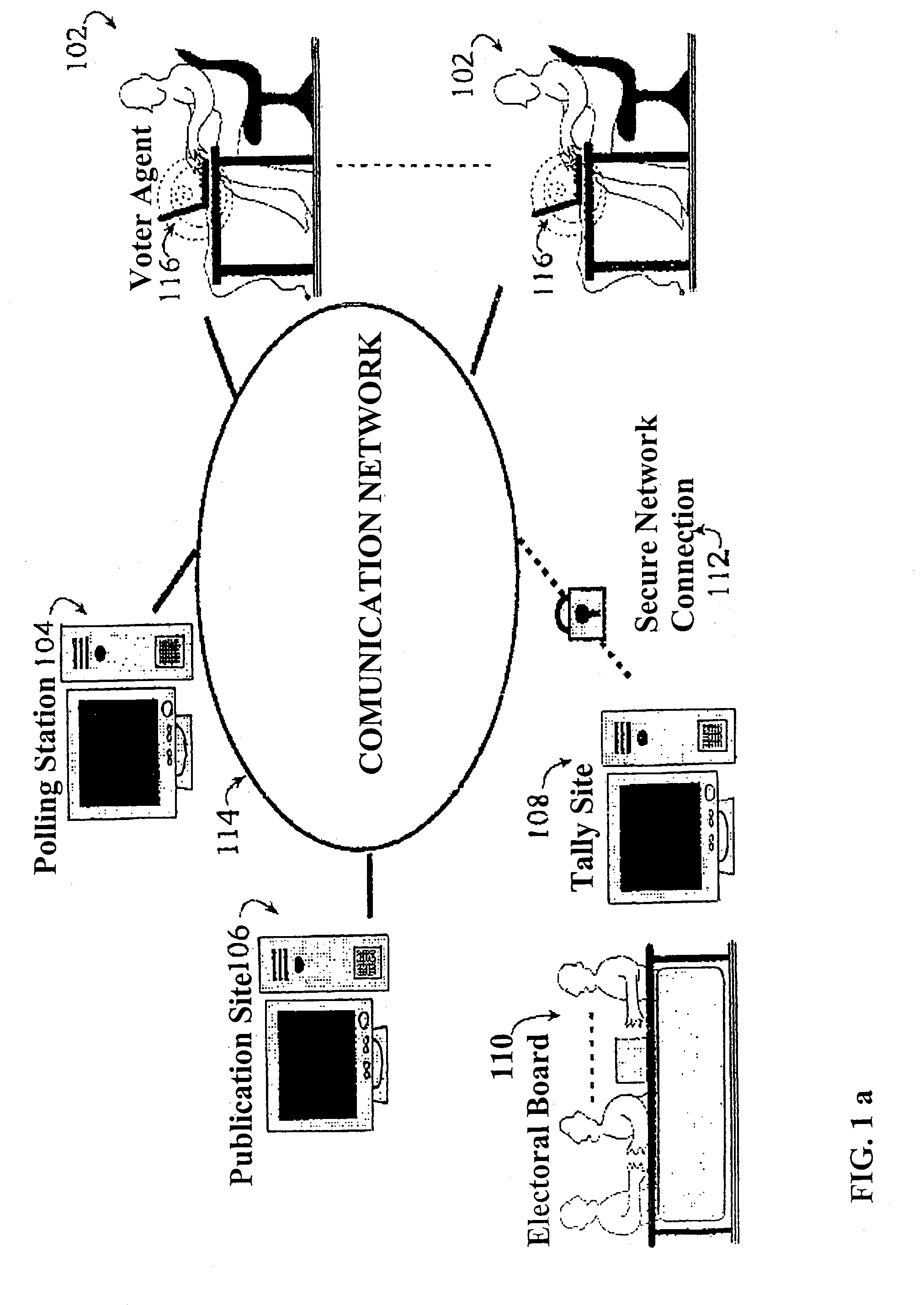
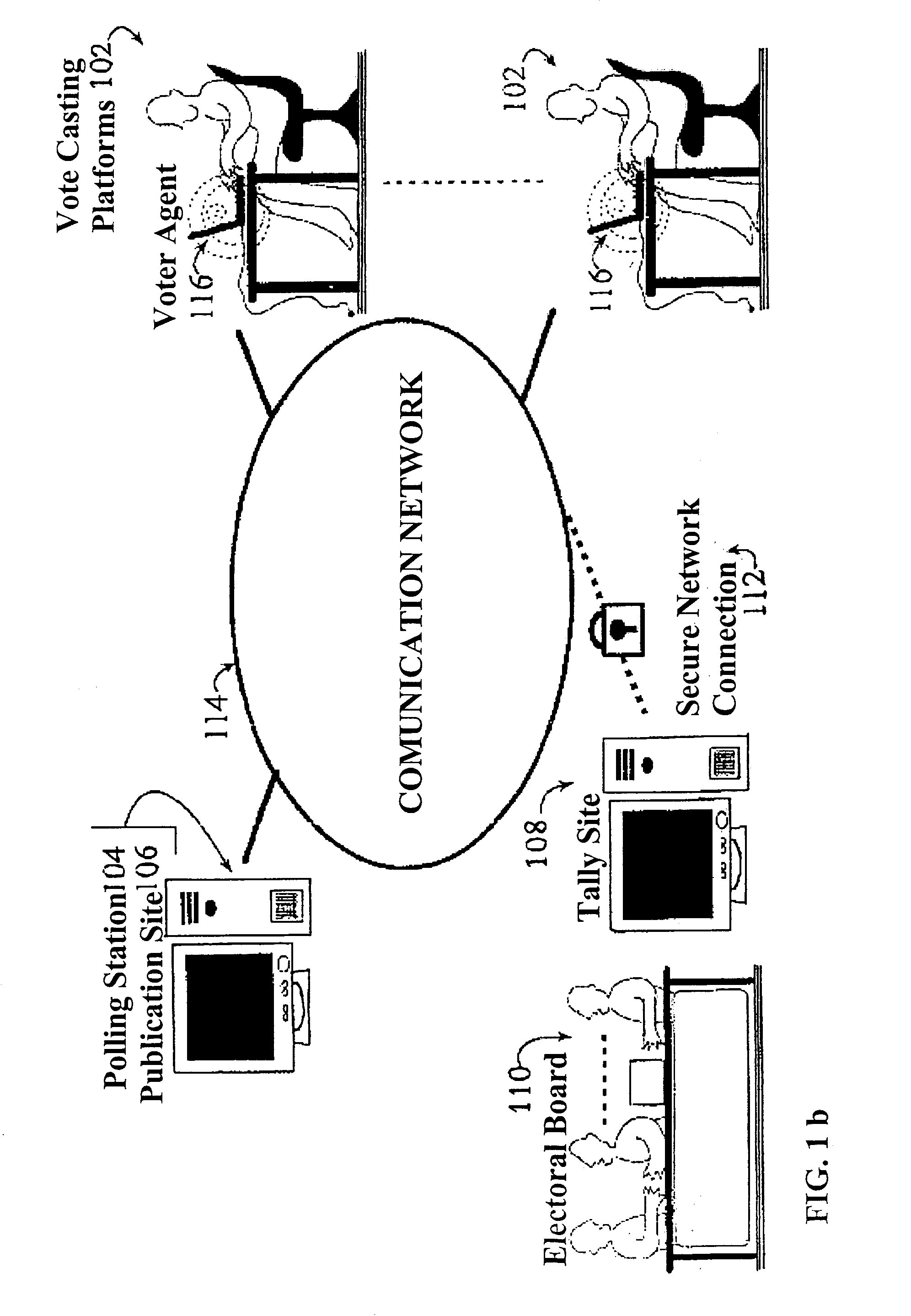
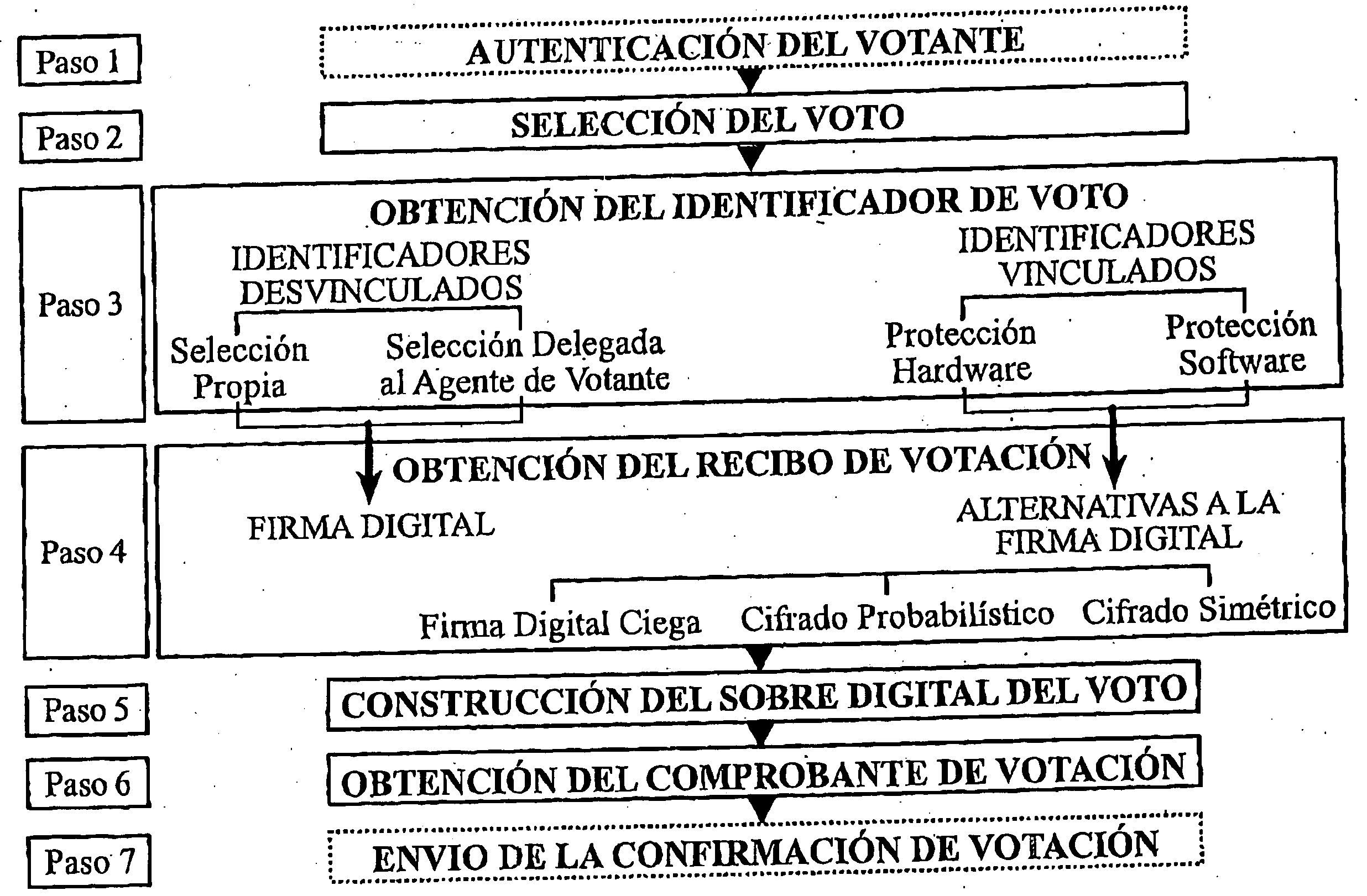
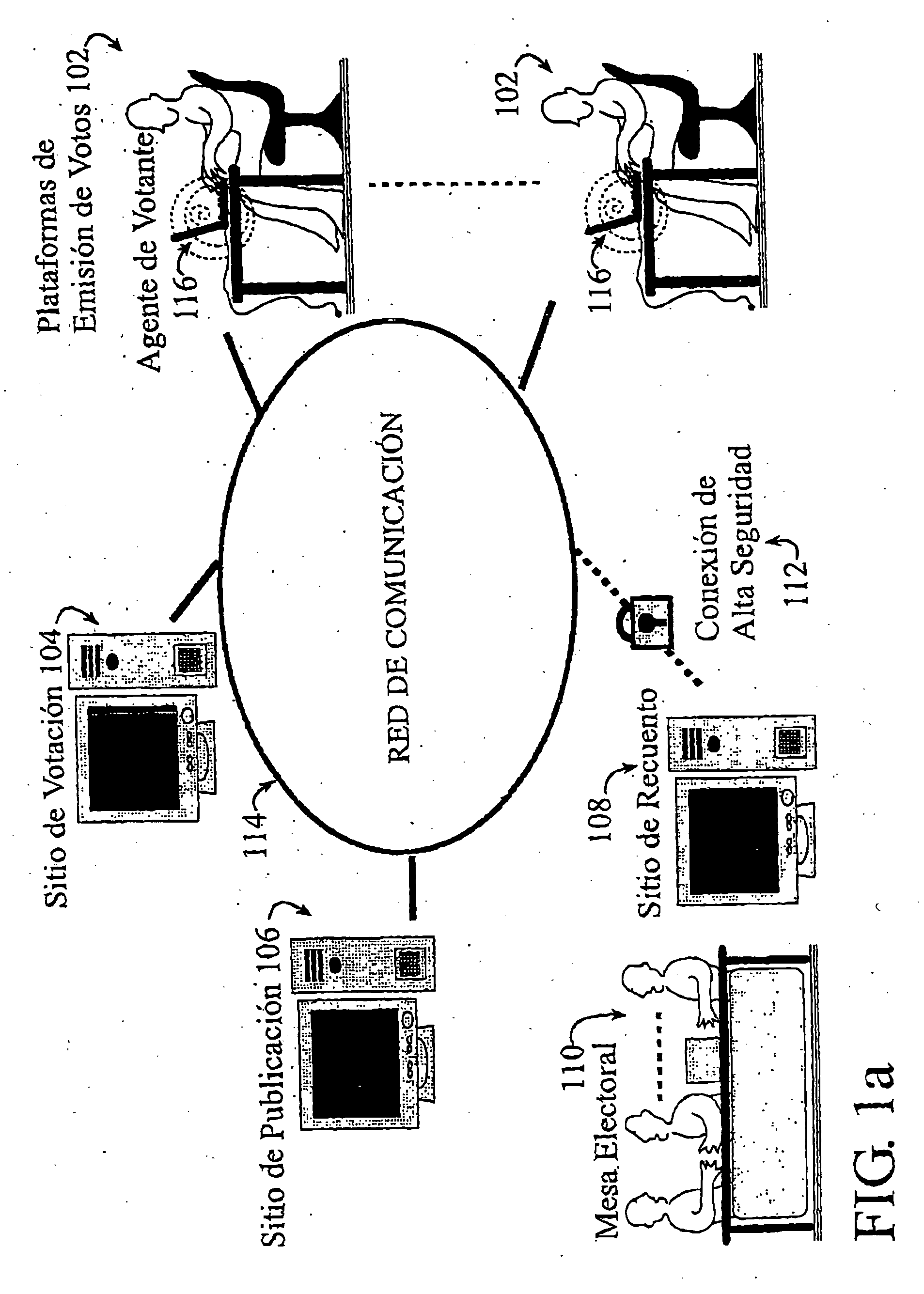
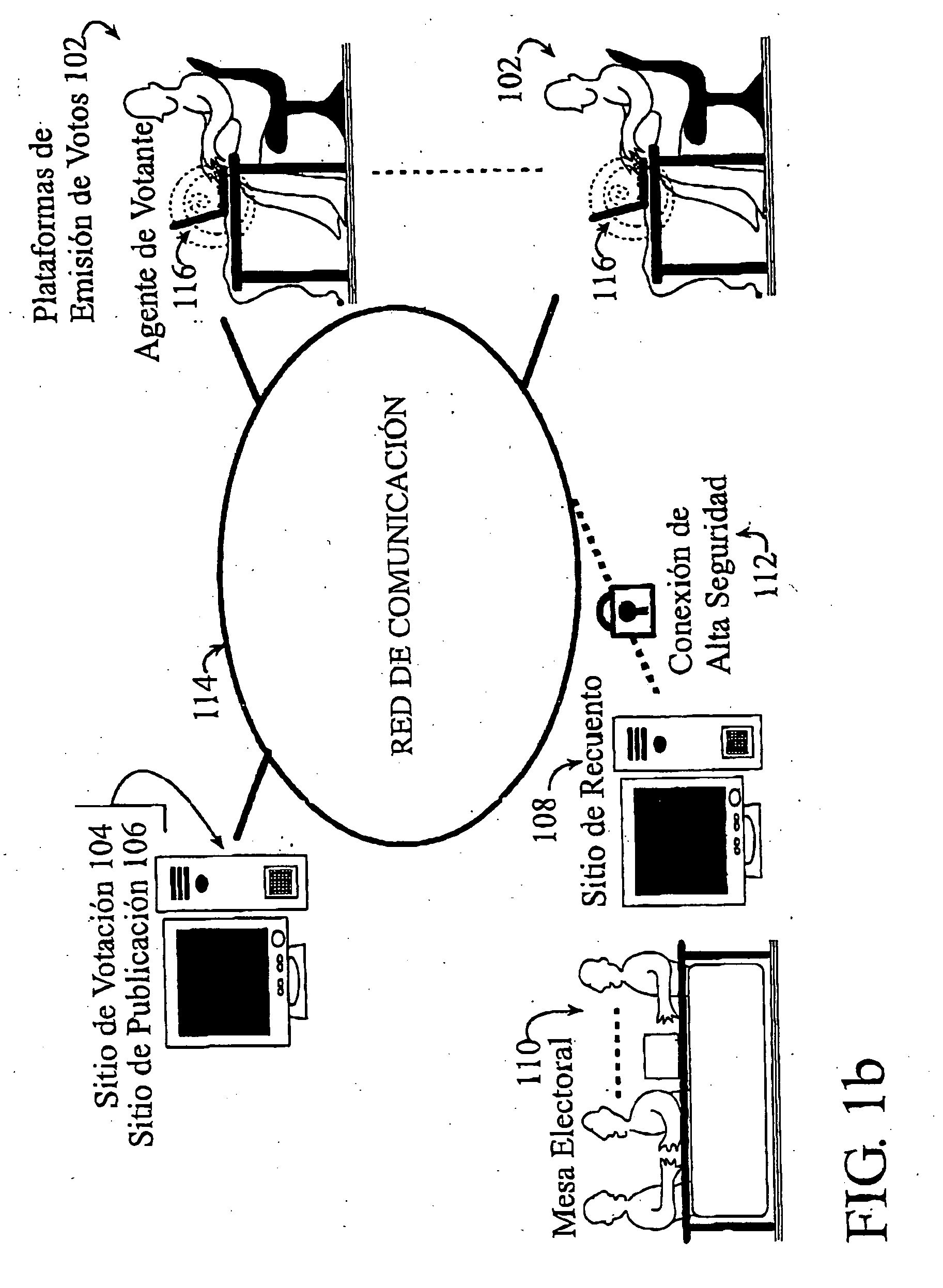
Secure remote electronic voting system and cryptographic protocols and computer programs employed
InactiveUS7260552B2Minimizing confidence levelHindering voters coercionVoting apparatusError detection/correctionCryptographic protocolSurvey result
The method employs interrelated cryptographic processes and protocols to provide reliability to vote casting, ballots recount, and verification of vote or poll results. These cryptographic processes and protocols jointly constitute a cryptographic voting scheme capable of meeting the specific reliability requirements of an electronic voting where voters remotely cast their votes. These reliability requirements include voter authentication and privacy; accurate results, the impossibility of coercion and sale of votes, verifying the final results and, if necessary, the secrecy of intermediate results before completing the vote or poll. The cryptographic voting method minimizes the confidence level to be placed on any of the electronic voting individual party and participants.
