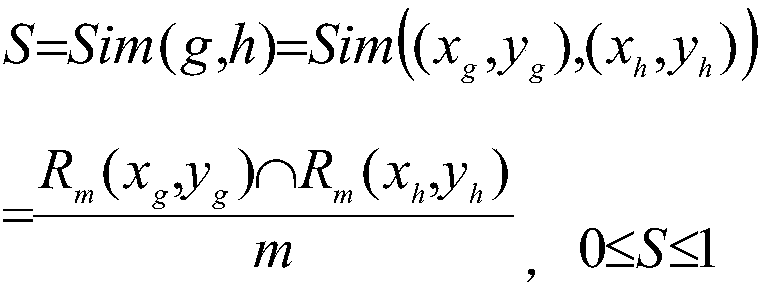Patents
Literature
160results about How to "Reduce the number of queries" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
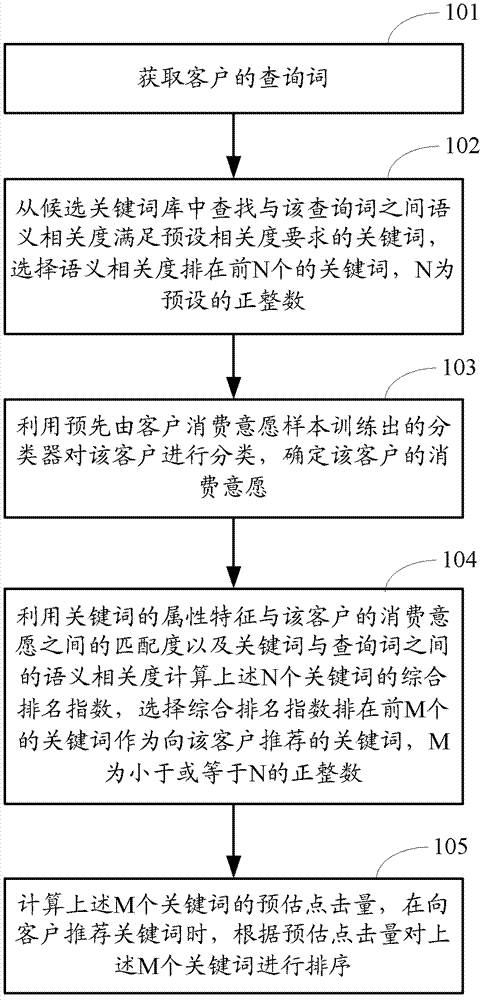
Method and device for recommending keyword
ActiveCN103092877AConsumption Willingness SatisfactionReduce the number of queriesMarketingSpecial data processing applicationsRanking indexData mining
The invention provides a method and device for recommending a keyword. The method comprises the steps of: obtaining a search term of a customer; classifying the customer by utilizing a classifier trained through consuming willingness samples of customers in advance, and determining the consuming willingness of the customer; and selecting the front M keywords from a candidate keyword library according to a comprehensive ranking index to serve as the keywords recommended to the customer, wherein the comprehensive ranking index of the keywords is calculated by utilizing a matching degree of attributive characteristics of keywords and consuming willingness of the customer and semantic relevancy between the keywords and the search item, and the M is a preset positive integer. The method and device for recommending the keyword can save recommendation resource and improve recommendation success rate.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
SDN resource matching and service path discovering method based on rumor spreading mechanism
InactiveCN105024853AEasy to findEfficient resource allocationNetworks interconnectionResource poolPathPing
The invention relates to an SDN resource matching and service path discovering method based on a rumor spreading mechanism. In the method, underlying physical network resources register access and control information including physical resource state and attribute in a virtual resource pool, so that virtual resources can be managed globally, and access interface can be called; when service resources make request at the same time, the rumor spreading mechanism of high priority is provided, and the network effectiveness and gain are improved; the distribution amount of node and chain resource request is detected in real time, and a node traversal search algorithm of high priority is used to determine an effective node candidate set that satisfy requirements for service resource; and according to the bandwidth requirements for inks at the two ends of node and the limitation of path hops, an effective path set is calculated, and thus, the whole process of resource search and service path discovery is realized. The method of the invention can improve the efficiency of service resource and path discovery, and improve the gain of the virtual network and the utilization rate of resources.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
IP address list storage and query method applied to DNS query
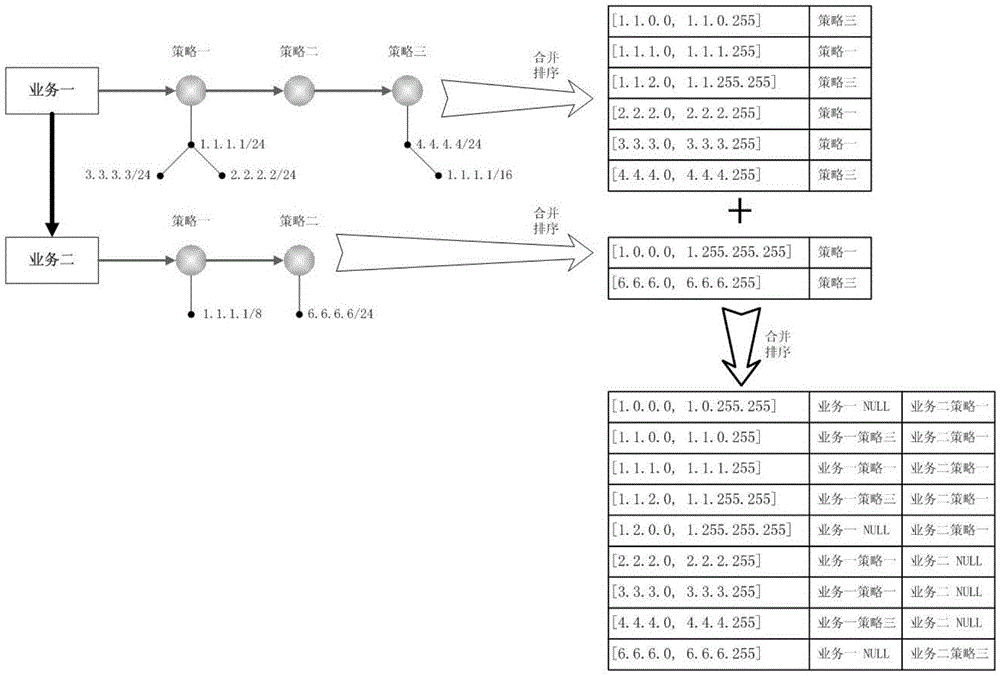
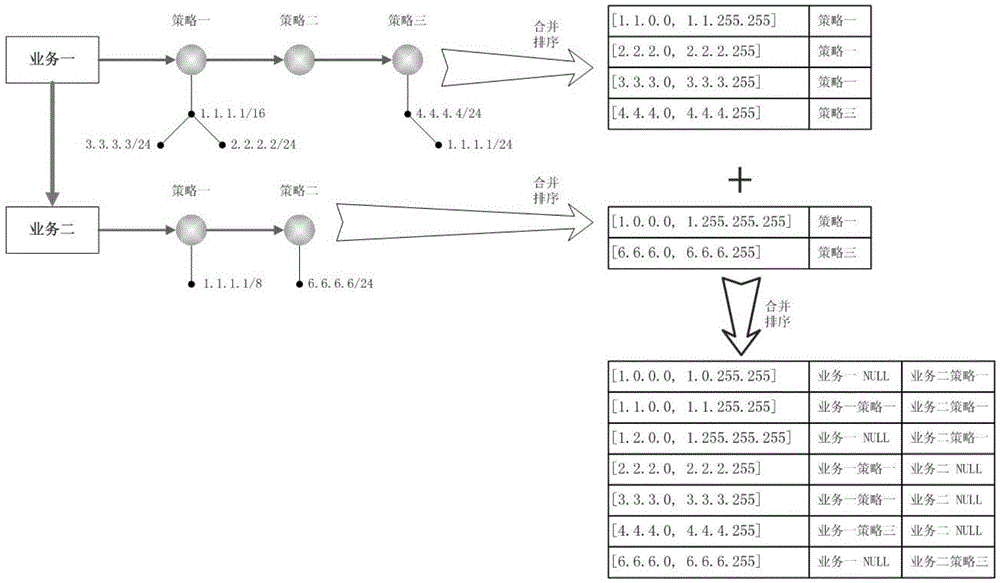
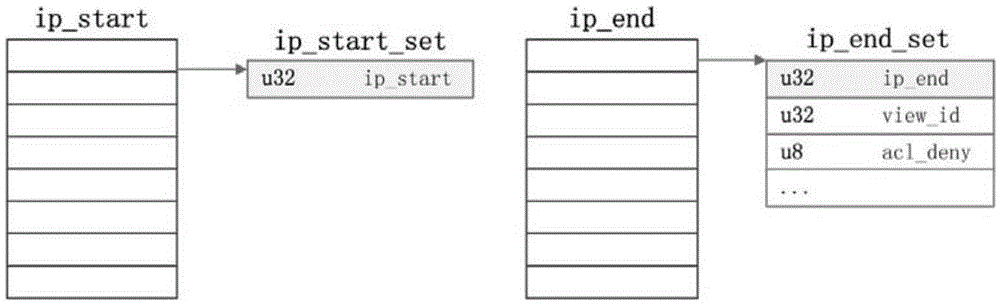
ActiveCN105635343AReduce the number of queriesReduced impact on query timeTransmissionArray data structureIp address
The invention relates to an IP address list storage and query method applied to DNS query. The method comprises the following steps: firstly carrying out deduplication processing on the IP address list of each strategy, and storing by using modes of a red black tree, an array, a linked list and the like; and then combining the IP address lists of different strategies of each service to construct an IP address list+strategy form and storing, following an IP longest matching principle or a priority principle in the combination process; and continuously combining the IP address list+strategy storage structures of different services to construct and store an IP address list+service+strategy form; sorting the IP address list+service+strategy storage structures according to IP address list initial address sizes; and performing the DNS query by using dichotomy and the like query method while in query. Through the adoption of the method provided by the invention, the existing IP storage structure is improved, the operation is simple, the query time can be reduced, and the query efficiency is improved.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
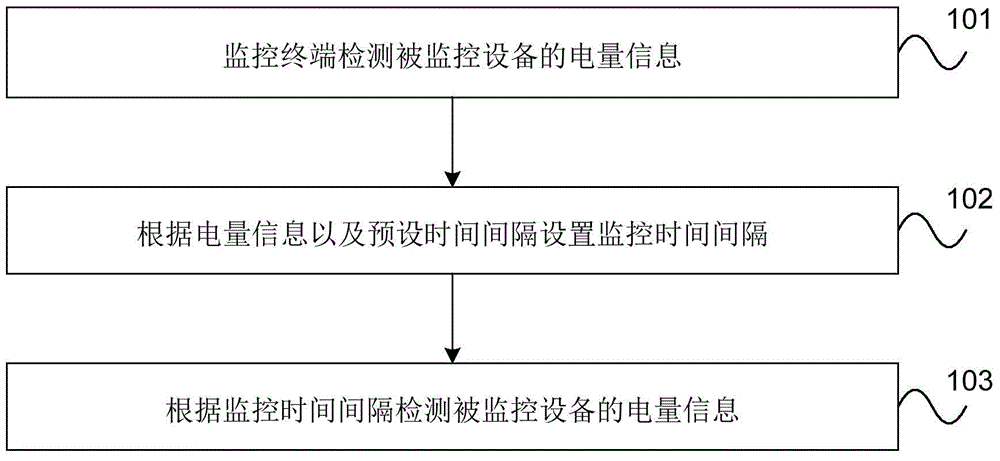
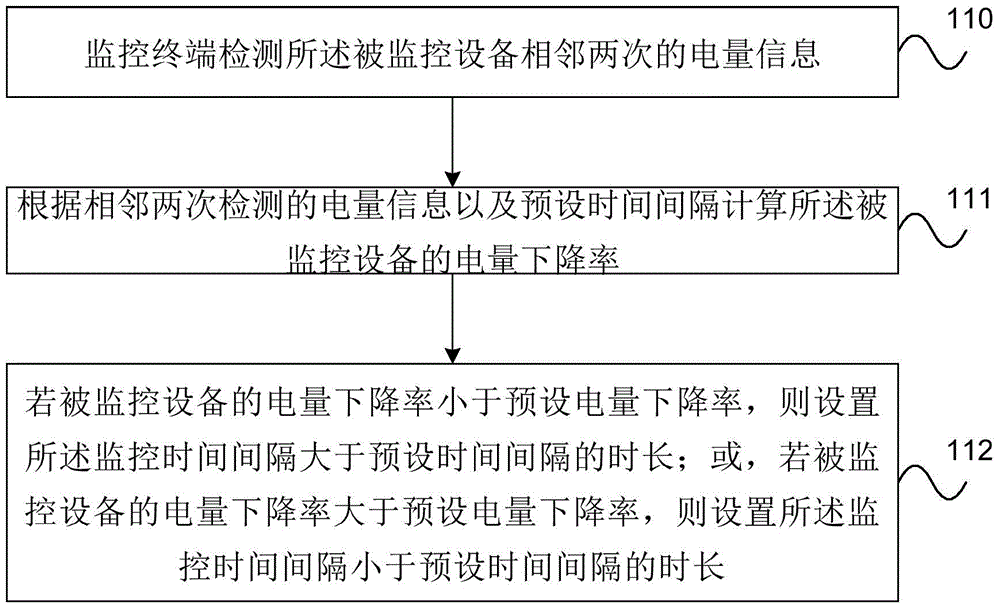
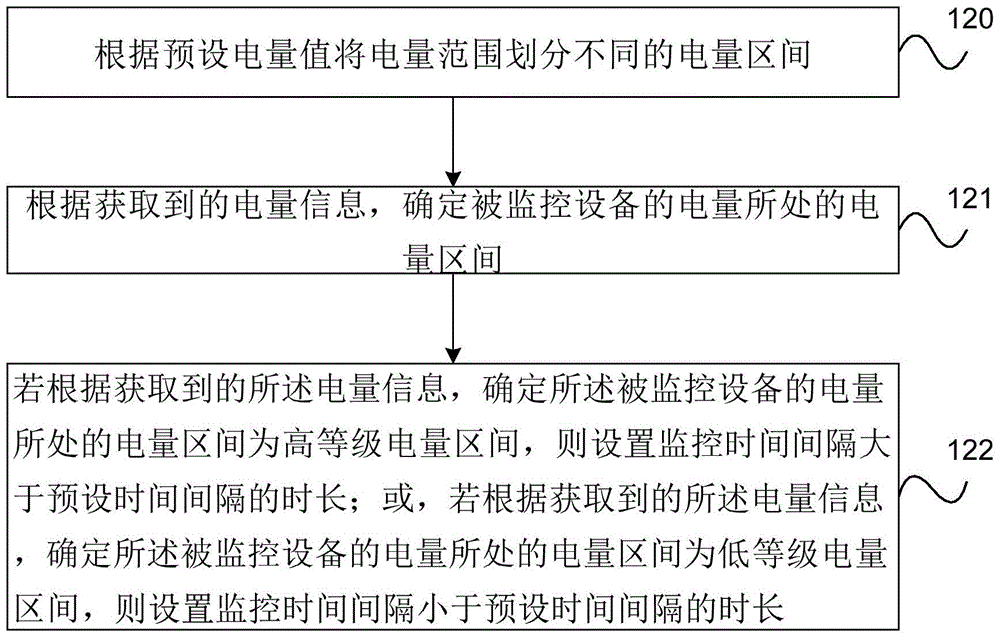
Method for detecting electric quantity of equipment, equipment, and system
ActiveCN104641245ASolve the waste of resourcesSave energyPower managementNear-field transmissionComputer terminalEngineering
The embodiment of the invention provides a method for detecting the electric quantity of equipment, the equipment, and a system. The method comprises the steps that a monitoring terminal detects the electric information of monitored equipment; the monitoring time interval is set according to the electric information and a preset time interval; and the electric information of the monitored equipment is detected according to the monitoring time interval. The method achieves the determination of the time interval between two times of detection according to the detected electric information, and fully saves the resources under the condition of not affecting a user.
Owner:HUAWEI TECH CO LTD
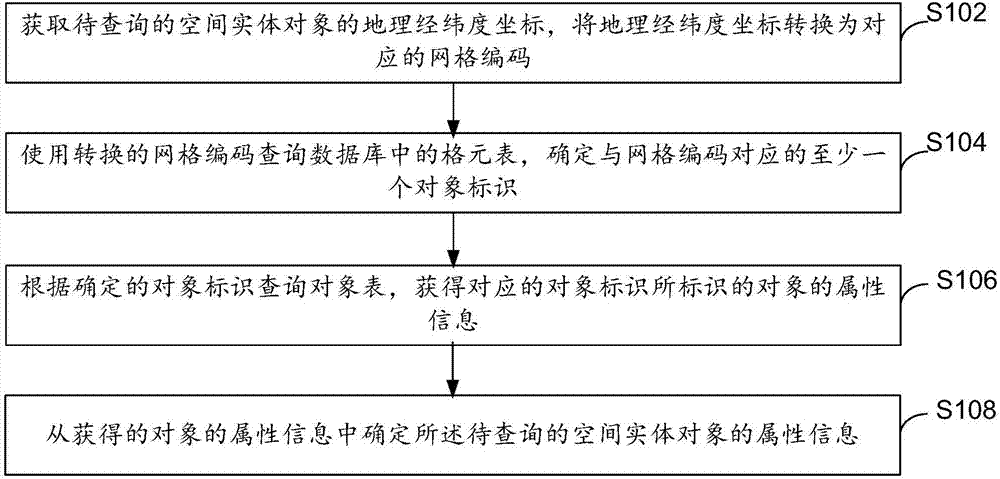
Geographic information data processing method and device
InactiveCN107153711AReduce the number of queriesImprove query speedGeographical information databasesSpecial data processing applicationsObject identifierData processing
The embodiment of the invention provides a geographic information data processing method and device. The geographic information data processing method comprises the following steps: acquiring geographic latitude and longitude coordinates of a spatial entity object to be inquired, and converting the geographic latitude and longitude coordinates into corresponding grid codes; inquiring grid elements in a database by use of the converted grid codes, and determining at least one object identifier corresponding to the grid codes, wherein corresponding relationships between the grid codes and the corresponding object identifiers are stored in the grid elements; inquiring an object table according to the determined object identifiers to obtain attribute information of objects identified by the corresponding object identifiers, wherein the object identifiers and the attribute information of the corresponding objects are stored in the object table; and determining attribute information of the spatial entity object to be inquired from the obtained attribute information of the objects. According to the embodiment of the invention, spatial inquiry conditions are converted into numerical matching of the grid codes, so that the effect of efficiently and accurately acquiring result data of geographic information data operation is achieved.
