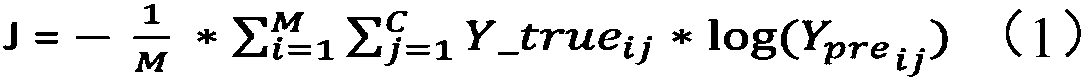Patents
Literature
43 results about "Software Security Vulnerability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A vulnerability is a security weakness in a software program that puts the program or computer at risk of malicious programs and users.
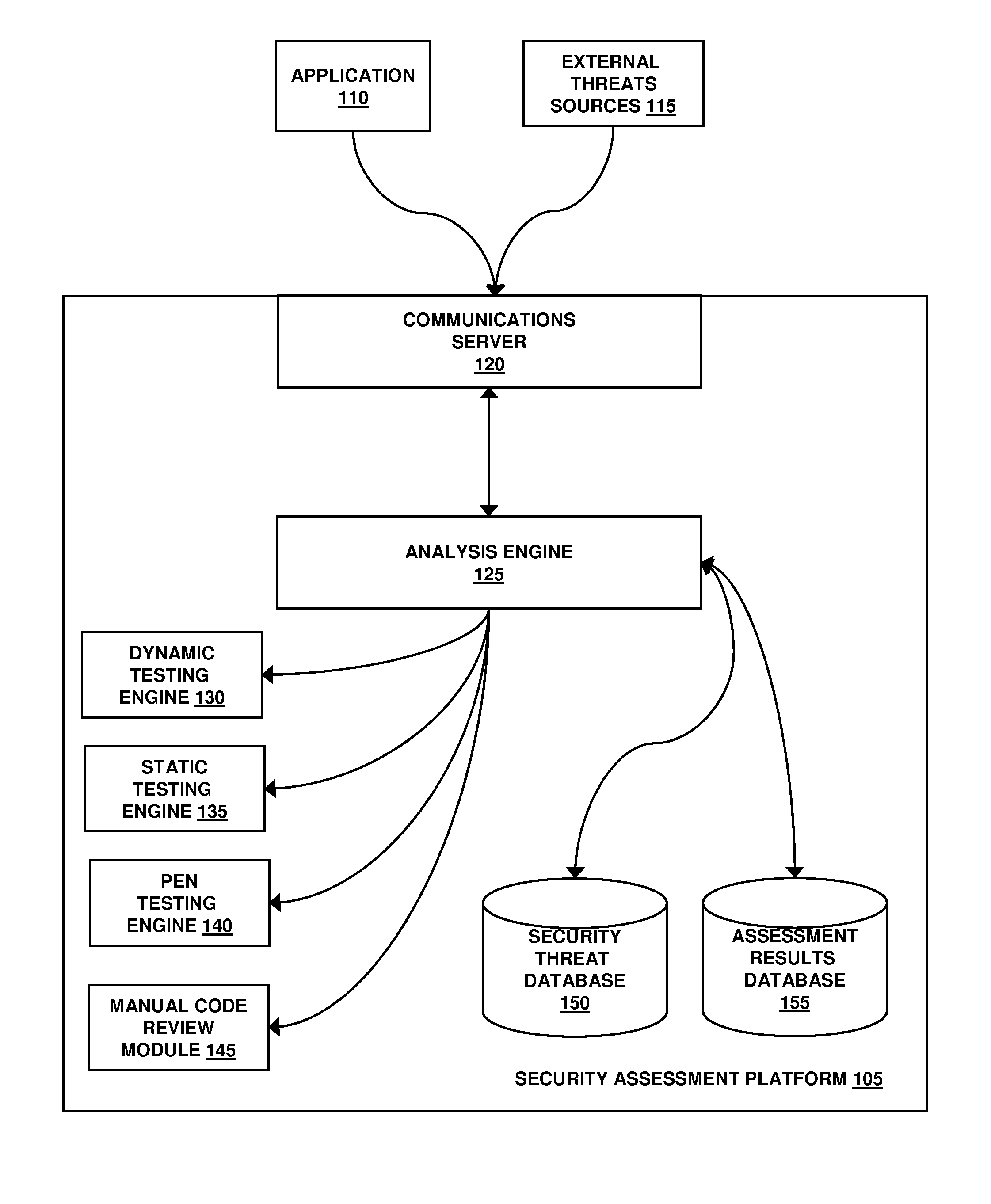
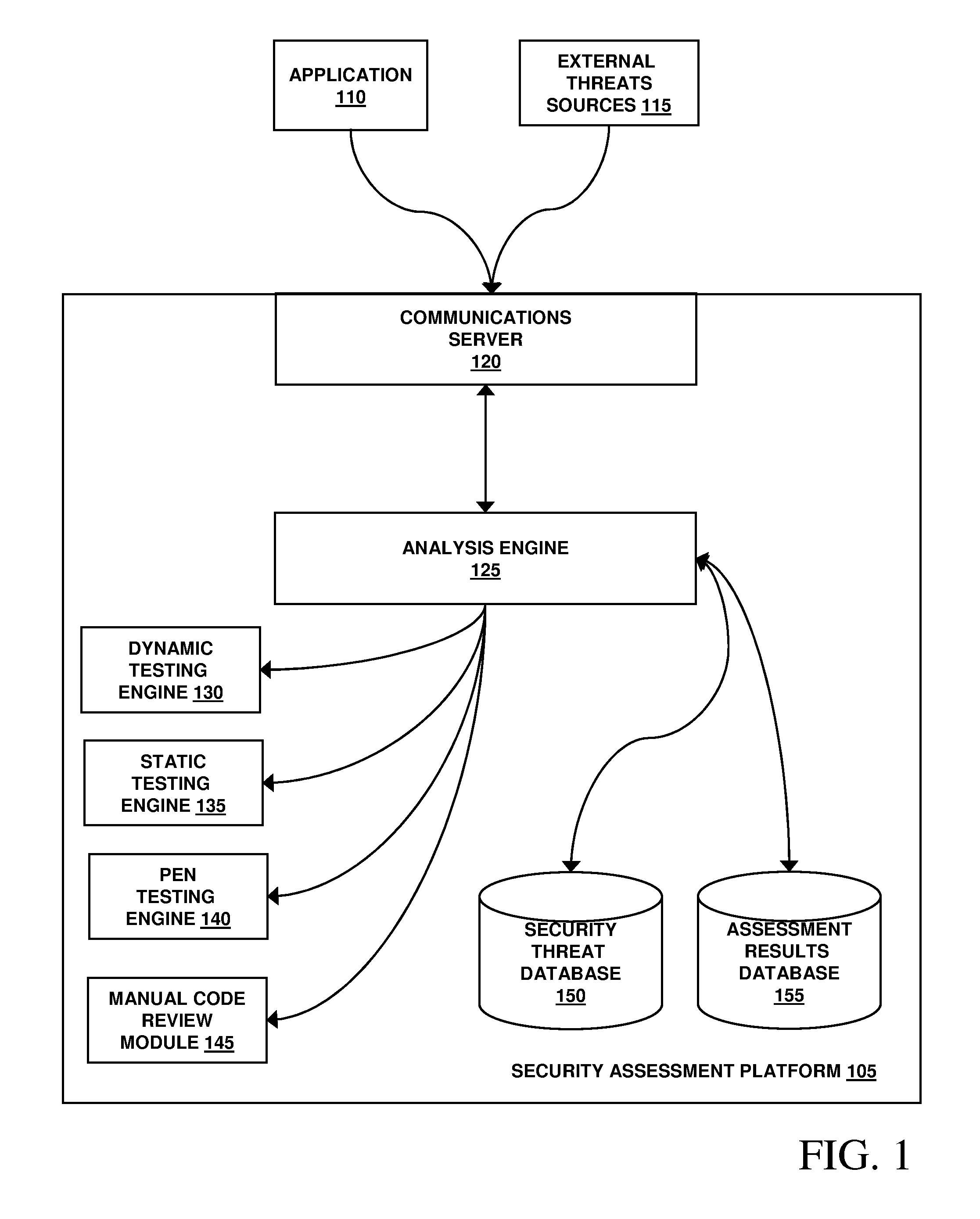
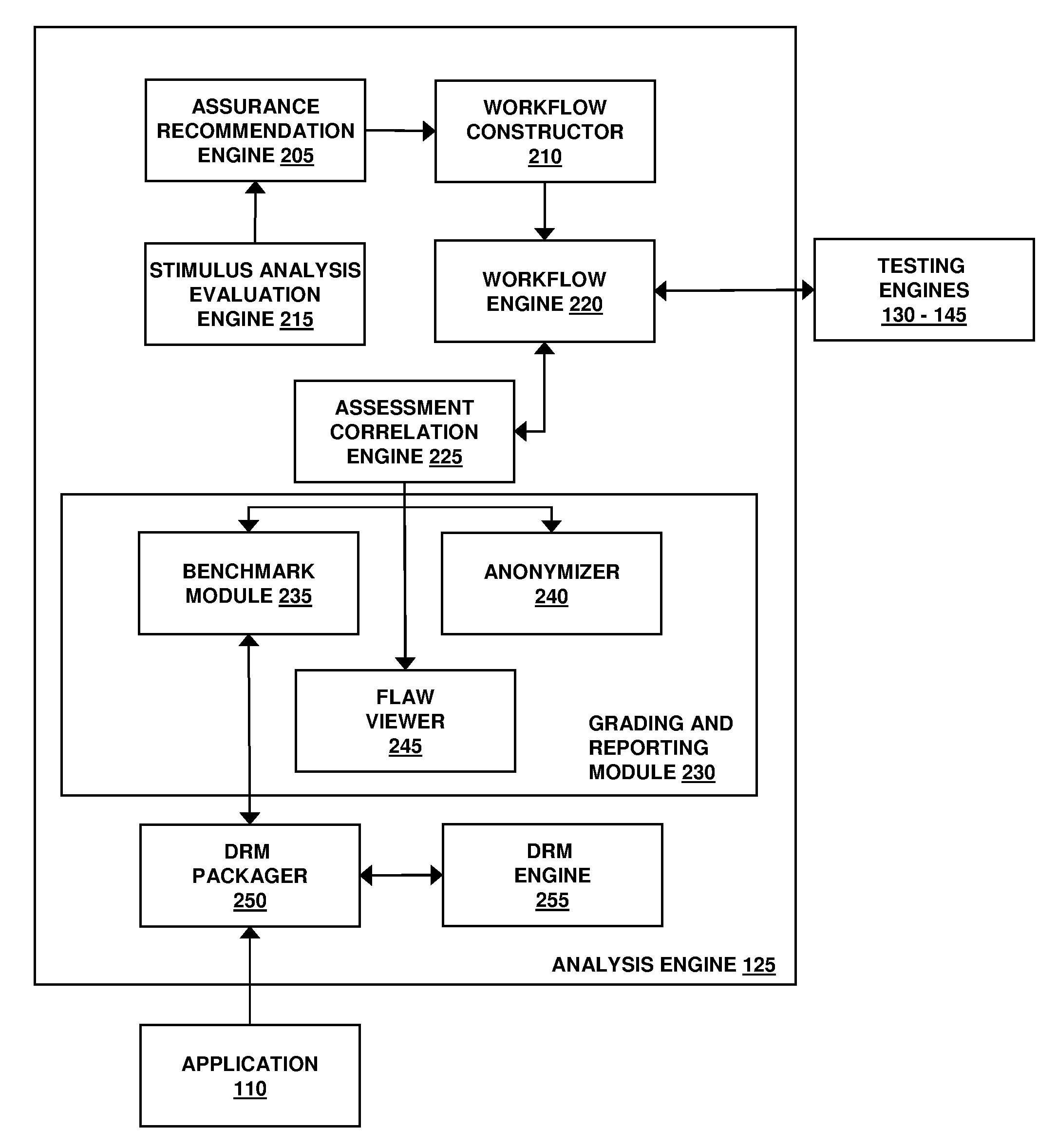
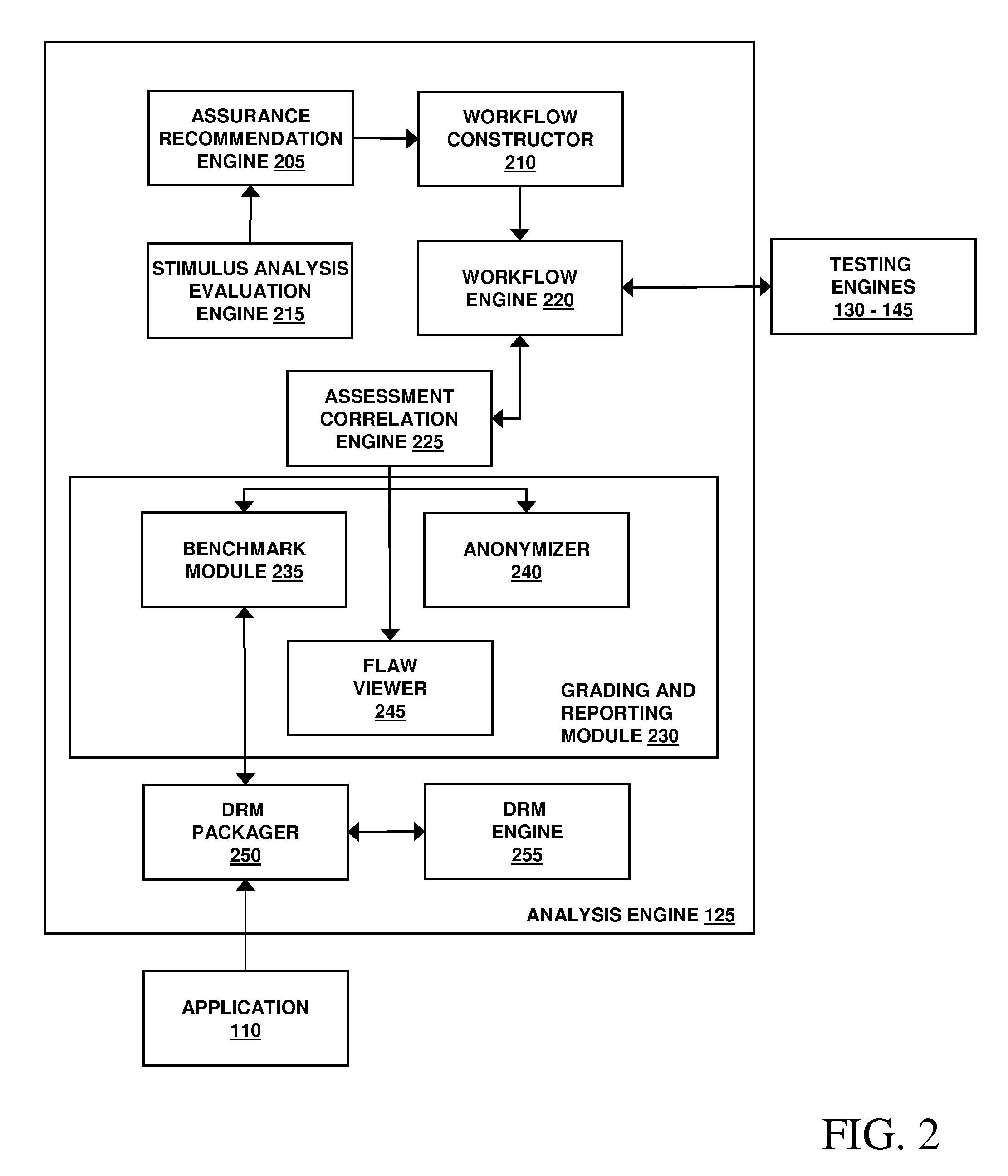
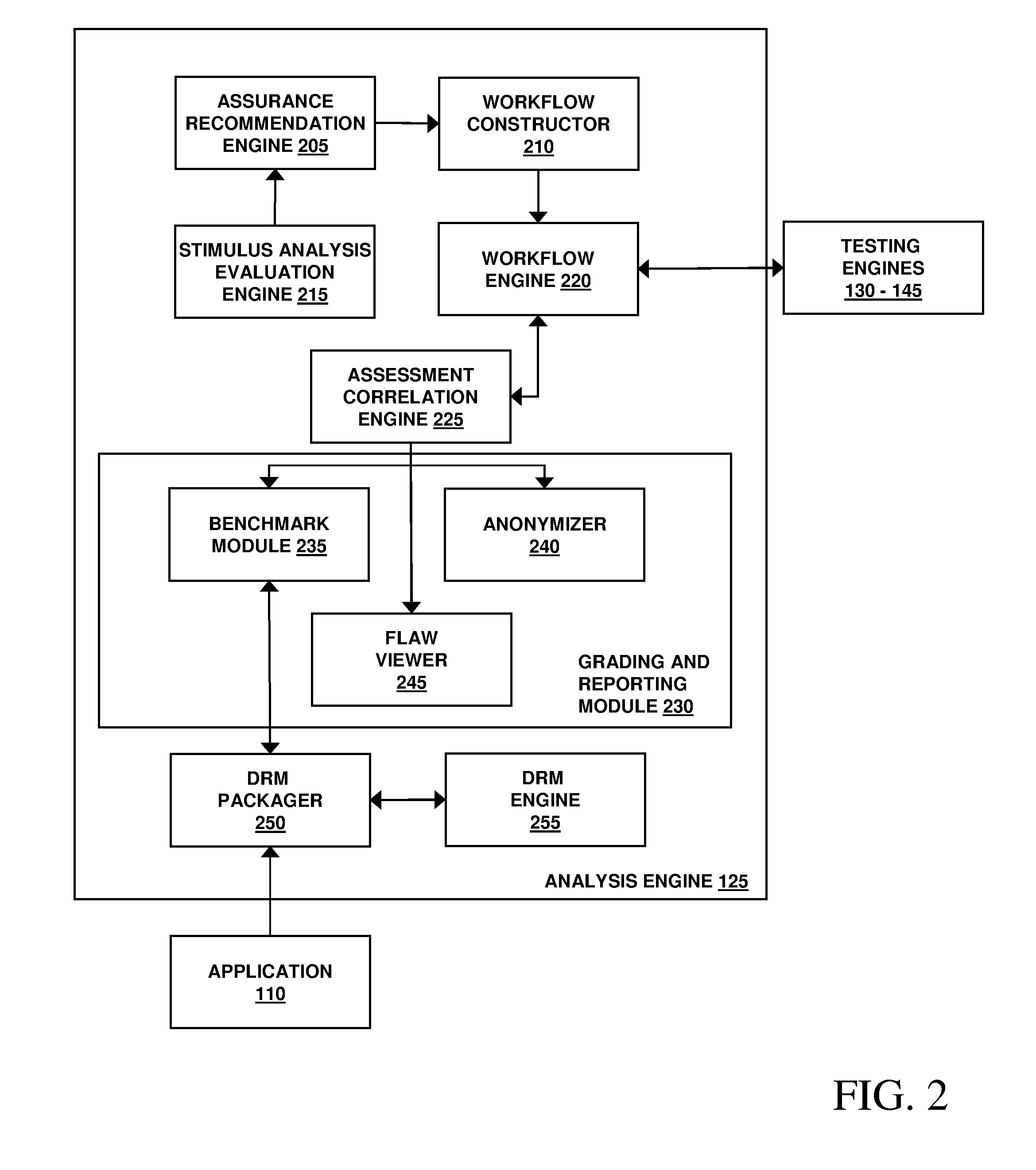
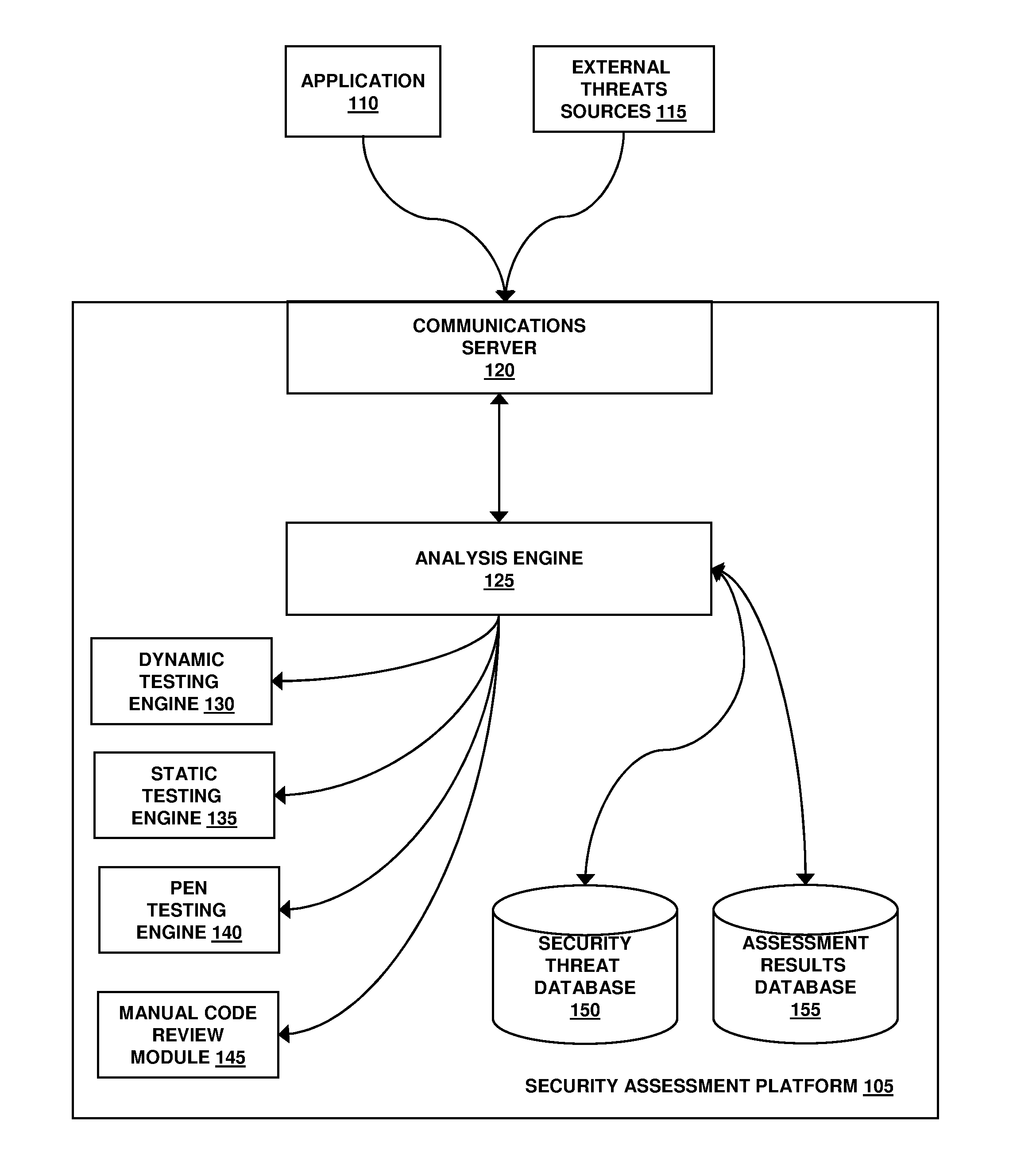
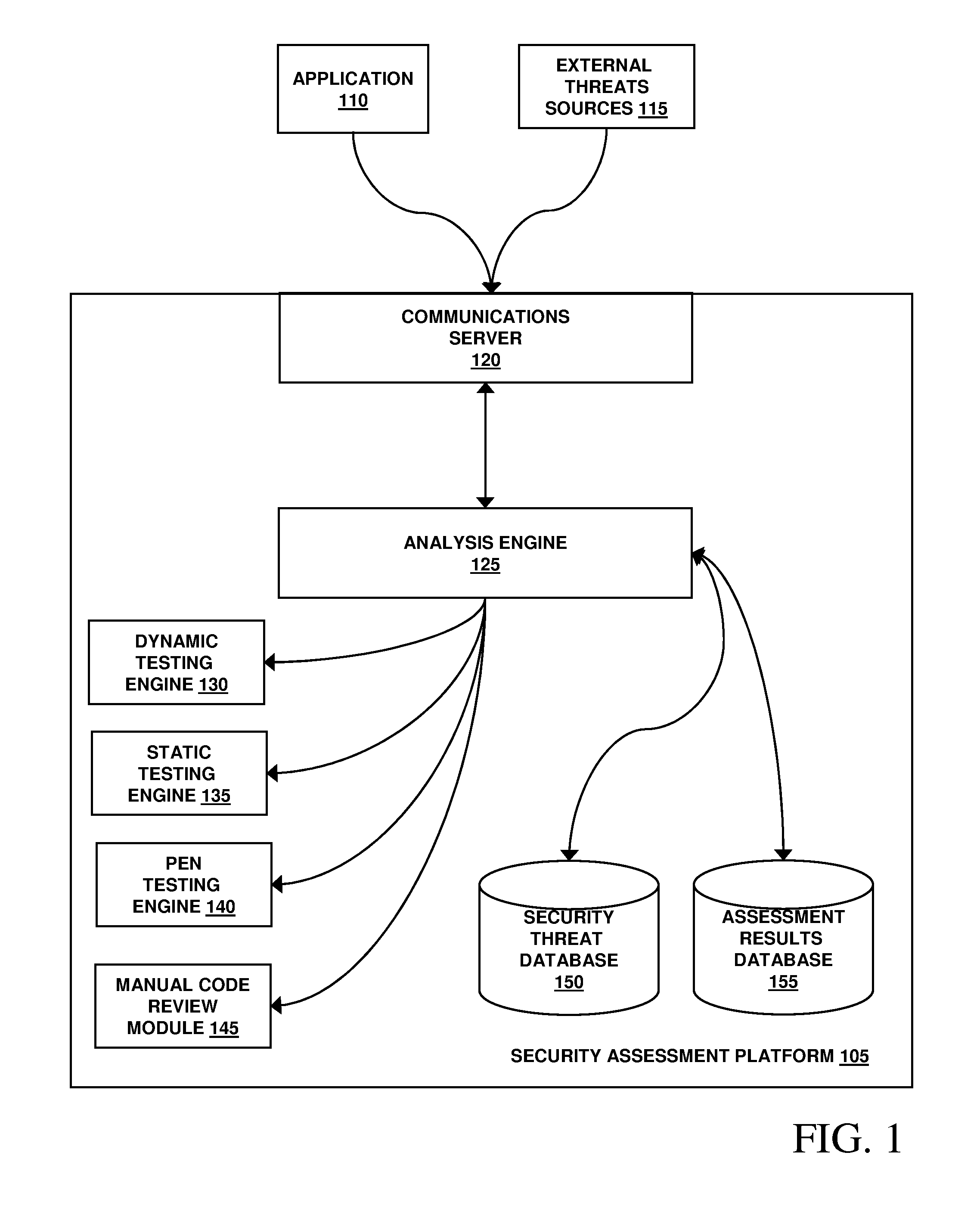
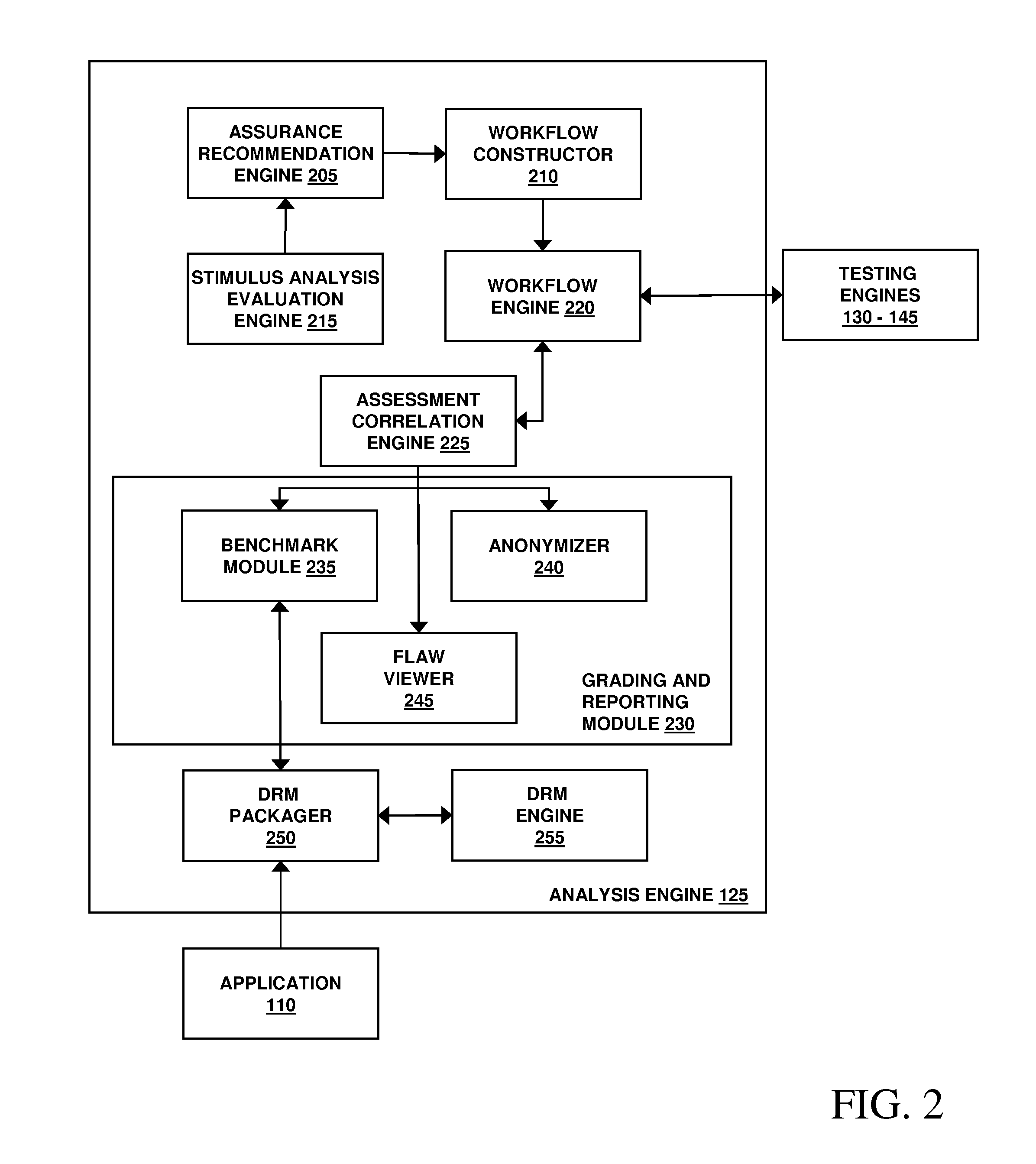
Assessment and analysis of software security flaws in virtual machines
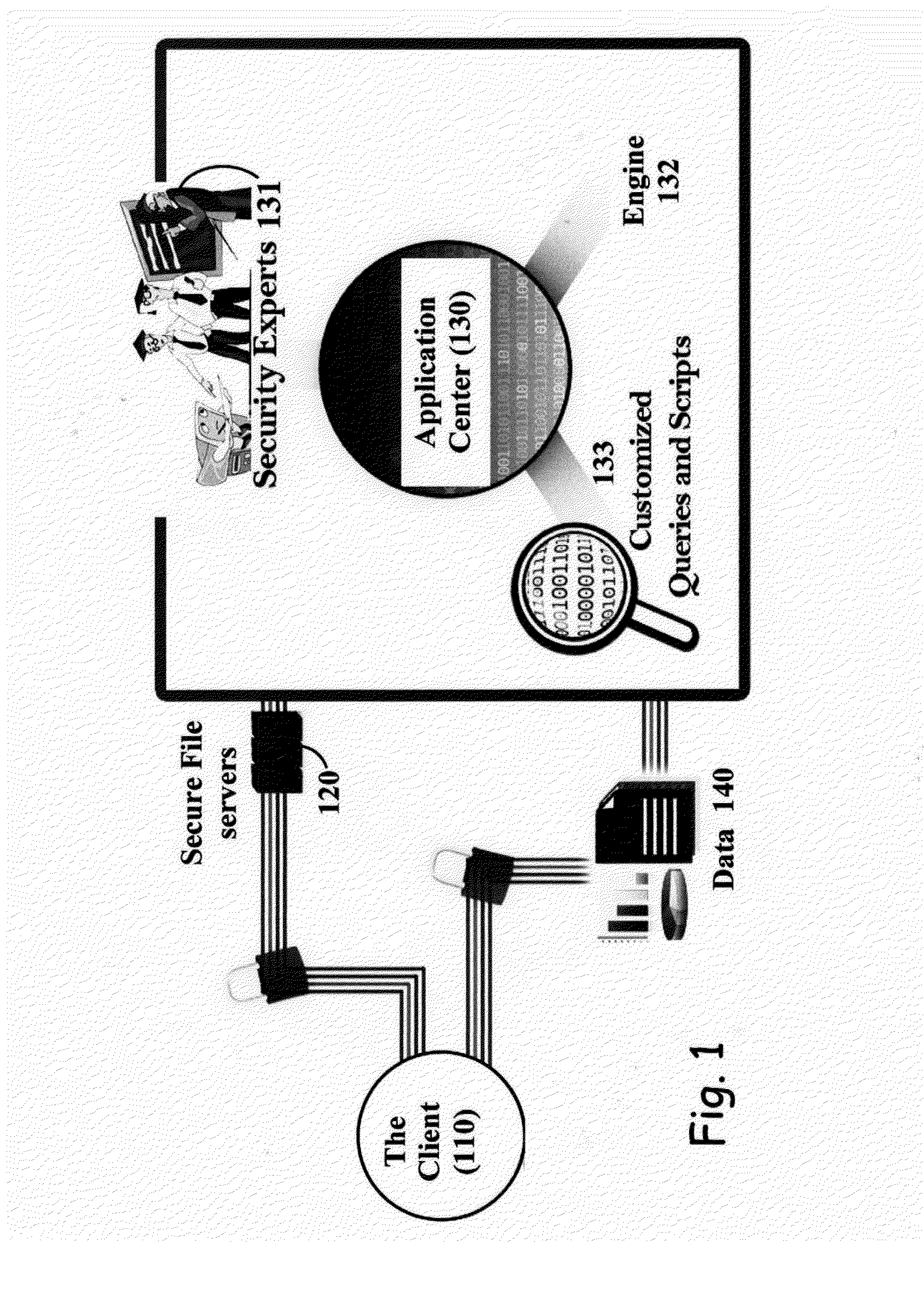
ActiveUS20120072968A1Facilitates benchmarkingFacilitates security assessment and vulnerability testingMemory loss protectionError detection/correctionSoftware engineeringSecurity analysis
Security analysis and vulnerability testing results are “packaged” or “bound to” the actual software it describes. By linking the results to the software itself, downstream users of the software can access information about the software, make informed