Software security vulnerability detection method and system for deep learning gradient guidance variation
A technology for software security and vulnerability detection, which is applied in neural learning methods, software testing/debugging, computer security devices, etc., can solve problems such as mutation, and achieve the effects of fine segmentation granularity, improved discovery efficiency, and high vulnerability efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
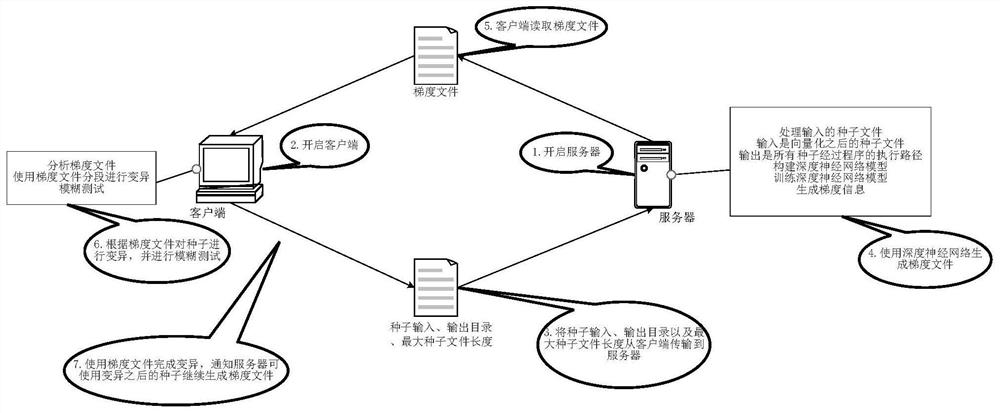
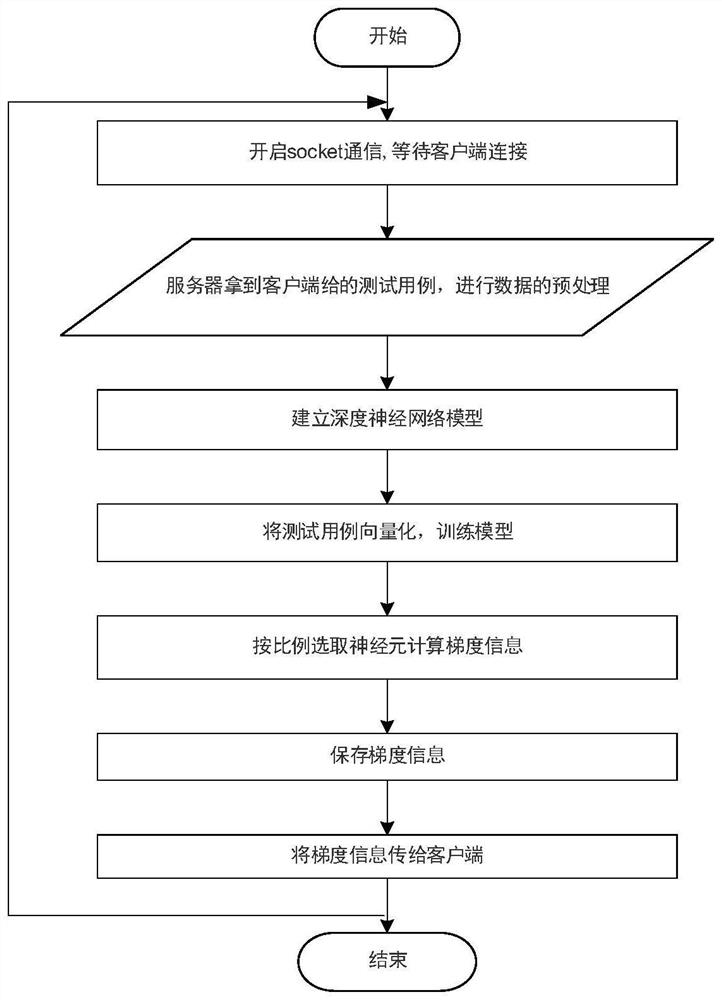
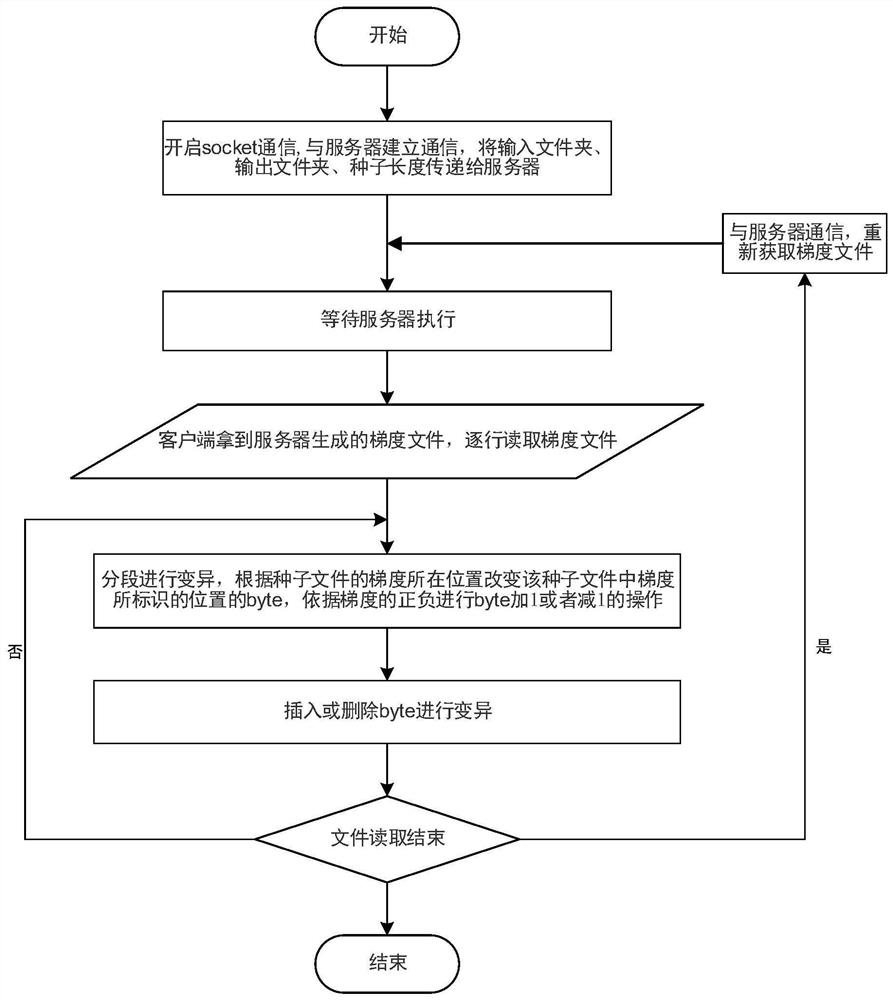
[0063] see Figure 1 to Figure 3 , this embodiment provides a method for detecting software security vulnerabilities using deep learning gradient-guided mutation, the method may be implemented by an electronic device, and the electronic device may be a terminal or a server. This method is a mutation-based grey-box fuzzing method, which uses program smoothing technology to calculate gradient information, and program smoothing uses deep neural network to achieve; where, program smoothing technology refers to a given program input, and the output of the program is continuous . The input of this method is the vectorized seed file, and the output is the branch information of all seeds, indicating the probability of the seed passing through each branch. The execution process includes the following steps:
[0064] S101, acquire test cases, and preprocess the acquired test cases, obtain the size of the largest test case in the test cases and the execution path of each test case in th...
no. 2 example
[0101] This embodiment provides a software security vulnerability detection system with deep learning gradient guidance mutation, the software security vulnerability detection system includes a server and a client: wherein,
[0102] Described server is used for obtaining test case, and the test case that obtains is preprocessed, obtains the size of maximum test case in test case and the execution path of each test case in the program under test; Establishes deep neural network model, described The deep neural network model comprises an input layer, an output layer and a plurality of hidden layers between the input layer and the output layer; wherein, the input dimension of the input layer is the size of the maximum test case, and the output layer's The number of output neurons is the total number of the execution path; the test case is vectorized, and the test case is used to train the deep neural network model after vectorization; gradient calculation is performed based on the...
no. 3 example
[0106] This embodiment provides an electronic device, which includes a processor and a memory; at least one instruction is stored in the memory, and the instruction is loaded and executed by the processor, so as to implement the method of the first embodiment.
[0107] The electronic device may have relatively large differences due to different configurations or performances, and may include one or more processors (central processing units, CPU) and one or more memories, wherein at least one instruction is stored in the memory, so The above instructions are loaded by the processor and perform the following steps:
[0108] S101, acquire test cases, and preprocess the acquired test cases, obtain the size of the largest test case in the test cases and the execution path of each test case in the program under test;
[0109] S102, establish a deep neural network model, the deep neural network model includes an input layer, an output layer and a plurality of hidden layers between th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com