Source code-oriented bipolar software security vulnerability graph construction method
A software security and construction method technology, applied in computer security devices, platform integrity maintenance, data mining, etc., can solve the problems of insufficient vulnerability map, coarse recording information granularity, low efficiency of vulnerability mining algorithm, etc., and achieve intuitive and clear map. Clear and accurate effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
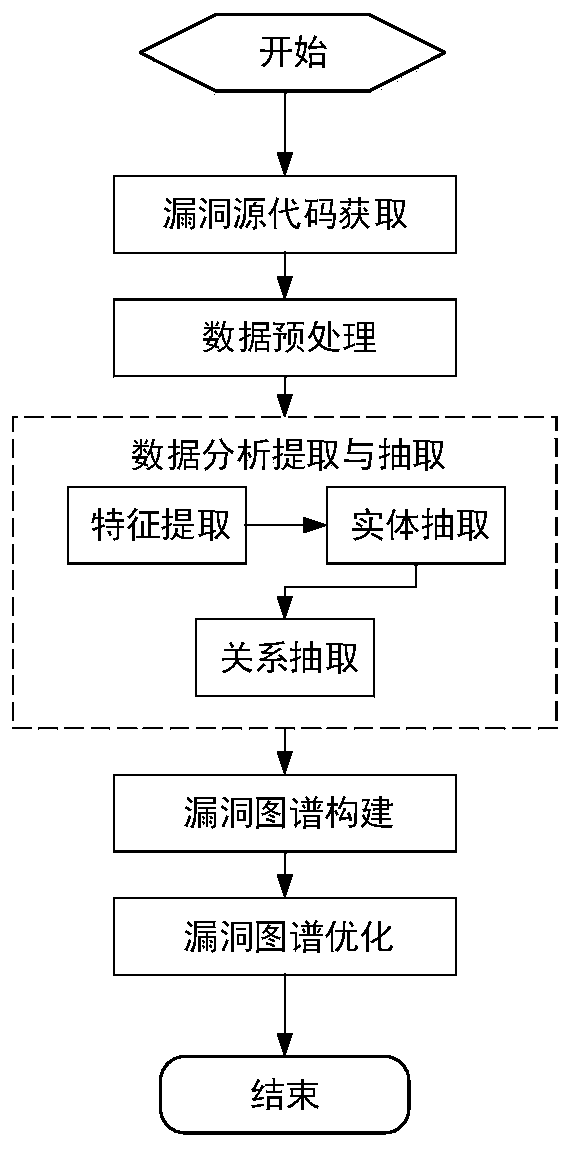
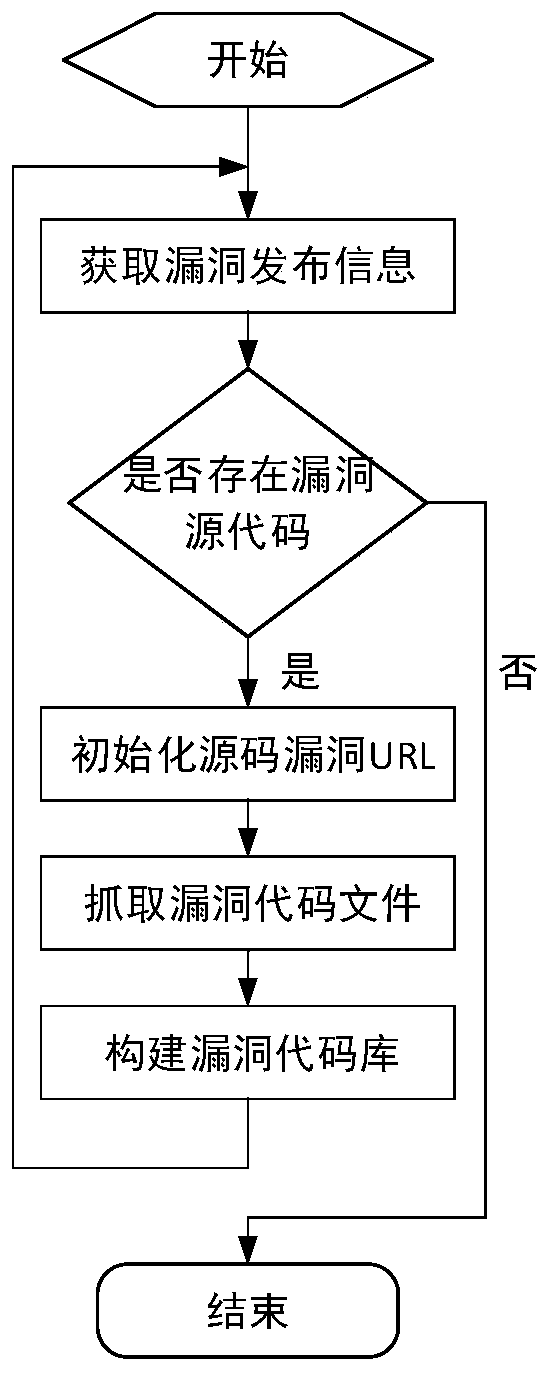
[0024] With the continuous development of Internet technology, hidden defects in software may lead to security vulnerabilities. These vulnerabilities are usually caused by developers leaving behind or improper handling when writing codes. Attackers can potentially damage systems and applications, bringing national security risks. a huge threat. Vulnerability graphs are used to describe and describe the relevant semantic structural features of vulnerabilities, express the complex characteristics of vulnerabilities, and use them to study the causes of vulnerabilities and exploit them.
