Patents
Literature
152results about How to "Technique is effective" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
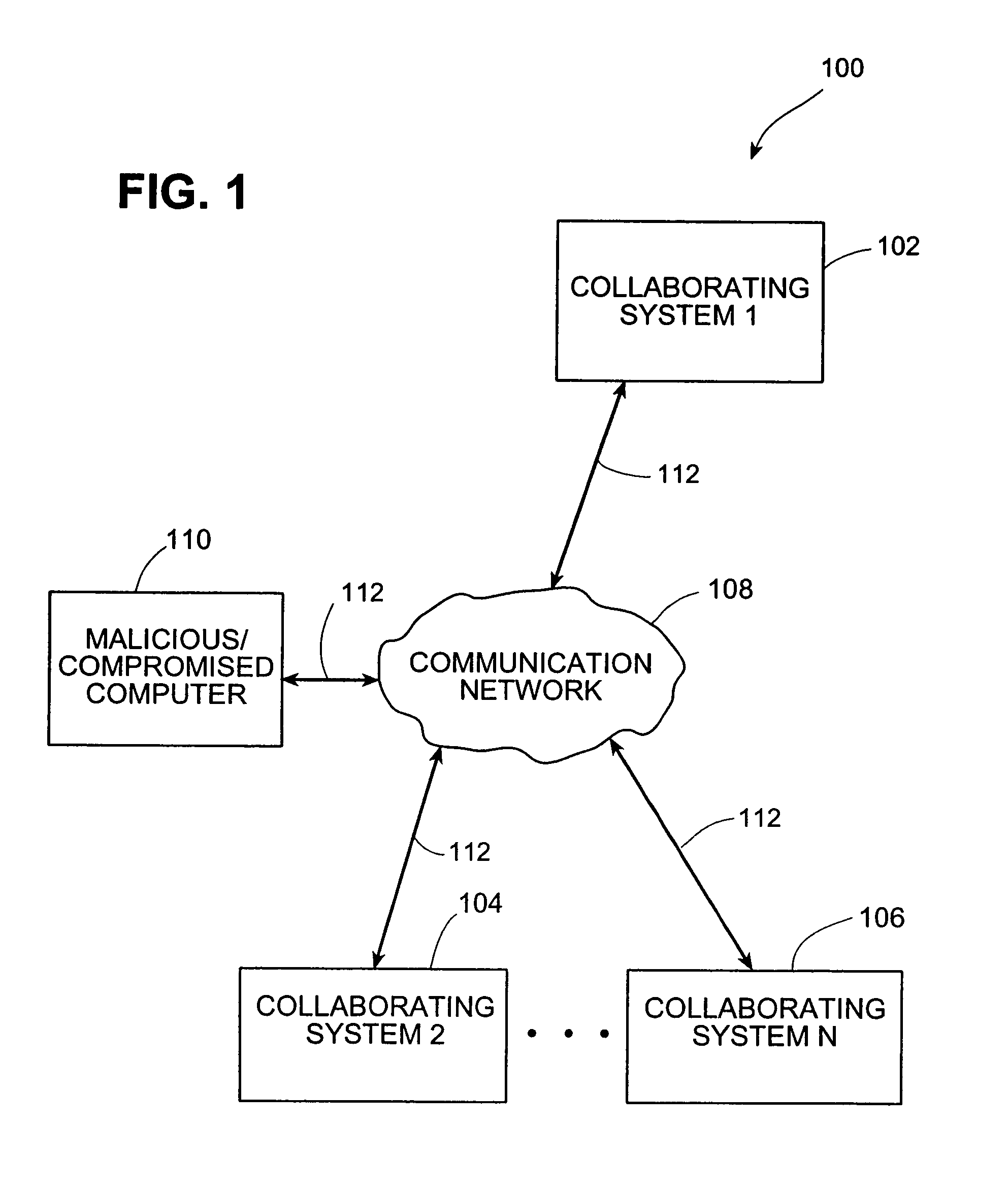
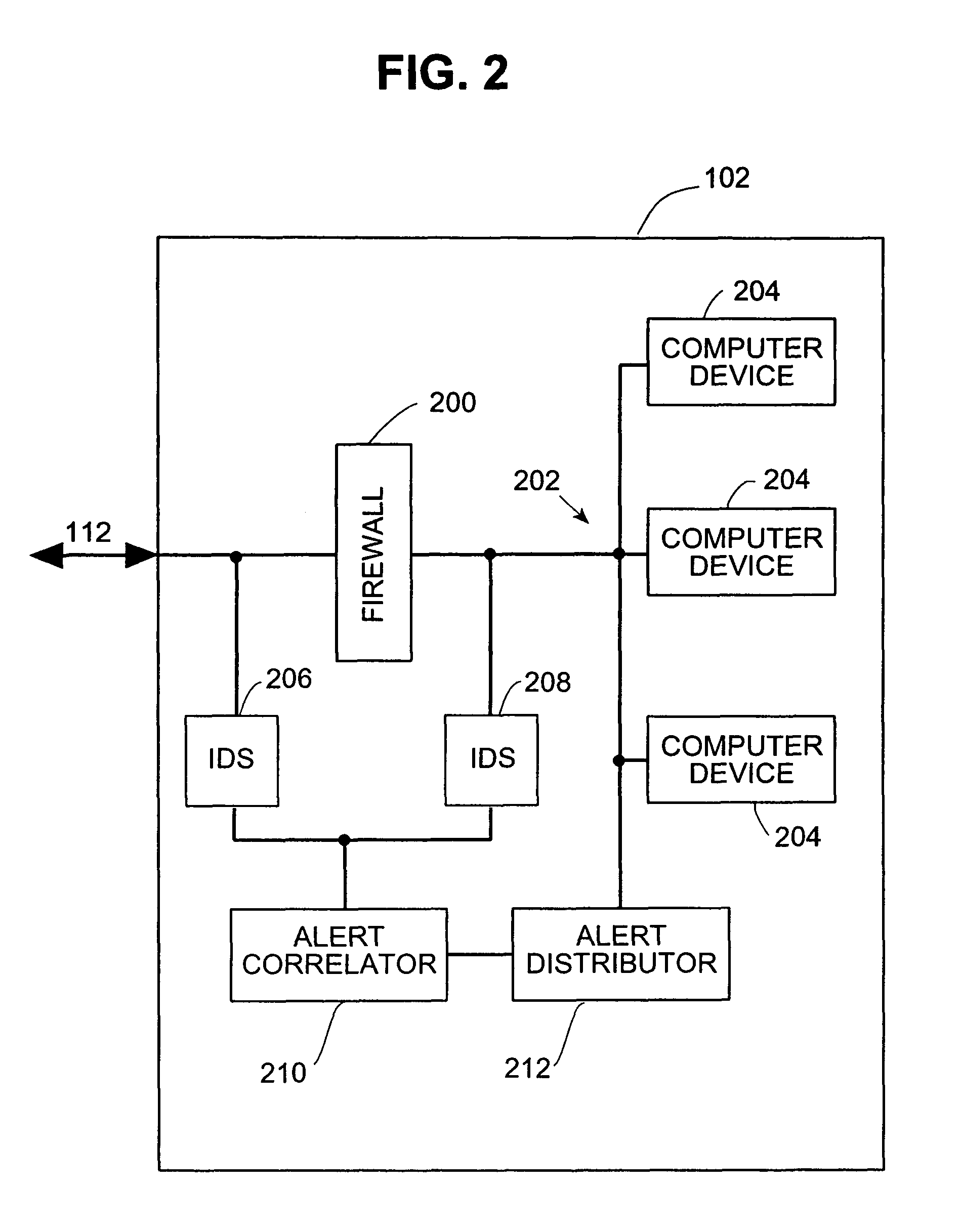
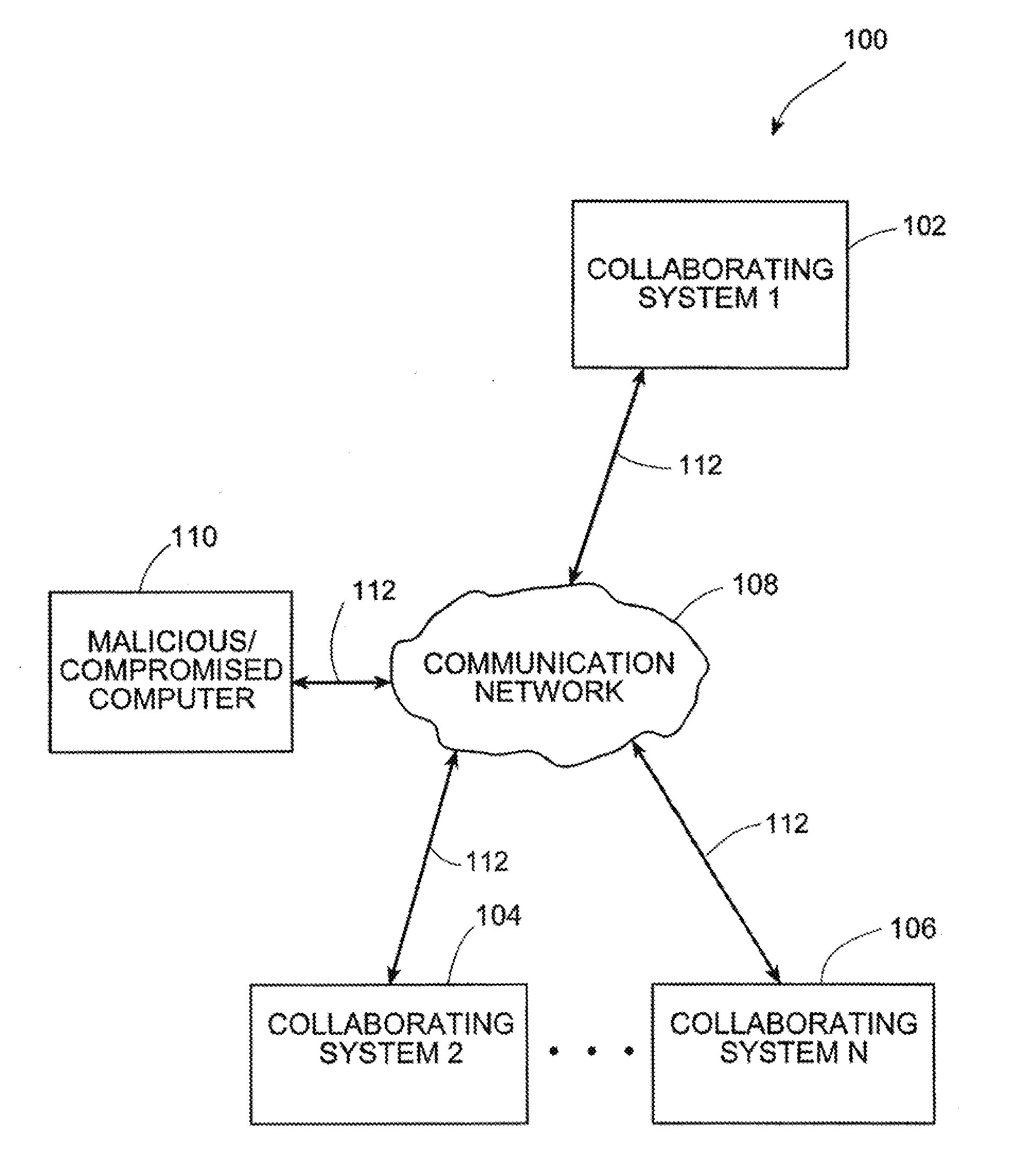
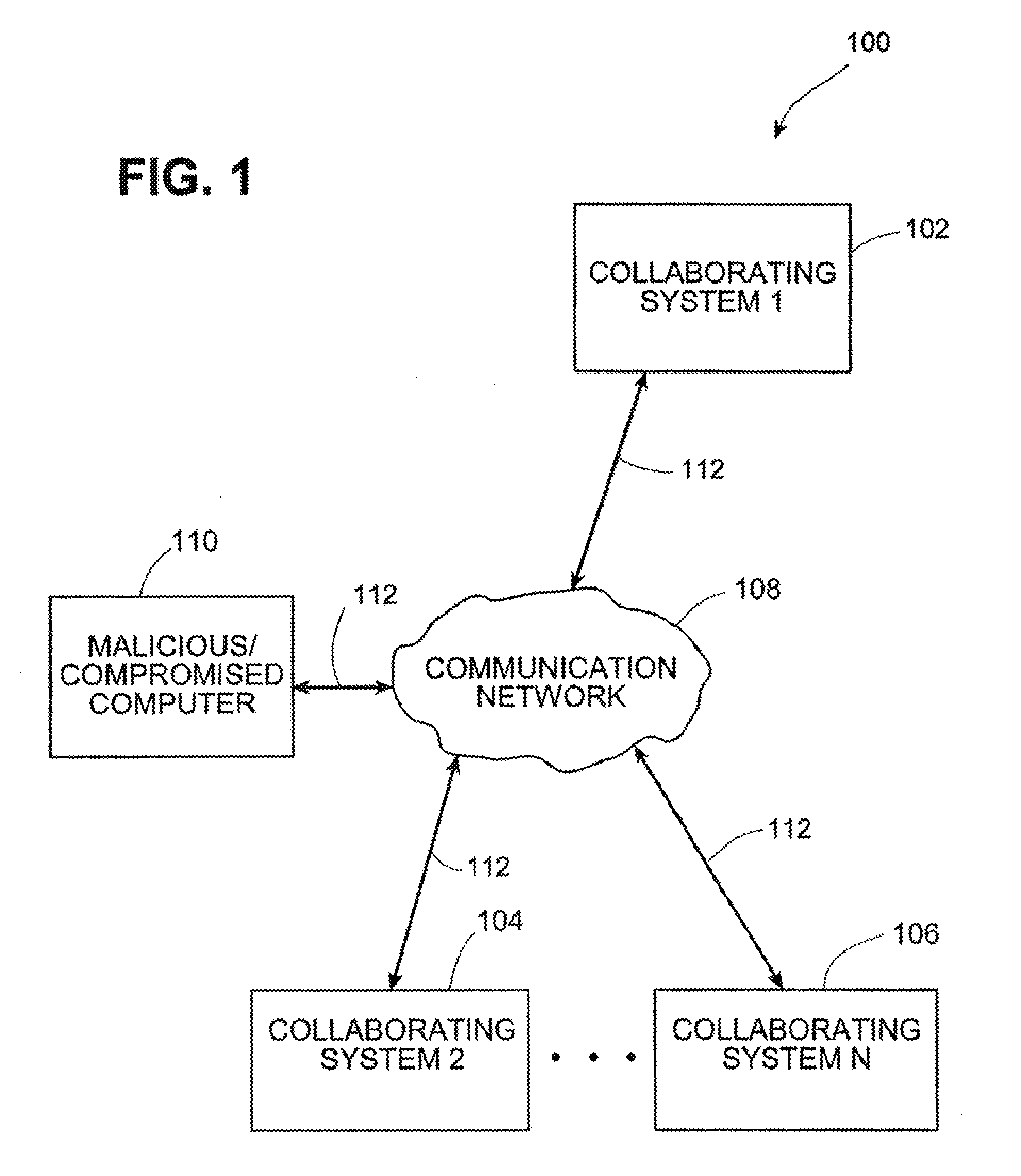
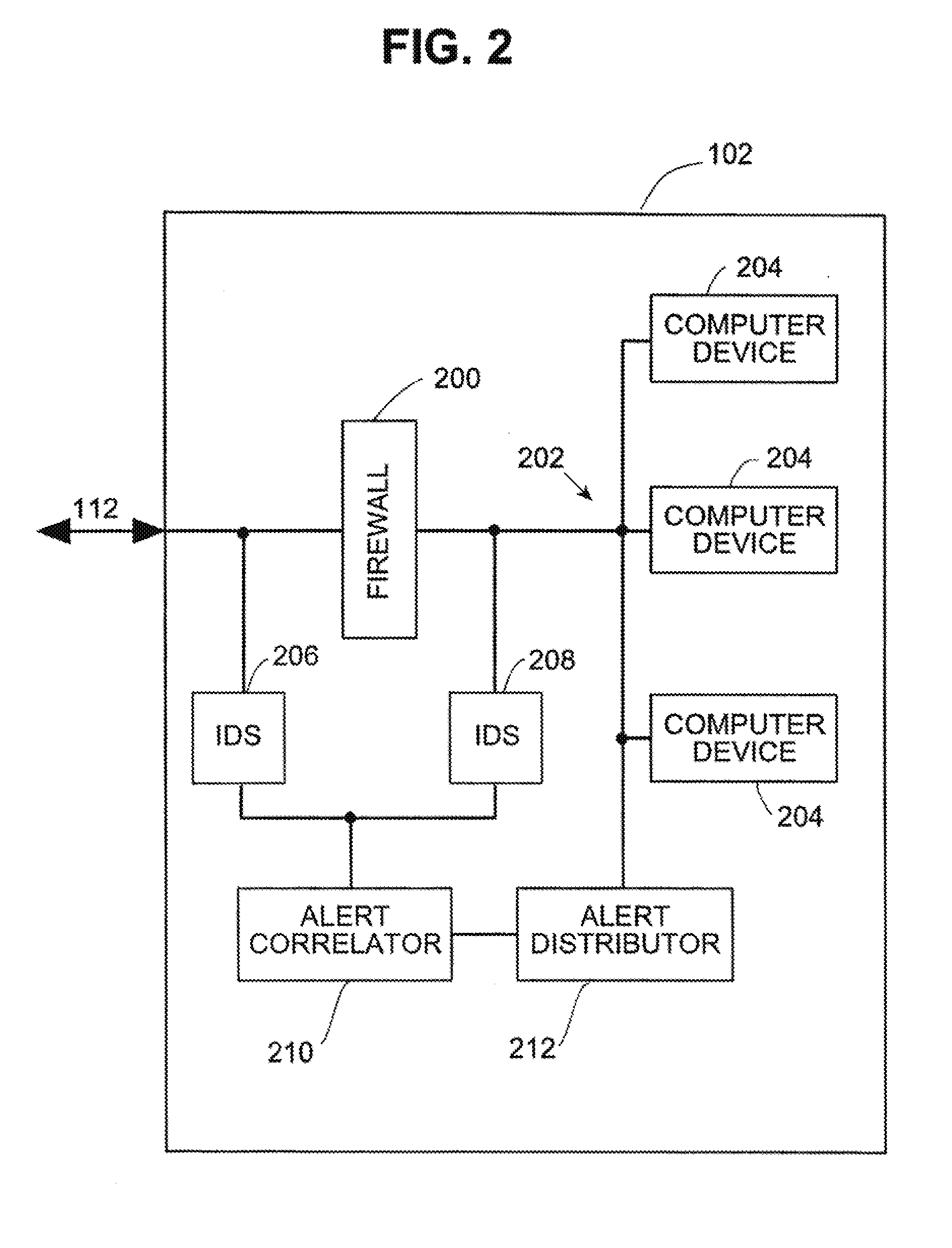
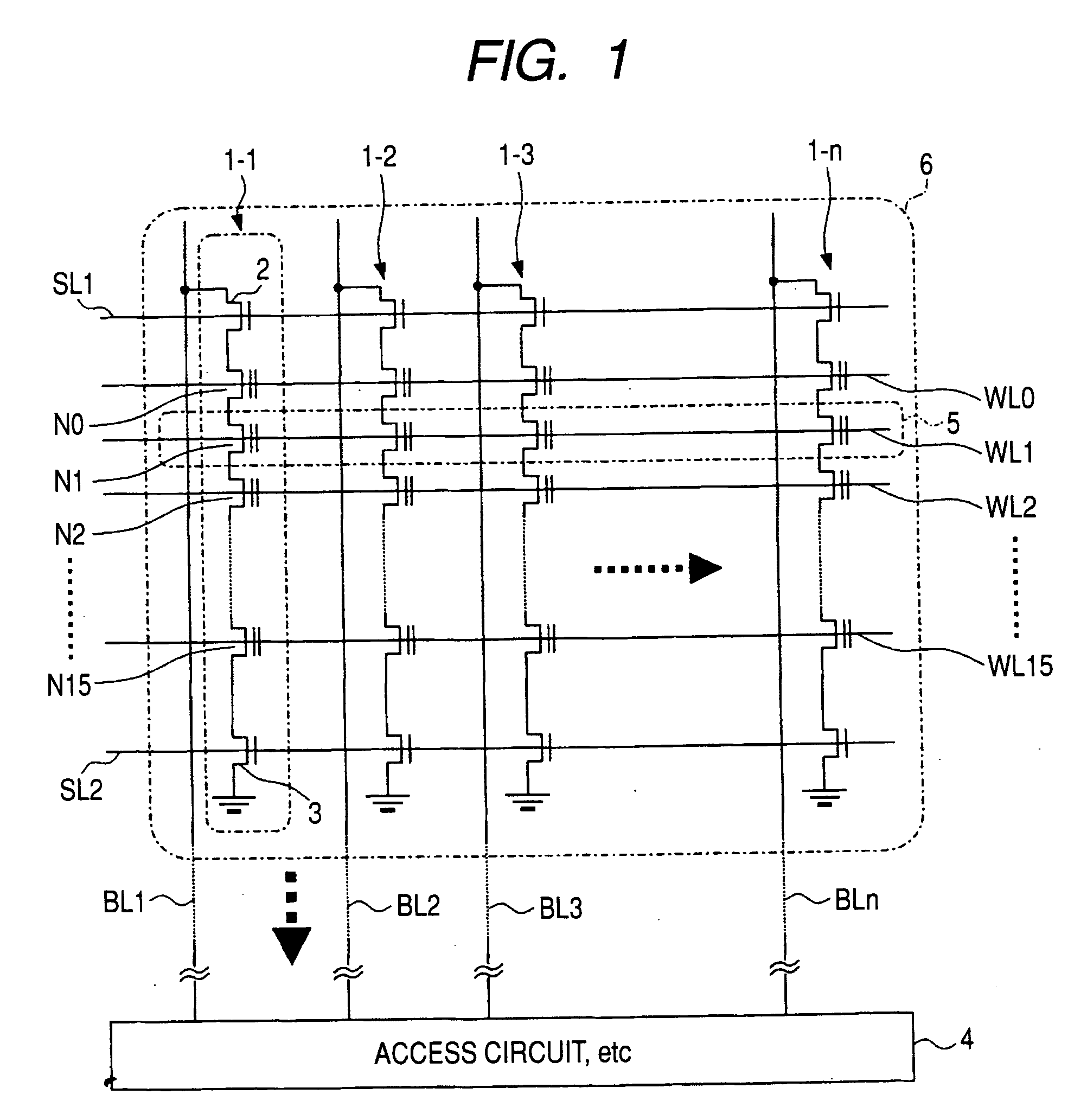
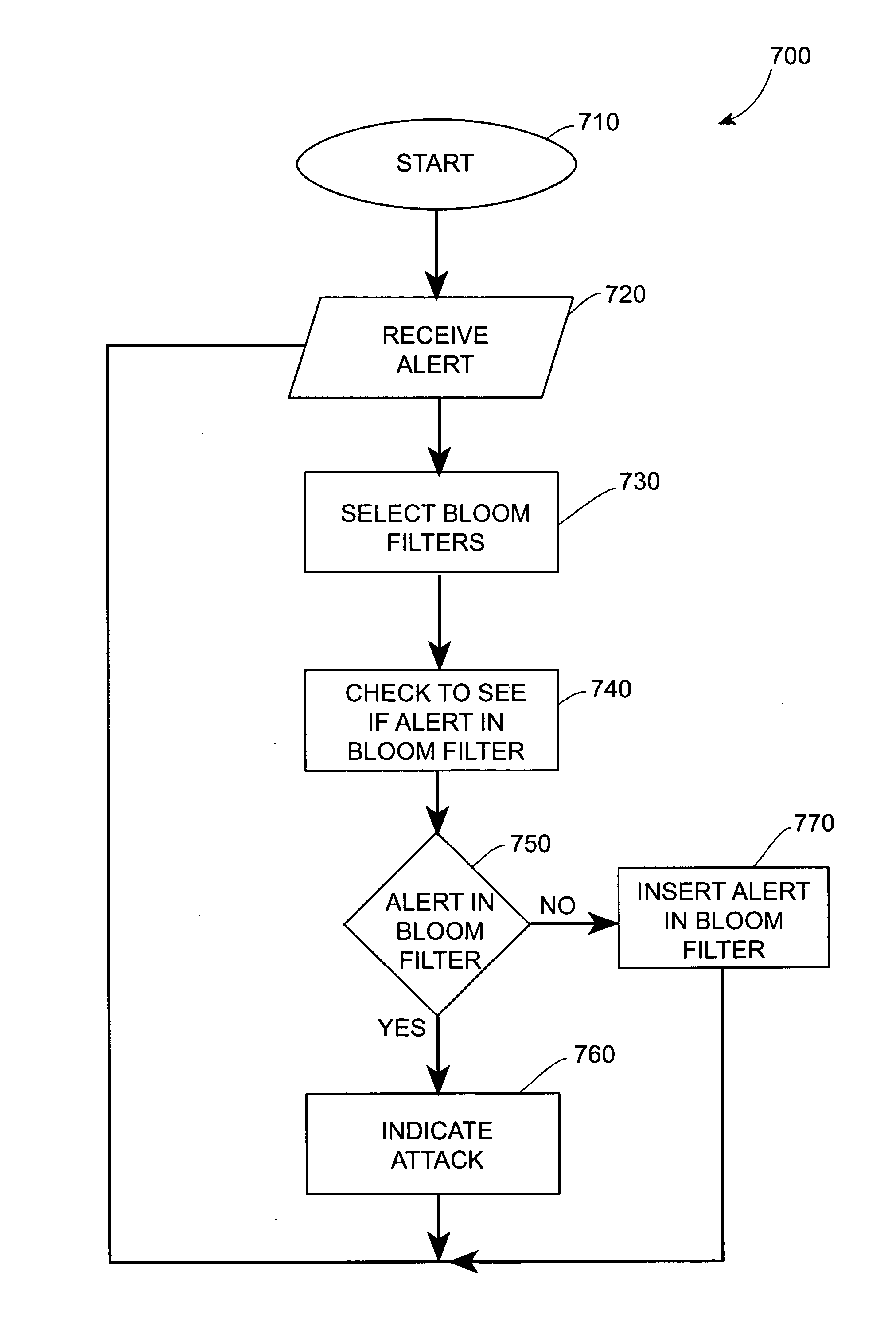
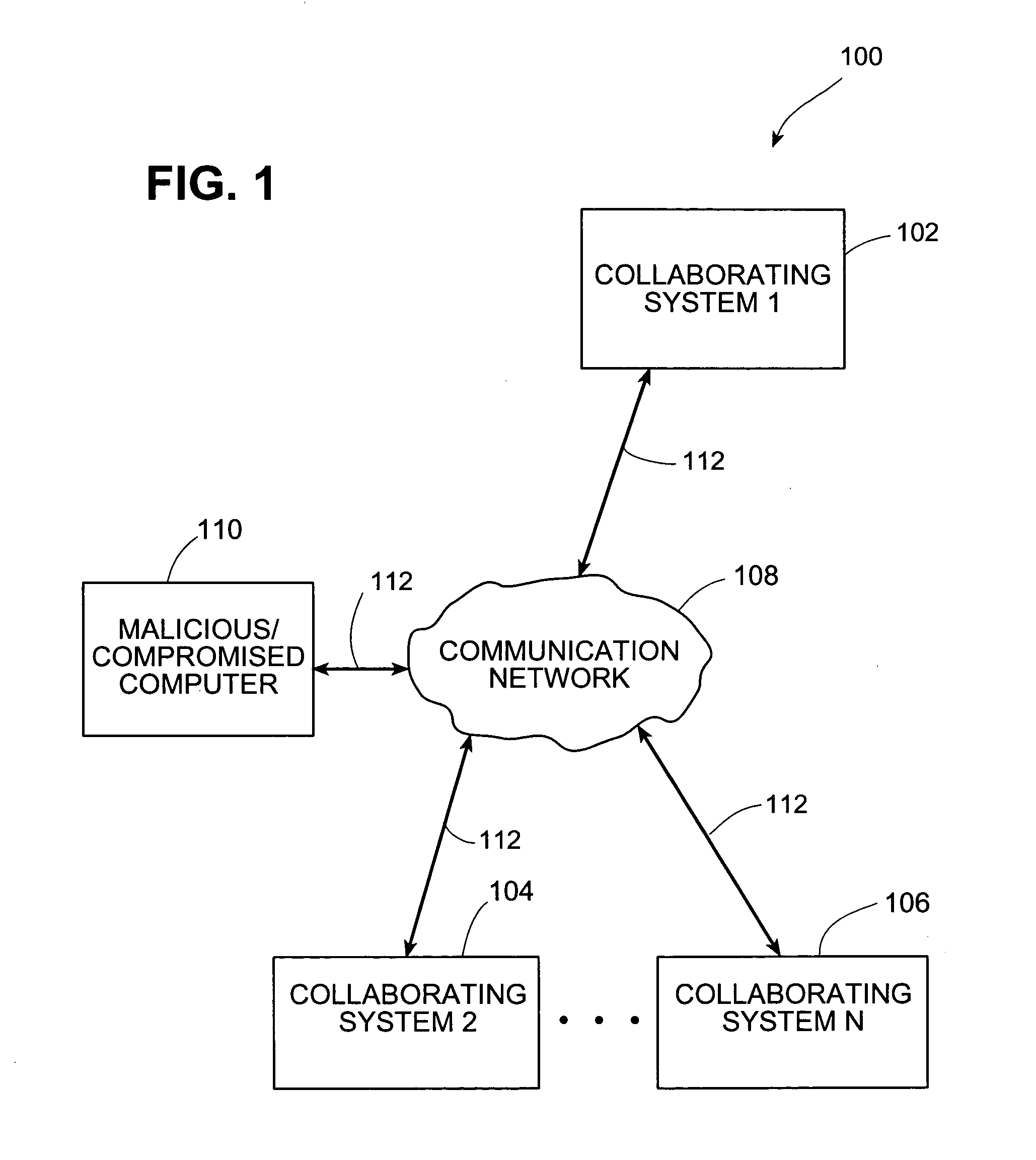
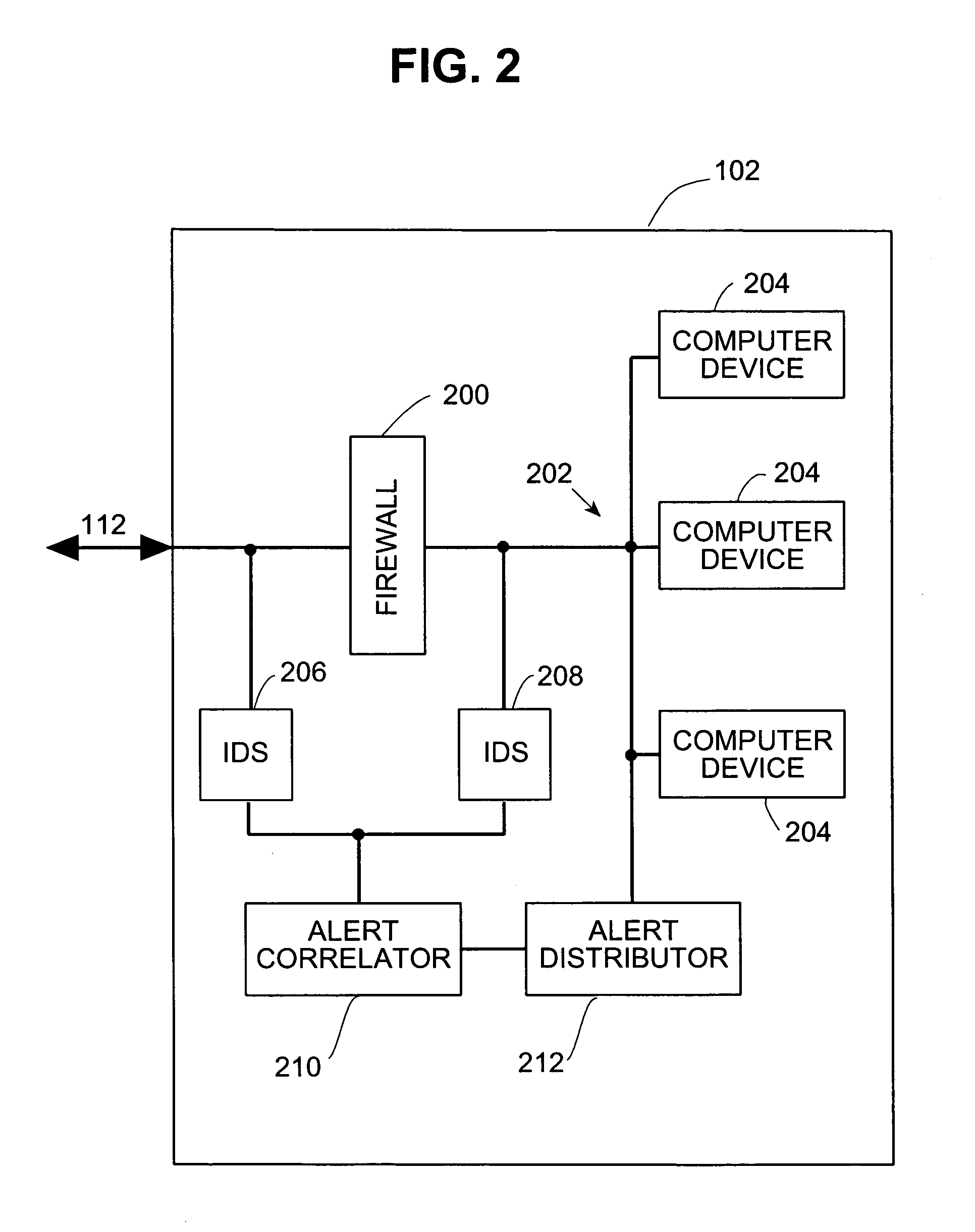
Systems and methods for correlating and distributing intrusion alert information among collaborating computer systems
ActiveUS7779463B2Technique is effectiveMemory loss protectionUser identity/authority verificationTraffic capacityEarly signs
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Systems and methods for correlating and distributing intrusion alert information among collaborating computer systems
ActiveUS7784097B1Technique is effectiveMemory loss protectionUnauthorized memory use protectionTraffic capacityCollaborative computing
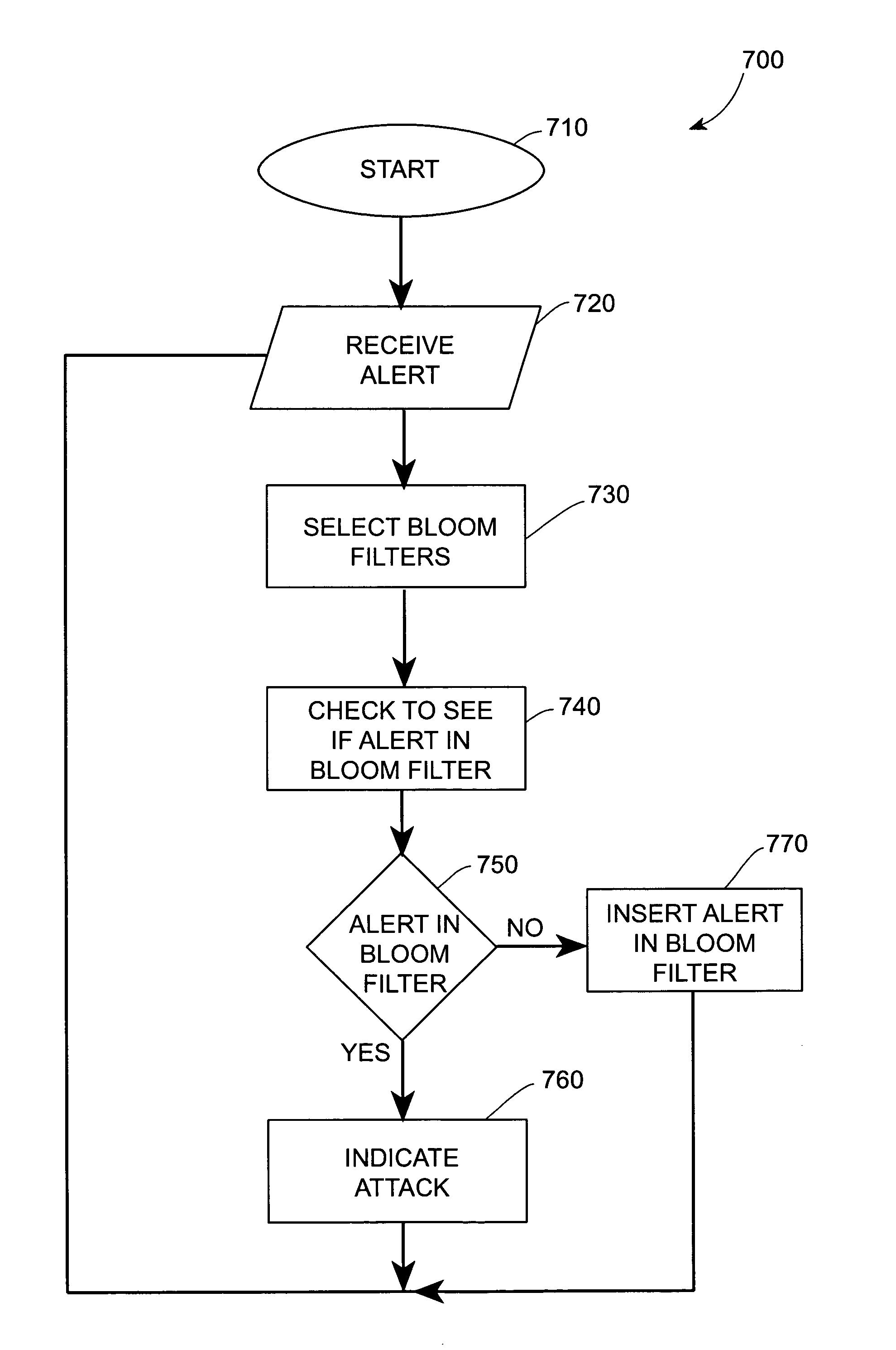
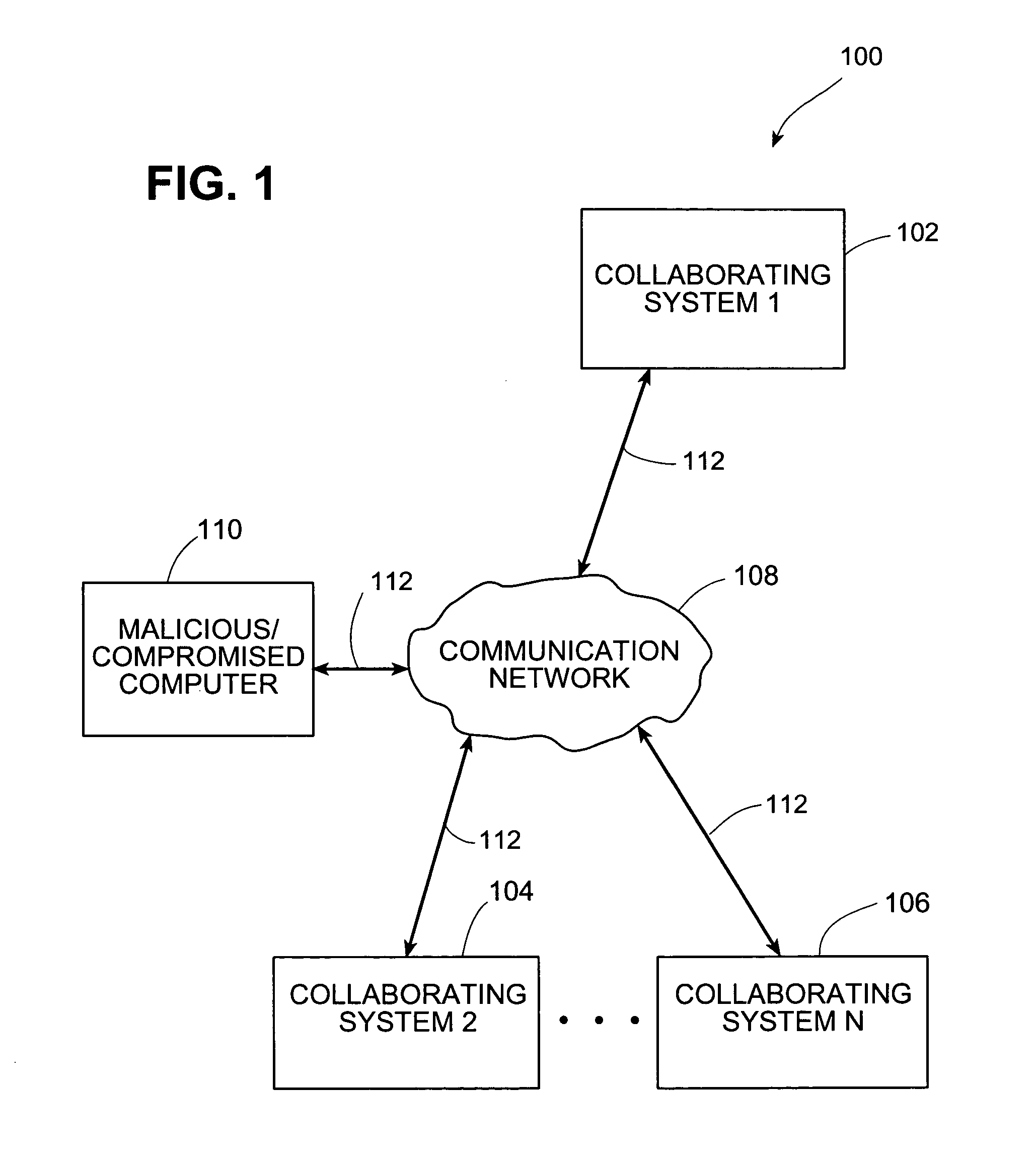
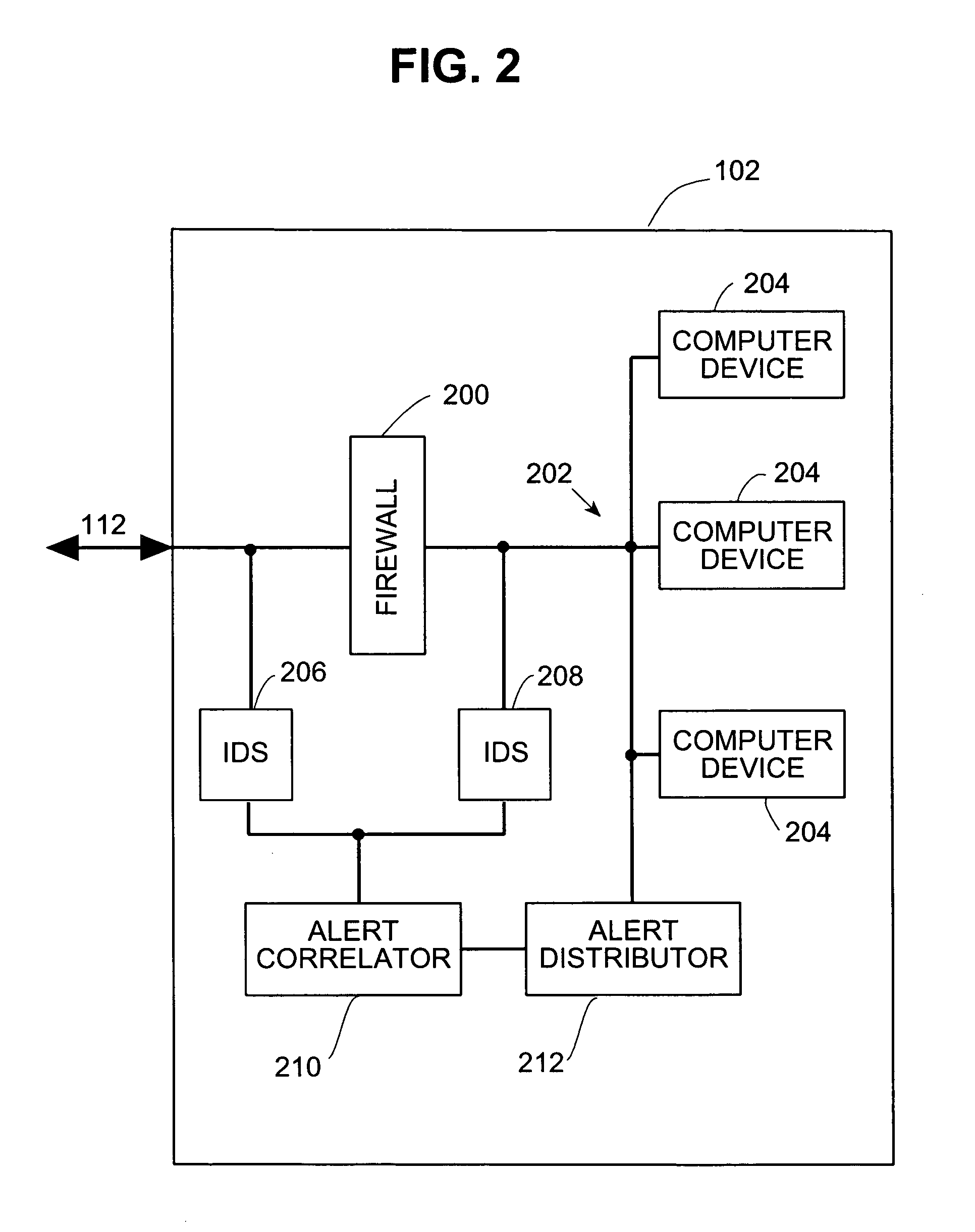
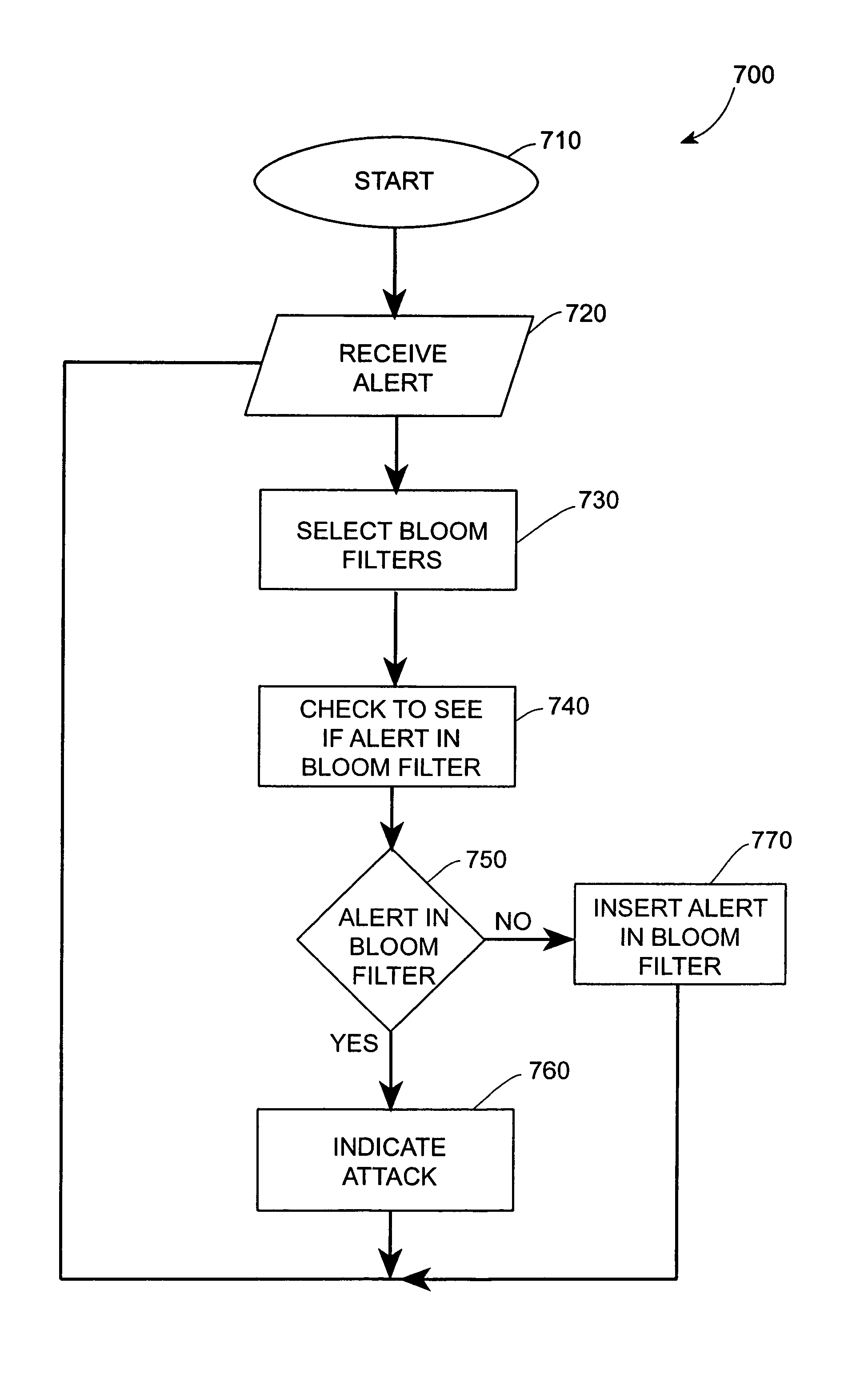
Systems and methods for correlating and distributing intrusion alert information among collaborating computer systems are provided. These systems and methods provide an alert correlator and an alert distributor that enable early signs of an attack to be detected and rapidly disseminated to collaborating systems. The alert correlator utilizes data structures to correlate alert detections and provide a mechanism through which threat information can be revealed to other collaborating systems. The alert distributor uses an efficient technique to group collaborating systems and then pass data between certain members of those groups according to a schedule. In this way data can be routinely distributed without generating excess traffic loads.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Systems and Methods for Correlating and Distributing Intrusion Alert Information Among Collaborating Computer Systems