Owner:北京旋极伏羲大数据技术有限公司
Method of using simple network management protocol to act multirariant block inquiry
InactiveCN1753402AOvercome speedOvercome resourcesTransmissionInformation repositoryManagement information base
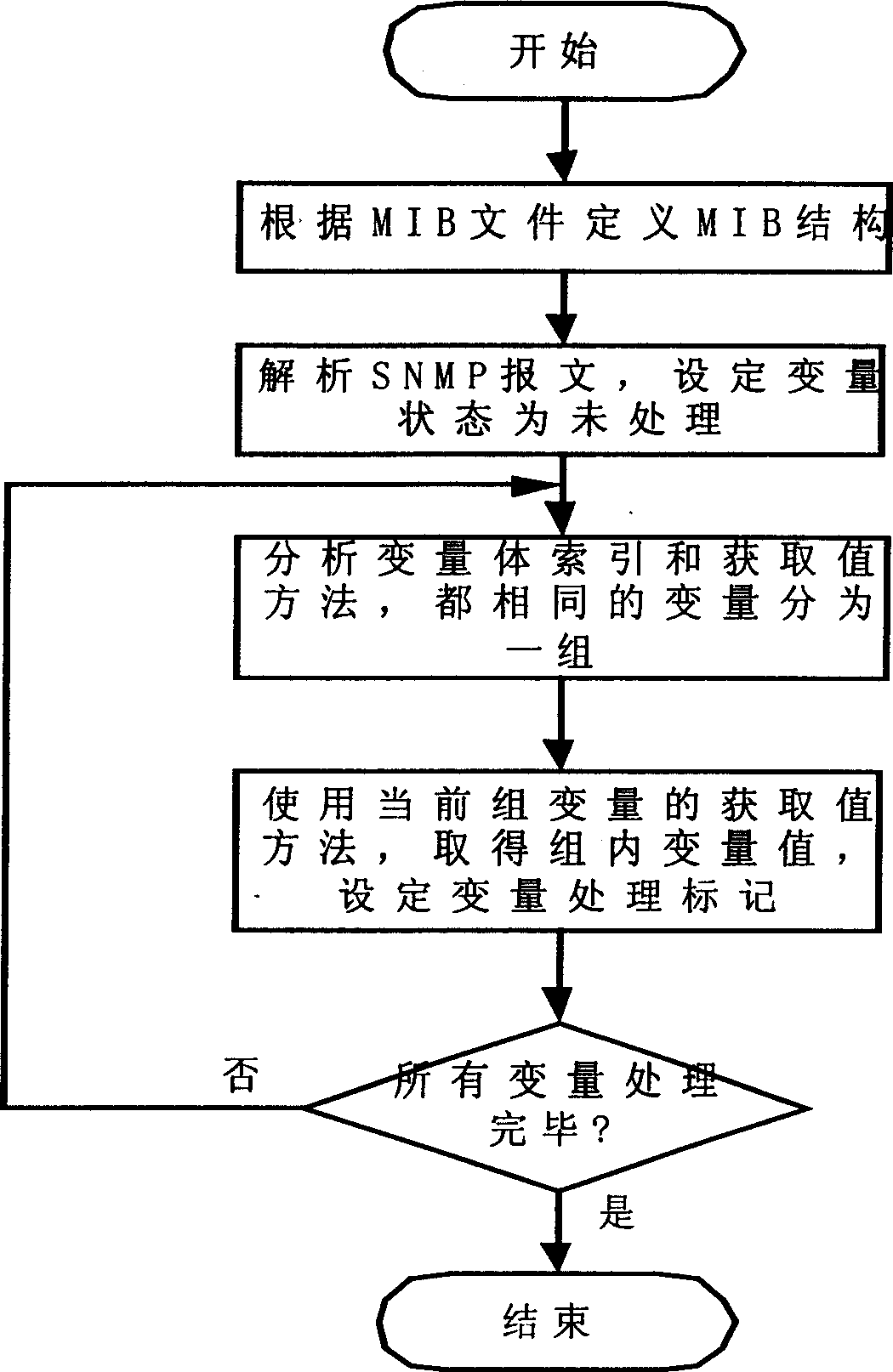
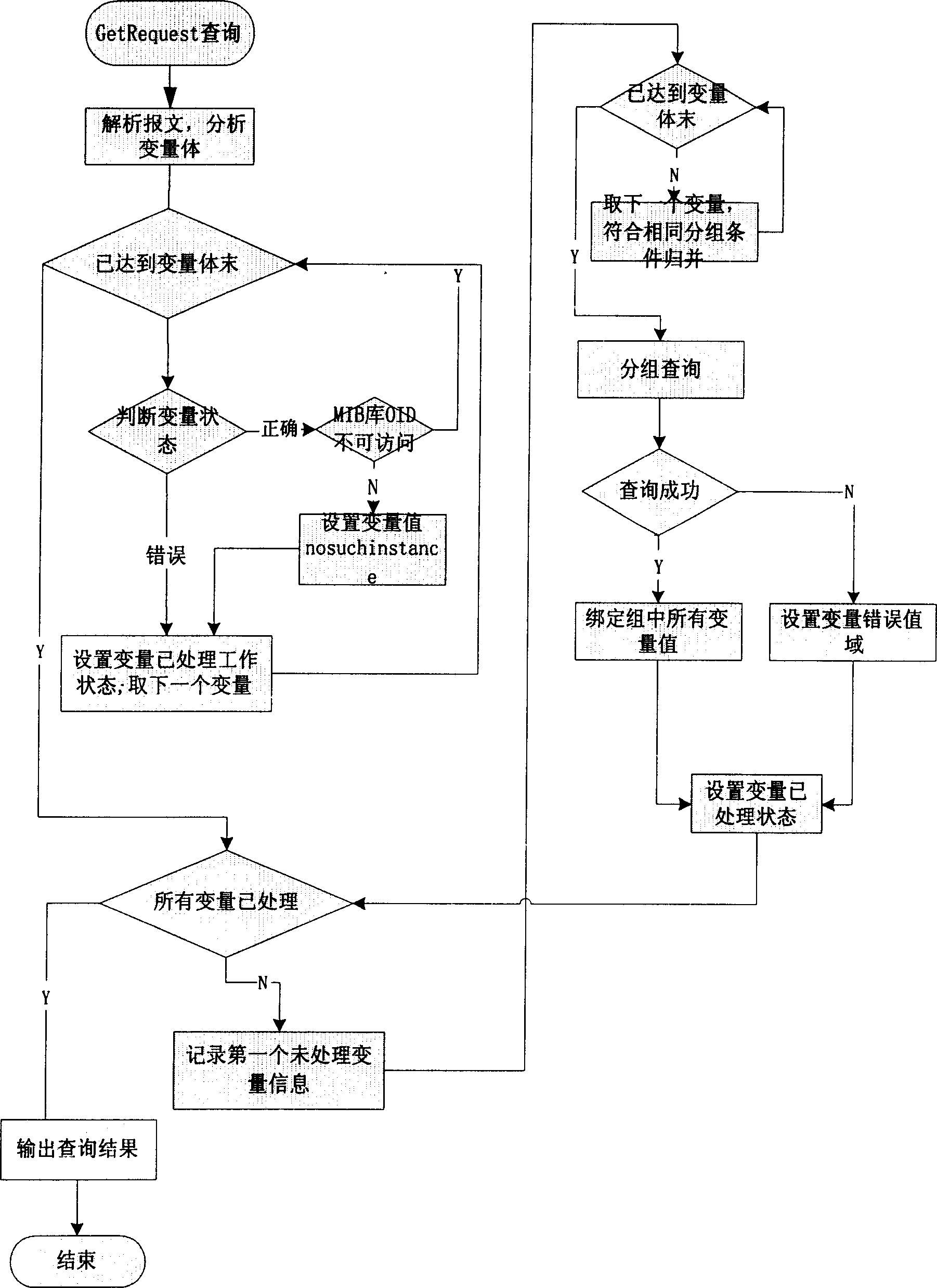
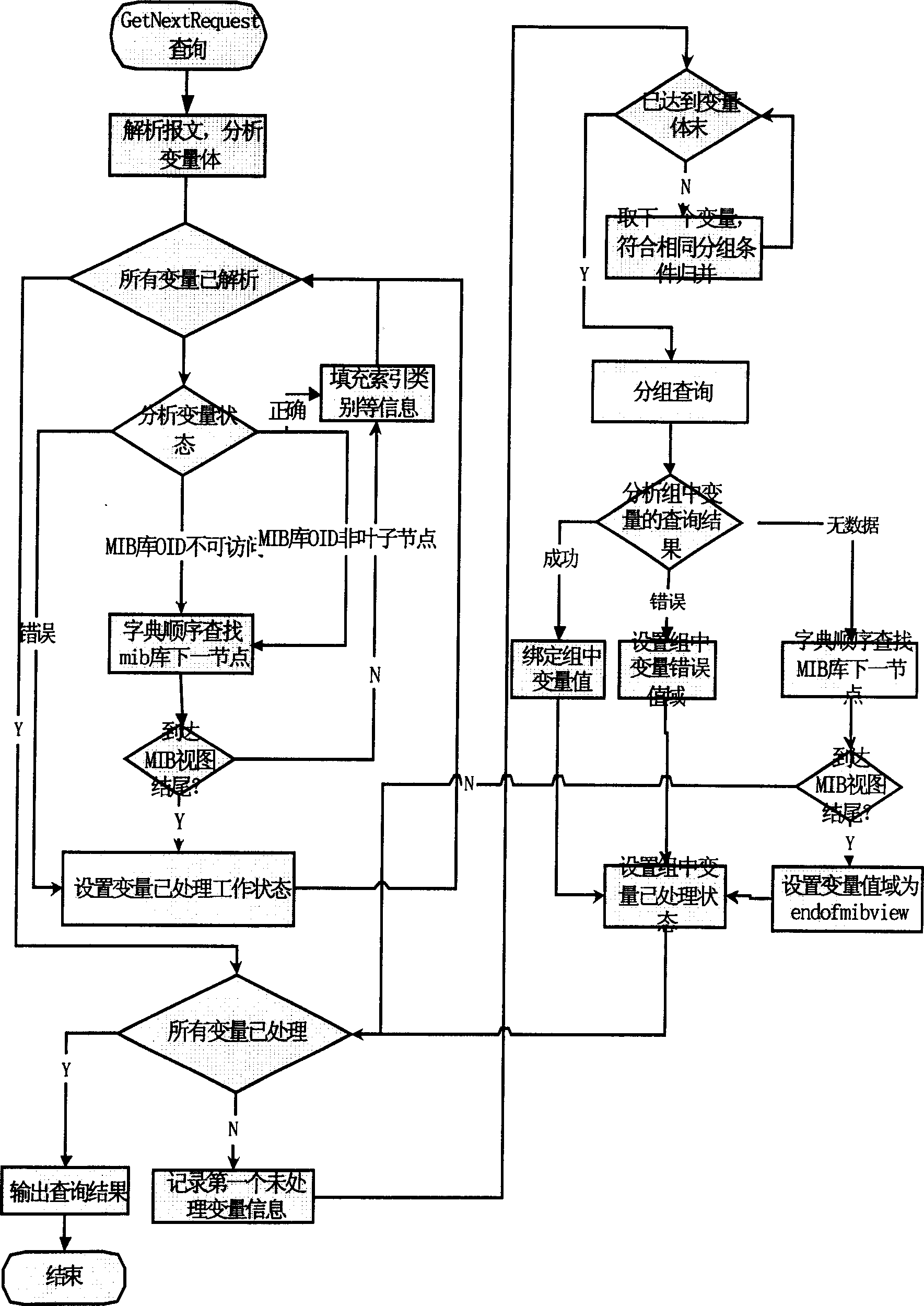
This invention relates to a packet inquiry method for SNMP proxy multiple variables, which defines the data structure of a SNMP proxy management information library based on the files, analyses SNMP messages, variables and processes them to design their state and the air working state and packet the un-processed variable based on the message operation kinds of the SNMP messages, dispatches the obtaining values of the objects in the packets, inquires data based on the information of the objects and the variable index values in the management information library to bind values of the variables if the enquiry is successful and mark the variables a processed state and processes them to design the variable state and working state if it is not successful and repeates the above steps till all of their working states are processed.
Owner:南通国邦科技发展有限公司
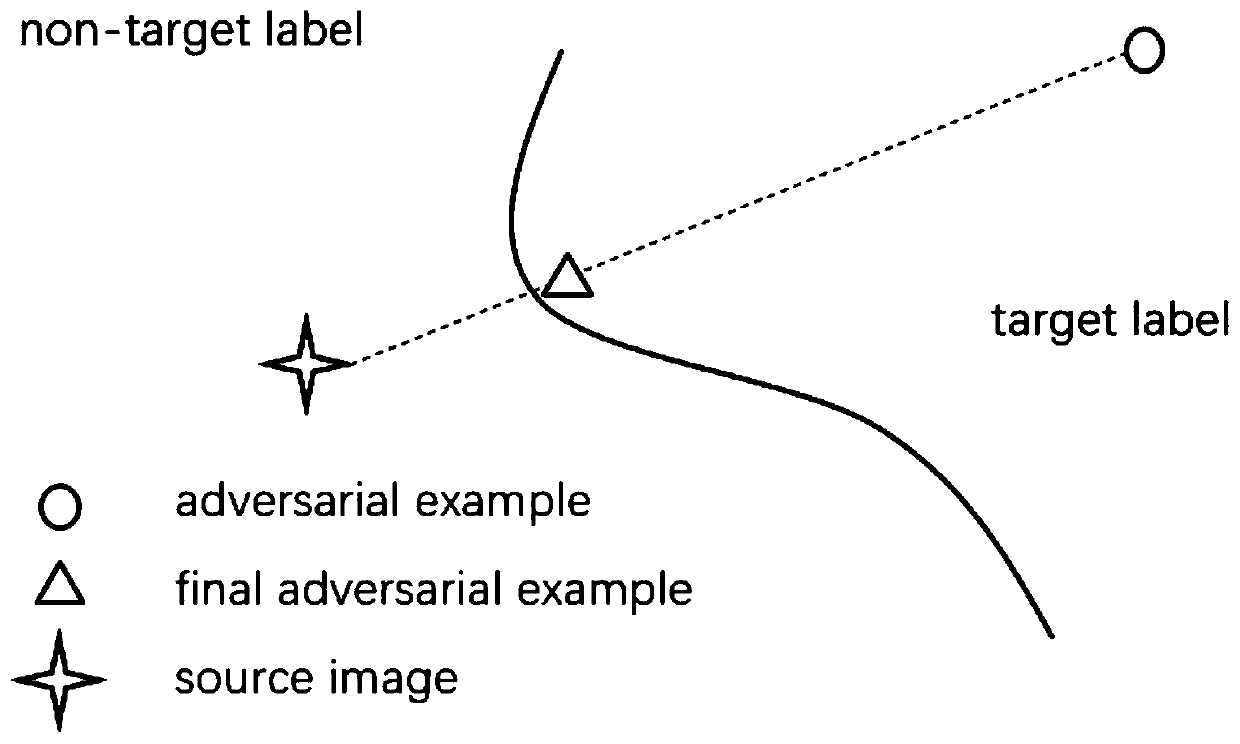
Adversarial sample generation method based on Bayesian optimization
ActiveCN110276377AReduce the impactReduce the number of queriesCharacter and pattern recognitionPlatform integrity maintainanceClassification resultBayesian optimization
The invention discloses an adversarial sample generation method based on Bayesian optimization. An existing black box attack method needs to inquire a large number of models to obtain optimization information. The adversarial sample generation method is characterized by taking an original picture as input, and determining the position to be optimized by calculating the gradient of the structural similarity of a disturbance picture and the original picture; performing sampling optimization in a selected position by using Bayesian optimization to obtain a disturbance value capable of increasing the loss function at the position; and selecting and optimizing a plurality of positions in an iteration mode to obtain a disturbance value, and stopping until the classification result of the disturbed image is changed or the maximum number of iterations is reached. According to the invention, the number of times of querying the target DNN model can be effectively reduced, and the number of disturbed pixel points is small.
Owner:HANGZHOU DIANZI UNIV
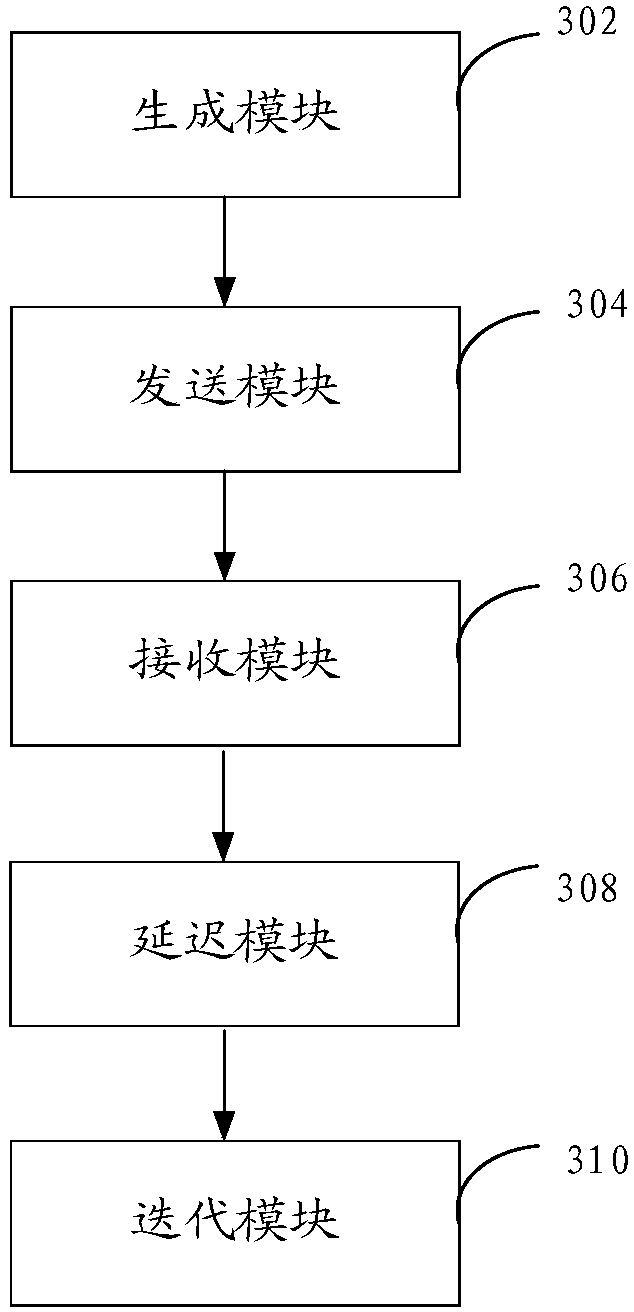
Learning resource recommendation system
ActiveCN106156354AReduce workloadQuality improvementElectrical appliancesSpecial data processing applicationsComputer scienceLearning resource
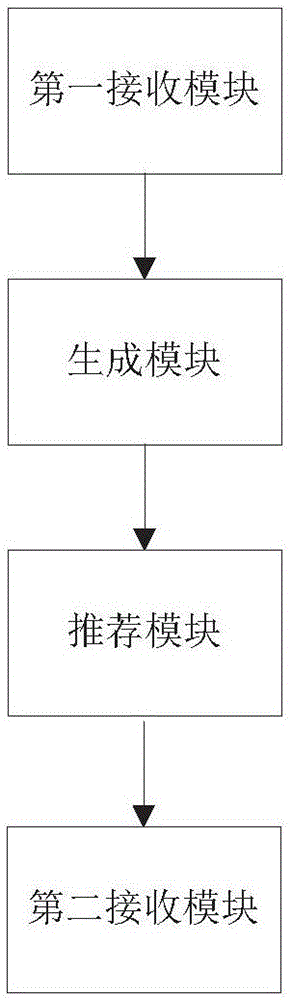
The invention provides a learning resource recommendation system. The system comprises a first receiving module, a generation module, a recommendation module and a second receiving module, wherein the first receiving module is used for receiving the curriculum, the push time of the curriculum and a question bank, and the question bank comprises the tile corresponding to each curriculum chapter; the generation module is used for generating test paper corresponding to each curriculum chapter according to the question bank, setting the recommendation time for the test paper, generating a classroom answer sheet by combining the test paper with the recommendation time and sending the classroom answer sheet to the recommendation module; the recommendation module is used for pushing the classroom answer sheet and the tiles of the curriculum chapters; the second receiving module is used for receiving search conditions, obtaining search results and receiving answers of the classroom answer sheet.