[0025] Existing studies have found that the granularity of recorded information in the vulnerability database is relatively coarse, and the available information is relatively small. Most of the vulnerability mining technologies are aimed at specific programming languages or types of vulnerabilities. Vulnerability mining algorithms are less efficient, and the false positive rate and false negat...
Embodiment 2
[0034] The construction method of the source code bipolar software security vulnerability map is the same as embodiment 1, the data analysis extraction and extraction described in step (3), including the following steps:
[0035] 3.1) Feature extraction
[0036] Vulnerability source code for feature extraction includes vulnerability code and patch code. Feature extraction is performed on preprocessed data through text mining; a tree classification with CWE-number as the root node and CVE-number as child nodes is obtained. The CWE-number in the feature classification obtained can be further divided into directory traversal, incorrect input validation, buffer overflow, cross-site scripting attack, SQL injection, information exposure and resource management error according to the type of vulnerability.
[0037] 3.2) Entity extraction
[0038] Entity extraction is also called named entity recognition. The tree classification obtained by feature extraction is used for entity recog...
Embodiment 3
[0043] The construction method of the source code bipolar software security vulnerability graph is the same as example 1-2, and the vulnerability graph described in the step (4) of the present invention is constructed, including the following steps:
[0044] 4.1) The subgraph is the basic unit of the vulnerability graph
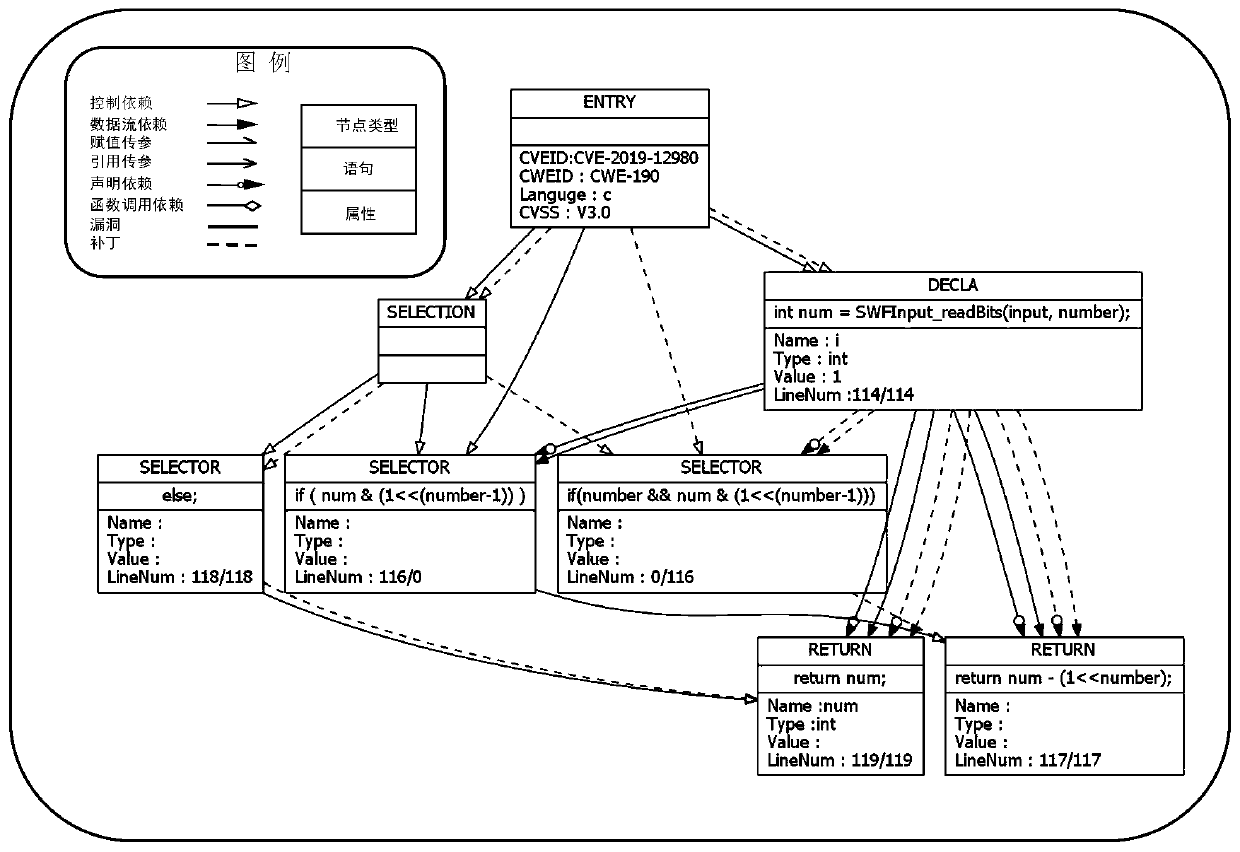
[0045] The subgraph starts from the position of the vulnerability patch code increase and decrease, and is a unit formed based on the CVE-number. , is the basic composition of the vulnerability graph. Analyze the subgraph nodes and the relationship between the nodes. The relationship between the nodes in the subgraph can be one-to-many or many-to-many, as shown in the attached image 3 As shown, arrows of different shapes are used to represent nodes and their relationships.
[0046] Subgraphs and subgraphs form a complete vulnerability map through CWE-numbers, G=g 1 ∪g 2 ∪…∪g n means that g n is the nth subgraph, n is the serial number of any subgraph, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com