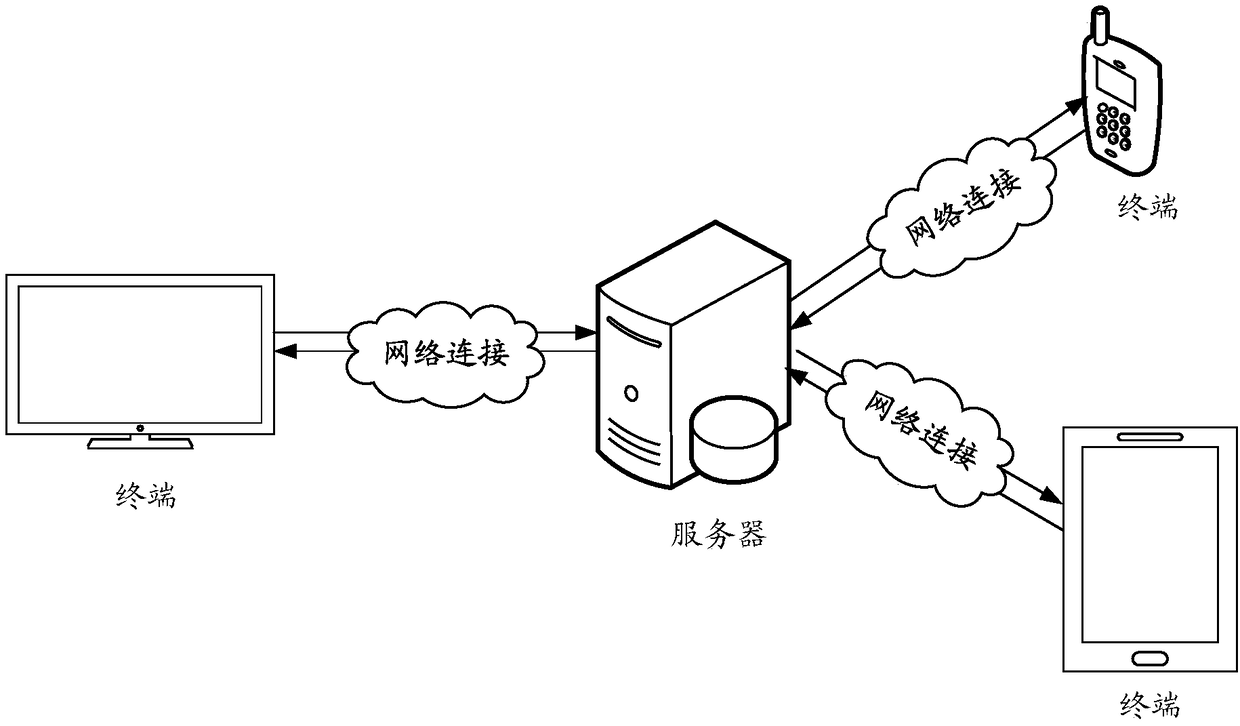
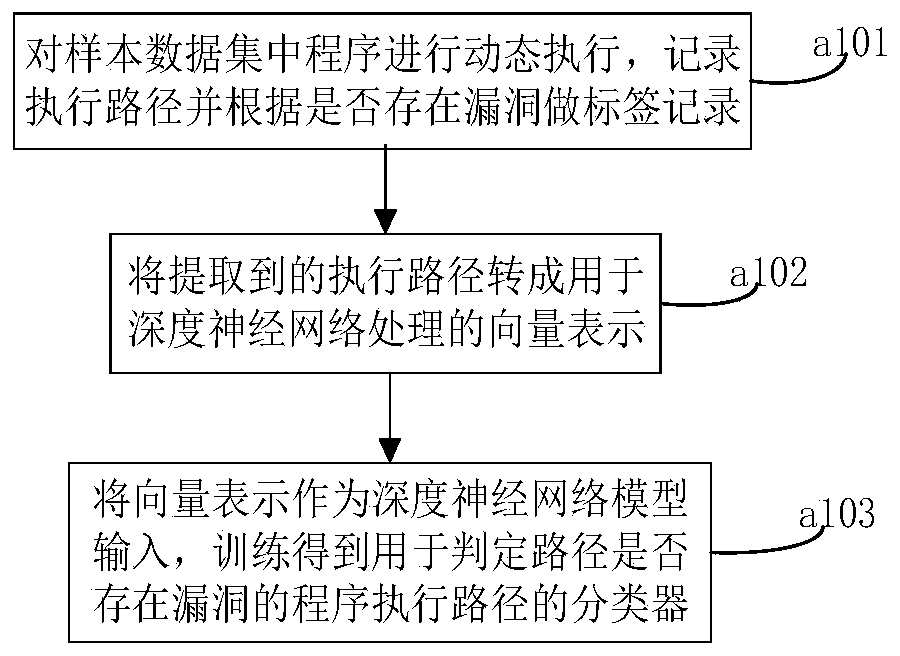
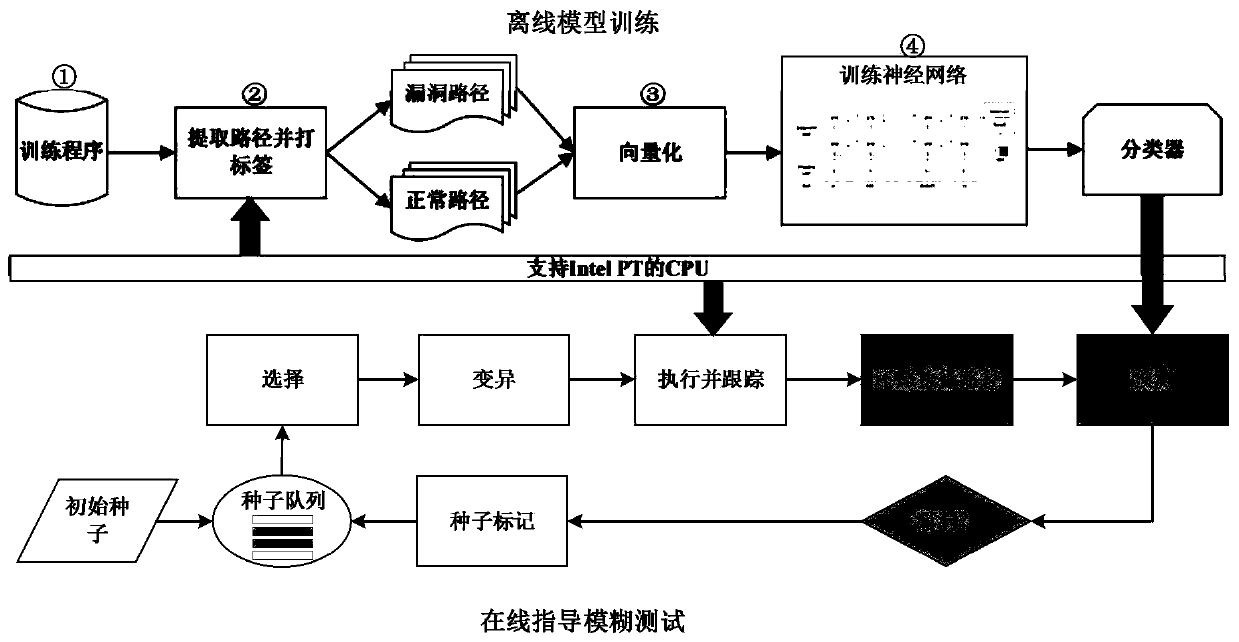
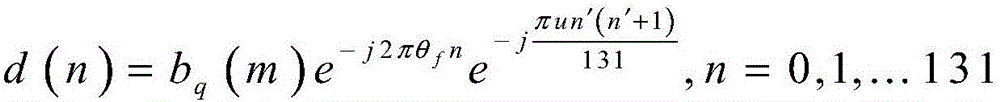Patents
Literature
199results about How to "Improve discovery efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
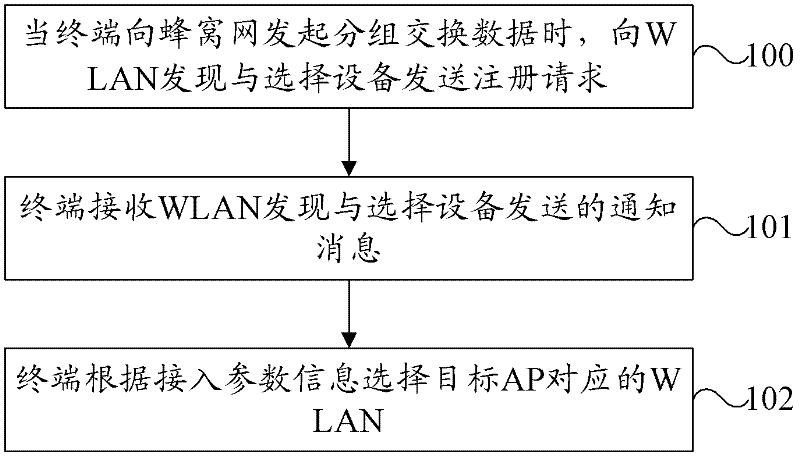
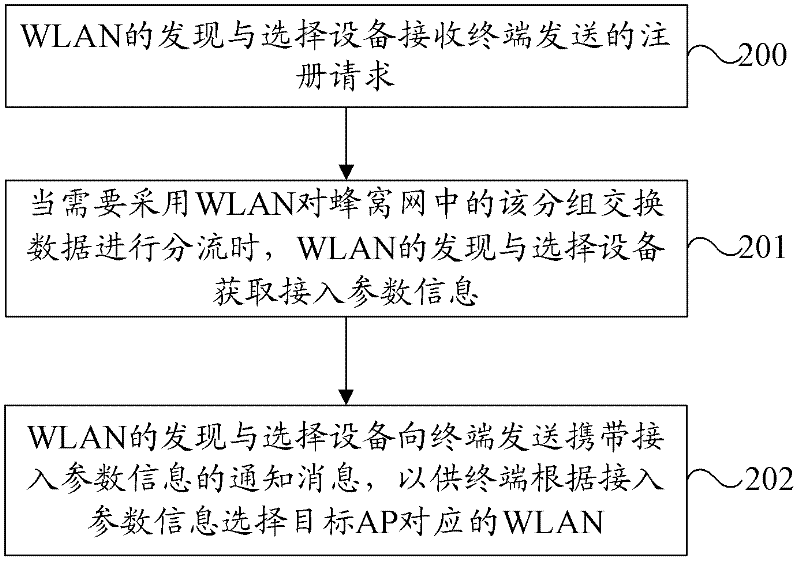
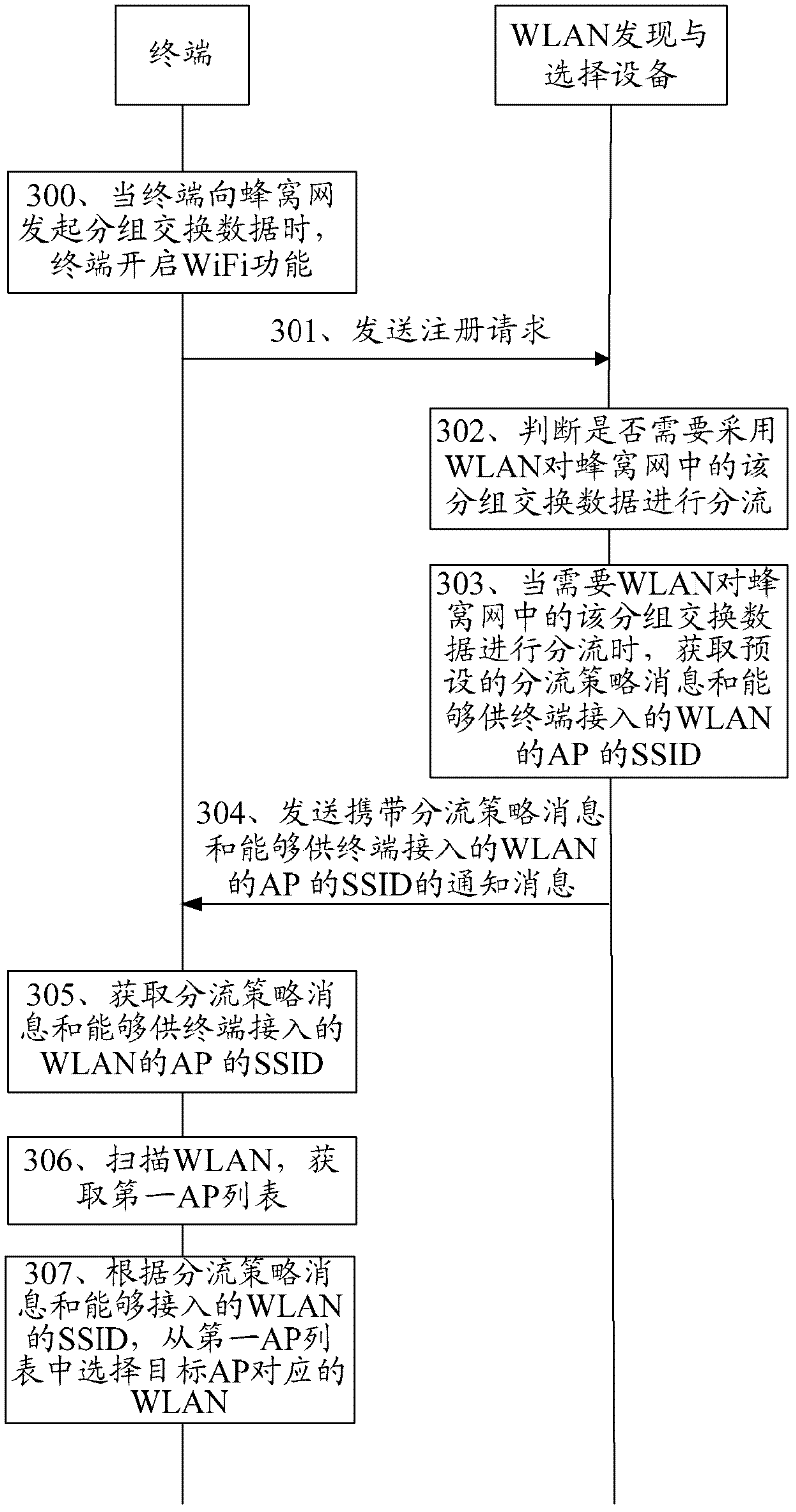
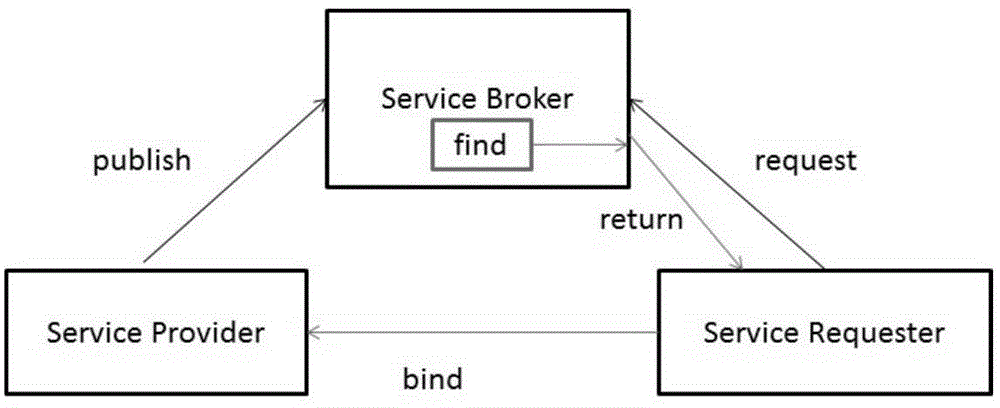
Discovery and selection method, equipment, system and terminal of wireless local area network (WLAN)
ActiveCN102647771AImprove discovery efficiencyImprove selection efficiencyAssess restrictionNetwork topologiesWireless access pointPacket switching
The embodiment of the invention provides a discovery and selection method, equipment, system and terminal of a wireless local area network (WLAN). The method comprises the following steps of: when initiating packet switch data to a cellular network, sending a registration request to the discovery and selection equipment of the wireless local area network; receiving a notification message sent by the discovery and selection equipment of the wireless local area network when determining that the wireless local area network needs to be used to offload the packet switch data in the cellular network, wherein the notification message carries access parameter information; and selecting a target wireless access point according to the access parameter information. With the technical scheme provided by the embodiment of the invention, when a terminal initiates the packet service data to the cellular network, the operation of discovery and selection of the WLAN are carried out, and thus the efficiency of discovery and selection of WiFi (Wireless Fidelity) can be effectively improved.