Owner:HUAIHAI INST OF TECH
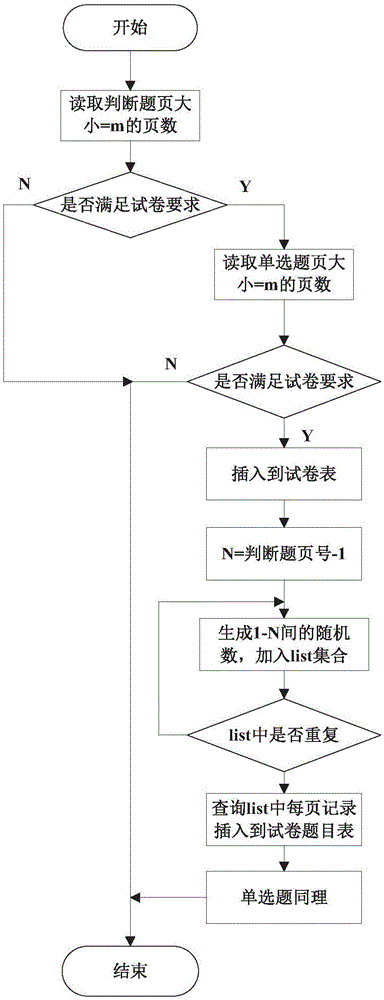
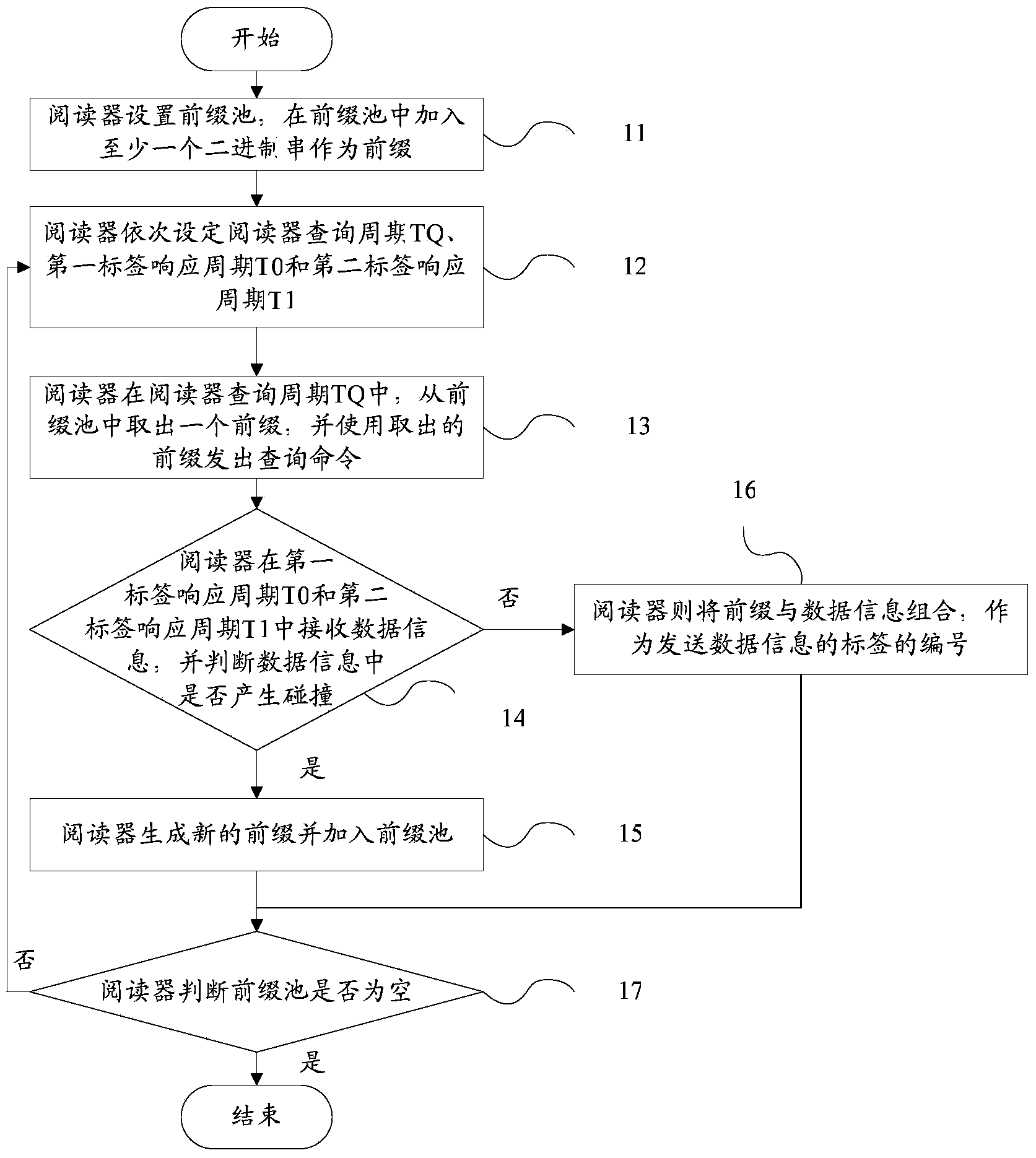
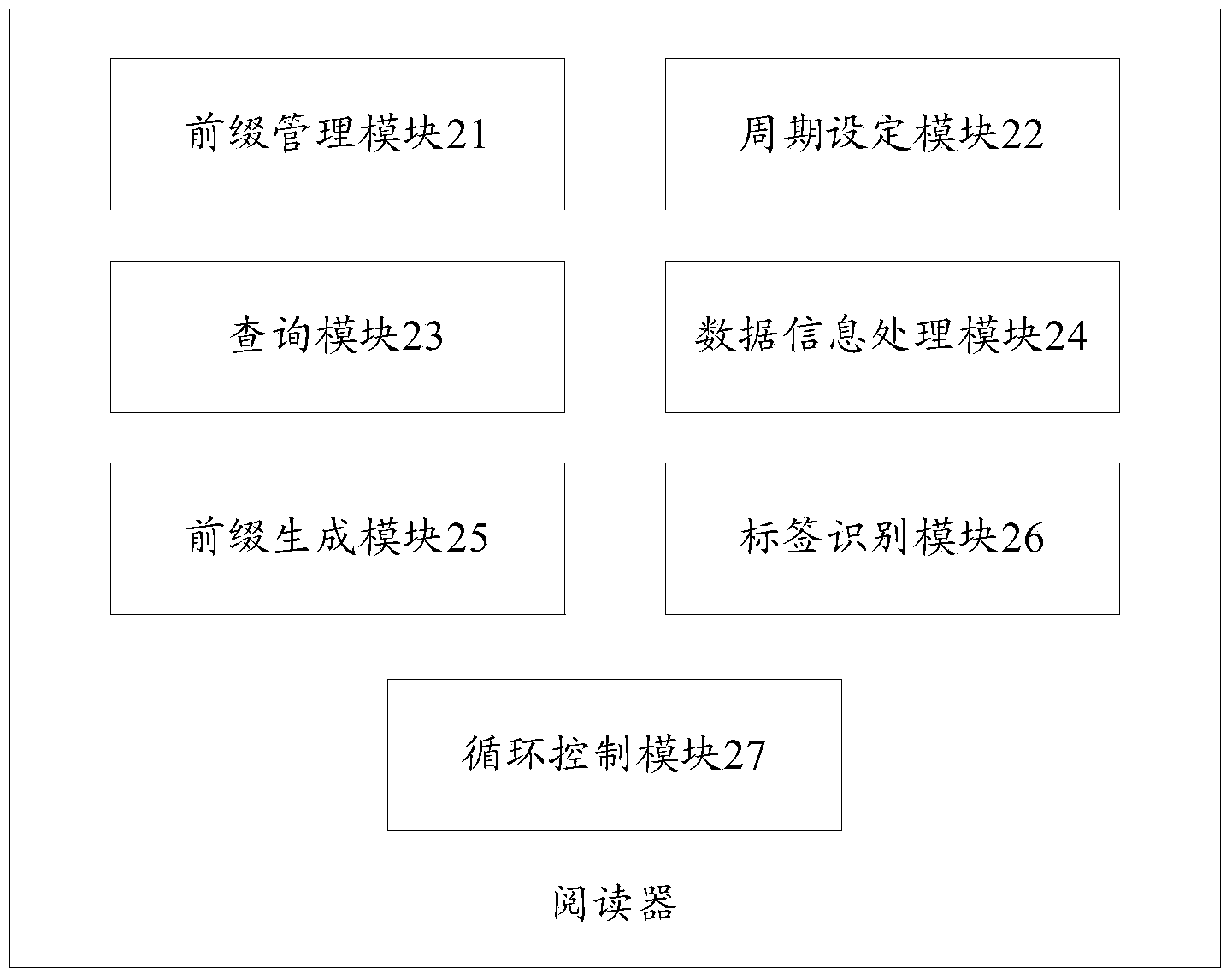
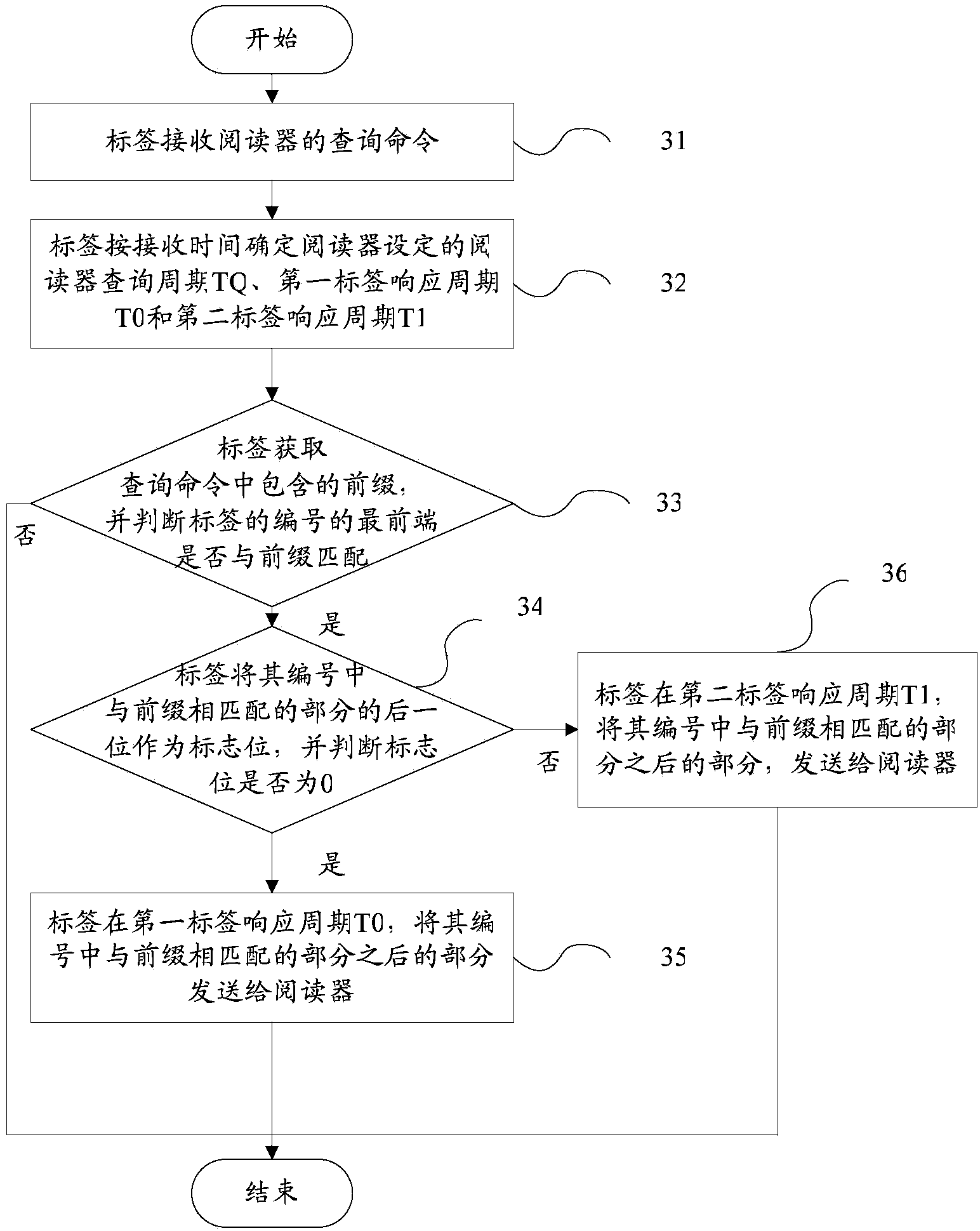
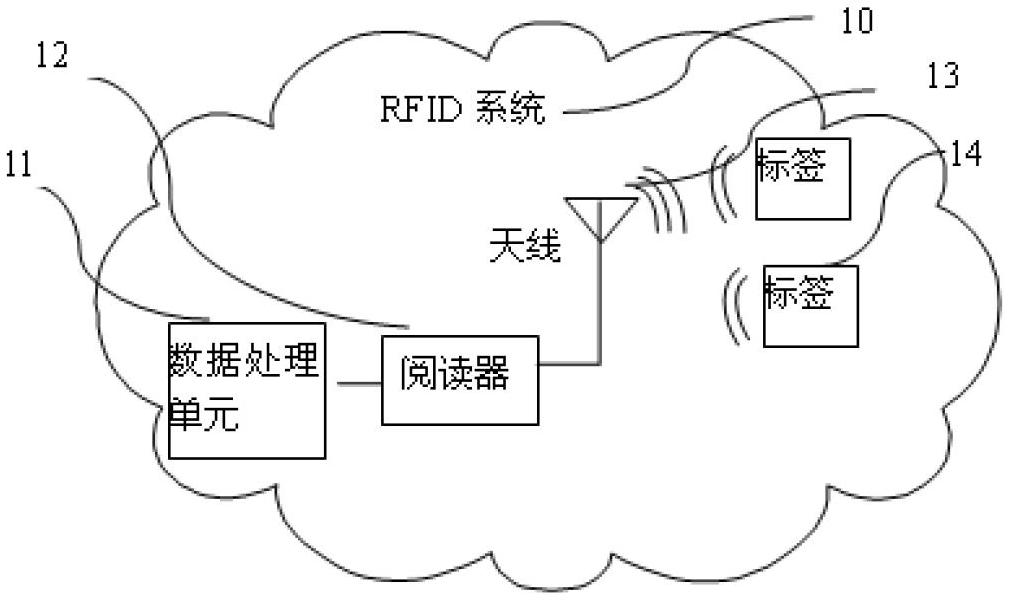
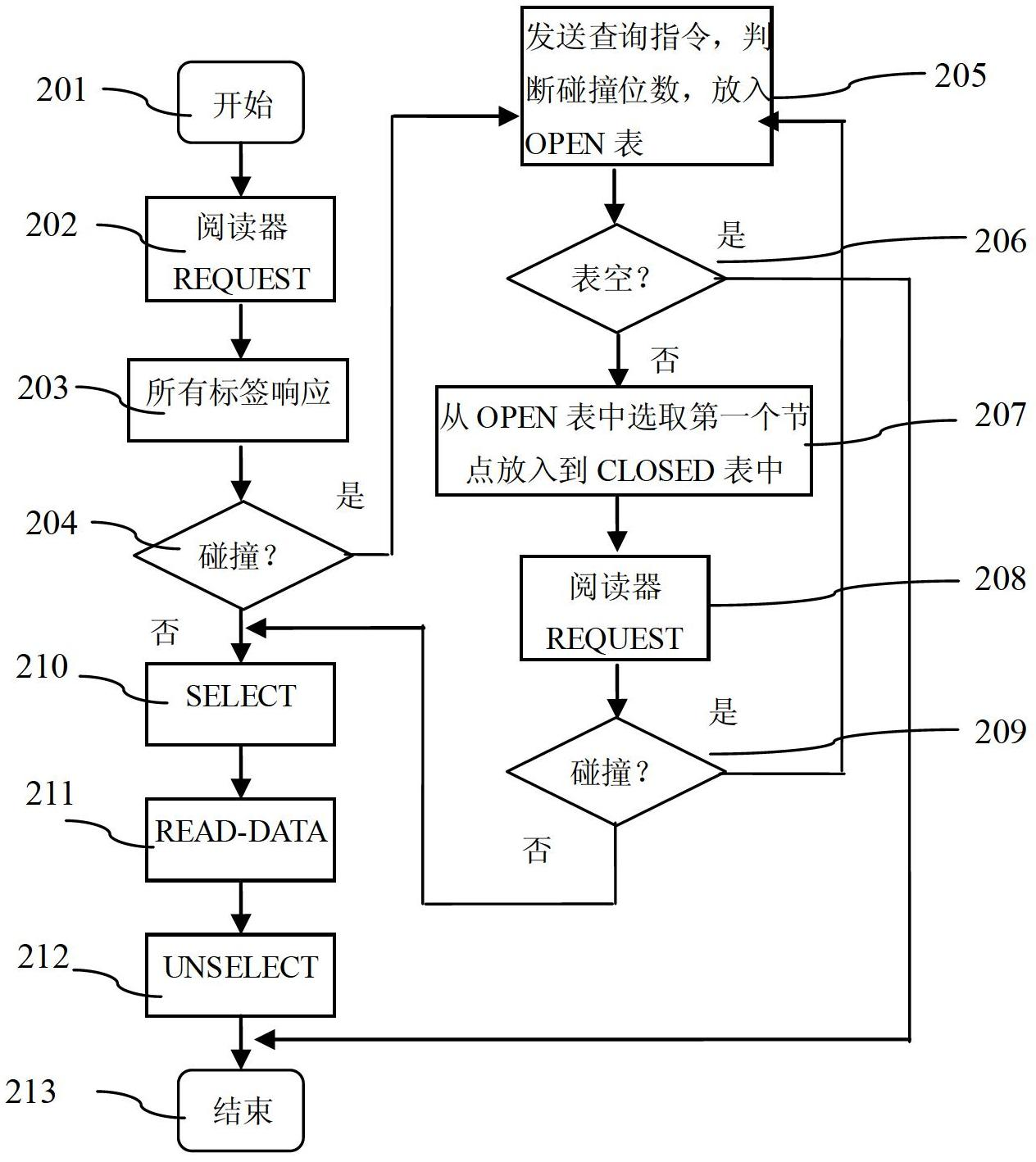
RFID multi-tag identification method, reader and tags
InactiveCN103473524AReduce storage spaceReduce processing timeSensing record carriersRecord carriers used with machinesComputer scienceEnergy consumption
The invention provides an RFID multi-tag identification method, a reader and tags which are mainly applied to an RFID multi-tag identification system to solve the problem of tag collision. The RFID multi-tag identification method divides a process of identifying the reader and the tags and exchanging information into a plurality of periods which comprise the inquiring period for the reader to generate inquiring orders to search the tags and the two response periods for the tags to respond the inquiring orders of the reader. The two groups of tags can respectively respond the same order of the reader in different response periods. One inquiring order of the reader can obtain response of the two groups of tags, so that the inquiring times of the reader in a multi-tag identification process is greatly reduced, the communication traffic between the reader and the tags is reduced in a tag identification process, and the system energy consumption is reduced. The RFID multi-tag identification method is simple and direct, easy to carry out and stable in performance, belongs to a non-memory anti-collision method and is suitable for passive RFID multi-tag identification systems and various RFID multi-tag identification application occasions.
Owner:SOUTHWEAT UNIV OF SCI & TECH
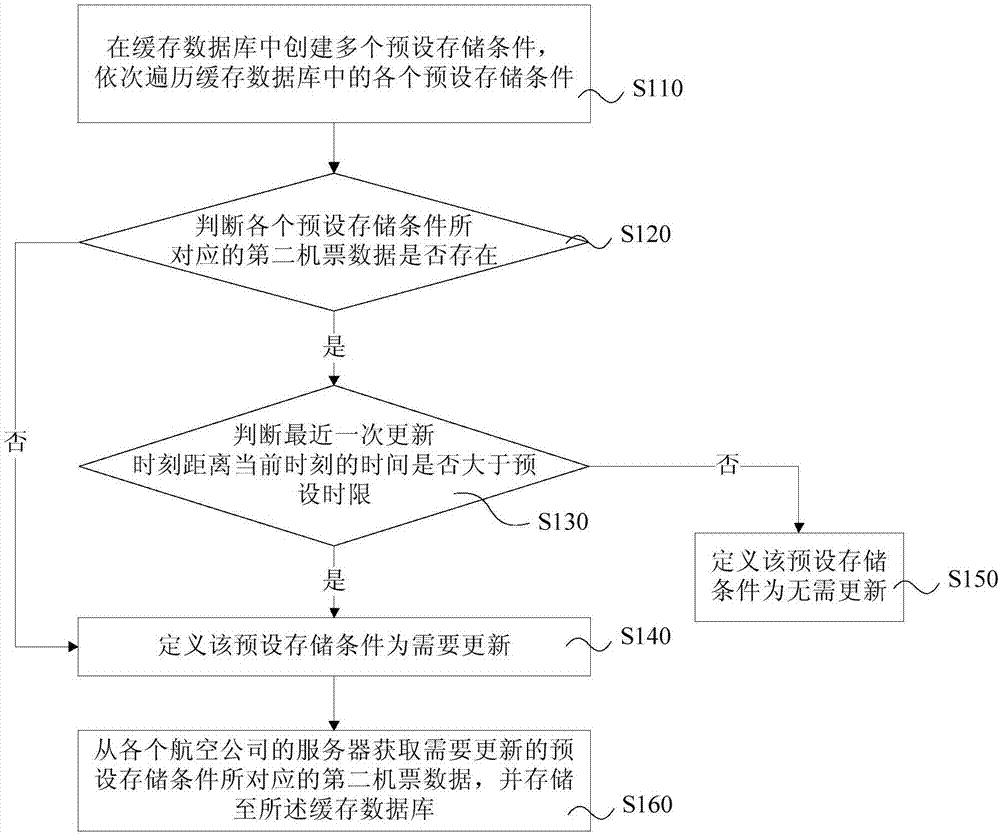
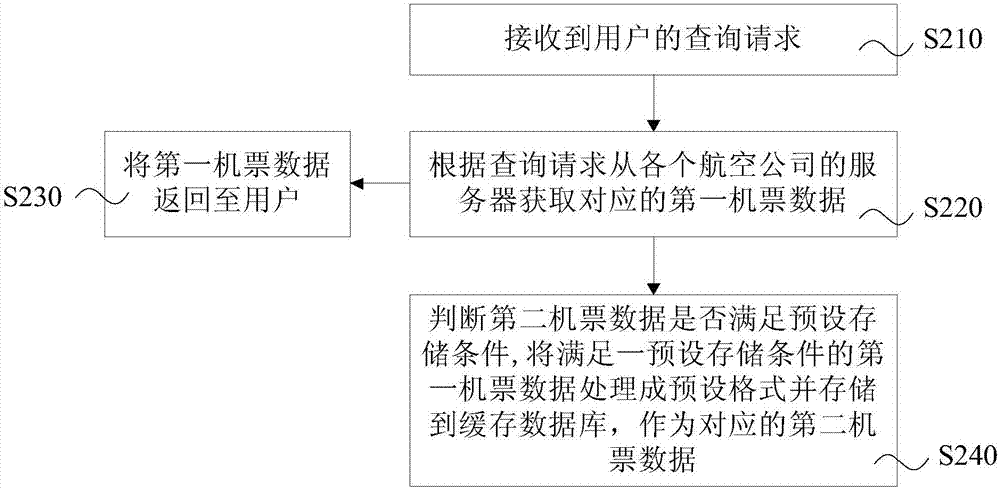
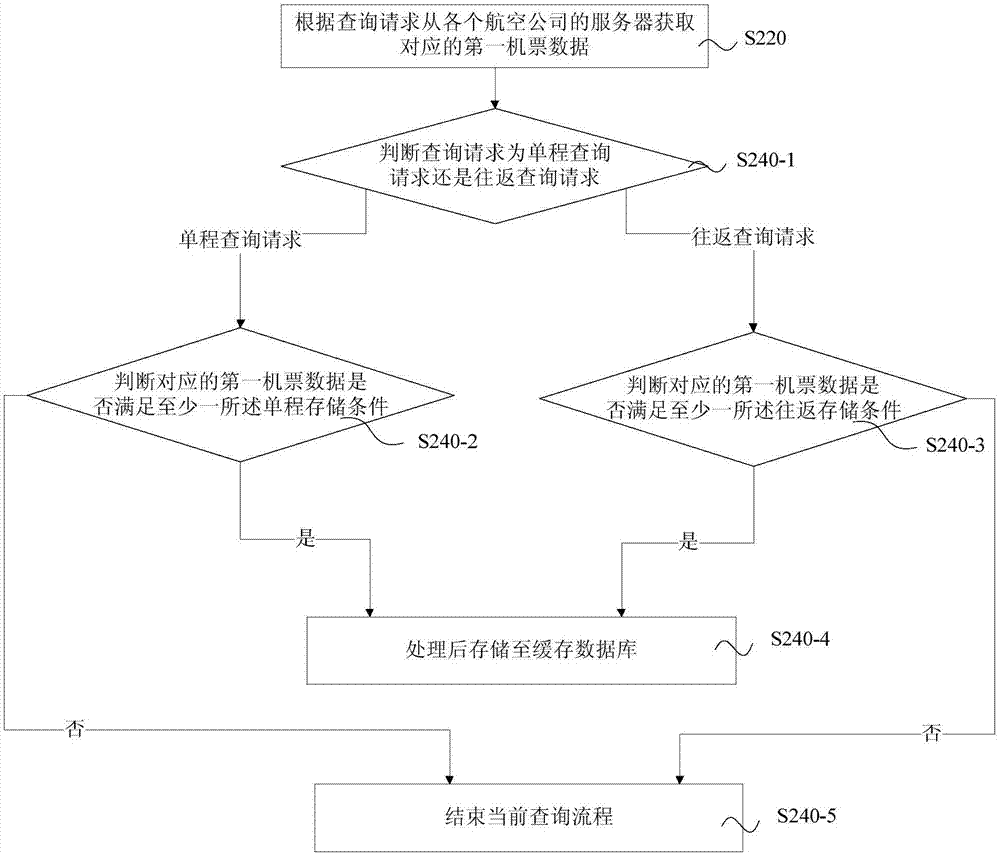
Active and passive combined airline ticket data acquisition method, system and device and storage medium
InactiveCN107291901AShort cycleImprove freshnessData processing applicationsWeb data indexingData acquisitionData needs
The invention provides an active and passive combined airline ticket data acquisition method, system and device and a storage medium. The method includes active query and passive query, all preset storage conditions in a cache database are traversed in active query, and update data are actively acquired from a server of an airline needing update. Passive query responds to a request of a user, second airline ticket data are acquired from the server of the airline, and the second airline ticket data conforming to the preset storage conditions are processed into a preset format and stored in the cache database. By storing hot air route data in passive query, the query frequency of requesting an airline system for acquiring low-price data is decreased, the airline ticket data of hot air routes are traversed by active query, real-time update is realized, the period of active query of the airline ticket data is shortened, the freshness of a tourism platform for displaying low-price cache data of the airline is improved, so that resources can be effectively allocated to air route data needing update in active query, and the use ratio of system resources is increased.