decisions about implementation of the software, and analyze the security risk across an entire system by accessing all (or most) of the reports associated with the executables running on the system and summarizing the risks identified in the reports.
Owner:VERACODE
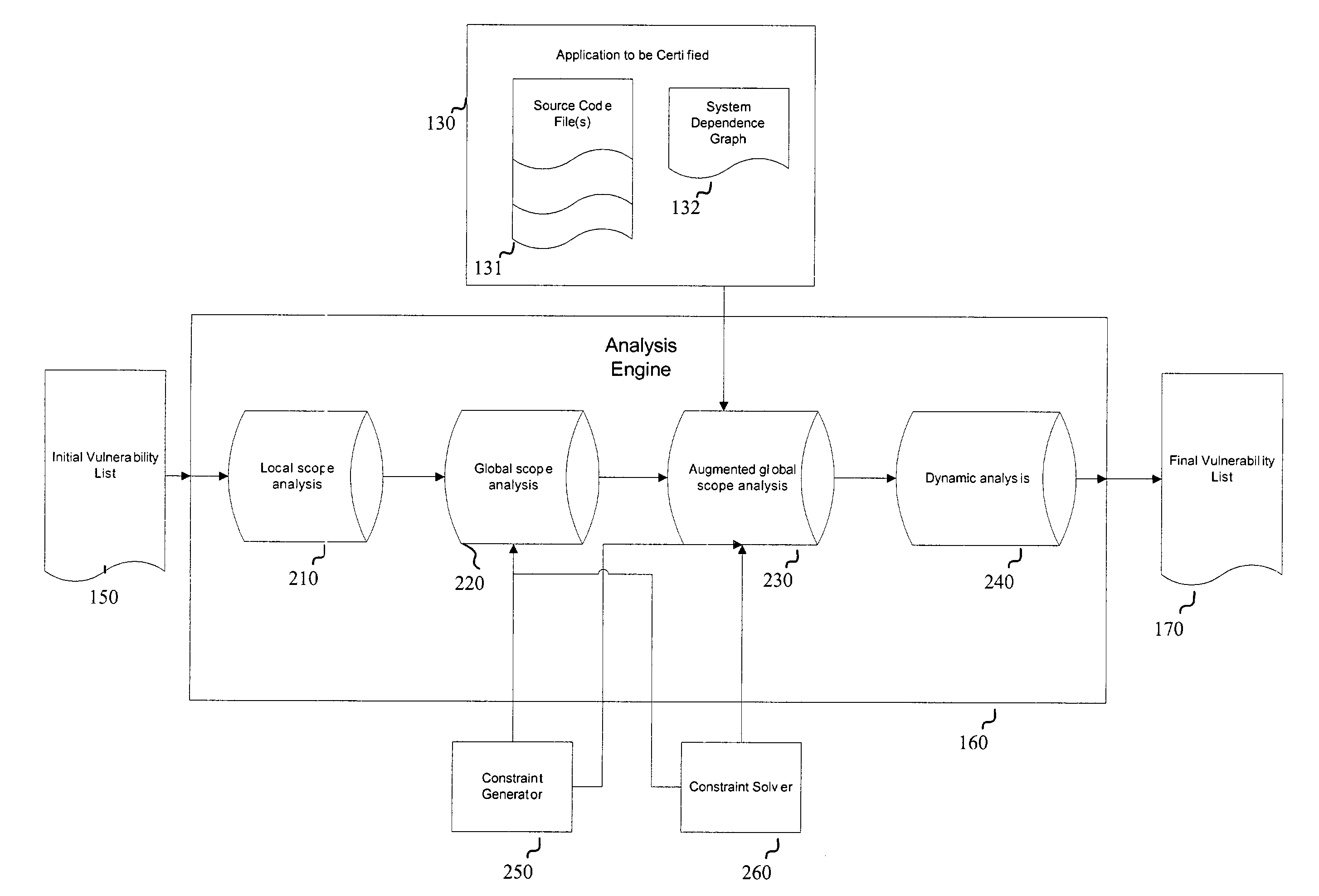
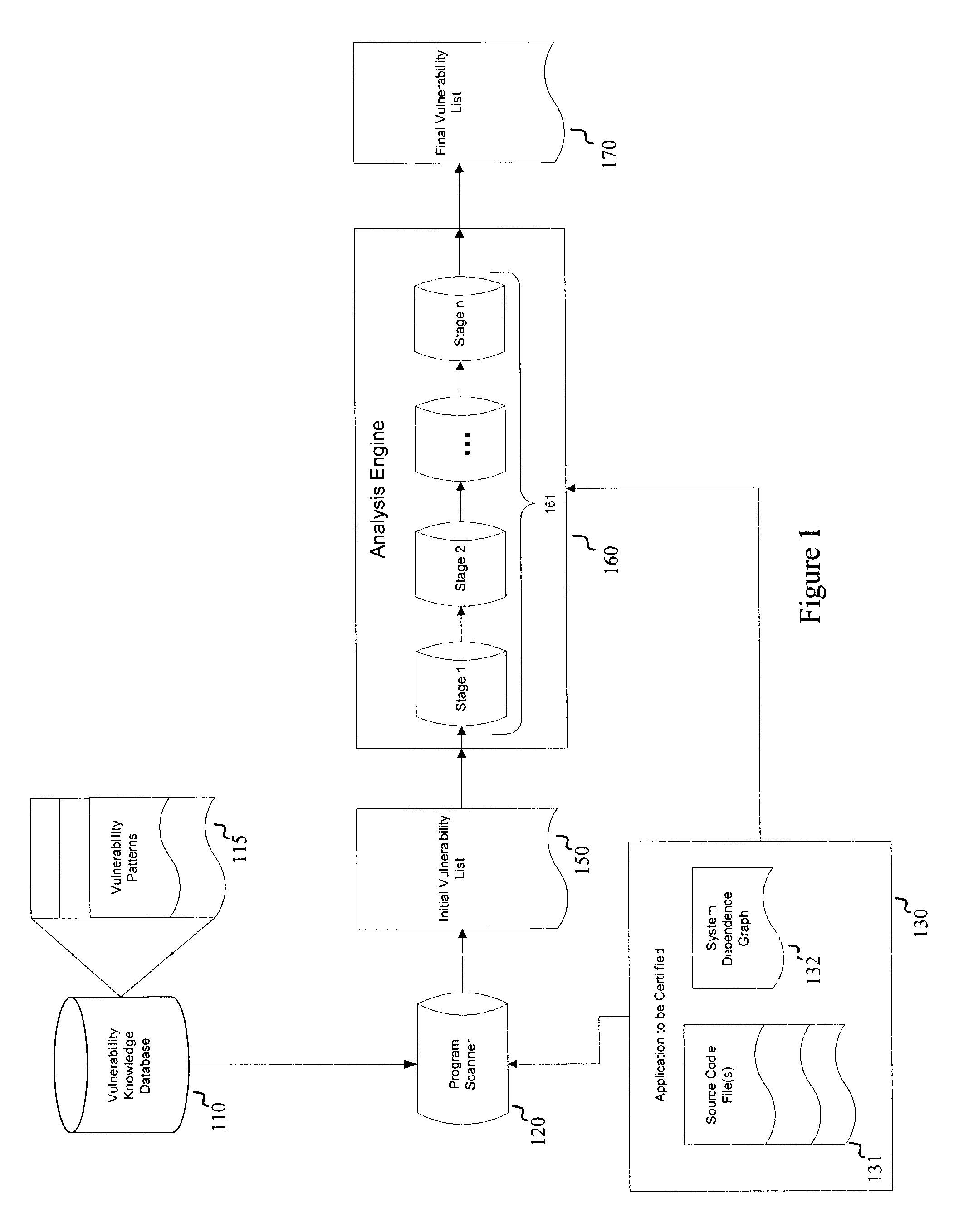
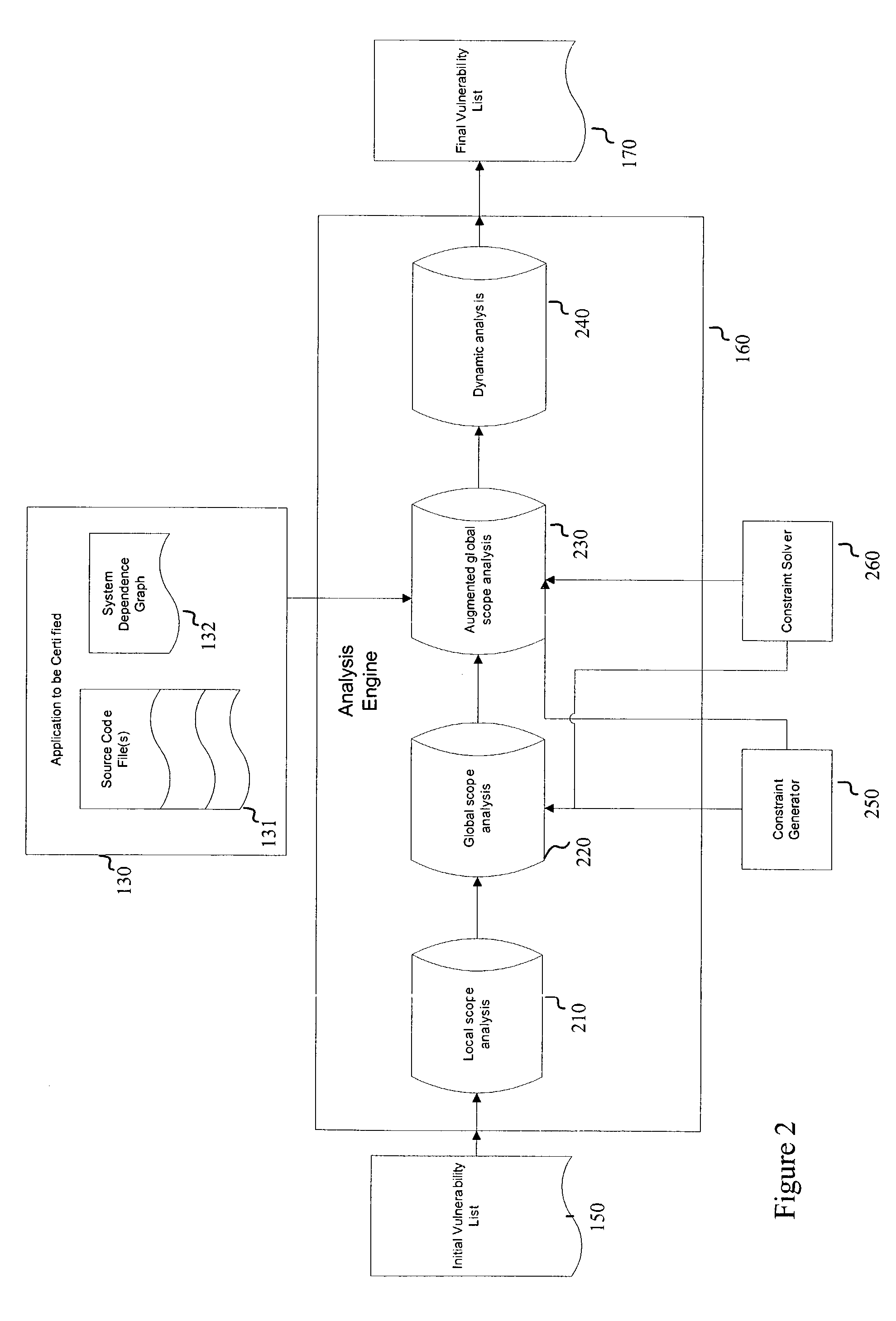
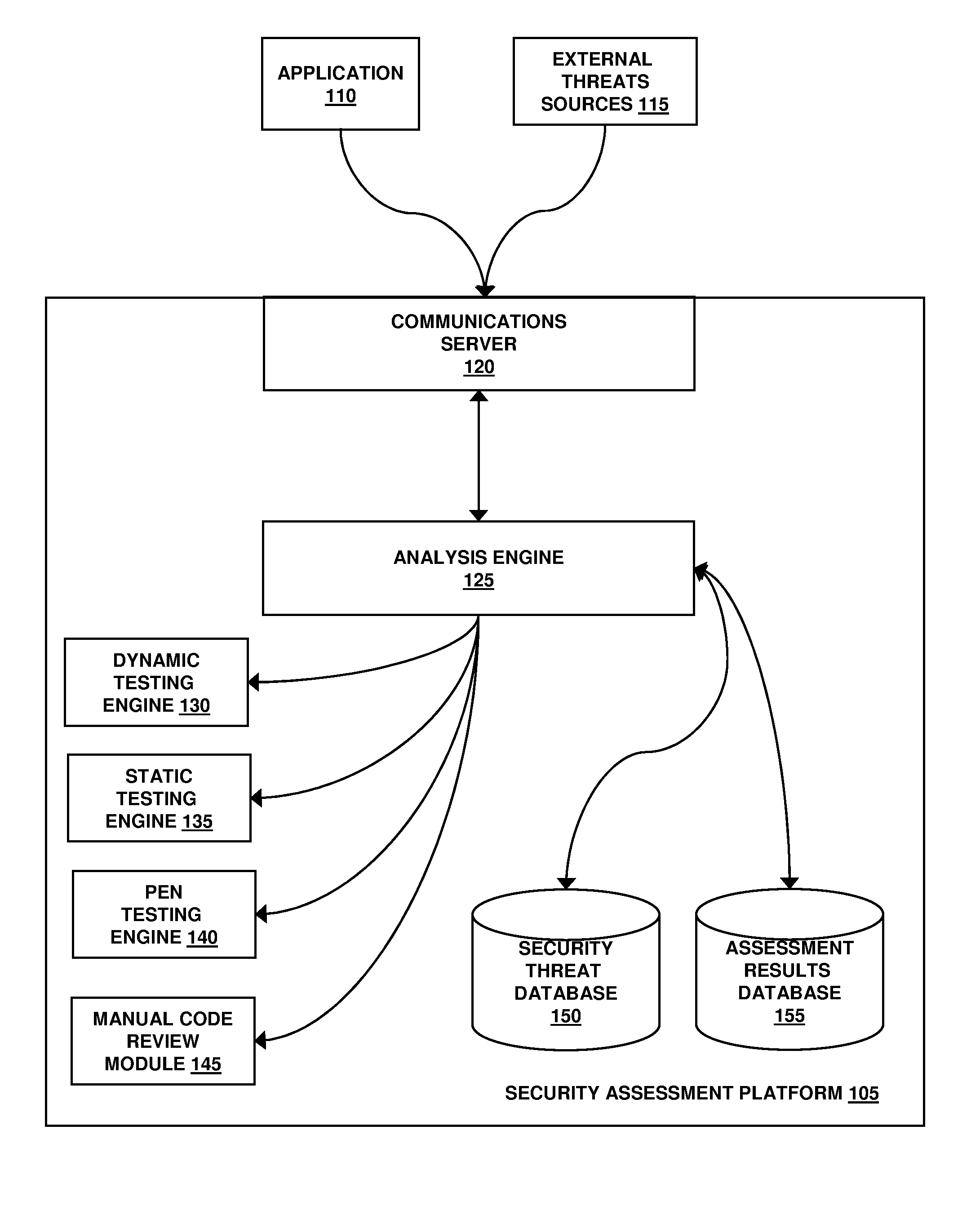
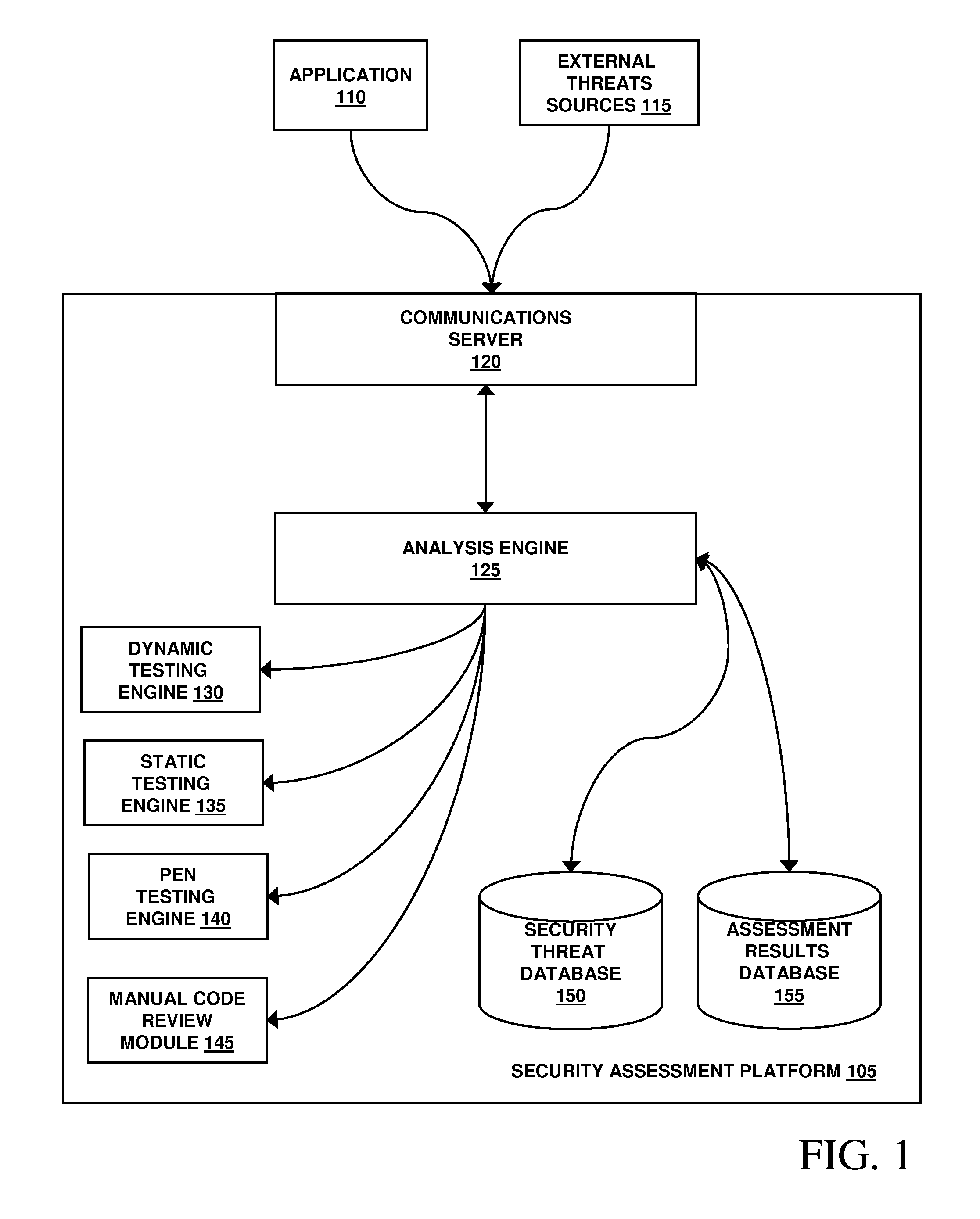
Systems and methods for detecting software security vulnerabilities
ActiveUS7392545B1Memory loss protectionUnauthorized memory use protectionApplication softwareVulnerability
Embodiments of the present invention relate to systems and methods for static analysis of a software application. According to an embodiment, a system includes a program scanner coupled to an analysis engine. The program scanner is configured to identify one or more vulnerability patterns in a software program and to output an initial potential vulnerability list. The analysis engine is configured to apply one or more rules to a potential vulnerability to determine whether the potential vulnerability is a vulnerability.