Owner:金湖县综合检验检测中心
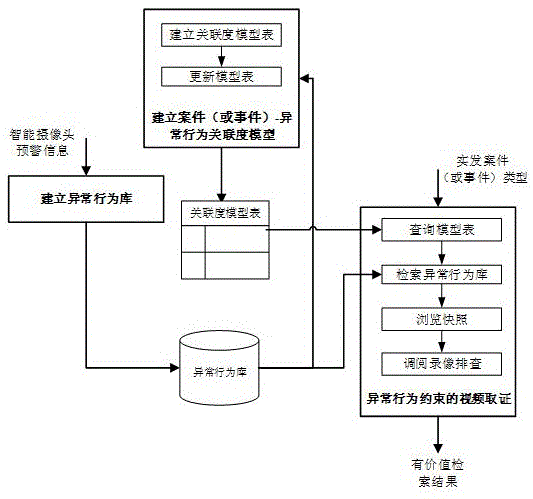
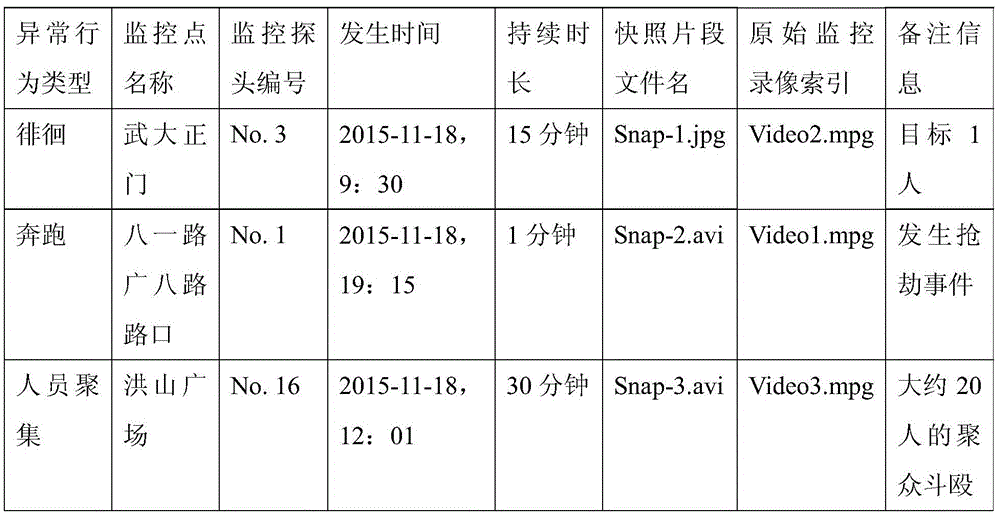
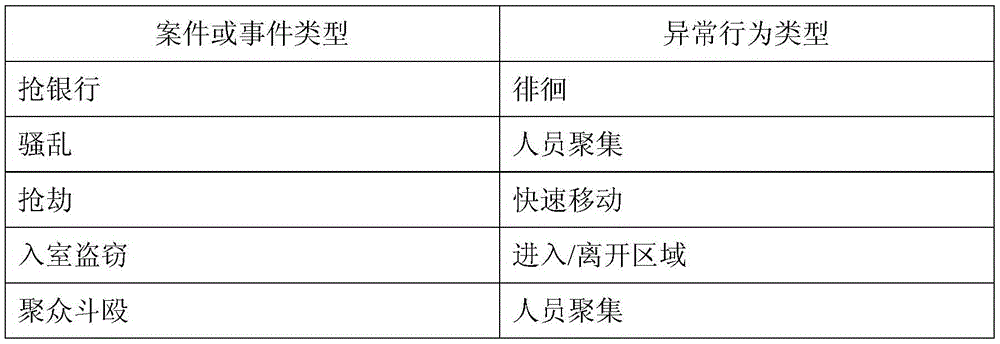
Video big data rapid searching method and system constrained by abnormal behavior early-warning information
ActiveCN105653690AImprove discovery efficiencyReduce the size of monitoring pointsSpecial data processing applicationsVideo retrievalVideo monitoring
The present invention discloses a video big data rapid searching method and system constrained by abnormal behavior early-warning information, wherein a massive video monitoring data clue investigation range is constrained by using abnormal behavior early-warning information sent out by an intelligent monitoring camera. The method comprises: receiving abnormal behavior early-warning information of a front-end intelligent camera, and establishing an abnormal behavior library; establishing a correlation model table, wherein the correlation model table stores a correlation between a case or event type and an abnormal behavior type; and according to the correlation model table, searching the abnormal behavior library, and positioning a corresponding valuable clue of monitoring point The method and system disclosed by the technical scheme of the present invention significantly reduce the size of recording data called in the video searching process and greatly improve valuable clue discovery efficiency.
Owner:WUHAN UNIV
SDN resource matching and service path discovering method based on rumor spreading mechanism
InactiveCN105024853AEasy to findEfficient resource allocationNetworks interconnectionResource poolPathPing
The invention relates to an SDN resource matching and service path discovering method based on a rumor spreading mechanism. In the method, underlying physical network resources register access and control information including physical resource state and attribute in a virtual resource pool, so that virtual resources can be managed globally, and access interface can be called; when service resources make request at the same time, the rumor spreading mechanism of high priority is provided, and the network effectiveness and gain are improved; the distribution amount of node and chain resource request is detected in real time, and a node traversal search algorithm of high priority is used to determine an effective node candidate set that satisfy requirements for service resource; and according to the bandwidth requirements for inks at the two ends of node and the limitation of path hops, an effective path set is calculated, and thus, the whole process of resource search and service path discovery is realized. The method of the invention can improve the efficiency of service resource and path discovery, and improve the gain of the virtual network and the utilization rate of resources.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Binary chop tracking method of shortest paths in network map
InactiveCN101788999AHigh speedOvercoming reverse order search and trace thinkingSpecial data processing applicationsAlgorithmStep number
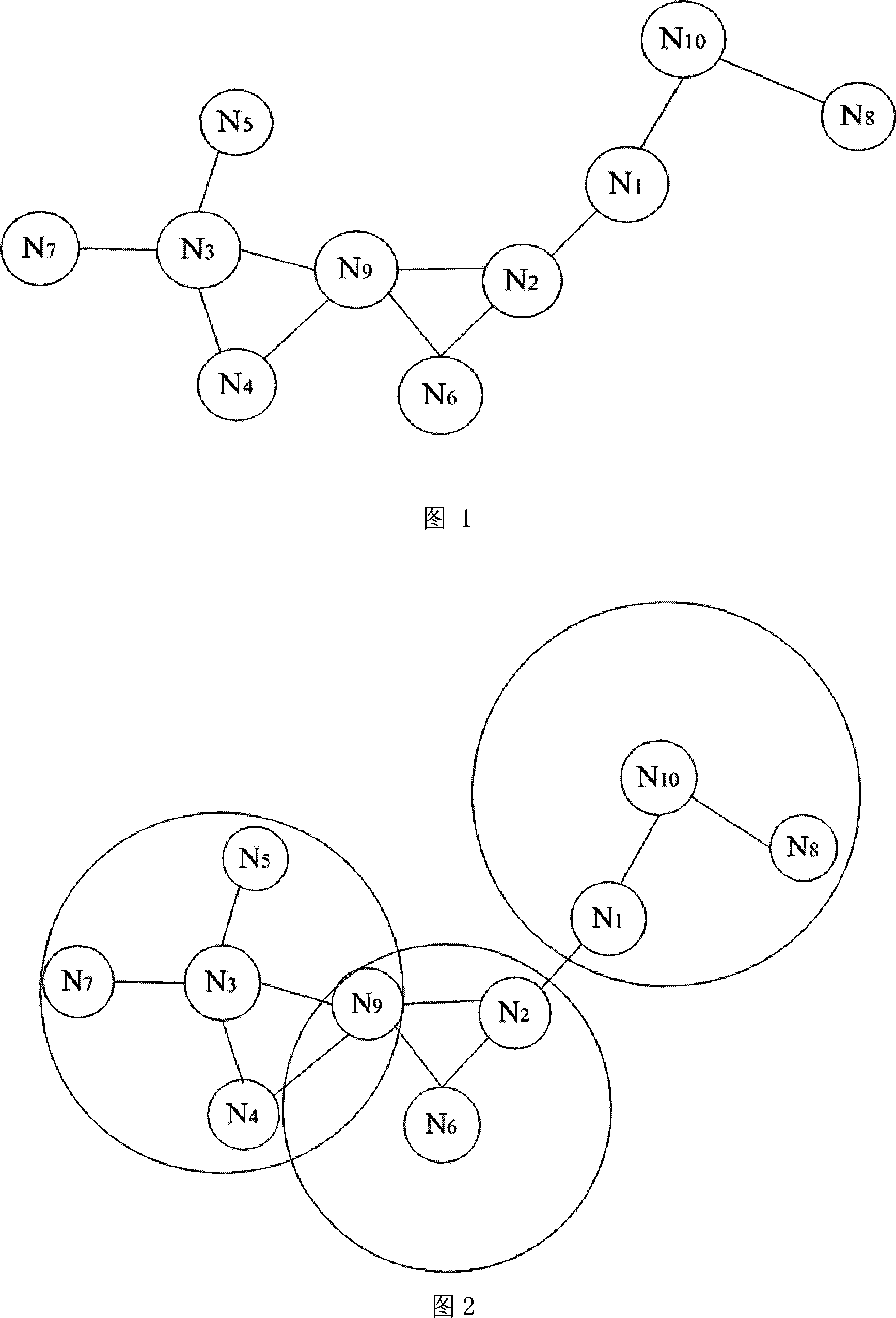
The invention discloses a binary chop tracking method of shortest paths in a network map, which is characterized in that the method comprises the following steps: extracting the step number of the shortest paths from a source node to a gathered node according to a shortest path step number matrix; reducing and separating the step number by half into the front step number and the back step number; searching nodes with the step number equal to the front step number in a source node row vector of the shortest path step number matrix, using the nodes as a front step number node set, searching nodes with the step number equal to the back step number in a gathered node column vector of the shortest path step number matrix, using the nodes as a back step number node set; taking an intersection set of the front step number node set and the back step number node set as middle nodes; using each node in the intersection as the reference; using the method for solving the middle node of the source node and the node, and the middle node of the node and the gathered node until the shortest path step number between the solved nodes is 1; and sequentially inserting the middle nodes into corresponding positions to obtain all shortest paths from the source node to the gathered node. The method of the invention is used for finding all shortest paths between two points, and the invention can provide various schemes for the preferential path selection of the network map abstracted from actual data.
Owner:ANHUI UNIVERSITY
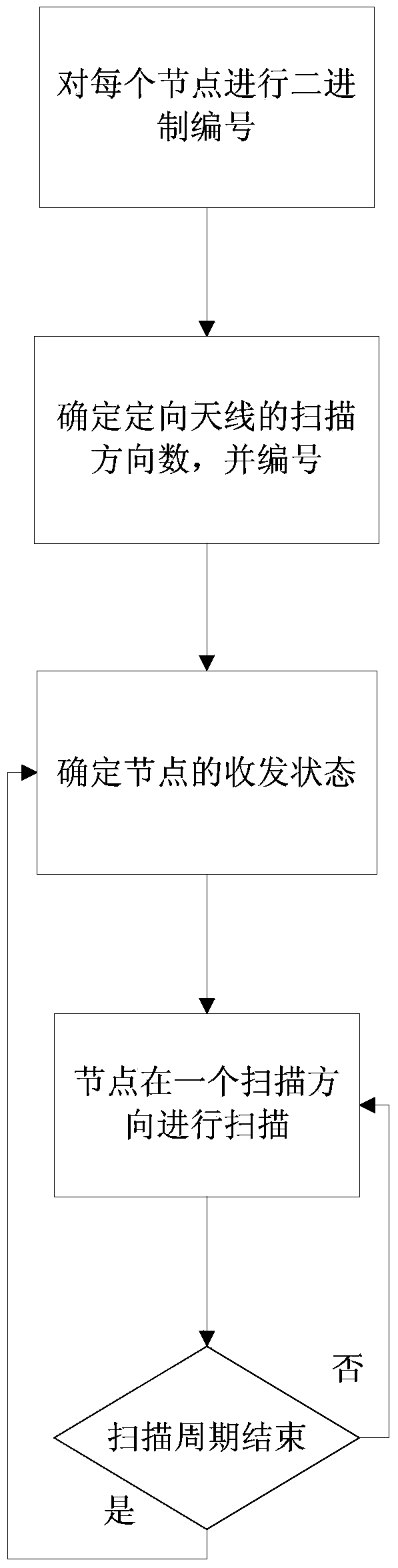
Novel neighbor finding method based on directional antenna
InactiveCN103686611AReduce the number of hopsImprove connectivityNetwork topologiesBroadcast service distributionInterference resistanceNeighbor finding
The invention discloses a novel neighbor finding method based on a directional antenna. The neighbor finding method comprises the following steps that binary system numbering is carried out on nodes, the antenna scanning direction is numbered, one node determines a receiving and sending mode according to the binary system number of the node, determines the scanning sequence according to the receiving and sending mode and carries out scanning at the neighbor finding stage according to the scanning sequence, and if a pair of receiving and sending nodes successfully come to a handshake protocol, it is shown that the neighbor finding process is successful. The novel neighbor finding method solves the problem of neighbor finding of the non-central networking under the condition of the directional antenna, the advantages of the high interference resistance and high space reused ratio of the directional antenna can be exploited to the full the flexible characteristic of entering and existing the network of the non-central networking are fully utilized, and the method has wide application prospects.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
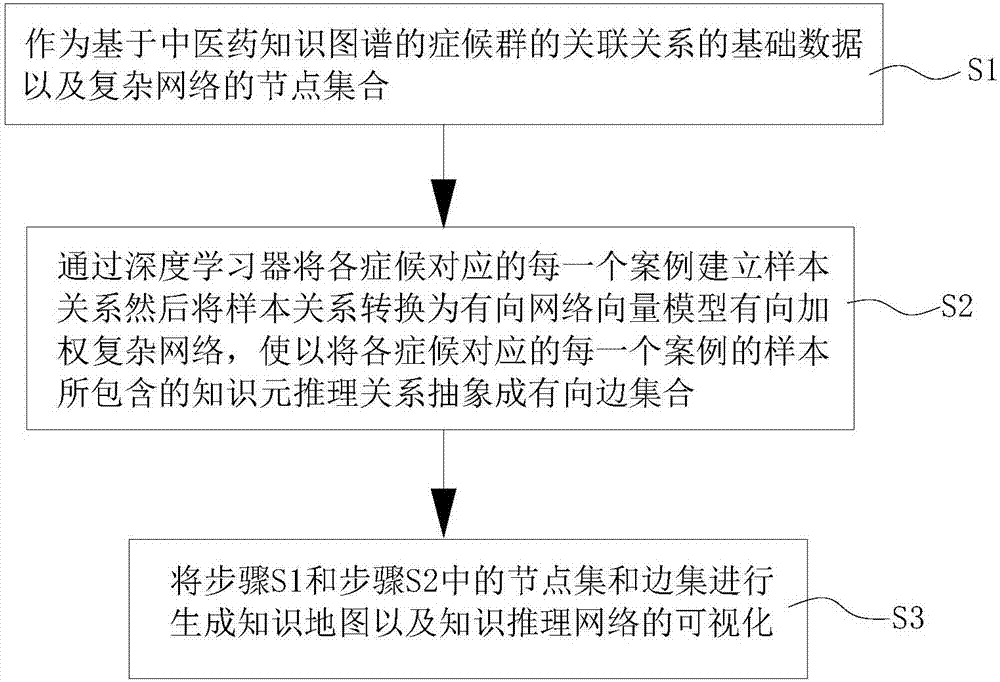
Method for constructing core symptom-differentiation relation based on traditional Chinese medicine knowledge graph
ActiveCN106933994AIncrease update frequencyImprove utilization efficiencySpecial data processing applicationsMedical recordKnowledge element
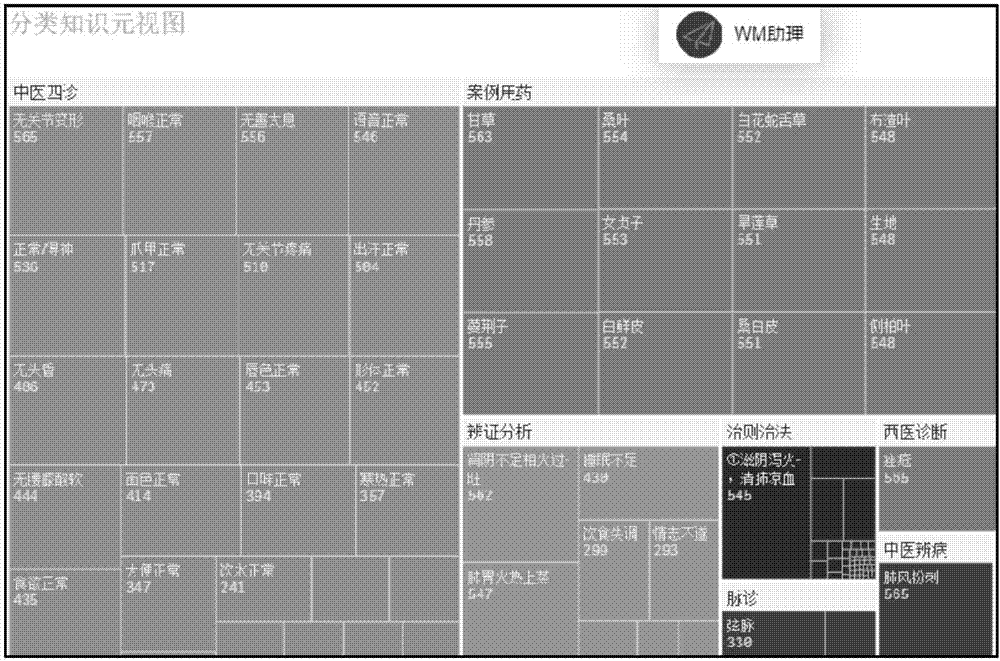
The invention discloses a method for constructing a core symptom-differentiation relation based on a traditional Chinese medicine knowledge graph. The method comprises the steps of mining and extracting a case set formed of four diagnostic methods information and differentiation factor knowledge elements of medical records of traditional Chinese medicine and auxiliary knowledge elements such as a theory, a rule, a prescription and a drug from literature of traditional Chinese medicine and a disease diagnosis database, establishing a sample relation for each case corresponding to the four diagnostic methods information and differentiation factors through a deep learner; then converting the sample relation into a directed-weighted complex network; abstracting a knowledge element inference relation included by the sample corresponding to each symptom into a directed edge set; and outputting a visual topological graph in a manner of a knowledge map and a knowledge inference network. According to the method, effective information carried by traditional Chinese medicine cases can be fully utilized, feature extraction and self-learning is realized to the maximum extent by use of a deep neural network, the construction of the visual topological graph for the traditional Chinese medicine symptoms and differentiation factors greatly improves the finding efficiency of potential knowledge and lays a foundation for intelligent diagnostic aid decision making of traditional Chinese medicine and recommendation of medicare guiding service.