Owner:CTRIP TRAVEL NETWORK TECH SHANGHAI0
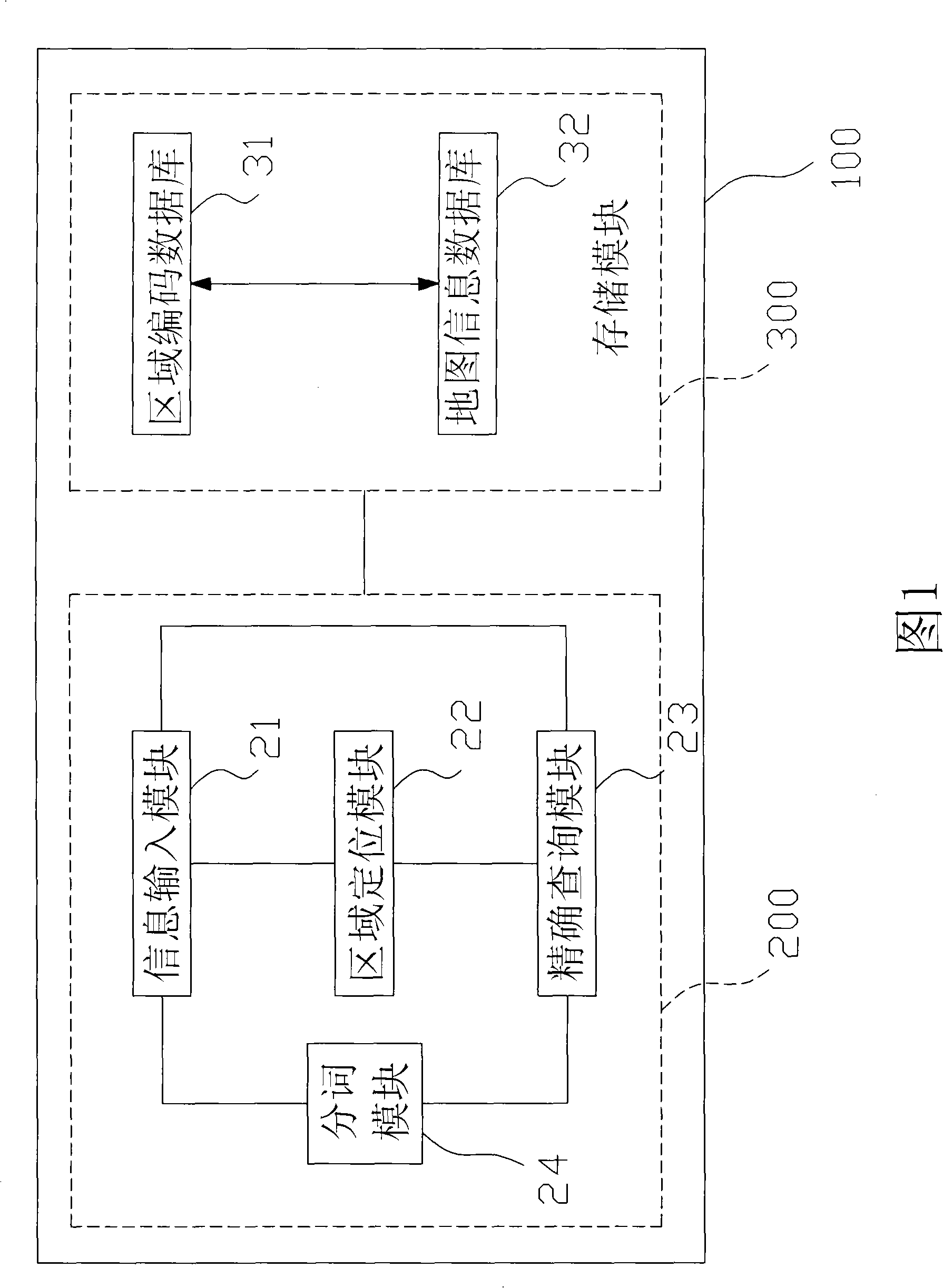
Search device and search method of geographical coordinates
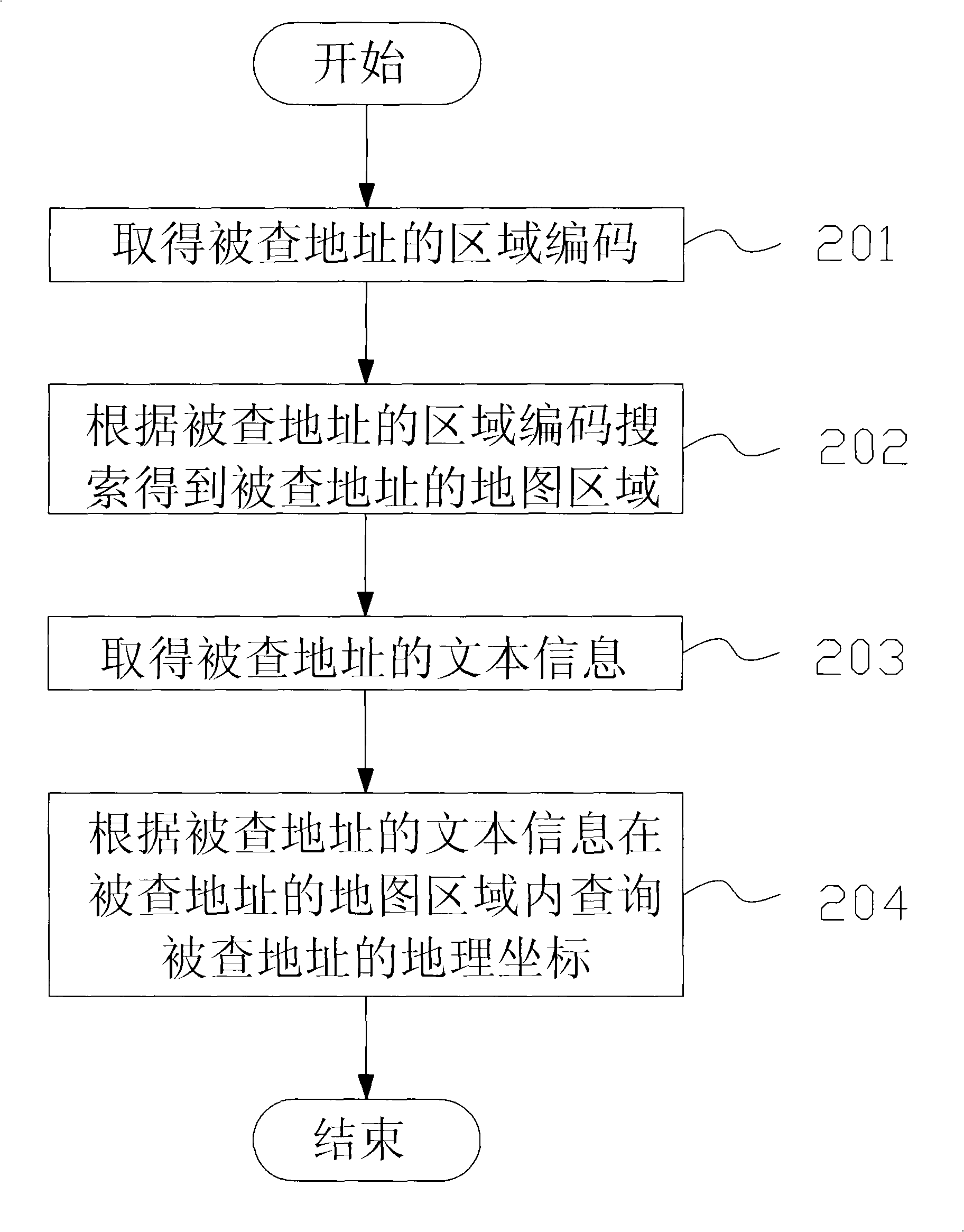
InactiveCN101270992AReduce the number of queriesReduce manual interventionNavigation instrumentsData miningMarine navigation
The invention provides a searching device and searching method for geographic coordinates, which is suitable for searching geographic coordinate of a searched address from a navigation device. The navigation device is provided with a regional coding database and a map information database, and the map information database is mutually mapped with the regional coding database. The searching device includes an information input module, a region locating module and an accurate search module. The searching method is achieved through the searching device and includes the following steps: region coding of the searched address is received by the information input module; according to the region coding of the searched address, the map region of the searched address can be searched by the region locating module; the text information of the searched address can be received by the information input module; and according to the text information of the searched address, the geographic coordinate of the searched address can be searched within the map region of the searched address by the accurate search module. The searching range is limited and shrunk through the region coding to increase the searching speed and precision.
Owner:HUANDA COMPUTER (SHANGHAI) CO LTD
Multiple tag dynamic bit arbitration anti-collision method for RFID system
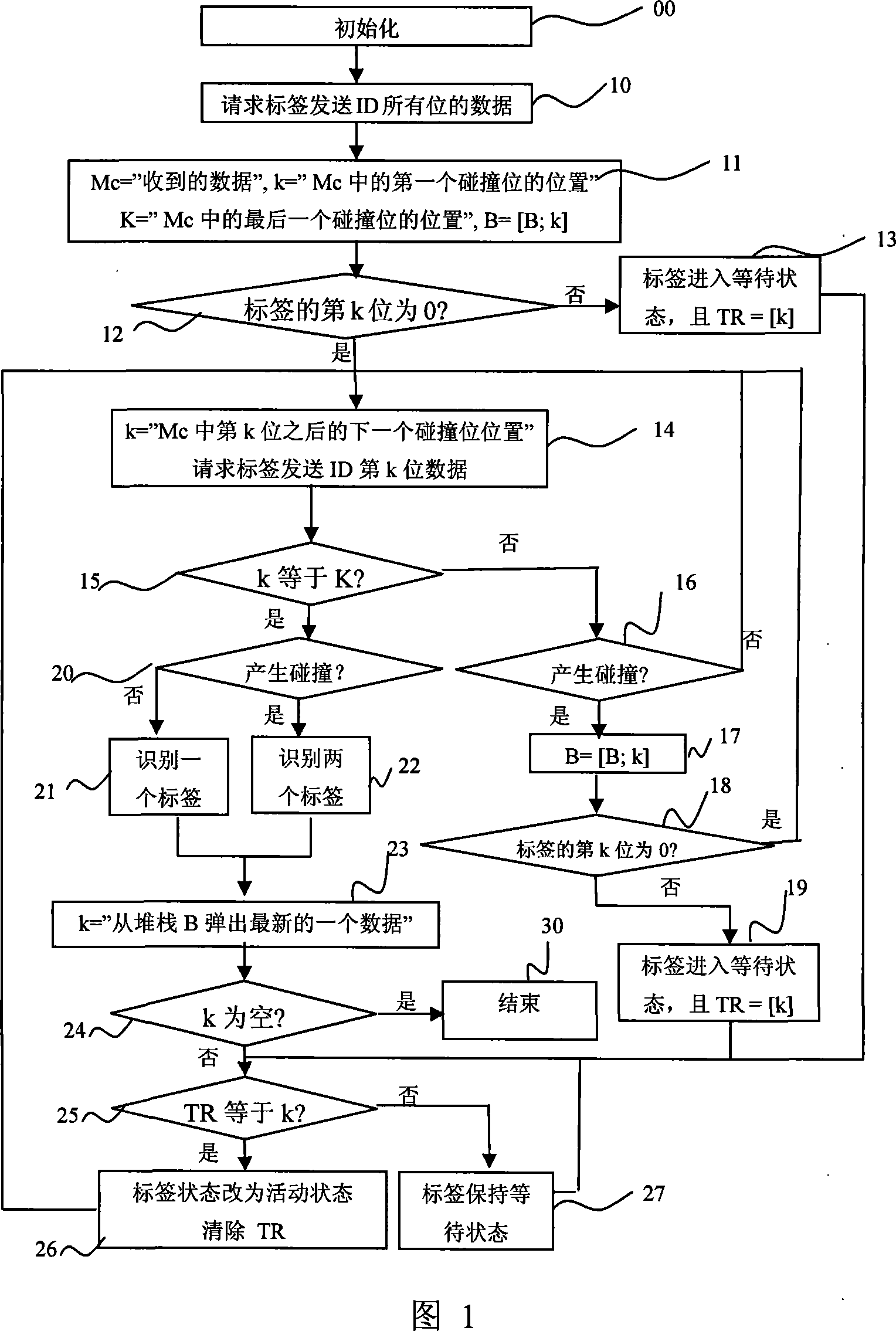
InactiveCN101079096ASimple structureLow implementation difficultySensing record carriersProcessor registerBinary tree
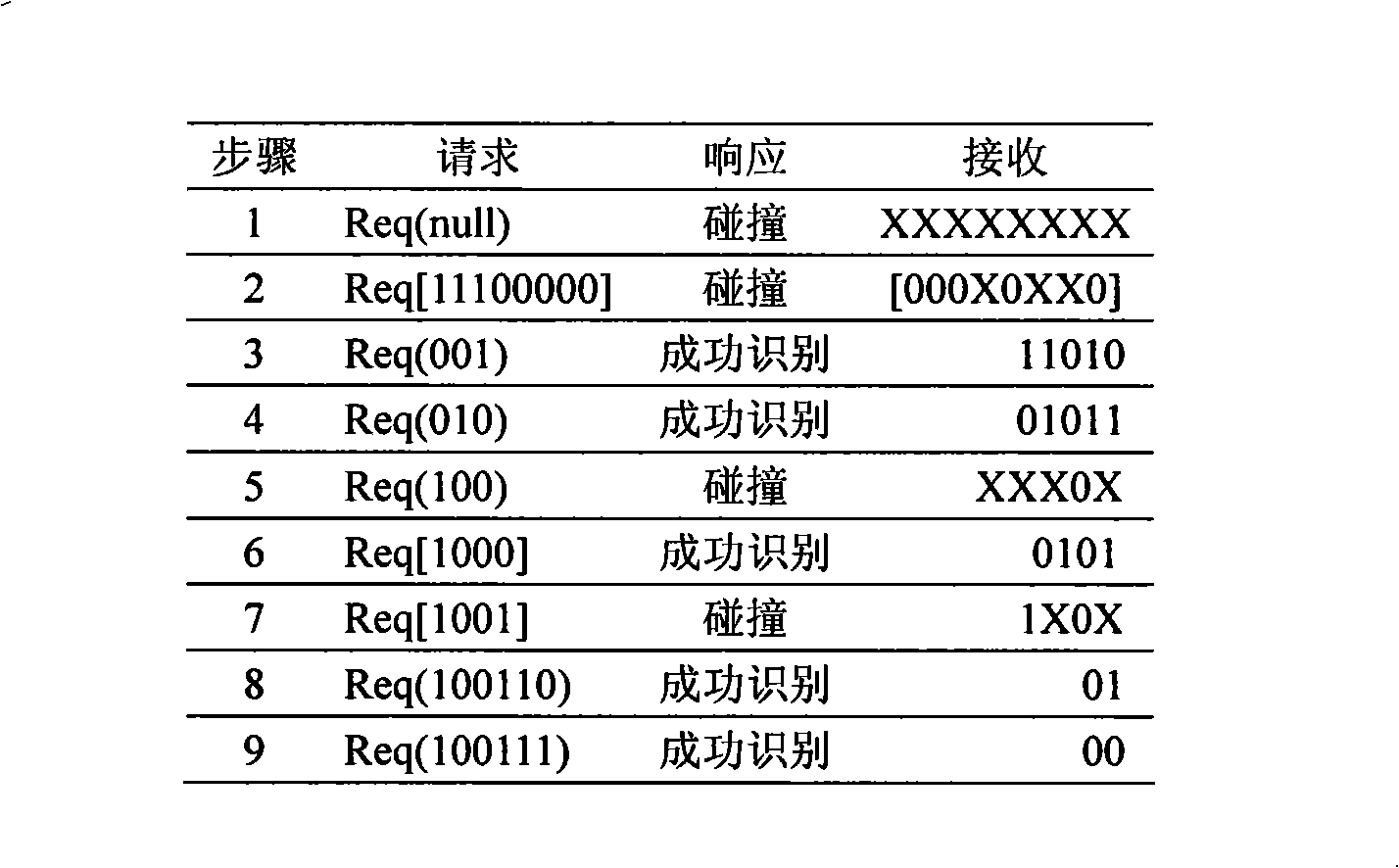
The invention discloses a multiple label dynamic bit arbitration anti-collision method for RFID system. The method uses a bit register in the label for saving the collision position information of the label in the identifying process; the saving unit of the reader is equipped with a collision position stack, a prefix stack, a temporary reservoir for recording the information of the collision process. The method comprises the following steps: initializing and inquiring the total mark code of the label firstly; inquiring the collision position according to the bit and recording the information of the collision position secondly; identifying the label and determining the next label entering in the active state according to the standard and completing identifying all the labels at last. The invention shows the advantages of binary tree search algorithm sufficiently, which reduces the inquiring times and the receiving bit number, provides a simple structure and a low energy.
