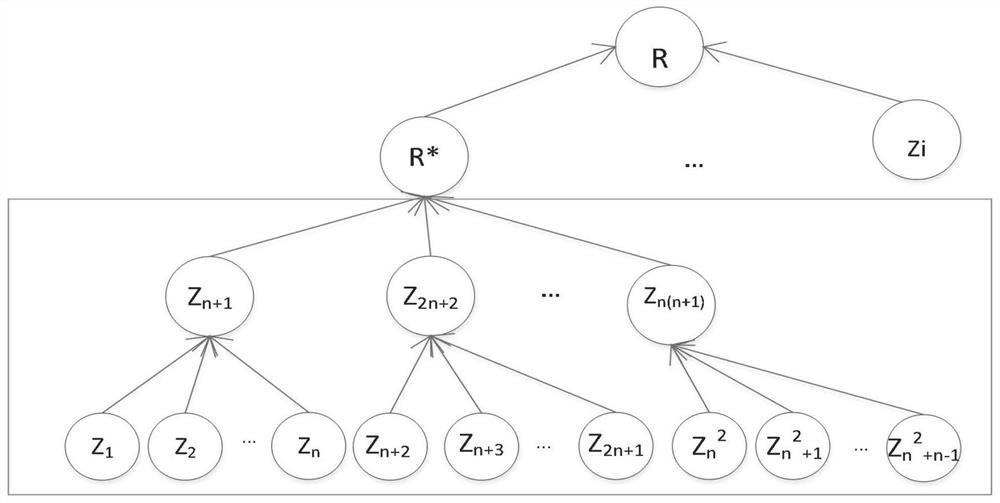
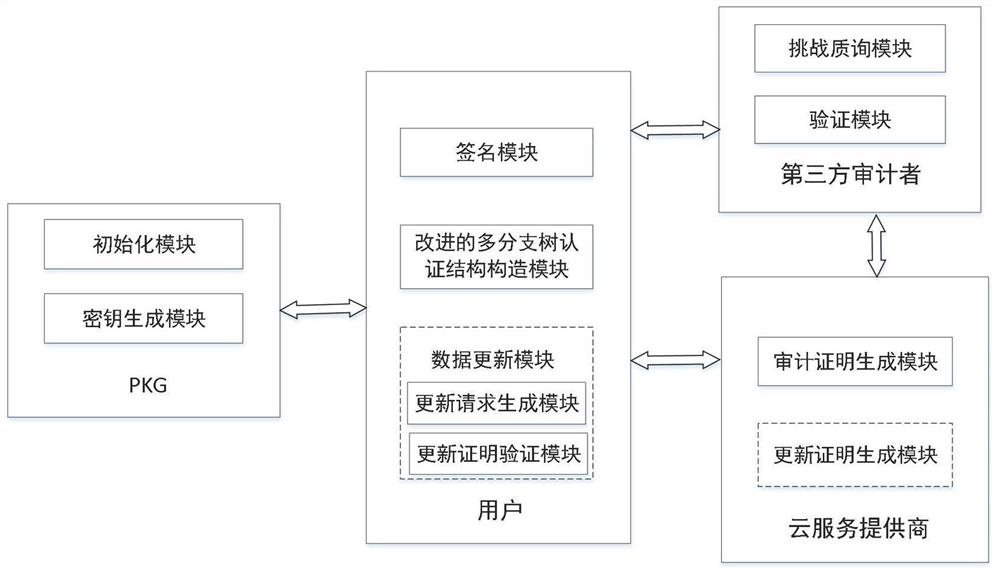
Integrity dynamic auditing method based on improved multi-branch tree in cloud environment
A multi-branch, cloud environment technology, applied in computing, digital data protection, instruments, etc., can solve the problem of data block query taking a long time, increasing the cost of users and third-party auditors, and excessive auxiliary information, etc. Shorten the length of the authentication path, improve the node utilization, and improve the effect of dynamic update
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
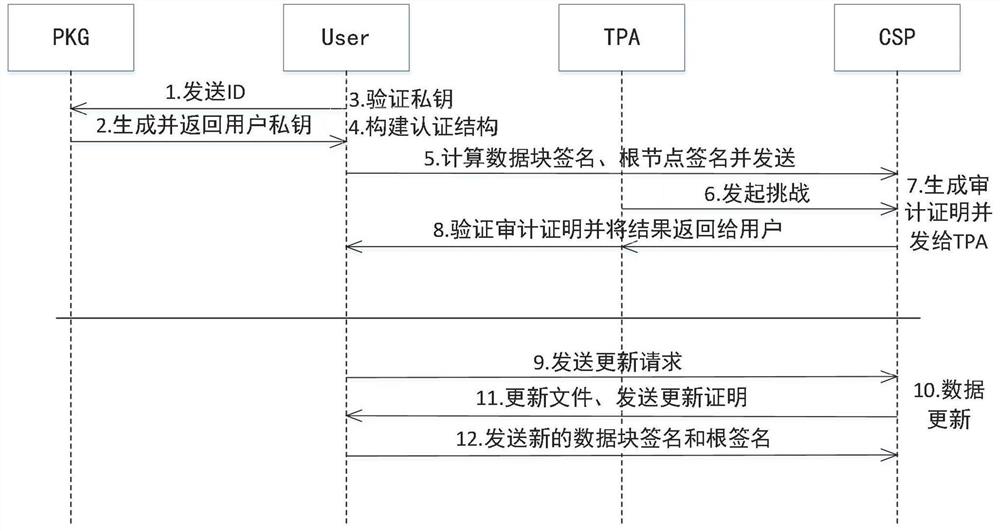
[0037] The specific implementation process of the identity-based data integrity dynamic audit method of the present invention is as follows: figure 2 shown, including the following steps:
[0038] Step 1: The user sends his user identity ID to the key generator PKG.
[0039] Step 2: Private key generation.
[0040] (1) PKG performs system initialization, and generates system public parameter PP and master key msk with a security parameter λ as input.
[0041] (2) PKG generates the corresponding private key for the user according to the identity information provided by the user, takes the public parameter PP, master key msk and user ID as input, outputs the private key skID corresponding to the ID and sends it through a secure channel to the user.
[0042] Step 3: Private key verification.
[0043] The user receives the private key sent by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com