Owner:SYNOPSYS INC
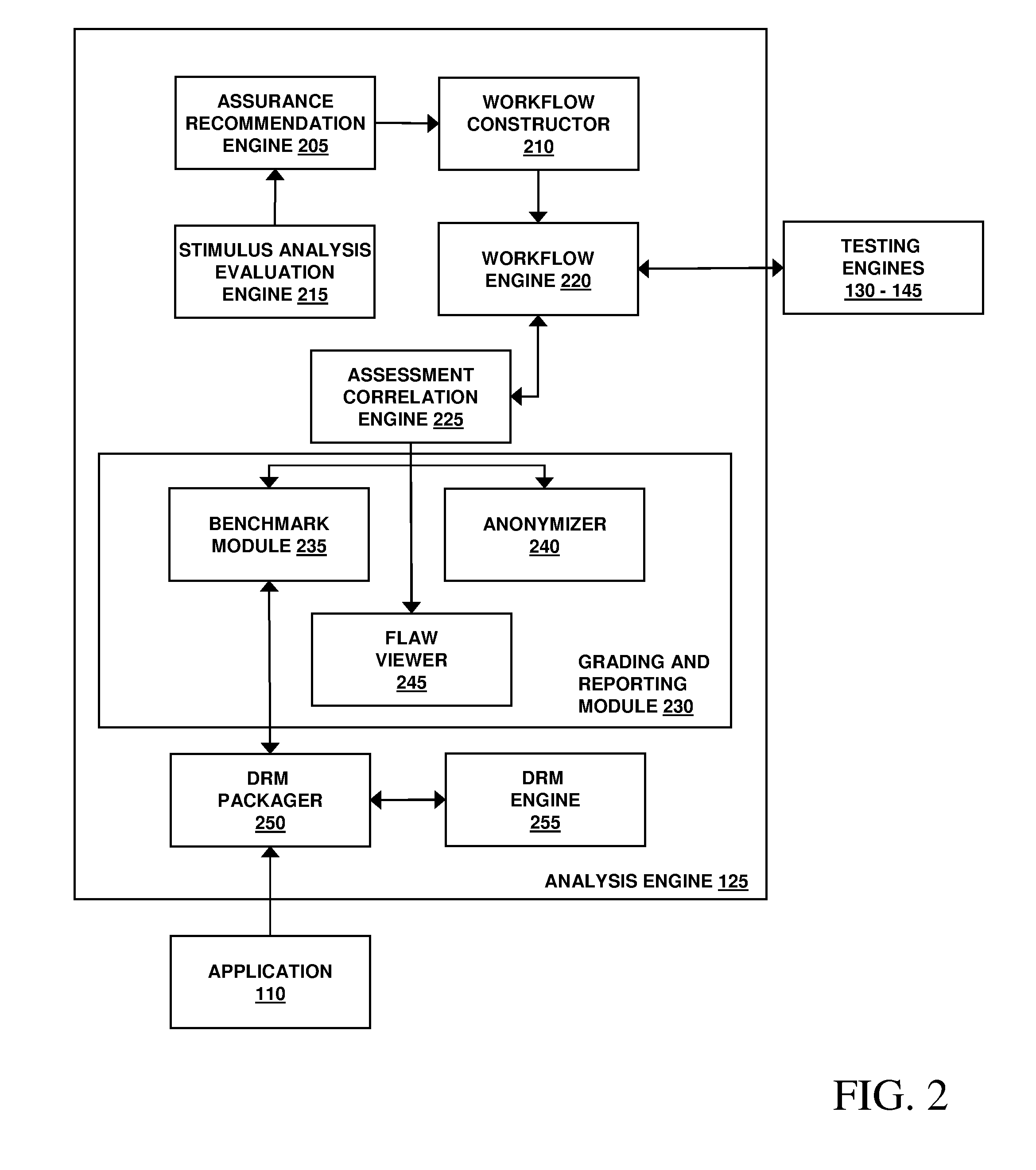
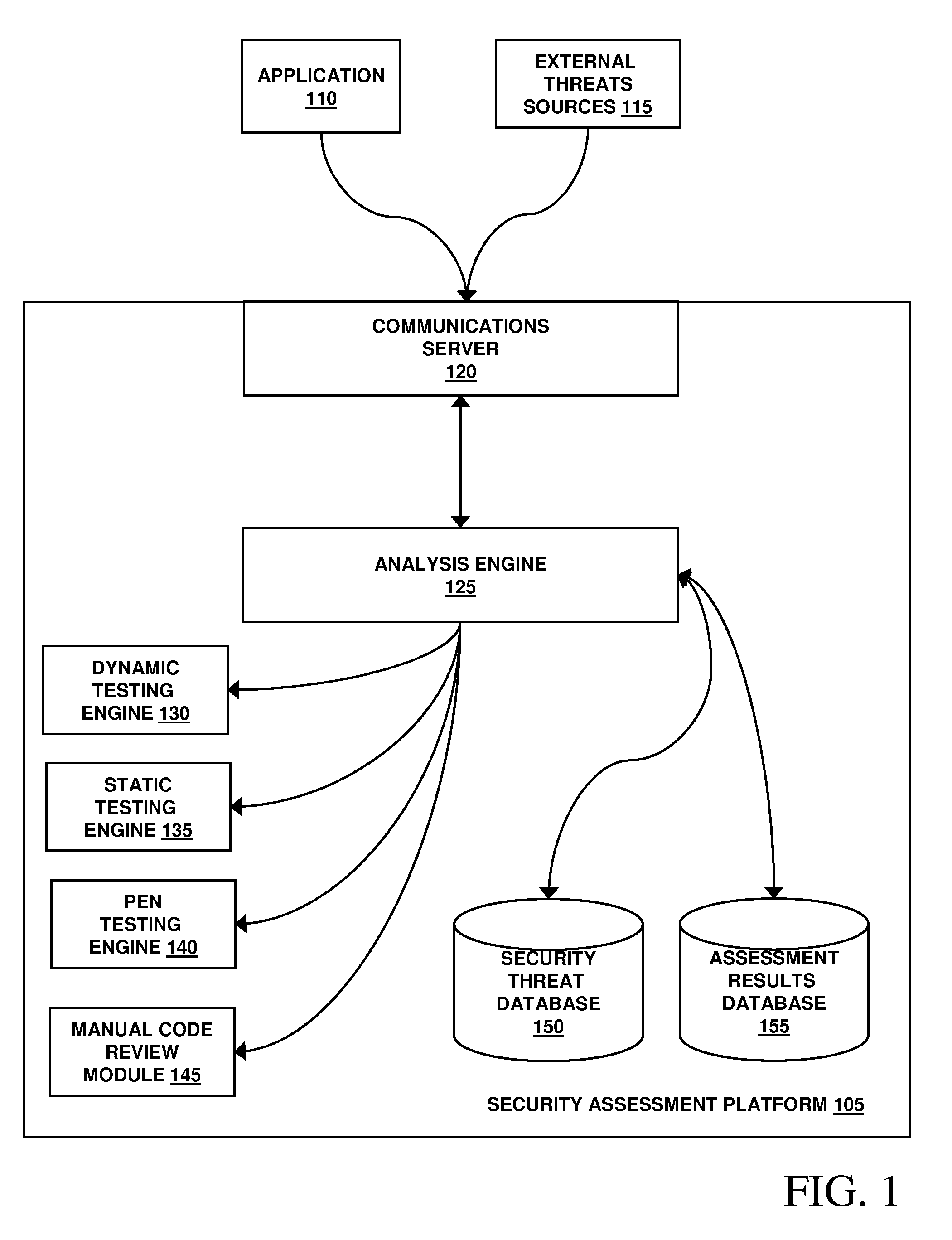
Assessment and analysis of software security flaws
InactiveUS20100281248A1Facilitates security assessment and vulnerability testingFacilitates benchmarkingMemory loss protectionDigital data processing detailsSecurity assessmentProgram planning
Security assessment and vulnerability testing of software applications is performed based at least in part on application metadata in order to determine an appropriate assurance level and associated test plan that includes multiple types of analysis. Steps from each test are combined into a “custom” or “application-specific” workflow, and the results of each test may then be correlated with other results to identify potential vulnerabilities and / or faults.
Owner:VERACODE
Assessment and analysis of software security flaws in virtual machines
ActiveUS8613080B2Facilitates security assessment and vulnerability testingFacilitates benchmarkingMemory loss protectionDigital data processing detailsSoftware engineeringSecurity analysis
Security analysis and vulnerability testing results are “packaged” or “bound to” the actual software it describes. By linking the results to the software itself, downstream users of the software can access information about the software, make informed decisions about implementation of the software, and analyze the security risk across an entire system by accessing all (or most) of the reports associated with the executables running on the system and summarizing the risks identified in the reports.
Owner:VERACODE
Detection device and method for security vulnerability of software
InactiveCN102541729ASatisfy attentionImprove use valueSoftware testing/debuggingSystems managementGoal system
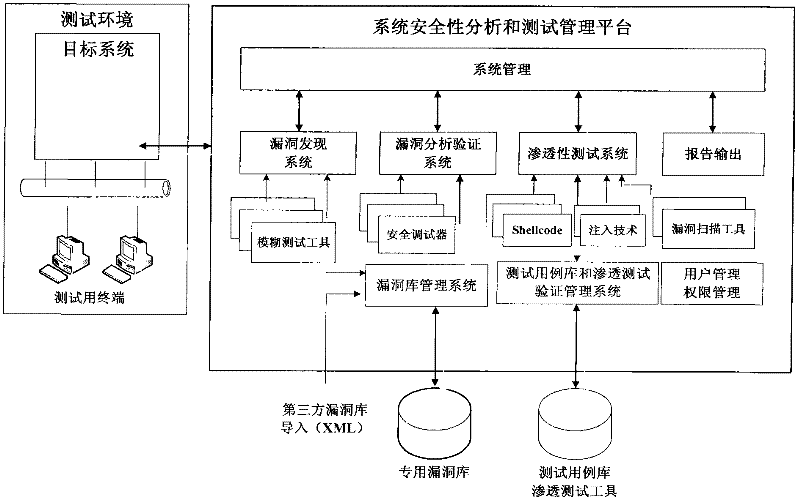
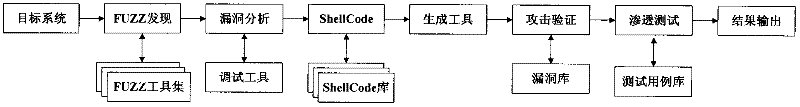
The invention relates to the field of computers, in particular to a detection device and method for a security vulnerability of a dedicated information system. According to the detection device and method disclosed by the invention, a tester can not only access a target system to a testing network but also access the detection device to a production system by connecting a test terminal with the target system, wherein the target system is located in the production system. As the core of the detection device, a system security analysis and test management platform comprises a vulnerability discovering system, a vulnerability authenticating and analyzing system, a permeability testing system, a vulnerability library, a test case library, a report outputting system, a user and permission management system, a system management platform and the like. When the detection device and method for the security vulnerability of the software, provided by the invention, are adopted, the vulnerability can be found before the application of the software, and corresponding strategies can be provided, so that the detection device and method meet the requirement on the emphasis on information security in the current society in a better manner; and moreover, the detection device and method have a higher application value.
Owner:AVIATION IND INFORMATION CENT
Systems and methods for defending against cyber attacks at the software level
InactiveUS20150121532A1Minimizing false negative rateEliminating false positiveMemory loss protectionError detection/correctionCyber-attackHigh level analysis
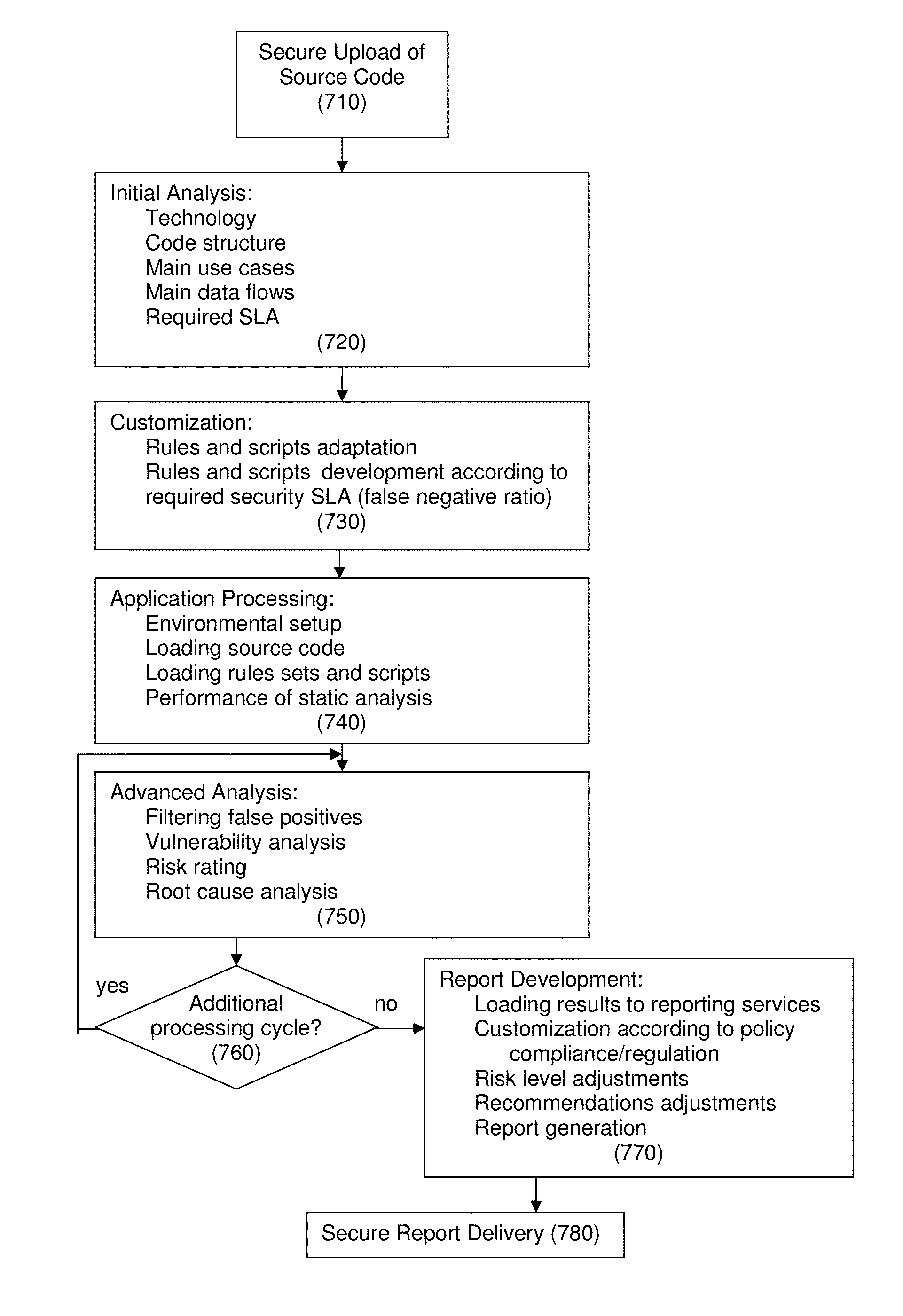
A method for a customized, scalable and cost-efficient solution to enable source code level solutions to provide zero percentage false positives as well as a controlled false negative ratio to detect software security vulnerabilities accurately and in time. The method includes secure uploading of the source code, initial analysis and customizing according to accuracy and depth defined to enable control of the false negative ratio. The method also includes application processing, advanced analyzing, performing report development and delivering a secure report. The initial analysis provides for a human analyst “built-in” as part of the process that performs the analysis on initial results and the filtering of the results to contain ONLY relevant security vulnerabilities
Owner:COMSEC CONSULTING
Method and device for detecting security flaws of software source codes
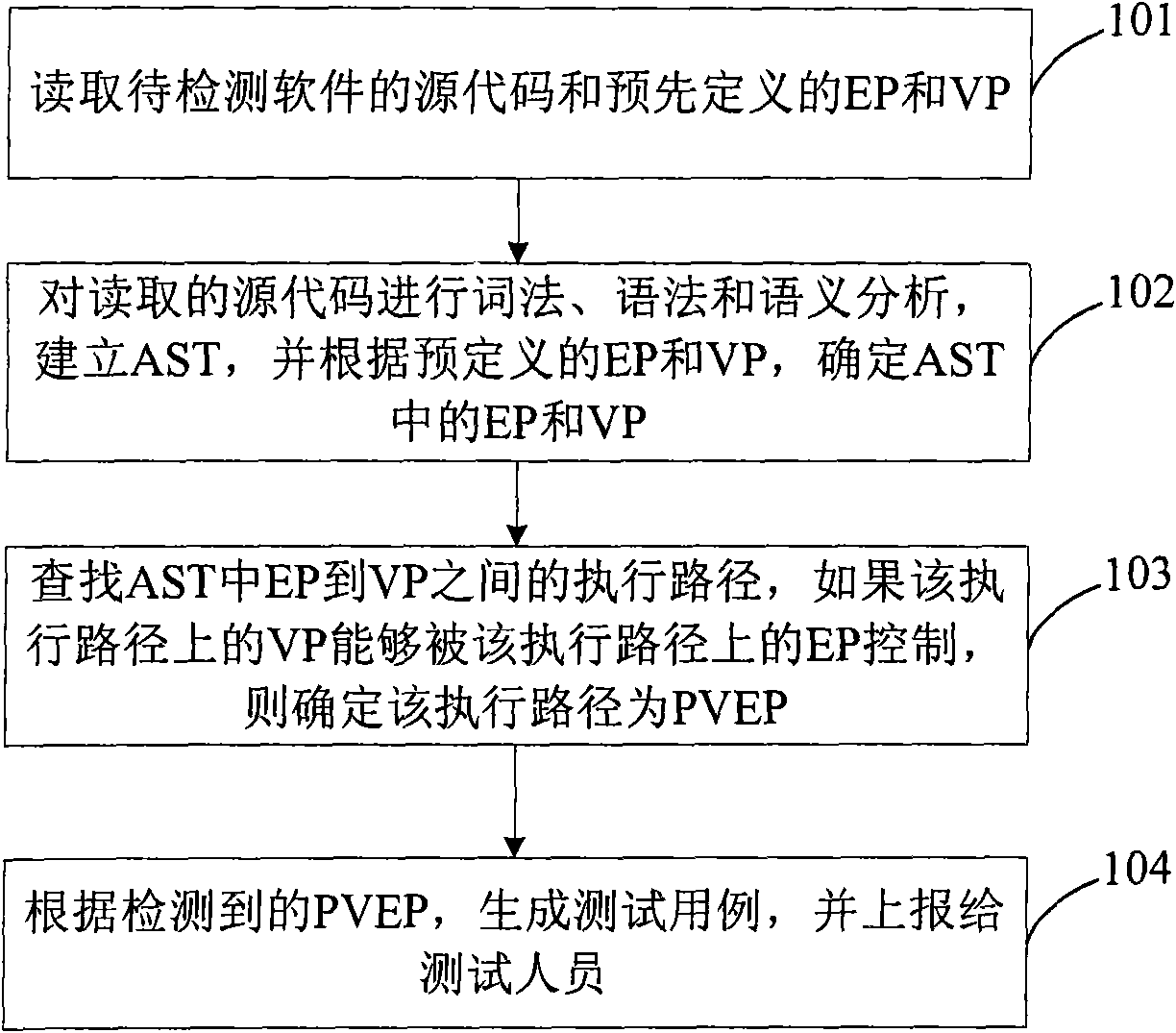
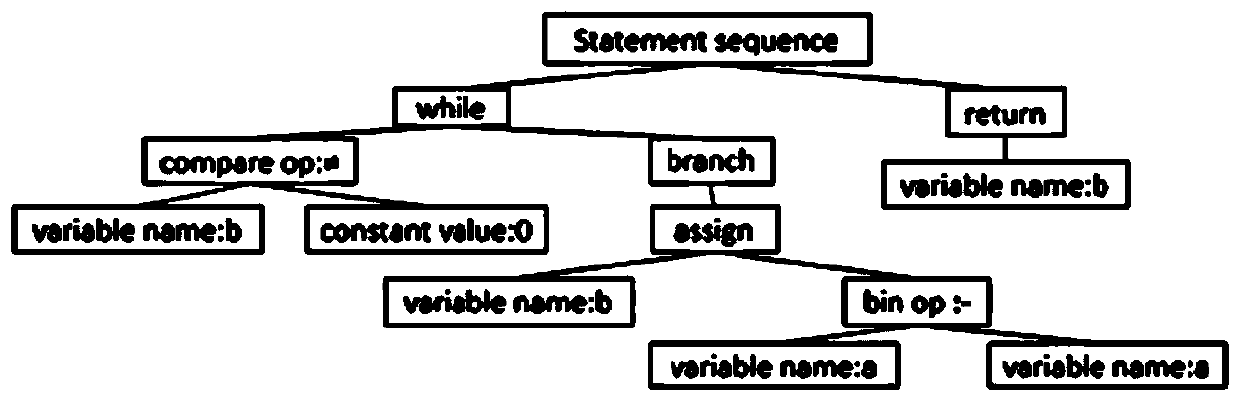
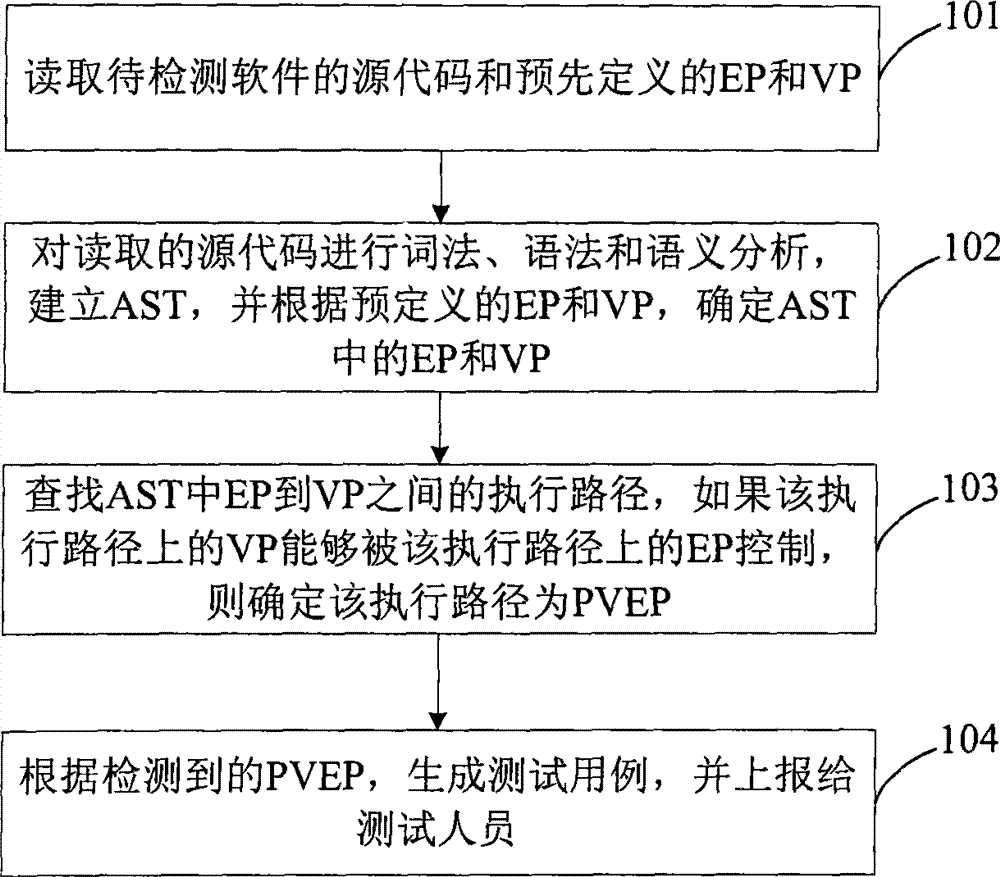
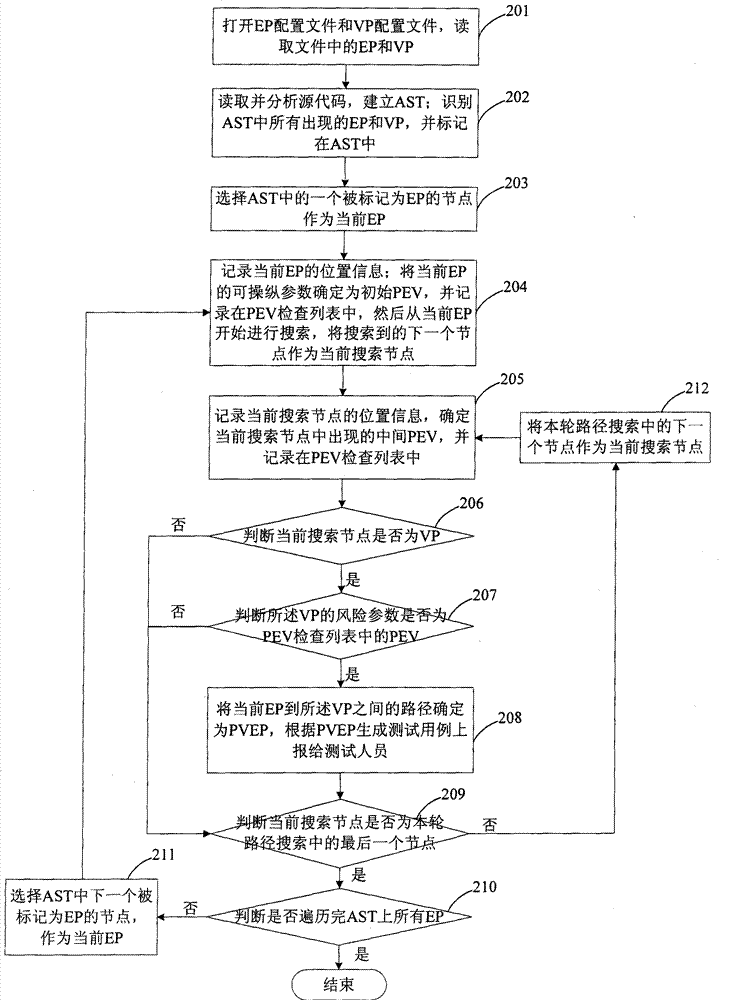
ActiveCN101661543AEasy to analyzeEfficient searchPlatform integrity maintainanceSource codeAbstract syntax tree
The invention discloses a method for detecting security flaws of software source codes. The method comprises the following steps: establishing an abstract syntax tree AST corresponding to source codesof software to be detected; determining controllable points and risk points of each node of the established AST according to predefined controllable points and risk points; and searching an executionpath between the controllable points and the risk points in the AST, and if the risk points on the execution path can be controlled by the controllable points on the execution path, the execution path is determined as a potential risk execution path probably causing the security flaws. The invention also discloses a device for detecting the security flaws of the software. The method and the device can effectively detect the security flaws existing in the source codes of the software.