Owner:SOUTH CHINA UNIV OF TECH
Business state query method and device, computer equipment and storage medium
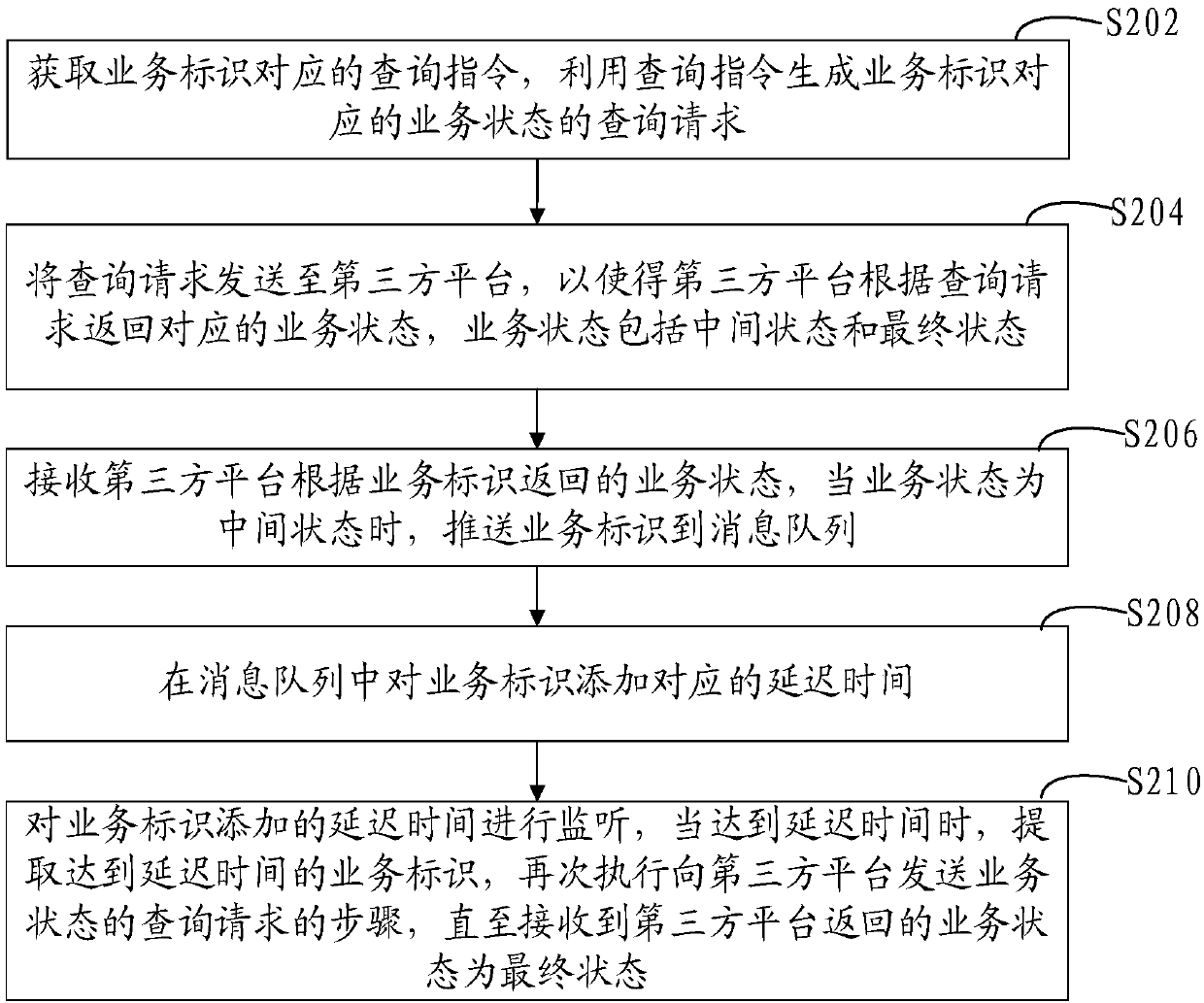
InactiveCN107943828AReduce consumptionReduce the number of queriesInterprogram communicationSpecial data processing applicationsThird partyMessage queue
The invention relates to a business state query method and device, computer equipment and a storage medium. The method comprises the following steps of: obtaining a query instruction corresponding toa business identifier and generating a query request of a business state corresponding to the business identifier by utilizing the query instruction; sending the query request to a third-party platform to ensure that the third-party platform returns a corresponding business state according to the query request, wherein the business state comprises an intermediate state and a final state; receivingthe business state returned by the third-party platform according to the business identifier, and pushing the business identifier to a message queue when the business state is the intermediate state;adding a corresponding delay time for the business identifier in the message queue; and monitoring the delay time added for the business identifier, and when the delay time arrives, extracting the business identifier which achieves the delay time, and re-executing the step of sending the query request of the business state to the third-party platform until the received business state returned bythe third-party platform is the final state.
Owner:深圳市牛鼎丰科技有限公司
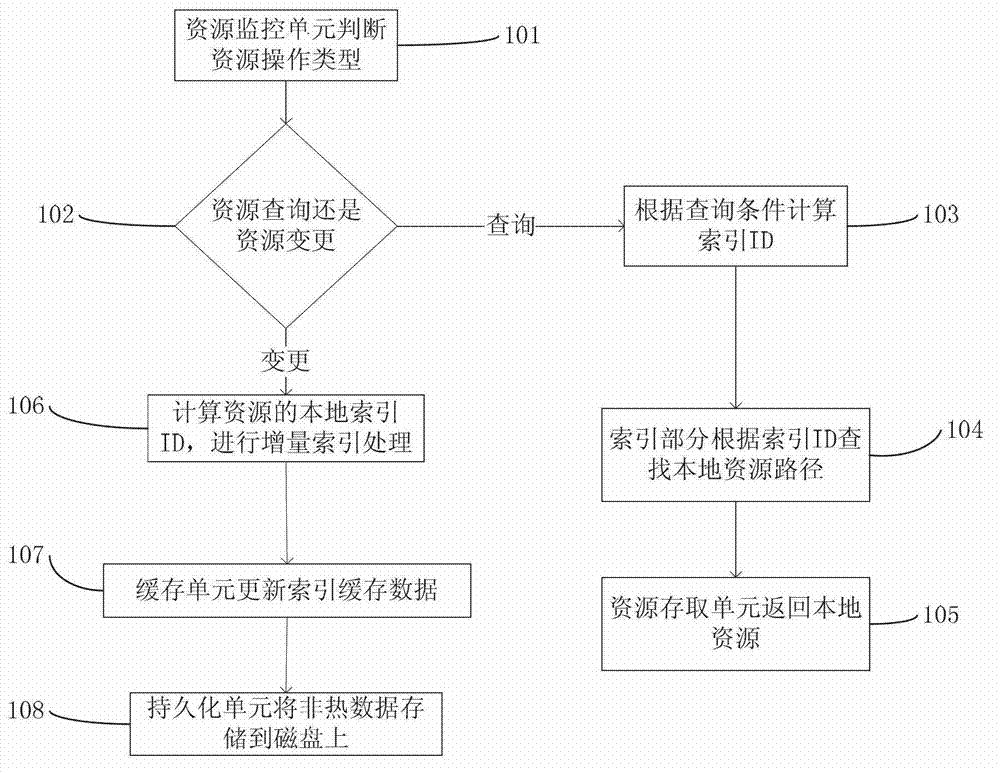
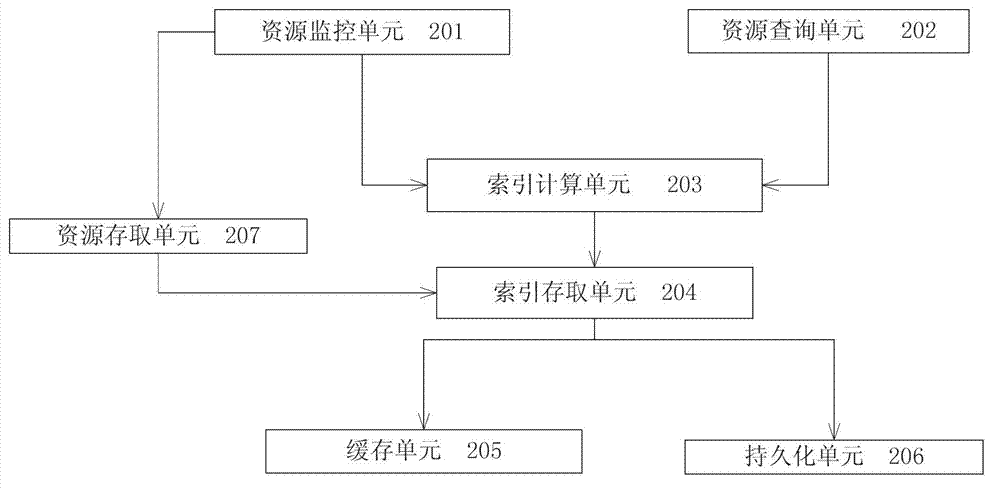
Index-based local resource quick retrieval system and retrieval method thereof
ActiveCN102968464AImprove query efficiencyImprove user experienceSpecial data processing applicationsMemory processingLow speed
The invention relates to the technical field of data retrieval and data cache, in particular to an index-based local resource quick retrieval system and a retrieval method thereof. The retrieval method comprises the following steps of: monitoring specified resource data by a resource monitoring unit to judge the operation type of a resource; performing incremental indexing operation processing on the resource by an indexing part aiming at change of the resource, updating local index data hierarchically and meanwhile performing memory processing on the changed resource by a resource access interface; and calculating a local index ID (Identity) of the resource by the indexing part according to query conditions aiming at query operation, and directly returning the resource by a resource access unit according to an index of an operation result if the resource which meets the result exists. According to the system and the method, the problem of low speed in search of a large number of small files under the conventional conditions is effectively solved, the response time is quickened, and the user experience is improved; and the system and the method can be used for retrieval of the local resource.
Owner:GUANGDONG ELECTRONICS IND INST
Adversarial sample generation method based on discrete wavelet transform
PendingCN111709435AReduce the impactReduce the number of queriesCharacter and pattern recognitionNeural architecturesEngineeringData mining
The invention discloses an adversarial sample generation method based on discrete wavelet transform. According to an existing black box attack method, a large number of models need to be inquired to obtain the optimization information. According to the method, an original picture is used as input, a gradient estimation method and a gradient descent method are combined, disturbance is iteratively added into a clear sample, and finally an adversarial sample capable of misleading a model is generated. In order to improve the attack efficiency, discrete wavelet transform is used for separating a high-frequency part and a low-frequency part of a sample, disturbance is only added to the low-frequency part, and the number of sampling points is dynamically adjusted in the process of estimating thegradient of the low-frequency part, so that the model query frequency required for generating an adversarial sample is reduced. According to the invention, the frequency of querying the target DNN model can be effectively reduced.
Owner:HANGZHOU DIANZI UNIV
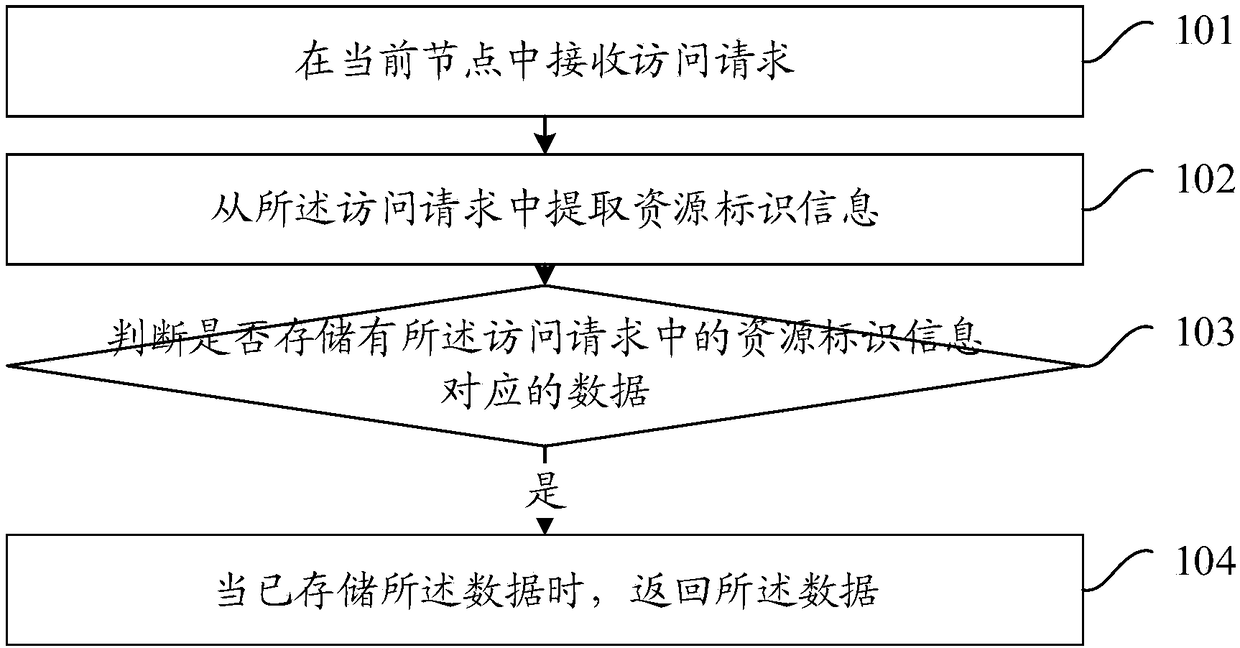
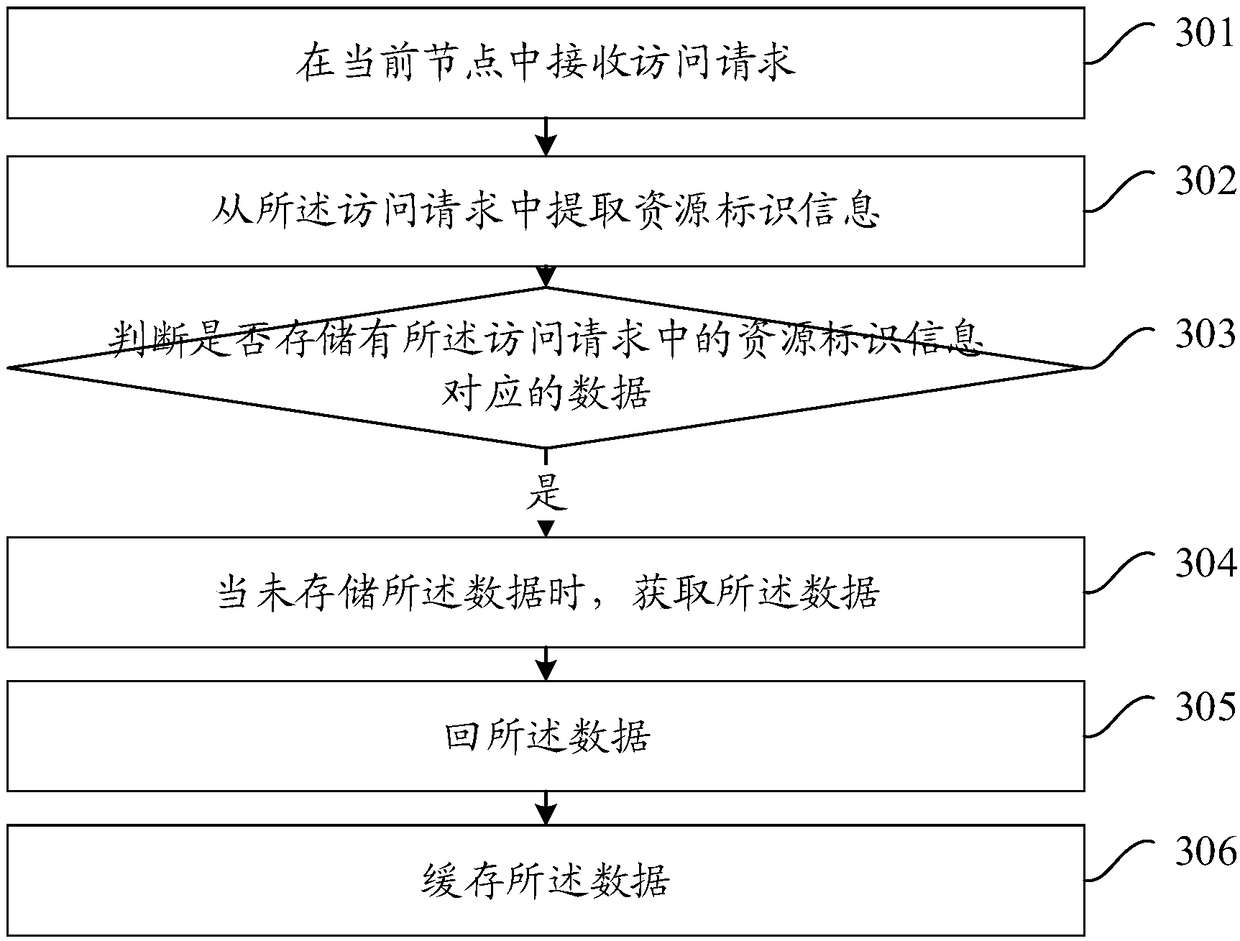
Data access method and device based on content delivery network (CDN)
InactiveCN108234639AReduce the number of queriesImprove hit rateTransmissionContent distributionContent delivery network
The embodiment of the invention provides a data access method and device based on a content delivery network (CDN). The CDN is provided with multiple nodes. The method includes the following steps: receiving an access request in a current node; extracting resource identification information from the access request; determining whether data corresponding to the resource identification information in the access request is stored; and when the data has been stored, returning the data. The data is cached and positioned through the resource identification information, the same data can be identified for caching in the case of multiple URLs, and thus the storage amount in the same case can be reduced, the number of queries of the data during querying can be reduced, the hit rate of the data canbe improved, the frequency of back-to-source operations can be reduced, and the access pressure on a source website can be reduced.
Owner:BEIJING QIHOO TECH CO LTD
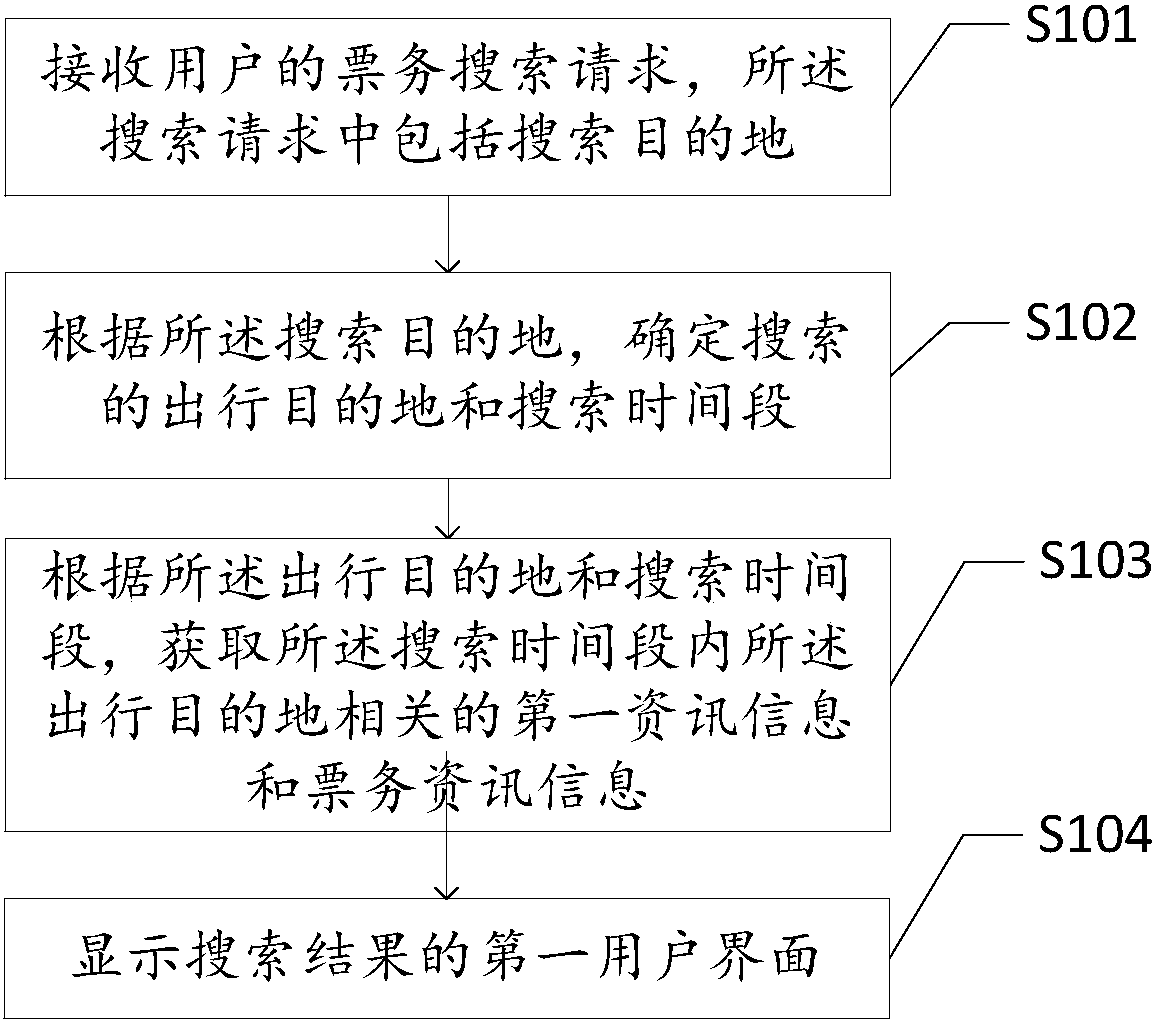
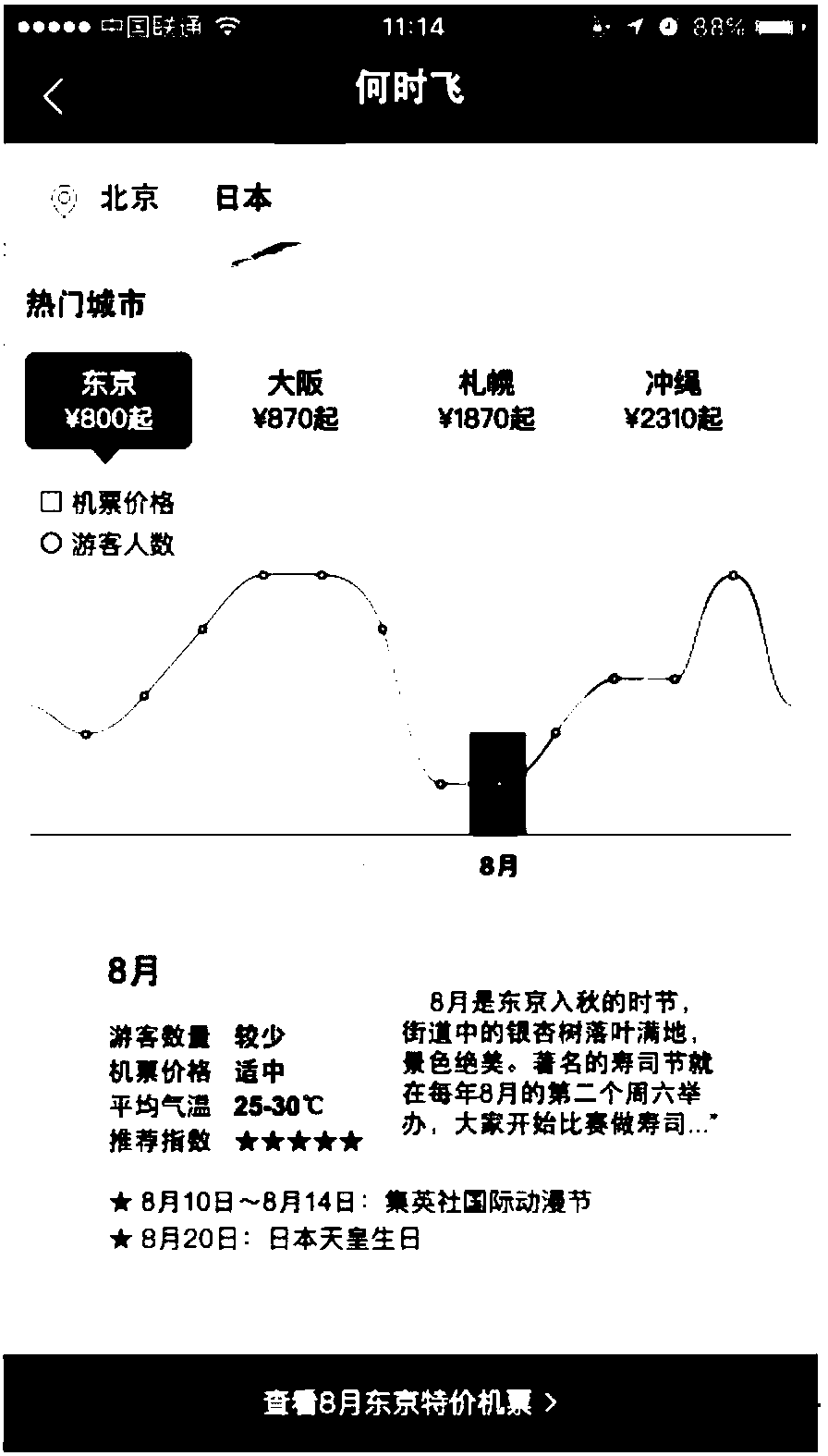
Information providing method and device based on ticket service searching
InactiveCN108268559AImprove experienceEasy to choose timeReservationsSpecial data processing applicationsDecision takingMultidimensional data
The invention discloses an information providing method and device based on ticket service searching. Through the method, first message information and ticket service message information related to atrip destination in a searching time period are obtained according to the trip destination, information with a reference value is provided for a user through a multidimensional data information way, and the user can make a basic decision for trip time through the first message information and ticket service message information provided by the method. In a word, by use of the method provided by theinvention, through multidimensional compound type information, including obtained first message information and ticket service message information and the like, the user is assisted in making a decision of trip time from each perspective, the information searching experience of the user is optimized, the interaction frequencies of a service side and a client side are reduced, and the pressure ofa server is reduced through the query frequencies of the service side. Meanwhile, the user can more conveniently, simply and quickly select time, the foreseeability of the user is enhanced, and user experience is improved.
