System for controlling access and distribution of digital property
a technology for controlling access and digital property, applied in the direction of television systems, unauthorized memory use protection, instruments, etc., can solve the problems of reducing sound quality, small, but noticeable, and affecting the economic benefits of the system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
examples
[0326] The following examples indicate some envisioned data and its packaging and rules. These examples are only intended to show some of the envisioned uses of the present invention, and are in no way intended to limit its uses.
[0327] Books
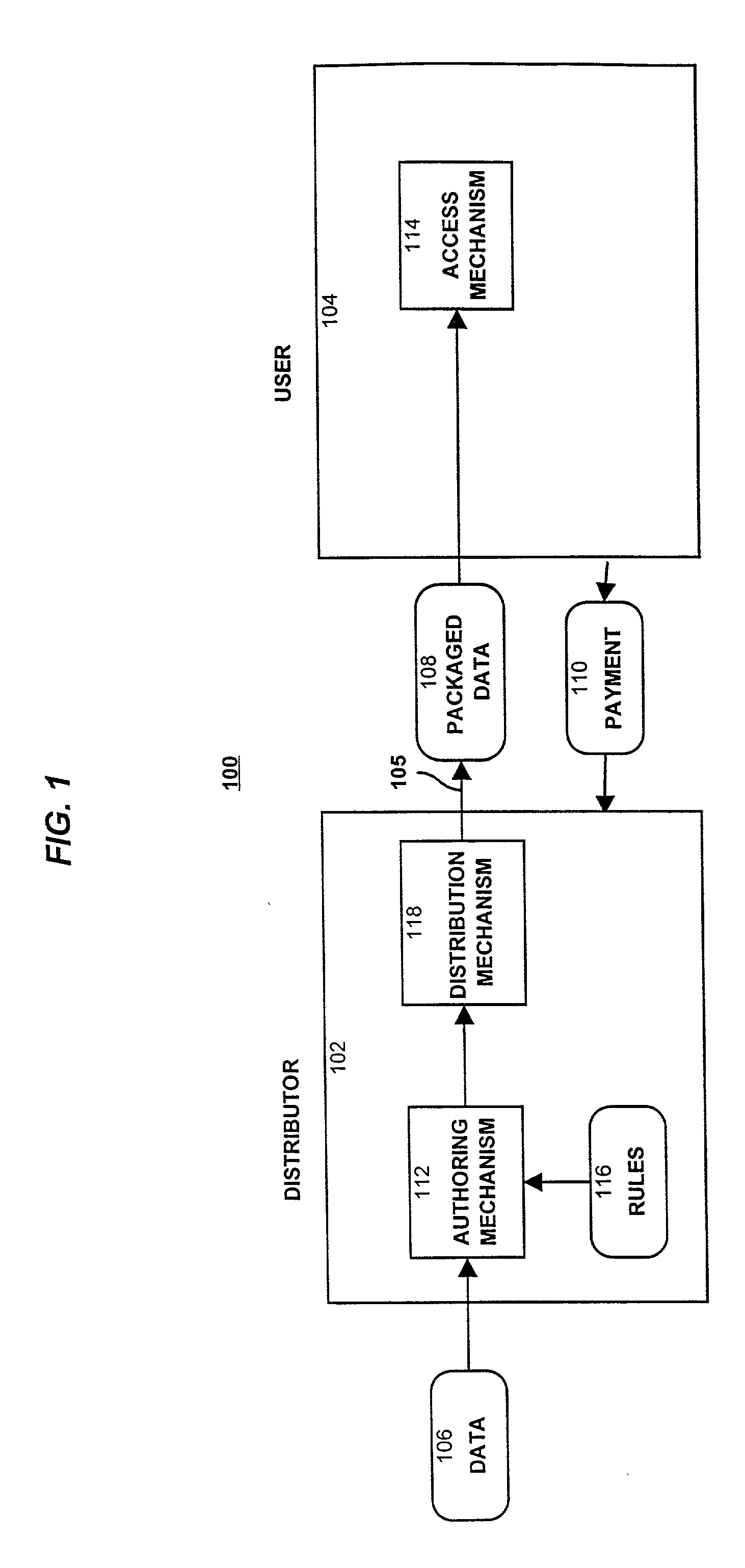
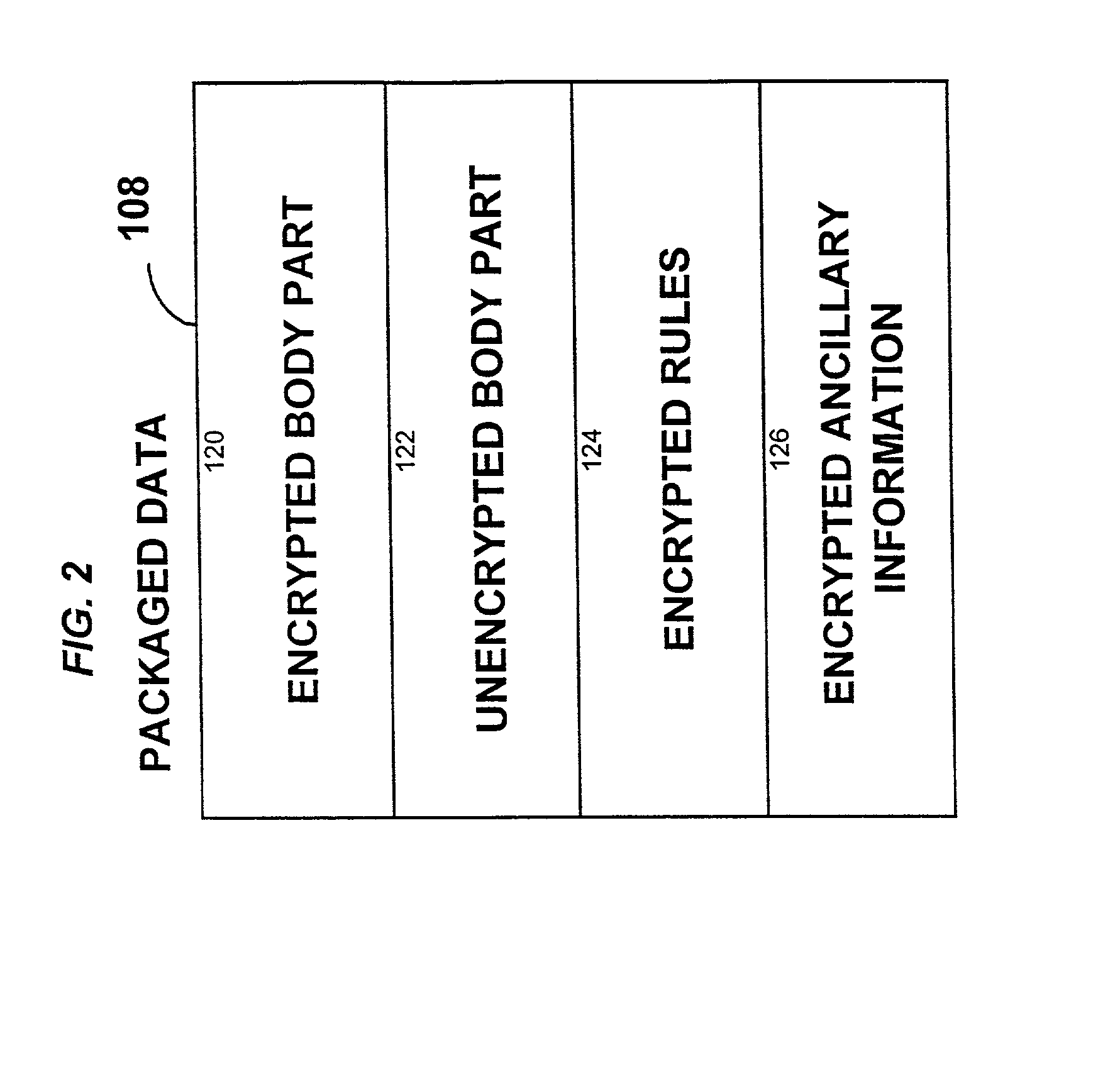
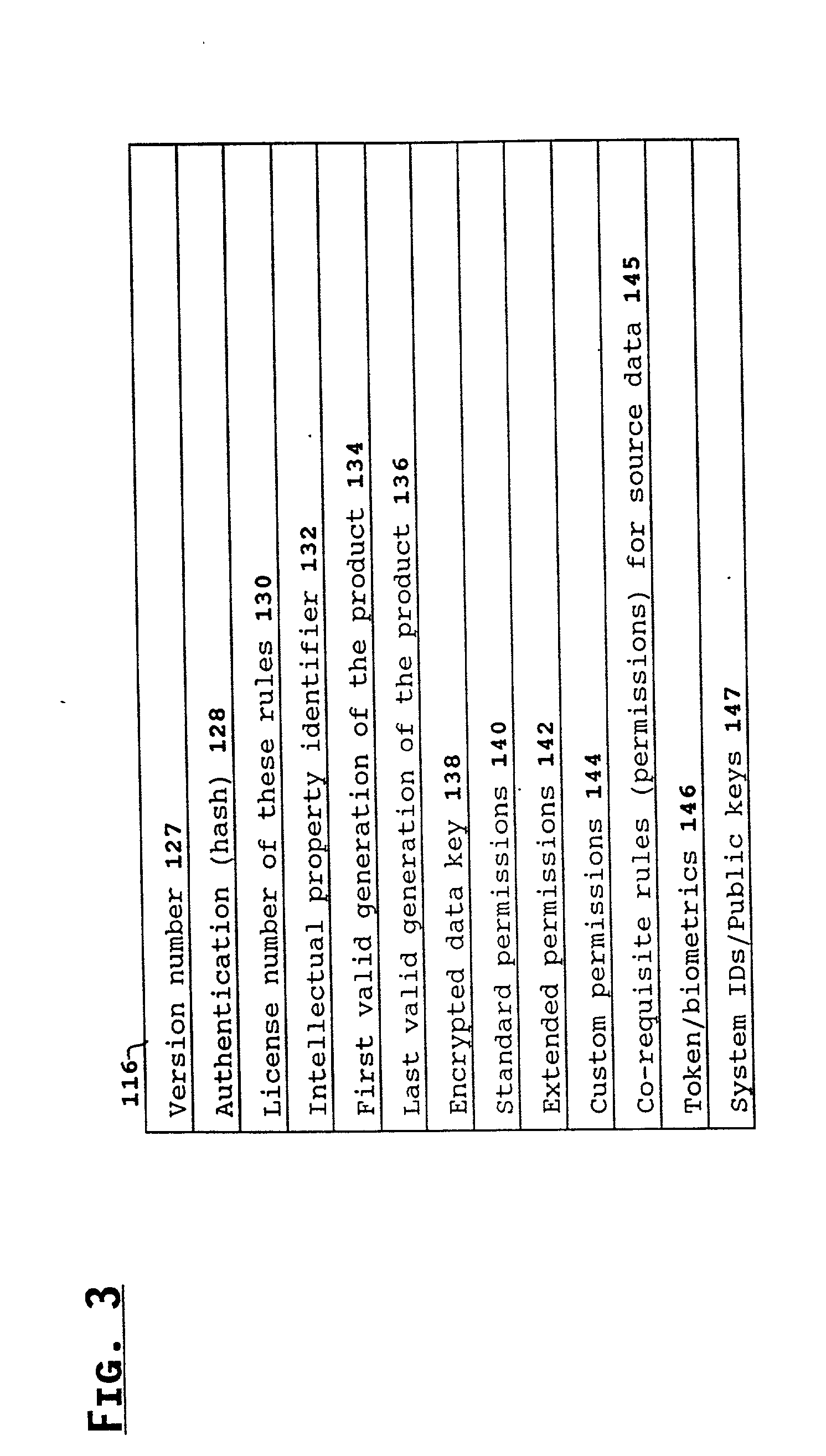
[0328] With reference to FIG. 18(a), a digital book 191 consists of an abstract 192, an index 194, and various chapters 196. Each chapter 196 comprises sections 198, and each section comprises text 200 and FIGS. 202. The distributor can decide to package the book 191 such that the abstract 192 and the index 194 are available for browsing, but all other data are protected (encrypted). If the rules specify that the text is restricted in certain ways, then the packaged data structure 108 has the form shown in FIG. 18(b), wherein encrypted body part 120 includes all chapters 196, unencrypted body part 122 includes the abstract 192 and index 194, and encrypted rules 124 contains the encrypted version of the rules.
[0329] Movies
[0330] With reference to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com