ActiveUS20100281542A1Technique is effectiveMemory loss protectionError detection/correctionTraffic capacityCollaborative computing
Systems and methods provide an alert correlator and an alert distributor that enable early signs of an attack to be detected and rapidly disseminated to collaborating systems. The alert correlator utilizes data structures to correlate alert detections and provide a mechanism through which threat information can be revealed to other collaborating systems. The alert distributor uses an efficient technique to group collaborating systems and then pass data between certain members of those groups according to a schedule. In this way data can be routinely distributed without generating excess traffic loads.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
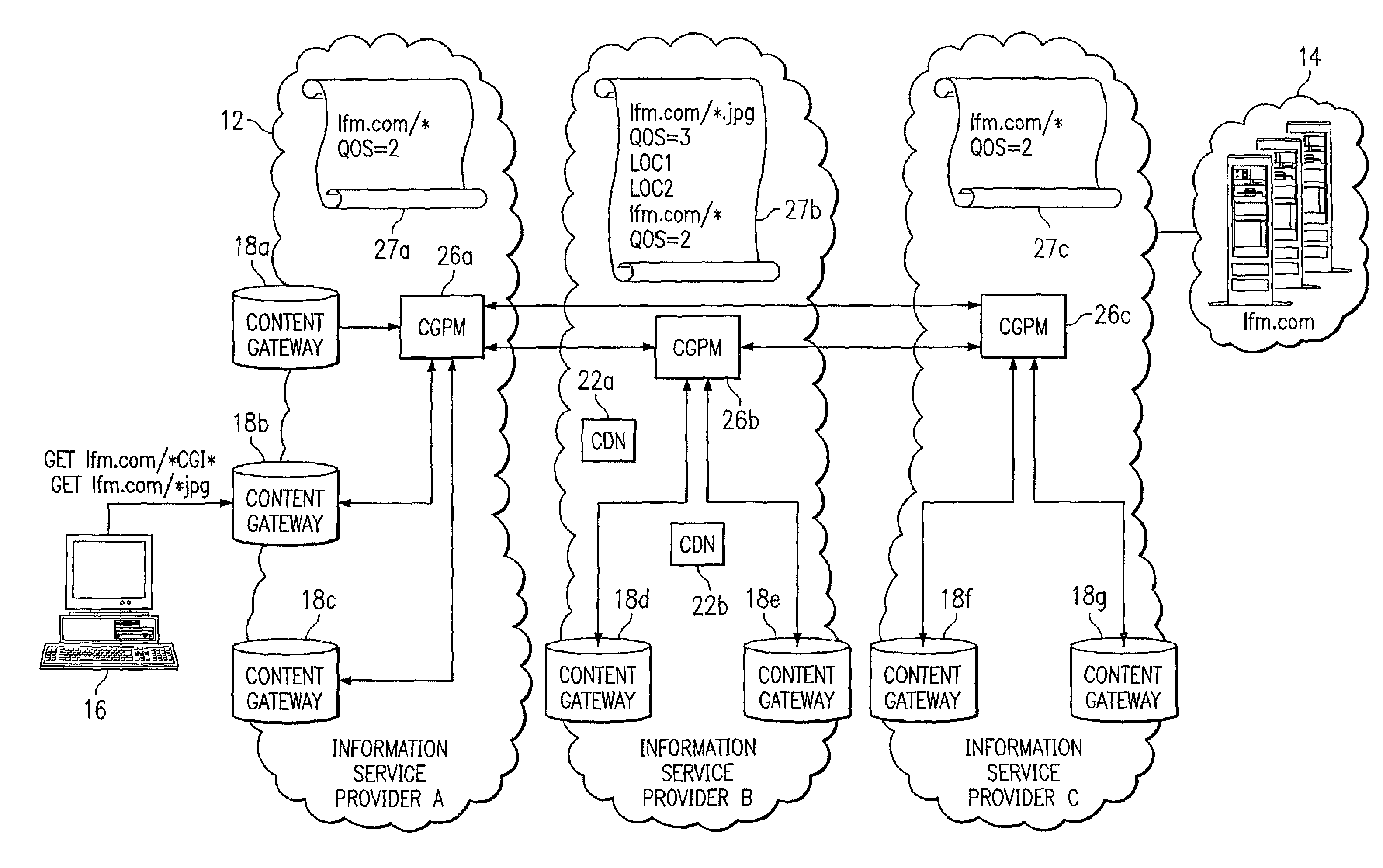
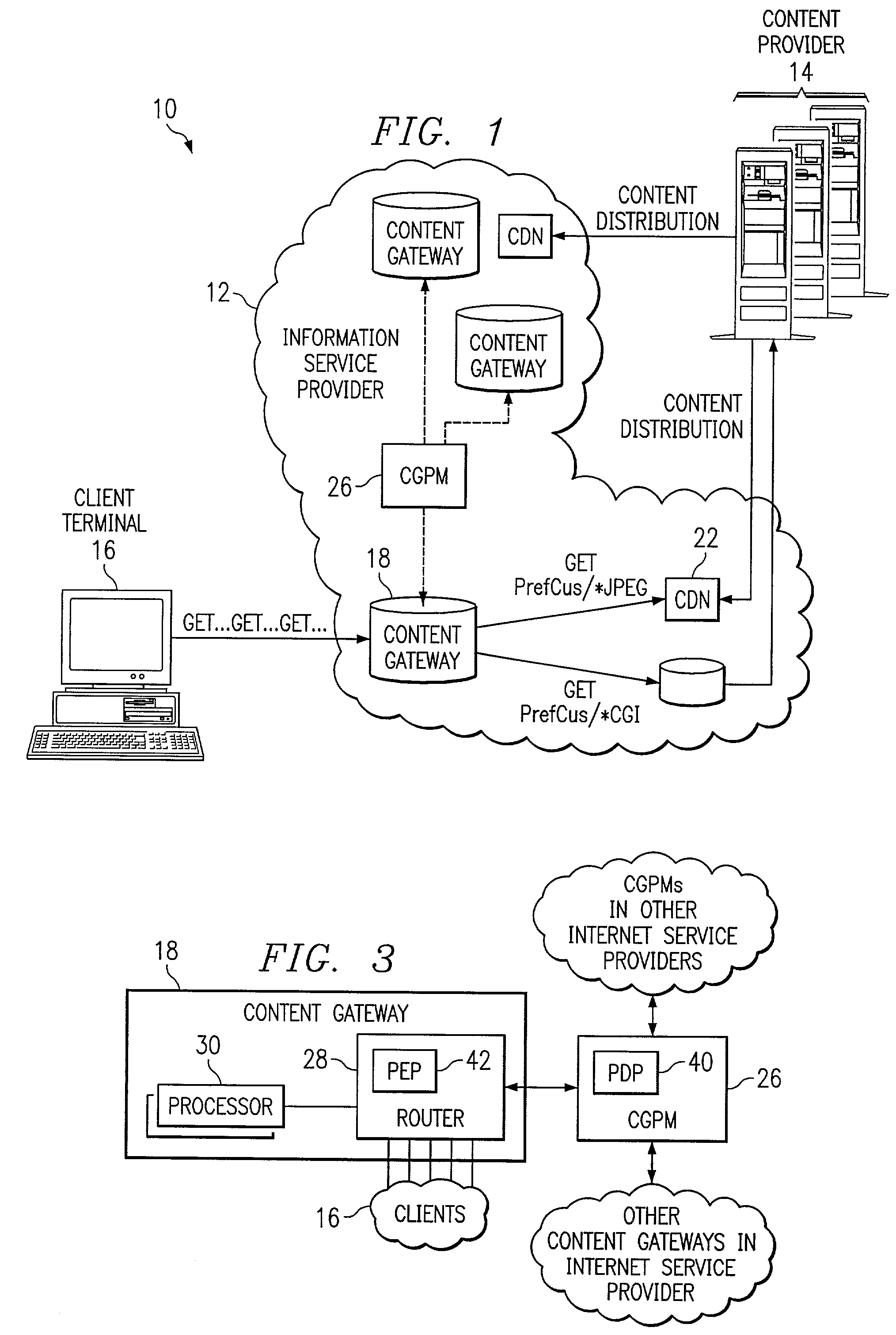
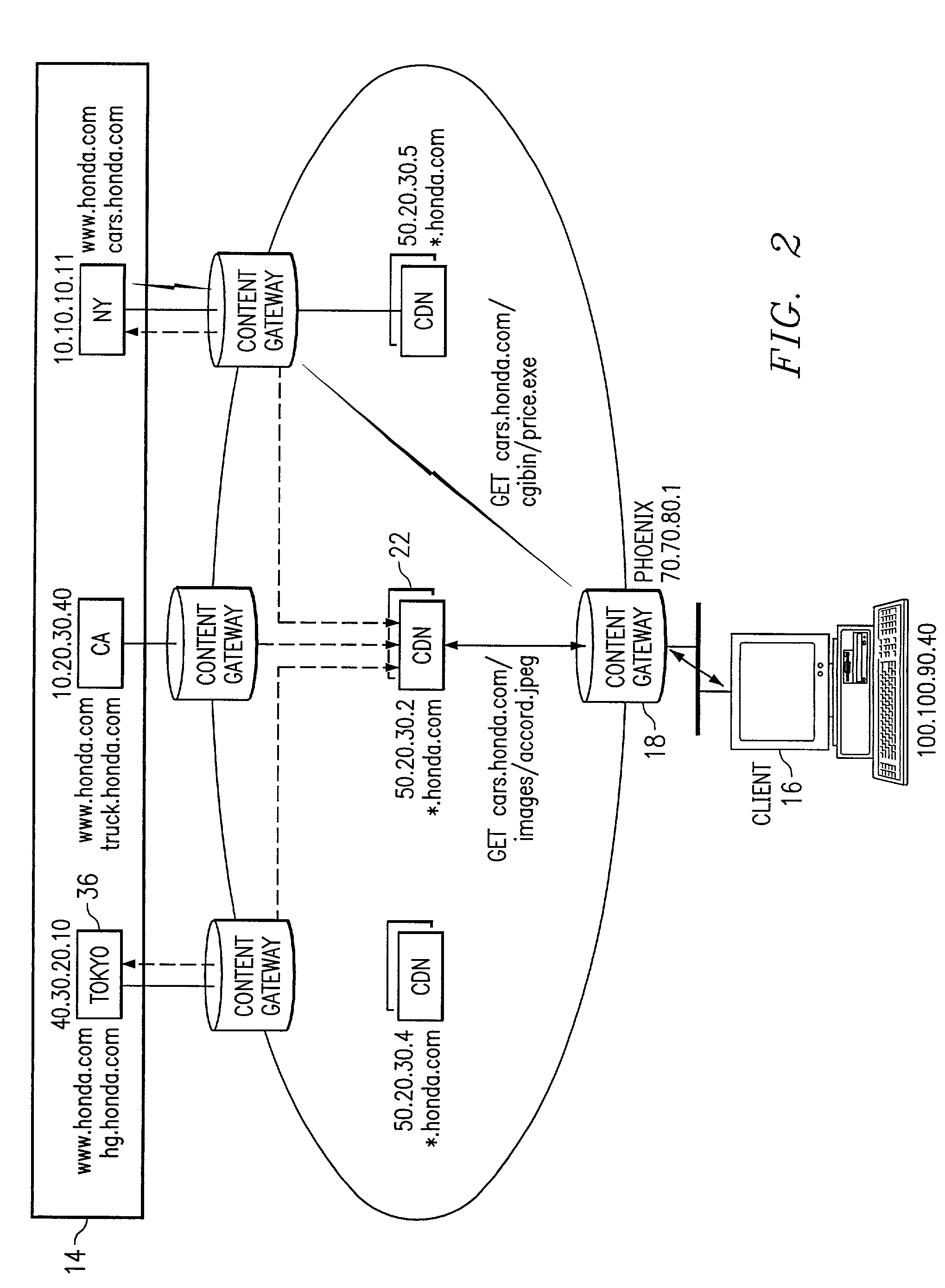
System and method for qualifying requests in a network
ActiveUS6968389B1Good serviceEliminate and greatly reduce disadvantageMultiple digital computer combinationsData switching networksDomain nameName server
An information service provider network includes a content gateway to process requests for information from a client terminal. The content gateway includes a router for receiving a domain name server query from an originator associated with a request for information. The router including a database defining a relationship between domain names and addresses associated with accelerated servicing of requests. The router determines whether the domain name of the domain name server query is indexed in the database. The domain name is qualified in response to the domain name being in the database. If qualified, the router sends an address to the originator of the query corresponding in the database to the domain name. The address is to a processor associated with the router that performs accelerated services on the request.