Owner:SIEMENS CHINA
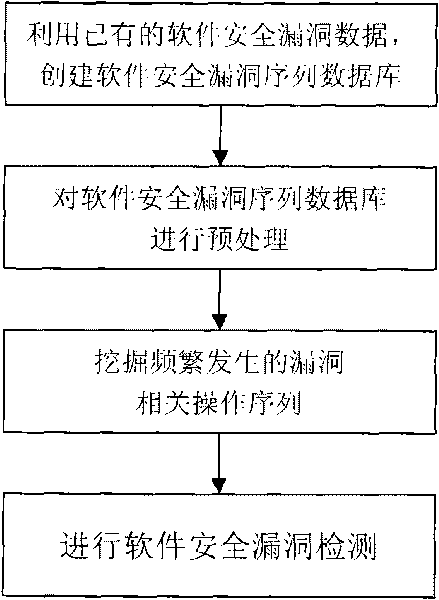
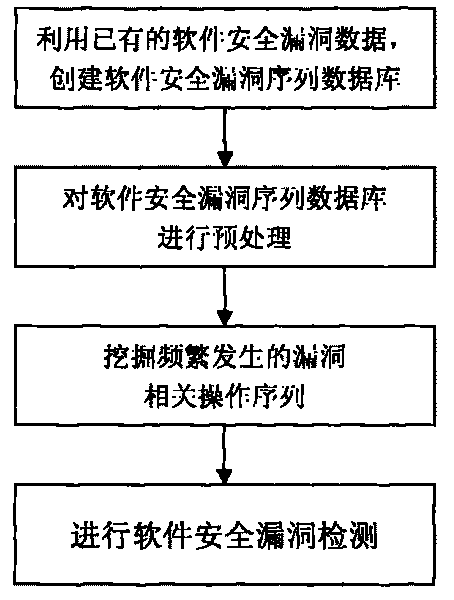
Software security flaw detection method based on sequential pattern mining
InactiveCN101710378AImprove detection efficiencyReduce the false negative rate of vulnerability detectionPlatform integrity maintainanceSpecial data processing applicationsSequence databaseSoftware system
The invention provides a software security flaw detection method based on sequential pattern mining. Firstly, a great quantity of relevant operation sequence data of a detected software security flaw is used for building a relevant operation sequence database of the security flaw; then, a closed sequential pattern mining arithmetic in the data mining is used to mine frequently appearing relevant operation sequence of the flaw; the mined frequently appearing relevant operation sequence of the flaw is used for detecting the security flaw of the current software system so as to lower flaw detection missing report rate as well as improve security flaw detection efficiency. Along with the accumulation of flaw data, the advantage of high security flaw detection efficiency of the invention is more outstanding.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +2
Assessment and analysis of software security flaws
ActiveUS9069967B2Facilitates security assessment and vulnerability testingFacilitates benchmarkingSoftware testing/debuggingPlatform integrity maintainanceSoftware engineeringSecurity analysis
Security analysis and vulnerability testing results are “packaged” or “bound to” the actual software it describes. By linking the results to the software itself, downstream users of the software can access information about the software, make informed decisions about implementation of the software, and analyze the security risk across an entire system by accessing all (or most) of the reports associated with the executables running on the system and summarizing the risks identified in the reports.
Owner:VERACODE
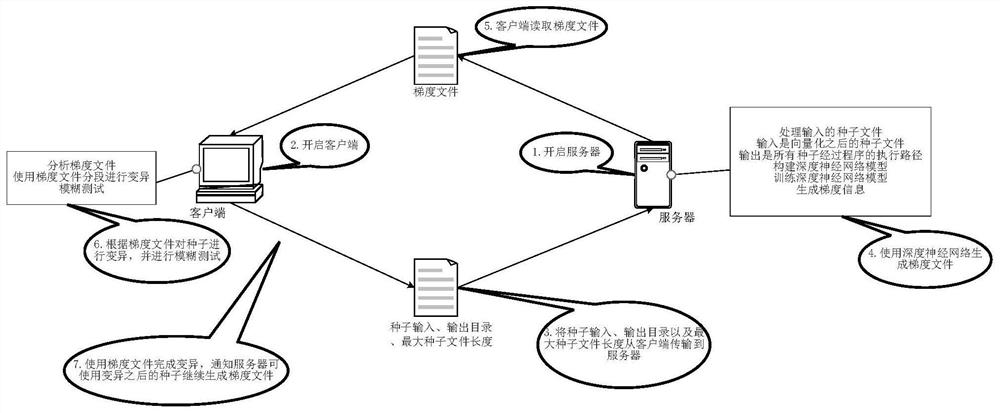
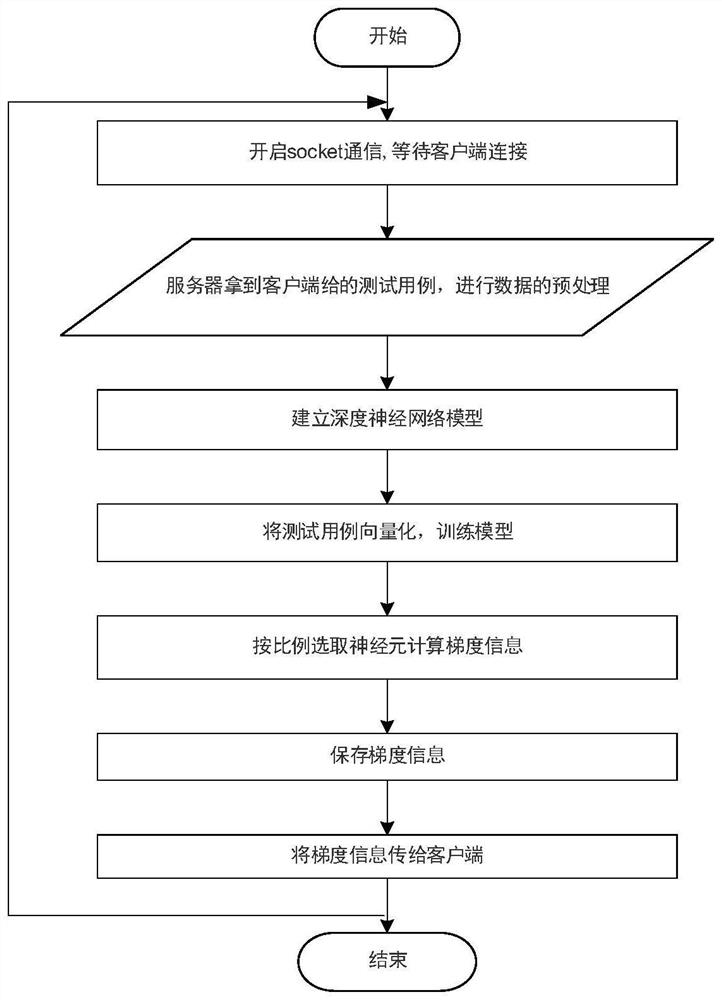
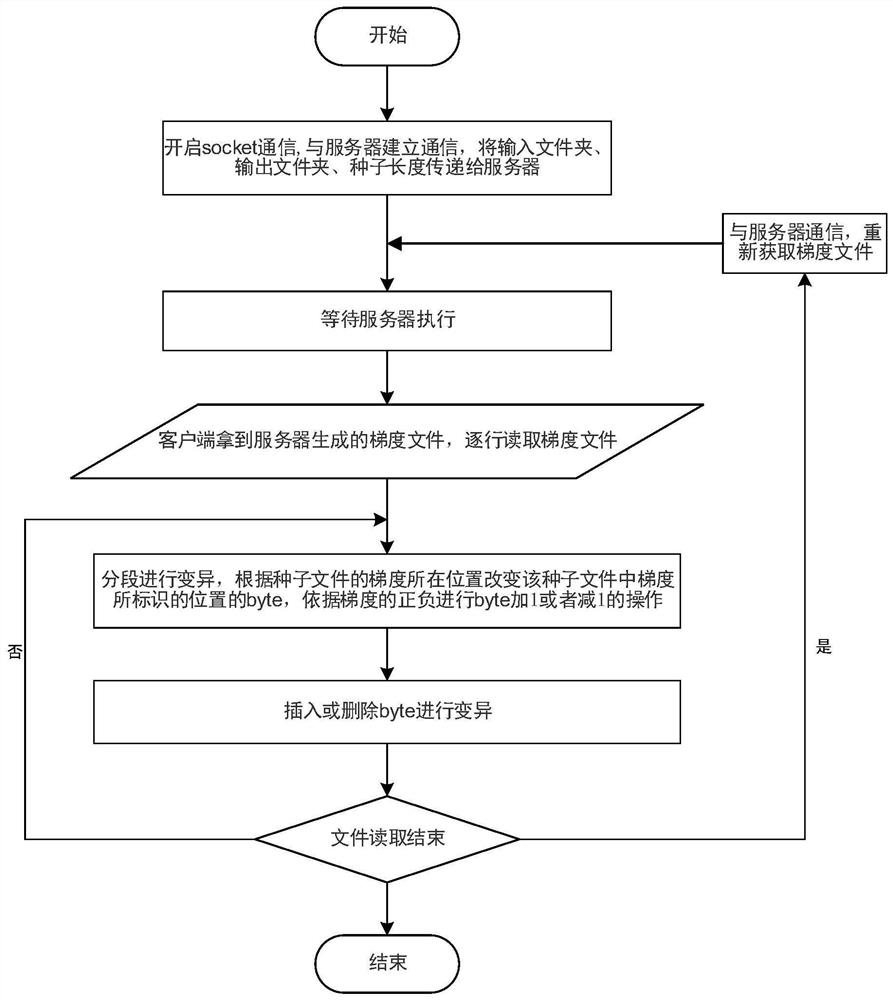
Software security vulnerability detection method and system for deep learning gradient guidance variation
ActiveCN112069061AProgram smoothingImprove smoothnessSoftware testing/debuggingPlatform integrity maintainanceAlgorithmEngineering
The invention discloses a software security vulnerability detection method and system for deep learning gradient guidance variation, and the method comprises the steps: obtaining test cases, carryingout the preprocessing, and obtaining the size of a maximum test case and an execution path of each test case in a tested program; establishing a deep neural network model, wherein the input dimensionof the input layer is the size of the maximum test case, and the number of output neurons of the output layer is the total number of execution paths; vectorizing the test cases, and training a deep neural network model by using the test cases; performing gradient calculation based on the trained deep neural network model to generate gradient information; and performing variation and fuzzy test onthe test case based on the gradient information to generate a test result. According to the method, a gradient guidance variation technology is adopted, gradient information is generated in combination with deep learning assistance, and the bottleneck problem in software security vulnerability mining can be effectively solved.
Owner:CHECC DATA CO LTD +1
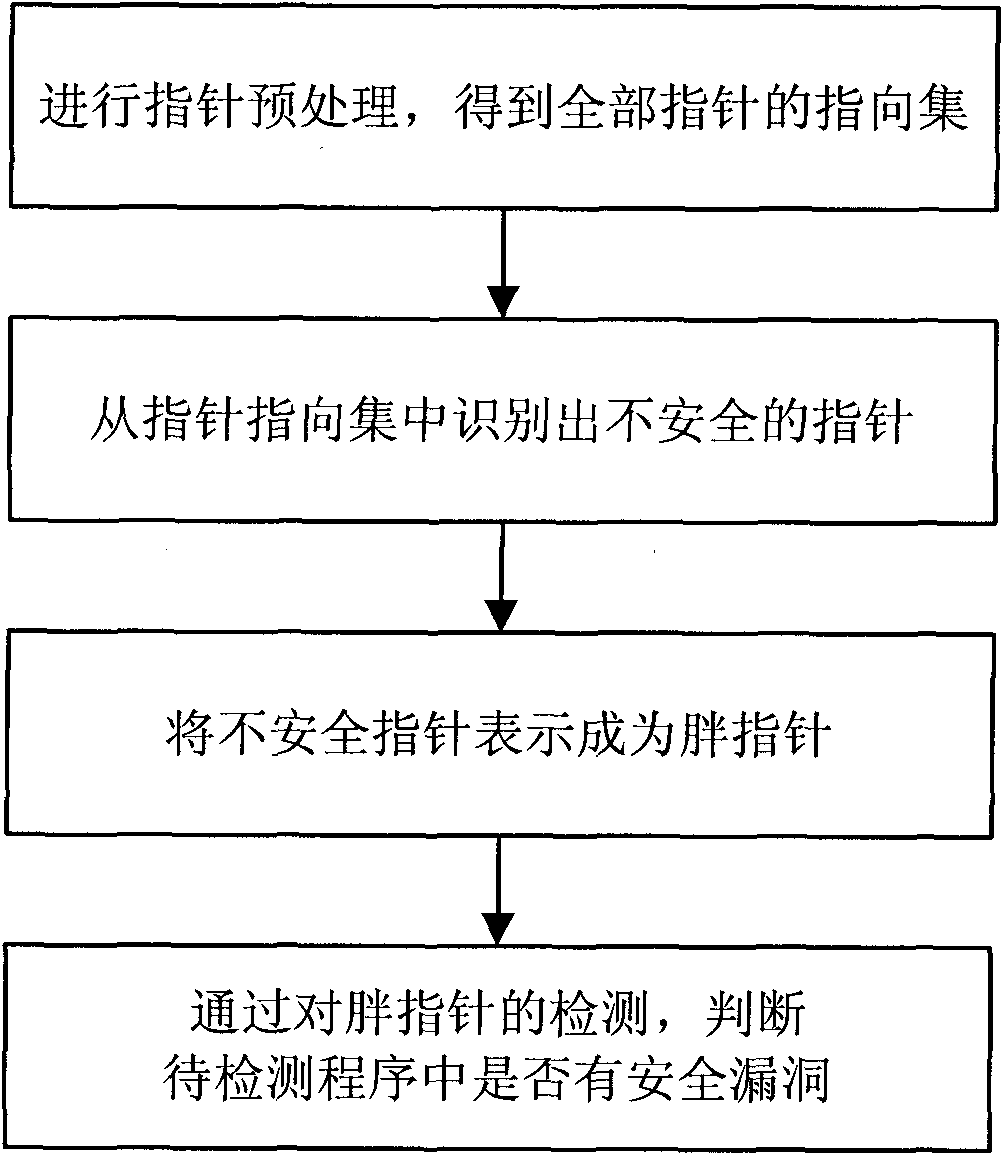
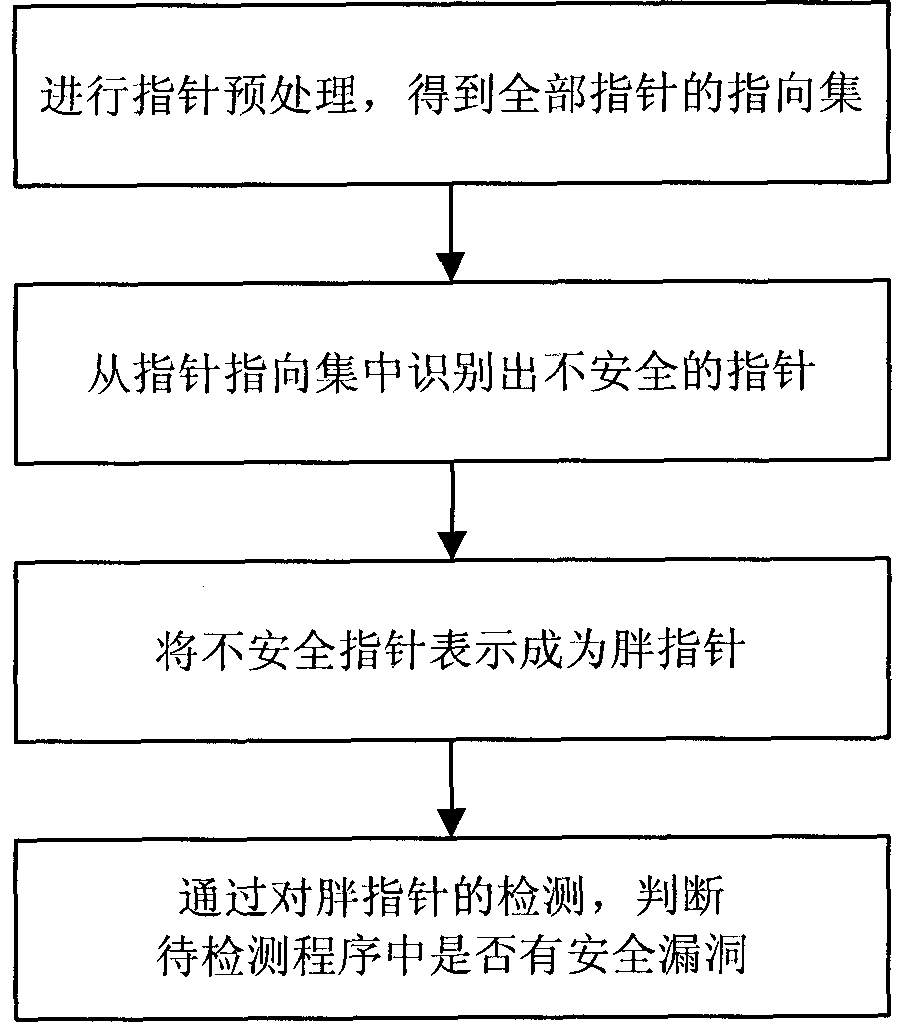
Pointer analysis-combined software security hole dynamic detection method
InactiveCN101833631AReduce resource consumptionProgram/content distribution protectionSoftware engineeringBuffer overflow
The invention relates to a software security hole dynamic detection method, in particular to a pointer analysis-combined software security hole dynamic detection method, and belongs to the technical field of information security. The software security hole dynamic detection method comprises the following steps of: identifying insecure pointers in a program to be detected; expressing the insecure pointers as fat pointers; and continuously checking the pointer state information contained in the fat pointers and finding the hole existing in the program to be detected by operating the program to be detected. The software security hole dynamic detection method can detect various holes simultaneously, such as a buffer area overflow hole, a suspended pointer hole, and the like, and can reduce the consumption of the system resources simultaneously.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
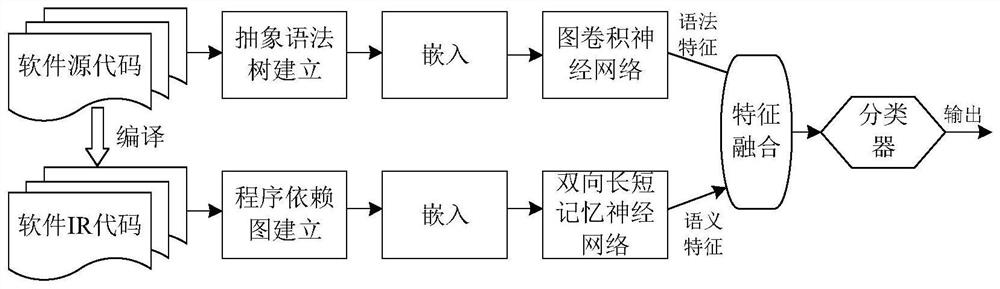
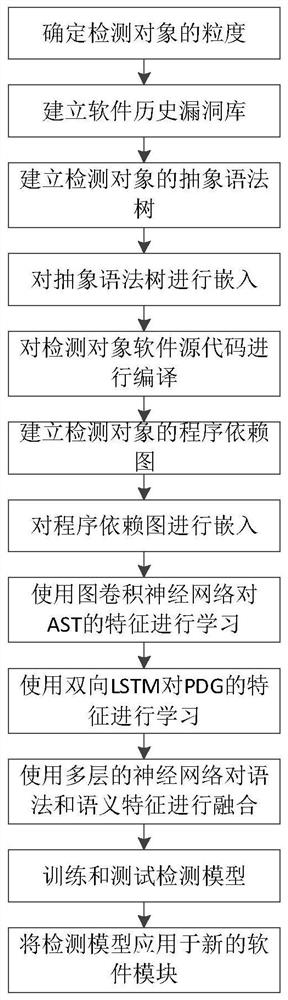
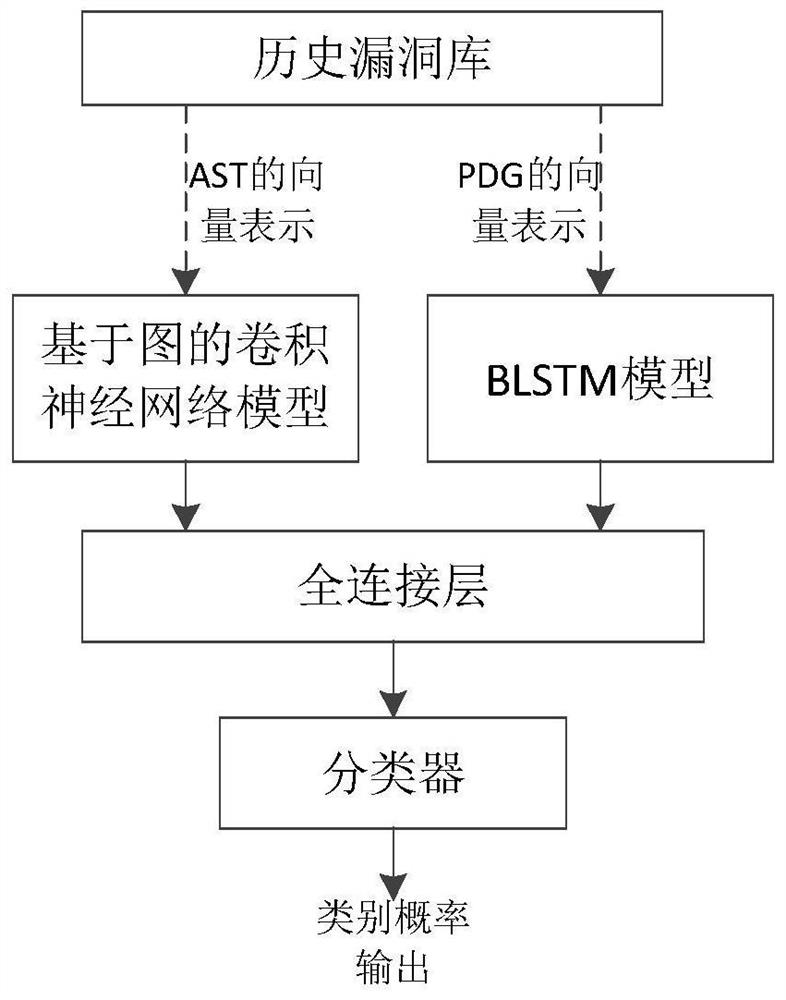
Software security vulnerability detection method based on grammatical features and semantic features
ActiveCN112541180AHigh precisionImprove accuracySoftware testing/debuggingPlatform integrity maintainanceTheoretical computer sciencePerformance index
The invention discloses a software security vulnerability detection method based on grammatical features and semantic features. The method comprises the following steps: 1, determining the granularityof a detection object; 2, establishing a software historical vulnerability library; 3, establishing an abstract syntax tree of the detection object; 4, embedding the abstract syntax tree; 5, compiling the source code of the detection object software; 6, establishing a program dependence graph of the detection object; 7, embedding the program dependence graph; 8, learning the features of the AST by using a graph convolutional neural network; and 9, learning the features of the PDG by using a bidirectional LSTM. The method has the advantages that the performance indexes of precision, accuracy and recall rate of the detection model are improved; and an AST tree structure is directly learned by adopting a graph neural network, so that any information is not lost, and the detection performanceof the model can be greatly improved by adopting a feature direct extraction mode based on the graph neural network.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +1