Owner:GUANGDONG HOSPITAL OF TRADITIONAL CHINESE MEDICINE
Universal construction method for protein-targeting chimeric molecule compound
InactiveCN103265635AReduce the numberImprove discovery efficiencyHybrid peptidesSpecial data processing applicationsChemical synthesisUniversal construction
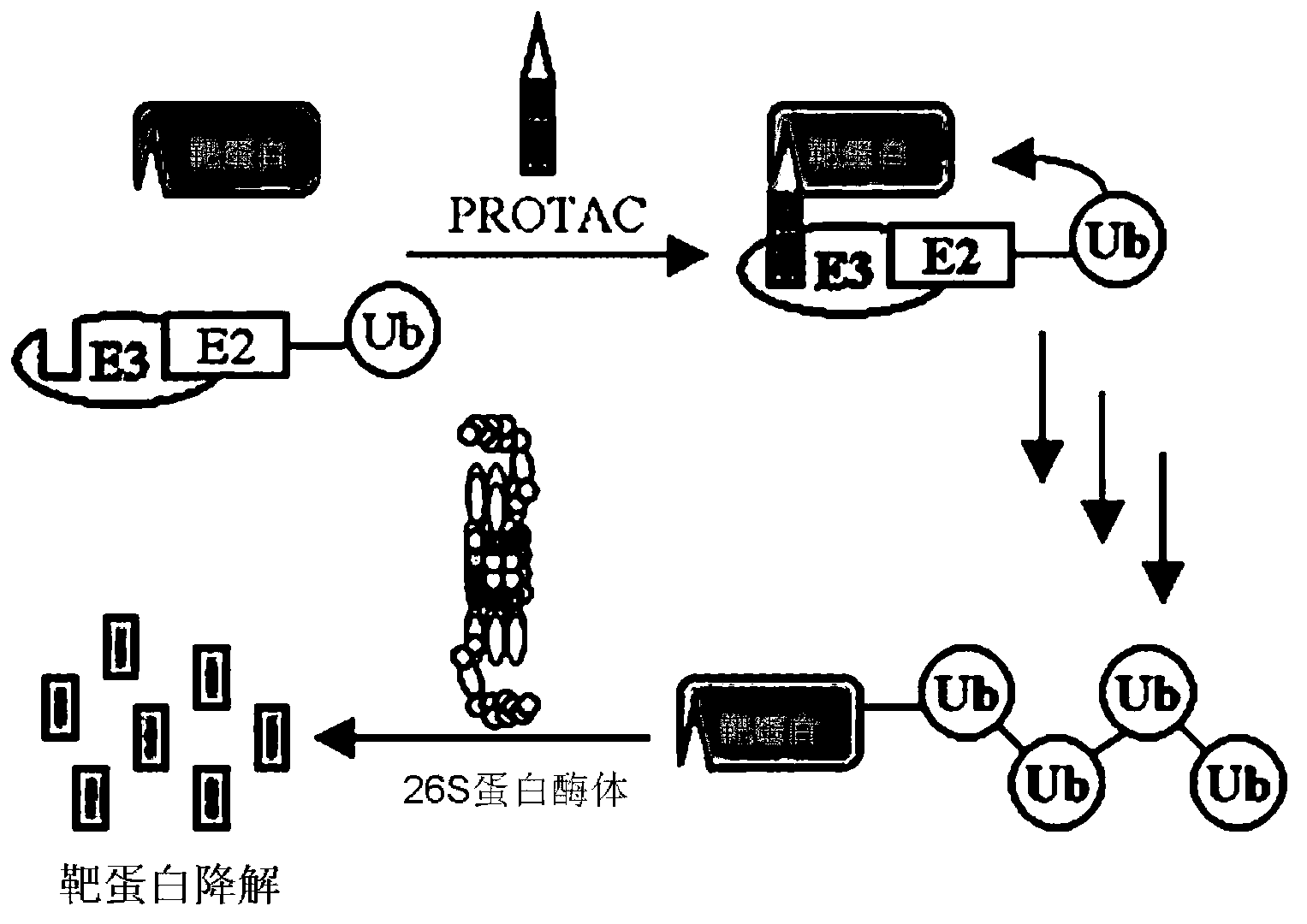
The invention discloses a universal construction method for a protein-targeting chimeric molecule compound. The objective of the invention is to provide a method for adjusting the level of proteins by degrading the proteins through targeted ubiquitination. The construction method mainly comprises the following steps: 1) locating and analyzing a three-dimensional structure of a target protein and predicting active sites; 2) selecting a compound database; 3) virtually screening ligand compounds having high degrees of adaption to the target protein by using a computer; 4) acquiring the screened ligand compounds and screening an optimal ligand compound of the target protein through detection of interaction between micromolecules and the proteins; 5) constructing a protein-targeting chimeric molecule compound composed of the optimal ligand compound of the target protein, ubiquitin ligase E3 identification ligand and Linker connecting the optimal ligand compound of the target protein to the ubiquitin ligase E3 identification ligand by using a combination manner simulated by the computer; and 6) chemically synthesizing the protein-targeting chimeric molecule compound. With the method provided by the invention, the protein-targeting chimeric molecule compound can be rapidly and highly efficiently prepared, and specific degradation of intracellular target proteins is realized.
Owner:THE FIRST AFFILIATED HOSPITAL OF SUN YAT SEN UNIV
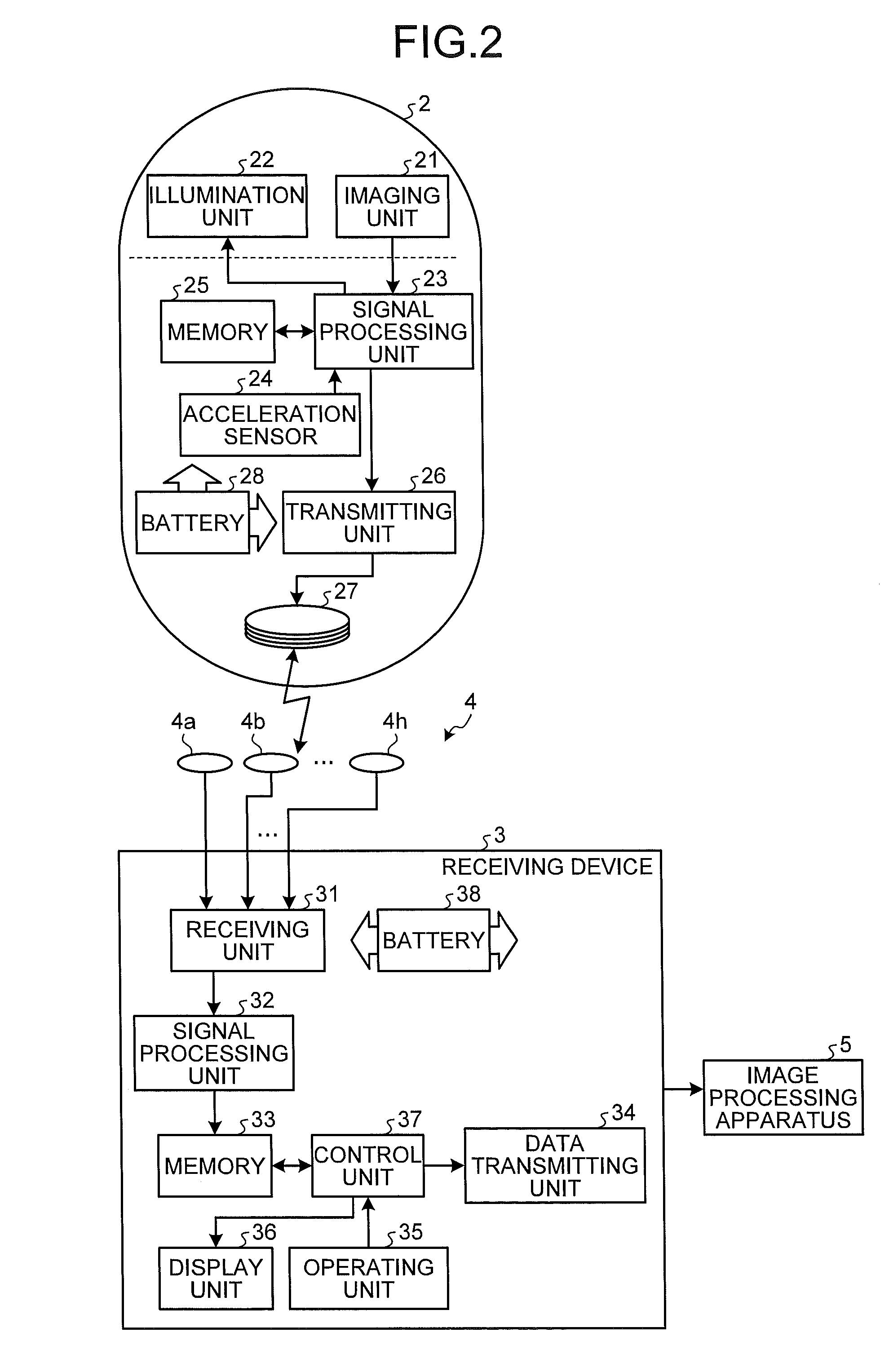
Image processing apparatus and image processing method
ActiveUS20140303435A1Improve discovery efficiencyShorten the time periodImage enhancementImage analysisImage extractionImaging processing
A image processing apparatus includes an image extraction unit that extracts first and second feature images representing first and second feature, respectively from a first image group acquired by sequentially capturing images of inside of a subject, and that further extracts third and fourth feature images representing first and second feature, respectively from a second image group acquired before the first image group, a feature data acquiring unit that acquires first and second feature data characterizing a movement of the capsule endoscope between the first and second feature images and between the third and the fourth feature images, respectively, a comparing unit that compares the first feature data with the second feature data, and a display control unit that performs, with respect to the first image group, display control based on a result of the comparison by the comparing unit.
Owner:OLYMPUS CORP
System and method for self-registration service discovery facing micro-service
The present invention provides a method for self-registration service discovery facing micro-service. The method comprises the following steps of: allowing all the nodes in a cluster to synchronouslyperceive newly published micro-service through a system mentioned above; allowing the service agent program of each node in the cluster to establish an IPTABLES forwarding rule to perform load balanceregulation of the micro-service; after the new service is published, allowing all the nodes in the cluster to perceive to set uniform access inlet for service, and on this basis, equally sharing a load balance task to each node of the cluster so as to effectively avoid that a load balance becomes performance bottlenecks on the basis of ensuring of the service rear-end example load balance. The present invention further provides a system for implementing the method.
Owner:INST OF INFORMATION ENG CAS
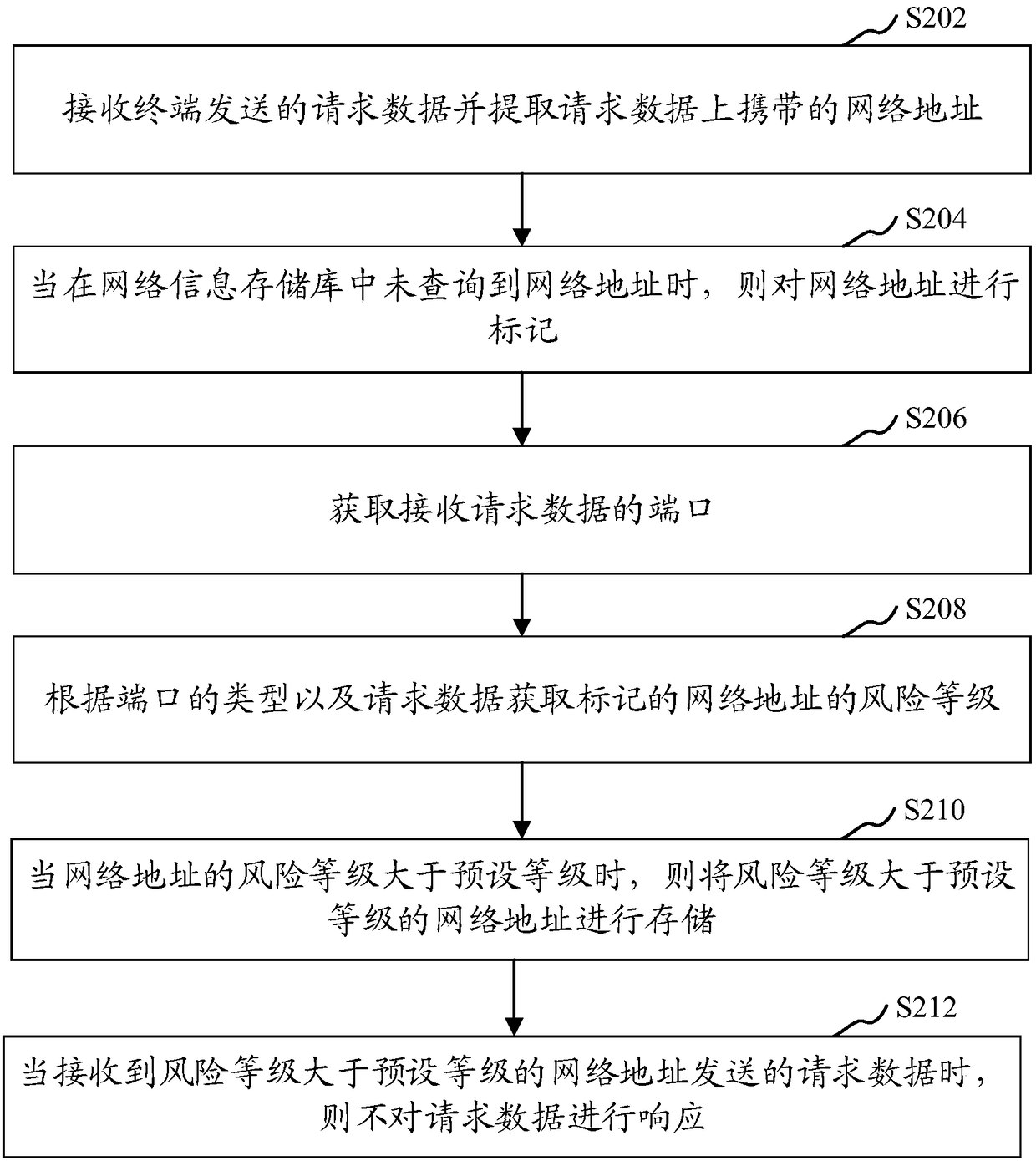
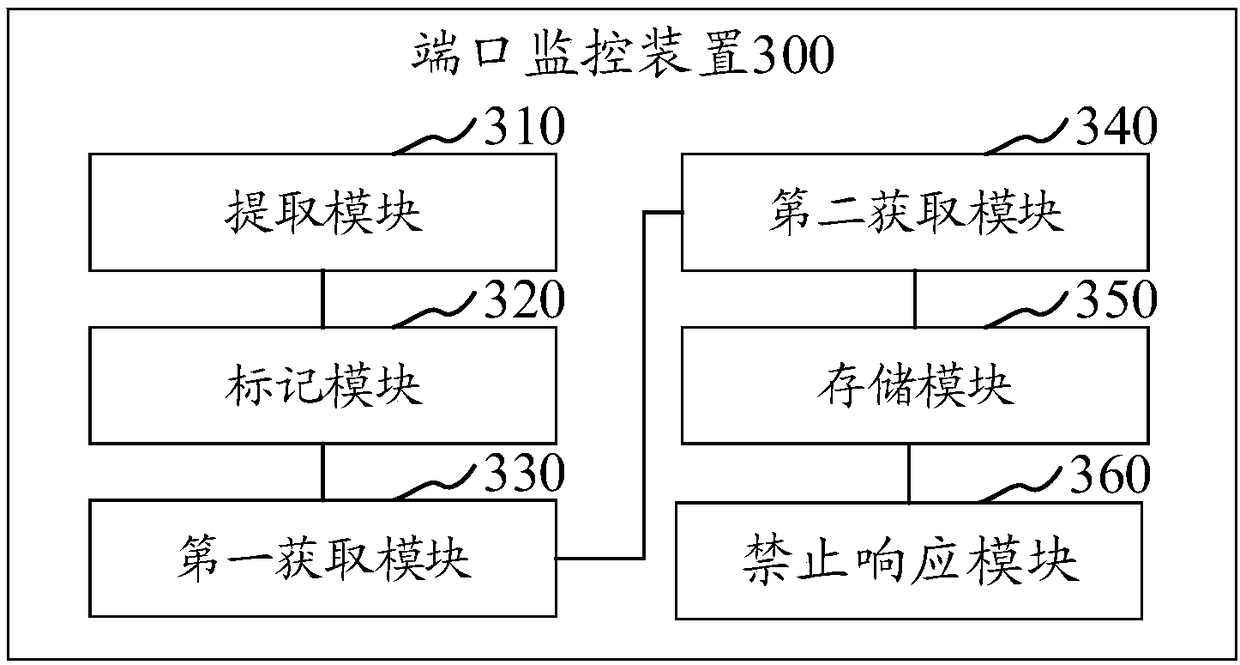
Port monitoring method and device, computer equipment and storage medium
The invention relates to a port monitoring method and device, computer equipment and a storage medium. The port monitoring method comprises the following steps: receiving the request data sent by a terminal and extracting the network address carried on the request data; marking the network address when the network address is not queried in the network information memory pool; obtaining a port to receive the request data; obtaining the risk level of the marked network address according to the type of the port and the request data; storing the network address with a risk level greater than a preset level when the risk level of the network address is greater than the preset level; and not responding to the request data when receiving the request data sent by the network address whose risk level is greater than the preset level. According to the invention, manual monitoring at any time is not required, therefore, the problem that the network address whose risk level is greater than the preset level is omitted because the manual monitoring can not be performed at certain special time is avoided, and the omission of the corresponding intrusion equipment is avoided; thus, the discovery efficiency can be improved, and the risk can be discovered in time.