Owner:CISCO TECH INC
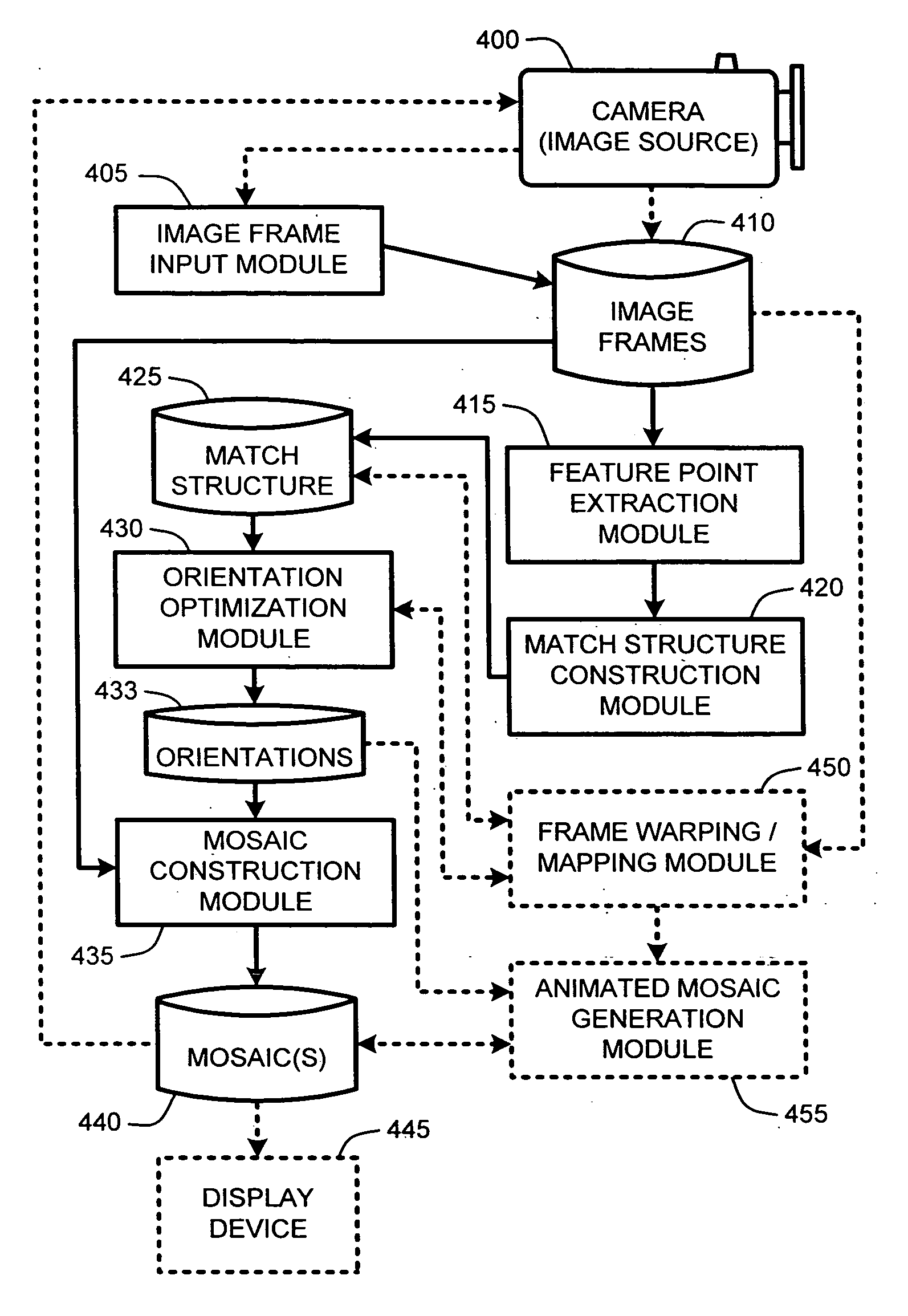
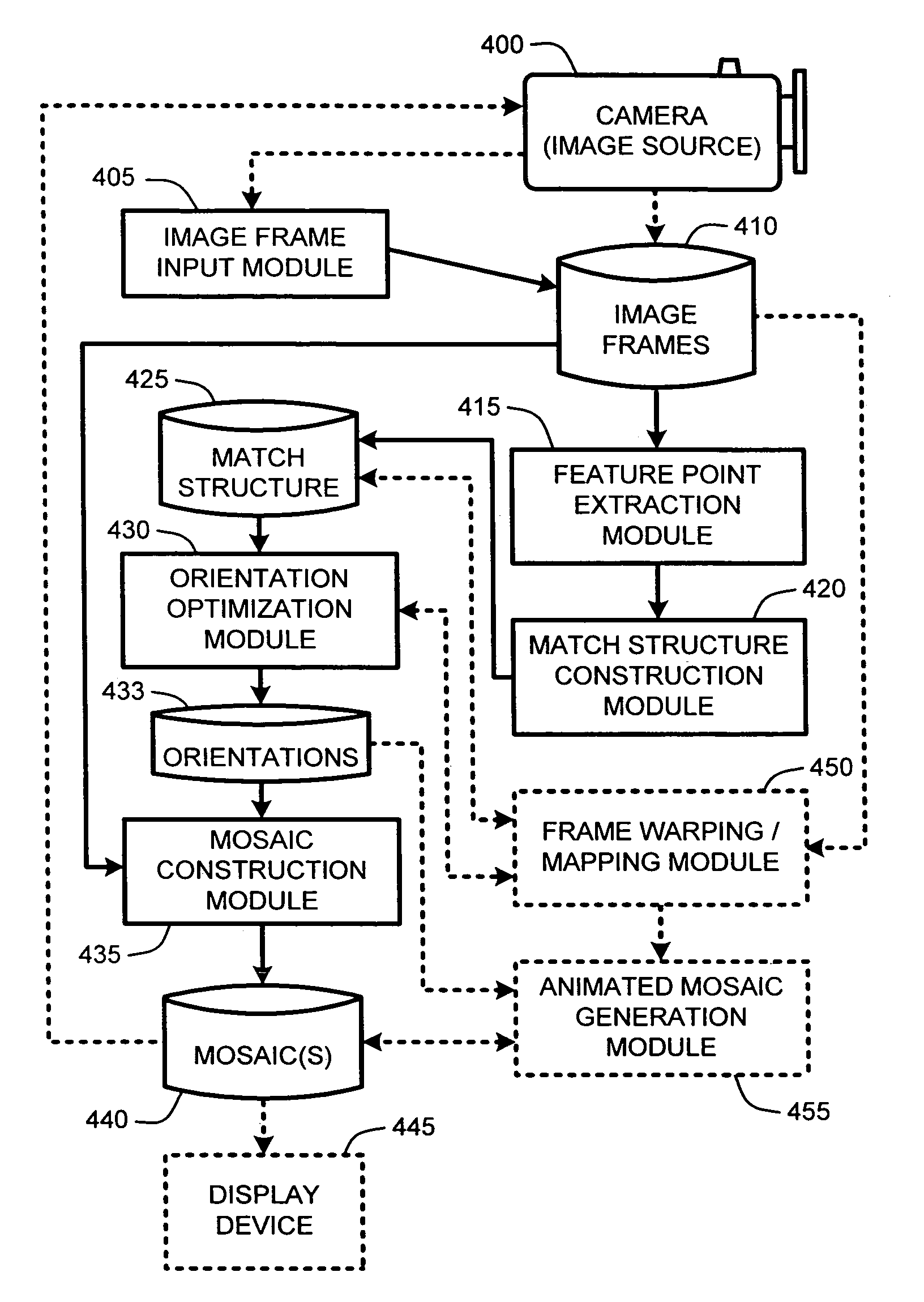
Video registration and image sequence stitching
ActiveUS20070031062A1Reduce computational complexityEasy constructionTelevision system detailsDigital data information retrievalIntermediate imageImage pair
A “Keyframe Stitcher” provides an efficient technique for building mosaic panoramic images by registering or aligning video frames to construct a mosaic panoramic representation. Matching of image pairs is performed by extracting feature points from every image frame and matching those points between image pairs. Further, the Keyframe Stitcher preserves accuracy of image stitching when matching image pairs by utilizing ordering information inherent in the video. The cost of searching for matches between image frames is reduced by identifying “keyframes” based on computed image-to-image overlap. Keyframes are then matched to all other keyframes, but intermediate image frames are only matched to temporally neighboring keyframes and neighboring intermediate frames to construct a “match structure.” Image orientations are then estimated from this match structure and used to construct the mosaic. Matches between image pairs may be compressed to reduce computational overhead by replacing groups of feature points with representative measurements.
Owner:MICROSOFT TECH LICENSING LLC
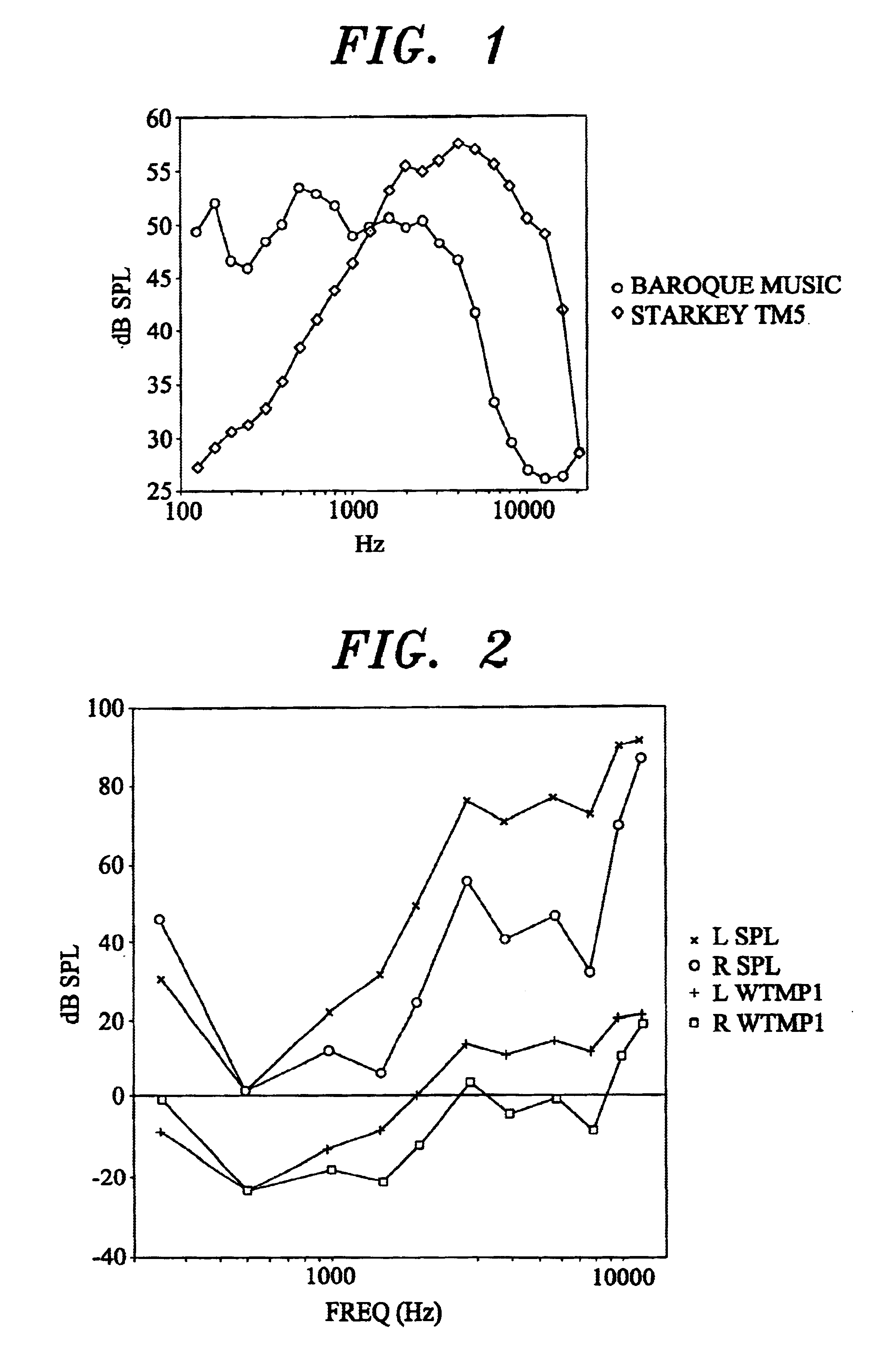
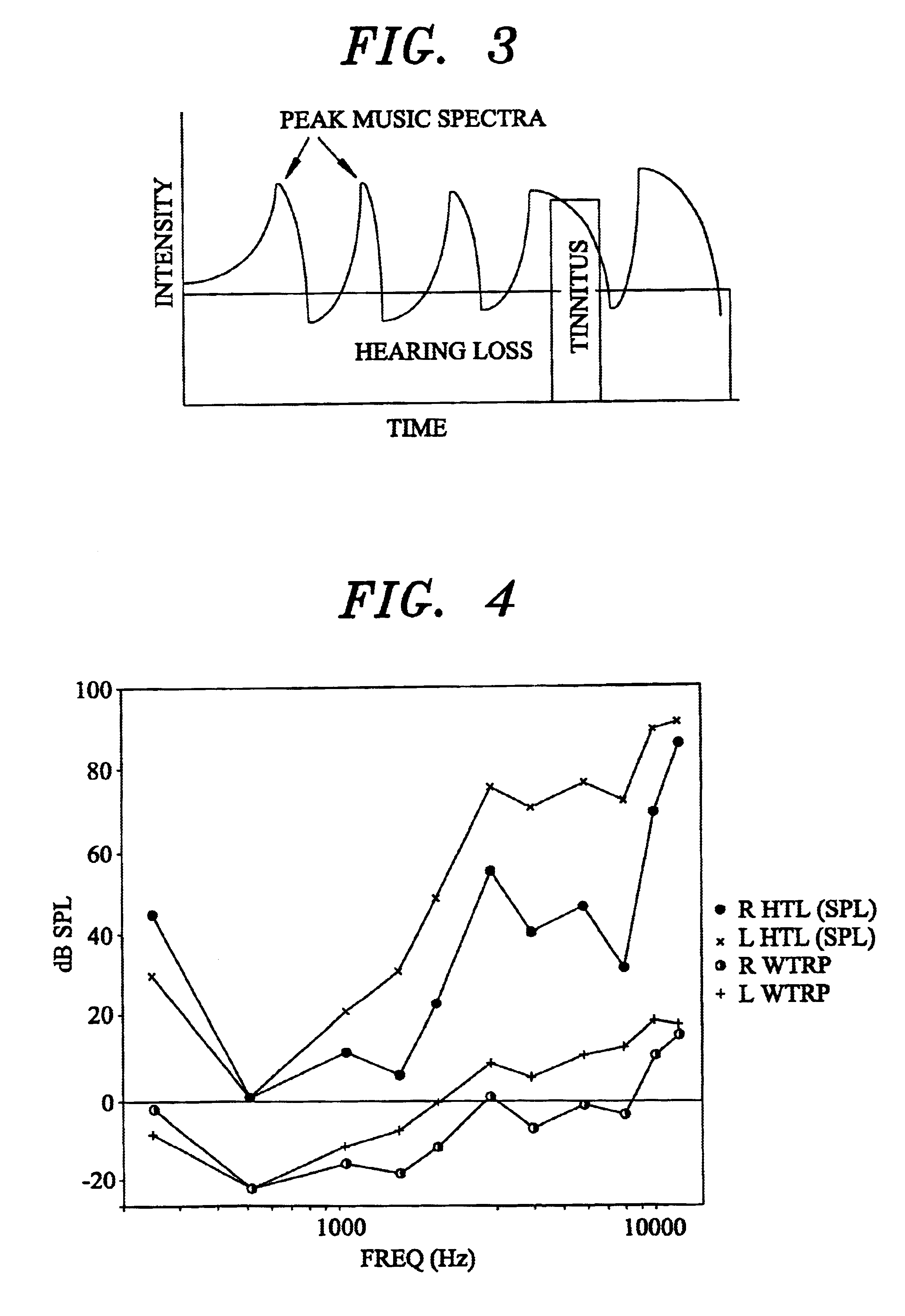
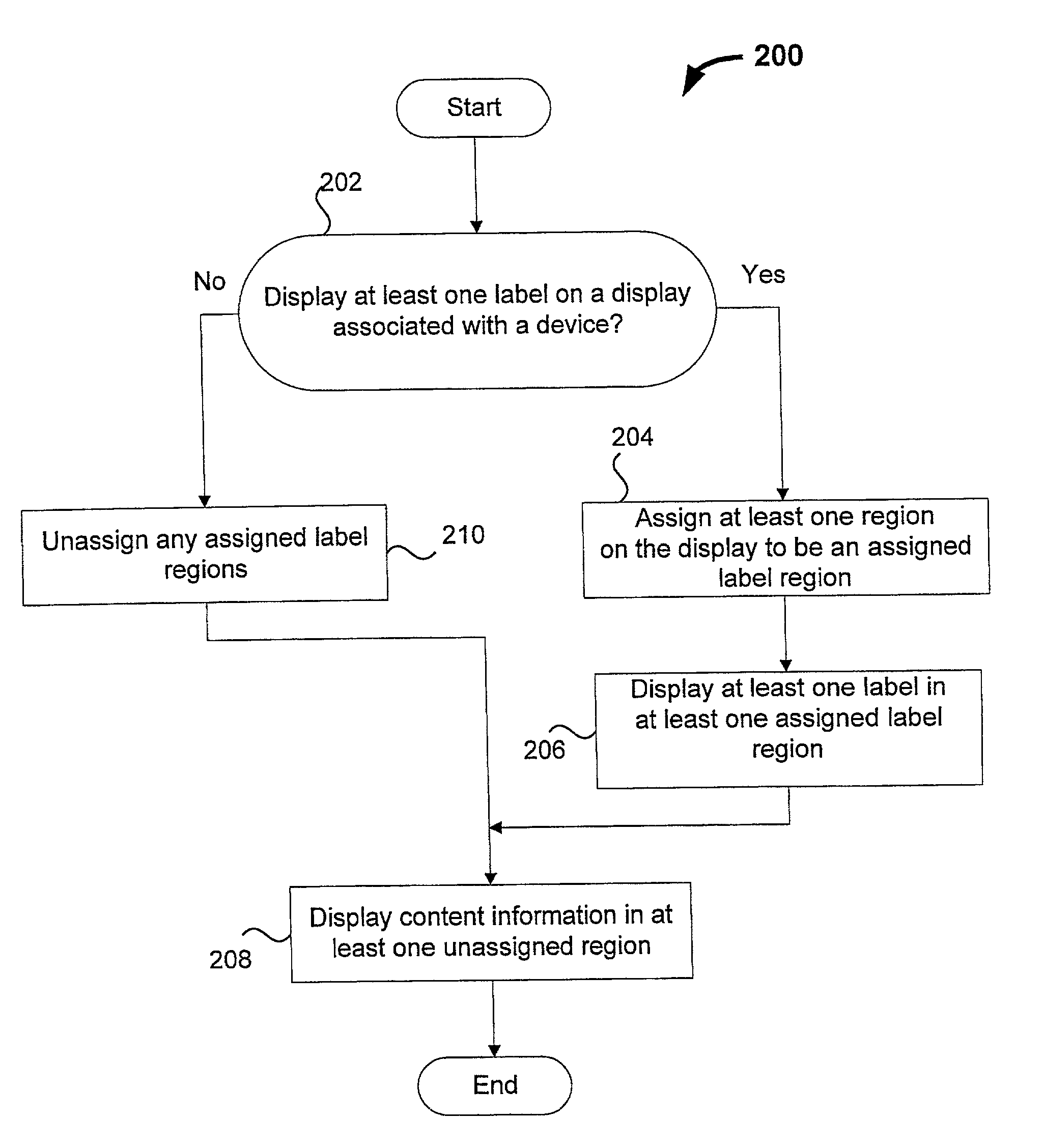
Tinnitus rehabilitation device and method
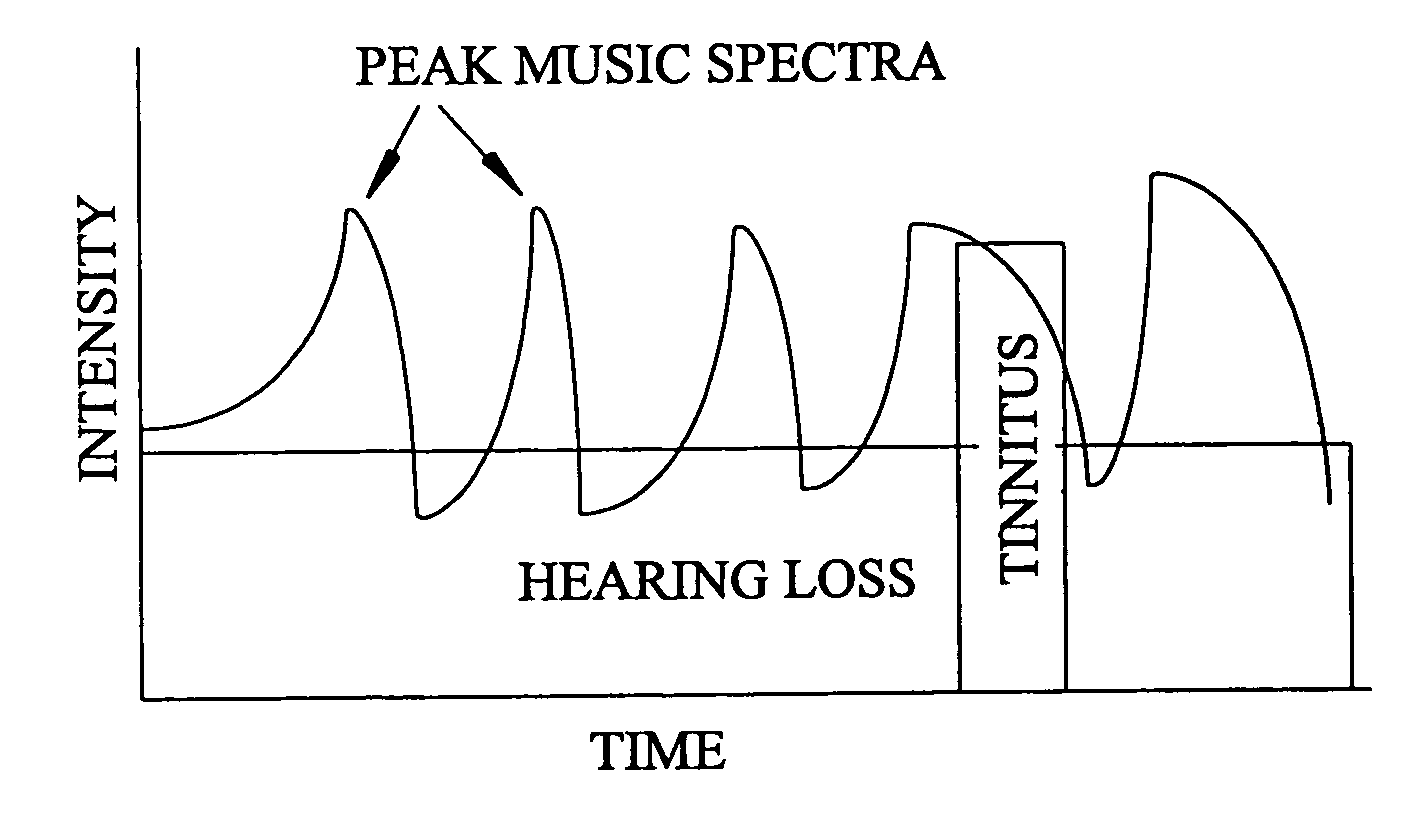
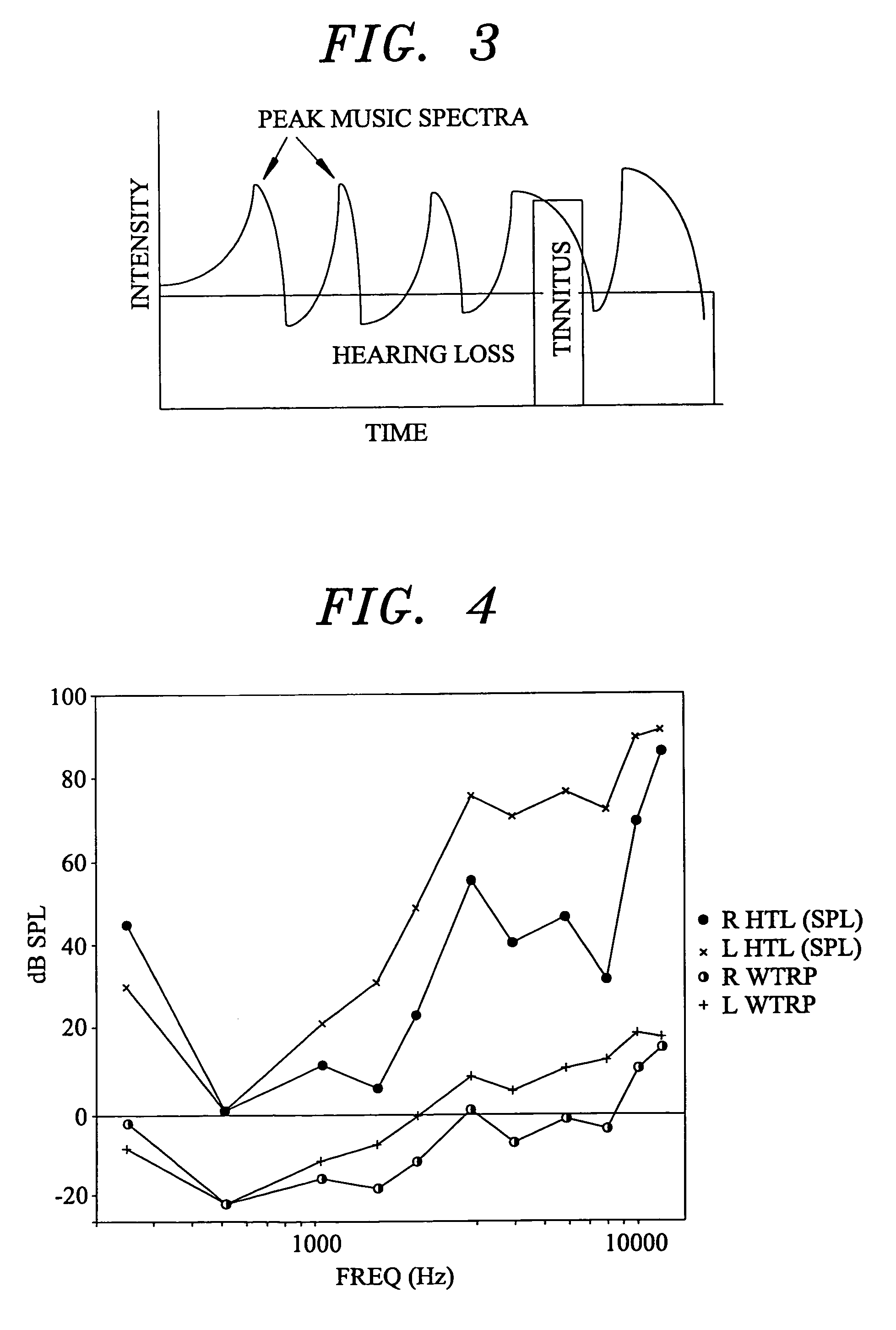
InactiveUS6682472B1Technique is effectiveEar treatmentElectric tinnitus maskersFrequency spectrumHabituation
A tinnitus method and device for providing relief to a person suffering from the disturbing effects of tinnitus is described. The method can be implemented entirely in software to spectrally modify an audio signal in accordance with a predetermined masking algorithm which modifies the intensity of the audio signal at selected frequencies. A predetermined masking algorithm is described which provides intermittent masking of the tinnitus wherein, at a comfortable listening level, during peaks of the audio signal the tinnitus is completely obscured, whereas during troughs the perception of the tinnitus occasionally emerges. In practice it has been found that such intermittent masking provides an immediate sense of relief, control and relaxation for the person, whilst enabling sufficient perception of the tinnitus for habituation and long term treatment to occur. Advantageously the predetermined masking algorithm is specifically tailored to the audiometric configuration of the person. For example, the masking algorithm may be partly tailored to the hearing loss characteristic of the person. A tinnitus rehabilitation device used in conjunction with a personal sound reproducing system is also described.
Owner:NEUROMONICS
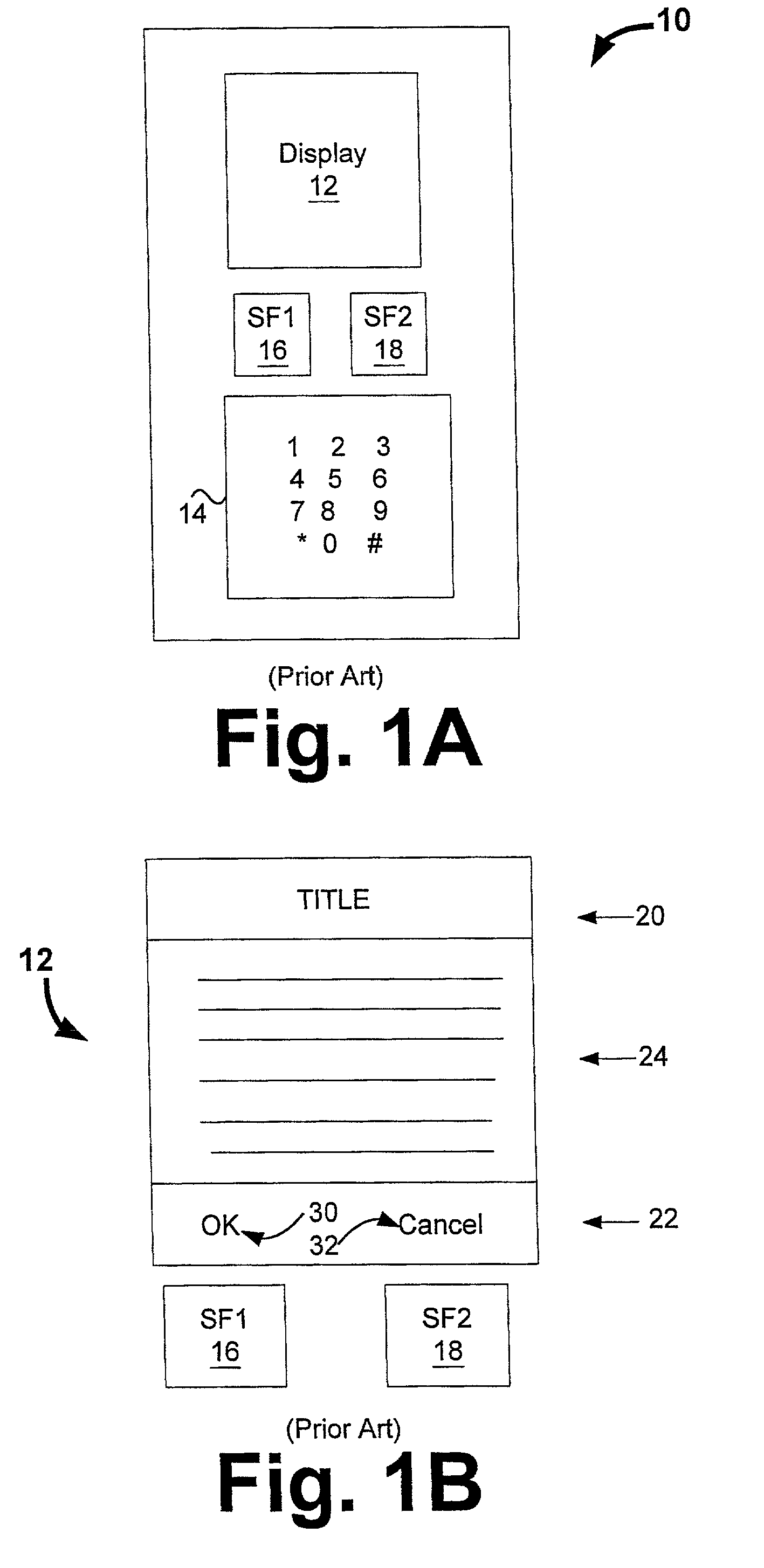
Dynamic display for communication devices
ActiveUS7020849B1Increase suitMore display areaCathode-ray tube indicatorsDigital output to display deviceDisplay deviceCommunication device
Techniques for displaying information on communication devices are disclosed. The techniques are highly beneficial for devices with relatively small viewing areas (e.g., remote wireless phones). An enhanced communication device can be implemented which can dynamically display information on an associated display. This means that there is no need to reserve various areas on the display for displaying. Instead, information may be assigned or unassigned to the different display portions dynamically. As a result, the display area can be used more efficiently.
Owner:GOOGLE LLC
Method for automatic detection and tracking of multiple targets with multiple cameras and system therefor
ActiveUS20100166260A1The result is stable and accurateEfficient integrationCharacter and pattern recognitionClosed circuit television systemsMarkov chainMulti camera
A method for automatically detecting and tracking multiple targets in a multi-camera surveillance zone and system thereof. In each camera view of the system only a simple object detection algorithm is needed. The detection results from multiple cameras are fused into a posterior distribution, named TDP, based on the Bayesian rule. This TDP distribution represents a likelihood of presence of some moving targets on the ground plane. To properly handle the tracking of multiple moving targets with time, a sample-based framework which combines Markov Chain Monte carlo (MCMC), Sequential Monte Carlo (SMC), and Mean-Shift Clustering, is provided. The detection and tracking accuracy is evaluated by both synthesized videos and real videos. The experimental results show that this method and system can accurately track a varying number of targets.
Owner:NAT CHIAO TUNG UNIV
Tinnitus rehabilitation device and method
InactiveUS20040131200A1Technique is effectiveElectric tinnitus maskersEar treatmentFrequency spectrumHabituation
A tinnitus method and device for providing relief to a person suffering from the disturbing effects of tinnitus is described. The method can be implemented entirely in software to spectrally modify an audio signal in accordance with a predetermined masking algorithm which modifies the intensity of the audio signal at selected frequencies. A predetermined masking algorithm is described which provides intermittent masking of the tinnitus wherein, at a comfortable listening level, during peaks of the audio signal the tinnitus is completely obscured, whereas during troughs the perception of the tinnitus occasionally emerges. In practice it has been found that such intermittent masking provides an immediate sense of relief, control and relaxation for the person, whilst enabling sufficient perception of the tinnitus for habituation and long term treatment to occur. Advantageously the predetermined masking algorithm is specifically tailored to the audiometric configuration of the person. For example, the masking algorithm may be partly tailored to the hearing loss characteristic of the person. A tinnitus rehabilitation device used in conjunction with a personal sound reproducing system is also described.