Owner:SCYTL ELECTION TECH SL
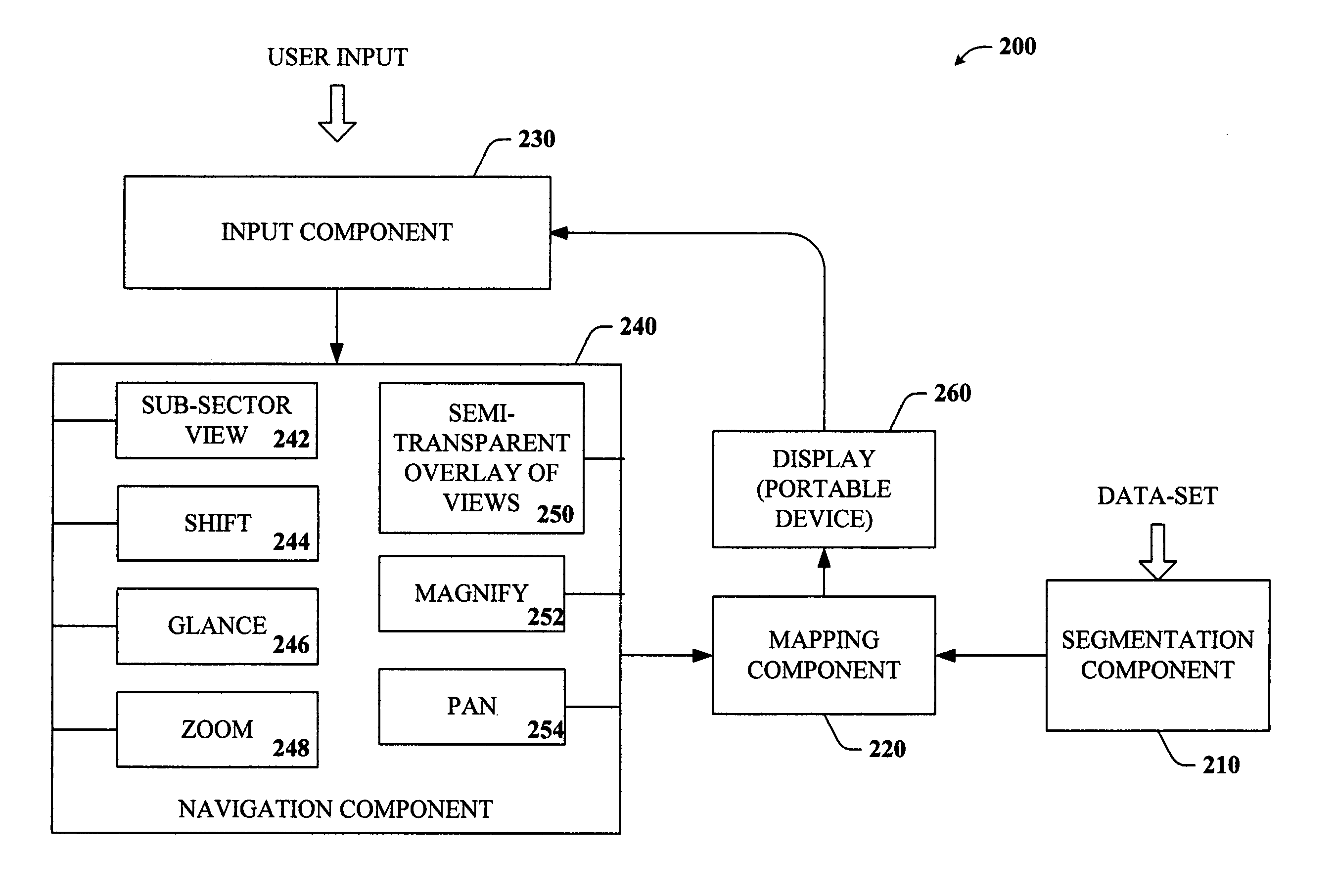
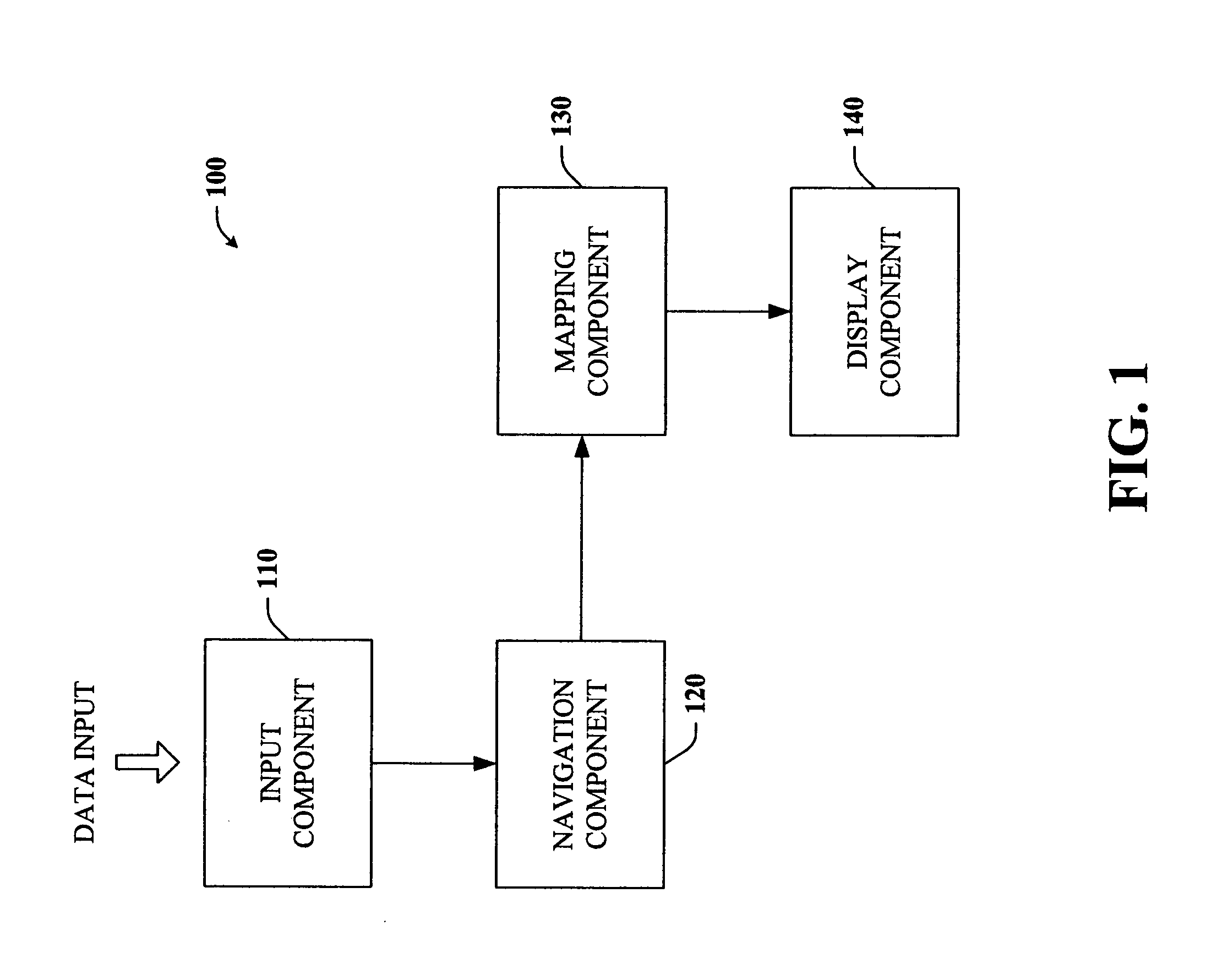
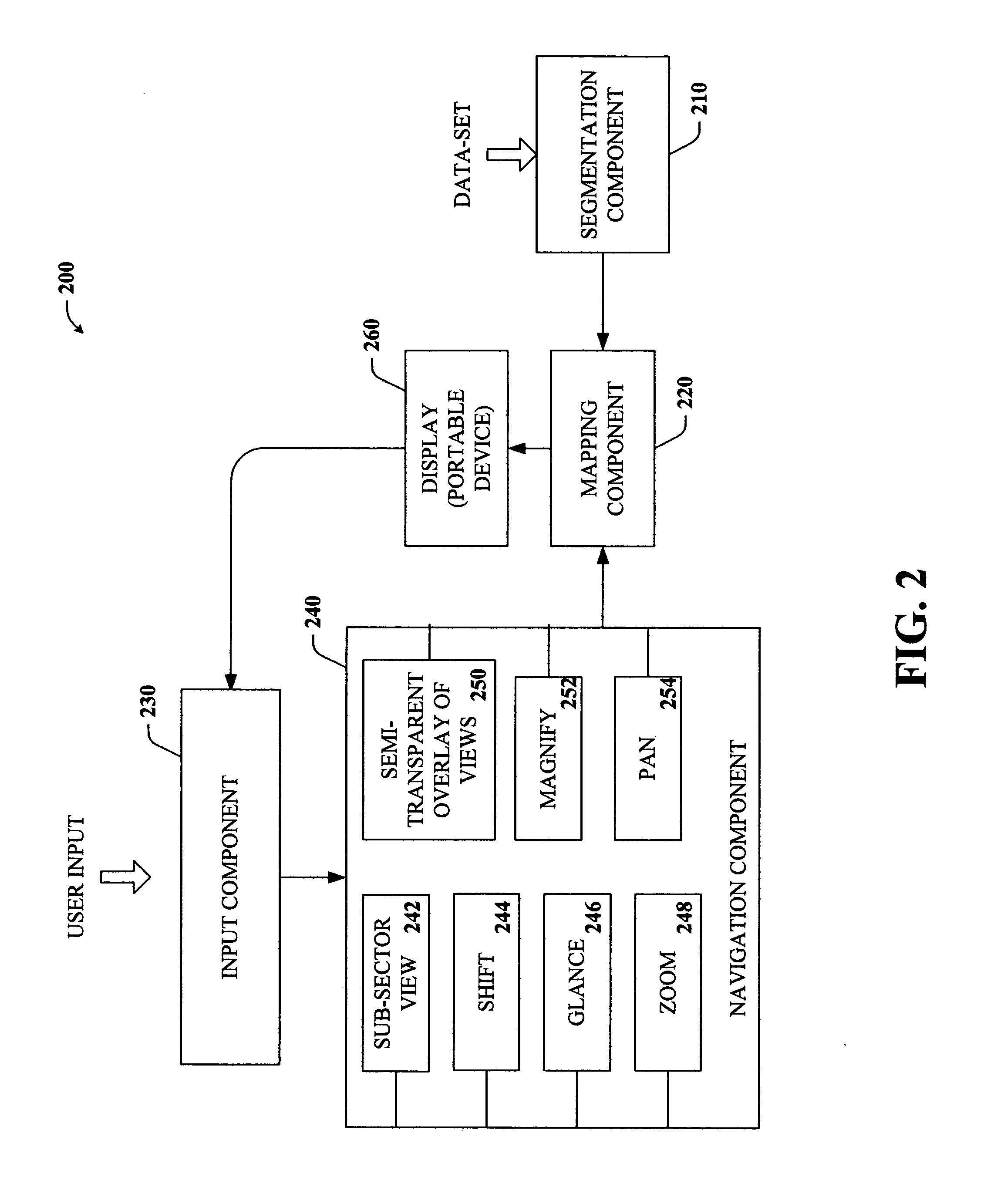
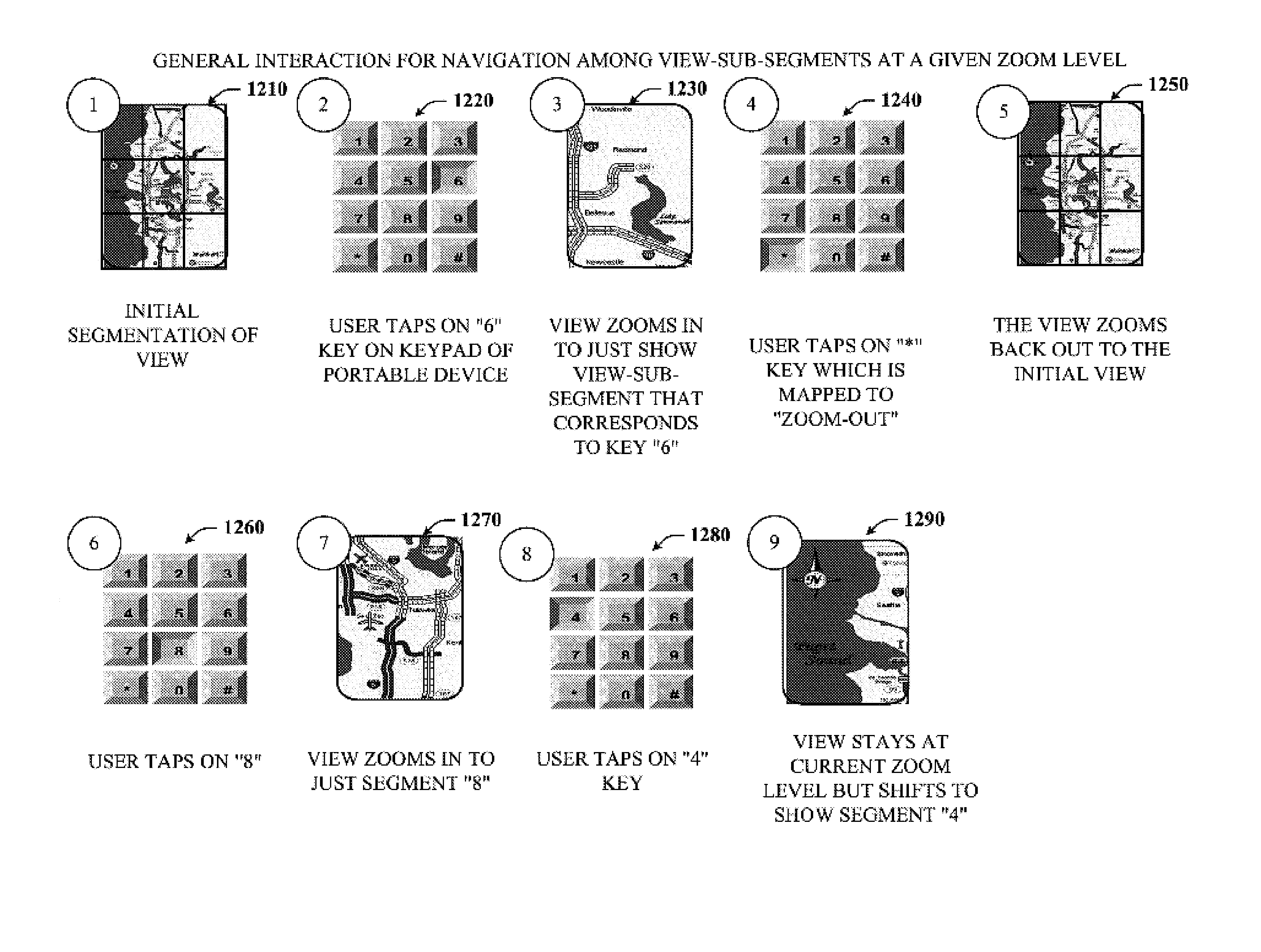
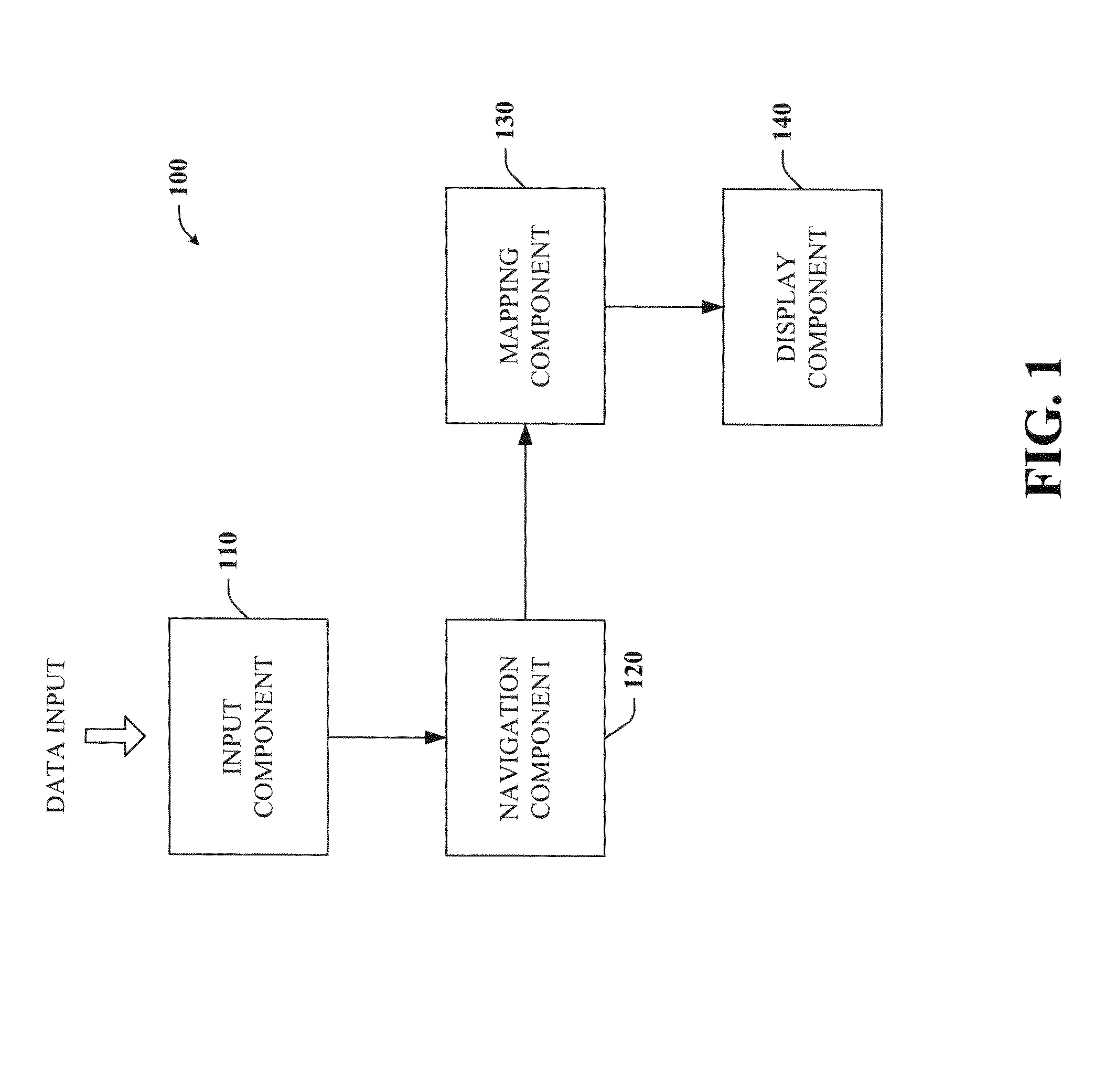
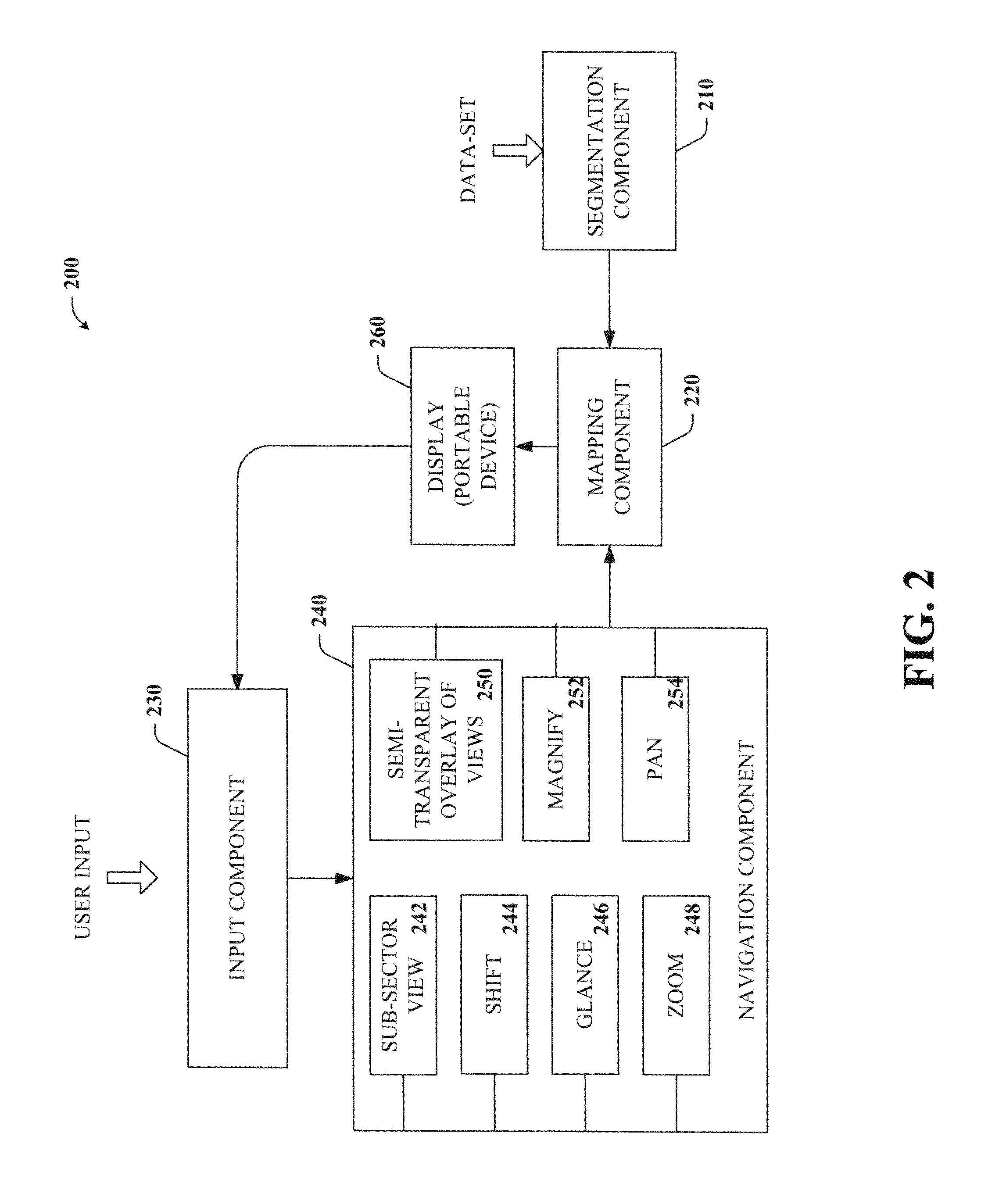
Key-based advanced navigation techniques
InactiveUS20050197763A1Smooth navigationLess detailInput/output for user-computer interactionInstruments for road network navigationAngle of viewMarine navigation
The present invention provides a unique system and method that facilitates navigating smoothly and gracefully through any type of content viewable on portable devices. Such navigation can be performed while preserving perspective and context with respect to a larger amount of content. The navigation can be key-based such that one or more keys of a keypad can be employed to browse through, zoom in, and / or zoom out of content. In one aspect, the content can be segmented into any number of sub-sectors or segments such that each segment can correspond to a particular number key, whereby particular portions of content can be viewed in greater or less detail by pressing or tapping on the corresponding number key. Furthermore, when viewing a first portion of content, nearby content can be glanced at by pressing and holding the respective key. When the key is released, the view returns to the first portion.
Owner:MICROSOFT TECH LICENSING LLC
Abstractions and automation for enhanced sharing and collaboration
InactiveUS20050232423A1Optimal information privacyReduce the burden onDigital data processing detailsUser identity/authority verificationInformation sharingCrowds
The present invention provides methods for using abstractions of people, including dynamic and static groups of people, to enhance the efficiency of the specification and automation of policies for sharing information between users with a “need-to-know.” An instance of the present invention can also provide these users information based on a “time-to-know.” By providing access to information based on group affiliation and properties of the content of the information, the present invention maintains optimal information privacy while minimizing encumbrances to sharing data with appropriate users and even at appropriate times. The present invention can be integrated with other communication technologies to facilitate access to information in a time appropriate manner. Other instances of the present invention employ automated and semi-automated, mixed-initiative techniques, to make information-sharing decisions. Additional instances of the present invention include the employment of machine-learning techniques to facilitate construction of access policies from the actions or profile of a single user or a community of users, including the construction of automated sharing agents that work in an automated or mixed-initiative manner to respond to real-time requests for information.
