VoIP safety meeting session key transmission method
A conference session and key technology, which is applied in the field of secure conference session key transmission, can solve the problems of no secret at all, complicated process, no VoIP security conference signature authentication, etc., to ensure confidentiality and integrity, and reduce communication costs Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention is described more fully below in conjunction with accompanying drawing:
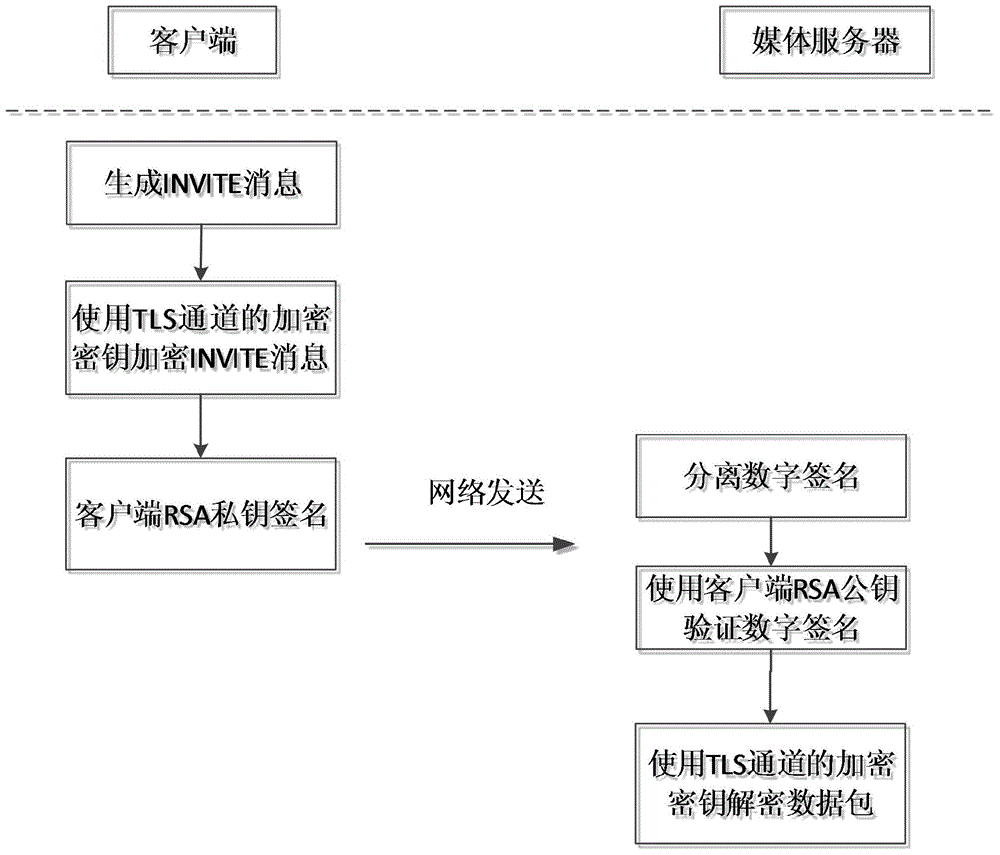
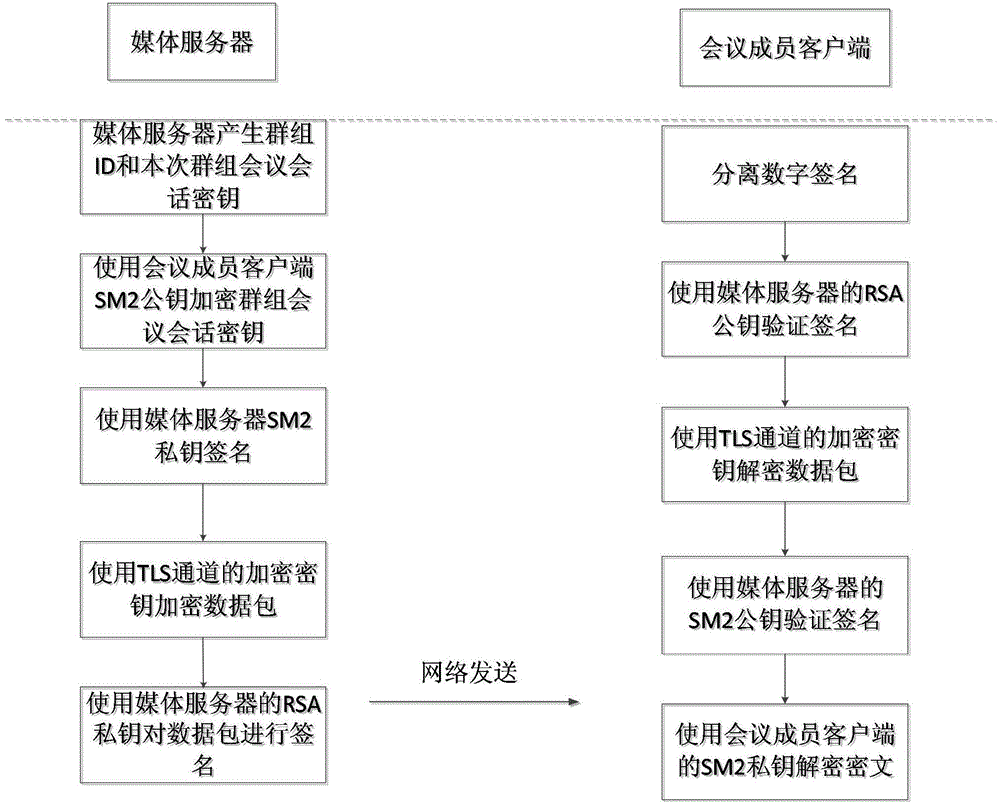
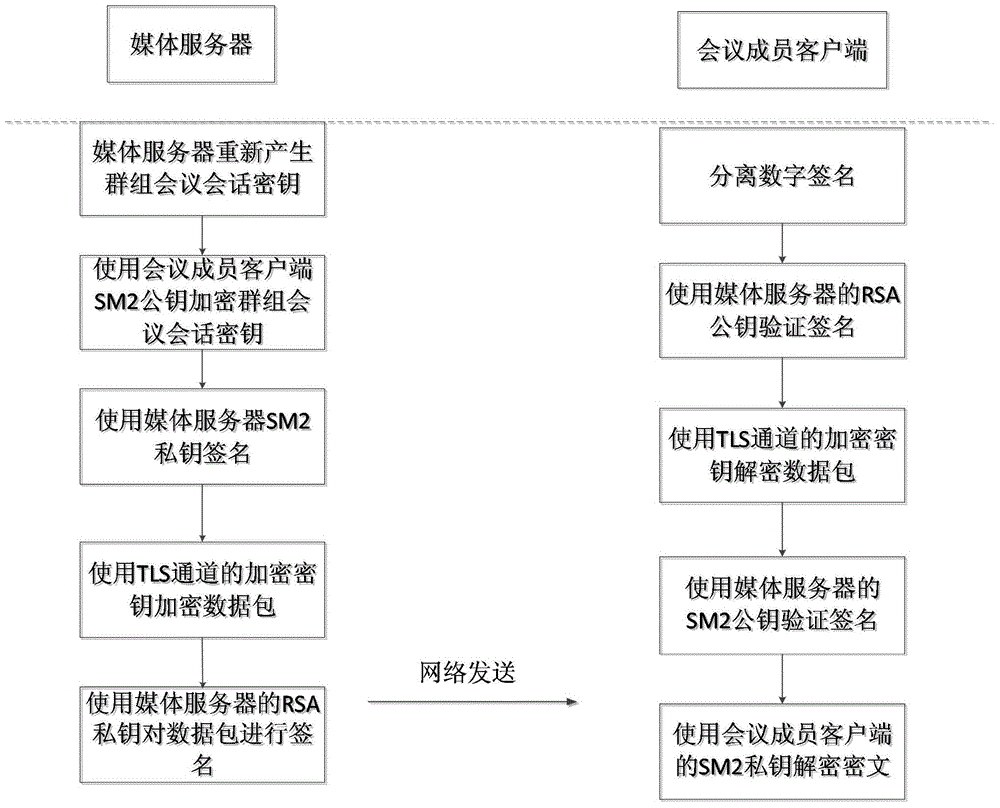
[0036] The present invention is a method applicable to mobile terminal VoIP secure conference session key transmission, including four stages: signaling security transmission stage, group conference session key transmission stage, group conference session key update stage and data security In the transmission stage, the TLS protocol is used to protect the signaling data in the first stage, and the two-layer encryption method of the RSA public key algorithm and the SM2 public key algorithm is used in the second stage to protect the transmission of the group meeting session key. The media server regenerates the session key of the group meeting at regular intervals, and distributes it to the clients of each meeting member. In the fourth stage, SRTP protocol and digital signature are used to protect the transmitted voice data.
[0037] Such as figure 1 As shown, in the signaling...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com