Owner:NEUROMONICS
Method and apparatus for grammatical packet classifier
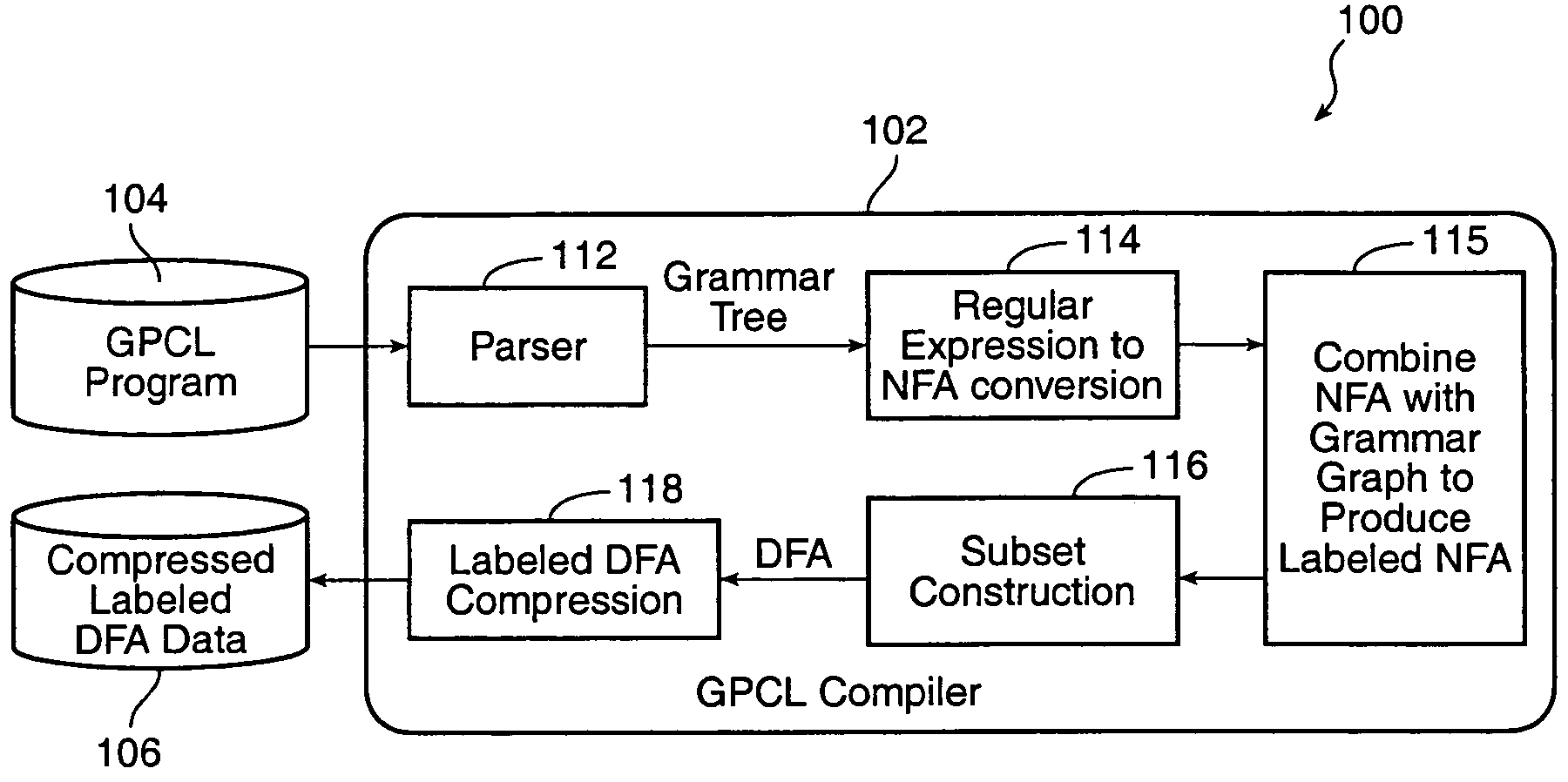
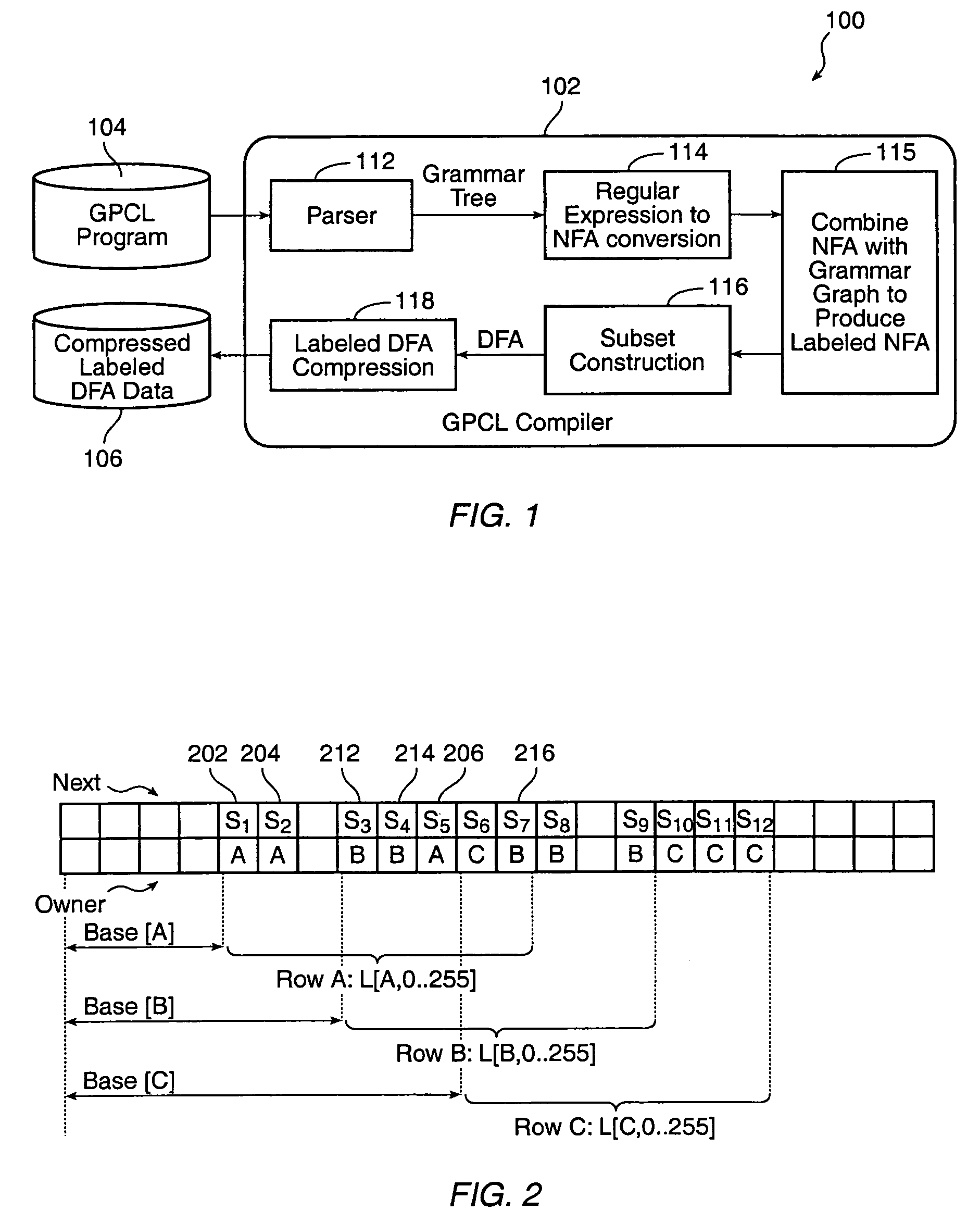
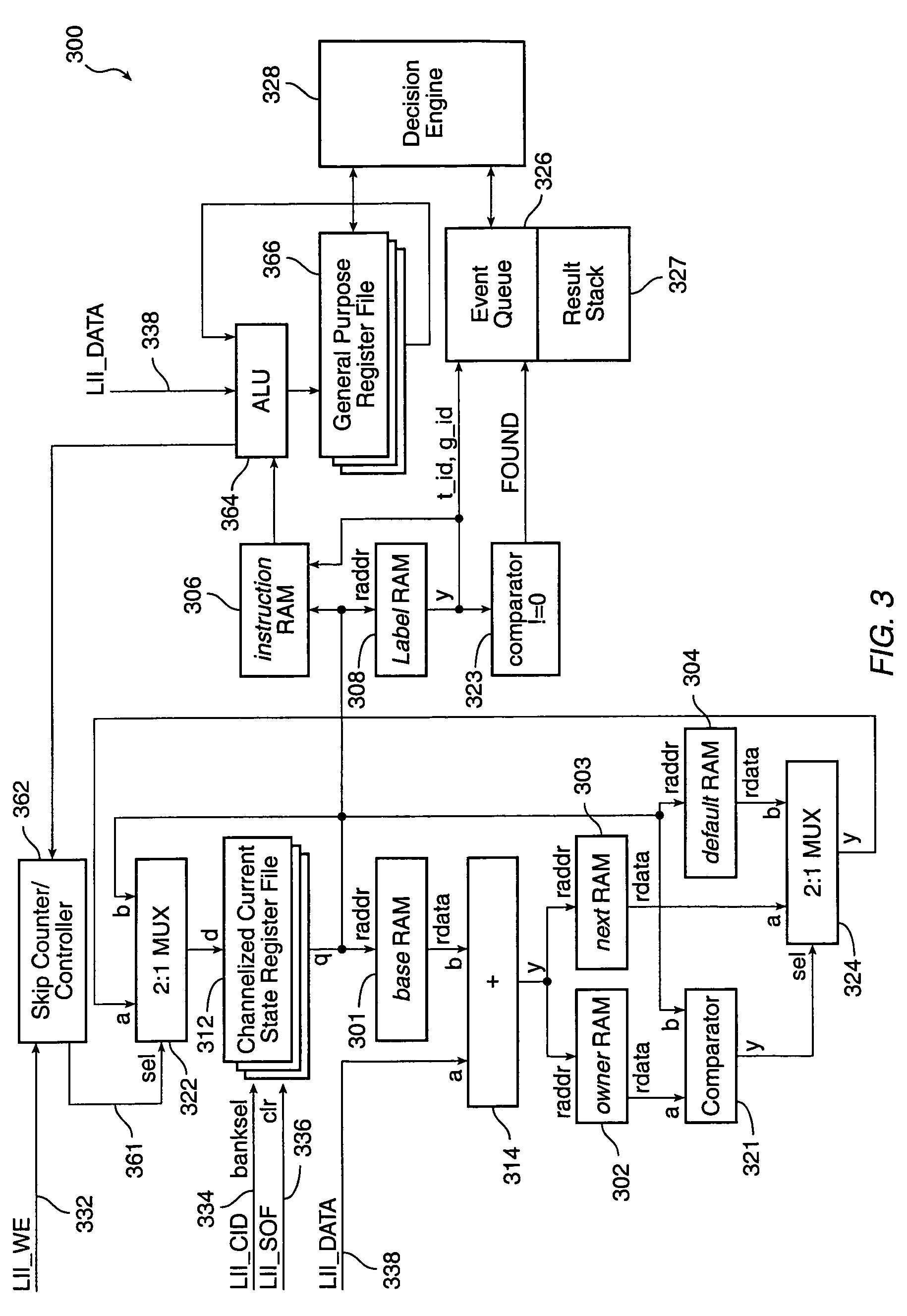
InactiveUS7188168B1Simple definitionAvoid explosionMultiple digital computer combinationsTransmissionRegular expressionComputer science
A packet classification language (GPCL) is provided to specify protocol hierarchies among data packets in a routing device. The GPCL uses regular expressions to match incoming data packets and a syntax to describe the protocol hierarchy. A GPCL compiler produces an enhanced DFA which incorporates the regular expression for recognizing constituent parts of a data packets and which incorporates the grammar graph defining the relationships among the constituent parts. A hardware implemented DFA is used to scan the input stream which constitutes the data packets.
Owner:PMC-SIERRA
Product authentication
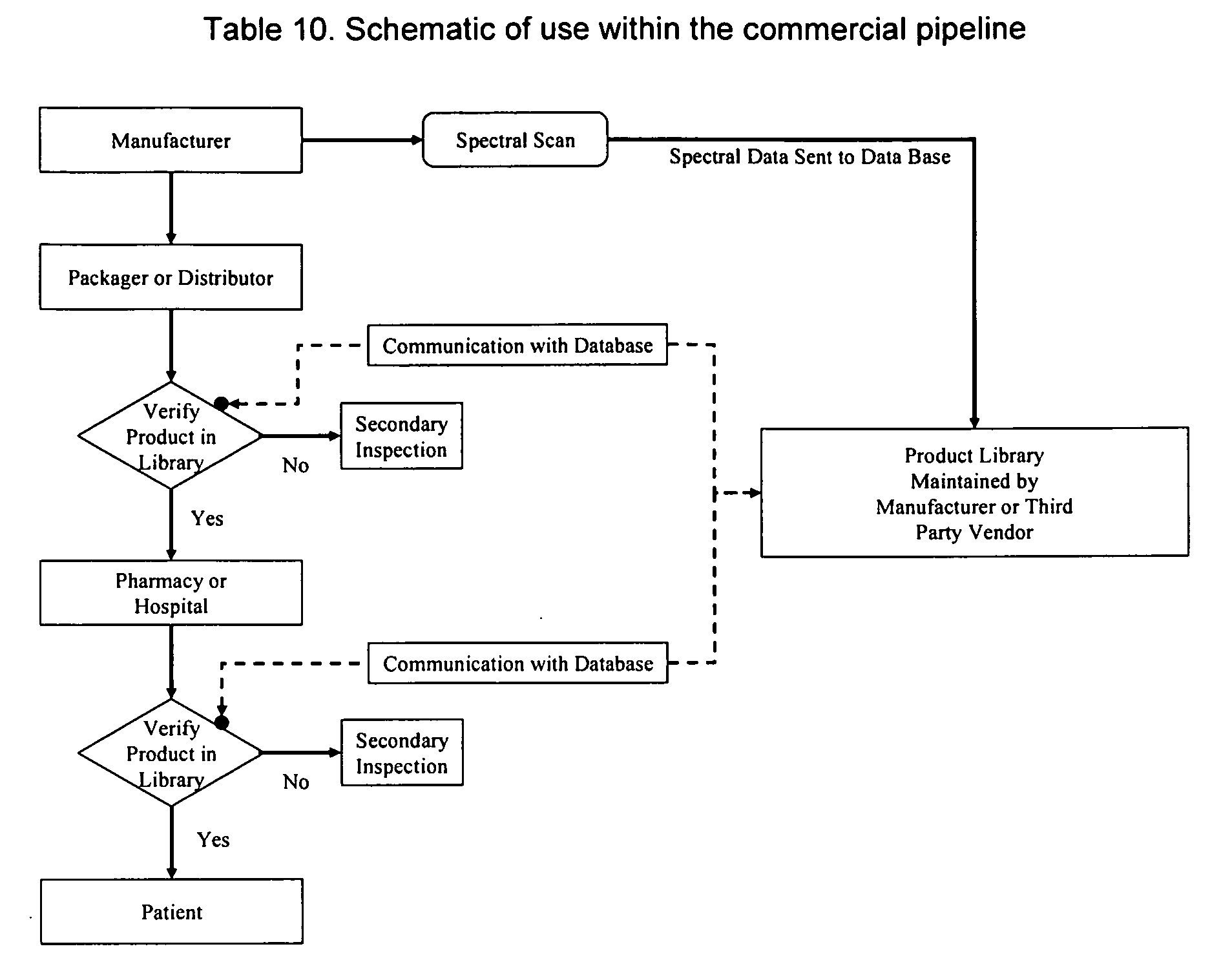
InactiveUS20060283931A1Rapid accurate approachPrevent the pharmaceutical product from being counterfeitedStampsRaman scatteringEngineeringErrors and residuals
A method is disclosed to verify and identify products through their product signatures in order to combat counterfeiting and reduce dispensing errors, using methods such as spectral analysis (e.g., near infrared spectroscopy). Furthermore, in order to actively evade product counterfeiting, a method is disclosed where an amount of one or more components of the product are varied (e.g., over time); the variation provides a different product signature, but falling within a desirable or necessary range.
Owner:UNIV OF MARYLAND
Storage device, computer system, and storage device access method
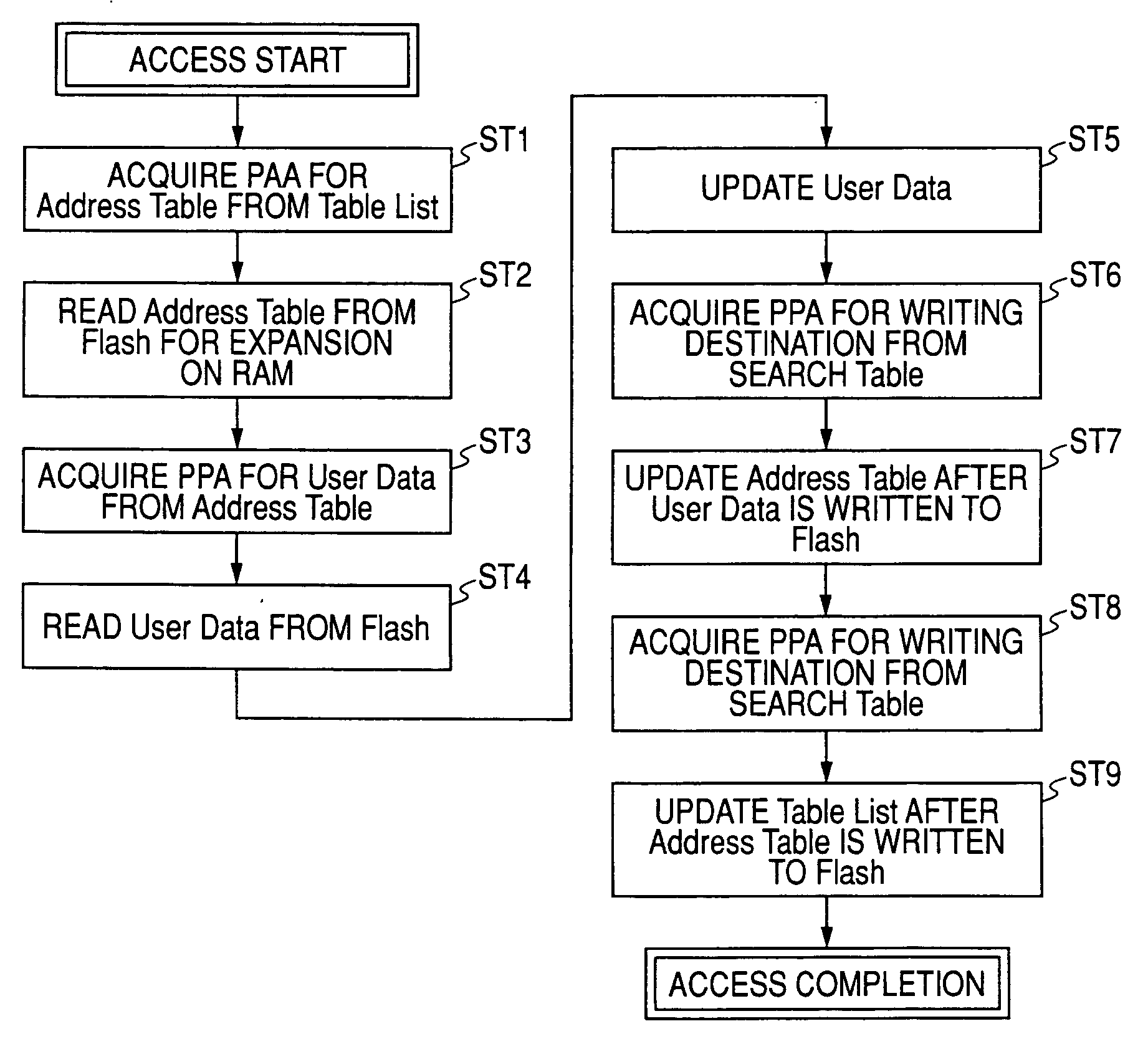
ActiveUS20070124531A1Technique is effectiveSwift and flexible access makingMemory adressing/allocation/relocationRead-only memoriesAccess methodEquipment computers
A storage device that includes: an address table; a cache memory; a flash memory device being a storage medium for user data; and a control circuit that is in charge of access management for the flash memory device. In the storage device, the control circuit makes access to the user data on the flash memory device via an address table, in the address table, with an index of an address value generated from an initial logical address, location information is acquired for the user data on the flash memory device corresponding to the index, and the address table is segmented in its entirety into a plurality of small address tables for every area of the index, and the small address tables being segmentation results are stored in the flash memory device, read as required when the user data is accessed, and expanded on the cache memory with entries of the small address tables.
Owner:SONY CORP
Systems and methods for correlating and distributing intrusion alert information among collaborating computer systems
ActiveUS20050257264A1Technique is effectiveMemory loss protectionUser identity/authority verificationTraffic volumeTraffic load
Systems and methods for correlating and distributing intrusion alert information among collaborating computer systems are provided. These systems and methods provide an alert correlator and an alert distributor that enable early signs of an attack to be detected and rapidly disseminated to collaborating systems. The alert correlator utilizes data structures to correlate alert detections and provide a mechanism through which threat information can be revealed to other collaborating systems. The alert distributor uses an efficient technique to group collaborating systems and then pass data between certain members of those groups according to a schedule. In this way data can be routinely distributed without generating excess traffic loads.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Contact center resource allocation based on work bidding/auction
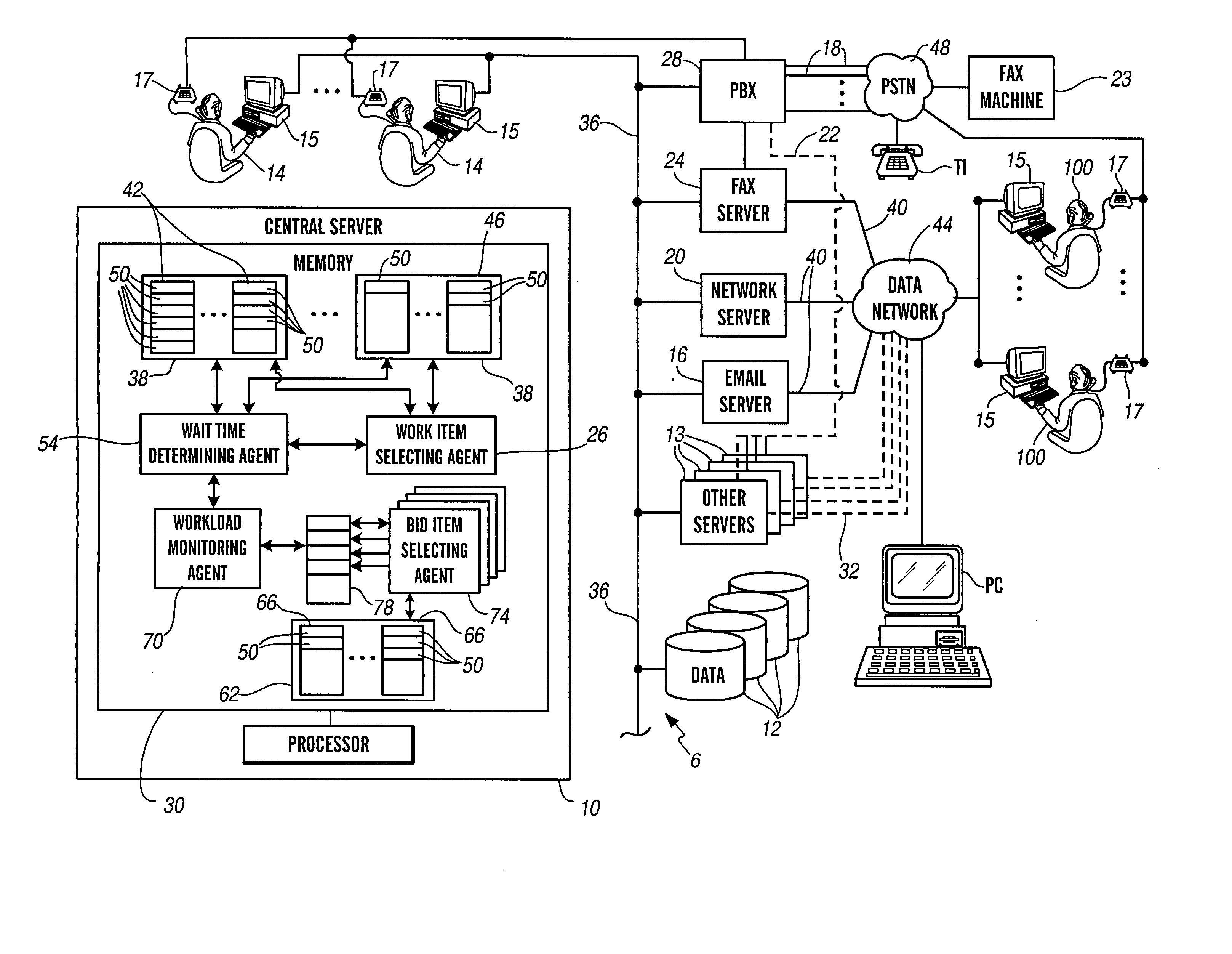
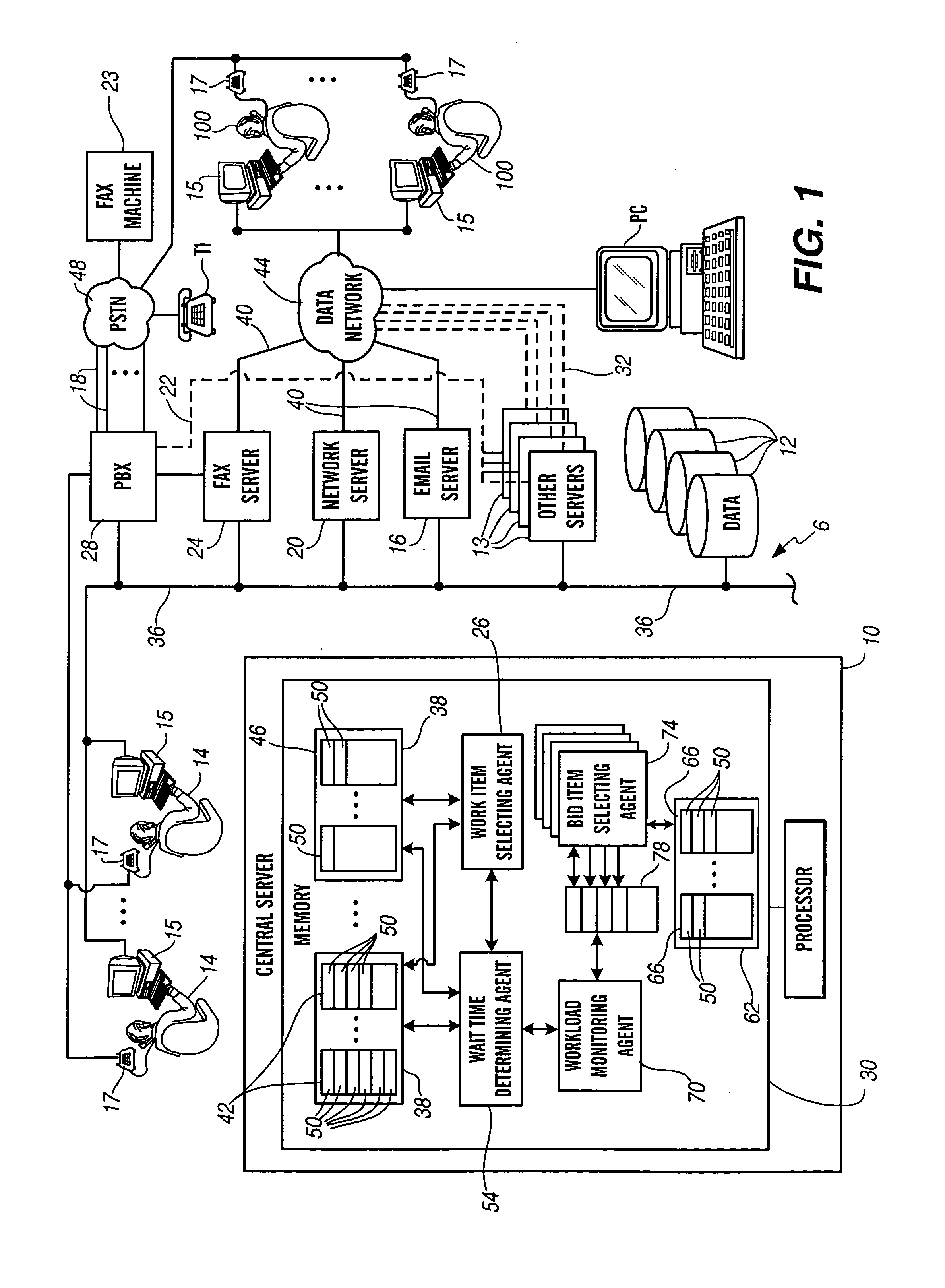
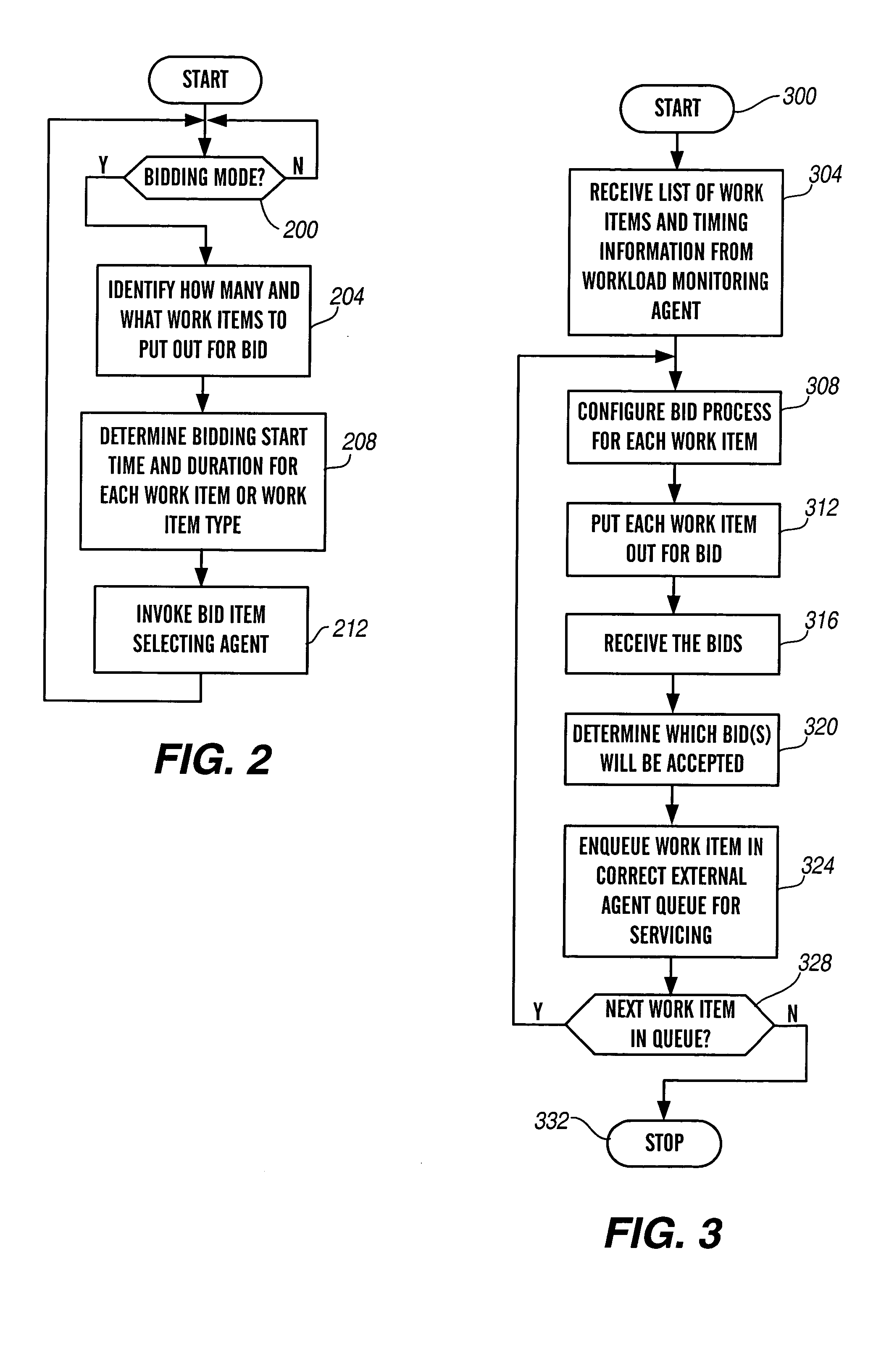
InactiveUS20050071241A1Effectively and optimally allocateImprove performanceSpecial service for subscribersCommerceContact centerWorkstation
A contact center for servicing a plurality of contacts received from a plurality of customers is provided. The contact center includes: (a) a plurality of workstations 15 corresponding to a plurality of resources 14; (b) a central server 10 in communication with the plurality of workstations, comprising: (i) at least one queue 42, 46 and / or 66 of contacts; and (ii) a bid item selecting agent 74 operable to (a) request at least some of the plurality of resources to submit a bid to service at least one contact; (b) receive at least one bid to service the at least one contact; and (c) select a resource from among the plurality of resources to service the at least one contact.