Owner:MICROSOFT TECH LICENSING LLC
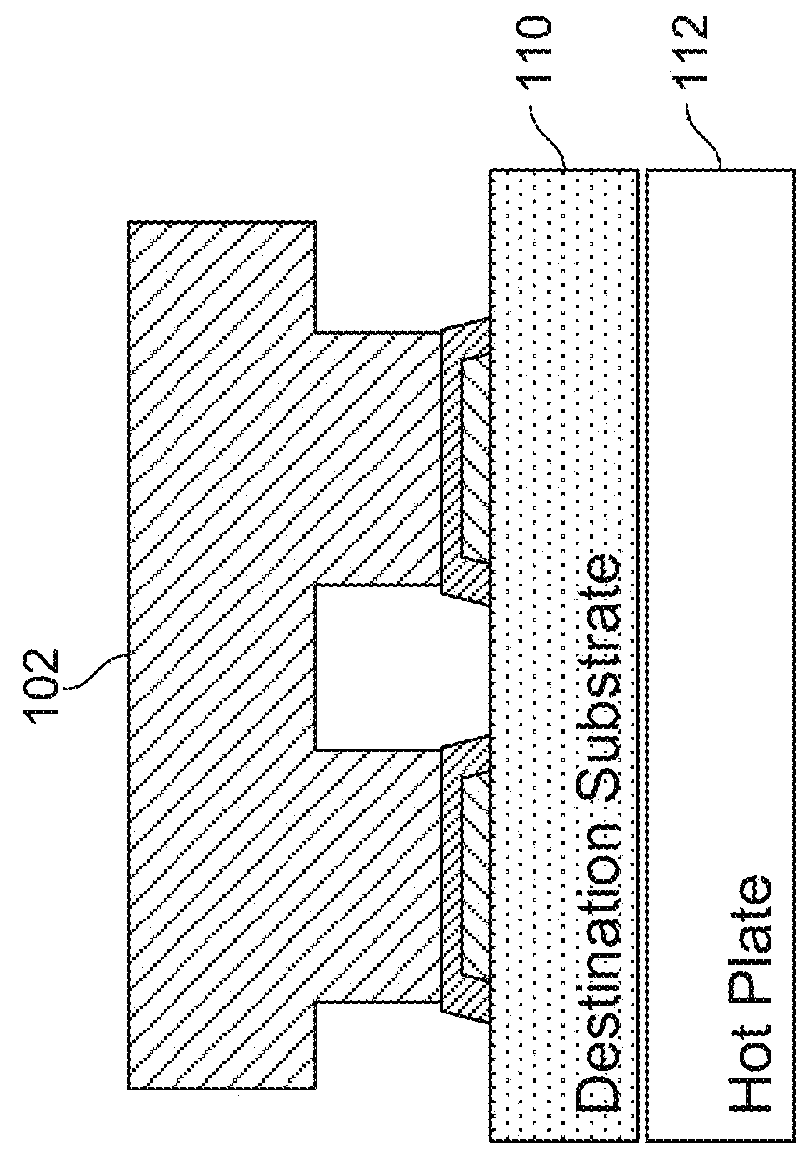
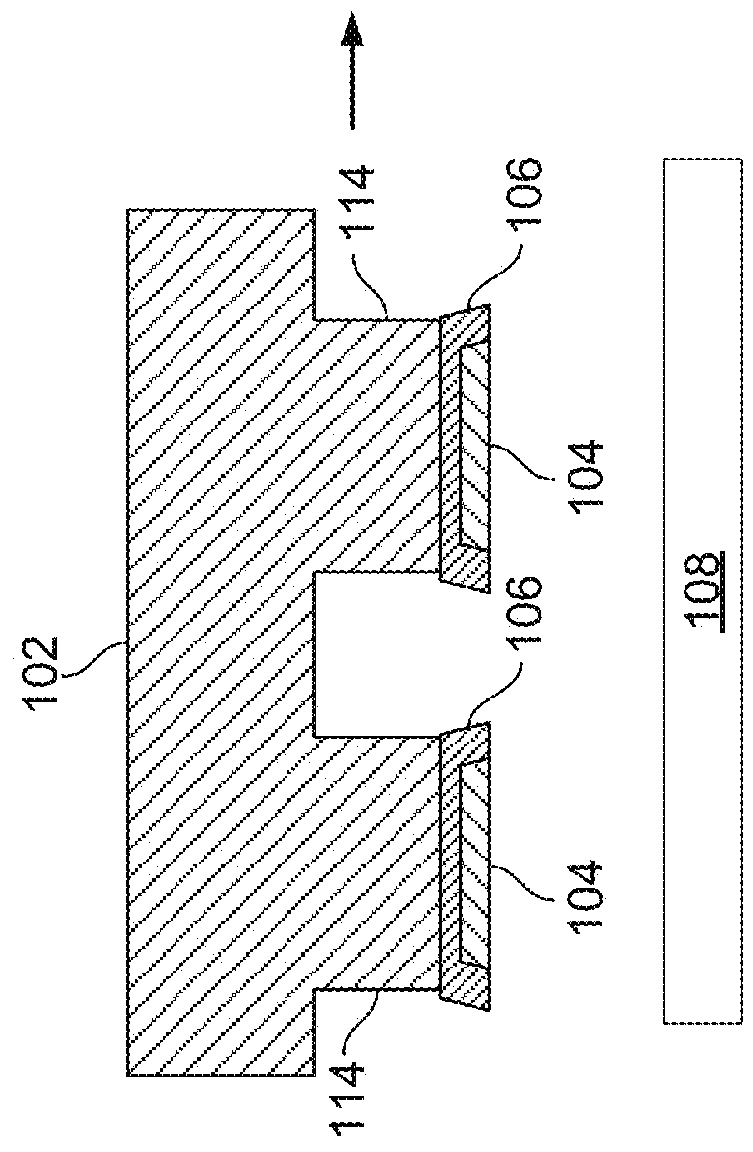
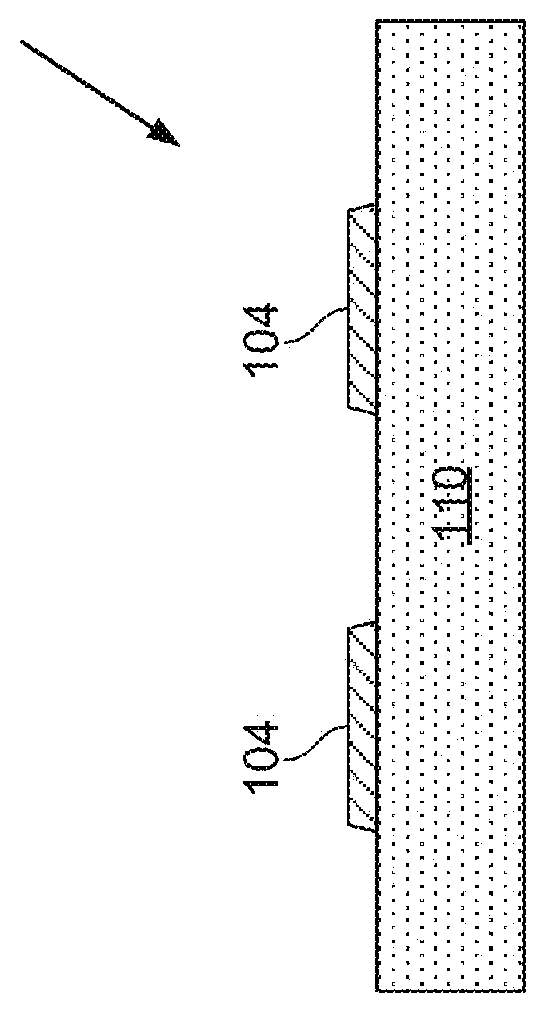
Apparatus and methods for micro-transfer-printing
ActiveUS9358775B2Increase heightImprove adhesionTransfer printingSemiconductor/solid-state device detailsSemiconductorSeparation system
In an aspect, a system and method for assembling a semiconductor device on a receiving surface of a destination substrate is disclosed. In another aspect, a system and method for assembling a semiconductor device on a destination substrate with topographic features is disclosed. In another aspect, a gravity-assisted separation system and method for printing semiconductor device is disclosed. In another aspect, various features of a transfer device for printing semiconductor devices are disclosed.
Owner:X DISPLAY CO TECH LTD
License devolution apparatus
InactiveUS20010032088A1Improve protectionReduce usageKey distribution for secure communicationDigital data processing detailsComputer hardwareLicense
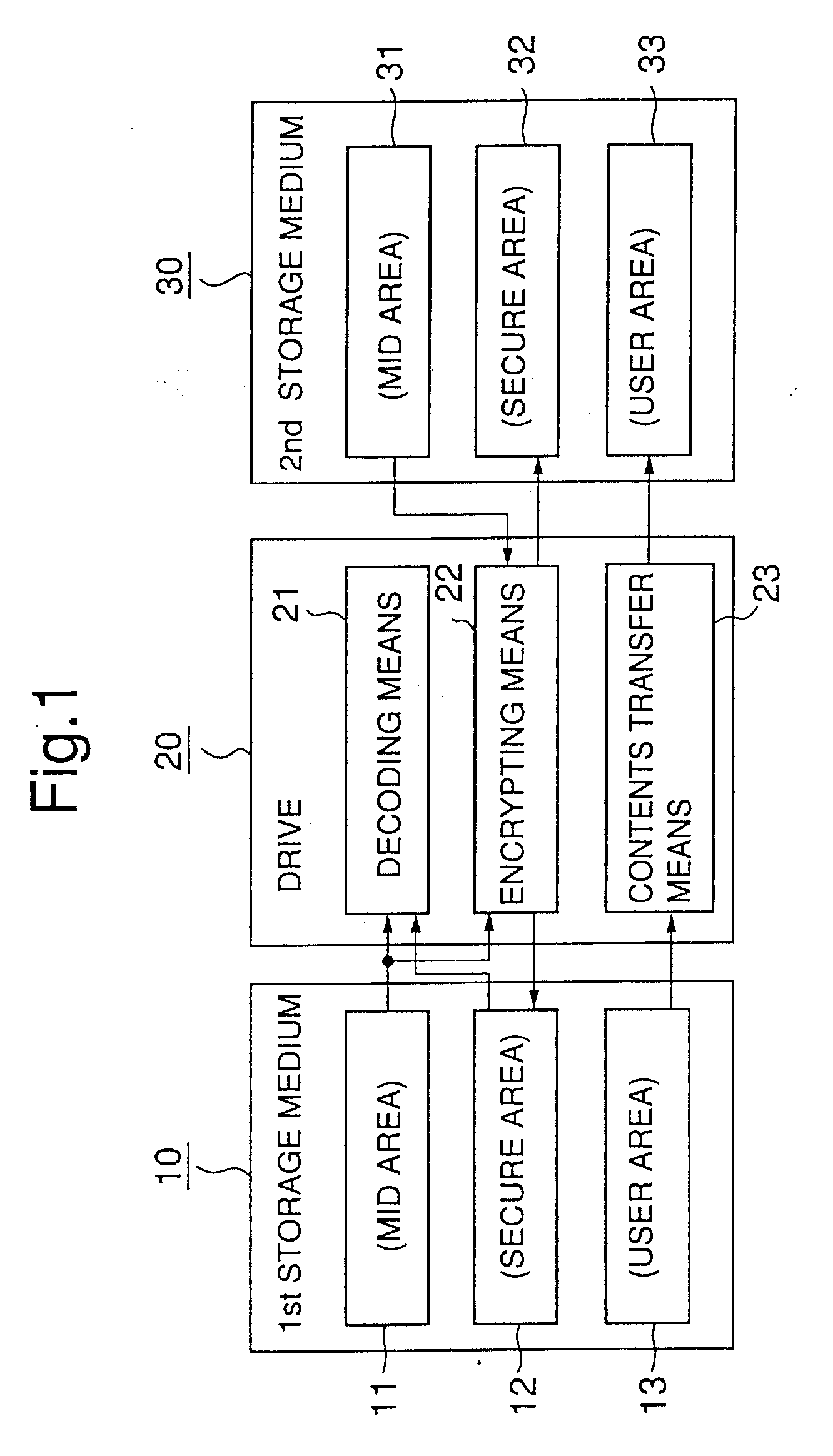
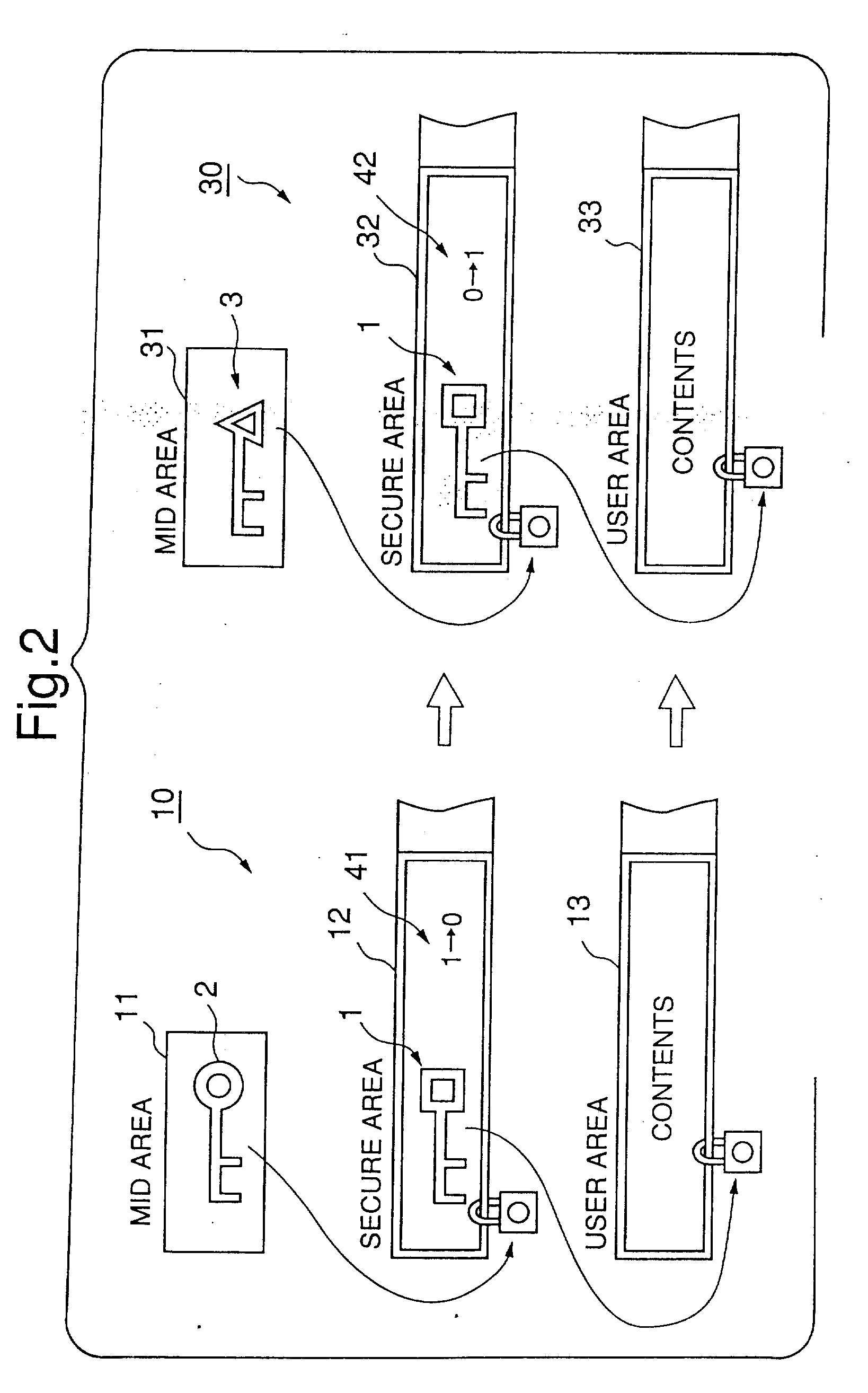
<heading lvl="0">Abstract of Disclosure< / heading> There is provided a license devolution system for devolving the right of using as to contents. The license devolution system makes it possible to copy or distribute contents while contributing to a protection of the copyright for the contents. Contents is encrypted with a first key. The first key and use information are encrypted with a second key consisting of a media ID for identifying a first storage medium in which the first key and the use information are stored. In order to devolve the right of using as to the contents, the contents is transferred to a second storage medium of a destination of devolution in the form of encryption. The first key and the use information are decoded with the media ID of the first storage medium, and further encrypted with the media ID of the second storage medium of the destination of devolution into storage in the second storage medium of the destination of devolution.
Owner:FUJITSU LTD
Imprint stamp
InactiveUS20060021533A1Facilitate easy mold releaseImprove fidelityNanoinformaticsPhotomechanical apparatusFluorineComposite material
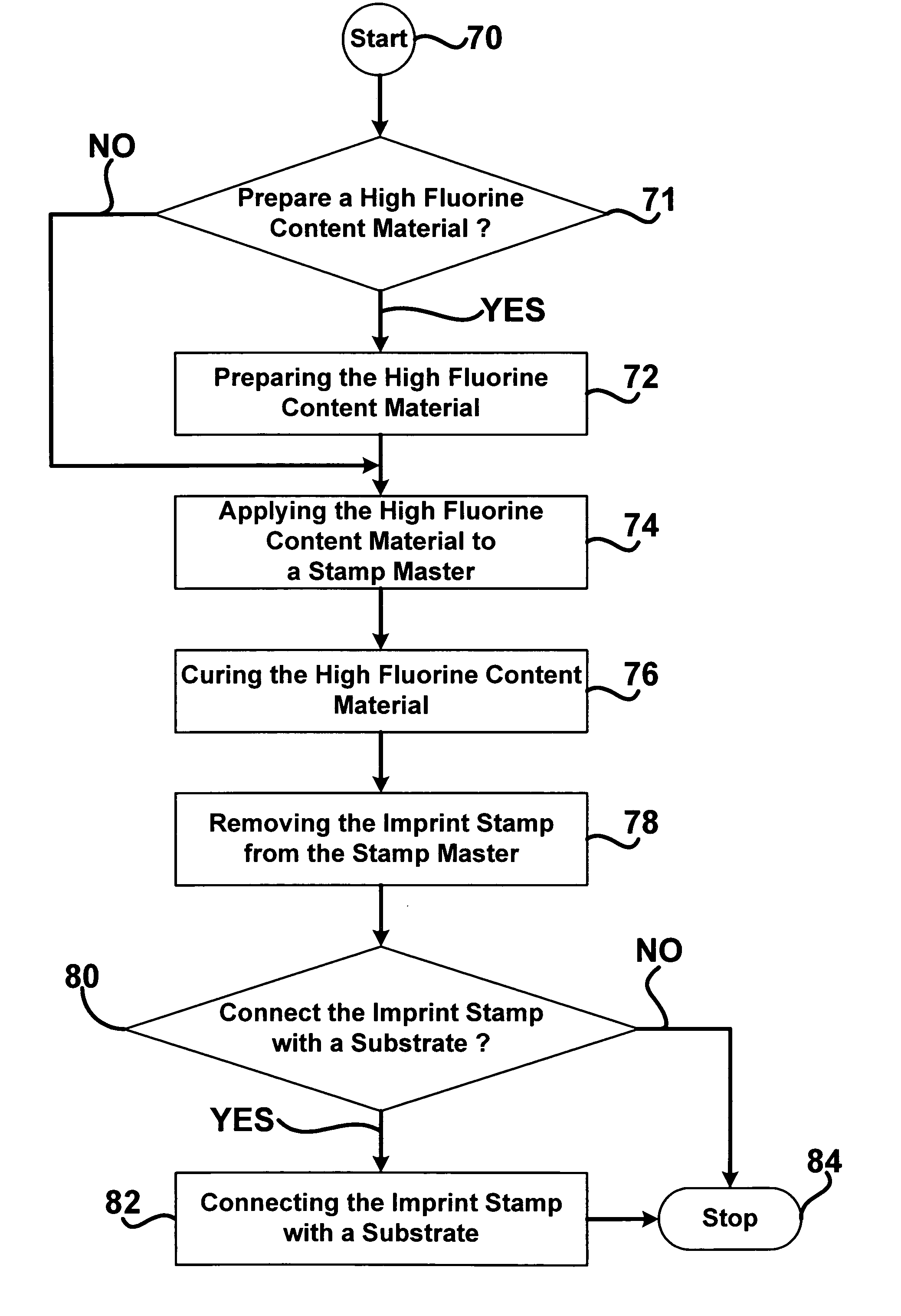
An imprint stamp made from a high fluorine content material and a method of fabricating an imprint stamp from a high fluorine content material are disclosed. The imprint stamp includes an imprint pattern that can be formed in the imprint stamp during a molding process wherein the high fluorine content material is applied to a mold that includes a pattern to be replicated in the high fluorine content material to form the imprint pattern. The high fluorine content material of the imprint stamp is resistant to blending, pairing, and swelling. An imprint stamp made from the high fluorine content material can be used for several hundred or more embossing steps without damage or wear to the imprint stamp and / or the imprint pattern.
Owner:HEWLETT PACKARD DEV CO LP
Hardware-based anti-virus system
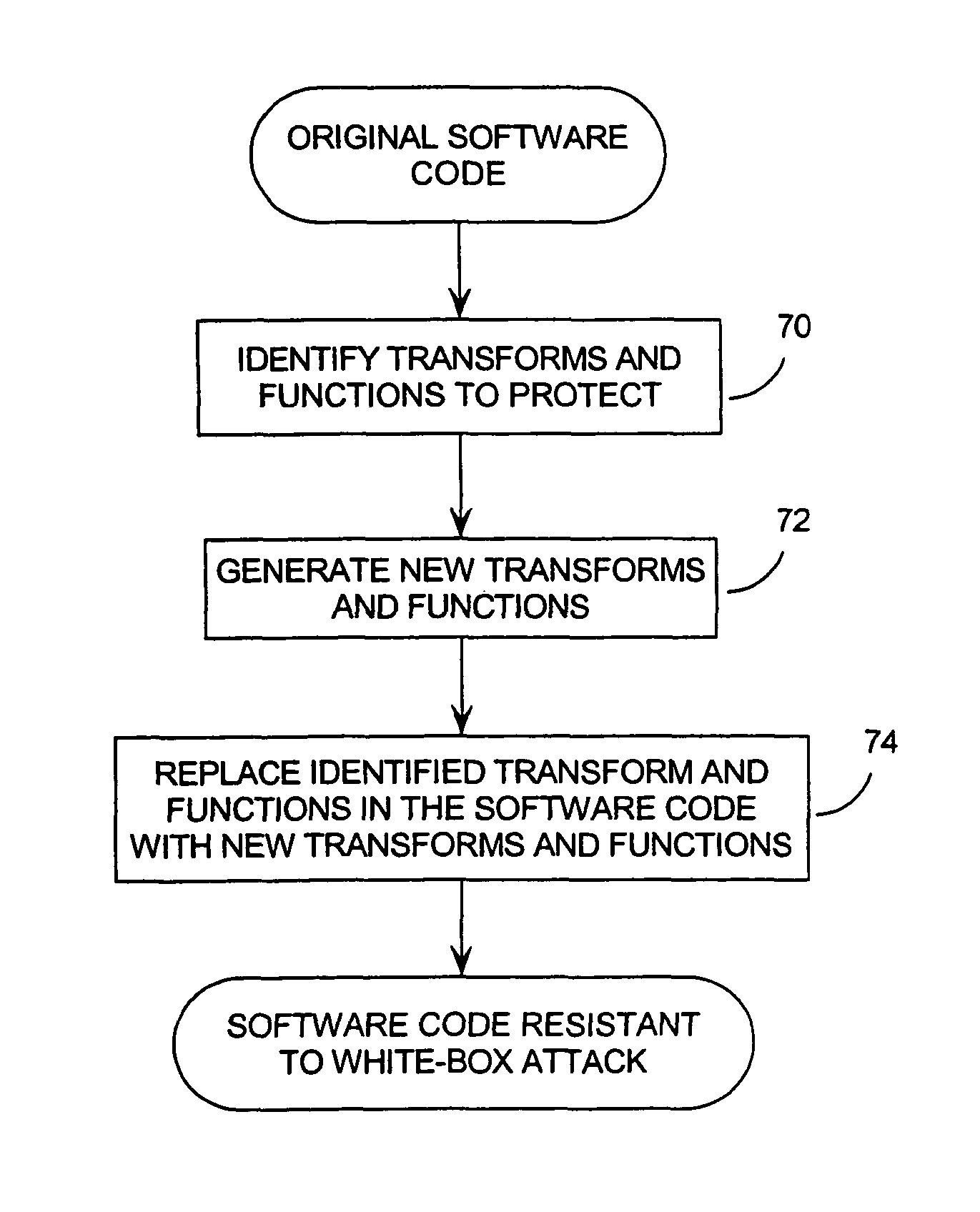
An anti-virus (AV) system based on a hardware-implemented AV module for curing infected computer systems and a method for updating AV databases for effective curing of the computer system. The hardware-based AV system is located between a PC and a disk device. The hardware-based AV system can be implemented as a separate device or it can be integrated into a disk controller. An update method of the AV databases uses a two-phase approach. First, the updates are transferred to from a trusted utility to an update sector of the AV system. Then, the updates are verified within the AV system and the AV databases are updated. The AV system has its own CPU and memory and can be used in combination with AV application.