Owner:ALIBABA GRP HLDG LTD
Method and device for querying data
ActiveCN106874325AReduce the number of queriesImprove query efficiencySpecial data processing applicationsDatabase
Owner:ANT WEALTH (SHANGHAI) FINANCIAL INFORMATION SERVICES CO LTD
Query track privacy protection method
ActiveCN109413067AReduce the number of queriesImprove privacy and securityLocation information based serviceTransmissionPrivacy protectionDifferential privacy
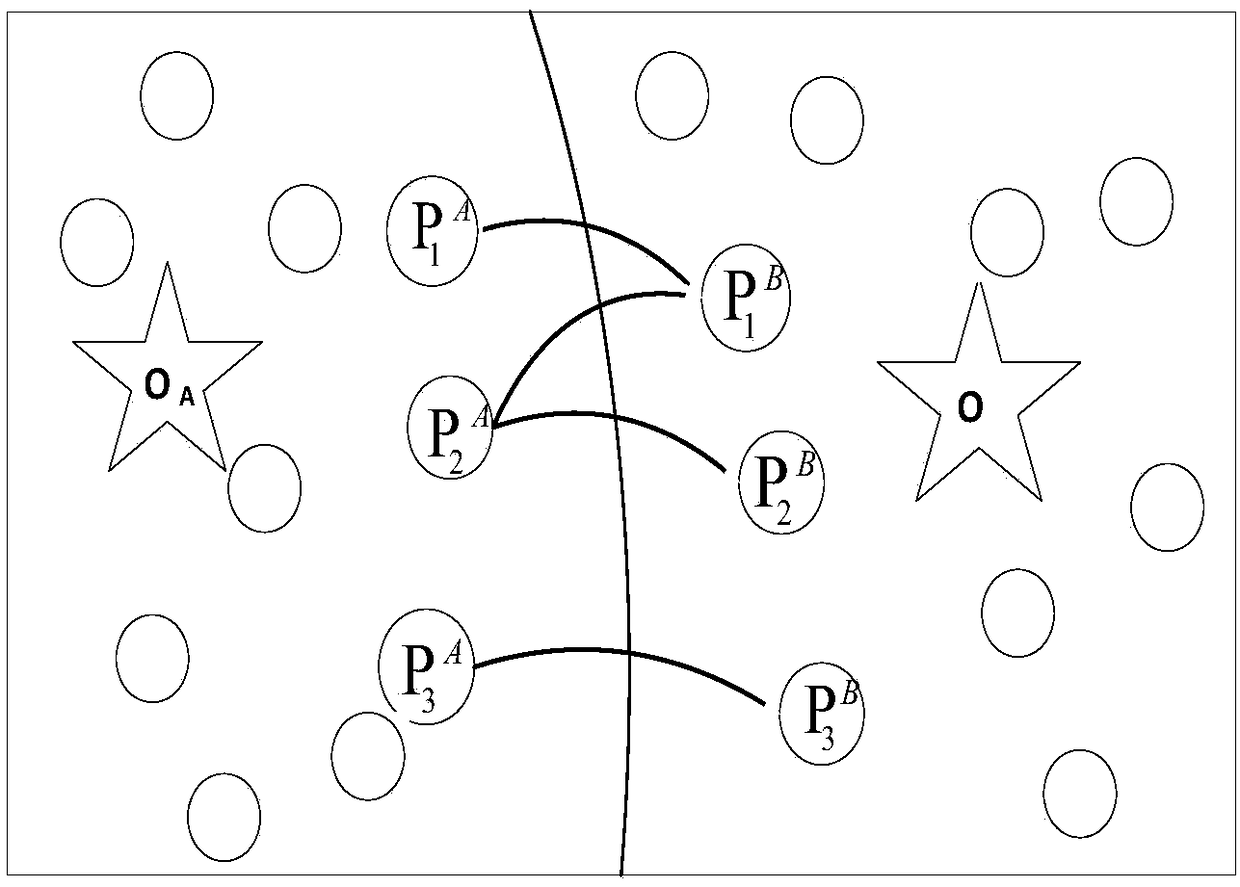
The invention discloses a query track privacy protection method, which is used for solving the privacy problem of continuous location service queries. Firstly, two query strategies of random locationsand suppression are designed on the basis of a service similarity principle, the problem of contradiction between quality of location services and privacy protection is solved, that is, service similarity is introduced for partitioning a map, when a user firstly requests a service in an area, a location is randomly selected in the same area to replace a real location thereof for requesting the service from a location server, then all subsequent queries in the same area are suppressed, and a result of a first query is directly utilized as a current query result; and secondly, a differential privacy protection method is introduced for controlling time intervals of cross-region queries, location privacy security of the cross-region queries is ensured, and the location correlation problem caused by short-time cross-region queries is solved.
Owner:FUJIAN NORMAL UNIV
Domain name query processing method
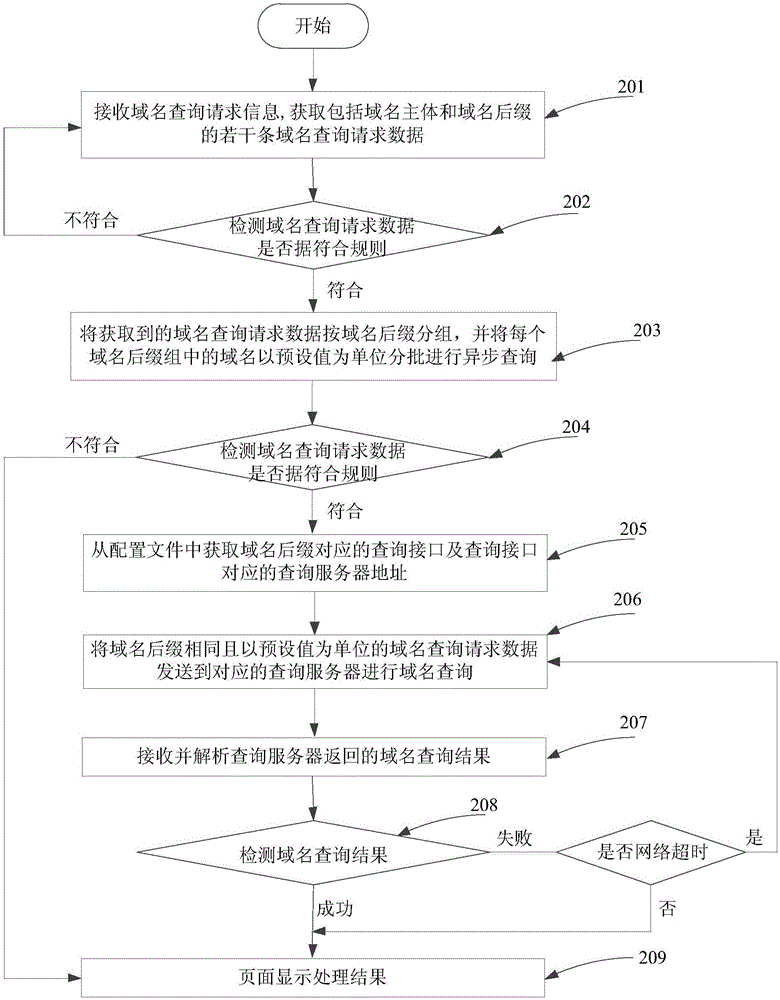
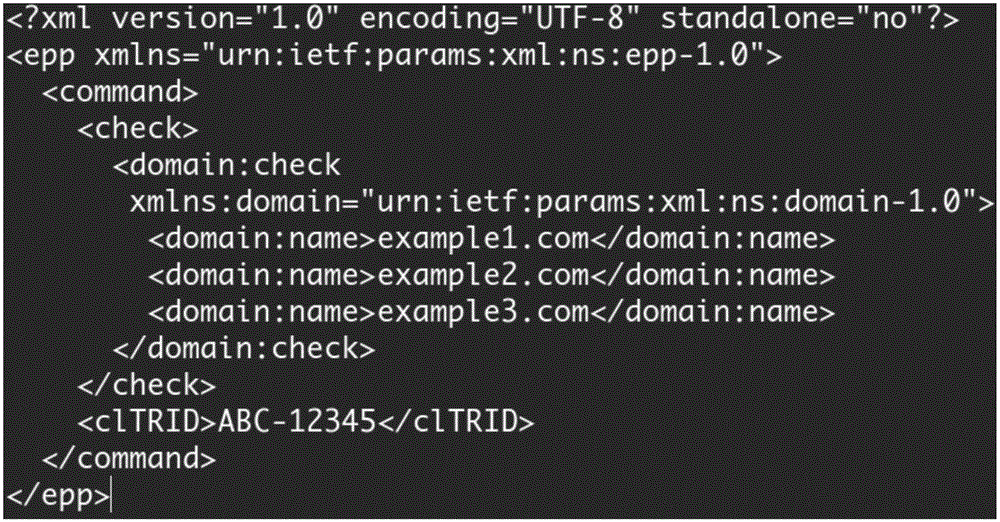
ActiveCN106412000AReduce the number of domain name queriesReduce domain name query pressureTransmissionData miningDomain name
The invention discloses a domain name query processing method. The method comprises the steps of receiving domain name query request information and obtaining multiple pieces of domain name query request data comprising domain name bodies and domain name suffixes; grouping the obtained domain name query request data according to the domain name suffixes and carrying out batched asynchronous query on domain names in each domain name suffix group by taking a preset value as a unit; obtaining query interfaces corresponding to the domain name suffixes and query server addresses corresponding to the query interfaces from a configuration file; sending the domain name query request data with the same domain name suffixes to the corresponding query servers for domain name query, wherein the domain name query data take the preset value as the unit; and receiving and analyzing domain name query results returned by the query servers. According to the domain name query method provided by the invention, the domain name query times and the query pressure of the query servers are reduced, the query response time is accelerated, and moreover, a query success rate is improved.
Owner:XIAMEN ENAME TECH CO LTD
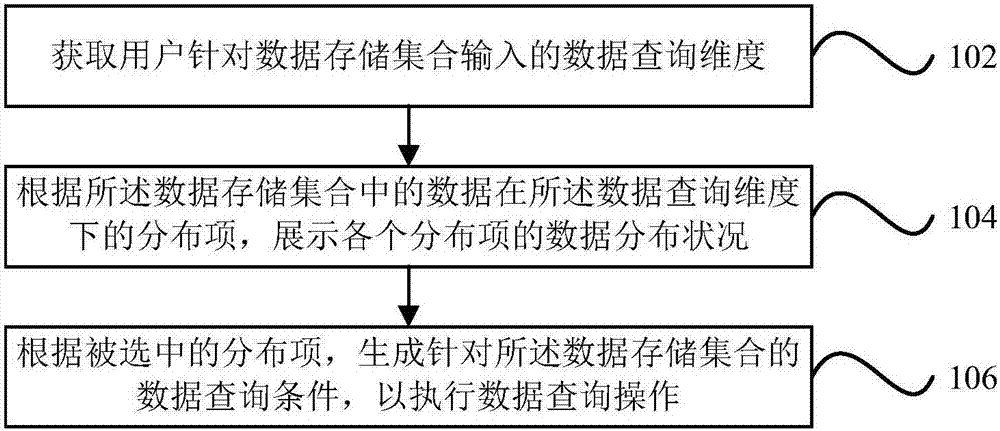
Data query methods and devices
InactiveCN107515875AMeet needsImprove matchOther databases queryingSpecial data processing applicationsData query
The application provides data query methods and devices. One of the methods can includes: acquiring a data query dimension input by a user for a data storage set; according to distribution items which are of data in the data storage set and under the data query dimension, displaying data distribution status of each distribution item; generating a data query condition for the data storage set according to a selected distribution item to execute a data query operation. Through the technical solution of the application, the data distribution status can be displayed before querying, and reasonably setting the data query condition by the user according to the same is facilitated.
Owner:ALIBABA GRP HLDG LTD
Adversarial sample generation method for image recognition model classification boundary sensitivity
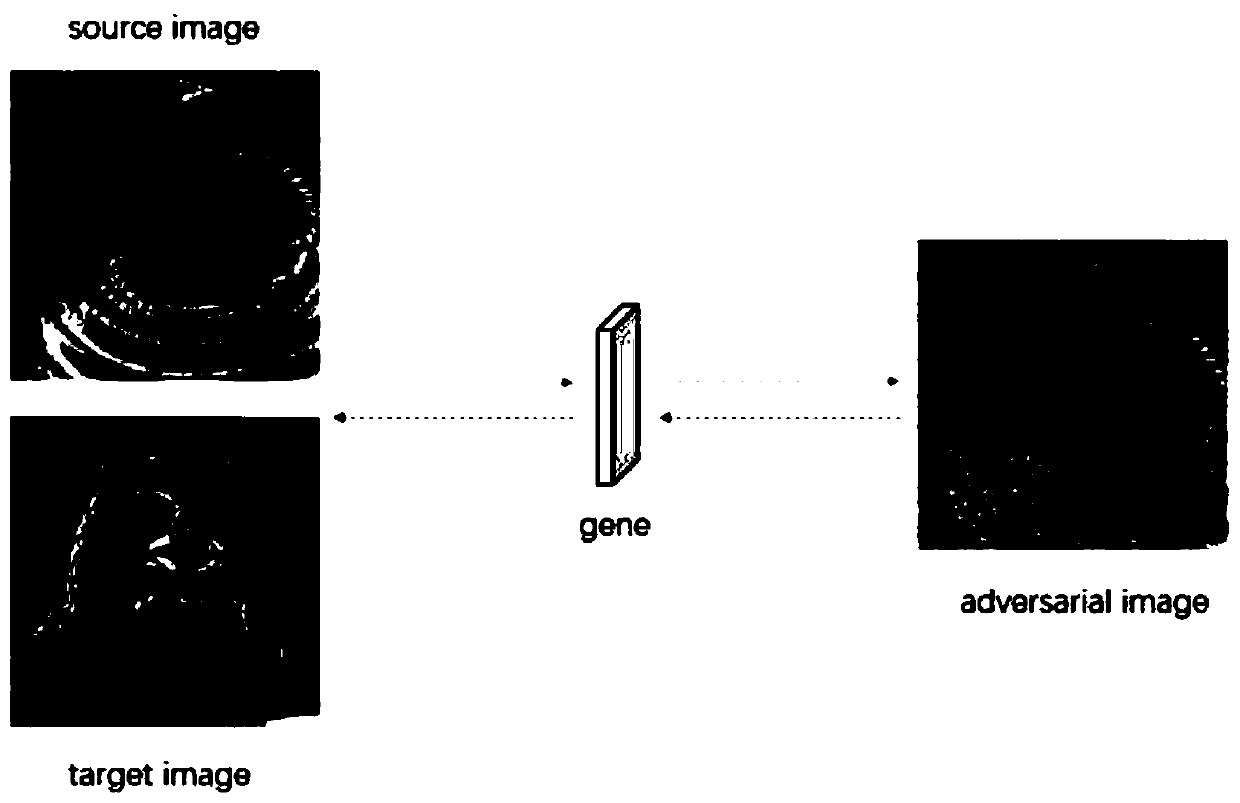
ActiveCN109961145AGood effectReduce the number of queriesCharacter and pattern recognitionGenetic algorithmsPopulationPixel value difference
The invention discloses an adversarial sample generation method for image recognition model classification boundary sensitivity, and belongs to the field of neural network security and machine adversary. The method comprises the following steps: step 1, setting initial parameters; 2, generating an initial gene population; step 3, carrying out gene crossover; step 4, carrying out gene variation; step 5, carrying out gene selection; step 6, performing gene evolution iteration; step 7, reducing the number of different pixel points of the adversarial sample and the original sample; step 8, reducing the number of different RGB channels of the adversarial sample and the original sample; and step 9, reducing the pixel value difference between the adversarial sample and the original picture. The black box attack method provided by the invention does not depend on the confidence coefficient returned by the model, and only needs one final classification label; the method has a very good effect on generating adversarial samples for large-scale pictures; under the condition that parameter adjustment is appropriate, the number of query times required by the method is smaller than that requiredby a common decision boundary-based attack method.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Tag anti-collision method based on self-adaptive hybrid query tree in RFID (radio frequency identification) system
InactiveCN102663333AImprove performanceAddressing impacts on anti-collision performanceSensing record carriersSpecial data processing applicationsTime delaysBinary tree
The invention relates to a tag anti-collision method based on a self-adaptive hybrid query tree in an RFID (radio frequency identification) system. The tag anti-collision method includes firstly, establishing a binary-to-ternary conversion method for electronic product codes (EPCs) of electronic tags, secondly, providing a method for constructing a ternary query tree to identify the tags, thirdly, valuing according to lengths of the EPCs to construct the hybrid query tree method to solve the problem of coexistence of a binary tree and a ternary tree, and finally, setting entry and departure mechanisms to acquire the tag anti-collision method of the self-adaptive hybrid query tree according to mobility of the tags. The tag anti-collision method based on the self-adaptive hybrid query tree in the RFID (radio frequency identification) system has the advantages that the ternary tree method has optimized performance in the tag anti-collision method based on a tree structure, the problem that complete ternary conversion of the EPCs fails is solved, the difficulty in identifying the moving tags is overcome, time delay of identification is shortened well, and the colliding and idling processes are reduced. In addition, the tag anti-collision method is suitable for RFID scenes with large-scale movable tags.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
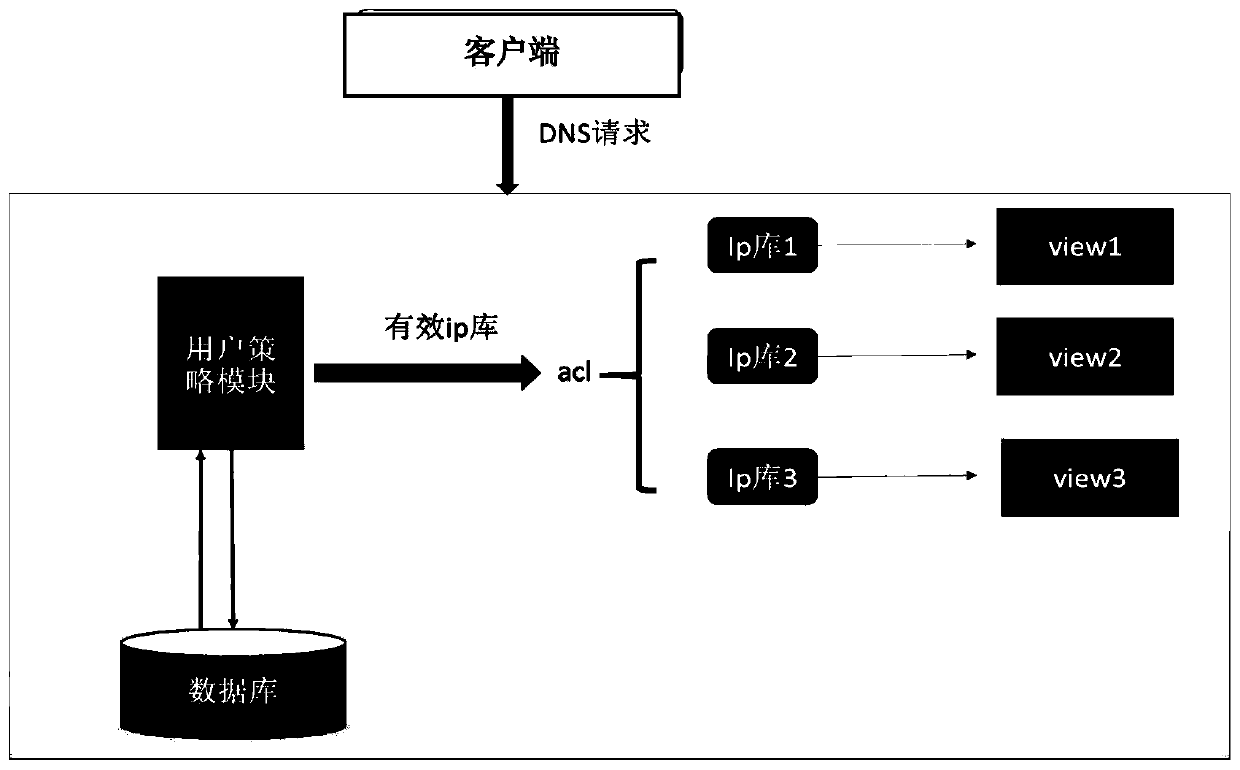
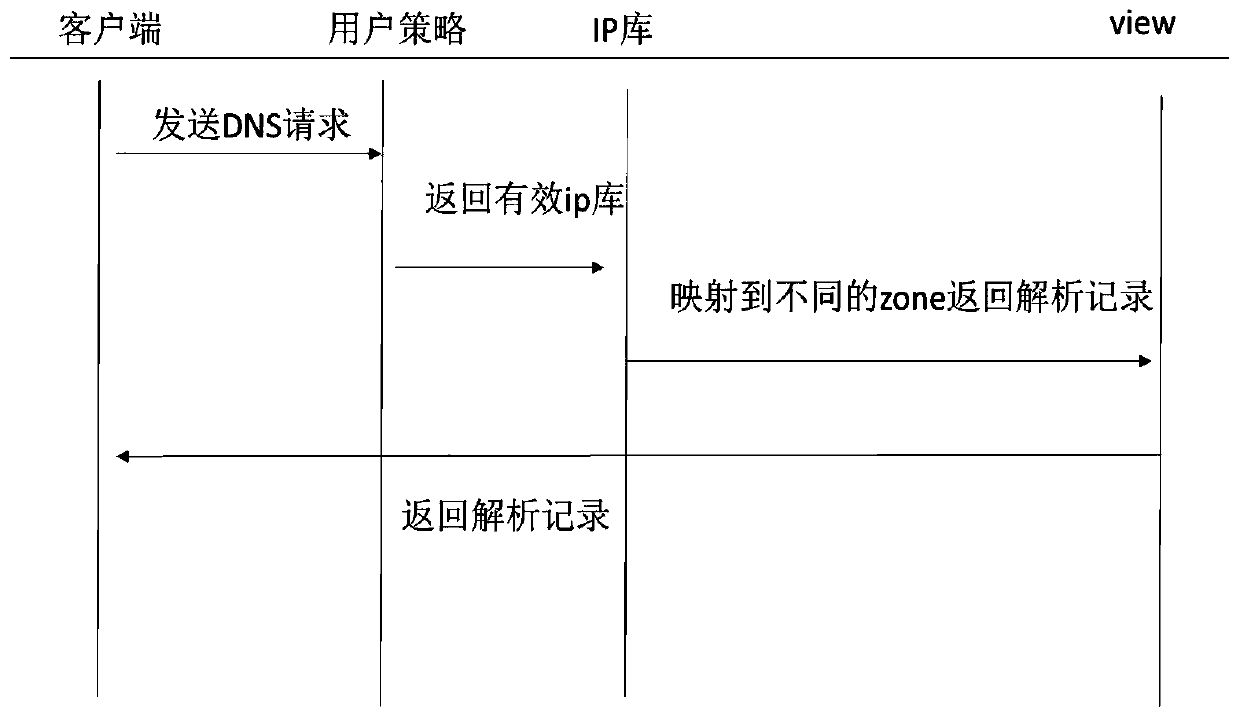
DNS intelligent scheduling method based on a user strategy
InactiveCN109905496AReduce the number of queriesImprove analysis efficiencyTransmissionDomain nameDistributed computing
The invention particularly relates to a DNS intelligent scheduling method based on a user strategy. According to the DNS intelligent scheduling method based on the user strategy, a user strategy module and a user strategy database are newly added in a DNS system; The IP library is classified according to operators and regions; After the user configures the line type and maps the domain name, the user strategy module automatically reads strategy information and stores the domain name and the corresponding regional operator combination into a database; And when the domain name resolution requestreaches the DNS system, the user strategy module inquires a corresponding regional operator according to the domain name, narrows the range of inquiring the IP library, and then accurately positionsthe IP library of the request source from the effective IP library so as to return different resolution results. According to the DNS intelligent scheduling method based on the user strategy, the problem that efficiency is low due to the fact that a large number of invalid IP libraries are frequently queried in a traditional DNS intelligent scheduling method is solved, the effective IP libraries are screened out by additionally arranging the user strategy module and the user strategy database, the query frequency is reduced, and therefore the analysis efficiency is greatly improved.