Owner:AVAYA INC
Video registration and image sequence stitching
ActiveUS7460730B2Easy constructionEnhance the imageTelevision system detailsDigital data information retrievalIntermediate imageImage pair
A “Keyframe Stitcher” provides an efficient technique for building mosaic panoramic images by registering or aligning video frames to construct a mosaic panoramic representation. Matching of image pairs is performed by extracting feature points from every image frame and matching those points between image pairs. Further, the Keyframe Stitcher preserves accuracy of image stitching when matching image pairs by utilizing ordering information inherent in the video. The cost of searching for matches between image frames is reduced by identifying “keyframes” based on computed image-to-image overlap. Keyframes are then matched to all other keyframes, but intermediate image frames are only matched to temporally neighboring keyframes and neighboring intermediate frames to construct a “match structure.” Image orientations are then estimated from this match structure and used to construct the mosaic. Matches between image pairs may be compressed to reduce computational overhead by replacing groups of feature points with representative measurements.
Owner:MICROSOFT TECH LICENSING LLC
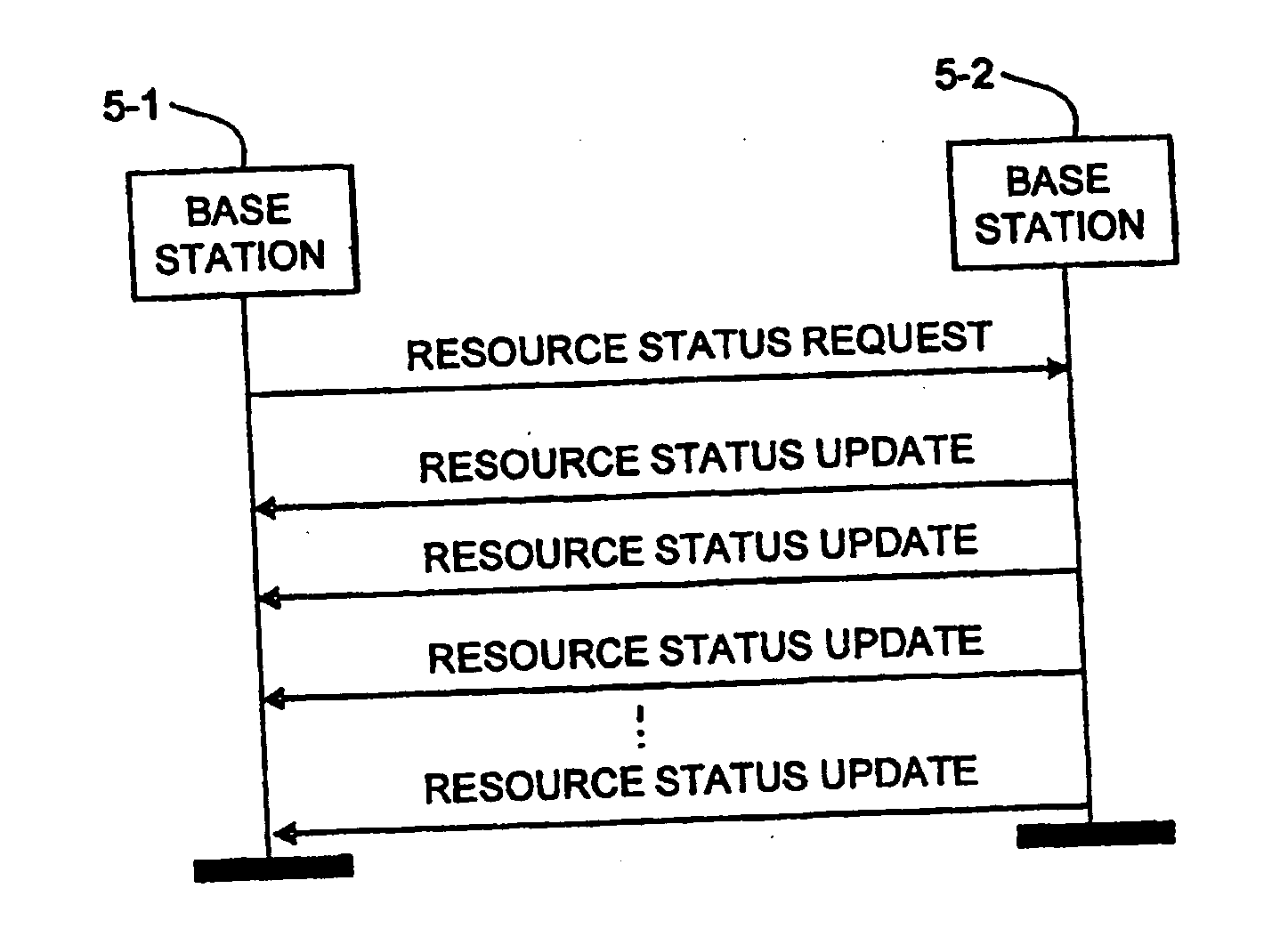
Signalling of resource status information between base stations for load balancing
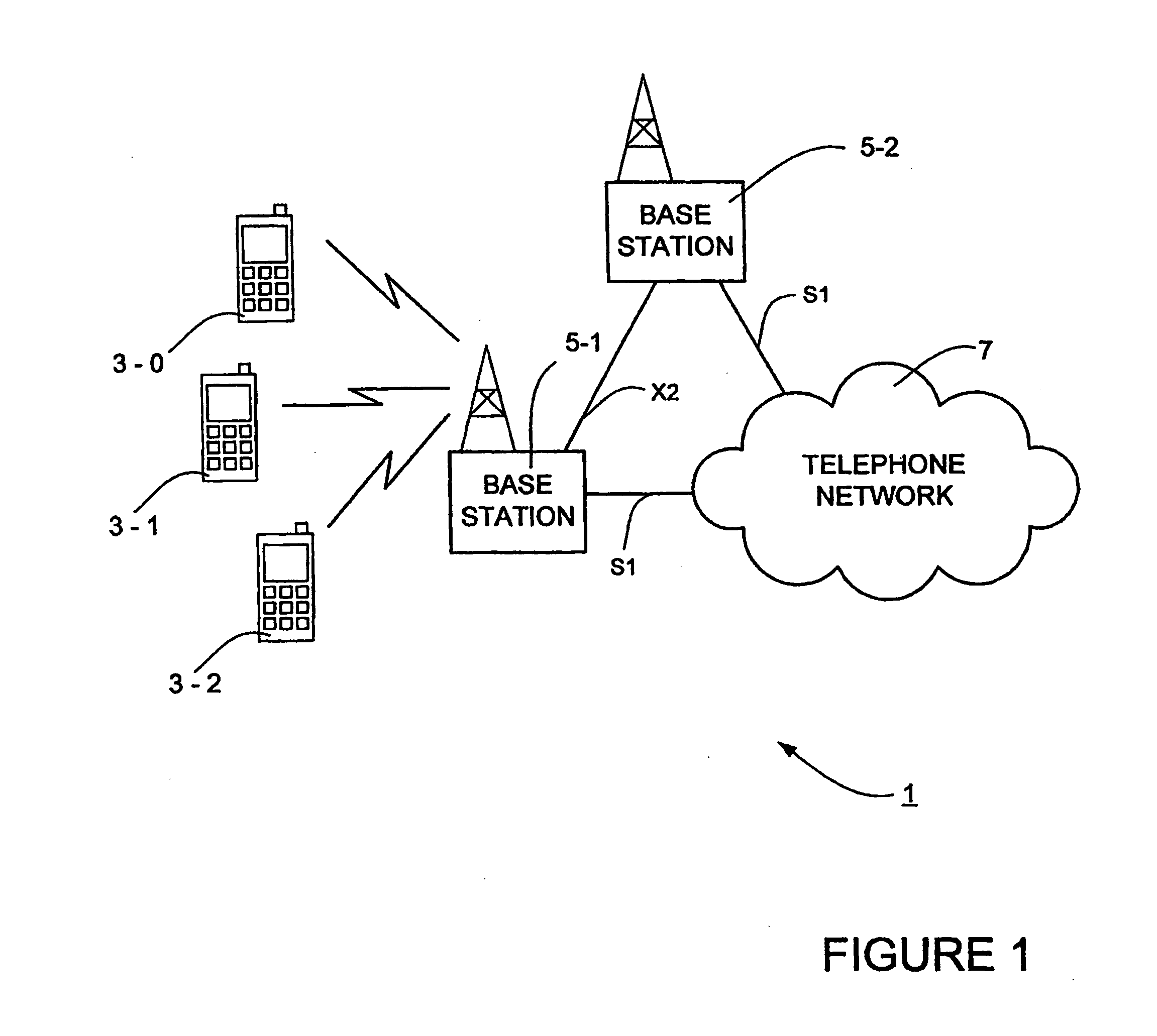
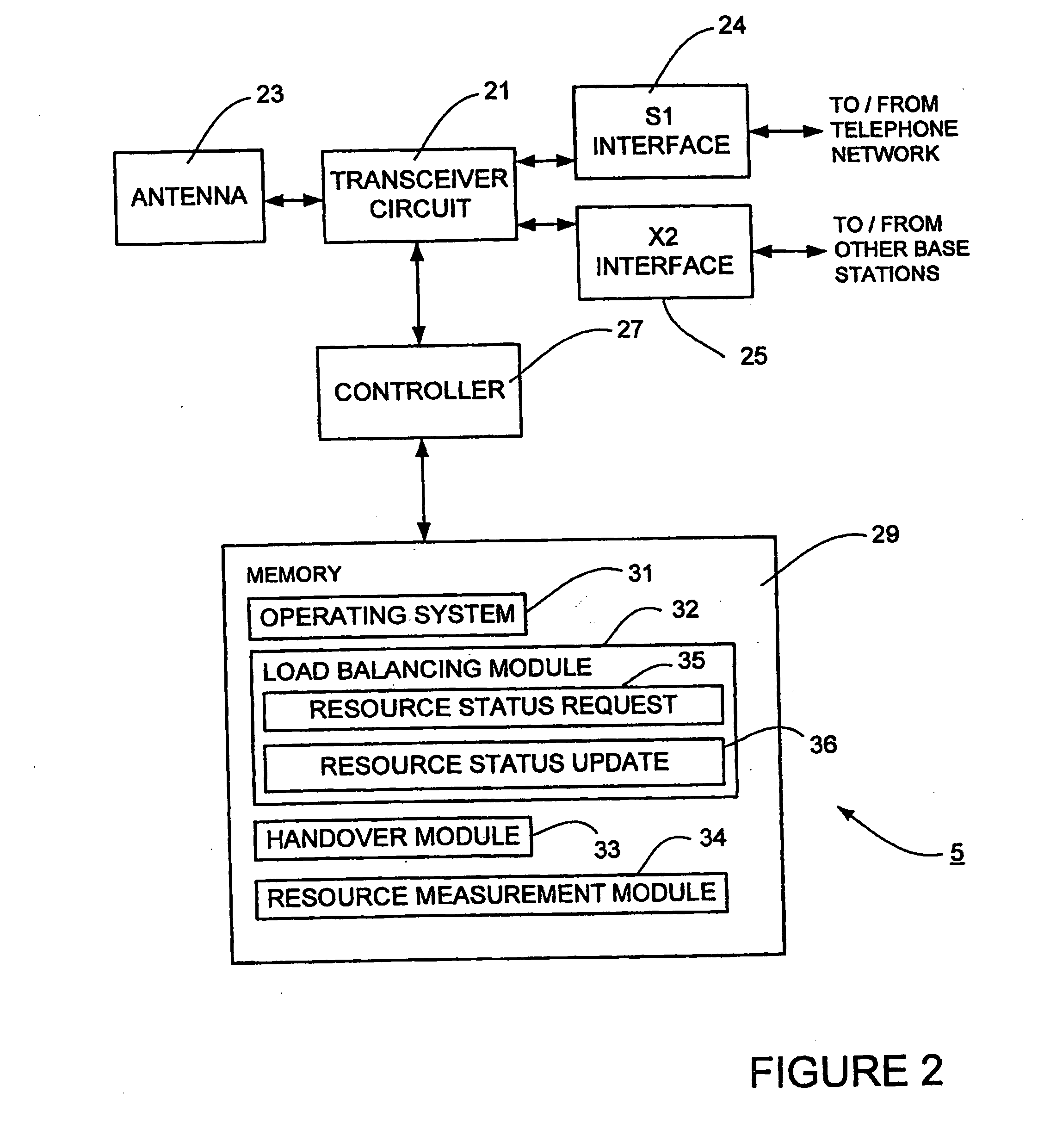
ActiveUS20110053598A1Technique is effectiveNetwork traffic/resource managementSubstation equipmentCommunications systemMobile communication systems
A mobile communications system is described in which base stations communicate with each other using a Master / Slave protocol to exchange load balancing information that can be used to control the handover of mobile devices amongst neighbouring base stations and / or neighbouring cells. The Master base station requests the Slave base station to provide a load status report to it either at a defined time or periodicity or in response to certain events.
Owner:NEC CORP
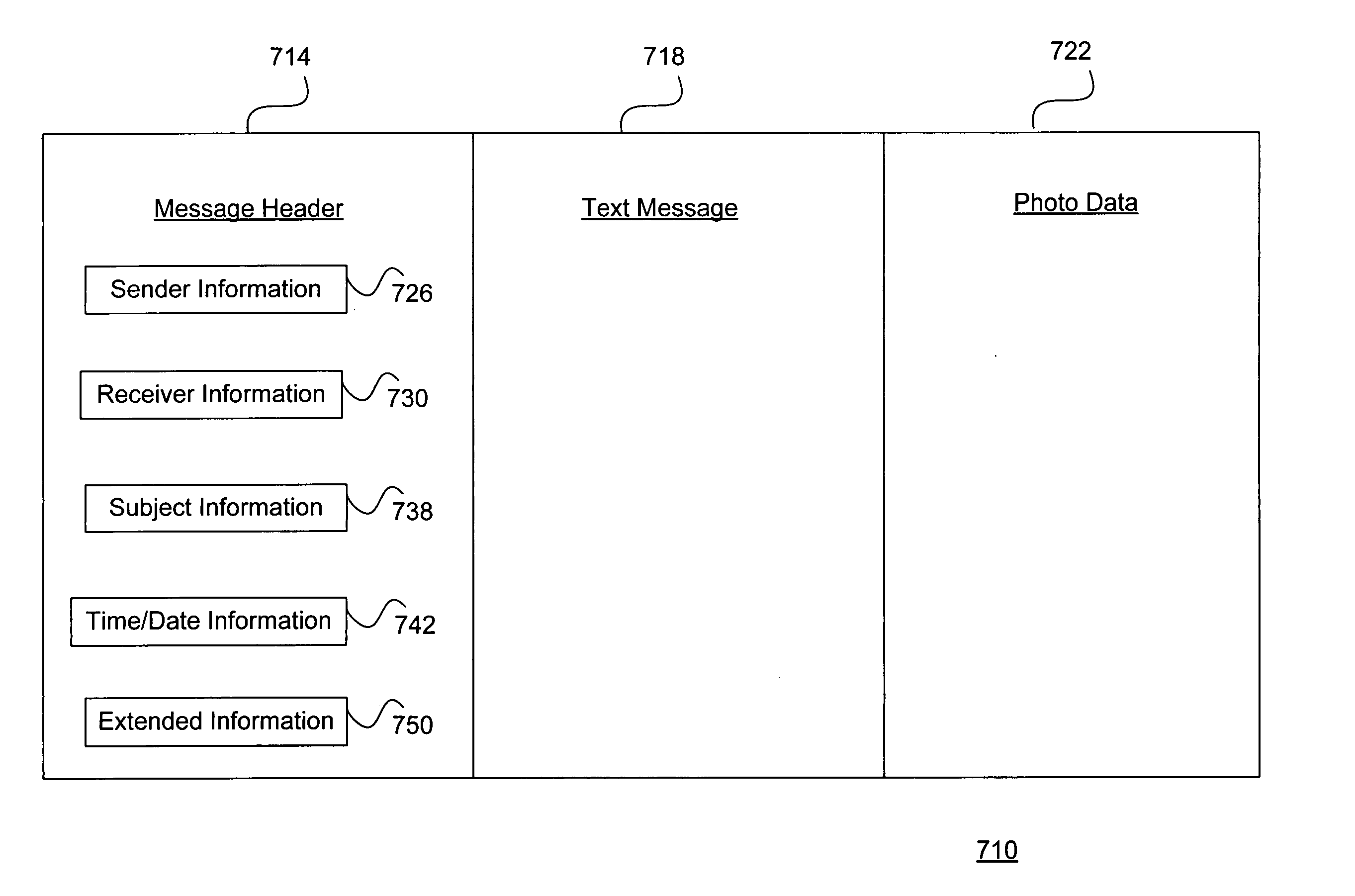
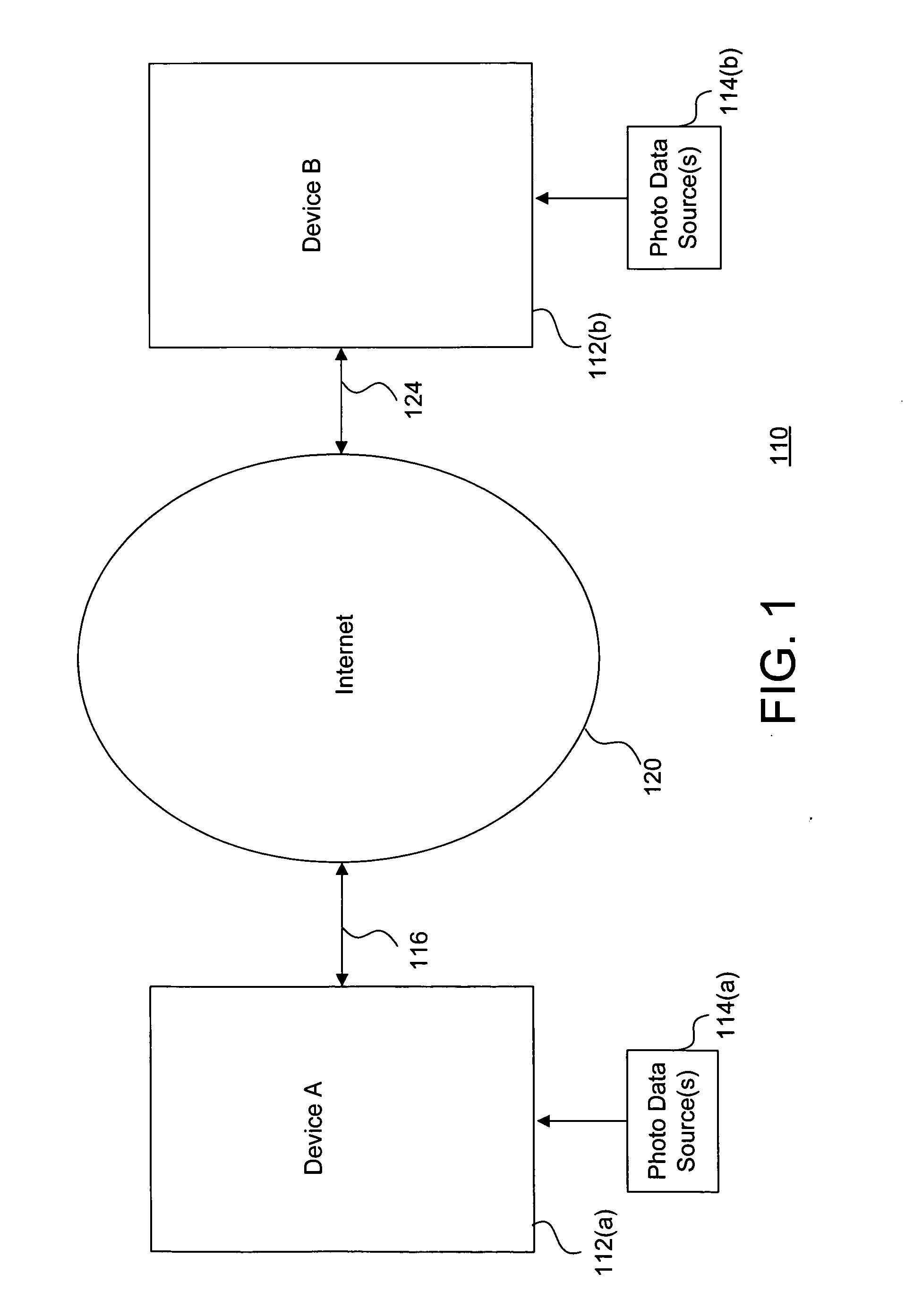
System and method for effectively exchanging photo data in an instant messaging environment
InactiveUS20060041627A1Increases entertainment valueImprove communication qualityMultiple digital computer combinationsData switching networksDisplay deviceElectronic network
A system and method for effectively exchanging photo data in an instant messaging environment includes a first device coupled to an electronic network for utilizing a first messaging program and a first messaging display to create text messages for performing messaging procedures. A photo data source such as a digital camera is configured to capture photo data when the first device is instructed to transmit the text messages by activating a “send message” icon on the first messaging display. The first messaging program automatically creates and transmits photo messages that include the photo data and corresponding text messages. A second device coupled to the electronic network may then utilize a second messaging program to receive and display the text messages and photo data from the transmitted photo messages upon a second messaging display. The second device may also similarly create and send reciprocal photo messages to the first device during the foregoing messaging procedures.
Owner:SONY INTERACTIVE ENTERTAINMENT AMERICA LLC
User interface for transactions
ActiveUS20170357972A1Faster and efficient methodFaster and efficient and interfaceCash registersBuying/selling/leasing transactionsAuthorizationAffordance
The present disclosure generally relates to techniques for managing contextual transactions. In some examples, at a sender electronic device, a first user provides authorization to purchase an item for a second user. In some examples, at a recipient device, the second user selects one or more attributes for the item and requests to claim the item. In some examples, an electronic device displays a representation of an item and a purchase affordance for purchasing the item using a payment system that is available on the electronic device.
Owner:APPLE INC
Disk array device
ActiveUS20060039108A1Eliminate the effects ofReduce environmental loadDigital data processing detailsAir heatersPower controllerEngineering
In a disk array device for cooling respective sections including a HDD by a fan, drop of cooling efficiency by the difference of conditions of HDD mounted and unmounted sections is prevented and the use of a dummy HDD is deleted / eliminated. A housing contains a HDA mounted on the HDD, a power controller board for performing control to the HDD, a power unit for supplying power to each section, a fan for cooling the housing therein, and a backboard for connecting all the sections. On one backboard surface, the HDA is mounted, which has a cooling function for making cooling air flowing in the housing and exhausting air from the housing via a region on which the HDA are mounted and via a vent hole on the backboard. For the vent hole, a shutter is mounted, which has a mechanism for adjusting an open area rate of the vent hole by opening when the HDA is mounted and closing when removed.
Owner:GOOGLE LLC
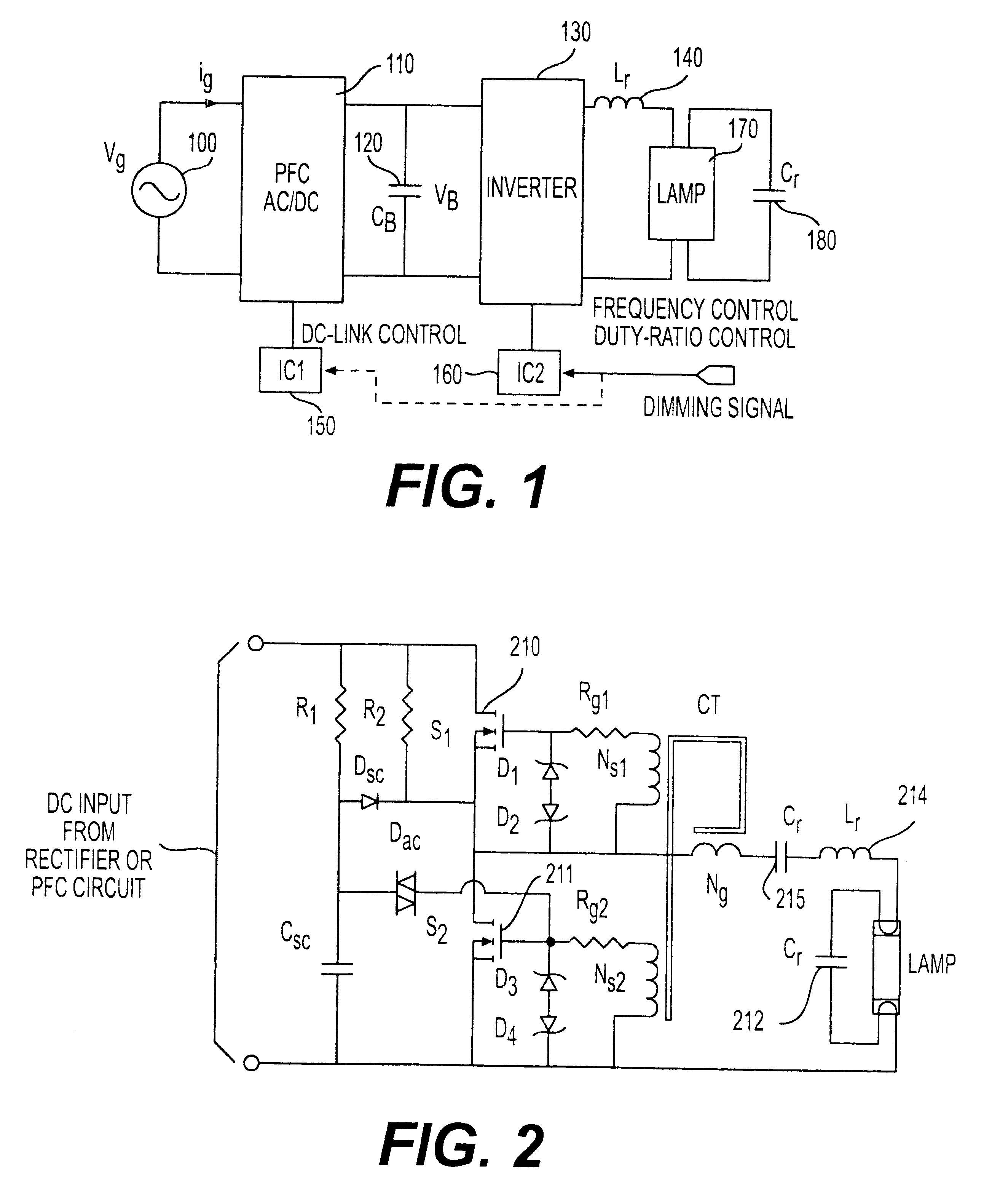
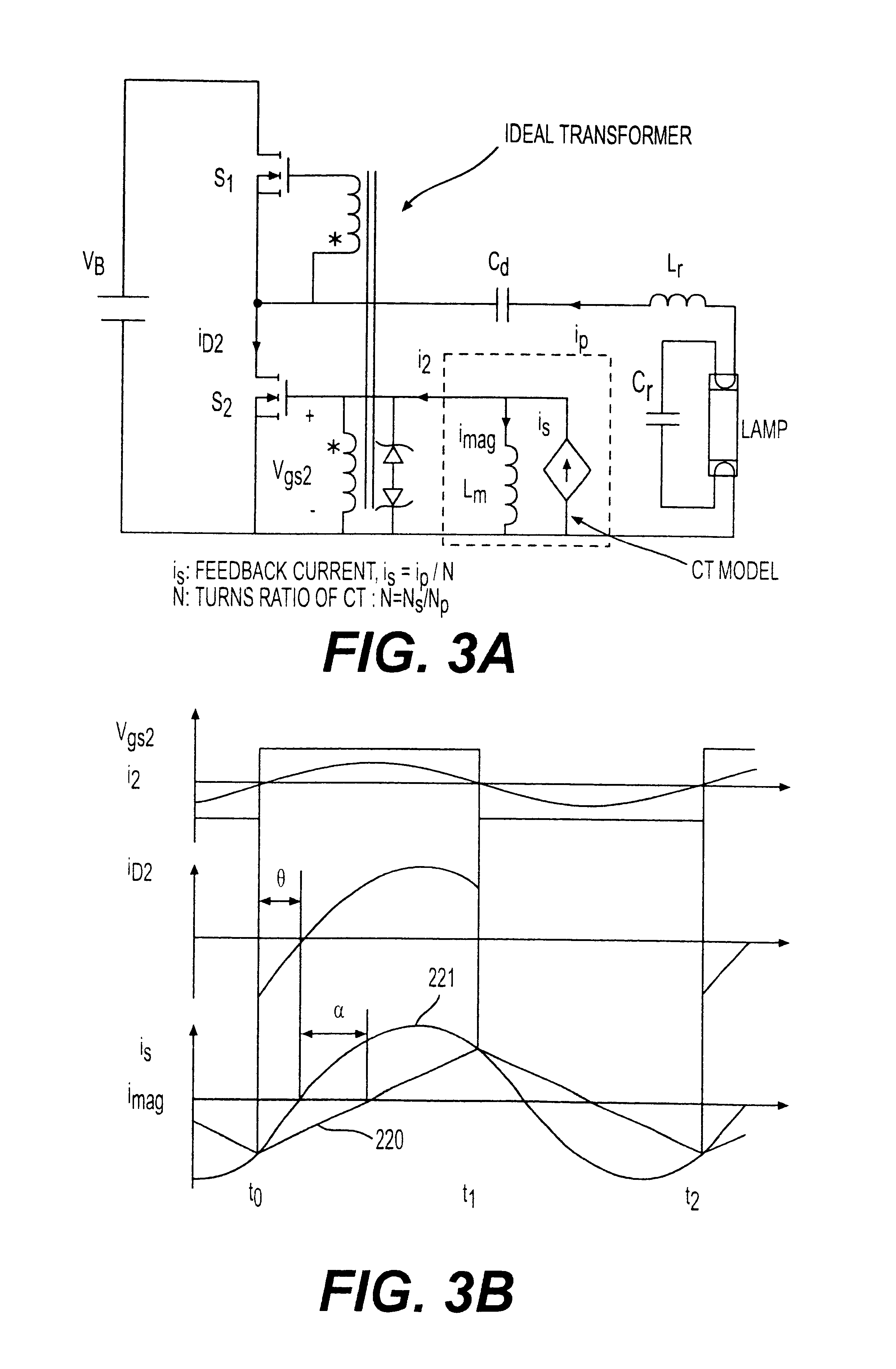
Self-oscillating electronic discharge lamp ballast with dimming control
InactiveUS6696803B2Improving crest factorTechnique is effectiveElectrical apparatusElectric light circuit arrangementCapacitanceModulation transformer
A simplified electronic ballast for a discharge lamp which provides dimming by control of inverter frequency through modulation of magnetizing current in a transformer such that the switching frequency is made substantially independent of the load presented. The principle of frequency control in a manner independent of the load is extendable to other types of loads and power supplies and converters to regulate power coupled to the load. Clamping capacitors are used to replace other clamping circuits in order to allow current injection to be controlled by a simple variable voltage while frequency control by current injection provides enhanced circuit performance.