Owner:AO KASPERSKY LAB
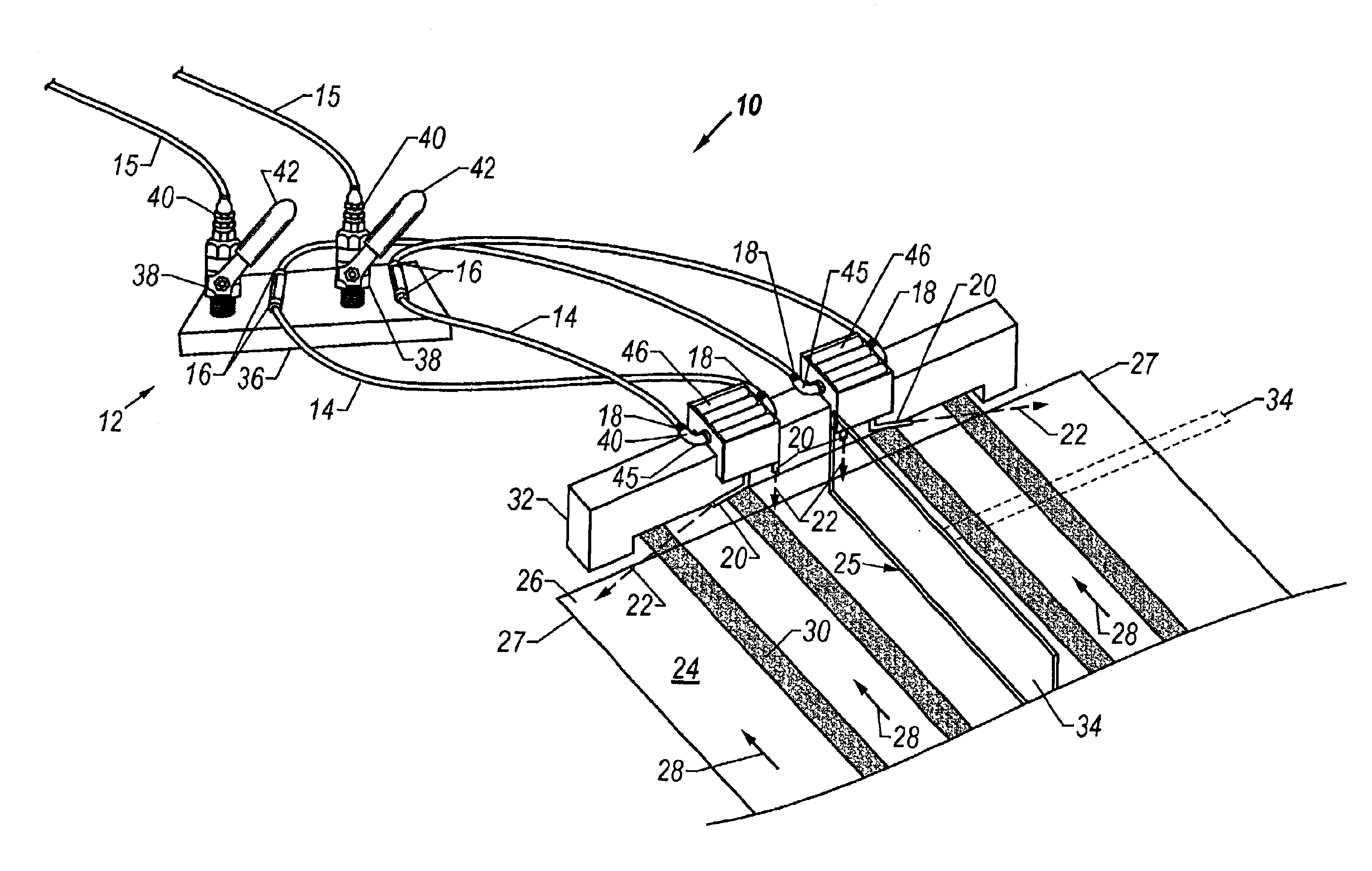
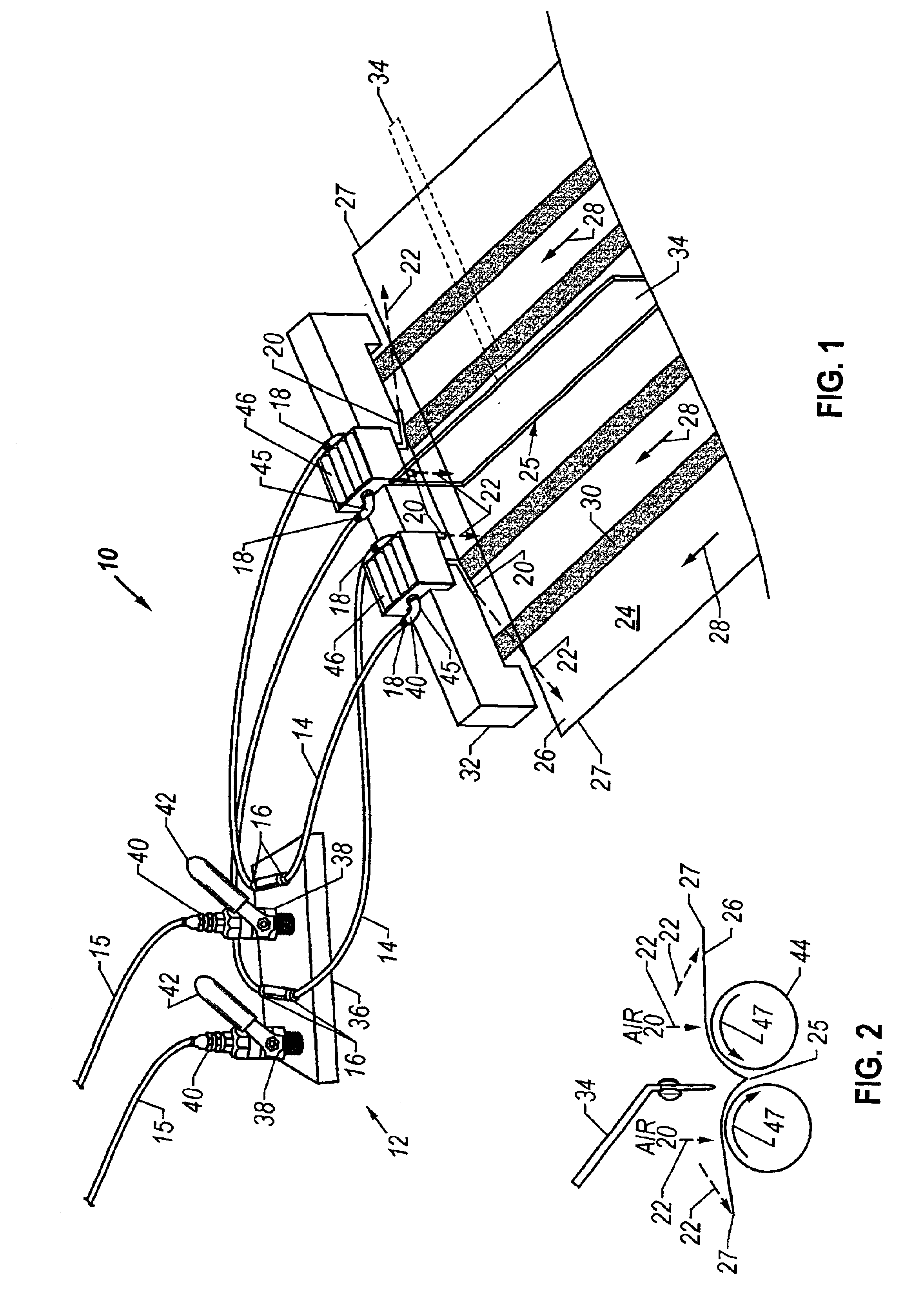
Air folder adjuster apparatus and method
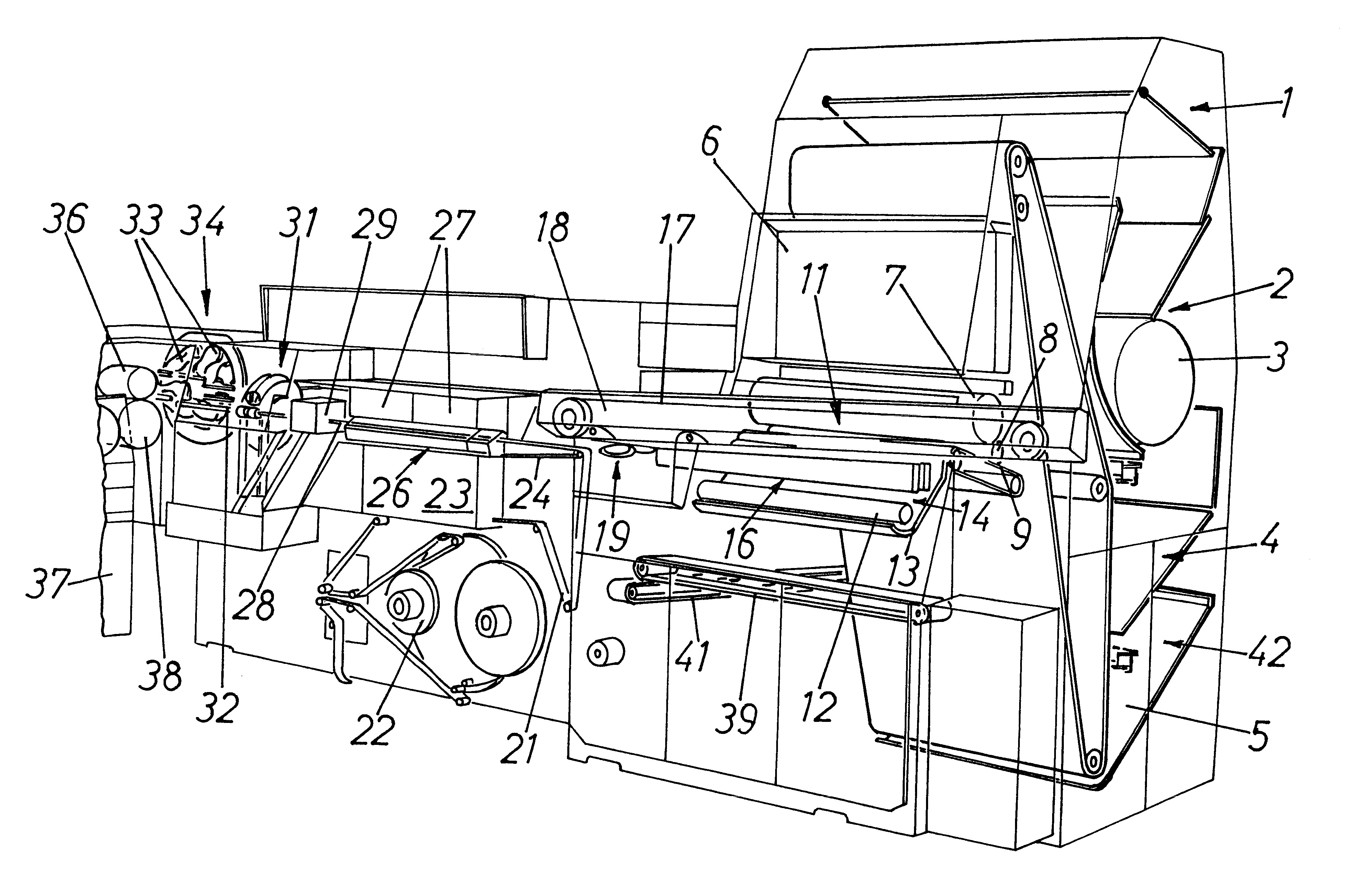
InactiveUS6840616B2Mechanical working/deformationFolding thin materialsPaper documentDocument preparation
An air folder adjuster (10) includes an air supply (12) and air supply tubing (14) connected to air supply (12) at end (16). The opposite end (18) of air supply tubing (14) is connected to one or more air nozzles (20). In a printing press utilized for folding documents such as books, air folder adjuster (10) is positioned so that air nozzles (20) direct compressed air from air supply (12) downward onto the head (26) of document (24) on either side of chopper arm (34) during the folding process thus ensuring that the document (24) lies flat, square, and untouched during the folding process and thereby allowing the elimination of chopper brushes altogether.
Owner:SUMMERS SCOTT
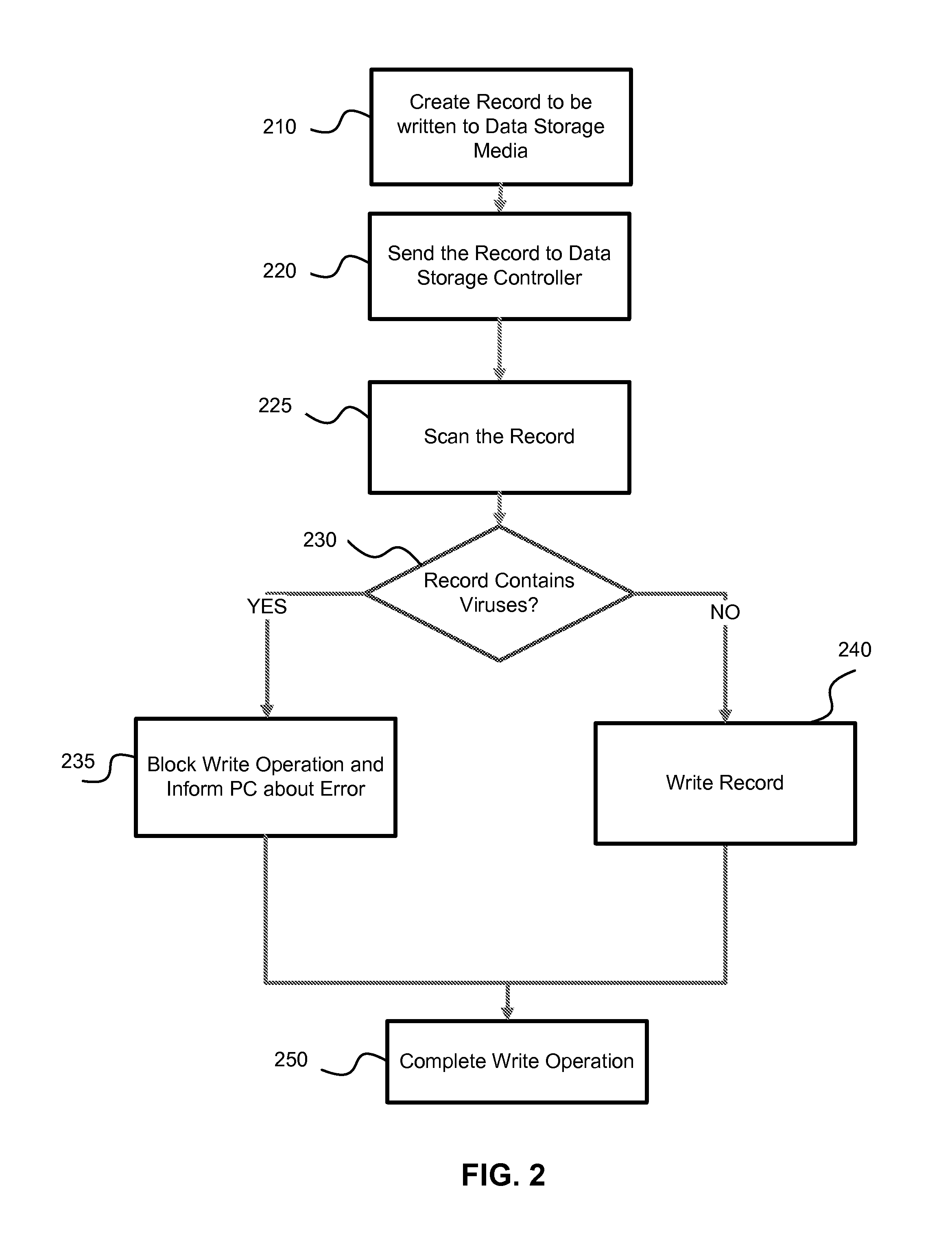
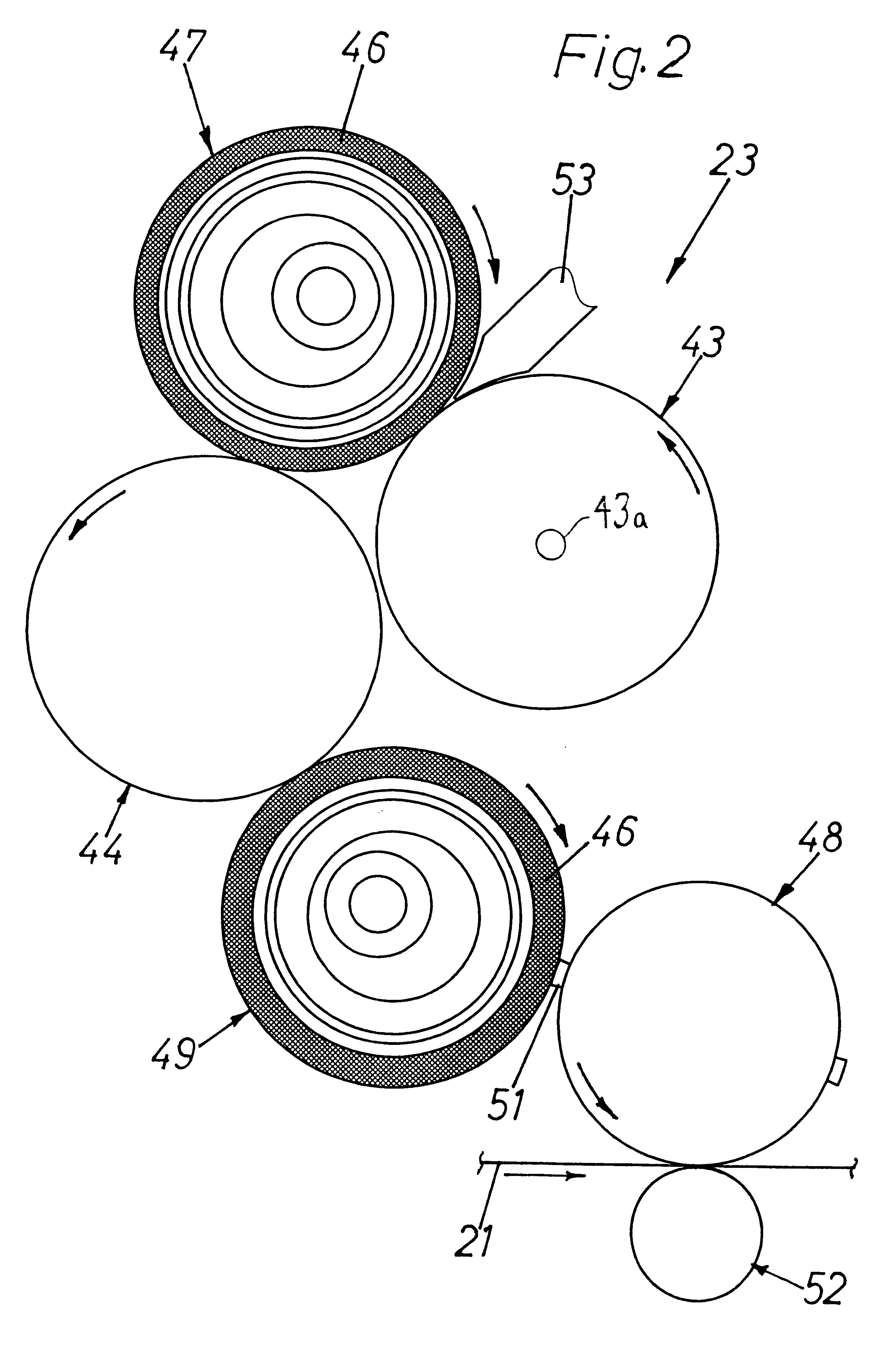
Sealing machine and method of controlling seal and its system
ActiveCN1623796ARealize automatic controlRealize managementProgram controlSpecial data processing applicationsGraphicsAutomatic control
The present invention provides a stamping machine, a stamping control method and a system thereof, wherein the method includes the following steps: opening the paper inlet and outlet door and moving in the stamping document to be used, and moving the stamping document to be used into a closed stamping machine , form the corresponding electronic text and / or graphic file of the document to be used, and display the picture of the document; automatically control the mobile seal, and control the seal to move to the corresponding printing position of the document to be printed according to the input printing command; complete stamping; remove the stamp After the file is removed, the sealed file is removed from the seal printing machine; the paper in and out door is closed. The printing machine and system adopting the above method realize the closed electronic control of the seal, and the whole printing process is carried out under the guarantee of safety, confidentiality and reliability, and has functions such as recording, verification and supervision.
