Key management method based on wireless Mesh netword
A key management and key technology, applied in key distribution, can solve the problems of system performance bottleneck, single point of failure, message length and large amount of cryptographic operations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
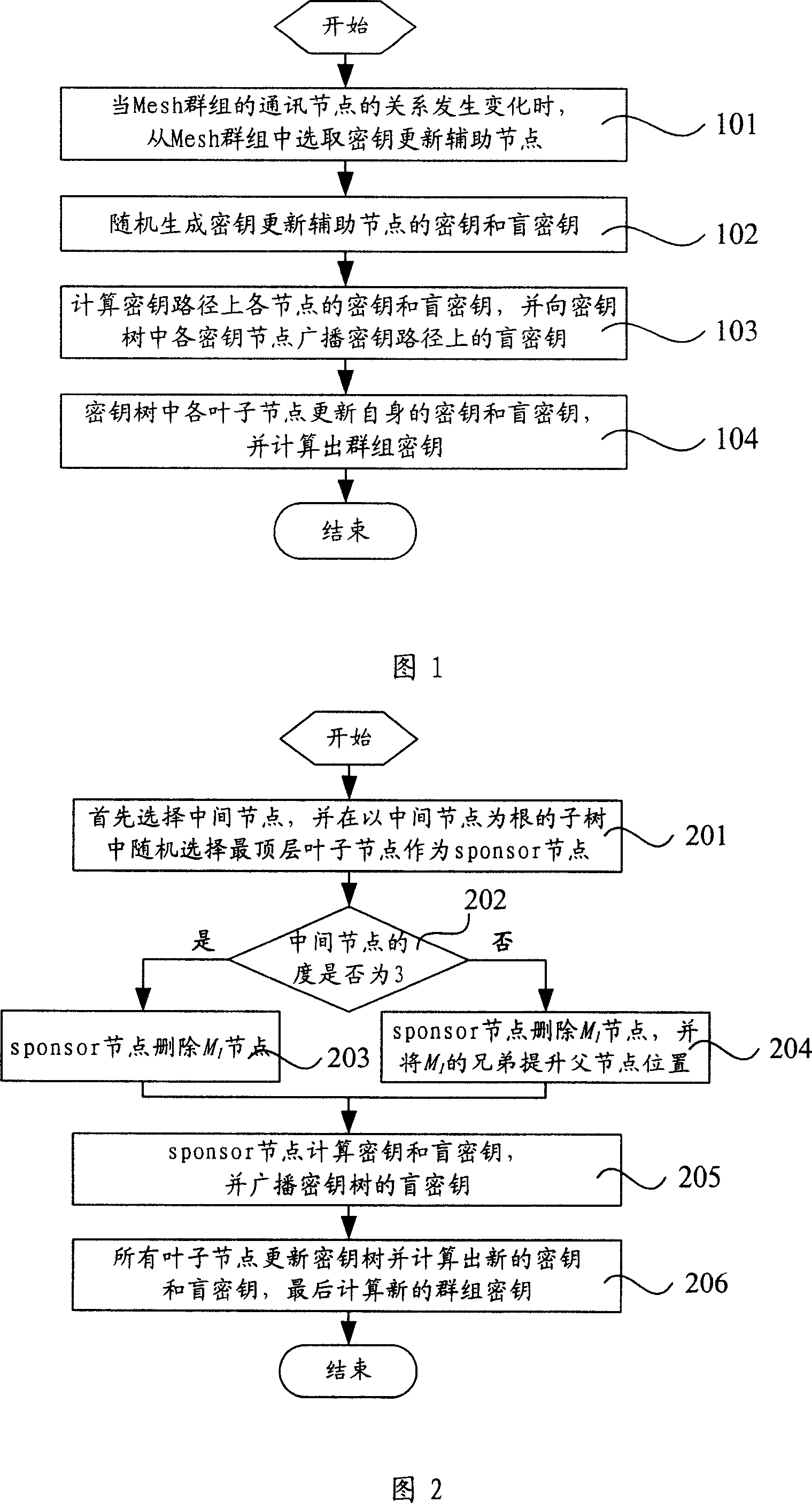
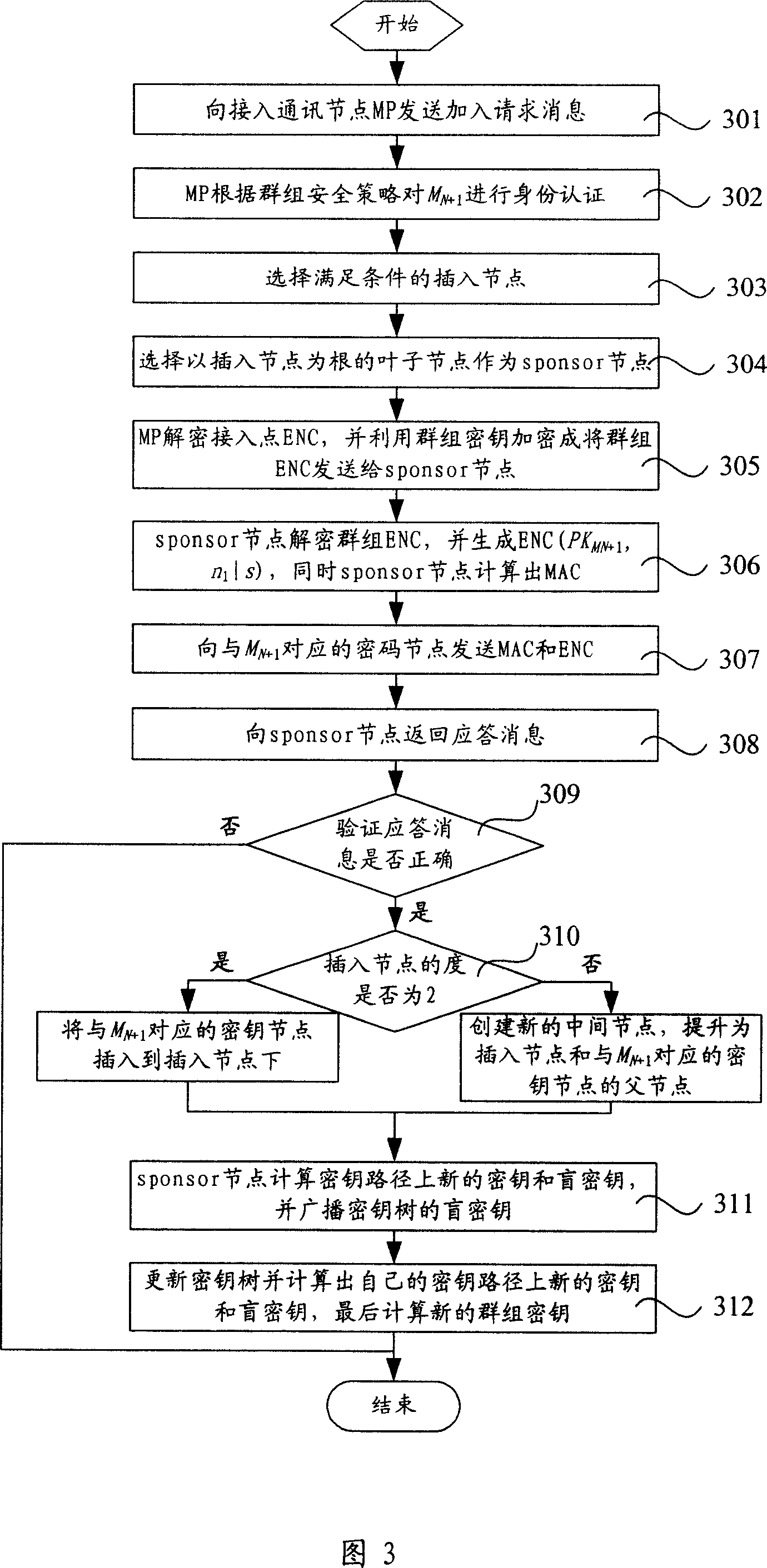
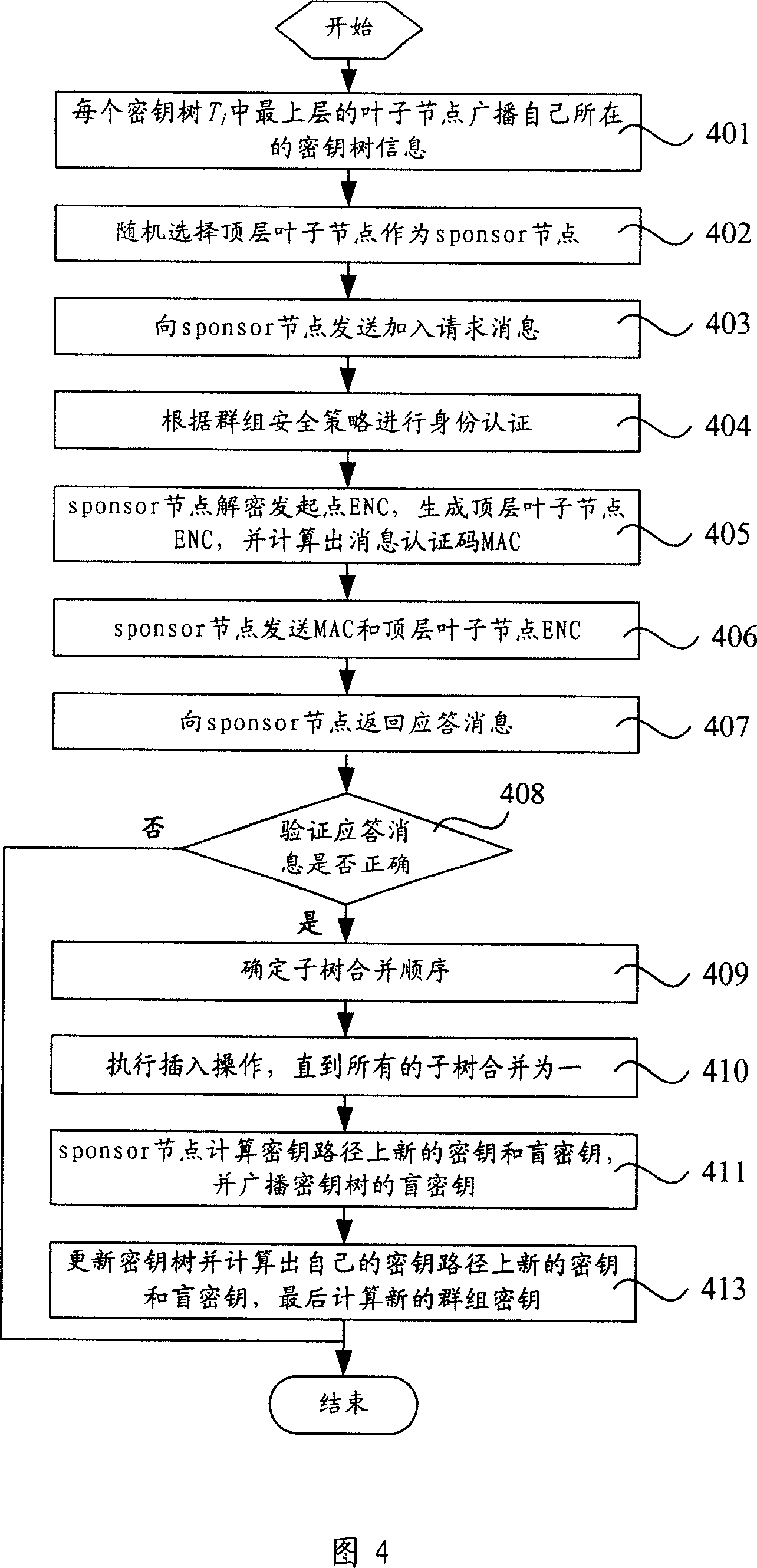
[0095] The free movement of nodes in the wireless Mesh network will lead to changes in the relationship between group nodes. Generally, there are four ways for node changes: member leaves, that is, the communication node leaves the Mesh communication group or is expelled from the Mesh communication group; member joins, that is, authorizes the communication node Join a Mesh communication group; Group merge, some communication subgroups merge into one communication group; Group split: Some communication subgroups are separated from the overall Mesh communication group.
[0096] When the relationship between the communication nodes of the Mesh group changes, the technical solution provided by the present invention should be able to deal with the node relationship change event accordingly. When a member join / member leave / group merge / group split event occurs, the original group key should be updated to ensure that the leaving member / group cannot access the current communication cont...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com