Owner:VIRGINIA TECH INTPROP INC
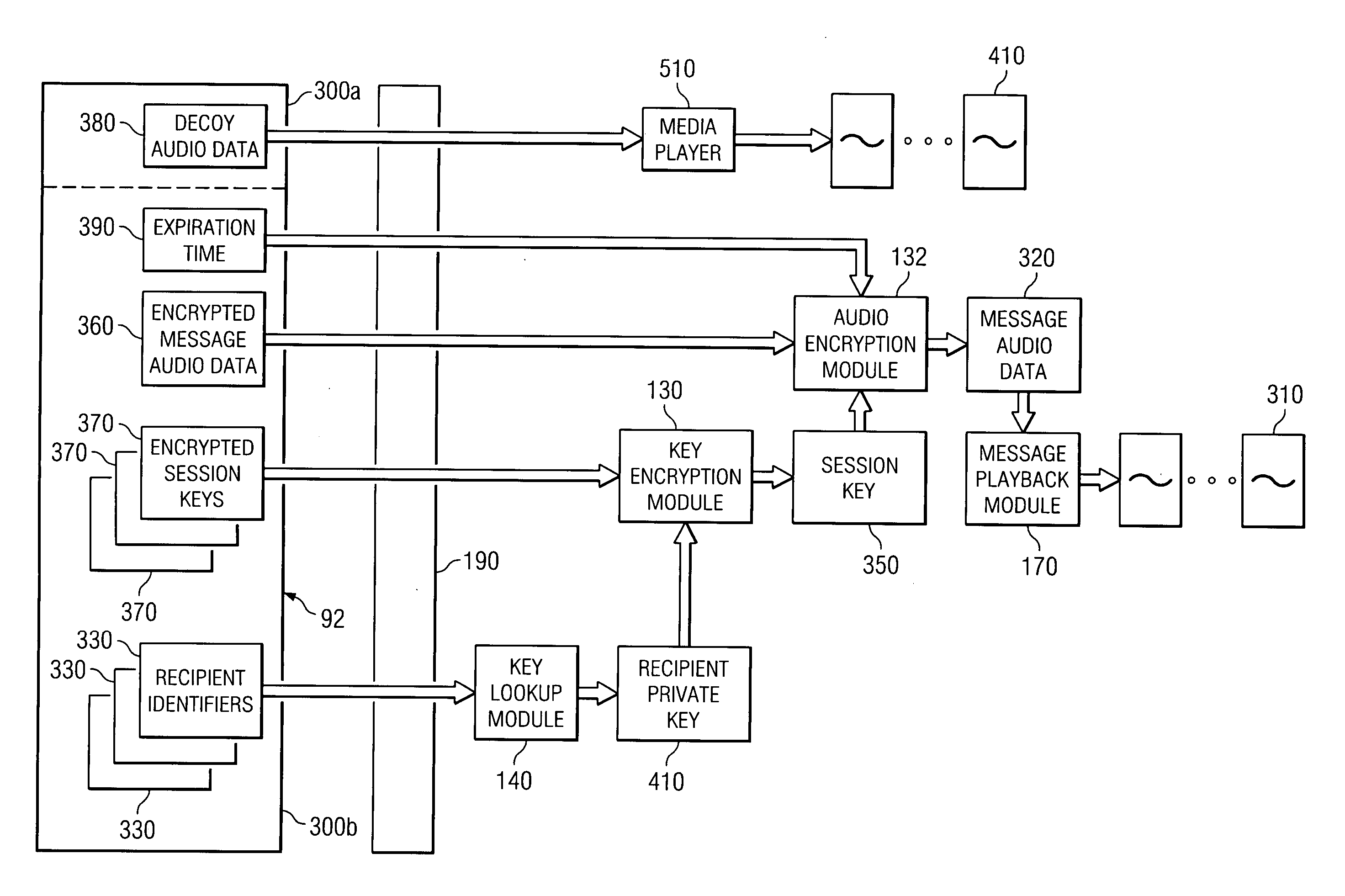
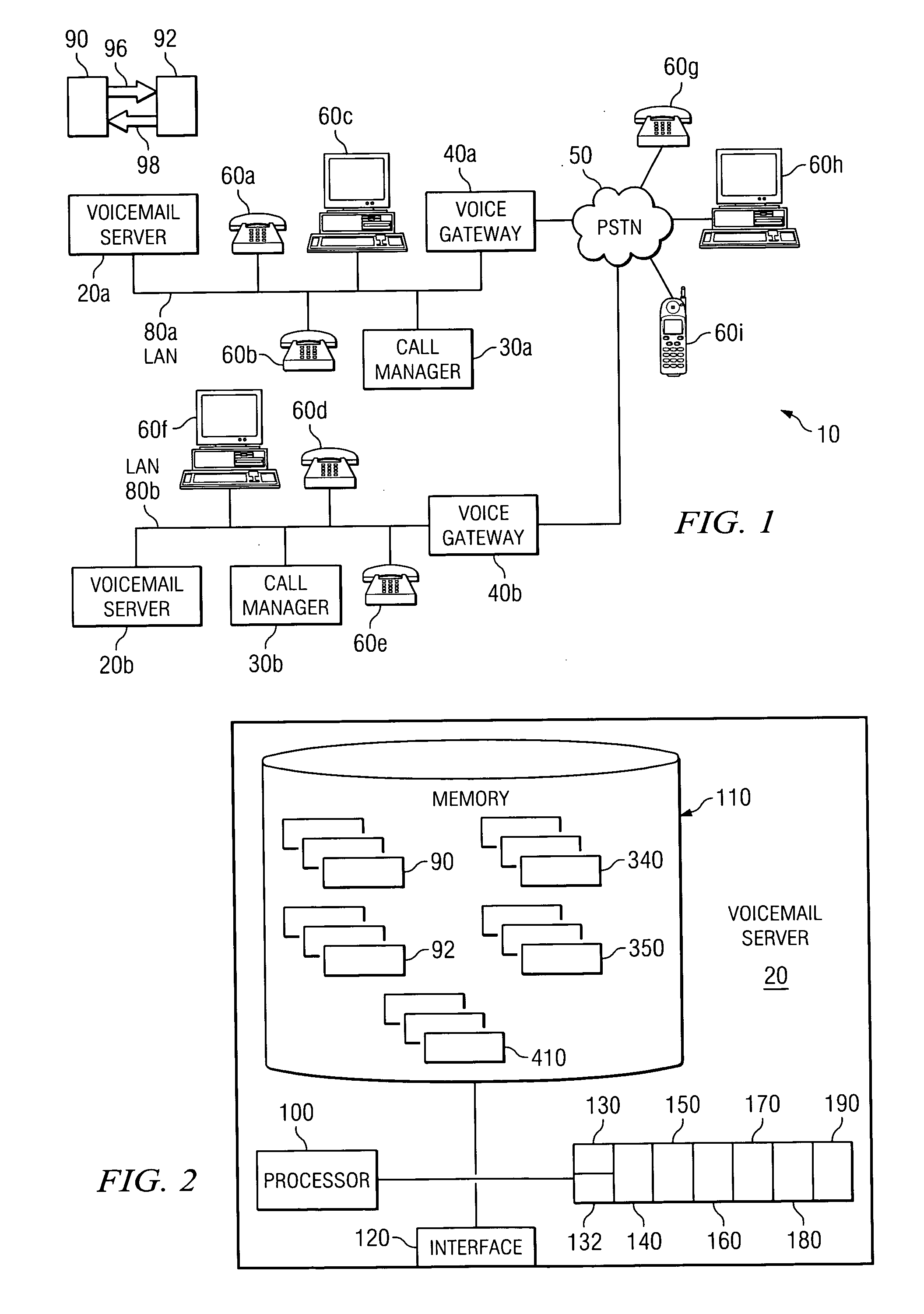
System and method for communicating confidential messages
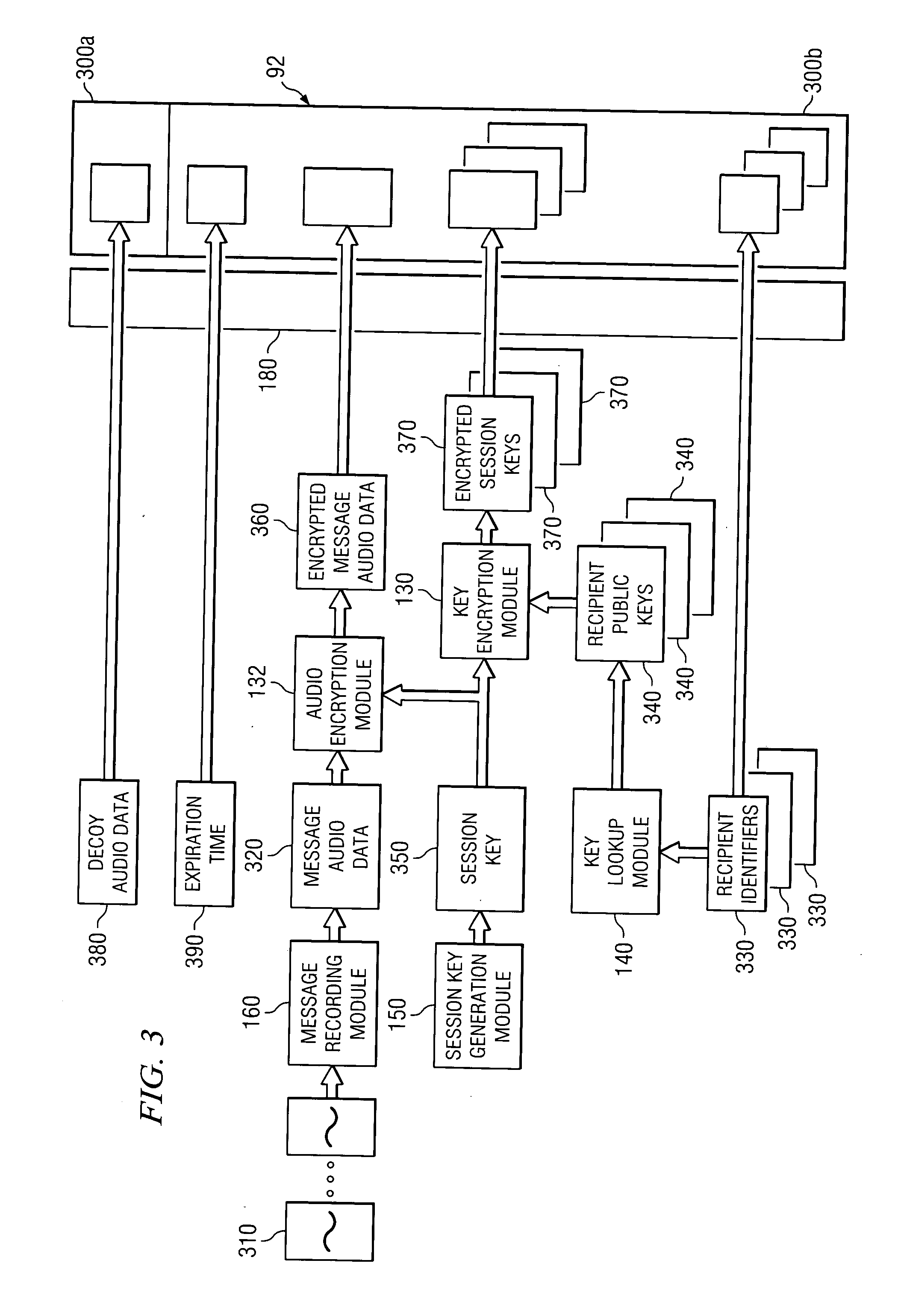
ActiveUS20060274856A1Disadvantage and problem associate with be substantially reduce and eliminateDisadvantages and reduced eliminatedUnauthorized memory use protectionHardware monitoringAudio frequencyData store
A method of recording messages includes recording audio data in a first file structured in accordance with a file format that defines a first portion and a second portion. The audio data is recorded in the first portion of the first file. The method also includes encrypting the audio data stored in the first portion of the first file and generating a second file structured according to the file format. The second file includes decoy audio data in the first portion of the second file and the encrypted audio data in the second portion of the second file. The decoy audio data indicates a confidential status of the second file or serves as a red herring to distract from the encrypted audio data in the second portion of the second file.
Owner:CISCO TECH INC
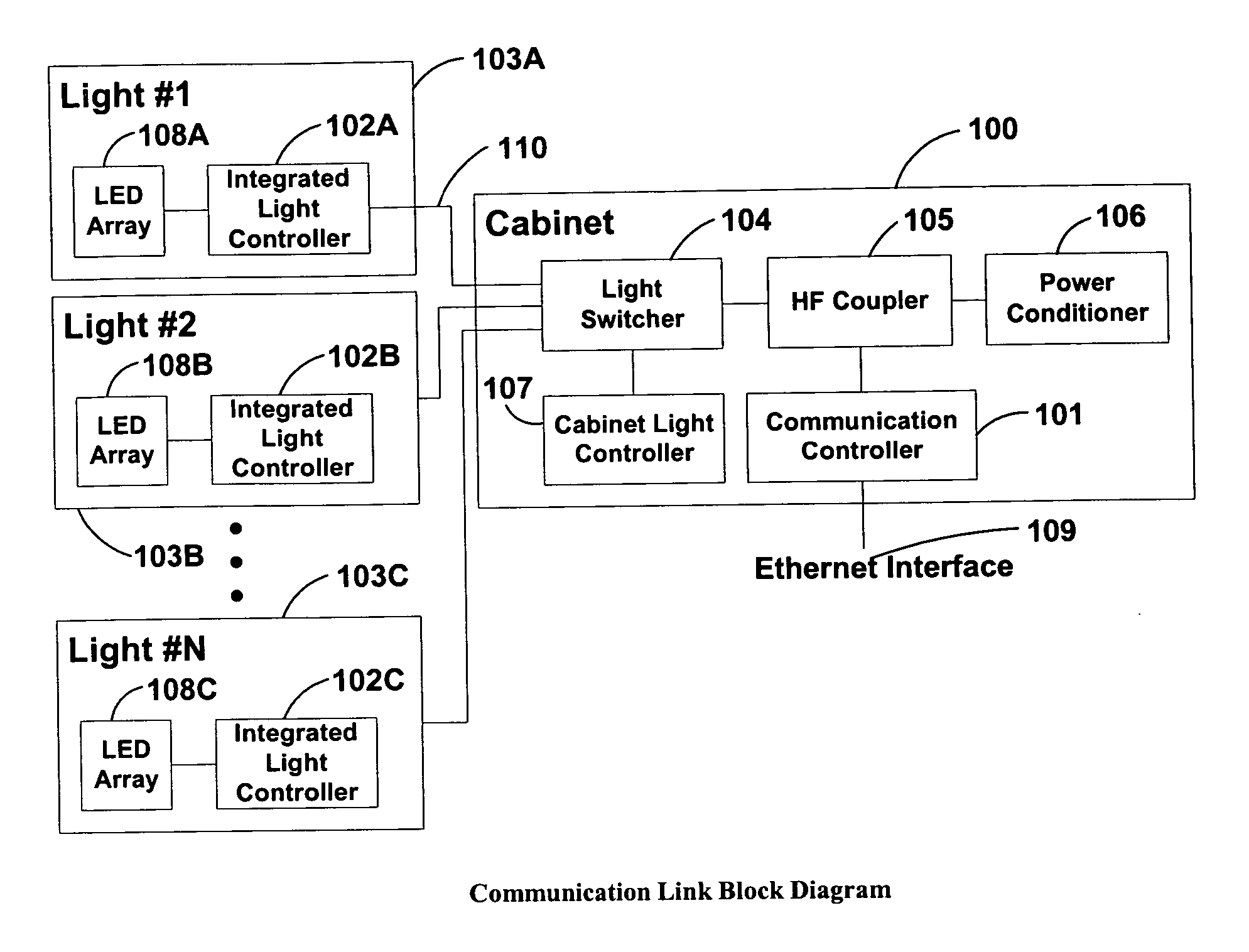
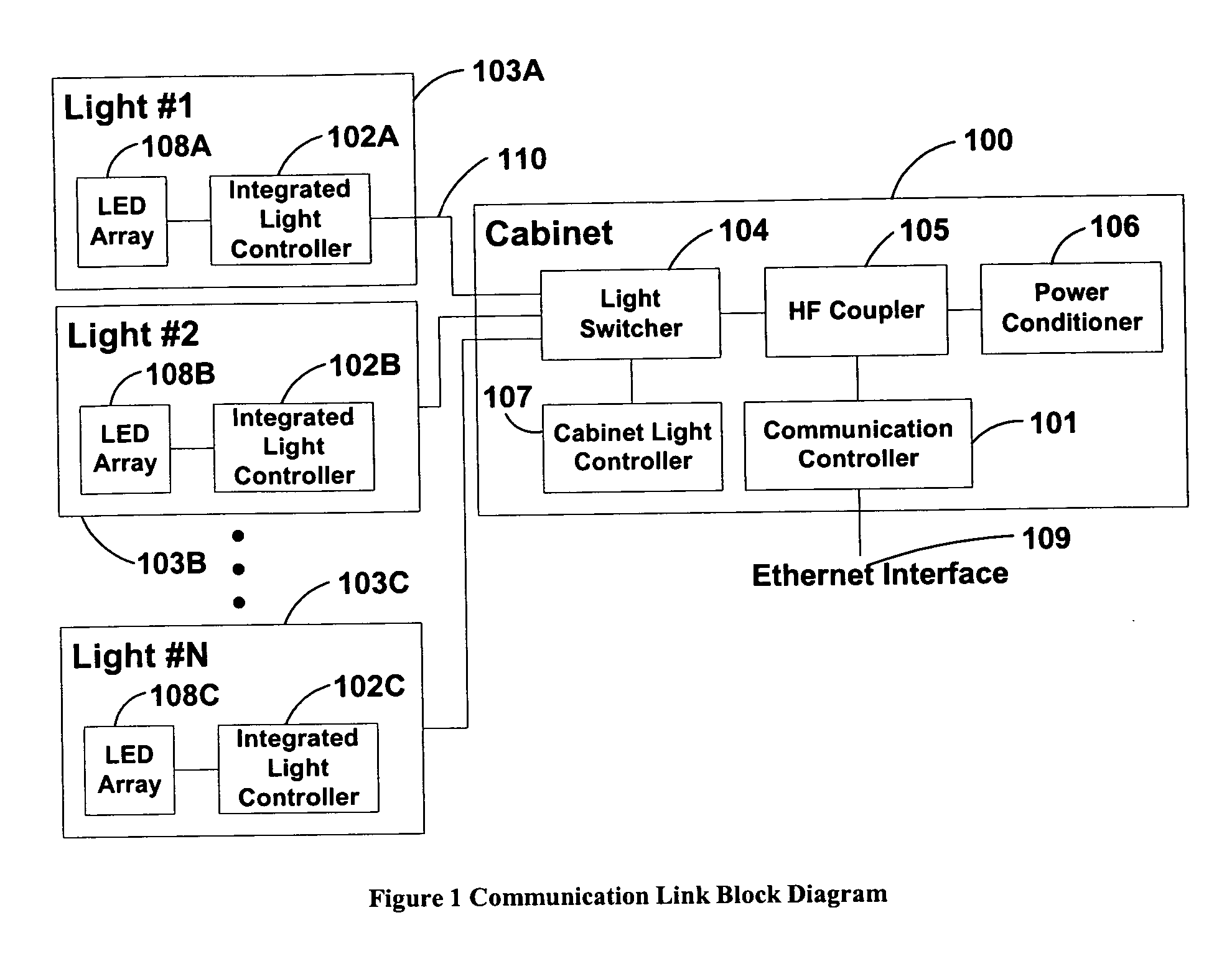
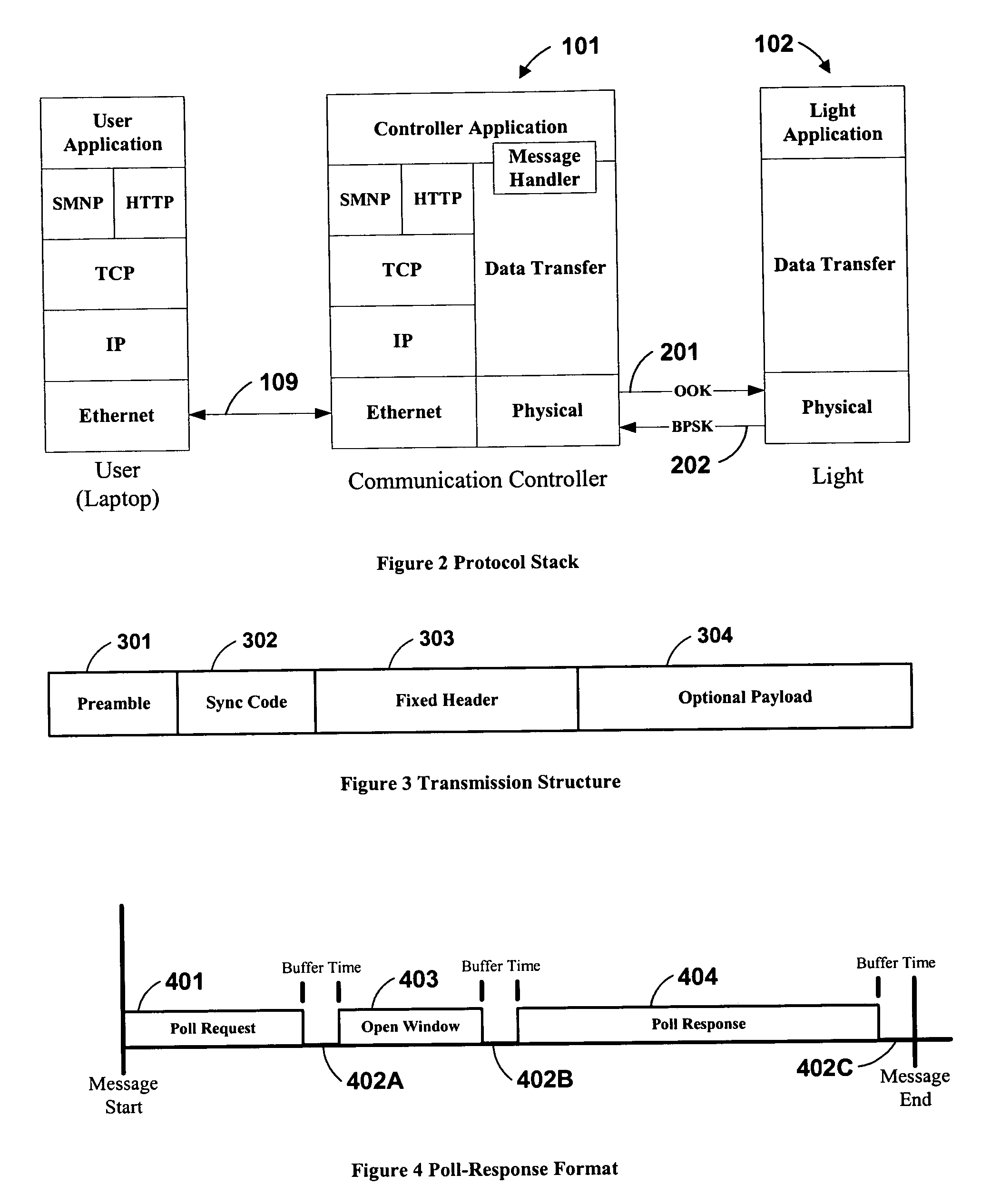
System and method of communications with traffic signals
InactiveUS20060039698A1Low costConvenient lengthTransmission monitoringTransmission monitoring/testing/fault-measurement systemsTelecommunications linkTraffic signal
The present invention comprises a system and method for communicating with a traffic signal by which at least one communication controller and integrated light controller are coupled by a high frequency (“HF”) coupler to a power line for transmission. In each of the directions of communication, specific transmission methods and data protocols are used over the communication link. The communication link protocol used for communication between the integrated light controller and the communication controller provides a robust method for framing data within a message structure that provides byte-by-byte synchronization and message integrity through a parity check per byte, and a checksum calculation.
Owner:OPTISOFT +2
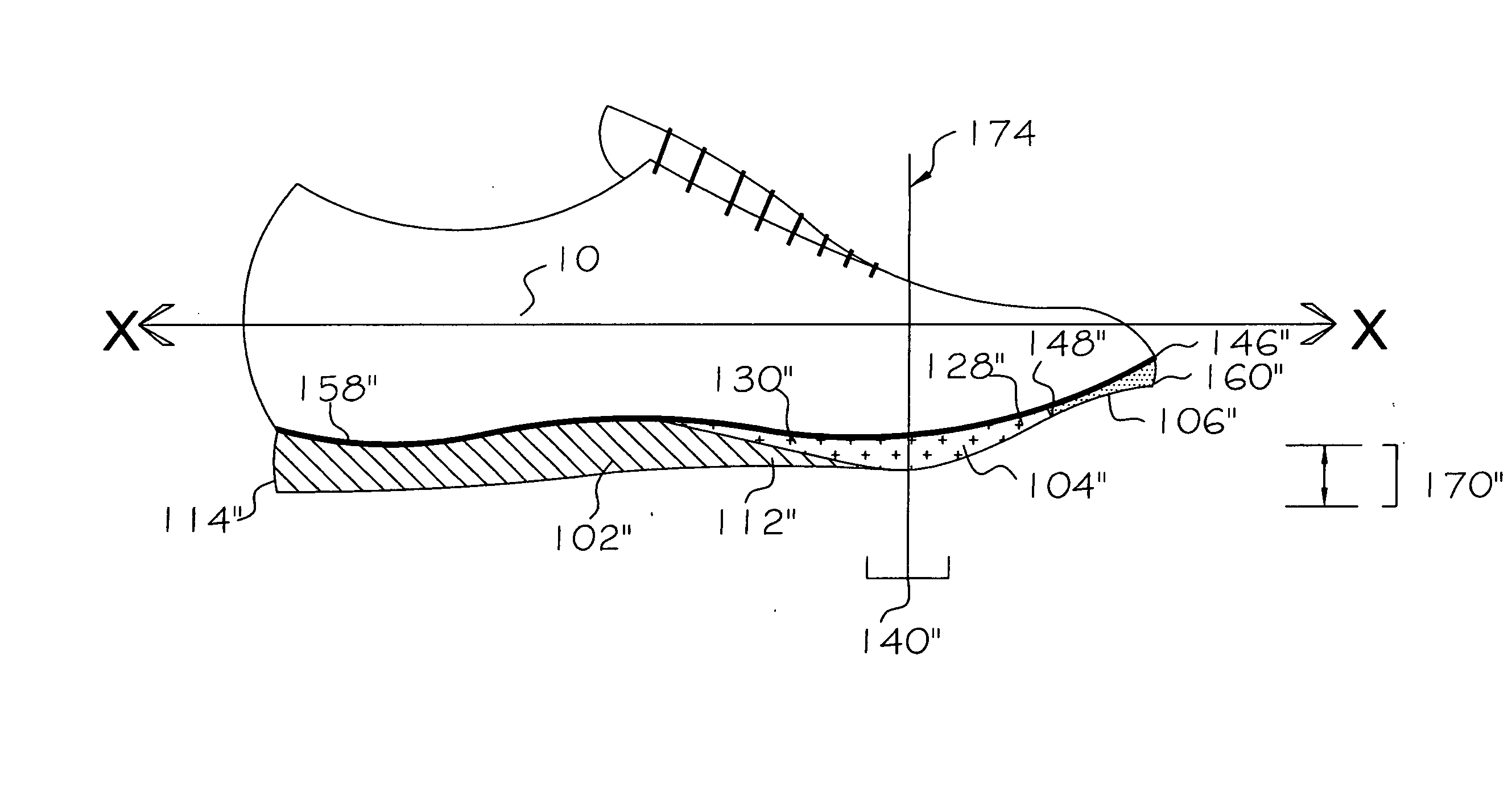
Energy translating footwear mechanism for enhancing forward
InactiveUS20070283599A1Technique is effectiveEfficiently displacedSolesInsolesFoot strikeMuscular tension
Owner:MULLEN KRISTYNA +3
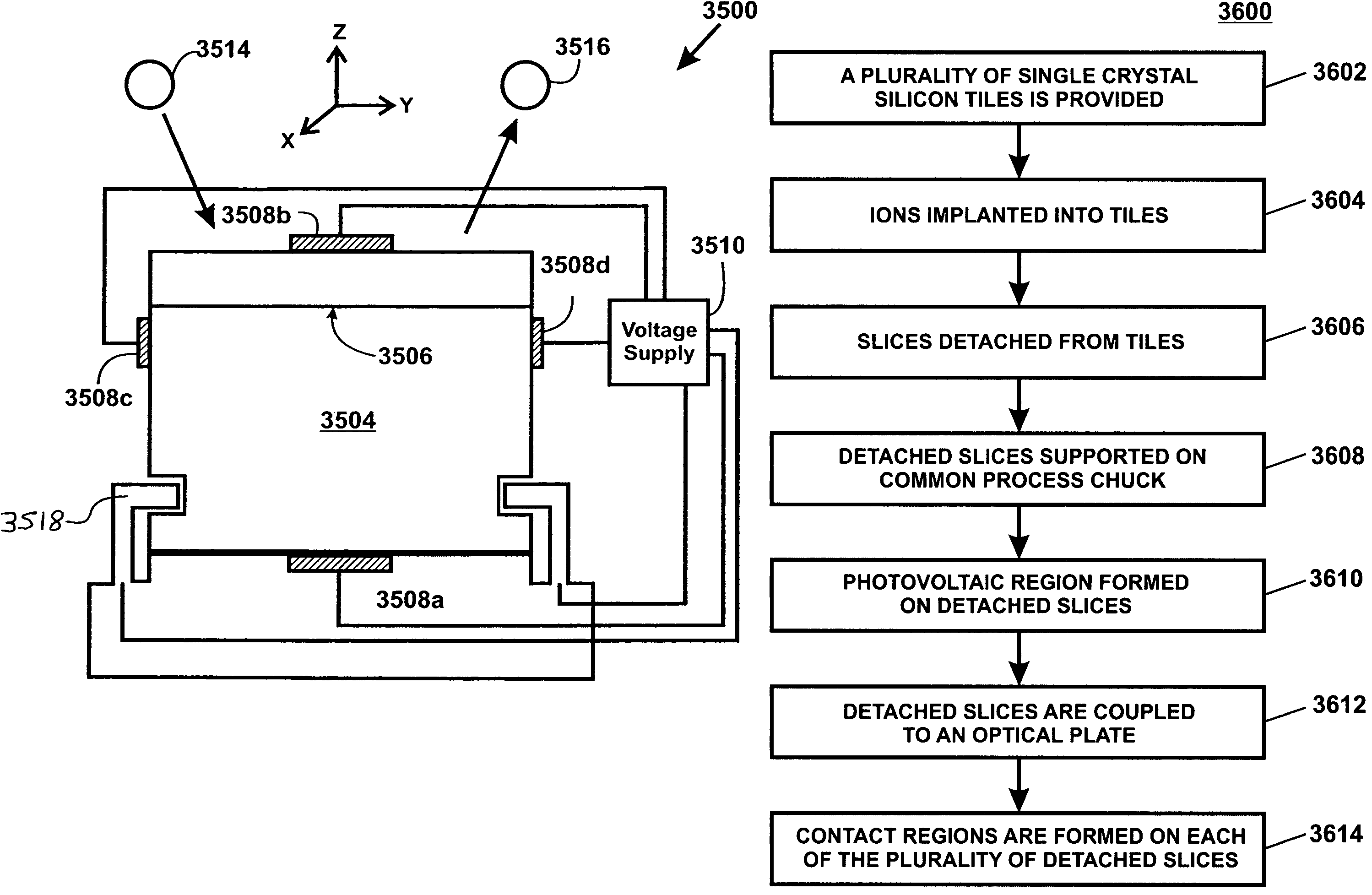
Method and structure for fabricating solar cells using a layer transfer process
InactiveUS7759220B2Easy to disassembleImprove bindingSemiconductor/solid-state device manufacturingSemiconductor devicesSolar cellMechanical pressure
A reusable silicon substrate device for use with layer transfer process. The device has a reusable substrate having a surface region, a cleave region, and a total thickness of material. The total thickness of material is at least N times greater than a first thickness of material to be removed. In a specific embodiment, the first thickness of material to be removed is between the surface region and the cleave region, whereupon N is an integer greater than about ten. The device also has a chuck member adapted to hold a handle substrate member in place. The chuck member is configured to hold the handle substrate in a manner to facilitate bonding the handle substrate to the first thickness of material to be removed. In a preferred embodiment, the device has a mechanical pressure device operably coupled to the chuck member. The mechanical pressure device is adapted to provide a force to cause bonding of the handle substrate to the first thickness of material to be removed.