Owner:BEIJING ORIENT JINYING INFORMATION TECH
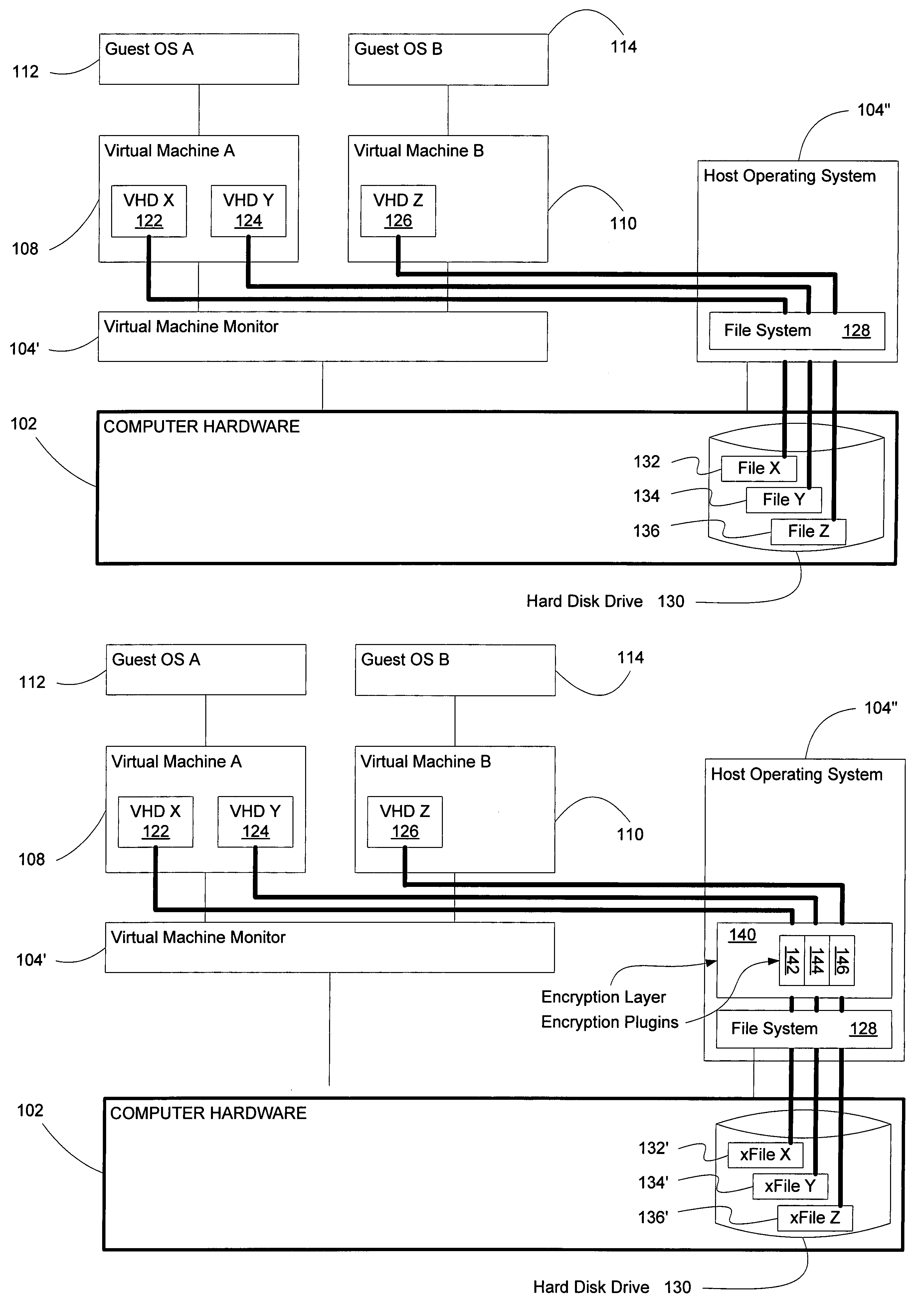
Systems and methods for data encryption using plugins within virtual systems and subsystems
ActiveUS7987497B1Improving data access securityImproved data access securityDigital data processing detailsUnauthorized memory use protectionHard disc driveData access
Several embodiments of the present invention provide a means for improving data access security in computer systems to support high-security applications, and certain of these embodiments are specifically directed to providing sector-level encryption of a virtual hard disk in a virtual machine environment. More specifically, certain embodiments are directed to providing sector-level encryption by using plug-ins in a virtual machine environment, thereby providing improved data access security in a computer system that supports high-security applications. Certain embodiments also use encryption plug-ins associated with standard encryption software for exchanging data between a virtual machine (VM) and its associated virtual hard drive(s) (VHDs). Moreover, several embodiments of the present invention are directed to the use of plug-in encryption services that interface with, and provide services for, a VM via a VM Encryption API (or its equivalent).
Owner:MICROSOFT TECH LICENSING LLC
Key-based advanced navigation techniques
InactiveUS7317449B2Facilitate navigating and browsingQuick ViewInput/output for user-computer interactionControl with pedestrian guidance indicatorMarine navigationMultimedia
The present invention provides a unique system and method that facilitates navigating smoothly and gracefully through any type of content viewable on portable devices. Such navigation can be performed while preserving perspective and context with respect to a larger amount of content. The navigation can be key-based such that one or more keys of a keypad can be employed to browse through, zoom in, and / or zoom out of content. In one aspect, the content can be segmented into any number of sub-sectors or segments such that each segment can correspond to a particular number key, whereby particular portions of content can be viewed in greater or less detail by pressing or tapping on the corresponding number key. Furthermore, when viewing a first portion of content, nearby content can be glanced at by pressing and holding the respective key. When the key is released, the view returns to the first portion.
Owner:MICROSOFT TECH LICENSING LLC
Microcontact printing
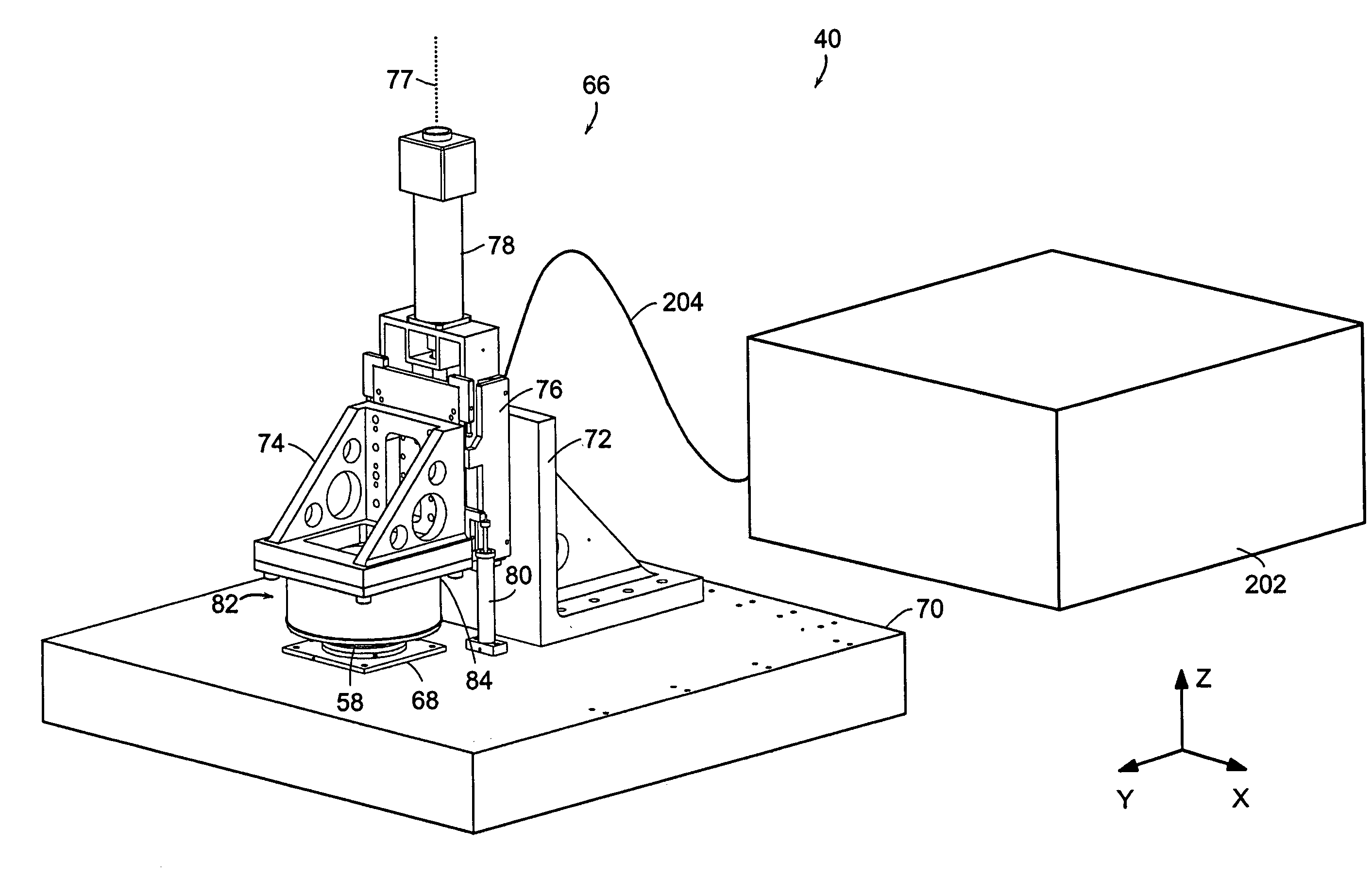
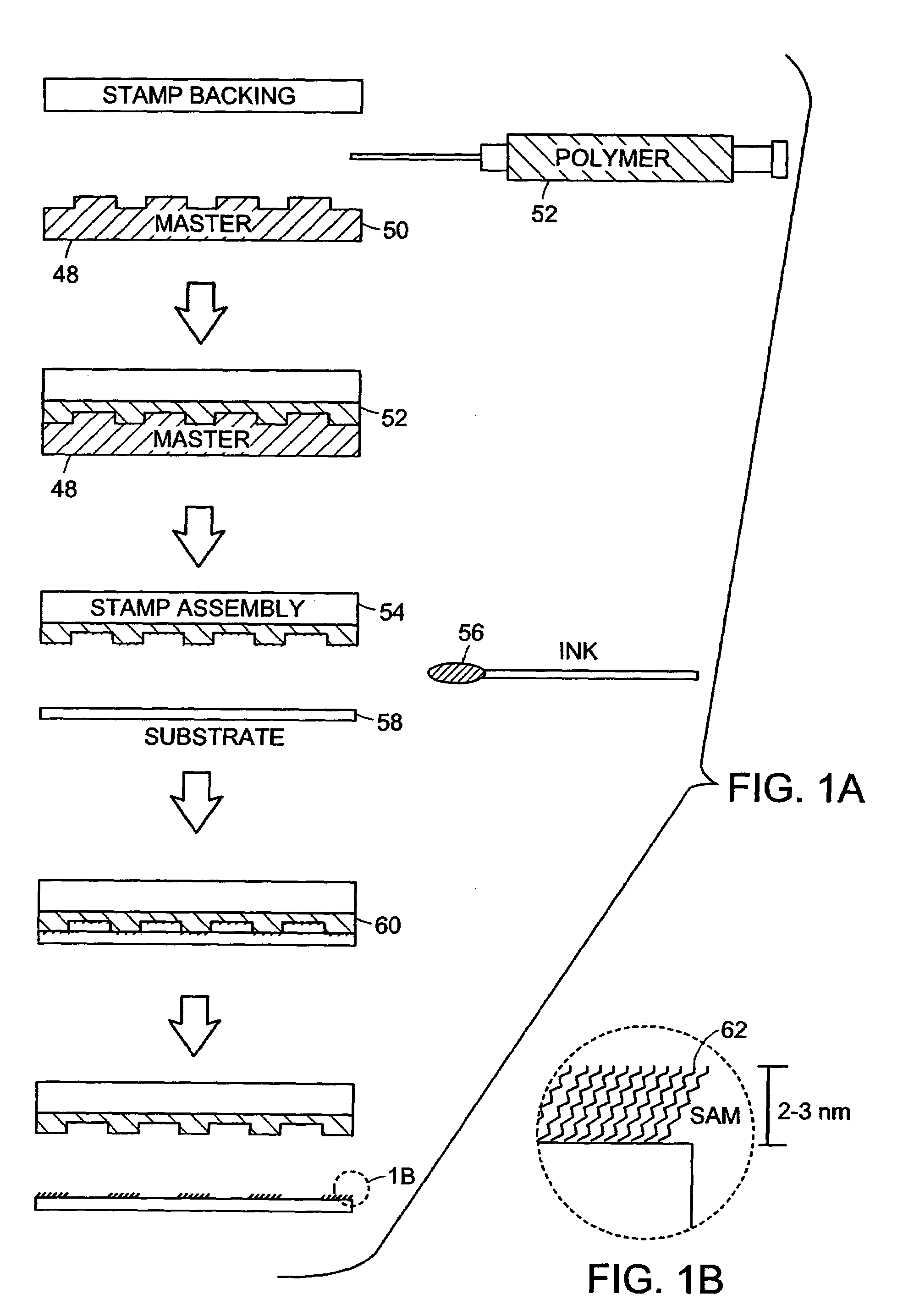
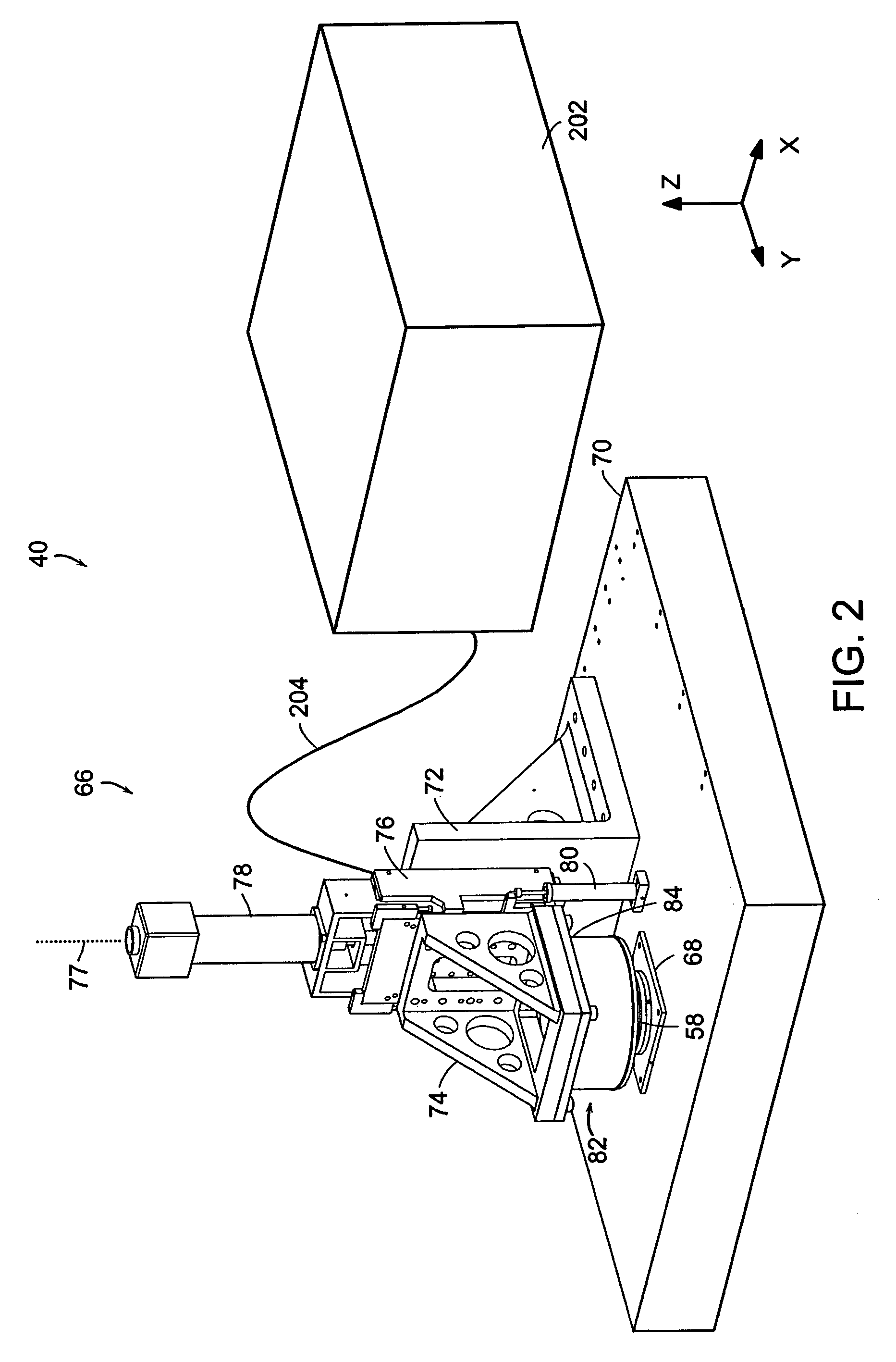
InactiveUS7117790B2Generate undesired patterning resultsControl distortionMaterial nanotechnologyNanoinformaticsMicrocontact printingEngineering
A microcontact printing tool having a print unit including a stamp head with a stamp and a wafer chuck for retaining a substrate. The stamp contained by the stamped head movable relative to the substrate by an actuator and a stage. A plurality of sensors detect the position of the stamp relative to substrate. A method of using the printing tool that includes a real-time feedback for consistent and accurate application of force during the printing of the substrate. The stamp head includes a pressure chamber carrying the stamp. The stamp backing is deflected prior to contact of the stamp with the substrate to form a minimum point and the stamp backing and the stamp is returned to a plane to create a printing propagation contact. An apparatus and method of producing the stamp on a stamp backing. The apparatus has a master backing and a stamping backing in close proximity and the stamp material drawn in through a vacuum. The stamp is separated from the master by use of a parting fluid.
Owner:MASSACHUSETTS INST OF TECH
Securized, multifunction, acquisition and processing terminal usable in the banking sector, in connection with games and in the electronic management of documents
InactiveUS6011850AHigh resolutionImprove linearityComplete banking machinesFinanceSpecific functionComputer module
The present invention relates to a securized, multifunction, acquisition and processing terminal more particularly usable in the banking sector, in connection with games and / or in the electronic management of documents, characterized in that it comprises: a mother board (13), having an interfacing bus with one or more standardized connectors to which can be connected standard input / output modules, at least one specific input / output module permitting the performance of specific functions incorporating at least one dedicated circuit, said module as its main function the supplying of the mother board with preorganized informations, in real time, concerning the specific functions and able to leave to said mother board any developed software processing of said informations.