Owner:PING AN TECH (SHENZHEN) CO LTD
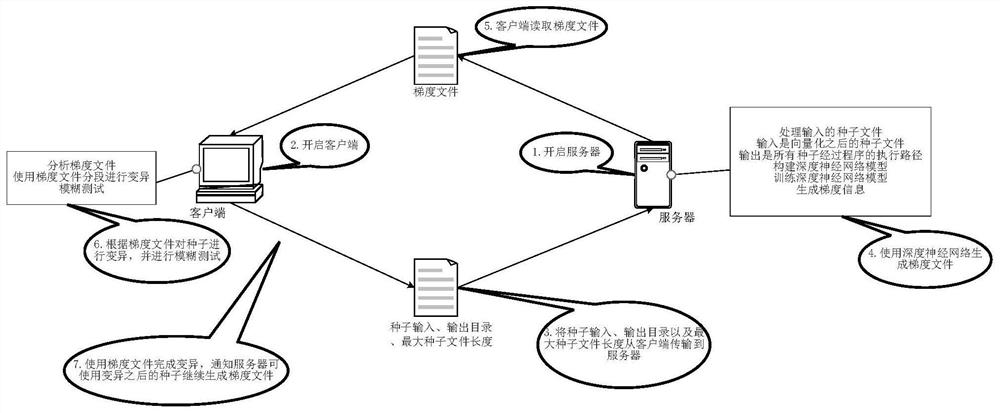
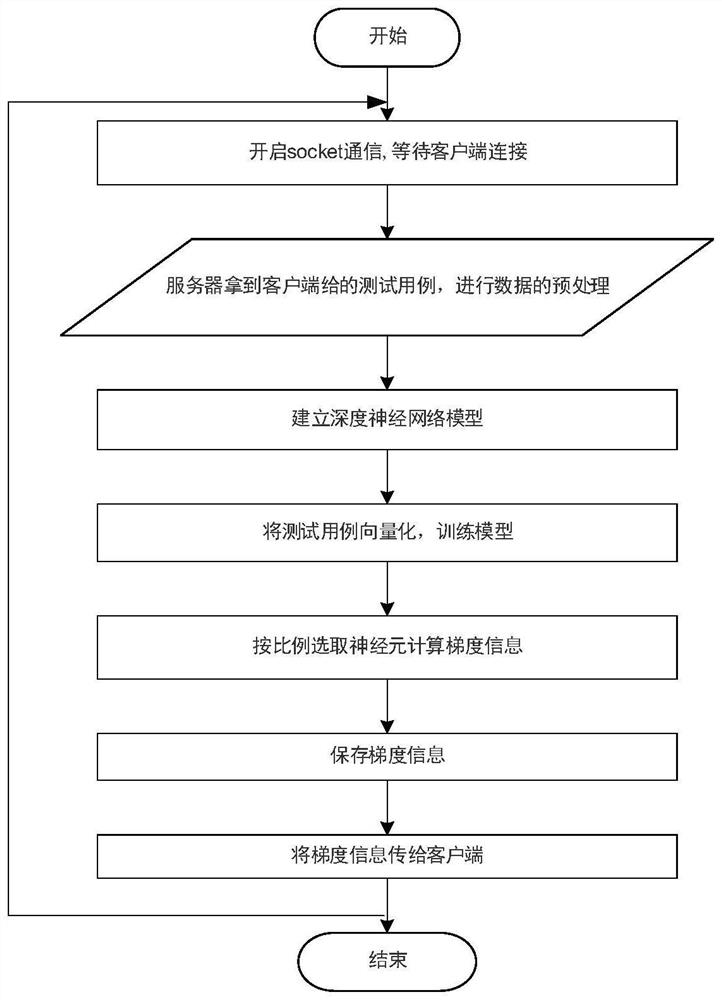
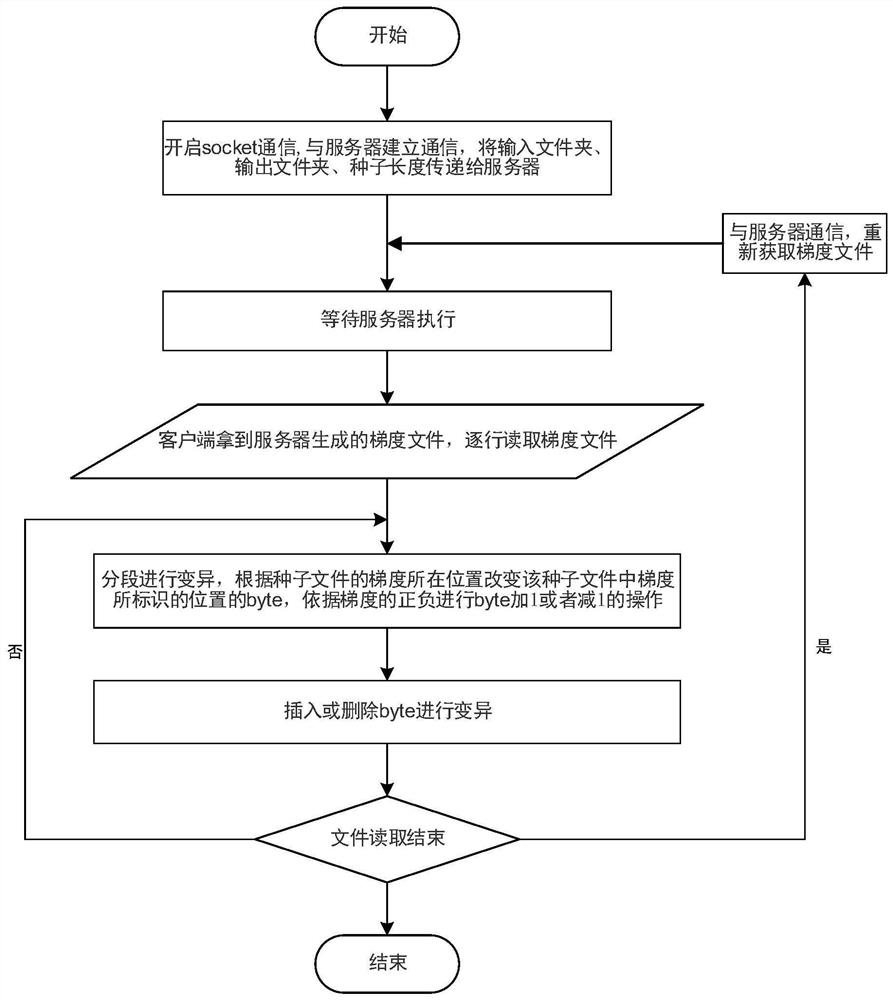
Software security vulnerability detection method and system for deep learning gradient guidance variation
ActiveCN112069061AProgram smoothingImprove smoothnessSoftware testing/debuggingPlatform integrity maintainanceAlgorithmEngineering
The invention discloses a software security vulnerability detection method and system for deep learning gradient guidance variation, and the method comprises the steps: obtaining test cases, carryingout the preprocessing, and obtaining the size of a maximum test case and an execution path of each test case in a tested program; establishing a deep neural network model, wherein the input dimensionof the input layer is the size of the maximum test case, and the number of output neurons of the output layer is the total number of execution paths; vectorizing the test cases, and training a deep neural network model by using the test cases; performing gradient calculation based on the trained deep neural network model to generate gradient information; and performing variation and fuzzy test onthe test case based on the gradient information to generate a test result. According to the method, a gradient guidance variation technology is adopted, gradient information is generated in combination with deep learning assistance, and the bottleneck problem in software security vulnerability mining can be effectively solved.
Owner:CHECC DATA CO LTD +1
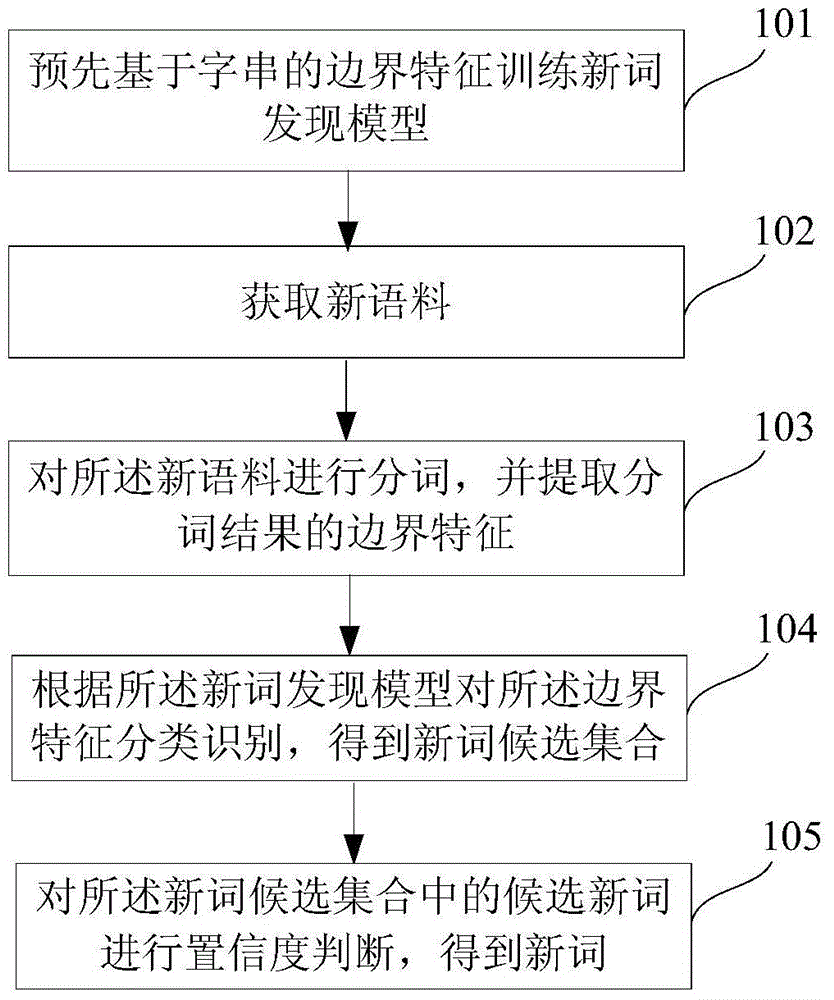
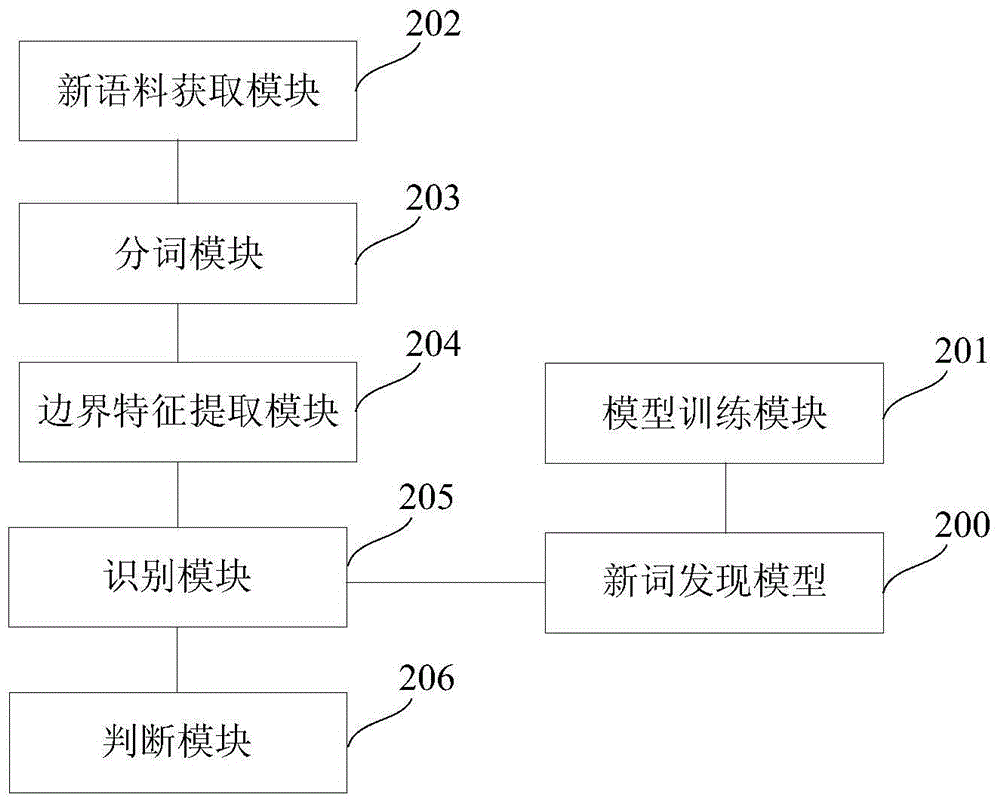
Neologism discovering method and system
ActiveCN106033462AImprove discovery efficiencyImprove reliabilitySpecial data processing applicationsSpeech recognitionWorkload
The invention discloses a neologism discovering method and system; the method comprises the following steps: training a neologism discovering model in advance according to word string boundary characteristics, wherein the word string boundary characteristics refer to the word string statistics characteristic; obtaining novel linguistic data; dividing the novel linguistic data, and extracting boundary characteristics of the dividing result; identifying the boundary characteristics in classification according to the neologism discovering model, thus obtaining a neologism candidate set; determining confidence of the candidate neologism in the neologism candidate set, thus obtaining neologisms. The method and system can effectively discover linguistic data neologism while reducing artificial marking workload.
Owner:IFLYTEK CO LTD
Cluster based service issuing and discovering method in self-organizing network facing to service
InactiveCN101163158AImprove usabilityImprove publishing efficiencyData switching by path configurationBroadcast radiationService-orientation
The invention belongs to the technical field of self-organization network, in particular to a sub-cluster-based service distribution and discovering method on the self-organization network facing service. The method is divided into three parts comprising a sub-cluster maintenance, a service distribution and a service discovering. The cluster maintenance is divided into two parts comprising a sub-cluster and a cluster updating; the service distribution comprises a service information establishment and a service information updating; the service discovering means after finishing the sub-cluster and the service distribution, a node discovers basic service on the self-organization network through a cluster head. The invention can effectively avoid the broadcast storm phenomenon of the prior service distribution and the service discovering method; the method can also use replaceable service to enhance the efficiency of the service discovering.
Owner:FUDAN UNIV
Discovery method, router and node equipment of path maximum transmission unit
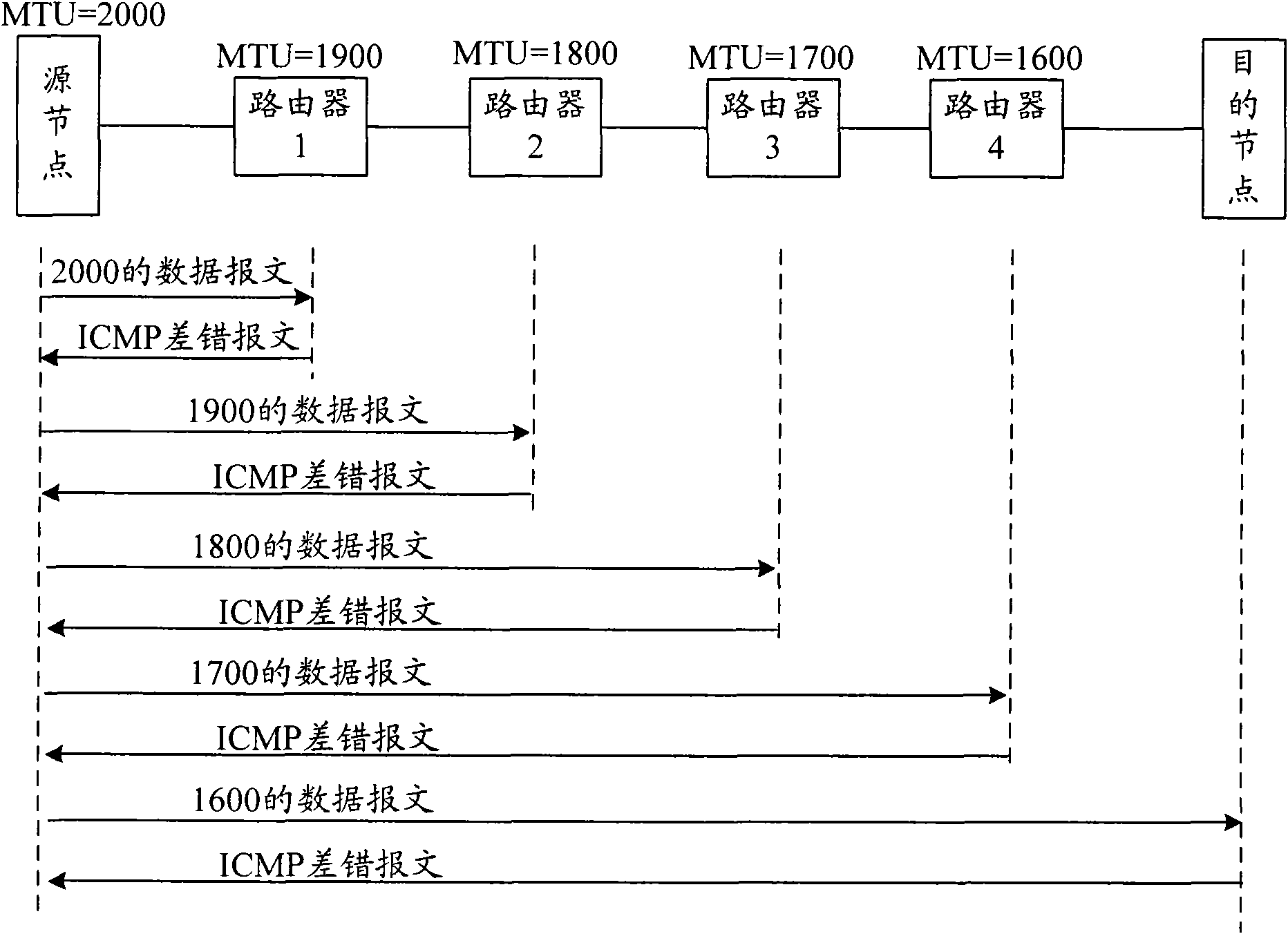
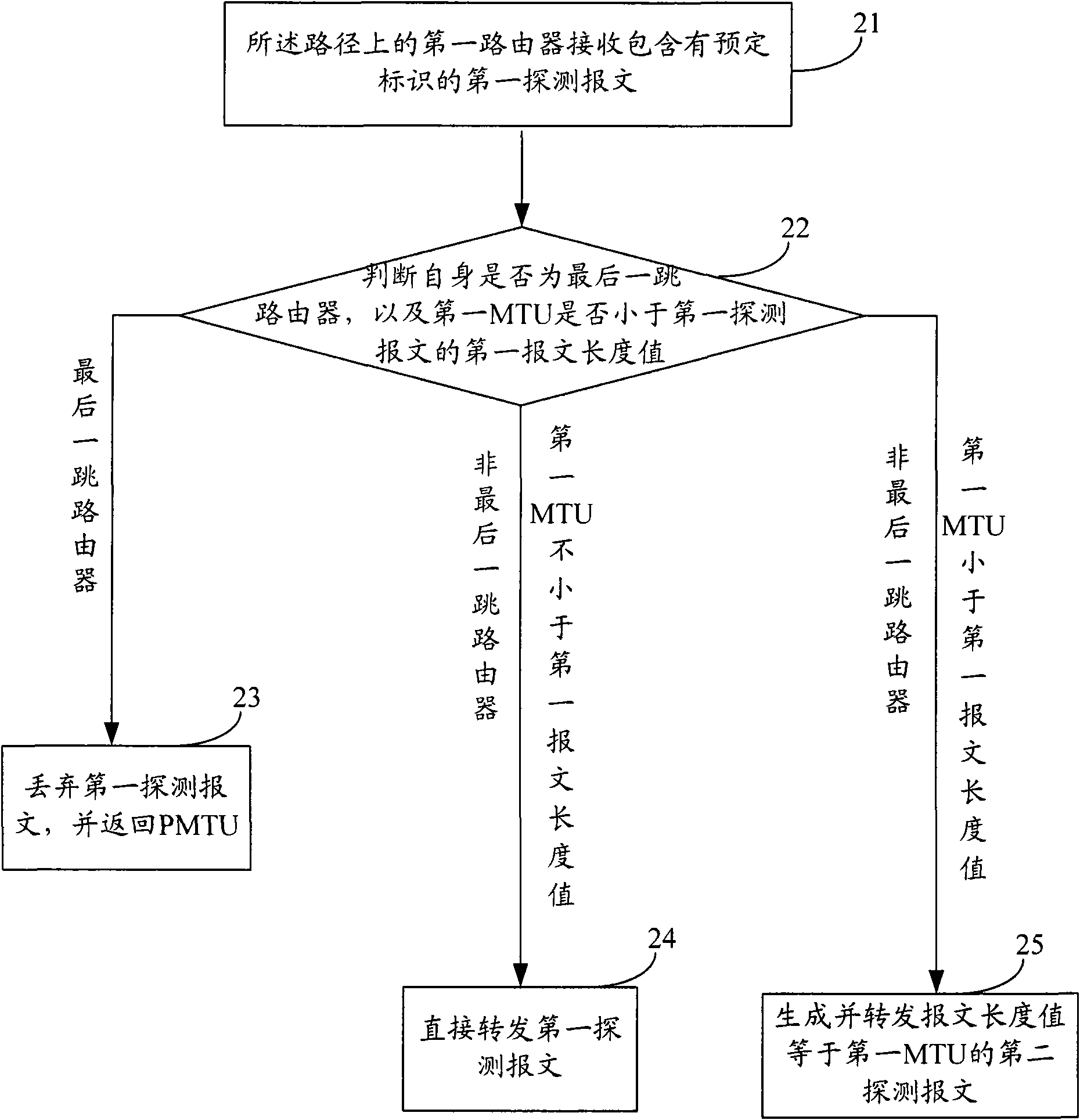
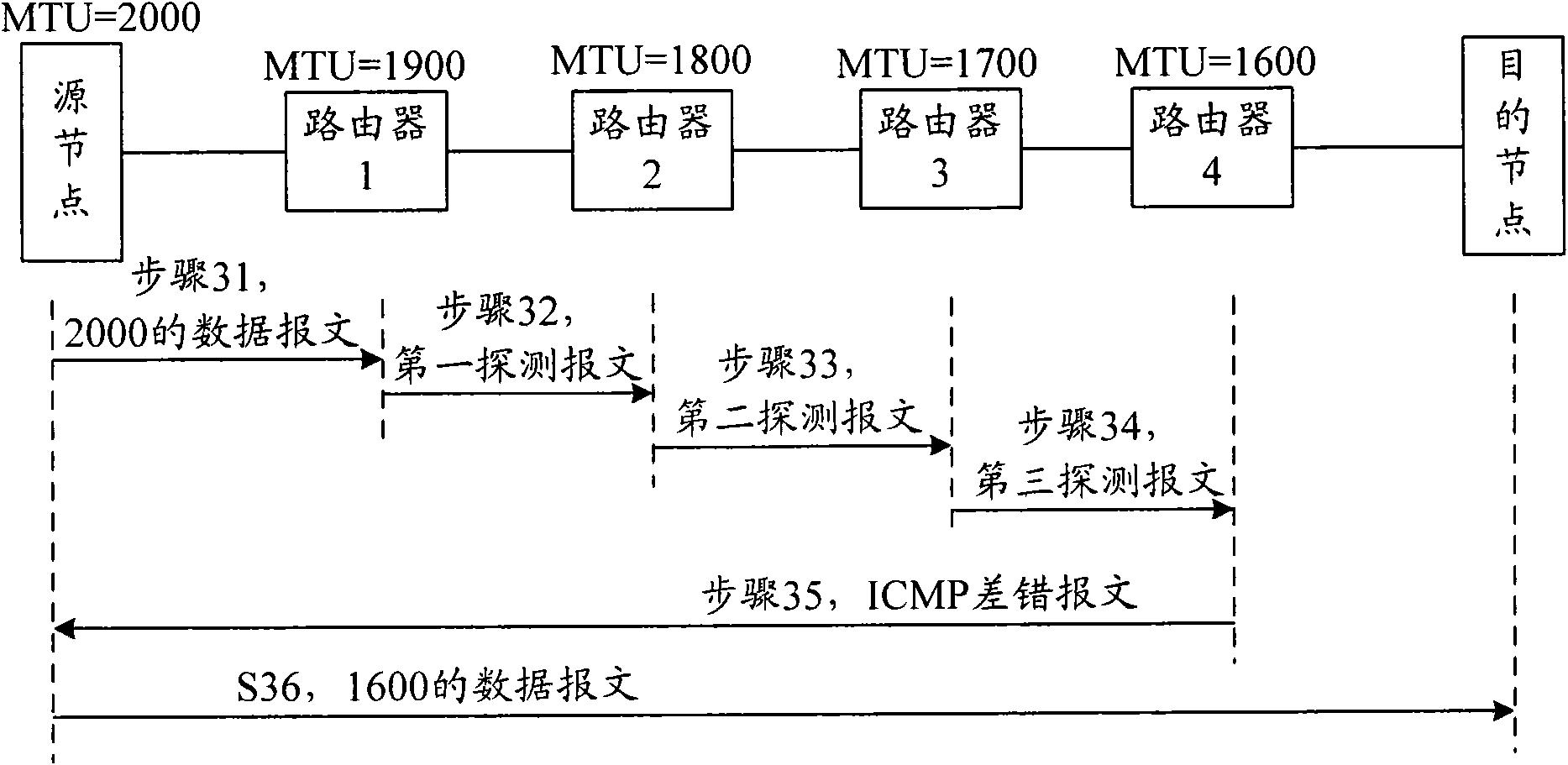
ActiveCN101616078AImprove discovery efficiencyReduce transfer timeData switching networksMessage lengthComputer science
The invention provides a discovery method, a router and node equipment of a path maximum transmission unit. The method realizes the discovery of PMTU by detecting the MTU of a router in the message length value transfer path of a message. According to the invention, the method can be compatible with the PMTU discovery mechanism in the prior art, the bandwidth resource can be saved, and the discovery efficiency of PMTU can be improved.