Owner:SILICON GENERAL CORPORATION
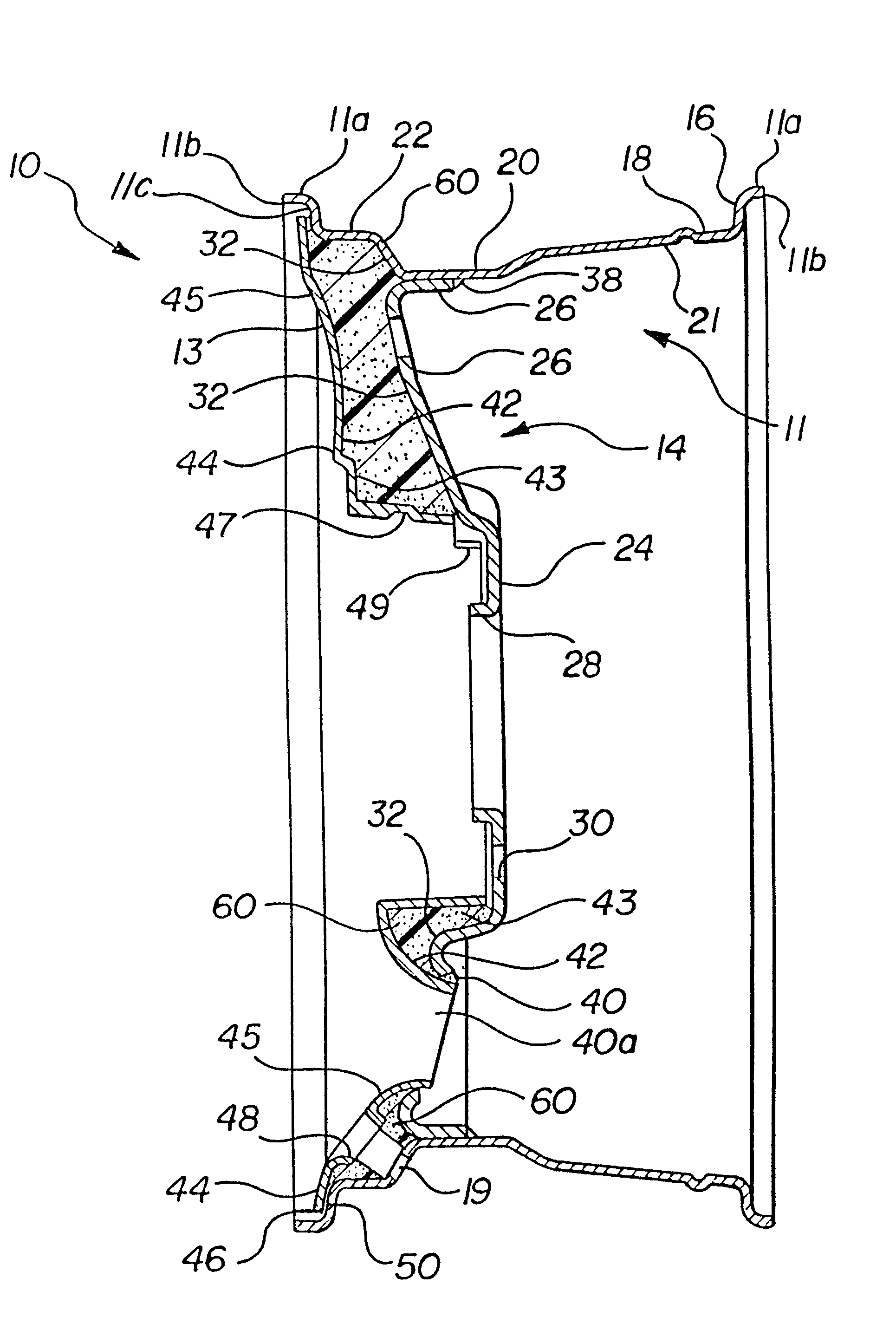
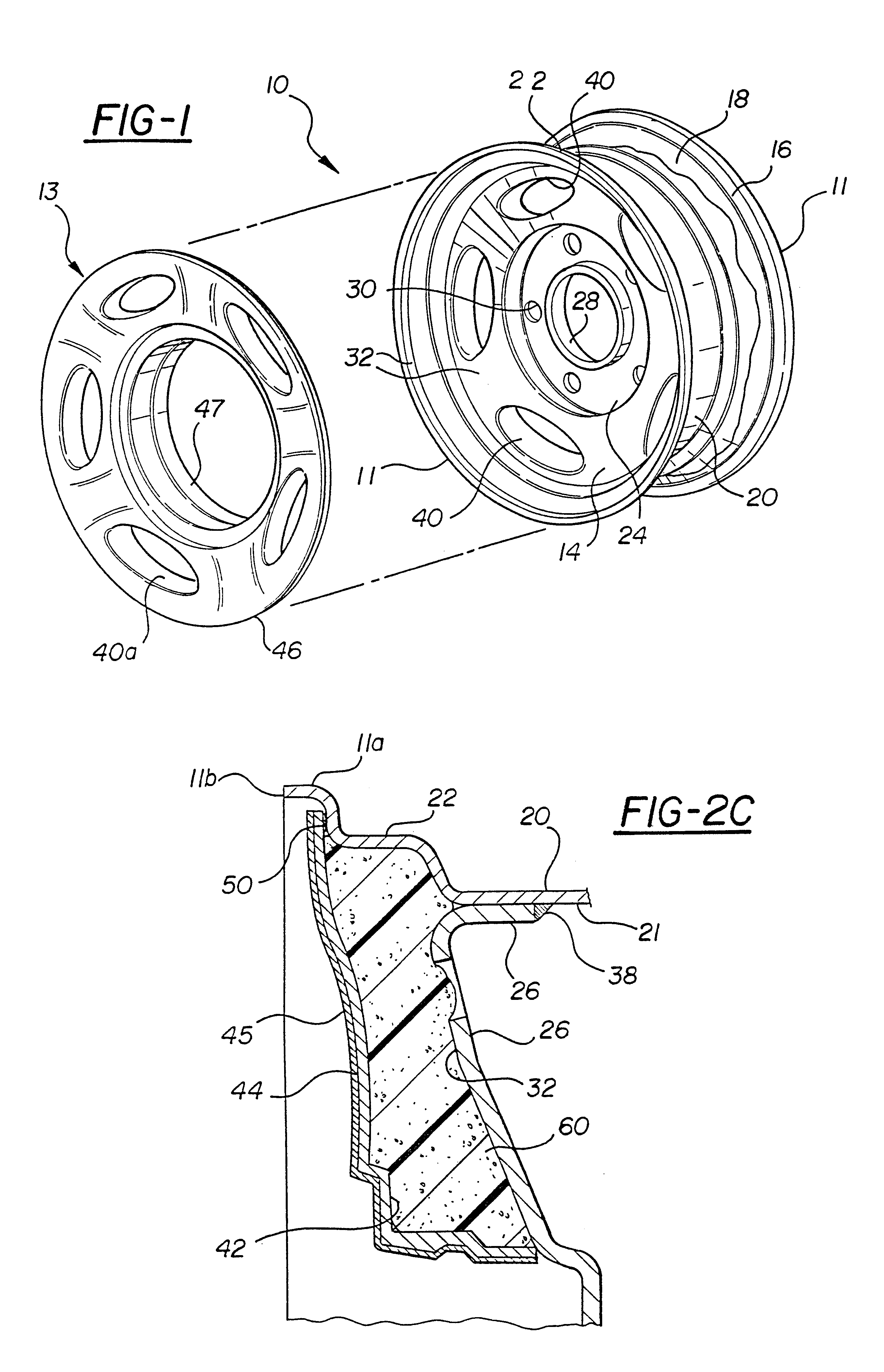
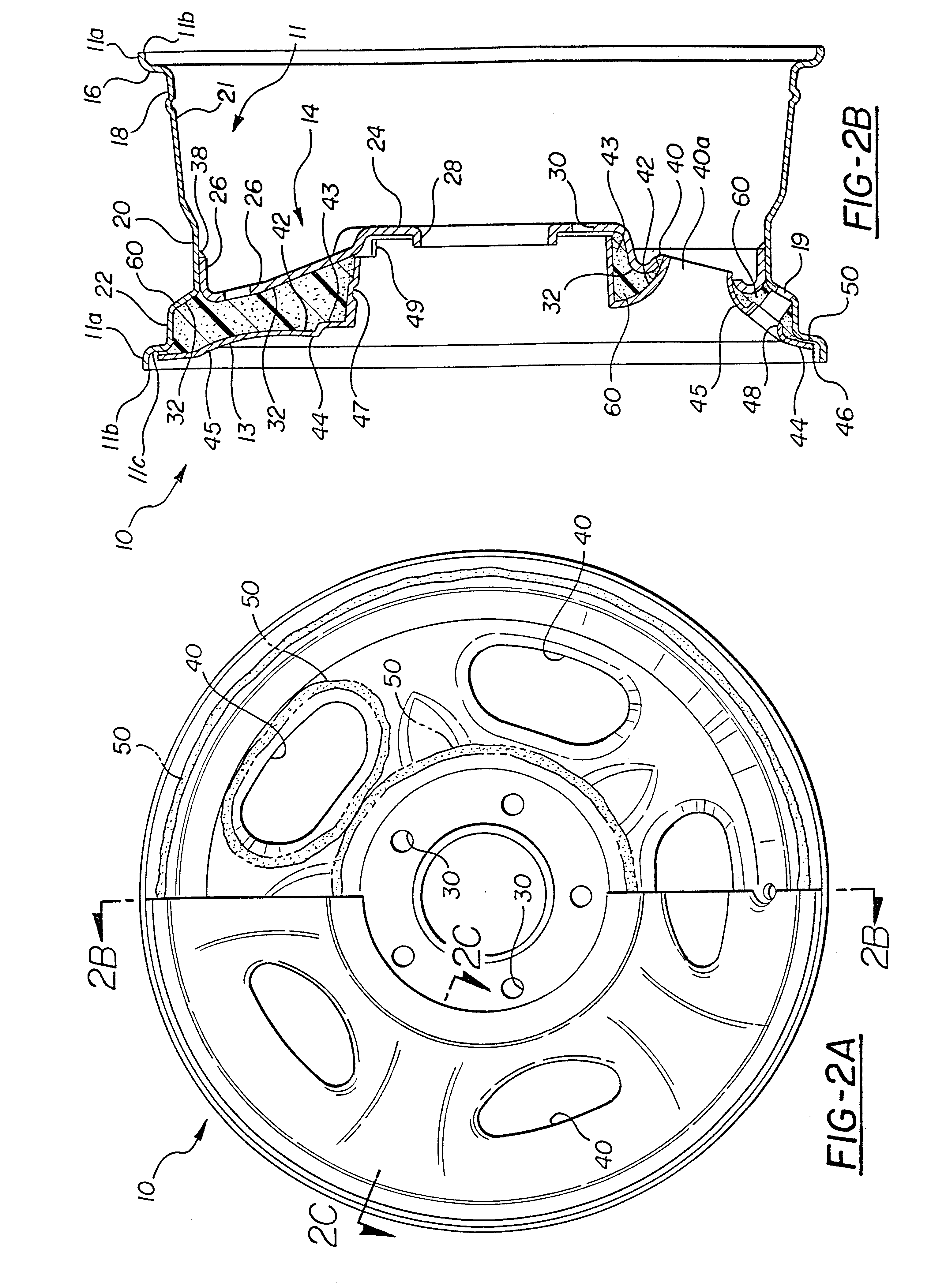
Vehicle wheel construction process
InactiveUS6346159B1Avoid Insufficient SealingPrevent escapeTailstocks/centresConfectioneryTurbineEngineering
An improved process for permanently attaching an overlay to a wheel disc, wherein the overlay is aligned and spaced apart from the wheel disc. A mold is created by a combination of the overlay, wheel disc and localized nests that engage at predetermined times during foam filling to close the mold. The mold is adequately sealed so that there is no foam leakage as the foam expands to fill the mold and, therefore, no final trimming of excess foam is required. The improved process is capable of accommodating a wheel having turbine openings therein.
Owner:LACKS INDUSTRIES INC
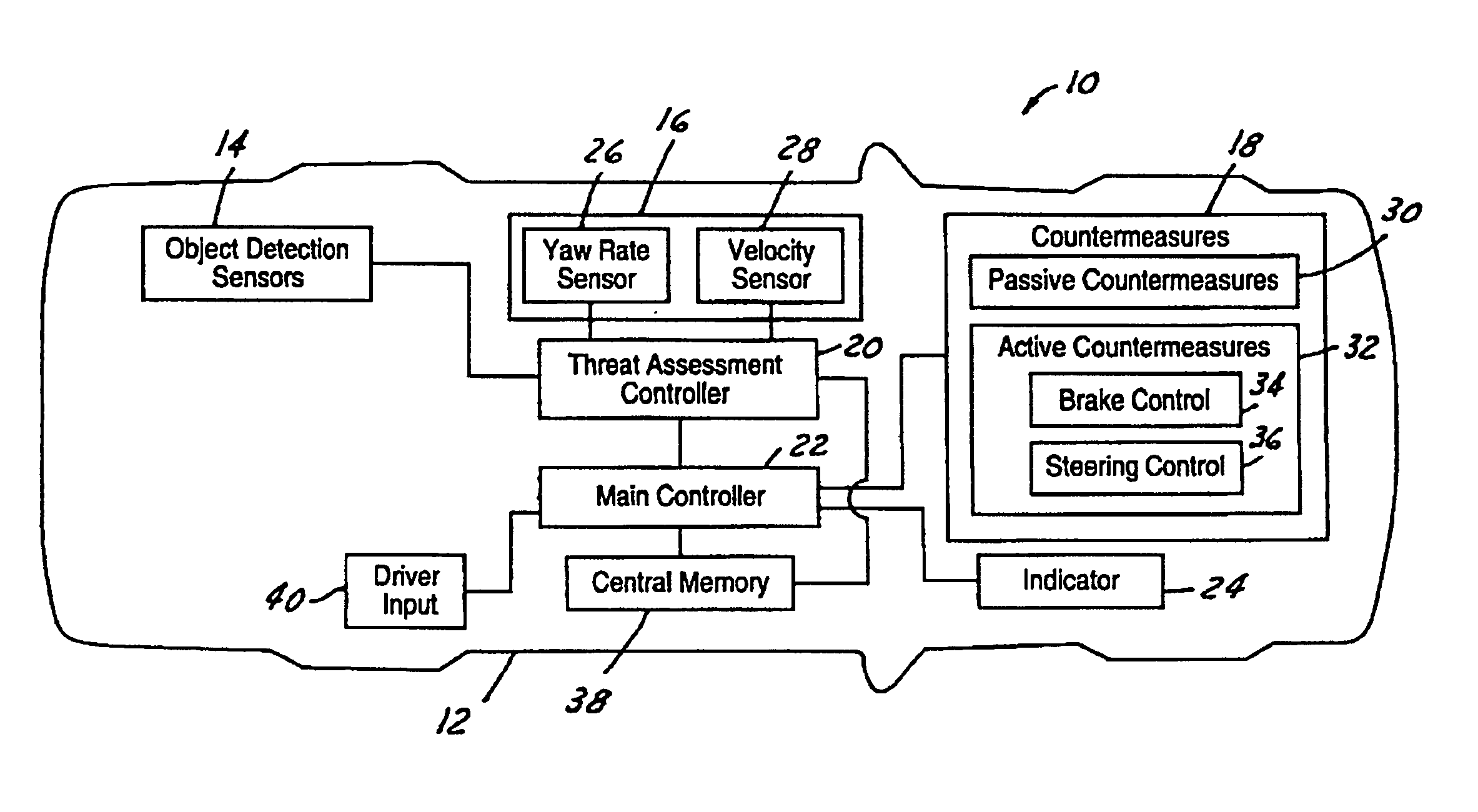
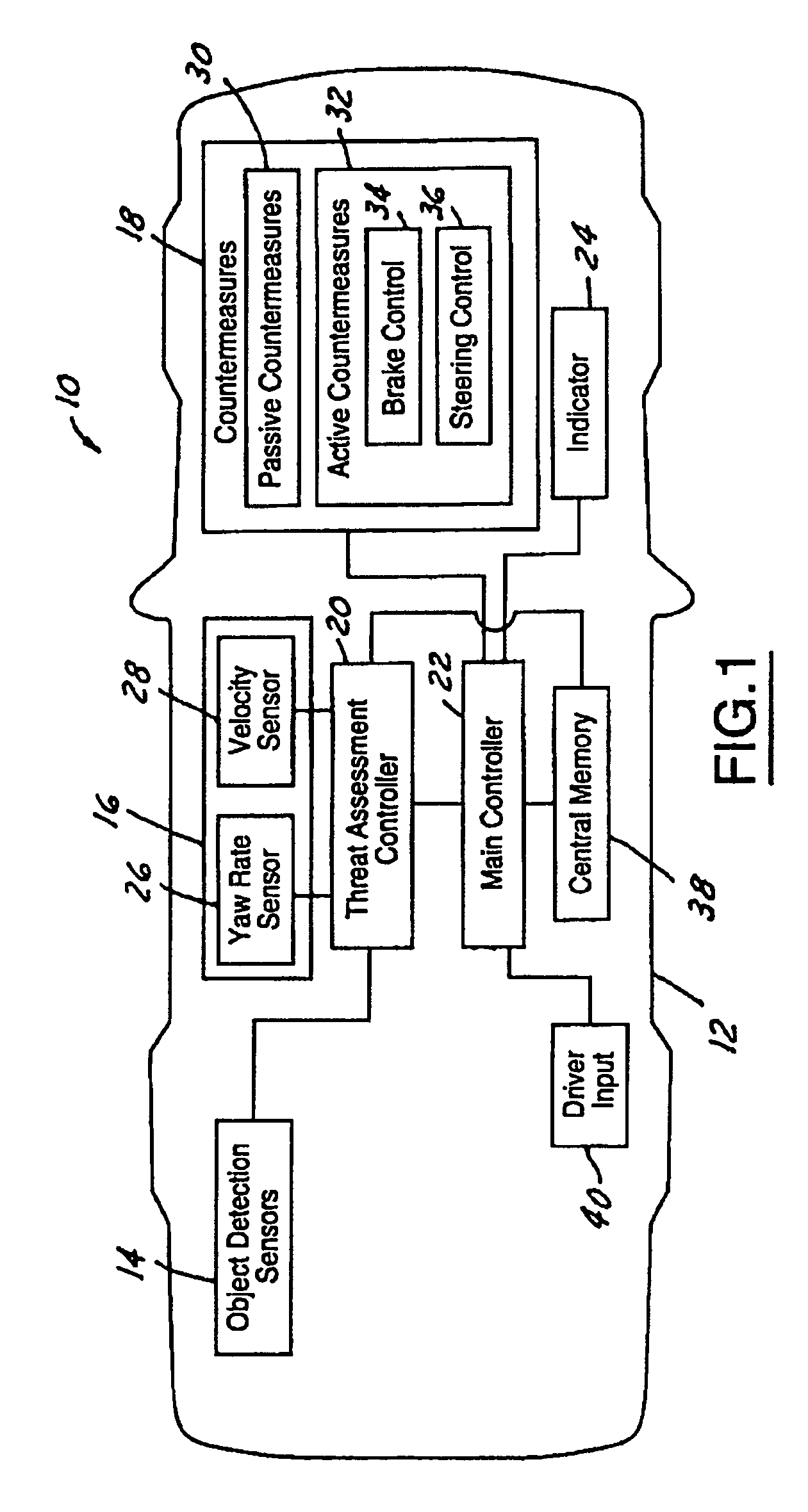
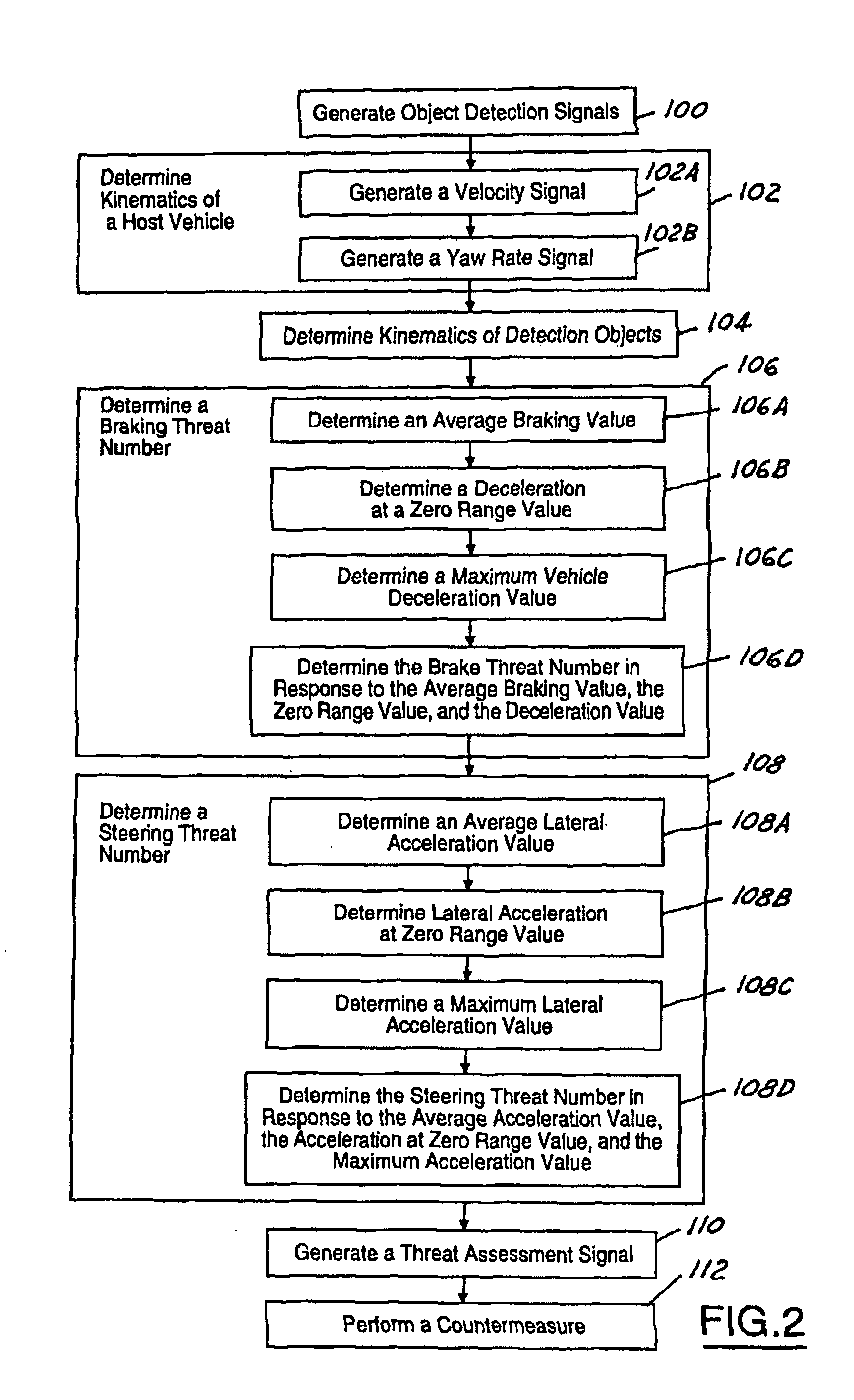
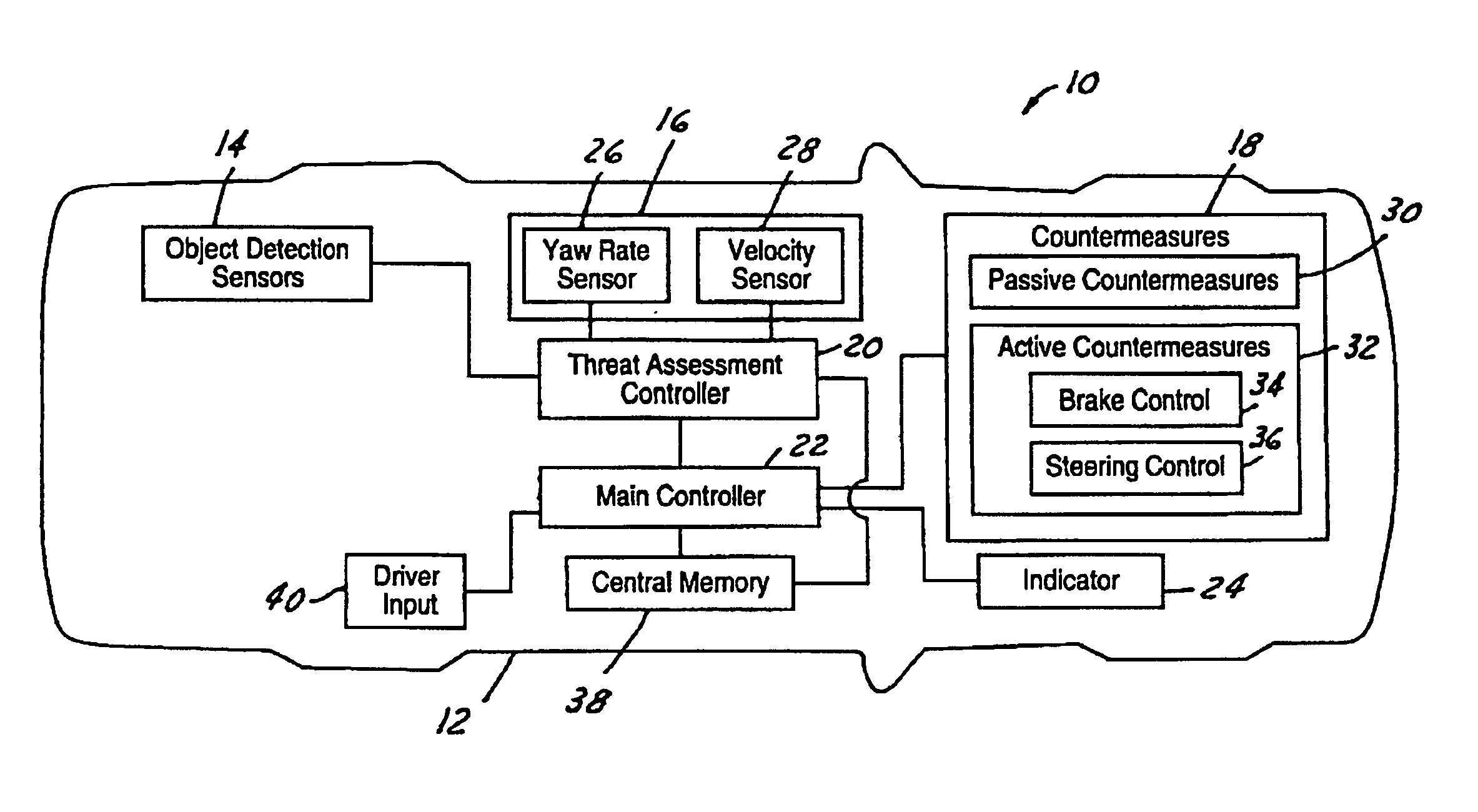
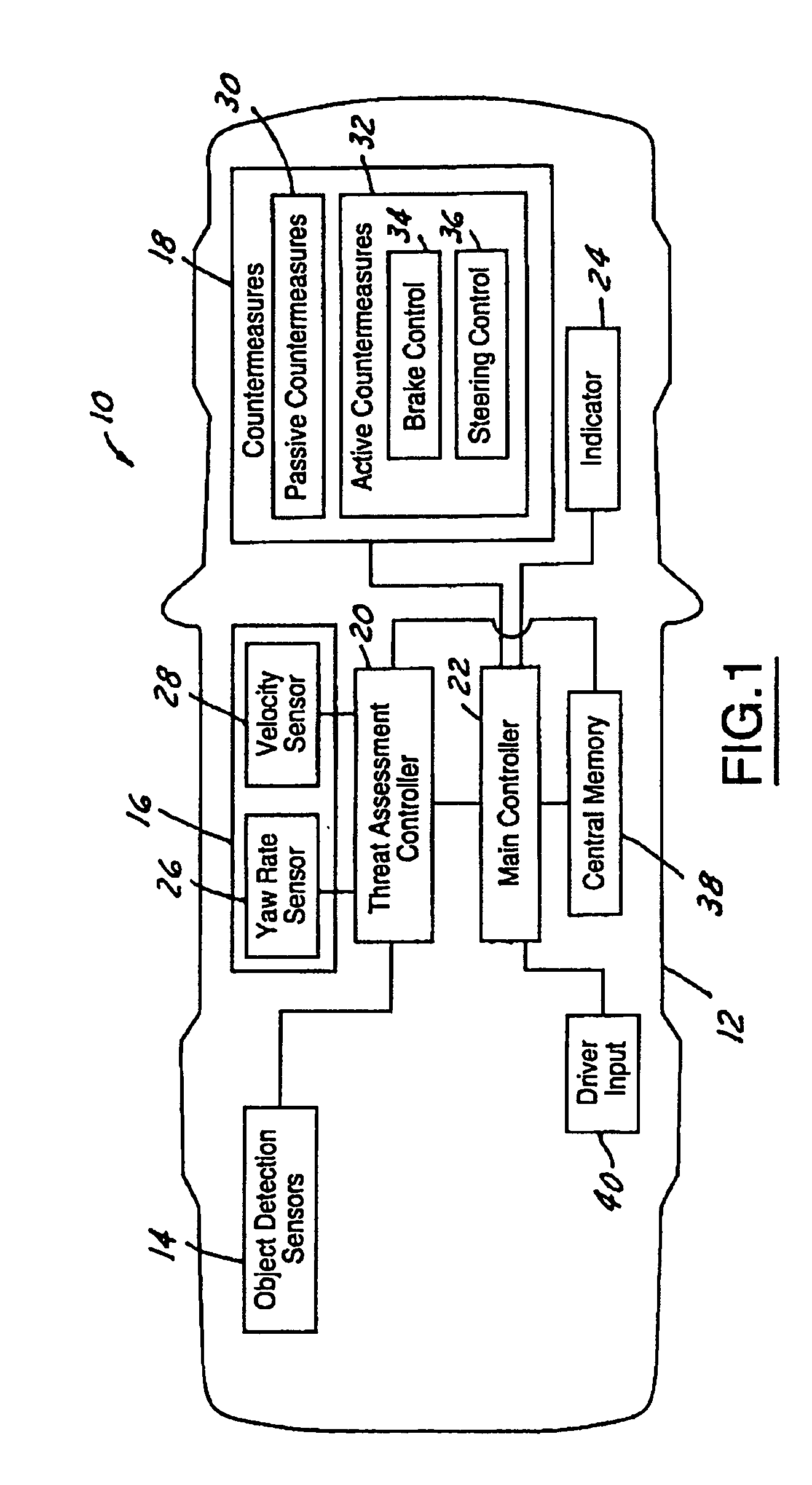
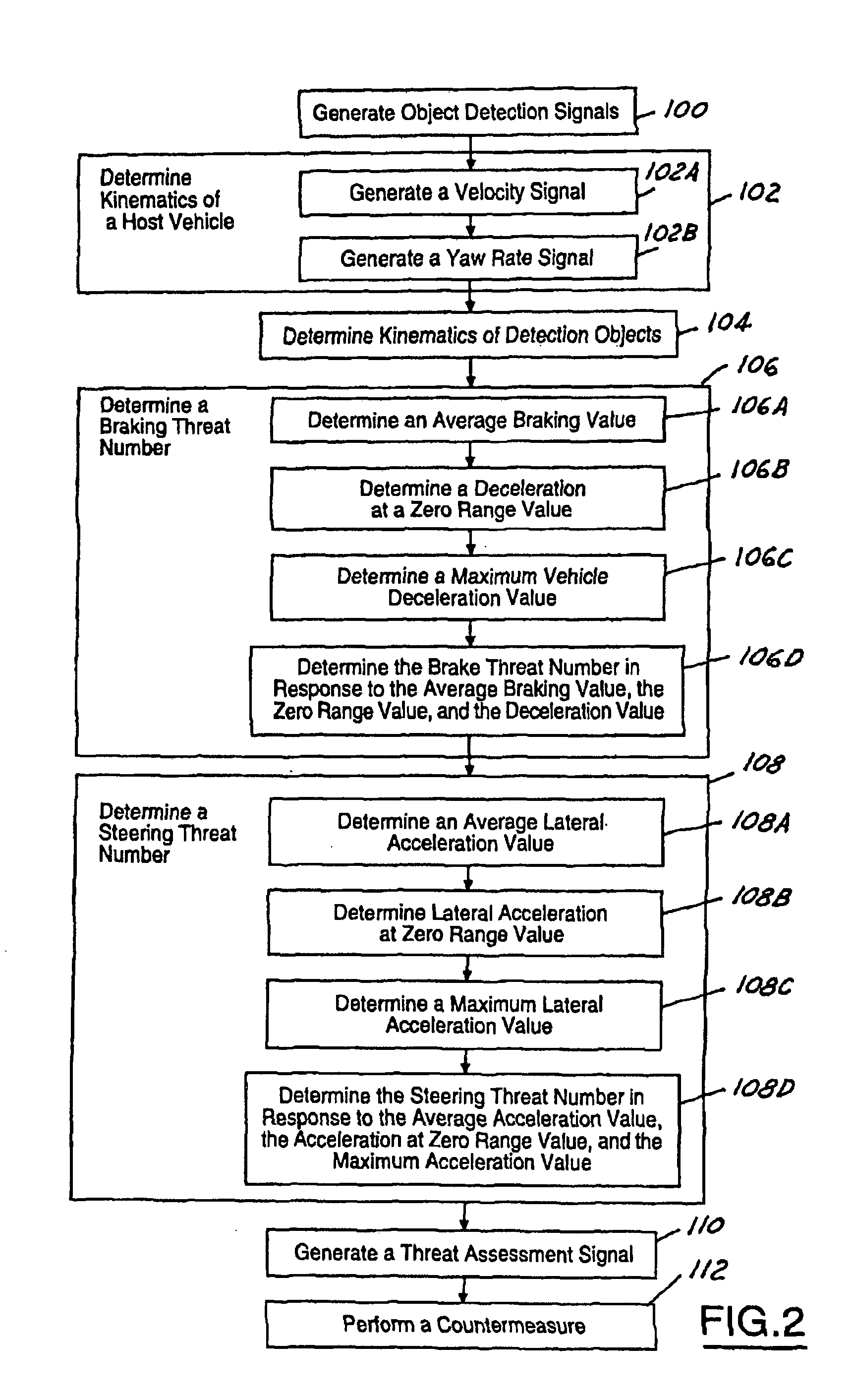
Threat level identification and quantifying system
ActiveUS7034668B2Technique is effectiveSimplifies threat assessmentBrake system interactionsDigital data processing detailsKinematicsEngineering
Methods of performing threat assessment of objects for a vehicle include detecting an object. Kinematics of the vehicle and of the object are determined. A brake threat number and a steering threat number are determined in response to the kinematics of the vehicle and the object. The threat posed by the object is determined in response to the brake threat number and the steering threat number.