Owner:BERTRAND DOMINIQUE +1
Method and system and article of manufacture for an N-tier software component architecture oilfield model
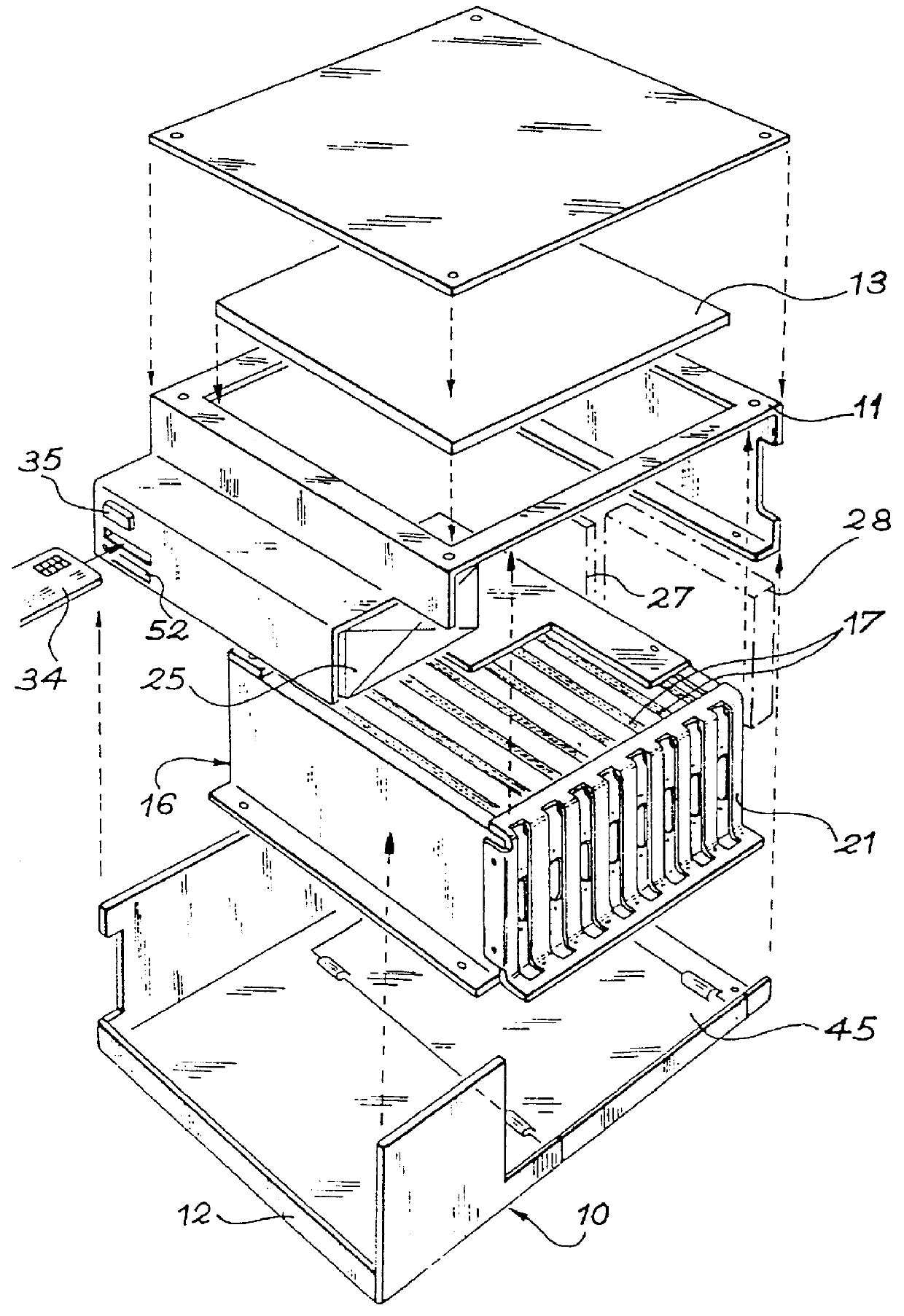
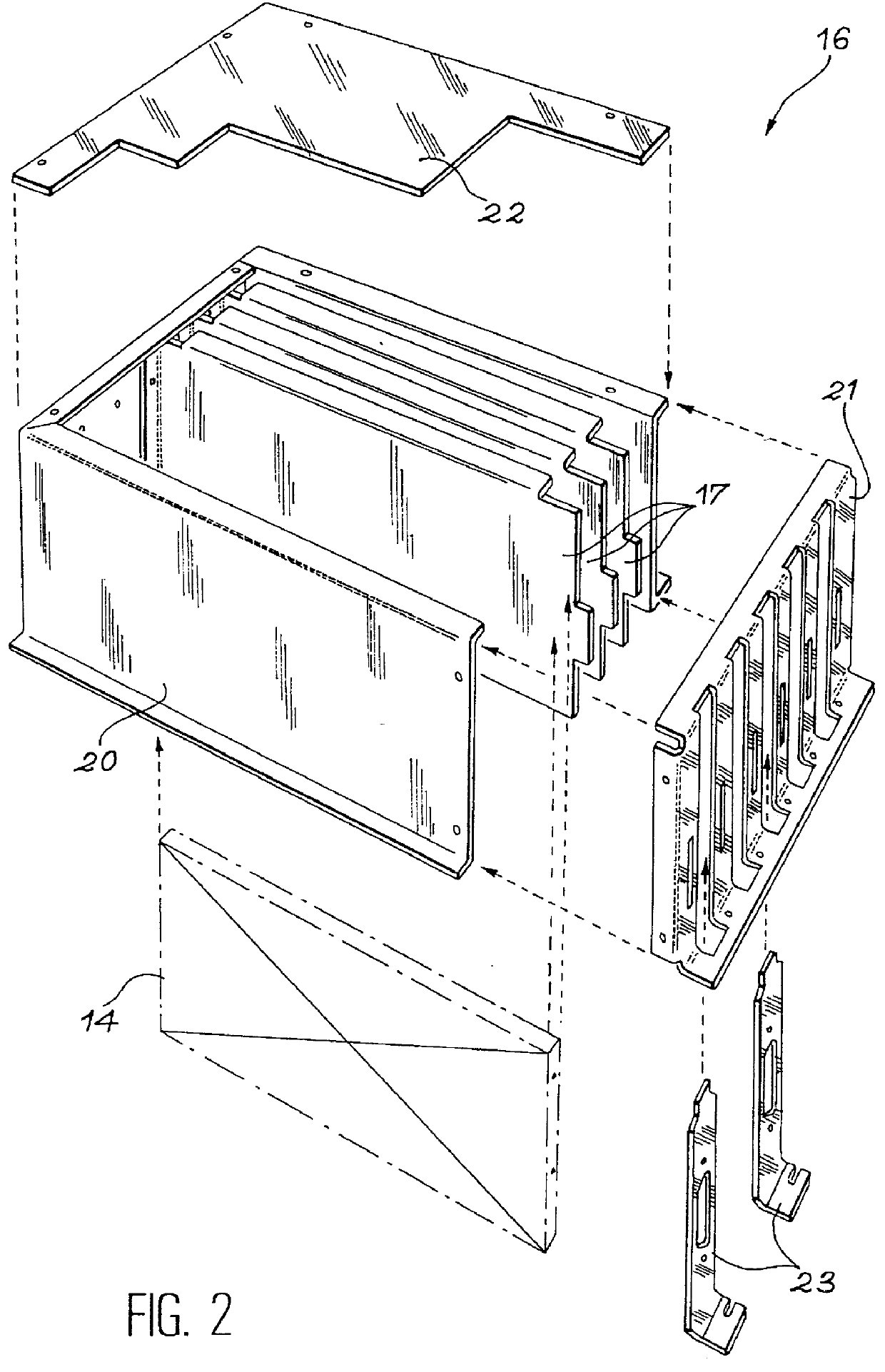
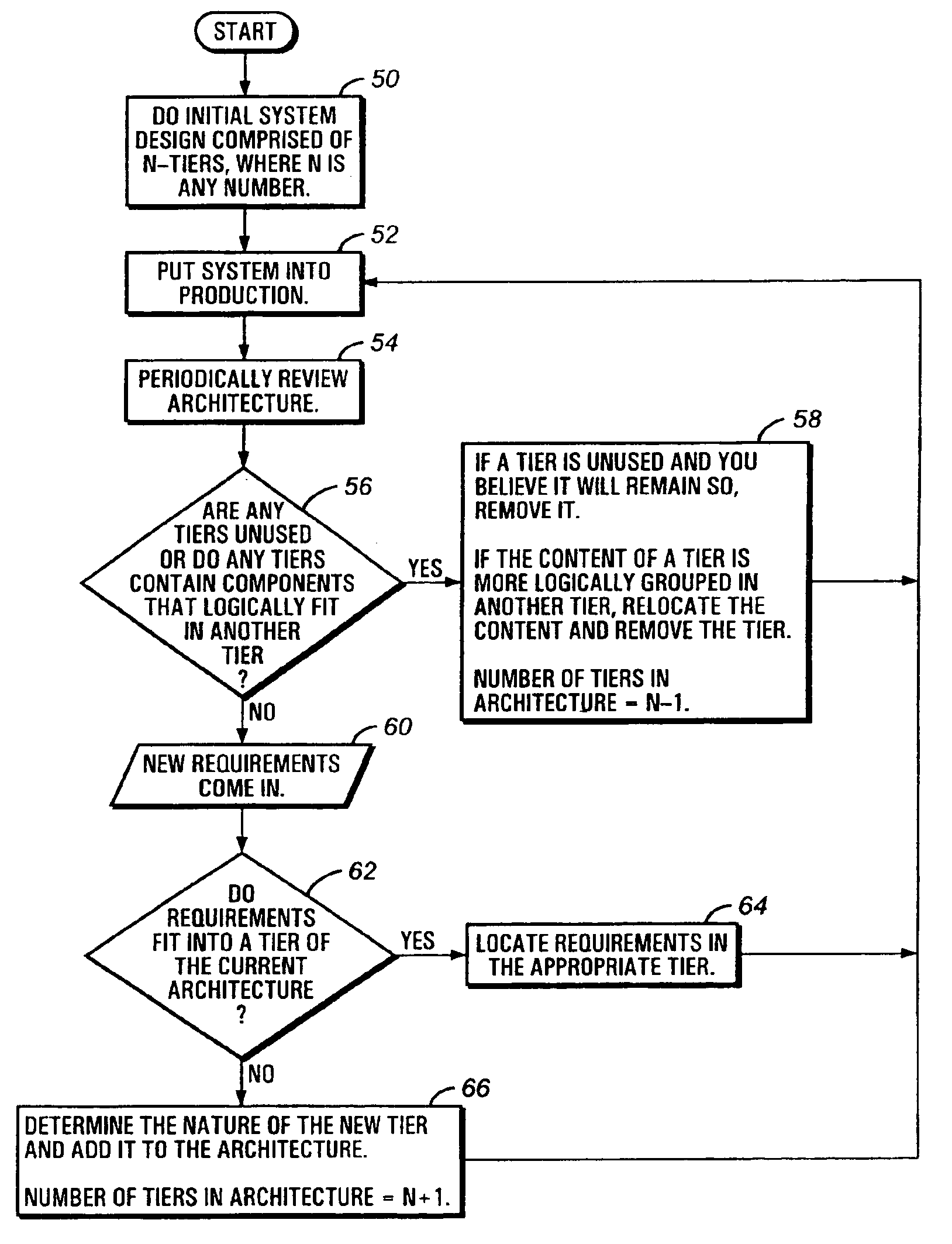
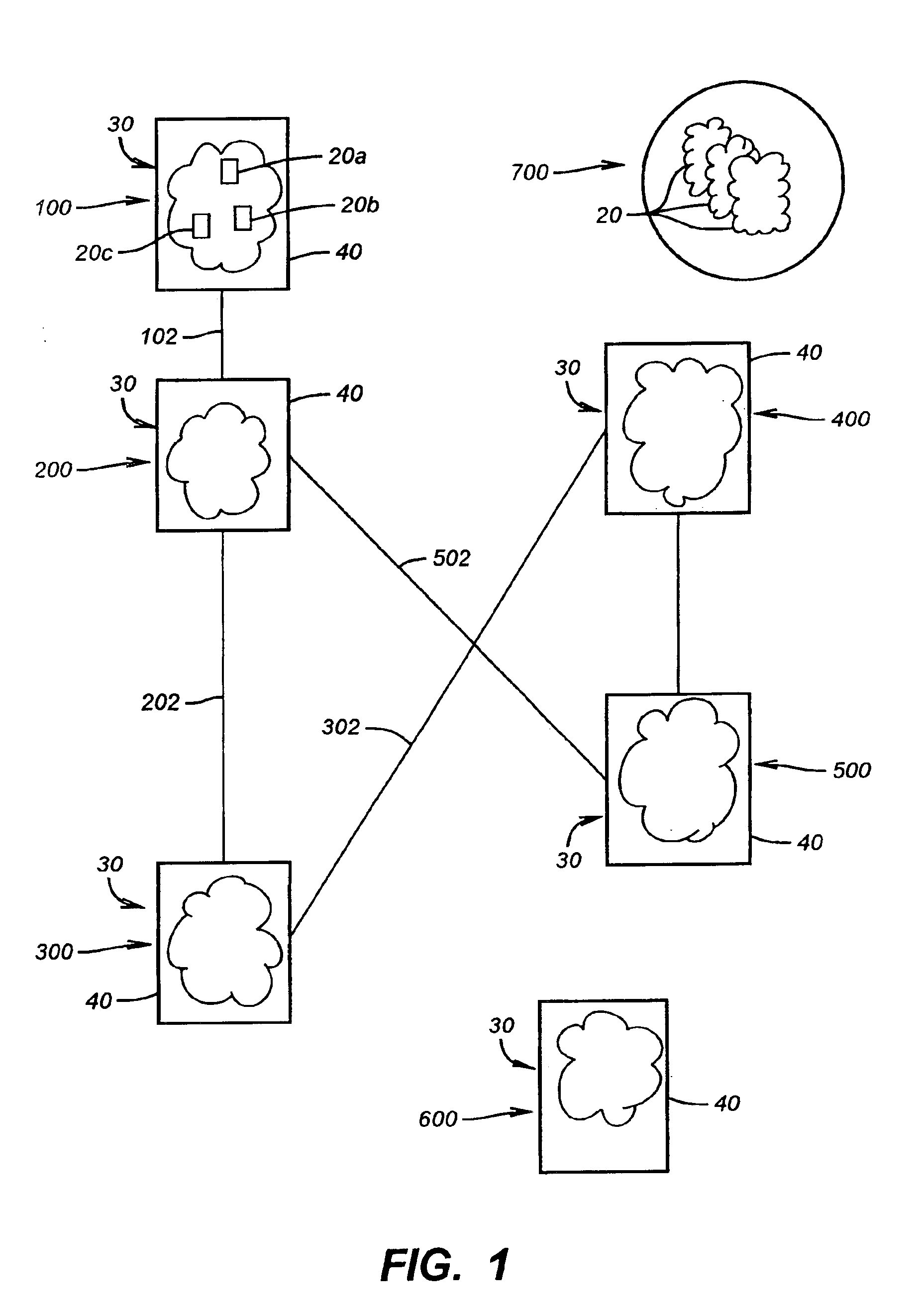
InactiveUS6931621B2Inking apparatusData processing applicationsComputer hardwareApplication software
A system and method for developing a software application for manipulating data associated with an asset are provided. The system includes at least one processing unit. The system further includes at least one memory store operatively connected to the processing unit. The system further includes an extensible N-tier software resident in and executable within the at least one processing unit, wherein N corresponds to a positive integer value. The system further includes an inventory of software components resident in the memory store wherein a plurality of tiers are generated from the inventory of a software components using the N-tier software, each tier being associated with at least one other tier, and each tier comprising a plurality of software components and performing a predetermined function relating to an asset.
Owner:BAKER HUGHES INC
Method, apparatus, and system for authentication using labels containing nucleotide sequences
InactiveUS20060286569A1Microbiological testing/measurementBiological testingHash functionNucleotide sequencing
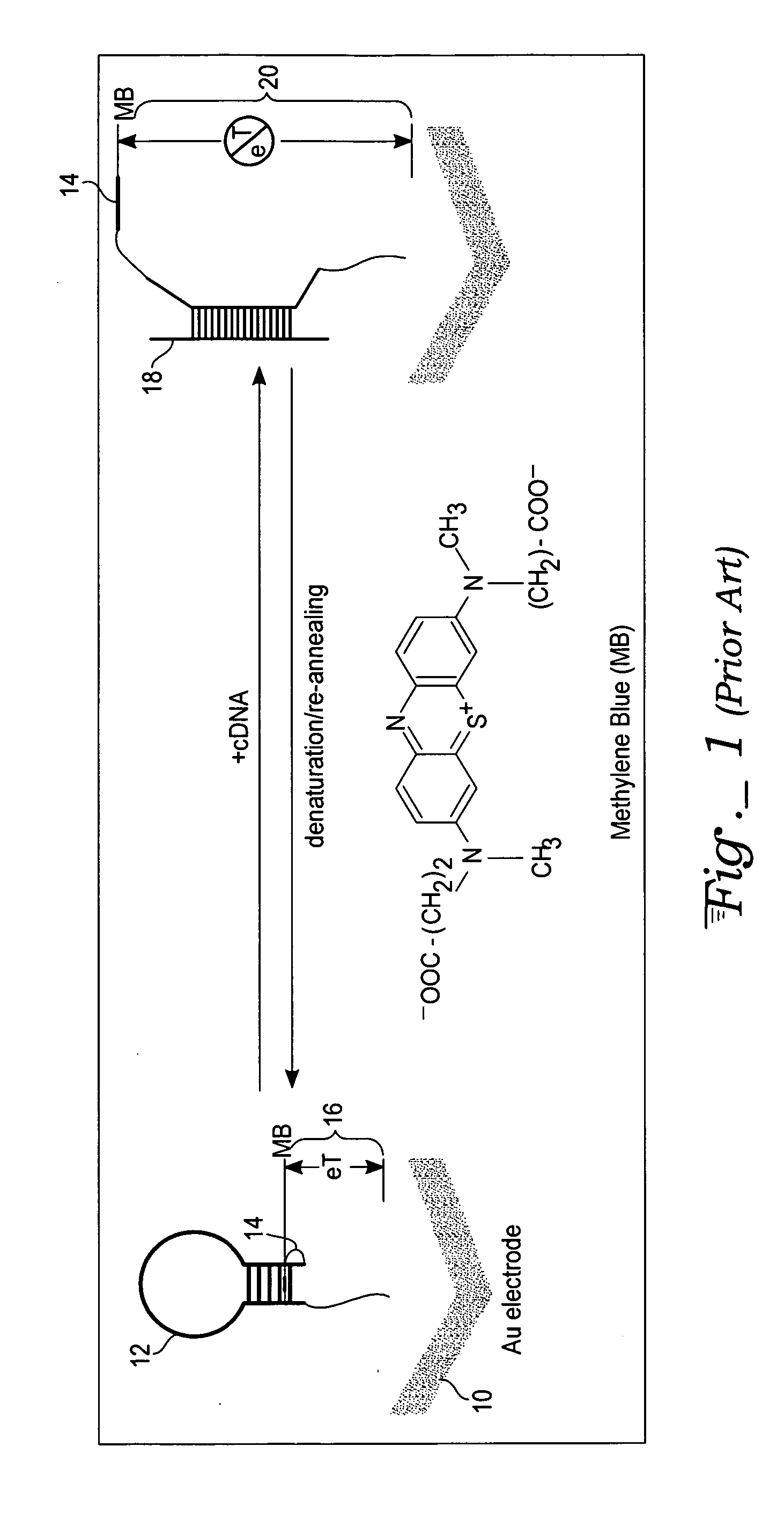
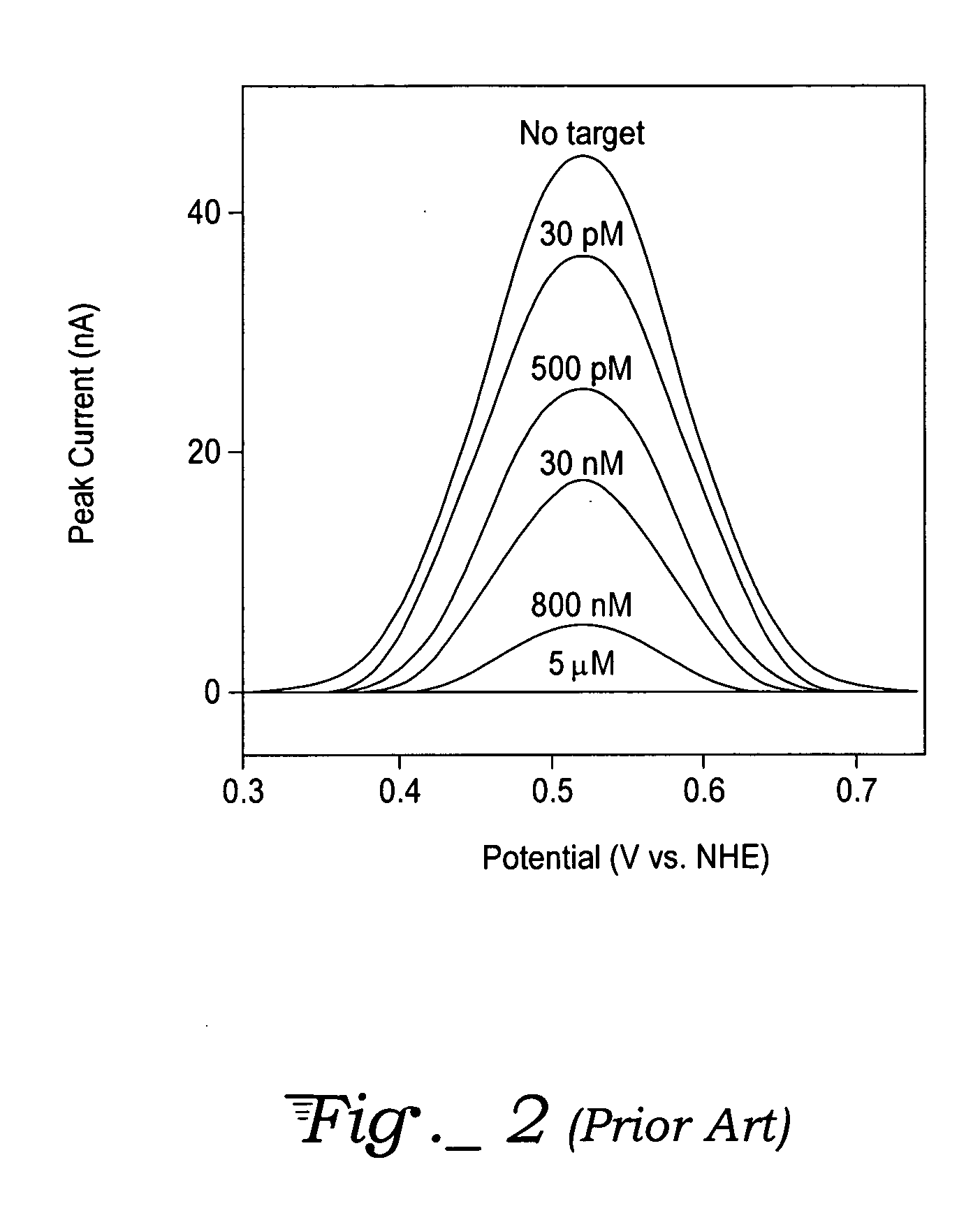
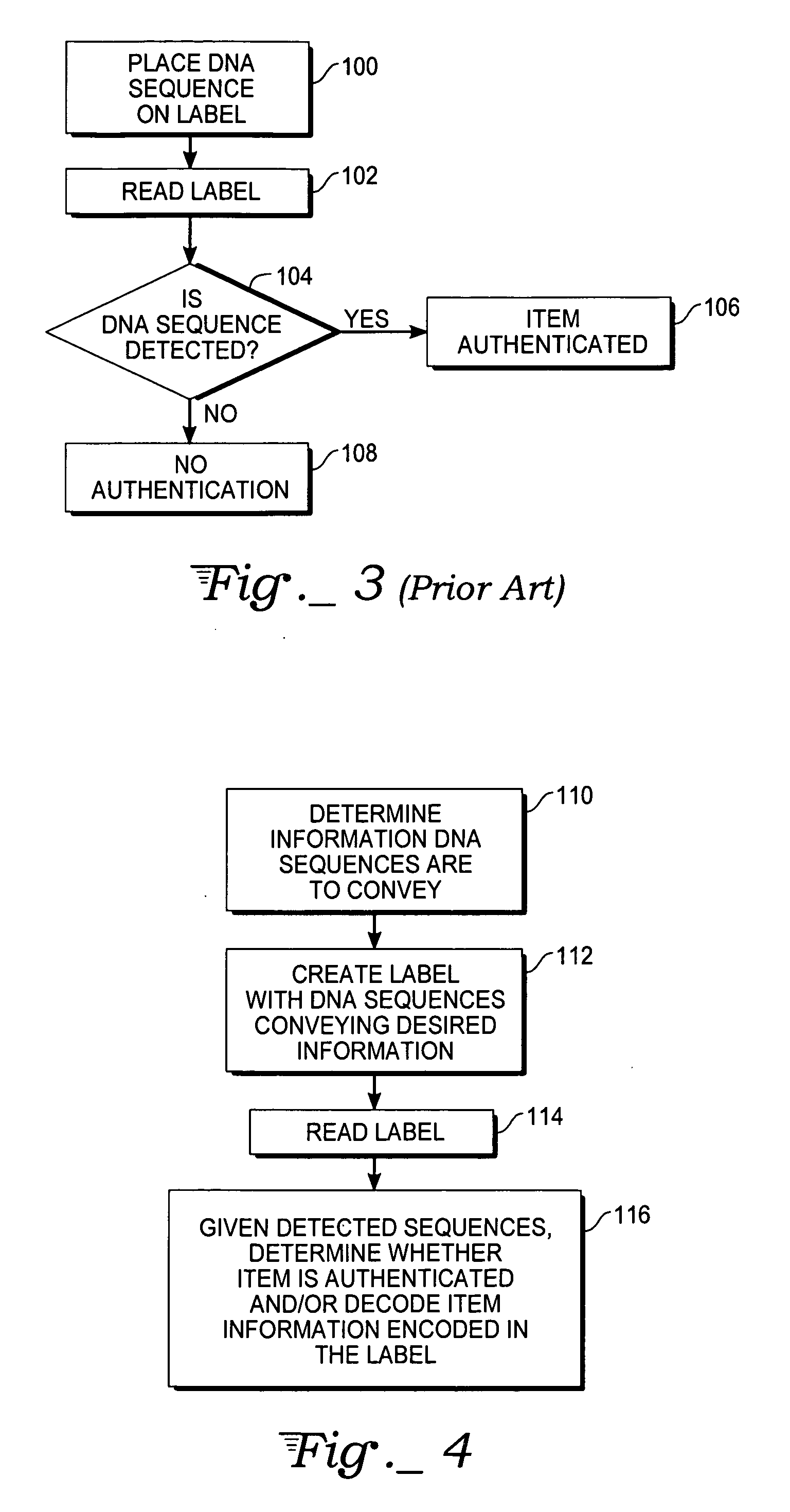
A method, label, and labeling system for labeling and authenticating an item are presented. At least one of a number of known nucleotide sequences associated with a predetermined amount of information is used as a label to be associated with an item. The label is then read with a reagentless sensor to detect the nucleotide sequence(s). The detected nucleotide sequence(s) is then associated with the appropriate information. The item is authenticated if the sensor detects the expected nucleotide sequence(s). The information in the DNA label may also be passed through a hash function or encrypted to further enhance security. The labels may also incorporate known non-natural nucleic acid analog sequences rather than nucleotide sequences, and a reader that reads known non-natural nucleic acid analog sequences may be employed.