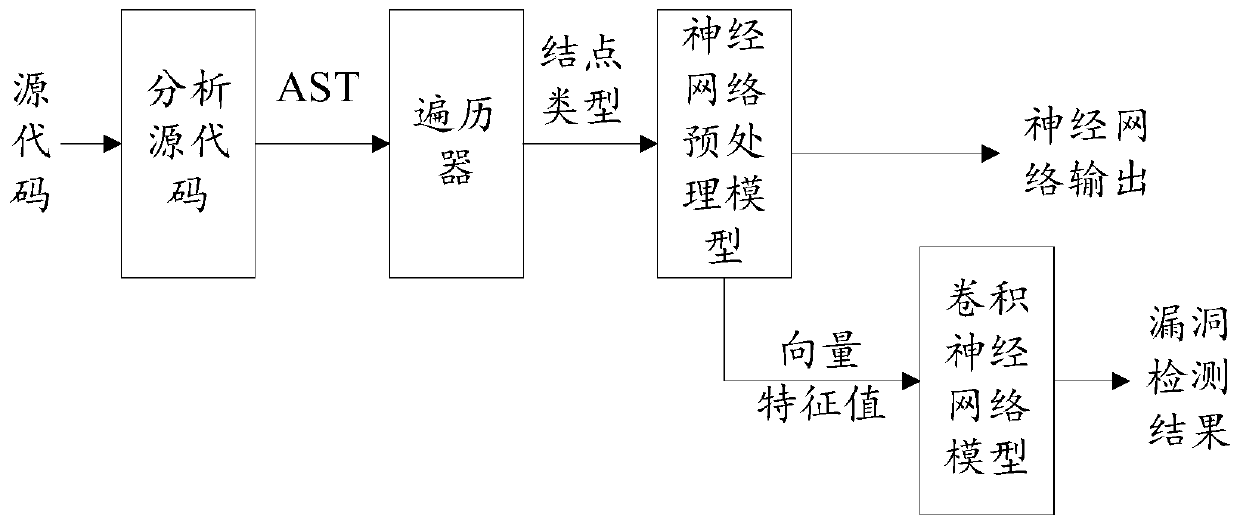
Software security vulnerability detection method based on tree structure convolutional neural network
ActiveCN110232280AExpress vector eigenvaluesThe results of the analysis are comprehensiveCharacter and pattern recognitionPlatform integrity maintainancePrediction probabilityAbstract syntax tree
The invention discloses a software vulnerability detection method based on a tree structure convolutional neural network, and the method comprises the steps: analyzing a source code to obtain an abstract syntax tree AST structure, and extracting the node type of each node in the AST structure; constructing a neural network pre-processing model containing an embeding layer, inputting the neural network pre-processing model into an extracted node type, and outputting a prediction probability of the node type; performing neural network training by using the node type; after training is completed,enabling the vector characteristic values output by the embeding layer to serve as input of a convolutional neural network model, taking whether vulnerabilities exist in source codes or not as labels, and training the convolutional neural network model to serve as a code classifier; and for the source code to be detected, extracting the node type in the AST structure of the source code, retraining the neural network preprocessing model, and inputting the vector characteristic value output by the embeding layer into the convolutional neural network model to obtain a vulnerability detection result. According to the method, the feature information in the code can be better extracted, so that a comprehensive analysis result can be given.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
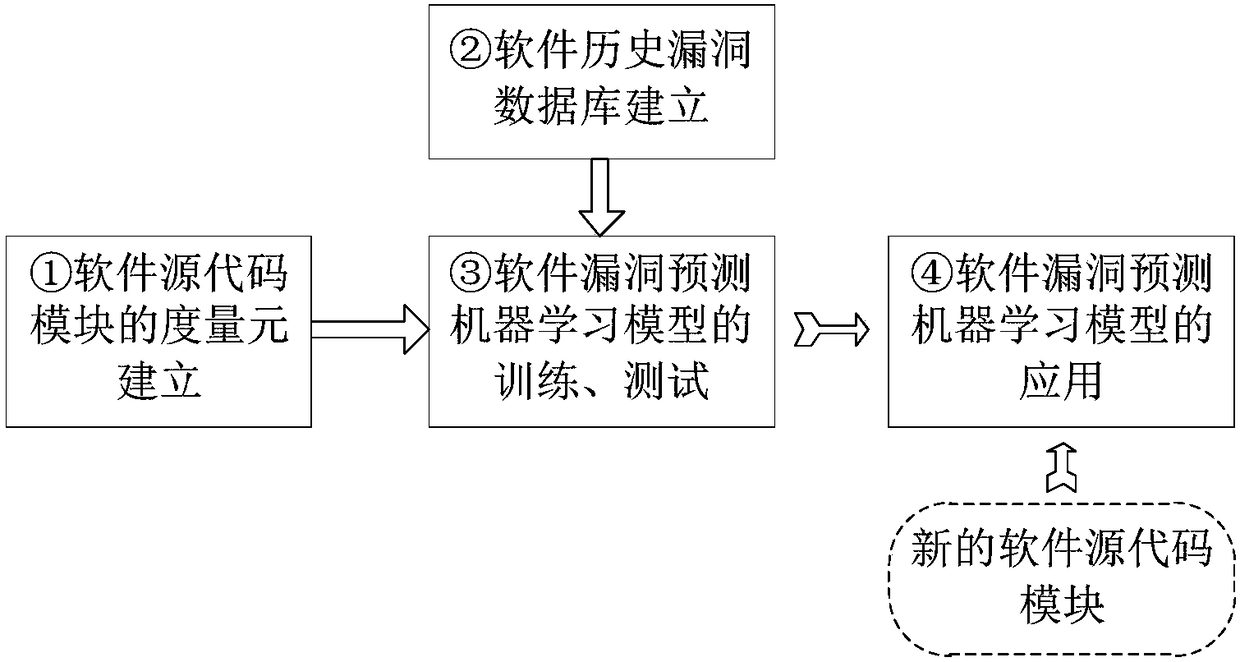
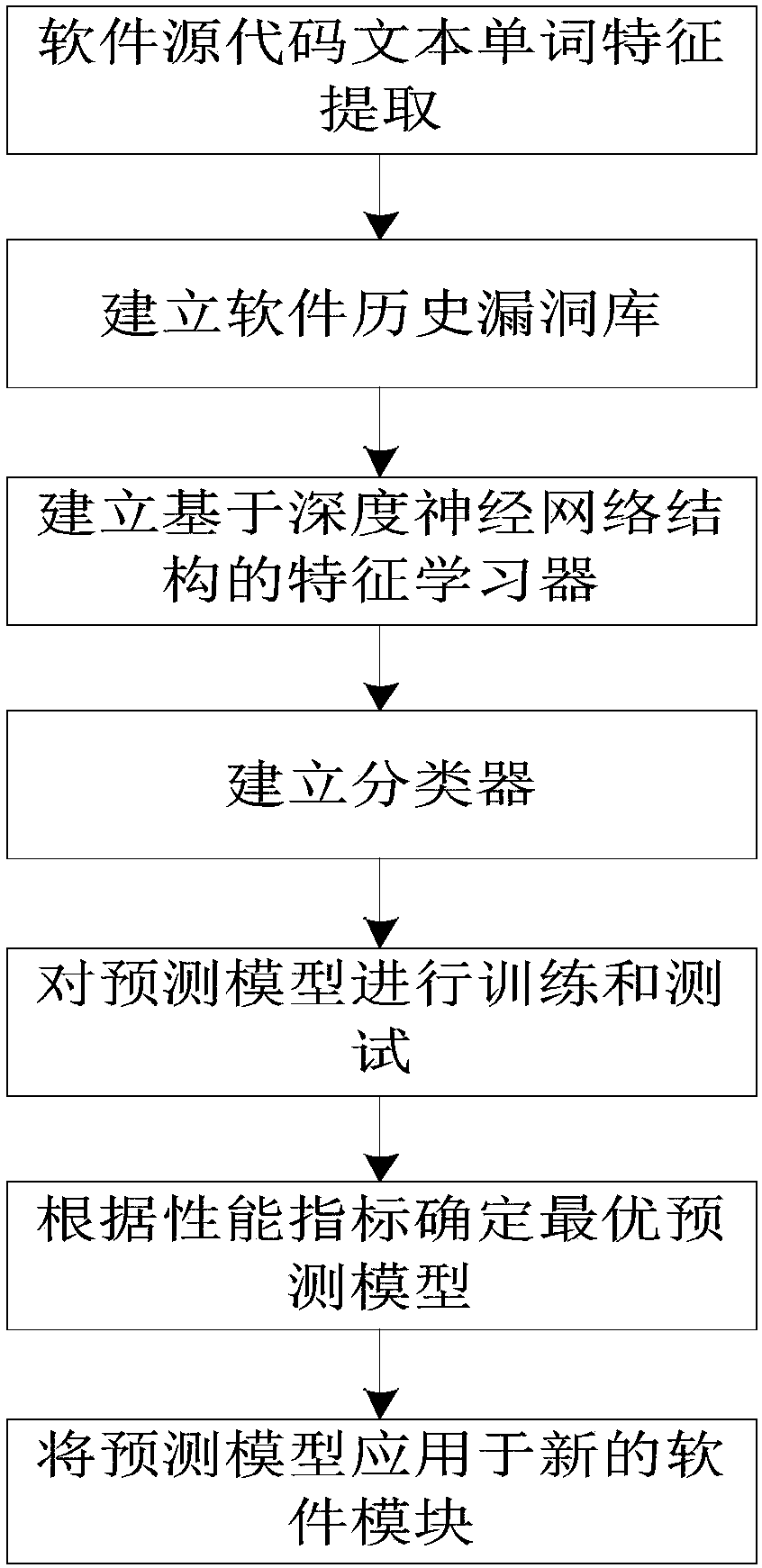
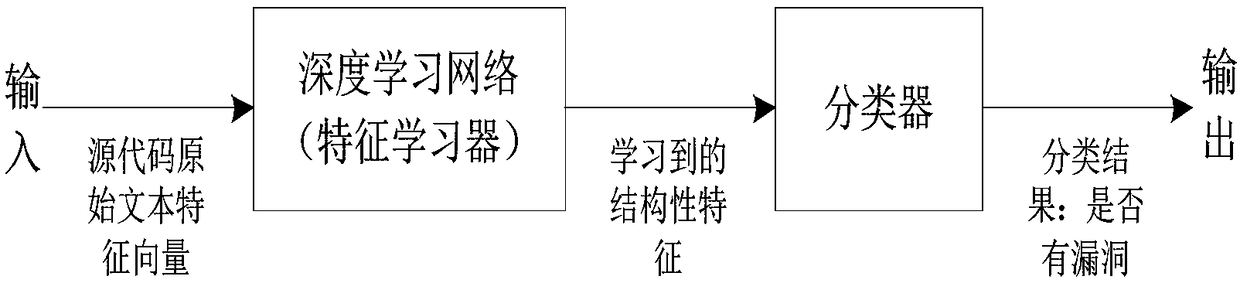
Text deep learning-based software security vulnerability prediction method
PendingCN108549817AHigh precisionImprove performance indicatorsNatural language data processingPlatform integrity maintainanceLearning basedTheoretical computer science
The invention discloses a text deep learning-based software security vulnerability prediction method, which learns features and knowledge from a historical software source code text by adopting a deepneural network model and a shallow machine learning algorithm, and can be used for predicting security vulnerabilities in new software source codes. According to the method, structural features in the features of the software source code text are learnt by adopting the deep neural network model; by taking the learnt features as inputs of a classifier, the classifier is subjected to training adjustment; an optimal vulnerability prediction model is obtained; and the method is used for vulnerability prediction of new software modules of software.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +1
Software security loophole prediction method based on assembly dependence diagram
ActiveCN107798245AClearly describe the connection strengthDescribe the connection strengthPlatform integrity maintainanceSoftware engineeringVulnerability
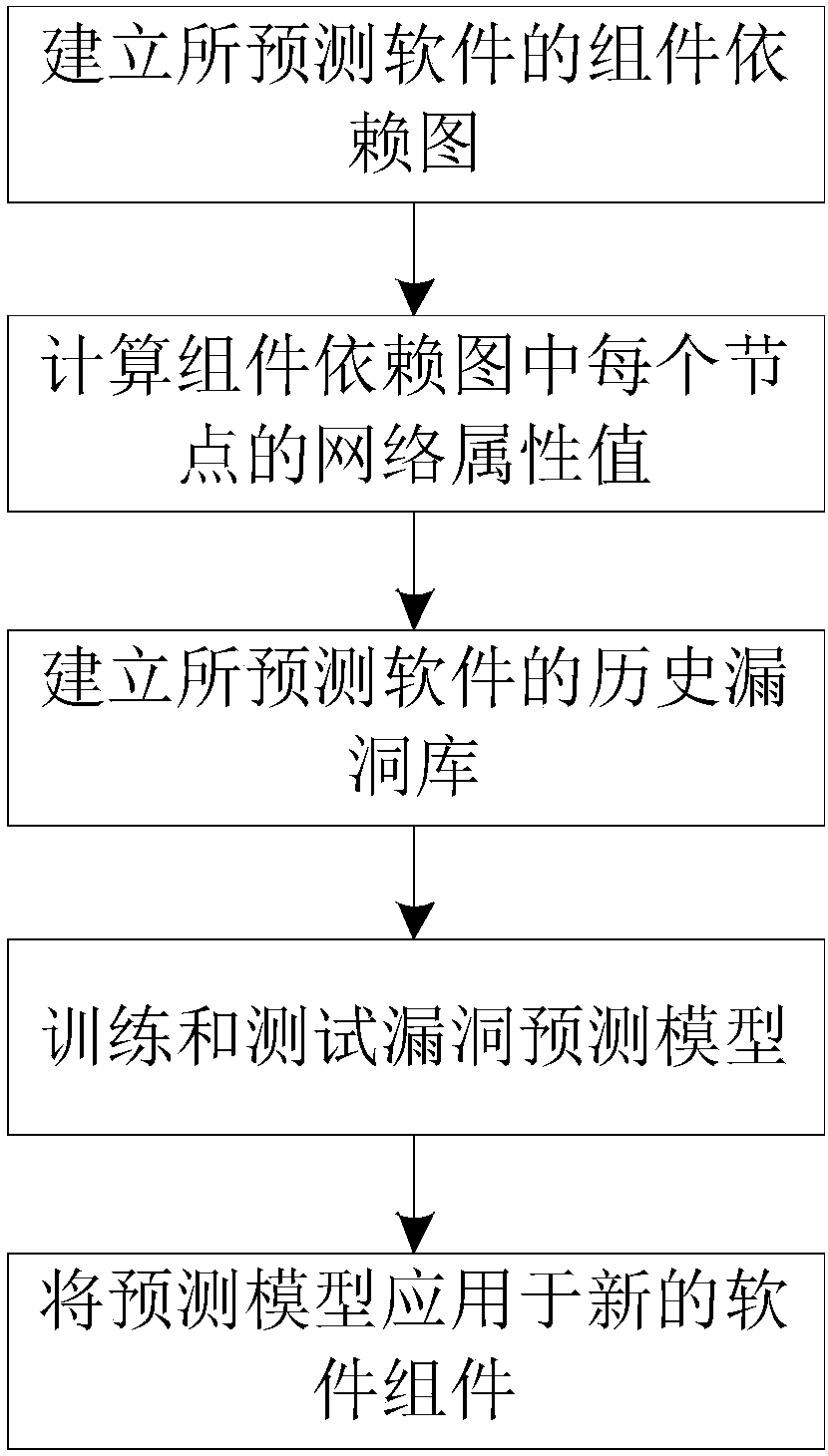
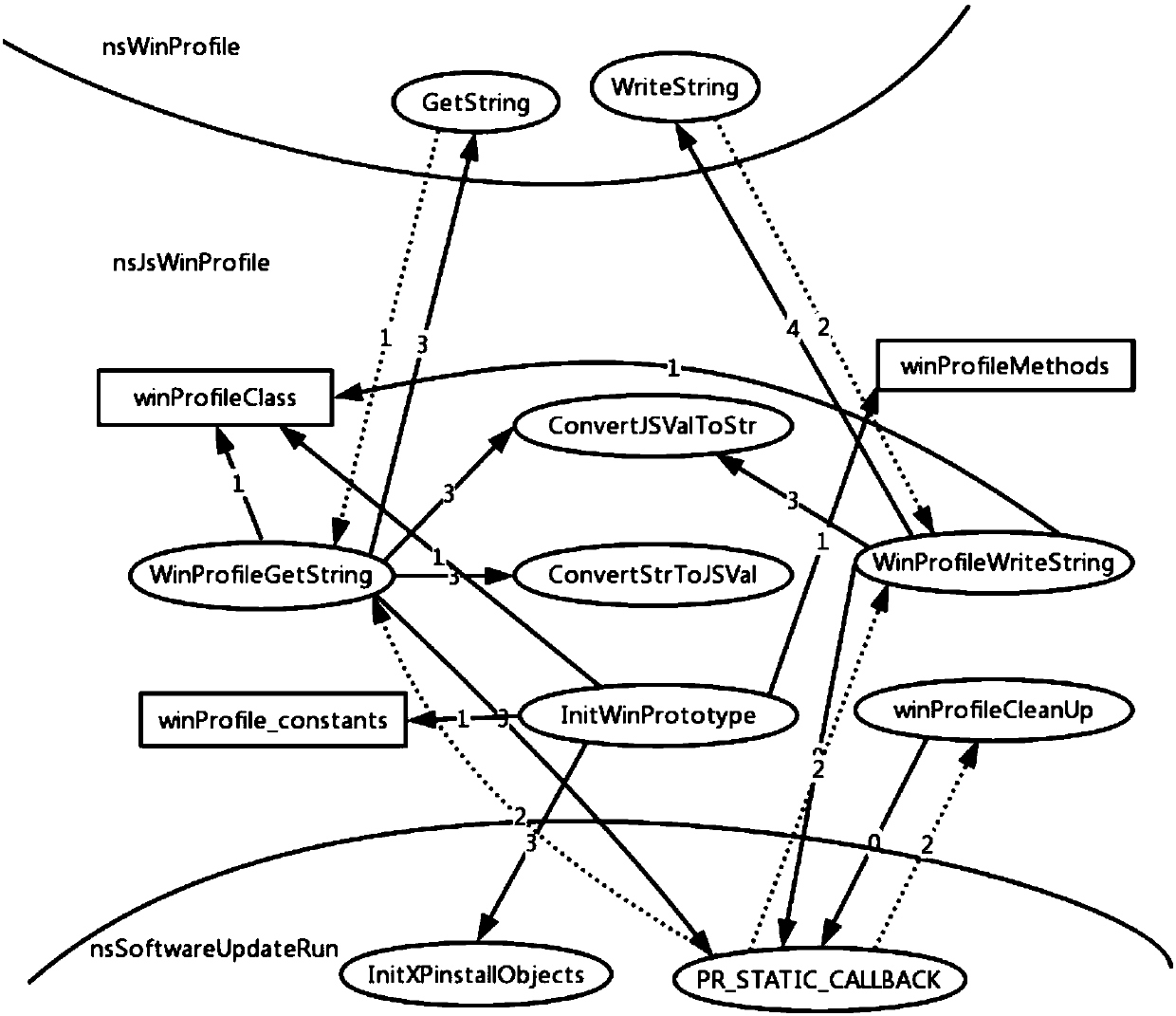
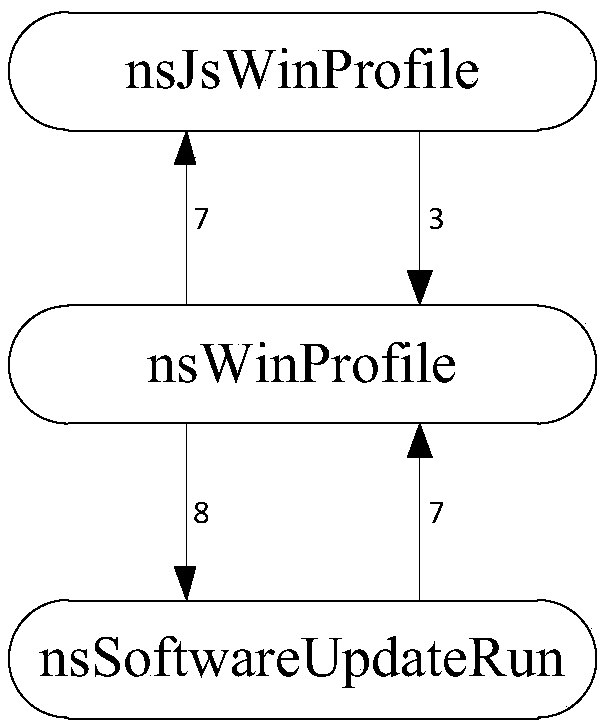
The invention provides a software security loophole prediction method based on an assembly dependence diagram and provides a software code measuring index from different angles to establish a loopholeprediction model. The software security loophole prediction method comprises the following steps that 1, the assembly dependence diagram of prediction software is established; 2, network attribute values of nodes in the assembly dependence diagram in the step 1 are calculated; 3, all software loopholes of the prediction software are searched from a disclosed software loophole library, and a historical loophole library of the software is established; 4, network attribute values, calculated in the step 2, of the nodes serve as inputs of a machine learning algorithm, the number of loopholes in the step 3 serves as an output of the machine learning algorithm, the machine learning algorithm is trained and tested, and a prediction model having optimal performance is determined according to performance evaluation indexes of the machine learning algorithm; 5, the prediction model having optimal performance obtained in the step 4 is applied to loophole prediction of new software assemblies ofa software project.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
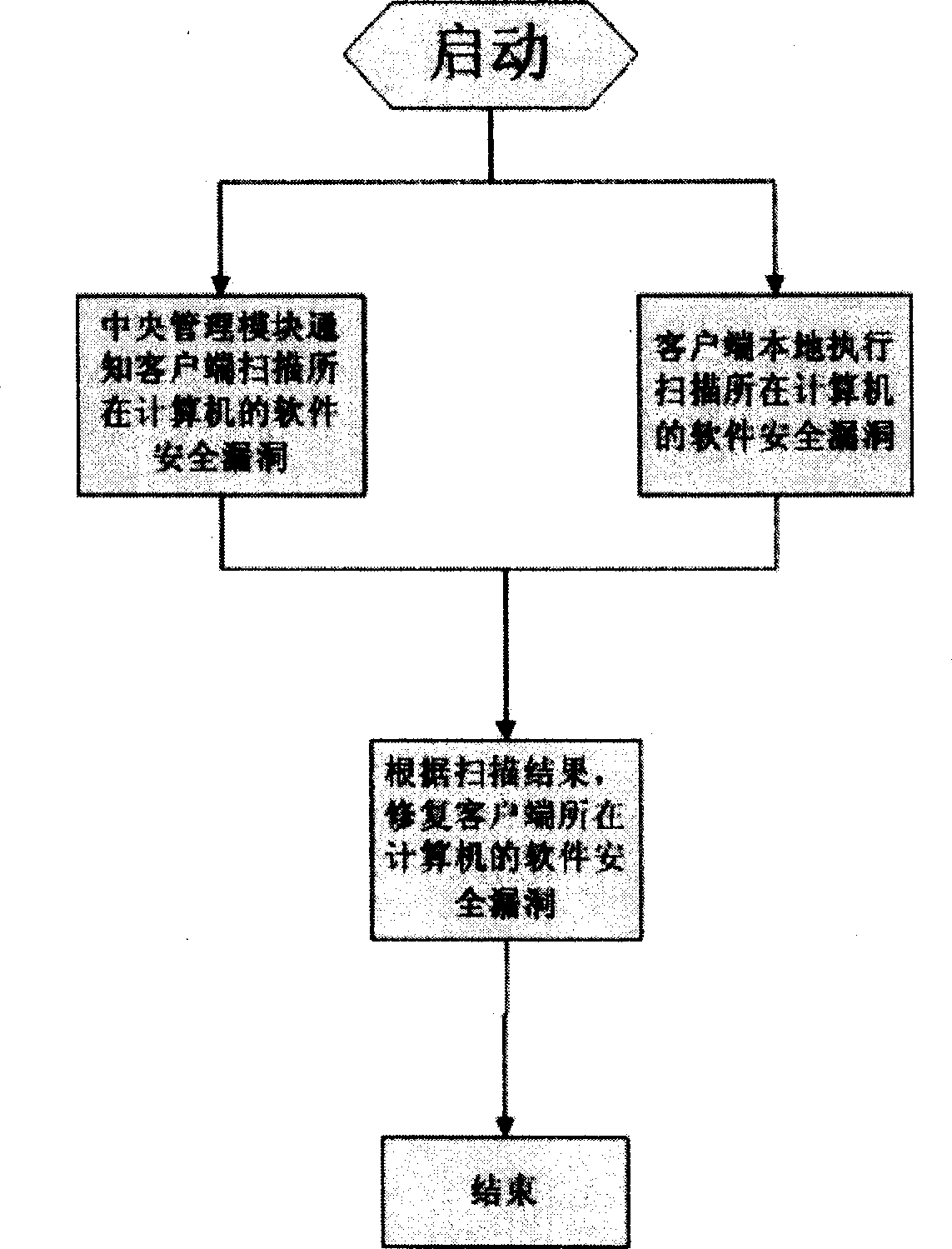
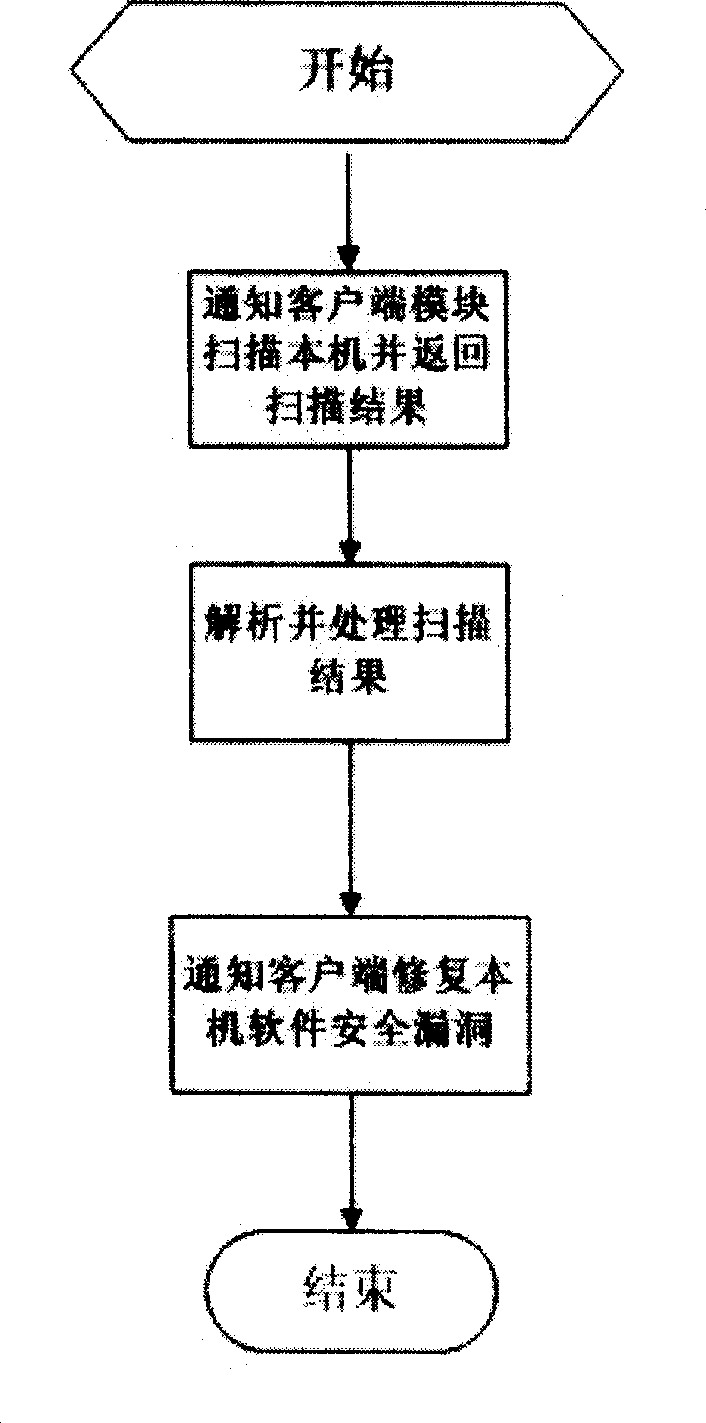
Computer software security loophole repairing apparatus and method
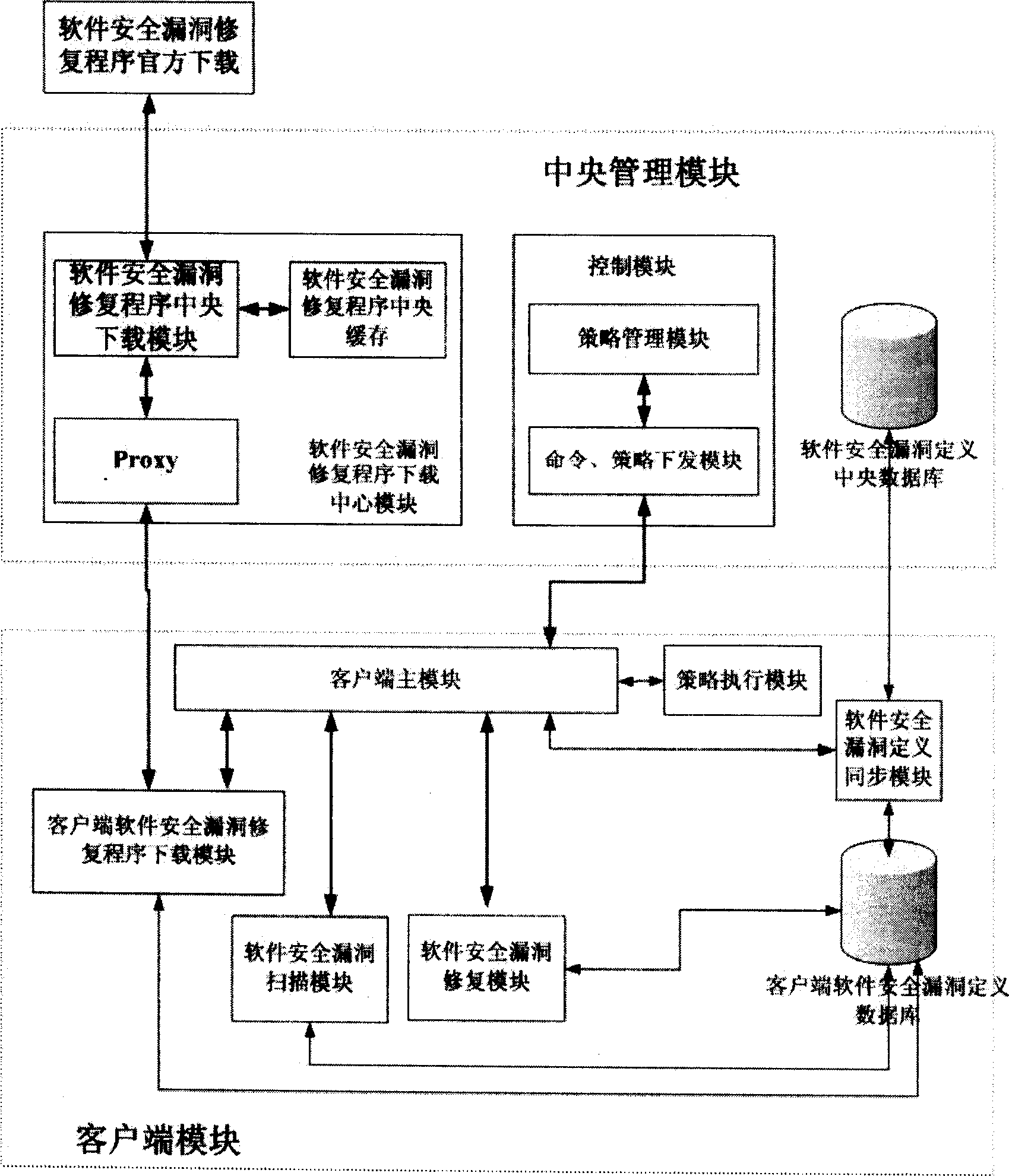
ActiveCN1766776ADigital data processing detailsSoftware testing/debuggingOperational systemSoftware engineering
The invention relates to a computer software safety loophole restoring apparatus and method in the field of computer. It also provides a restoring method which comprises two achieving method: 1) first it uses the communication managing module to inform client end to scan the software safety loophole of the computer and restores the software safety loophole by the scanning result; 2) first it uses the client to scan the software safety loophole of the computer and restores the software safety loophole by the scanning result.