Owner:上海浪潮云计算服务有限公司
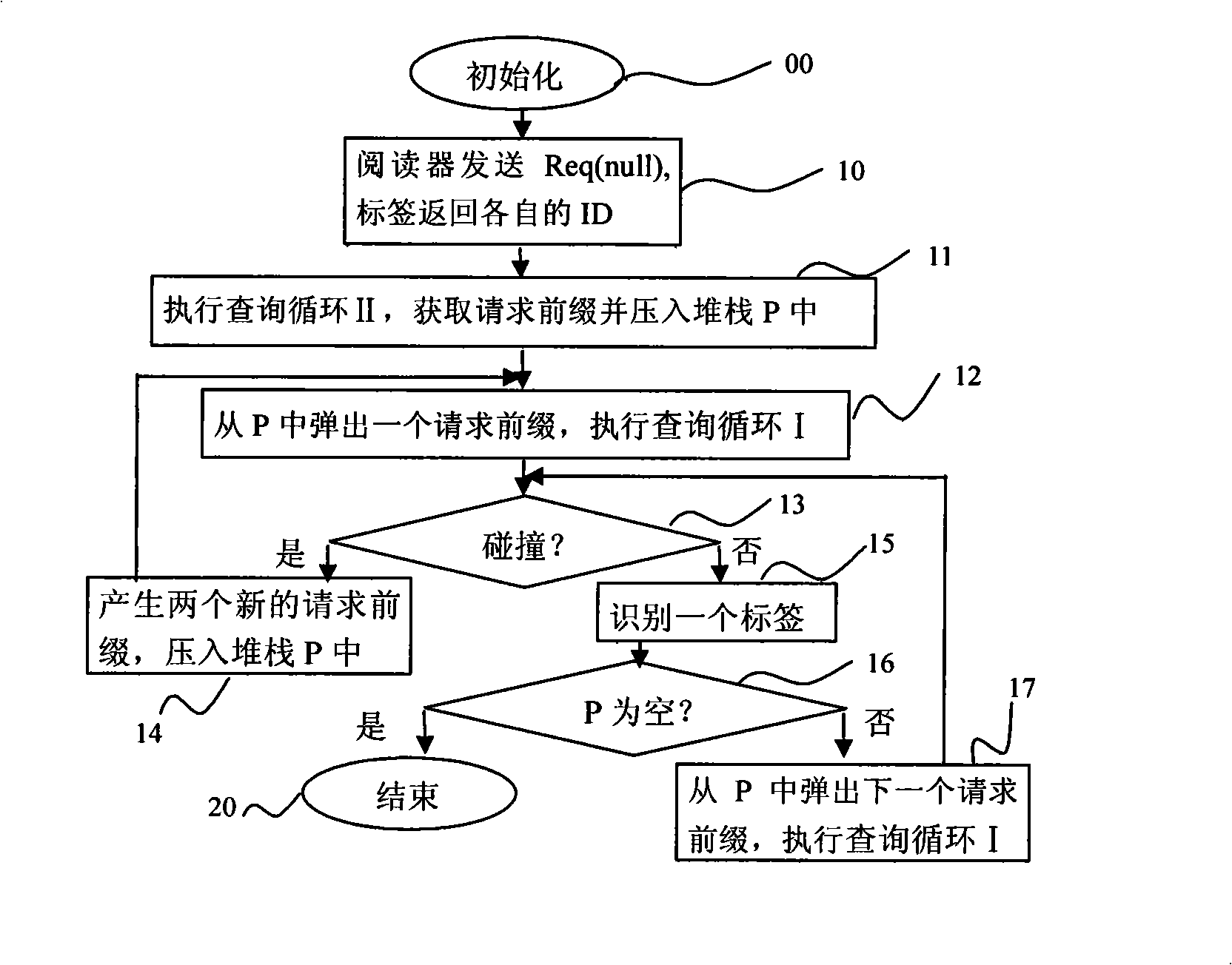
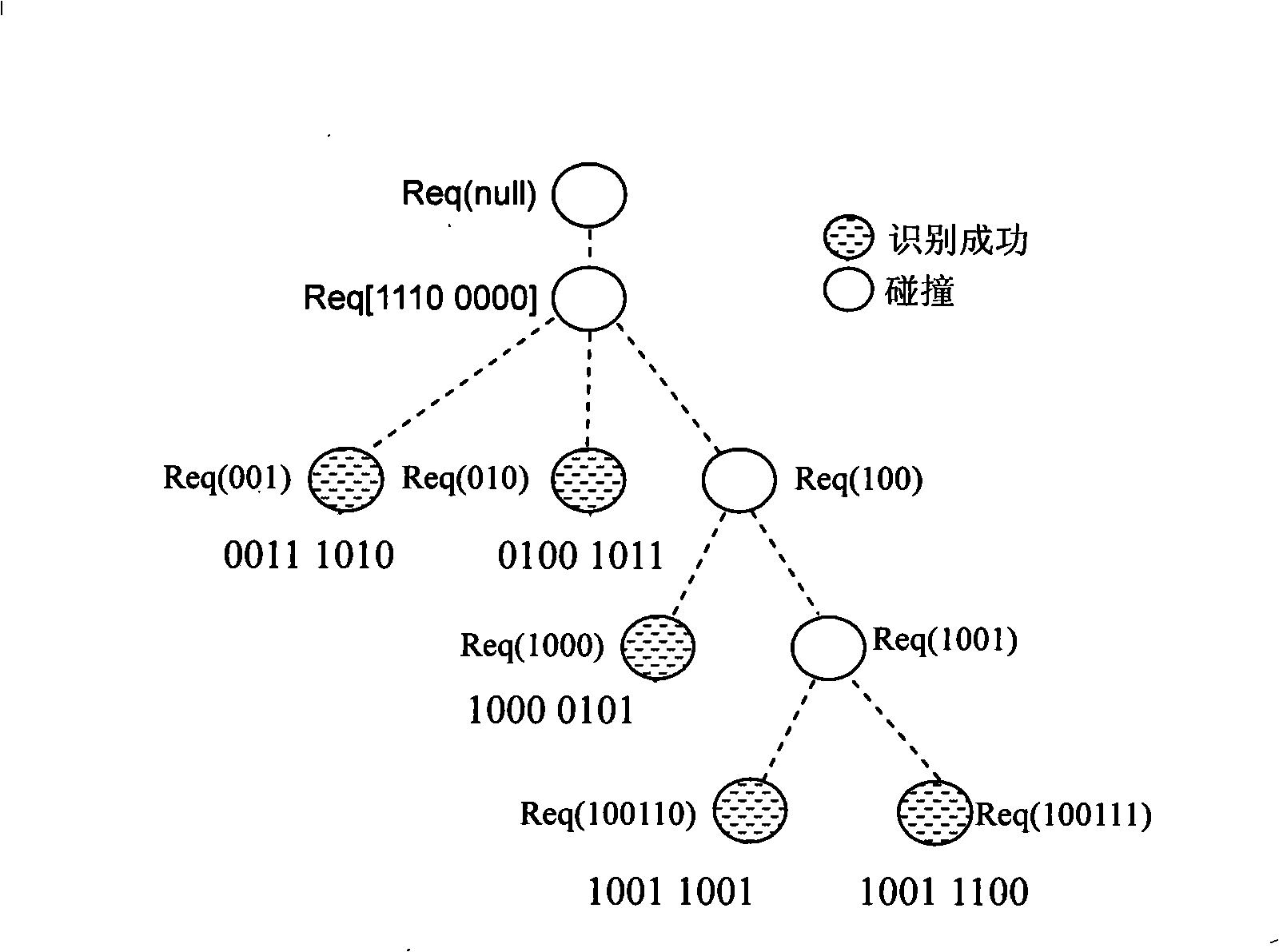
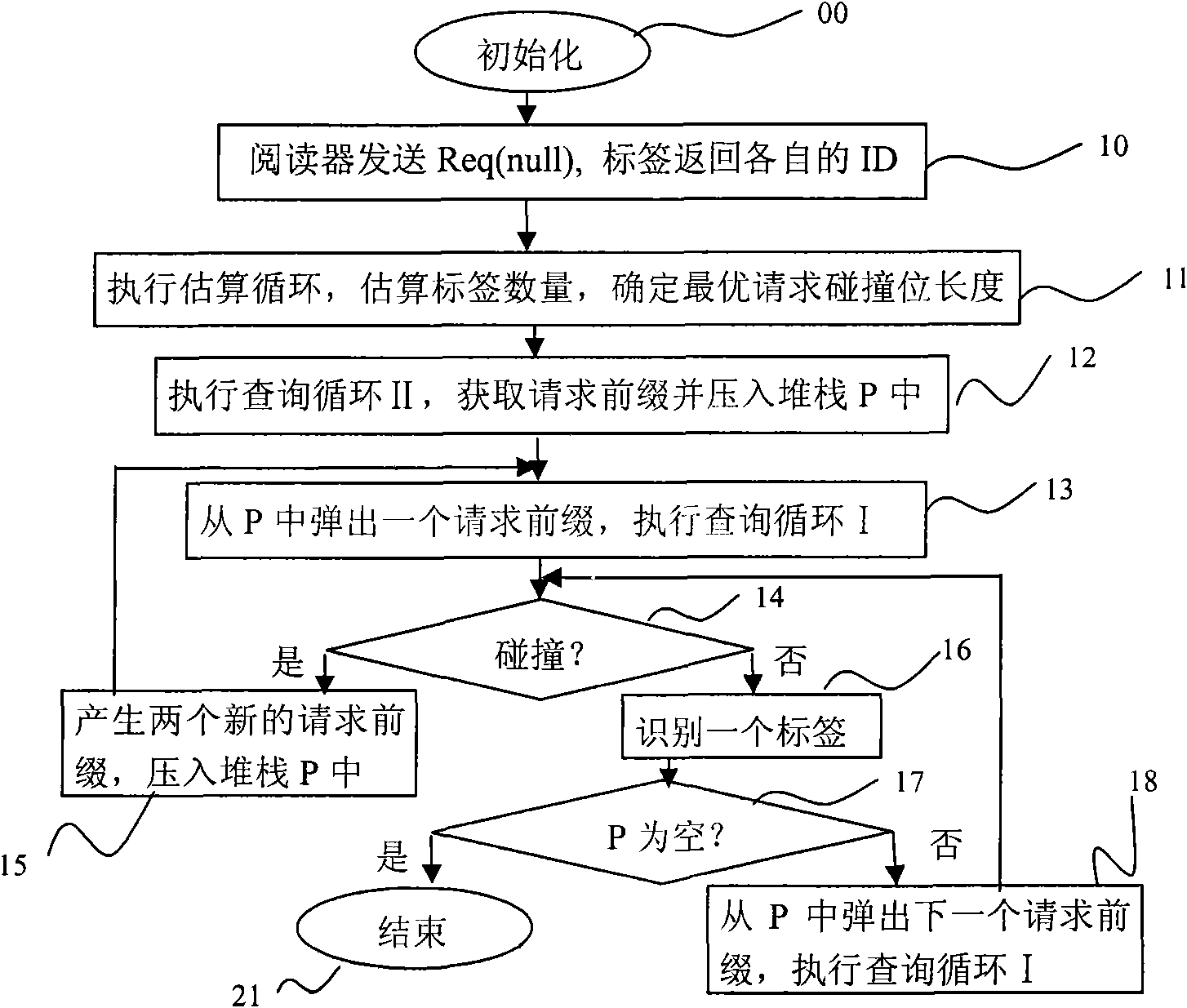
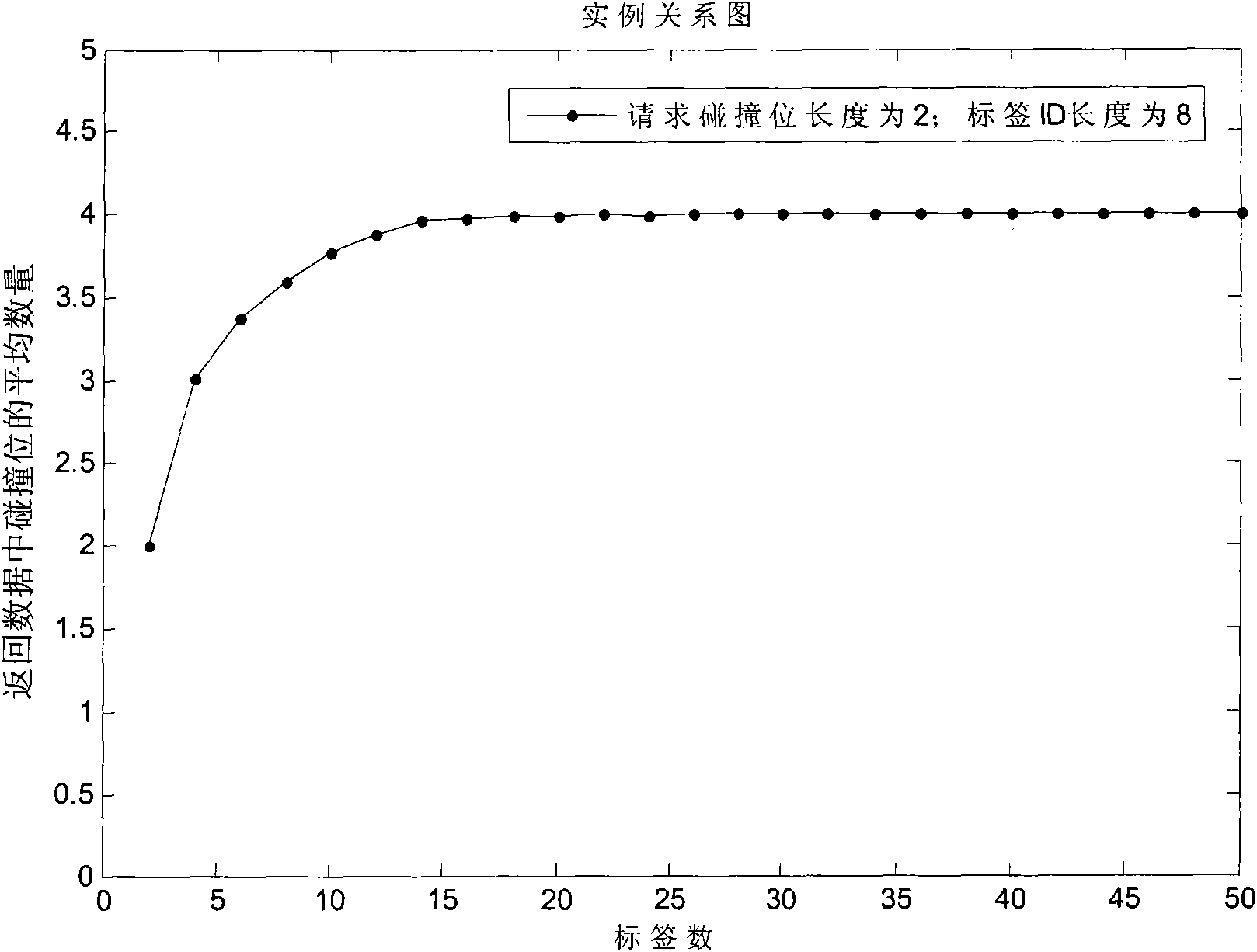
Label recognition anti-collision method for RFID system
InactiveCN101324916AImprove recognition efficiencyQuick identificationSensing record carriersSystem identificationEmbedded system
The invention discloses a tag identification and anti-collision method for an RFID system. The method provides a novel enquiry circulation, that is, an enquiry circulation II to acquire a request prefix and greatly reduce the times of the whole enquiry and whole number of transmission bits. The method comprises the following steps: firstly, the request prefix is acquired through the enquiry circulation and pressed in a stack; secondly, a request prefix pops up from the stack and an enquiry circulation I is conducted; if no collision occurs, a tag is identified; if collision happens, another two request prefixes are acquired and pressed in the stack; and another request prefix pops up from the stack, and the enquiry circulation I is conducted; the steps are repeated until the stack is empty and all tags are identified. The method has the advantages of easy operation, reduced energy consumption, identification efficiency of a system as high as 87.0 percent, and suitability for applying to the RFID system.
