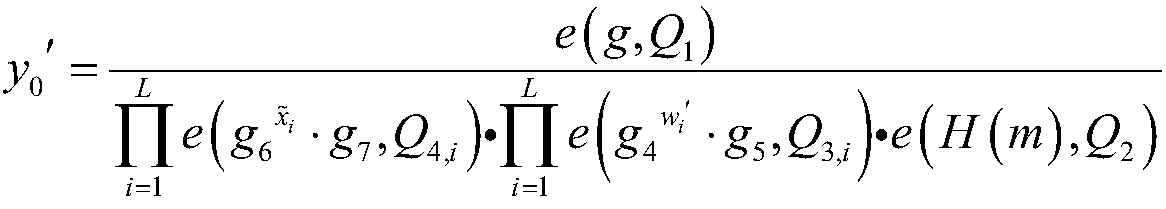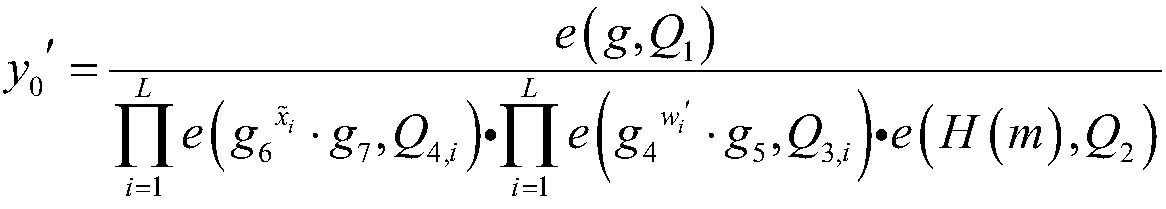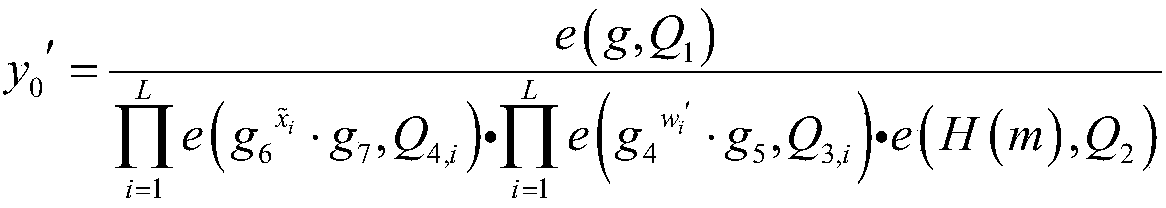Attribute base network signature method supporting dynamic attractive space
An attribute space and attribute-based technology, which is applied to public keys for secure communications, encryption devices with shift registers/memory, and key distribution, can solve problems such as inflexible use and inability to independently define message access structures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0054] A specific embodiment of the present invention is an attribute-based network signature method supporting dynamic attribute space, the steps of which are:
[0055] A. Parameter generation
[0056] A1. Generation of system public key and private key
[0057] The system respectively constructs the q-factorial method cyclic group G and the q-factorial method cyclic group Y, and there is a bilinear mapping relationship y=e(g a , g b ); where q is greater than 2 512 , y is an element in the cyclic group Y of q factorial method, e(g a , g b ) represents the element g in the cyclic group G of the q factorial method a and element g b Perform bilinear mapping operations;
[0058] The system randomly selects a number from the integers 1 to q as the system's master key α; the system randomly selects the generator g of the cyclic group G of the q factorial method 1 As the system's first public key g 1 , and then get the second public key g of the system 2 , The system th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com