Software security vulnerability detection method based on runtime non-execution state mode
A vulnerability detection and software security technology, applied in the field of network security, can solve problems such as unstable vulnerability detection capability, leaving dirty data, etc., to achieve the effect of stable testing capability and low false negative rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] In order to better understand the technical solutions of the present invention, the embodiments will be described in detail below in conjunction with the accompanying drawings.
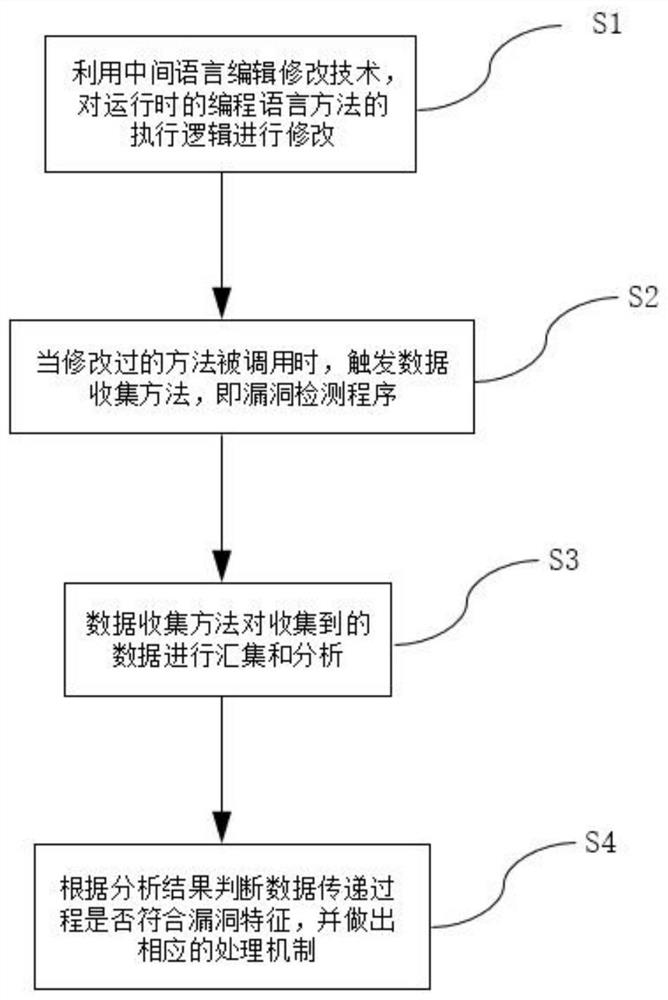
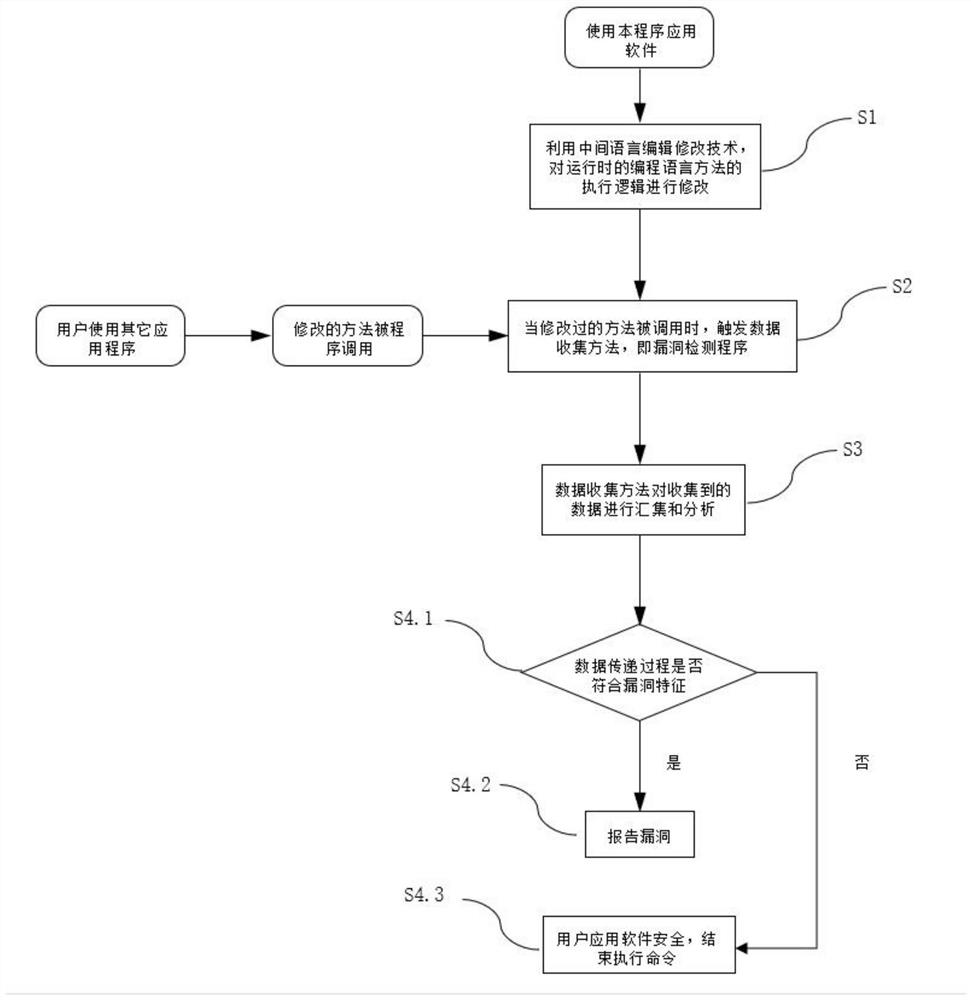
[0031] see figure 1 and figure 2 The illustrated embodiment: a method for detecting software security vulnerabilities based on the runtime non-executable state mode, the implementation process includes the following steps:
[0032] S1: Use the intermediate language editing and modification technology to modify the execution logic of the programming language method at runtime, that is, insert a call to the data collection method of the vulnerability detection program into the original execution logic. The data collection method described is a pre-collected method. When these methods are collected, some tags will be assigned to them, such as being controlled by the outside world, spreading the data content to another data object, filtering html tags and Special symbols, etc. can be filtered. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com