Owner:KINGSOFT
Sequence pattern software security vulnerability-based detection method
InactiveCN104778403AHigh precisionFast updatePlatform integrity maintainanceFeature vectorSoftware system
The invention discloses a sequence pattern software security vulnerability-based detection method. The method comprises the following steps: A, storing known security vulnerability records in a database, and classifying the security vulnerability records in the database to form a plurality of security vulnerability sequences; B, extracting a characteristic vector of each security vulnerability sequence to serve as a mark of each security vulnerability sequence; C, comparing an operated program statement with the characteristic vectors in the step B by an on-line monitoring module, and comparing a source code of a software system with the security vulnerability sequences in the step A by an off-line scanning module; D, de-noising a security vulnerability comparison result obtained in the step C and then storing a comparison result of the identified security vulnerability in the security vulnerability sequence nearest to the security vulnerability, and outputting the comparison result of the non-identified security vulnerability through a human-computer interaction module. The defects of the prior art can be improved, and meanwhile the speed and accuracy of detection are improved.
Owner:JIANGSU NANDASOFT TECHNOLOGY COMPANY LIMITED
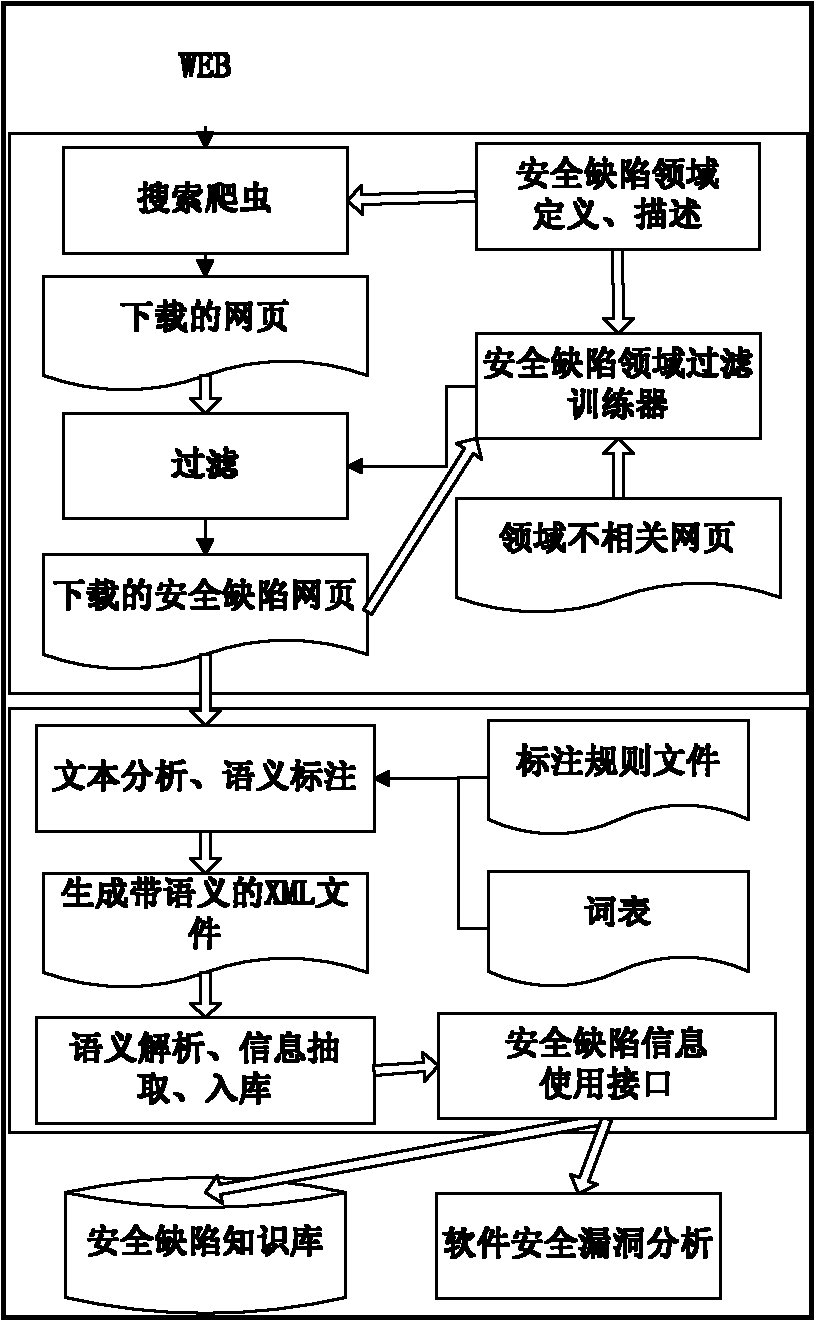
Method for obtaining software security defects based on vertical search and semantic annotation
ActiveCN101814098AEffective filteringAutomatically find security flawsSpecial data processing applicationsSoftware engineeringSemantic annotation
The invention belongs to the field of dependable computing, in particular to a method for obtaining software security defects based on vertical search and semantic annotation, which comprises the steps of: firstly, creeping a security defect information webpage published on a World-Wide-Web by using a field search creeper, providing a forceful filter support for the search creeper completing the task by a security defect filed filter trainer; secondly, carrying out semantic annotation on downloaded webpages to enable the webpages to be carried out with semantic information and allow a machine to be understood; thirdly, designing an annotation analysis tool for further carrying out information extraction on the annotated information; and fourthly, providing an interface for carrying out a software security knowledge base and a software security hole analysis by using the information. The invention can provide a large quantity of data and the forceful support for the software security knowledge base and the software security hole analysis.
Owner:江苏永达电力电信安装工程有限公司
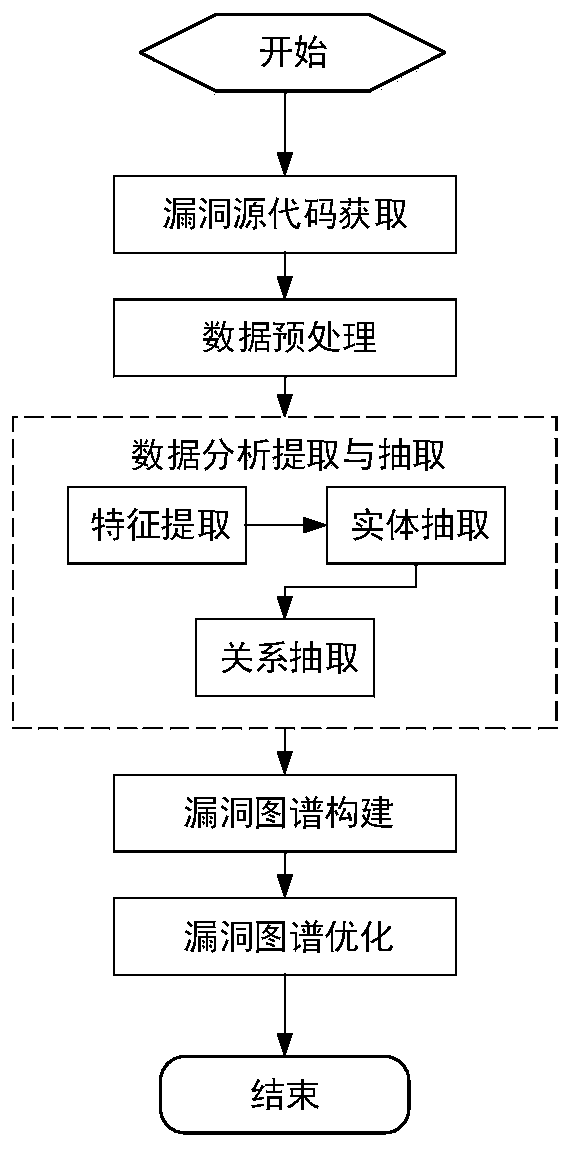
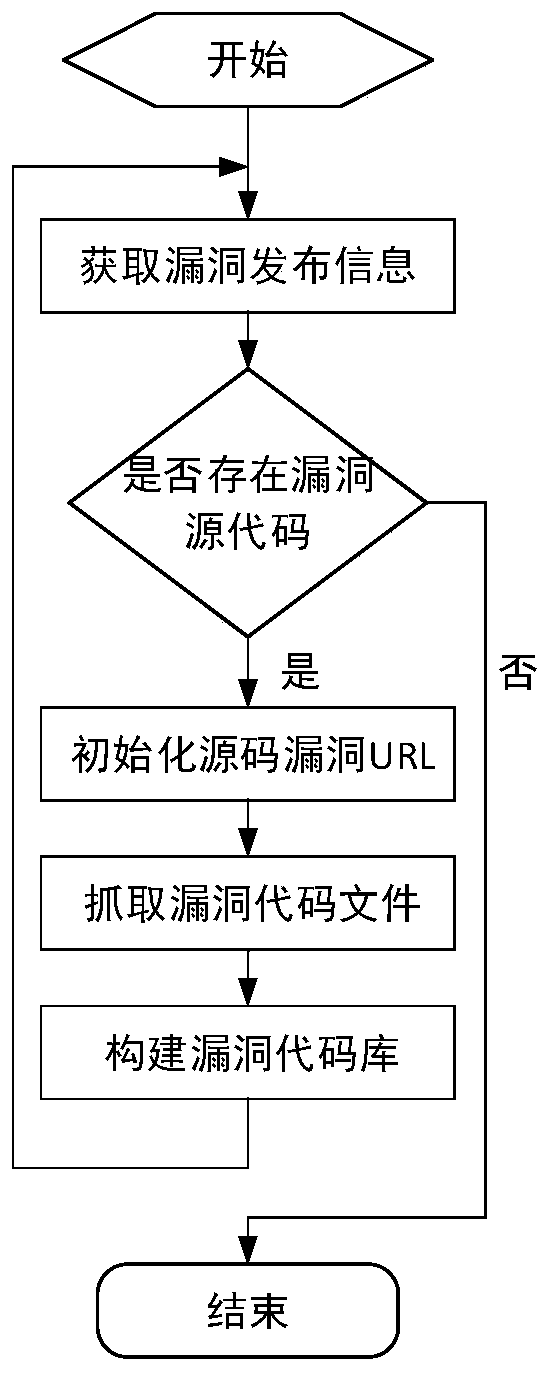
Source code-oriented bipolar software security vulnerability graph construction method
ActiveCN110909364AEmbodies the intricate relationshipHigh precisionWeb data indexingData miningTheoretical computer scienceEngineering
The invention discloses a source code-oriented bipolar software security vulnerability graph construction method, solving the problems of single vulnerability feature, lack of semantic information andlow vulnerability mining precision in a current vulnerability graph model. The technical scheme includes the steps: obtaining vulnerability source codes through crawlers; preprocessing the vulnerability source codes; carrying out data analysis and extraction, including feature extraction, entity extraction and relationship extraction; constructing a vulnerability graph, including taking the sub-graph as a basic unit of the vulnerability graph, and visualizing and storing the vulnerability graph; and performing vulnerability graph optimization: removing a large amount of redundant informationby pruning the sub-graph to achieve vulnerability graph optimization. According to the vulnerability graph constructed by the invention, the forward and reverse characteristics of the vulnerability are displayed at the same time through comparison; the complex relation among the characteristic items is embodied; existing semantic structure information is enriched; a reliable basis is provided forresearch of vulnerability causes; vulnerability mining precision is improved; system software safety is guaranteed; and the vulnerability graph is used for computer security vulnerability mining and management.
Owner:XIAN TECH UNIV
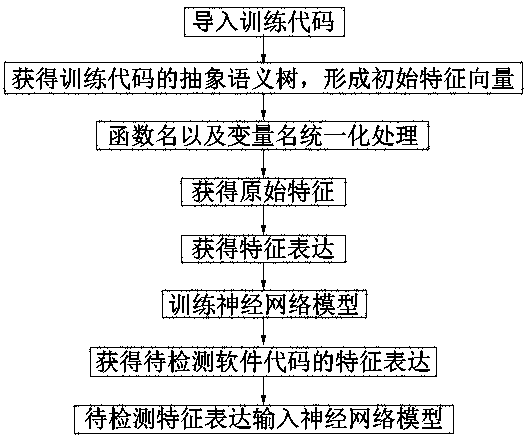
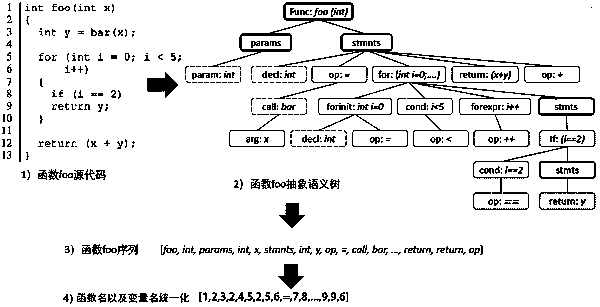
Function-level software vulnerability detection method
PendingCN109657466ASave manpower and material resourcesPlatform integrity maintainanceNeural learning methodsFeature vectorSemantic tree
The invention relates to the technical field of software security vulnerability detection, in particular to a function-level software vulnerability detection method, which comprises the following steps of: A) importing a training code; B) obtaining an abstract semantic tree of the training code to form an initial feature vector; C) unifying the function name and the variable name; D) obtaining original features; E) obtaining a characteristic expression; F) training a neural network model; And G) obtaining the feature expression of the to-be-detected software code, and inputting the to-be-detected feature expression into the neural network model trained in the step F to obtain a vulnerability detection result. The substantial effects of the invention are as follows: the scheme uses a seriesof simple methods to cooperate with Bi-; The LSTM neural network is used for processing codes, advanced abstract semantic features of functions can be directly extracted, manpower and material resources are saved, and cross-project vulnerability detection can be implemented through the extracted advanced abstract semantic features.
Owner:杭州英视信息科技有限公司
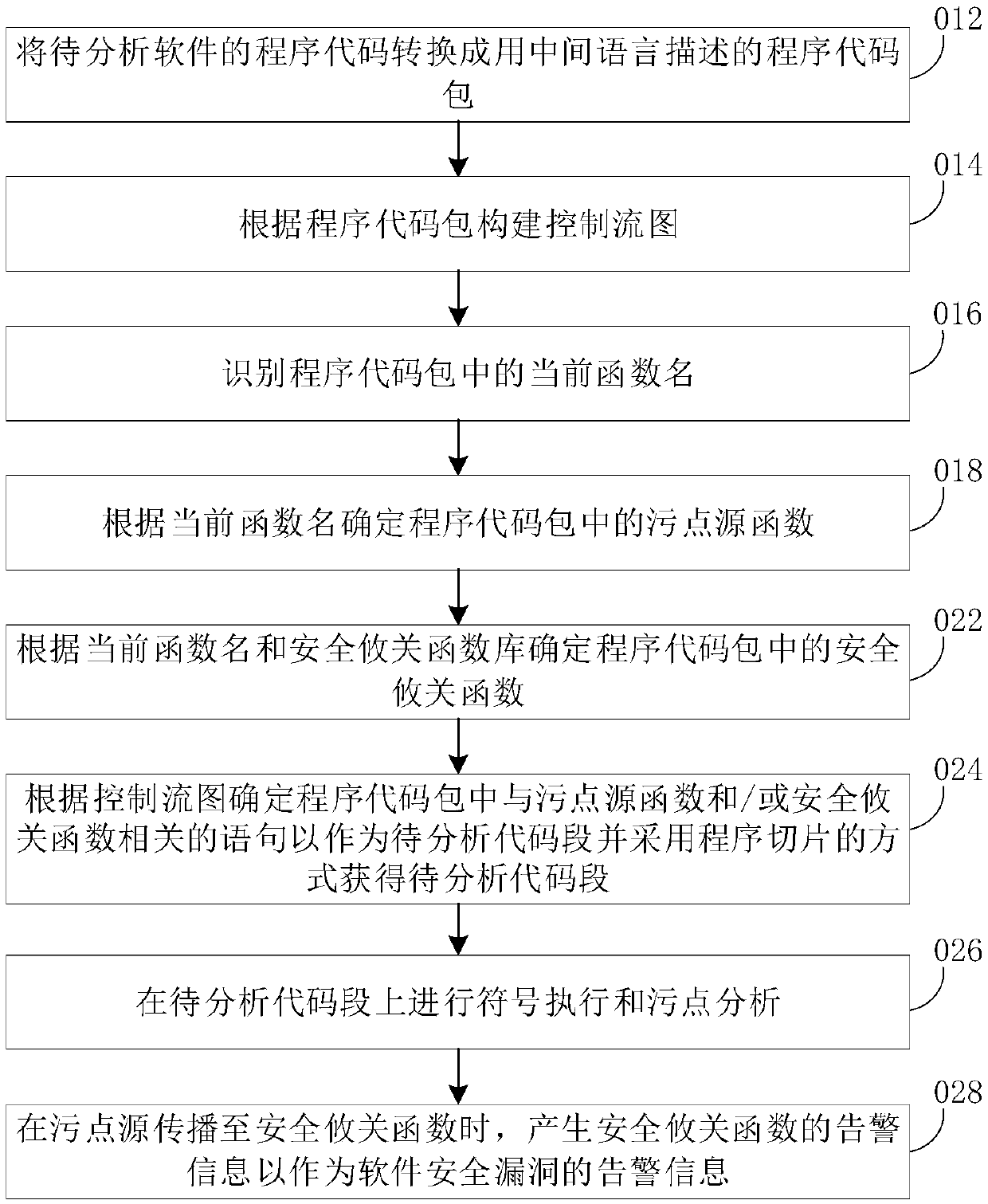
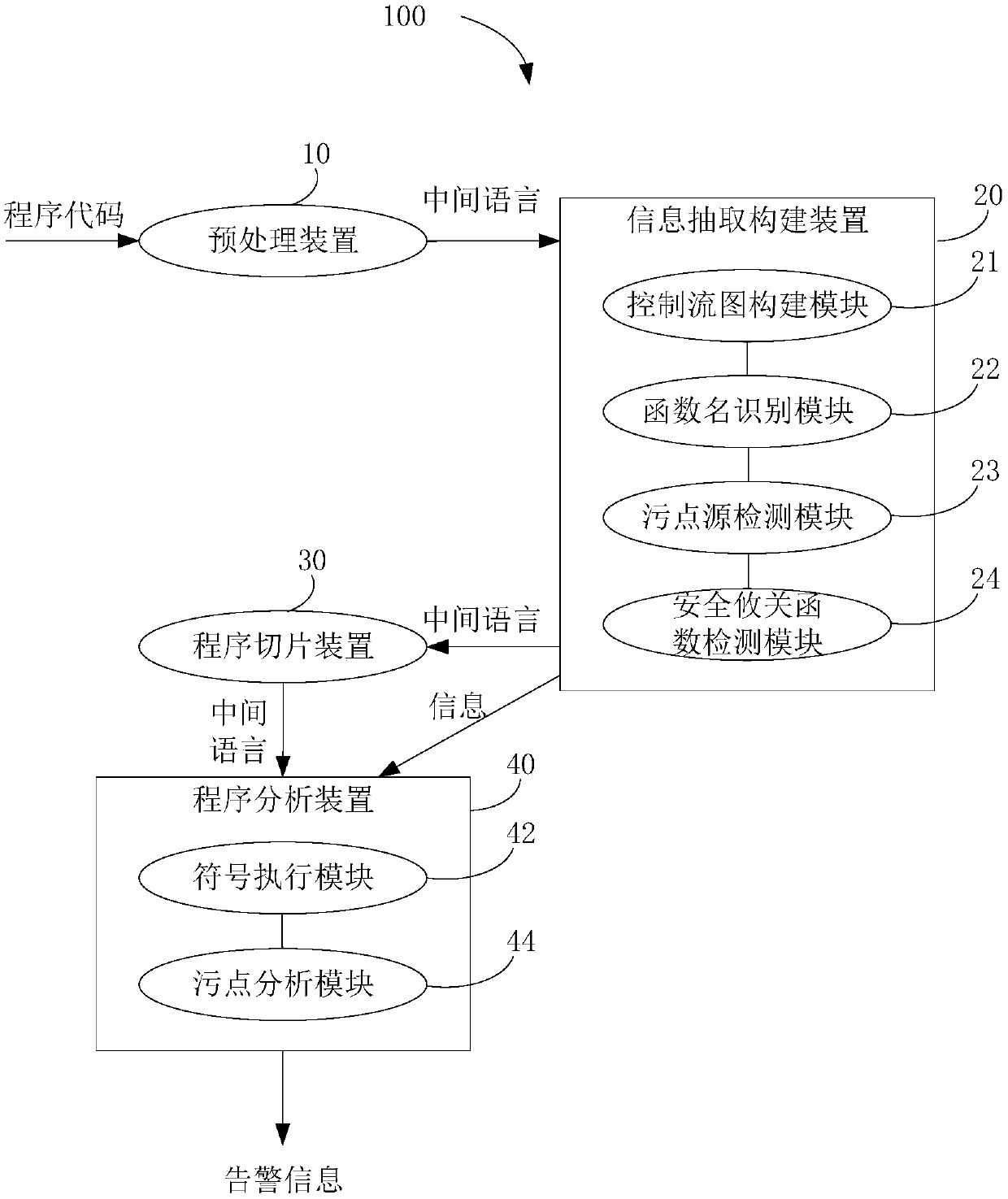
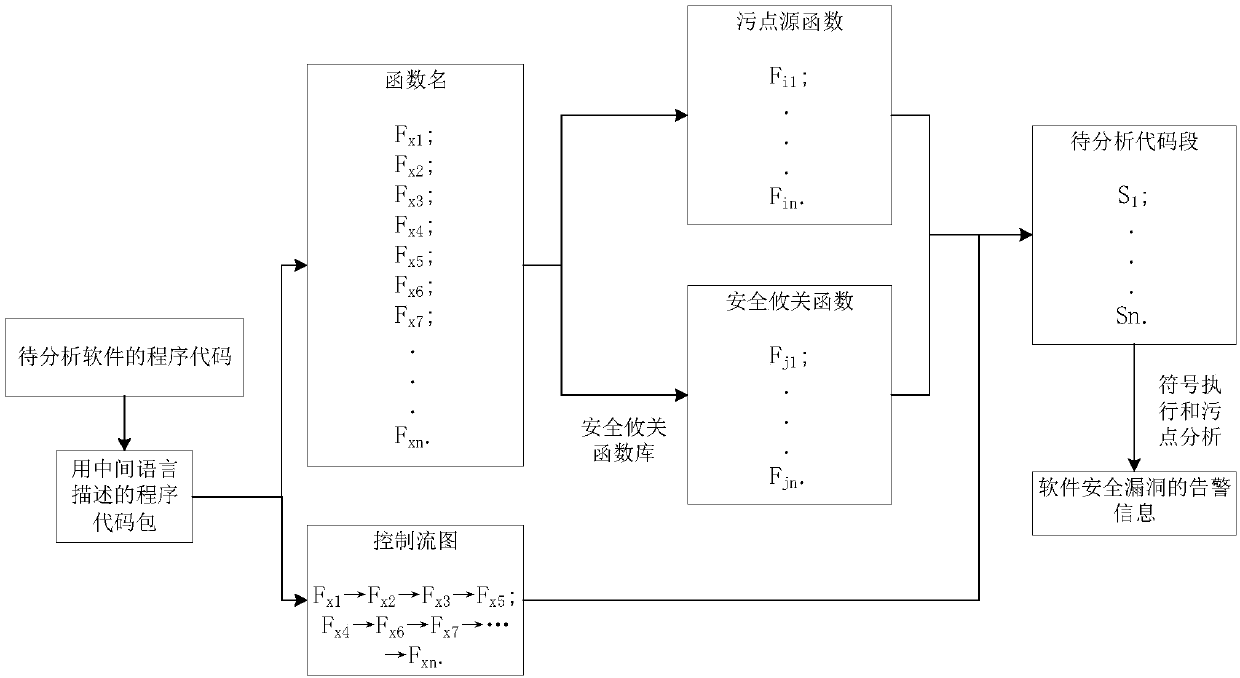
Software security vulnerability discovery method and system, storage medium and computer device
ActiveCN110197072AFully automatic processNo human intervention requiredSoftware testing/debuggingPlatform integrity maintainanceSource functionCritical function
The invention discloses a software security vulnerability discovery method. The mining method comprises the following steps: converting to-be-analyzed software into a program code package in an intermediate language form; constructing a control flow graph and identifying a current function name according to the program code package; determining a stain source function and a stain source accordingto the current function name; determining a safety critical function according to the current function name and the safety critical function library; obtaining statements related to the stain source function and / or the security critical function to serve as to-be-analyzed code segments; carrying out symbol execution and stain analysis on the to-be-analyzed code segment; and when the stain source is propagated to the security critical function, generating alarm information of the software security vulnerability. The invention further discloses a discovery system, a computer readable storage medium and a computer device. According to the discovery method, the discovery system, the computer readable storage medium and the computer device, the warning information of the software security holecan be directly generated according to the program code of the to-be-analyzed software, the process is full-automatic, and manual participation is not needed.