Owner:NEW H3C TECH CO LTD
Web service discovery method based on memorization service cluster mapping catalogue
The invention discloses a web service discovery method based on a memorization service cluster mapping catalogue. According to the web service discovery method, services with the same or similar function are gathered to build a service cluster, the services in the service cluster are classified according to the service cluster mapping catalogue, and the purpose that the services in the service cluster change from the unordered state to the order state is achieved. According to a service cluster parameter matrix, services, with the catalogue items corresponding to a service chain list, in the mapping catalogue are sequenced, a virtual service group is provided, and a memorization service chain list is further provided. According to the organization structure of the memorization service cluster mapping catalogue, a new service cluster parameter matrix corresponding to the memorization service cluster mapping catalogue is provided; on the basis of the memorization service cluster mapping catalogue and the new service cluster parameter matrix corresponding to the memorization service cluster mapping catalogue, the semantic Web service discovery method based on the memorization service cluster mapping catalogue is provided, and therefore after a specific service cluster is positioned, a Web service meeting the requirement can be returned more quickly.
Owner:SHANDONG UNIV OF SCI & TECH
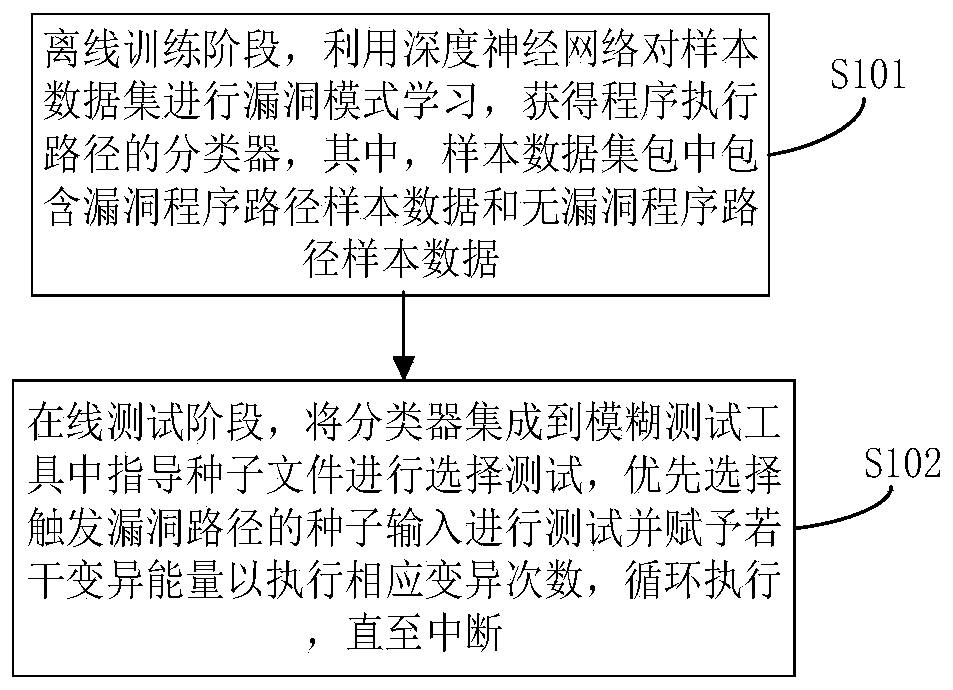
A program path sensitive grey box testing method and device
ActiveCN109902024AIncrease trigger rateImprove discovery efficiencySoftware testing/debuggingGray box testingData set
The invention belongs to the technical field of software testing. The invention particularly relates to a program path sensitive grey box testing method and device. The method comprises the steps thatin the offline training stage, vulnerability mode learning is conducted on a sample data set through a deep neural network, a classifier of a program execution path is obtained, and a sample data setpackage comprises vulnerability program path sample data and vulnerability-free program path sample data; and in an online test stage, the classifier is integrated into a fuzzy test tool to guide a seed file to perform a selection test, seed input triggering a vulnerability path is preferentially selected to perform the test, endowing the test with a plurality of variation energies to execute corresponding variation times, and performing cyclic execution until interruption. The method fills up the blank of vulnerability path sample influence analysis, does not depend on a complex dynamic analysis technology, does not bring about a large overhead problem, can be effectively combined with other grey box test technologies, improves vulnerability discovery efficiency, can be directly suitablefor a binary program, does not depend on a source code, and is high in applicability.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
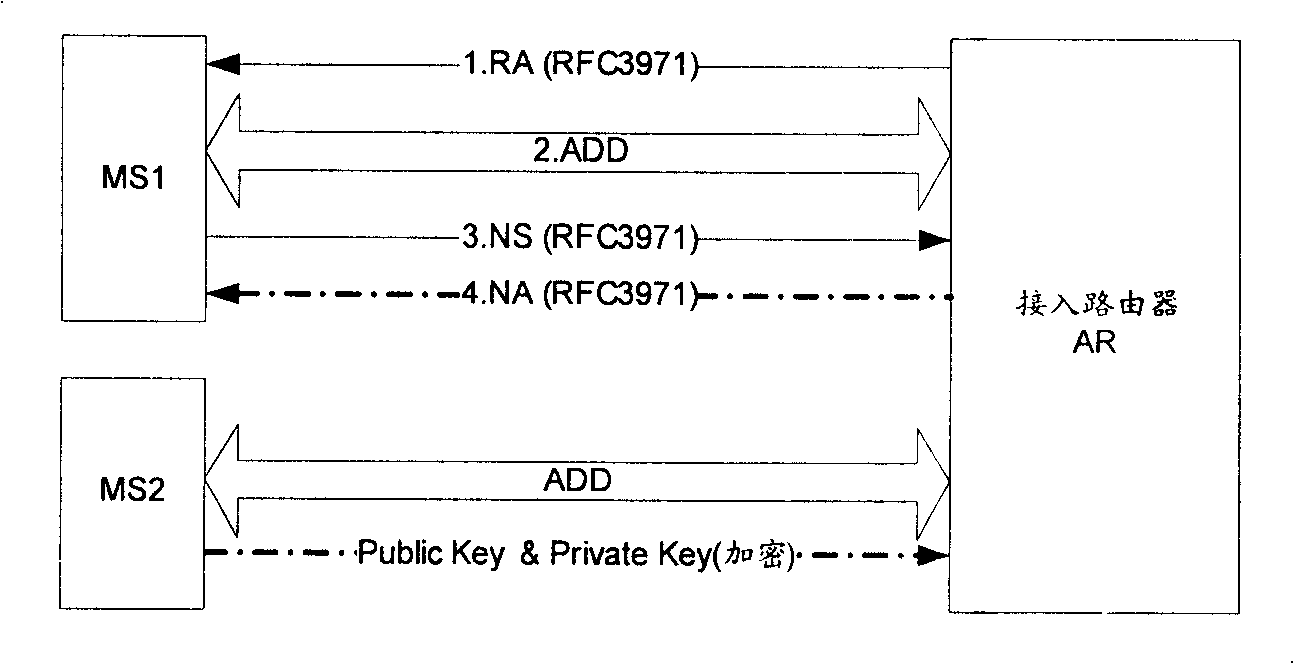
Safety neighbor discovering method, network appliance and mobile station
InactiveCN101247642AAvoid information exchangeImprove discovery efficiencyRadio/inductive link selection arrangementsSecurity arrangementSecure Neighbor DiscoveryTransfer procedure
The present invention provides a safety neighbor discovery method, network equipment and mobile station. The mobile station sends neighbor request information to trusting network equipment; the network equipment processes neighbor discovery according with received neighbor request message, and acting replies neighbor broadcast message according with neighbor discovery result; the mobile station obtains neighbor discovery result according with received neighbor broadcast message; the network equipment processes neighbor discovery and acting replies neighbor broadcast message according with neighbor transmitting result after passing authentication for received neighbor request message during said message transmitting process; and / or the mobile station processes message authentication for received neighbor broadcast message, and obtains neighbor discovery result message after authentication successfully. High level signaling transmitting on gap is reduced, precious gap resource of network is saved and safety neighbor discovery efficiency is increased by using the safety neighbor discovery method, network equipment and mobile station provided by the invention.
Owner:HUAWEI TECH CO LTD
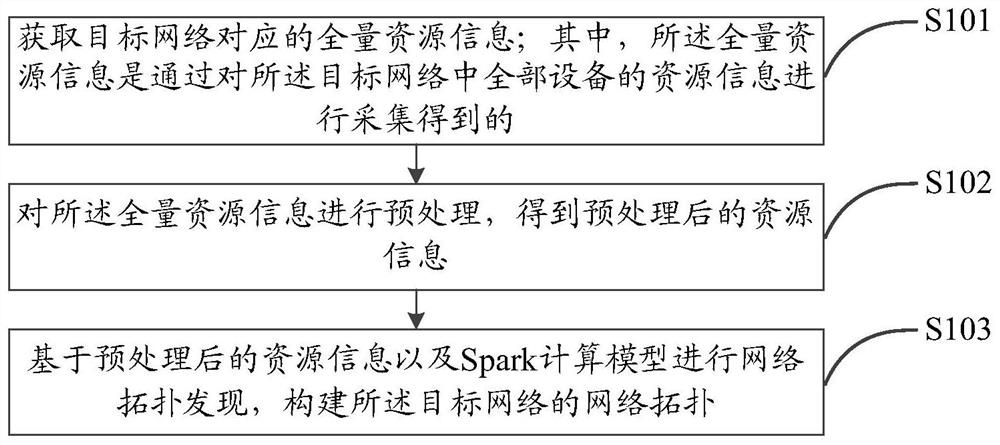
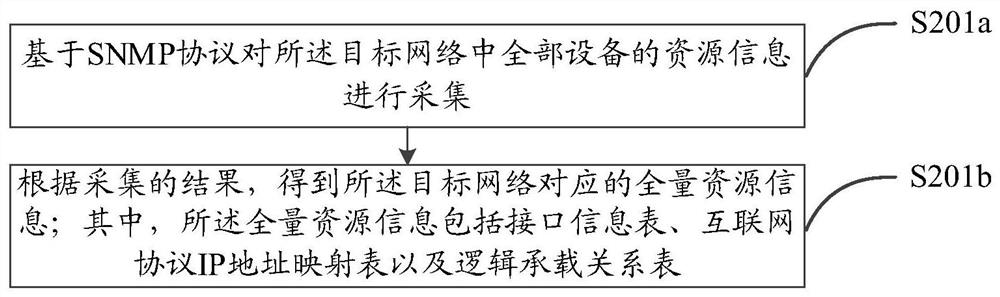
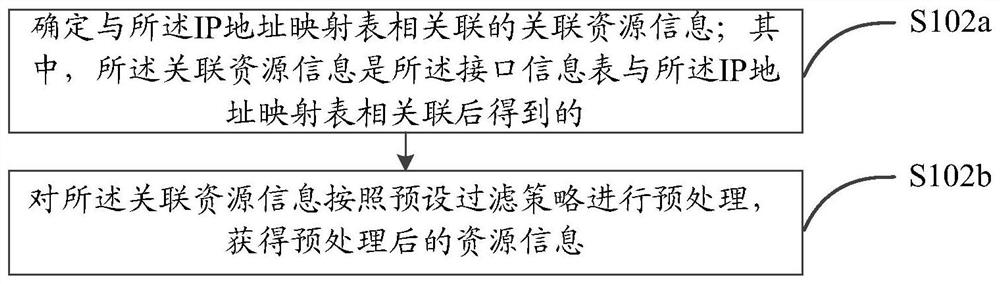
Network topology discovery method and device and computer storage medium
ActiveCN111953507AImprove discovery efficiencyShorten collection timeData switching networksResource informationLogical topology
The embodiment of the invention discloses a network topology discovery method and device and a computer storage medium. The method comprises the following steps: acquiring total resources informationcorresponding to a target network; wherein the total resources information is obtained by collecting resources information of all equipment in the target network; preprocessing the total resources information to obtain preprocessed resources information; performing network topology discovery based on the preprocessed resources information and a Spark calculation model, and constructing a network topology of the target network; thus, as the resource information of all the equipment in the target network is completely acquired at a time, the acquisition time is greatly shortened, and the networktopology discovery efficiency is improved; besides, by preprocessing the full resource information, the logic topology of the large IP network can be quickly discovered, and a Spark calculation modelcan be applied, so that the physical topology is discovered through one-step analysis based on the logic topology, and the network topology discovery efficiency is further improved.