Owner:BAR OR YUVAL +3
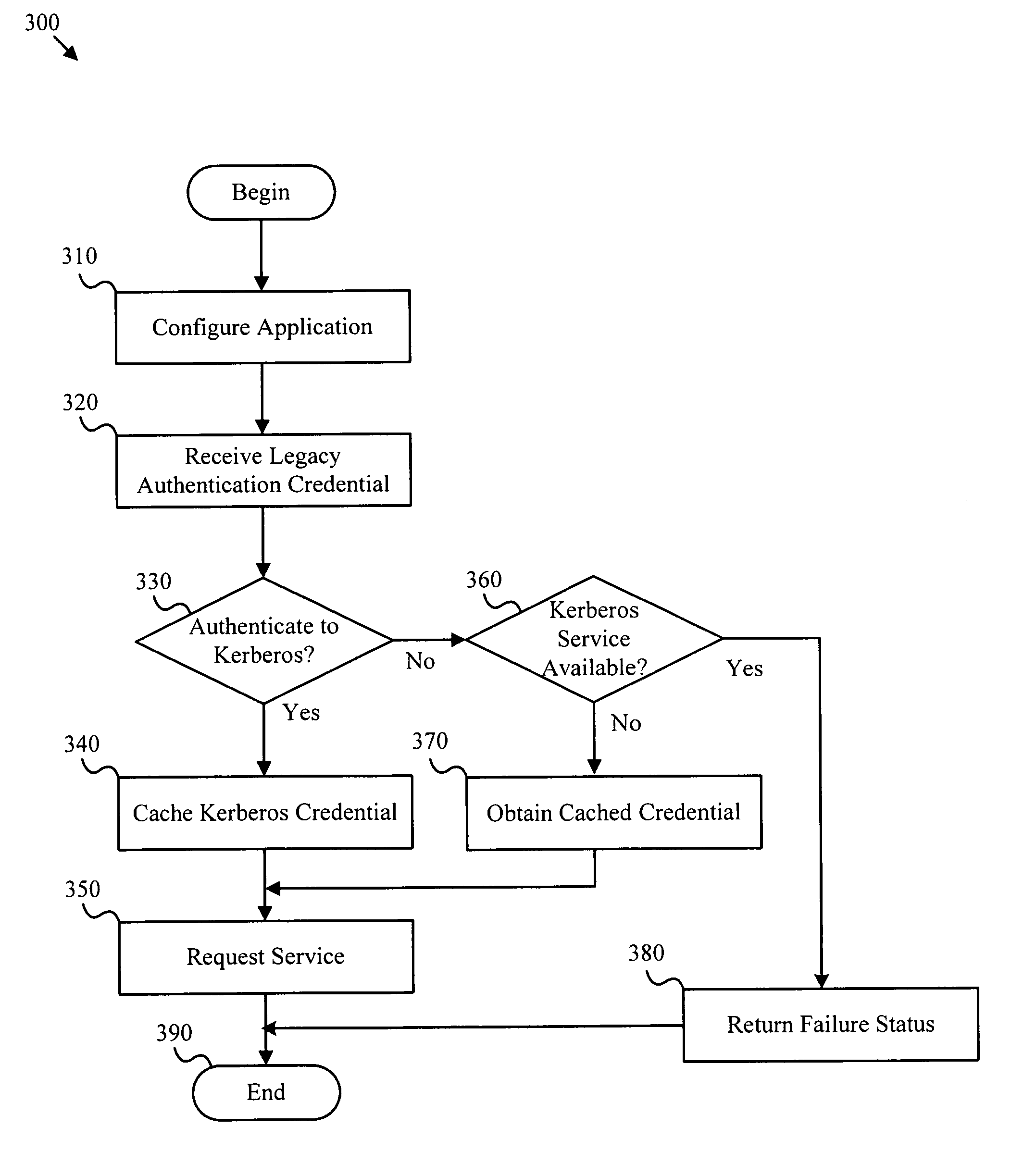
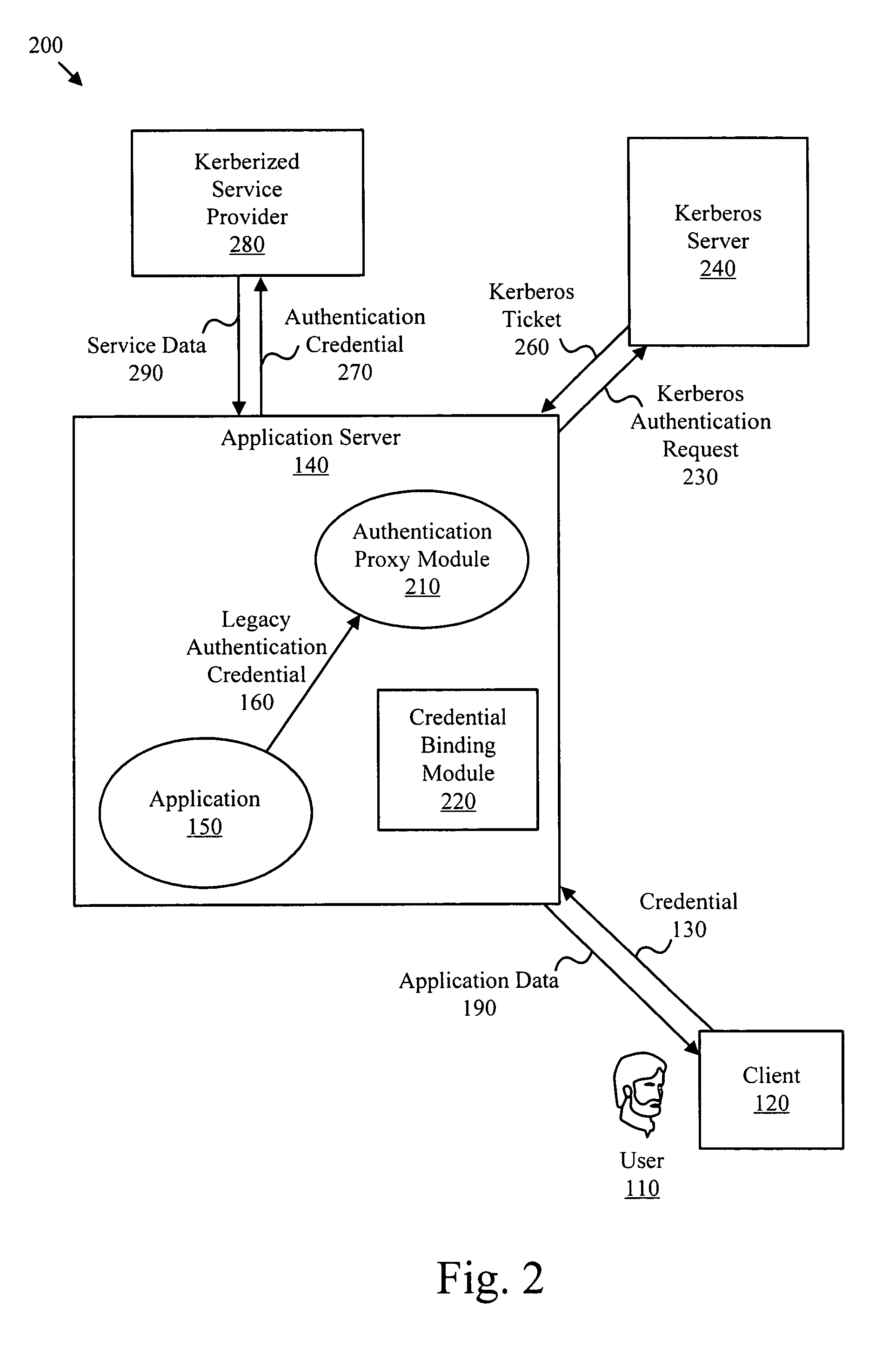
Apparatus, systems and methods to provide authentication services to a legacy application
ActiveUS7904949B2Digital data processing detailsUser identity/authority verificationInternet Authentication ServicePassword
Owner:QUEST SOFTWARE INC
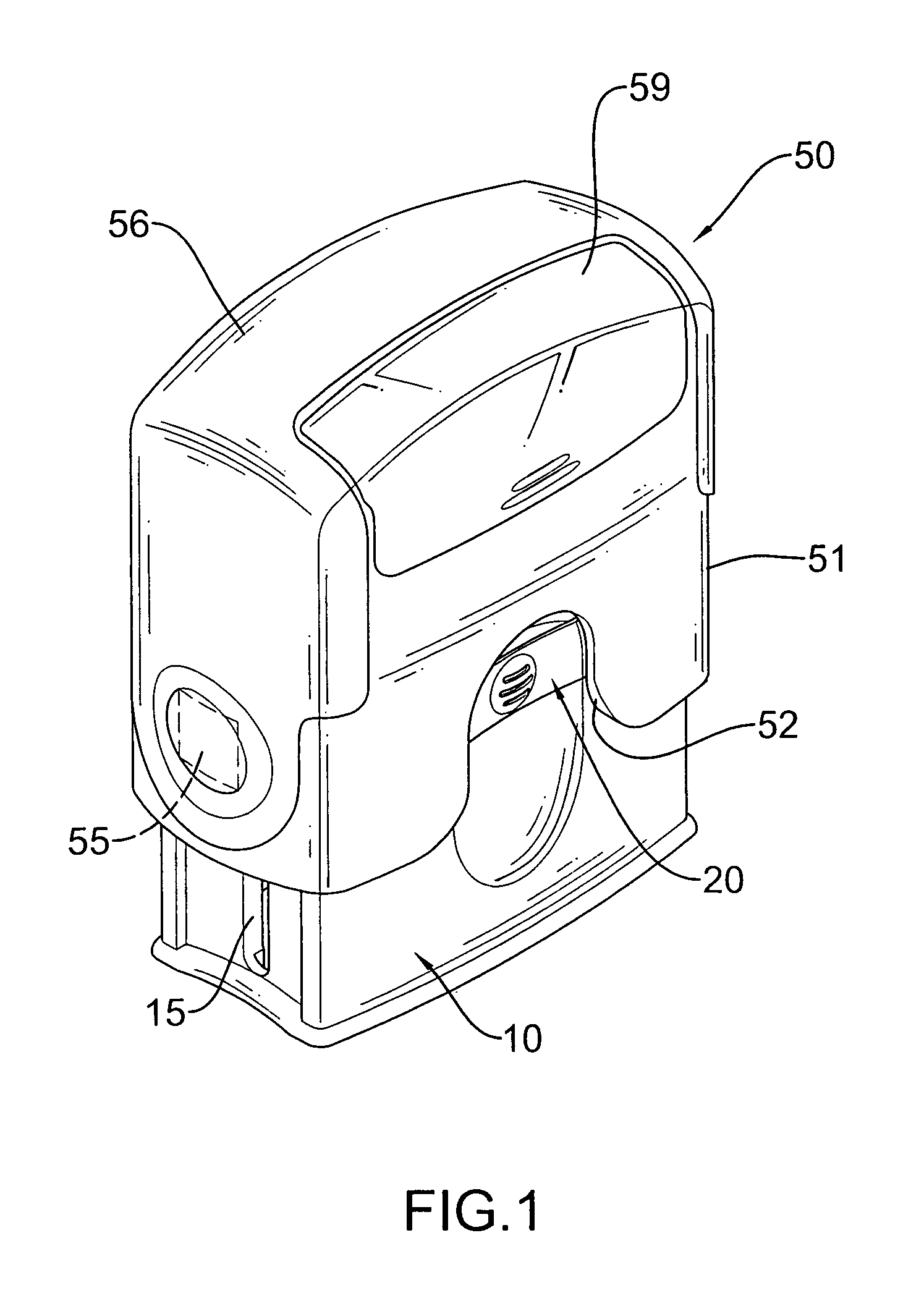
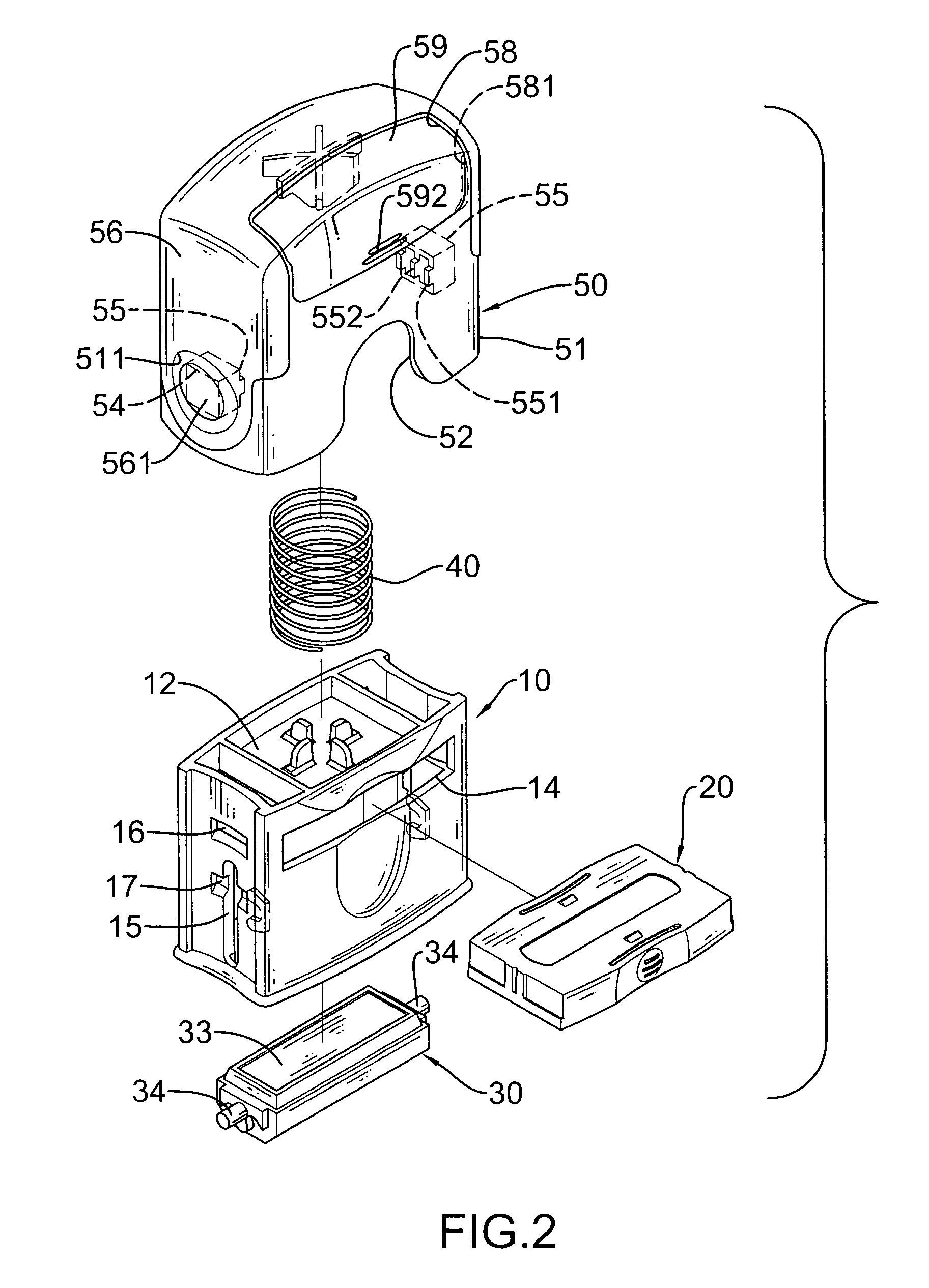
Housing assembly for a self-inking stamp
A housing assembly for a self-inking stamp includes a movable case, two pressing keepers and a protective film. The movable case has two opposite sides and two keeper mounting holes respectively defined through the sides of the movable case and aligned with each other. The pressing keepers are respectively and retractably mounted in the keeper mounting holes. The protective film is attached to the movable case and has two covering areas respectively aligned with and covering the pressing keepers. Consequently, the pressing keepers are completely enclosed and covered by the protective film, which will prevent gaps around the pressing keepers from being caulked or clogged with the contaminants as dust, skin oil or ink. In addition, the protective film will provide an improved touching feeling when a person holds the self-inking stamp.
Owner:SHIH SHINY
Method and Apparatus for Logging Based Identification
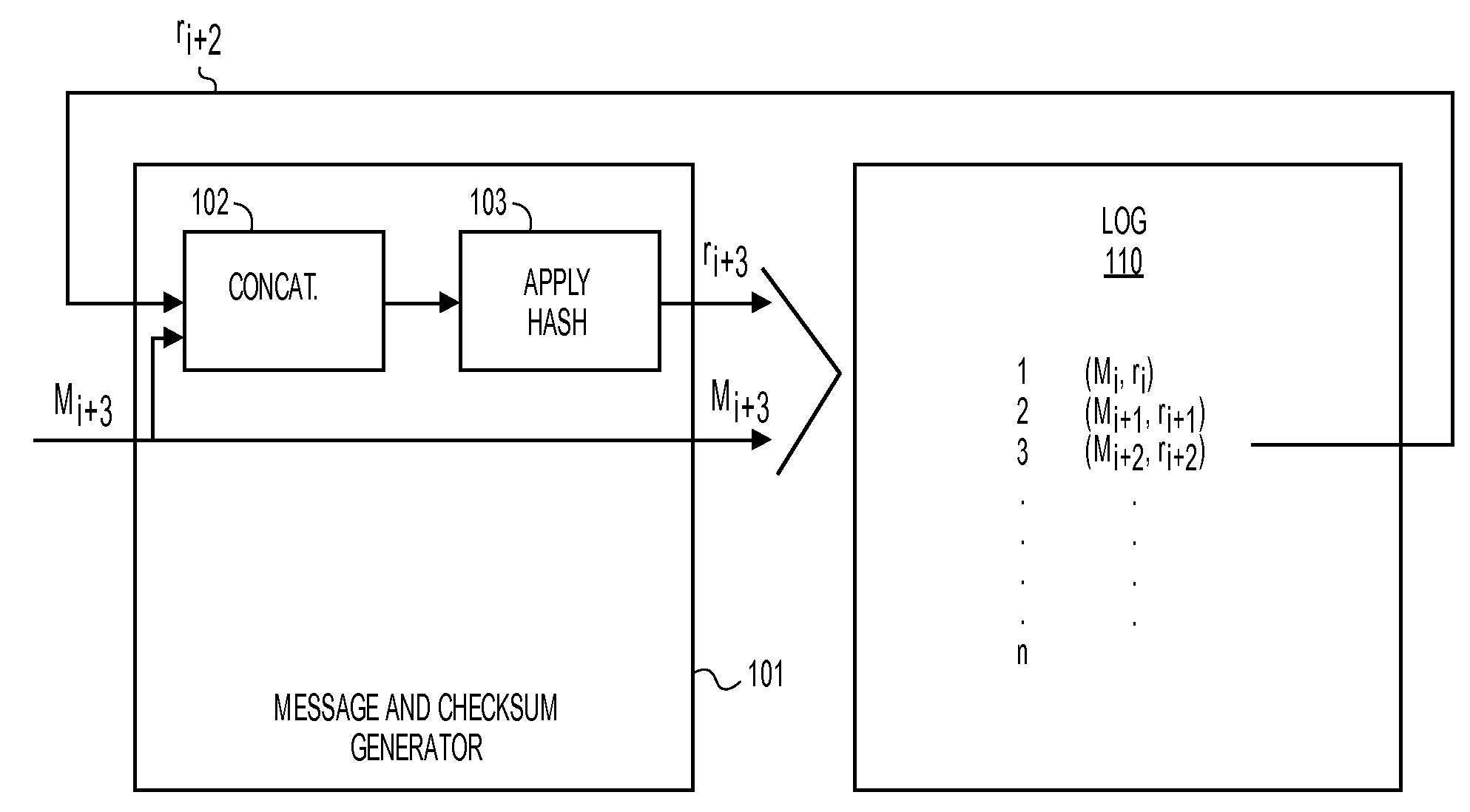
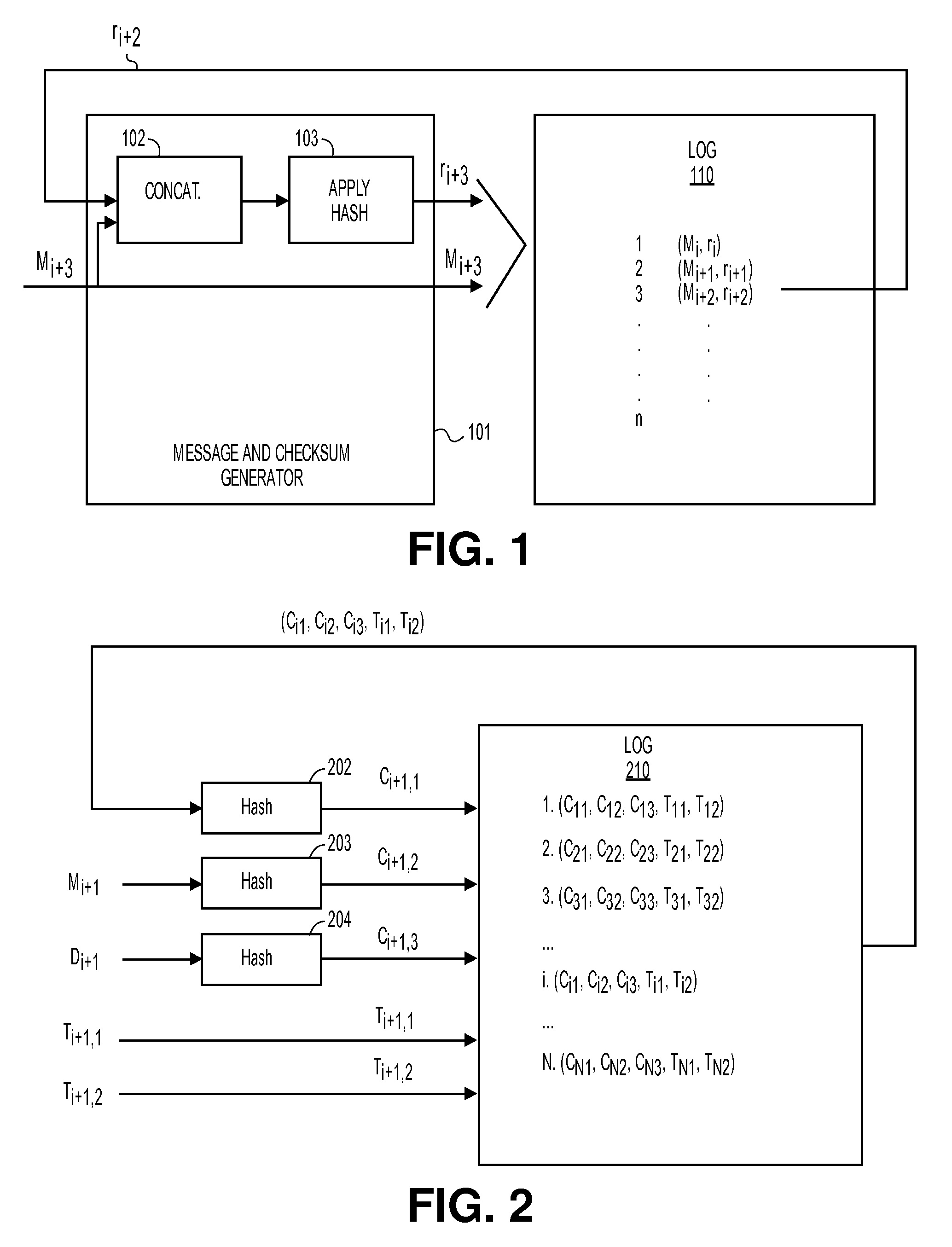
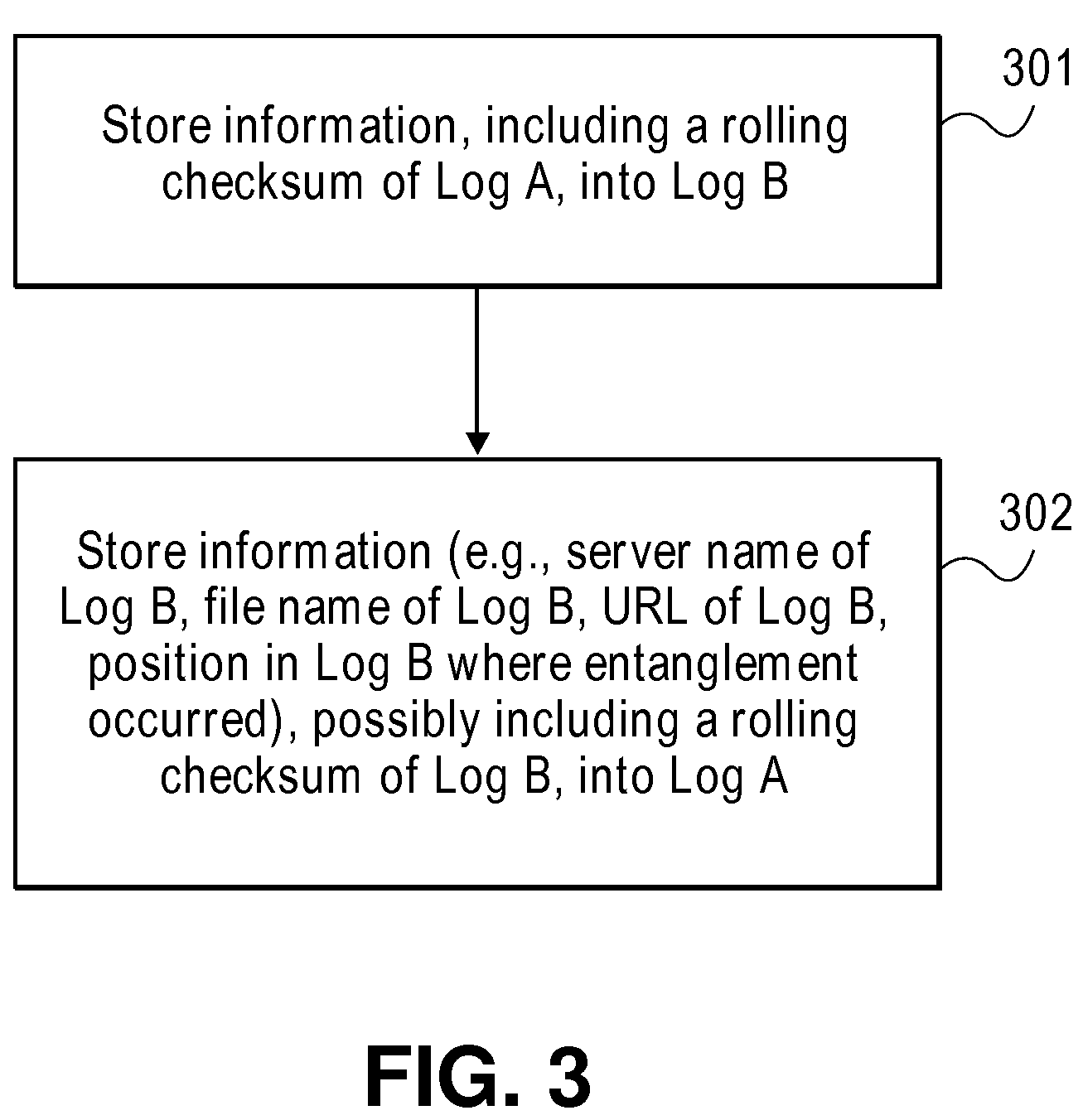
ActiveUS20100088517A1User identity/authority verificationStampingTheoretical computer scienceHash chain
A method and apparatus for logging based identification are described. In one embodiment, the method comprises extracting entries of a hash chained log that represents a series of previous transactions. The method may also comprise ordering hash values of the entries extracted from the hash chained log into an ordered list. In one embodiment, the method may further comprise producing a cryptographic hash of the ordered list.