Owner:TENCENT TECH (SHENZHEN) CO LTD
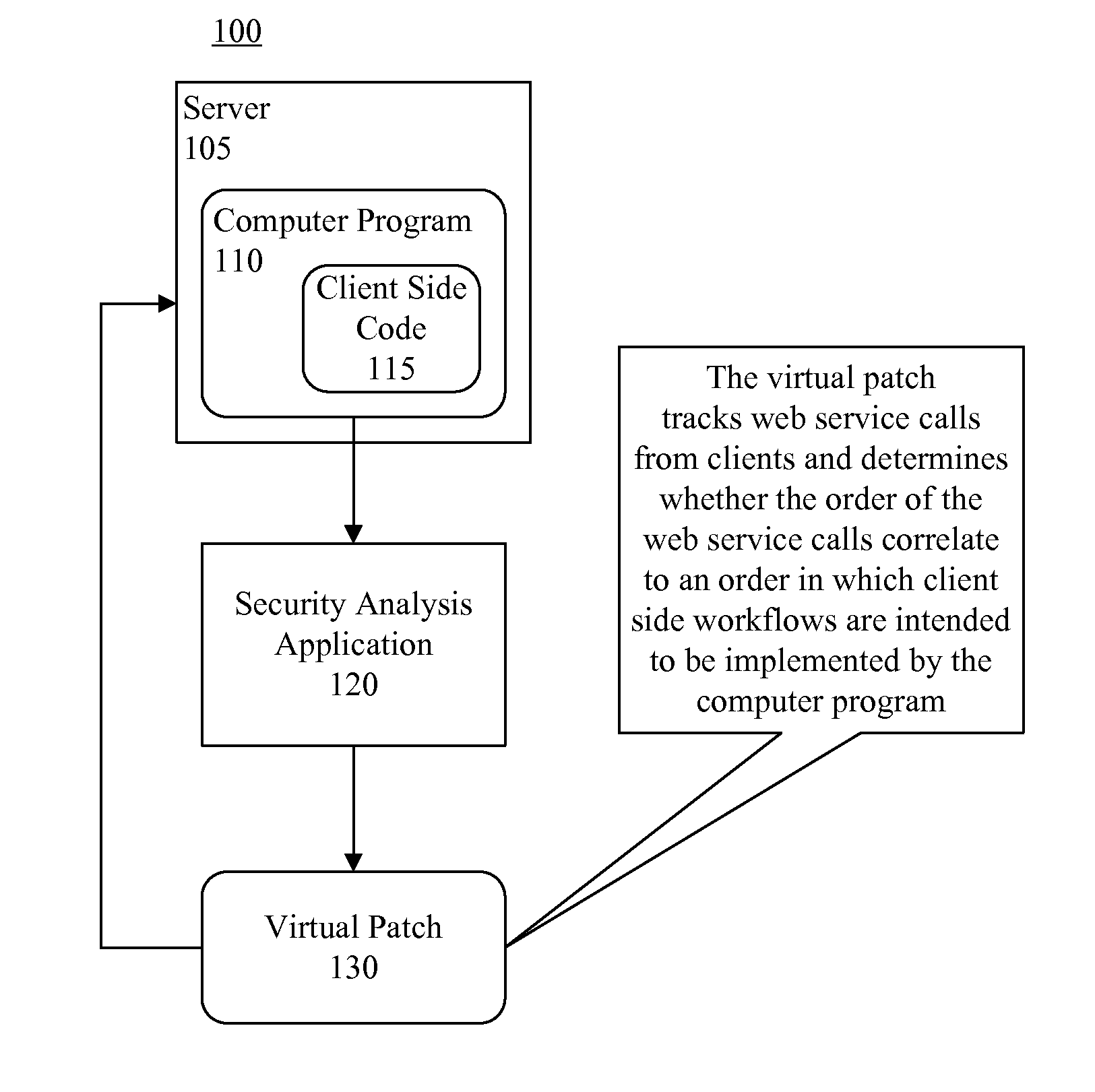
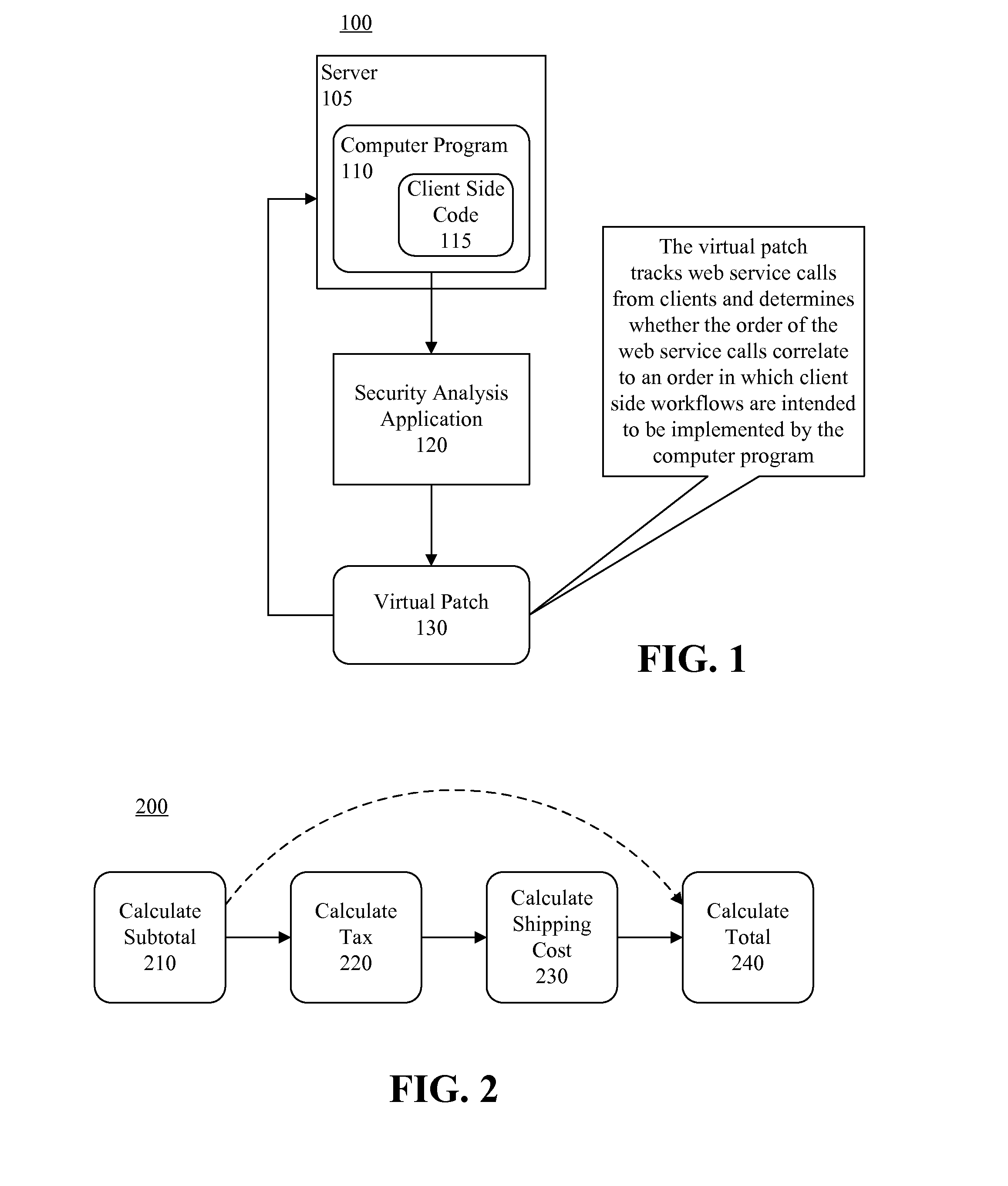
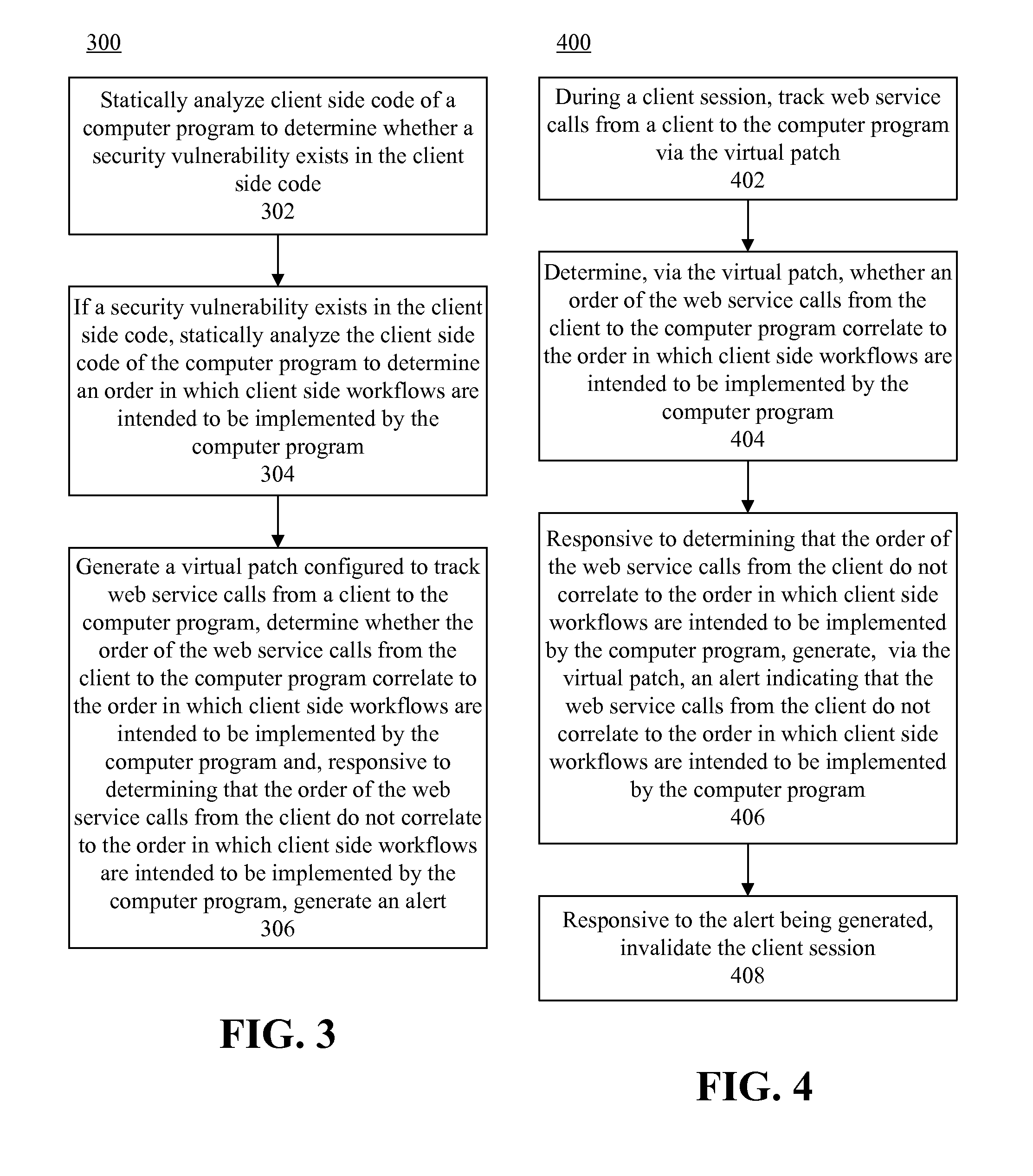
Correcting workflow security vulnerabilities via static analysis and virtual patching
InactiveUS20140096258A1Memory loss protectionError detection/correctionStatic timing analysisWeb service
A computer program can be statically analyzed to determine an order in which client side workflows are intended to be implemented by the computer program. A virtual patch can be generated. When executed by a processor, the virtual patch can track web service calls from a client to the computer program, and determine whether the order of the web service calls from the client to the computer program correlate to the order in which client side workflows are intended to be implemented by the computer program. If the order of the web service calls from the client to the computer program do not correlate to the order in which client side workflows are intended to be implemented by the computer program, an alert can be generated.
Owner:IBM CORP
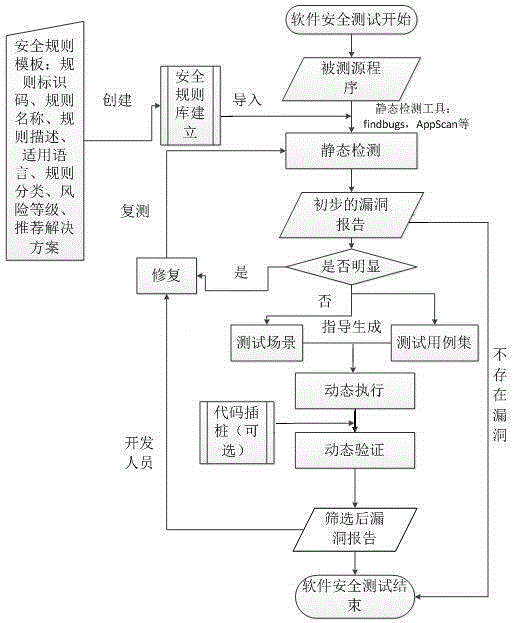
Software security testing method
InactiveCN105335290AImprove applicabilityImprove accuracySoftware testing/debuggingPlatform integrity maintainanceDynamic methodSoftware engineering
The invention discloses a software security testing method, which belongs to the field of software testing. According to the invention, through establishing a security rule template, creating a to-be-tested software security rule base based on the template, and importing a defined software security rule base into a software security flaw scanning tool to carry out software security static-testing, a preliminary software security flaw report is formed; and then the preliminary software security flaw report is tested by using the testing method with combination of a static method and a dynamic method. The method can improve the applicability and accuracy of software security testing.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
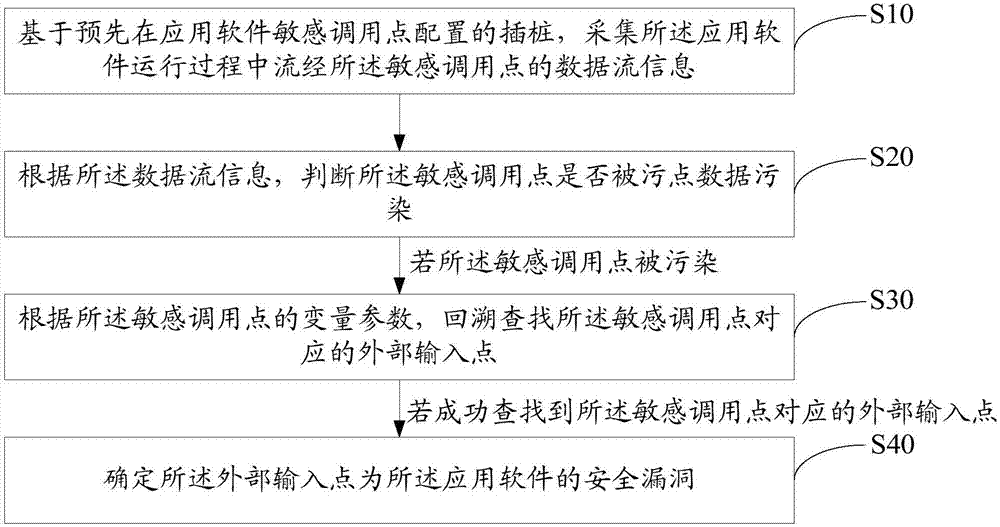
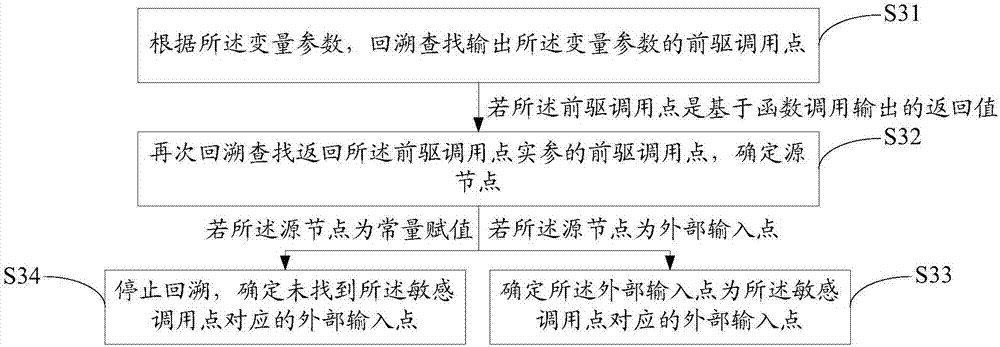
Method and system for detecting security hole of application software
ActiveCN107038378AIncreased Security VulnerabilitiesWith safety detectionPlatform integrity maintainanceData streamSoftware engineering
The invention discloses a method for detecting a security hole of application software. The method comprises the steps of collecting data flow information which flows through a sensitive calling point in a running process of the application software based on a pitching pile configured on the sensitive calling point of the application software in advance; judging whether the sensitive calling point is polluted by tainted data according to the data flow information; if the sensitive calling point is polluted, reversibly finding out an external input point corresponding to the sensitive calling point according to a variable parameter of the sensitive calling point; and if the external input point corresponding to the sensitive calling point is successfully found out, determining the external input point as the security hole of the application software. The invention also discloses a system for detecting the security hole of the application software. According to the method and the system, the detection efficiency for the safety bug of the application software is greatly improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Method and system for detecting security hole of application software
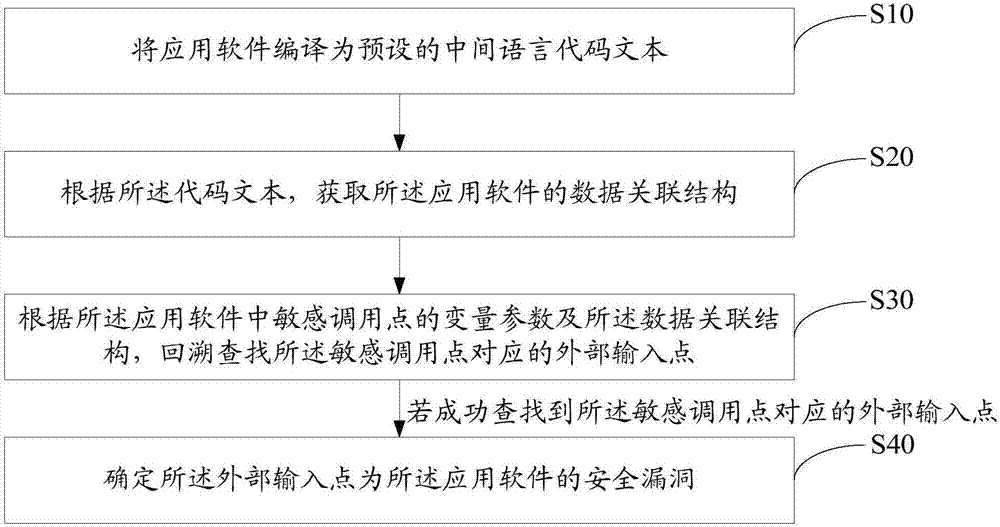
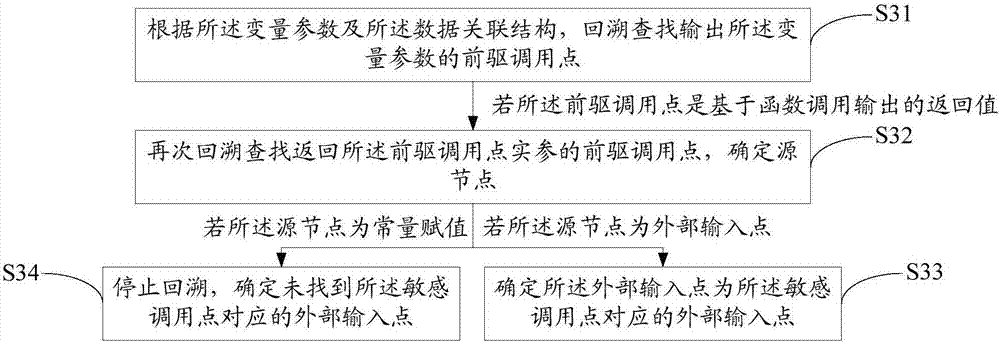
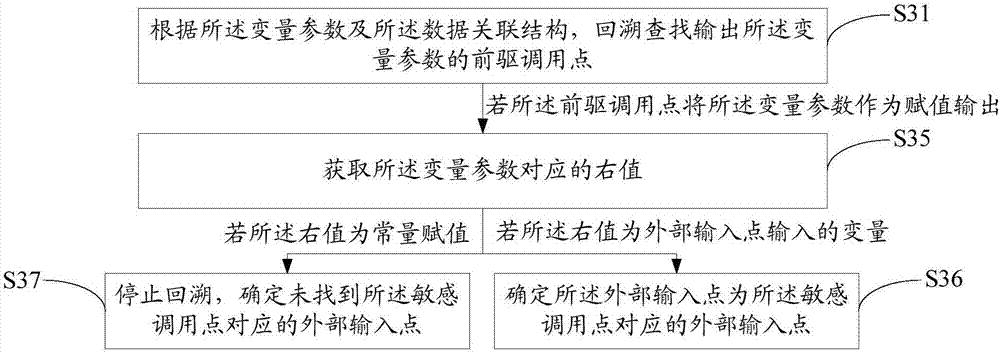
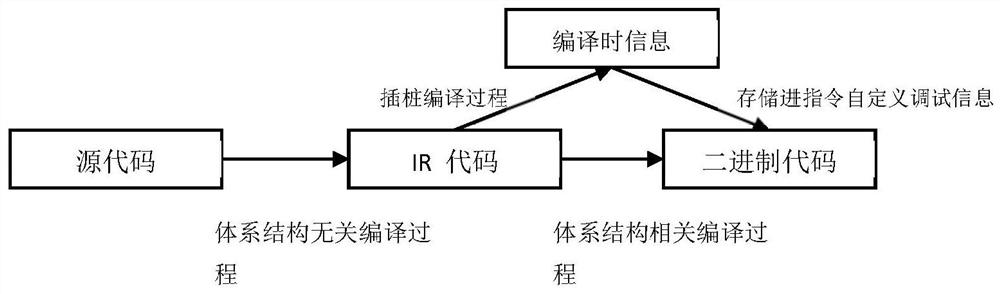
ActiveCN107038115AAvoid rough checksReduce workloadSoftware testing/debuggingSoftware engineeringApplication software
The invention discloses a method for detecting a security hole of application software. The method comprises the steps of compiling the application software into a preset intermediate language code text; acquiring a data association structure of the application software according to the code text; reversibly finding out an external input point corresponding to a sensitive calling point according to a variable parameter of the sensitive calling point and the data association structure in the application software; and if the external input point corresponding to the sensitive calling point is successfully found out, determining the external input point as the security hole of the application software. The invention also discloses a system for detecting the security hole of the application software. According to the method and the system, the detection efficiency for the security hole of the application software is greatly improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
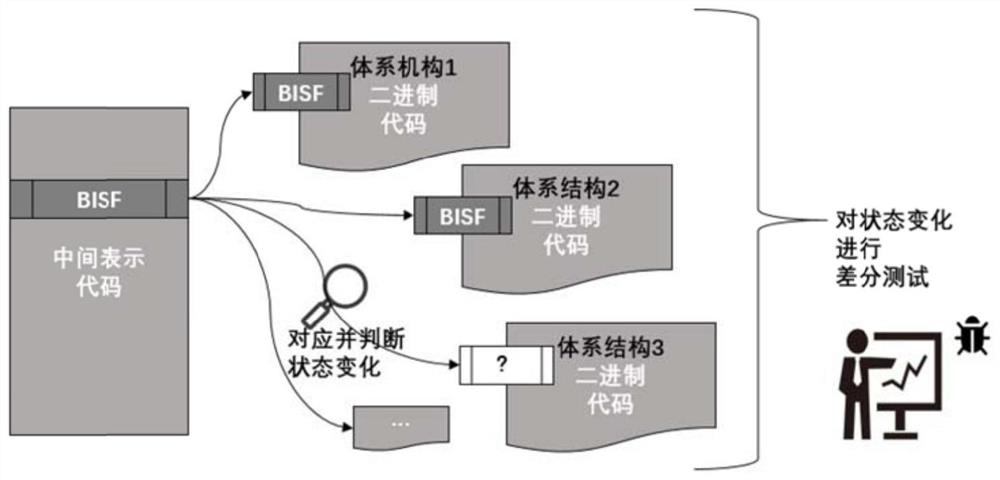
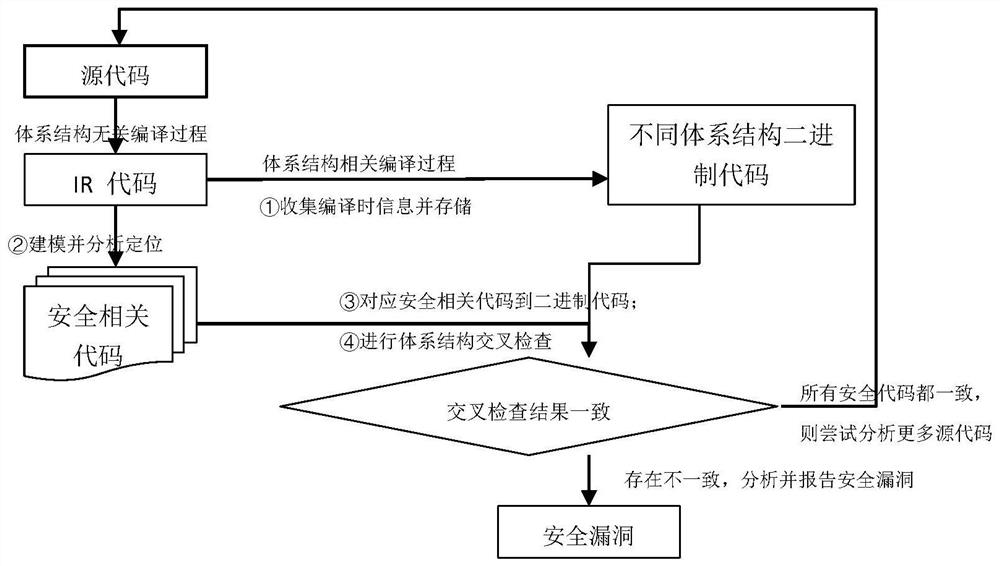
Compiler security test method based on system structure cross check
The invention provides a compiler security test method based on system structure cross check. The method is used for detecting software security vulnerabilities introduced when a compiler compiles common open source software into different system structure binary codes. Due to the fact that the changes of the safety related codes before and after compiling meet the system structure consistency, the software vulnerabilities introduced by the compiler can be detected by comparing the changes and conducting system structure cross check. The method comprises the following steps of: modeling and positioning a safety related instruction, corresponding to an IR (Intermediate Representation) code and a binary code, judging the change of a semantic state of the safety related instruction, and carrying out cross check on a system structure. By means of the method, efficient and accurate positioning of the software security vulnerabilities introduced by the compiler is achieved.