Owner:FORD GLOBAL TECH LLC
Threat level identification and quantifying system
ActiveUS20050090955A1Efficient techniqueSimplifies threat assessmentBrake system interactionsDigital data processing detailsThreat levelKinematics
Methods of performing threat assessment of objects for a vehicle include detecting an object. Kinematics of the vehicle and of the object are determined. A brake threat number and a steering threat number are determined in response to the kinematics of the vehicle and the object. The threat posed by the object is determined in response to the brake threat number and the steering threat number.
Owner:FORD GLOBAL TECH LLC
Matching consumers with billers having bills available for electronic presentment
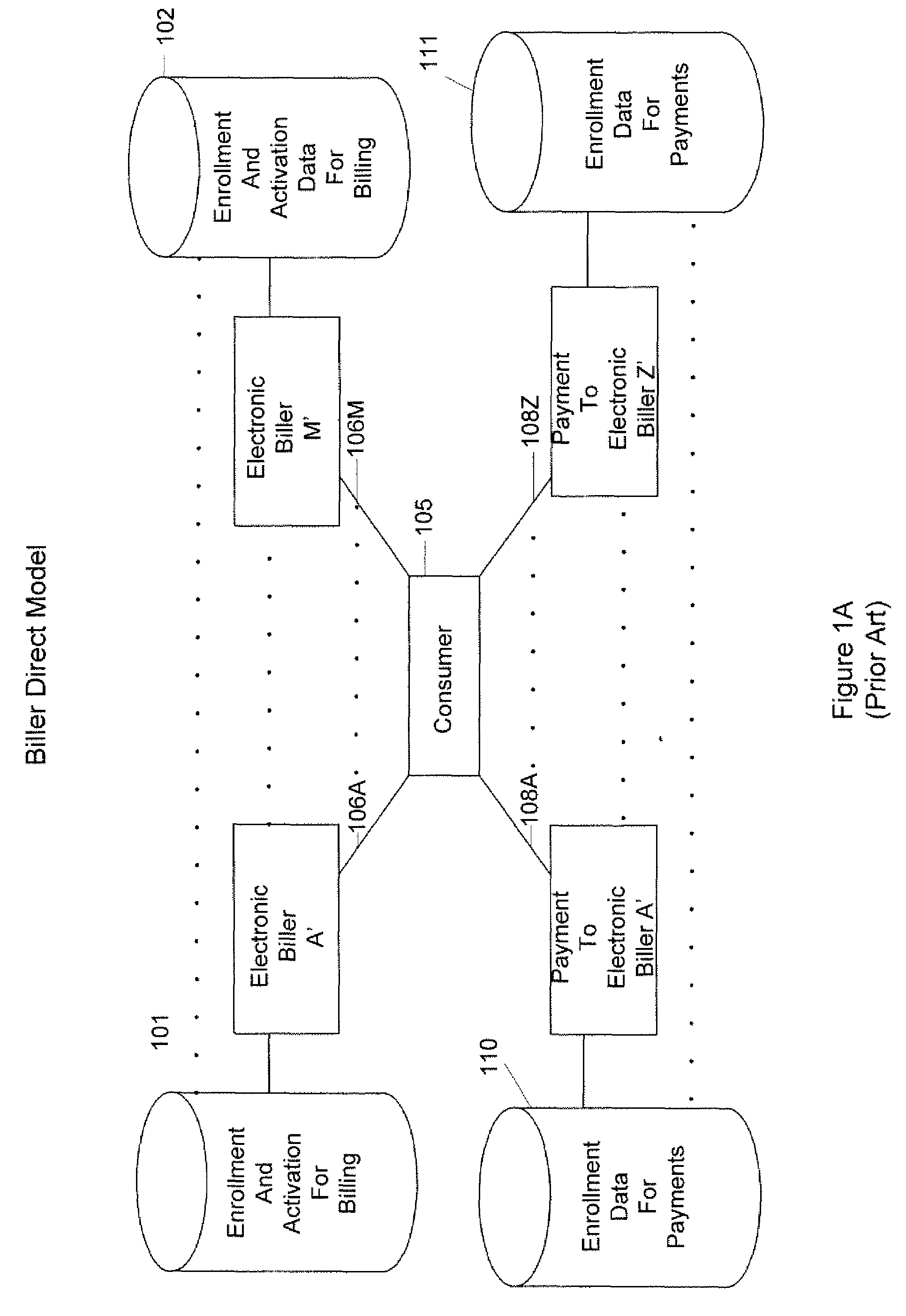
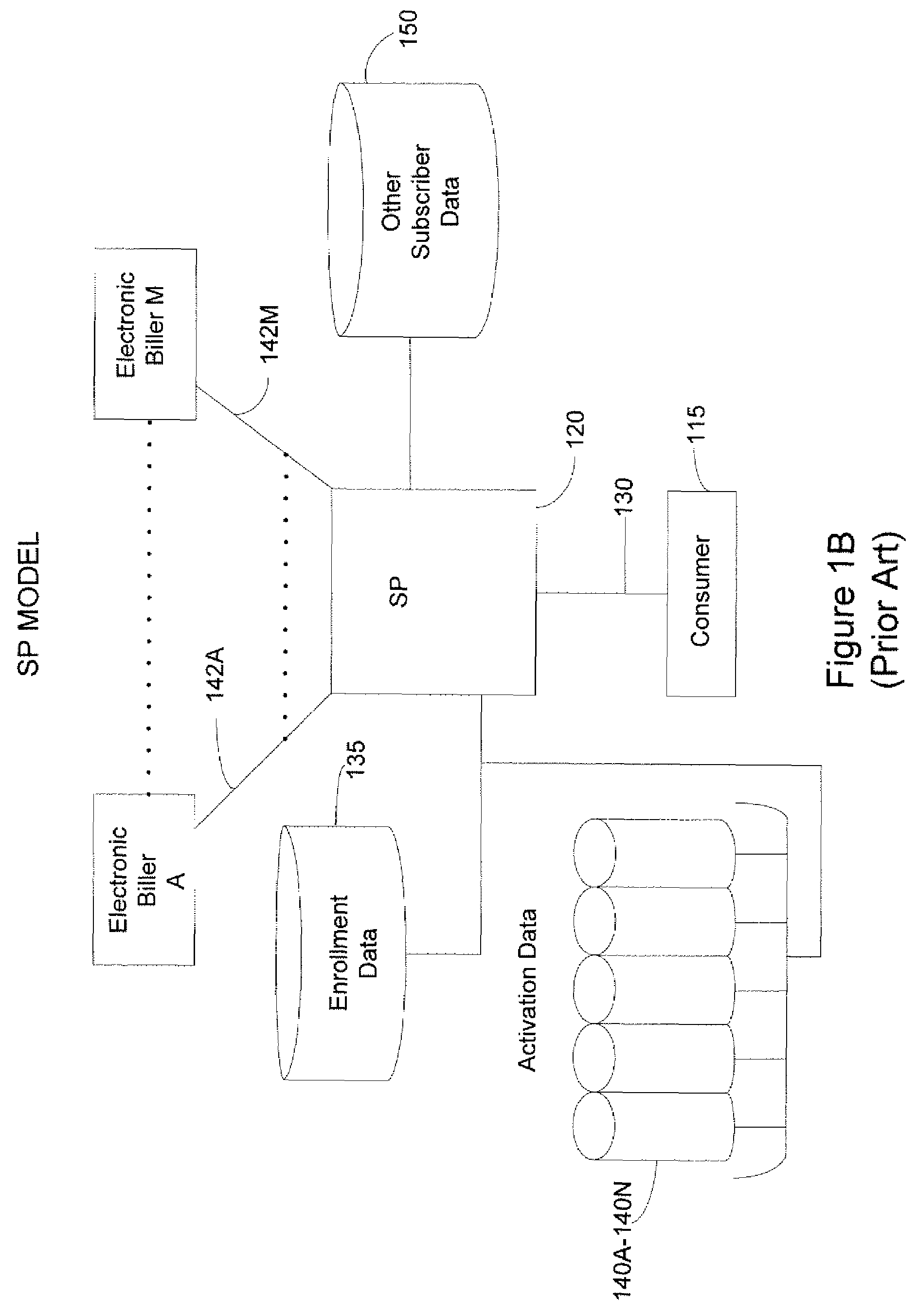
ActiveUS7526448B2Easy to implementEasy programmingAcutation objectsFinanceInformation retrievalElectronic records
A technique for identifying electronic billers of a consumer whose bills are available by electronic presentment is provided. A request to identify electronic billers of the consumer is received. This request includes information that identifies the consumer, but excludes any information identifying any biller, electronic or not, of the consumer. From this information that does not identify any biller of the consumer, one more candidate electronic billers of the consumer are identified. Then, a positive determination is made that at least one of these candidate electronic billers is definitely an electronic biller of the consumer. Thus, electronic billers of the consumer are identified without the consumer identifying any biller.
Owner:CHECKFREE SERVICES CORP
Method and apparatus for implementing efficient data dependence tracking for multiprocessor architectures
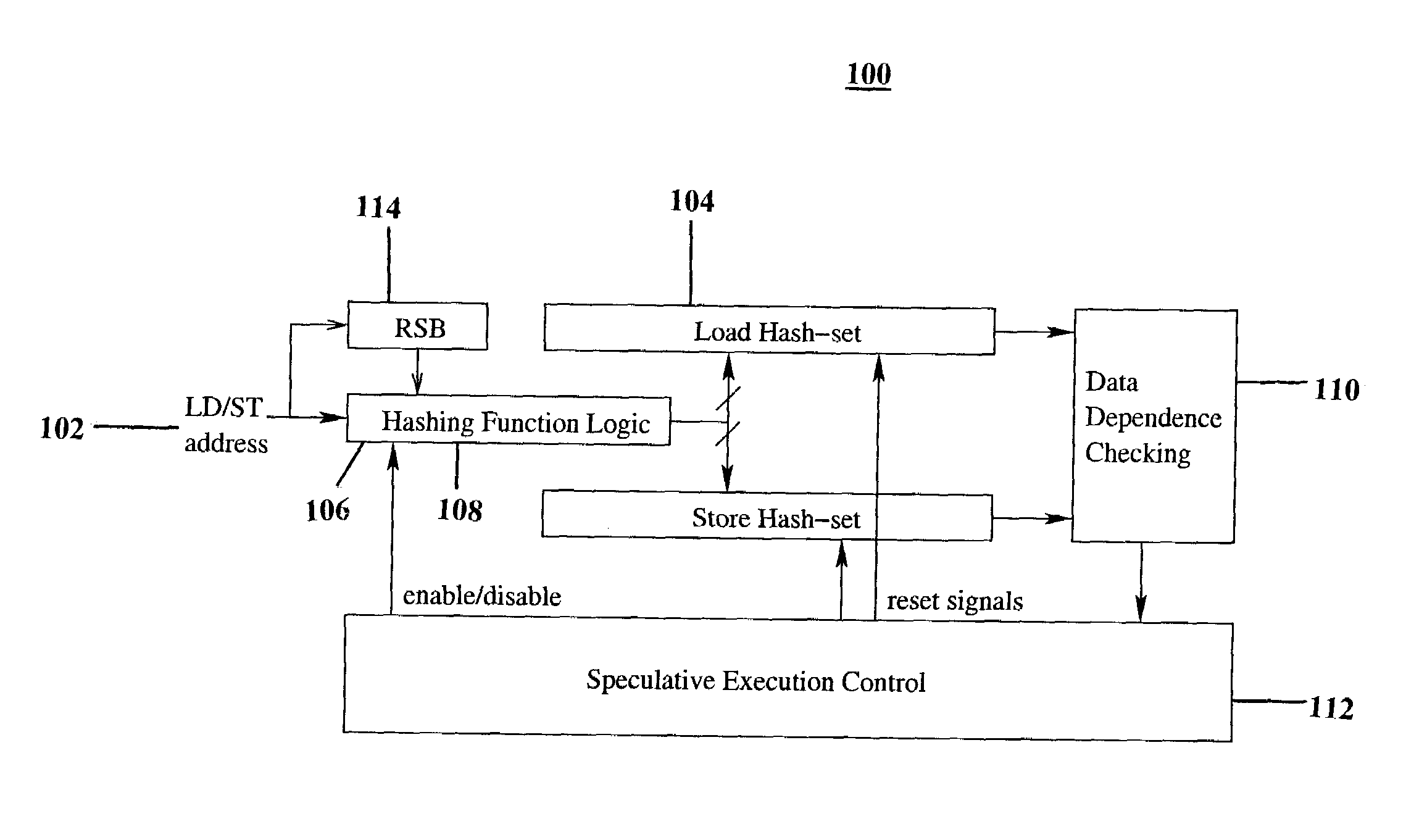
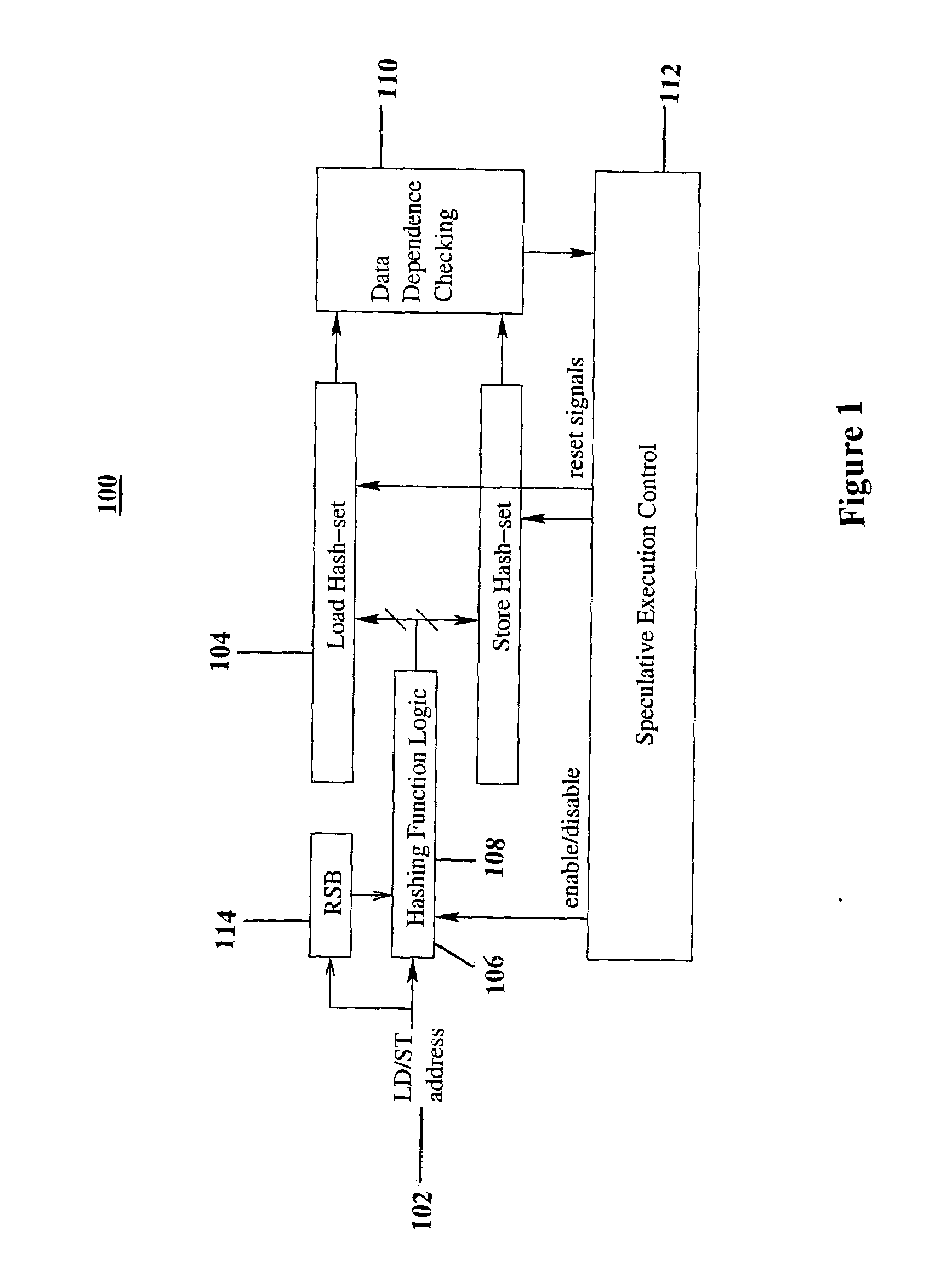
InactiveUS20080162889A1Simple and efficientEasy to controlDigital computer detailsMemory systemsData dependenceMultiprocessor architecture
A system for tracking memory dependencies includes a speculative thread management unit, which uses a bit vector to record and encode addresses of memory access. The speculative thread management unit includes a hashing unit that partitions the addresses into a load hash set and a store hash set, a load hash set unit for storing the load hash set, a store hash set unit for storing the store hash set, and a data dependence checking unit that checks data dependence when a thread completes, by comparing a load hash set of the thread to a store hash set of other threads.
Owner:IBM CORP
Method and means for tolerating multiple dependent or arbitrary double disk failures in a disk array
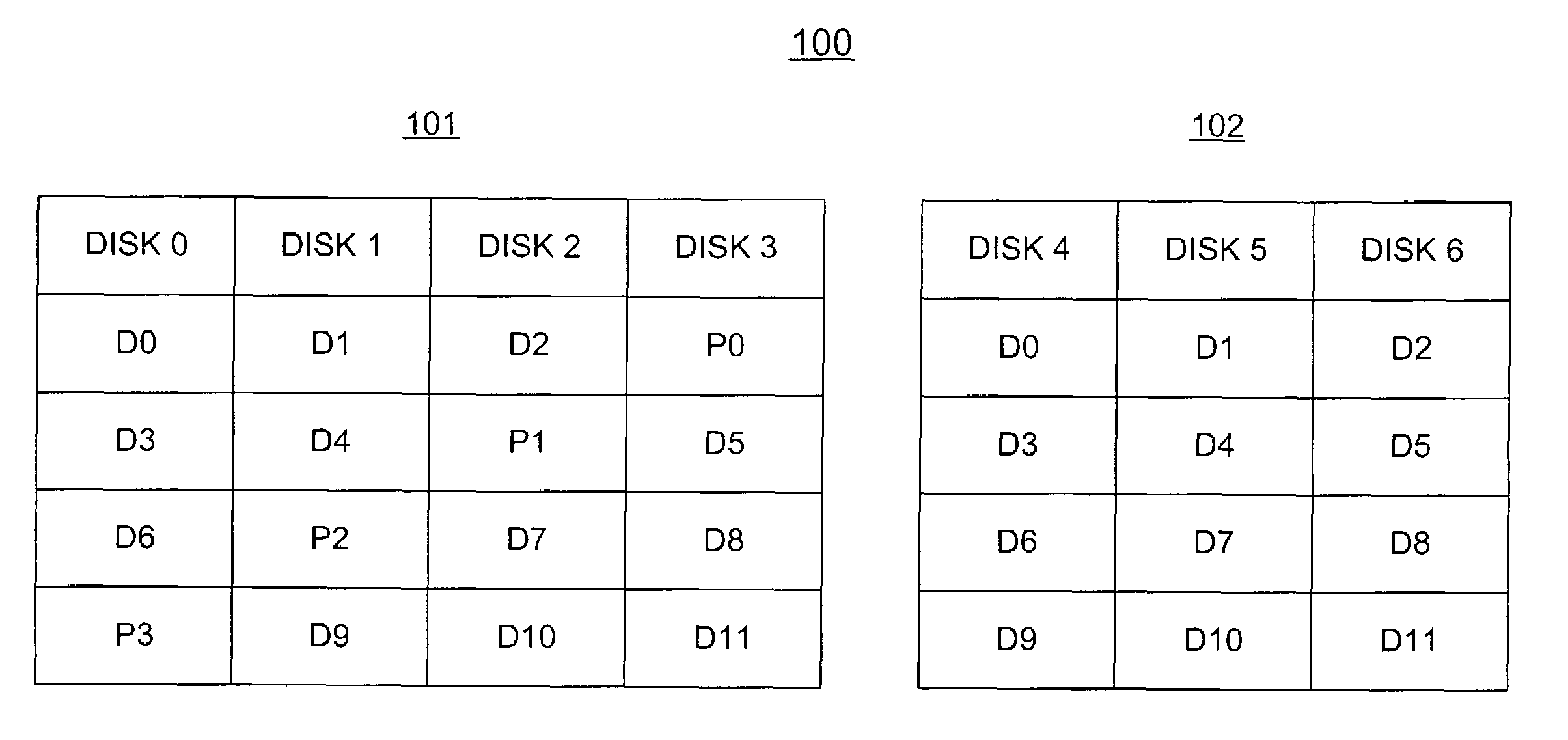
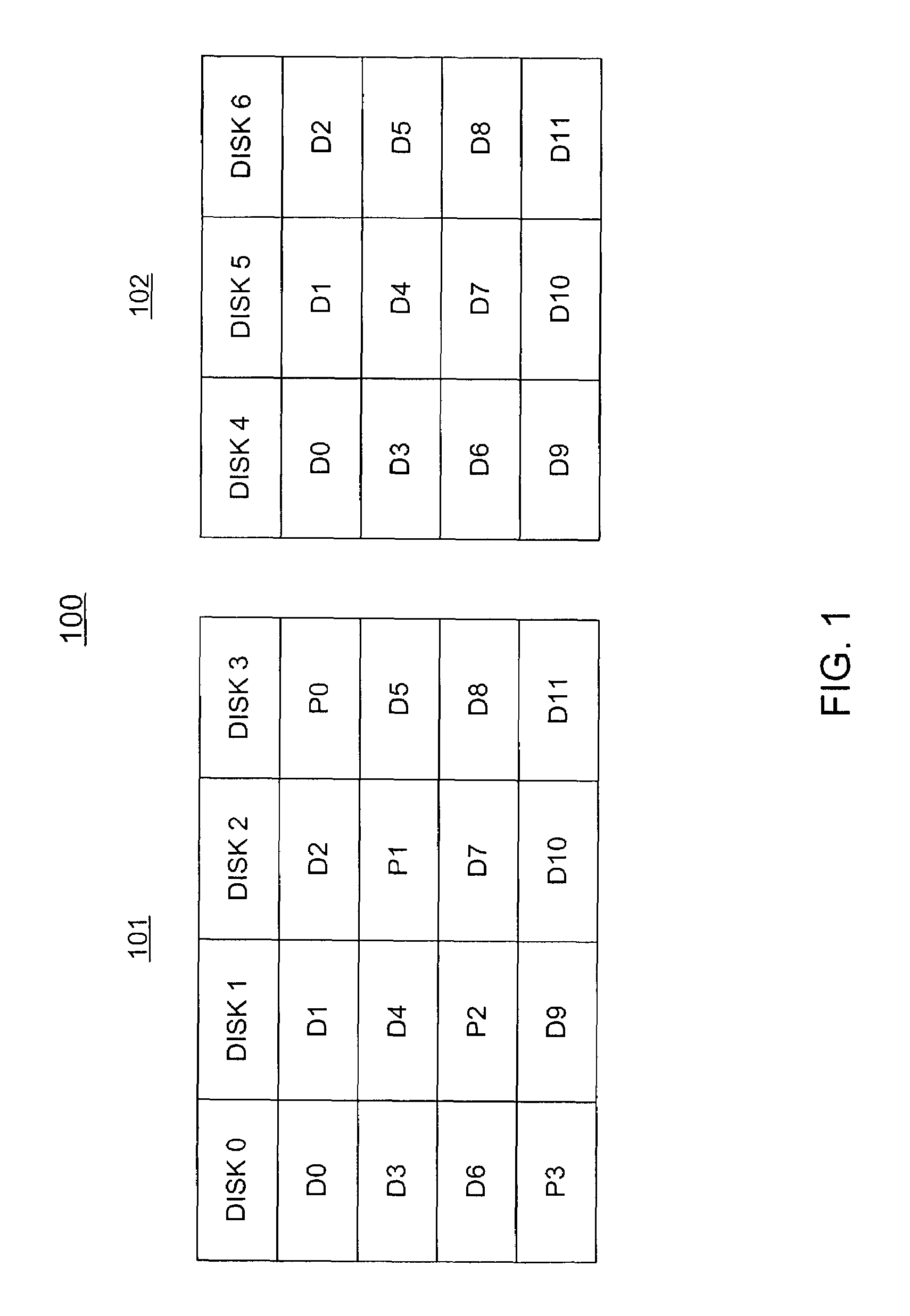
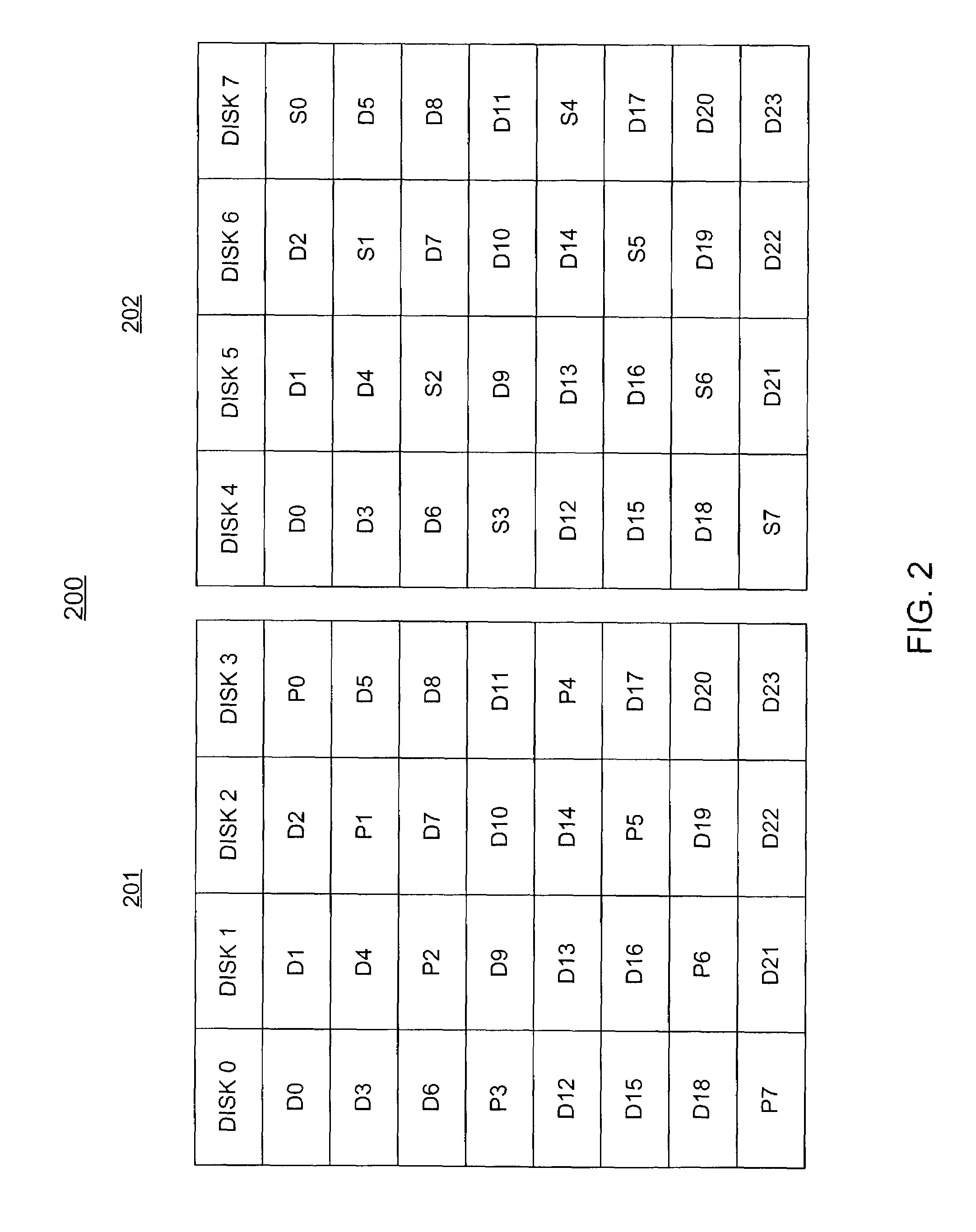
Stored data can be recovered from a disk array having at least 2n+1 physical disks that are capable of storing n physical disks worth of data when any two disks fail, or when more than two dependent disks fail. Data is stored in data stripes that are divided into n substantially equal-sized strips and are distributed across the n disks. Each data stripe has a corresponding parity strip that is generated by including the data strips in the data stripe only once when the parity strip is generated. The data strips of each data stripe, the copy of each such data strip and the corresponding parity strip are distributed across the disks in such a manner that the data strips of each data stripe, the copy of each such data strip and the corresponding parity strip are each on a respectively different disk of the disk array.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com