Owner:RICOH KK
Secure remote electronic voting system and cryptographic protocols and computer programs employed
InactiveUS20050021479A1Efficient implementationDrawback and limitationVoting apparatusError detection/correctionCryptographic protocolConfidence score
The method employs interrelated cryptographic processes (210) and protocols (202,204,206,208,212,214), specially designed to provide reliability to vote casting, ballots recount, and verification of vote or poll results. These cryptographic processes and protocols jointly constitute a cryptographic voting scheme capable of meeting the specific reliability requirements of an electronic voting where voters remotely cast their votes. More specifically, these reliability requirements include voter authentication and privacy; accurate results, the impossibility of coercion and sale of votes, verifying the final results and, if necessary, the secrecy of intermediate results before completing the vote or poll. The proposed cryptographic voting scheme allows minimizing the confidence level to be placed on any of the electronic voting individual party and participants. Moreover, the cryptographic voting scheme significantly improves the implementation practical aspects with regard to prior works in secure electronic voting methods and systems.
Owner:SCYTL ELECTION TECH SL
Secure method and system for biometric verification
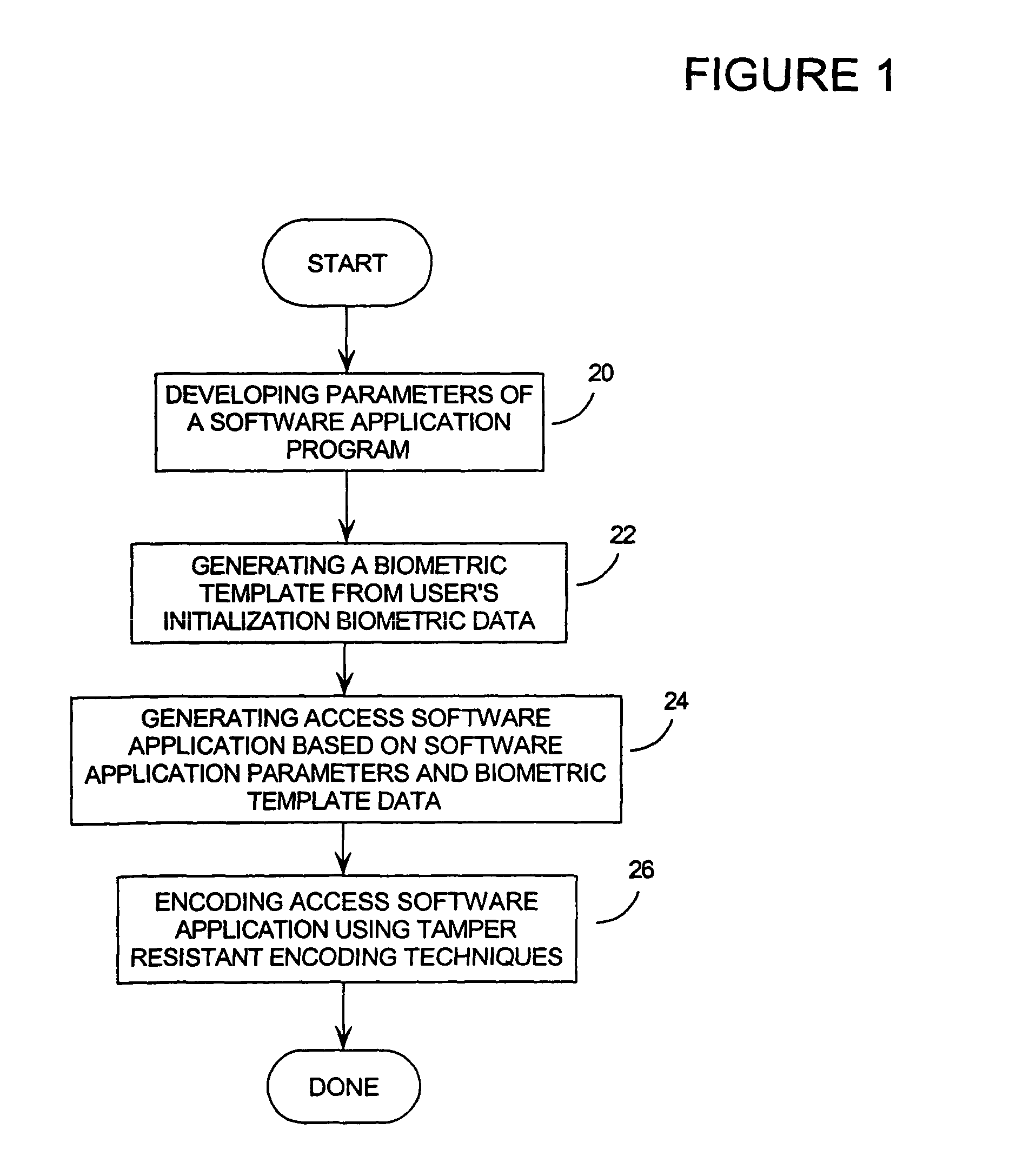
InactiveUS7797549B2Electric signal transmission systemsMultiple keys/algorithms usageControl flowBiometric data
There is a need in the computer software and data industries to protect content from unauthorized access to private information. Alphanumeric passwords have been shown to offer very weak protection. Biometrics (personal traits such as fingerprints and hand-written signatures) offer superior protection, but still have a number of weaknesses. The most significant weakness is that there is no existing way to protect the stored biometric data itself; and once a person's fingerprint data has been obtained by an attacker, the use of that fingerprint can no longer be considered secure. The invention solves the problem by securing the access software application that manages the biometric data using tamper-resistant encoding techniques. These tamper-resistant encoding techniques include: data-flow, control-flow, mass-data and white-box encoding.
Owner:IRDETO ACCESS
Apparatus for applying printed matter to webs of wrapping material for smokers' products
Owner:HAUNI MASCHINENBAU AG
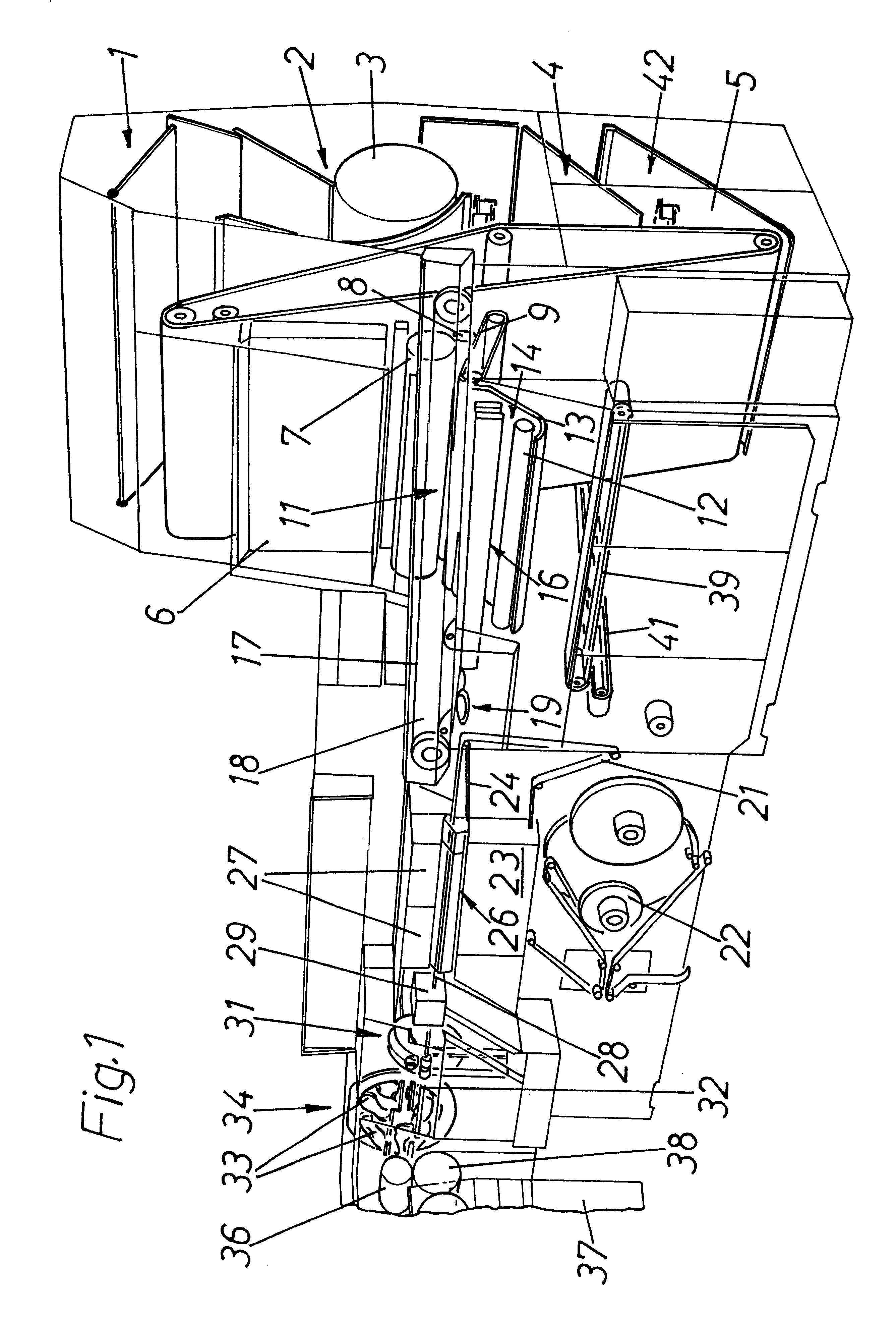
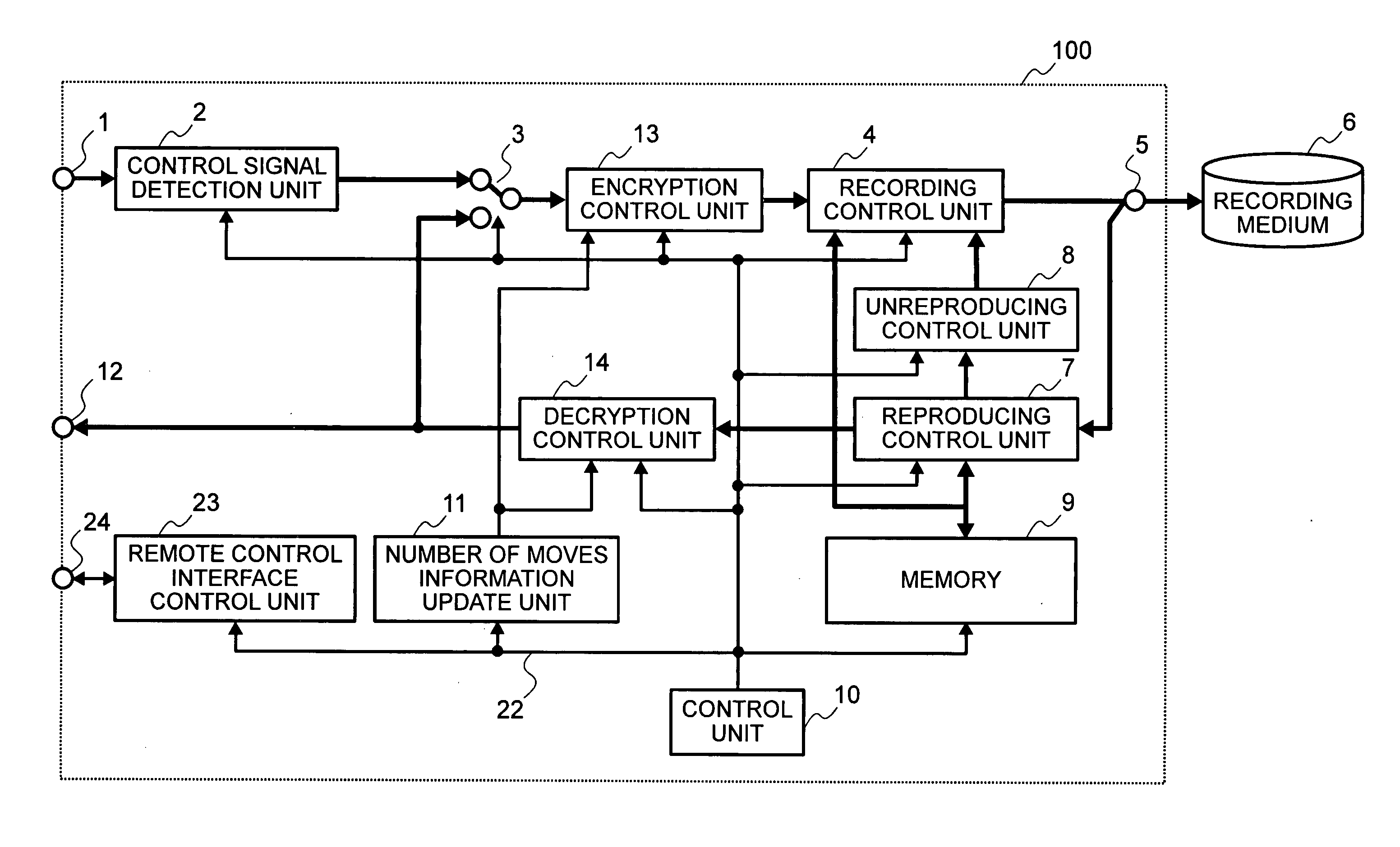
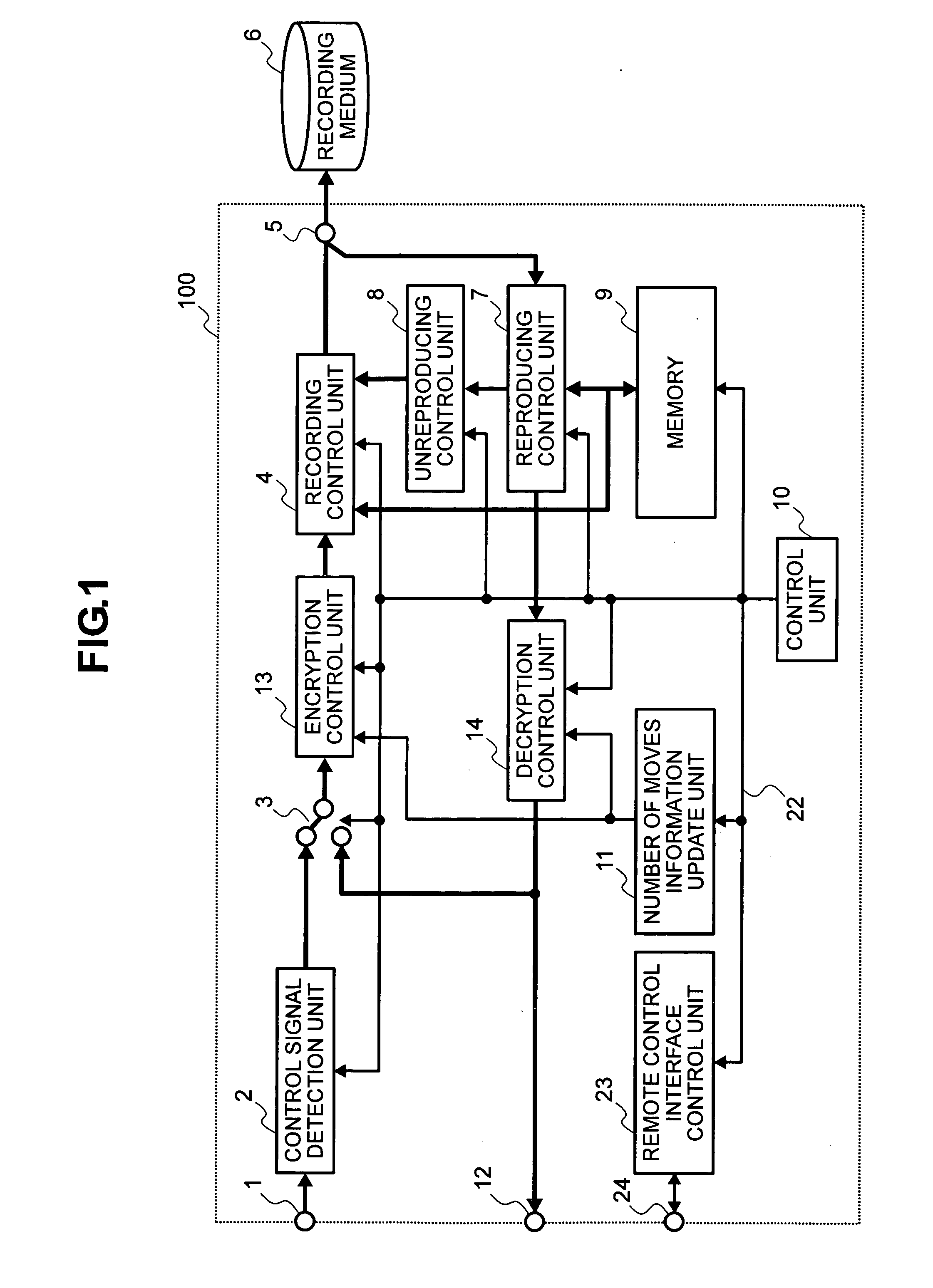
Digital information recording and reproducing method and apparatus therefor
InactiveUS20060077825A1Improve user friendlinessHigh precisionOptical re-recordingDigital data processing detailsCopy controlBit rate
To solve the problem inhibiting the copyright protection caused by reason that there are no means for restricting the number of backups to other media, which makes it impossible for a copyright owner to specify the allowable number of backups for the content of “Copy One Generation”, disclosed herein is a digital information recording and reproducing method. The method is so configured that: a first piece of digital information and copy control information of the first piece of digital information is received, wherein the copy control information is for controlling the recording of the first piece of digital information on a recording medium; and when the received copy control information is Copy One Generation indicating that only one generation copy of digital information is allowed, a plurality of the first pieces of digital information are recorded on a first recording medium as the first piece of digital information and a second piece of digital information, wherein the first piece of digital information is different in format or in bit rate from the second piece of digital information.
Owner:MAXELL HLDG LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com