Owner:NANJING UNIV
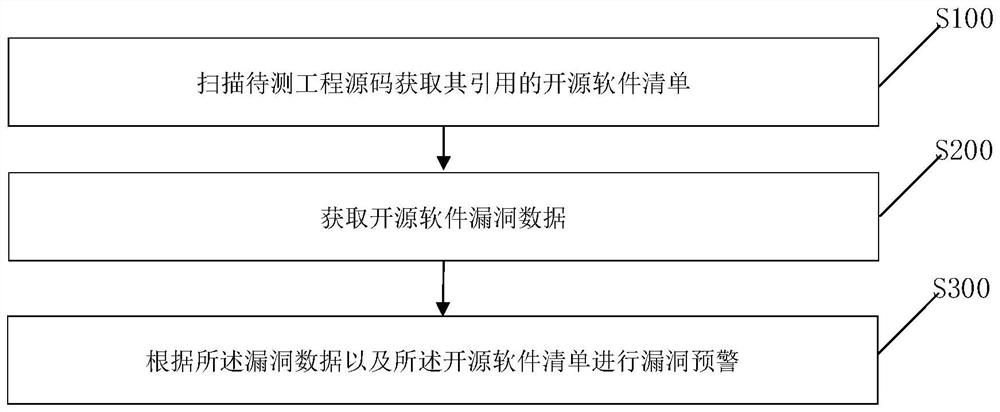
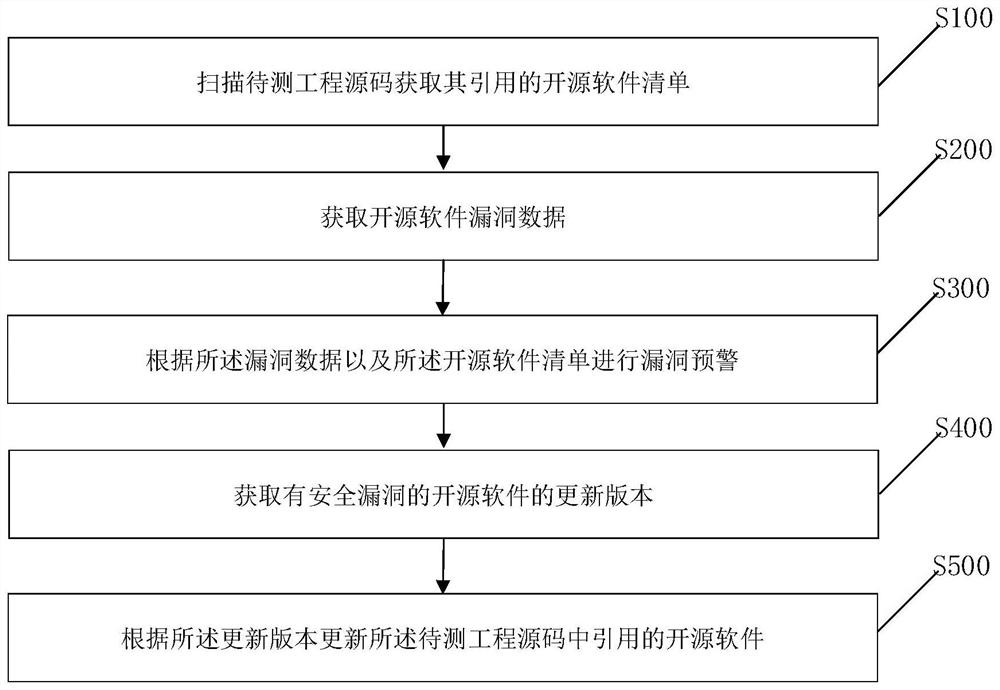
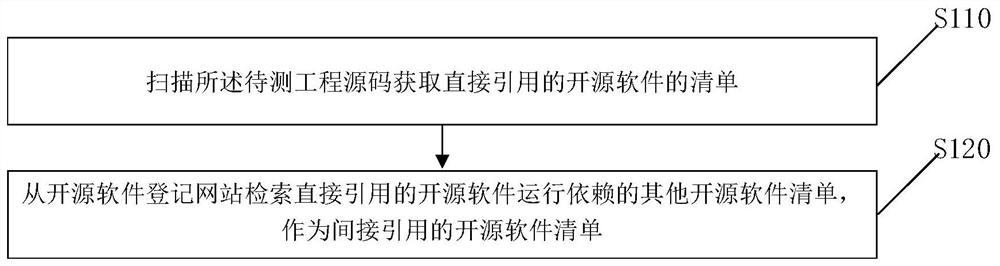
Open source software security vulnerability processing method and device
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Software security vulnerability detection method based on runtime non-execution state mode
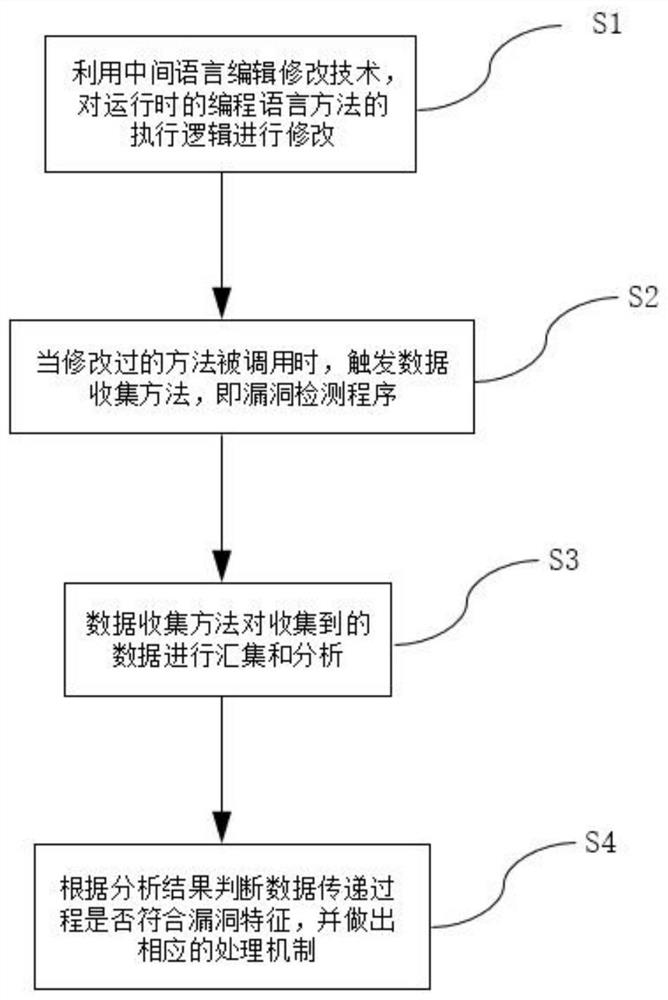
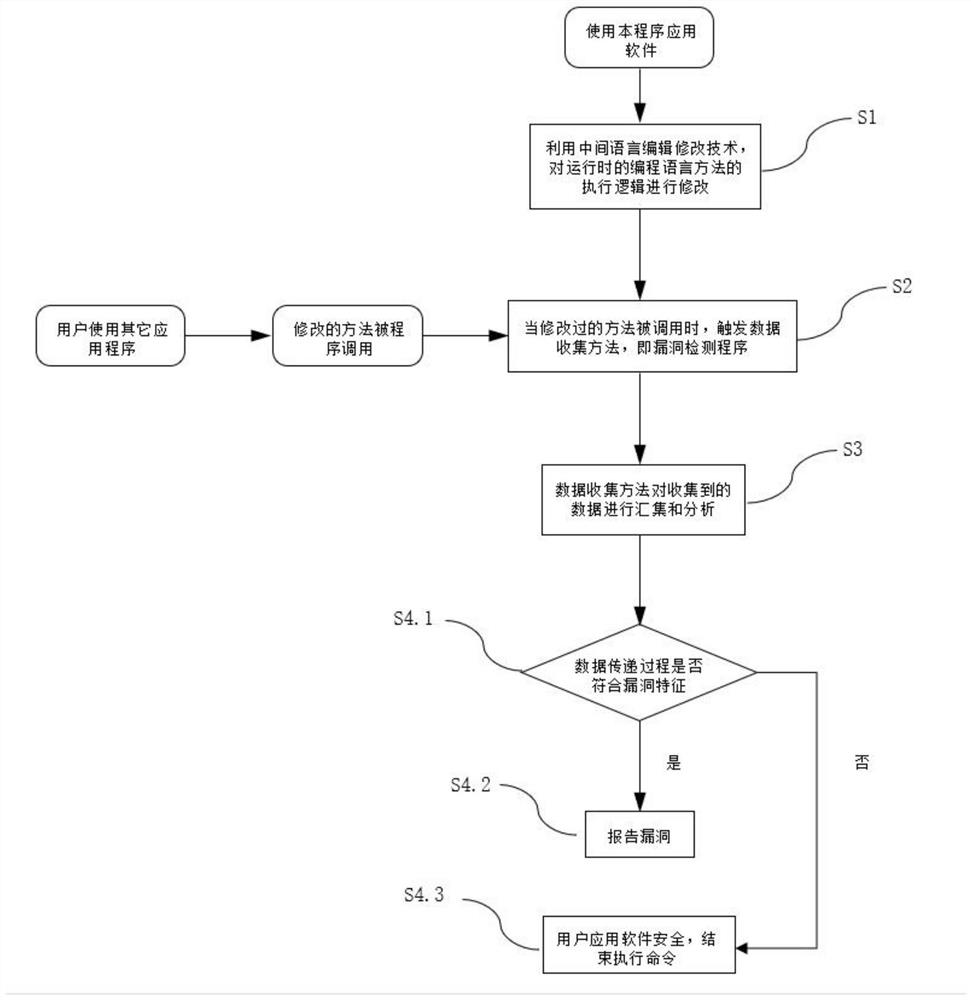
PendingCN111723375AWill not generateImprove test performancePlatform integrity maintainanceApplication softwareLogisim
The invention discloses a software security vulnerability detection method based on a runtime non-execution state mode, and relates to the technical field of network security. The implementation process comprises the following steps: modifying execution logic of a runtime programming language method by utilizing an intermediate language editing and modifying technology; when the modified method iscalled, triggering a data collection method, namely a vulnerability detection program; using the data collection method to collect and analyze the acquired data; and S4, judging whether the data transmission process conforms to vulnerability characteristics or not according to an analysis result in the step S3, and making a corresponding processing mechanism. According to the software security vulnerability detection method, the implementation program is always in a non-execution state during running, non-perceptual testing can be carried out on application software, and dirty data cannot begenerated; the technology does not depend on payload, the test capability is stable, and application software for data encryption and data signature verification can be tested.
Owner:杭州孝道科技有限公司
Open source software security vulnerability patch positioning method based on sorting
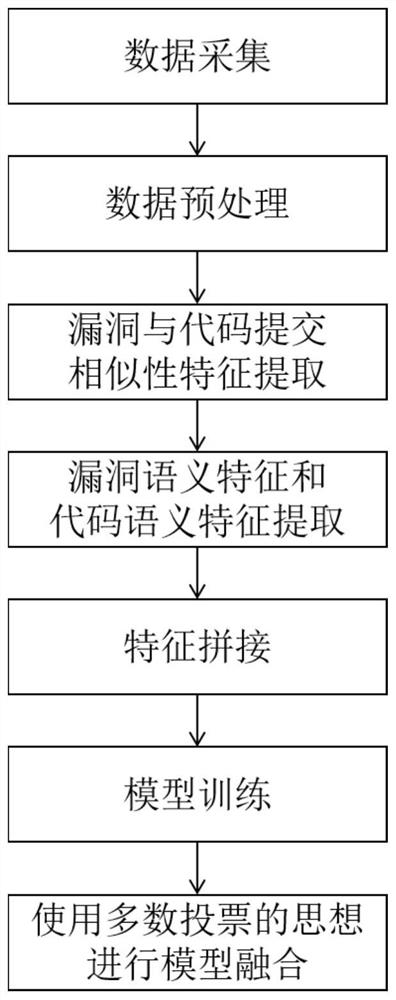
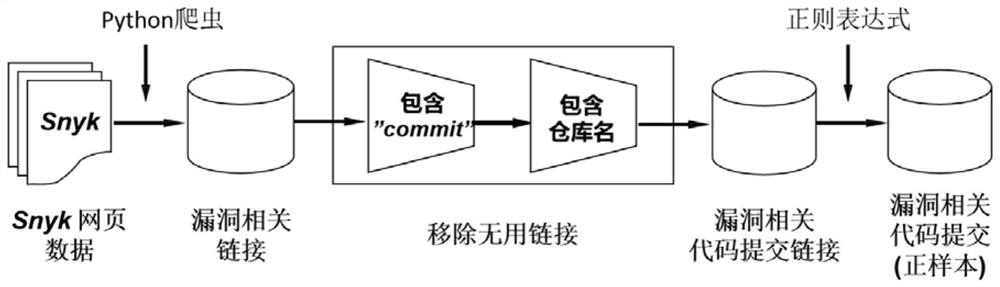
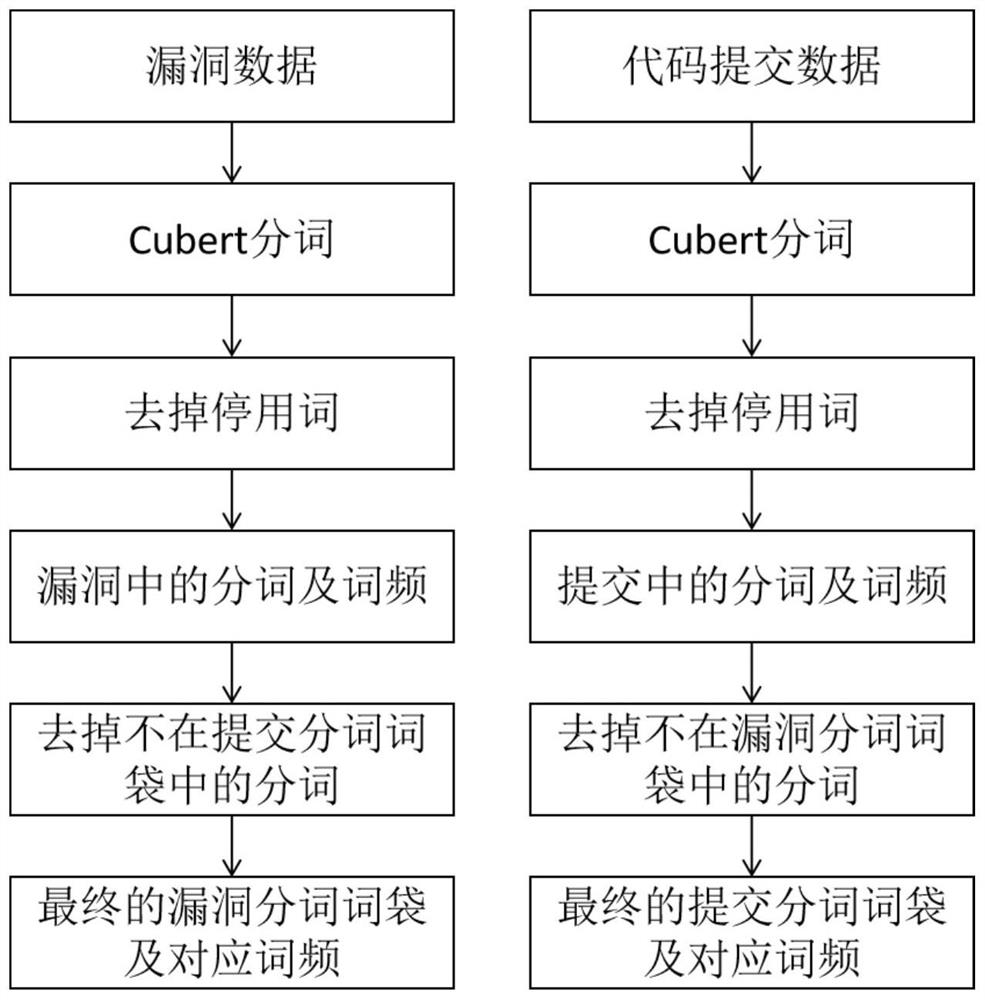
PendingCN114386048AImprove final performanceTrue meaning goodSemantic analysisCharacter and pattern recognitionStatistical analysisTheoretical computer science
The invention provides a sorting-based open source software security vulnerability patch positioning method. The method specifically comprises the following steps: collecting vulnerability and code submission data from a website; extracting vulnerability and code submission similarity characteristics of four dimensions including code lines, vulnerability identities, vulnerability repair positions and segmented word bags by using a data mining and statistical analysis method; training a bug field text semantic coding module based on a Bert model, and extracting bug semantic features and code submission semantic features by using the semantic coding module; splicing the semantic features of the vulnerability and the semantic features of the code submission to form all features of the vulnerability and the code submission; model training; and carrying out model fusion by using a majority voting thought. According to the method, features can be extracted from vulnerabilities and code submission, a vulnerability patch submission sorting model is established, code submission in an open source software warehouse is sorted according to the matching degree with the vulnerabilities, and the number of submission codes needing to be checked by patch labeling personnel is effectively reduced.
Owner:ZHEJIANG UNIV CITY COLLEGE
Method and device for detecting security flaws of software source codes
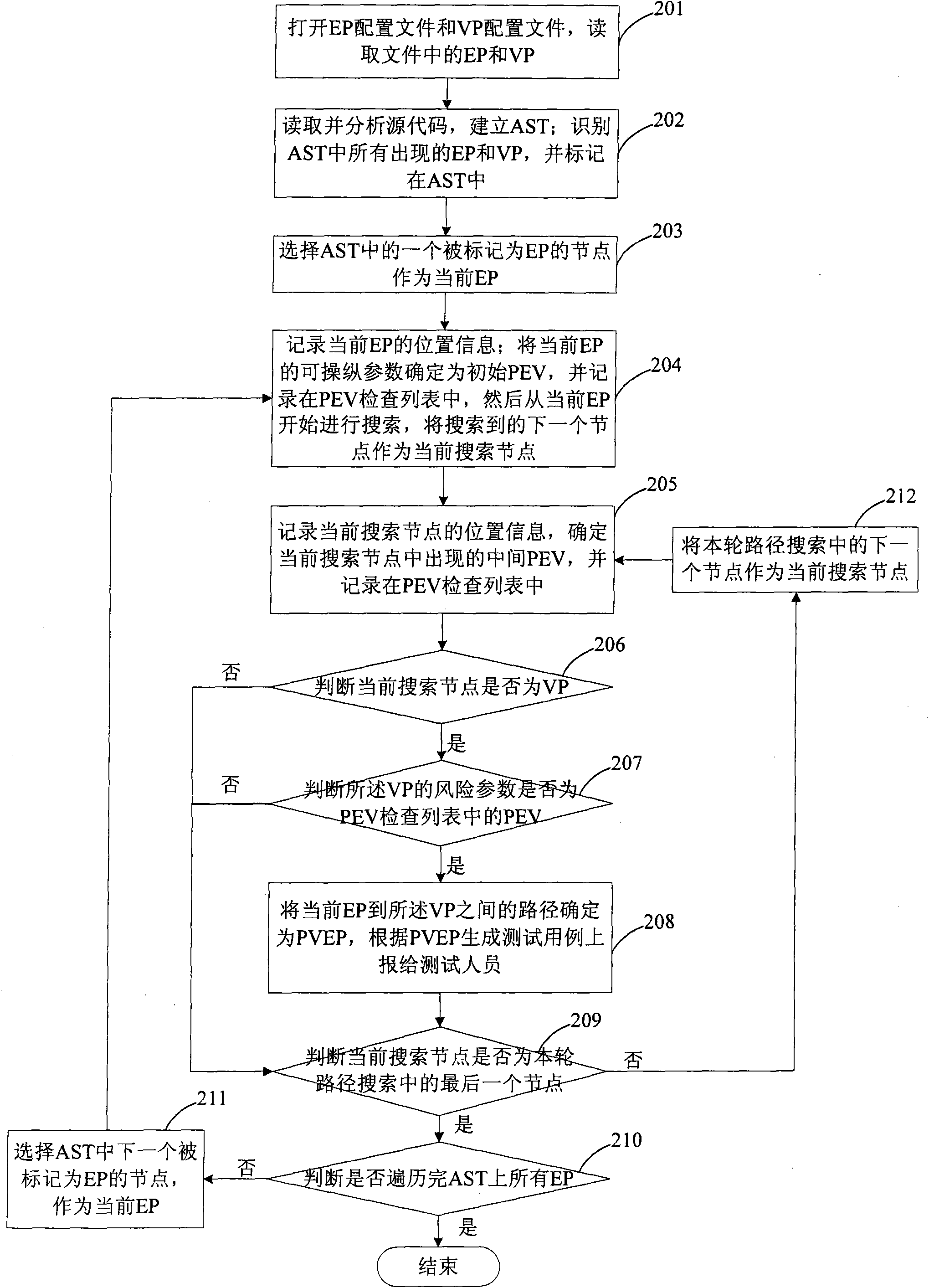
ActiveCN101661543BEasy to analyzeEfficient searchPlatform integrity maintainanceSource codeAbstract syntax tree
The invention discloses a method for detecting security flaws of software source codes. The method comprises the following steps: establishing an abstract syntax tree AST corresponding to source codesof software to be detected; determining controllable points and risk points of each node of the established AST according to predefined controllable points and risk points; and searching an executionpath between the controllable points and the risk points in the AST, and if the risk points on the execution path can be controlled by the controllable points on the execution path, the execution path is determined as a potential risk execution path probably causing the security flaws. The invention also discloses a device for detecting the security flaws of the software. The method and the device can effectively detect the security flaws existing in the source codes of the software.
Owner:SIEMENS CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com