Owner:SOUTH CHINA UNIV OF TECH
Black box depth model adversarial sample generation method
ActiveCN111507384AReduce the number of queriesIncrease success rateCharacter and pattern recognitionNeural learning methodsBlack boxComputer engineering
The invention relates to a black box depth model adversarial sample generation method, which can effectively reduce the query frequency of a model. The method aims at solving the problems that a traditional black box attack method is large in solution space, difficult to optimize and high in query frequency. For an input picture, a low-frequency frequency-based anti-noise space is randomly selected, and a high-dimensional optimization problem of anti-noise is converted into a low-dimensional optimization problem of corresponding amplitude, so that the purpose of effectively reducing the queryfrequency of the model is achieved.
Owner:XIAMEN UNIV
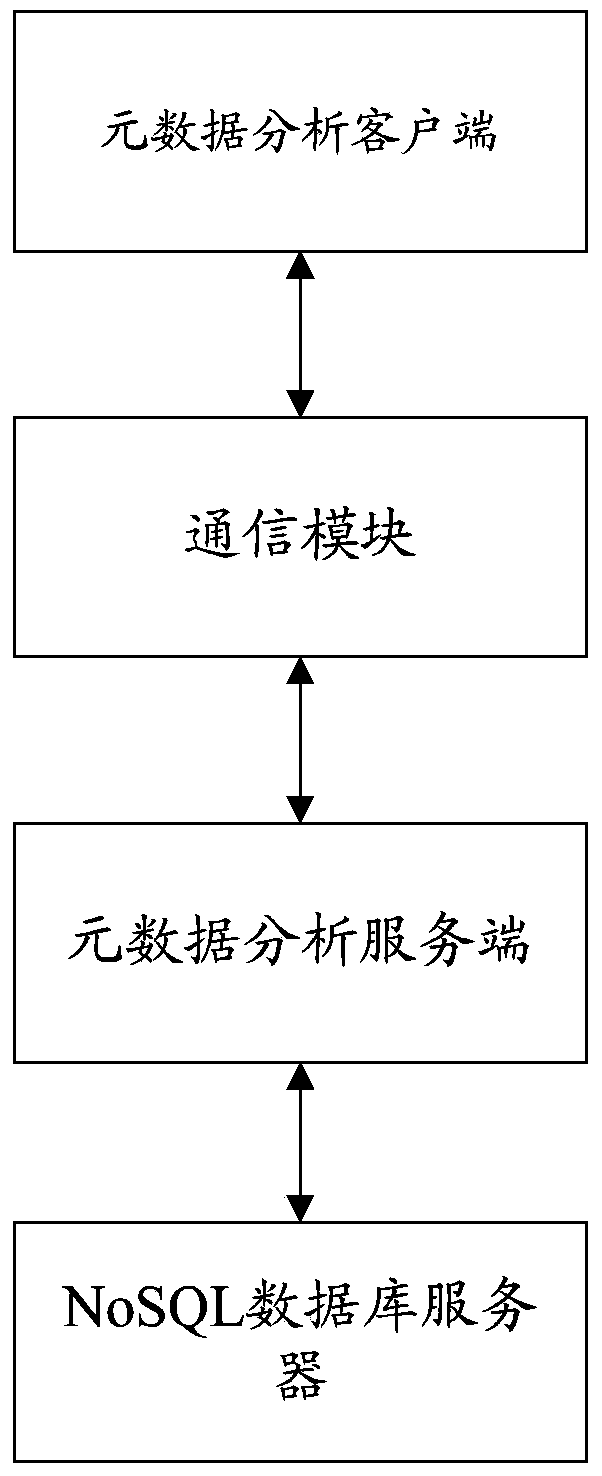
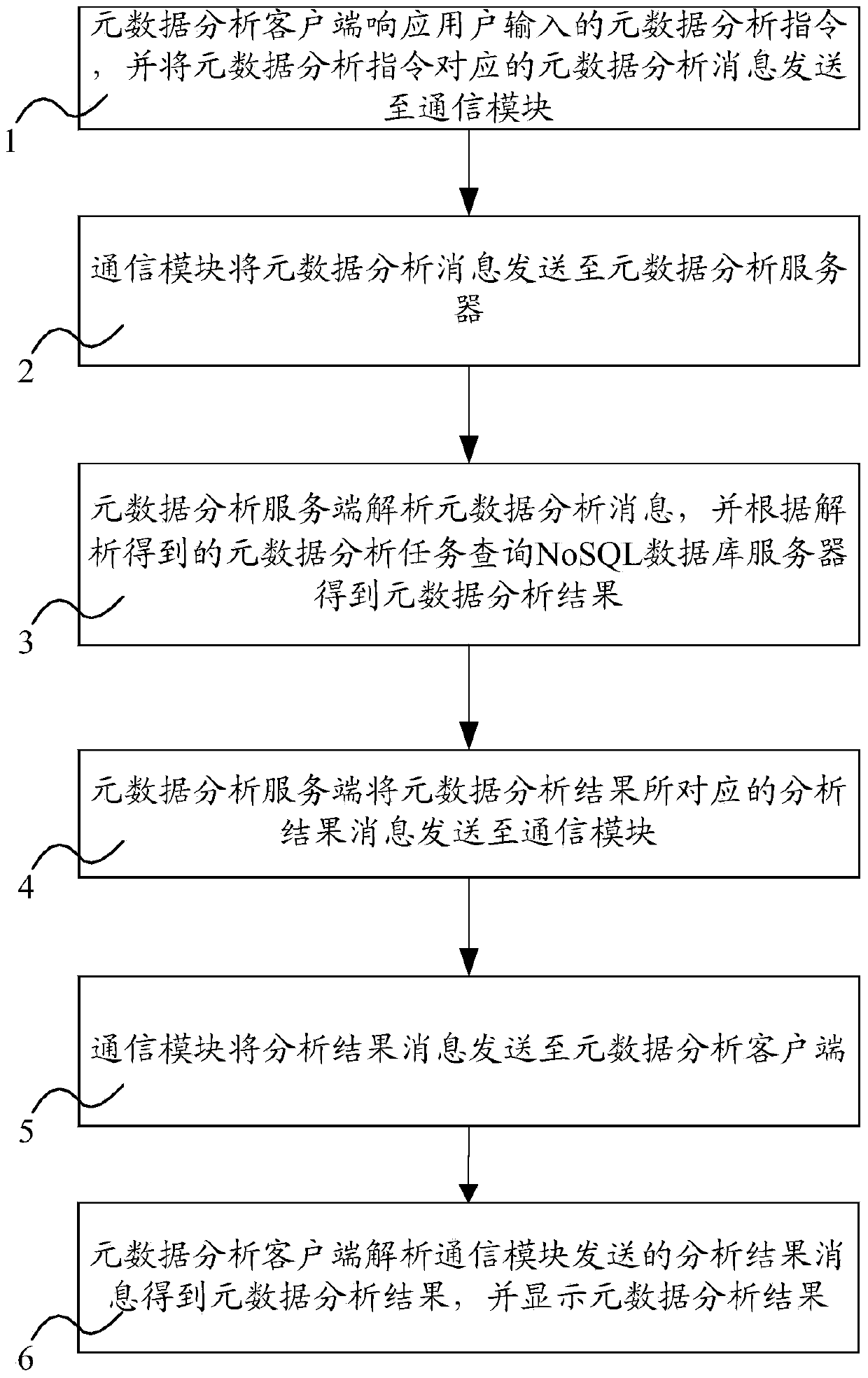
System and method for realizing metadata cache and analysis based on NoSQL and method
InactiveCN104199978AReduce head seek timeImprove efficiencySpecial data processing applicationsData bufferServer-side
Owner:PRIMETON INFORMATION TECH
Binary search anti-collision method with unknown label quantity estimation function
InactiveCN101650770ARecognition efficiency is stableImprove efficiency and stabilitySensing record carriersBit-length
The invention discloses a binary search anti-collision method with unknown label quantity estimation function. The method includes that: a reader sends a label identification request, all labels return the whole identification code; estimation circulation is executed, the reader estimates the label quantity according to collision bit quantity returned by a search circulation II and determines request collision bit length of a next search circulation; the search circulation II is executed to obtain request prefix, the request prefix is pressed into a stack; one request prefix is popped out fromthe stack, the search circulation I is executed, if no collision is existed, one label is identified, or two new request prefixes are obtained to be pressed into the stack; and the process is repeatedly executed until the stack is empty and all the labels are identified. The invention utilizes interrelation of label quantity and collision bit quantity returned by the search circulation II to estimate the label quantity and combines the search circulation I and the search circulation II to rapidly identify the labels, the average search times for identification on one label is maintained to be1.26-1.15, so that label identification efficiency is improved.
Owner:SOUTH CHINA UNIV OF TECH
Deterministic anti-collision algorithm based on multi-prefix matching of query tree method
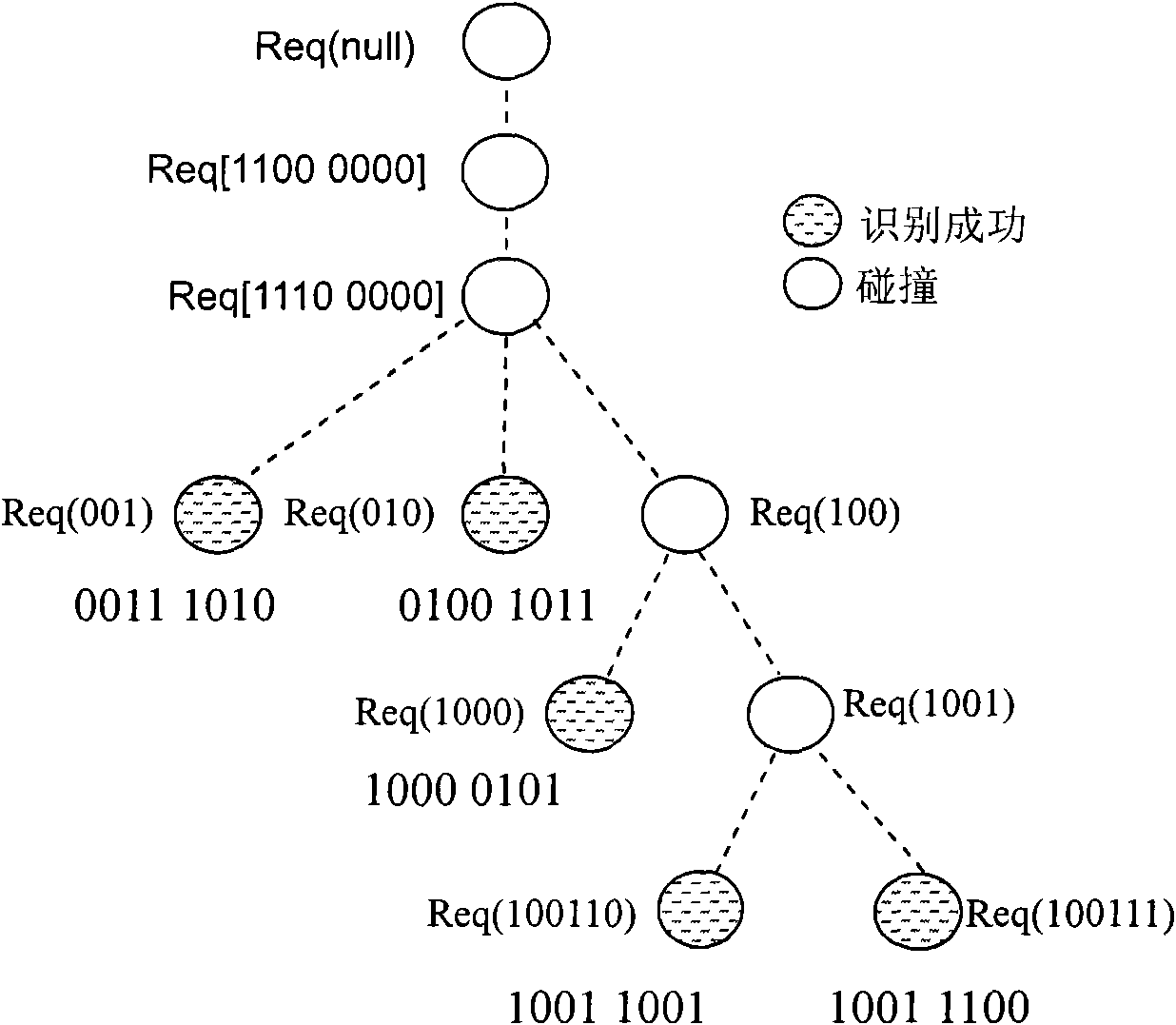
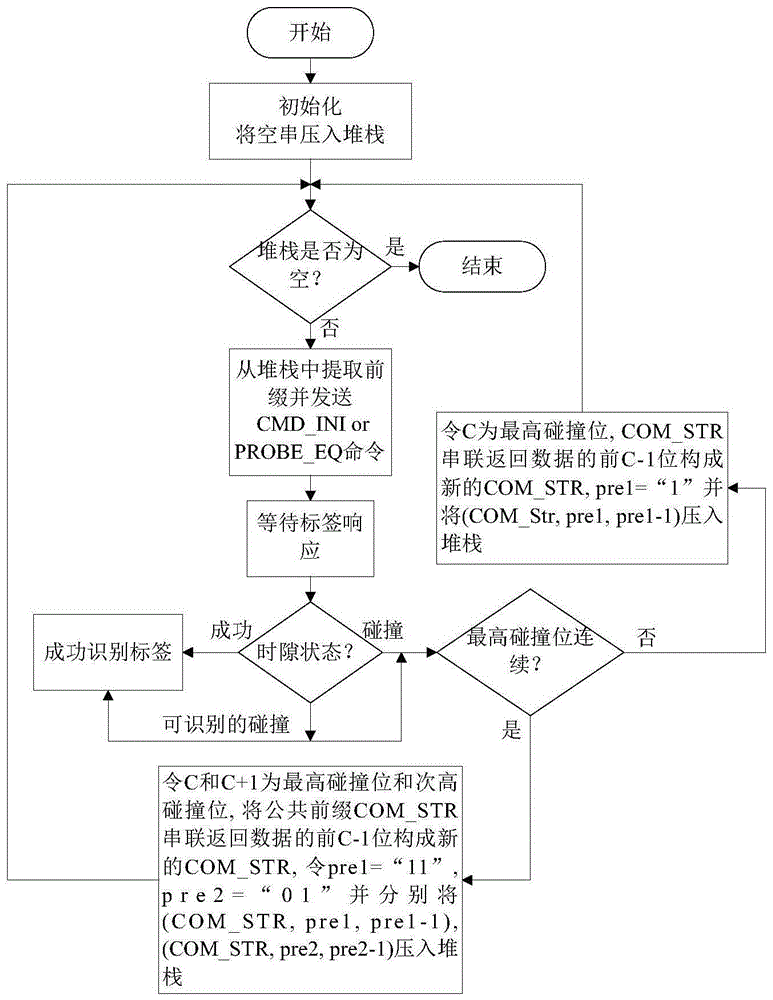
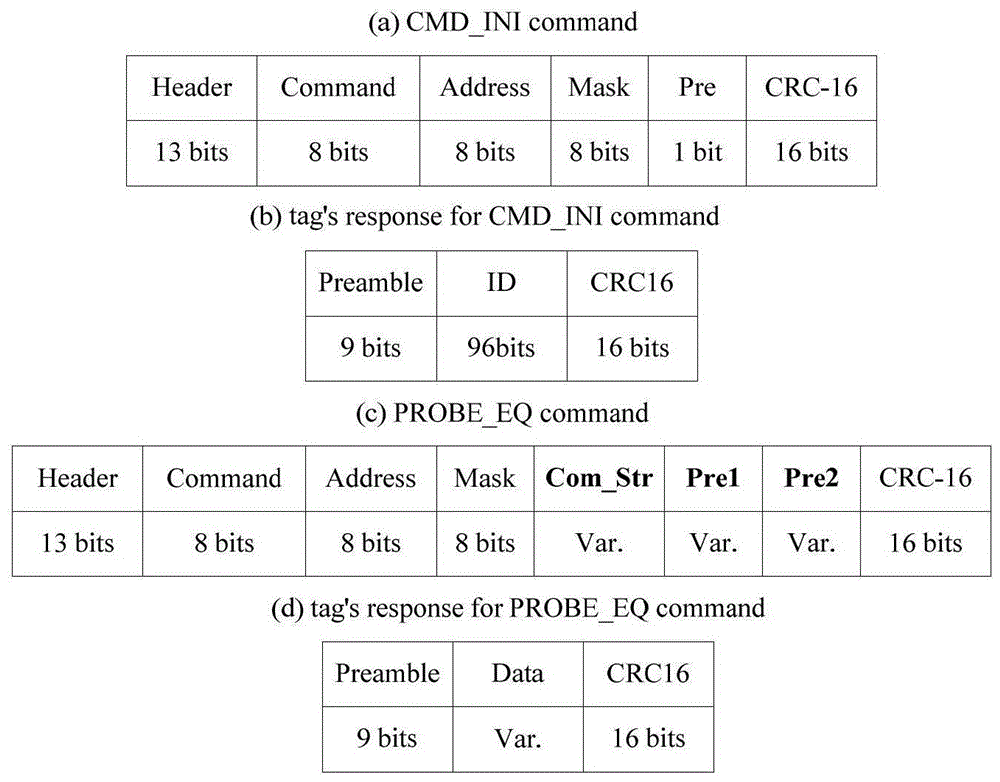
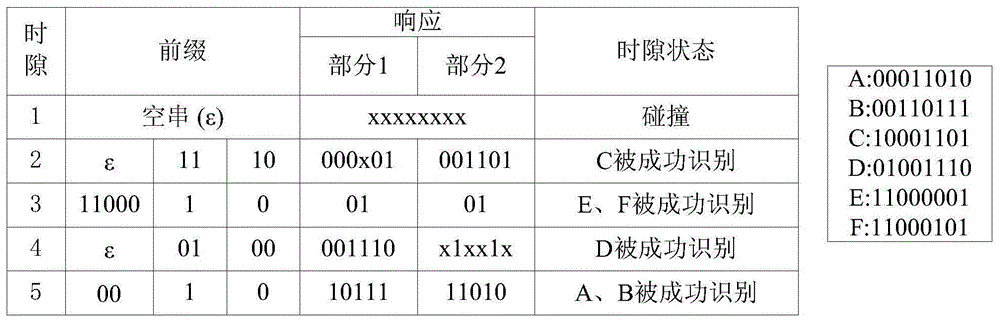
ActiveCN105046181AEliminate idle slots or empty nodesReduce the number of queriesSensing record carriersDeterministic encryptionReader writer
The present invention discloses a deterministic anti-collision algorithm based on multi-prefix matching of a query tree method. The algorithm comprises the following steps of: reading a query prefix and sending a query command by a reader-writer; receiving the query command and responding matching by a tag; receiving the response by the reader-writer; responding a successful end process, generating collision and going to step 4; detecting response collision positions, and if the highest collision position and the second-highest collision position are continuous collision positions, going to step 5; if the highest collision position and the second-highest collision position are not continuous collision positions, going to step 6; forming a new common prefix, giving a subsequent numerical value, pressing into a stack respectively at last, and going to step 7; forming a new common prefix, giving a subsequent numerical value, pressing into a stack at last, and going to step 7; if the stack is determined to be empty, ending the entire identification process; or otherwise, returning to step 1. The deterministic anti-collision algorithm has the following beneficial effects: a multi-prefix matching and query technology is introduced, the identification of multiple tags by one time slot is realized by virtue of a prefix 1 and a prefix 2, idle time slots of a multi-ary algorithm are completely eliminated, the query times is reduced, and the query efficiency is improved.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Multi-label anti-collision guiding identification method for RFID system
InactiveCN102663332AAvoid backtracking searchesReduce the number of queriesSensing record carriersFir systemPost collision
The invention, which relates to the radio frequency identification (RFID) field in the internet of things, discloses a multi-label anti-collision guiding identification method for an RFID system. The method mainly comprises the following steps that: a reader sends a query command, all labels return whole label numbers and the reader receives data; after the reader determines that there is collision, a binary tree is obtained by splitting at a highest collision bit, wherein a left sub-tree branch is 0 and a right sub-tree branch is 1, and the reader issues a query instruction again and a query sequence is realized based on a guiding mode; and according to the guide mode, a branch with fewest collision bits is searched first. According to the invention, backtracking searching of a dynamic binary identification method can be avoided and the number of times for query is reduced; identification efficiency of a reader on multiple labels is substantially improved; and the provided method is suitable for rapid identification of the multiple electronic labels by the reader in an RFID system.
Owner:HUAZHONG NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com