Owner:CHINA MOBILE SUZHOU SOFTWARE TECH CO LTD +1
System and method for testing network link performance of terminal equipment
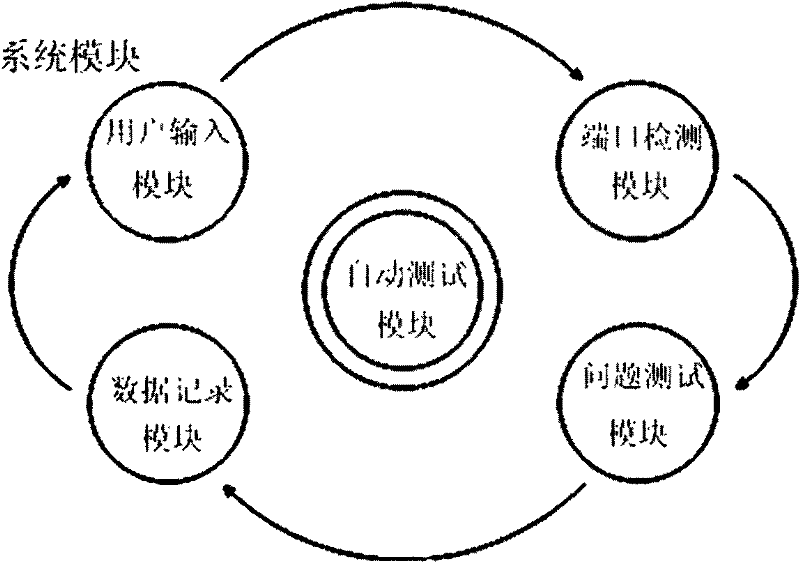
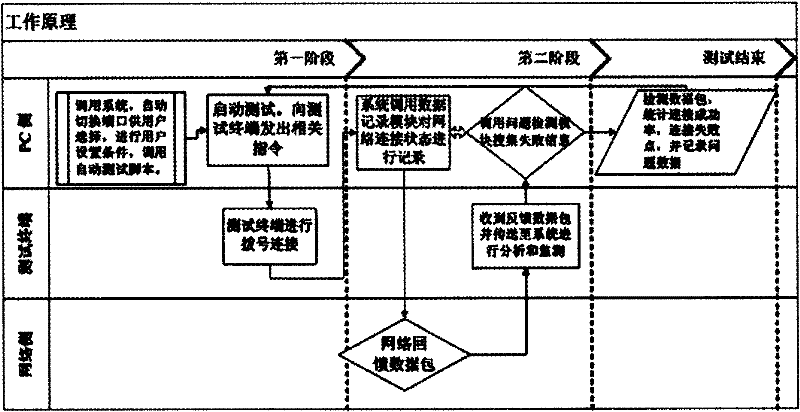
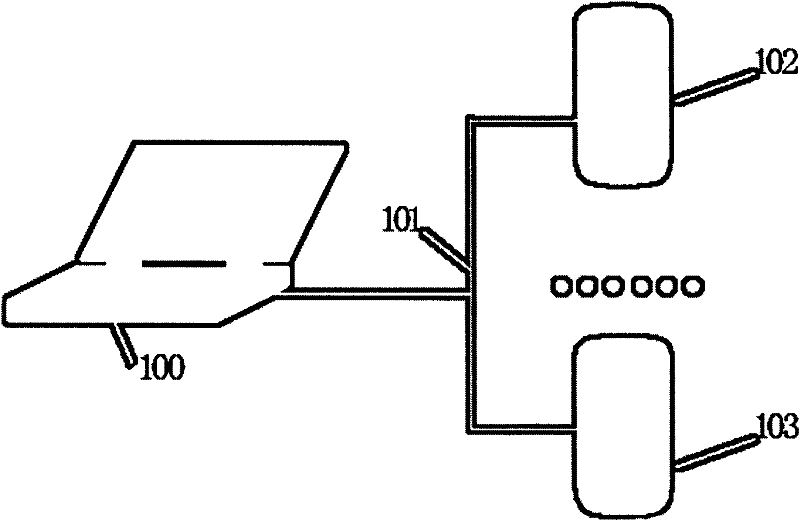
InactiveCN102413484AImprove accuracyRisk reduction factorWireless communicationTest scriptNetwork link
The invention discloses a system and a method for testing the network link performance of terminal equipment. The system comprises five main modules, namely a user input module, a port detection module, an automatic test script module, a data record module and a problem monitoring module, which can jointly complete each function of the whole test and system and are mutually independent and dispensable. By the invention, a PC (personal computer) and communication terminal equipment can perform automatic operation, monitoring, data recording and other treatments after physical connection; the problems of a great number of manual operations, inconsistent results and the like in the communication terminal test; the terminal equipment can be automatically detected and processed by the system, messages and signaling can be monitored in the establishing process of data service, and the data and failed points can be recorded and fed back for reporting, thus the method and the system for the terminal test data and report can be obtained.
Owner:西安龙飞软件有限公司
Group discovery method and system for attribute network
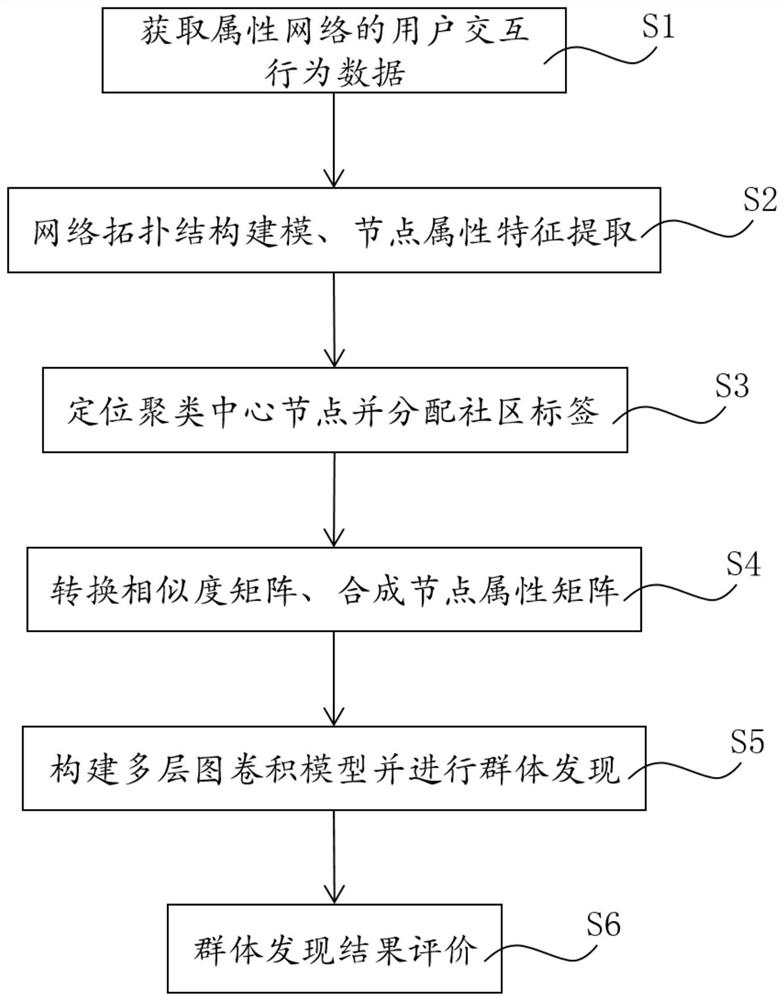
ActiveCN112925989AImprove discovery efficiencyImprove performanceData processing applicationsDigital data information retrievalTheoretical computer scienceEngineering
The invention belongs to the field of network data mining, and discloses a group discovery method and system for an attribute network, which are used for accurately identifying a potential group structure in the attribute network, and comprises the following steps: obtaining user interaction behavior data of the attribute network; modeling an attribute network topology and a node attribute set by preprocessing the attribute network data; positioning a potential clustering center node based on the node degree centrality measurement and the relative distance between the nodes; converting the network adjacency matrix into a similar matrix according to the topological structure information, and synthesizing a node attribute matrix at the same time; carrying out deep fusion on structure information and node attributes at the same time by using a multilayer graph convolution model, and automatically identifying a complete group structure; and finally, evaluating a group discovery result. The method and system can face large-scale attribute network data, reveals the group structure under low time complexity, is high in universality to complex networks, and has high application value.
Owner:CHINA JILIANG UNIV
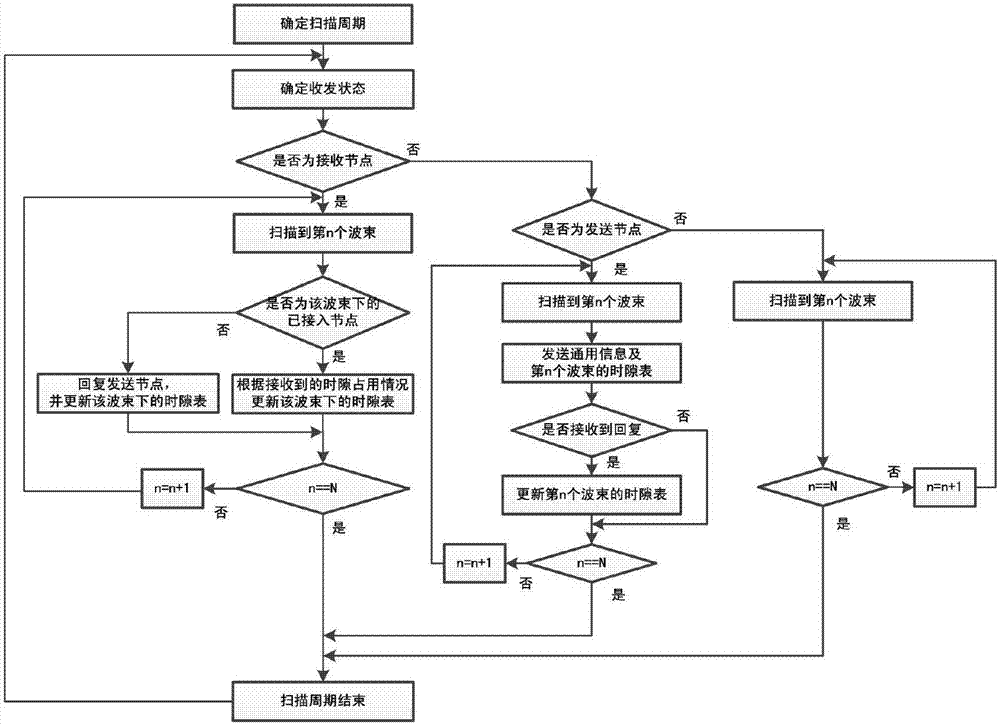
Directional center-less ad-hoc network neighbor discovery method for reducing collision probability
ActiveCN107071755AImprove discovery efficiencyReduce the probability of collisionNetwork topologiesNetwork planningCollision probabilityTelecommunications link
The present invention discloses a directional center-less ad-hoc network neighbor discovery method for reducing collision probability. The method comprises the following steps: determining a beam scanning period and scanning mode according to the number of antenna beams of a node; and randomly determining a transceiving status of each neighbor discovery beam scanning period, so as to classify the nodes as a transmitting node, a receiving node or a silent node. A transmitting node broadcasts a time slot table of a beam in different beam directions. A receiving node performs time slot allocation according to a received time slot table in a beam direction, and updates a local time slot table. A silent node neither transmits nor receives a signal within an entire beam scanning period. The method disclosed by the present invention can greatly reduce the collision probability in a directional center-less ad-hoc network when multiple nodes perform accessing in a same beam direction, and can effectively solve the problem that multiple communication links working in a same beam direction interfere with each other, thereby reducing network establishment time and improving network accessing and working efficiency.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
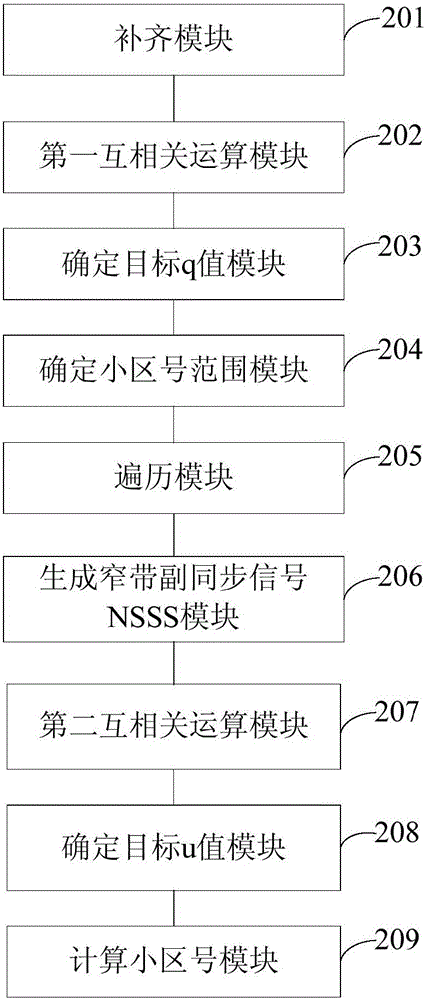
Cell discovery method and apparatus based on NB-IoT system
ActiveCN106851783AReduce in quantityReduce the number of cross-correlation operationsAssess restrictionMutual correlationAlgorithm
The embodiment of the invention provides a cell discovery method and apparatus based on an NB-IoT system. The method comprises the following steps: performing mutual correlation operation on narrowband sub-synchronous signals NSSS in received signals with q sequences in local signals to obtain first correlation values, determining a q value corresponding to the maximum first correlation value as a target q value, and determining a cell number range through the target q value; traversing each cell number within the cell number range, correspondingly generating a u value for each cell number, separately substituting the generated u values into a narrowband sub-synchronous signal NSSS generation formula to generate the narrowband sub-synchronous signals NSSS; performing mutual correlation operation on the generated narrowband sub-synchronous signals NSSS and the narrowband sub-synchronous signals NSSS in the received signals to obtain second correlation values, determining the u value corresponding to the maximum second correlation value as a target u value; and calculating the cell number corresponding to a base station that sends the received signals according to the target q value and the target u value. The scheme can improve the cell discovery efficiency.
Owner:BEIJING UNIV OF POSTS & TELECOMM
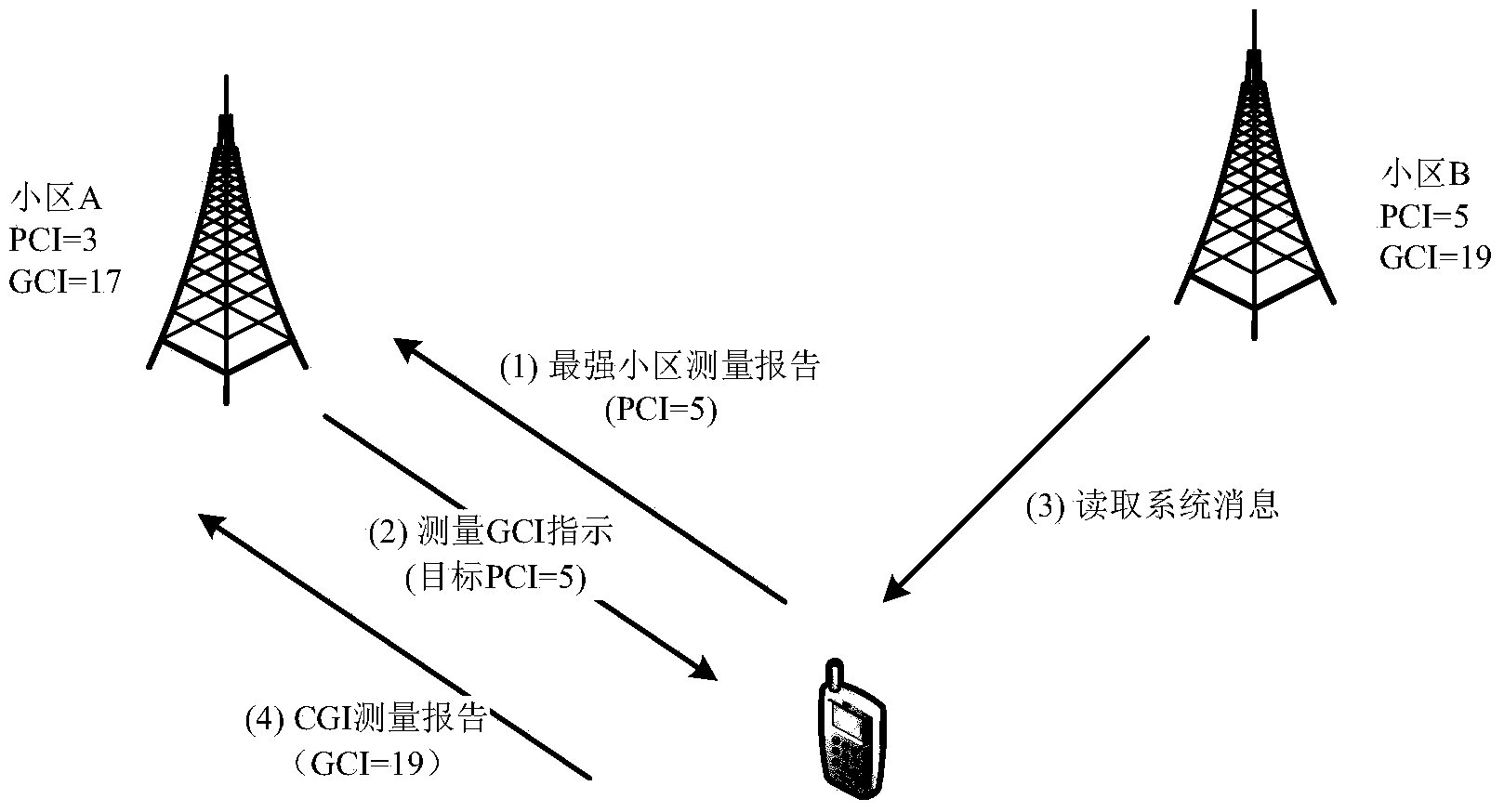
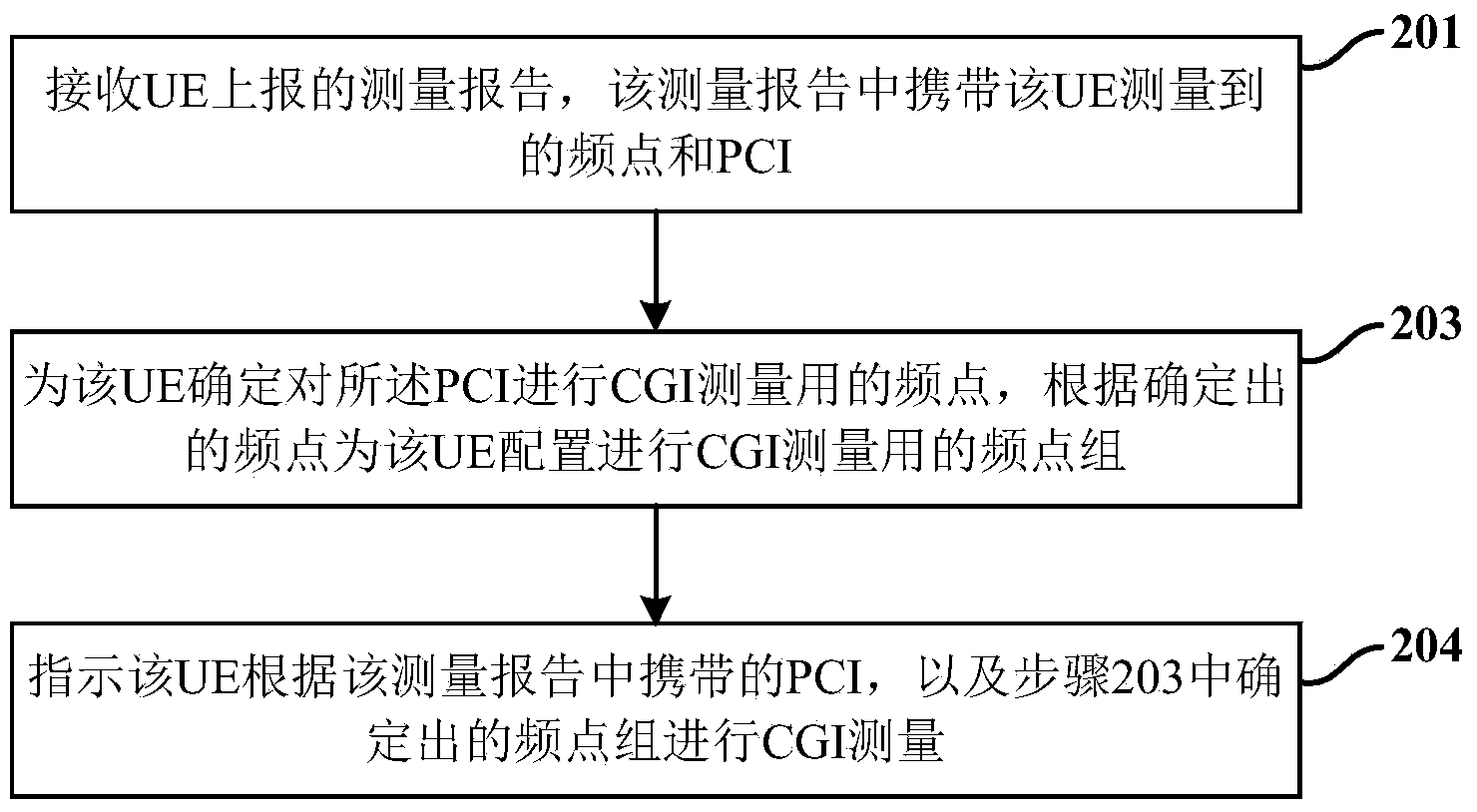
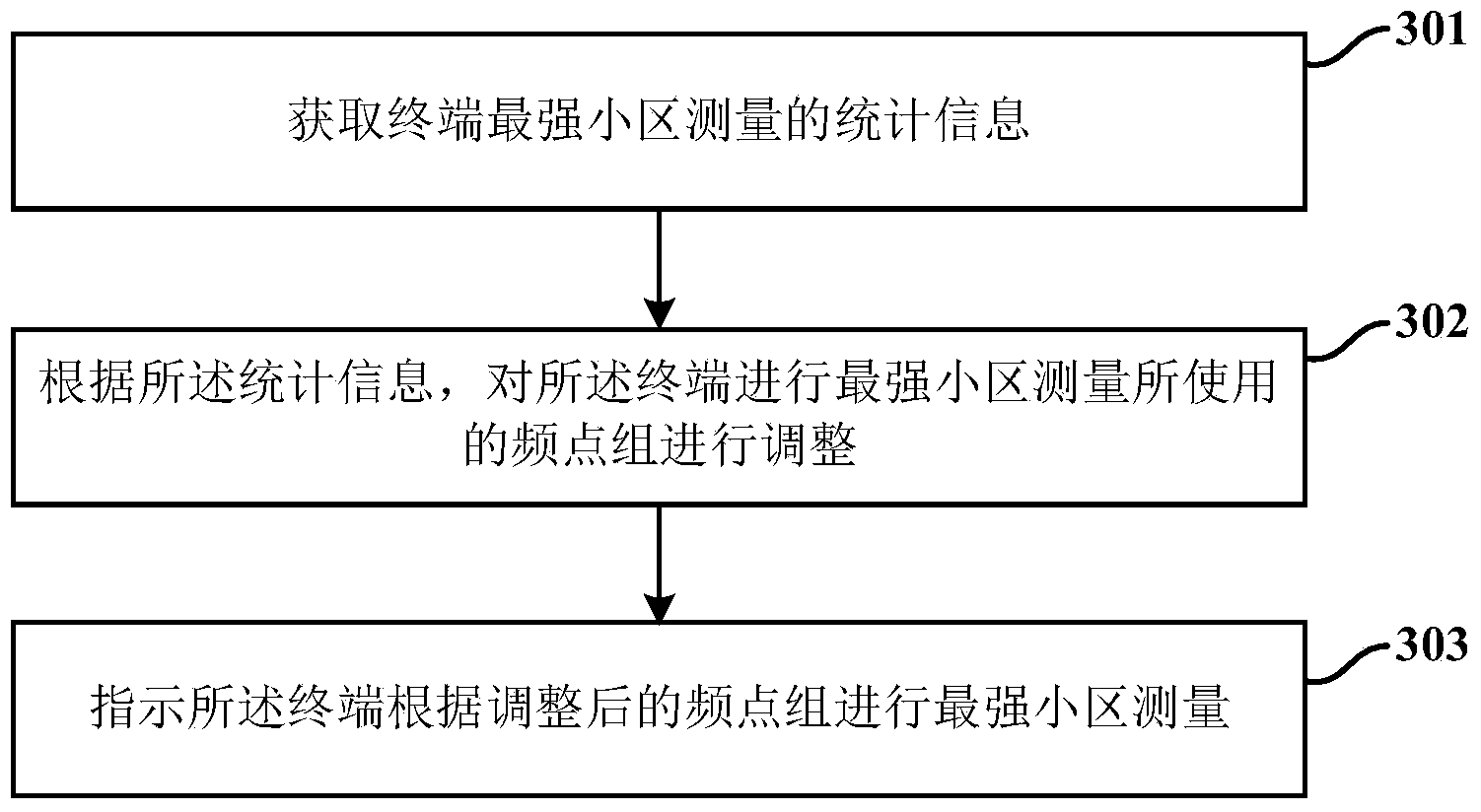
ANR measurement configuration method and device thereof
Provided is an ANR measurement configuration method and device thereof. In a CGI measurement direction process, a measurement report of a terminal is received. The measurement report carries frequency points measured by the terminal and a PCI. The frequency points used for measuring CGI of PCI are confirmed by the terminal. A frequency point group used for measuring CGI of the terminal configuration is confirmed according to the confirmed frequency points.CGI measurement is carried out by indicating the terminal according to the PCI and the frequency point group. In the process of measurement configuration of the strongest cell, statistical information of the strongest cell measurement is obtained. According to the statistical information, the frequency points used by the strongest cell measurement by the terminal are adjusted. The strongest cell measurement is carried out by the terminal according to the frequency point group after adjusting.
Owner:HUAWEI TECH CO LTD
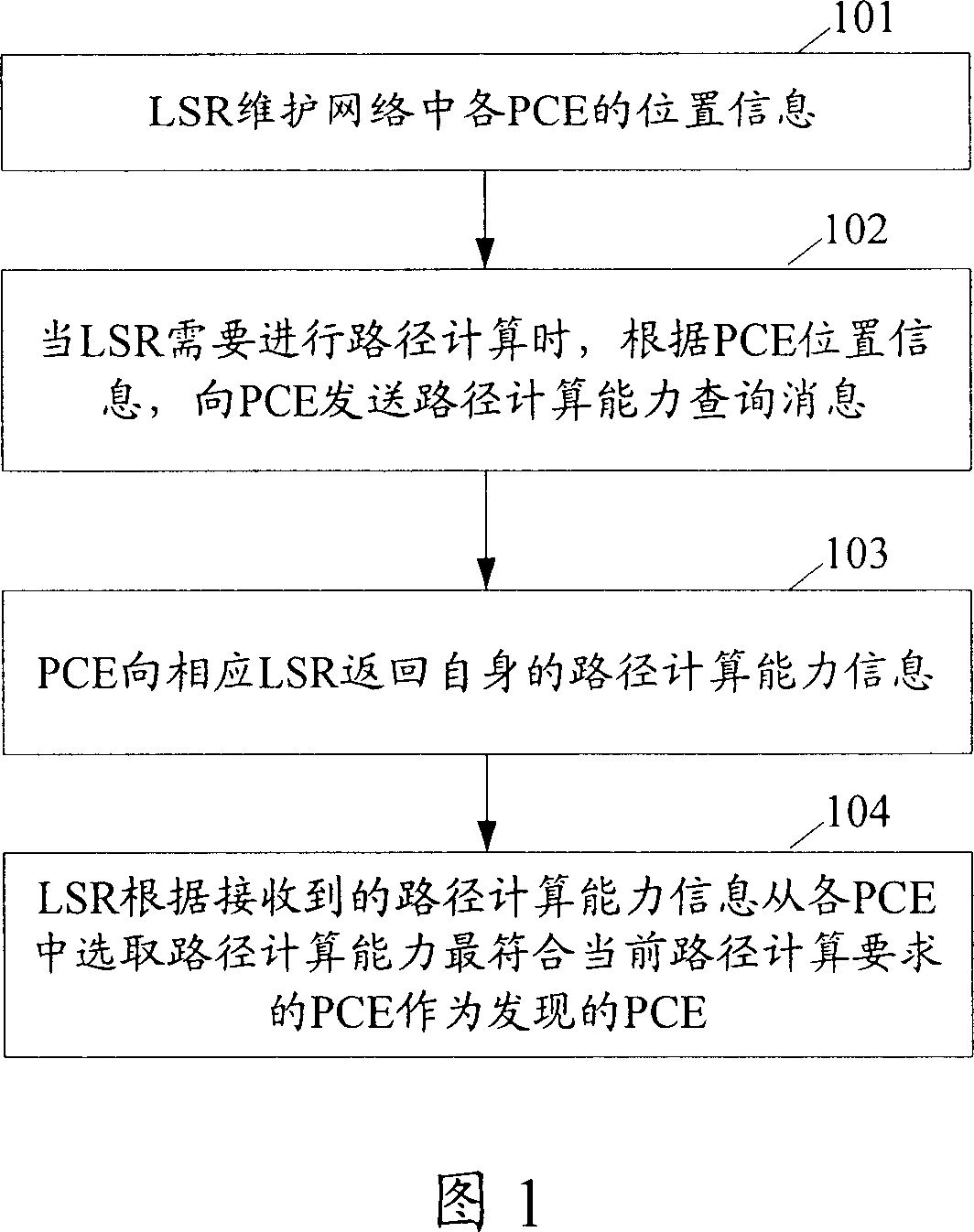
Method for discovering unit of route calculation
InactiveCN101094168AImprove discovery efficiencyReduce trafficData switching networksTraffic volumeReal-time computing
The method comprises: when needing to make path calculation, the label switch router (LSR) in network gets the path calculation capacity information of each PCE in network, and according to the obtained path calculation capacity information, finds PCE. In the invention, only LSR having path calculation request can make PCE finding so as to avoid the LSR without path calculation request makes PCE finding.
Owner:HUAWEI TECH CO LTD
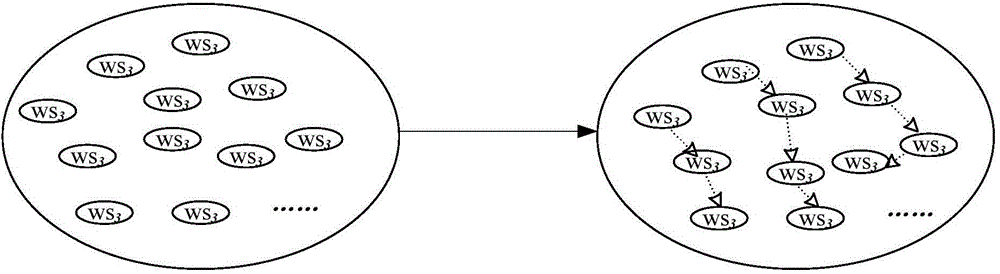
Service combining and replacing method based on service cluster
InactiveCN104902018AImprove discovery efficiencyImprove combination efficiencyTransmissionDistributed computingWeb service composition
The invention discloses a service combining and replacing method based on a service cluster. The service cluster is constructed with an existing service clustering method, and a formal description method of services and the service cluster is put forward based on a Petri network; and the input and output parameters of the services are represented in an abstract way, and the input and output parameters of the services are described through a parameter matrix. Through adoption of a service matching method in the invention, universality and individuality can be fully realized among the services in the service cluster, and the service discovery and combining efficiencies are increased by narrowing of a service discovery range. A Web service combining and replacing method is provided through improvements on a service cluster model. Parallel combination and serial combination of the services in the service cluster are described respectively, and rapid service combination is realized in the service cluster, so that efficient service combination and replacement are realized. Through adoption of the service replacing method in the invention, single service replacement in the service cluster can be realized, and service combination and replacement in the service cluster can be realized.
Owner:SHANDONG UNIV OF SCI & TECH
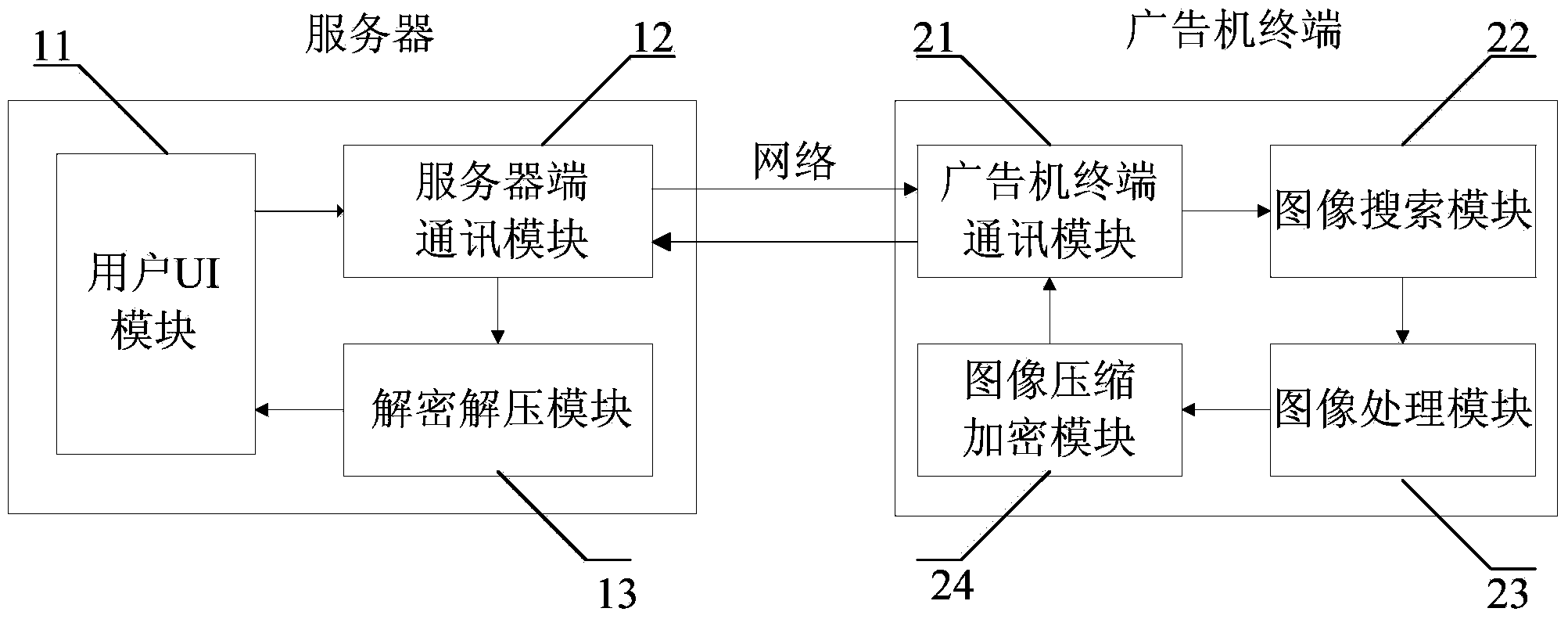
Advertising machine system with long-distance screen capture function and method of advertising machine system
InactiveCN104244029AWith remote screenshot functionEasy to communicate in real timeSelective content distributionComputer terminalMachining system
The invention provides an advertising machine system with a long-distance screen capture function and a method of the advertising machine system. An advertising machine at least comprises a server, a network and a plurality of advertising machine terminals, and the server sends out a current image request to the advertising machine terminals, receives and displays current image information sent by the advertising machine terminals; the network is respectively connected with the server and the advertising machine terminals; the advertising machine terminals receive the current image request of the server and sends the current image information to the server. According to the advertising machine system with the long-distance screen capture function and the method of the advertising machine system, all content, including playing content of advertisement, a terminal abnormal display state and a terminal maintenance interface, displayed on screens of the advertising machine terminals can be visually seen at the server end, and accordingly the advertising machine terminals can be further managed and controlled.
Owner:上海信颐电子科技有限公司
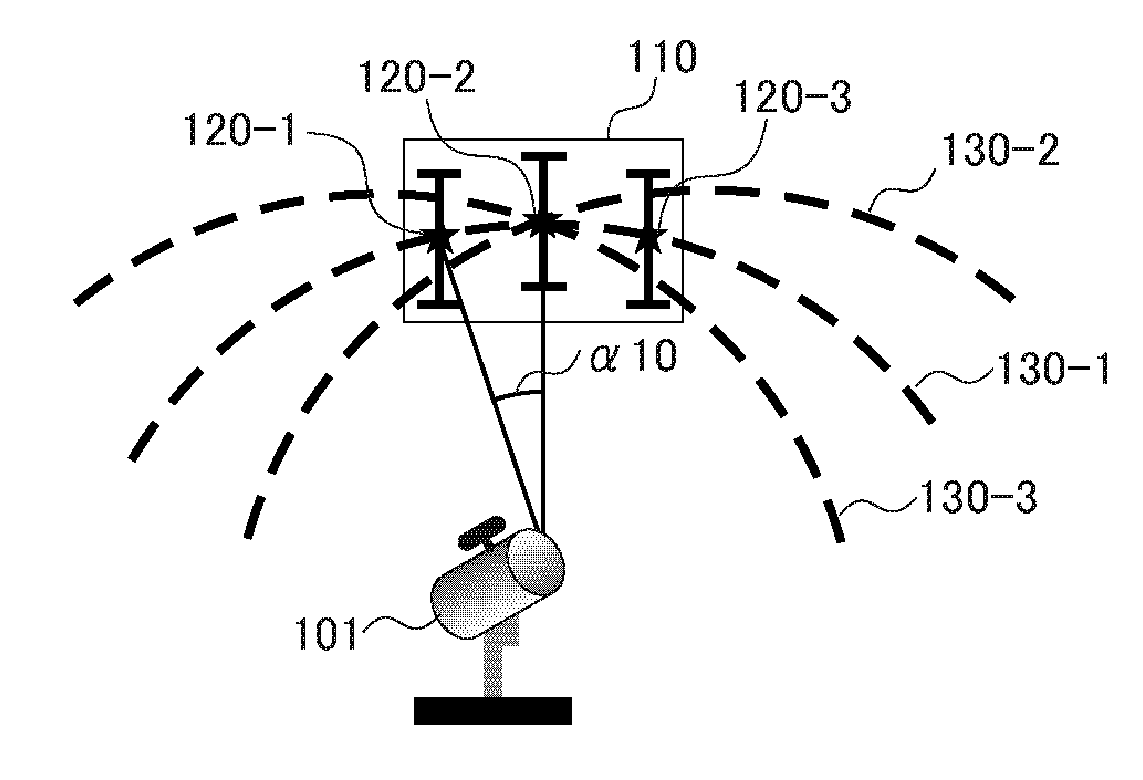
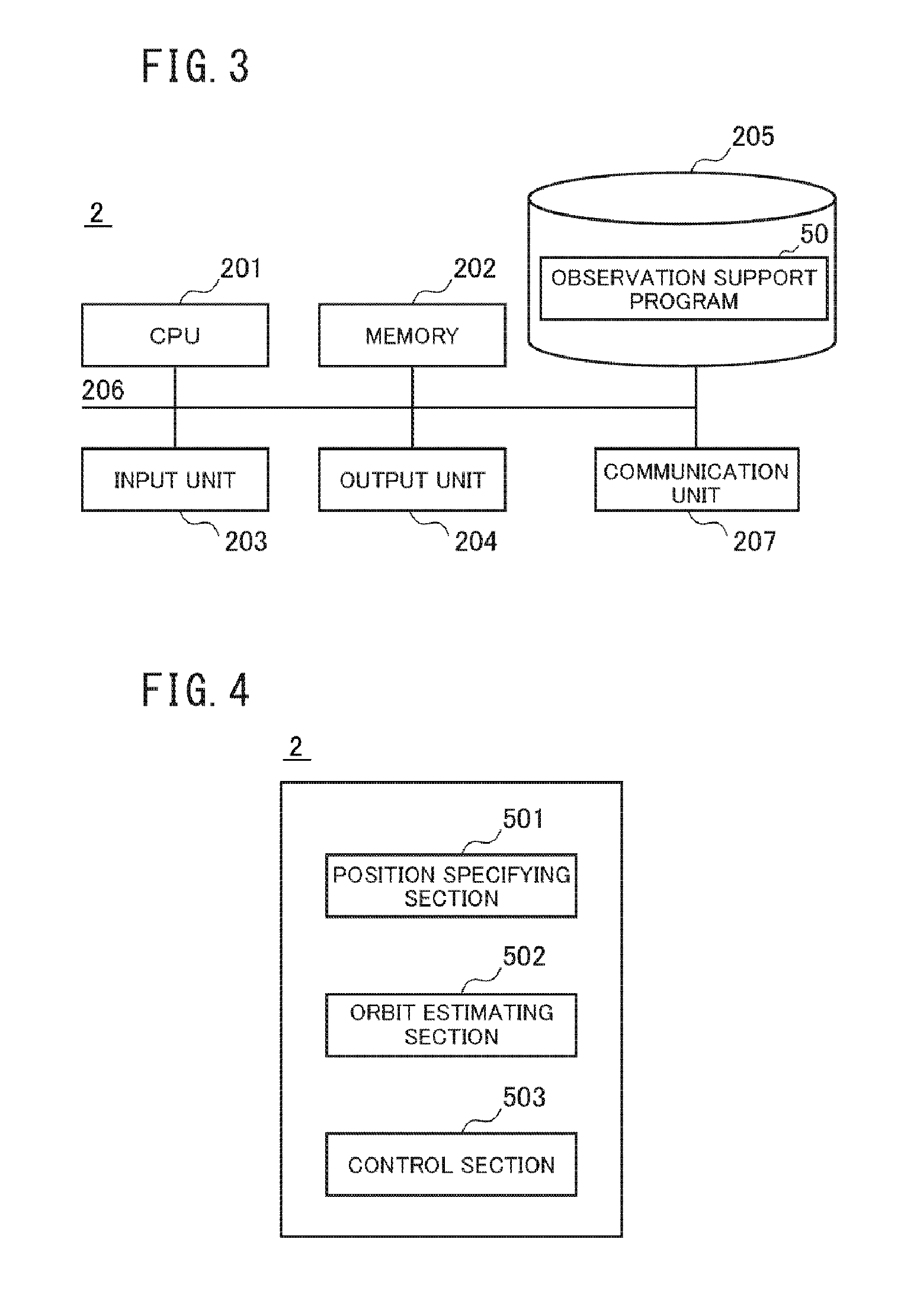
Observation supporting apparatus and observation supporting method
ActiveUS20150323305A1Improve discovery efficiencyImprove efficiencyDigital computer detailsSpeed measurement using gyroscopic effectsOrbitField of view
An observation supporting apparatus includes a position specifying section which specifies a coordinate point of a moving object detected in a viewing field through once observation. An orbit estimating section calculates an estimate orbit of the moving object in the viewing field based on the specified coordinate points. Data necessary to estimate the position of the moving object out of the viewing field is acquired using the estimate orbit by the orbit estimating section.
Owner:MITSUBISHI HEAVY IND LTD
Neighbor discovery method for mobile ad hoc network based on directional antenna
InactiveCN106792620AImprove discovery efficiencyShorten the timeNetwork topologiesNetwork data managementTelecommunicationsDirectional antenna
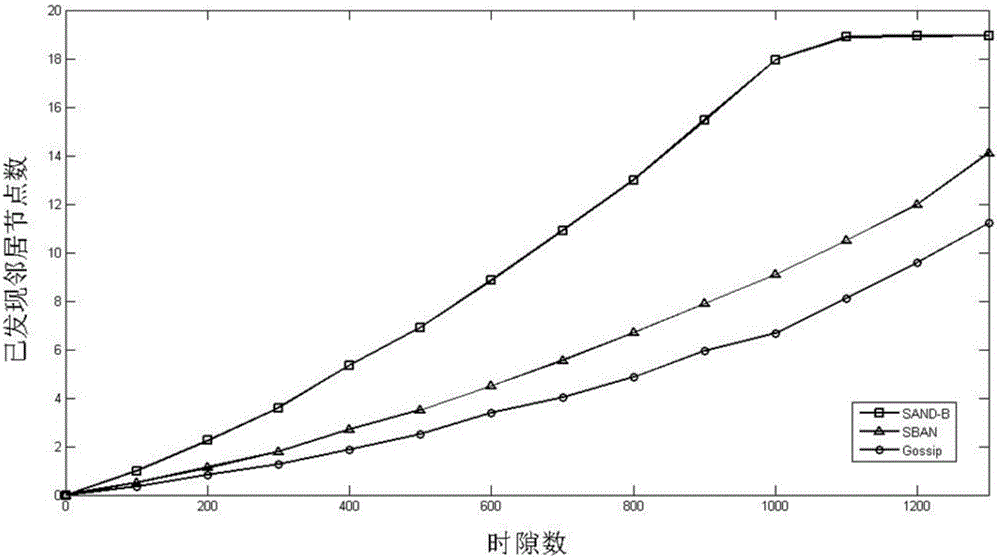
The invention discloses a neighbor discovery method for a mobile ad hoc network based on a directional antenna. By adoption of the neighbor discovery method, the technical problem of low neighbor discovery efficiency of the existing network neighbor discovery method is solved. The technical scheme is as follows: in every neighbor scanning process, each node discovers a certain number of neighbors, so the node can use the existing neighbor information to accelerate the neighbor discovery process. As the existing neighbor information is used, neighbor tables are continuously exchanged, compared with the method in the background art, the method has the advantage that the existing information is fully used, and whether a neighbor relationship exists is directly judged by an algorithm, therefore the time of active scanning detection is shortened. Compared with the background art, the method has the advantages that the neighbor discovery time is greatly shortened, and the neighbor discovery efficiency is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
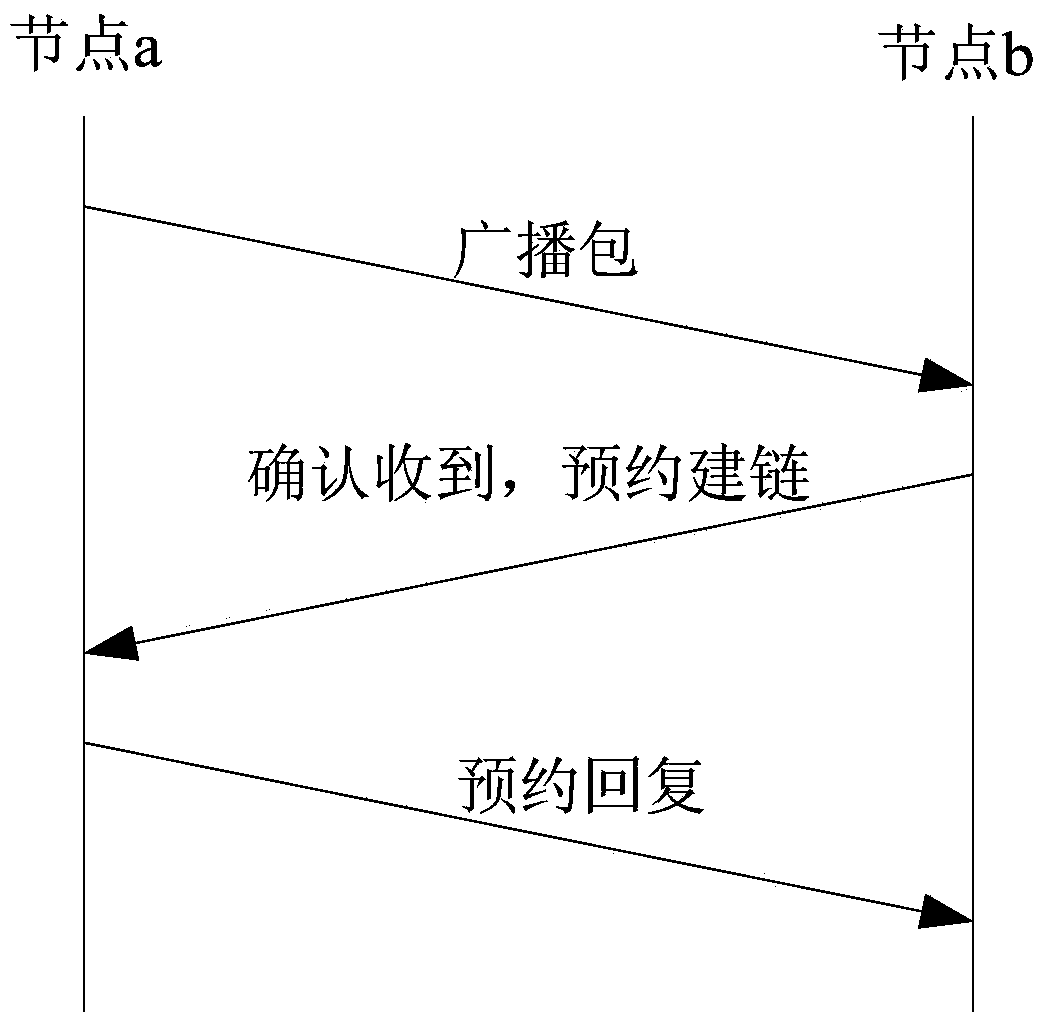
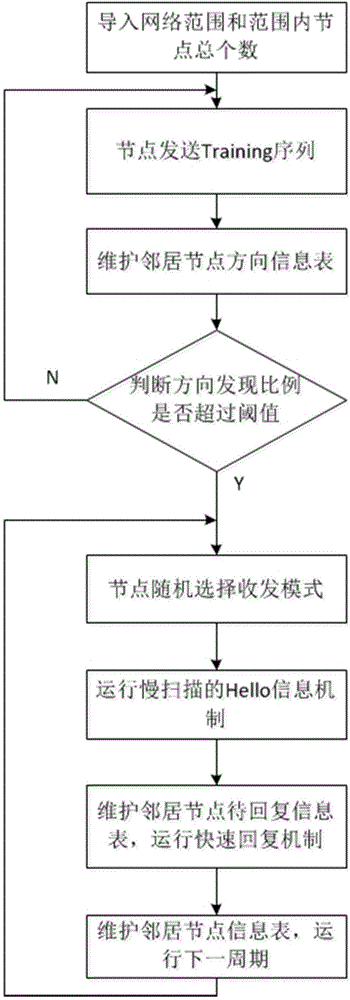
Neighbor node finding method based on beam forming antenna
ActiveCN104469731AReduce overheadImprove securityAssess restrictionNetwork data managementDirection informationComputer science
The invention relates to a neighbor node finding method based on a beam forming antenna. The method comprises the following steps that (1) a network range and the total number of nodes within the range are input; (2) the optimum distribution of intervals formed when an omnibearing finding stage sends Training sequences is calculated; (3) a receiving node maintains a neighbor node direction information table according to the Training sequences; (4) when the neighbor node direction finding proportion exceeds a threshold value, an orientation finding stage is started; (5) an independent transmitting and receiving mode is selected before a period starts; (6) the node runs a slow-scanning Hello information mechanism; (7) the node receiving Hello information maintains a neighbor node to-be-relied information table, a rapid reply mechanism is made to run, the node in the receiving mode is selected to enter a rely information receiving stage. Compared with the prior art, on the basis of the asynchronous time slot, the reliability of the neighbor nodes is ensured through two handshakes, and the neighbor nodes can be rapidly and effectively found.
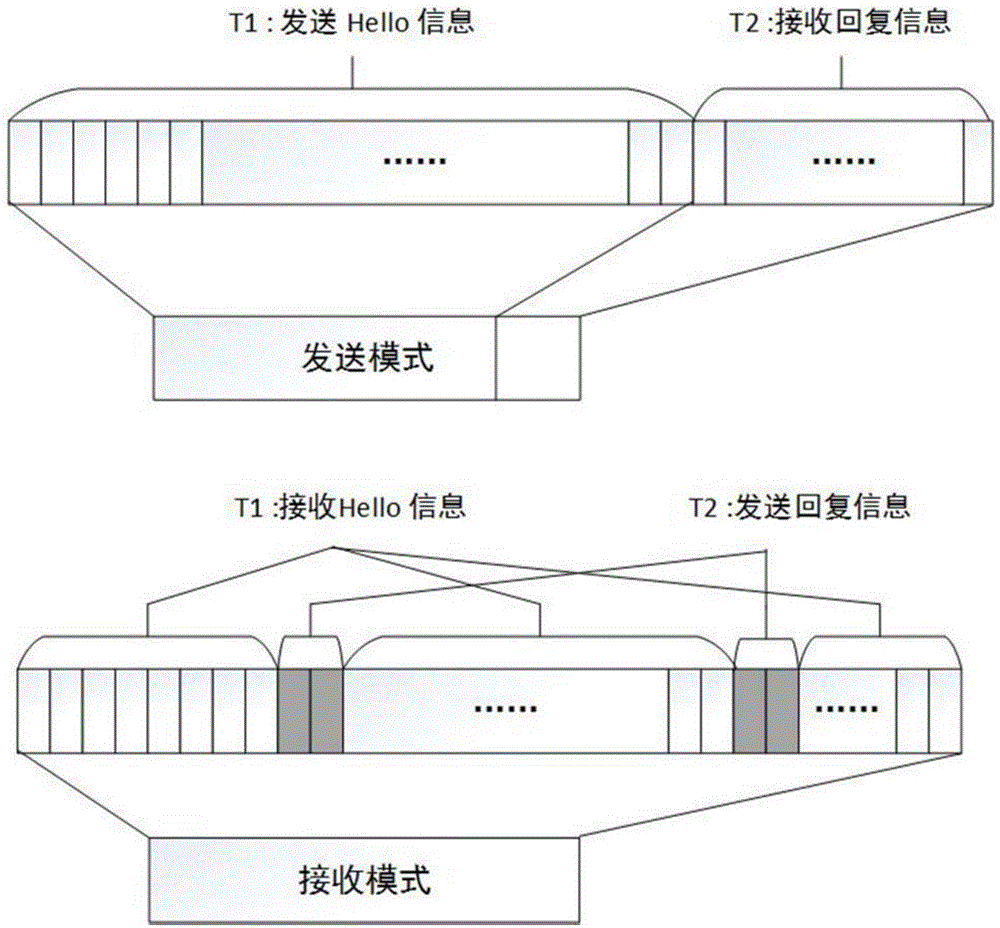
Owner:SHANGHAI JIAO TONG UNIV
Leaky cable/antenna feeder real-time monitoring apparatus and working method thereof
InactiveCN103344880ARapid positioningImprove troubleshooting efficiencyFault locationElectromagnetic electron waveComputer module
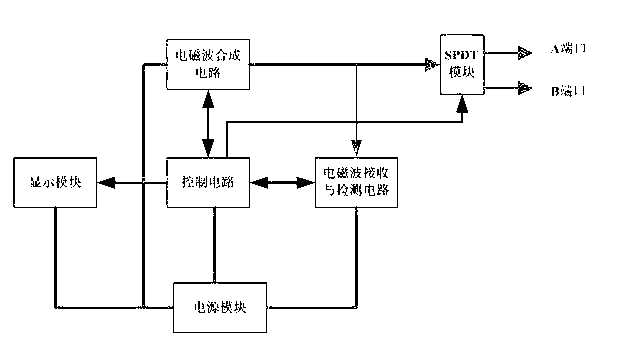
The invention provides a leaky cable / antenna feeder real-time monitoring apparatus and a working method thereof. The real-time monitoring apparatus is composed of a power supply module, an SPDT module, an electromagnetic wave synthesis circuit, an electromagnetic wave receiving and detection circuit, a display module and a control circuit. An electromagnetic wave is generated by the electromagnetic wave synthesis circuit; an output port is selected by a dual-channel radio frequency port of the SPDT module so as to output an electromagnetic wave signal to an antenna feeder or a leaky cable; when the electromagnetic wave runs into a fault point and is reflected the electromagnetic wave receiving and detection circuit receives the electromagnetic wave, detects the signal intensity and sends data to the control circuit; and the control circuit determines a fault level and fault position according to the detected data and sends the determination information to an alarm display lamp, and the fault position and the fault level are sent to a network management center by a network cable interface so as to display the information for the staff. According to the invention, the following beneficial effects are as follows: a fault point positioning function, a real-time on-line monitoring function, a dual-channel monitoring function and a function of adjustability of frequency for monitoring are realized, thereby providing convenience for fault monitoring of a leaky cable or an antenna feeder.
Owner:NANJING TICOM TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com